Page 1
SG-500 VP N Security G atew ay U ser's M anual
VPN Security Gateway
SG-500
User’s Manual
Page 2

SG-500 VPN Security Gateway User’s Manual
Copyright
Copyright© 2007 by PLANET Technology Corp. All rights reserved. No part of this publication may be
reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language or computer
language, in any form or by any means, electronic, mechanical, magnetic, optical, chemical, manual or
otherwise, without the prior written permission of PLANET.
PLANET makes no representations or warranties, either expressed or implied, with respect to the contents
hereof and specifically disclaims any warranties, merchantability or fitness for any particular purpose. Any
software described in this manual is sold or licensed "as is". Should the programs prove defective following
their purchase, the buyer (and not this company, its distributor, or its dealer) assumes the entire cost of all
necessary servicing, repair, and any incidental or consequential damages resulting from any defect in the
software. Further, this company reserves the right to revise this publication and to make changes from time
to time in the contents hereof without obligation to notify any person of such revision or changes.
All brand and product names mentioned in this manual are trademarks and/or registered trademarks of their
respective holders.
Disclaimer
PLANET Technology does not warrant that the hardware will work properly in all environments and
applications, and makes no warranty and representation, either implied or expressed, with respect to the
quality, performance, merchantability, or fitness for a particular purpose.
PLANET has made every effort to ensure that this User’s Manual is accurate; PLANET disclaims liability
for any inaccuracies or omissions that may have occurred.
Information in this User’s Manual is subject to change without notice and does not represent a commitment
on the part of PLANET. PLANET assumes no responsibility for any inaccuracies that may be contained in
this User’s Manual. PLANET makes no commitment to update or keep current the information in this User’s
Manual, and reserves the right to make improvements to this User’s Manual and/or to the products described
in this User’s Manual, at any time without notice.
If you find information in this manual that is incorrect, misleading, or incomplete, we would appreciate your
comments and suggestions.
Trademarks
The PLANET logo is a trademark of PLANET Technology.
This documentation may refer to numerous hardware and software products by their trade names. In most, if
not all cases, these designations are claimed as trademarks or registered trademarks by their respective
companies.
CE mark Warning
This is a class B device. In a domestic environment, this product may cause radio interference, in which case
the user may be required to take adequate measures.
Federal Communication Commission Interference Statement
This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to
Part 15 of FCC Rules. These limits are designed to provide reasonable protection against harmful
interference in a residential installation. This equipment generates, uses, and can radiate radio frequency
energy and, if not installed and used in accordance with the instructions, may cause harmful interference to
radio communications. However, there is no guarantee that interference will not occur in a particular
installation. If this equipment does cause harmful interference to radio or television reception, which can
be determined by turning the equipment off and on, the user is encouraged to try to correct the interference
by one or more of the following measures:
1. Reorient or relocate the receiving antenna.
2. Increase the separation between the equipment and receiver.
3. Connect the equipment into an outlet on a circuit different from that to which the receiver is connected.
4. Consult the dealer or an experienced radio technician for help.
Page 3

SG-500 VPN Security Gateway User’s Manual
FCC Caution:
To assure continued compliance (example-use only shielded interface cables when connecting to computer or
peripheral devices). Any changes or modifications not expressly approved by the party responsible for
compliance could void the user’s authority to operate the equipment.
This device complies with Part 15 of the FCC Rules. Operation is subject to the Following two conditions: (1)
This device may not cause harmful interference, and (2) this Device must accept any interference received,
including interference that may cause undesired operation.
R&TTE Compliance Statement
This equipment complies with all the requirements of DIRECTIVE 1999/5/EC OF THE EUROPEAN
PARLIAMENT AND THE COUNCIL OF 9 March 1999 on radio equipment and telecommunication
terminal Equipment and the mutual recognition of their conformity (R&TTE)
The R&TTE Directive repeals and replaces in the directive 98/13/EEC (Telecommunications Terminal
Equipment and Satellite Earth Station Equipment) As of April 8, 2000.
WEEE
To avoid the potential effects on the environment and human health as a result of the presence of
hazardous substances in electrical and electronic equipment, end users of electrical and electronic
equipment should understand the meaning of the crossed-out wheeled bin symbol. Do not dispose
of WEEE as unsorted municipal waste and have to collect such WEEE separately.
Safety
This equipment is designed with the utmost care for the safety of those who install and use it. However,
special attention must be paid to the dangers of electric shock and static electricity when working with
electrical equipment. All guidelines of this and of the computer manufacture must therefore be allowed at all
times to ensure the safe use of the equipment.
Revision
User’s Manual for VPN Security Gateway
Model: SG-500
Rev: 1.0 (July, 2007)
Part No: EM-SG500v1
Page 4

