Page 1

Avid® iNEWS
Administration Guide
®
Page 2

Legal Notices
Product specifications are subject to change without notice and do not represent a commitment on the part of Avid
Technology, Inc.
The software described in this document is furnished under a license agreement. You can obtain a copy of that license by
visiting Avid's Web site at www.avid.com. The terms of that license are also available in the product in the same directory as
the software. The software may not be reverse assembled and may be used or copied only in accordance with the terms of the
license agreement. It is against the law to copy the software on any medium except as specifically allowed in the license
agreement.
Avid products or portions thereof are protected by one or more of the following United States Patents: 4,970,663; 5,267,351;
5,309,528; 5,355,450; 5,396,594; 5,440,348; 5,467,288; 5,513,375; 5,528,310; 5,557,423; 5,577,190; 5,584,006; 5,640,601;
5,644,364; 5,654,737; 5,715,018; 5,719,570; 5,724,605; 5,726,717; 5,729,673; 5,745,637; 5,752,029; 5,754,851; 5,799,150;
5,812,216; 5,828,678; 5,842,014; 5,852,435; 5,999,406; 6,038,573; 6,061,758; 6,141,007; 6,211,869; 6,532,043; 6,546,190;
6,596,031; 6,636,869; 6,747,705; 6,763,523; 6,766,357; 6,813,622; 6,847,373; 7,081,900; RE40,107; 7,403,561; 7,433,519;
D352,278; D372,478; D373,778; D392,267; D392,268; D392,269; D395,291; D396,853; D398,912.
Other patents are pending.
This document is protected under copyright law. An authorized licensee of Avid iNEWS Command may reproduce this
publication for the licensee’s own use in learning how to use the software. This document may not be reproduced or
distributed, in whole or in part, for commercial purposes, such as selling copies of this document or providing support or
educational services to others. This document is supplied as a guide for Avid iNEWS Command. Reasonable care has been
taken in preparing the information it contains. However, this document may contain omissions, technical inaccuracies, or
typographical errors. Avid Technology, Inc. does not accept responsibility of any kind for customers’ losses due to the use of
this document. Product specifications are subject to change without notice.
Copyright © 2010 Avid Technology, Inc. and its licensors. All rights reserved.
The following disclaimer is required by Apple Computer, Inc.:
APPLE COMPUTER, INC. MAKES NO WARRANTIES WHATSOEVER, EITHER EXPRESS OR IMPLIED, REGARDING
THIS PRODUCT, INCLUDING WARRANTIES WITH RESPECT TO ITS MERCHANTABILITY OR ITS FITNESS FOR ANY
PARTICULAR PURPOSE. THE EXCLUSION OF IMPLIED WARRANTIES IS NOT PERMITTED BY SOME STATES. THE
ABOVE EXCLUSION MAY NOT APPLY TO YOU. THIS WARRANTY PROVIDES YOU WITH SPECIFIC LEGAL RIGHTS.
THERE MAY BE OTHER RIGHTS THAT YOU MAY HAVE WHICH VARY FROM STATE TO STATE.
The following disclaimer is required by Sam Leffler and Silicon Graphics, Inc. for the use of their TIFF library:
Copyright © 1988–1997 Sam Leffler
Copyright © 1991–1997 Silicon Graphics, Inc.
Permission to use, copy, modify, distribute, and sell this software [i.e., the TIFF library] and its documentation for any purpose
is hereby granted without fee, provided that (i) the above copyright notices and this permission notice appear in all copies of
the software and related documentation, and (ii) the names of Sam Leffler and Silicon Graphics may not be used in any
advertising or publicity relating to the software without the specific, prior written permission of Sam Leffler and Silicon
Graphics.
THE SOFTWARE IS PROVIDED “AS-IS” AND WITHOUT WARRANTY OF ANY KIND, EXPRESS, IMPLIED OR
OTHERWISE, INCLUDING WITHOUT LIMITATION, ANY WARRANTY OF MERCHANTABILITY OR FITNESS FOR A
PARTICULAR PURPOSE.
IN NO EVENT SHALL SAM LEFFLER OR SILICON GRAPHICS BE LIABLE FOR ANY SPECIAL, INCIDENTAL, INDIRECT
OR CONSEQUENTIAL DAMAGES OF ANY KIND, OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER OR NOT ADVISED OF THE POSSIBILITY OF DAMAGE, AND ON ANY THEORY OF
LIABILITY, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
The following disclaimer is required by the Independent JPEG Group:
This software is based in part on the work of the Independent JPEG Group.
This Software may contain components licensed under the following conditions:
Copyright (c) 1989 The Regents of the University of California. All rights reserved.
2
Page 3

Redistribution and use in source and binary forms are permitted provided that the above copyright notice and this paragraph
are duplicated in all such forms and that any documentation, advertising materials, and other materials related to such
distribution and use acknowledge that the software was developed by the University of California, Berkeley. The name of the
University may not be used to endorse or promote products derived from this software without specific prior written
permission. THIS SOFTWARE IS PROVIDED ``AS IS'' AND WITHOUT ANY EXPRESS OR IMPLIED WARRANTIES,
INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE.
Copyright (C) 1989, 1991 by Jef Poskanzer.
Permission to use, copy, modify, and distribute this software and its documentation for any purpose and without fee is hereby
granted, provided that the above copyright notice appear in all copies and that both that copyright notice and this permission
notice appear in supporting documentation. This software is provided "as is" without express or implied warranty.
Copyright 1995, Trinity College Computing Center. Written by David Chappell.
Permission to use, copy, modify, and distribute this software and its documentation for any purpose and without fee is hereby
granted, provided that the above copyright notice appear in all copies and that both that copyright notice and this permission
notice appear in supporting documentation. This software is provided "as is" without express or implied warranty.
Copyright 1996 Daniel Dardailler.
Permission to use, copy, modify, distribute, and sell this software for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that copyright notice and this permission notice appear in
supporting documentation, and that the name of Daniel Dardailler not be used in advertising or publicity pertaining to
distribution of the software without specific, written prior permission. Daniel Dardailler makes no representations about the
suitability of this software for any purpose. It is provided "as is" without express or implied warranty.
Modifications Copyright 1999 Matt Koss, under the same license as above.
Copyright (c) 1991 by AT&T.
Permission to use, copy, modify, and distribute this software for any purpose without fee is hereby granted, provided that this
entire notice is included in all copies of any software which is or includes a copy or modification of this software and in all
copies of the supporting documentation for such software.
THIS SOFTWARE IS BEING PROVIDED "AS IS", WITHOUT ANY EXPRESS OR IMPLIED WARRANTY. IN PARTICULAR,
NEITHER THE AUTHOR NOR AT&T MAKES ANY REPRESENTATION OR WARRANTY OF ANY KIND CONCERNING THE
MERCHANTABILITY OF THIS SOFTWARE OR ITS FITNESS FOR ANY PARTICULAR PURPOSE.
This product includes software developed by the University of California, Berkeley and its contributors.
The following disclaimer is required by Nexidia Inc.:
© 2006 Nexidia. All rights reserved.
Manufactured under license from the Georgia Tech Research Corporation, U.S.A. Patent Pending.
The following disclaimer is required by Paradigm Matrix:
Portions of this software licensed from Paradigm Matrix.
The following disclaimer is required by Ray Sauers Associates, Inc.:
“Install-It” is licensed from Ray Sauers Associates, Inc. End-User is prohibited from taking any action to derive a source code
equivalent of “Install-It,” including by reverse assembly or reverse compilation, Ray Sauers Associates, Inc. shall in no event be
liable for any damages resulting from reseller’s failure to perform reseller’s obligation; or any damages arising from use or
operation of reseller’s products or the software; or any other damages, including but not limited to, incidental, direct, indirect,
special or consequential Damages including lost profits, or damages resulting from loss of use or inability to use reseller’s
products or the software for any reason including copyright or patent infringement, or lost data, even if Ray Sauers Associates
has been advised, knew or should have known of the possibility of such damages.
The following disclaimer is required by Videomedia, Inc.:
“Videomedia, Inc. makes no warranties whatsoever, either express or implied, regarding this product, including warranties with
respect to its merchantability or its fitness for any particular purpose.”
“This software contains V-LAN ver. 3.0 Command Protocols which communicate with V-LAN ver. 3.0 products developed by
Videomedia, Inc. and V-LAN ver. 3.0 compatible products developed by third parties under license from Videomedia, Inc. Use
of this software will allow “frame accurate” editing control of applicable videotape recorder decks, videodisc recorders/players
and the like.”
3
Page 4

The following disclaimer is required by Altura Software, Inc. for the use of its Mac2Win software and Sample
Source Code:
©1993–1998 Altura Software, Inc.
The following disclaimer is required by Ultimatte Corporation:
Certain real-time compositing capabilities are provided under a license of such technology from Ultimatte Corporation and are
subject to copyright protection.
The following disclaimer is required by 3Prong.com Inc.:
Certain waveform and vector monitoring capabilities are provided under a license from 3Prong.com Inc.
The following disclaimer is required by Interplay Entertainment Corp.:
The “Interplay” name is used with the permission of Interplay Entertainment Corp., which bears no responsibility for Avid
products.
This product includes portions of the Alloy Look & Feel software from Incors GmbH.
This product includes software developed by the Apache Software Foundation (http://www.apache.org/).
© DevelopMentor
This product may include the JCifs library, for which the following notice applies:
JCifs © Copyright 2004, The JCIFS Project, is licensed under LGPL (http://jcifs.samba.org/). See the LGPL.txt file in the Third
Party Software directory on the installation CD.
Avid Interplay contains components licensed from LavanTech. These components may only be used as part of and in
connection with Avid Interplay.
Attn. Government User(s). Restricted Rights Legend
U.S. GOVERNMENT RESTRICTED RIGHTS. This Software and its documentation are “commercial computer software” or
“commercial computer software documentation.” In the event that such Software or documentation is acquired by or on behalf
of a unit or agency of the U.S. Government, all rights with respect to this Software and documentation are subject to the terms
of the License Agreement, pursuant to FAR §12.212(a) and/or DFARS §227.7202-1(a), as applicable.
Trademarks
003, 192 Digital I/O, 192XD I/O, 888 I/O, Adrenaline, AirPlay, AirSPACE, AirSPACE HD, AirSpeed, ALEX, Alienbrain, AniMatte,
AudioMarket, AudioPages, AudioSuite, AudioVision, AutoSync, Avid, Avid Advanced Response, Avid DNA, Avid DNxcel,
Avid DNxHD, AVIDdrive, Avid DS Assist Station, Avid EditStar, Avid Learning Excellerator, Avid Liquid,
Avid Liquid Chrome Xe, Avid MEDIArray, Avid Mojo, AvidNet, AvidNetwork, Avid NewStar, Avid Remote Response,
AVIDstripe, Avid Unity, Avid Unity ISIS, Avid VideoRAID, Avid Xpress, AVoption, AVX, Beauty Without The Bandwidth,
Blacktooth, Boom, C|24, CamCutter, CaptureManager, ChromaCurve, ChromaWheel, Command|24, Conectiv, CountDown,
DAE, Dazzle, Dazzle Digital Video Creator, Deko, DekoCast, D-Fi, D-fx, DigiDelivery, Digidesign, Digidesign Audio Engine,
Digidesign Intelligent Noise Reduction, DigiDrive, DigiLink, DigiMeter, DigiSerial, Digital Nonlinear Accelerator, DigiTranslator,
DINR, DNxchange, do more, DVD Complete, D-Verb, Eleven, Equinox, EveryPhase, ExpertRender, Fastbreak, Fast Track,
FieldPak, Film Composer, FilmScribe, Flexevent, FluidMotion, FXDeko, G7, G-Rack, HD Core, HD Process, HDPack,
Hollywood DV-Bridge, Hybrid, HyperControl, HyperSPACE, HyperSPACE HDCAM, IllusionFX, Image Independence, iNEWS,
iNEWS Assign, iNEWS ControlAir, Instantwrite, Instinct, Intelli-sat Broadcasting Recording Manager, Intelli-Sat, InterFX,
Interplay, inTONE, Intraframe, iS9, iS18, iS23, iS36, ISIS, IsoSync, KeyRig, KeyStudio, LaunchPad, LeaderPlus, Lightning,
ListSync, Lo-Fi, Magic Mask, Make Anything Hollywood, make manage move | media, Marquee, M-Audio, M-Audio Micro,
Maxim, Mbox, MCXpress, Media Browse, Media Composer, MediaDock, MediaDock Shuttle, Media Fusion, Media Illusion,
MediaLog, Media Reader, Media Recorder, MEDIArray, MediaShare, MediaStream, Media Suite, Meridien, MetaFuze,
MetaSync, MicroTrack, Midiman, MissionControl, Mix Rack, MixLab, Moviebox, Moviestar, NaturalMatch, Nearchive,
NetReview, NewsCutter, Nitris, NRV-10 interFX, Octane, OMF, OMF Interchange, OMM, OnDVD, Open Media Framework,
Open Media Management, Palladium, Pinnacle, Pinnacle DistanTV, Pinnacle Geniebox, Pinnacle HomeMusic,
Pinnacle MediaSuite, Pinnacle Mobile Media, Pinnacle PCTV, Pinnacle PCTV HD Ultimate Stick, Pinnacle PCTV Nano Stick,
Pinnacle PCTV To Go, Pinnacle Scorefitter, Pinnacle Studio, Pinnacle Studio MovieBoard, Pinnacle Systems, Pinnacle
VideoSpin, ProEncode, ProServices, ProSessions, Pro Tools, QuietDrive, Recti-Fi, Reel Tape Delay, Reel Tape Flanger,
Reel Tape Saturation, RetroLoop, rS9, rS18, Salesview, Sci-Fi, Scorch, Scorefitter, ScriptSync,
SecureProductionEnvironment, Session, Show Center, Sibelius, SIDON, Soft SampleCell, Soft-Clip Limiter,
Sound Designer II, SPACE, SPACEShift, SpectraGraph, SpectraMatte, Starplay, SteadyGlide, Streamfactory, Streamgenie,
StreamRAID, Strike, Structure, Studiophile, SubCap, Sundance Digital, Sundance, Symphony, SYNC HD, SynchroScience,
4
Page 5

SynchroScope, Syntax, Targa, TDM FlexCable, Thunder, Titan, Titansync, TL Aggro, TL AutoPan, TL Drum Rehab,
TL Everyphase, TL Fauxlder, TL In Tune, TL MasterMeter, TL Metro, TL Space, TL Utilities, Torq, Torq Xponent, Transfuser,
Trigger Finger, Trillium Lane Labs, TruTouch, UnityRAID, Vari-Fi, Velvet, Venom, VideoRAID, Video Slave Driver, VideoSPACE,
VideoSpin, Vortx, Xdeck, X-Form, Xmon, Xponent, X-Session, and X-Session Pro are either registered trademarks or
trademarks of Avid Technology, Inc. in the United States and/or other countries.
Footage
Arri — Courtesy of Arri/Fauer — John Fauer, Inc.
Bell South “Anticipation” — Courtesy of Two Headed Monster — Tucker/Wayne Atlanta/GMS.
Canyonlands — Courtesy of the National Park Service/Department of the Interior.
Eco Challenge British Columbia — Courtesy of Eco Challenge Lifestyles, Inc., All Rights Reserved.
Eco Challenge Morocco — Courtesy of Discovery Communications, Inc.
It’s Shuttletime — Courtesy of BCP & Canadian Airlines.
Nestlé Coffee Crisp — Courtesy of MacLaren McCann Canada.
Saturn “Calvin Egg” — Courtesy of Cossette Communications.
“Tigers: Tracking a Legend” — Courtesy of www.wildlifeworlds.com, Carol Amore, Executive Producer.
"The Big Swell" — Courtesy of Swell Pictures, Inc.
Windhorse — Courtesy of Paul Wagner Productions.
Arizona Images — KNTV Production — Courtesy of Granite Broadcasting, Inc.,
Editor/Producer Bryan Foote.
Canyonlands — Courtesy of the National Park Service/Department of the Interior.
Ice Island — Courtesy of Kurtis Productions, Ltd.
Tornados + Belle Isle footage — Courtesy of KWTV News 9.
WCAU Fire Story — Courtesy of NBC-10, Philadelphia, PA.
Women in Sports – Paragliding — Courtesy of Legendary Entertainment, Inc.
News material provided by WFTV Television Inc.
GOT FOOTAGE?
Editors — Filmmakers — Special Effects Artists — Game Developers — Animators — Educators — Broadcasters — Content
creators of every genre — Just finished an incredible project and want to share it with the world?
Send us your reels and we may use your footage in our show reel or demo!*
For a copy of our release and Avid’s mailing address, go to www.avid.com/footage.
*Note: Avid cannot guarantee the use of materials submitted.
Avid iNEWS v3.3 Administration Guide • 0130-30XXX-01 • Created 6/17/13 • This document is distributed by
Avid in online (electronic) form only, and is not available for purchase in printed form.
5
Page 6

