Philips protok01 DATASHEETS

HT CM400
HT RM440 Family
HT RM800 Family
Interface Protocol Reader ↔ Host
Revision 1.1
February 1997Product Specification

Introduction Rev. 1.0 98-02-10
Table of Contents
1 Introduction................................................................................................................ 5
1.1 Abbreviations................................................................................................................. 6
1.2 Definitions .....................................................................................................................7
2 Provided Host Software Modules............................................................................. 8
2.1 Introduction...................................................................................................................8
2.2 Using the Provided Host Software Modules................................................................... 9
3 Communication Reader-Host.................................................................................. 10
3.1 Introduction................................................................................................................. 10
3.2 Ordinary Protocol ........................................................................................................ 11
3.3 Extended Protocol ....................................................................................................... 11
3.4 Transfer Timeout Intervals........................................................................................... 12
3.5 Command Set .............................................................................................................. 13
3.6 Status Byte .................................................................................................................. 15
3.7 Command Description for Operating Mode..................................................................16
3.7.1 GetSnr............................................................................................................. 16
3.7.2 GetSnr_Adv..................................................................................................... 17
3.7.3 SelectSnr.......................................................................................................... 18
3.7.4 SelectLast........................................................................................................ 19
3.7.5 HaltSelected..................................................................................................... 20
3.7.6 ReadPage......................................................................................................... 21
3.7.7 ReadBlock....................................................................................................... 22
3.7.8 WritePage........................................................................................................ 23
3.7.9 WriteBlock ...................................................................................................... 24
3.7.10 TagAuthent.................................................................................................... 25
3.7.11 MutualAuthent............................................................................................... 26
3.7.12 GetSnr_LT..................................................................................................... 27
3.7.13 GetSnrReset_LT............................................................................................ 28
3.7.14 HaltSelected_LT............................................................................................ 29
3.7.15 ReadPage_LT ................................................................................................ 30
3.7.16 ReadPageInv_LT ........................................................................................... 31
3.7.17 WritePage_LT................................................................................................ 32
3.7.18 ReadPit_LT.................................................................................................... 33
3.7.19 ReadPublicB_LT............................................................................................ 34
3.7.20 ReadMiro....................................................................................................... 35
3.7.21 ReadPit.......................................................................................................... 36
3.7.22 WritePit .........................................................................................................37
3.7.23 WritePitBlock ................................................................................................ 38
3.7.24 PollTags......................................................................................................... 39
3.7.25 PollKbTags.................................................................................................... 41
3.7.26 GetVersion..................................................................................................... 43
3.7.27 Reset.............................................................................................................. 44
Htswp.doc/HS Page 2 (104)

98-02-10 Rev. 1.0 Introduction
3.7.28 HFReset......................................................................................................... 45
3.7.29 StopCommand ............................................................................................... 46
3.7.30 ReadInput...................................................................................................... 47
3.7.31 SetOutput ......................................................................................................48
3.7.32 ConfigPorts.................................................................................................... 49
3.7.33 ReadPorts ...................................................................................................... 50
3.7.34 WritePorts...................................................................................................... 51
3.7.35 ReadEEData .................................................................................................. 52
3.7.36 WriteEEData.................................................................................................. 52
3.7.37 SetProxTrmTime............................................................................................ 53
3.7.38 SetModuleAdr ............................................................................................... 54
3.7.39 SetHFMode ...................................................................................................55
3.7.40 StartFFT........................................................................................................ 56
3.7.41 ReadBCD....................................................................................................... 57
3.7.42 SetBCD .........................................................................................................58
3.7.43 SetBCDOffset................................................................................................ 59
3.7.44 ReadLRStatus................................................................................................ 59
3.7.45 SetPowerDown.............................................................................................. 60
3.7.46 ReadAllPage .................................................................................................. 61
3.7.47 GetDspVersion .............................................................................................. 62
3.7.48 KeyInitMode.................................................................................................. 63
3.8 Command Description for KeyInit Mode...................................................................... 64
3.8.1 Reset................................................................................................................ 64
3.8.2 WriteSerNum................................................................................................... 65
3.8.3 ReadEEPROM................................................................................................. 66
3.8.4 WriteEEPROM................................................................................................ 67
3.8.5 ReadControl..................................................................................................... 68
3.8.6 WriteControl.................................................................................................... 69
3.8.7 ReadSecret_LT................................................................................................ 70
3.8.8 WriteSecret_LT............................................................................................... 71
3.8.9 ReadControl_LT.............................................................................................. 72
3.8.10 WriteControl_LT........................................................................................... 73
3.8.11 WritePitSecurity............................................................................................. 74
3.8.12 WritePitPassword........................................................................................... 75
3.9 Examples to Access HITAG 1 Transponders................................................................ 76
3.9.1 Long Range: Anticollision Cycle ...................................................................... 76
3.9.2 Proximity/Long Range: READ PLAIN............................................................. 77
3.9.3 Proximity/Long Range: WRITE PLAIN........................................................... 77
3.9.4 Proximity/Long Range: READ CRYPTO......................................................... 78
3.9.5 Proximity/Long Range: WRITE CRYPTO....................................................... 78
3.10 Examples to Access HITAG 2 Transponders.............................................................. 79
3.10.1 Proximity/Long Range: READ....................................................................... 79
3.10.2 Proximity/Long Range: WRITE..................................................................... 79
4 Transponders........................................................................................................... 80
4.1 HITAG 1 Transponders ............................................................................................... 80
4.1.1 Memory Organization ......................................................................................80
4.1.2 Anticollision..................................................................................................... 81
4.1.3 Operation-Modes and Configuration ................................................................82
Page 3 (104) Htswp.doc/HS

Introduction Rev. 1.0 98-02-10
4.1.4 Configuration of Delivered HITAG 1 Transponders ......................................... 85
4.2 HITAG 2 Transponders ............................................................................................... 86
4.2.1 Memory Organization ......................................................................................86
4.2.2 Operation-Modes and Configuration ................................................................87
4.2.3 Configuration of Delivered HITAG 2 Transponders ......................................... 89
4.3 PIT (PCF793x) Transponders ...................................................................................... 90
4.3.1 Memory Organization ......................................................................................90
4.4 MIRO / µEM (H400x) Transponders........................................................................... 91
4.4.1 Memory Organization ......................................................................................91
5 Personalization ........................................................................................................ 92
5.1 Introduction................................................................................................................. 92
5.2 Personalization Concept...............................................................................................92
5.3 Personalization of HITAG 1 Transponders................................................................... 97
5.3.1 Definition of Keys and Logdata........................................................................97
5.3.2 Changing Keys and Logdata............................................................................. 98
5.4 Personalization of HITAG 2 Transponders................................................................. 100
5.4.1 Definition of Passwords and Keys .................................................................. 100
5.4.2 Changing Passwords and Keys ....................................................................... 101
6 Security Considerations........................................................................................ 102
6.1 Data Reliability........................................................................................................... 102
6.1.1 Data Stream betwee n Read/W rite Device and T ranspond er................................. 102
6.1.2 Checking User Data ....................................................................................... 102
6.2 Data Privacy .............................................................................................................. 103
Author: Dieter Köckinger
Htswp.doc/HS Page 4 (104)

98-02-10 Rev. 1.0 Introduction
1 Introduction
This description refers to the interface between a host (e.g. PC) and a contactless 125 kHz
read/write device based on the HITAG Communication Controller, as there is e.g. the
HT CM400 (HITAG Core Module), HT RM440 family (HITAG Proximity Reader Module)
and HT RM800 family (HITAG Long Range Reader Module).
For easy and quick development of application specific host software Philips Semiconductors
provides a C-Library, Source- and Header-Files. These tools can be found on the floppy disk
added to this description.
Following transponders of the 125 kHz family are supported:
• HITAG 1
• HITAG 2
• MIRO / µEM (H400x)
• PIT (PCF793x)
Additional Features:
• High security by using cryptography, mutual authentication and password verification
• Addressing multiple (up to 255) read/write devices on a RS485-Bus
• Programmable port pins: 4 outputs; 2 inputs;
optional (requiring a special hardware because signals are not available on pin connectors
of Philips Semiconductors’ Core Module): 8 pins either in-/output configurable or for
connection to a keyboard-matrix up to 12 keys
• 85 bytes of user-defined data can be stored in an EEPROM of the read/write device
System Requirements to use Philips Semiconductors’ C-Library PROLIB6:
• IBM-PC or compatible (minimum 286 processor) with available serial interface
• Borland C-Compiler (Version 3.1 recommended)
Page 5 (104) Htswp.doc/HS