SG-500 VPN Security Gateway User’s Manual
Table of Contents
CHAPTER 1: INTRODUCTION ...................................................................... 1
1.1 FEATURES....................................................................................................................................1
1.2 PACKAGE CONTENTS...................................................................................................................2
1.3 VPN SECURITY GATEWAY TOP VIEW ..........................................................................................2
1.4 VPN SECURITY GATEWAY REAR PANEL......................................................................................2
1.5 SPECIFICATION ............................................................................................................................3
CHAPTER 2: SYSTEM................................................................................... 4
2.1 ADMINISTRATION ........................................................................................................................4
2.2 ADMIN.........................................................................................................................................5
2.3 PERMITTED IPS ...........................................................................................................................8
2.4 LOGOUT ......................................................................................................................................9
2.5 SOFTWARE UPDATE ...................................................................................................................10
2.6 CONFIGURE ...............................................................................................................................11
2.7 SETTINGS ..................................................................................................................................12
2.8 DATE/TIME................................................................................................................................22
2.9 MULTIPLE SUBNET ....................................................................................................................23
2.10 ROUTE TABLE..........................................................................................................................28
2.11 DHCP.....................................................................................................................................32
2.12 DDNS.....................................................................................................................................34
2.13 HOST TABLE............................................................................................................................36
2.14 LANGUAGE..............................................................................................................................37
CHAPTER 3 INTERFACE............................................................................. 38
3.1 INTERFACE ................................................................................................................................39
3.2 LAN..........................................................................................................................................42
3.3 WAN.........................................................................................................................................43
3.4 DMZ.........................................................................................................................................48
CHAPTER 4 POLICY OBJECT..................................................................... 50
4.1 ADDRESS...................................................................................................................................50
4.2 EXAMPLE ..................................................................................................................................53
4.3 SERVICE ....................................................................................................................................60
4.4 CUSTOM ....................................................................................................................................63
4.5 GROUP ......................................................................................................................................67
4.6 SCHEDULE.................................................................................................................................70
4.7 QOS ..........................................................................................................................................73
Page 5

SG-500 VPN Security Gateway User’s Manual
4.8 EXAMPLE ..................................................................................................................................77
4.9 AUTHENTICATION......................................................................................................................79
4.10 EXAMPLE ................................................................................................................................85
4.11 CONTENT BLOCKING...............................................................................................................89
4.12 URL........................................................................................................................................93
4.13 SCRIPT.....................................................................................................................................96
4.14 P2P .........................................................................................................................................98
4.15 IM.........................................................................................................................................100
4.16 DOWNLOAD...........................................................................................................................102
4.17 VIRTUAL SERVER...................................................................................................................104
4.18 EXAMPLE ..............................................................................................................................108
4.19 IPSEC VPN...........................................................................................................................122
CHAPTER 5 POLICY.................................................................................. 223
5.1 POLICY....................................................................................................................................225
5.2 EXAMPLE ................................................................................................................................229
CHAPTER 6 WEB VPN / SSL VPN............................................................ 247
6.1 SETTINGS ................................................................................................................................250
CHAPTER 7 ANOMALY FLOW IP.............................................................. 260
7.1 SETTINGS ................................................................................................................................261
CHAPTER 8 MONITOR.............................................................................. 271
8.1 LOG........................................................................................................................................271
8.2 TRAFFIC LOG...........................................................................................................................273
8.3 EVENT LOG .............................................................................................................................278
8.4 CONNECTION LOG...................................................................................................................281
8.5 LOG BACKUP...........................................................................................................................284
8.6 ACCOUNTING REPORT .............................................................................................................286
8.7 OUTBOUND .............................................................................................................................289
8.8 INBOUND.................................................................................................................................295
8.9 STATISTICS ..............................................................................................................................301
8.10 WAN.....................................................................................................................................303
8.11 POLICY..................................................................................................................................305
8.12 WAKE ON LAN......................................................................................................................307
8.13 STATUS ..................................................................................................................................309
8.14 INTERFACE ............................................................................................................................310
8.15 AUTHENTICATION..................................................................................................................312
8.16 ARP TABLE ...........................................................................................................................313
8.17 DHCP CLIENTS.....................................................................................................................314
Page 6

