
NH Series
8169-B
User's Manual
This book corresponds to the current rmware version 1.11.
Intro
Introduction
Thank you for purchasing the PATLITE "NH Series" (henceforth, written as "this product") Network Monitoring
Signal Tower. Please read this NH Series instruction manual (henceforth, written as "this book") carefully
before installation. In addition, please store this manual for future reference when performing maintenance,
repairs or inspections. When performing maintenance and repairs, etc., please be sure to reread this book.
After reading this book, if there are any questions regarding this product, please contact your PATLITE Sales
Representative from the contact list indicated at the end of this book.
Notice
►The copyrights of this book is owned by the PATLITE Company, Inc. (henceforth referred to as "our
company"). Any reproduction, duplication, alteration, or extracting portions of this book, etc., without
written permission from our company is forbidden.
►Specications, the design, and other contents written in this book may be changed for improvements
without prior notice and may result in differences from the actual product purchased.
►This product meets severe quality control and inspection requirements prior to shipment, but if some
failure or defect is found, please contact the place of purchase, or your PATLITE Sales Representative
(indicated on the last page) to solve the issue.
►This product (software is included) is for the use of general ofce work, home and for personal use, it
has been developed, designed and manufactured for general applications, such as for industry, and it
is not designed for applications which demands high safety requirements, such as medical application
equipment or systems used in connection directly, or indirectly, with human life.
Please understand prior to use that no responsibility is taken at our company for damages or other
disadvantages, due to customers using this product beyond the scope of its general application, or from
any claims from third parties.
• When using this product for applications in which equipment of higher reliability than the general
application demands, such as a computer system, etc., please use suitable safety design
countermeasures against system failure, etc.
►Please understand that our company does not take any responsibility for damage and other
disadvantages this product (software is included) has caused due to the customer using this product,
or any claims from third parties.
►Due to the characteristics of the LED's, variations in brightness and color of the indicating lamps may
occur.
►This product (Body only) conforms to EN standards and shows the CE Markings.
►The AC Adaptor included does not conform to the EN standards, therefore does not show CE Markings
►To retain the UL certication for the main unit, it is required to use an AC adaptor with UL Listing. .
2

FCC Compliance
This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part
15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a
residential installation. This equipment generates, uses and can radiate radio frequency energy and, if not installed
and used in accordance with the instructions, may cause harmful interference to radio communications.
However, there is no guarantee that interference will not occur in a particular installation.
If this equipment does cause harmful interference to radio or television reception, which can be determined by
turning the equipment off and on, the user is encouraged to try to correct the interference by one or more of the
following measures:
• Reorient or relocate the receiving antenna.
• Increase the separation between the equipment and receiver.
• Connect the equipment into an outlet on a circuit different from that to which the receiver is connected.
• Consult the dealer or an experienced radio/TV technician for help.
You are cautioned that changes or modications not expressly approved by the party responsible for compliance
could void your authority to operate the equipment.
This device complies with FCC RF radiation exposure limits set forth for an uncontrolled environment. The
antenna used for this transmitter is built-in, therefore, the transmitter must provide separation of at least 20cm from
all persons.
For safe application, observe the following:
Intro
The following symbols classifes the following into different catagories and explains the level of harm inicted
if the cautions are disregarded.
Warning
Caution
Prohibited This symbol indicates “Prohibited”, which should not be carried out by all means.
Enforced This symbol indicates “Enforced”, which should be observed and carried out by all means.
Please
Note
Indicates an imminently dangerous condition: Failure to follow the instructions may lead to death or serious injury.
Indicates a potentially dangerous condition: Failure to follow the instructions may lead to slight injury or property damage.
Indicates something to observe before using this product.
Notice regarding supplementary information or convenient explanation is indicated.
3
Intro
Cautionary Notes
Prior to installation, read all notes and use this product correctly.
• Do not disassemble or alter the product. Failure to comply may result in re, electric shock, or
failure.
Prohibited
Enforced
• The power supply rating is AC 100-240V. Do not allow the voltage to exceed the specied
voltage tolerance. Failure to comply will result in internal circuitry damage. Moreover, there is
fear of re.
• When plugging the power cord into the power receptacle, be sure to check there is no dust
accumulation on the plug, and insert into the power receptacle completely. By allowing dust to
adhere to the power supply terminal, it can be the result of re or failure from short-circuiting.
• Since dust can accumulate after a long time, and with moisture, can cause the dust to become
conductive, in order to prevent the phenomenon of ignition from dust accumulation, it is best
to periodically wipe the transformer and socket terminal with a damp cloth. By allowing dust to
adhere to the power supply terminal, it can be the result of re or failure from short-circuiting.
• When replacing LED units, etc., please be sure to turn off the power rst to prevent electric
shock.
• When an unusual odor, sound or smoke comes out of the product, immediately disconnect the
power, then contact your nearest PATLITE Sales Representative.
Warning
Enforced
Prohibited
Caution
• When moving this product, please do not grasp by the Signal Tower portion of this product.
Be sure to carry it from the base of the unit, to prevent any cause of failure or trouble.
• Please place this product on a level surface, such as a desk etc.
• When installing it in high places, such as on top of a shelf, please use the rubber feet provided
as an accessory, along with adhesive tape, and a support base for the bottom of the body to
prevent it from falling.
• Do not expose it to high temperatures, such as near a re and do not use it in humid places.
Moreover, do not use this machine in locations where corrosive or combustible gas is present.
• If foreign substances, such as water, medicine; or metals, such as copper, low carbon steel wire,
fall into this product, please do not use it.
Possible cause of failure may occur.
• Do not disassemble or attempt to repair this product by any means. Failure to comply will
result in equipment damage or re.
• Do not bend the power supply cables or signal wires recklessly. Disconnection will result in this
machine breaking down.
• Do not install or run wiring near, or where equipment (such as solenoids, etc.) generate strong
electric or magnetic elds, or near any power lines. Failure to comply may result in malfunction
due to inductive noise.
• Do not place any part of this product (Body, AC Adaptor, Rubber Feet) where infants can reach
it. If it is swallowed accidentally, it could be detrimental. If it is suspected of being swallowed,
please consult an emergency medical center immediately.
Regarding the Trademarks or Registered Trademarks
• Microsoft, Windows, and Internet Explorer are registered trademark of the Microsoft Corporation of America,
Japan and other countries.
• Firefox is the trademark or registered trademark of the Mozilla Foundation of America and other countries.
• The company names and brand names written in this book are trademarks or registered trademarks of each
company.
4

Handling Cautions
This product is for indoor use only. Do not use it outdoors.
When installing this product, please avoid installation in the following places:
• Where its exposed to direct sunlight
• Where high temperatures, such as near re, or in a humid place
• Where drastic temperature and humidiy changes are present
• Where its exposed to an environment with poor ventillation
• Where its exposed to vibrations exceeding the specications
• Where its exposed to corrosive gas
• Where its exposed to a salty air environment
• Where its exposed to dust, iron powder, etc.
• Where its exposed to high concentrations of chemicals or oil mist
• Where its exposed to rain, or other types of wet environments
Maintenance and Inspection
►Cleaning
• When cleaning, be sure to disconnect the power before doing so.
• The cleaning of this product should be with a soft cloth and a neutral detergent (such as dish soap),
diluted with water and should be wiped lightly. Since it is easy to crack the surface of the product
when wiping with too much strength, please be careful.
• Do not wipe this product with volatile chemicals, or chemically treated dustcloth containing benzine,
thinner etc.
• Please do not wipe with a cloth containing too much moisture. If moisture gets inside the product, it
can cause short circuiting, electric shock, or re.
• Periodically remove dust from the electric socket to prevent a re hazard. By allowing dust to adhere
to the power supply terminal, it can be the result of re or failure from short-circuiting.
Intro
►Inspection
• Please check the following contents when inspecting this product.
Inspection Checklist Inspection Contents
Supplied Power Source Power Supply Voltage Tolerance Tolerable Voltage Range should be from AC 100 to 240V
Surrounding
Environment
Ambient Temperature Operating Temperature Range should be from 0 to 40oC
Ambient Humidity Operating Humidity Range should be 20 to 80% RH
Presence of Dust No dust should be accumulated
Product Checklist
Although our company takes all possible quality control measures to ensure proper packing of this product,
if there should be any missing items, please refer to the last page to contact your nearest PATLITE Sales
Representative.
• NH Series Main Unit (1 Body and 1 Stand)
• Quick Start Operation Manual (1 Sheet)
• Adhesive Seal (8 Sheets)
• Rubber Feet (4 Pieces)
• Support Base (1 Piece)
• AC Adaptor (1 Unit)
*The AC Adaptor for NHL-3FB1N-RYG is not enclosed.
5

Table of Contents
1 Product Outline 9
1.1 Outer Dimensional Drawing 9
1.2 Part Names and Functions 10
1.3 Model Number Conguration 10
1.4 General Specications 11
1.5 AC Adaptor Specications 11
1.6 Description of Functionality 12
1.6.1 Monitoring Function 12
1.6.2 Transmission Commands 12
1.6.3 Transmission Function Conguration 13
1.6.4 Setup and Updates 13
2 Installation Procedure and Flowchart 14
2.1 Network Signal Tower Flowchart 14
2.1.1 Manually Setting Up Network 14
2.1.2 DHCP Function Setup 15
2.2 Signal Tower Installation 16
2.3 Power Supply Input 17
2.4 LAN Connection 17
2.5 Network Setup 18
2.5.1 Logging In 18
2.5.2 Setting the IP Address 18
2.5.3 Setup Verication 19
2.6 Network Setup with the DHCP Function 20
2.6.1 Setup Method with the “TEST” Switch 20
2.6.2 Setup Method with the Web Setup Tool 20
2.7 Operation Settings 21
2.7.1 Setting the Clock 21
2.7.2 Normal Mode Setup 21
3 Functionality Details 22
3.1 Signal Tower Control Functions 22
3.2 Buzzer Control Functions 22
3.3 Test Functions 23
3.4 SNMP Function 23
3.4.1 SNMP SET Control Function for Signal-Tower 24
6

3.4.2 SNMP GET Status Acquisition Function for Signal-Tower 24
3.4.3 TRAP Reception Function 24
3.4.4 TRAP Transmission Function 24
3.5 PHN Command Reception Function 25
3.6 PNS Command Reception Function 27
3.7 E-mail Sending Function 29
3.7.1 E-mail Message Contents 29
3.8 RSH Command Function 30
3.8.1 RSH Commands 30
3.8.2 RSH Alert Timer Reset Function 32
3.9 Ping Monitoring Function 34
3.9.1 Ping Monitoring Function (Nodes 1 to 20) 34
3.9.2 Ping Monitoring Function (Nodes 21 to 24) 35
3.9.3 Ping Monitoring Function (“Clear” Command Outside Sources) 36
3.10 Application Monitoring Function 37
3.11 "Clear" Control Function 38
3.12 Normal Mode Settings 38
3.13 Reinitialization Function 38
3.14 Event Log Output Function 38
3.15 Conguration Data Save/Load Setup 39
3.16 Firmware Update Function 39
4 Function Setup 40
4.1 System Setup Screen 41
4.2 Clock Setup Screen 42
4.2.1 Synchronizing with the PC clock 43
4.2.2 Synchronizing with an NTP server 44
4.3 User Authentication Conguration Screen 45
4.4 SNMP Setup Screen 46
4.4.1 SNMP SET/GET 46
4.4.2 SNMP TRAP Transmission 46
4.5 Socket Communication Setup Screen 47
4.6 Mail Transmission Setup Screen 48
4.7 Message Contents Setup Screen 50
4.8 RSH Command Setup Screen 51
4.9 TRAP Reception Setup Screen 54
4.10 Ping Monitor setup Screen 57
4.10.1 Ping Monitor Conguration (Screen Numbers 1 to 20) 57
4.10.2 Ping Monitor Conguration (Screen Numbers 21 to 24) 59
7
4.11 Application Monitor Setup Screen 61
4.12 "Clear" Control Setup Screen 64
4.13 Normal Mode Setup Screen 65
4.14 Test Button Setup Screen 66
4.15 Output Control Setting for Signal Tower Screen 67
4.16 Reinitialization Setup Screen 68
4.17 Reboot Screen 69
4.18 Event Log Screen 70
4.19 Conguration Save/Load Setup Screen 71
4.20 Firmware Update Screen 72
4.21 Setup Table Entry Screen 73
5 MIB 74
5.1 MIB Denition List 74
5.2 PATLITE MIB SPECIFICATIONS 75
6 Replacement and Option Parts 77
6.1 Replacement Parts 77
6.2 Signal Tower Unit Color Arrangement 78
6.2.1 NHL Signal Tower Unit (Color) Rearrangement Method 78
6.3 Option Parts 79
6.3.1 Wall Mount Bracket 79
6.3.2 Partition Mounting Bracket 80
7 Troubleshooting 82
8 Freeware Terms of Agreement 83
8.1 GNU GENERAL PUBLIC LICENCE 83
8.2 GNU LESSER GENERAL PUBLIC LICENSE 88
8.3 NET-SNMP 90
8.4 BSD LICENCE 93
Revision History 94
8
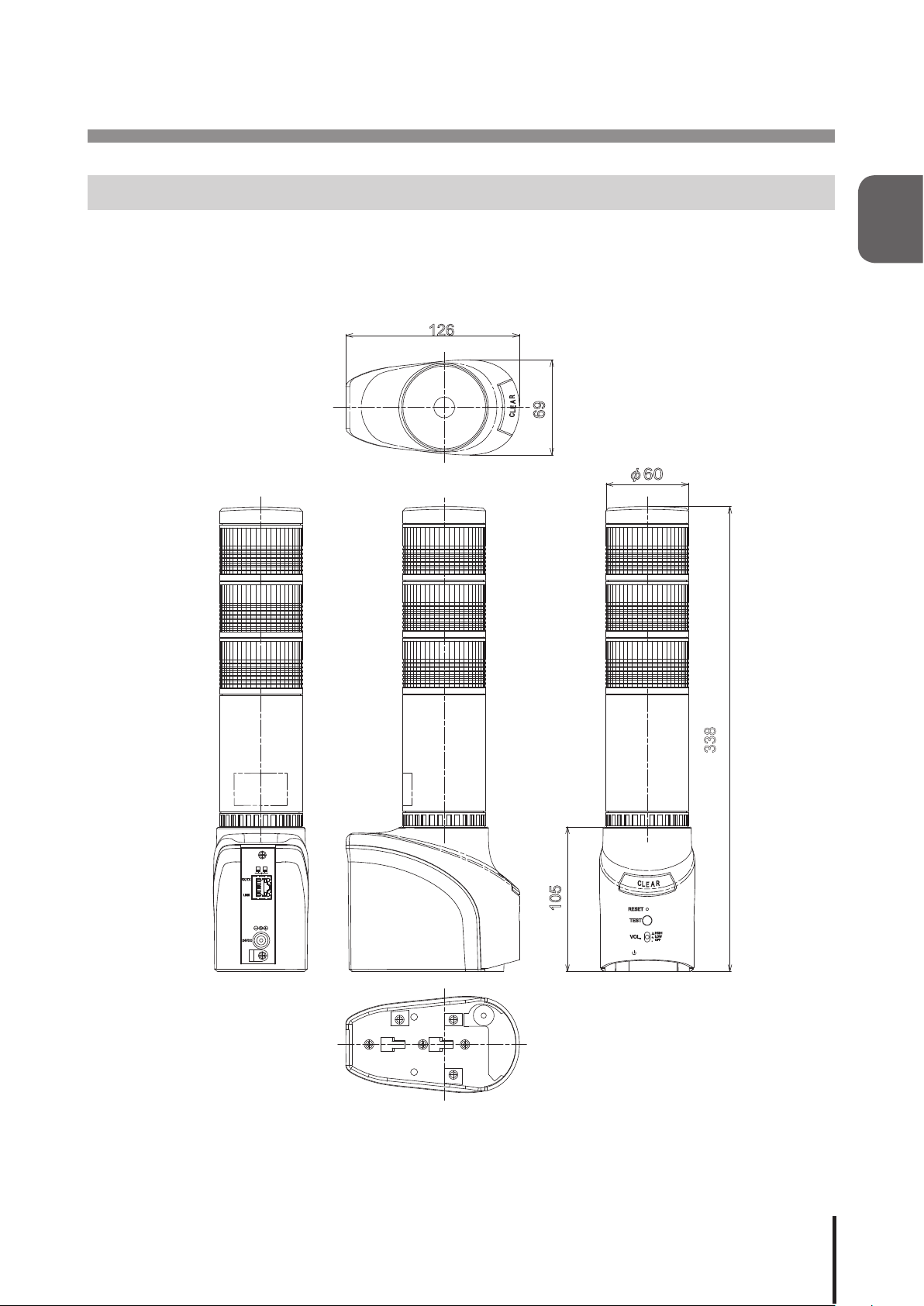
1 Product Outline
φ60
126
338
NHL-3FB1□-RYG
69
105
1.1 Outer Dimensional Drawing
1
Outer Dimensional Drawing
9
1
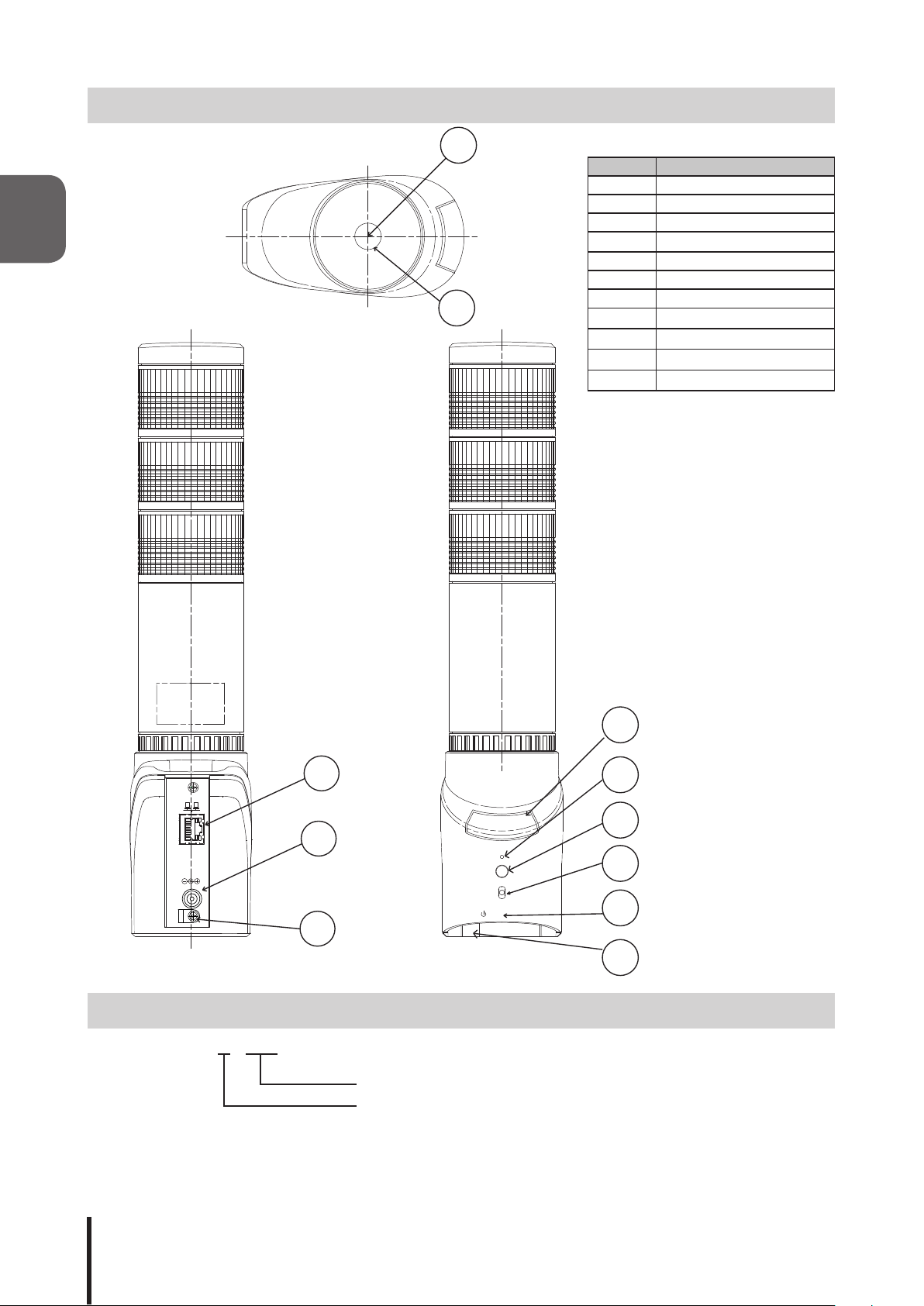
1.2 Part Names and Functions
7
R
C
8
Number Name
1 CLEAR Switch
2 RESET Switch
A
E
L
3 TEST Switch
4 Volume Level Switch
5 Status LED
6 Buzzer Diaphram
7 Center Shaft
8 Cover Seal
9 LAN Connector
10 Power Outlet
11 Power Cable Clamp
9
RX/TX
24VDC
LINK
10
C
TEST
VOL.
11
1.3 Model Number Conguration
NHL
-
3FB1
□ -
RYG
RYG
: LED units are in order from top to bottom of red, yellow, and green
U: AC Adaptor Included N: AC Adaptor not Included
1
2
R
L
A
E
3
4
HIGH
LOW
OFF
5
6
10

