Page 1

CopperLink Model CL2300
Ethernet Extender
User Manual
Important
This is a Class A device and is not intended for use in a residential environment.
Sales Office: +1 (301) 975-1000
Technical Support: +1 (30
E-mail: suppor
WWW: www
Part Number: 07MCL2300-UM, Rev
Revised: May 18, 2018
1) 975-1007
t@patton.com
.patton.com
. B
Page 2

Patton Electronics Company, Inc.
7622 Rickenbacker Drive
Gaithersburg, MD 20879 USA
Tel: +1 (301) 975-1000
Fax: +1 (301) 869-9293
Support: +1 (301) 975-1007
Web: www.patton.com
E-mail: support@patton.com
Trademark Statement
The term CopperLink is a trademark of Patton Electronics Company. All other trade-
marks presented in this document are the property of their respective owners.
Copyright © 2015–2018, Patton Electronics Company. All rights reserved.
The information in this document is subject to change without notice. Patton
Electronics assumes no liability for errors that may appear in this document.
Warranty Information
Patton Electronics warrants all CopperLink components to be free from defects, and
will—at our option—repair or replace the product should it fail within one year from
the first date of the shipment.
This warranty is limited to defects in workmanship or materials, and does not cover
customer damage, abuse or unauthorized modification. If the product fails to perform
as warranted, your sole recourse shall be repair or replacement as described above.
Under no condition shall Patton Electronics be liable for any damages incurred by the
use of this product. These damages include, but are not limited to, the following: lost
profits, lost savings and incidental or consequential damages arising from the use of or
inability to use this product. Patton Electronics specifically disclaims all other warran-
ties, expressed or implied, and the installation or use of this product shall be deemed
an acceptance of these terms by the user.
Page 3

Summary Table of Contents
1 General Information .......................................................................................................................................... 16
2 Installing the CL2300........................................................................................................................................ 20
3 Configuration and Operation............................................................................................................................. 25
4 CL2300 Bridging Contexts ................................................................................................................................29
5 IP Context Overview ......................................................................................................................................... 35
6 Command Line Interface (CLI) ......................................................................................................................... 43
7 Accessing the CLI .............................................................................................................................................. 47
8 System Image Handling ..................................................................................................................................... 59
9 Configuration File Handling.............................................................................................................................. 63
10 Basic System Management ................................................................................................................................. 74
11 Wizard Interface ................................................................................................................................................ 83
12 IP Routing......................................................................................................................................................... 89
13 SNMP Configuration ........................................................................................................................................ 94
14 Contacting Patton for assistance....................................................................................................................... 109
A Compliance Information ................................................................................................................................. 112
B Specifications .................................................................................................................................................. 114
3
Page 4
Table of Contents
About This Guide ...................................................................................................................................................... 11
Audience............................................................................................................................................................... 11
Structure............................................................................................................................................................... 11
Precautions ........................................................................................................................................................... 12
Safety When Working With Electricity ...........................................................................................................13
General Observations ......................................................................................................................................14
Typographical Conventions Used in this Document ............................................................................................ 14
General Conventions ......................................................................................................................................14
1 General Information .......................................................................................................................................... 16
Overview ...............................................................................................................................................................17
Conceptual Overview ............................................................................................................................................18
Default Configuration ...........................................................................................................................................19
2 Installing the CL2300........................................................................................................................................ 20
CopperLink CL2300 Front Panel..........................................................................................................................21
Planning the Installation........................................................................................................................................21
Contents of package ........................................................................................................................................21
What you will need .........................................................................................................................................21
Installation ......................................................................................................................................................22
Connecting the Line Interface ...............................................................................................................................22
Connecting Console Interface ...............................................................................................................................23
Connecting the Ethernet Interface.........................................................................................................................24
Connecting Power.................................................................................................................................................24
3 Configuration and Operation............................................................................................................................. 25
Introduction..........................................................................................................................................................26
Connect with SSH ................................................................................................................................................26
Connect with Console...........................................................................................................................................26
Change the IP address (default: 192.168.200.10) ..................................................................................................26
Change the default username.................................................................................................................................26
Save the Configuration ..........................................................................................................................................26
CopperLink LINE Commands..............................................................................................................................27
Local and Remote ...........................................................................................................................................27
Annex Type ....................................................................................................................................................27
Line Rate Configuration .................................................................................................................................27
Modulation Scheme ........................................................................................................................................27
CopperLink Ports ...........................................................................................................................................27
Signal to Noise Ratio ......................................................................................................................................27
Description .....................................................................................................................................................27
Use Profile ......................................................................................................................................................28
Service Mode ..................................................................................................................................................28
4
Page 5

CopperLink CL2300 User Manual Table of Contents
Shutdown .......................................................................................................................................................28
Exit .................................................................................................................................................................28
Show ...............................................................................................................................................................28
4 CL2300 Bridging Contexts ................................................................................................................................ 29
Configuration Task List.........................................................................................................................................30
Optional .........................................................................................................................................................30
Context Switch: HW Bridge..................................................................................................................................30
Switch Mode Groups .....................................................................................................................................30
Switch Mode VLANS .....................................................................................................................................30
Port Configuration ..........................................................................................................................................31
Bindings ..........................................................................................................................................................32
Context Bridge: SW Bridge Introduction ..............................................................................................................32
Bridge Groups ................................................................................................................................................33
CopperLink Line: Overview ..................................................................................................................................34
CopperLink Line Configuration Parameters ...................................................................................................34
Mandatory Configuration List (local sets payload rate) ...................................................................................34
5 IP Context Overview ......................................................................................................................................... 35
Introduction..........................................................................................................................................................36
Packet Processing in the IP Context ......................................................................................................................37
Classifier .........................................................................................................................................................39
Network Address Port Translation (NAPT) ....................................................................................................39
Routing-table Selection ...................................................................................................................................39
Access Control Lists (ACL) .............................................................................................................................39
Routing ...........................................................................................................................................................39
Packet Processing To/From Local Applications ...............................................................................................40
IP Context Overview Configuration Task List.......................................................................................................40
Planning Your IP Configuration............................................................................................................................40
IP Interface Related Information .....................................................................................................................40
Configuring Physical Ports ..............................................................................................................................41
Creating and Configuring IP Interfaces ...........................................................................................................41
Configuring Packet Classification ...................................................................................................................41
Configuring Network Address Port Translation (NAPT) ................................................................................42
Configuring Static IP Routing ........................................................................................................................42
Configuring Access Control Lists (ACL) .........................................................................................................42
Configuring Quality of Service (QoS) .............................................................................................................42
6 Command Line Interface (CLI) ......................................................................................................................... 43
Introduction..........................................................................................................................................................44
Command modes ..................................................................................................................................................44
CLI prompt ....................................................................................................................................................44
Navigating the CLI .........................................................................................................................................45
Command editing .................................................................................................................................................45
Command help ...............................................................................................................................................45
The No Form .................................................................................................................................................45
5
Page 6

CopperLink CL2300 User Manual Table of Contents
Command completion ....................................................................................................................................45
Command history ...........................................................................................................................................46
Command Editing Shortcuts ..........................................................................................................................46
7 Accessing the CLI .............................................................................................................................................. 47
Introduction..........................................................................................................................................................48
Accessing the CLI task list .....................................................................................................................................48
Accessing via the console port .........................................................................................................................49
Accessing via a secure configuration session over SSH .....................................................................................49
Using an alternate TCP listening port for the Telnet or SSH server ................................................................50
Disabling the Telnet or SSH server .................................................................................................................50
Logging on ......................................................................................................................................................50
Selecting a secure password .............................................................................................................................51
Password encryption .......................................................................................................................................52
Configuring operators, administrators, and superusers ....................................................................................52
Displaying the CLI version .............................................................................................................................54
Displaying account information ......................................................................................................................54
Checking identity and connected users ...........................................................................................................54
Command index numbers ...............................................................................................................................55
Ending a Telnet, SSH or console port session .................................................................................................57
Showing command default values ...................................................................................................................58
8 System Image Handling ..................................................................................................................................... 59
Introduction..........................................................................................................................................................60
System image handling task list .............................................................................................................................60
Displaying system image information .............................................................................................................60
Copying system images from a network server to Flash memory .....................................................................61
9 Configuration File Handling.............................................................................................................................. 63
Introduction..........................................................................................................................................................64
Understanding Configuration Files .................................................................................................................64
Shipping Configuration.........................................................................................................................................66
Configuration File Handling Task List..................................................................................................................66
Copying Configurations Within the Local Memory ........................................................................................67
Replacing the Startup Configuration with a Configuration from Flash Memory .............................................68
Copying Configurations To and From a Remote Storage Location .................................................................69
Replacing the Startup Configuration with a Configuration Downloaded from TFTP Server ..........................69
Displaying Configuration File Information .....................................................................................................70
Modifying the Running Configuration at the CLI ..........................................................................................71
Modifying the Running Configuration Offline ...............................................................................................72
Deleting a Specified Configuration .................................................................................................................73
10 Basic System Management ................................................................................................................................. 74
Introduction..........................................................................................................................................................75
Basic System Management Configuration Task List ..............................................................................................75
Managing Feature License Keys ......................................................................................................................75
6
Page 7

CopperLink CL2300 User Manual Table of Contents
Setting System Information ............................................................................................................................76
Setting the System Banner ..............................................................................................................................77
Setting Time and Date ....................................................................................................................................78
Configuring Daylight Savings Time Rules ......................................................................................................78
Display Clock Information .............................................................................................................................79
Display Time Since Last Restart ......................................................................................................................79
Configuring the Web Server ...........................................................................................................................80
Restarting the System ......................................................................................................................................80
Displaying the System Logs .............................................................................................................................81
Displaying Reports ..........................................................................................................................................81
Configuring the blink interval .........................................................................................................................82
Configuring the Syslog Client .........................................................................................................................82
11 Wizard Interface ................................................................................................................................................ 83
Introduction..........................................................................................................................................................84
Browser Notes .......................................................................................................................................................84
Connect with Web GUI........................................................................................................................................84
Management IP Setup .....................................................................................................................................86
Line Setup .......................................................................................................................................................86
12 IP Routing......................................................................................................................................................... 89
Introduction..........................................................................................................................................................90
Basic Routing ........................................................................................................................................................90
Static Routes ...................................................................................................................................................90
System Routes .................................................................................................................................................91
Dynamic Routes .............................................................................................................................................92
Show Routes ...................................................................................................................................................92
Basic Static Routing Example ..........................................................................................................................92
13 SNMP Configuration ........................................................................................................................................ 94
Introduction..........................................................................................................................................................95
Simple Network Management Protocol (SNMP) ..................................................................................................95
SNMP Basic Components ..............................................................................................................................95
SNMP Basic Commands ................................................................................................................................95
SNMP Management Information Base (MIB) ................................................................................................96
Network Management Framework .................................................................................................................96
Identification of a CL2300 via SNMP...................................................................................................................97
SNMP Tools .........................................................................................................................................................97
SNMP Configuration Task List.............................................................................................................................97
Setting Basic System Information ..........................................................................................................................97
Setting Access Community Information..............................................................................................................100
Setting Allowed Host Information.......................................................................................................................101
Specifying the Default SNMP Trap Target..........................................................................................................101
Displaying SNMP Related Information...............................................................................................................102
Using the ManageEngine SNMP Utilities ...........................................................................................................102
Using the MibBrowser ..................................................................................................................................103
7
Page 8

CopperLink CL2300 User Manual Table of Contents
Using the TrapViewer ...................................................................................................................................104
Standard SNMP Version 1 Traps ........................................................................................................................107
SNMP Interface Traps ........................................................................................................................................108
14 Contacting Patton for assistance....................................................................................................................... 109
Introduction........................................................................................................................................................110
Contact information............................................................................................................................................110
Warranty Service and Returned Merchandise Authorizations (RMAs).................................................................110
Warranty coverage ........................................................................................................................................110
RMA numbers ..............................................................................................................................................111
A Compliance Information ................................................................................................................................. 112
Compliance .........................................................................................................................................................113
PSTN ...........................................................................................................................................................113
Radio and TV Interference ..................................................................................................................................113
CE Declaration of Conformity ............................................................................................................................113
Authorized European Representative ...................................................................................................................113
B Specifications .................................................................................................................................................. 114
LAN Connection.................................................................................................................................................115
CopperLink Connection ...............................................................................................................................115
CopperLink Line Rate and CopperLink Distance................................................................................................115
Line Rate ......................................................................................................................................................115
Distance ........................................................................................................................................................115
LED Status Indicators .........................................................................................................................................116
Console ...............................................................................................................................................................116
Power Supply ......................................................................................................................................................116
External AC ..................................................................................................................................................116
External DC .................................................................................................................................................116
Physical ...............................................................................................................................................................116
8
Page 9
List of Figures
1 Ethernet bridging over a twisted-pair connection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
2 Remote/CPE Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
3 CL2300 front panel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
4 CL2300 rear panel options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
5 CL2300 (RJ-45) twisted-pair line interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
6 Pinout for two devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
7 RJ-45 to RJ-11 cable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
8 DB-9-to-RJ-45 cable diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
9 CL2300 10/100Base-T RJ-45 Connector Pin-out . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
10 Switch mode VLANS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
11 Bridge Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
12 Breaking down Trinity IOS concepts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
13 IP context and related elements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
14 Processing order of IP services attached to an IP interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
15 Setup for initial configuration via the console port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
16 Sample configuration file . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
17 Local memory regions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
18 Remote memory regions for Trinity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
19 Login . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
20 Wizard Homepage . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
21 Choose Wizard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
22 Basic Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
23 Configure Preview Option . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
24 Confirmation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
25 Static route example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
26 ManageEngine MibBrowser displaying some of the System Group objects . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
27 ManageEngine MibBrowser Settings Button on the Toolbar . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104
28 ManageEngine TrapViewer displaying received traps . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104
29 ManageEngine Trap Details window of TrapViewer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
9
Page 10
List of Tables
1 General conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
2 CL2300 LED description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
3 Details available in the Trap Details window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106
10
Page 11

About This Guide
This guide describes the CopperLink Model CL2300 hardware, installation and basic configuration.
Audience
This guide is intended for the following users:
• Operators
• Installers
• Maintenance technicians
Structure
This guide contains the following chapters and appendices:
• Chapter 1, starting on page 16, provides a general introduction to the CL2300
• Chapter 2, starting on page 20, provides information about installing the CL2300
• Chapter 3, starting on page 25, provides information on configuring the CL2300
• Chapter 4, starting on page 29, provides information on CL2300 bridging
• Chapter 5, starting on page 35, provides information on the IP context overview
• Chapter 6, starting on page 43, provides information about the Command Line Interface (CLI)
• Chapter 7, starting on page 47, provides information on accessing the CLI
• Chapter 8, starting on page 59, provides information on system image handling for the CL2300
• Chapter 9, starting on page 63, provides information about configuration file handling for the CL2300
• Chapter 10, starting on page 74, provides information about basic system management
• Chapter 11, starting on page 83, provides information about the Wizard
• Chapter 12, starting on page 89, provides information about IP routing
• Chapter 13, starting on page 94, provides information about SNMP configuration
• Chapter 14, starting on page 109, provides information on contacting Patton technical support for assis-
tance
• Appendix A, starting on page 112, provides compliance information for the CL2300
• Appendix B, starting on page 114, provides specifications for the CL2300
For best results, read the contents of this guide before you install the CopperLink CL2300.
11
Page 12

CopperLink CL2300 User Manual
T
Precautions
Notes and cautions, which have the following meanings, are used throughout this guide to help you become
aware of potential Router modem problems. Warnings relate to personal injury issues, and Cautions refer to
potential property damage.
Note A note presents additional information or interesting sidelights.
The alert symbol and IMPORTANT heading calls attention to
important information.
IMPORTAN
The alert symbol and CAUTION heading indicate a potential hazard. Strictly follow the instructions to avoid property damage.
CAUTION
The shock hazard symbol and CAUTION heading indicate a
potential electric shock hazard. Strictly follow the instructions to
avoid property damage caused by electric shock.
CAUTION
WARNING
WARNING
The alert symbol and WARNING heading indicate a potential safety hazard. Strictly follow the warning instructions
to avoid personal injury.
The shock hazard symbol and WARNING heading indicate
a potential electric shock hazard. Strictly follow the warning instructions to avoid injury caused by electric shock.
12
Page 13
CopperLink CL2300 User Manual
Safety When Working With Electricity
• Do not open the device when the power cord is con-
nected. For systems without a power switch and without
WARNING
an external power adapter, line voltages are present
within the device when the power cord is connected.
• For devices with an external power adapter, the power
adapter shall be a listed Limited Power Source. The
mains outlet that is utilized to power the device shall be
within 10 feet (3 meters) of the device, shall be easily
accessible, and protected by a circuit breaker in compliance with local regulatory requirements.
• For AC powered devices, ensure that the power cable
used meets all applicable standards for the country in
which it is to be installed.
• For AC powered devices which have 3 conductor power
plugs (L1, L2 & GND or Hot, Neutral & Safety/Protective
Ground), the wall outlet (or socket) must have an earth
ground.
• For DC powered devices, ensure that the interconnecting
cables are rated for proper voltage, current, anticipated
temperature, flammability, and mechanical serviceability.
• WAN, LAN & PSTN ports (connections) may have hazard-
ous voltages present regardless of whether the device is
powered ON or OFF. PSTN relates to interfaces such as
telephone lines, FXS, FXO, DSL, xDSL, T1, E1, ISDN,
Voice, etc. These are known as “hazardous network voltages” and to avoid electric shock use caution when
working near these ports. When disconnecting cables for
these ports, detach the far end connection first.
• Do not work on the device or connect or disconnect
cables during periods of lightning activity
WARNING
This device contains no user serviceable parts. This
device can only be repaired by qualified service personnel.
In accordance with the requirements of council directive 2002/96/
EC on Waste of Electrical and Electronic Equipment (WEEE),
ensure that at end-of-life you separate this product from other
waste and scrap and deliver to the WEEE collection system in
your country for recycling.
13
Page 14

CopperLink CL2300 User Manual
This device is NOT intended nor approved for connection
to the PSTN. It is intended only for connection to customer
premise equipment.
WARNING
Electrostatic Discharge (ESD) can damage equipment and
impair electrical circuitry. It occurs when electronic printed circuit
cards are improperly handled and can result in complete or inter-
CAUTION
mittent failures. Do the following to prevent ESD:
Always follow ESD prevention procedures when removing and
replacing cards.
Wear an ESD-preventive wrist strap, ensuring that it makes good
skin contact. Connect the clip to an unpainted surface of the
chassis frame to safely channel unwanted ESD voltages
to ground.
To properly guard against ESD damage and shocks, the wrist
strap and cord must operate effectively. If no wrist strap is available, ground yourself by touching the metal part of the chassis.
General Observations
• Clean the case with a soft slightly moist anti-static cloth
• Place the unit on a flat surface and ensure free air circulation
void exposing the unit to direct sunlight and other heat sources
• A
rotect the unit from moisture, vapors, and corrosive liquids
• P
Typographical Conventions Used in this Document
This section describes the typographical conventions and terms used in this guide.
General Conventions
The procedures described in this manual use the following text conventions:
Table 1. General conventions
Convention Meaning
Garamond blue type
Helvetica bold type Commands and keywords are in boldface font.
Helvetica bold-italic type Parts of commands, which are related to elements already named by the user,
Italicized Helvetica type Variables for which you supply values are in italic font
Helvetica type Indicates the names of fields or windows.
Garamond bold type Indicates the names of command buttons that execute an action.
Indicates a cross-reference hyperlink that points to a figure, graphic, table, or section heading. Clicking on the hyperlink jumps you to the reference. When you
ha
ve finished reviewing the reference, click on the Go to Previous View
button
are in boldface italic font.
in the Adobe® Acrobat® Reader toolbar to return to your starting point.
14
Page 15
CopperLink CL2300 User Manual
Table 1. General conventions (Continued)
Convention Meaning
< > Angle brackets indicate function and keyboard keys, such as <SHIFT>, <CTRL>,
<C>, and so on.
[ ] Elements in square brackets are optional.
{a | b | c} Alternative but required keywords are grouped in braces ({ }) and are separated
by vertical bars ( | )
screen Terminal sessions and information the system displays are in screen font.
node The leading IP address or nodename of a SmartNode is substituted with node in
boldface italic font.
SN The leading SN on a command line represents the nodename of the SmartNode
# An hash sign at the beginning of a line indicates a comment line.
15
Page 16
Chapter 1 General Information
Chapter contents
Overview ...............................................................................................................................................................17
Conceptual Overview ............................................................................................................................................18
Default Configuration ...........................................................................................................................................19
16
Page 17