SG-500 VPN Security Gateway User’s Manual
Chapter 1: Introduction
The innovation of the Internet has created a tremendous worldwide venue for E-business and
information sharing, but it also creates network security issues. New model of Planet’s VPN
Security Gateway SG-500, a special designed of VPN security gateway, provides SSL and IPSec
VPN. The SSL VPN function supports up to 5 SSL VPN connection tunnels. The IPSec VPN
feature provides IKE, SHA-1, and MD5 Authentication. It is specifically designed for SOHO
networks.
The SG-500 provides Content Blocking feature to block specific URL, Script, IM, P2P, and
download file. Also, it is built-in Anomaly Flow IP function. This function supports Hacker and
Blaster Alert. An administrator could use this function to watch and track an attacker. Also, the QoS
function provides Guaranteed Bandwidth and Priority Bandwidth Utilization.
Both the NAT mode and DMZ mode are supported, and therefore can maintain the existing network
infrastructure without reconfiguring. The SG-500 provides policy-based firewall protection and
several hacker protections to prevent hackers’ attack. Besides, the comprehensive alarm and log
function allow the network manager to easily enhance the security of local network.
1.1 Features
z One 10/100Mbps LAN, DMZ, and WAN port
z NAT mode and DMZ mode
z DMZ mode requires no changing for the original network structure
z The VPN security gateway supports SSL VPN and IPSec VPN. The SSL VPN function
supports up to 5 SSL VPN connection tunnels. The IPSec VPN has DES, 3DES, and AES
encryption and SHA-1 / MD5 authentication. The network traffic over public Internet is
secured.
z Traffic classification based on IP, IP range/subnet, and TCP/UDP port range
z Guaranteed and maximum bandwidth with three levels of priorities
z Policy-based bandwidth management
z Assign daily and weekly access schedule to each individual policy
z Professional Monitor function includes Log, Accounting Report, Statistics, and Status
z MRTG-like Traffic Statistics, easy to trace and analyze
z Multi-Servers Load Balancing
z Dynamic DNS and DHCP server functions
z Content Filter includes URL, Script, P2P, IM, and Download blocking
z Hacker Alert and Anomaly Flow Detection
z Virtual Server and IP mapping (Multi-DMZ Host)
z Multi-language Web UI and easy to manage
z User authentication based on user name and password
- 1 -
Page 7
SG-500 VPN Security Gateway User’s Manual
1.2 Package Contents
The following items should be included:
♦ VPN Security Gateway
♦ Power Adapter
♦ Quick Installation Guide
♦ User’s Manual CD
♦ RJ-45 cable
♦ Wall-mount kit
If any of the contents are missing or damaged, please contact your dealer or distributor immediately.