6
Page 7

Contents
Using This Guide . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
Symbols and Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
If You Need Help. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
...With the Syntax of Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
Avid Training Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Chapter 1 Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Overview of iNEWS. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
System Administrator Tasks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Chapter 2 Connect Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Network Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Dialogs for Connect Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Building a Dialog . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Dialog Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Dialog Examples . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Adding System Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Setting up the Service . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Console Connect Sessions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Chapter 3 Database Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
Establishing Security Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
User Passwords . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Checking Password Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
Forcing Individual Users to Change Their Passwords . . . . . . . . . . . . . . . . . . . . 43
. . . At an iNEWS Workstation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
Tracking User Activity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
Tracking User Login Activity and Date Created . . . . . . . . . . . . . . . . . . . . . . . . . 44
. . . At an iNEWS Workstation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
. . . At the Console . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Listing Users Currently Logged in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Recording Logins . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
7
Page 8

Using Group Security to Control System Access . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
Chapter 4 Database Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
Monitoring Free Space. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
Understanding Database Storage Units . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
Monitoring the Free List. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
Understanding How the System Copies Stories . . . . . . . . . . . . . . . . . . . . . . . . 51
Tracking Database Space over Time. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
Using the hogs Command to Obtain Information . . . . . . . . . . . . . . . . . . . . . . . 52
Using dbserver and dbfree to Obtain Information . . . . . . . . . . . . . . . . . . . . . . . 53
Increasing Database Space for Immediate Use. . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Maintaining the Database. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Checking the Database for Errors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Cleaning the Database . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
Cleaning Your Database Offline . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
Cleaning Your Database with Online Dbvisit . . . . . . . . . . . . . . . . . . . . . . . 59
Chapter 5 Avid System Monitoring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
Using SNMP Monitoring on the iNEWS Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
Installing and Enabling the SNMP Agent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
Chapter 6 Backing Up the iNEWS System. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
Tape Operations. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 68
Establishing Policies for Backup Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . 68
Backing up the iNEWS Database. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
The dbdump Command. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
Backing up the Entire Database to Tape. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70
Tapeless Database Backup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
Backing up Individual Queues. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 77
Notes on Backing up the Database. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
Restoring Data to the iNEWS Database . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
The dbrestore Command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
Restoring a First-Level Directory. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
Listing Tape Contents and Backup Dates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
Listing Contents of a Tape . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
Listing Items Dumped on a Particular Date . . . . . . . . . . . . . . . . . . . . . . . . 82
8
Page 9

Listing the Date of Each Backup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
Searching a Tape . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
The searchtape Command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
Searching a Tape for Stories. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
Searching a Tape by Word(s) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Searching a Tape by Word and Date Range. . . . . . . . . . . . . . . . . . . . . . . . 85
Searching a Tape by Word and Day . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
Searching a Tape by Word and Month . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
Specifying a Maximum Number of Stories to Search . . . . . . . . . . . . . . . . . 86
Checking for Free Space on a Database . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Adding Blocks to the Free List. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Restoring the Database . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
Disaster Recovery Planning . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
Disaster Recovery Dbdump . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
Create Minimal dbdump . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
Backing up Software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
Backing up System Site Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 90
The sitedump Command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 90
Chapter 7 Disconnects . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91
Normal System Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92
Disconnects. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92
Detecting a Disconnect . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
Types of Disconnect. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 95
Causes of Disconnects. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
Disconnect Recovery . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97
Recovery Worksheet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
Chapter 8 Troubleshooting. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
iNEWS Workstation Problems . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104
A User Cannot Log in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104
A User Cannot Establish a Session . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104
A User Cannot Access an Item . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106
9
Page 10

Group Permissions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106
Busy Stories . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106
Wire Problems . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
Data Receiver . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
Locked Blocks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
How to Check Process Status (ps Command). . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
Power Failure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110
Network Failure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110
netstat -i Command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
Output Errors (TX-ERRs) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
Input Errors (RX-ERRs) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
iNEWS and FTS Connectivity (ftsdebug Command) . . . . . . . . . . . . . . . . . . . . . . . 112
Checking Communication between iNEWS and FTS Servers . . . . . . . . . . . . 113
Community . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Appendix A Command References . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
Programs Invoked by iNEWS. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
Commands Used by Avid Personnel Only . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
Linux Commands Used in iNEWS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
Console Server Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
broadcast. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
configure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
connect . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
ctraits. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
dbclean . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122
dbclose . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
dbdev and dbsize . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
dbdump . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
dbfree . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
dblines . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
dboriginal. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
dbpurge
(Superuser conditional) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127
dbrestore . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 128
10
Page 11

dbserver . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
dbsort . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
dbtraits . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
dbvisit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 132
dictionary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
diskclear
(Superuser only) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
diskcopy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135
doc . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135
ed . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 136
enter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 136
force
(Superuser only) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 136
grpcheck. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
gtraits
(Superuser only) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
help. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
hogs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
idiff . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
list . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
list B . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
list C . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 144
list c . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 144
list d . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 145
list g . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 146
list p . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 146
list q . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
list s . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
list sq . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 150
list u
. . . . . . . . . . . . . . . . . . . . . . . . . . . 150
logout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 152
makemontab. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 152
makeshift (Super user only) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 153
maketab
11
Page 12

(Superuser only) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 154
mapcheck . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 154
msgclean . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
offline. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
online. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
otod . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
reconnect. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 160
remove . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 160
rename
(Superuser only) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 160
reorder. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 161
restart . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 161
searchtape. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 162
send. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 162
sendlong . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
shutdown . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
sitedump
(Superuser only) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
siterestore
(Superuser only) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
startup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164
status. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164
stop . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 165
su. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 165
unbusy. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 166
utraits
(Super user only) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 166
version. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
wholockedit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 168
Job List Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170
at . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170
blockmode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170
bpoll. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170
bscan. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
12
Page 13

charset . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
distribution . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
dup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
every. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
extension . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
fast . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
ignore . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
ignore-del . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
local . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
mailto . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
move. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
number . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
on . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
open . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
order . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
passive . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
poll . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
publish . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
put . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
quiet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
remote . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
remove . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
replace . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
scan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
send-del . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
sendform . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 177
sendpassword . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 177
source. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 177
validate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 177
Dialog Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 177
capture . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178
delay. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178
diag. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178
13
Page 14

echo. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
escape. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
expect . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
heol . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
mapin. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
mapout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
message . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
pass. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
pause. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
stop . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
timer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
type . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
wait . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
Appendix B System Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 185
/etc/hosts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 186
/site/config . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
/site/system . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 199
SYSTEM.CLIENT.WINDOWS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 200
SYSTEM.COLORS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
SYSTEM.CONFIGURE.301-ACTION . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
SYSTEM.GROUPS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 202
SYSTEM.INTERPLAY . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 202
SYSTEM.LISTS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 203
SYSTEM.MAP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 203
SYSTEM.MOS-MAP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 205
SYSTEM.RESOURCE . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 206
SYSTEM.WIRES.DISTRIBUTION . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 209
SYSTEM.WIRES.KEYWORDS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 210
SYSTEM.WIRES.KEYWORDS-AP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 211
SYSTEM.WIRES.KEYWORDS-AP2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 212
Appendix C Standard Dictionaries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 213
Using Dictionaries to Define Messages and Commands . . . . . . . . . . . . . . . . . . . . 214
14
Page 15

Customizing Dictionaries. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 216
Changing Default Dictionary Values. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 216
Restoring Dictionary Defaults. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 218
Utility Messages Dictionary (/site/dict/messages) . . . . . . . . . . . . . . . . . . . . . . . . . . 219
DBServer Program Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 220
Disconnect Program Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 220
Category and Keyword Check Program Messages . . . . . . . . . . . . . . . . . . . . . 220
Keyboard Check Program Messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 221
Keyboard Check Program Messages for Macros. . . . . . . . . . . . . . . . . . . . . . . 222
Grpcheck Messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 224
Wire Program Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 225
Mail Server Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 225
Map Check Program Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 225
Validation (Action) Server. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 226
Seek Server Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 226
Last Login Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
Print Server Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
dbtraits Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
Save Error (Workstation) Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 228
Queues Dictionary (/site/dict/queues) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 228
Words Dictionary (/site/dict/words) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230
Keyboard Macros Dictionary (/site/dict/keymacros) . . . . . . . . . . . . . . . . . . . . . . . . 233
Case-shifting Dictionary (/site/dict/shift) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 235
MCS Dictionary (/site/dict/mcs) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 237
Device Types Used by Monitor Servers and Drivers . . . . . . . . . . . . . . . . . . . . 238
Special Strings Recognized by the Monitor Server . . . . . . . . . . . . . . . . . . . . . 238
Error Messages for the Monitor Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 238
Status Reported in Device Status Field . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 241
Job List Command Dictionary (/site/dict/joblist) . . . . . . . . . . . . . . . . . . . . . . . . . . . 241
D Messages Dictionary (/site/dict/dmessages) . . . . . . . . . . . . . . . . . . . . . . . . . . . . 243
S Messages Dictionary (/site/dict/smessages) . . . . . . . . . . . . . . . . . . . . . . . . . . . . 243
Appendix D Environment Variables . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 247
Registry Editor. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 248
15
Page 16

Environment Variables (Registry Values). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 249
CCColor. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 249
DestinationOrder . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 251
MailLookup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 252
MsgMailAlert . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 253
PIColor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 254
RGB Hexadecimal Color Chart. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 255
ShowTimingBar . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 256
SyncToServer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 260
VT Compatibility . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 261
DisableCommandLine . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 263
Environmental Variables for Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 264
Appendix E Managing Traits at the Console . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 267
Viewing User Traits from the Console . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 268
Modifying User Traits from the Console. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 269
Changing a User’s Password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 270
Listing Users Who Do Not Have Passwords . . . . . . . . . . . . . . . . . . . . . . 272
User Traits Console Command Summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 276
Managing Database Traits from the Console. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 279
Getting Basic Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 279
Getting Detailed Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 280
Changing Database Traits from the Console . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 281
Changing a Parent Directory Only. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 281
Database Traits Console Command Summary . . . . . . . . . . . . . . . . . . . . . . . . . . . 281
Sortfield . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 289
Changing a Queue’s Sort Field . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 290
Starting the Queue Sort Function from the Console. . . . . . . . . . . . . . . . . 290
Purge Interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 291
Mailbox Attribute. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 292
The dis Column . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 292
FTSindex Attribute . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 294
Interplay Attribute . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 294
Managing Group Traits at the Console . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 295
16
Page 17

Read Group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 295
Write Group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 295
Editorial Group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 296
Notify Group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 296
Restricting Access Using Read and Write Limitations . . . . . . . . . . . . . . . . . . . 297
Removing Directory or Queue Restrictions . . . . . . . . . . . . . . . . . . . . . . . . . . . 298
Appendix F The Line Editor, ed . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 299
Starting ed. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 300
Specifying Lines to Edit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 300
Searching the File . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 302
Searching Tips. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 303
Editing Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 303
Saving Changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 306
Quitting ed . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 306
Index
17
Page 18

18
Page 19

Using This Guide
Congratulations on your purchase of your Avid iNEWS system. It is a vital part of the Avid
news system solution that integrates with other Avid systems and third-party equipment to
provide an ideal nonlinear workflow and optimize the news production process.
This guide is part of a two-book set designed to keep pace with current advances in the Avid
system’s news production capabilities. The set—made up of this book and the Avid iNEWS
Setup and Configuration Guide—is a comprehensive resource of all administrative
information you will need to take advantage of the many options available to you.
This guide will lead you through even the most complex procedures with task-oriented
instructions. The information provided here builds on basic news production procedures
described in the help system and other user-based guides, while adding a complete
explanation of all of the tools and techniques required to manage the newsroom computer
system, including useful tips, shortcuts, and custom options.
The documentation describes the software features and hardware related to the iNEWS
n
newsroom computer system, which is extremely customizable. Your system might not contain
certain features and/or hardware that are covered in the documentation.
Symbols and Conventions
Avid documentation uses the following symbols and conventions:
Symbol or Convention Meaning or Action
n
c
w
A note provides important related information, reminders,
recommendations, and strong suggestions.
A caution means that a specific action you take could cause harm to
your computer or cause you to lose data.
A warning describes an action that could cause you physical harm.
Follow the guidelines in this document or on the unit itself when
handling electrical equipment.
Page 20

Symbol or Convention Meaning or Action
> This symbol indicates menu commands (and subcommands) in the
order you select them. For example, File > Import means to open the
File menu and then select the Import command.
This symbol indicates a single-step procedure. Multiple arrows in a list
indicate that you perform one of the actions listed.
(Windows), (Windows
only), (Macintosh), or
(Macintosh only)
Bold font Bold font is primarily used in task instructions to identify user interface
Italic font Italic font is used to emphasize certain words and to indicate variables.
Courier Bold font
Ctrl+key or mouse action Press and hold the first key while you press the last key or perform the
If You Need Help
If you are having trouble using your Avid product:
1. Retry the action, carefully following the instructions given for that task in this guide. It
is especially important to check each step of your workflow.
2. Check the latest information that might have become available after the documentation
was published:
- If the latest information for your Avid product is provided as printed release notes,
they ship with your application and are also available online.
This text indicates that the information applies only to the specified
operating system, either Windows or Macintosh OS X.
items and keyboard sequences.
Courier Bold font identifies text that you type.
mouse action. For example, Command+Option+C or Ctrl+drag.
20
- If the latest information for your Avid product is provided as a ReadMe file, it is
supplied on your Avid installation CD or DVD as a PDF document
(README_product.pdf) and is also available online.
You should always check online for the most up-to-date release notes or ReadMe
because the online version is updated whenever new information becomes
available. To view these online versions, select ReadMe from the Help menu, or visit
the Knowledge Base at www.avid.com/readme.
3. Check the documentation that came with your Avid application or your hardware for
maintenance or hardware-related issues.
Page 21

4. Visit the online Knowledge Base at www.avid.com/onlinesupport. Online services are
available 24 hours per day, 7 days per week. Search this online Knowledge Base to find
answers, to view error messages, to access troubleshooting tips, to download updates,
and to read or join online message-board discussions.
...With the Syntax of Commands
If you are at the console and are unsure about the function of a command, use the help
command.
To view instructions about using a command:
If You Need Help
t Use the following command:
For instance, type:
The following data appears:
dbvisit -<d or v or i> [-r or -c name] [-s] [-l] [block# ...]
‘r’ for read only
‘s’ for “slow” to eliminate cache usage
‘c’ use checkpoint partition (forces “-s”)
‘i’ to just validate isam files
‘l’ to list link count distribution
Lengthy console displays might be edited to emphasize only the most important information
n
in this guide. An ellipsis (...) represents portions of the console display not shown in the text.
Also, because of the margin limitations of this guide, command lines might appear wrapped
to multiple lines. This does not necessarily indicate the need to press an Enter key. Unless
otherwise indicated, commands should be typed on a single line, allowing the computer to
wrap the text whenever the command line stretches beyond the screen margin.
help dbvisit
help
<command name>
for an explanation of the dbvisit command.
21
Page 22