CopperLink CL2300 User Manual 1 • General Information
Overview
Patton’s CopperLink™ Model CL2300 is a cost effective Ethernet Extender capable of achieving bandwidth
rates of over 60 Mbps. The CL2300 is the ideal choice for providing internet access to bandwidth hungry small
to medium size offices, wireless backhaul, Metro Ethernet, even LAN-to-LAN extensions.
The Model CL2300 can bond from 1 to 4 pairs to increase overall bandwidth. Each pair is capable of 5.7 to
15.3 Mbps depending on your distance requirements. The ability to configure pair bonding and various line
rate modes enables service providers, integrators and businesses to choose the best available rate vs. reach com
bination for the application.
The CL2300 is a layer two device. This means that it operates on the MAC layer and much of its functionality
is analogous to that of an Ethernet switch. The CL2300 has limited routing functionality. It is capable of rout
ing traffic only for the purpose of in-band or out-band management of the device.
The CL2300 defaults to plug-n-play mode which enables CopperLink Extenders to pair up automatically at
the best rate achievable. Should a pair be faulty the CL2300 will automatically adjust the line rate to ensure the
network connection remains stable.
In addition to offering Patton’s highly regarded CopperLink plug-n-play
features, the managed CopperLink series adds a higher level of network control for the more demanding appli
cations.
The network management port is securely protected. Stateful Firewall inspection of traffic, accomplished
through the creation of Access Control Lists (ACLs), enables the filtering of traffic based on numerous criteria
including source and destination IP address, port, connection state, and protocol.
-
-
-
Logical and physical ports are selectable for bridging. Features such VLANs are configurable on a per-port
basis. Bridged traffic can be tagged and prioritized according to user defined parameters.
The CL2300 offers easy installation. The variety of configuration options include CLI via console (RS232),
Telnet, or SSH. Also included is HTTP web-based management, and SNMP.
Patton's managed CopperLink series offer the versatility and reliability demanded for the most critical network
applications at an affordable price.
Overview 17
Page 18
CopperLink CL2300 User Manual 1 • General Information
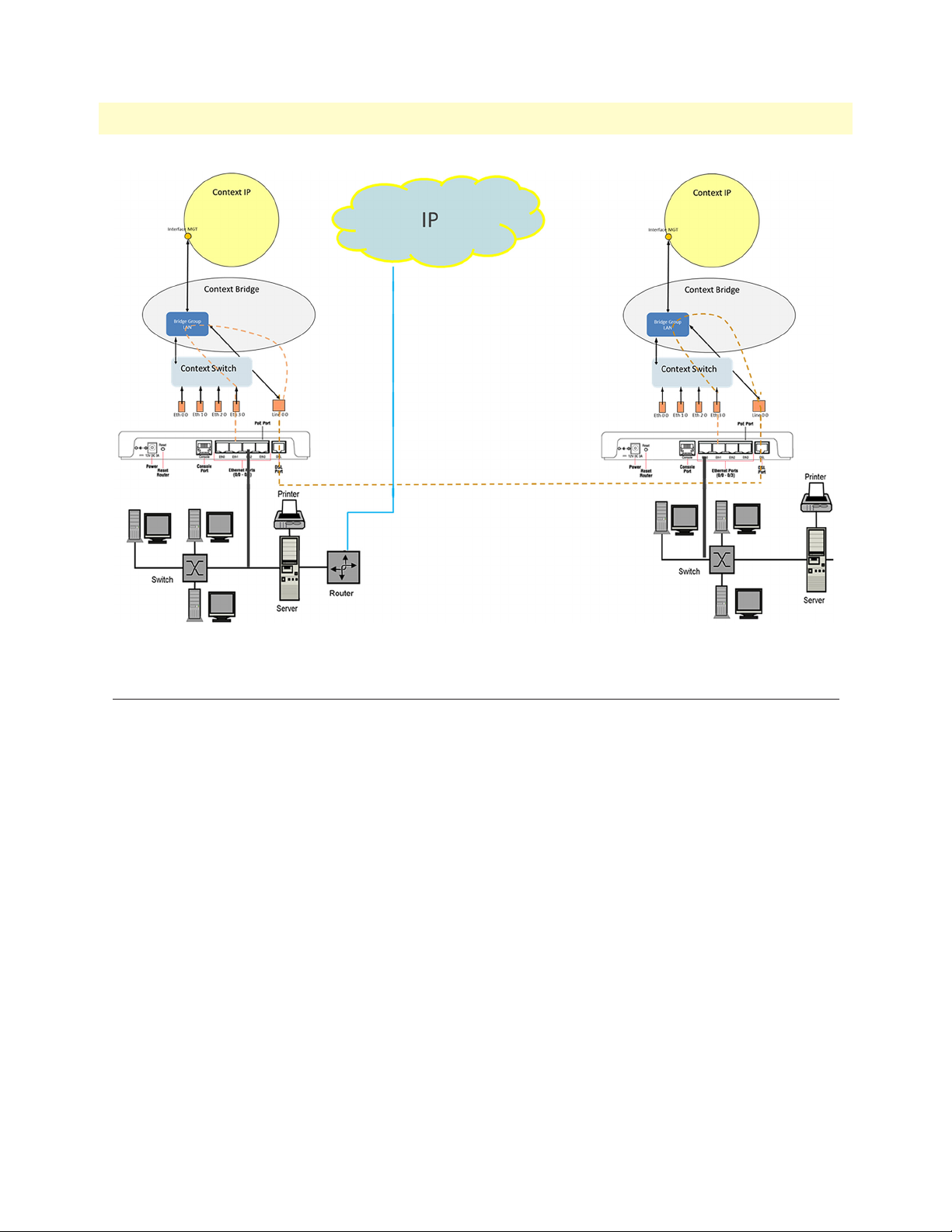
Figure 1. Ethernet bridging over a twisted-pair connection
Conceptual Overview
This guide will break down the configuration concepts in figure 1 so the technician will know how to manipu-
late the data flow at every level of the Open Systems Interconnection (OSI) model. It will also give you a
detailed look at the management and system lev
plug-n-play mode Ethernet extenders, Patton has provided for more advanced capabilities and extreme flexibility in configuring the units for your desired application requirements.
el of the units. Although the units are capable of being simple
Conceptual Overview 18
Page 19
CopperLink CL2300 User Manual 1 • General Information
Default Configuration
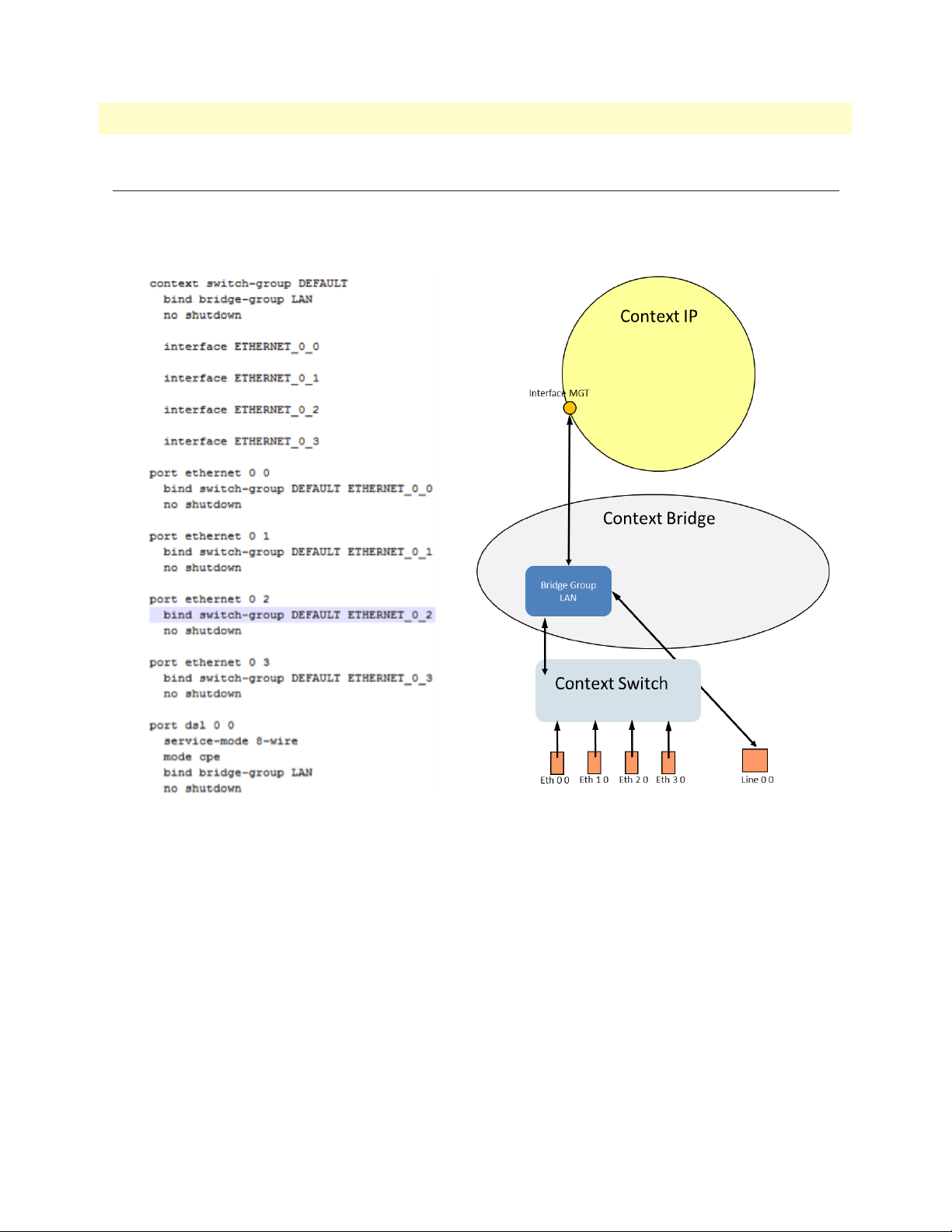
Let’s look at the data flow in combination with the conceptual view of the CL2300. This configuration is a
remote/CPE configuration is shown in figure 2
Figure 2. Remote/CPE Configuration
Traffic flow is as follows: Ethernet (Eth) ports are bound to Context Switch. Context Switch and Line are
bound to the Bridge Group LAN. This is how the traffic moves from the Line ports to the Ethernet Switch.
Default Configuration 19
Page 20
Chapter 2 Installing the CL2300
Chapter contents
CopperLink CL2300 Front Panel..........................................................................................................................21
Planning the Installation........................................................................................................................................21
Contents of package ........................................................................................................................................21
What you will need .........................................................................................................................................21
Installation ......................................................................................................................................................22
Connecting the Line Interface ...............................................................................................................................22
Connecting Console Interface ...............................................................................................................................23
Connecting the Ethernet Interface.........................................................................................................................24
Connecting Power.................................................................................................................................................24
20
Page 21
CopperLink CL2300 User Manual 2 • Installing the CL2300
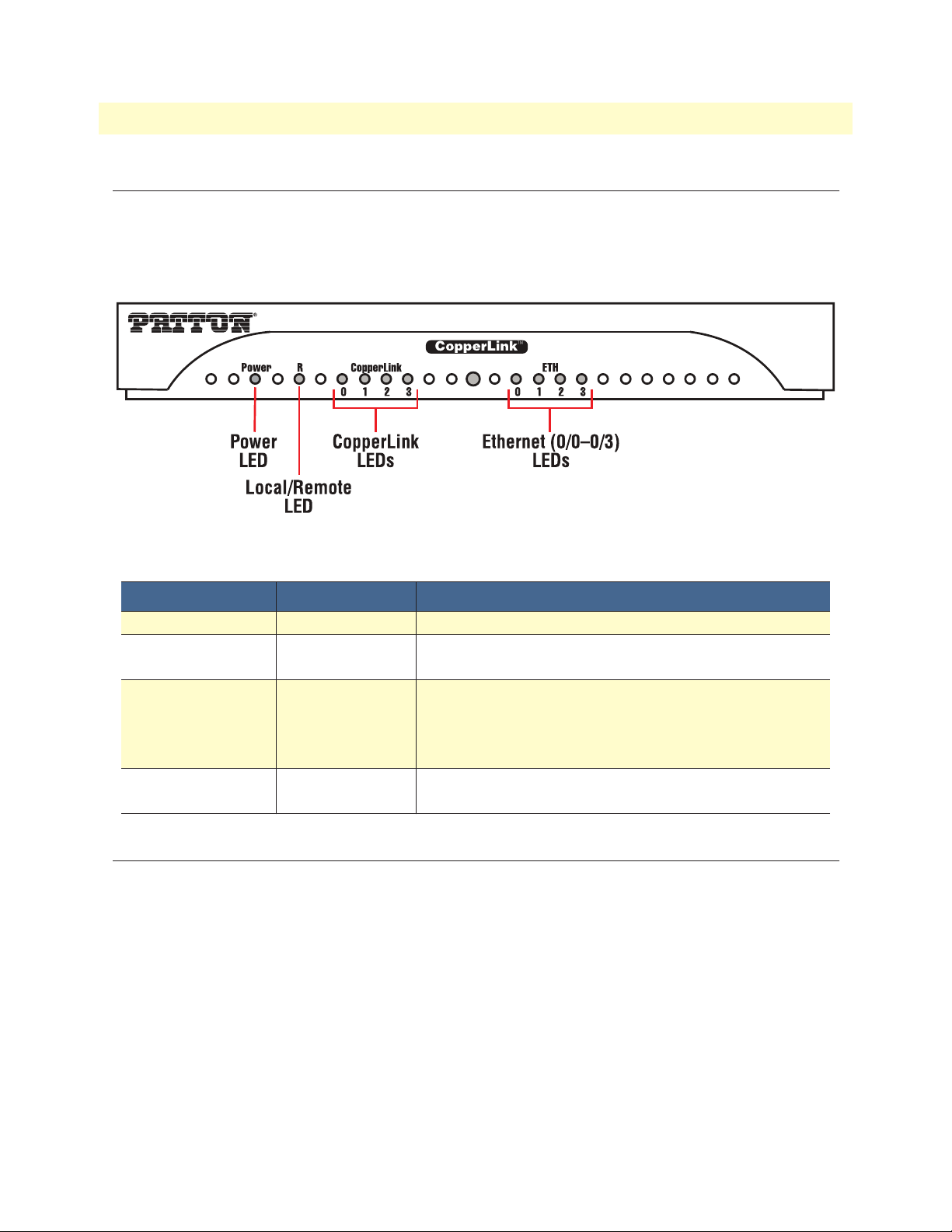
CopperLink CL2300 Front Panel
The CL2300 features front panel LEDs that monitor power, Ethernet signals, CopperLink connection, and
remote/local setting. Figure 3 shows the location of the LEDs. Table 2 describes LED functions.Before apply-
ing power to the CL2300, review Chapter 2, “Connecting Power” on page 24 to verify that the unit is con-
nected to the appropriate power source.
Figure 3. CL2300 front panel
Table 2. CL2300 LED description
LED Indication Description
Power ON The device is powered on.
CPE OFF
ON
CopperLink Pair
(one LEAD for each
port [1 on 3301, 2 on
3302, 4 on 3304])
Ethernet
(0/0-0/3)
OFF
ON
SLOW BLINK
FAST BLINK
ON
OFF
CopperLink (WAN) is configured as Local
CopperLink (WAN) is configured as Remote.
Port is configured as DOWN.
Port is in data mode.
Port is in handshake mode (looking for a remote signal).
Port is in training mode (active communication with remote).
Port is linked.
Data is passing over the port.
Planning the Installation
Contents of package
• CL2300 Long Range E
• E
xternal power supply for CopperLink Model CL2300
• E
thernet cable with RJ45 plugs on each end (included)
What you will need
efault IP address: 192.168.200.10
• D
• D
efault username: admin
• D
efault password: (no password)
• Computer r
unning Microsoft Windows software
thernet Extender
CopperLink CL2300 Front Panel 21
Page 22
CopperLink CL2300 User Manual 2 • Installing the CL2300
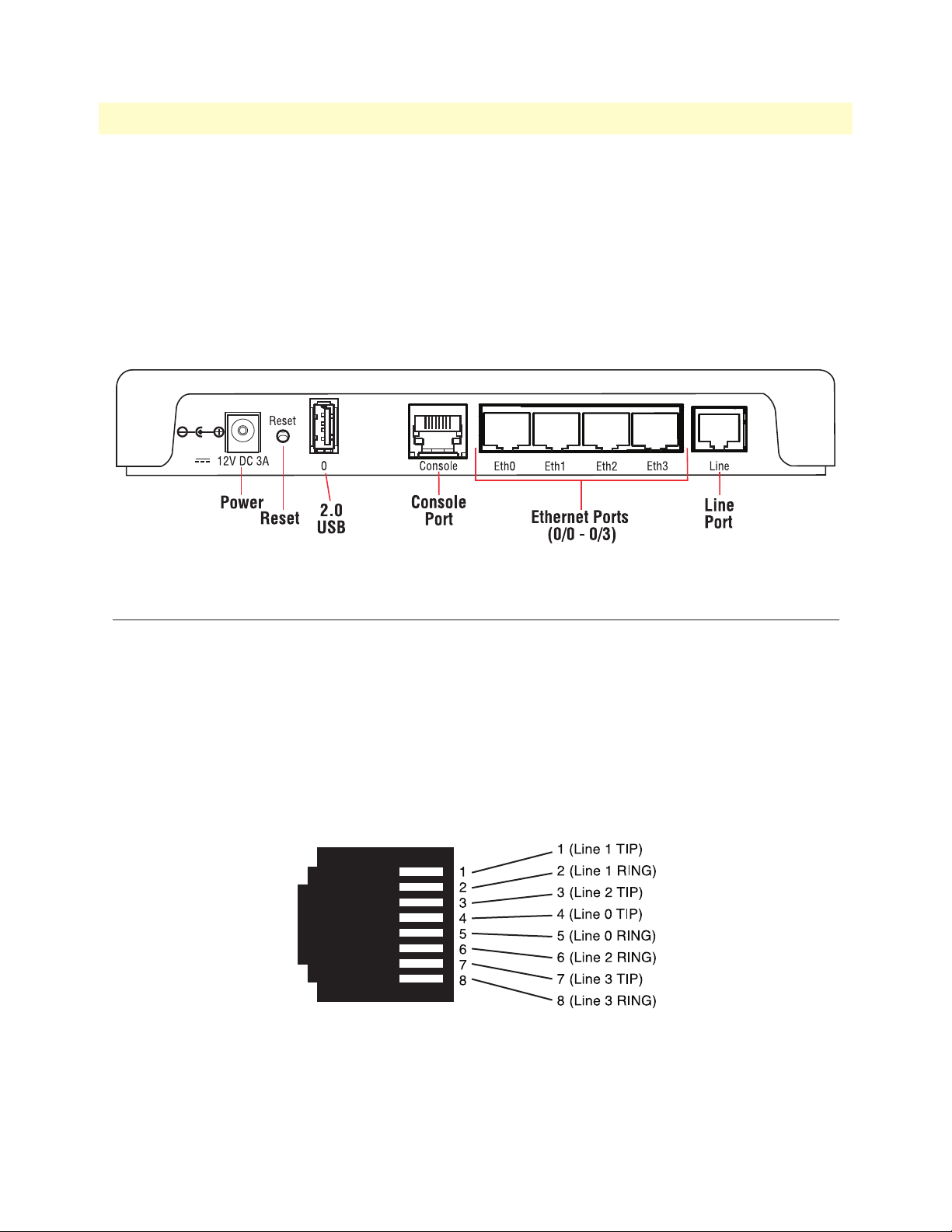
Installation
To install the CL2300 Ethernet Extender, do the following:
1. Connect the line inter
Note See figure 4 for the rear panel arrangements
2. Connect the E
thernet interface (refer to “Connecting the Ethernet Interface” on page 24).
3. Connect the po
face between the units (refer to “Connecting the Line Interface” on page 22).
wer plug (refer to “Connecting Power” on page 24)
Figure 4. CL2300 rear panel options
Connecting the Line Interface
Follow the steps below to connect the CL2300 interfaces.
1. T
o function properly, the two CL2300s must be connected together using twisted-pair, unconditioned,
dry, metal wire, between 19 (0.9mm) and 26 AWG (0.4mm). Leased circuits that run through signal
equalization equipment are not acceptable.
2. The E
thernet Extender is equipped with an RJ-45 interface jack (Line), which conforms to the T568B
standard. As such, any standard Category 5e cable can be used to directly connect two extenders. Depending on the extender model, it will have a two-wire, four-wire or eight-wire interface
Observe the signal/pin relationship on the CL2300’s L
Figure 5. CL2300 (RJ-45) twisted-pair line interface
ine interface jack for each pair in figure 5.
Figure 6 shows the proper way to wire a cable with an RJ-45 jack on one end and four RJ-11jacks on the other
(see figure 7 on page 23).
Connecting the Line Interface 22
Page 23
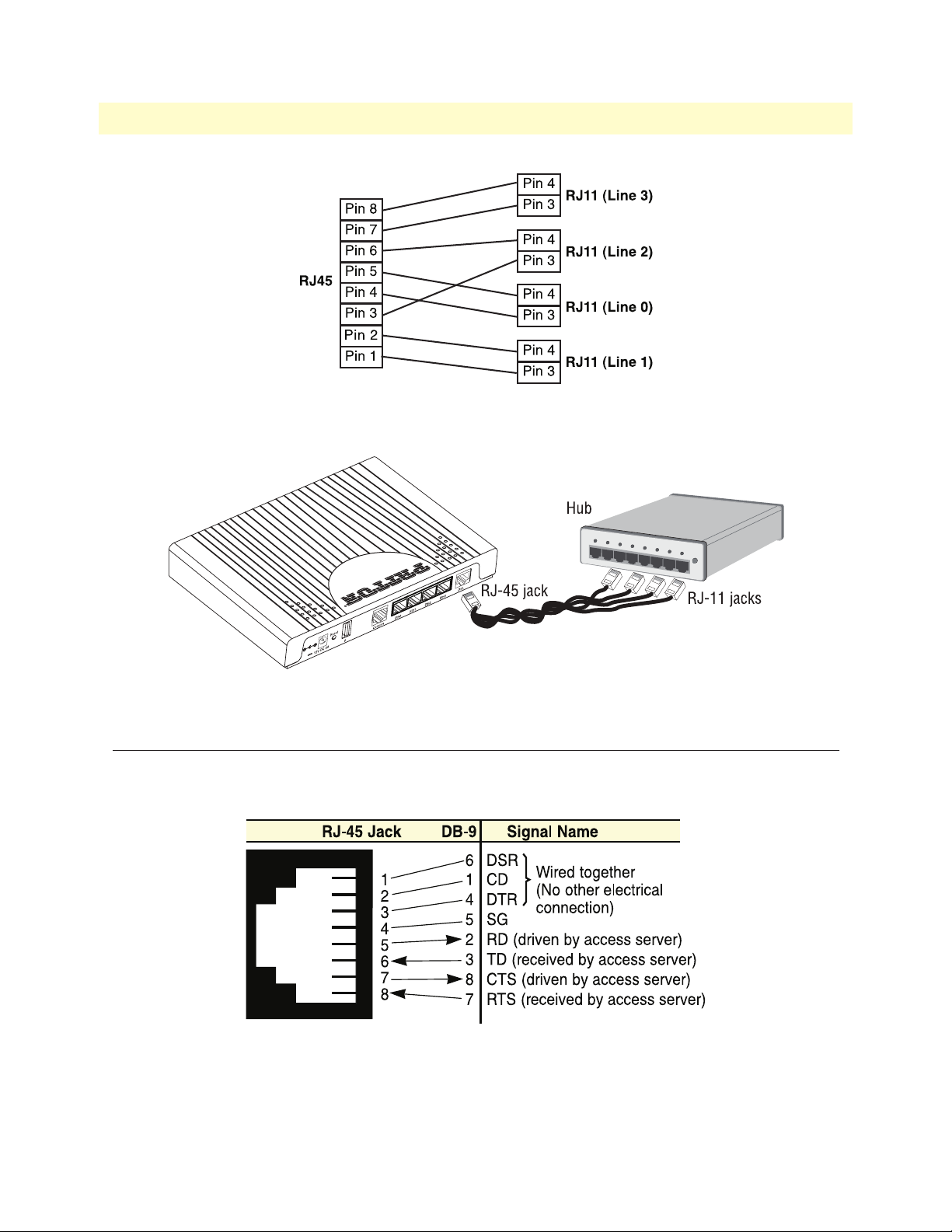
CopperLink CL2300 User Manual 2 • Installing the CL2300
Figure 6. Pinout for two devices
Figure 7. RJ-45 to RJ-11 cable
Connecting Console Interface
Install the supplied RJ-45-to-RJ-45 cable with the DB9-RJ45 adapter between the CL2300 RS-232 port and
an open serial port on your computer. If you need to assemble your own cable, refer to the pinout diagram in
figure 8
.
Figure 8. DB-9-to-RJ-45 cable diagram
Connecting Console Interface 23
Page 24