Introduction Rev. 1.0 98-02-10
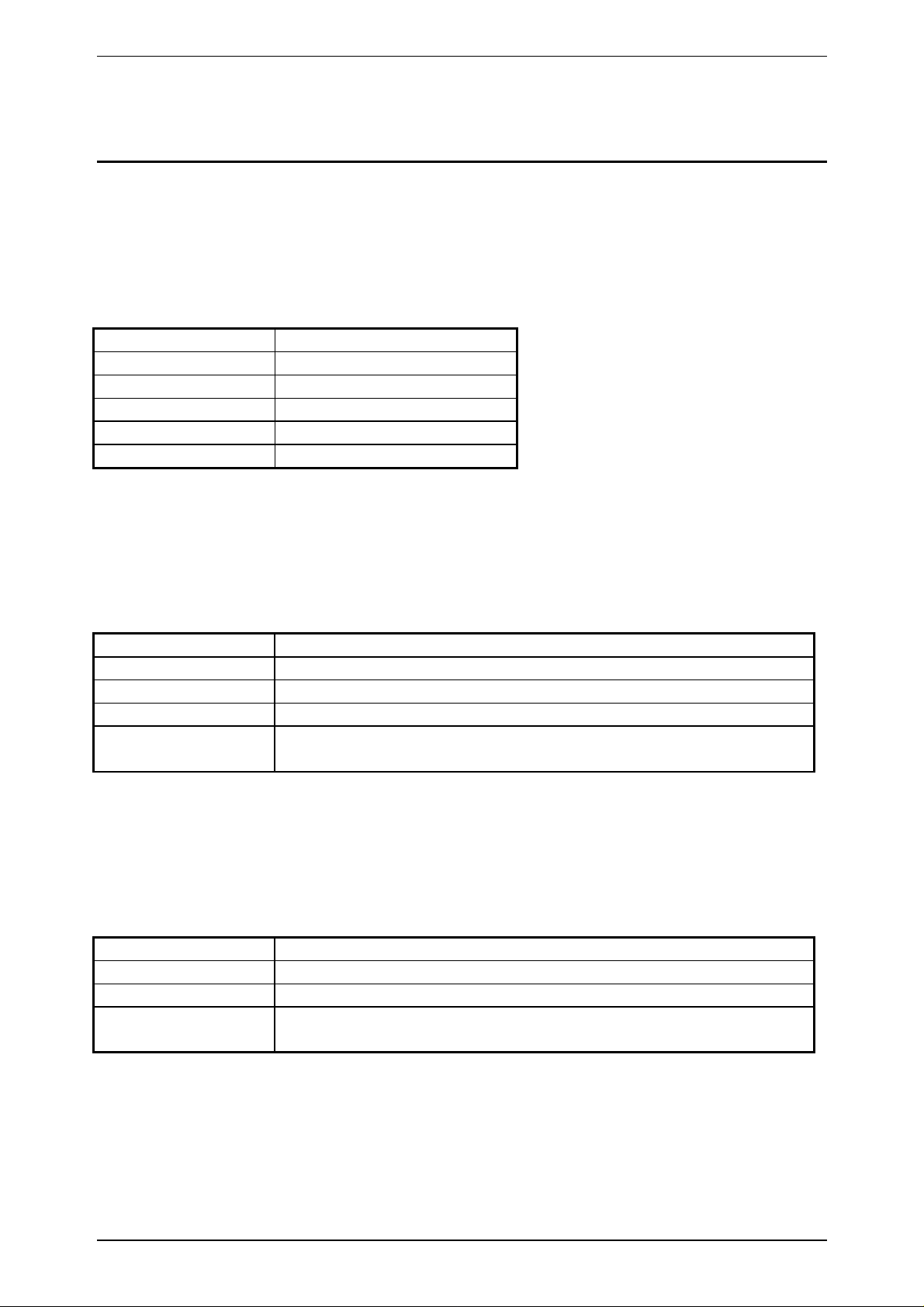
1.1 Abbreviations
Please find in the following a list of the abbriviations used in this document.
addr Address
BCC Block Check Character
BYTE_T Byte (unsigned character)
char Character
CRC Cyclic Redundancy Check
DSP Digital Signal Processor
DWORD_T Double Word (unsigned)
FFT Fast Fourier Transformation
HF High Frequency
LSB Least Significant Byte
MSB Most Significant Byte
nmb Number
OTP One Time Programmable
pagenr Page Number
RF Radio Frequency
ro Read Only
r/w Read/Write
RWD Read/Write Device
snr Serial Number
TAG (tag) Transponder
wo Write Only
Htswp.doc/HS Page 6 (104)

98-02-10 Rev. 1.0 Introduction
1.2 Definitions
Data sheet status
Objective specificationThis data sheet contains target or goal specifications for product development.
Preliminary specificationThis data sheet contains preliminary data; s upplementary data may be
published later.
Product specification This data sheet c ontains final produc t spec ifications .
Limiting values
Limiting values given are in accordance with the Absolute Max imum Rating Syst em (IEC 134).
Stress above one or more of the limiting values may cause permanent damage to the device.
These are stress ratings only and operation of the device at thes e or at any other c onditions
above those given in the Characteristics s ection of the specific ation is not implied. Ex posure to
limiting values for extended periods may affect devic e reliability.
Application information
Where application information is given, it is advisory and does not form part of the specification.
Life support applications
These products are not designed for use in life support appliances, devices, or systems where
malfunction of these products can reasonably be expected to result in personal injury. Philips
Semiconductors´ customers using or selling these products for use in such applications do so on
their own risk and agree to fully indemnify Philips Semiconductors for any damages resulting from
such improper use or sale.
Page 7 (104) Htswp.doc/HS
Provided Host Software Modules Rev. 1.0 98-02-10
2 Provided Host Software Modules
2.1 Introduction
On the Floppy Disk added to this description you will find the following tools:
Library Files:
PROLIB6C.LIB Compact Memory Model
PROLIB6H.LIB Huge Memory Model
PROLIB6L.LIB Large Memory Model
PROLIB6M.LIB Medium Memory Model
PROLIB6S.LIB Small Memory Model
PROLIB6T.LIB Tiny Memory Model
Depending on the Memory Model you choose for host software you have to include the
corresponding Library File in your project.
These Libraries are helpful for developing DOS software in Standard C language with a Borland
C-Compiler.
Header Files:
PROLIB6.H HITAG 1 / MIRO / RWD function declarations
PROLBLT6.H HITAG 2 function declarations
PROLBPH6.H PIT function declarations
PROLBMU6.H Multiple RWD function declarations (Network)
PROLVEG6.H Function declarations for a special project requiring a special Reader-
Hardware and -Software
Each Header File provides function declarations with detailed information about the use of
commands.
Depending on the used command function (e.g. proloc_GetSnr) you have to include the
corresponding Header File(s) in your application specific source file.
Source Files:
PROLIB6.C HITAG 1 / MIRO / RWD functions
PROLBLT6.C HITAG 2 functions
PROLBPH6.C PIT functions
PROLVEG6.C Functions for a special project requiring a special Reader-Hardware
and -Software
The code in the Source Files is identical with the code included in the Library Files.
There is no Source File for using multiple RWD’s because all necessary code is located in the
Header File PROLBMU6.H.
For developing software on other platforms by using other compilers we recommend to use our
Source Files and Header Files and make your specific adaptations.
Htswp.doc/HS Page 8 (104)

98-02-10 Rev. 1.0 Provided Host Software Modules
2.2 Using the Provided Host Software Modules
Communication via the serial interface between the host and the read/write device is handled by
using interrupts. As a consequence a host-program only has to test a flag (RWDEot) periodically
to recognize the end of a communication sequence. Meanwhile the program can execute other
functions while the data transfer is running in the background.
To do this, however, some flags are needed:
RWDEot: Helps to identify the end of a communication sequence
flag is set to 0 at a library function request
flag is set to 1 at the end of the serial protocol
RWDErr: Saves the error code
0 ... errorfree execution
<0 ... error has occured
RWDDataLen: Saves the number of bytes received via the serial interface.
Can take any value between 0 and 24.
• To open the serial port on the host system use function (Header File PROLIB6.H)
proloc_open(char *ComStr) // *ComStr="COM1" for COM1
// *ComStr= "COM2" for COM2
• To close the serial port on the host system use function (Header File PROLIB6.H)
proloc_close()
In order to prevent undesired side effects use proloc_close before program end or before a
new proloc_open.
• To change BCC calculation (when entering or leaving KeyInitMode) use function
(Header File PROLIB6.H)
proloc_SetBCCMode(BYTE_T mode) // mode=0x00: Operating Mode
// mode=0x01: KeyInit Mode
• For communication in Extended Protocol use commands with ‘Proloc_M’-prefix (Header File
PROLBMU6.h)
The names of the commands described in the following have to be prefixed with „proloc_“
to get the correspoding names in the C-Library (e.g. function proloc_GetSnr() for command
GetSnr) for Ordinary Protocol.
All Header Files contain short examples to illustrate the usage of each command.
Page 9 (104) Htswp.doc/HS