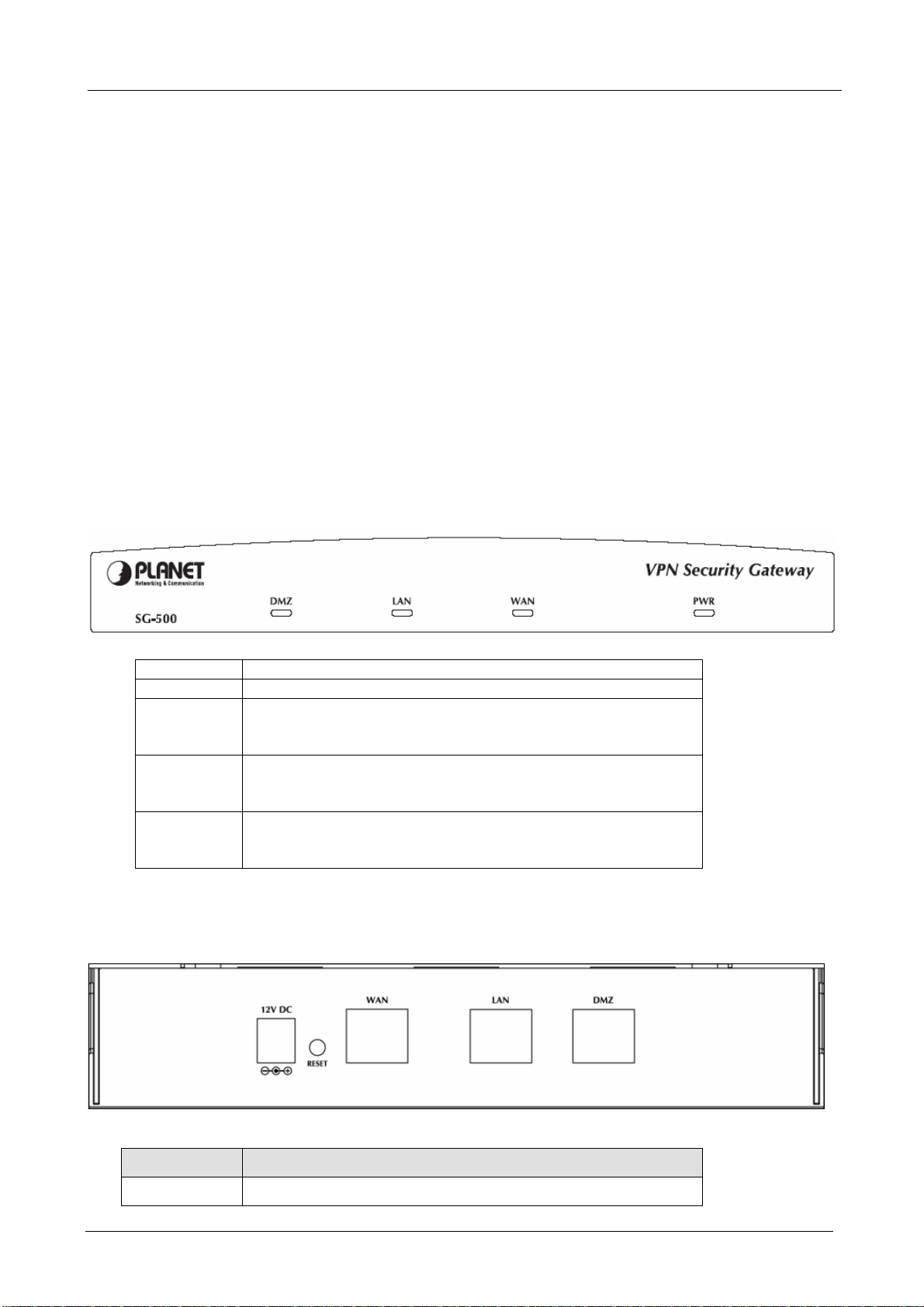
1.3 VPN Security Gateway Top View
LED Description
PWR Power is supplied to this device.
WAN Steady on indicates the port is connected to other network
device.
Blink to indicates there is traffic on the port
LAN Steady on indicates the port is connected to other network
device.
Blink to indicates there is traffic on the port
DMZ Steady on indicates the port is connected to other network
device.
Blink to indicates there is traffic on the port
1.4 VPN Security Gateway Rear Panel
Port or button Description
Power 12V DC, 1.5A
- 2 -
Page 8
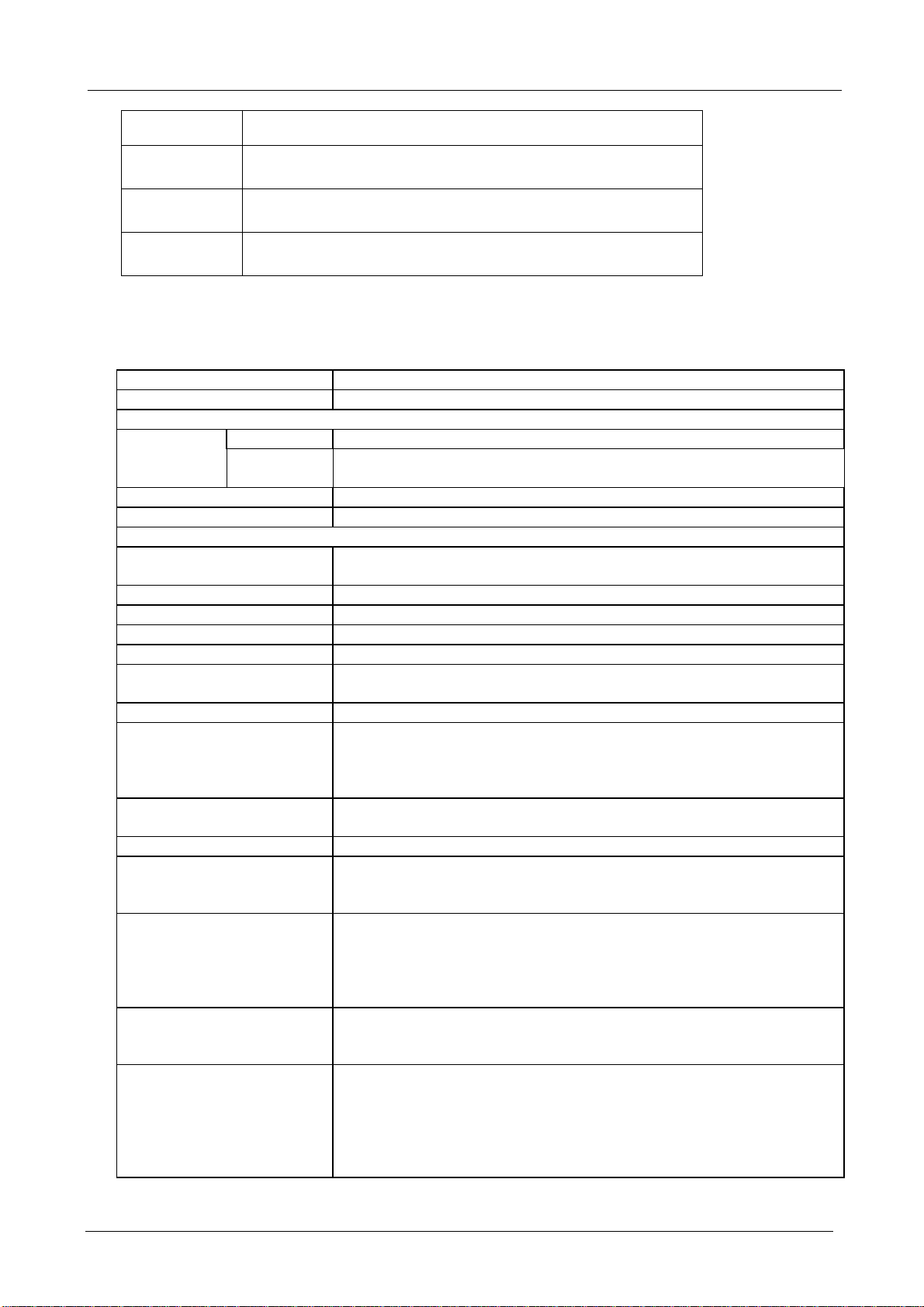
SG-500 VPN Security Gateway User’s Manual
RESET
WAN
Press this button to restore to factory default settings.
Connect to your xDSL/Cable modem or other Internet
connection device
LAN
Connect to your local PC, switch, or other local network
device
DMZ
Connect to your local PC, switch, or other local network
device
1.5 Specification
Product VPN Security Gateway
Model SG-500
Hardware
WAN 1 x 10/100Base-TX Connections
LAN
DMZ
Button Reset button for hardware reset / factory default
System LED PWR, WAN, LAN, DMZ
Software
Maximum Controlled
Concurrent Session
New Session / Second 1,000
SSL VPN Tunnels Up to 5 tunnels
Management Web (English, Traditional Chinese, Simplified Chinese)
Operation Mode DMZ_NAT, DMZ_Transparent, NAT
WAN connection type in
NAT mode
Traffic Classification IP, IP subnet, and TCP/UDP port
Bandwidth Allocation Policy rules with Inbound/Outbound traffic management
Log Traffic Log, Event Log, Connection Log, Log backup by mail or
Statistics WAN port statistics and policy statistics with graph display
Firewall Security Policy-based access control
Hacker Alert and
Anomaly Flow Detection
Alarm Traffic alarm for user-defined traffic level
Other Functions Firmware Upgradeable through Web
1 x 10/100Base-TX, Auto-MDI/MDI-X
1 x 10/100Base-TX, Auto-MDI/MDI-X
20,000
PPPoE, DHCP, and Fixed IP
Guaranteed and maximum bandwidth
Scheduled in unit of 30 minutes
3 Priorities
syslog server
Stateful Packet Inspection (SPI)
Scheduled in unit of 30 minutes
Detect SYN Attack, Detect ICMP Flood, Detect UDP Flood,
Detect Ping of Death Attack, Detect Tear Drop Attack, Detect IP
Spoofing Attack, Filter IP Route Option, Detect Port Scan Attack,
Detect Land Attack, Virus-Infected Blocking, E-Mail Alert
Notification, NetBIOS Notification
Event alarm for hacker attack
The alarm message can sent to administrator by e-mail
NTP support
Configuration Backup and Restore through Web
Dynamic DNS support
Multiple NAT and multiple DMZ (mapped IP) support
Multiple server load balancing
- 3 -
Page 9