CopperLink CL2300 User Manual 2 • Installing the CL2300
Connecting the Ethernet Interface
The Long Range Ethernet Extender has four unshielded RJ-45 Auto-MDIX10/100Base-T interfaces. These
ports are designed to connect directly to a 10/100Base-T device or network. You may connect this port to a
hub or PC using a straight through or crossover cable that is up to 328 ft. long.
.
1
2
3
4
5
6
7
8
1 TX+ (data output)
2 TX- (data output)
3 RX+ (data input)
4 (no connection)
5 (no connection)
6 RX- (data input)
7 (no connection)
8 (no connection)
Figure 9. CL2300 10/100Base-T RJ-45 Connector Pin-out
Connecting Power
The Long Range Ethernet Extender does not have a power switch, so it powers up as soon as it is plugged in.
The power connection is made via the barrel jack on the rear panel of the CL2300. No configuration is neces-
sary for the power supply.
An external AC or DC power supply is available separately. This connection is made via the barrel jack on the
ear panel of the CL2300. No configuration is necessary for the power supply.
r
DC power (supplied via the power supply jack to the CL2300) must meet the following requirements; DC
po
wer supplied must be regulated 12VDC ±5%, 1.0A minimum. Center pin is +12V. The barrel type plug has
a 2.5/5.5/10mm I.D./O.D./Shaft Length dimensions.
Connecting the Ethernet Interface 24
Page 25
Chapter 3 Configuration and Operation
Chapter contents
Introduction..........................................................................................................................................................26
Connect with SSH ................................................................................................................................................26
Connect with Console...........................................................................................................................................26
Change the IP address (default: 192.168.200.10) ..................................................................................................26
Change the default username.................................................................................................................................26
Save the Configuration ..........................................................................................................................................26
CopperLink LINE Commands..............................................................................................................................27
Local and Remote ...........................................................................................................................................27
Annex Type ....................................................................................................................................................27
Line Rate Configuration .................................................................................................................................27
Modulation Scheme ........................................................................................................................................27
CopperLink Ports ...........................................................................................................................................27
Signal to Noise Ratio ......................................................................................................................................27
Description .....................................................................................................................................................27
Use Profile ......................................................................................................................................................28
Service Mode ..................................................................................................................................................28
Shutdown .......................................................................................................................................................28
Exit .................................................................................................................................................................28
Show ...............................................................................................................................................................28
25
Page 26

CopperLink CL2300 User Manual 3 • Configuration and Operation
Introduction
You can connect a PC to configure the CopperLink CL2300 using the CLI.
Connect with SSH
1. Connect the Ethernet cable.
2. Connect the power supply.
3. Connect via SSH to the default address 192.168.200.10
4. Login with the default username admin and no password.
Connect with Console
1. Connect the RS232 Console cable.
2. Connect the power supply.
3. Login with the default username admin and no password.
Change the IP address (default: 192.168.200.10)
Follow the command sequence below.
node~>enable
node~#configure
node~(cfg)#context ip ROUTER
node~(ctx-ip)[router]#interface LAN
node~(if-ip)[router.LAN]#no ipaddress 192.168.200.10/24
node~(if-ip)[router.LAN]#ipaddress <new address>/<new mask>
Change the default username
The default username will be removed once a new one is created.
Follow the command sequence below.
node~>enable
node~#configure
node~(cfg)#superuser <username> password <password>
Save the Configuration
Follow the command sequence below.
node~>enable
node~#configure
node~(cfg)#copy running-config startup-config
Introduction 26
Page 27

CopperLink CL2300 User Manual 3 • Configuration and Operation
CopperLink LINE Commands
Local and Remote
This will set the Ethernet Extender as Local or Remote. Local is typically used at the network, Remote is typically used at the remote device or remote network. Your CopperLink CL2300 when received in a 2pk is
eady configured one CL2300 as Local and one CL2300 as Remote.
alr
node(cfg) (prt-line) [0/0]#mode {local|remote}
Annex Type
Please consult support before changing this setting.
node~(pf)[<name>]# annex-type { b-g | a-f }
Line Rate Configuration
This will increase the line rate of the CL2300. Your CopperLink CL2300 is defaulted to automatically select
the optimal rate based on the distance (adaptiv
node(prt-line)[0/0]# payload-rate {adaptive [max <192..15296>] | <192..15296>}
Modulation Scheme
Note higher TC-PAM rates will increase maximum payload rates available but will decrease distance. Your
CopperLink CL2300 is defaulted to automatically select the optimal setting. P
reach chart to determine your optimal setting if you choose to hard set this value. Higher TC-PAM rates are
ideal for shorter cable runs offering max symmetrical (upstream/downstream) speeds of 11.4 Mbps
(TCPAM64) and 15.3 Mbps (TCPAM128) per pair.
node(prt-line)[0/0]# tcpam {auto(16/32) | auto(64/128) | 16 | 32 | 64 | 128}
e).
lease consult manual for rate
CopperLink Ports
The configurations below are used to configure various aspects of the CopperLink port(s).
node~(cfg)# port line 0 0
Signal to Noise Ratio
Configures the acceptable noise margin for adaptive rate. SNR is the relative strength of the Copperlink signal
oise ratio. 6dB is generally the lowest dB recommended in order for the modem to be able to sync. Gener-
to N
ally speaking, as overall bandwidth increases, your signal to noise ratio decreases. The higher the number the
. Your CL2300 is defaulted at 6 giving you the highest likelihood to connect.
better
node(prt-line)[0/0]# snr-margin <-10..22>
Below 6dB bad
6dB-10dB fair
11dB-20dB good
Description
This is the description of the port/line (CopperLink connection). (Ex: "This line goes to building 4") When
entering a description with spaces in the text, the description must be in quotations.
node~(prt-line)[0/0]# description <description>
CopperLink LINE Commands 27
Page 28

CopperLink CL2300 User Manual 3 • Configuration and Operation
Use Profile
Configures the acceptable noise margin for adaptive rate. SNR is the relative strength of the CopperLink signal
to Noise ratio. 6dB is generally the lowest dB recommended in order for the modem to be able to synch.
node~(prt-line)[0/0]# use profile <name>
Service Mode
Configures the number of pairs (wires) you want to use. The CL2300 will default to the maximum number of
wires available on your version of the CopperLink. CL2301 (2-wire); CL2302 (4-wire); CL2304 (8-wire).
node~(prt-line)[0/0]# service-mode { 2-wire | 4-wire | 6-wire | 8-wire }
Shutdown
Disables or Enables CopperLink port(s).
node~(prt-line)[0/0]# [no] shutdown
Exit
Goes back to parent mode.
node~(prt-line)[0/0]# exit
Show
Displays all the configured options of the CL2300 CopperLink port(s)
node(cfg)# show prt-line 0
CopperLink LINE Commands 28
Page 29
Chapter 4 CL2300 Bridging Contexts
Chapter contents
Configuration Task List.........................................................................................................................................30
Optional .........................................................................................................................................................30
Context Switch: HW Bridge..................................................................................................................................30
Switch Mode Groups .....................................................................................................................................30
Switch Mode VLANS .....................................................................................................................................30
Port Configuration ..........................................................................................................................................31
Bindings ..........................................................................................................................................................32
Context Bridge: SW Bridge Introduction ..............................................................................................................32
Bridge Groups ................................................................................................................................................33
CopperLink Line: Overview ..................................................................................................................................34
CopperLink Line Configuration Parameters ...................................................................................................34
Mandatory Configuration List (local sets payload rate) ...................................................................................34
29
Page 30
CopperLink CL2300 User Manual 4 • CL2300 Bridging Contexts
Configuration Task List
To properly configure the CL2300, perform the tasks described in the following sections:
• Configur
• Configur
• Configur
• Configur
• Configur
e Ports: All CopperLink and Ethernet Ports must be configured (see page 34)
e Context Switch: Is it a VLAN application or unmanaged switch application? (see page 30)
e Context Bridge: All traffic must run through the SW bridge (see page 32)
e Bridge Groups: Context Bridge must have at least one Bridge Group (see page 33)
e Bindings: Make sure ports, interfaces and contexts are bound (see page 32)
Optional
• Configur
• Configur
e Context IP (see Chapter 5, "IP Context Overview" on page 35)
e IP Interface for Management Only (see Chapter 5, "IP Context Overview" on page 35)
Context Switch: HW Bridge
Context Switch is the hardware MAC switching (conceptual entity) support for the Embedded Trinity Device.
This functionality allows the unit to function as a managed or unmanaged layer 2 VLAN switch. Managing
your traffic flow with Context Switch commands will significantly enhance the performance especially when
handling the tagging/untagging of VLAN traffic. The switch is set by default as layer two unmanaged switch
with no VLAN support for passing transparent traffic.
Description
Switch Mode Groups Allows you to put Ethernet ports into isolation groups at the HW layer
Switch Mode VLANS Allows you to put the Ethernet ports into 802.1q VLAN trunk mode
Switch Mode Groups
By default the Switch mode is set for all Ethernet Ports to be in same isolation group on in the same switch.
This means that all of the E
thernet Ports are one switch and all traffic flow on all ports will follow the same
path. Switch mode groups also allow you to divide the switch into more than one switch device and this can be
used for traffic isolation. This is the best way to setup your device if you are not using VLAN traffic.
Switch Mode VLANS
If your network design includes the use of VLAN traffic it’s best to the put the switch into VLAN mode. This
mode allo
ws you to decide if you want the port to be used as an “access port” or “trunk port” and the tagging/
untagging can be performed at the HW layer. Tagging and Untagging of VLANS is an ideal way to isolate your
traffic for purposes of higher level of security, QoS and or network monitoring for management purposes
Configuration Task List 30
Page 31

CopperLink CL2300 User Manual 4 • CL2300 Bridging Contexts
Figure 10. Switch mode VLANS
Port Configuration
Description
Configure Port
Arp Enable ARP
Interface Enter ‘interface’ configuration mode
• Permit untagged- permit all traffic
• Permit untagged encapsulate- permit all untagged traffic and tag with
VLAN ID
• Permit VLAN- Allow traffic tagged with VLAN ID
• Deny VLAN- Deny traffic tagged with VLAN ID
• Permit ALL- Permit all untagged traffic
Multicast Enable Multicast
VLAN Not supported (bind VLAN’s directly to the interface or port)
Shutdown
Session Create PPPoE session
No Disable features or reset to default behavior
Context Switch: HW Bridge 31
Page 32

CopperLink CL2300 User Manual 4 • CL2300 Bridging Contexts
Bindings
Bindings form the association between circuits or ports and the interfaces configured on a context. No user
data can flo
w on a circuit or Ethernet port until some higher-layer service is configured and associated with it.
Bindings are configured statically in the port configuration.
Context Bridge: SW Bridge Introduction
Context Bridge is the software MAC switching (conceptual entity) side of the Trinity Embedded Device. This
allows the configuration of the unit to be highly flexible and perform all the switching level functions that any
normal switch can do but at a software or CPU level. This can be used like the context switch-group entity to
perform the same functions such as isolate, manage or dictate the traffic flow of all IP traffic at the MAC layer.
If you are unable or need a more complex configuration than the Context switch-group can perform then you
may need the flexibility of using software enabled bridge functions to get the job done.
When setting up the device you must decide the best and most efficient way to pass traffic from the Ethernet
orts to the WAN (EFM) ports. In routed modes the traffic path will always be routed at layer 3 from one
P
interface to the other before it passes correctly. In the bridging mode all traffic will pass transparently though
either a context switch or context bridge. Context Bridge can be used in combination with Context IP as you
can see the in the example below. Bridging traffic is more efficient and easier to maintain when you need to
pass the traffic between two Trinity Embedded Devices that are on the same network, such as the diagram
below
.
Figure 11. Bridge Network
Context Bridge: SW Bridge Introduction 32
Page 33

CopperLink CL2300 User Manual 4 • CL2300 Bridging Contexts
Context IP is your routing core. You
may configure as many interfaces as
needed. Remember to bind to the
correct interface
You are not limited to how many
bridge-groups you can create inside
of the Context bridge.
Bridge Groups
Bridge Group Enters or creates a bridge-group
No Disable features or reset to default behaivior
Aging MAC table aging value in seconds
Arp Arp Enable
Filter Filter Command for MAC
Mulitcast Enable Multicast
Session Create PPPoE session
Settap configure a bridge tap
Shutdown Shutdown the selected interface
STP Configure spanning tree
VLAN Enter a VLAN Configuration
If you have VLAN’s on your network,
remember to configure
“switch mode vlans”
Figure 12. Breaking down Trinity IOS concepts
Description
• Permit{src | any}{dest | any}[VLAN ID]
Context Bridge: SW Bridge Introduction 33
Page 34

CopperLink CL2300 User Manual 4 • CL2300 Bridging Contexts
CopperLink Line: Overview
Configuration details for creating a DSL or Line Connection. Connections can only be made between two
modems. These modems must have manual configurations to create a link.
Description
Annex-type Must match on both modems
Mode Must be opposites
• Example: Local <–> Remote
Payload Rate Local Payload Configuration
Service-mode Local Service-mode configuration
CopperLink Line Configuration Parameters
Description
Annex-type Configure annex (must match peer)
Bind Interface, bridge-group
Description text information
Mode local and remote
Payoad-rate “adaptive” “max”
Service-mode 4 wire (2–4–8 wire support)
Snr-margin Max for line connection quality
Tcpam 16/32 64/128
VLAN Configures VLAN interface
Mandatory Configuration List (local sets payload rate)
Description
Mode Local or Remote
Annex type (must match other side)
Bind Must bind CopperLink port to bridge-group or interface
Service-mode Must match
Shutdown
CopperLink Line: Overview 34
Page 35