Avid Training Services
Avid makes lifelong learning, career advancement, and personal development easy and
convenient. Avid understands that the knowledge you need to differentiate yourself is always
changing, and Avid continually updates course content and offers new training delivery
methods that accommodate your pressured and competitive work environment.
To learn about Avid's new online learning environment, Avid Learning Excellerator
(ALEX), visit http://learn.avid.com.
For information on courses/schedules, training centers, certifications, courseware, and
books, please visit www.avid.com/training or call Avid Sales at 800-949-AVID
(800-949-2843).
™
22
Page 23

1 Introduction
The iNEWS newsroom computer system is an integrated digital news production system,
which provides journalists, producers, directors, writers, and technical personnel with an
array of tools to make their jobs easier.
This chapter contains the following main sections:
• Overview of iNEWS
• System Administrator Tasks
- Basic Tasks
- User Tasks
- Database Tasks
- Security Tasks
- Customizing the System
- Storage Maintenance Tasks
- Device Tasks
- Reviewing Default Settings
- Troubleshooting
Page 24

Overview of iNEWS
An iNEWS newsroom computer system provides:
• News gathering from text sources
• News production, including:
- Story creation and script editing
- Association of machine control items to script
- Show planning and creation
- Show archiving
- Contact organization and scheduling
• News to air, including:
- On-air playback control
- File exporting
- Internet publishing
Some primary components of iNEWS include:
• Linux-based computers running the iNEWS Server software. In this guide, these host
computers are referred to as the iNEWS Servers, or individually as server A, server B,
and so forth.
• A Windows-based computer running the PuTTY Command Sender program. This
computer is known as the console.
• Windows- or Vista-based computers running the iNEWS client software. These
computers are known as iNEWS Workstations.
• Windows-based computers running the iNEWS Data Receiver software, which is used
to ingest wires and other text-based research material
• Other peripherals, such as printers and teleprompters.
Additionally, the iNEWS system is capable of interfacing with a wide variety of production
devices. Avid iNEWS Command provides a central point of control for numerous video
servers and graphics devices, or MOS protocol may be used to send playlists to
MOS-compatible playout controllers.
Page 25

System Administrator Tasks
The following sections describe common system administrator responsibilities and tasks.
Basic Tasks
Before you can customize or maintain the iNEWS newsroom computer system, you must
learn several basic tasks, which include:
• Start up or shut down iNEWS Server software, which includes logging out users and
taking the system offline.
• Back up a site file before making file modifications.
• Send system administrator commands from the console to one or more of your system’s
computers.
• Become a console superuser, capable of performing actions that are only accessible to
users with superuser permissions.
User Tasks
A user is anyone who can log in to the database and use iNEWS NRCS. Your
responsibilities regarding users are:
System Administrator Tasks
• Monitor user information, such as users’ access privileges and which users are currently
logged in.
• Customize the traits of users’ accounts to enable users to more effectively use the
system.
• Provide a new employee access to the information stored in the iNEWS NRCS database
by creating a new user account.
• Remove user accounts of former employees to prevent improper access to the iNEWS
NRCS database.
Database Tasks
The iNEWS system database contains the information your organization needs to function.
A system administrator’s tasks associated with the database include:
• Design forms (that is, story templates) to display important information about stories in
a queue.
• Monitor changes to files and queues in the database.
• Unlock or delete any item in the database, and recover items that were accidentally
deleted or corrupted.
25
Page 26

1 Introduction
• Create new folders or queues in the iNEWS system database to meet your organization’s
• Remove a directory or queue from the database, if it is no longer used.
• Change the name or traits of an existing directory or queue.
• Assign the mailbox trait to queues for configuring automatic story distribution into and
Security Tasks
There are many ways to ensure the security of your iNEWS system. Your responsibilities
regarding system security include:
• Monitor and change passwords or force users to change them by setting up system
• Monitor user login activity to guard against unauthorized use of the iNEWS system.
• Assign security to a directory or queue, limiting access to a specific group of users.
• Restrict database access by placing users into security groups based on job roles and
Customizing the System
expanding needs—including setting up rundowns.
out of queues.
checks and modifications.
need for information.
26
Your responsibilities regarding customization include:
• Customize command names, message text, and other items by changing their entries in
your system’s dictionary files.
• Create templates for the CG Title Entry tool.
• Design and assign custom keyboards for users with a unique set of keyboard macros.
Storage Maintenance Tasks
You will want to monitor the database regularly to ensure adequate storage. Storage
maintenance tasks include:
• Monitor how much free space is available in the database and, if necessary, increase the
amount to prevent the system from running out of space.
• Perform preventive database maintenance by periodically running certain utility
programs that can find and fix minor problems before they become serious.
• Backup the entire database or portions of it onto tape, so if necessary, the information
can be restored to the database later.
• Make a backup copy of files any time you make important changes.
Page 27

System Administrator Tasks
Device Tasks
A device is any kind of hardware or software that performs a specific function when it is set
up on the iNEWS system. Your responsibilities regarding devices include:
• List the parameters of any device running on your system or list all devices of one type.
• Add any type of device to your system, if you have the capacity and license permission.
• Edit site-specific files, to change the setup information for a device in your system’s
configuration file.
• Reconfigure the system so it recognizes any changes you make to your system’s
devices.
• Set up printer styles so users can print stories or queues in predetermined formats. For
example, a director rundown only showing specific rundown fields.
• Set up servers, which are utility programs automatically performing various actions on
the database.
• Change wire distribution and sorting of data coming into your database from a wire
service to queues based on their category codes or content.
• (Optional) Write dialogs—lists of instructions—for each connect service to automate
the connection process. A connect service is a device that connects a user to a remote
computer system.
Reviewing Default Settings
Your responsibilities regarding system profiles, default settings, and command syntax
include:
• Changing a system profile setting to change your system’s operation.
• Reviewing default settings of all system profile parameters.
• Reviewing command syntax for edit, console, and job list commands.
Troubleshooting
Your troubleshooting responsibilities include:
• Transfer system activities from a halted computer to other system computers. If a
computer connected to the system has been halted, bring the system back to operation
using the remaining computers
• Reconnect a computer that has been halted. Following routine maintenance, reintegrate
a computer into your system’s operation.
27
Page 28

1 Introduction
28
Page 29

2 Connect Services
Connect services are utilities you can set up to enable iNEWS users to connect to other
computers or information services over the network, such as a remote console for your
iNEWS newsroom computer system.
This chapter contains the following main sections:
• Network Services
• Adding System Services
• Console Connect Sessions
Page 30

2 Connect Services
Network Services
It is useful to set up a service to let you connect to your iNEWS Servers. For instance, setting
up network remote connect services lets you perform many administrative tasks from your
iNEWS Workstation rather than from the console.
Dialogs for Connect Services
A dialog is a script that tells the service what prompts to expect from the device it connects
to, and provides the service with appropriate responses for each prompt. Using any service
involves some routine activities, such as logging in, that you do each time you use that
service. You can create a dialog for any service to handle these routine activities.
Building a Dialog
This section explains how to design and create a simple dialog that logs a user in to an
information service. Once logged in, the dialog yields control to the user until he/she is
ready to close the connection. Then the dialog logs the user out of the service and closes the
connection.
When you design a dialog, it is helpful to turn on the
perform the procedure you want to incorporate into the dialog. This way, steps in that
procedure are captured to a story that you can refer to while designing the dialog; each line
in the dialog is built as a line of the story.
This process includes the most commonly used dialog commands.
To build a dialog:
1. Create a dialog queue.
Each dialog must be in a separate queue in the SYSTEM.DIALOGS directory. The first
step in creating a new dialog is to go to SYSTEM.DIALOGS and create a queue to hold
it. The name you give this queue is also the name of the dialog, so choose a queue name
that describes what the dialog does, such as Console, for a dialog used during connect
sessions to the console. See the iNEWS Setup and Configuration Guide for more
information about adding new directories, queues or stories.
2. Open a new story in the queue and build the dialog.
3. Type a message that will be displayed on the user’s workstation, indicating the
connection is being established, using the following format:
message text
The message dialog command displays on the user’s screen whatever text you enter in
place of the text parameter.
capture
connect command and
30
Page 31

Network Services
4. Type:
wait CONNECT
When you use a modem to make the connection, you want the dialog to wait until the
modem sends the word CONNECT to the workstation, signaling it has made the
connection.
If necessary, use these additional commands to accommodate the login procedure:
Command Description
delay
type
5. To send your login data, such as an account number, type
nn
text
Use this command to pause the dialog while the service continues connect
and login processes.
(nn is the number of seconds you want the dialog to pause before continuing
to the next command)
Use the type command to send a text message to the device to which the
workstation is being connected.
type text
with text being the
account number.
pass
6. Type
to yield control to the user after login is complete.
This command instructs the dialog to pass whatever the user enters to the device to
which the service has connected.
pass x
Use
should be a character or symbol, such as the at symbol (@), he or she will not normally
use.
pass
Use
the connection.
7. Type commands to log out of the service.
When the user exits a connection using the quit connect command, the dialog resumes
and performs the logout process and closes the connection.
8. Attach the dialog to the service by placing the dialog’s name in the service’s dialog
parameter in the service table, located in the SYSTEM.SERVICE queue.
9. Type the
Dialog Commands
Available dialog commands are flexible enough to script entire connect sessions. For
instance, a dialog could be constructed to automatically log in to the remote console and
“unbusy” a rundown if desired.
to include a character the user can enter to cue the dialog to resume. The x
alone to instruct the system to accept what the user enters until he/she closes
configure -s
command to incorporate this change into the service.
31
Page 32

2 Connect Services
The available dialog commands are reviewed in “Command References” on page 117.
Dialog Examples
Here are a few examples of dialogs for remote console connect services:
In the example, <cr> and <lf> are used to indicate a “carriage return” and “line feed.”
Adding System Services
A service consists of two parts:
• A network resource, set up as a device in the configuration file (/site/config).
• The service, set up in the service table in the database file (SYSTEM.SERVICE); it uses
the resource to make a connection.
To add a new service to your system, you must design and build the service and select a
network resource for the service to use. If an appropriate resource does not exist, create
one.
32
Page 33

Setting up the Service
To set up the service and its resource:
1. Determine whether the service and its resource exists.
Try connecting to a service you want. If it works, then the necessary programs are
installed. If you cannot find the service, or one does not work, call Avid for help.
2. Choose a device number for the resource and a name for the service. In the following
examples, the service name is console.
Check your configuration file (/site/config) to determine the appropriate device number
for your new resource. For a network resource, choose a number in the range you have
reserved for services, servers, and similar devices. Ensure the number you choose is out
of the range used for normal devices.
See the iNEWS Setup and Configuration Guide for more information on the Site
n
Configuration file and selecting servers via the PuTTYCS application.
3. Add the resource to the configuration file on each server in your system.
a. Add the device number of the network resource to the reslist line in the server’s host
definition.
Adding System Services
b. To keep the network resource available if you bring down one of the system servers,
add this line to any appropriate alternate host definitions.
The following steps use ed to modify system files. If you are unfamiliar with this line editor,
n
see “The Line Editor, ed” on page 299.
ed
c. Use
The general format for a network resource configuration line is:
resource <device #> <resource name> <device name>
Parameter Description
device # Identifies resource’s device number.
resource name Name you want to give to the resource. Network resources can share the
device name Resource’s device name. If you do not want to give it a name, put a hyphen
(line editor) to open the configuration file. The display will look similar to:
NRCS-A
$ ed /site/config
1356
same name; services choose the first available resource of the correct kind.
In the following example, we call the resource net.
in this position.
33
Page 34

2 Connect Services
For instance, our new network resource configuration line would look like this:
resource 220 net - ; net connect
4. Add the service to the service table in the database.
Each service installed in your system is defined on a separate line in your system’s
service table, which is the first story in SYSTEM.SERVICE. Each service defined in the
service table consists of a few parameters that determine how the service behaves. It
does not matter where in the service table you add the new line.
A service line has six parameters in this general format:
<service> <host> <dialog> <resource> <group> <command>
The following table contains information on service line formats:
Parameter Definition
service Name you want the service to have.
host Name of the server where you want the service to look for its resource. List
the target server’s name in your system’s /etc/hosts file.
A hyphen in this position will force the service to search each server until it
finds one that has a resource it can use.
34
dialog If you want the service to use a dialog, put the dialog name in this position of
the service line. Otherwise, fill this position with a hyphen.
resource Name of the resource you want the service to use.
group You can restrict who can use the service by specifying a user group. If you do
not want to restrict access, place a hyphen in this position.
command Specifies the command you want the service to use to handle communication.
To create a service using telnet, type the
specify the program’s full pathname and include the system name to which
you are connecting.
telnet
command here. Ensure you
You will need one such service line for each server on your system. Use the ssh
command in the following way:
/usr/bin/ssh <servername> -1 <username>
The following sample entries in SYSTEM.SERVICE let you establish a network
connection to your console from an iNEWS Workstation session.
a - console console sysops /usr/bin/ssh NRCS-A -l so
b - console console sysops /usr/bin/ssh NRCS-B -l so
Page 35

Adding System Services
The resource assigned to the service must be configured on the computer you want to
log in to.
5. (Optional) Create a dialog for the service.
If you want your service to follow certain instructions every time it is invoked, create a
dialog for the service containing those instructions. See “Building a Dialog” on page 30
for more information.
6. (Optional) Test your configuration changes on iNEWS. See the iNEWS Setup and
Configuration Guide for more information on testing the site configuration file.
7. Reconfigure the system.
This causes your system to note changes and incorporate them into appropriate
programs. Do the following:
See the iNEWS Setup and Configuration Guide for more information on selecting servers
n
and the superuser mode.
a. Select the console window for the master computer (typically server A).
b. Enter superuser mode.
c. Type what appears in bold text:
NRCS-A# offline
d. If you added a new resource or modified an existing one in the process of creating a
new service, reconfigure your system by typing the following:
NRCS-A# configure
If you modified an existing service or added a service that uses an existing network
resource, you did not make any changes to your system’s configuration file. So, you
need to have the system note only changes made to the service table by typing the
following:
NRCS-A# configure -s
8. When the prompt returns, type what appears in bold text:
NRCS-A# online
9. Exit superuser mode by holding the Control key (Ctrl) down and typing the letter D. A
message similar to the following will appear:
A Tue Oct 5 00:18:58 2000 msg System being configured
When you see the system prompt, the network service you created and its resource you
added (if any) is ready for use.
10. (Optional) Back up site files.
35
Page 36

2 Connect Services
If you have made significant changes, back up your site files with the
command.
Console Connect Sessions
To connect to the console from an iNEWS Workstation—that is, after the network
remote connect service and its resources are set up—do the following:
1. Log in to any iNEWS Workstation, with a user account allowed to use the Connect to
Service feature.
2. Select Communicate > Connect to Service. The Connect to Service dialog box will
appear, offering you a list of services.
As shown in this example, two options are provided to connect to the console—each
option corresponding to a different iNEWS Server.
sitedump
console
36
3. Double-click on the service you want.
A dialog box will appear with a dialog (as defined in the SYSTEM.DIALOGS) that
requests a password.
4. Type in the password and press Enter.
5. Once connected, the dialog box will display the console prompt, similar to what appears
on the console when you are logged in as a system operator.
Here is an example of a remote console connection:
Page 37