Communication Reader-Host Rev. 1.0 98-02-10
3 Communication Reader-Host
3.1 Introduction
The host (e.g. PC) communicates with the contactless 125 kHz read/write device via a serial
interface using a baud rate of 9600 baud.
Data transfer details are: 1 start bit, 8 data bits, 1 stop bit and no parity bit, the Least Significant
Bit is sent first.
Each communication sequence consists of a block of bytes sent by the host, and a block of bytes
answered by the reader.
All bytes are transmitted transparently, i.e. you can use any character between 0x00 and 0xFF.
Block Length:
Block Length is the sum of all transferred bytes including Block Length but excluding BCC.
Block Title:
The Command Byte if sent from host to reader.
The Status Byte if sent from reader to host.
Data:
Data bytes are only transmitted if data is transferred.
BCC:
The BCC (Block Check Character) is calculated by bytes 1 to n-1 (n=number of bytes of the
whole communication sequence).
A different BCC calculation in Operating Mode (mode of the reader for using standard
commands) and in KeyInit Mode (mode of the reader device for using personalization commands)
helps to avoid the overwriting of secret data accidentally.
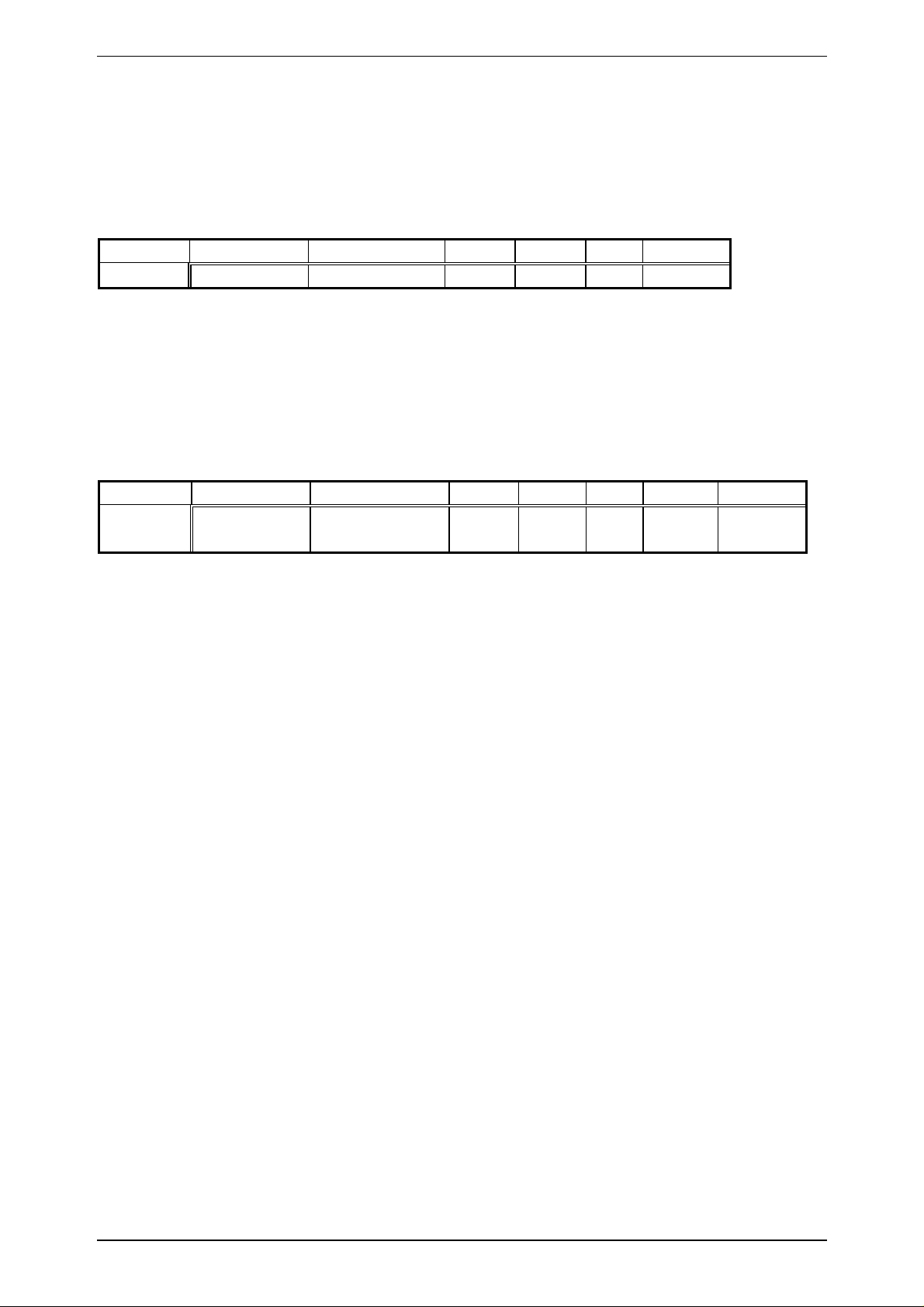
BCC calculation in Operating Mode of the reader:
The BCC is computed by EXOR-operation of all block data bytes including Block
Length.
EXOR for 1 Bit: Example for command
A B EXOR
00
01
10
11
0
1 Byte 3: BCC
1
0
Byte 1: Block Length
Byte 2: Command Byte
:
GetSnr
0000 0010 0x02
0100 0111 0x47
0100 0101 0x45
BCC calculation in KeyInit Mode of the reader:
The BCC is computed by adding all block data bytes including Block Length. The least
significant eight bits are used as BCC.
Htswp.doc/HS Page 10 (104)
98-02-10 Rev. 1.0 Communication Reader-Host
3.2 Ordinary Protocol
If only a single read/write device with a node address equal to zero is connected to the host (e.g.
on a RS232 serial line) the Ordinary Protocol is used to address this reader.
Format of the Ordinary Protocol (HOST→READER and READER→HOST):
Byte 1 2 3 4 ...... n
Function
Block Length Block Title data data ......... BCC
3.3 Extended Protocol
If more than one read/write devices with node addresses different from zero are connected to the
host (e.g. on a RS485 serial line) the Extended Protocol is used to address a single reader.
Format of the Extended Protocol (HOST→READER and READER→HOST):
Byte 1 2 3 4 ...... n-1 n
Function
Block Length
+ 0x80
Block Title data data ......... Node
Address
BCC
Differences to Ordinary Protocol: Bit 7 of Block Length is set, and the Node Address is inserted
just before BCC.
If a reader’s node address is different from zero, the reader enters net-mode. In this mode the
reader expects all commands from the host to be sent in Extended Protocol including the right
Node Address (except SetModuleAdr). If the host transmits a string that does not meet these
conditions, the command is ignored, and there will be no answer from the reader (whereas a
reader being not in net-mode - with node address equal to zero - would at least answer with a
SERIAL ERROR message).
The command SetModuleAdr is used to assign a unique node address to a device whose serial
number is known. This command should be sent in Ordinary Protocol. If the right serial number
was sent, there will be an answer from the read/write device. This answer is sent in Ordinary
Protocol if the former node address of the reader was zero, otherwise the answer is sent in
Extended Protocol.
For communication in Extended Protocol use commands with ‘Proloc_M’-prefix. For further
information see Header File PROLBMU6.h.
Page 11 (104) Htswp.doc/HS

Communication Reader-Host Rev. 1.0 98-02-10
3.4 Transfer Timeout Intervals
Character Delay:
Character Delay is the maximum time permitted to elapse between sending two consecutive
characters of a block.
Character Delay ≤ 150 ms
Block Delay:
Block Delay is only necessary if an error has occurred in the serial communication.
To allow for re-synchronization in that case of malfunction there must be a minimum interval defined as Block Delay - until sending the next block.
Block Delay ≥ 160 ms
Htswp.doc/HS Page 12 (104)

98-02-10 Rev. 1.0 Communication Reader-Host
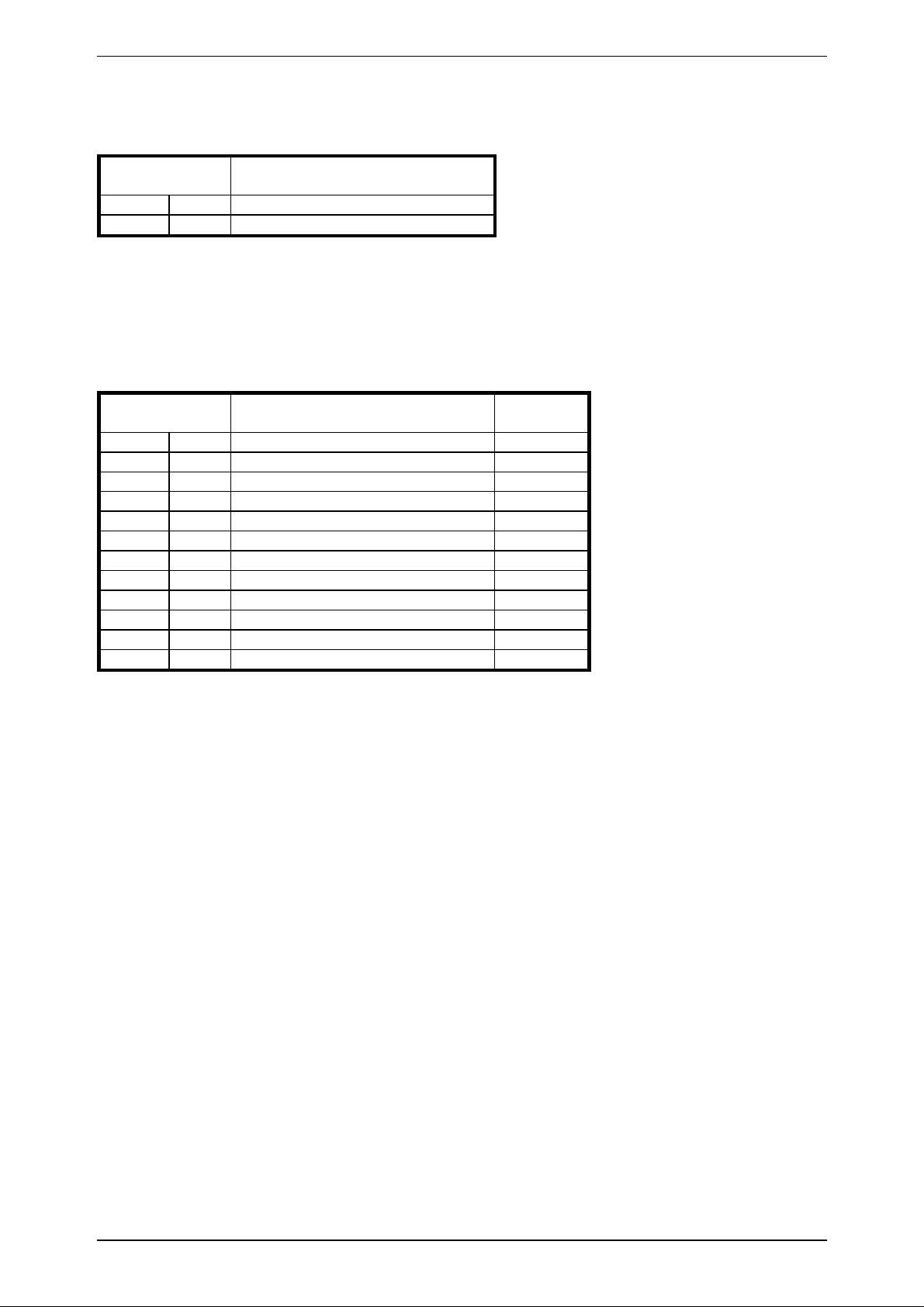
3.5 Command Set
The Command Byte is part of the block sent from the host.
Command Bytes used in a Proximity (P) and/or Long Range (L) Reader:
Operating Mode:
COMMAND COMMAND NAME READER TRANSPONDERS
BYTE
'A' 0x41 MutualAuthent P/L
'B' 0x42 ReadBlock P/L
'D' 0x44 SetPowerDown L
'E' 0x45 ReadEEData P/L
'F' 0x46 StartFFT / SetBCD L
'G' 0x47 GetSnr P/L
'H' 0x48 HaltSelected P/L
'I' 0x49 ReadInput P/L
'K' 0x4B KeyInitMode P/L
'L' 0x4C SetHFMode P/L
'M' 0x4D ReadMiro P/L P/L
'O' 0x4F SetOutput P/L
'P' 0x50 ReadPage P/L
'R' 0x52 Reset P/L
'S' 0x53 SelectSnr / SelectLast P/L
'T' 0x54 ReadPit P
'V' 0x56 GetVersion P/L
'a' 0x61 TagAuthent P/L
'b' 0x62 WriteBlock P/L
'c' 0x63 ConfigPorts P/L
e' 0x65 WriteEEData P/L
'f' 0x66 ReadBCD L
'h' 0x68 HFReset P/L
'i' 0x69 ReadPorts P/L
'l' 0x6C PollTags P/L P/L P/L P
'o' 0x6F WritePorts P/L
'p' 0x70 WritePage P/L
'r' 0x72 ReadLRStatus L
't' 0x74 WritePit P
'u' 0x75 WritePitBlock P
0x80 GetSnr_LT / GetSnrReset_LT P/L
0x81 HaltSelected_LT P/L
0x82 ReadPage_LT P/L
0x83 ReadPageInv_LT P/L
0x84 WritePage_LT P/L
0x85 ReadPit_LT P
0x90 PollKbTags P/L P/L P/L
0x91 SetModuleAdr P/L
0x9E ReadPublicB_LT P/L
0xA1 SetProxTrmTime P/L
0xA2 GetSnr_Adv P/L
0xA4 SetBCDOffset L
0xA6 StopCommand P/L
HITAG 1 HITAG 2 MIRO PIT
Page 13 (104) Htswp.doc/HS
Communication Reader-Host Rev. 1.0 98-02-10
Additional commands for a special project requiring a special Reader-Hardware
and -Software:
COMMAND
BYTE
0x98 ReadAllPage
'v' 0x76 GetDspVersion
COMMAND NAME
KeyInit Mode:
The KeyInit Mode is a mode of all HITAG Readers for using a set of personalization commands.
COMMAND
BYTE
'C' 0x43 ReadControl P/L
'R' 0x52 Reset (Switch to Operating Mode) P/L
'V' 0x56 ReadSecret_LT P/L
'W' 0x57 WriteSecret_LT P/L
'X' 0x58 ReadEEPROM P/L
'Y' 0x59 WriteEEPROM P/L
'c' 0x63 WriteControl P/L
's' 0x73 WriteSerNum P/L
'v' 0x76 WritePitSecurity P
'w' 0x77 WritePitPassword P
0x90 ReadControl_LT P/L
0x91 WriteControl_LT P/L
COMMAND NAME READER
Htswp.doc/HS Page 14 (104)