1.4 General Specications
Item Specication
Model NHL-3FB1U-RYG NHL-3FB1N-RYG
Rated Voltage (Body) DC24V
AC Adaptor Rated Voltage AC 100V to 240V ―
AC Adaptor Operating Voltage Range
Power Consumption
Operating Temperature Range 0oC to 40oC (No Condensation)
Storage Temperature Range -10oC to 60oC (No Condensation)
Relative Humidity from 20 to 80% RH (No Condensation)
Insulation Resistance More than 1MΩ at DC500V between the terminals and the chassis
Withstanding Voltage
EMI Noise Characteristics AC1000Vp~p Pulse Width: 1μsec
Vibration Resistance 19.6m/s
Sound Level
Buzzer Sound Three-position adjustable switch for "HIGH", "LOW" and "OFF"
Signal Tower NHL:φ60 Type Clear Globe
"CLEAR" Switch Pushbutton Switch
"RESET" Switch Tact Switch
"BUZZER" Switch Slide Switch
Communication
Method
Mounting
AC Adaptor not included)
(
Protection Rating IP2x
Accessories
Ethernet
Location Indoors Only
Direction Desktop or wall-mount in the upright position
Mass
Body Red Amber Green Blue White Buzzer
2.0W 1.5W 1.5W 0.8W 0.8W 0.8W 2.0W
AC1000V and less than 10mA applied for 1 minute between the terminals and
Distance from buzzer diaphram (Upright Position) of 1m and "A" balance)
(
AC Adaptor, Rubber Feet, Adhesive Seal,
AC 90V to 264V ―
chassis without breaking insulation
2
HIGH: 80dB or more / LOW: 70dB or less
Physical Layer: 10BASE-T/100BASE-TX
Auto-negotiation/ Full Duplex/ Half Duplex
(
Data Link Layer: CSMA/CD
Network Link Layer: IP・ARP・ICMP
Transport Layer: TCP・UDP
Application Layer: HTTP・RSH・SMTP・SNMP
POP・DNS・Socket・NTP・DHCP
800g
Rubber Feet, Adhesive Seal, Support
Support Base
1
)
・
Base
Please
When there is no "Auto-negotiation" on the HUB side, sometimes communication is inoperable.
1.5 AC Adaptor Specications
When ordering an AC Adaptor separately, use the following specications. Since the voltage output of AC
Adaptors drop when there is insufcient current (example: unregulated transformers, etc.), be sure to use an
output current rating above the recommended rating. Failure to comply may result in failure of this product.
Be sure to use AC Adaptors with built-in regulation systems to ensure a regulated output voltage (switching
power supplies, etc.)
[Recommended AC Adaptor Specications]
DC Secondary Output
Voltage : 24V DC ±5%
Current : 0.75A to 1A max
Plug Length : 9.5mm
Plastic Housing : 11mm dia.
Plug Connector Outer Diameter : 5.5mm dia.
Plug Connector Inner Diameter : 2.1mm dia.
9.5
φ5.5
+
φ2.1
φ11
-
11