Console Connect Sessions
6. You can now perform various administrative tasks through the console connect session,
as opposed to doing them while physically located at the console.
c
To stop a console connect session, press Ctrl+D. Do not close the dialog box by selecting
File > Close or by clicking on the X button in the upper-right corner.
37
Page 38

2 Connect Services
38
Page 39

3 Database Security
This chapter describes how to use various features in the iNEWS newsroom computer
system to establish and maintain database security.
This chapter contains the following main sections:
• Establishing Security Procedures
• User Passwords
• Checking Password Status
• Tracking User Activity
• Using Group Security to Control System Access
Page 40

3 Database Security
Establishing Security Procedures
Use the following guidelines to improve the security of your system:
• Set up official security procedures and have everyone follow them.
• Keep track of your backup tapes. You can get user passwords from a backup tape.
• Assign users superuser status only when they need it.
• If any user does not need superuser status, remove it. Create two user accounts for staff
members who need superuser privileges—one to be a superuser and another to be a
regular user. That way, you can track activity of superuser accounts.
• Change the superuser password regularly.
• Ensure that users do not use their names, station call letters, or other easily guessed
words as passwords. Require everyone to include at least one non-alphabetic character
such as a punctuation mark or a number.
• Use the system profile to set a required minimum length for all passwords so no one
uses a short password.
• For devices for which you have dedicated resources—that is, devices that have a
one-to-one correspondence between the physical device and device number used to
identify it—use device name security on workstations in specific locations and put the
device ID in a group.
• If you have dedicated resources, you can put a MODIFY-DEV field in the queue’s story
form if you suspect that someone has broken into a user’s account. When changes are
made to stories created after the MODIFY-DEV field has been added, the system puts
the device name of the workstation where changes were made in that field. This
information is kept internally, but having the MODIFY-DEV field makes it visible to
users.
• Be familiar with valid user accounts on your system. Restrict access to these account
names to protect against unauthorized outside access.
User Passwords
Your iNEWS newsroom computer system protects against unauthorized access by giving
each authorized user a password to log into the system. Group security, described under
“Using Group Security to Control System Access” on page 47, lets you control specific
areas of your database that each user can access.
For added security, iNEWS uses encryption to pass user credentials to the server.
40
Page 41

Checking Password Status
A user account without a password is an open door to your system. You should always give a
user a password when you add the user to your system. See the iNEWS Setup and
Configuration Manual for more information on setting up new user accounts.
However, if you suspect that a user does not have a password or has not changed it in awhile,
you can find out for certain from any iNEWS Workstation.
For information on how to check password status from the console, see “Listing Users Who
n
Do Not Have Passwords” on page 272.
To check user password status from an iNEWS Workstation:
1. Log in as a system administrator—that is, use a superuser account.
2. Select Tools > Options > Users.
The Manage User Accounts dialog box appears.
Checking Password Status
3. Type an asterisk (*) in the User ID field if it does not already appear.
The iNEWS system recognizes this as a wildcard and therefore will search the entire
database of users.
The other criteria options available in this dialog box are explained in the iNEWS Setup and
n
Configuration Manual.
4. Click the Advanced button.
41
Page 42

3 Database Security
The Advanced Search Settings dialog box appears with All Users selected by default.
5. Do one of the following:
t To search for all users without passwords, select Users Without Passwords.
t To search for all users who have not changed their password within a specific time,
select Date Range. Then click Password Changed, and specify the time frame to
search.
6. Click OK to confirm your advanced search setting or click Cancel to cancel it.
7. Click Search to initiate the search.
A progress bar appears if a lengthy search is underway. Results of the search appear in
the User List field in the center of the Manage User Accounts dialog box.
As a system administrator, you can change a user’s password. Change a user’s password
to provide a new user with a temporary password or to supply an established user with a
new password if the user forgets it and cannot log in. See the iNEWS Setup and
Configuration Manual for more information on how to do this from any iNEWS
Workstation. For steps on how to change a user’s password from the console using the
utraits console command, see “Changing a User’s Password” on page 270.
42
Page 43
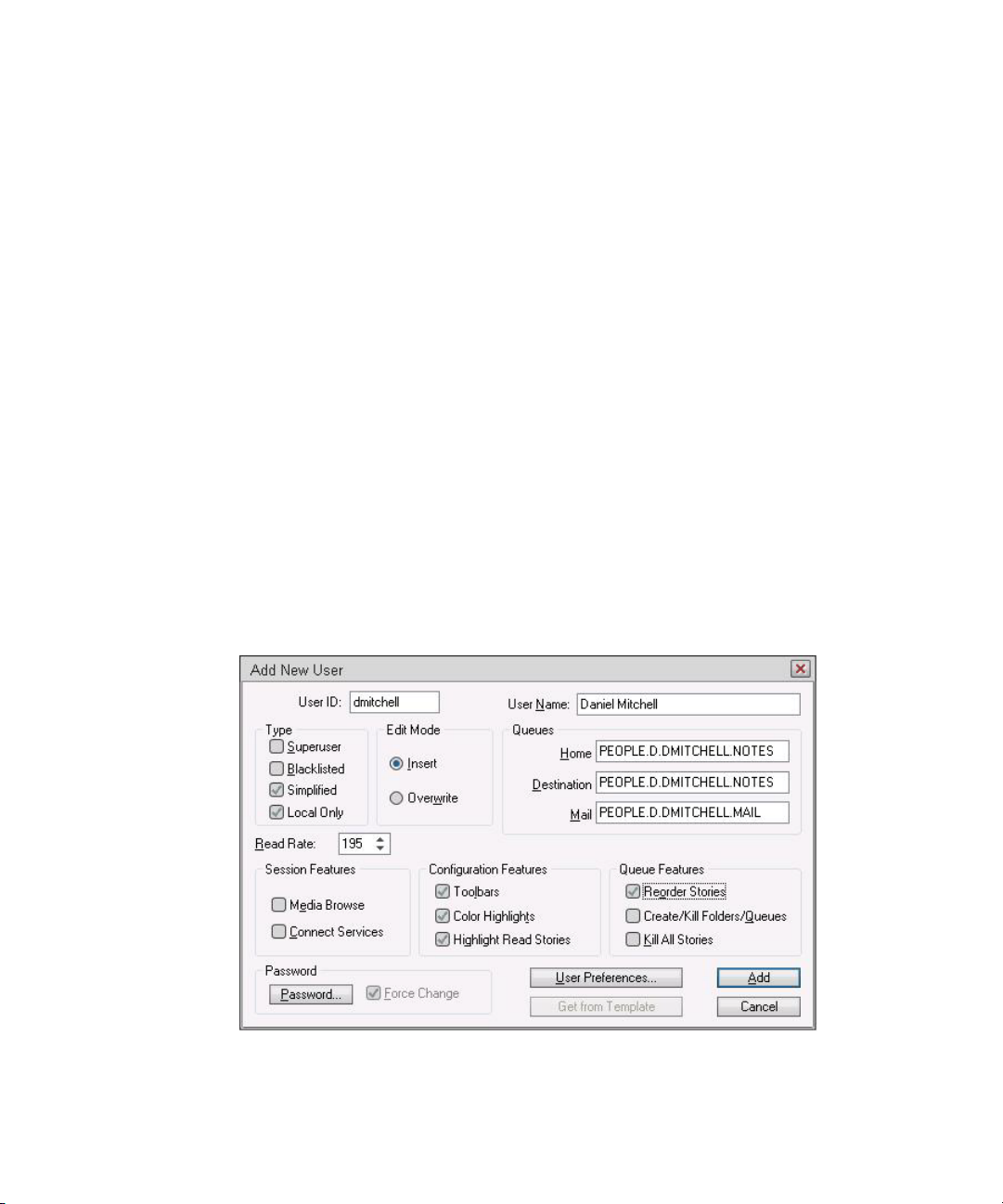
Forcing Individual Users to Change Their Passwords
Occasionally, you might have individual users who do not change their passwords as
required. When that happens, you can force them to change their password at their next
login. You can do this for a single user at an iNEWS Workstation.
To force multiple users to change their passwords—such as all users who haven’t changed
their passwords in the past six months—you must go to the console. For steps on how to
force password changes from the console, see “Changing a User’s Password” on page 270.
. . . At an iNEWS Workstation
To force an individual user to change his or her password:
1. Select Tools > Options > Users.
The Manage User Accounts dialog box appears.
2. Type the user name in the User ID field.
3. Click Search.
4. Select the user name when it appears in the dialog box.
5. Click Modify.
Checking Password Status
The Modify User Account dialog box appears.
6. Check the Force Change box.
7. Click OK.
43
Page 44

3 Database Security
The next time the user logs in, he or she will be required to choose a new password.
Tracking User Activity
Keep a record of who uses iNEWS and when they use it by following the procedures
described in this section. These security measures can ensure there is no unauthorized use of
your system.
At an iNEWS Workstation, you can determine:
• Last login date of one or more user accounts
• Date user accounts were created
• Users currently logged in
At the console, you can determine attempted and successful logins.
Tracking User Login Activity and Date Created
You can search for a user account’s last login and the date the user account was created from
an iNEWS Workstation.
. . . At an iNEWS Workstation
To search for a user’s last login:
1. Select Tools > Options > Users.
The Manage User Accounts dialog box appears.
2. Click Advanced. The Advanced Search Settings dialog box appears.
3. Click Date Range.
4. Do one of the following:
t To search for user accounts with a last login date that matches a specified date
range, click Last Login.
t To search for user accounts created within a specified date range, click Account
Created.
5. Specify a date range in the From and To fields.
6. Click OK.
7. Click Search.
The requested user name information appears.
44
Page 45

. . . At the Console
Another command you can type at the console will give you valuable information about
users:
list u-t [<username>]
This command shows the date and time a user account was created, date and time of last
login, and date and time of last password change.
If you do not specify a particular user name to check, you will get a listing for all users.
Listing Users Currently Logged in
From the iNEWS Workstation, you can see a list of all users logged in, and you can find out
whether a specific user is currently logged in.
To see a list of all logged-in users:
1. Press Ctrl+L or select Communicate > Messages > Logged In Users.
A dialog box appears with a list of users currently logged in.
2. Click OK when you are done looking at the list.
Tracking User Activity
To determine whether a specific user is logged in:
1. Select the Message bar.
2. Type the user name in the To field.
3. Move cursor to the message field, using the mouse or Tab key.
4. One of three symbols appears to the left of the To field, depending on what you type in
the To text box:
Icon Description
If the user is currently logged in, an icon of connected cables appears to the left of the
user name.
If the user is not currently logged in, an icon of disconnected cables appears to the left of
the user name.
If there is no such user name in the system, a question mark appears to the left of the user
name.
45
Page 46

3 Database Security
Recording Logins
Keep track of successful and attempted logins to preserve system security. You can spot
unauthorized users, people logging in at odd hours, or repeated attempts to guess passwords.
To monitor logins from different types of devices:
1. Change the value for the W_LOGTYPES token in the dictionary /site/dict/words. A
typical definition for this token might look like this:
W_LOGTYPES/G
Each letter in the W_LOGTYPES value represents a different type of device that can log
in on an iNEWS newsroom computer system.
The letters are the same ones that appear in the first column of a list s or list c display for
these device types.
2. To track logins by device type, add the appropriate letter to the W_LOGTYPES value.
Use the following letters:
Letter Description
G iNEWS Workstation
46
g Web Client
B Web sessions
C Community sessions
cCOM
A Interplay (Instinct or NewsCutter)
a Web Services API
I Instinct
For instance, to track logins from all devices on your system, change the
W_LOGTYPES line to look like this:
W_LOGTYPES/GBc
The letters can appear in any order.
On a busy system, this can create a large amount of console activity.
n
Page 47

Using Group Security to Control System Access
3. When a user logs in at a device of a type listed in W_LOGTYPES, a message similar to
the following is sent to the console:
Apr 5 16:25:47 NRCS-A G3494: Attempted login bloyd 172.24.96.247
3.1.1.2/3.1.1.3 RH5
This message includes the device type and number, time of login, user name, IP address
of PC used, and client version number.
4. A logout message similar to the following is sent to the console when the user logs out:
Apr 5 16:23:55 NRCS-A G3495: Logout fiatala 172.24.96.247 {9}
3.1.1.2/3.1.1.3 RH5
A failed login—that is, an invalid user name or password—produces a message similar
to this:
Apr 5 16:25:47 NRCS-A G3494: Attempted login bogus 172.24.96.247
3.1.1.2/3.1.1.3 RH5
Regardless of the W_LOGTYPES value, a message is always sent to the console when a
superuser logs in or out. This message includes (n) if the user is a superuser. An
unsuccessful login by a superuser generates a message only if the device type used is
included in W_LOGTYPES.
Using login tracking in conjunction with console history and disk logging, you can keep
accurate records of who is using your system and when and where they are connecting
to it.
A listing of currently logged in users may be obtained from the console using the list s
command. See “list s” on page 149 for more information.
Using Group Security to Control System Access
Your system is designed to be used by a wide range of people. For the system to
accommodate so many diverse job roles, restrict sensitive areas of your database to
authorized users. The system’s powerful security features let you restrict access to important
directories and queues.
c
Security ensures that only authorized people can view or make changes to important
queues. It does not provide absolute privacy, because superusers can open any story
while performing normal system maintenance. Warn your staff not to store personal or
confidential material in the database.
Many security features in iNEWS involve establishing groups and assigning privileges and
restrictions to them. The iNEWS Setup and Configuration Manual gives you complete
information about using the group features in iNEWS to help you maintain system security.
47
Page 48

3 Database Security
48
Page 49

4 Database Management
This chapter provides you with information required to manage the iNEWS database, where
all business data, such as stories, is stored. Much of the iNEWS system data is stored in
configuration files, which is covered in the Avid iNEWS Setup and Configuration Guide.
This chapter contains the following main sections:
• Monitoring Free Space
• Tracking Database Space over Time
• Increasing Database Space for Immediate Use
• Maintaining the Database
Page 50

4 Database Management
Monitoring Free Space
The iNEWS newsroom computer system is constantly collecting wire stories and adding
them to the database while the news staff adds scripts, rundowns, memos, assignment sheets,
and other stories. To avoid running out of disk space, iNEWS tracks old stories. As stories
get old, the system purges them.
Distribution and purging of disk space is called the database cycle. In this cycle, wire stories
are collected and stored in the database for a specific interval of time. Other news items,
such as scripts and assignment sheets, are created by the news staff and also kept for a preset
period of time, called the purge interval, which is set individually for each queue. Any story
older than its queue’s purge interval is purged, and its space is reclaimed for new stories.
The purge interval is a database trait, so you can set different purge intervals for queues and
directories, depending on the information they hold. Setting purge intervals appropriate for
stories in various queues helps keep the database from growing too large.
Once an hour, at 15 minutes after the hour, an automatic dbpurge program scans each queue
for stories older than the queue’s purge interval and moves these stories into the Dead queue.
Stories sent to the Dead queue are not erased until the system needs the space. Until the
system reclaims this space, stories in the Dead queue can be read, searched, edited, copied,
or printed. To retrieve a story from the Dead queue, select the story and copy it to a different
queue in the database, where you have write permission.
Although you can open stories in the Dead queue, they are marked for removal and will be
permanently removed when the system detects the computer is running out of storage space.
Your system keeps track of the space available by examining and maintaining a list of free
space on the disk. The free list is explained in “Monitoring the Free List” on page 51.
Understanding Database Storage Units
Your computer’s disk is divided into blocks. The database portion of the disk is divided into
1024-byte blocks. When a story is saved, the system allocates as many blocks as necessary
to hold the story and then divides the story among those blocks.
Blocks used to hold a story need not be sequential; a story can be saved in blocks that are
apart. To tie together all blocks, each block contains a reference to the block containing the
next part of the story.
A block is either “in use” or “free”.
Previous versions of iNEWS worked on 32-bit operating systems with 1k blocks; iNEWS v4.0
n
and later runs on RHEL 6, a 64-bit OS with 4k blocks.
50
Page 51