98-02-10 Rev. 1.0 Communication Reader-Host
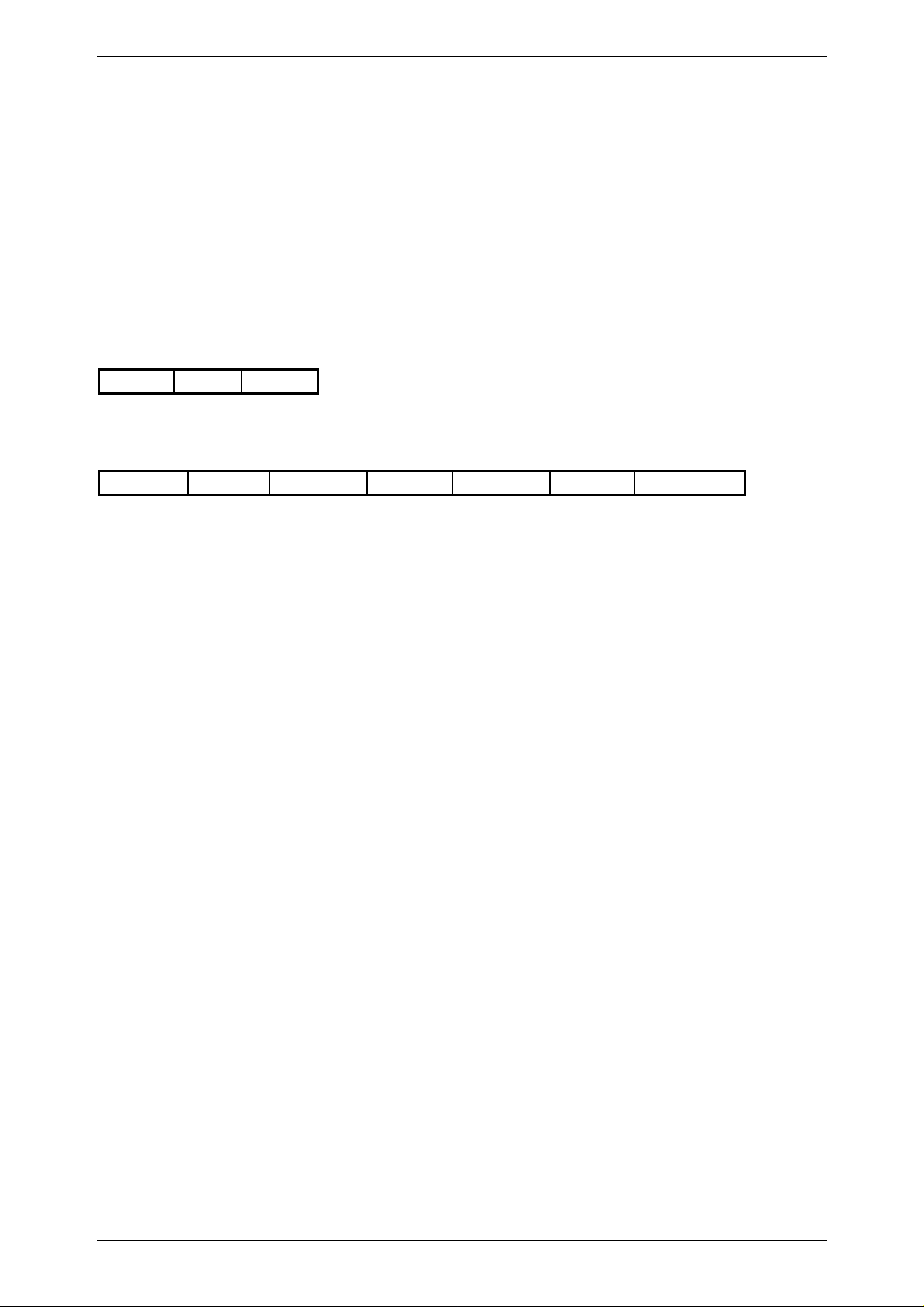
3.6 Status Byte
The read/write device returns a Status Byte indicating an error if different from 0.
The following Error Codes are defined:
VALUE ERROR NAME DESCRIPTION
0 no error
-1 SERIAL ERROR Error at the serial interface.
-3 NOTAG There was no answer of a transponder
detected by the read/write device.
-4 TIMEOUT There is not enough energy available to write
to the transponder.
-5 INCORRECT PASSWORD RWD The HITAG 2 password of the read/write
device is invalid.
-6 INCORRECT PASSWORD TAG The HITAG 2 password of the transponder is
invalid.
-7 AUTHENTICATION ERROR An error occurred during the authentication
process.
-8 ACKNOWLEDGEMENT ERROR The acknowledgement was not received
correctly.
-9 CRYPTOBLOCK NOT INIT A cryptographic command was transmitted
without authentication between the read/write
device and transponder.
-10 EEPROM ERROR EEPROM ( of the r ead /write device )
acknowledgement error.
-11 EEPROM WRONG OLD DATA On comparison old and new data prove
inconsistent.
-12 EEPROM WRITE PROTECTED You attempted to write to the read/write
device EEPROM, although writing was not
allowed.
-13 EEPROM READ PROTECTED You attempted to read from the read/write
device EEPROM, although reading was not
allowed.
-14 PIT DATA OVERFLOW New PIT-Data were received by the host
before the host-program read the old PITData (error generated by C-Library during
command ReadPit).
-15 CRC ERROR Wrong CRC from a HITAG 1 transponder in
Advanced Protocol Mode.
-20 ANTENNA OVERLOAD Long Range Reader: Broken or badly
detuned antenna (error only after command
ReadLRStatus).
Page 15 (104) Htswp.doc/HS