SG-500 VPN Security Gateway User’s Manual
Chapter 2: System
2.1 Administration
“System” is the managing of settings such as the privileges of packets that pass through the SG-500
and monitoring controls. The System Administrators can manage, monitor, and configure SG-500
settings. But all configurations are “read-only” for all users other than the System Administrator;
those users are not able to change any setting of the SG-500.
- 4 -
Page 10

SG-500 VPN Security Gateway User’s Manual
2.2 Admin
Define the required fields of Administrator
Administrator Name:
The user name of Administrators and Sub Administrator for the SG-500. The admin user name
cannot be removed; and the sub-admin user can be removed or configure.
The default Account: admin; Password: admin
Privilege:
The privileges of Administrators (Admin or Sub Admin). The user name of the main
Administrator is Administrator with reading / writing privilege. Administrator also can
change the system setting, log system status, and to increase or delete sub-administrator.
Sub-Admin may be created by the Admin by clicking
New Sub Admin
. Sub Admin have
only read and monitor privilege and cannot change any system setting value.
Configure:
Click Modify to change the “Sub-Administrator’s” password or click Remove to delete a “Sub
Administrator.”
- 5 -
Page 11

SG-500 VPN Security Gateway User’s Manual
Adding a new Sub Administrator
STEP 1﹒In the Admin Web UI, click the New Sub Admin button to create a new Sub
Administrator.
STEP 2﹒In the Add New Sub Administrator Web UI and enter the following setting:
Sub Admin Name: sub_admin
Password: 12345
Confirm Password: 12345
STEP 3﹒Click OK to add the user or click Cancel to cancel it.
Add New Sub Admin
- 6 -
Page 12

SG-500 VPN Security Gateway User’s Manual
Modify the Administrator’s Password
STEP 1﹒In the Admin Web UI, locate the Administrator name you want to edit, and click on
Modify in the ConFigure field.
STEP 2﹒The Modify Administrator Password Web UI will appear. Enter the following
information:
Password: admin
New Password: 52364
Confirm Password: 52364
STEP 3﹒Click OK to confirm password change.
Modify Admin Password
- 7 -
Page 13

SG-500 VPN Security Gateway User’s Manual
2.3 Permitted IPs
STEP 1﹒Add the following setting in Permitted IPs of Administration:
Name: Enter master
IP Address: Enter 163.173.56.11
Netmask: Enter 255.255.255.255
Service: Select Ping and HTTP
Click OK
Complete add new permitted IPs
Setting Permitted IPs Web UI
Complete Add New Permitted IPs
To make Permitted IPs be effective, it must cancel the Ping and We b U I selection in the Web UI of
SG-500 that Administrator enter. (LAN, WAN, or DMZ Interface)
Before canceling the Web U I selection of Interface, must set up the Permitted IPs first, otherwise, it wou ld
cause the situation of cannot enter Web UI by appointed Interface.
- 8 -
Page 14

SG-500 VPN Security Gateway User’s Manual
2.4 Logout
STEP 1﹒Click Logout in System to protect the system while Administrator is away.
Confirm Logout Web UI
STEP 2﹒Click OK and the logout message will appear in Web UI.
Logout Web UI Message
- 9 -
Page 15