Monitoring the Free List
The free list is the list of free space on the disk. By keeping track of space in the free list, the
system can detect when it is running low on space. It runs an automatic
which removes the oldest stories from the Dead queue and adds the space to the free list,
where it is made available to the system. This way, dbserver maintains the volume of free
space available in the database.
The free list measures space in blocks (a block=1024 bytes), and has a lower limit called the
lowwater mark, which represents the least amount of free space available. When the space
available drops below the lowwater mark, the system runs dbserver to reclaim enough space
from the Dead queue to rebuild the free list to the highwater mark.
Together, the highwater and lowwater marks determine the free list’s normal operational
range. If the system cannot get back up to the highwater mark after reclaiming free space,
the user will get a low on space message. Create free space immediately, as explained in the
following section.
Understanding How the System Copies Stories
You can configure iNEWS to distribute a wire story to several queues when it is received.
Likewise, two or more users can put copies of the same story into their personal queues. If
you copy and distribute enough stories, a large portion of the database can become cluttered
with the copies.
Monitoring Free Space
dbserver
program,
To avoid filling up the disk with copies of stories, your system keeps only the original story
on the disk. When a story is copied to another queue, your system puts a reference to the
original story in the queue that will hold the copy.
When someone opens a copy of a story, the system uses the reference to find the original
story. It makes a working copy of that story, which it sends to the user. If the user examines
the working copy and makes no changes, the working copy is deleted when the user closes
the story.
However, if the user makes changes to the working copy and saves it, the system saves that
copy as a story, replacing the reference.
In most cases, you can treat a reference to an actual story as if it were the story. The only
time you need to take references into consideration is when setting purge intervals. When the
system references a story to several different queues, each reference takes on the purge
interval of the queue. When a reference becomes older than its queue’s purge interval, the
computer puts the reference, not the actual story, in the Dead queue.
51
Page 52

4 Database Management
The space used for a story becomes free only when the last reference to the story has been
removed from the system.
Tracking Database Space over Time
Do not wait until you encounter an “out-of-space” condition before you start to think about
database storage. There are two ways you can get a good picture of space usage over time:
• The “hogs” report
• The information generated by the dbfree command
Using the hogs Command to Obtain Information
The hogs command displays how much space particular queues are using in the database. It
uses this format:
hogs [<directory or queue name>]
To get a hogs report on the People directory, type:
hogs people
52
A screen similar to the following appears:
% USED SHARED HELD LOCKED PURGE QUEUE NAME
0 36 20 0 0 0 PEOPLE.LEVY.BYLINE
0 128 20 0 0 0 PEOPLE.LEVY.FINAL
0 32 40 0 0 0 PEOPLE.LEVY.FORM
...
0 425 40 0 0 0 PEOPLE.WALTERS.NOVEL
The USED column contains the number of blocks used in that queue. The SHARED column
indicates the number of blocks used in that queue that are also used in other queues. To get
the number of blocks used only by that queue, subtract the SHARED count from the USED
count. If any queue has a substantially greater number of used blocks than the others,
examine that queue more closely.
Page 53

Increasing Database Space for Immediate Use
To obtain a hogs report on the entire database, type:
hogs .
To send a hogs report to yourself, type:
NRCS-A# sh
# hogs . | mail <your username> &
For more examples on how to use the hogs command, see “hogs” on page 138.
n
Using dbserver and dbfree to Obtain Information
To obtain an accurate idea of how much space is being used by stories in the system:
1. Empty out the Dead queue and reclaim all space used in it. Type:
dbserver 16000000
You must run dbserver when other programs like dbpurge are not running.
n
2. The next day, or after completion, run the dbfree program to see how much space is
being devoted to functions in your newsroom you consider critical.
3. Repeat this process from time to time, so you are aware of trends in space usage.
Use the information to make decisions on projected storage needs, and how space is
used.
Increasing Database Space for Immediate Use
If your database has not reached the “Low on Space” point, but you want to increase free
space for immediate use, do the following:
To increase free space for immediate use:
1. Type the command that appears on bold:
NRCS-A$ dbfree
database size 16,386,300 free 1,746,564 = 11%, freelist 1,493
The dbfree command—used by a system operator or a superuser—displays database
size, free list size, and percentage of remaining database available. The freelist number
indicates how many database blocks are used to hold the free list. The free list is
compressed. This results in anywhere from 250 to 5,000 free-block numbers contained
in each free list block. In this example, 1,493 blocks are used to hold the 1,746,564 free
block numbers. That is an average of 1,169 free block numbers per free list block.
53
Page 54

4 Database Management
2. Back up old material to tape and remove it from the database.
3. Check and reset purge intervals of Wires directories and queues.
To view purge intervals at the console, type:
list d wires
Information similar to the following appears:
SRPlo-LIsUG-QSXWFiT sortfield purge dis mbox directory
D-R-----I----Q-XW--- TITLE P4.0 D1 - WIRES
D-R-----I----Q-XW--- TITLE P4.0 D1 - WIRES.ALL
D-R-----I----Q-XW--- TITLE P4.0 D1 - WIRES.AP
...
One of the biggest consumers of database space in a newsroom is the Wires directory.
Because wire stories lose much of their value after a few days, most newsrooms set a
purge interval of 2 or 3 days. In this example, all Wires directories and queues have a
purge interval of four days. The purge interval is a database trait you can customize for
each database directory or queue. For more information on modifying database traits,
including purge intervals, see the Avid iNEWS Setup and Configuration Guide.
Maintaining the Database
The following sections describe the two most important maintenance procedures you should
perform regularly on your database:
• Check the database for errors
• Clean up the database on a monthly basis
Checking the Database for Errors
In the large databases typically maintained by newsrooms, minor errors can develop in some
stories as a result of vast amounts of information the system processes every day. These
errors can grow and eventually begin to damage the database if they are not removed.
To check stories in your database for errors, use the dblines console command, which
examines every story in the database. You can run dblines on any server while the system is
online. It can point out problems or errors in the structure of the database, find queue
corruption that must be fixed before a dbvisit is run, and make some repairs. It cannot
reclaim unreferenced blocks, adjust link counts, or rebuild the free list; dbvisit is required for
that.
54
Page 55

Maintaining the Database
Since dblines examines every story in your database, it requires several hours to complete its
task, so run dblines before you go home at night. By the time you return in the morning, it
should be done.
When dblines discovers an error, it ordinarily sends an error message to the console.
However, if you run it at night, you can have the system send its messages to a log file for
you to review the next day.
For more information on the various commands used in this section, see “Command
n
References” on page 117.
To execute the command and have it send output to a log file:
1. Enter superuser mode on the master computer.
2. Type:
To execute the dblines command so it logs at a specified time:
1. Enter superuser mode on the master computer
2. Get the current time, using the date command:
You must use 24-hour military time.
n
3. Set the schedule, such as 5 minutes later, using the at command:
4. Type the dblines command line:
dblines . > /tmp/dblines.log
You can also use the at command to schedule the dblines command to run at a specified
time. For instance:
NRCS-A# date
Sat Jul 10 11:05:07 EDT 2010
NRCS-A# at 11:10
/exc/dblines . > /tmp/dblines.log
<Ctrl+D>
Pressing Ctrl+D after entering the command line marks the end of commands to be
executed according to the at schedule. Afterwards, the server prompt returns to the
original prompt, showing the server name, such as NRCS-A#.
After the dblines is complete, you can check the log file for error messages, by using the
grep command:
NRCS-A# grep failed /tmp/dblines.log
55
Page 56

4 Database Management
This searches the log file for the word failed. If there are no errors involving queue
corruption, such as <queue> scan failed , <queue> read error, or unable to open
<queue>, the prompt will simply be returned. If there are any error messages related to
queue corruption, call Avid for assistance.
If you want to review the entire log, you can use the doc command to place a copy in a
queue you specify. For instance, replacing the previous example, the sequence of
commands (shown in bold) may appear similar to the following:
You must use 24-hour military time.
n
NRCS-A# at 11:10
/exc/dblines . |/exc/doc-ptu people.sysadmin.notes
<Ctrl+D>
job 1001340600.a at Sat Jul 10 11:10:00 2010
NRCS-A#
In the example, the system would execute the dblines command at 11:10, and then place
the output in PEOPLE.SYSADMIN.NOTES. As indicated by the pound sign (#) in the
prompt, you must be in superuser mode to execute the commands.
Cleaning the Database
Over the course of a month, the iNEWS database may develop minor errors in its
structure—the overall organization in which individual stories are arranged. These errors are
the result of normal database cycles in which old material is removed and new information is
added.
These errors grow and begin to damage the database if you do not remove them. The
database cleanup procedure identifies errors so you can repair them before they become
harmful.
Unless you are instructed to perform this procedure more often, do a database cleanup once
n
a month.
You can conduct database cleanup, using the dbvisit command, while your system offline or
online. The procedures for each are provided in the following sections:
• Cleaning Your Database Offline
• Cleaning Your Database with Online Dbvisit
56
Page 57

Cleaning Your Database Offline
The database cleanup procedure using the dbvisit command requires you to briefly take your
system offline, preventing users from logging in.
The day before performing the monthly database cleanup offline, do the following:
1. Select the console window for the master computer (typically server A).
Maintaining the Database
2. Type
To check the database structure for errors, dbvisit must perform a cursory check of stories in
n
the database, including those in the Dead queue. You can shorten the time it takes dbvisit to
examine the database by using dbserver to empty the Dead queue first.
The dbserver command initiates a day-long operation and should be done one day ahead of
the next steps in this procedure. Your system remains online during the operation.
After the dbserver operation is completed, you are ready to clean up the database
offline, by doing the following:
1. Shutdown the system, by completing the following steps:
For more details on the procedure for shutting down the system, see the Avid iNEWS Setup
n
and Configuration Guide.
dbserver 16000000
Starting the day before, allows time for the system to complete this process, which may
take several hours, before you run dbvisit.
a. From the PuTTYCS application, select the PuTTY Filter created for sending server
commands to all servers, such as iNEWS Consoles.
b. Take the system offline.
c. Log out all users.
The dbvisit command cannot examine stories being edited. You must log out
everyone on the system and stop all news programs on the servers before running
dbvisit.
to empty the Dead queue.
c
d. Run the stop all console command on all servers to stop all workstations, wires, and
other devices from making further changes to the database.
After using the stop all command, wait a few seconds for the prompt to reappear. When
it does, proceed to the next step.
If conducting a dbvisit offline, ensure system is offline and that you have stopped all
network devices. If you do not do this before cleaning your database, you may corrupt
the data when you perform the cleanup. For procedures to conduct an online dbvisit,
see “Cleaning Your Database with Online Dbvisit” on page 59.
57
Page 58

4 Database Management
2. Start the database cleanup by doing the following:
a. Select the console window for the master computer (typically server A).
b. Enter superuser mode.
c. Type:
Running dbvisit on all servers instead of just the master computer is an option, performed by
n
dbvisit -dr
typing
dbvisit is running on the master server. The read-only dbvisit cannot be started until the
read-write dbvisit reaches the 'traversing directory' phase. After dbvisit runs on all
computers, the output can be compared to verify the integrity of the mirror.
dbvisit -d
A message similar to the following appears:
09:31:45 opening database
09:31:45 traversing roots
The -d instructs dbvisit to print a period each time it visits a new queue and a colon
for every 1,000 stories in a queue. After you have done a few cleanups, you can
judge how far dbvisit has progressed by the number of periods it has printed. When
you run dbvisit, it begins with the root file structure and then examines the entire
directory. As it inspects the root files and then the directory, dbvisit prints messages
indicating its progress.
-l
Add the
the output. If there are link count discrepancies, the system will list them. Such
advisory messages about high and low link counts are not errors, however, you will
be prompted to correct them.
The dbvisit process has four main phases:
flag (the letter L) to include the link count distribution information in
. The 'r' indicates read-only mode, and it can run while the read-write
58
- Visiting the “root” blocks
- Traversing the project, directory and queue structures
- Visiting the stories
- Updating the free list and fixing link counts
3. Beginning with iNEWS version 4.x, dbvisit was modified so that it would no longer
allow you to update the free list if critical errors are found in the database. Instead, if
critical errors are found, dbvisit will attempt to traverse the directories, reporting all
errors it finds, and then completes without offering an opportunity to update the free list.
Errors reported during the traversal of stories are not considered critical. Therefore, if
the system presents you with the question: Update the free list (y/n)?, do one of the
following:
y
t Type
t Type
to update the free list.
n
to skip the update.
Page 59

Maintaining the Database
If there are many story errors, you may want to skip the update and contact Avid to assess
n
the problems.
In addition to spotting errors in the database structure, dbvisit collects any
unreferenced blocks and puts them on the free list. Unreferenced blocks are not
used by any story and are not a part of the free list. They are stray blocks that cannot
be used until they are put on the free list. Skipping this update of the free list retains
the old free list. While this means that unreferenced blocks are not collected back to
the free list, you can add them to the free list later by performing another dbvisit.
4. Restart your system, by doing the following:
a. From the PuTTYCS application, select the PuTTY Filter created for sending server
commands to all servers, such as iNEWS Consoles.
b. Exit superuser mode by pressing Ctrl+D.
c. Type
d. Type
The system displays Hot-to-go messages as the devices start. If a device cannot be
started, a failed message is displayed for that device. Wait for the other devices to start,
then use standard procedures to restart failed devices, as covered in the Avid iNEWS
Setup and Configuration Guide.
Cleaning Your Database with Online Dbvisit
If performing a dbvisit offline prevents usage of your system for too long a period of time,
there is a way to run dbvisit while your system is online, letting system administrators do
crucial database maintenance without stopping iNEWS users from doing their work.
The strategy used to allow an online dbvisit is to checkpoint the system in a quiet/inactive
state, and to maintain the checkpoint state by copying any block that is to be change in the
database onto the checkpoint partition, namely /dev/rp5backup prior to writing the block
onto the database partition - /dev/rp5.
Your system must be shutdown briefly before initiating checkpoint mode. But after
checkpoint is turned on, you can bring your system online for iNEWS users while
performing database cleanup with the dbvisit command.
Do not conduct an online dbvisit without checkpoint mode initiated.If you do, not do this
n
before cleaning your database, you may corrupt the data when you perform the cleanup.
online
restart all
to bring the system back online.
to restart all devices.
59
Page 60

4 Database Management
To perform an online dbvisit:
1. Bring the iNEWS system down and close the database on all servers. This is only for the
very brief period of time it takes to ensure checkpoint mode is active.
a. From the PuTTYCS application, select the PuTTY Filter created for sending server
commands to all servers, such as iNEWS Consoles.
b. Type
c. Type
offline
logout all
to take the system offline.
to logout all users. You might want to broadcast a message to
users prior to this so they can save their work and prepare for the brief downtime.
d. Type
shutdown
to stop all devices and close the database.
e. The system will present a warning and question: Do you really want to do this?
y
(y/n)? Type
to shut down the system.
2. Initiate checkpoint mode.
a. (Optional) Type the
status
command to determine which server is the master
computer and view the current status of the database.
For instance:
WAVD-A# status
A is OFFLINE and has been CONFIGURED. ID is WAVD.
System is AB. Master is A.
Disk status is OK. The database is CLOSED.
b. Select the console window for the master computer (typically server A).
c. Type
Attempting to turn checkpoint on while the database is open will result in the following
n
warning: Database must be CLOSED when activating checkpoint --
checkpoint on
to reopen the database in checkpoint mode.
60
3. Bring the iNEWS system online.
a. From the PuTTYCS application, select the PuTTY Filter created for sending server
commands to all servers, such as iNEWS Consoles.
b. Type
online
c. (Optional) Type the
to bring the system online.
status
command to view the current status of the database.
For instance:
WAVD-A# status
A is ONLINE and has been CONFIGURED. ID is WAVD.
System is AB. Master is A.
Disk status is OK. The database is OPEN with checkpoint.
Page 61