Communication Reader-Host Rev. 1.0 98-02-10
3.7 Command Description for Operating Mode
The Operating Mode is a mode of the reader for using a set of standard commands as described in
the following.
In this mode the BCC is computed by EXOR-operation of all block data bytes including Block
Length.
The command KeyInitMode is used to enter t he KeyInit Mode ( mode of the r ead/write device for
using personalization commands), and a different set of commands becomes available.
3.7.1 GetSnr
This command provides the seri al number of a HITAG 1 transponder in Standard Protocol Mode.
For further information on the Standard Protocol Mode see chapter „Transponders“.
C-Function: void proloc_GetSnr (DWORD_T *snr, BYTE_T *more);
Header-File: PROLIB6.H
Serial protocol:
HOST - READ/WRITE DEVICE
0x02 'G' 0x45
READ/WRITE DEVICE - HOST
7 0 ------ 31 24
n+2 Status SNR-LSB ------ SNR-MSB more BCC
n = 0 if an error occurred (error code in Status).
n = 5 if data were read from a transponder (Status = 0).
more: Proximity Reader: more is always 0.
Long Range Reader: more equal to one indicates that there is at least one additional
transponder in the reading area of the read/write device.
Status: 0 ... no error
-1 ... SERIAL ERROR
-3 ... NOTAG
Htswp.doc/HS Page 16 (104)
98-02-10 Rev. 1.0 Communication Reader-Host
3.7.2 GetSnr_Adv
This com mand provides the serial n umber of a HITAG 1 transponder and sets the transponder into
Advanced Protocol Mode (command is not available for HITAG 1 transponders based on ASIC
HT1 ICS30 01x ; only available for HITAG 1 transponders based on ASIC HT1 ICS30 02x).
For further information on the Advanced Protocol Mode see chapter „Transponders“.
C-Function: void proloc_GetSnr_Adv (DWORD_T *snr, BYTE_T *more);
Header-File: PROLIB6.H
Serial protocol:
HOST - READ/WRITE DEVICE
0x02 0xA2 0x45
READ/WRITE DEVICE - HOST
7 0 ------ 31 24
n+2 Status SNR-LSB ------ SNR-MSB more BCC
n = 0 if an error occurred (error code in Status).
n = 5 if data were read from a transponder (Status = 0).
more: Proximity Reader: more is always 0.
Long Range Reader: more equal to one indicates that there is at least one additional
transponder in the reading area of the read/write device.
Status: 0 ... no error
-1 ... SERIAL ERROR
-3 ... NOTAG
Page 17 (104) Htswp.doc/HS

Communication Reader-Host Rev. 1.0 98-02-10
3.7.3 SelectSnr
This command selects the HITAG 1 transponder with a specified serial number. The content of
the transponder’s Configuration Page is returned.
If there is no such transponder in the field, a NOTAG error message is displayed.
ATTENTION: The serial number has to be the same as received with the preceding
GetSnr.
C-Function: void proloc_SelectSnr (DWORD_T snr, DWORD_T *otp);
Header-File: PROLIB6.H
Serial protocol:
HOST - READ/WRITE DEVICE
7 0 ------ 31 24
0x06 'S' SNR-LSB ------ SNR-MSB BCC
READ/WRITE DEVICE - HOST
7 0 ------ 31 24
n+2 Status OTP-LSB ------ OTP-MSB BCC
OTP: Configuration Page of HITAG 1
n = 0 if an error occurred (error code in Status).
n = 4 if data were read from a transponder (Status = 0).
Status: 0 ... no error
-1 ... SERIAL ERROR
-3 ... NOTAG
Htswp.doc/HS Page 18 (104)

98-02-10 Rev. 1.0 Communication Reader-Host
3.7.4 SelectLast
Selects the HITAG 1 transpo nder with the serial number that was read executing the last error free GetSnr command.
This command is an abbreviated version of SelectSnr as no serial number has to be transmitted via
the serial interface and the content of the Configuration Page is not returned.
C-Function: void proloc_SelectLast (void);
Header-File: PROLIB6.H
Serial protocol:
HOST - READ/WRITE DEVICE
0x02 'S' 0x51
READ/WRITE DEVICE - HOST
0x02 Status BCC
Status: 0 ... no error
-1 ... SERIAL ERROR
-3 ... NOTAG
Page 19 (104) Htswp.doc/HS