SG-500 VPN Security Gateway User’s Manual
2.5 Software Update
STEP 1﹒Select Software Update in System, and follow the steps below:
To obtain the version number from Version Number and obtain the latest version
from Internet. And save the latest version in the hardware of the PC, which manage
the SG-500
Click Browse and choose the latest software version file.
Click OK and the system will update automatically.
Software Update
It takes 3 minutes to update software. The system will reboot after update. During the updating time,
please don’t turn off the PC or leave the Web UI. It may cause some unexpected mistakes. (Strong suggests
updating the software from LAN to avoid unexpected mistakes.)
- 10 -
Page 16

SG-500 VPN Security Gateway User’s Manual
2.6 Configure
The Configure is according to the basic setting of the SG-500. In this section the definition is
Setting, Date/Time, Multiple Subnet, Route Table, DHCP, Dynamic DNS, Hosts Table, and
Language settings.
- 11 -
Page 17

SG-500 VPN Security Gateway User’s Manual
2.7 Settings
SG-500 Configuration:
The Administrator can import or export the system settings. Click OK to import the file into
the SG-500 or click Cancel to cancel importing. You also can revive to default value here.
Email Settings:
Select Enable E-mail Alert Notification under E-mail Settings. This function will enable the
SG-500 to send e-mail alerts to the System Administrator when the network is being attacked
by hackers or when emergency conditions occur. (It can be set from SettingsAnomaly Flow IP in System to detect Anomaly Flow Attacks)
Web Management (WAN Interface):
The System Manager can change the port number used by HTTP port anytime. (Remote Web
UI management)
After HTTP port has changed, if the administrator wants to enter Web UI from WAN, he will have to
change the port number of browser (For example: http://61.62.108.172:8080).
MTU Setting:
It provides the Administrator to modify the networking package length anytime. Its default
value is 1500 Bytes.
- 12 -
Page 18

SG-500 VPN Security Gateway User’s Manual
Dynamic Routing (RIPv2)
By enable LAN, WAN, or DMZ Port to send and receive RIPv2 packets, the SG-500 appliance
can communicate with internal or external routers and dynamically update the route table (The
MIS engineers can set up routing information update timer and routing information timeout
when it stop to receive the RIPv2 packets and the router will automatically cancel the dynamic
routing table).
SIP protocol pass-through:
When user use VoIP or Video Conference has abnormally situation, can use this function to
resolve this problem.
Administration Packet Logging:
After enable this function; the SG-500 will record packet which source IP or destination
address is SG-500. And record in Traffic Log for System Manager to inquire about.
Define the required fields of Time Settings
Synchronize Time/Date:
Synchronizing the SG-500 with the System Clock. The administrator can configure the
SG-500’s date and time by either syncing to an Internet Network Time Server (NTP) or by
syncing to your computer’s clock.
GMT:
International Standard Time (Greenwich Mean Time)
Daylight saving time setting:
When user live in the time zone implement daylight saving time, during this time unit will
adjust system time as the local time.
- 13 -
Page 19

SG-500 VPN Security Gateway User’s Manual
Define the required fields of Multiple Subnet
Forwarding Mode:
To display the mode that Multiple Subnet use. (NAT mode or Routing Mode)
WAN Interface Address:
The IP address that Multiple Subnet corresponds to WAN.
LAN Interface Address/Subnet Netmask:
The Multiple Subnet range.
- 14 -
Page 20

SG-500 VPN Security Gateway User’s Manual
NAT Mode:
It allows Internal Network to set multiple subnet address and connect with the Internet through
different WAN IP Addresses. For example, the lease line of a company applies several real IP
Addresses 168.85.88.0/24. The company is divided into R&D department, service, sales
department, procurement department, and accounting department. The company can
distinguish each department by different subnet for the purpose of managing conveniently. The
settings are as the following:
1. R&D department subnet:192.168.1.1/24 (LAN) ÅÆ 168.85.88.253 (WAN)
2. Service department subnet: 192.168.2.1/24 (LAN) ÅÆ 168.85.88.252 (WAN)
3. Sales department subnet: 192.168.3.1/24 (LAN) ÅÆ 168.85.88.251 (WAN)
4. Procurement department subnet
192.168.4.1/24 (LAN) ÅÆ 168.85.88.250(WAN)
5. Accounting department subnet
192.168.5.1/24 (LAN) ÅÆ 168.85.88.249(WAN)
The first department (R&D department) had set while setting interface IP; the other four ones have
to be added in Multiple Subnet. After completing the settings, each department uses the different
WAN IP Address to connect to the Internet. The settings of each department are as following:
Service Sales Procurement Accounting
IP Address 192.168.2.2~254 192.168.3.2~254 192.168.4.2~254 192.168.5.2~254
Subnet Netmask 255.255.255.0 255.255.255.0 255.255.255.0 255.255.255.0
Gateway 192.168.2.1 192.168.3.1 192.168.4.1 192.168.5.1
Routing Mode:
It is the same as NAT mode approximately but does not have to correspond to the real WAN IP
address, which let internal PC to access to Internet by its own IP (External user also can use the
IP to connect with the Internet).
- 15 -
Page 21