Maintaining the Database
Users can now log in to iNEWS.
4. Start the database cleanup by doing the following:
a. Select the console window for the master computer (typically server A).
b. Enter superuser mode.
c. Type:
More details on the dbvisit command syntax and all of its flags are provided in Command
n
References appendix of this guide. See“dbvisit” on page 132 for more information.
5. Beginning with iNEWS version 4.x, dbvisit was modified so that it would no longer
allow you to update the free list if critical errors are found in the database. Instead, if
critical errors are found, dbvisit will attempt to traverse the directories, reporting all
errors it finds, and then completes without offering an opportunity to update the free list.
Errors reported during the traversal of stories are not considered critical. Therefore, if
the system presents you with the question: Update the free list (y/n)?, do one of the
following:
dbvisit -cd
A message similar to the following appears:
09:31:45 2013-06-30 Using checkpoint partition
09:31:45 traversing roots
-----message truncated for documentation brevity-----
The dbvisit process has four main phases:
- Visiting the “root” blocks
- Traversing the directory, queue, and project structures
- Visiting the stories
- Updating the free list and fixing link counts
y
t Type
t Type
If there are many story errors, you may want to skip the update and contact Avid to assess
n
the problems.
6. At the end of the dbvisit process, you might be presented with the question: Do you
want to turn off the checkpoint (y/n)?
t Type
to update the free list.
n
to skip the update.
y
to turn checkpoint mode off.
A message similar to the following appears:
09:51:17 Checkpoint partition closed
09:51:17 complete - Elapsed time: 20:32
61
Page 62

4 Database Management
7. (Optional) Type the
status
command to view the current status of the database.
For instance:
WAVD-A# status
A is ONLINE and has been CONFIGURED. ID is WAVD.
System is AB. Master is A.
Disk status is OK. The database is OPEN.
62
Page 63

5 Avid System Monitoring
This chapter provides you with information about monitoring iNEWS Server statistics via an
SNMP monitoring application such as Avid System Monitor (ASM).
This chapter contains the following main sections:
• Using SNMP Monitoring on the iNEWS Server
• Installing and Enabling the SNMP Agent
Page 64

5 Avid System Monitoring
Using SNMP Monitoring on the iNEWS Server
Avid iNEWS version 4.5 supports SNMP monitoring. SNMP monitoring applications, such
as Avid System Monitor, lets you monitor system level environmental information
dynamically through an SNMP agent. Avid System Monitor also lets you graph this
information over time. For example, the following data can be graphed over time in the Avid
System Monitor web page interface:
•Average CPU load
• Number of CPU interrupts per second
• System uptime
• Swap space (disk space reserved for memory when RAM is fully loaded)
• System memory usage
•CPU usage
By default, the SNMP Agent is not enabled.
Installing and Enabling the SNMP Agent
64
This section describes how to install and enable the SNMP agent on the iNEWS Server. See
your Avid representative for information about setting up an Avid System Monitor server
and configuring it to monitor the iNEWS Server.
These steps should be performed only by qualified Avid personnel.
n
To install the SNMP agent on the iNEWS server:
1. Install the net-snmp Red Hat 6 packages. This will create a /etc/snmp directory.
2. Set up the snmpd.conf configuration file. In the /etc/snmp directory, locate the
snmpd.conf file. Using a Linux editor, open the configuration file and add the following
information near the top of the file.
a. Replace the public value in
b. Locate the line with
city.
c. Locate the line with
3. Save the changes and exit.
rocommunity public
syslocation
syscontact
and add your location, such as the name of your
and add your iNEWS administrator email.
with your community name.
Page 65

Installing and Enabling the SNMP Agent
To enable the SNMP agent process:
t In a console to the server, type:
# service snmpd start
t (Optional) Set snmpd to automatically start at boot by typing:
# chkconfigsnmpd on
To disable the SNMP agent process:
t In a console to the server, type:
# service snmpd stop
65
Page 66

5 Avid System Monitoring
66
Page 67

6 Backing Up the iNEWS System
Proper maintenance of the iNEWS system requires three kinds of backups:
• Database backups—of the iNEWS database
• Software backups—of iNEWS software and the operating system
• System file backups—of files like /site/config and /etc/hosts
This chapter explains the procedures for the various types of backups necessary to maintain
the iNEWS system. It also provides general information about using tapes and tape drives or
conducting a tapeless backup for iNEWS on RedHat Enterprise Linux.
This chapter contains the following main sections:
• Tape Operations
• Backing up the iNEWS Database
- Backing up the Entire Database to Tape
- Tapeless Database Backup
- Backing up Individual Queues
• Restoring Data to the iNEWS Database
• Disaster Recovery Planning
• Backing up Software
• Backing up System Site Files
Page 68

6 Backing Up the iNEWS System
Tape Operations
When making backup tapes, pay particular attention to the write-protect tab on the tape. If
you have trouble writing to the tape, check the tab and try moving it in the opposite
direction.
When loading a tape, ensure the tape has finished loading before issuing tape commands.
Trying to access the tape before it is ready may result in a “hung” process that waits forever
for the tape to be ready. The only solution is a reboot. For DAT tapes, wait at least a minute
after all tape activity lights cease blinking to be sure the tape is properly loaded.
Always clearly label tapes with the type of backup tape it is, date it was produced, and
n
command used to produce it. Ensure that your tapes can be found quickly, in case of
emergency.
Since the database is mirrored on all servers in your system, it does not matter on which
server you produce the database backup tape. You might want to rotate which server does the
database tape dump so the tape drives wear evenly and you extend the life of the drives.
Alternatively, you might want to always run the backup on one server’s drive so you have
another, relatively unused drive standing by in case the heavily-used drive develops
problems. However, for software and site file backups, Avid recommends separate backups
be made on each iNEWS Server.
Later in this chapter, various procedures are provided for checking data on tapes, searching
for specific data on tapes, and restoring data from tapes. For more information, see “Listing
Tape Contents and Backup Dates” on page 81 and “Searching a Tape” on page 84.
Establishing Policies for Backup Procedures
Since your software and system files change infrequently, you do not need to back them up
very often. Your database, however, changes hundreds or even thousands of times every day,
so they need more frequent backups
Avid recommends your station establish and follow a local backup policy for each type of
data in your iNEWS system.
The following list has some general backup guidelines:
• Since the database is mirrored across multiple servers you have built-in hardware
redundancy. Backups also provide some protection against the rare cases of database
corruption.
• One approach is weekly backups rotating through 5 tapes, one for each week of the
month. If you need to keep old data for a period of time you may supplement the five
tape rotation with 12 more tapes labeled with the months in the year.
68
Page 69

• Do not store archived material beneath daily show production queues. Segregate archive
material under it’s own directory.
• If you archive old shows on your system, you might want to produce dbdump tapes that
cover old years For instance, ARCHIVE.2008 through ARCHIVE.2009, and store them
separately.
• It is a good idea to make extra copies of the tapes and store them off site. If your
computer room is destroyed, you can buy new servers. But if the computer room is
destroyed with all backup tapes stored in the room, your data is lost. Many corporations
use off-site storage services for backup tapes.
Backing up the iNEWS Database
Database backups provide insurance against system calamities. Also, to free up space in the
database, you can back up stories to a tape—or to a file, which can be transferred to another
computer for storage—and then remove those stories from the database.
Avid recommends making frequent backups of important material and the entire database.
To back up database items, you will need to use the dbdump console command.
Backing up the iNEWS Database
The dbdump Command
The dbdump command backs up the news database, including the People files, show
rundowns, wire stories, and root database information such as user accounts, passwords, and
directory traits. All user, database, and group traits are stored within the database.
The simplest form of the dbdump command is:
NRCS-A# dbdump c
The c stands for create. When you use this command, it overwrites any information currently
on the tape and does a full database backup of everything—except the contents of any queue
or directory with its skip flag enabled.
The skip flag is a database trait that prevents the dbdump c command from backing up
n
contents of queues and directories. Generally, Wires queues and the Dead queue are usually
skip-flagged so they are not backed up. This results in less time for the backup and less tape
used. If a dbdump reaches the end of the tape and still has more data to back up, you will be
prompted for another tape. For more information on skip flags—also known as the Skip
Backup database trait—see the iNEWS Newsroom Computer System Setup and
Configuration Manual.
69
Page 70

6 Backing Up the iNEWS System
For instance, to dump all database items contained in the SCRIPTS.2010 directory to tape,
you could type:
dbdump c -n script.2010
If you already have dbdump material on tape and you want to append another dbdump to the
end of it, use the following command:
NRCS-A# dbdump ad
An append does not overwrite dbdump information currently on the tape. See “Backing up
Individual Queues” on page 77 for more information.
To minimize the impact of any potential problems, perform dbdump at less critical usage
n
periods.
Backing up the Entire Database to Tape
This section provides the procedure for backing up the iNEWS database to a tape. For
information on tapeless database backups, see “Tapeless Database Backup” on page 72.
To back up the entire database to tape:
c
1. Insert a tape into a server’s tape drive.
2. Select the server that has the backup tape. For information on selecting a server, see the
iNEWS Newsroom Computer System Setup and Configuration Manual.
3. Type
When backing up the database onto a tape, anything on that tape is overwritten by the
new copy of the database.
4. Type
dbdump c
A verification request similar to the following appears:
Do you really want to create a new archive? (n/y)
y
to begin copying the database to tape.
Information similar to the following appears:
Starting Dump(1), block(0)
dumping isam user
...
3121 stories dumped
Ending Dump(1), block(223)
.
70
Page 71

Backing up the iNEWS Database
As dbdump copies, the console displays messages like those above. The number of
stories dumped and the ending block mentioned in these messages depends on your
system.
When the console prompt returns, the backup is done. You can then verify the backup.
Otherwise, remove the tape from the drive. Set the tape’s write protect switch to the on
position, return it to its case, and write the date on the case label.
5. (Optional) Type
dbrestore tdv
at the console to verify the backup was
complete—that everything you wanted backed up was copied to tape.
The dbrestore tdv console command lists every directory and queue on the tape. Since
the tape contains most of the database, this list is very long.
To list contents of a tape, the server must read the entire tape; therefore, listing contents
n
takes approximately as long as it does to back up the database to tape.
A truncated example of the output of the dbrestore tdv command looks like this:
Listing tape contents only!
Type Stories Name
Dir
Que DEAD
Dir SYSTEM
Dir SYSTEM.KEYBOARDS
Que 1 SYSTEM.KEYBOARDS.000-INSTALLATION
...
Que 3 TEST.SMITH
3630 stories listed
The first column of the listing identifies whether the item is a queue or a directory. If it is
a queue, the second column indicates how many stories are in that queue. The third
column displays the name of the directory or queue.
If any queues in the list do not have stories listed, then either the queue has no stories, or
the queue has its skip flag enabled. If the skip flag is enabled, the queue name is copied
to tape, but none of its stories are copied. In the previous example, the Dead queue does
not have any stories on the tape.
6. When the list is complete, remove the tape.
7. Set the tape’s write protect switch to the on position, and write the date on the case label.
71
Page 72

6 Backing Up the iNEWS System
Tapeless Database Backup
Instead of backing up the iNEWS database to tapes for potential restoration, you can dump
the information to a file and then transfer (FTP) the backed up data to another computer for
storage. The more compact way to do this is to use the dbdump C command piped through
gzip and directed to create a file in the /tmp/directory. For instance, type:
NRCS-A$: dbdump C -f+ |gzip > /tmp/061709.gz
To dump information to a file without the gzip option:
1. On an iNEWS Server, use the dbdump command in the following format:
dbdump Cv -f <path/file name>
For instance, type:
NRCS-A$ dbdump Cv -f /tmp/dbdump.061709
The C option creates a new dump file, and the v option switches on the verbose mode,
which gives you an idea of progress. After you enter the command, a message similar to
the following is displayed:
Starting Dump(1) Block(0), dumped on 2009-06-17 16:33:37
Dumping ISAM files
Dumping user
Dumping message
Dumping group
Dumping system-blobs
Dumping community
Type Stories Name
Dir
Dir SHOW
Dir SHOW.TRAINING
Que SHOW.TRAINING.RUNDOWN
Que SHOW.TRAINING.CG
Que SHOW.TRAINING.VIDEO
Que 44 SHOW.TRAINING.MASTER
72
Page 73

Backing up the iNEWS Database
…
Que 1 SHOW.MOSGWE
Que 31840 SHOW.VID-ID
Dir SHOW.SCRIPTWRITING
Que SHOW.SCRIPTWRITING.ONE
Que SHOW.SCRIPTWRITING.TWO
Que SHOW.SCRIPTWRITING.THREE
Que 5 SHOW.NEWSTARTEST
Que ARCHIVE.SCRIPTS.2009
310 directories scanned
1684 queues dumped
3109046 stories dumped
Ending Dump(1) Block(136), dumped on 2009-06-17 16:33:37
2. On a Windows-based PC with at least 16 GB free for storage, start a command prompt
CMD
session, by selecting Start > Run and then entering
3. Navigate to the directory on the PC where you want to store the backup file by typing
and the directory path. In this example, the directory is
.
C:\dbdumps
cd
.
4. At the cmd prompt, type
ftp -i
and press Enter to start the FTP session.
73
Page 74

6 Backing Up the iNEWS System
5. Then type the open command using the following format:
open <resolvable name or IP of iNEWS Server> 49152
The numerical value at the end of the command line is the number for the port, which
should be 49152.
74
so
6. Type
and press Enter. Then enter the system operator password when prompted. A
message will appear to indicate whether the login was successful.
Page 75

Backing up the iNEWS Database
7. Type
8. Type
cd /tmp
binary
to change to the /tmp directory.
to change to binary mode.
9. (Optional) You can list the directory contents to get the name of the file you want to
transfer, by entering the command:
ls -l
10. To transfer the dump file, enter the get command using the following format:
get /tmp/<filename>
75
Page 76

6 Backing Up the iNEWS System
76
The FTP command prompt will reappear in the window as a definitive indication that
the transfer has finished. However, you can check the directory on the Windows PC for
the presence of the file; it is created as soon as the transfer begins, and the size will
continue to grow during the transfer process.
The file will be much larger than the one shown in the example here, so the transfer can take
n
a while to complete. Avid suggests conducting file transfers (FTP) from computers that do
not have aggressive power saving settings in place.
Page 77

Backing up the iNEWS Database
11. Type
12. Type
bye
to end the FTP session.
exit
to exit the command prompt window.
You are now ready to remove the temporary dump file.
While you can leave one or two in the /tmp folder temporarily, Avid recommends that no
n
more than a couple of database dump files be kept at any given time. Removal of older dump
files will help avoid running out of hard drive space on the server.
13. Use the rm command at the console to remove old database dump files from the /tmp
folder on iNEWS.
a. Enter superuser mode, first.
NRCS-A$ su
Password:
b. Type the rm command, using the following format:
NRCS-A# rm /tmp/dbdump061709-div
rm: remove regular file ‘/tmp/dbdump061709-div’?
rm /tmp/<file name>
c. Type y to answer verification question.
rm: remove regular file ‘/tmp/dbdump061709-div’? y
d. (Optional) When the prompt reappears, such as NRCS-A#, you can verify the file’s
removal by viewing the contents of the /tmp folder again.
NRCS-A$ cd /tmp
NRCS-A$ ls -l
Backing up Individual Queues
Individual queues can be backed up by specifying the -n flag and listing up to 10 queue or
directory names:
NRCS-A# dbdump c –n <queue or directory name>
To back up individual queues or directories to tape:
1. Insert tape into a server’s drive and select that server.
2. Use the dbdump command in one of the following formats:
t If you do not have a tape that already contains a backup, insert a new tape and back
up the queue. For instance, to back up SCRIPTS.2010.FEB on a new tape, type:
dbdump c -n scripts.2010.feb
77
Page 78