Communication Reader-Host Rev. 1.0 98-02-10
3.7.5 HaltSelected
Puts the selected HITAG 1 transponder into Halt Mode, which means that this transponder
remains silent until it leaves and reenters the RF field.
You can reset a transponder previously turned off by HaltSelected using the command HFReset
or putting it out of RF field.
C-Function: void proloc_HaltSelected (void);
Header-File: PROLIB6.H
Serial protocol:
HOST - READ/WRITE DEVICE
0x02 'H' 0x4A
READ/WRITE DEVICE - HOST
0x02 Status BCC
Status: 0 ... no error
-1 ... SERIAL ERROR
-8 ... ACKNOWLEDGEMENT ERROR
Htswp.doc/HS Page 20 (104)
98-02-10 Rev. 1.0 Communication Reader-Host
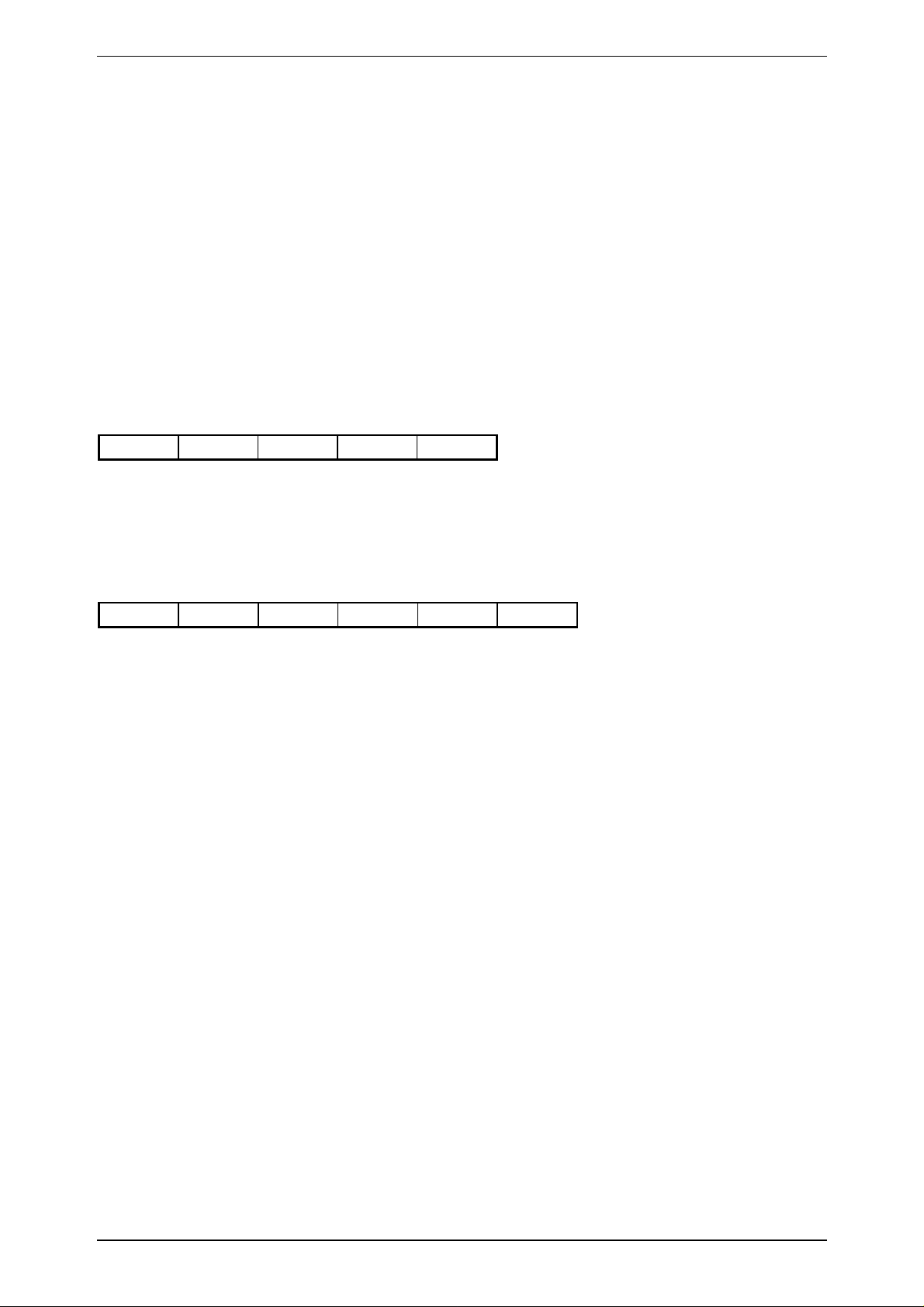
3.7.6 ReadPage
Reads a page (4 bytes) of a selected HITAG 1 transponder.
If no transponder is selected, a NOTAG message will be generated even if there is a transponder
in the communication field of the antenna.
Using the byte -crypto- you define whether you want to work in Plain or in Crypto Mode.
Access to the secret area is only possible in Crypto Mode after a mutual authentication.
If -crypto- equals 1 (Crypto Mode) and you did not run an authentication procedure before,
Status will be set to -9.
C-Function: void proloc_ReadPage (BYTE_T crypto, BYTE_T pagenr, char *data);
Header-File: PROLIB6.H
Serial protocol:
HOST - READ/WRITE DEVICE
0x04 'P' crypto pagenr BCC
crypto: 0x00 ... Plain Mode
0x01 ... Crypto Mode
pagenr: page number
READ/WRITE DEVICE - HOST
n+2 Status data[0] ....... data[3] BCC
n = 0 if an error occurred (error code in Status).
n = 4 if data were read from a transponder (Status = 0).
Status: 0 ... no error
-1 ... SERIAL ERROR
-3 ... NOTAG
-9 ... CRYPTOBLOCK NOT INIT
Page 21 (104) Htswp.doc/HS
Communication Reader-Host Rev. 1.0 98-02-10
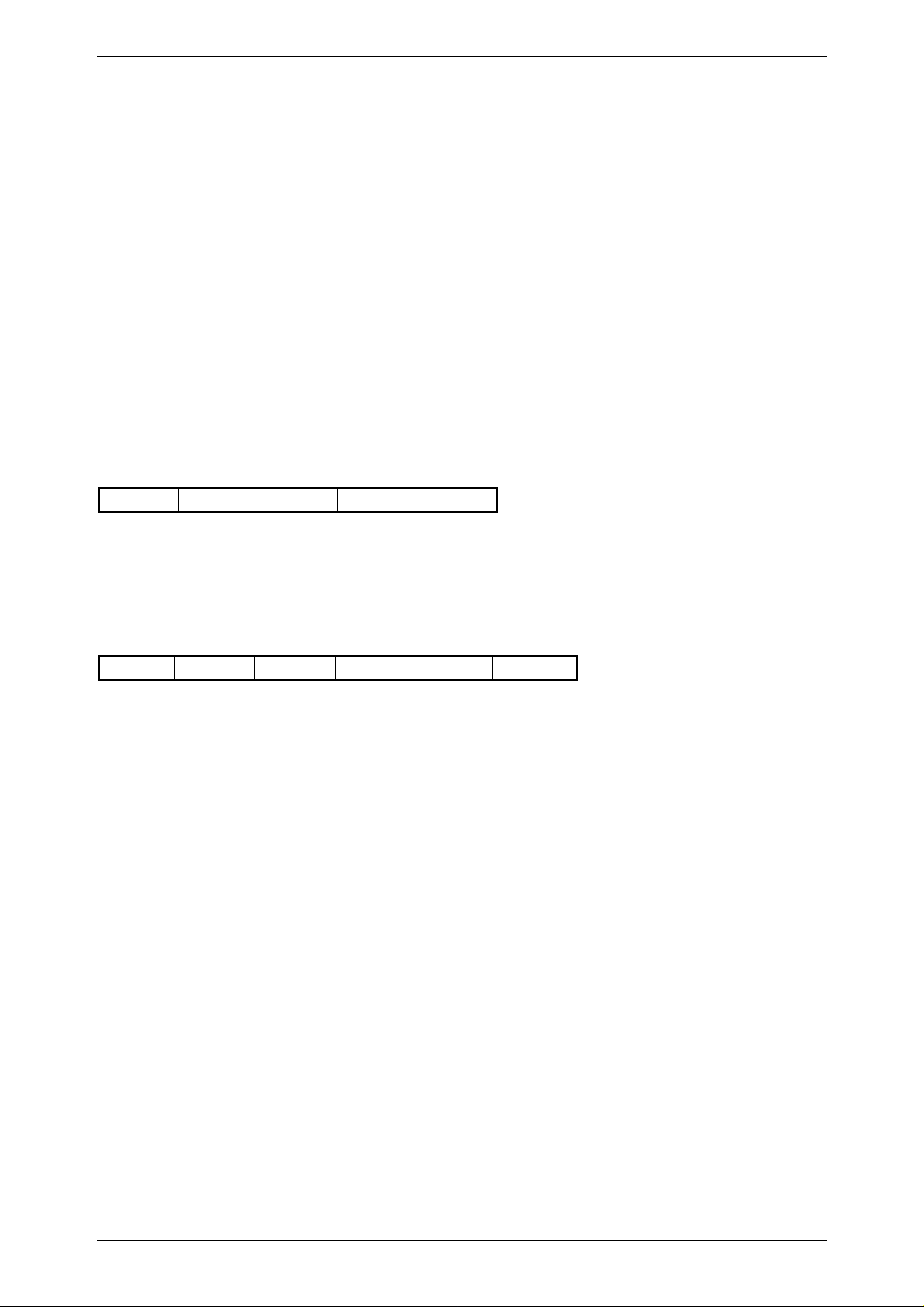
3.7.7 ReadBlock
Reads a block (16 bytes) of the selected HITAG 1 transponder.
If no transponder is selected, a NOTAG message will be generated even if there is a transponder
in the communication field of the antenna.
The start address is specified by -pagenr-. Data is read from the start address until the end of the
corresponding block. Thus a data length of 4, 8, 12 or 16 bytes is possible.
Use byte -crypto- to define whether you want to work in Plain or in Crypto Mode.
Access to the secret area is only possible in Crypto Mode after a mutual authentication.
If -crypto- equals 1 (Crypto Mode) and you did not run an authentication procedure before,
Status will be set to -9.
C-Function: void proloc_ReadBlock (BYTE_T crypto, BYTE_T pagenr, char *data);
Header-File: PROLIB6.H
Serial protocol:
HOST - READ/WRITE DEVICE
0x04 'B' crypto pagenr BCC
crypto: 0x00 ... Plain Mode
0x01 ... Crypto Mode
pagenr: page number (for start address)
READ/WRITE DEVICE - HOST
n+2 Status data[0] ....... data[n-1] BCC
n = 0 if an error occurred (error code in Status).
n = 4, 8, 12, 16 depending on the page address if data were read from a transponder (Status = 0).
Status: 0 ... no error
-1 ... SERIAL ERROR
-3 ... NOTAG
-9 ... CRYPTOBLOCK NOT INIT
Htswp.doc/HS Page 22 (104)
98-02-10 Rev. 1.0 Communication Reader-Host
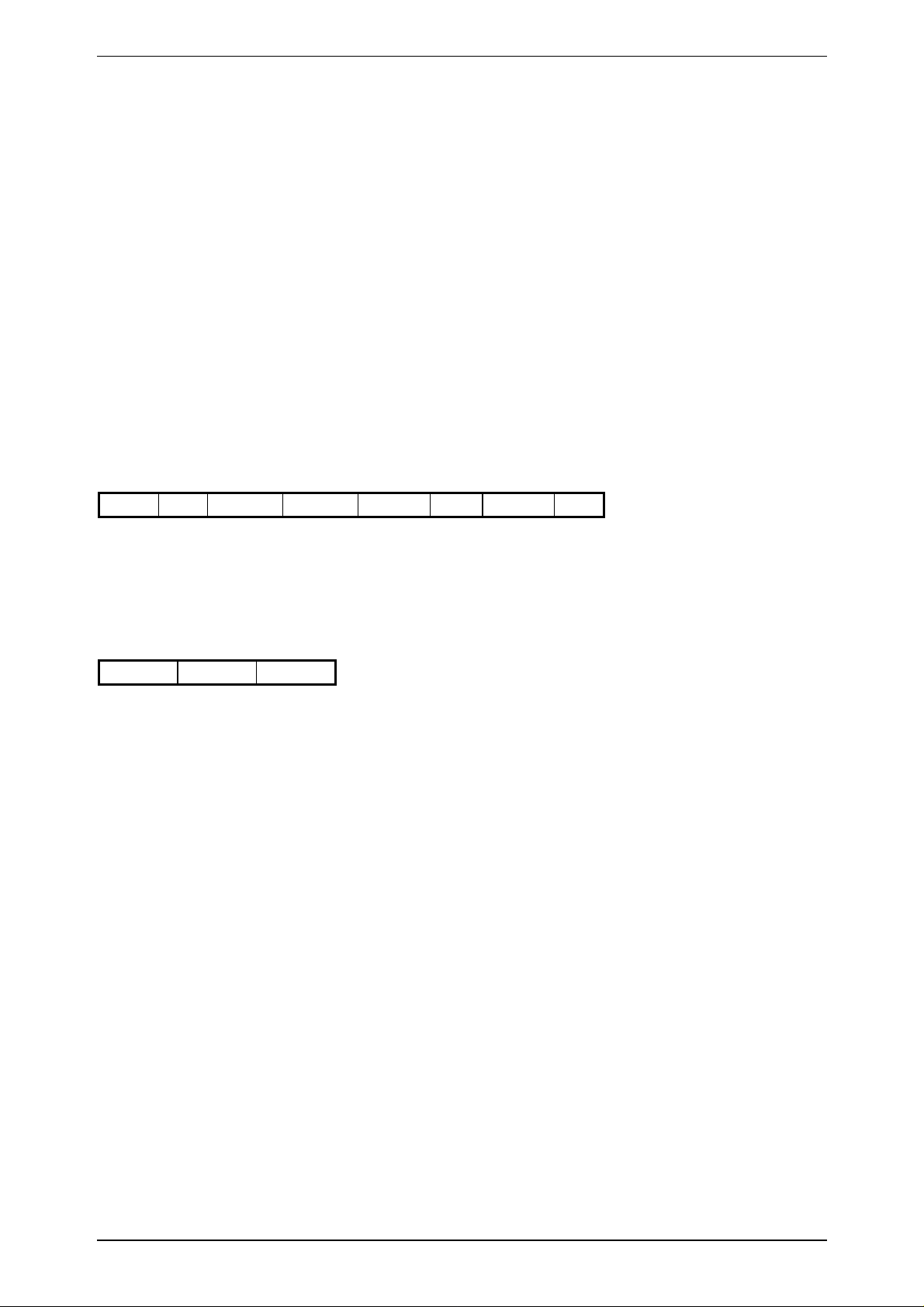
3.7.8 WritePage
Writes a page (4 bytes) to the selected HITAG 1 transponder.
If no transponder is selected, a NOTAG message will be generated even if there is a transponder
in the communication field of the antenna.
Use byte -crypto- to define whether you want to work in Plain or in Crypto Mode.
Access to the secret area is only possible in Crypto Mode after a mutual authentication.
If -crypto- equals 1 (Crypto Mode) and you did not run an authentication process before, Status
will be set to -9.
ATTENTION: To substantially increase the data reliability we strictly recommend to read
the previously written data (read after write).
C-Function: void proloc_WritePage (BYTE_T crypto, BYTE_T pagenr, char *data);
Header-File: PROLIB6.H
Serial protocol:
HOST - READ/WRITE DEVICE
0x08 'p' crypto pagenr data[0] ....... data[3] BCC
crypto: 0x00 ... Plain Mode
0x01 ... Crypto Mode
pagenr: page number
READ/WRITE DEVICE - HOST
0x02 Status BCC
Status: 0 ... no error
-1 ... SERIAL ERROR
-3 ... NOTAG
-4 ... TIMEOUT
-9 ... CRYPTOBLOCK NOT INIT
Page 23 (104) Htswp.doc/HS