1
1.6 Description of Functionality
The following explains the functionality featured in this product.
1.6.1 Monitoring Function
This product can monitor the connectivity of a network device.
PING
MONITOR
Monitors "keepalive" Network/Device signals
The Ping Monitor can monitor the connectivity for a
maximum of 24 nodes with this product. If the monitor
cannot obtain a response due to an abnormality in the
circuit or equipment in the node, it judges an abnormal
state and the Signal Tower warns a supervisor with
light and sound.
Among the 24 nodes, four
nodes (21st to 24th) can
be set up for more detailed
monitoring parameters.
With a user's creation of adding an application utilizing
the transmission command, monitoring of the operating
circumstances is possible. (Maximum of 4 nodes)
SNMP
v1 v2c
Low-cost Monitor networking equipment.
A network monitor Signal Tower can tell an
administrator about generated abnormalities and
hindrances promptly as an SNMP command to
respond with light and sound to an SNMP TRAP from
the equipment (UPS, a printer, a router, a switch,
etc.) via the network.
•
It can distinguish the
variable bindings.
•
The registration of 16 groups (4
nodes per group) is possible.
SELF DIAGNOSIS
It is possible without control from the network, to
instead use the test switch on the front of the product
to check the functions of the Signal Tower and buzzer.
1.6.2 Transmission Commands
RSH
It is controllable by the exible RSH
protocol.
With network integrated management
software and various event monitoring
tools, it is possible to trigger lighting,
ashing, buzzer sound, and buzzer
sound synchronized with the Signal
Tower lights.
Event Occurance: Command Execution (Lighting Tier, Sounding Buzzer)
RSH Example: rsh 192.168.10.1 -l root alert 111001
Event Occurance: Command Execution (Lighting Tier, Sounding Buzzer)
PNS Example Code: 58H,58H,53H,00H,00H,06H,01H,01H,01H,00H,00H,01H
SOCKET
Compatible with PHN Commands.
The Signal Tower and buzzer are controllable
by a 2 byte command.
* Compatible with the NHE-3 FB, NHC-3
FB, NHM-3 FB and PHN-3FBE1.
* Some functions are limited.
Event Occurance: Command Execution
(Flashing Tier Lights, Buzzer Sound)
PHN Example Code: 57H,17H
The commands are compatable with the new PNS.
The Signal Tower and buzzer are controllable through the PNS
command. All the different patterns are controllable.
TRANSMISSION
12
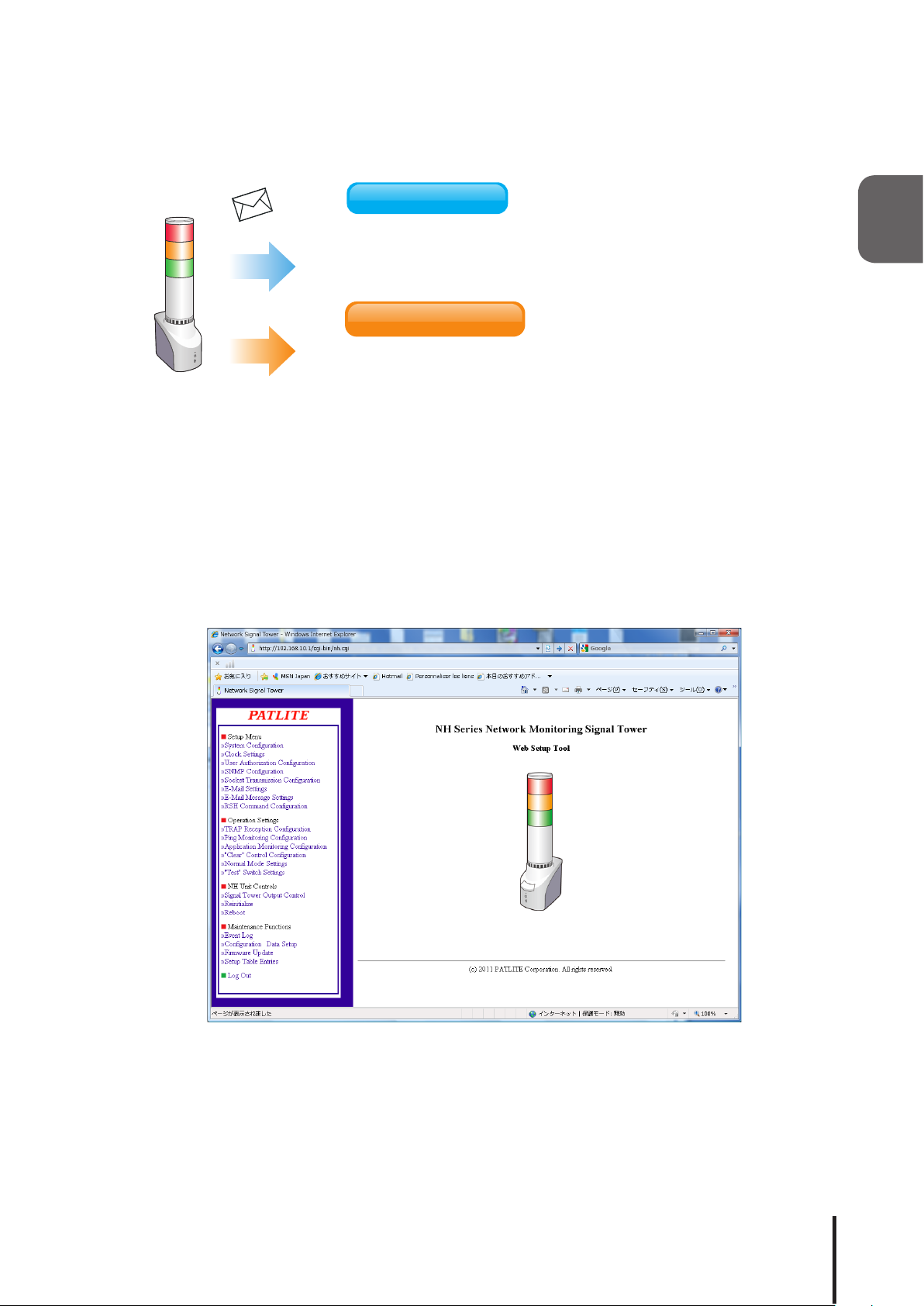
1.6.3 Transmission Function Conguration
An E-mail and TRAP transmission can be sent at the time of an event occurance.
E-mail
E-mail
Send to a maximum of 8 selectable addresses
A subject title and the text corresponding to the subject title
can be created for the occured event.
It uses the authentication protocol for POP and SMTP.
SNMP
Transmission
v2c
SNMP TRAP Transmission
The transmission can send an e-mail to a maximum of eight
selectable addresses.
1.6.4 Setup and Updates
With a web setup tool, a detailed setup containing the IP Address of the product can be arranged. The rmware
can also be upgraded remotely.
Fig. 1.6.1 Web Setup Tool Screen
1
13
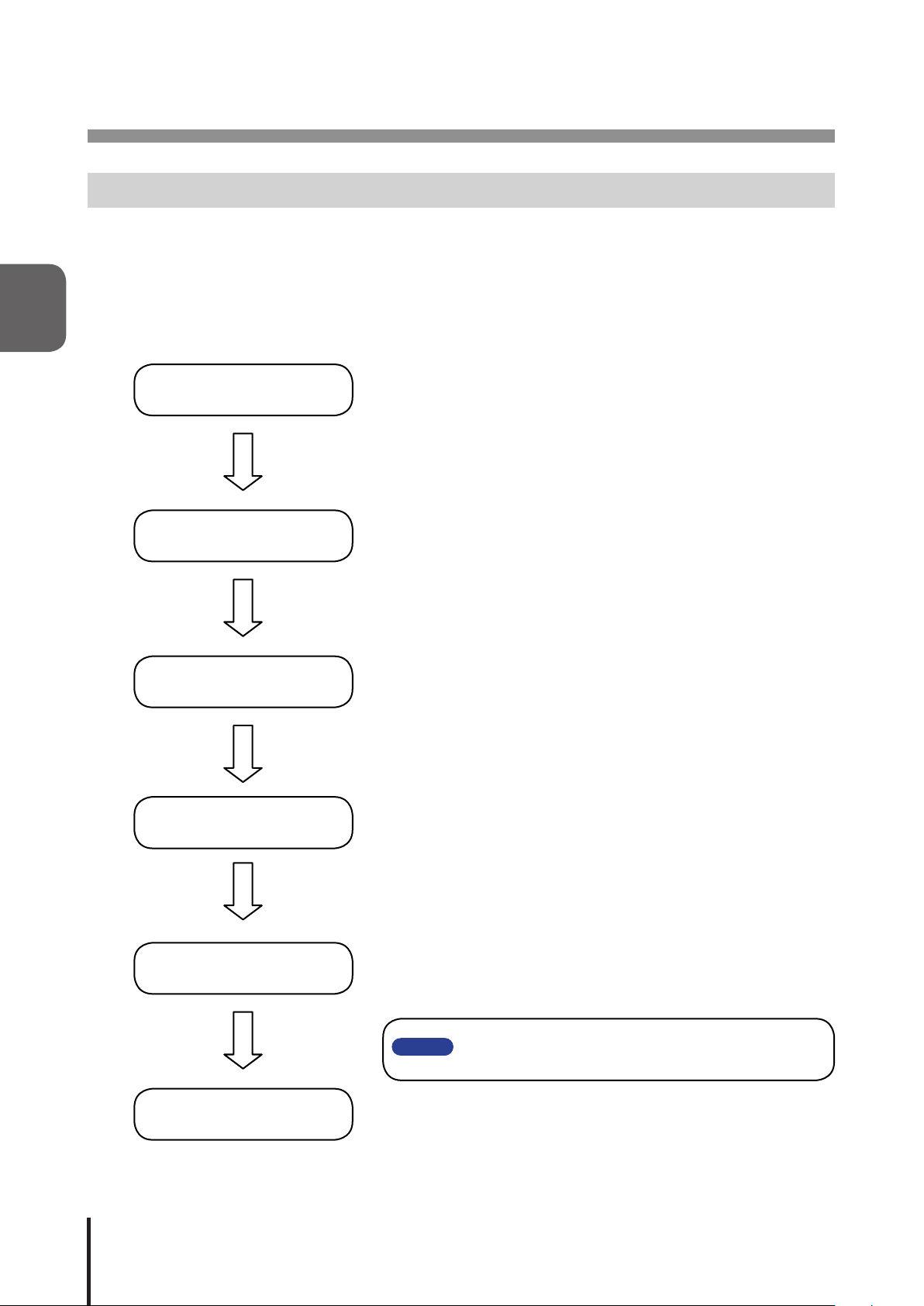
2
2 Installation Procedure and Flowchart
2.1 Network Signal Tower Flowchart
The Signal Tower offers two methods for conguring the network, "Manual Network Setup", and "Automatic Network
Setup", which uses the DHCP server function.
2.1.1 Manually Setting Up Network
Please install this product on a level surface. If necessary, use the
Signal Tower Installation
Power Supply Input
accessories (rubber foot, adhesive seal, support base) if needed
when installing.
Connect the AC Adaptor to this product Using the cable clamp will
prevent the power cord from being unintentionally pulled out. (Refer
to 2.3 "Power Supply Input")
LAN Connection
Network Setup
Operation Settings
Connect the LAN cable to this product.
Set up the network environment conguration. Refer to on how to
setup the network.
Set up the detailed settings after the network environment has
been congured
Please
Aftercompletingthedesiredsetupconguration,rebootthis product
by pressing the "reset" button, or removing the power for a few
seconds and reapplying it for the changes to take effect.
14
Start-up
This product is now ready to be used.
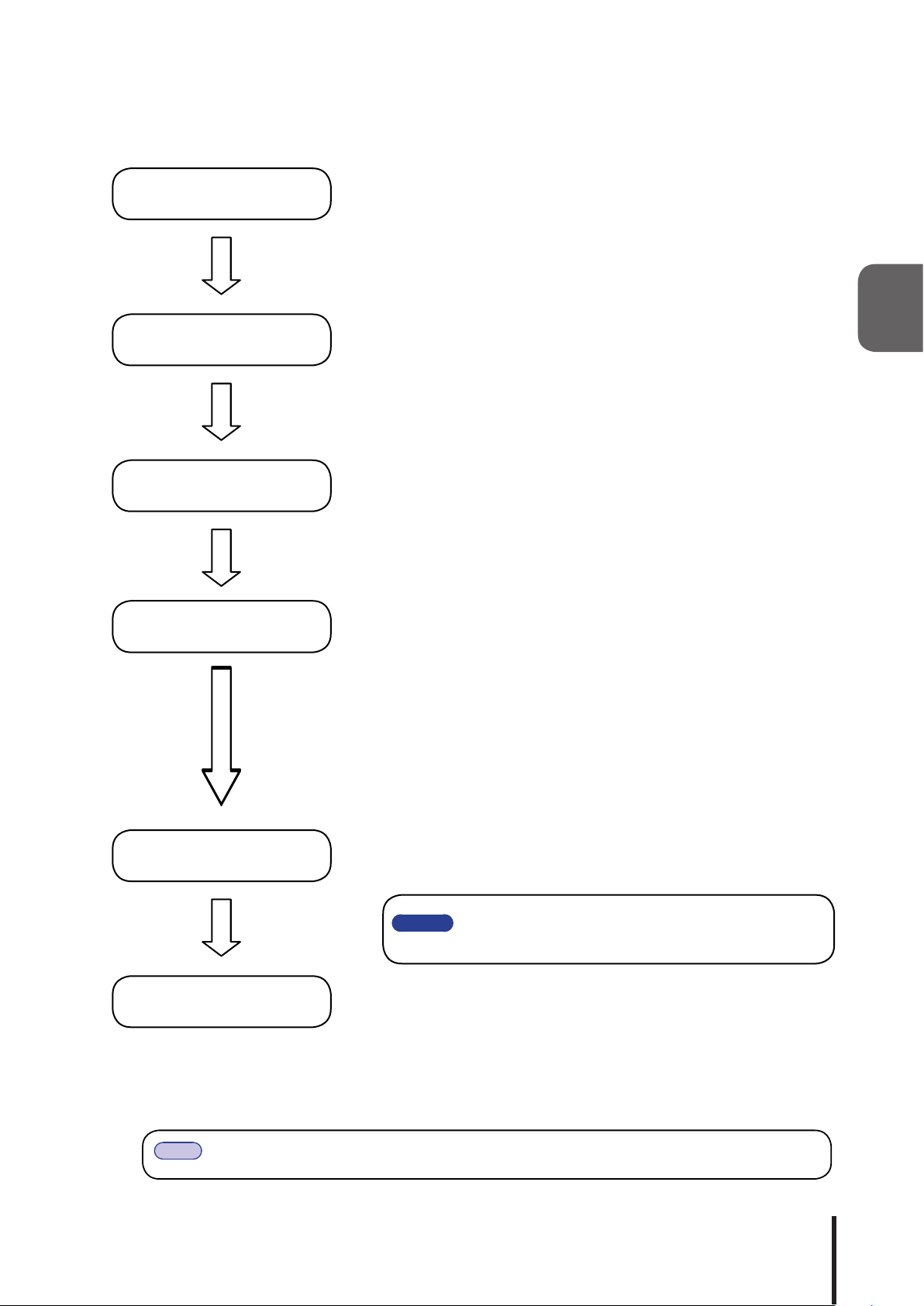
2.1.2 Automtically Setting Up Network
Please install this product on a level surface. If necessary, use the
Signal Tower Installation
accessories (rubber foot, adhesive seal, support base) if needed
when installing.
Power Supply Input
LAN Connection
DHCP Setup
Set the volume level switch to "LOW", then push the "TEST" switch
while inserting the AC Adaptor plug into the power outlet. Use the
cable clamp to prevent the power cord from being unintentionally
pulled out. (Refer to 2.3 "Power Supply Input")
Connect the LAN cable to this product.
If this product is unable to connect with a DHCP Server, the Signal
Tower status will start using the ashing pattern2 on all LED units,
then will use the factory default network information set at the
time of shipment. If that condition occurs, then either try again
to connect with a DHCP Server, or manually set up the network.
Re fer t o "2. 5 Net work Setup" o n how to se tup t he network
manually. If this product is able to connect to a DHCP Server, in
order to know the network information, it is recommended to use
Patlite's "PNS Manager" software for the NH Series.
2
Operation Settings
Start-up
Note
Once the DHCP function is working, it will automatically start up the next time the product is
turned on, or rebooted.
Set up the detailed settings after the network environment has
been congured
Please
This product is now ready to be used.
Aftercompletingthedesiredsetupconguration,rebootthis product
by pressing the "reset" button, or removing the power for a few
seconds and reapplying it for the changes to take effect.
15
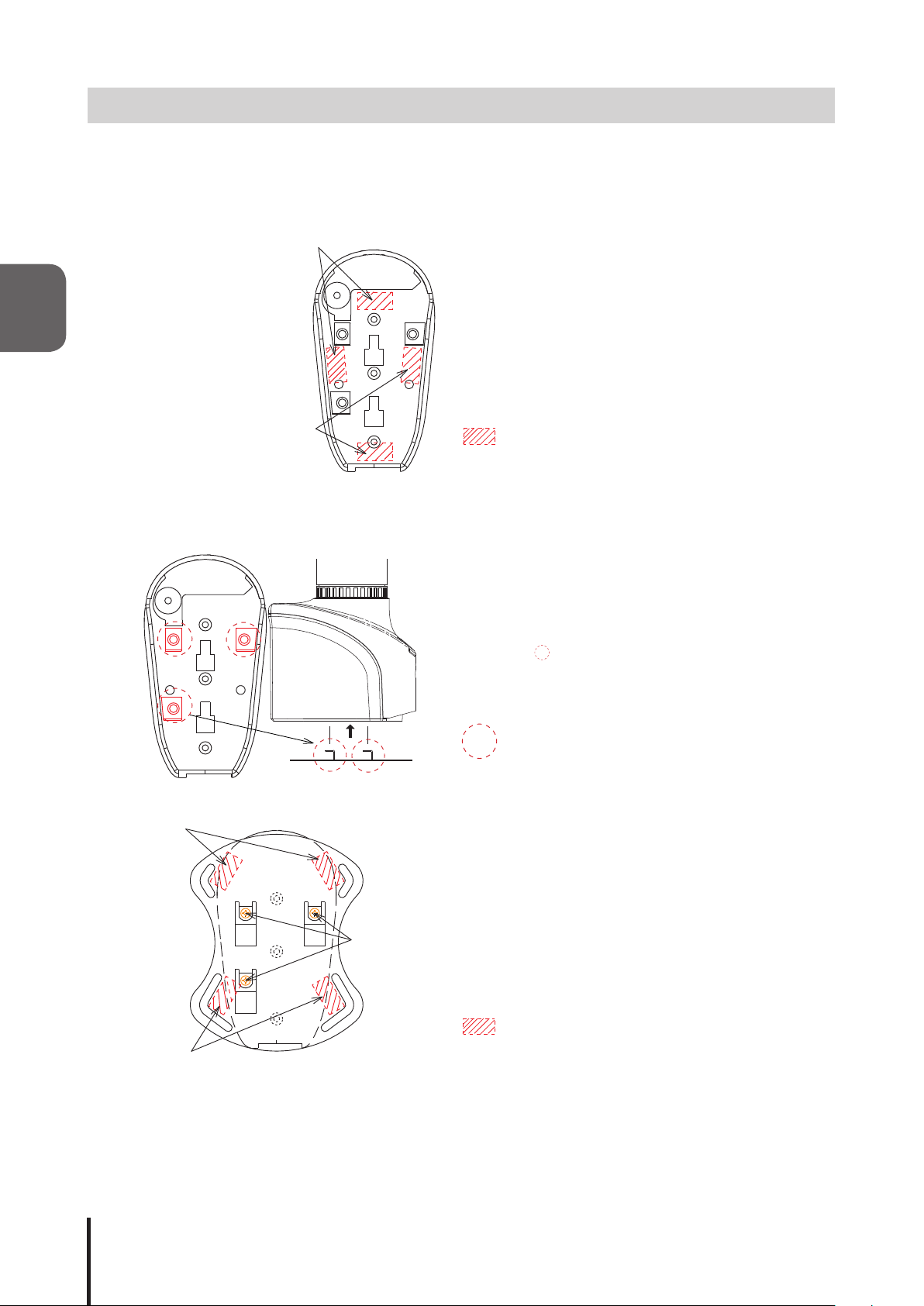
2.2 Signal Tower Installation
This product is to be intalled on a level surface. Also, use the included accessories (rubber feet, adhesive seal,
support base) when needed during installation.
Installation Example 1: Rubber Feet to prevent from sliding on a at and slippery surface
2
Attachment Area
[Installation]
Strip off the adhesive backing and stick the adhesive
seal or rubber feet in the shaded area, indicated on the
gure to the left.
Attachment Area
Adhesive seal or rubber feet attachment area
Installation Example 2: Increasing surface area for a sturdy surface (before adding adhesive seals or rubber feet)
[Installation]
1. Support Base is attached to the part indicated by the
circle " ".
Attachment Area
Attachment Area
Clamp with
3 screws
Support Base attachment area
2. Secure the Support Base with screws.
3. Use an M4 screw (or M4 bolt, etc.) to attach the
Support Base onto the installation surface and tighten
it with M4 nuts.
Adhesive seal or rubber feet attachment area
16
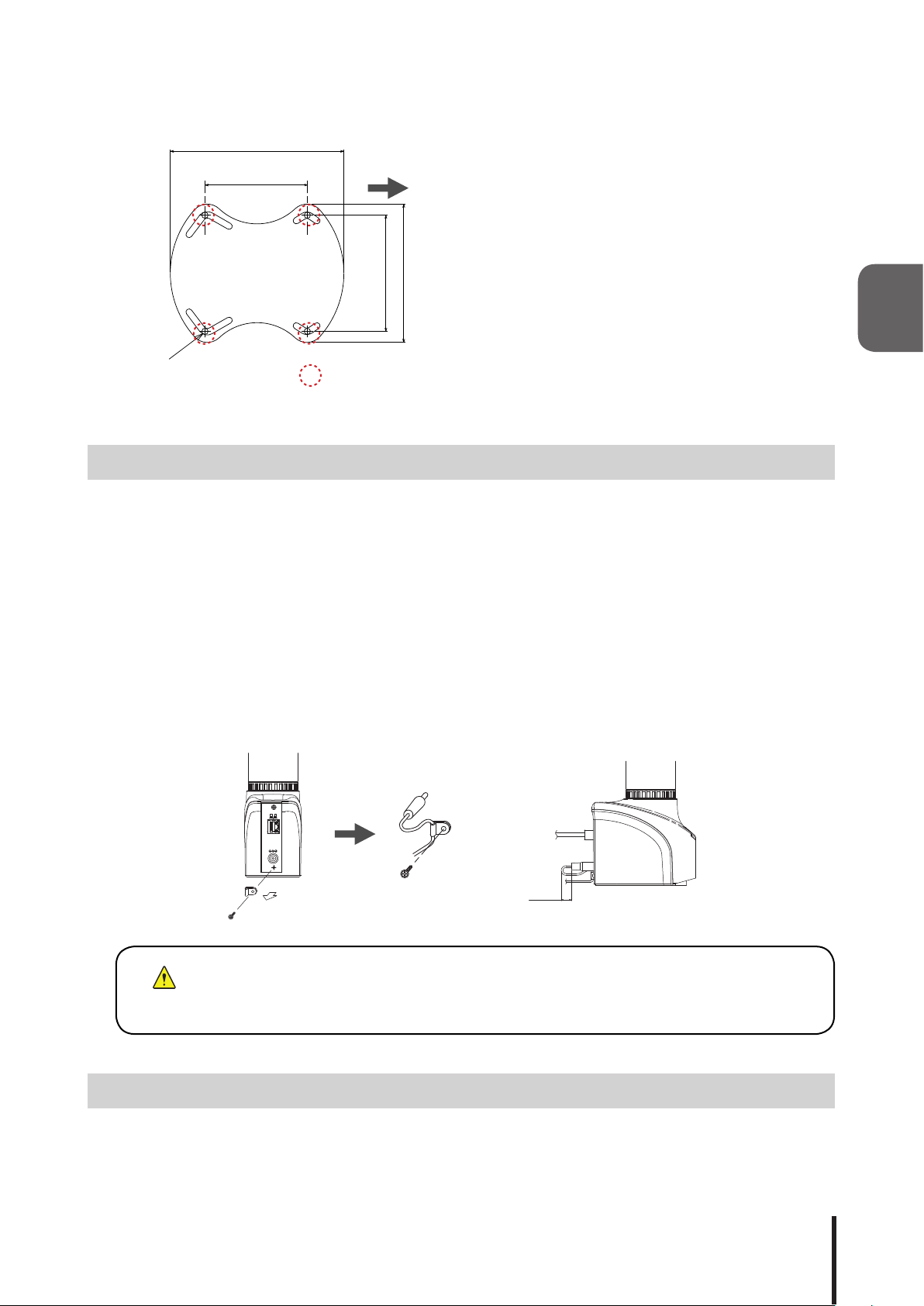
Installation Example 3: Permanent Surface Installation (screw-support base)
125.5
[Installation]
Front Direction of Product
74
1. Drill holes with a diameter of 4.5mm onto a flat
surface to install.
2. Afx the Support Base accessory to this product.
Please do not attach the rubber feet or adhesive
84
100
※
seals when clamping the Support Base with screws.
3. Use an M4 screw (or M4 bolt, etc.) to attach the
Support Base onto the installation surface and
4-φ4.5
tighten it with M4 nuts.
Location for
tapping 4.5mm
holes
2.3 Power Supply Input
Attach the power plug for this product in accordance with the gure below. This product requires at least 30
seconds for the boot-up sequence to complete.
[Power Plug Mounting Instruction]
2
1. Remove the clamp for the power cable.
2. Pass the power cable through the clamp.
3. Insert the power plug into this product.
4. Screw the clamp down to tighten it, and ensure enough slack (about 15mm) has been given to the power
cable.
5. When power is supplied to this product, the lights will all turn on for about 1 second.
Fig. 2.3.1 Power Cable Mounting Diagram
RX/TX
LINK
24VDC
(15)mm
• Periodically check whether dust builds up on the electric socket and clean it if dust builds up.
Ensure maintenance is performed to avoid dust build-up, because it may result in re if too much
Warning
dust is allowed to build up.
• Do not touch the electric socket with wet hands. Failure to comply will result in electric shock.
2.4 LAN Connection
Connect the LAN cable to this product. Use either a catagory 5 LAN cable, or twisted-pair cable (UTP or
STP) for this application.
17
2.5 Network Setup
The IP address at the time of factory shipments for this product is
To change the IP address, rst log in from a personal computer (henceforth, written as “PC”) web browser to
access the settings for it.
192.168.10.1
.
2
Note
The recommended browser should be equivalent to or higher than Internet Explorer 6
or Firefox 3.5.
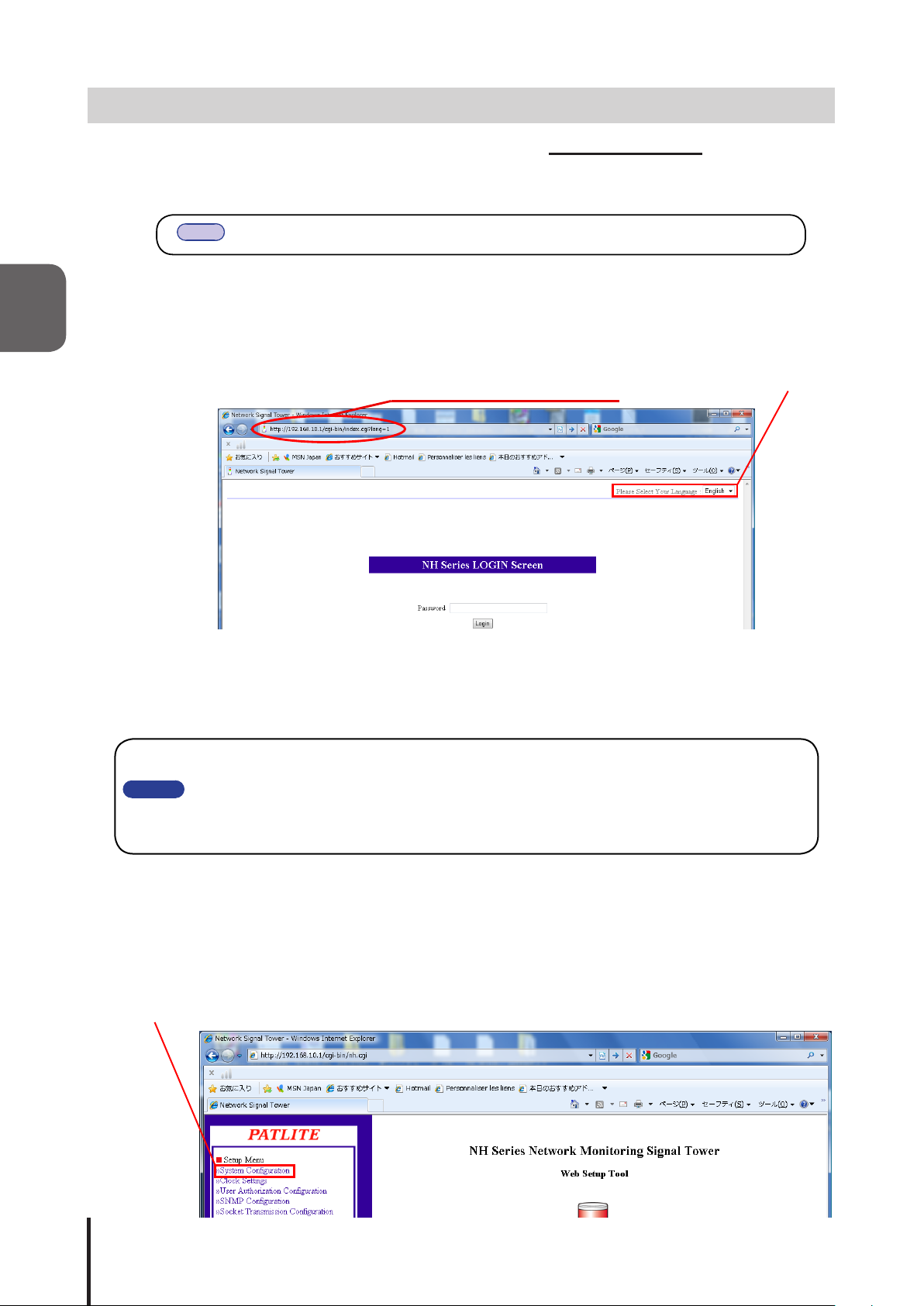
2.5.1 Logging In
By logging in from a web browser, access can be made to various setups for this product.
In order to log in, the current IP address for this product needs to be entered into the address part of the web
browser. (Refer to Fig. 2.5.1)
Fig. 2.5.1 Login Screen
<Web Browser Address Input> http://192.168.10.1/index.htm
When the login screen is displayed, go to the upper right of the screen where "Please Select Your Language" is
located to select the preferred language. Enter "patlite" in the password eld, then click the "Logging In" button.
The default password is set to “patlite.” Please be sure to change the password to prevent any security breaching.
Select Language
• If 10 minutes or more of no activity has elapsed after logging in, a time-out causes an
automatic log out. When that occurs, please log in again.
Please
• If garbled characters occur and the screen is not displayed normally, change the character
code for Unicode (UTF-8) to correct it.
• To prevent from being setup in two or more places, this product does not support double-
login capabilities. To log in from another location, be sure the last computer is logged out.
2.5.2 Setting the IP Address
After logging in, a web setup tool screen will be displayed (Refer to Fig. 2.5.2). The set up item list is displayed
on the left-hand side of the screen.
Click "System Conguration" to display the system setup screen.
Fig. 2.5.2 Web Setup Tool Screen
Click "System Conguration"
18
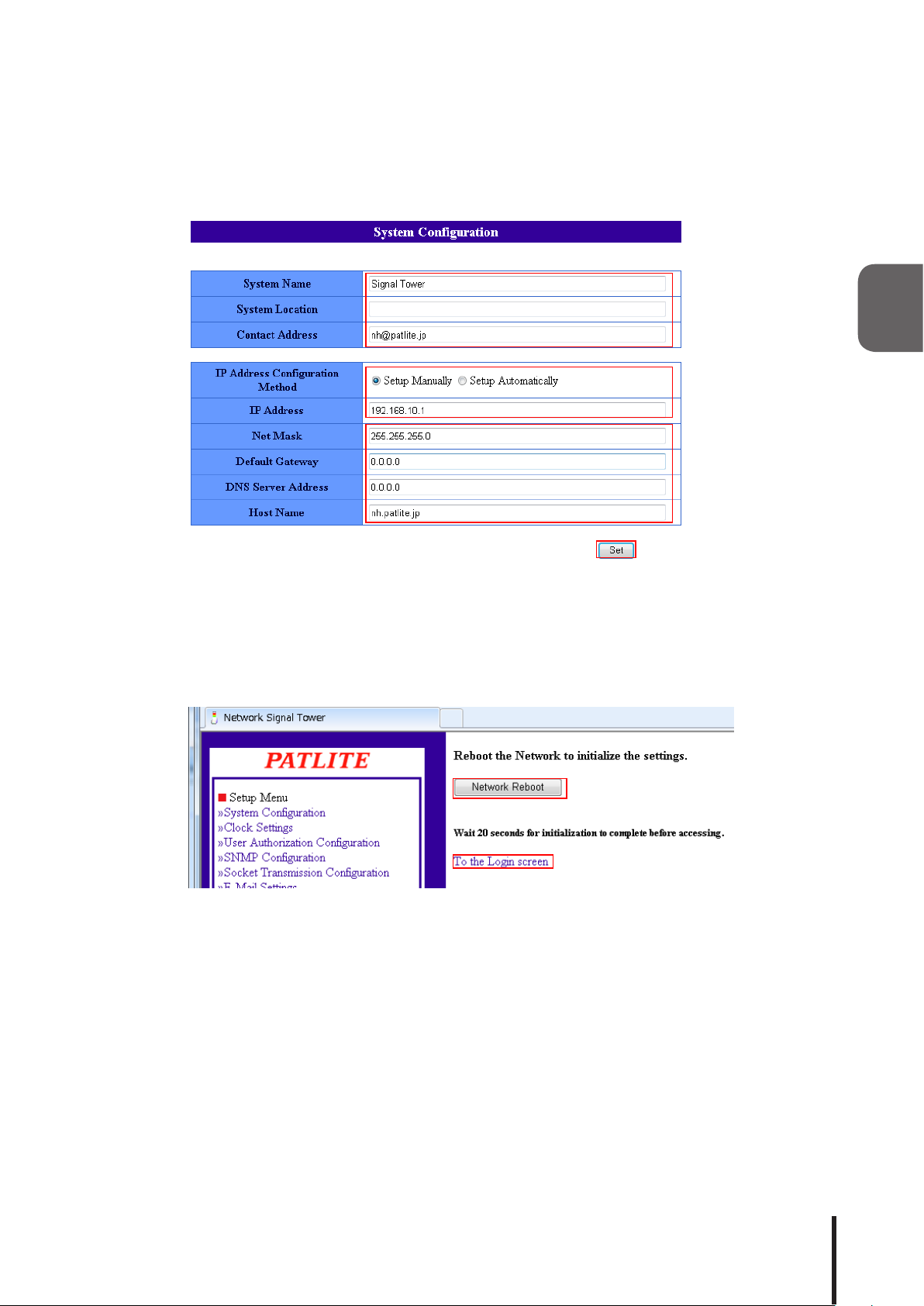
The network protocol can be changed on the system setup screen.
[Setting Method]
1. Please enter the new IP address for this product.
2. Set up the net mask, default gateway, etc. if needed.
3. After the changes are completed, click the "Set" button for the changes to take effect.
Fig. 2.5.3 System Setup Screen (for Manual Setup)
②
①
②
③
4. After the "Set" button has been clicked, then when the Network Reboot Screen is displayed, click the
"Network Reboot" button for the changes to take effect (Refer to Fig. 2.5.4).
5. The execution of the network setup changes takes about 20 seconds. After the waiting time elapses, click
"To the Login screen" to log back in (Refer to Fig. 2.5.1).
Fig. 2.5.4 Network Reboot Screen
2
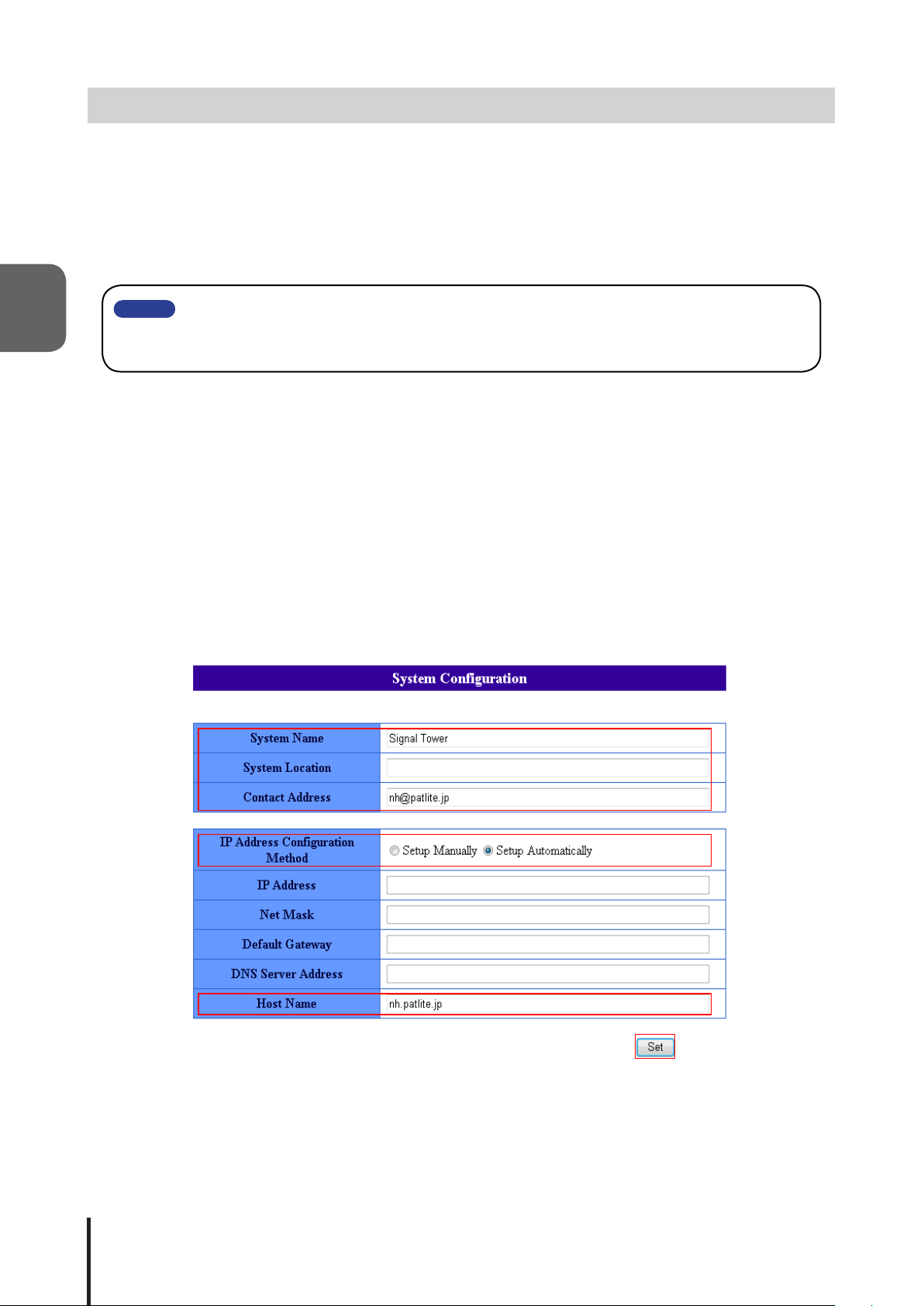
2.5.3 Setup Verication
If the web browser address is reflecting the changed value of the IP address after clicking "To the Login
screen", the setup of the new IP address has been successful. However, in cases where the preset value of
other networks had been changed, be sure to enter the proper IP Address value where it was moved to in order
to verify it in the system setup screen.
④
⑤
19
2.6 Network Setup with the DHCP Function
This product can access a DHCP Server to acquire network information.
2.6.1 Setup Method with the “TEST” Switch
1. First, connect this product with the network environment to be used. (Refer to Fig. 2.5.3)
2. Set the volume level switch to "LOW" before applying power to this product.
3. Push the "TEST" Switch while inserting the power connector into the power outlet.
4. The DHCP function takes effect when this product starts up.
2
Please
If this product is unable to access a DHCP Server, it will return to the factory default network
information. When the DHCP function is used, any future connections are started after the
DHCP function setup is activated. When it is necessary to use the manual settings, please use
the Web Setup Tool and our PNS Manager software tool.
2.6.2 Setup Method with the Web Setup Tool
1. Select the IP Address Setup Method in the "System Conguration" screen as "Setup Automatically."
(Refer to Fig. 2.6.1)
2. Setup the device and host name, etc. as needed.
3. Click the "Set" button to save all changes and to activate them.
4. After the "Set" button is clicked, the Web Setup Tool changes to another screen to reboot the product; click
the "Network Reboot" icon to continue. (Refer back to Fig. 2.5.4)
5. Rebooting the network takes about 20 seconds.
Fig. 2.6.1 System Setup Screen (for DHCP Automatic Setup)
②
①
②
③
20