6 Backing Up the iNEWS System
A verification request appears:
Do you really want to create a new archive? (n/y)
If there is nothing on the tape that you want to save, type y to continue. A message
similar to the following will appear:
Starting track(1), block(0)
47 stories dumped
Ending track(1), block(34)
When you back up a queue, dbdump ignores the queue’s skip flag, so you can use it to back
n
up a queue or directory that has its skip flag enabled. You can also use this process to save a
queue or directory to tape before removing it from the database. For instance, if you want to
restore database space by removing a queue with material no longer used, use dbdump to
backup the queue first. Then, if you need it later, you can retrieve it from the tape.
t If you have previous backups on the tape, append the next backup to the tape with:
dbdump a -n <queue or directory name>
You can append additional backups to that tape until you use up all space on the
tape. Continuing with the previous example, the next day you would insert the same
tape, make sure its write protect is off, and then type
scripts to the tape:
dbdump a
to append that day’s
78
For instance, after making the first backup of SCRIPTS.2010.FEB shown in the
previous example, back up SCRIPTS.2010.MAR the following month by inserting
the same tape and entering the following:
dbdump a -n scripts.2010.mar
If you try to use dbdump a with a tape that does not already contain at least one backup, you
n
get an Empty tape message. If this happens, use dbdump c instead.
3. When the console prompt returns, the backup is done. Remove the tape and set the
write-protect switch on. Date the tape case label.
4. To verify the backup, type:
dbrestore tdv
This list should be short, but it could take time to complete if the tape contains several
weeks’ worth of backups.
Page 79

Notes on Backing up the Database
If you try to back up data to a write-protected tape on the Linux platform, you get a message
similar to the following:
NRCS-A# dbdump c
Do you really want to create a new archive? (y/n) y
Starting Dump(1) Block (0), dumped on Thur Jul15 ‘0:36:14: 2010
dumping isam user
Please remove tape.
Insert continuation tape (make sure safety is off)
When continuation tape is ready type: y (RETURN)
If the tape is write-protected, remove it from the drive. On some tape drives you can change
the write-protect without removing the tape. Set the write protect switch to off, insert the
tape, and repeat dbdump.
Restoring Data to the iNEWS Database
Daily backups usually take very little time and generally do not affect system performance.
However, backing up a large amount of material to tape may hinder system performance, so
you should only do it during times of lighter system use.
If you have a very large database, the full database backup may require two or more tapes.
The system prompts you to insert the next tape. Remove the current tape, number it as tape
number one, and insert another tape. The server automatically continues copying the
database when you insert the second tape.
Restoring Data to the iNEWS Database
The following sections describe how to restore data from tape.
The dbrestore Command
Tapes produced with the dbdump command can be read back in and restored using the
dbrestore command. The most common use of the dbrestore command is to restore a specific
queue or directory. This is done by specifying the name on the command line:
NRCS-A# dbrestore d –n <queuename> <queuename> ...
79
Page 80

6 Backing Up the iNEWS System
You can use the dbrestore tdv command to verify that you can properly read a dbdump tape.
n
Check free space before you restore large amounts of data to the database. Before you
dbrestore stories or queues to your database from tape, ensure you have enough free space
available to hold the restored stories. You can create free space using the dbserver command
to empty out some of the Dead queue and add that space to the free list. A conservative
estimate would be to have 10 free blocks for every story you plan to restore.
When the -i option is used with the dbrestore command, dbrestore does not create any index
n
requests in SYSTEM.INDEX when stories are restored to indexed queues.The dbrestore
process is slowed when attempting to create index requests. Avid recommends the database
be restored using the -i option and the stories be re-indexed at a later time.
Restoring a First-Level Directory
Restoring a first-level directory, such as Scripts, as opposed to SCRIPTS.FEB, is the same as
restoring queues and other directories. However, when restoring such a directory, you also
have the option of restoring it under a new name. Use:
dbrestore d -n <old dir. name>[=<new dir. name>]
If the new directory does not already exist, dbrestore creates it.
80
For instance, suppose you have a directory called Scripts and you want to restore a previous
backup of this directory to another directory called Scripts-temp, which does not exist. Type:
dbrestore d -n scripts=scripts-temp
A message similar to the following appears:
744 stories restored
Since Scripts-temp does not exist, dbrestore creates it before restoring Scripts-temp. When
dbrestore has restored all stories in Scripts-temp, it displays a message indicating how many
stories were restored.
If you want to restore a specific directory, be sure to always include the
n
name. If you do not, dbrestore tries to restore everything on the tape to your database, which
could cause your system to run out of space.
You may not restore a first-level directory to a lower level. In the example above, for
instance, we could not have restored the Scripts directory to SCRIPTS.MAY.
-n
and the directory
Page 81

Restoring Data to the iNEWS Database
When you restore a first-level directory to an existing directory, it acquires the traits of that
directory. If dbrestore must create the directory, it uses database traits of the directory it is
restoring.
c
If the new directory name is longer than the old one, there is a possibility that
sub-directory names may become too long and cannot be restored. When the new name
is longer than the old name, the dbrestore program will prompt with the following
warning message: WARNING: Alias too long! It should be shorter or the same length
as current directory name to avoid exceeding directory name length restrictions.
Do you really want to continue? (n/y)
Listing Tape Contents and Backup Dates
When restoring a directory, you might need to examine the tape’s contents to ensure the
directory you want to restore is actually on that tape. Otherwise, if you attempt to restore a
directory or queue that is not on the tape, the system may take several minutes to search the
entire tape before reporting no stories restored.
The pages that follow show you how to use the dbrestore command to list the directories and
queues that have been backed up on a tape, to find out if the tape contains any stories saved
after a certain date, and to find out the date of each backup on the tape.
Listing Contents of a Tape
If you want to list every directory and queue on the tape, as well as the number of stories in
each queue, to the server with the tape drive, type:
dbrestore tdv
81
Page 82

6 Backing Up the iNEWS System
Information similar to the following appears:
Listing tape contents only!
Type Stories Name
Dir
Que DEAD
Dir SYSTEM
Dir SYSTEM.KEYBOARDS
...
Que 3 TEST.SMITH
3630 stories listed
Each line in the list consists of three columns and identifies a directory or a queue that has
been saved to the tape:
• The Type column indicates whether the line lists information about a directory or a
queue. Directories are identified by Dir and queues by Que.
• The Stories column is used only in lines beginning with Que and identifies how many
stories are in that queue. Use this number as a guide to how much space you need to
restore the queue. If there is no number, the queue is empty. (The queue is empty
because either no stories existed in the queue or the queue’s skip flag was enabled.)
The Name column identifies the directory or queue by name.
If you attempt to restore a queue with no stories, you see the following message:
no stories restored
Listing Items Dumped on a Particular Date
To list items dumped on a particular date:
1. Use the following format of dbrestore:
dbrestore td -d <date>
2. Enter the date in YYMMDD (year, month, day) or YYYYMMDD format.
Begin single-digit months and days with a zero, such as 04 for April. Also check for
items dumped to tape during a month by using the year and the month (YYMM).
82
Page 83

Restoring Data to the iNEWS Database
You can check to see what was dumped to a tape during a year by specifying just the
year (YY).
For instance, to list everything dumped in October 2009, type:
dbrestore td -d 0910
A message similar to the following appears:
Listing tape contents only!
Type Stories Name
Dir
Dir SHOW.TODAY
Que 34 SHOW.TODAY.SCRIPTS
Que 3 SHOW.TODAY.RUNDOWNS
Continuing with Dump(2) Block(0)
Dumped Thu Jul15 10:30:19 2009
Dir SHOW.TODAY
Que 27 SHOW.TODAY.SCRIPTS
Que 3 SHOW.TODAY.RUNDOWNS
67 stories listed
In the previous example, the tape contains only backups from two dates: the first backup
and one made on July 15, 2009. Notice the date of the first backup is not included in the
listing. To find the date of the first backup, type the
below.
The dbrestore displays a Continuing with Dump
second dump.
Listing the Date of Each Backup
To list the dates of each backup on a tape:
t Type:
dbrestore tf
A message similar to the following appears:
Listing tape contents only!
Starting: Dump(1) Block(0)
Dumped Tue Jul10 15:33:01 2009
Continuing with Dump(2) Block(0)
Dumped Thu Jul15 10:30:19 2009
Elapsed time: 00:13
dbrestore tf
message just before processing the
command described
83
Page 84

6 Backing Up the iNEWS System
In the example, the tape contains two backups, one done on July 10, 2009, and another
done on July 15, 2009.
Searching a Tape
You can retrieve individual stories from a tape by searching for a word contained in the
story.
The searchtape Command
The searchtape command allows you to search through a tape looking for a specific word.
Stories that contain that word are restored to the SYSTEM.SEARCHTAPE queue. There is a
maximum number of stories or hits that will be restored with the searchtape command. This
default is specified in the /site/system file. See “Searching a Tape by Word(s)” on page 85
for more information.
When you list a tape’s contents, your system must read all information on the tape to
n
generate a list of the contents. If the tape contains much information, listing the tape’s
contents takes a significant amount of time.
Because searching tapes for stories takes a long time and can reduce system performance,
restrict tape searches to periods of lighter system use. Avid recommends running all tape
operations during non-critical periods, not during shows.
Searching a Tape for Stories
To search a tape for stories:
1. Combine one or more keywords with a date or range of dates, as described in the
following sections.
2. When the system finds a story matching the search criteria, it restores the story to the
database. Because stories on tape may be old versions of stories still in the database, the
system restores them to the SYSTEM.SEARCHTAPE queue. This prevents the system
from putting an old version of a story in a queue that contains the current version of the
same story.
After restoring a story to SYSTEM.SEARCHTAPE, you can move it to any queue.
Before restoring stories from tape, check how much free space remains in your database at
n
the console. See “Checking for Free Space on a Database” on page 87 for more
information.
84
Page 85

Searching a Tape by Word(s)
Restoring Data to the iNEWS Database
To search a tape by word(s), follow the searchtape command with the word
word(s) for which you want to search.
Use this form of the command:
searchtape for <words>
If you include more than one search word, the system searches for stories that contain any
words for which you are searching. You can search for up to 20 words at a time with this
command.
For instance, to search for stories that contain either helicopter or president, type:
searchtape for helicopter president
A message similar to the following appears:
8 stories restored to SYSTEM.SEARCHTAPE
This command finds stories with the word president and it also finds stories with the word
helicopter. It would not limit the results to stories that contained both president and
helicopter.
It is not possible to construct Boolean (and) searches using the searchtape command.
n
Always include the word “for” and one or more words for which you want to search when
you use the searchtape command. Even if you use a date or a date range as part of the search
criteria, as explained in the next section, you must include a word or words for which you
want the system to search.
for
and the
Use search criteria that is as specific as possible:
• Always use a narrow range of dates
• Use a small number of search words
• Use words likely to appear only in stories for which you are searching
Searching a Tape by Word and Date Range
To restrict a search to stories backed up between certain dates:
1. Include the range of dates to which you want to restrict the search in the
command.
The command format for this kind of search is:
searchtape from <date> to <date> for <words>
searchtape
85
Page 86

6 Backing Up the iNEWS System
Dates must be in YYMMDD (year, month, day) or YYYYMMDD format, and single
digit months and days must begin with a zero (for instance, April is 04). If you want to
specify only a month or year, shorten the date format to YYMM or just YY.
2. Follow the second date with the word
To restore stories archived between May 1, 2000, and May 21, 2000, that contain the
word helicopter, type:
searchtape from 000501 to 000521 for helicopter
A message similar to the following appears:
6 stories restored to SYSTEM.SEARCHTAPE
The searchtape command looks for stories saved to tape within the dates you specify. It does
n
not look for stories created within those dates.
Searching a Tape by Word and Day
To search for stories saved to tape on a particular day, use the search format:
searchtape just <date> for <words>
To search for stories backed up on May 15, 2010 that contains the words helicopter or
president, type:
for
and the word(s) for which you want to search.
searchtape just 100515 for helicopter president
Searching a Tape by Word and Month
To search for stories saved to tape during a particular month, follow
and shorten the date to the year and month (YYMM).
For instance, to search a tape for any story saved to tape in February, 2009 that contains the
word helicopter, type:
searchtape just 0902 for helicopter
Specifying a Maximum Number of Stories to Search
To specify a maximum number of stories for searchtape to restore, include the word max and
the number of stories you want to restore.
To search a tape for all stories that contain the word president, type:
searchtape for president
If you do not specify a maximum, the system restores up to 50 stories.
86
searchtape
with
just
Page 87

If you specify a maximum number, searchtape stops when that number of stories has been
restored, or when all stories containing the text have been found—whichever comes first.
To search a tape for the first 10 stories containing president, type:
searchtape max 10 for president
Anytime you specify more than 50 stories to restore, you are reminded that this could cause
the system to run out of disk space.
When the search is complete, searchtape stops and displays a message indicating the number
of stories it has restored.
To cancel the restore operation at any time while in progress, press Delete.
Checking for Free Space on a Database
To check free space on a database:
1. Select a server.
For information on selecting a server, see the iNEWS Newsroom Computer System Setup and
n
Configuration Manual.
Restoring Data to the iNEWS Database
2. Type:
Adding Blocks to the Free List
To add 100 blocks to the free list:
1. Select the master computer (typically server A).
2. Type:
dbfree
A message similar to the following appears:
database size 16,386,300 free 3,288,408 = 20%, freelist 3,730
In the previous message example the freelist item indicates how many database blocks
are used to hold the free list. The freelist is compressed. You should have 10 free blocks
for each story you want to restore. For instance, if you expect to find 10 stories to
restore, you should have 100 free blocks. Add extra space to the free list before
conducting a search because the search may find and restore more stories than you
expect.
dbserver 3288508
The number after dbserver must be the sum of the additional blocks and the free blocks
from dbfree.
A message similar to the following appears:
NRCS-A Sat Jul24 10:29:26 2010 dbserver complete-exiting
.
87
Page 88

6 Backing Up the iNEWS System
At this message, dbserver is finished and you may proceed. You can run dbfree again to
verify that you have enough space.
Restoring the Database
When a story being restored has more than 1,000 lines, the following message is displayed:
Warning: Large story being restored.
Queue: FUTURES.FEBRUARY
Title: "Senate Hearing"
Size: 1004 lines (approximate)
Press <del> to skip this story.
If the story size continues to grow, the following message prints every 1500 lines:
Large story continuing: 1500 lines
Press <del> to skip this story.
To skip the large story, press Delete while it is being restored.
Disaster Recovery Planning
Having a complete dbdump of the database ensures that you can restore your data in case of
calamity; however, restoring a complete dbdump to a freshly initialized database can be very
time-consuming and leave the newsroom without access to the system until the full database
dbrestore finishes. On very large databases, the full database dbrestore can take from 12 to
36 hours.
Planning a separate, efficient disaster recovery dbdump/dbrestore procedure can
significantly speed up the time before the system becomes functional to users.
Disaster Recovery Dbdump
The first step is to create a stripped down dbdump that contains the directory structure and
minimal amount of queues and directories needed to bring the system online. After the
minimal dbdump was restored, users can start working while the remainder of the database
is restored from the last full database dbdump tape.
88
Page 89