Communication Reader-Host Rev. 1.0 98-02-10
3.7.9 WriteBlock
Writes a block (16 bytes) to the selected HITAG 1 transponder.
If no transponder is selected, a NOTAG message will be generated even if there is a transponder
in the communication field of the antenna.
The start address is specified by -pagenr-. Data is written from the start address until the end of
the corresponding block. Thus a data length of 4, 8, 12 or 16 bytes is possible.
Use byte -crypto- to define whether you want to work in Plain or in Crypto Mode.
Access to the secret area is only possible in Crypto Mode after a mutual authentication.
If -crypto- equals 1 (Crypto Mode) and you did not run an authentication procedure before,
Status will be set to -9.
ATTENTION: To substantially increase the data reliability we strictly recommend to read
the previously written data (read after write).
C-Function: void proloc_WriteBlock (BYTE_T crypto, BYTE_T pagenr, char *data);
Header-File: PROLIB6.H
Serial protocol:
HOST - READ/WRITE DEVICE
n+4 'b' crypto pagenr data[0] ....... data[n-1] BCC
crypto: 0x00 ... Plain Mode
0x01 ... Crypto Mode
pagenr: page number (for start address)
READ/WRITE DEVICE - HOST
0x02 Status BCC
Status: 0 ... no error
-1 ... SERIAL ERROR
-3 ... NOTAG
-4 ... TIMEOUT
-9 ... CRYPTOBLOCK NOT INIT
Htswp.doc/HS Page 24 (104)

98-02-10 Rev. 1.0 Communication Reader-Host
3.7.10 TagAuthent
Carries out t he single authentication procedure for HIT AG 1 transponders (authentication of the
transponder). The authentication procedure is aborted after sending the transponder logdata.
Using -keyinfo- you can choose between Key/Logdata Set A and B.
This command can be used - e.g. - to check if Keys and Logdata in the transponder and the
re a d/ w r it e de vice a r e the s ame . ( "C he c k, if the t r a ns pon de r is me mbe r o f t h e s a me ` family´ a s t he
read/write device").
ATTENTION: You cannot use any Crypto commands after TagAuthent.
After this abbreviated authentication procedure the transponder can only be accessed using
GetSnr or the command HFReset.
C-Function: void proloc_TagAuthent (BYTE_T keyinfo);
Header-File: PROLIB6.H
Serial protocol:
HOST - READ/WRITE DEVICE
0x03 'a' keyinfo BCC
keyinfo: 0x00 ... Key/Logdata Set A
0x01 ... Key/Logdata Set B
READ/WRITE DEVICE - HOST
0x02 Status BCC
Status: 0 ... no error
-1 ... SERIAL ERROR
-7 ... AUTHENTICATION ERROR
Page 25 (104) Htswp.doc/HS

Communication Reader-Host Rev. 1.0 98-02-10
3.7.11 MutualAuthent
Carries out the full authentication procedure between the transponder and the read/write device.
After this mutual authentication you are allowed to edit areas which can only be accessed in
Crypto Mode.
Using -keyinfo- you can choose between Key/Logdata Set A and B.
Use a Plain command (that is still encrypted), HFReset or GetSnr (resets the already selected
transponder) to exit this mode.
C-Function: void proloc_MutualAuthent (BYTE_T keyinfo);
Header-File: PROLIB6.H
Serial protocol:
HOST - READ/WRITE DEVICE
0x03 'A' keyinfo BCC
keyinfo: 0x00 ... Key/Logdata Set A
0x01 ... Key/Logdata Set B
READ/WRITE DEVICE - HOST
0x02 Status BCC
Status: 0 ... no error
-1 ... SERIAL ERROR
-7 ... AUTHENTICATION ERROR
Htswp.doc/HS Page 26 (104)
98-02-10 Rev. 1.0 Communication Reader-Host
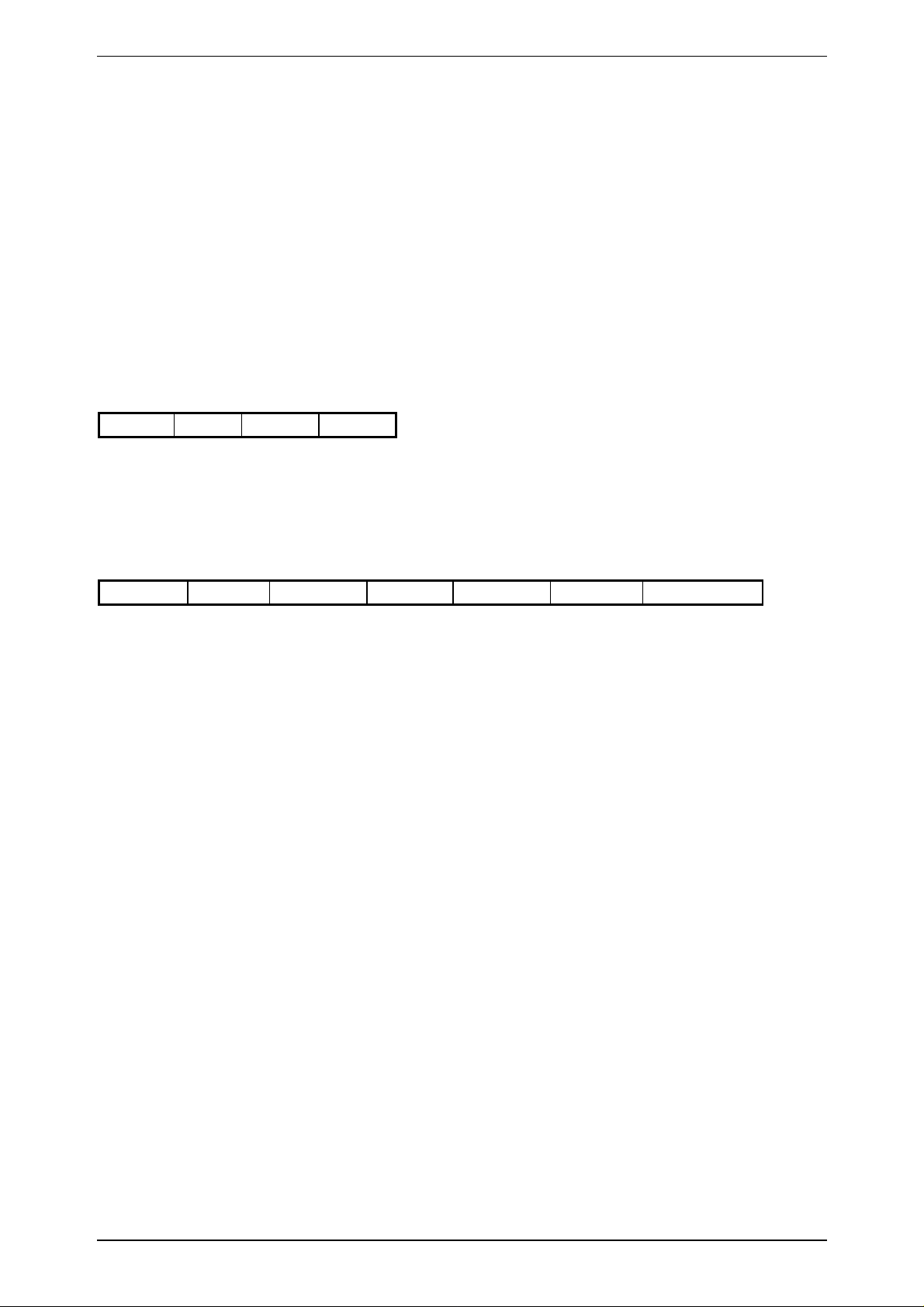
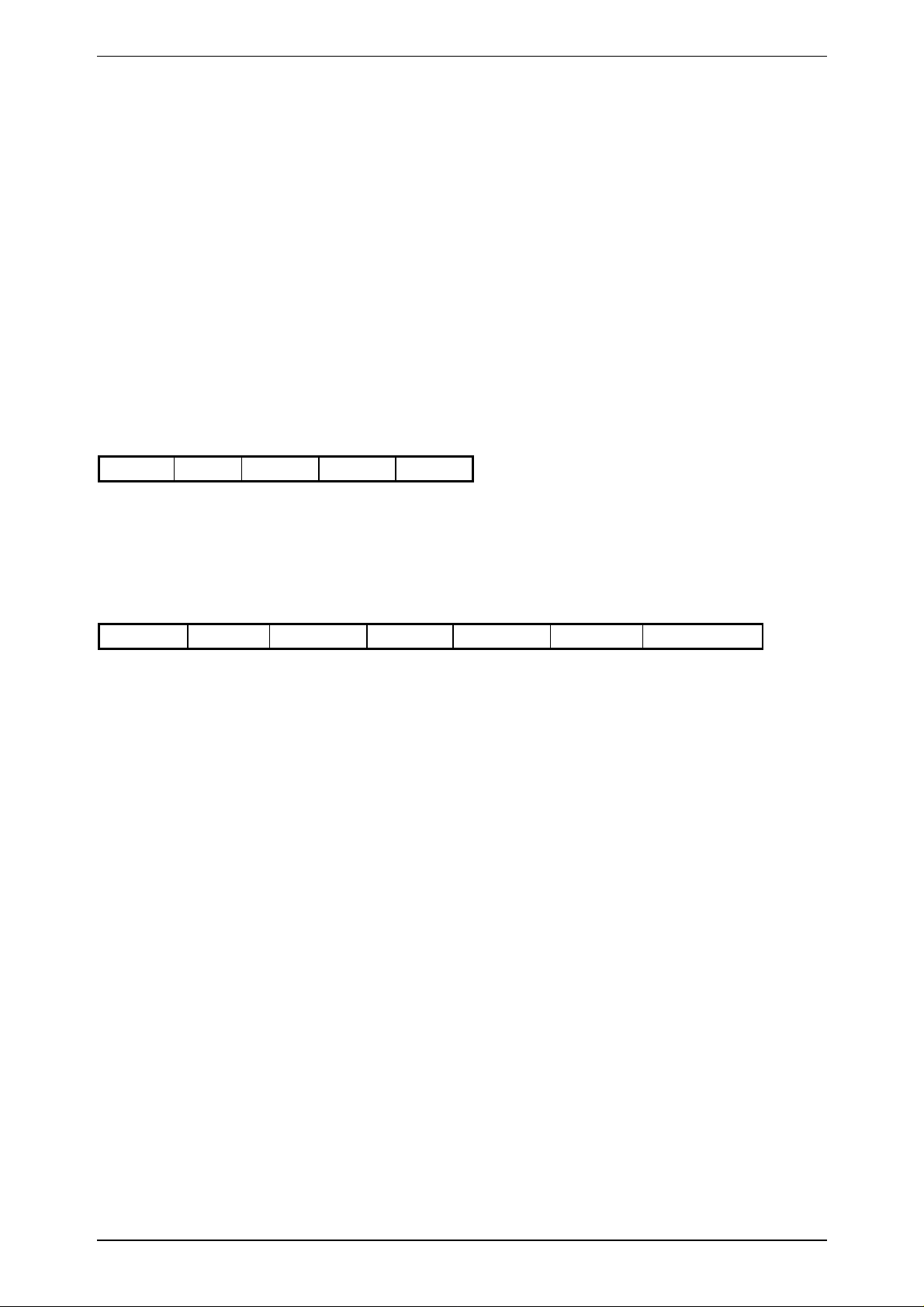
3.7.12 GetSnr_LT
This command is applied to a HITAG 2 transponder being in Password or Crypto Mode.
The command selects the transponder and provides its serial number and Configuration Byte
-config-.
If the byte -Status- shows „no error“ the transponder is selected and ready for read or write
accesses.
The byte -mode- selects one of two possible modes: Password or Crypto.
C-Function: void proloc_GetSnr_LT (BYTE_T mode, DWORD_T *snr, BYTE_T *config);
Header-File: PROLBLT6.H
Serial protocol:
HOST - READ/WRITE DEVICE
0x03 0x80 mode BCC
mode: 0x00 ... Password
0x01 ... Crypto
READ/WRITE DEVICE - HOST
7 0 ------ 31 24
n+2 Status SNR-LSB ------ SNR-MSB config BCC
config: Configuration Byte of HITAG 2
n = 0 if an error occurred (error code in Status).
n = 5 if data were read from a transponder (Status = 0).
Status: 0 ... no error
-1 ... SERIAL ERROR
-3 ... NOTAG
-5 ... INCORRECT PASSWORD RWD
-6 ... INCORRECT PASSWORD TAG
-7 ... AUTHENTICATION ERROR
Page 27 (104) Htswp.doc/HS
Communication Reader-Host Rev. 1.0 98-02-10
3.7.13 GetSnrReset_LT
This command is applied to a HITAG 2 transponder which is currently not in Password or Crypto
Mode but in one of the Public Modes. The command selects the transponder and provides its
serial number and Configuration Byte.
If the byte -Status- shows „no error“ the transponder is selected and ready for read or write
accesses.
The byte -mode- decides whether the selection process for the transponder is done corresponding
to the Password Mode or the Crypto Mode.
C-Function: void proloc_GetSnrReset_LT (BYTE_T mode, DWORD_T *snr,
BYTE_T *config);
Header-File: PROLBLT6.H
Serial protocol:
HOST - READ/WRITE DEVICE
0x03 0x80 mode ‘M’ BCC
mode: 0x00 ... Password
0x01 ... Crypto
READ/WRITE DEVICE - HOST
7 0 ------ 31 24
n+2 Status SNR-LSB ------ SNR-MSB config BCC
config: Configuration Byte of HITAG 2
n = 0 if an error occurred (error code in Status).
n = 5 if data were read from a transponder (Status = 0).
Status: 0 ... no error
-1 ... SERIAL ERROR
-3 ... NOTAG
-5 ... INCORRECT PASSWORD RWD
-6 ... INCORRECT PASSWORD TAG
-7 ... AUTHENTICATION ERROR
Htswp.doc/HS Page 28 (104)