2.7 Operation Settings
2.7.1 Setting the Clock
The clock for this product can be set up. For setting the clock on this product, the following are two methods.
► Communicates with the PC clock to adjust the time when logging in.
► Communicates with an NTP server to adjust the time for this product.
Refer to "4.2 Time Setup Screen" for details on setting the time.
Please
If the power supply is not applied for more than a day and a half, the generated time may be
cleared or delayed, and the clock should be reset again.
2.7.2 Normal Mode Setup
The normal state of operation of this product can be displayed by using the "Normal Mode" setup. When this
product is in its normal state of operation, the condition, such as the Green LED in the "ON" condtion, can be
indicated on the Signal Tower, once the setup is complete.
Refer to "4.13 Normal Mode Setup Screen" for setting up the "Normal Mode" operating status of this product."
Note
If the normal operating condition does not require any status lights to stay on, then there is
no need to set this parameter up.
2
21
3
3 Functionality Details
This section explains the available functions of this product, and their differences by the timing charts indicated
below.
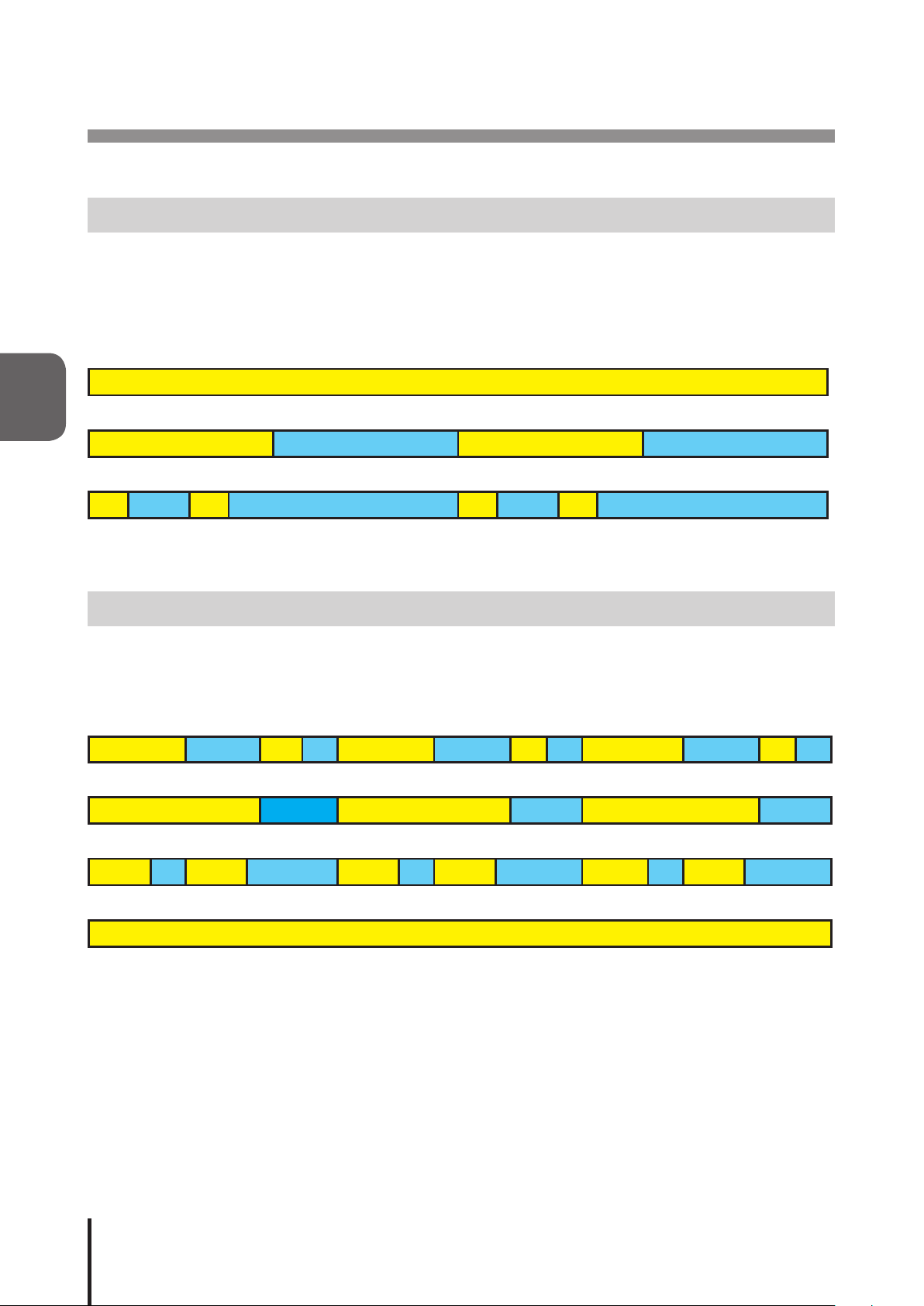
3.1 Signal Tower Control Functions
Three kind of operating patterns for the LED Signal Tower is available, such as continuous lighting, ashing
pattern1, and ashing pattern2.
Continuous “ON”
ON
Flashing Pattern1 [Repetitive 500ms “ON”; 500ms “OFF”]
ON OFF ON OFF
Flashing Pattern2 [Repetitive 80ms “ON”, 170ms “OFF”, 80ms “ON”, 170ms “OFF”; 500ms “OFF”]
ON OFF ON OFF ON OFF ON OFF
3.2 Buzzer Control Functions
Four kind of buzzer sounds, such as; buzzer pattern1, buzzer pattern2, buzzer pattern3, and buzzer pattern4,
are available to distinguish a variety of conditions with the use of audible and visual warnings.
Buzzer Pattern1 [Repetitive 250ms “ON”; 250ms “OFF”]
ON OFF ON OFF ON OFF ON OFF ON OFF ON OFF
Buzzer Pattern2 [Repetitive 500ms “ON”; 500ms “OFF”]
ON OFF ON OFF ON OFF
Buzzer Pattern3 [Repetitive 200ms “ON”, 50ms “OFF”, 200ms “ON”; 550ms “OFF”]
ON OFF ON OFF ON OFF ON OFF ON OFF ON OFF
Buzzer Pattern4 [Continuous “ON”]
ON
22
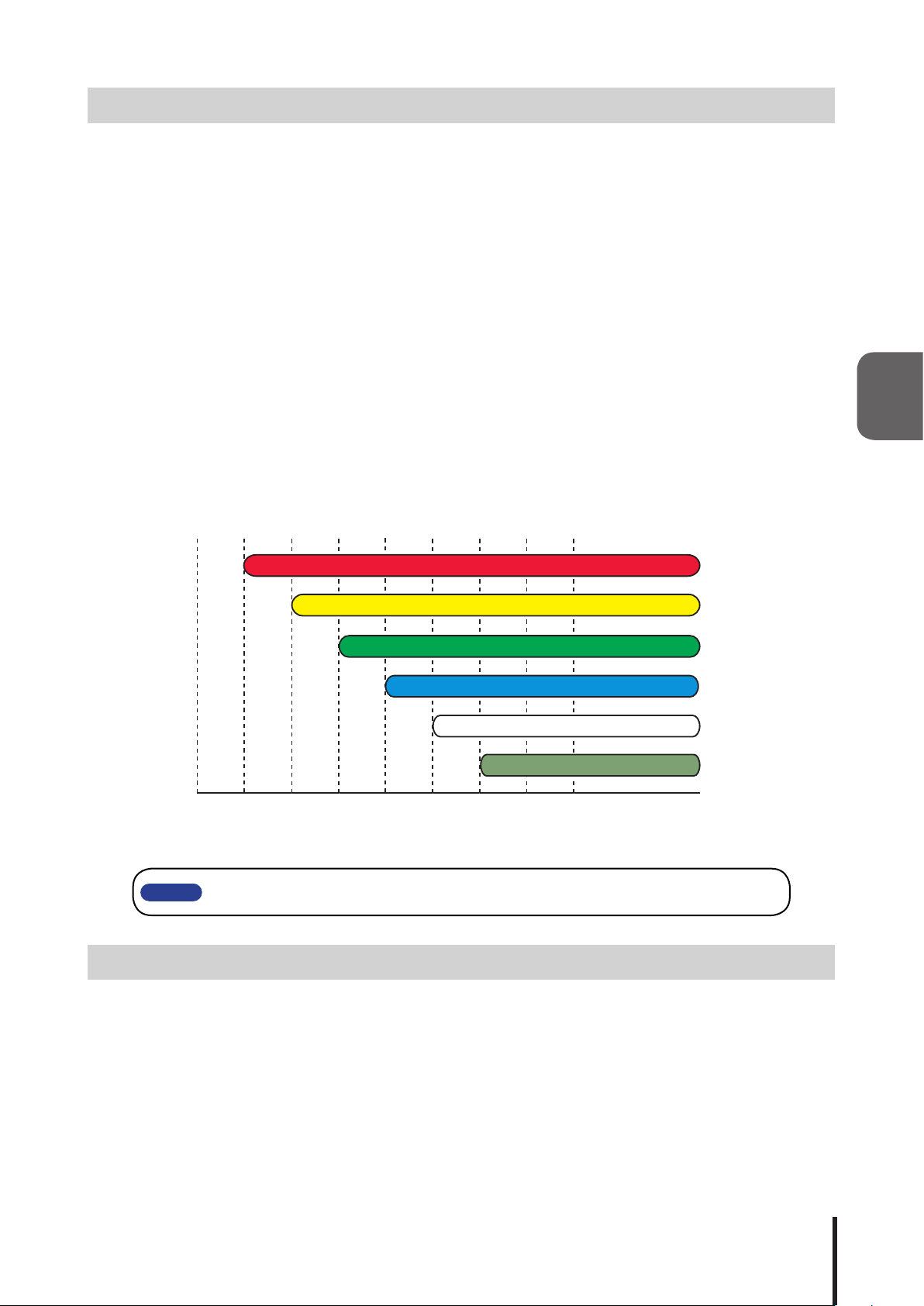
3.3 Test Functions
The test function does a sequential check of the Signal Tower and buzzer, as well as checking other
operations. The test operation lights up the tower lights and buzzer every second in steps; in the order of red,
yellow, green, blue, white, and buzzer. When only a three-tiered Signal Tower is in use, a time delay between
the third tier and buzzer sound will occur. Stopping the test operation can be performed 7 seconds after
execution, when the buzzer test is complete (it takes about 1 second).
[Test Function Starting Method]
When the Test Button is Depressed
•
When the "test" or "dotest" Commands are Received by the RSH
•
[Test Function Stopping Method]
When the CLEAR Switch is Depressed
•
When the RSH receives a "Clear" or "Doclear" Command
•
From an SNMP "Clear" Command
•
From the Web Setup Tool of the Signal Tower Operation Screen
•
From a PNS Command sending a Clear Command Transmission
•
Fig. 4.3.1 Detailed View of Test Operation
3
Signal Tower Red
Signal Tower Amber
Signal Tower Green
Signal Tower Blue
Signal Tower Clear
Buzzer Sound Pattern1
0 1 3 4 5 7
Please
During the test operation, this product stops receiving everything else except the Ping
monitoring application.
....
Time (sec)62
3.4 SNMP Function
This product can control the Signal Tower, and acquisition the status and TRAP reception using the SNMP
functions. For customers who purchased this product, Please download the MIB le for use with the SNMP
functions. Furthermore, for details on the setting method of this product, refer to “4.4 SNMP Setting Screen”.
23
3
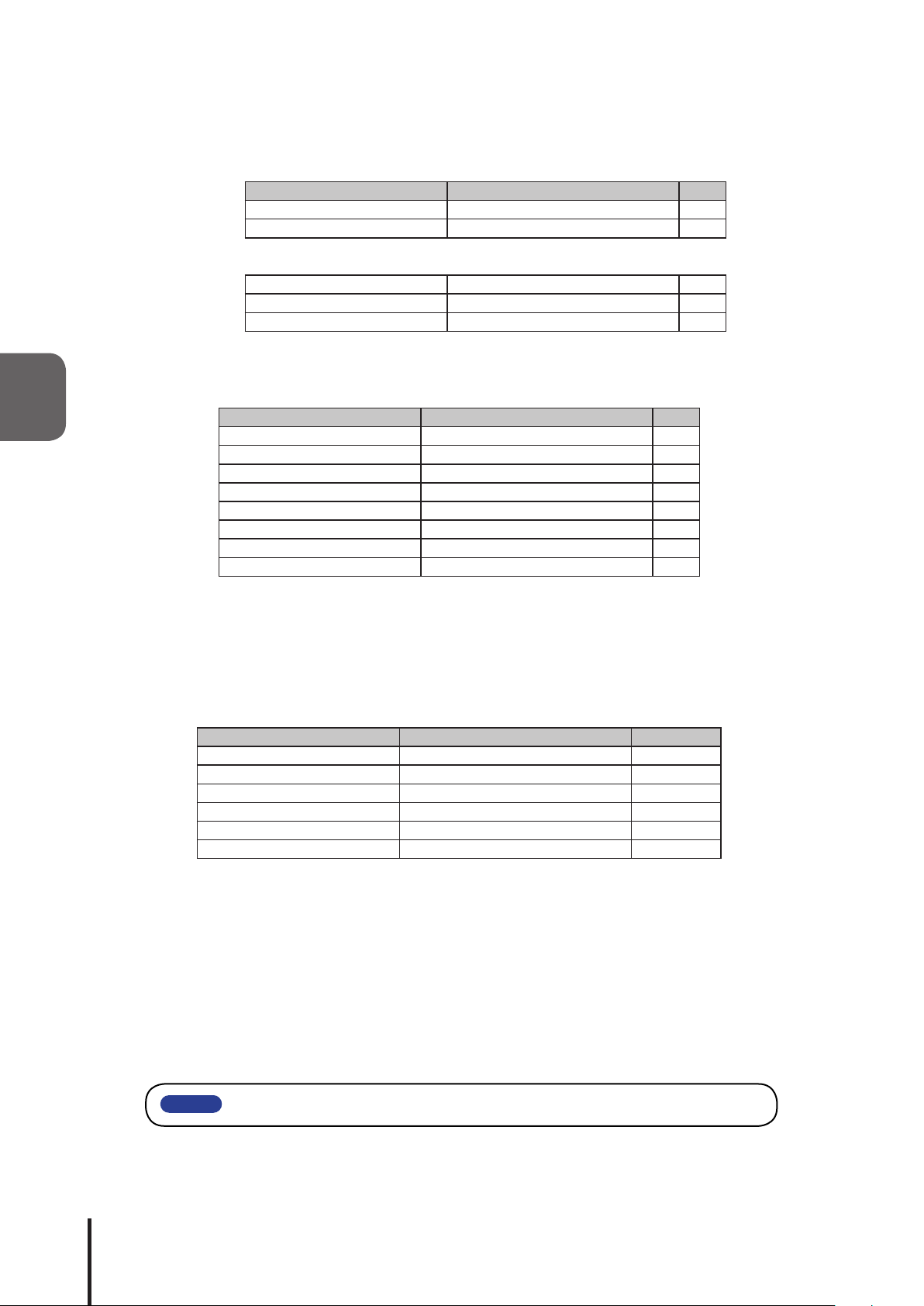
3.4.1 SNMP SET Control Function for Signal-Tower
The Signal Tower and buzzer are controllable through the SNMPSET command.
The following is an example to control the “on” and ”off” for the Signal Tower lighting and buzzer.
[Application Example 1] Turning the red unit on. Set it up as followed:
Object Object ID Value
controlLightControlState 1.3.6.1.4.1.20440.4.1.5.1.2.1.2.1 2
controlLightControlTimer 1.3.6.1.4.1.20440.4.1.5.1.2.1.3.1 0
[Application Example 2] Operating the ashing pattern1 for the amber unit. Set it up as followed:
Object Object ID Value
controlLightControlState 1.3.6.1.4.1.20440.4.1.5.1.2.1.2.2 3
controlLightControlTimer 1.3.6.1.4.1.20440.4.1.5.1.2.1.3.2 0
[Application Example 3] With the red unit ashing pattern2, and amber ashing pattern1, after 5 seconds,
the green turns on with the buzzer synchronized with light pattern2. Set it up as
followed:
Object Object ID Value
controlLightControlState 1.3.6.1.4.1.20440.4.1.5.1.2.1.2.1 5
controlLightControlTimer 1.3.6.1.4.1.20440.4.1.5.1.2.1.3.1 0
controlLightControlState 1.3.6.1.4.1.20440.4.1.5.1.2.1.2.2 3
controlLightControlTimer 1.3.6.1.4.1.20440.4.1.5.1.2.1.3.2 0
controlLightControlState 1.3.6.1.4.1.20440.4.1.5.1.2.1.2.3 2
controlLightControlTimer 1.3.6.1.4.1.20440.4.1.5.1.2.1.3.3 5
controlLightControlState 1.3.6.1.4.1.20440.4.1.5.1.2.1.2.6 3
controlLightControlTimer 1.3.6.1.4.1.20440.4.1.5.1.2.1.3.6 0
3.4.2 SNMP GET Status Acquisition Function for Signal-Tower
The Signal Tower status is acquisitioned through the SNMP GET command. The following is an example of a
Signal Tower status acquisition.
[Application Example 1] The red is lighting, the amber is ashing pattern1, green is off, blue is ashing
pattern2 and white is on. The buzzer sound pattern3 is an example of
acquisitioning the Signal Tower status.
Object Object ID GET Value
controlLightCurrentState 1.3.6.1.4.1.20440.4.1.5.1.2.1.4.1 2
controlLightCurrentState 1.3.6.1.4.1.20440.4.1.5.1.2.1.4.2 3
controlLightCurrentState 1.3.6.1.4.1.20440.4.1.5.1.2.1.4.3 1
controlLightCurrentState 1.3.6.1.4.1.20440.4.1.5.1.2.1.4.4 4
controlLightCurrentState 1.3.6.1.4.1.20440.4.1.5.1.2.1.4.5 2
controlLightCurrentState 1.3.6.1.4.1.20440.4.1.5.1.2.1.4.6 4
3.4.3 TRAP Reception Function
With the set-up containing the designated sender or with the OID included, the TRAP is received. When
the TRAP transmission is sent, the information, e-mail transmission and time of reception according to the
Signal Tower can be included. For further details on the setting method, refer to “4.9 TRAP Reception Setting
Screen”.
3.4.4 TRAP Transmission Function
The TRAP is sent to the designated sender when the TRAP Reception setup for this product is done. For
further details on the setting method, refer to “4.4 The SNMP Conguration Screen”.
24
Please
Set the community name for the TRAP transmission of this product to "public."
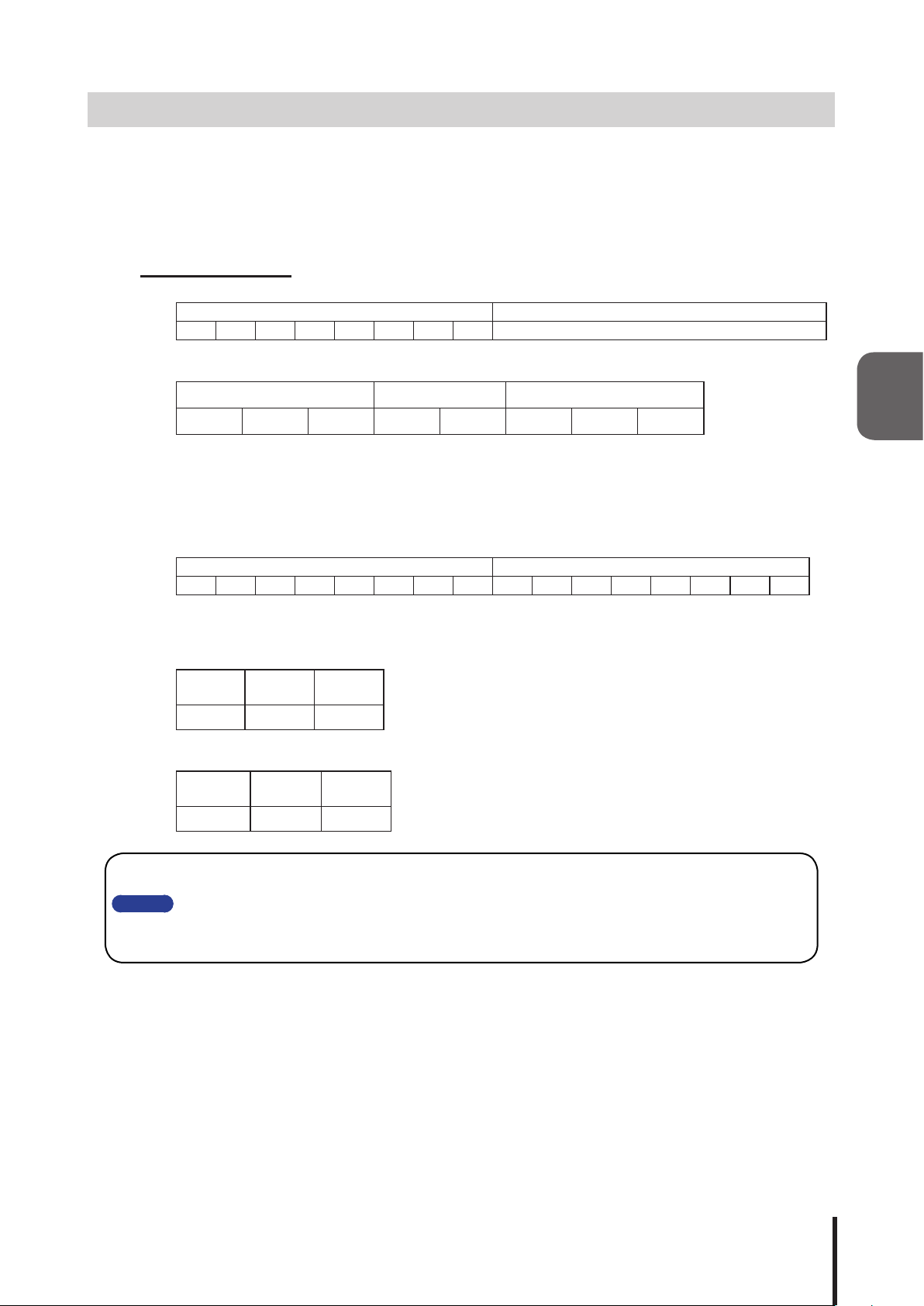
3.5 PHN Command Reception Function
The socket communication control protocol used with the PHN Series (ex. PHN-3FBE1) is being used to
control this product. The socket communications protocol can be selected from either "TCP" or "UDP", and
a port number from"10000" to "65535" can be set. The following explains the PHN commands used by the
socket communication function. For further details of the setting method, refer to "4.5 Socket Communication
Conguration Screen".
Writing Command
Transmitting the following data controls the Signal Tower and buzzer.
"W" (57H) Operation Data 8 Bits
0 1 0 1 0 1 1 1 Reference of Operation Data Contents
Details of Operation Data
Signal Tower Flashing Buzzer Signal Tower Lighting
Green Amber Red Pattern2 Pattern1 Green Amber Red
[Example of sending the writing command transmission]
To operate the Signal Tower with a "red lighting, amber ashing, green lighting, and buzzer pattern2",
enter into the operation data a "1" bit to make it turn ON and a "0" bit to make it turn OFF.
Command
[
0 1 0 1 0 1 1 1 0 1 0 1 0 1 0 1
]
"W" (57H) Operation Data (55H)
3
Please
Response from this product
Normal response (output response)
“A”
(41H)
1 Byte 1 Byte 1 Byte
Response Error (output failed)
“N”
(4EH)
1 Byte 1 Byte 1 Byte
In case lighting and ashing are simultaneously turned on by a PHN command, priority is given to
the lighting command.
In case buzzer patterns are turned on simultaneously, priority is given to the pattern1 command.
For further details regarding the PHN Series, please contact your nearest PATLITE Sales
Representative.
"C"
(43H)
“A”
(41H)
"K"
(4BH)
"K"
(4BH)
25