Chapter 5 IP Context Overview
Chapter contents
Introduction..........................................................................................................................................................36
Packet Processing in the IP Context ......................................................................................................................37
Classifier .........................................................................................................................................................39
Network Address Port Translation (NAPT) ....................................................................................................39
Routing-table Selection ...................................................................................................................................39
Access Control Lists (ACL) .............................................................................................................................39
Routing ...........................................................................................................................................................39
Packet Processing To/From Local Applications ...............................................................................................40
IP Context Overview Configuration Task List.......................................................................................................40
Planning Your IP Configuration............................................................................................................................40
IP Interface Related Information .....................................................................................................................40
QoS Related Information ..........................................................................................................................41
Configuring Physical Ports ..............................................................................................................................41
Creating and Configuring IP Interfaces ...........................................................................................................41
Configuring Packet Classification ...................................................................................................................41
Configuring Network Address Port Translation (NAPT) ................................................................................42
Configuring Static IP Routing ........................................................................................................................42
Configuring Access Control Lists (ACL) .........................................................................................................42
Configuring Quality of Service (QoS) .............................................................................................................42
35
Page 36

CopperLink CL2300 User Manual 5 • IP Context Overview
Introduction
This chapter outlines the Trinity Internet protocol (IP) context and its related components. You will get the fundamental understanding on how to set up your CL2300 to make use of IP related services.
The following sections describe the configuration steps necessary to put together certain IP services and the references to the related chapters that explain the issue in more detail.
The IP context in Trinity is a high level, conceptual entity that is responsible for all IP-related protocols and
ser
vices for data and voice. The IP context performs much of the same functions as a standalone IP router, and
since every context is defined by a name, the IP context is named ROUTER by default.
In figure 13 below, the IP context with all its related elements is contained within the area on the left, which
has a gray fill (find a short description of those elements below). The right side displays the related CS context,
which communicates with the IP context via gate
the subject of this chapter, they are illustrated in figure 13 with gray lines instead of black ones.
ways. Since the CS context and its related components are not
Figure 13. IP context and related elements
The IP context contains the following entities:
• R
outing tables
• Logical IP inter
• Links to ser
Introduction 36
face
vice profiles
Page 37

CopperLink CL2300 User Manual 5 • IP Context Overview
Since the IP context represents a virtual IP4 and IPv6 dual-stack router, it contains up to 251 routing tables for
static routes (not depicted in
figure 13 on page 36). The routing tables decide whether received packets are
delivered to a local application (example, CLI, web server, SIP gateway) or routed via another IP interface to a
remote network host.
The IP context may contain an arbitrary number of logical interfaces. Unlike other operating systems where a network interface is identical to a physical port, we distinguish physical ports from logical interfaces. A logical interface contains all IP-related configuration parameters that are common to all ports, such as the IP address, for
example. As depicted in
figure 13 on page 36, a physical port or circuit is bound bottom-up to one logical IP
interface. Hence, each IP interface reflects the IP-protocol of a physical port or circuit.
Applications such as SIP gateways may also be bound to an IP interface. A top-down binding defines over
which IP interface (and hence over which physical port or circuit) an application communicates.
Packet Processing in the IP Context
Several IP service profiles can be assigned to the individual logical interfaces in the context (see figure 13).
These profiles control the flow of packets through the router. They classify packet streams, control which packets may enter/leave the device via Access Control Lists (ACL), perform Network and Port Address Translation
(NAPT) and deal with Quality-of-Service (QoS) information in packet headers.
Note that there is a different packet-processing chain for each interface depending on its configuration, i.e.,
each interface maintains its own configuration of how the packets are classified, a different ACL, etc. However,
to make having the same configuration on multiple interfaces easier, we moved the configuration parameters to
profiles. The use command attaches a profile to an interface, such that the same profile can be used by different
interfaces.
Packet Processing in the IP Context 37
Page 38

CopperLink CL2300 User Manual 5 • IP Context Overview
Figure 14 shows the journey of a packet through the IP context and the order in which the attached profiles
process the packet.
Figure 14. Processing order of IP services attached to an IP interface
Packet Processing in the IP Context 38
Page 39

CopperLink CL2300 User Manual 5 • IP Context Overview
Classifier
The classifier is the first profile that inspects an incoming packet. The classifier assigns a traffic class to each
packet. You can think of the traffic-class as if every packet in the router has a tag attached to it, on which the
classification can be noted. The traffic-class tags exist only inside the router, but layer 2 priority bits (802.1pq
class-of-service) and IP header type-of-service bits (TOS field) can be used to mark a specific packet type for
the other network devices. By default the traffic-class tag is default.
A powerful packet-matching filter in the classifier profile lets you inspect any combination of IP, UDP, TCP or
ICMP header fields and assign a traffic-class to the matching packet flow. For example, you may configure to
tag all UDP packets to a destination port between 5000 and 8000, and shorter than 500 bytes with the trafficclass VOICE. The traffic-class tag can later be used in other IP service profiles, e.g., to filter packets in the ACL
or to do policy routing by selecting a routing-table based on the traffic-class.
Network Address Port Translation (NAPT)
After classification is done, the packet is handed over to the NAPT profile-if one is used on the current interface. Network Address Port Translation (NAPT), which is an extension to NAT, uses TCP/UDP ports in addition to network addresses (IP addresses) to map multiple private network addresses to a single outside address.
Thus the NAPT profile may change the destination address and port of an incoming packet.
Routing-table Selection
You may configure policy routing by selecting a different routing table based on some header fields of the
incoming packet. You may also use the traffic-class (tagged before in the Classifier) to make a routing-table
decision. For example, you may direct all packets tagged with the VOICE traffic-class to a separate routing
table while processing the other traffic with the default routing table.
Note The routing-table selection for an incoming packet is performed after
NAPT, i.e., you will see the translated (private) addresses and ports
Access Control Lists (ACL)
An access control list is a sequential collection of permit and deny conditions that apply to packets on a certain
interface. You can use the same packet-matching mechanism as in the classifier and the routing-table selection
to decide whether the specified packet flow is permitted to enter the router or is rejected.
The ACL filter is passed after the routing decision has been made. This allows you to apply an ACL to an
input-output interface pair. For example, you may use a specific profile for all packets entering the router via
the LAN interface and leaving it over the DMZ interface.
Routing
Once a packet traversed all ingress packet filters (controlled by the attached profiles), the router decides
whether the packet is destined to an application of the gateway itself or shall be routed to a remote host. For
this purpose it performs a best-prefix match on the destination IP address in the routing-table, which was pre
viously selected. If no routing-table has been selected explicitly, the DEFAULT table is consulted.
If the packet is to be sent to a remote host, it traverses the egress filters of the IP interface (depicted in
figure 14), an egress ACL, another possibility to classify the packet, NAPT translations and finally, a service-
policy profile, which can be used to map an internal traffic-class to IP TOS field values.
-
Packet Processing in the IP Context 39
Page 40

CopperLink CL2300 User Manual 5 • IP Context Overview
Packet Processing To/From Local Applications
If the packet is not sent to a remote host, and is destined for a local application (e.g. CLI, the web server, or SIP
signaling packets), another set of packet-processing filters is traversed after the routing decision has been made.
In particular, another ACL profile dedicated only for locally-terminated flows is passed. This allows you to cre
ate specific ACL profiles to protect the local device while having different ACL profiles for routed traffic.
After passing the ACL, voice data packets (RTP/SRTP) are diverted to the voice processing engine whereas the
remaining traffic reaches one of the running service applications.
Packets that have been generated by applications on the device also traverse a set of packet-processing filters-a
classifier to tag packets with a traffic-class, routing-table selection, and another outbound ACL for locally-gen
erated traffic.
As shown at the top of figure 14 on page 38, the local packet-processing filters are not attached to a specific
logical IP interface. All packets to/from a local application rather pass the same set of filters. There is a special
local mode within the IP context in which classifier and ACL profiles for local applications can be attached.
The local mode also hosts routing-selection commands for locally-generated traffic (see chapter
ing” on page 89 for more information).
12, “IP Rout-
IP Context Overview Configuration Task List
The following sections describe the basic tasks involved in IP context configuration. Many parameters have
acceptable default values, which in most cases do not need to be explicitly configured. Hence not all of the con
figuration tasks below are required. Depending on your application scenario, some tasks are mandatory while
others are optional. The following tasks use a bottom-up approach, starting from the ports, followed by the
interfaces and up to the services running on the device. Read through the tasks in order to learn a general
understanding of the whole network before moving onto more detailed instructions.
-
-
-
• Planning your IP configuration (see page 40)
• Configuring physical ports (see page 41)
• Creating and configuring IP interfaces (see page 41)
• Configuring packet classification (see page 41)
• Configuring Network Address Port Translation (NAPT) (see page 42)
• Configuring static IP routing (see page 42)
• Configuring Access Control Lists (ACL) (see page 42)
• Configuring quality of service (see page 42)
Planning Your IP Configuration
The following subsections provide network connection considerations for Ethernet ports. Patton recommends
that you draw a network overview diagram displaying all neighboring IP devices. Do not begin configuring the
IP context until you have completed the planning of your IP environment.
IP Interface Related Information
Setting up the basic IP connectivity for your device requires at least the following information:
• IP addresses used for Ethernet LAN and WAN ports
IP Context Overview Configuration Task List 40
Page 41

CopperLink CL2300 User Manual 5 • IP Context Overview
• IP Subnet mask used for Ethernet LAN and WAN ports
• Length for Ethernet cables
• IP addresses of the central SIP registrar
• IP addresses of the central PSTN gateway for SIP-based calls
QoS Related Information
Check with your access service provider if there are any QoS-related requirements, which you need to know
prior to configuring Trinity QoS management. Check the following with your access service provider:
• What is the dedicated bandwidth, which you have agreed with your access service provider?
• How does your provider perform packet classification, e.g. which ToS bits have to be used to define the sup-
ported classes of service?
Configuring Physical Ports
Port configuration includes parameters for the physical and data link layer, such as framing and encapsulation
formats or media access control. Before any higher-layer user data can flow through a physical port, you must
associate that port with an interface within the IP context. This association is referred to as a binding. For
information and examples on how to configure ports, refer to the respective port type’s chapter.
Creating and Configuring IP Interfaces
The number and names of IP interfaces depend upon your application scenario. An interface is a logical construct that encapsulates network-layer protocol and service information, such as IP addressing. Therefore,
interfaces are configured as part of the IP context (the virtual router) and represent logical entities that are only
usable if a physical port (Ethernet) or circuit (VLAN) is bound to them.
An interface name can be any arbitrary string, but for ease of identification use self-explanatory upper-case
names that describe the use of the interface, e.g. LAN, WAN.
Several IP-related configuration parameters are necessary to define the behavior of such an interface. The most
obvious parameters are one or multiple IP addresses and the IP net masks that belong to them. Several profile
types can also be attached to an IP interface to define how packets arriving on the interface or leaving over it are
processed.
Configuring Packet Classification
A classifier profile can be attached to each IP interface. It contains rules to match packet flows based on the
header fields of the packets and tag them with an internal traffic-class. This traffic-class is usually used in con
junction with other services. For example, an ACL may have filter rules that drop all packets tagged with a certain traffic-class, or policy routing may be configured to select a dedicated routing-table for a packet flow of a
given traffic-class. Trinity tests packets against the classifier rules one by one. The first match determines the
traffic-class. Because Trinity stops testing rules after the first match, the order of the classifier rules is critical. If
no conditions match or if there is no classifier profile attached to an interface, the software tags receive packets
with the DEFAULT traffic-class, whereas all packets generated by local applications are tagged with the
LOCAL-DEFAULT traffic-class, except generated RTP/SRTP packets, which are tagged as LOCAL-VOICE.
-
Classifier profiles can be attached to several entities in Trinity-on any local IP interface and in the local mode of
the IP context. In both places classifier profiles can be attached separately for inbound and outbound packets.
Planning Your IP Configuration 41
Page 42

CopperLink CL2300 User Manual 5 • IP Context Overview
Configuring Network Address Port Translation (NAPT)
You can configure NAPT by creating a profile that is afterwards used on an explicit IP interface. In Trinity terminology, an IP interface uses a NAPT profile, as shown in figure 13 on page 36.
Configuring Static IP Routing
Trinity allows you to define static routing entries, which are destination-address-to-egress-interface mappings
established by the network administrator prior to the beginning of routing. These mappings do not change
unless the network administrator alerts them. Algorithms that use static routes are simple to design, and work
well in environments in which network traffic is relatively predictable and where network design is relatively
simple.
Routing entries are grouped in routing-tables. A set of route commands in the IP interface can be used to select
the routing-table for inbound traffic for different packet-header fields. The route command in the local mode,
within the IP context configures the routing-table to consult for locally-generated traffic. Trinity tests packets
against the routing-table-selection rules one by one. The first match determines the routing-table to use.
Because Trinity stops testing rules after the first match, the order of the routing-selection rules is critical. If no
conditions match or if there is no route command in the interface, the software uses the DEFAULT routing
table.
Configuring Access Control Lists (ACL)
Packet filtering helps to control packet movement through the network. Such control can help to limit network
traffic and restrict network use by certain users or devices. An access control list is a sequential collection of per
mit and deny conditions that apply to packets on a certain interface. Access control lists can be configured for
all routed network protocols (IP, ICMP, TCP, UDP, and SCTP) to filter the packets of those protocols as the
packets pass through a device. Trinity tests packets against the conditions in an access list one by one. The first
match determines whether Trinity accepts or rejects the packet. Because Trinity stops testing conditions after
the first match, the order of the conditions is critical. If no conditions match, the software rejects the address.
-
Configuring Quality of Service (QoS)
A service-policy profile can be attached to an IP interface to manage QoS for network traffic, as shown in
Figure 13 on page 36. QoS refers to the ability of a network to provide improved service to selected network
traffic over various underlying technologies including Ethernet and 802.x type networks, as well as IP-routed
networks. In particular, QoS features provide improved and more predictable network service by providing the
following features:
• Supporting dedicated bandwidth
• Improving loss characteristics
• Avoiding and managing network congestion
• Shaping network traffic
• Setting traffic priorities across the network
Planning Your IP Configuration 42
Page 43

Chapter 6 Command Line Interface (CLI)
Chapter contents
Introduction..........................................................................................................................................................44
Command modes ..................................................................................................................................................44
CLI prompt ....................................................................................................................................................44
Navigating the CLI .........................................................................................................................................45
Initial mode ..............................................................................................................................................45
System changes ..........................................................................................................................................45
Configuration ...........................................................................................................................................45
Changing Modes .......................................................................................................................................45
Command editing .................................................................................................................................................45
Command help ...............................................................................................................................................45
The No Form .................................................................................................................................................45
Command completion ....................................................................................................................................45
Command history ...........................................................................................................................................46
Command Editing Shortcuts ..........................................................................................................................46
43
Page 44

CopperLink CL2300 User Manual 6 • Command Line Interface (CLI)
Introduction
The primary user interface to the CL2300 is the command line interface (CLI). You can access the CLI via the
Patton device console port or through a Telnet or SSH session. The CLI lets you configure the complete
CL2300 functionality. You can enter CLI commands online or as a configuration script in the form of a text
file. The CLI also includes monitoring and debugging commands. CLI commands are simple strings of key
-
words and user-specified arguments.
This chapter gives an overview of the CLI and the basic features that allow you to navigate the CLI and edit
commands effectively. The following topics are covered:
• Command Modes
• Command Editing (see page 45)
Command modes
The CLI is composed of modes. There are three mode groups: the operator, the administrator mode and the con-
figure mode. The configuration mode group contains all of the remaining modes. A command mode is an envi-
ronment within which a group of related commands is valid. All commands are mode-specific, and certain
commands are valid in more than one mode. A command mode provides command line completion and con
text help within the mode. The command modes are organized hierarchically.
-
CLI prompt
For interactive (online) sessions, the system prompt is displayed as:
devicename>
In the operator exec mode, the system prompt is displayed as:
devicename#
In the administrator exec mode and in the different configuration modes, the system prompt is displayed as:
devicename(mode)device#
Where:
• devicename is the currently configured name of the Patton device, the IP address or the hardware type of the
device that is being configured
• mode is a string indicating the current configuration mode, if applicable.
• name is the name of the instance of the current configuration mode
Example: the prompt in radius-client mode, assuming the devicename device and the instance deepblue is:
device(radius)[deepblue]#
Introduction 44
Page 45

CopperLink CL2300 User Manual 6 • Command Line Interface (CLI)
Navigating the CLI
Initial mode
When you initiate a session, you can log in with operator or administrator privileges. Whichever login you use,
the CLI is always set to operator exec (non-privileged exec) mode by default upon startup. This mode allows
you to examine the state of the system using a subset of the available CLI commands.
System changes
In order to make changes to the system, the administrator exec (privileged exec) mode must be entered. The
enable user interface command is used for this purpose (the enable command is only accessible if you are
logged in as an administrator). Once in administrator exec mode, all of the system commands are available to
you.
Configuration
To make configuration changes, the configuration mode must be entered by using the configure command in
the administrator exec mode.
Changing Modes
The exit command moves the user up one level in the mode hierarchy (the same command works in any of
configuration modes). For example, when in pvc configuration mode, typing exit will take you to framerelay
configuration mode.
The exit command terminates a CLI session when typed from the operator exec mode.
A session can also be terminated by using the logout command within any mode.
Command editing
Command help
To see a list of all CLI commands available within a mode, type a question mark <?> or the <tab> key at the
system prompt in the mode of interest. A list of all available commands is displayed. Commands that have
become available in the current mode are displayed at the bottom of the list, separated by a line. Commands
from higher hierarchy levels are listed at the top.
You can also type the question mark or the <tab> key while in the middle of entering a command. Doing so
displays the list of allowed choices for the current keyword in the command. Liberal use of the question mark
functionality is an easy and effective way to explore the command syntax.
The No Form
Almost every command supports the keyword no. Typing the no keyword in front of a command disables the
function or “deletes” a command from the configuration. For example, to enable the DHCP server trace tool,
enter the command debug dhcp-server. To subsequently disable the DHCP server trace, enter the command
no debug dhcp-server.
Command completion
You can use the <tab> key in any mode to carry out command completion. Partially typing a command name
and pressing the <tab> key causes the command to be displayed in full up to the point where a further choice
has to be made. For example, rather than typing configure, typing conf and pressing the <tab> key causes the
Command editing 45
Page 46

CopperLink CL2300 User Manual 6 • Command Line Interface (CLI)
CLI to complete the command at the prompt. If the number of characters is not sufficient to uniquely identify
the command, the CLI will provide a list with all commands starting with the typed characters. For example, if
you enter the string co in the configure mode and press <tab>, the selections configure, copy, and context are
displayed. The CLI may be configured to automatically complete commands without pressing the <tab> key.
This will only happen if a unique completion option exists.
Command Purpose
[no] cli auto-completion Enable or disable CLI automatic command completion.
Command history
Trinity maintains a list of previously entered commands that you can go through by pressing the <up-arr
ow>
and <down-arrow> keys, and then pressing <enter> to enter the command. The show history command displays a list of the commands you can go through by using the arrow keys.
Command Editing Shortcuts
Trinity CLI provides a number of command shortcuts that facilitate editing of the command line. Command
editing shor
tcuts are summarized below. The syntax <Ctrl>-<p> means press the <p> key while holding down
the keyboard’s control key (sometimes labeled Control, Ctl, or Ctrl, depending on the keyboard and operating
system of your computer). <Esc>-<f> is handled differently; press and release the escape key (often labeled Esc
on many keyboards) and then press the <f> key.
Keyboard Description
<Ctrl>-<p> or <up-arrow> Recall previous command in the command history.
<Ctrl>-<n> or <down-arrow> Recall next command in the command history.
<right-arrow> Move cursor forward one character.
<left-arrow> Move cursor backward one character.
<Esc>-<f> Move cursor forward one word.
<Esc>-<b> Move cursor backward one word.
<Ctrl>-<a> Move cursor to beginning of line.
<Ctrl>-<e> Move cursor to end of line.
<Ctrl>-<k> Delete to end of line.
<Ctrl>-<u> Delete to beginning of line.
<Ctrl>-<d> Delete character.
<Ctrl>-<c> Quit editing the current line.
<Ctrl>-<v> Insert a code to indicate to the system that the keystroke immediately
following should be treated as normal text, not a CLI command.
For example, pressing the question mark <?> character in the CLI
prints a list of possible tokens. If you want to use the “?” in a configuration command, e.g. to enter a regular expression, press Ctrl-v immedi-
ately followed by the question mark <?>.
Command editing 46
Page 47