Define the required fields of DHCP
Subnet:
The domain name of LAN
Netmask:
The LAN Netmask
Gateway:
The default Gateway IP address of LAN
Broadcast IP:
The Broadcast IP of LAN
Define the required fields of DDNS
SG-500 VPN Security Gateway User’s Manual
Domain Name:
The domain name that provided by DDNS
WAN IP Address:
The WAN IP Address, which the domain name corresponds to.
Define the required fields of Host Table
Domain Name:
It can be set by System Manager. To let the internal user to access to the information that
provided by the host by this domain name
Virtual IP Address:
The virtual IP address respective to Host Table. It must be LAN or DMZ IP address.
- 16 -
Page 22

SG-500 VPN Security Gateway User’s Manual
System Settings- Exporting
STEP 1﹒In System Setting Web UI, click on button next to Export System Settings to Client.
STEP 2﹒When the File Download pop-up window appears, choose the destination place where to
save the exported file and click on Save. The setting value of SG-500 will copy to the
appointed site instantly.
Select the Destination Place to Save the Exported File
- 17 -
Page 23

SG-500 VPN Security Gateway User’s Manual
System Settings- Importing
STEP 1﹒In System Setting Web UI, click on the Browse button next to Import System Settings
from Client. When the Choose File pop-up window appears, select the file to which
contains the saved SG-500 Settings, then click OK.
STEP 2﹒Click OK to import the file into the SG-500
Enter the File Name and Destination of the Imported File
Upload the Setting File Web UI
- 18 -
Page 24

SG-500 VPN Security Gateway User’s Manual
Restoring Factory Default Settings
STEP 1﹒Select Reset Factory Settings in SG-500 Configuration Web UI
STEP 2﹒Click OK at the bottom-right of the page to restore the factory settings.
Reset Factory Settings
Enabling E-mail Alert Notification
STEP 1﹒Device Name: Enter the Device Name or use the default value.
STEP 2﹒Select Enable E-mail Alert Notification under E-Mail Settings.
- 19 -
Page 25

SG-500 VPN Security Gateway User’s Manual
STEP 3﹒Sender Address: Enter the Sender Address. (Required by some ISPs.)
STEP 4﹒SMTP Server IP: Enter SMTP server’s IP address.
STEP 5﹒E-Mail Address 1: Enter the e-mail address of the first user to be notified.
STEP 6﹒E-Mail Address 2: Enter the e-mail address of the second user to be notified. (Optional)
STEP 7﹒Click OK on the bottom-right of the screen to enable E-mail Alert Notification.
Enable E-mail Alert Notification
Click on Mail Test to test if E-mail Address 1 and E-mail Address 2 can receive the Alert Notification
correctly.
- 20 -
Page 26

SG-500 VPN Security Gateway User’s Manual
Reboot SG-500
STEP 1﹒Reboot SG-500:Click Reboot button next to Reboot SG-500 Appliance.
STEP 2﹒A confirmation pop-up page will appear.
STEP 3﹒Follow the confirmation pop-up page; click OK to restart SG-500.
Reboot SG-500
- 21 -
Page 27

SG-500 VPN Security Gateway User’s Manual
2.8 Date/Time
STEP 1﹒Select Enable synchronize with an Internet time Server.
STEP 2﹒Click the down arrow to select the offset time from GMT.
STEP 3﹒Enter the Server IP / Name with which you want to synchronize.
STEP 4﹒Set the interval time to synchronize with outside servers.
System Time Setting
Click on the Sync button and then the SG-500’s date and time will be synchronized to the
Administrator’s PC
The value of Set Offset From GMT and Server IP / Name can be looking for from Assist.
If the local area executes the daylight saving time, then enable the daylight saving time setting.
- 22 -
Page 28

SG-500 VPN Security Gateway User’s Manual
2.9 Multiple Subnet
Connect to the Internet through Multiple Subnet NAT or Routing Mode by the IP address that set by
the LAN user’s network card.
Preparation
To connect the Internet, WAN IP (211.22.22.22) connects with ATUR.
- 23 -
Page 29

SG-500 VPN Security Gateway User’s Manual
Adding Multiple Subnet
Add the following settings in Multiple Subnet of System function:
Click on New Entry
Alias IP of LAN Interface: Enter 172.16.30.1
Netmask:Enter 255.255.255.0
WAN:Enter Interface IP211.22.22.22, and choose NAT in Forwarding Mode
Click OK
Complete Adding Multiple Subnet
Add Multiple Subnet Web UI
- 24 -
Page 30

SG-500 VPN Security Gateway User’s Manual
WAN Interface can use Assist to enter the data.
After setting, there will be two subnets in LAN: 192.168.1.0/24 (default LAN subnet) and
172.16.30.0/24. So if LAN IP is:
192.168.1.xx, it must use NAT Mode to connect to the Internet.
162.172.50.xx, it’s also use NAT mode through WAN (The Internet Server can see your WAN IP directly).
The SG-500’s Interface Status:
WAN IP:211.22.22.22
LAN Port IP:192.168.1.1
LAN Port Multiple Subnet:172.16.30.1
Multiple Subnet Network
- 25 -
Page 31