3
Reading Command
The current operating status of this product is requested.
“R” (52H) 8 Bit
0 1 0 1 0 0 1 0
Response from this product
Signal Tower Flashing Buzzer Signal Tower Lighting
Green Amber Red Pattern2 Pattern1 Green Amber Red
[Example for a data acquisition response]
Signal Tower with Red/Amber Lighting: Response Data: 0000 0011 = 03H
Responding Data (03H) 8 bit
0 0 0 0 0 0 1 1
Signal Tower with Green Flashing and Buzzer Pattern1 Response Data: 1000 1000 = 88H
Responding Data (88H) 8 bit
1 0 0 0 1 0 0 0
Please
The PHN command is not capable of controlling Flashing Pattern2, Buzzer Pattern3,
or Buzzer Pattern4.
26
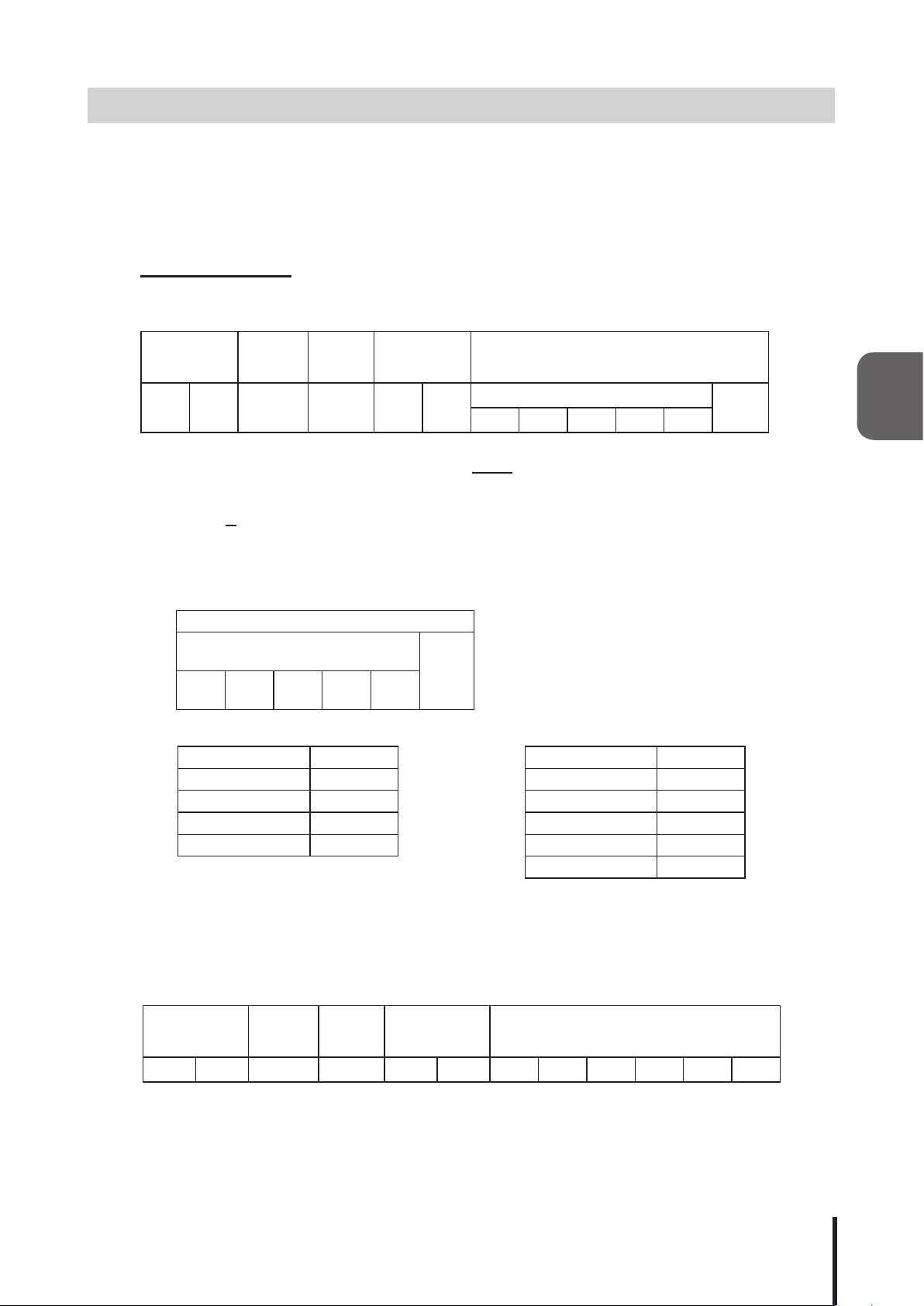
3.6 PNS Command Reception Function
The PNS command is an exclusive PATLITE command protocol, which controls the Patlite NHL Series Signal
Tower and buzzer. The socket communications protocol can be selected between "TCP" and "UDP", and the
communication ports are available from "10000" to "65535".
The following explains the PNS commands being used with a socket communication setup.
(*) This function is not available for the NHC/NHE/NHM-3FB Models.
Writing Command
The following is the protocol used to transmit data to control the Signal Tower and buzzer.
By entering the proper data, the buzzer and LED unit operation from the Signal Tower can be controlled.
Product
Classication
"XX”
58H 58H 53H 00H 00H 06H
Product Classication
Product classication of this product is xed at
Identier
"S"
Identier
"S" is used.
Data Size
(Empty) Data Size Data Control Bits 6 bit (Refer to table below)
Signal Tower
Red Amber Green Blue White
"XX"
.
Buzzer
3
Capacity of data control bits (data to transmit)
Data Transmission Conguration
Data Control Bits 6 bit
Signal Tower
Buzzer
Red Amber Green Blue White
[Signal Tower] [Buzzer]
Non-ashing 00H Stop 00H
Flashing 01H Buzzer Pattern1 01H
Flashing Pattern1 02H Buzzer Pattern2 02H
Flashing Pattern2 03H Buzzer Pattern3 03H
No Change 09H Buzzer Pattern4 04H
No Change 09H
Example of sending the writing command transmission
[
When writing a command for the Signal Tower to operate with "Red Lighting + Amber Flashing Pattern1+
Green Flashing Pattern2+ Buzzer Pattern4"
Command
[
Product
Classication
"XX”
58H 58H 53H 00H 00H 06H 01H 02H 03H 00H 00H 04H
]
Identier
"S"
(Empty) Data Size Data Control Bits 6 bit
]
27
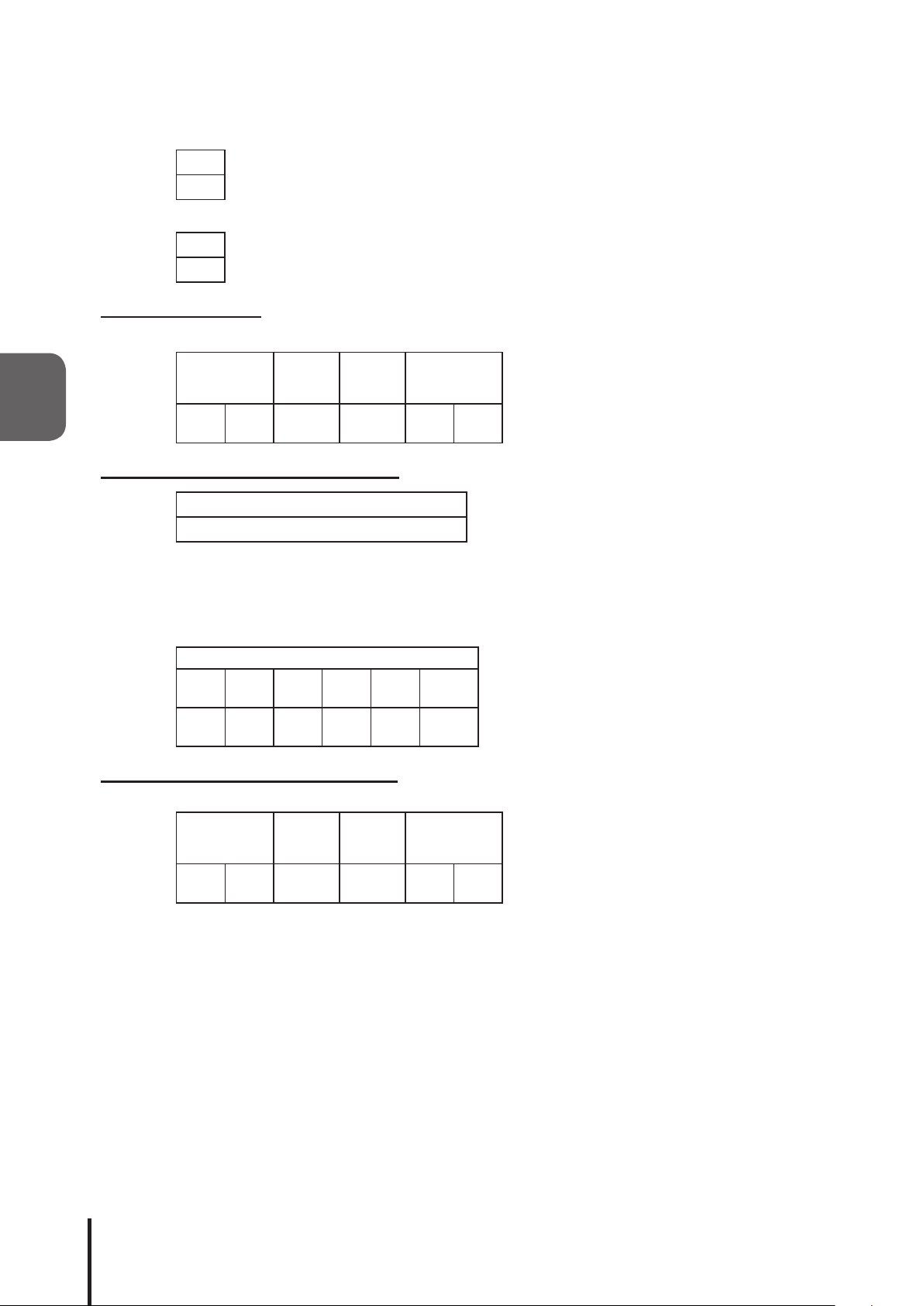
3
Response from this product
Normal response (output response)
ACK
06H
Response Error (output failed)
NAK
15H
Reading Command
Transmitting the following data will execute the status of the Signal Tower and buzzer.
Product
Classication
"XX”
58H 58H 47H 00H 00H 00H
Identier
"G"
(Empty) Data Size
Response from the Read Command
Data Control Bits 6 bit
Refer to "Capacity of Data Control Bits"
Example for a data acquisition response
[
Signal Tower “Red: Flashing Pattern1, Amber: Flashing Pattern2, Green: Lighting with no buzzer” is
read, and the response from this product is indicated in the following table after the command transmission.
Data Control Bits 6 bit
Red Amber Green Blue White Buzzer
02H 03H 01H 00H 00H 00H
Status Condition "Clear" Command
The change in the operating state for this product is made when setting up the "Normal Mode Setup".
Product
Classication
"XX”
58H 58H 43H 00H 00H 00H
Identier
"C"
(Empty) Data Size
]
28
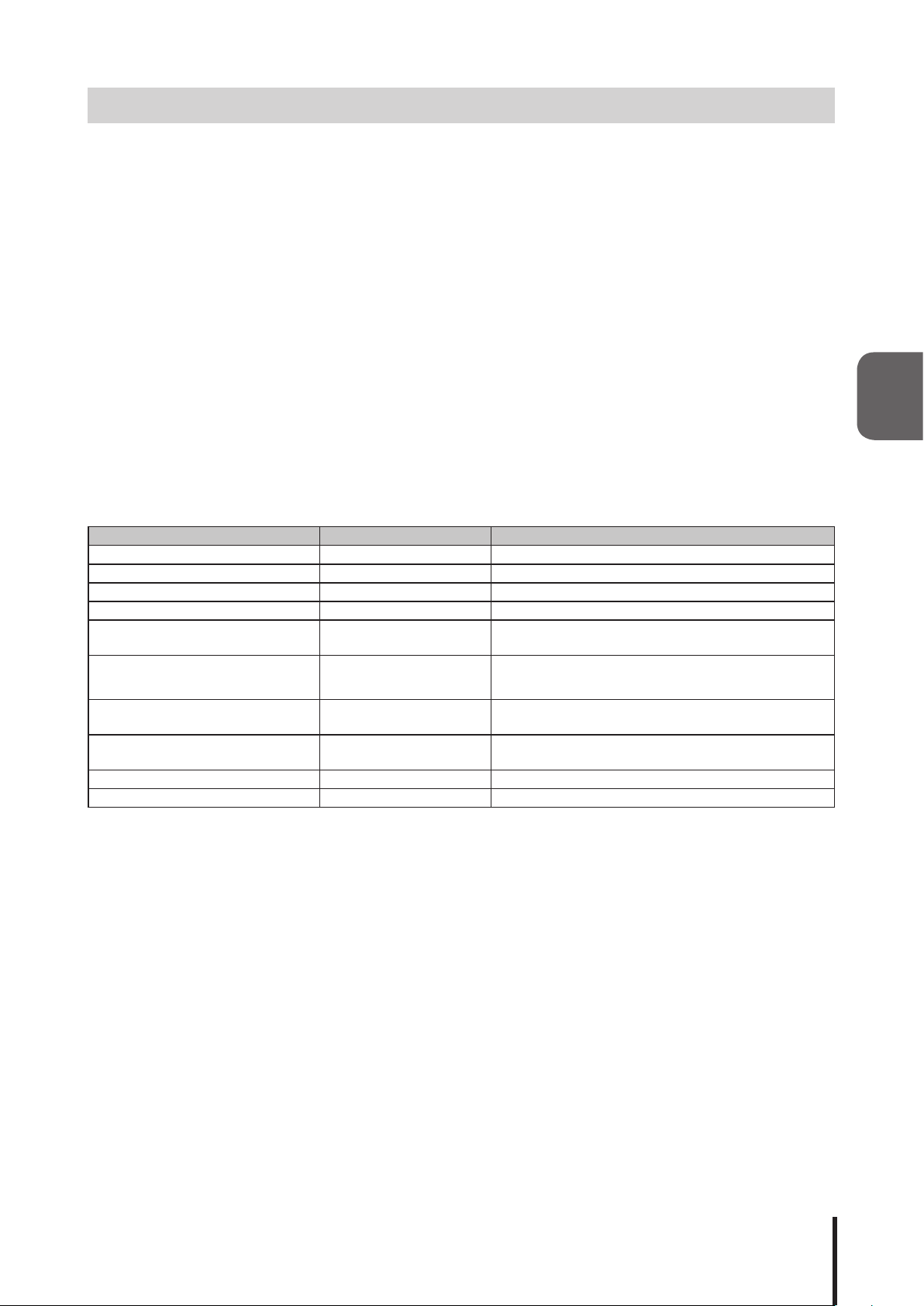
3.7 E-mail Sending Function
It can transmit up to eight registered e-mail addresses. The subject and message of the transmitting mail
can be registered for 16 different situations per subject title to be transmitted via e-mail to the 8 registered
addresses. The user authentication method during transmission can be selected from either "SMTP
Authentication", "POP Authentication", or "No Authentication". Refer to "4.6 E-mail Sending Setup Screen"
and "4.7 E-mail Message Setup Screen" for further details of the setting method.
3.7.1 E-mail Message Contents
The registration of 16 subjects and 16 messages for transmitting mail can be selected in combination when
sending an alert message of up to 8 registered E-mail addresses. The e-mail text would include the equipment name, its location, the sender, the message, and supplementary information indicated in table 3.7.1 below. The contents of the registered subject is indicated.
If the 17th xed e-mail subject title “NH-ORIGINAL” is selected, the equipment location, message transmission time stamp, and event contents is indicated. If the 17th e-mail subject text is selected as “None”, nothing
is indicated in the text.
Registered subject title when selecting No. 17 is "NH-ORIGINAL"
[
System Location: YY/MM/DD hh:mm Contents of the event: Name
Table 3.7.1 Fixed Written Subject Contents
Generated Event Indicated Event Contents Indicated Name
TRAP Reception Blank TRAP Monitor Setup Registered Group Name
Execute "Clear" by pushbutton “: CLEAR-Switch” Blank
Execute "Clear SNMP" “: CLEAR-SNMP” Blank
Execute "Clear RSH" “: CLEAR-RSH” Blank
Ping Monitor Abnormality Detection “: PING-Error”
Ping Monitor Recovery Detection “: PING-Recover”
Application Monitor Abnormality
Detection
Application Monitor Recovery
Detection
Execute “Clear RSH Command” “: RSH-Executes” Blank
“TEST” button pressed “: TEST-Switch” Blank
“: APP-Error”
“: APP-Recover”
The equipment name registered in the Ping Monitor
The equipment name registered in the Ping Monitor
]
setup
setup
The equipment name registered in the Application
Monitor setup
The equipment name registered in the Application
Monitor setup
3
29