Chapter 7 Accessing the CLI
Chapter contents
Introduction..........................................................................................................................................................48
Accessing the CLI task list .....................................................................................................................................48
Accessing via the console port .........................................................................................................................49
Console port procedure .............................................................................................................................49
Accessing via a secure configuration session over SSH .....................................................................................49
Accessing via a Telnet session ....................................................................................................................50
Telnet Procedure .......................................................................................................................................50
Using an alternate TCP listening port for the Telnet or SSH server ................................................................50
Disabling the Telnet or SSH server .................................................................................................................50
Logging on ......................................................................................................................................................50
Selecting a secure password .............................................................................................................................51
Password encryption .......................................................................................................................................52
Factory preset superuser account ...............................................................................................................52
Configuring operators, administrators, and superusers ....................................................................................52
Creating an operator account ....................................................................................................................52
Creating an administrator account ............................................................................................................53
Creating a superuser account .....................................................................................................................53
Displaying the CLI version .............................................................................................................................54
Displaying account information ......................................................................................................................54
Checking identity and connected users ...........................................................................................................54
Command index numbers ...............................................................................................................................55
Ending a Telnet, SSH or console port session .................................................................................................57
Showing command default values ...................................................................................................................58
47
Page 48

CopperLink CL2300 User Manual 7 • Accessing the CLI
T
Introduction
The CL2300 is designed for remote management and volume deployment. The management and configuration of CL2300 is therefore based on IP network connectivity. Once a CL2300 is connected to, and addressable in, an IP network, you can remotely perform all configuration, management, and maintenance tasks.
This chapter describes the procedures for entering commands via the command line interface (CLI), to obtain
help, to change operator mode, and to terminate a session. You can access the CL2300 as follows:
• D
irectly, via the console port (if available)
• R
emotely, via the IP network (by using a Telnet or SSH application)
The ports available for connection and their labels are shown in the getting started guide that came with your
unit. R
up and down arrow keys, you can find many of your previously entered commands. Another time-saving tool
is command completion. If you type part of a command and then press the <tab> key, the Trinity shell will
present you with either the remaining portion of the command or a list of possible commands. These features
are described in Chapter 6, “Command Line I
disabled if desired.
emember that the CLI supports a command history and command completion. By scrolling with the
nterface (CLI)” on page 43. The telnet and SSH server can be
Although Trinity supports concurrent sessions via SSH or the
console port, we do not recommend working with more than
IMPORTAN
one session to configure the CL2300. However, using one session for configuration and another for debugging is a good idea.
Accessing the CLI task list
The following sections describe the basic tasks involved in accessing the command line interface. Depending
on your application scenario, some tasks are mandatory while others could be optional.
• A
ccessing via the console port (see page 49)
• A
ccessing via a SSH session (see page 50)
• U
sing an alternate TCP listening port for the SSH server (see page 50)
• D
isabling the SSH server (see page 50)
• Logging on (see page 50)
• S
electing a secure password (see page 51)
• Configuring operators and administrators (see page 52)
• D
isplaying the CLI version (see page 54)
• S
witching to another log-in account (see page 54)
• Checking identity and connected users (see page 54)
• E
nding a SSH or console port session (see page 57)
Introduction 48
Page 49

CopperLink CL2300 User Manual 7 • Accessing the CLI
Accessing via the console port
If a console port is available, the host computer can be connected directly to it with a serial cable (see
Figure 15). The host must use a terminal emulation application that supports serial interface communication.
Serial interface
Host
Figure 15. Setup for initial configuration via the console port
Note You do not need to configure IP settings if you access the Patton device via
Console
Node
Node
the console port.
Console port procedure
Before using the CLI to enter configuration commands, do the following:
et up the hardware as described in the getting started guide.
1. S
2. Configur
3. Connect the serial terminal to y
e your serial terminal as described in the getting started guide.
our Patton device. Use a serial cable according to the description in the get-
ting started guide included with your Patton device.
4. P
ower on your device. A series of boot messages are displayed on the terminal screen. At the end of the
boot sequence, press the <return> key and the login screen will be displayed. Proceed with logging in.
Accessing via a secure configuration session over SSH
SSH is the most commonly used and recommended method for connecting to a Patton device. A partial implementation of secure shell according RFC 4251, RFC 4252, RFC 4253 and RFC 4254 is provided. It is possible
to open a secur
e configuration session over SSH to a Patton device.
Note The copy tftp and http functions are still insecure!
The SSH Transport Layer supports the following Algorithms: “ssh-rsa” or ‘ssh-dsa” public key for signing, “diffie-hellmann-group1-sha1” and “diffie-hellmann-group14-sha1” for key exchange, “3des-cbc”, “aes256-cbc”
aes128-cbc” for encryption, “hmac-sha1” and “hmac-md5” for data integrity. For user authentication,
and “
only the method “password” is supported. On the Connection Layer, only the request for an interactive command shell is supported. After the first startup of Trinity, the RSA or DSA server host key is going to be calculated. The RSA or DSA server host key is calculated only once and always remains the same.
Mode: Configur
Step Command Purpose
1 device(cfg)#terminal ssh use auth <AAA profile name> Set the AAA profile which is going to be
Accessing the CLI task list 49
e
used for user authentication. The AAA
profile “default” is used when another
profile is not specified.
Page 50

CopperLink CL2300 User Manual 7 • Accessing the CLI
Accessing via a Telnet session
It is way faster than console access. The Telnet host accesses the CL2300 via its network interface.
Note If the IP configuration of the Ethernet port (LAN port) is not known or is
incorrectly configured, you will have to use the console interface.
Telnet Procedure
Before you begin to use the CLI to input configuration commands, do the following:
et up the Patton device as described in the getting started guide included with your device.
1. S
2. Connect the host (PC) or hub to the P
3. P
ower on your device and wait until the Run LED lights.
4. O
pen a Telnet session to the IP address shown in the getting started guide.
5. P
roceed with logging in.
atton device as described in the getting started guide.
Using an alternate TCP listening port for the Telnet or SSH server
The following command defines an alternate listening port for the telnet or SSH server.
Mode: Configur
Step Command Purpose
1 device(cfg)# terminal [telnet | ssh] port <port> Uses TCP port <port> for accepting telnet or
e
SSH connections
Disabling the Telnet or SSH server
The telnet or SSH server can be disabled using the following command.
Mode: Configur
Step Command Purpose
1 device(cfg)# no terminal [telnet | ssh] Disables the telnet or SSH server
e
Logging on
Accessing the CL2300 via the local console port or via a Telnet session opens a login screen. The following
description of the login pr
ocess is based on a Telnet session scenario but is identical to that used when accessing
via the local console port.
The opening Telnet screen you see resembles that shown below. The window header bar shows the IP address
of the CL2300.
A factory preset superuser account with name admin and an empty passwor
d is available when you first access
the unit. For that reason, use the name admin after the login prompt and simply press the <enter> key after the
password prompt.
Accessing the CLI task list 50
Page 51

CopperLink CL2300 User Manual 7 • Accessing the CLI
T
$ telnet 172.16.54.79
Trying 172.16.54.79…
Connected to 172.16.54.79.
Escape character is '^]'.
Patton Electronics Company CL2300
Release: 3.1.0 2013/01/20
Trinity login: admin
Password:
Trinity >
Upon logging in you are in operator execution mode, indicated by the “>” as command line prompt. Now you
can enter system commands.
Note Details on the screen, such as the IP address in the system prompt and win-
dow header bar, may be different on your unit.
You are responsible for creating a new administrator account to
maintain system security. Patton Electronics accepts no respon-
IMPORTAN
sibility for losses or damage caused by loss or misuse of passwords. Please read the following sections to secure your
network equipment properly.
Selecting a secure password
It is not uncommon for someone to try to break into (often referred to as hacking) a network device. The network administrator should do everything possible to make the network secure. Carefully read the questions
w and see if any applies to you:
belo
• D
o your passwords consist of a pet’s name, birthdays or names of friends or family members, your license plate
number, social security number, favorite number, color, flower, animal, and so on?
• D
o you use the same password repeatedly? (Example: Your ATM PIN, cell phone voice mail, house alarm set-
ting code, etc.)
• Could y
• I
s your password less than six characters long?
our password or a portion thereof be found in the dictionary?
To prevent unauthorized access, you should select passwords that are not dictionary words or any of the abovementioned examples. E
very password should be at least 6 characters long and include at least one capital letter,
one number, and one lowercase letter.
A good example of a password is: 3Bmshtr
You are probably asking yourself, “How am I going to remember that?” It’s easy, the password above is an acronym taken from: “three blind mice, see how they run.” Making a good password is that easy—but please, don’t
use the abo
ve example password for your CL2300!
Accessing the CLI task list 51
Page 52

CopperLink CL2300 User Manual 7 • Accessing the CLI
Password encryption
Unencrypted passwords can be stolen by hackers using protocol analyzers to scan packets or by examining the
configuration file—to pr
otect against that type of theft, Trinity encrypts passwords by default. Encryption pre-
vents the password from being readable in the configuration file.
• Plain text
• E
ncrypted text (for example, the password mypassword always appears in encrypted form as HUAvCYeILW-
Zz3hQvS0IEpQ== encrypted when doing a sho
w command)
The command sho
w running-config always displays the passwords in encrypted format. To encrypt a pass-
word, enter the password in plain format and retrieve the encrypted format from the running-config or store it
permanently into the star
tup-config (with the command copy running-config startup-config).
Factory preset superuser account
Trinity contains a factory preset superuser account with the name admin (no passwor
ds). When a new supe-
ruser account has been defined in the configuration, the preset admin account will delete after reboot. You can
eate more than one superuser account, but there has to be at least one superuser account defined. If, for some
cr
reason, the last superuser account is deleted, the factory preset administration account with the name admin
and an empty password is automatically recreated.
Configuring operators, administrators, and superusers
Creating an operator account
Operators do not have the privileges to run the enable command and ther
efore cannot modify the system con-
figuration. Operators can view partial system information.
Creating a new operator account is described in the following procedure:
Mode: O
Step Command Purpose
1 device>enable Enters administration execution mode
2 device#configure Enters configuration mode
3 device(cfg)# operator name password password Creates a new operator account name and
4 copy running-config startup-config Saves the change made to the running con-
perator execution
password password
figuration of the Patton device, so that it will
be used following a reload
Example: Create an operator account
The following example shows how to add a new operator account with a login name suppor
t and a matching
password of s4DF&qw. The changed configuration is then saved.
Accessing the CLI task list 52
Page 53

CopperLink CL2300 User Manual 7 • Accessing the CLI
device>enable
device#configure
device(cfg)#operator support password s4DF&qw
device(cfg)#copy running-config startup-config
Creating an administrator account
Administrators can run the enable command and access additional information within the
Trinity configuration modes. Therefore administrators can modify the system configuration, as well as view all relevant system
information.
Creating a new administrator account is described in the following procedure:
Mode: O
Step Command Purpose
1 device>enable Enters administration execution mode
2 device#configure Enters configuration mode
3 device(cfg)# administrator name password password Creates a new administrator account
4 device(cfg)#copy running-config startup-config Permanently stores the new administra-
perator execution
name and password password
tor account parameters.
Example: Create an administrator account
The following example shows how to add a new administrator account with a login name super and a matching
passwor
d Gh3*Ke4h.
device>enable
device#configure
device(cfg)#administrator super password Gh3*Ke4h
device(cfg)#copy running-config startup-config
Creating a superuser account
Superusers can run the enable command and access additional information within the
Trinity configuration
modes. Therefore, superusers can modify the system configuration, as well as view all relevant system information. Superusers can also create new users (whereas administrators do not have that functionality).
Creating a new superuser account is described in the following procedure:
Mode: O
Step Command Purpose
1 device>enable Enters administration execution mode
2 device#configure Enters configuration mode
3 device(cfg)# superuser name password password Creates a new superuser account name
4 device(cfg)#copy running-config startup-config Permanently stores the new superuser
perator execution
and password password
account parameters.
Example: Create a superuser account
Accessing the CLI task list 53
Page 54

CopperLink CL2300 User Manual 7 • Accessing the CLI
The following example shows how to add a new superuser account with a login name super and a matching
password Gh3*Ke4h.
device>enable
device#configure
device(cfg)#superuser super password Gh3*Ke4h
device(cfg)#copy running-config startup-config
Displaying the CLI version
This procedure displays the version of the currently running CLI.
Mode: O
Step Command Purpose
1 device>show version cli Displays the CLI version
perator execution
Example: Displaying the CLI version
The following example shows how to display the version of the current running CLI on your device, if you
star
t from the operator execution mode.
device>show version cli
CLI version: 3.00
Displaying account information
You can use the sho
w command to display information about existing administrator and operator accounts.
This command is not available for an operator account.
The following procedure describes how to display account information:
Mode: A
Step Command Purpose
1 device#show accounts Displays the currently-configured administrator and operator
dministrator execution
accounts.
Example: Display account information
The following example shows how to display information about existing administrator and operator accounts.
device#show accounts
# UserName AccessLevel Status
0 super superuser (logged out:0)
1 admin administrator (logged out:0)
2 op operator (logged out:0)
Checking identity and connected users
The who command displays who is logged in or giv
es more detailed information about users. Depending on
the execution mode, the command displays varying information. In administrator execution mode, the command output is more detailed and shows information about the ID, user name and location. In operator execution mode, only the user name being used at the moment is reported, which helps checking the identity.
Accessing the CLI task list 54
Page 55

CopperLink CL2300 User Manual 7 • Accessing the CLI
Mode: Administrator or operator execution
Step Command Purpose
1 Trinity(cfc)#who Shows more detailed information about the users ID, name, state, idle time
and location
or
Trinity>who Shows the user login identity
Example: Checking identity and connected users
The following example shows how to report who is logged in or more detailed information about users,
depending on the ex
ecution mode in which you are working.
Used in administrator execution mode:
Trinity(cfg)#who
# User Name Login Time Location
0 admin 01/01/2000 00:08:59 console
1 admin 01/01/2000 00:11:36 telnet 172.16.54.135:55404
Used in operator execution mode:
Trinity>who
You are operator support
Command index numbers
A command index number (indicated by the boldface 1, 2, and 3 index numbers in the example belo
w) indi-
cates the position of a command in a list of commands (that is, a command with index 1 will appear higher in
the configuration file than one with index 3).
192.168.1.1(pf-voip)[default]#show running-config
...
profile voip default
codec 1 g711ulaw64k rx-length 20 tx-length 20
codec 2 g711alaw64k rx-length 20 tx-length 20
codec 3 g723-6k3 rx-length 30 tx-length 30
dejitter-max-delay 200
...
Commands that make use of index numbers always show the index in the running config. However, the index
can be omitted when entering the command. If you enter such a command with an index, it is inserted into list
at the position defined by the index. If you enter such a command without an index, it is placed at the bottom
of the list. Also, you can change a commands position in a listing (moving it up or down in the list) by changing its index number.
Example 1: M
oving the G.723 codec from position 3 in the list to position 1 at the top of the list.
Listing before changing the G.723 codec index number:
profile voip default
codec 1 g711ulaw64k rx-length 20 tx-length 20
codec 2 g711alaw64k rx-length 20 tx-length 20
Accessing the CLI task list 55
Page 56

CopperLink CL2300 User Manual 7 • Accessing the CLI
codec 3 g723-6k3 rx-length 30 tx-length 30
dejitter-max-delay 200
...
Listing after changing index number:
192.168.1.1(pf-voip)[default]#codec 3 before 1
192.168.1.1(pf-voip)[default]#show running-config
...
profile voip default
codec 1 g723-6k3 rx-length 30 tx-length 30
codec 2 g711ulaw64k rx-length 20 tx-length 20
codec 3 g711alaw64k rx-length 20 tx-length 20
dejitter-max-delay 200
...
Note Succeeding indexes are automatically renumbered.
Example 2: Moving the G.723 codec back position 3
This command moves the G.723 codec from the top to third place. As a result, the other two codecs move up
in the list as their indexes are automatically renumbered to accommodate the new third-place codec.
Accessing the CLI task list 56
Page 57

CopperLink CL2300 User Manual 7 • Accessing the CLI
192.168.1.1(pf-voip)[default]#codec 1 after 3
192.168.1.1(pf-voip)[default]#show running-config
...
profile voip default
codec 1 g711ulaw64k rx-length 20 tx-length 20
codec 2 g711alaw64k rx-length 20 tx-length 20
codec 3 g723-6k3 rx-length 30 tx-length 30
dejitter-max-delay 200
...
Example 3: Inserting a codec at a specific position in the list.
This command assigns the G.729 codec the index number 1 so the codec appears at the top of the list.
192.168.1.1(pf-voip)[default]#codec 1 g729 tx-length 30 rx-length 30 silence-sup-
pression
192.168.1.1(pf-voip)[default]#show running-config
...
profile voip default
codec 1 g729 rx-length 30 tx-length 30 silence-suppression
codec 2 g711ulaw64k rx-length 20 tx-length 20
codec 3 g711alaw64k rx-length 20 tx-length 20
codec 4 g723-6k3 rx-length 30 tx-length 30
dejitter-max-delay 200
...
Ending a Telnet, SSH or console port session
Use the logout command in the operator or administration ex
sion. To confirm the logout command, y
Mode: O
Step Command Purpose
1 device>logout Terminates the session after a confirmation by the user.
perator execution
ou must enter yes on the dialog line as shown in the example below.
ecution mode to end a Telnet or console port ses-
Example: End a Telnet or console port session
The following example shows how to terminate a session from the administrator execution configuration
mode.
device>logout
Press 'yes' to logout, 'no' to cancel:
After confirming the dialog with “yes”, the Telnet session is terminated.
Note Using the command exit in the operator execution mode also terminates a
Telnet or console port session, but without any confirmation dialog.
Accessing the CLI task list 57
Page 58

CopperLink CL2300 User Manual 7 • Accessing the CLI
Showing command default values
If a command is set to its default value, it is not displayed in the running-config in order to make it more readable. There are a few exceptions to this rule. The command cli config defaults makes commands also appear in
unning-config that are set to default values. no cli config defaults turns it off.
the r
Step Command Purpose
1 device>enable Enters administration execution mode
2 device#configure Enters configuration mode
3 device(cfg)# superuser name password password Creates a new superuser account name
and password password
4 device(cfg)# cli config defaults Generate a command even if it reflects
the default setting (Default: Disabled)
Accessing the CLI task list 58
Page 59

Chapter 8 System Image Handling
Chapter contents
Introduction..........................................................................................................................................................60
System image handling task list .............................................................................................................................60
Displaying system image information .............................................................................................................60
Copying system images from a network server to Flash memory .....................................................................61
59
Page 60