SG-500 VPN Security Gateway User’s Manual
WAN IP (10.10.10.1) connects to the Router of ISP (10.10.10.2) directly. The IP address provided
by ISP is 162.172.50.0/24
Add the following settings in Multiple Subnet of System function:
Click on New Entry
Alias IP of LAN Interface: Enter 162.172.50.1
Netmask:Enter 255.255.255.0
WAN:Enter Interface IP: 10.10.10.1, and choose Routing in Forwarding Mode
Click OK
Complete Adding Multiple Subnet
Multiple Subnet Web UI Setting
After setting, if LAN IP of SG-500 is 162.172.50.xx, it uses Routing Mode (Internet Server can see
your IP 162.172.50.xx directly)
- 26 -
Page 32

SG-500 VPN Security Gateway User’s Manual
The SG-500’s Interface Status:
WAN IP:10.10.10.1
LAN Port IP:192.168.1.1
LAN Port Multiple Subnet:162.172.50.1
Multiple Subnet Network
- 27 -
Page 33

SG-500 VPN Security Gateway User’s Manual
2.10 Route Table
To connect two different subnet router with the SG-500 and makes them to
connect to Internet through SG-500.
Preparation
Company A: WAN (61.11.11.11) connects with ATUR to Internet
LAN subnet: 192.168.1.1/24
The Router1 which connect with LAN (10.10.10.1, support RIPv2) its LAN subnet
is 192.168.10.1/24
Company B: Router2 (10.10.10.2, support RIPv2), its LAN subnet is 192.168.20.1/24
Company A‘s Router1 (10.10.10.1) connect directly with Company B‘s Router2 (10.10.10.2).
- 28 -
Page 34

SG-500 VPN Security Gateway User’s Manual
STEP 1﹒Enter the following settings in Route Table in System function:
Destination IP: Enter 192.168.10.1
Netmask: Enter 255.255.255.0。
Gateway: Enter 192.168.1.252
Interface: Select LAN
Click OK
Add New Static Route1
STEP 2﹒Enter the following settings in Route Table in System function:
Destination IP: Enter 192.168.20.1
Netmask: Enter 255.255.255.0
Gateway: Enter 192.168.1.252
Interface: Select LAN
Click OK
Add New Static Route2
- 29 -
Page 35

SG-500 VPN Security Gateway User’s Manual
STEP 3﹒Enter the following setting in Route Table in System function:
Destination IP: Enter 10.10.10.0
Netmask: Enter 255.255.255.0
Gateway: Enter 192.168.1.252
Interface: Select LAN
Click OK
Add New Static Route3
- 30 -
Page 36

SG-500 VPN Security Gateway User’s Manual
STEP 4﹒Adding successful. At this time the computer of 192.168.10.1/24, 192.168.20.1/24 and
192.168.1.1/24 can connect with each other and connect to Internet by NAT.
Route Table Setting
- 31 -
Page 37

SG-500 VPN Security Gateway User’s Manual
2.11 DHCP
STEP 1﹒Select DHCP in System and enter the following settings:
Domain Name:Enter the Domain Name
DNS Server 1: Enter the distributed IP address of DNS Server1.
DNS Server 2: Enter the distributed IP address of DNS Server2.
WINS Server 1: Enter the distributed IP address of WINS Server1.
WINS Server 2: Enter the distributed IP address of WINS Server2.
LAN Interface:
Client IP Address Range 1: Enter the starting and the ending IP address
dynamically assigning to DHCP clients. The default value is 192.168.1.2 to
192.168.1.254 (it must be in the same subnet)
Client IP Address Range 2: Enter the starting and the ending IP address
dynamically assigning to DHCP clients. But it must in the same subnet as
Client IP Address Range 1 and the range cannot be repeated.
DMZ Interface: the same as LAN Interface. (DMZ works only if to enable DMZ
Interface)
Leased Time: Enter the leased time for Dynamic IP. The default time is 24 hours.
Click OK and DHCP setting is completed.
- 32 -
Page 38

SG-500 VPN Security Gateway User’s Manual
DHCP Web UI
When selecting Automatically Get DNS, the DNS Server will lock it as LAN Interface IP. (Using
Occasion: When the system Administrator starts Authentication, the users’ first DNS Server must be the
same as LAN Interface IP in order to enter Authentication Web UI)
- 33 -
Page 39

SG-500 VPN Security Gateway User’s Manual
2.12 DDNS
STEP 1﹒Select Dynamic DNS in System function. Click New Entry button
Service providers:Select service providers.
Automatically fill in the WAN IP:Check to automatically fill in the WAN IP.。
User Name:Enter the registered user name.
Password:Enter the password
Domain name:Enter Your host domain name
Click OK to add Dynamic DNS.
DDNS Web UI
Complete DDNS Setting
- 34 -
Page 40

SG-500 VPN Security Gateway User’s Manual
Chart
Meaning Update
successfully
Incorrect
username or
Connecting
to server
Unknown error
password
If System Administrator had not registered a DDNS account, click on Sign up then can enter the
website of the provider.
If you do not select Automatically fill in the WAN IP and then you can enter a specific IP in WAN
IP. Let DDNS to correspond to that specific IP address.
- 35 -
 Loading...
Loading...