3.8 RSH Command Function
3.8.1 RSH Commands
RSH (remote shell) is a CUI program which executes a shell command from one computer to another computer
via a computer network. The following explains how to control the Signal Tower via the RSH command.
The command syntax which this product can receive is indicated below. For the setting method of the "RSH
Command Connection Authentication /Operation after Reception", refer to "4.8 RSH Command Reception
Setup Screen".
Table 3.8.1 Receivable Commands
Command Contents
alert Controls Signal Tower/Buzzer
clear/doclear Returns to Normal Mode
status Acquisitions the Signal Tower Status
test/dotest Executes a Self-test
3
Using the RSH Commands
Command Input Method
rsh IP address [-l Login Name ] Command [Option]
Command Input Method (when the designated sender address is inactive)
rsh IP address -l Common login name when designated sender address is inactive Command [Option]
: indicates a space. [ ]: indicates an option.
Note
The use of login abbreviations for the login name is limited to when the account name and the PC
are registered (in half-width alphanumeric characters) on the command reception screen which
transmits the RSH command.
alert Command
Contents : To control the Signal Tower and buzzer.
Syntax : alert rygbcz [sec]
Return Value : Status after command is executed
Option : Refer to Table 3.8.2.
Table 3.8.2 RSH Command Option Explanation
Type Explanation
rygbc Turning on and off of the Signal Tower LED Units and Buzzer Alarms
r r: Red (0) Light Off (1) Lighting (2) Flashing Pattern1 (3) Flashing Pattern2 (9) No Change
30
y y: Amber (0) Light Off (1) Lighting (2) Flashing Pattern1 (3) Flashing Pattern2 (9) No Change
g g: Green (0) Light Off (1) Lighting (2) Flashing Pattern1 (3) Flashing Pattern2 (9) No Change
b b: Blue (0) Light Off (1) Lighting (2) Flashing Pattern1 (3) Flashing Pattern2 (9) No Change
c c: White (0) Light Off (1) Lighting (2) FlashingPattern1 (3) Flashing Pattern2 (9) No Change
z z: Buzzer Alarm (0) Buzzer Off (1) Pattern1 (2) Pattern2 (3) Pattern3 (4) Pattern4 (9) No Change
Restores the Signal Tower to its previous command status. When the time exceeds the set value, it returns
sec
to the previous Signal Tower condition. The time can be set from zero to 99. The status will not return if no
input or a zero has been entered.
[Command Transmission Example]
Ex. 1) A product with an IP address of [192.168.10.10] and designated sender user name of "root",
with Red Lighting, Green Lighting and Buzzer Pattern2 On:
rsh 192.168.10.10 -l root alert 101002
Ex. 2) A product with an IP address of [192.168.10.10] and a common login name of "patlite",
with Red Lighting and White Flashing Pattern2:
rsh 192.168.10.10 -l patlite alert 100020

[Command Transmission Example - cont.]
Ex. 3) A product with an IP address of [192.168.10.10] and a designated sender user name of "root",
with the Red Lighting, Amber Flashing Pattern2, Green Lighting and Buzzer Pattern3, all on for 20
seconds:
rsh 192.168.10.10 -l root alert 131003 20
Ex. 4) A product with an IP address of [192.168.10.10] with Red Lighting, Amber Flashing Pattern2, Green
Lighting, Buzzer Pattern3, all on for 20 seconds (no login name)
rsh 192.168.10.10 alert 131003 20
clear/doclear Command
Contents : To clear the Signal Tower and Buzzer, returning to the Normal Mode.
Syntax : clear [-p] [-z] , doclear [-p] [-z]
Return Value : Status after command is executed
Option : Refer to Table 3.8.3.
Table 3.8.3 clear/doclear Command Option Explanation
Type Explanation
-p Turn off all Signal Tower Lights
-z Turn off Buzzer Alarm
None Return to Normal Mode
[Command Transmission Example]
Ex. 1) A product with an IP address of [192.168.10.10] and a common login name of "patlite",
with all the Signal Tower Lights turned off:
rsh 192.168.10.10 -l patlite clear -p
with all the Signal Tower Lights turned off (no login name):
rsh 192.168.10.10 clear -p
3
Ex. 2) A product with an IP address of [192.168.10.10] and a designated sender user name of "root",
with the Buzzer alarm turned off:
rsh 192.168.10.10 -l root doclear -z
with the Buzzer alarm turned off (no login name):
rsh 192.168.10.10 clear -z
Ex. 3) A product with an IP address of [192.168.10.10] and a designated sender user name of "root",
with all the Signal Tower Lights and Buzzer returned to the Normal Mode:
rsh 192.168.10.10 -l root clear
with all the Signal Tower Lights and Buzzer returned to the Normal Mode (no login name):
rsh 192.168.10.10 clear
status Command
Contents : Return the present status of the Signal Tower and buzzer to Normal Mode.
Syntax : status
Return Value : Current Condition rygbcz
[Command Transmission Example]
Ex. 1) A product with an IP address of [192.168.10.10] acquisitions the operating state of the Signal Tower.
The designated sender user name for the Signal Tower status acquisition is "patlite".
rsh 192.168.10.10 -l patlite status
Response: 201003
The login name was omitted for status acquisition of the Signal Tower.
rsh 192.168.10.10 status
Response: 201003
31

3
test/dotest Command
Contents : Executes conrmation of the Signal Tower and buzzer operation in sequence order of Red,
Amber, Green, Blue, White and Buzzer Pattern1.
Syntax : test , dotest
Return Value : None
[Command Transmission Example]
Ex. 1) A product with an IP address of [192.168.10.10] can verify operation of the Signal Tower.
The common login name for the Signal Tower status conrmation is "patlite".
rsh 192.168.10.10 -l patlite test
rsh 192.168.10.10 -l patlite dotest
Signal Tower status conrmation is executed (no Login Name):
rsh 192.168.10.10 test
rsh 192.168.10.10 dotest
Ex. 2) A product with an IP address of [192.168.10.100] can verify operation of the Signal Tower.
The designated sender user name for the Signal Tower status conrmation is "root"
rsh 192.168.10.100 -l root test
rsh 192.168.10.100-l root dotest
Signal Tower status conrmation is executed (no Login Name):
rsh 192.168.10.100 test
rsh 192.168.10.100 dotest
3.8.2 RSH Alert Timer Reset Function
The RSH alert timer reset function is capable of being selected for "Shared" or "Individual" when setting up the
timer function for the Signal Tower lights and buzzer control.
(Refer to 3.8.2 "Timer Reset Function")
Shared : Each Signal Tower tier and buzzer are controlled by a common timer.
Individual : Each Signal Tower tier and buzzer are controlled by individual timers.
32

The following explains the difference in operation between the "Shared" and "Individual" selection for this
Alert Timer Reset Function set for "Shared"
The execution affects the influence of the timer when the command is sent.
Alert Timer Reset Function set for "Individual"
The execution does not affect the influence of the timer when the command is sent.
Example 2
Operation
Example 2
Operation
10 sec0 sec 3 sec 13 sec
[Elapsed Time]
10 sec0 sec 3 sec 13 sec
[Elapsed Time]
Remaining time changes from
7 seconds to 10 seconds
Remaining time is 7 seconds
Red status “No Change”, Green
starts at 10 seconds, with a
remainder of 10 seconds
Red stays “ON”
Red and Green
turn “OFF”
The red LED starts at 10 seconds,
with a remainder of 10 seconds
Red turns “OFF”
Green turns “OFF”
The red LED starts at 10 seconds,
with a remainder of 10 seconds
Red status “No Change”, Green
starts at 10 seconds, with a
remainder of 10 seconds
Example 1
Operation
Example 1
Operation
product when setting up the alert timer reset function.
[Procedure]
Ex. 1) Transmit the command to the products IP address [192.168.10.10]. Use the login name [root], then
execute the following commands of [Red Lighting; other colors no status change; no buzzer status
change] for 10 seconds.
rsh 192.168.10.10 -l root alert 199999 10
Ex. 2) 3 seconds after "Ex.1)", transmit the command to the products IP address [192.168.10.10]. Use the
login name [root], then execute the following commands of [Green Lighting; other colors no status
change; no buzzer status change] for 10 seconds.
rsh 192.168.10.10 -l root alert 991999 10
3
33

3
3.9 Ping Monitoring Function
The Ping transmission is used to monitor the response of a device in a network. A maximum of 24 nodes can
be monitored and the control of abnormality detection and abnormality recovery can be set up separately. The
Ping monitor setup for No's. 21 to 24 has a few more adjustable parameters. Refer to "4.10 Ping Monitoring
Setup Screen" for details on the setting method.
3.9.1 Ping Monitoring Function (Nodes 1 to 20)
The monitoring period is xed at 60 seconds for numbers 1 through 20 of the Ping Monitor to transmit one Ping
per device to monitor for every period. The Ping Monitor function starts soon after the completion of the Ping
Monitor setting. When there is no Ping response during the monitoring period, a judgement for the number
of times the abnormalities in a Ping response is counted, and when the number of times for transmission is
compared with the setup value for judgment, the decision is made as to whether an abnormality has occured
or not, and the result causes a status change based on the Ping Monitor Settings.
Example) When the number of times for transmission is set to "1".
Fig. 3.9.1 Ping Monitoring Function (For Ping Monitor Setting Screen No. 1 to 20)
Monitoring
Side
NHL Side
The Ping monitor
starts after the
completion of the
Web setup tool.
Ping Monitor
Condition
Ping Monitoring Period
When there is no Ping
response during a Ping
monitoring period
Judgement: Abnormal
Ping Monitoring
Abnormal Condition
When there is a Ping
response during a Ping
Detection Abnormality
period
Judgement: Recovery
Ping
Transmission
Ping Monitor Condition
When there is a Ping
response during a Ping
monitoring period
Judgment: No Abnormalities
Ping
Reply
34
Please
・One count per Transmission
・With the preset value set as "1",
judgement is a Ping monitor abnormality.
・Changes to Abnormality
Detection Condition
If a "Clear" operation (Refer to 3.11 "Clear Control Function") is executed when a monitoring detection is
active, it will return to the monitoring condition from the abnormality detection status.
Even with the double-push clear setting, once the clear button is pressed, the status will return to the
monitoring condition.
For other functions outside the "Clear" operation, because they do not control the abnormality detection
condition, the Ping monitor abnormality status will remain uncleared. Any operations outside a “Clear
command may be due to the Ping Monitoring Function which continues to remain active when it is in
operation.
・Monitor Recovery
Condition
・Condition returns to a
monitoring state
The monitoring
condition continues

3.9.2 Ping Monitoring Function (Nodes 21 to 24)
The following explains the function of operation for setting up the frequency of transmissions and the number
of transmissions within the frequency number. The monitor period can be set up from 1 to 600 seconds for the
Ping monitor period.
The following is an example of setting the number of times to transmit with a value of "2" and "3".
With the number set for "2", the transmission will send two "packets", and if judgement of an abnormal condition
continues to be generated twice, the Ping Monitor Condition detects an abnormality. If the transmission number
is set to "3", then the transmission will send three "packets" during the Ping monitoring period. (Refer to the
following gure)
A judgement of abnormality is detected at the time of the following monitoring periods.
1. If one ping response out of three "packets" is recieved, then judgement of no abnormality is detected.
2. If all three ping responses were not answered among the three "packets", it counts as one time for judging
that an abnormality is occuring.
3. Even in the following time period, if there is no ping response, the number of times to count an abnormality is
counted as one time. The total number of transmission times is set to "2", and the Ping Monitoring Abnormality
Condition is executed.
Note
When the Abnormality Judgement Value is set as a "1", if the next Ping Monitoring Abnormality Condition
is judged as "no abnormality", then the number of judging abnormality is cleared (back to "0").
3.9.2 Ping Monitoring Function (For Ping Monitor Setting Screen No. 21 to 24)
3
Monitoring
Side
NHL Side
Set up with the Web
Setup Tool
Ping Monitoring starts
after setup
completion
Judgment: No Abnormalities
Ping Monitoring Period
1st time : Reply
2nd time : No Reply
3rd time : Reply
When there is a Ping
response during a Ping
monitoring period
(Judging “Abnormal” the 1st time)
Ping Monitoring
Condition
1st time : No Reply
2nd time : No Reply
3rd time : No Reply
When there is no
Ping response at all
during a Ping
monitoring period
(Judging “Abnormal” the 2nd time)
Judgment: Abnormal
Ping
Transmission
1st time : No Reply
2nd time : No Reply
3rd time : No Reply
When there is no
Ping response at all
during a Ping
monitoring period
Judgment: Abnormal
Ping
Reply
Ping Monitoring
Abnormal Condition
Please
With the number of transmissions set
to "2", the judgement decides its a
Ping monitor abnormality.
Execution starts when abnormality is detected
If a "Clear" operation (Refer to 3.11 “Clear Control Function”) is executed when a monitoring detection
is active, it will return to the monitoring condition. With the double-push clear setting, the status will
return to the monitoring condition on the rst press of the "CLEAR" button.
35

3
3.9.3 Ping Monitoring Function (“Clear” Command Outside Sources)
(When a "Clear" execution from an outside source is requested at the time of abnormality detection)
The following is an example for the procedure when an executed "Clear" command is received from an outside source
while the Ping Monitoring function detects an abnormality ("Clear" command executed via the "Clear" switch, RSH
"Clear" Command, PNS "Clear" command, SNMP "Clear" Command, or a "Clear" Command from the Web Setup
Tool).
Example) When a "Clear" command is transmitted from an outside source at the time an abnormality is detected by
the Ping Monitor.
1. From the monitoring condition, when a monitoring abnormality occurs, the condition of the Signal
Tower changes at the time of detecting the abnormality.
2. If a "Clear" command is received during the abnormality detection, the status of abnormality detection
will be cleared and it will return to its normal mode.
3. If there is a Ping response from the next Ping monitor execution, the monitoring condition will continue
as normal.
If there is no response, the condition will immediately return to the abnormality detection mode.
Fig. 3.9.3 Setting screen 21 to 24 operation ow-chart example
Monitoring
Side
NHL Side
Set up with the
Web Setup Tool
Ping Monitoring
starts after setup
completion
Ping Monitoring
Condition
Ping Monitoring
Period
When there is no Ping
response during the ping
monitoring period
Abnormality detection
and judgment
"Clear" Execution
Ping Monitoring
Abnormal Condition
When abnormality is
detected, a "Clear"
command is executed
The condition of the
detected abnormality will
be in the "Clear" status.
Ping
Transmission
Ping Monitoring
Condition
When there is a Ping response
during the monitoring condition
The monitoring
condition continues
"Clear"
Execution
Ping Monitoring Condition
Ping Monitoring
Abnormal Condition
36
Please
Execution starts when
abnormality is
detected
In cases where it returns to a monitoring condition from a "Clear" command, it
will not branch to the "Ping Recovery" operation from an abnormal detection.
Condition returns to
a monitoring state
If the abnormality is
cleared from the "Clear"
command, the "Ping
Recovery" operation is
not necessary
When there is no Ping response
during the monitoring condition
An abnormal condition
will be detected

3.10 Application Monitoring Function
By creating an additional transmission command for a customer's application, this product can monitor the
response of the application by receiving the data from it.
If data is not received within the monitoring period, it makes a judgement that the communication has become
abnormal, and at the time of the abnormality, sends a status change to the Signal Tower. After a generated
event, if data is received from the monitored candidate, it will detect a recovery from the abnormal operation.
Refer to "4.11 Application Monitoring Conguration Screen" for details on the setting method.
As an example, with a monitoring period of 30 seconds, the received data from the application is monitored.
1. After the setup is complete and it receives data from the address monitoring point, the monitoring will
commence.
2. If data is received within the monitoring period of 30 seconds, it will be judged as having no abnormalities.
3. However, if the data is not able to be received within the allotted period (30 seconds in this example), it
makes a judgment of abnormality.
Once judged as abnormal, the operation at the time of the detected abnormality is carried out.
4. If data is received from the application after detecting a generated event of abnormality, it will detect a
recovery from the abnormality.
The operation at the time of recovery from the abnormal condition will return to its monitoring condition
again.
Fig. 3.10.1 Detailed Example of Application Monitoring
3
Application Monitor
Side
NHL Side
Monitoring Condition
Application Monitoring Period
Application
Monitoring Period
Application Monitoring
lapsed time reset
Application Monitor
re-start
Response
Monitoring Abnormal Condition Monitoring Condition
When data couldn't be
received during a
monitor reception period
Application Monitoring
abnormal detection start
Data
Transmission
When data was received
during the detection of an
abnormality
Application Monitor
Recovery Start Execution
Data
Application Monitoring Period
Monitor Starting
Point
Please
Application Monitoring
Condition
Recovery from an abnormal operation can only occur if a monitored condition was
detected as abnormal.
37

3.11 "Clear" Control Function
The "Clear" operation is accessible from the following commands; "Clear" command executed via the "Clear"
switch, RSH "Clear" Command, PNS "Clear" command, SNMP "Clear" Command, or a "Clear" Command
from the Web Setup Tool.
Refer to "4.12 "Clear' Control Setup Screen" for details on the setting method.
3.12 Normal Mode Settings
The Signal Tower can be set up to display its "normal state of operation", based on the user's preference for
lights and buzzers to be on when no warning conditions occur. Refer to "4.13 Normal Mode Setup Screen" for
details on setting it up via the Web Setup Tool.
3.13 Reinitialization Function
3
From the Web Setup Tool, this unit can be reinitialized to revert all settings back to the default (factory)
settings, while leaving the network settings as is when resetting the other settings. Refer to "4.16
Reinitialization Setup Screen" for details on the setting method.
Also, it can initialize the network settings of this product to its default settings in addition to returning the other
settings to their default settings.
Method for full initialization, including the network setup
【
1. Set the volume level switch to the "HIGH" position.
2. Turn on the power supply while simultaneously pushing the "TEST" switch.
3. After the Signal Tower does an all-point lighting test, the Signal Tower lights go out. Release the switch
after all the Signal-Tower lights are out.
4. The Signal Tower will light up again about 1 minute after. The Signal Tower will then flash Pattern1
afterward to indicate the initialization is complete.
5. Push the clear button to stop the ashing.
If the Ping monitor etc. are set up, an abnormal operation detection may occur.
※
Method for initialization to revert the network settings back to the factory default value
【
1. Set the volume level switch to the "OFF" position.
2. Turn on the power supply while simultaneously pushing the "CLEAR" and "TEST" switch.
3. After the Signal Tower does an all-point lighting test, the buzzer will make an audible sound. Release the
switch after the buzzer sounds.
4. When the Signal Tower goes out, it indicates the completion of initilization.
Please
Do not overexert pressure to the "CLEAR" switch, "TEST" switch and volume level switch. Failure
to comply may damage the unit.
】
】
3.14 Event Log Output Function
The Web Setup Tool displays an event log. Moreover, it is possible to download it as a text le. The following
is the description of the recording mode labels for the event log.
Event Name coldStart Event Contents No Display
Event Details Records at the moment of start up.
Event Name ACCESS Event Contents No Display
Event Details
Event Name MAIL Event Contents E-mail Transmission
Event Details Records at the moment of an e-mail transmission.
38
Records at the moment of authentication failure.
Records at the moment of Web login failure.

Event
Name
Event
Details
PING Event Contents
It records when the Ping monitor status changes.
"Ping Monitoring Error": When an abnormality event in the Ping monitor occurs, it records it with the target
IP address.
"Ping Recovery": When an abnormality in the Ping monitor is restored, it records it with the target IP
address.
Ping monitor abnormalities and the IP address object
Ping abnormality response and the IP address object
Event
Name
Event
Details
Event
Name
Event
Details
Event
Name
Event
Details
Event
Name
Event
Details
APL Event Contents
It records when an abnormality in the application monitor is detected.
"Application Monitoring Error": It records when the abnormalities in an application monitor occurs.
"Applicaton Recovery": It records when the abnormality in the application monitor is restored.
TRAP Event Contents Trap reception IP address and the designated sender
When a registered Trap is received, it is recorded with the IP address of the designated sender.
CLEAR Event Contents
The Signal Tower is returned to its normal operating status during operation.
"CLEAR" Switch": It records when the clear switch to this product is pushed.
"SNMP": It records when a "CLEAR" has been executed by the SNMP Command (controlLightSnmpClear).
"RSH": It records when a "CLEAR" has been executed by the RSH Command, and displays the
designated sender IP address.
"PNS Command": It records when a "CLEAR" has been executed by the PNS Command.
RSH Event Contents
It records when the RSH Command is executed. (The "clear" execution is not included)
"ALERT": When the alert command is executed, it records the argument and designated sender IP
address.
An IP address is not written in cases where the designated sender address is inactivated.
※
"Status": The status command is recorded at the time of execution.
"Test": The test command records at the time of execution.
Application Monitoring Error
Applicaton Recovery
"RSH" IP address and designated sender
Web Setup Tool "Clear"
"PNS" Command
IP address, command argument, and the "alert" designated sender.
"Status"
"Test"
"CLEAR Switch"
”SNMP” Command
※
3
Event
Name
Event
Details
SNMP Event Contents ”CONTROL”
When this product is operated by the SNMP Set Commands, the Signal-Tower color and buzzer conditions
are recorded.
The applicable command is "controlLightControlState".
3.15 Conguration Data Save/Load Setup
The setting menu for this product is read and can be saved as conguration data on the PC.
Also, conguration data which was read can be selected to be written in.
The cong setup is done from the Web Setup Tool.
Refer to "4.19 Conguration Data Save/Load Setup Screen" for the setting method.
3.16 Firmware Update Function
The rmware for this product can be updated.
The rmware is updated via the Web Setup Tool.
Refer to "4.20 Firmware Update Screen" for the setting method.
39

4
4 Function Setup
The function setup is available in order to take advantage of the various functions. To access the settings, click the
setup items on the left-hand side of the Web Setup Tool to open the set up screen for the various functions.
Setup Category Setup Screen Setup Contents
System Conguration Sets up the network parameters.
Clock Setup Sets up the time for this product.
User Authorization Conguration Sets up the login password for this product.
Sets up the functions for the SNMP SET/GET and TRAP
transmission.
Sets up the ports to control the PHN Command and PNS
Command outputs.
Setup for writing the message contents to be transmitted by
E-mail.
Setup for receiving the rsh command and to send the E-mail
when an rsh reception and TRAP transmission are executed.
The setup which controls the status condition when a TRAP
or TRAP reception is recieved.
The setup of the address for the monitored equipment and
the management when an abnormality is detected.
The setup is to verify whether data can be received from the
monitored object.
The setup for sending an E-mail when the “Clear” switch is
pressed, and for the TRAP transmission setup.
A setting, such as turning on a Green LED Unit, to indicate a
normal condition.
The setup for sending an E-mail when the “Test” switch is
pressed, and for the TRAP transmission setup.
Reboots this product after settings have been changed to put
them into effect.
The setup items can be saved as cong data and reloaded at
any time.
The list of items, their setup and operation contents, and the
current rmware version is displayed.
Setup Menu
Operation
Settings
NH Unit
Controls
Maintenance
Functions
SNMP Conguration
Socket Transmission Conguration
E-mail Settings Setup for sending E-mail notications.
E-Mail Message Settings
RSH Command Conguration
TRAP Reception Conguration
Ping Monitor Conguration
Application Monitoring Conguration
“Clear” Control Conguration
Normal Mode Settings
“Test” Switch Settings
Signal Tower Output Control The Signal Tower status is controlled from the browser.
Reinitialization The settings return to factory default values.
Reboot
Event Log The event log is displayed and can be downloaded.
Conguration Data Save/Load Setup
Firmware Update The Firmware update function can be done from this screen.
Setup Table Entries
40
Please
After the desired setup is completed, reboot this product by pressing the "reset"
switch or by disconnecting the power and reconnecting it.