98-02-10 Rev. 1.0 Communication Reader-Host
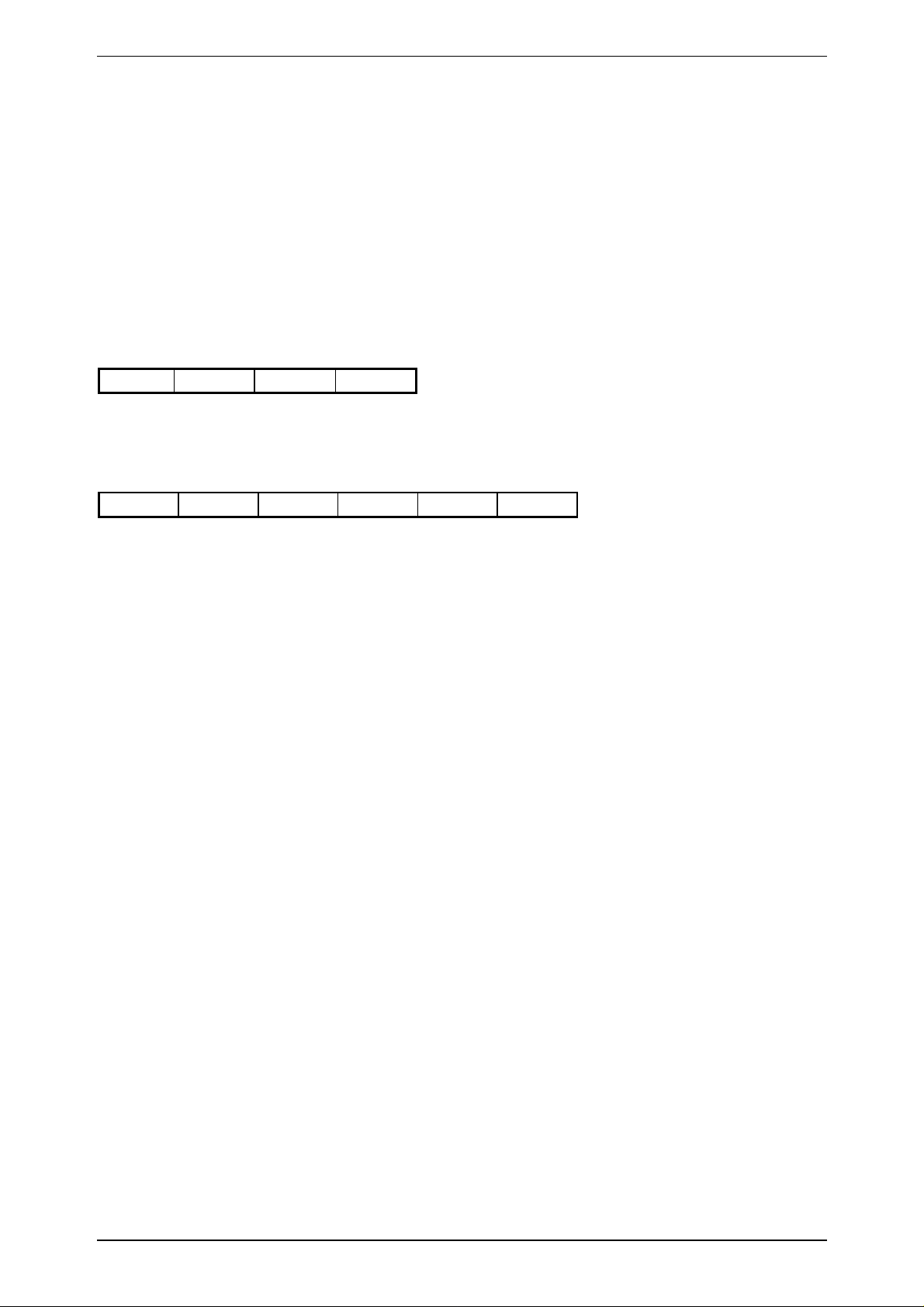
3.7.14 HaltSelected_LT
Puts the selected HITAG 2 transponder into Halt Mode, which means that this transponder
remains silent until it leaves the RF field.
You can reset a transponder previously turned off by HaltSelected_LT using the command
HFReset or putting it out of RF field.
C-Function: void proloc_HaltSelected_LT (void);
Header-File: PROLBLT6.H
Serial protocol:
HOST - READ/WRITE DEVICE
0x02 0x81 0x83
READ/WRITE DEVICE - HOST
0x02 Status BCC
Status: 0 ... no error
-1 ... SERIAL ERROR
-8 ... ACKNOWLEDGEMENT ERROR
Page 29 (104) Htswp.doc/HS
Communication Reader-Host Rev. 1.0 98-02-10
3.7.15 ReadPage_LT
Reads a page (4 bytes) of a selected HITAG 2 transponder.
If no transponder is selected, a NOTAG message will be generated.
Th is command should be used toget h er with R eadPageInv_LT to co mpare plain data with the bitinverted data to gain maximum data reliability.
C-Function: void proloc_ReadPage_LT (BYTE_T pagenr, char *data);
Header-File: PROLBLT6.H
Serial protocol:
HOST - READ/WRITE DEVICE
0x03 0x82 pagenr BCC
pagenr: page number
READ/WRITE DEVICE - HOST
n+2 Status data[0] ....... data[3] BCC
n = 0 if an error occurred (error code in Status).
n = 4 if data were read from a transponder (Status = 0).
Status: 0 ... no error
-1 ... SERIAL ERROR
-3 ... NOTAG
Htswp.doc/HS Page 30 (104)
 Loading...
Loading...