CopperLink CL2300 User Manual 8 • System Image Handling
Introduction
System image handling management is a complex and feature rich system allowing a user to perform various
upgrades on the devices. It allows a user to perform full upgrades and partial upgrades. It allows to upgrade system configuration seamlessly. The upgrades tasks are supported both from the CLI and WMI. You can copy
files to flash fr
om TFTP and local flash space. You can also upgrade from HTTP.
System image handling task list
To load and maintain system images, perform the tasks described in the following sections:
• D
isplaying system image information
• Copying system images fr
• Copying system configuration files to flash memor
om a network server to the Flash memory
y
Displaying system image information
This procedure displays information about system images and driver software.
Mode: A
Step Command Purpose
1 # show system info Lists the system software release version, information about optional inter-
dministrator execution
face cards mounted in slots and other information that is the currently running system software. If you have just completed a download of new
system software from the tftp server, you must execute the reload command in order to be running with the new system software. This applies
equally to driver software. In some cases, the device may reboot itself.
Introduction 60
Page 61

CopperLink CL2300 User Manual 8 • System Image Handling
# show system info
Product Description
===============================================
Company Name:Patton Electronics Company
Company Url:http://www.patton.com
Model:CL2300
Model Description: Ethernet Extender
Serial Number:00A0BA09094A
Enterprise Oid :1.3.6.1.4.1.1768
Product Oid:1.3.6.1.4.1.1768.300.3
Version :3.3-sandrianov@poseidon/19
Build Date :2013/07/09
Build Host:sandrianov@poseidon
Build Number:19
Build Type:Branch
Source Revision:57124ec
Host Name:00A0BA09094A
System Description:
System Contact:
System Location:
System Provider:
System Subscriber:
System Supplier:
Banner:Patton Electronics Company CL2300
Branch:3.3-sandrianov@poseidon/19 2013/07/09
Copying system images from a network server to Flash memory
As mentioned previously, the system image file contains the application software that runs Trinity; it is loaded
into the flash memory at the Patton Electronics Co. factory. Since most of the voice and data features of the
CL2300 are defined and implemented in the application software, upgrading to a new release might be neces
sary if you want to have additional voice and data features available. A new system image file must be stored
permanently into the flash memory of your CL2300 to be present when booting the device. Since the system
image file is preloaded at the Patton Electronics Co. factory, you will have to download a new Trinity applica
tion software only if a major software upgrade is necessary or if recommended by Patton Electronics Co. Under
normal circumstances, downloading a system image file should not be needed.
Downloading a new system image file means storing it permanently at a defined location within the Patton
device flash memory. To store the system image file, you must use a special download image bundle file. This
bundle file contains directions for the system that describe how to handle the system image file and where to
store it. The direction for the system upgrade contained in a file called manifest which is a part of the upgrade
image.
-
-
System image handling task list 61
Page 62

CopperLink CL2300 User Manual 8 • System Image Handling
Mode: Administrator access
Step Command Purpose
1 device(cfg)# copy tftp://server-ip-address>/<delivery-
file>.tar flash:
2 device(cfg)# copy tftp://<address>/upgrade-
image.tar flash-cfg:
Downloads the image file from the TFTP
server at address <address> and starts
the s
ystem image download process.
This progress is visualized with a progress bar, printing dots according to the
time elapsed since the start of each
upgrade operation
Does the same as the command above.
But it will also erase the flash partition.
Think of this as a factory erase.
System image handling task list 62
Page 63

Chapter 9 Configuration File Handling
Chapter contents
Introduction..........................................................................................................................................................64
Understanding Configuration Files .................................................................................................................64
Shipping Configuration.........................................................................................................................................66
Configuration File Handling Task List..................................................................................................................66
Copying Configurations Within the Local Memory ........................................................................................67
Replacing the Startup Configuration with a Configuration from Flash Memory .............................................68
Copying Configurations To and From a Remote Storage Location .................................................................69
Replacing the Startup Configuration with a Configuration Downloaded from TFTP Server ..........................69
Displaying Configuration File Information .....................................................................................................70
Modifying the Running Configuration at the CLI ..........................................................................................71
Modifying the Running Configuration Offline ...............................................................................................72
Deleting a Specified Configuration .................................................................................................................73
63
Page 64

CopperLink CL2300 User Manual 9 • Configuration File Handling
Introduction
This chapter describes how to upload and download configuration files to and from a CL2300. A configuration file is a batch file of Trinity commands used in the software modules that perform specific functions of the
CL2300. This chapter also describes some aspects of configuration file management. Refer to chapter
tem Image Handling” on page 59 for more information.
This chapter includes the following sections:
• Shipping configuration (see page 66)
• Configuration file handling task list (see page 66)
All Patton devices are shipped with a configuration file installed in the factory, which is stored in their flash
memory.
A configuration file is like a script file containing Trinity commands that can be loaded into the system. Configuration files may also contain only partial configurations. This allows you to keep a library of command
sequences that you may want to use as required. By default, the system automatically loads the shipping config
uration from the flash memory if no user-specific configuration is defined as the startup configuration.
Changing the current running configuration is possible as follows:
You may change the running configuration interactively. Interactive configuring requires that you access the
CLI by using the enable command to enter administrator execution mode. You must then switch to the con
figuration mode with the command configure. Once in configuration mode, enter the configuration commands that are necessary to configure your CL2300.
8, “Sys-
-
-
• You can also create a new configuration file or modify an existing one offline. You can copy configuration files
from the flash memory to a remote server. Transferring configuration files between the flash memory and a
remote system requires the Trivial File Transfer Protocol (TFTP). The TFTP server must be reachable through
one of the CL2300 network interfaces.
See Chapter 7, "Accessing the CLI" on page 47 for information concerning access to the CLI.
The following sections focus on Trinity memory regions and software components that can be copied within
the memory or uploaded/downloaded between a TFTP server and the memory of the CL2300. Refer to chap
ter 8, “System Image Handling” on page 59 for a brief description of how Trinity uses system memory.
Understanding Configuration Files
Configuration files contain commands that are used to define the functionality of Trinity. During system startup,
the command parser reads the factory or startup configuration file command-by-command, organizes the argu
ments, and dispatches each command to the command shell for execution. If you use the CLI to enter a command during operation, you alter the running configuration accordingly. In other words, you are modifying a live,
in-service system configuration.
Figure 16, shows the characteristics of a configuration file. It is stored on a TFTP server in the file myconfig.cfg
for later download. The command syntax used to enter commands with the CLI and add commands in configuration files is identical. For better comprehension, you can add comments in configuration files. To add a line
with a comment to your configuration file, simply begin the line with the hash (#) character. The command
parser skips everything after the hash character to the end of the line.
-
Introduction 64
Page 65

CopperLink CL2300 User Manual 9 • Configuration File Handling
#----------------------------------------------------------------#
# My Configuration File
#----------------------------------------------------------------#
# SNTP configuration used for time synchronization
cli version 3.00
sntp-client
sntp-client server primary 172.16.1.10 port 123 version 4
sntp-client poll-interval 600
sntp-client gmt-offset + 01:00:00
# system definitions
system
clock-source 1 2
hostname device
# IP context configuration
context ip router
route 0.0.0.0 0.0.0.0 172.19.32.2 1
route 172.19.41.0 255.255.255.0 172.19.33.250
route 172.19.49.0 255.255.255.0 172.19.33.250
# interface LAN used for connection to internal network
interface lan
ipaddress 172.19.33.30 255.255.255.0
mtu 1500
# interface WAN used for connection to access network
interface wan
ipaddress 172.19.32.30 255.255.255.0
mtu 1500
# CS context configuration
context cs switch
no shutdown
# routing table configuration
routing-table called-e164 rtab
route 2. dest-interface telecom-operator
# interface used to access the PSTN telecom operator
interface isdn telecom-operator
route call dest-interface sip
# interface used to access the VoIP telecom provider
interface sip voip-provider
route call dest-table rtab
remoteip 172.19.33.60
bind gateway sip
# SIP gateway primarily used
gateway sip
faststart
no ras
Introduction 65
Page 66

CopperLink CL2300 User Manual 9 • Configuration File Handling
gatekeeper-discovery auto
bind interface lan router
no shutdown
port ethernet 0 0
medium auto
encapsulation ip
bind interface lan router
no shutdown
port ethernet 0 1
medium 10 half
encapsulation ip
bind interface wan router
no shutdown
Figure 16. Sample configuration file
Each configuration file stored in the flash memory needs a unique name. The user has to assign a file name to
any user-specific configuration. Trinity predefines some names for configuration files. These are the shipping
configuration (shipping-config), startup configuration (startup-config), minimal configuration (minimal-config)
and running configuration (running-config) file names.
Shipping Configuration
The CL2300 is delivered with a shipping configuration in the logical region config:. This shipping configuration
initially parameterizes the most useful network and component settings of Trinity.
Once a user-specific configuration is created and stored as the startup configuration, the shipping configuration is no longer used, but still remains in the persistent memory. It is possible to switch back to the shipping
configuration at any time during the operation of a CL2300 configuration. The
getting started guide describes
the restoration procedure for restoring the default settings.
Configuration File Handling Task List
This section describes how to create, load, and maintain configuration files. Configuration files contain a set of
user-configured commands that customize the functionality of your CL2300 to suit your own operating
requirements.
The tasks in this chapter assume that you have at least a minimal configuration running on your system. You
can create a basic configuration file by using the configure command; see section
Configuration at the CLI” on page 71 for details.
To display, copy, delete, and download or upload configuration files, perform the tasks described in the following sections:
• Copying configurations within the local memory (see page 67)
• Replacing the startup configuration with a configuration from the Flash memory (see page 68)
“Modifying the Running
• Copying configurations to and from a remote storing location (see page 69)
• Replacing the startup configuration with a configuration downloaded from the TFTP server (see page 69)
Shipping Configuration 66
Page 67

CopperLink CL2300 User Manual 9 • Configuration File Handling
• Displaying configuration file information (see page 70)
• M
odifying the running configuration at the CLI (see page 71)
• M
odifying the running configuration offline (see page 72)
• D
eleting a specified configuration (see page 73)
Copying Configurations Within the Local Memory
Configuration files may be copied into the local memory in order to switch between different configurations.
emember the different local memory regions in Trinity as shown in figure 17.
R
Local Memory Regions
Copy Configuration Files within
the persistent Memory Region
Store the current Running
Configuration persistently
Local(Intelligent Access Device)
config:
¥Shipping
Configuration
Òshipping-configÓ
(read-only)
¥Startup
Configuration
Òstartup-configÓ
¥ User specific
Configuration
Òuser-configÓ
Only on Startup to execute
the Startup or Shipping
Figure 17. Local memory regions
VolatilePersistent
system:
¥current Running
Configuration
Òrunning-configÓ
Configuration
In most cases, the interactively modified running configuration known as the running-config, which is located
in the volatile memory region system:, is copied into the persistent memory region config. This running config is
stored under the name startup-config and replaces the existing startup configuration.
You can copy the current running configuration into the persistent memory region config: under a user-specified name, if you want to preserve that configuration.
In addition, an already existing configuration is usually copied into the persistent memory region config: by
using a user-specified name, for conservation or later activation.
As shown in figure 17 the local memory regions are identified by their unique names, like config:, which is
located in flash memory, and system:, which is the system RAM, i.e. the volatile memory. As already mentioned,
Configuration File Handling Task List 67
Page 68

CopperLink CL2300 User Manual 9 • Configuration File Handling
configuration files in the same memory region need a unique name. For example, it is not possible to have two
configuration files with the name running-config in the memory region config:.
As you might expect, the copy command does not mo
ve but replicates a selected source to a target configuration file in the specified memory region. Therefore the source configuration file is not lost after the copy process. There are four predefined configuration file names for which it is optional to specify the memory region,
namely shipping-config, star
Mode: A
Step Command Purpose
dministrator execution
1 device#copy {shipping-config | startup-con-
fig | minimal-config | running-config | config:
source-name } config: target-name
tup-config, minimal-config and running-config.
Copies the selected source configuration file
source-name as target configuration file target-
name into the local memory.
Example: Backing up the startup configuration
The following example shows how to make a backup copy of the startup configuration. It is copied under the
name backup into the flash memor
device#copy startup-config config:backup
y region config:.
Replacing the Startup Configuration with a Configuration from Flash Memory
It is possible to replace the startup configuration by a configuration that is already present in the flash memory.
ou can do so by copying it to the area of the flash memory where the startup configuration is stored.
Y
Mode: A
dministrator execution
Step Command Purpose
1 device# copy config:backup startup-config Replaces the existing persistent startup con-
figuration with the startup configuration
backup already present in flash memory.
Note The configuration backup can be a previously backed up configuration or
previously downloaded from a TFTP server.
Configuration File Handling Task List 68
Page 69

CopperLink CL2300 User Manual 9 • Configuration File Handling
Copying Configurations To and From a Remote Storage Location
Configuration files can be copied from local memory (persistent or volatile region) to a remote data store. From
Trinity, the remote TFTP server is represented by the memory region tftp: in combination with the IP
within
address of the TFTP server and the name and path of the configuration file. We will explain the usage of the
remote memory region tftp: in the following section more detailed. Another typical task is uploading the current
running configuration to the remote data store for backup purpose, or if an extensive configuration file is to be
edited on the remote host. In this case the running configuration, named running-config, which is to be found in
the volatile memory region system: is transferred to the TFTP server. On the TFTP server the running configuration is stored to a file whose name is defined as one of the arguments of the copy command.
Figure 18. Remote memory regions for Trinity
Finally, configuration files, i.e. the startup configuration or a user-specific configuration that is stored in the
persistent memory region config: are often uploaded to the remote data store for backup, edit or cloning purposes. The latter procedure is very helpful when you have several Patton devices, each using a configuration
which does not gr
eatly differ from the others, or which is the same for all devices. During the configuration of
the CL2300 according to your requirements, the running configuration of this device, named running-config
and located in the volatile memory region system:, is edited. Next, the configuration is tested and if everything
is as required, the running configuration is copied as startup configuration, named startup-config, into the persistent memory region config: of the target device. After this, the star
tup configuration is transferred to the
TFTP server, where it can be distributed to other Patton devices. These devices therefore get clones of the starting system if the configuration does not need any modifications.
Replacing the Startup Configuration with a Configuration Downloaded from TFTP Server
From within the administration execution mode, you can replace the startup-configuration by downloading a
configuration fr
Configuration File Handling Task List 69
om the TFTP server into the flash memory area where to store the startup configuration.
Page 70

CopperLink CL2300 User Manual 9 • Configuration File Handling
Mode: Administrator execution
Step Command Purpose
1 device(cfg)# copy tftp://ip-address[:port]/new-
startup config:startup-config
Downloads the configuration file new-startup from
the TFTP server at address ip-address replacing
the existing persistent startup configuration. Optionally you can enter the UDP port where the TFTP
server listens. If the port is not specified, the default
port 69 is used. This progress is visualized with a
counter, counting up from 0 to 100% according to
the downloaded amount of the file size. Should the
download fail, an error message % File Transfer -
Get failed is displayed.
Example: Sample configuration download from the TFTP server
The following example shows how to replace the persistent startup configuration in the flash memory of a Patton device by overwriting it with the configuration contained in the file new-star
tup located on the TFTP
server at IP address 172.16.36.80.
1. D
ownload the startup configuration with the copy command into the flash memory area where to store
the startup configuration.
device>enable
device#configure
device(cfg)#copy tftp://172.16.36.80/user/new-startup config:startup-config
Download...100%
device(cfg)#
2. Check the content of the persistent startup configuration by listing its command settings with the show
command.
device#show config:startup-config
Displaying Configuration File Information
This procedure describes how to display information about configuration files
Mode: A
show config: Lists all persistent configurations
show running-config Displays the contents of the running configuration file
show startup-config Displays the contents of the startup configuration file
show running-config current-mode Displays only the running-config of the current mode.
show running-config "<some
mode>"
Configuration File Handling Task List 70
dministrator execution
Command Purpose
Displays the running-config of any named mode
Page 71

T
CopperLink CL2300 User Manual 9 • Configuration File Handling
It is recommended that you never save a configuration in startupconfig or a user-specific configuration with the cli config defaults
IMPORTAN
Note Application files can be very long when displayed (by using the show com-
command because the additional list of default commands consumes significant portions of the conf
ig: memory.
mand). To make them easier to read, many default commands are not displayed when executing the sho
w running-config command. However, the
administrator may want to see the entire configuration, including these normally “hidden” default commands. To see all commands, execute the cli
config defaults command. B
y issuing a show running-config command
afterwards, you will see all the commands, a list which is significantly longer.
To hide these hidden commands again, issue the no cli config
defaults command.
Modifying the Running Configuration at the CLI
Trinity accepts interactive modifications on the currently running configuration via the CLI. Interactive configuring needs access to the CLI. Use the enable command to enter administrator ex
ecution mode, and then
switch to the configuration mode by typing the command configure. Once in configuration mode, you can
enter the configuration commands that are necessary to your Patton device’s operation. When you configure
Trinity by using the CLI, the shell executes the commands as you enter them.
When you log in using the CLI, all commands you enter directly modify the running configuration located in
olatile memory region system: (or RAM) of your device. Because it is located in volatile memory, to be
the v
made permanent, your modifications must be copied to the persistent (non-volatile) memory. In most cases
you will store it as the upcoming startup configuration in the persistent memory region config: under the name
startup-config. On the next start-up the system will initialize itself using the modified configuration. After the
startup configuration has been saved to persistent memory, you have to restart the device by using the reload
command to cause the system to initialize with the new configuration.
The execution command r
• for
ced—reloads the system without prompting for confirmation or for saving the running-configuration (no
eload accepts with the following option:
need to type yes or no). The question whether to save the running-configuration is automatically answered with
no, the question whether to reload or not with yes.
Mode: A
Step Command Purpose
dministrator execution
1 device#configure Enters administrator configuration mode
2 Enter all necessary configuration commands.
3 device(cfg)#copy running-config startup-config Saves the running configuration file as the
upcoming startup configuration
4 device(cfg)#reload Restarts the system
Example: Modifying the running configuration at the CLI
The following example shows how to modify the currently running configuration via the CLI and save it as the
star
tup configuration.
Configuration File Handling Task List 71
Page 72

CopperLink CL2300 User Manual 9 • Configuration File Handling
device#configure
device(cfg)#…
device(cfg)#copy running-config startup-config
device(cfg)#reload
Press 'yes' to restart, 'no' to cancel: yes
The system is going down
Modifying the Running Configuration Offline
In cases of complex configuration changes, which are easier to do offline, you may store a configuration on a
TFTP ser
ver, where you can edit and save it. Since the CL2300 is acting as a TFTP client, it initiates all file
transfer operations.
First, upload the running configuration, named running-config, from the CL2300 to the TFTP server. You can
then edit the configuration file located on the TFTP server by using any regular text editor. Once the configuration has been edited, download it back into the device as upcoming startup configuration and store it in the
persistent memor
y region config: under the name startup-config. Finally, restart the CL2300 by using the reload
command to activate the changes.
Mode: Administrator execution
Step Command Purpose
1 device#copy running-config tftp://
device-ip-address[:port]/current-config
2 Offline editing of the configuration file current-config on
3 device#copy tftp://device-ip-address/
current-config config: startup-config
4 device#reload Restarts the system
Uploads the current running configuration as file currentconfig to the TFTP server at address device-ip-address.
Optionally you can enter the UDP port where the TFTP
server listens. If the port is not specified, the default port
69 is used. This progress is visualized with a counter,
counting up from 0 to 100% according to the downloaded
amount of the file size. If the upload should fail an error
message “% File Transfer - Put failed” is displayed.
the TFTP server using any regular text editor.
Downloads the modified configuration file current-config
from the TFTP server at address device-ip-address into
the persistent memory region config: by using the name
startup-config. This progress is visualized with a counter,
counting up from 0 to 100% according to the downloaded
amount of the file size. Should the download fail, an error
message “% File Transfer - Get failed” is displayed.
Example: Modifying the running configuration offline
The following example shows how to upload the running configuration from the CL2300 to the file curr
ent-
config on a TFTP server at IP address 172.16.36.80. The uploaded configuration file is written into the root
directory specified by the TFTP server settings, and overwrites any existing file with the same name. Read your
TFTP server manual to get a thorough understanding of its behavior. After this, the configuration file is available for offline editing on the TFTP server. Once the configuration file curr
ent-config has been modified, it is
downloaded from the TFTP server, at IP address 172.16.36.80, into the persistent memory region config: using
the name startup-config. It will become active after a reload.
Configuration File Handling Task List 72
Page 73