4.1 System Setup Screen
Th e net wor k par ame ters for thi s pro duc t can be setu p t hrou gh a bro wser. Th e def aul t IP add ress is
"
192.168.10.1
The parameters can be setup from the System Setup Screen (Fig. 4.1.1 System Setup Screen) from the default values
as shown in Table 4.1.1.
".
Fig. 4.1.1 System Setup Screen
4
Table 4.1.1 System Setup Parameters
Item Contents Default Value Input Parameter
System Name The name for this product can be set. Signal Tower
System Location
Contact Address Setup the contact address. nh@patlite.jp
IP Address
Conguration Method
IP Address Setup the IP address of this product. 192.168.10.1 IP address format X
Netmask Setup the subnet mask of this product. 255.255.255.0 IP address format X
Default Gateway Setup the default gateway of this product. 0.0.0.0 IP address format O
DNS Server Address Setup the DNS server of this product. 0.0.0.0 IP address format O
Host Name Setup a host name nh.patlite.jp
Please
The setup location of this product can be
entered.
Select between Manual or Automatic IP
address conguration.
The values for "Setting Option" in this manual has to have a valid entry, or can be left blank.
O Indicates the entry can be omissible, or any entry within the set parameters.
X Indicates the entry cannot be omissible. Enter a valid parameter.
– Indicates an entry which cannot be omitted, or abbreviated. The value has to be entered in
accordance to the customer's environment.
Blank
Setup
Manually
Full/Half-width Characters
Maximum 31 Characters
Half-width alphanumeric
characters and underscore
“_”
Maximum 31 Characters
Mail address format
Maximum 63 Characters
Select Radio Button X
Enter a legitimate host name
Maximum 63 Characters
Setting
Option
—
O
O
O
41

4
4.2 Clock Setup Screen
The clock setup for this product can be done through a browser. The clock setup can be accessed through the
System Setup Screen (Fig. 4.2.1 Clock Setup Screen) from the default values as shown in Table 4.2.1.
Fig. 4.2.1 "Clock Setup" Screen
Table 4.2.1 Clock Setup Parameters
Item Contents
NTP Server Address Setup the NTP server address. Blank
Time Calibration Interval
Two kind of clock setup methods are indicated below:
• Synchronizing with the PC clock time when logging in.
• Adjusting clock of this product when communicating with an NTP server.
Setup the interval to communicate
with an NTP server.
Default
Value
0
Input Parameter
Server’s Host Name or IP address
Maximum of 63 characters
Half-width numbers from 0 to 1440
(minutes)
Setting
Option
O
O
42

4.2.1 Synchronizing with the PC clock
Clicking the "Manually Setup Clock" button will synchronize with the time on the PC which has been logged into
this product.
Setup Method
[
1. Compare the columns between the "NH Monitor Time" and the "Host Computer Time".
2. Click the "Manually Setup Clock" button to synchronize the time with the PC which is logged in.
Please
]
Due to the reading delay in the software, this product may not reect the exact time down to the
second to match the PC, so there may be a few seconds of a delay.
When not using an NTP server, please check the time of this product periodically.
If power to this unit is disconnected for about a day and a half, it may result in an offset of the time,
so it is highly recommended that the customer who uses this product to resynchronize the time.
Fig. 4.2.2 "Manually Setup Clock" Setup Screen Before
4
Fig. 4.2.3 "Manually Setup Clock" Setup Screen After
43

4
4.2.2 Synchronizing with an NTP server
An NTP server can be linked by entering the NTP server address to synchronize with the clock in this product,
and the time updated by sending a request for time adjustment to that NTP server.
Setup Method
[
1. Enter the NTP server address in the "NTP Server Address" column.
2. Enter a value for the interval to communicate with the NTP server in the "Time Calibration Interval" column.
3. Click the "Set" button to activate the setup.
]
Fig. 4.2.4 NTP server Clock Setup Screen
①
②
Please
③
• Depending on the NTP server, too many requests within an alloted time may cause
the server to disconnect for their security reasons.
• Some NTP servers may require the customer to submit an application to receive a
password for access, which is beyond the scope of this product. It is the customer’s
responsibility to coordinate with that service.
44

4.3 User Authentication Conguration Screen
Setup a password to log into the Setup Screen for this product.
Enter a password, then re-enter the password to verify its entry, then click the "Set" button to activate it. The
next time for logging in will ask for the new password. The password entry will allow up to 16 half-width
alphanumeric characters and a period.
Setup Method
[
1. Enter the password to be changed into the "Password" column.
2. Enter the same password to be changed into the "Re-enter Password" column to verify the entry.
3. Click the "Set" button to activate the setup.
Log in with the new password the next time the login screen appears.
]
Fig. 4.3.1 User Authentication Setup Screen
①
②
③
4
Table 4.3.1 User Authentication Setup Parameters
Item Contents
Password Setup a new password. Blank
Re-enter
Password
Conrm the new password Blank
Default
Value
Input Parameter
Half-width alphanumeric character and period “.”
Maximum 16 Characters
Half-width alphanumeric character and period “.”
Maximum 16 Characters
Setting
Option
X
X
45

4
4.4 SNMP Setup Screen
With an SNMP, this product can communicate outside the community name for the notication of a TRAP, using
the SNMP SET/GET in reference to each item for this product, and generate the event with this product.
4.4.1 SNMP SET/GET
An SNMP SET/GET can be setup.
[Setup Method]
1. Select the "Active" radio button to enable the SNMP function.
2. Enter the SET/GET community parameter.
4.4.2 SNMP TRAP Transmission
An SNMP TRAP Transmission can be setup.
[Setup Method]
3. Select the "Active" radio button to enable the TRAP transmission function.
4. Enter the TRAP Transmission community parameter and the TRAP transmission frequency.
5. Enter in the TRAP Address column, the IP address for sending the TRAP notication to.
6. Click the "Set" button to activate the setup.
TRAP command which is transmitted when the TRAP is active
OID: 1.3.6.1.4.1.20440.4.1.6.3
Name: trapPatliteTrapReceived
Fig. 4.4.1 SNMP Setup Screen
①
②
③
④
⑤
46
⑥

Item Contents
SNMP Function
SET Community
Name
GET Community
Name
TRAP Transmission
Function
TRAP Transmission
Community Name
TRAP Transmission
Frequency
TRAP IP Address
to Receiver
Table 4.4.1 SNMP Setup Parameters
Setup to Activate/Inactivate the
SNMP function.
Setup the name to use when reading
an SNMP setup value.
Setup the name to use when writing
an SNMP setup value.
Setup to Activate/Inactivate the trap
transmission function.
Setup the community name for the
trap which is transmitting.
Setup for the number of times a trap
can be transmitted
IP address format for the destination
of sending a TRAP transmission to.
Default
Value
Active — —
private
public
Inactive — —
public
Blank
Half-width alphanumeric character
and underscore “_”
Maximum 32 Characters
Half-width alphanumeric character
and underscore “_”
Maximum 32 Characters
Half-width alphanumeric character
and underscore “_”
Maximum 32 Characters
1 Half-width numbers from 1 to 10 —
Characters which can be used for a
server address
Maximum 63 Characters
Input
Parameter
Setting
Option
—
—
—
O
4.5 Socket Communication Setup Screen
Set up for the use of the PHN Command and PNS Command with Socket Communication.
[Setup Method]
1. Select either "TCP" or "UDP" in the "Protocol" eld for the communication method.
2. Enter the port to be used in the "Port Number" eld.
3. Click the "Set" button to save all entries.
Fig. 4.5.1 Socket Communication Setup Screen
4
①
②
③
Table 4.5.1 Socket Communication Setup Parameters
Item Contents
Protocol Select from TCP or UDP TCP — —
Port Number Set the reception port number 10000 Half-width numbers from 10000 to 65535 —
Note
Refer to 3.5 “PHN Command Reception Function” for PHN Commands.
Refer to 3.6 "PNS Command Reception Function" for PNS Commands.
Default
Value
Input
Parameter
Setting
Option
47

4
4.6 Mail Transmission Setup Screen
This product can be set up to send E-mail messages. The following are events which will transmit E-mail
messages.
When transmitting an E-mail, it is transmitted in sequence from the smaller address number to the larger
address number of the recipient.
E-mail Transmitting Event
At the time of an RSH command reception
•
At the time of a TRAP reception
•
At the time when the "CLEAR" button is pressed.
•
At the time when a "Clear SNMP" command is executed.
•
At the time of a Ping monitoring abnormality and Ping recovery event.
•
At the time of an application monitoring abnormality and recovery event.
•
[Setup Method]
1. Set up the SMTP mail server address and port number.
2. When using the SMTP authentication, set up the account name and SMTP authentication password.
When using the POP authentication, set up the POP account name and POP authentication password.
Select "None" for when authentication is not necessary.
3. Set up in the designated sender address column the E-mail address of the designated sender.
4. Set up the address of the recipient.
5. Click the "Set" button to save all settings.
Fig. 4.6.1 Mail Transmission Setup Screen
①
②
③
48
④
⑤

Item Contents
SMTP Server
Address
SMTP Port
Number
Authentication
Protocol
Encrypted
Connection
SMTP Account
Name
SMTP Authentication
Password
POP3 Server
Address
POP3 Port Number
Account Name
Password
Source Address
Destination Addresses
1 through 8
Table 4.6.1 E-mail Transmission Setup Protocol
Set the IP Address of the SMTP
Server
Set the port number of the
SMTP Server
Select among “SMTP Authentication/POP Authentication/No
Authentication”.
Select between “SSL”, “TLS” or
“None”.
Set the user name for SMTP
Authentication.
Set up the password for SMTP
Authentication.
Set up the POP3 server IP Address.
Set up the port number for the
POP3 server.
Set up the user name of the
POP Authentication.
Set up the password for POP
Authentication
Set up the E-mail address for
the designated sender.
Set up the destination addresses
for the E-mail to be sent to.
Default
Value
Characters which can be used for a
0.0.0.0
25 Half-width numbers from 1 to 65535 —
No
Authentication
None — —
Blank
Blank
Blank
110 Half-width numbers from 1 to 65535 —
Blank
Blank
Blank
Blank
server address
Maximum 63 Characters
Half-width alphanumeric characters,
characters which can be used for
E-mail addresses
Maximum 32 characters
Half-width alphanumeric characters
Maximum 32 characters
Characters which can be used for a
server address
Maximum 63 Characters
Half-width alphanumeric characters,
characters which can be used for
E-mail addresses
Maximum 32 characters
Half-width alphanumeric characters
Maximum 32 characters
Characters which can be used for an
E-mail address
Maximum 63 Characters
Characters which can be used for an
E-mail address
Maximum 63 Characters
Input Parameter
— —
Setting
Option
—
O
O
O
4
O
O
O
O
49

4
4.7 Message Contents Setup Screen
The following is the setup of E-mail subject titles and message contents for E-mail Sending. When sending E-mails,
the contents can be personalized to match the coinciding mail notications by entering a subject title and message
content to transmit.
[Setup Method]
1. Enter in the "Subject" eld a subject title to transmit by e-mail.
(Use full or half-width alphanumeric characters of up to 31 characters)
2. Enter in the "Message" eld a text message to transmit by e-mail.
(Use full or half-width alphanumeric characters of up to 63 characters)
3. Click the "Set" icon button to save all entries.
Fig. 4.7.1 Message Contents Setup Screen
①
Table 4.7.1 Message Contents Setup Protocol
Item Contents Default Value Input Parameter
Subject
1 through 16
Message
1 through 16
Subject titles from 1
to 16 can be entered
Messages from 1 to
16 can be entered
Message from Signal Tower
Blank
Full or half-width alphanumeric characters
Maximum 31 Characters
Full or half-width alphanumeric characters
Maximum 63 Characters
50
②
③
Setting
Option
O
O

4.8 RSH Command Setup Screen
RSH (remote shell) Commands can control the Signal Tower and buzzer on this product.
The following explains the setup to be able to receive the RSH Commands.
[Setup Method]
RSH Server Function
1. When receiving the RSH Commands, rst turn on the RSH Server function by selecting "Active."
RSH Alert Timer Reset Function
2. A timer can be implemented to control the operating timing of each tier and the buzzer with an RSH
command sent to the Signal Tower.
If the "Shared" function is selected, the timing control for each color can be in common
If the "Separate" function is selected, the timing control for each color is controlled individually.
E-mail Transmission
3. To have E-mail Sending when an RSH Command has been received, and for it to make a report, select
"Active".
Select "Inactive" to prevent any E-mail Sending.
When E-mail Sending is selected for "Active"
4. Select the desired E-mail contents to transmit from the registered subject titles and the text messages
after the E-mail Sending is activated.
After the E-mail contents are selected, choose the E-mail recipients.
TRAP Transmission
.
4
5. To have a trap transmission sent after an RSH Command, select "Active" for TRAP transmission to
transmit the TRAP.
If the TRAP Transmission is not utilized, select "Inactive".
The "TRAP Command" for this product to receive when the TRAP condition occurs
OID: 1.3.6.1.4.1.20440.4.1.6.5
Name: trapPatliteRshExecuted
Designated E-mail Sender Address Setup
6. If address restrictions are made for sending an RSH Command to a designated recipient, select "Active"
for the designated sender address.
If no restrictions have been made, select "Inactive".
When "Inactive" is selected for designated sender addressing
7. Enter a common login name while the designated sender IP address is invalid.
Click the "Set" button on the lower right side of the screen for the settings to be saved.
When "Active" is selected for designated sender addressing
8. Enter the IP address into the designated sender IP address column to allow command execution. A
maximum of 16 accounts can be registered.
To allow activation for command execution, enter a login name.
9. Click the "Set" icon button to initiate the setup.
51

4
Please
When using this product with the internal timer function, if the RSH Alert Timer Reset
Function is changed, the timers for all the LEDs and buzzer is canceled.
Fig. 4.8.1 RSH Command Setup Screen
①
②
③ ④
⑤
⑥
⑦
⑧
⑨⑦
52

Item Contents
RSH Server
Function
RSH Alert Timer
Reset Function
E-mail
Transmission
Subject
Message
E-mail
Receiver
TRAP
Transmission
Designated
Sender Address
Invalid Designated
Sender Address/
Common Login Name
IP Address
Sender IP Address
Login Name
Table 4.8.1 RSH Command Setup Parameters
Default
Value
Select Active/Inactive for the RSH server
function.
Select “Shared” or “Separate” to control
the Signal Tower lights and buzzer
Select Active/Inactive for sending an Email when a command is received.
Select the subject title for the mail to be
transmitted.
Select the message text for the mail to be
transmitted.
Select the recipient to send E-mail to. Undened ― ―
Select Active/Inactive for the TRAP
transmission when an RSH Command is
received.
Setup a designated address for a sender
when an RSH Command is recieved.
When the designated sender address
setup is not active, up to 16 accounts can
be used to notify senders when an RSH
Command is received.
The designated IP address used when a
command is executed.
The login name used is entered to allow
command execution.
Active ― ―
Inactive ― ―
1. Message ― ―
1: ― ―
Inactive ― ―
Active ― ―
Blank IP Address Format O
Blank
Blank
Input Parameter
― ―
Half-width alphanumeric char-
acter, period “.”, hyphen “-”
Maximum 16 Characters
Half-width alphanumeric char-
acter, period “.”, hyphen “-”
Maximum 16 Characters
Setting
Option
O
O
4
53

4
4.9 TRAP Reception Setup Screen
Setup for permitting a TRAP reception and its operation after the TRAP communication is received.
[Setup Method]
1. Enter a group name.
2. Enter an address name for the TRAP designated sender*.
3. Enter the OID of the TRAP received in the TRAP number column.
4. Enter the OID into the variable-bindings column*
* Refer to the following below:
5. Set up the operation for the Signal Tower when a TRAP is received.
6. Select the E-mail Sending conguration when receiving a TRAP.
When the E-mail Sending is "Active"
Select the subject title and message after the E-mail Sending is activated.
7. Select "Active" when using the TRAP transmission.
"TRAP Command" received when a TRAP condition occurs
OID: 1.3.6.1.4.1.20440.4.1.6.3
Name:. trapPatliteTrapReceived
8. Click the "Set" button to save the settings.
Please
Note
.
Please
Note
A TRAP number cannot be omitted if a TRAP designated sender address name is omitted. When
a TRAP number has been duplicated and is registered into the group, the least signicant setup
number in the group is used. The following group number after that number is not used.
• If the TRAP designated address is entered, then the TRAP number column and variable bindings can
be omitted. When the TRAP number column and variable bindings are omitted, then all operations will
be received by the TRAP transmission address which was setup for the TRAP designated sender.
• When a TRAP designated sender address name is omitted, the operation is determined only by the
TRAP number.
• Among two existing variable binding registrations, the rst registration is also possible.
• If the TRAP designated sender address name and TRAP number is omitted, it will not operate, even
with variable bindings registered.
54

Fig. 4.9.1 TRAP Reception Setup Screen
①
②
③
④
4
⑤
⑥
⑦
⑧
55

Table 4.9.1 TRAP Reception Setup Parameters
4
Item Contents
Group Name Setup a group name Blank
Trap Designated
Sender
Addresses 1 to 4
Trap Number
Items 1 to 4
OID Items 1 to 4
(variable bindings)
Model Items 1 to 4
(variable bindings)
Value Items 1 to 4
(variable bindings)
Red
Amber
Green
Blue
White
Buzzer
E-mail Transmission
Subject Select the E-mail subject title 1. Message ― ―
Message Select the E-mail message to text 1: ― ―
TRAP Transmission
Setup the designated TRAP sender addresses
from 1 to 4 for a group
Setup the Object ID TRAP numbers to receive
trap commands from 1 to 4 for the group
Setup the TRAP command object ID with variable bindings for items 1 to 4
Setup the variable bindings object ID model to
receive TRAP commands. Only integer types
can be selected
Setup the variable binding’s object ID to receive
traps.
Select from: OFF- ON- Lighting- Flashing1Flashing2- No Flashing- No Change
Select from: OFF- ON- Lighting- Flashing1Flashing2- No Flashing- No Change
Select from: OFF- ON- Lighting- Flashing1Flashing2- No Flashing- No Change
Select from: OFF- ON- Lighting- Flashing1Flashing2- No Flashing- No Change
Select from: OFF- ON- Lighting- Flashing1Flashing2- No Flashing- No Change
Select from: Pattern1- Pattern2- Pattern3- Pattern4- Stop- No Change
Select the Active/Inactive condition for the E-mail
Sending.
Select the Active/Inactive condition for the trap
transmission.
Default
Value
Blank IP Address Format O
Blank
Blank
Integer ― ―
0 Integer (0 to 65535) ―
No Change ― ―
No Change ― ―
No Change ― ―
No Change ― ―
No Change ― ―
No Change ― ―
Inactive ― ―
Inactive ― ―
Input Parameter
Full/Half-size Characters
Maximum 32 Characters
Integers and Period “.”
Maximum 127 Charac-
ters
Integers and Period “.”
Maximum 127 Charac-
ters
Setting
Option
O
O
O
56