Create Minimal dbdump
The entire structure of the database, along with your designated minimal set of queues, can
be backed up, specifying the list of essential queues (or directories) to be backed up:
NRCS-A# dbdump ci -d -n <directory or queuename> ...”
The -d option dumps the news directory skeleton but will not dump any stories. The -n option
n
will dump the stories in any directories and/or queues specified. The i option will dump the
isam files.
The essential directories would be System and possibly Show and a few daily Assignments
queues. The System directory must be part of the minimal dbdump.
If master rundown skeletons are stored elsewhere, add them to your list of essential queues.
This may be the bare minimum of directories needed to get a show on the air.
Do not store archives of shows beneath the Shows directory. Having years of archive
n
material mixed in along with your rundowns and master rundowns will slow the dbrestore
significantly. If restoring Assignments queues, ensure you restore only daily queues needed
to operate; do not include all future files in the minimal dbdump.
Backing up Software
You may list up to 10 directories and queues with the -n option of the dbdump program.
NRCS-A# dbdump ci -d -n system shows assignments
In case of disaster, this minimal dbdump would be the first tape restored to the system. Since
it will not contain many stories, to dbdump to or dbrestore from this tape is relatively quick
and users can resume work while the remainder of the material trickles in from the full
dbdump tape.
This minimal dbdump tape should be updated periodically.
Backing up Software
Your system uses programs and site-dependent configuration files, called site files, to adapt
it to your newsroom operations and run the workstations, printers, wires, and other devices.
These programs and site files make your system software unique from that found in any
other newsroom.
It is important you keep a current copy of your software on tape in case you need to restore
the software area of the disk. Anytime you make major changes to the system
software—such as extracting new programs from an update tape—make a new software
backup.
89
Page 90

6 Backing Up the iNEWS System
Likewise, when you make major changes to a site file, update the software backup to include
these changes. For instance, if you add a new wireserver to your system, you define that
workstation in the configuration file. This represents an important change to this site file so,
after modifying this file, update your software backup tape.
Backing up System Site Files
Your system uses site files in combination with software taken from your release CD and
update tapes. Back up your site files on a separate tape. If anything happens to your system,
you can use your release CD and site file backup to rebuild your system software.
Make a new site file backup after making significant changes to any site file. For instance,
adding a wireserver to your system requires that you modify your configuration file
(/site/config). After making this change, make a new site file backup.
To make a separate sitedump tape for each server, repeat this procedure on each server. After
backing up a server’s site files, ensure you label the tape to clearly indicate which server’s
site files are on it.
The sitedump Command
90
The sitedump command backs up files in the /site directory and certain key files in the /etc
directory. This is where all of your site-specific configuration files are kept. The tape should
be updated whenever you make changes to your configuration.
To back up your system’s site files to tape:
1. Insert the tape into the master computer (typically server A).
2. Select the master computer.
3. Enter superuser mode.
4. Type:
5. When the sitedump is done and the prompt returns, exit from superuser mode by
6. Remove the tape and label it. Include the date and type of backup.
sitedump
Linux systems can make sitedumps to their hard drives.
sitedump -f /backups/<date>.sitedump
pressing Ctrl+D.
Page 91

7 Disconnects
This chapter provides vital information to help you recover from a system disconnect.
This chapter contains the following main sections:
• Normal System Status
• Disconnects
• Disconnect Recovery
Page 92

7 Disconnects
Normal System Status
The displays will vary when the system is a triple system configuration.
On a dual server system, the status command will show the system is AB, with both servers
connected to each other. A display similar to the following will appear on server A:
NRCS-A# status
A is ONLINE and has been CONFIGURED. ID is NRCS.
System is AB. Master is A.
Disk status is OK. The database is OPEN.
The system status is reported identically on both servers in the system. For instance, a
display similar to the following will appear on server B:
NRCS-B# status
B is ONLINE and has been CONFIGURED. ID is NRCS.
System is AB. Master is A.
Disk status is OK. The database is OPEN.
When the system is dual and databases are mirroring between the two servers, a story
written on one server is automatically mirrored to the database of the other server. When the
system is connected and has the normal prompt, the servers are in communication with each
other and the disk mirroring process is active.
Disconnects
If the servers disconnect from each other, the databases are no longer mirrored between the
two servers and immediate attention is required. Since mirroring has stopped, stories written
by users on server A will not be seen by users logged in to server B. There will be two
entirely separate databases.
There is no way to reintegrate two disparate databases. You must decide which database will
be retained as the master database, and the other database must be erased. The steps for
recovering from a disconnect are outlined later in “Procedures” on page 97.
92
Page 93

Disconnects
If a disconnect occurs, users may want to export the stories they are working on to local hard
drives, in addition to normally saving them to the server. They can export stories by selecting
File > Export Story. This will make a backup copy of the story on the local hard drive of
their PC. Since they may be logged in to the server containing the non-master database that
will be erased, this will give them a backup copy, which could be re-imported if necessary.
c
When the servers disconnect, stories written on server A are not mirrored to server B
and stories saved on B are not mirrored to A. The system issues a popup to alert users
who must contact their system administrator immediately.
Detecting a Disconnect
You can check to see if the servers are connected to each other and mirroring at any time
using the status command at the console. If they are connected and properly mirroring, they
will both agree on the system status and it will report that the system is dual (AB):
System is AB.
See “Types of Disconnect” on page 95 for more information.
If the servers disconnect, a disconnect warning message appears on the console.
93
Page 94

7 Disconnects
On the Linux platform, the messages include detailed information from the driver (mp) that
controls the mirroring:
Jul 13 07:45:44 nrcs-a IO handler: B silent for 30 seconds
Jul 13 07:45:44 nrcs-a IO handler: LINK TO B FAILED, DISCONNECTING B
Jul 13 07:46:05 nrcs-a msg: 66 to server on computer A
Jul 13 07:46:25 nrcs-a S508: [15028] monitor 508 508 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S510: [15029] monitor 510 510 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S238: [14998] seek 238 238 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S240: [14999] seek 240 240 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S236: [14997] seek 236 236 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S232: [14995] seek 232 232 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S234: [14996] seek 234 234 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S254: [15001] action 254 254 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S504: [15026] monitor 504 504 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S506: [15027] monitor 506 506 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S508: [15028] monitor 508 508 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S510: [15029] monitor 510 510 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S238: [14998] seek 238 238 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S240: [14999] seek 240 240 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S236: [14997] seek 236 236 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S232: [14995] seek 232 232 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S234: [14996] seek 234 234 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S254: [15001] action 254 254 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S258: [15003] action 258 258 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S252: [15000] action 252 252 Server - Hot-to-go
Jul 13 07:46:25 nrcs-a S256: [15002] action 256 256 Server - Hot-to-go
94
Page 95

Jul 13 07:46:25 nrcs-a disconnect: B COMPUTER DISCONNECTED
In addition to console warning messages, a warning message is broadcast to all users
currently logged in to the system via a popup window at the workstations.
Types of Disconnect
When the servers disconnect, one may disconnect from the other, or they may both
disconnect from each other.
If they have disconnected from each other, each will report that it is a single system, with
itself as the master:
NRCS-A# status
A is ONLINE and has been CONFIGURED. ID is NRCS.
System is A. Master is A.
Disk status is OK. The database is OPEN.
The single system status is reported identically on both servers:
Disconnects
c
NRCS-B# status
B is ONLINE and has been CONFIGURED. ID is NRCS.
System is B. Master is B.
Disk status is OK. The database is OPEN.
The other possibility is that servers will disconnect, but one of the servers will not note the
disconnect. In this case, one will report that the system is single while the other states the
system is still AB.
Regardless of the report, once one of the servers has disconnected, the system must be
recovered following the procedures in this chapter. The steps outlined are the only way to
recover and get the servers back in mirror.
If the system has disconnected, you cannot simply reboot the servers and bring it back
up normally. Rebooting and connecting two servers together after a disconnect can
lead to database corruption!
95
Page 96

7 Disconnects
Causes of Disconnects
Servers are normally in constant communication with each other. When a story is saved, the
server tries to mirror that change across to the other server’s database. If the server cannot
contact the other server for a period of 30 seconds, it assumes the worst—that the other
server has died and is not available and that as the surviving server it must be responsible for
the entire system.
Knowing this design, it is obvious that network outages will cause a disconnect, as will the
loss of power by one server.
A “dirty” network leading to numerous network output errors (called RX-ERRs, as revealed
by the netstat -i command) can cause a disconnect, particularly if the output errors are
rapidly climbing.
A software error that leads to a looping condition that causes a server to become so busy it
cannot respond to a mirroring request could also theoretically lead to a disconnect.
Hardware failures such as the failure of a network card or hard drive may also lead to
disconnects.
Disconnect Recovery
This section provides an overview of recovering your system from a disconnect, recovery
procedures, and a quick reference worksheet you can use should a disconnect occur.
Overview
After a system has disconnected, one server must be selected to continue on as the master
computer. This server will be referred to as the survivor. The other server will be referred to
as the failed server.
Before the failed server can be reconnected to the survivor, it must be rebooted and its
database wiped clean. After the database on the failed server has been cleared, the server can
be reconnected to the survivor and the master database copied back across from the survivor.
Because one server’s database will be selected as the master database and the other’s
database erased, discovering a disconnect as soon as possible minimizes the possibility of
data loss.
96
Page 97

In normal dual-server operation, half the devices and sessions are configured on one server
and the other half are configured on the other server. The most important thing to do after a
disconnect is to reconfigure the survivor so that it knows it must be responsible for all
devices and sessions. You can then restart any network devices that were running on the
failed server.
The steps are covered in more detail in the next section, “Procedures” on page 97.
n
The disconnect recovery steps are as follows:
1. Reboot the failed server.
2. Clear the database on the failed server.
3. Reconnect the failed server.
4. Copy the database to the failed server.
5. Log out and stop all servers and resources.
6. Reconfigure the system.
7. Start up all servers and resources.
Procedures
Disconnect Recovery
This section contains an example of recovery from a disconnect of a dual AB system. The
steps might vary when the system is a triple system configuration. Triple system
configuration customers might need to contact Avid for more specific instructions.
In the example, it is assumed that server A was chosen as the survivor and server B was
designated the failed server:
•NRCS-A–survivor
• NRCS-B–failed server
The failed server is also referred to as the revived server after it is reconnected to the system.
If you reverse the roles of the servers during your disconnect and make B the survivor and
n
server A the failed server, remember to adjust which server you issue the commands on
appropriately. The steps shown in the following example assume server A is the survivor;
reverse A and B throughout the process if server B is chosen as your survivor.
It is assumed (for this example) that when the servers disconnected, server A became a
single system (system is A, master is A) and server B also became a single system (system is
B, master is B). In this situation, users logged in on A can continue working and saving
stories. Users logged in on B can also continue working and saving stories, but since the
servers are not mirroring, anything saved to server A’s database is not copied over to server
B’s database, and vice versa.
97
Page 98

7 Disconnects
The databases on the machines are no longer mirrored. The only recourse is to choose one of
the servers’ databases to become the master database. The database on the other server is
wiped clean and then recopied from the master server.
To export a story to a local hard drive:
t Select File > Export Story.
To recover the system:
1. Choose one master machine to continue working with (survivor)
2. Halt and reboot the disconnected (failed) server using the following command:
Users logged on to the failed server (B) are creating stories on a database that is going to
be wiped clean. That information will be lost unless stories created after the disconnect
are first exported to the local hard drive so they can be imported to the survivor once the
user logs in to the other server.
It does not matter whether you choose server A or B as your master computer. What is
important is to choose one quickly. You may choose one server over the other if it has
more users logged in on it. Or you may choose the server that has the show producer
logged in on it. If you are about to enter a show, you may pick the one that runs the
teleprompter. Or you may choose A as the survivor so the steps exactly shadow
instructions in this section.
NRCS-B# shutdown
NRCS-B# reboot
98
3. Log in to the rebooted failed server as system operator, then become superuser.
a. At the login prompt, log in as the system operator user (so):
iNEWS Newsroom Computer System
login: so
Password:
Last login: Mon Jul 19 07:17:23 on ttyS0
?:
b. When you log back in you will be at the question mark prompt because the server is
not yet named (connected). You must be in superuser mode for the next step:
?:su
Password:
?#
For more information on superuser mode, selecting servers, and configuring the system, see
n
the iNEWS Newsroom Computer System Setup and Configuration Manual.
Page 99

Disconnect Recovery
4. Select the failed (disconnected) server on the console and use the diskclear command to
wipe the database off the failed server.
The display will look similar to the following (with what you type appearing in bold):
?# diskclear -
DANGER -- This program DESTROYS all information on this computer's
data base.
Do you wish to save the current data base? (y/n): n
Are you sure you wish to CLEAR the disk? (n/y): y
? Mon Jan 3 16:18:23 2000 diskclear CLEARING DATA BASE
? Mon Jan 3 16:18:23 2000 Each dot represents 10,000 blocks. The
entire database = 1677 dots.
........10.........20.........30.........40.........50
.........60.........70.........80.........90.........100
.........110......
The diskclear will print a sequence of dots and numbers as it clears the disk. For
instance, on a full 16 gigabyte database, the dots and numbers count to 16,000. The
diskclear may take some time to complete.
5. Reconnect the failed server to the survivor.
a. After the diskclear has completed you can reconnect the servers. Select both (all)
servers on the console and type:
reconnect <failed> master=<survivor> net=ab
b. Depending on which one failed and which one is master, you would enter one of the
following commands:
reconnect a master=b net=ab
reconnect b master=a net=ab
A few moments after entering the command, the failed server will regain its normal,
named prompt. Communication and mirroring between the servers is reestablished.
6. Begin copying the database back over to the failed server.
a. Select the revived (failed) server only on the console and begin a diskcopy:
NRCS-B# diskcopy -9
Users can continue working while the diskcopy continues in the background.
7. When the diskcopy has completed, stop all servers and devices.
99
Page 100

7 Disconnects
8. Reconfigure the system (survivor).
At this point, all devices and sessions are running on the survivor—that is, master
computer—even the ones that normally run on the other, revived server. These devices,
utility programs, and sessions eventually need to run in their normal place on the revived
server.
Schedule a time to log the users off and stop the servers and devices. At that time, run
the following commands on the survivor:
NRCS-A# offline
NRCS-A# logout all
NRCS-A# stop all
The system is now running in a dual AB configuration. When you run the configure
command, the system will reconsult the /site/config file and divide responsibility for
which server will run the devices, half for server A and half for B:
NRCS-A# offline
NRCS-A# configure
NRCS-A# online
Wait for the system being configured messages to appear on both servers before moving
on to the next step.
100
c
9. Start up the revived server.
When you run startup on the revived server, the devices and utility programs (such as
action servers or txnet links) on that server are started and it is placed online:
NRCS-B# startup
10. Restart all of the survivor’s devices by typing
The system is now running normally (dual) with all sessions and devices in their normal
places.
If server B was selected as the master database, it is now the master computer. Since
either server can run as master, nothing further needs to be done. If you want to make
server A the master computer again, perform a normal system shutdown, reboot and
startup, as described in iNEWS Newsroom Computer System Setup and Configuration
Manual.
Wait for the diskcopy to complete before rebooting the system to make server A the
master computer again. Database corruption may result if the system is taken down
before the diskcopy completes. If the system loses power or must be rebooted; the
master computer that contains the full database must be brought up in a single server
configuration, and the disconnect recovery procedure restarted again.
restart all
on the master computer.
 Loading...
Loading...