CopperLink CL2300 User Manual 9 • Configuration File Handling
device#copy running-config tftp://172.16.36.80/user/current-config
Upload...100%
At this point in time, the offline editing of the configuration file current-config on the TFTP server takes place.
device#copy tftp://172.16.36.80/user/ current-config config:startup-config
Download...100%
device#reload
Press 'yes' to restart, 'no' to cancel: yes
The system is going down
Deleting a Specified Configuration
This procedure describes how to delete configuration files from the CL2300 flash memory region config:.
Mode: A
dministrator execution
Step Command Purpose
1 device#show config: Lists the loaded configurations
2 device#erase config:name Deletes the configuration name from the flash memory.
Example: Deleting a specified configuration
The following example shows how to delete a specific configuration from among a set of three available configurations in Flash memory. The configuration named minimal is to be deleted, since it is no longer used.
1. U
se the command show config: to list all available configurations.
device#show config:
Persistent configurations:
backup
minimal
startup-config
shipping-config
2. Delete the configuration named minimal explicitly.
device#erase config:minimal
3. Enter again the command show config: to check if the selected configuration was deleted successfully from
the set of available configurations.
device#show config:
Persistent configurations:
backup
startup-config
shipping-config
Configuration File Handling Task List 73
Page 74

Chapter 10 Basic System Management
Chapter contents
Introduction..........................................................................................................................................................75
Basic System Management Configuration Task List ..............................................................................................75
Managing Feature License Keys ......................................................................................................................75
Setting System Information ............................................................................................................................76
Setting the System Banner ..............................................................................................................................77
Setting Time and Date ....................................................................................................................................78
Configuring Daylight Savings Time Rules ......................................................................................................78
Display Clock Information .............................................................................................................................79
Display Time Since Last Restart ......................................................................................................................79
Configuring the Web Server ...........................................................................................................................80
Restarting the System ......................................................................................................................................80
Displaying the System Logs .............................................................................................................................81
Displaying Reports ..........................................................................................................................................81
Configuring the blink interval .........................................................................................................................82
Configuring the Syslog Client .........................................................................................................................82
74
Page 75

CopperLink CL2300 User Manual 10 • Basic System Management
Introduction
This chapter describes parameters that report basic system information to the operator or administrator, and
their configuration. The following are basic parameters that can be established when setting up a new system:
• D
efining the system's hostname
• S
etting the location of the system
• P
roviding reference contact information
• S
etting the clock
Additionally, the following tasks are described in this chapter:
• S
etting the system banner
• E
nabling the embedded web server
Basic System Management Configuration Task List
All tasks in the following sections are optional, though some such as setting time and calendar services and system information are highly recommended.
To configure basic system parameters, perform the tasks described in the following sections.
• M
anaging feature license keys (see page 75)
• Setting system information (see page 76)
• Setting the system banner (see page 77)
• Setting time and date (see page 78)
• Displaying clock information (see page 79)
• Displaying time since last restart (see page 79)
• Configuring and starting the web server (see page 80)
• Restarting the system (see page 80)
• Displaying the system event log (see page 81)
• Identifying a unit by flashing all LED’s (see page 82)
Managing Feature License Keys
Several features of the firmware require a system specific license key to be installed to enable the feature.
This section describes how to install the feature license keys on your equipment.
Mode: Configur
Step Command Purpose
1 device(cfg)#install license license-key Install the license key
2 Repeat step 1 for any additional license keys
e
Introduction 75
Page 76

CopperLink CL2300 User Manual 10 • Basic System Management
Example: Installing license keys from the console
The following example shows the command used to install license keys manually on the console.
device(cfg)#install license 10011002R1Ws63yKV5v28eVmhDsVGj/JwKqIdpC4Wr1BHaN-
tenXUYF/2gNLoihifacaTPLKcV+uQDG8LJis6EdW6uNk/GxVObDEwPFJ5bTV3bIIfUZ1eUe+8c5OpCCd7PSAe83Ty2c/
CnZPSlEjIrVlJrr8VhOr1DYxkEV9evBp+tSY+y9sCeXhDWt5Xq15SAPlznTLQmym7fDakvm+zltzswX/
KX13sdkR0ub9IX4Sjn6YrvkyrJ2dCGivTTB3iOBmRjV1u
After installing license keys, you can check if the license keys have been added successfully to your system using
the following command.
Mode: Configur
Step Command Purpose
1 device(cfg)#show licenses Display all installed licenses
e
Example: Displaying installed licenses
The following example shows the command used to display all installed licenses on a system and a sample of its
output.
device(cfg)#show licenses
VPN [vpn]
License serial number: 14343534
Status: Active
device(cfg)#
Setting System Information
The system information includes the following parameters:
• Contact
• H
ostname
• Location
• P
rovider
• S
ubscriber
• S
upplier
By default there is no information specified for any of the above parameters.
System contact information tells the user how to contact the information service, e.g. the help line of the service provider. The contact information may be any alphanumeric string, including spaces, that is no longer
than one line.
This entry corresponds to the MIB II system sysContact object.
The system name, also called the hostname, is used to uniquely identify the CL2300 in your network. The
selected name should follo
w the rules for ARPANET hostnames. Names must start with a letter, end with a let-
ter or digit, and have as interior characters only letters, digits, and hyphens. Names must be 63 characters or
wer. For more information, refer to RFC 1035. This entry corresponds to the MIB II system sysName object.
fe
After setting the hostname of the CL2300 the CLI prompt will be replaced with the chosen name.
Basic System Management Configuration Task List 76
Page 77

CopperLink CL2300 User Manual 10 • Basic System Management
Assigning explanatory location information to describe the system physical location of your device (e.g. server
room, wiring closet, 3rd floor, etc.) is very supportive. This entry corresponds to the MIB II system sysLocation
object.
The system provider information is used to identify the provider contact for the CL2300, together with information on how to contact this provider. The provider is a company making services available to subscribers.
ovider information may be any alphanumeric string, including spaces, that is no longer than one line.
The pr
This entry corresponds to the Patton Electronics enterprise-specific MIB provider object.
The system subscriber information is used to get in touch with subscriber for the CL2300, together with information on how to contact this subscriber. The subscriber is a company or person using one or more services
om a provider. The subscriber information may be any alphanumeric string, including spaces, that is no lon-
fr
ger than one line. This entry corresponds to the Patton Electronics enterprise-specific MIB subscriber object.
The system supplier information is used to get in touch with the supplier for the CL2300, together with information on how to contact this supplier. The supplier is a company delivering Patton devices to a provider. The
supplier information may be any alphanumeric string, including spaces, that is no longer than one line.
This
entry corresponds to the Patton Electronics enterprise-specific MIB supplier object.
Mode: Configure
Step Command Purpose
1 device(cfg)#system contact information Sets the contact information to information
2 device(cfg)#system hostname information Sets the hostname to information
3 device(cfg)#system location information Sets the location information to information
4 device(cfg)#system provider information Sets the provider information to information
5 device(cfg)#system subscriber information Sets the subscriber information to information
6 device(cfg)#system supplier information Sets the supplier information to information
Note If the system information must have more than one word, enclose it in dou-
ble quotes.
Example: S
etting system information
The following example shows the commands used to configure the contact information for the CL2300, if you
star
t from the operator execution mode.
device(cfg)#system contact "Bill Anybody, Phone 818 700 1504"
device(cfg)#system hostname device
device(cfg)#system location “Wiring Closet, 3rd Floor”
device(cfg)#system provider “Best Internet Services, contact@bis.com, Phone 818 700
2340”
device(cfg)# system subscriber “Mechanical Tools Inc., jsmith@mechtool.com, Phone
818 700 1402”
device(cfg)# system supplier “WhiteBox Networks Inc., contact@whitebox.com, Phone
818 700 1212”
Setting the System Banner
The system banner is displayed on all systems that connect to your CL2300 via Telnet, SSH, or a serial connection. It appears at login and is useful for sending messages that affect administrators and operators, such as
scheduled maintenance or system shutdo
Basic System Management Configuration Task List 77
wns. By default no banner is present on login.
Page 78

CopperLink CL2300 User Manual 10 • Basic System Management
To create a system banner use the banner command followed by the message you want displayed. If the banner
message has to be formed out of more than one word the information is enclosed by double quotes. Adding the
escape sequence “\n” to the string forming the banner creates a new line on the connected terminal screen. Use
the no banner command to delete the message.
Mechanical Tools Inc.
jsmith@mechtool.com
Phone 818 700 1402
login:
Mode: Configure
Step Command Purpose
1 device(cfg)#banner message Sets the message for the system banner to message
Example: Setting the system banner
The following example shows how to set a message for the system banner for the CL2300, if you start from the
configuration mode.
device(cfg)#banner \n#\n# The password of all operators has changed\n# please con-
tact the administrator\n#"
Setting Time and Date
All Patton devices provide time-of-day and date services. These services allow the products to accurately keep
track of the curr
ent time and date. The system clock specifies year, month, day, hour, minutes, and optionally
seconds. The time is in 24-hour format yyyy-mm-ddThh:mm:ss and is retained after a reload.
Mode: Configure
Step Command Purpose
1 device(cfg)#clock set yyyy-mm-ddThh:mm:ss Sets the system clock to yyyy-mm-
ddThh:mm:ss
Example: Setting time and date
The following example shows the commands used to set the system clock of your device to August 6, 2001 at
16:55:57, if y
device(cfg)#clock set 2001-08-06T16:55:57
ou start from the operator execution mode.
Configuring Daylight Savings Time Rules
Trinity allows configuring daylight saving time rules, which affect the local clock offset without changing the
configuration. After booting up and loading the configuration, the daylight saving r
ules are checked and
applied automatically. The rules consist of a default-offset and one or multiple dst-rules. The offset of a dst-rule
is active if the local clock is between the specified start and stop time of the rule. If the local clock is outside the
specified start and stop time of all specified rules, then the default-offset is active.
Basic System Management Configuration Task List 78
Page 79

CopperLink CL2300 User Manual 10 • Basic System Management
Mode: Configure
Step Command Purpose
1 device(cfg)#clock local default-offset
(+hh:mm | -hh:mm)
Configures the offset of your time zone from
GMT. This offset is used if no other dst rule is
currently active. Default: +00:00
Display Clock Information
This procedure describes how to display the current date and time
Mode: Both in operator and administrator ex
Step Command Purpose
1 device>show clock Display the local time.
ecution
Example: Display clock information
The following example shows the commands used to display the time and date settings of your device in local
time, if y
ou start from the operator execution mode.
device>show clock
2001-08-06T16:55:57
Display Time Since Last Restart
This procedure describes how to display the time since last restart
Mode: O
perator execution
Step Command Purpose
1 device>show uptime Display the time since last restart.
Example:
The following example shows how to display the uptime of your device, if you start from the configuration mode.
device>show uptime
The system is up for 54 days, 23 hours, 44 minutes, 18 seconds
Basic System Management Configuration Task List 79
Page 80

CopperLink CL2300 User Manual 10 • Basic System Management
T
Configuring the Web Server
The embedded web server has two parameters that are configurable.
Note Changing the language parameter does not affect the language of the web
configuration pages.
Mode: Configur
Step Command Purpose
1 device(cfg)#webserver [http |
https] port port-number
e
Start the http or https server, and set the listening port number.
The default port number for the http web server is 80, and the
default port number for the https web server is 443.
Example: Configuring and starting the Web server
The following example shows how to set the web server language and the listening port of your device, if you
star
t from the configuration mode.
device(cfg)#webserver http port 80
device(cfg)#webserver http
Restarting the System
In case the CL2300 has to be restarted, the r
eload command must be used. The reload command includes a
two-dialog, where the user is allowed to store any unsaved configuration data and finally confirms the
system restart.
Restarting the system interrupts running data transfers and all
voice calls.
IMPORTAN
The execution command reload has been enhanced with the following option:
• for
ced—reloads the system without prompting for confirmation or for saving the running-configuration (no
need to type yes or no). The question whether to save the running-configuration is automatically answered with
no, the question whether to reload or not with yes.
Mode: A
Step Command Purpose
dministrator execution
1 device#reload Restarts the system
Example: Restarting the system
The following example shows how to restart the currently running system, if you start from the administrator
ex
ecution mode.
Basic System Management Configuration Task List 80
Page 81

CopperLink CL2300 User Manual 10 • Basic System Management
device#reload
System configuration has been changed.
Press 'yes' to restart, 'no' to cancel: yes
The system is going down
Displaying the System Logs
The system logs contain warnings and information from the system components of Trinity3. In case of problems it is often useful to check the event or the supervisor logs for information about malfunctioning system
components.
The event log stores general events such as flash full, DSP failed etc., comparable with the event
log on Windows NT. The supervisor log stores information from the system supervisor such as memory full,
task failed etc.
System resets may have a number of reasons, the most prominent being a manual reset issued on the Telnet/
console (‘r
eload’). Other reset reasons include power off failures and system failures. In order to pinpoint the
problem, the reset log contains the reset cause.
Mode: Administrator execution
Step Command Purpose
1 device#show log event Show event log.
2 device#show log supervisor Show log of the system supervisor. Used For example, after an
unexpectedly reboot.
3 device#show log reset Output a list of reset reasons (with date and time).
4 device#show log boot Displays the console and log messages captured during startup of
the unit.
Displaying Reports
The show reports command is used to dump combined system information. The show reports command
sequentially ex
show version
show clock
show uptime
show log reset
show log boot
show log event
show log supervisor
show factory-config
show startup-config
show running-config
ecutes the following log commands:
Mode: Administrator execution
Step Command Purpose
1 device#show reports Dumps the combined system information.
Basic System Management Configuration Task List 81
Page 82

CopperLink CL2300 User Manual 10 • Basic System Management
Configuring the blink interval
When there are many Trinity devices in the same location, use this command to flash all the LED’s on a specific
unit for a specified period of time.
Step Command Purpose
1 device #blink <seconds> Enter an integer for the period of time you want the
This makes identification of the physical unit very easy.
LED’s to flash on the physical unit.
Configuring the Syslog Client
Syslog is a protocol for sending event notification messages across IP networks to message collectors (Syslog
ver). It uses transport protocol UDP on port 514. A syslog-message exits on the three main part Priority,
ser
Header and Message whereas the header is split into Facility and Severity and the header into Timestamp and
Hostname. The whole syslog-message (Priority, Header and Message) contains only printable characters and
the maximum length is 1024 bytes.
Mode: Configur
Step Command Purpose
1 device(cfg)#syslog-client Enters syslog client configuration mode.
e
Mode: Syslog Client
Step Command Purpose
1 device(syslog-client)#[no] remote { <ipv4
host> | <ipv6 host> } [ tcp | udp ] [ <port> ]
Creates a new remote destination and enters its configuration mode. The 'no' form of the command
removes an existing remote destination. The protocol
type and port are optional. If not included, the default
UDP port 512 will be used.
Mode: Remote
Step Command Purpose
1 device(syslog-client)(remote)#[no] facility
<service name> <severity>
Creates a new log expression for a remote destination. It exists on a facility that determines from which
source messages must be accepted and a severity
that defines up to which level the messages of the
given facility must be sent. The 'no' form of the command disables sending of messages from the given
facility.
Basic System Management Configuration Task List 82
Page 83

Chapter 11 Wizard Interface
Chapter contents
Introduction..........................................................................................................................................................84
Browser Notes .......................................................................................................................................................84
Connect with Web GUI........................................................................................................................................84
Management IP Setup .....................................................................................................................................86
Line Setup .......................................................................................................................................................86
83
Page 84

CopperLink CL2300 User Manual 11 • Wizard Interface
Introduction
The Trinity Embedded Devices are designed with an intuitive Command Line Management Interface. They
also have a limited or basic Web Management Interface for easy firmware support and access to the XML Wizard function. This Chapter will give you a quick walk through how to use the Wizard that has been loaded on
to the device fr
by using your favorite color code or text editor. The wizard is a simple XML script that loads your new graphical changed into the startup configuration file saves and reboots. This means that the Wizard changes don’t
affect any r
tion until the unit is rebooted.
om the Patton Factory. These Wizards can be both imported and exported and modified easily
unning configurations. These changes are simply static and do not affect your running configura-
Browser Notes
Recommended that you use the most recent browser with the latest security updates. You may find the XML
scripting does not work well with older outdated browsers. We have tests with Chrome 39, MS IE 9, and Firefox 33. If you are experiencing page display problems please update your browser with the latest update. Once
ou have updated your favorite browser you can access the device with the newly configured IP address or the
y
Factory Default IP: 192.168.200.10/24
Connect with Web GUI
1. Connect the ethernet cable.
2. Connect the po
3. Connect via w
pack local units.
4. Log in with the default username admin without a passwor
Once the network connection is established, you will be able to reach the CL2300 Web GUI. Log in to the
W
eb GUI using the following credentials in figure 19.
• U
sername: admin
• P
assword: [blank
wer supply.
eb browser to the default address 192.168.200.10 OR connect to 192.168.200.11 for 2
d.
Figure 19. Login
Introduction 84
Page 85

CopperLink CL2300 User Manual 11 • Wizard Interface
The CL2300 includes a Wizard within the GUI. The icon to the wizard is in the top right corner of your
browser as it displays in figure 20.
Figure 20. Wizard Homepage
Once the wizard icon is selected, you will have the options of supported set ups as shown in figure 32. Click on
CL2300 Basic Setup.
Figure 21. Choose Wizard
Clicking on the CL2300 Basic Setup will bring up the most common configurations used on the CopperLink
Ethernet Extenders.
Figure 22 on page 86 depicts options to configure through the Basic Setup Wizard.
Connect with Web GUI 85
Page 86

CopperLink CL2300 User Manual 11 • Wizard Interface
Figure 22. Basic Setup
User Access: (optional configuration) Users may change the password for the admin user.
Management IP Setup
tatic: create your own IP address, netmask and gateway (optional-the gateway is required for remote manage-
• S
ment).
• DHCP: The CL2300 management por
• B
oth: This choice will assign two IP addresses (one static and one DHCP to the management port.)
• M
anagement VLAN ID: (optional) define a VLAN ID for management traffic.
t will accept an IP address from a DHCP server.
Line Setup
This is where you can manually set your CopperLink line options.
Note The Copperlink Ethernet Extenders by default are set to plug-and-play oper-
ation
Connect with Web GUI 86
Page 87

CopperLink CL2300 User Manual 11 • Wizard Interface
• Line Type (Local or Remote): This will set the Ethernet Extender as Local or Remote. Local is typically used
at the network, Remote is typically used at the remote device or remote network. Your CopperLink CL2300
when received in a 2pk is already configured one CL2300 as Local and one CL2300 as Remote.
• Service Mode: Configures the number of pairs (wires) you want to use. The CL2300 will default to the maxi-
mum number of wires available on your version of the CopperLink. CL2301 (2-wire); CL2302 (4-wire);
CL2304 (8-wire).
• Annex: Please consult support before changing this setting.
• Line Rate Configuration: This will increase the potential line rate of the CL2300. Your CopperLink CL2300
is defaulted to automatically select the optimal rate based on the distance (adaptive).
Note There are two mates: Normal (TCPAM16|32) and Extended
(TCPAM64|128). Selecting the Extended mode will double the bandwith,
but will reduce the reach (distance) in half. Default is normal.
On the bottom right corner of the CL2300 Basic Configuration wizard page to preview configurations and
reboot.
Figure 23 depicts what you can expect to see if you click on the preview tab.
Connect with Web GUI 87
Page 88

CopperLink CL2300 User Manual 11 • Wizard Interface
Figure 23. Configure Preview Option
When the user chooses the save and reboot option, a prompt will ask you to confirm. If the configuration is
correct, select “Yes” as shown in figure 24.
Figure 24. Confirmation
Typically the time to reboot and reestablish a Copperlink link and pass traffic once again will be under 2 minutes.
Connect with Web GUI 88
Page 89

Chapter 12 IP Routing
Chapter contents
Introduction..........................................................................................................................................................90
Basic Routing ........................................................................................................................................................90
Static Routes ...................................................................................................................................................90
Configuring static routes ...........................................................................................................................90
System Routes .................................................................................................................................................91
Dynamic Routes .............................................................................................................................................92
Show Routes ...................................................................................................................................................92
Basic Static Routing Example ..........................................................................................................................92
89
Page 90

CopperLink CL2300 User Manual 12 • IP Routing
Introduction
The Trinity IP Routing facility consists of the two major functionalities: Basic Routing and Policy Routing.
Basic Routing
Under Basic Routing is to be understood the destination IP address based next-hop determination. The nexthop or gateway selection is done by matching a set of routing rules entered by the user (static-route), received
through a routing-protocol (dynamic-route) or added by the system (system-route). Routing entries which
specify a gateway as next-hop are also called gateway-routes. Networks that are directly reachable through a
device’s network-port are specified through interface-routes. Instead of a gateway they specify an outgoing
interface.
In the context ip configuration mode exists a system created routing-table called DEFAULT. This table contains all Basic Routing information and cannot be deleted by the user. Actually it is possible to created additional routing-tables with a user defined name but such user-created tables are part of the Policy Routing and
do not have any use in Basic Routing.
All Basic Routing features are available for IPv4 as well as for IPv6.
Static Routes
These are user managed gateway and interface routes and are getting exported in the running-config. In the
output of the show route command they are flagged with an “R”. Another flag “U” indicates if the route is up
or not. A static gateway-route is becoming active (up) if the gateway is reachable. For this we need the follow
ing conditions:
-
• At least one IP address in the gateway’s network has to be configured.
• The IP interface which owns the IP address has to be bound from a network-port.
• The network-port’s link state has to be up.
A static interface-route is becoming active (up) if:
• The specified outgoing interface is bound from a network-port.
• The specified outgoing interface has at least one IP address configured.
• The network-port’s link state has to be up.
Configuring static routes
A route is clearly identified by its destination address/mask combination and the metric. That means it is
allowed to configure several time the same destination, using the same or different gateways, but with a differ
ent metric value. The metric in a static route has the meaning of a priority where lower value means higher priority.
Static route differentiation by metric is useful if a destination network is reachable through different gateways.
Usually gateways are located in the same network as the device itself. If the link to the gateway with lowest met
ric is going down, this static-route is becoming unavailable. In that case the device’s router will select the route
to the destination with the next higher metric and another gateway is going to be used.
-
-
Introduction 90
Page 91

CopperLink CL2300 User Manual 12 • IP Routing
Mode: Administrator execution
Step Command Purpose
1 [device](cfg)#context ip [ROUTER ] Enters the context IP ROUTER
configuration mode.
2 [device](ctx-ip)[ROUTER]#routing-table [ DEFAULT ] Enters the routing-table DEFAULT
configuration mode.
3 [device][ROUTER.DEFAULT]#route { <network>/<mask-
size> | <network><mask> |default | default-v6 } { gateway
<gw-address> | interface <if-name> } [ metric <metric> ]
OR
[device][ROUTER.DEFAULT]#no route <network>/<mask-
size> [ metric <metric> ]
Adds a static route.
Removes a static route.
Syntax:
Parameter Explanation
network The destination network address in the dot-format a.b.c.d for IPv4 and in the
colon-format a:b:c::x for IPv6.
mask-size Number of mask-bits defining the destination network.
mask The destination network mask in the dot-format a.b.c.d for IPv4 and in the
colon-format a:b:c::x for IPv6.
default Short form for defining a default IPv4 route.
It configures network/mask-size with 0.0.0.0/0.
default-v6 Short form for defining a default IPv6 route.
It configures network/mask-size with ::/0.
gw-address The address of the next-hop router that can access the destination network. In
the dot-format a.b.c.d for IPv4 and in the colon-format a:b:c::x for IPv6.
interface The name of the outgoing interface to be used for reaching the destination net-
work.
metric Metric value of the route.
Default: 0
Note To configure a default static IP route, use 0.0.0.0 for the network number
and mask (or ::/0 for a default IPv6 route). A valid next-hop address or interface is required.
System Routes
For each assigned IP address the system automatically creates route entries for the belonging network into the
AULT routing-table. That means, all directly available networks are known by the system and don’t have
DEF
Basic Routing 91
Page 92

CopperLink CL2300 User Manual 12 • IP Routing
to be configured. The system-routes are of type interface-route means, only the outgoing interface is specified
and do not have the gateway parameter. In the output of the show route command they are flagged with
an “S”.
Dynamic Routes
This kind of routes is assigned to the system either by a routing-protocol (RIP, BGP) or through a device configuration protocol (DHCP, PPP). In the output of the show route command they are flagged with a D. A
dynamic-r
oute is active under the same condition as a static-route.
Show Routes
Execution of show running-config command only displays the static-routes which have been added to the system. Neither dynamic-routes nor system-routes are shown there. To get an overview of all routes actually
wn by the system the show route command has to be executed.
kno
Mode: O
perator execution
Step Command Purpose
1 [device]#show route [ <details> ] Displays route information
Default: 0
Output:
Routing Tables
===============================================
Flags: C - dhCp, D - Dynamic, G - use Gateway, H - target is a host
R - useR, U - route is Up, S - System
Routing Table DEFAULT, ID = 254
Destination Gateway Flags Metric Interface Source
172.16.32.0/19 SU 0 WAN 172.16.45.7
30.30.30.0/24 172.16.45.4 RU 0
172.16.32.0/19 SU 0 WAN 172.16.60.7
0.0.0.0/0 172.16.32.1 CDGU 0 eth0
Basic Static Routing Example
The picture below shows an Internetwork consisting of three routers, a CL2300 in the middle, and the four
autonomous networ
ks, with network addresses 10.1.5.0/16, 172.16.40.0/24, 172.17.100.0/24 and 10.2.5.0/
16. The CL2300 shall be configured for the following IP routing scenario:
All packets for the Workstation with IP address 10.1.5.10 shall be forwarded to the next-hop router Calvin. All
packets for network 10.2.5.0/16 shall be forwarded to the next-hop router Hobbes.
Basic Routing 92
Page 93

CopperLink CL2300 User Manual 12 • IP Routing
Figure 25. Static route example
Example Configuration:
context ip ROUTER
routing-table DEFAULT
route 10.1.5.10/32 gateway 172.16.40.2 metric 0
route 10.2.0.0/16 gateway 172.17.100.2 metric 0
Show Route Output:
Routing Tables
===============================================
Flags: C - dhCp, D - Dynamic, G - use Gateway, H - target is a host
R - useR, U - route is Up, S - System
Routing Table DEFAULT, ID = 254
Destination Gateway Flags Metric Interface Source
172.16.40.0/24 SU 0 LAN 172.16.40.1
172.17.100.0/24 SU 0 WAN 172.17.100.1
10.1.5.10/32 172.16.40.2 RU 0
10.2.0.0/16 172.17.100.2 RU 0
Basic Routing 93
Page 94

Chapter 13 SNMP Configuration
Chapter contents
Introduction..........................................................................................................................................................95
Simple Network Management Protocol (SNMP) ..................................................................................................95
SNMP Basic Components ..............................................................................................................................95
SNMP Basic Commands ................................................................................................................................95
SNMP Management Information Base (MIB) ................................................................................................96
Network Management Framework .................................................................................................................96
Identification of a CL2300 via SNMP...................................................................................................................97
SNMP Tools .........................................................................................................................................................97
SNMP Configuration Task List.............................................................................................................................97
Setting Basic System Information ..........................................................................................................................97
Setting Access Community Information..............................................................................................................100
Setting Allowed Host Information.......................................................................................................................101
Specifying the Default SNMP Trap Target..........................................................................................................101
Displaying SNMP Related Information...............................................................................................................102
Using the ManageEngine SNMP Utilities ...........................................................................................................102
Using the MibBrowser ..................................................................................................................................103
Using the TrapViewer ...................................................................................................................................104
Standard SNMP Version 1 Traps ........................................................................................................................107
SNMP Interface Traps ........................................................................................................................................108
94
Page 95

CopperLink CL2300 User Manual 13 • SNMP Configuration
Introduction
This chapter provides overview information about Simple Network Management Protocol (SNMP) and
describes the tasks used to configure those of its features supported.
This chapter includes the following sections:
• Simple Network Management Protocol (SNMP)
• SNMP tools (see page 97)
• SNMP configuration task list (see page 97)
• Using the ManageEngine SNMP utilities (see page 102)
• Standard SNMP version 1 traps (see page 107)
Simple Network Management Protocol (SNMP)
The Simple Network Management Protocol (SNMP) is an application-layer protocol that facilitates the
exchange of management information between network devices. It is part of the Transmission Control Proto
col/Internet Protocol (TCP/IP) suite. SNMP enables network administrators to manage network performance,
find and solve network problems, and plan for network growth.
-
SNMP Basic Components
An SNMP managed network consists of three key components: managed devices, agents, and network-management systems (NMSs).
A managed device is a network SN that contains an SNMP agent and resides on a managed network. Managed
devices collect and store management information and make this information available to NMSs using SNMP.
Managed devices, sometimes called network elements, can be routers and access servers, switches and bridges,
hubs, computer hosts, or printers.
An agent is a network-management software module that resides in a managed device. An agent has local
knowledge of management information and translates that information into a form compatible with SNMP.
An NMS executes applications that monitor and control managed devices. NMSs provide the bulk of the processing and memory resources required for network management. One or more NMSs must exist on any managed network.
SNMP Basic Commands
Managed devices are monitored and controlled using four basic SNMP commands: read, write, trap, and traversal operations.
• The read command is used by an NMS to monitor managed devices. The NMS examines different variables
that are maintained by managed devices.
• The write command is used by an NMS to control managed devices. The NMS changes the values of variables
stored within managed devices.
• The trap command is used by managed devices to asynchronously report events to the NMS. When certain
types of events occur, a managed device sends a trap to the NMS.
• Traversal operations are used by the NMS to determine which variables a managed device supports and to
sequentially gather information in variable tables, such as a routing table.
Introduction 95
Page 96

CopperLink CL2300 User Manual 13 • SNMP Configuration
SNMP Management Information Base (MIB)
A Management Information Base (MIB) is a collection of information that is organized hierarchically. MIBs
are accessed using a network-management protocol such as SNMP. They are comprised of managed objects and
are identified by object identifiers.
Managed objects are accessed via a virtual information store, termed the Management Information Base or
MIB. Objects in the MIB are defined using the subset of abstract syntax notation one (ASN.1) defined in the
SMI. In particular, an object identifier, an administratively assigned name, names each object type. The object
type together with an object instance serves to uniquely identify a specific instantiation of the object. For
human convenience, a textual string, termed the descriptor, to refer to the object type, is often used.
An object identifier (OID) world-wide identifies a managed object in the MIB hierarchy. The MIB hierarchy
can be depicted as a tree with a nameless root, the levels of which are assigned by different organizations.
Network Management Framework
This section provides a brief overview of the current SNMP management framework. An overall architecture is
described in RFC 2571 “An Architecture for Describing SNMP Management Frameworks.” The SNMP man
agement framework has several components:
• Mechanisms for describing and naming objects and events for the purpose of management. The first version,
Structure of Management Information (SMIv1) is described in RFC 1155 “Structure and Identification of
Management Information for TCP/IP-based Internets”, RFC 1212 “Concise MIB Definitions”, RFC 1213
“Management Information Base for Network Management of TCP/IP-based Internets: MIB-II”, and RFC
1215 “A Convention for Defining Traps for use with the SNMP”. The second version, SMIv2, is described in
RFC 2233 “The Interfaces Group MIB using SMIv2”, RFC 2578 “Structure of Management Information
Version 2 (SMIv2)”, RFC 2579 “Textual Conventions for SMIv2”, and RFC 2580 “Conformance Statements
for SMIv2”.
-
• Message protocols for transferring management information. The first version, SNMPv1, is described in RFC
1157 “A Simple Network Management Protocol (SNMP).” The second version, SNMPv2, which is not an
Internet standards track protocol, is described in RFC 1901 “Introduction to Community-Based SNMPv2”
and RFC 1906 “Transport Mappings for Version 2 of the Simple Network Management Protocol
(SNMPv2)”.
• Protocol operations for accessing management information. The first set of protocol operations and associated
protocol data unit (PDU) formats is described in RFC 1157. The second set of protocol operations and associ
ated PDU formats is described in RFC 1905 “Protocol Operations for Version 2 of the Simple Network Management Protocol (SNMPv2)”.
• A set of fundamental applications described in RFC 2573 “SNMP Applications” and the view-based access
control mechanism described in RFC 2575 “View-Based Access Control Model (VACM) for the Simple Net
work Management Protocol (SNMP)”.
-
-
Simple Network Management Protocol (SNMP) 96
Page 97

CopperLink CL2300 User Manual 13 • SNMP Configuration
T
Identification of a CL2300 via SNMP
All product models have assigned sysObjectID.
Refer to the getting started guide of your product, or see the MIB definition file (.my) for sysObjectIDs.
The SNMP agent running in Trinity is SNMP version 1
(SNMPv1) and SNMP version 2 (SNMPv2) compliant.
SNMP version 3 (SNMPv3) is not currently supported.
IMPORTAN
SNMP Tools
Patton recommends the ManageEngine.
Refer to section “Using the ManageEngine SNMP Utilities” on page 102 for more detailed information on
how to use these tools.
SNMP Configuration Task List
To configure SNMP, perform the tasks described in the following sections. The tasks in the first three sections
are required; the tasks in the remaining sections are optional, but might be required for your application.
• S
etting basic system information (required) (see page 97)
• S
etting access community information (required) (see page 100)
• S
etting allowed host information (required) (see page 101)
• S
pecifying the default SNMP trap target (optional) (see page 101)
• D
isplaying SNMP related information (optional) (see page 102)
Setting Basic System Information
The implementation of the MIB-II system group is mandatory for all systems. By default, an SNMP agent is
configured to have a value for any of these variables and responds to get commands from a NMS.
The following MIB II panels should be set:
• sysContact
• sysLocation
• sysN
The system sysContact object is used to define the contact person, together with information on how to contact that person.
Assigning explanatory location information to describe the system physical location (e.g. server room, wiring
closet, 3r
ame
d floor, etc.) is very supportive. Such an entry corresponds to the MIB II system sysLocation object.
The name used for sysName should follow the rules for ARPANET host names. Names must start with a letter,
end with a letter or digit, and hav
e as interior characters only letters, digits, and hyphens. Names must be 63
characters or fewer. For more information, refer to RFC 1035.
This procedure describes how to set these MIB-II system group objects.
Identification of a CL2300 via SNMP 97
Page 98

CopperLink CL2300 User Manual 13 • SNMP Configuration
Mode: Administrator execution
Step Command Purpose
1 device(cfg)#system contact name Sets the contact persons name
2 device(cfg)#system location location Sets the system location
3 device(cfg)#system hostname hostname Sets the system hostname and command line prompt
If any of the command options name, location, or hostname has to be formed out of more than one word, the
information is put in “double quotes”.
Note Enter an empty string “” to get rid of any of the system settings.
The MIB-II system group values are accessible for reading and writing via the following SNMP objects:
• .iso
.org.dod.internet.mgmt.mib-2.system.sysContact
• .iso
.org.dod.internet.mgmt.mib-2.system.sysName
• .iso
.org.dod.internet.mgmt.mib-2.system.sysLocation
After setting these values according to 1 through 3 any SNMP MIB browser application should read the values
using a get or get-next command as sho
wn in figure 26.
The procedure to use the SNMP MIB browser is:
• E
nter the community string public into the Community field in the upper right corner of the window. For
safety reasons each entered character is displayed with a “*”.
• A
ccess any of the supported MIB system group object by using the GetNext button from the button bar of the
window.
Setting Basic System Information 98
Page 99

CopperLink CL2300 User Manual 13 • SNMP Configuration
Figure 26. ManageEngine MibBrowser displaying some of the System Group objects
Example: Setting the system group objects
In the following example the system information is set for later access via SNMP. See figure 26 for a typical
MIB browser application accessing these MIB-II system group objects representing the system information.
device>enable
device#configure
device(cfg)#system contact "Bill Anybody, Phone 818 700 1504"
device(cfg)#system location "Wiring Closet, 3rd floor"
device(cfg)#system hostname "device"
(cfg)#
After entering a host name the prompt on the CLI no longer displays the IP address of the Ethernet port over
which the Telnet session is running but shows the newly entered host name.
Setting Basic System Information 99
Page 100

CopperLink CL2300 User Manual 13 • SNMP Configuration
Setting Access Community Information
SNMP uses one or more labels called community strings to delimit groups of objects (variables) that can be
viewed or modified on a CL2300. The SNMP data in such a group is organized in a tree structure called a
Management Information Base (MIB). A single device may have multiple MIBs connected together into one
large structure, and various community strings may provide read-only or read-write access to different, possibly
overlapping portions of the larger data structure. An example of a read-only variable might be a counter showing the total number of octets sent or received through an interface. An example of a read-write variable might
be the speed of an inter
Community strings also provide a weak form of access control in earlier versions of SNMP version 1 and 2.
SNMP v
ersion 3 provides much improved access control using strong authentication and should be preferred
over SNMP version 1 and 2 wherever it is supported. If a community string is defined, then it must be provided in any basic SNMP query if the requested operation is to be permitted by the CL2300. Community
strings usually allo
will be limited to one group of read-only or read-write objects described in an individual MIB.
In the absence of additional configuration options to constrain access, knowledge of the single community
string for the CL2300 is all that is required to gain access to all objects, both read-only and read-write, and to
modify any read-write objects.
Note Security problems can be caused by unauthorized individuals possessing
face, or the hostname of a CL2300.
w read-only or read-write access to the CL2300. In some cases, a given community string
knowledge of read-only community strings so they gain read access to confidential information stored on an affected device. Worse can happen if they
gain access to r
ead-write community strings that allow unauthorized remote
configuration of affected devices, possibly without the system administrators
being aware that changes are being made, resulting in a failure of integrity
and a possible failure of CL2300 availability. To prevent these situations,
define community strings that only allow read-only access to the MIB
objects should be the default.
Choosing community names is like choosing a password. Do not use easily guessed ones; do not use commonly
wn words, mix letters and other characters, and so on. If you do not intend to allow anyone to use SNMP
kno
write commands on your system, then you probably only need one community name.
This procedure describes how to define your own SNMP community.
Mode: Configur
Step Command Purpose
1 device(cfg)#snmp community name { ro |
rw }
e
Configures the SNMP community name with read-only
or read/write access
Use the no command option to remove a SNMP community setting.
Example: S
etting access community information
In the following example the SNMP communities for the default community public with read-only access and
the undisclosed community N
ot4evEryOne with read/write access are defined. Only these valid communities
have access to the information from the SNMP agent.
Setting Access Community Information 100
 Loading...
Loading...