4.10 Ping Monitor setup Screen
By setting an IP address or a host name to the address column, the Ping monitor can be used.
When the Ping monitor detects an abnormality, it generates a monitor abnormality condition as a result. After
a monitor abnormality is generated, if there is a response from a Ping request, it will then determine a recovery
from the abnormal condition, and will continue its normal operation after restoration.
A maximum number of 24 Ping monitors can be registered. Although, screen numbers from 1 to 20 have a
xed Ping monitoring period of 60 seconds, screen numbers 21 to 24 have adjustable Ping monitoring periods.
4.10.1 Ping Monitor Conguration (Screen Numbers 1 to 20)
[Setup Method]
1. Select the screen number (No. 1-20) to setup the Ping monitoring parameters.
2. Enter the IP address for a target to monitor.
3. Enter the device name for a target to monitor.
4. Set up the number of transmission times (number of times a Ping request is sent to determine a Ping
abnormality).
5. Setup the status change for the Signal Tower when a monitor abnormality is detected.
6. To send an E-mail when a monitor abnormality occurs, set the E-mail Sending to "Active".
When the E-mail Sending is activated:
Register the subject and the message text to transmit.
When the E-mail Sending is activated
Register the subject and the message text to transmit. Then, select the recipient for the E-mail Sending.
7. When using the TRAP transmission, set to "Active".
TRAP command transmitted when the TRAP is active
OID: 1.3.6.1.4.1.20440.4.1.6.1
Name: trapPatliteAlarmAdded
4
Fig. 4.10.1 Ping Monitor Setup Screen
①
②
③
④
⑤
⑥
⑦
57

4
[Setup Method Continued]
8. Setup for Signal-Tower operation when a recovery from a monitor abnormality occurs.
9. To send an E-mail when a monitor abnormality recovery occurs, set the E-mail Sending to "Active".
When the E-mail Sending is activated
Register the subject and the message text to transmit. Then, select the recipient for the E-mail Sending.
10. When using the TRAP transmission, set to "Active".
11. Click the "Set" button to activate the setup.
TRAP Command received when TRAP condition occurs
OID: 1.3.6.1.4.1.20440.4.1.6.2
Name: trapPatliteAlarmRemoved
Fig. 4.10.2 Ping Monitor Setup Screen 2
⑧
⑨
⑩
⑪
Table 4.10.1 Ping Monitor Setup Parameters
Item Contents
Monitoring Target
Address
Equipment
Name
TRAP Transmission
Frequency
Red
Amber
Green
Blue
White
Buzzer
Email Transmission
Subject Select the E-mail subject title 1. Message ― ―
Message Select the E-mail message to text 1: ― ―
TRAP Transmission Select the Active/Inactive condition for the trap transmission. Inactive ― ―
Setup the IP address or host name for ping monitoring.
Setup the name for the Ping transmission monitoring.
Setup the number of Ping requests. 0 Half-size Integers 0 to 30 ―
Select from: OFF- ONing2- No Flashing- No Change
Select from: OFF- ONing2- No Flashing- No Change
Select from: OFF- ONing2- No Flashing- No Change
Select from: OFF- ONing2- No Flashing- No Change
Select from: OFF- ONing2- No Flashing- No Change
Select from:
Pattern1- Pattern2- Pattern3- Pattern4- Stop- No Change
Select the Active/Inactive condition for the E-mail Sending.
Lighting- Flashing1- Flash-
Lighting- Flashing1- Flash-
Lighting- Flashing1- Flash-
Lighting- Flashing1- Flash-
Lighting- Flashing1- Flash-
Default
Value
Blank
Blank
No Change ― ―
No Change ― ―
No Change ― ―
No Change ― ―
No Change ― ―
No Change ― ―
Inactive ― ―
Input Parameter
IP Address or Host Name
Maximum 63 Characters
Full/Half-size Characters
Maximum 32 Characters
Setting
Option
O
O
58

4.10.2 Ping Monitor Conguration (Screen Numbers 21 to 24)
The following explains the Ping monitor setting method. A maximum number of 24 Ping monitors can be
registered.
Although the monitoring periods for screen numbers 1 through 20 is fixed at 60 seconds, the transmission
number in columns 21 through 24 can be changed (1 to 600 seconds).
[Setup Method]
1. Select the screen number between 21 to 24 to setup the Ping monitoring parameters.
2. Enter the IP address for a target to monitor.
3. Enter the device name for a target to monitor.
4. Set up the number of transmission times.
5. Set up the monitoring duration.
6. Set up the number of Ping requests within the duration.
7. Setup the condition for the Signal Tower when a monitor abnormality is detected.
8. To send an E-mail when a monitor abnormality occurs, set the E-mail Sending to "Active".
When the E-mail Sending is activated
Register the subject and the message text to transmit. Then, select the recipient for the E-mail Sending.
9. When using the TRAP transmission, set to "Active".
TRAP command transmitted when the TRAP is active
OID: 1.3.6.1.4.1.20440.4.1.6.1
Name: trapPatliteAlarmAdded
Fig. 4.10.3 Ping Monitor Setup Screen (Screen Number No. 21)
4
①
②
③
④
⑤
⑥
⑦
⑧
⑨
59

10. Setup the condition for the Signal Tower when a monitor abnormality recovery is detected.
11. To send an E-mail when a monitor abnormality recovery occurs, set the E-mail Sending to "Active".
When the E-mail Sending is activated
Register the subject and the message text to transmit. Then, select the recipient for the E-mail Sending.
12. When using the TRAP transmission, set to "Active".
TRAP Command received when TRAP condition occurs
OID: 1.3.6.1.4.1.20440.4.1.6.2
Name: trapPatliteAlarmRemoved
13. Click the "Set" button to save the settings.
Fig. 4.10.4 Ping Monitor Setup Screen 2 (Screen Numbers 21 through 24)
4
⑩
⑪
⑫
⑬
Table 4.10.2 Ping Monitor Setup Parameters ( Screen Numbers 21 to 24)
Item Contents
Monitoring Duration Setup the duration for sending a Ping response. 60 1 to 600 (sec) ―
Transmission Frequency The number of Pings to transmit within the monitoring duration
Default
Value
1 1 to 30 (times) ―
Input
Parameter
Setting
Option
60

4.11 Application Monitor Setup Screen
Setup for monitoring an application. The data reception of the target is monitored.
If data is not received within the monitoring period, it detects the communication as being abnormal, and
generates an abnormality event. After a generated event, if data is received from the monitored candidate, it
will detect a recovery from the abnormal operation.
[Setup Method]
1. Select from screen number 1 to 4 to setup an application monitor.
2. Enter the address for the targeted monitor.
3. Enter the receiving port number.
4. Enter a device name.
5. Set up the monitoring period.
Operation Setting for Monitoring Abnormality
6. Setup the condition for the Signal Tower when a monitor abnormality is detected.
7. To send an E-mail when a monitor abnormality occurs, set the E-mail Sending to "Active".
When the E-mail Sending is activated
Register the subject and the message text to transmit. Then, select the recipient for the E-mail Sending.
8. When using the TRAP transmission, set to "Active".
Fig. 4.11.1 Application Monitor Setup Screen
4
①
②
③
④
⑤
⑥
⑦
⑧
61

4
TRAP Command received when TRAP condition occurs
OID: 1.3.6.1.4.1.20440.4.1.6.6
Name: trapPatliteMonitorAppAlarmAdded
Output Control Setting for Monitoring Error Recovery
9. Setup the condition for the Signal Tower when a monitor abnormality recovery is detected.
10. To send an E-mail when a monitor abnormality recovery occurs, set the E-mail Sending to "Active".
When the E-mail Sending is activated
Register the subject and the message text to transmit. Then, select the recipient for the E-mail Sending.
11. When using the TRAP transmission, set to "Active".
TRAP Command received when TRAP Transmission condition occurs
OID: 1.3.6.1.4.1.20440.4.1.6.7
Name: trapPatliteMonitorAppAlarmRemoved
12. Click the "Set" icon button to initiate the setup.
Fig. 4.11.2 Application Monitor Setup Screen
⑨
⑩
⑪
⑫
62

Table 4.11.1 Application Monitor Setup Parameters
Item Contents
Monitoring Target
Address
Reception Port
Number
Equipment
Name
Monitoring
Duration
Red
Amber
Green
Blue
White
Buzzer
Email
Transmission
Subject Select the E-mail subject title 1. Message ― ―
Message Select the E-mail message to text 1: ― ―
TRAP
Transmission
Setup the IP address for transmission monitoring. Blank IP Address Format O
Set up the reception port used for the application
monitoring.
Setup the name for the Ping transmission monitoring.
Setup the duration for monitoring the application
software.
Select from: OFF- ONNo Flashing- No Change
Select from: OFF- ONNo Flashing- No Change
Select from: OFF- ONNo Flashing- No Change
Select from: OFF- ONNo Flashing- No Change
Select from: OFF- ONNo Flashing- No Change
Select from:
Pattern1- Pattern2- Pattern3- Pattern4- Stop- No Change
Select the Active/Inactive condition for the E-mail Sending.
Select the Active/Inactive condition for the trap
transmission.
Lighting- Flashing1- Flashing2-
Lighting- Flashing1- Flashing2-
Lighting- Flashing1- Flashing2-
Lighting- Flashing1- Flashing2-
Lighting- Flashing1- Flashing2-
Default
Value
Half-width numbers 9000-
0
Blank
0
No Change ― ―
No Change ― ―
No Change ― ―
No Change ― ―
No Change
No Change ― ―
Inactive ― ―
Inactive ― ―
9999 (When the address
column for the monitor is
Full/Half-width Characters
Maximum 31 Characters
Half-width alphanumeric
1 through 60000(sec)
Input
Parameter
blank, it is 0)
―
Setting
Option
―
O
O
―
4
63

4
4.12 "Clear" Control Setup Screen
Setup the operation to clear the status with the "CLEAR" button, or to combine with other commands to clear
the Signal Tower status.
Clear All : A function to clear both the Signal Tower and buzzer status and return to its normal
mode of operation.
Depress twice to clear all : One press of the "CLEAR" button to stop the buzzer sound.
Pressing the "CLEAR" button a second time returns it to its normal mode of
operation.
[Setup Method]
1. When using the "CLEAR" button to return to its normal mode after an E-mail Sending and TRAP
transmission are received, select the "Active" radio button.
2. When using the "CLEAR" command from an SNMP clear execution to return to its normal mode after an
E-mail Sending and TRAP transmission are received, select the "Active" radio button.
3. When using the "CLEAR" from an RSH command execution to return to its normal mode after an E-mail
Sending and TRAP transmission are received, select the "Active" radio button.
When selecting "Active" for E-mail Sending
Select the preferred E-mail subject title and text.
Select the Receiver for the E-mail to be sent to.
4. Select the clear switch setup for either "Clear All" or "Depress twice to clear all".
5. Click the "Set" button to save the settings.
"TRAP Command" received when a TRAP condition occurs
OID: 1.3.6.1.4.1.20440.4.1.6.4
Name: trapPatliteClearExecuted
Fig. 4.12.1 "Clear" Control Setup Screen
①
②
③
④
⑤
Table 4.12.1 "Clear" Control Setup Parameters
Item Contents Default
Value
E-mail Sending Select the Active/Inactive condition for the E-mail Sending. Inactive ― ―
Subject Select the E-mail subject title 1. Message ― ―
Message Select the E-mail message to text 1: ― ―
Unassigned 1 to 8 Select from 1 to 8 Addresses to send E-mail to. Unassigned ― ―
TRAP Transmission
Select the Active/Inactive condition for the TRAP Transmission.
Inactive ― ―
Input
Parameter
Setting
Option
“CLEAR” Button Setting
64
Select the setup conditions for when the “CLEAR” button is pressed.
Clear All ― ―

4.13 Normal Mode Setup Screen
Set up the status of the Signal Tower for its normal operating condition.
[Setup Method]
1. Select the desired status for the Signal Tower to be at its normal operating condition.
2. Click the "Set" icon button to initiate the setup.
3. After the setup is complete, press the "Clear" switch on the body for the normal operating condition to be
displayed.
Fig. 4.13.1 Normal Mode Setup Screen
①
Table 4.13.1 Normal Mode Setup Parameters
Item Contents
Signal
Tower
Select from:
Red
Lighting
Amber
Lighting
Green
Lighting
Blue
Lighting
White
Lighting
Default
Value
Do not
light-up
Input
Parameter
— —
②
Setting
Option
4
65

4
4.14 Test Button Setup Screen
The following settings can be used to output an operation when the "TEST" button is pressed.
[Setup Method]
To output an E-mail Sending and TRAP transmission when the "TEST" button is pressed, select the "Active"
radio button.
When sending an E-mail, select the "Active" radio button
1. Select the preferred E-mail subject title and text.
Select the Receiver for the E-mail to be sent to.
The "TRAP Command" for this product to receive when the TRAP condition occurs
OID: 1.3.6.1.4.1.20440.4.1.6.8
Name: trapPatliteTestSwExecuted
2. Click the "Set" button to activate the setup.
Fig. 4.14.1 Test Switch Setup Screen
①
②
Table 4.14.1 Test Switch Setup Parameters
Item Contents
E-mail Sending Select the Active/Inactive condition for the E-mail Sending. Inactive — —
Subject Select the E-mail subject title 1: Message — —
Message Select the E-mail message to text 1: — —
Unassigned 1 to 8 Select from 1 to 8 Addresses to send E-mail to. Unassigned — —
Receiver Select the Address to send E-mail to Unused — —
TRAP Transmission Select the Active/Inactive condition for the TRAP Transmission Inactive — —
Default
Value
Input
Parameter
Setting
Option
66
Note
Refer to "3.3 Test Functions" for more information on the test operation.

4.15 Output Control Setting for Signal Tower Screen
Verify the current operating status, and output a condition status for the Signal Tower.
[Setup Method]
1. Check the current operating condition of the Signal Tower.
2. Select the desired outputs for the Signal Tower status in the "Output Control" column to operate it.
3. Click the "Execute Output" button. The Signal Tower output will reect the setup performed in (2).
4. If the "Execute Clear" button is clicked, it will return to the "Normal Mode" status.
Fig. 4.15.1 Signal Tower Output Control Screen
① ②
4
③
④
Table 4.15.1 Signal Tower Output Control Setup Parameters
Item Contents
Red Select from: OFF- ON-
Amber Select from: OFF- ON-
Green Select from: OFF- ON-
Blue Select from: OFF- ON-
White Select from: OFF- ON-
Buzzer Select from:Pattern1- Pattern2- Pattern3- Pattern4- Stop ― ― ―
Lighting- Flashing1- Flashing2- No Flashing- No Change
Lighting- Flashing1- Flashing2- No Flashing- No Change
Lighting- Flashing1- Flashing2- No Flashing- No Change
Lighting- Flashing1- Flashing2- No Flashing- No Change
Lighting- Flashing1- Flashing2- No Flashing- No Change
Default
Value
― ― ―
― ― ―
― ― ―
― ― ―
― ― ―
Input
Parameter
Setting
Option
67

4
4.16 Reinitialization Setup Screen
The setup parameters can be reset to their default values by initializing this product. The network setup can be
selected to be excluded from initialization.
If the network setup is also required to be reset to its factory defaults, it can be selected to be initialized with the rest of
the setup parameters.
If the "Reinitialize Network Settings" is not checked, all but the network setup is initialized.
"Network Setup" refers to the "IP address for this product, Net Mask, Default
Note
Gateway, DNS server address and Host Name" parameters in the System Setup
Screen.
[Setup Method]
When the initialization does not require the network setup to be included
1. Put a "Check" in the box for "Network Reboot".
2. Click the "Reinitialize Execute" button.
When the network setup also needs to be reinitialized
2. Just click the "Reinitialize Execute" button.
Please
If the network setup is also initialized, since the IP address will return to its
factory default value of “192.168.10.1”, the network has to be setup again.
Fig. 4.16.1 Reinitialization Screen
①
②
68

4.17 Reboot Screen
This product can be rebooted just by clicking the "Reboot" button.
1. Once the "Reboot" button is clicked, a new screen will display a message indicating it is rebooting.
2. Click "To the Login screen" on the new screen to log back in.
Please
If this product is rebooted, because all of the event log data will be erased, it is
recommended to download the event log prior to rebooting, for reloading afterwards.
Fig. 4.17.1 Reboot Screen
4
Fig. 4.17.2 Login after Reboot Screen
69

4
4.18 Event Log Screen
Events from this product are logged and is shown in the event log.
By clicking the "Event Log Download", an event log le can be downloaded.
A maximum of 255 logged events are acquirable.
The event log data will be erased if either of the following operations are executed.
Please
• Turning the power supply "OFF"
• Reinitializing this product from the initialization screen.
• Rebooting this product from the “Reboot Screen”.
• Updating the rmware.
Fig. 4.18.1 Event Log Screen
70

4.19 Conguration Save/Load Setup Screen
The conguration for this product can be read, and saved as cong data on the PC.
Moreover, the conguration le read off of this product can be selected and uploaded.
Please
[Setup Method]
Reading Conguration Data
1. Click the "Read" button to save the cong data onto the logged in PC.
Writing Conguration Data
2. Click the "Browse..." button to select the cong data to write into this product.
3. Click the "Write" button to start the uploading of the cong data.
4. After the cong data is uploaded, this product will automatically reboot.
The network setup and user information is not included in the cong data.
Fig. 4.19.1 Conguration Save/Load Setup Screen
4
①
②
③
71

4.20 Firmware Update Screen
The rmware for this product can be updated.
After the rmware has been updated, this product automatically reboots.
[Setup Method]
1. Click the "reference" button to designate the rmware to rewrite for this product.
2. Clicking the "update" button will start the rmware update.
Do not disconnect the power cable or LAN cable during the update.
Possible cause of failure may occur.
Please
Updating the rmware does not affect the current setup parameters, however, it
does affect the Event Log. Therefore, it is recommended to backup the “Event
Log” prior to updating the rmware.
Fig. 4.20.1 Firmware Update Setup Screen
①
4
②
Fig. 4.20.2 Firmware Update Failure Screen
72
Please
Fig. 4.20.2 shows the type of screen in case an error occurs during the rmware update.
If an error occurs during the rmware update, please try again.
If an error repeatedly occurs during the rmware update process, please contact your
nearest Patlite Sales Representative.

4.21 Setup Table Entry Screen
The "Setup Table Entry" screen lists and displays the contents of settings, operation functions, such as application
monitor abnormality and abnormality restoration; Ping monitor abnormality and abnormality restoration; TRAP
reception setup operations, as well as the rmware version of this product.
The solid circle indicates when the E-mail Sending and TRAP transmission are activated. The dash lines display
where items selected are not changed.
[Display]
1. Current rmware version.
2. "TRAP Output Control Setting for Reception" table entries (1-16) to indicate setup conditions.
3. "PING Operation Setting for Monitoring Abnormality" table entries (1-16) to indicate setup conditions.
Fig. 4.21 Setup Table Entry Screen
①
4
②
③
73

5 MIB
With this product, there is an exclusive MIB (Management Information Base) for the NH Series, and the
monitor controls can be operated by the SNMP manager, etc.
5.1 MIB Denition List
5
iso(1)
networkSignalTower(1)
org(3)
ident(1)
cong(2)
alarm(3)
monitor(4)
dod(6)
identSwInitVersion(1)[OCTET STRING]
■
identSwAgentVersion(2)[OCTET STRING]
■
identHwVersion(3)[OCTET STRING]
■
pingServer(1)
internet(1)
pingServerNumEntries(1)[INTEGER]
■
pingServerTable(2)
private(4)
enterprises(1)
patlite(20440)
patliteModule(4)
pingServerTableEntry(1)
pingServerTableIndex(1)[INTEGER]
pingServerName(2)[OCTET STRING]
pingServerAlertValue(3)[INTEGER]
pingServerIpAddress(4)[OCTET STRING]
74
trapCatcher(2)
logDump(3)
logDumpEventLog1(1)[OBJECT IDENTIFIER]
logDumpEventLog2(2)[OBJECT IDENTIFIER]
logDumpEventLog3(3)[OBJECT IDENTIFIER]
Note Please use the PRHS when acquisitioning a SNMP data log dump
.

control(5)
controlLight(1)
■controlLightNumEntries(1)[INTEGER]
controlLightTable(2)
controlLightTableEntEntry(1)
controlLightDeviceColor(1)[INTEGER]
controlLightControlState(2)[INTEGER]
controlLightControlTimer(3)[INTEGER]
controlLightCurrentState(4)[INTEGER]
controlLightSnmpClear(3)[INTEGER]
trap(6)
■trapPatliteAlarmAdded(1)[OBJECT IDENTIFIER]
■trapPatliteAlarmRemoved(2)[OBJECT IDENTIFIER]
■trapPatliteTrapReceived(3)[OBJECT IDENTIFIER]
■trapPatliteClearExecuted(4)[OBJECT IDENTIFIER]
■trapPatliteRshExecuted(5)[OBJECT IDENTIFIER]
■trapPatliteAppMonitorAlarmAdded(6)[OBJECT IDENTIFIER]
■trapPatliteAppMonitorAlarmRemoved(7)[OBJECT IDENTIFIER]
■trapPatliteTestSwExecuted(8)[OBJECT IDENTIFIER]
5.2 PATLITE MIB SPECIFICATIONS
The following explains the MIB Specication for the NH Series Monitoring Tower.
iso(1)
org(3)
dod(6)
internet(1)
private(4)
enterprises(1)
networkSignalTower(1)
ident(1)
cong(2)
alarm(3)
monitor(4)
control(5)
trap(6)
5
patlite(20440)
patliteModule(4)
75

5
Table 6.2.1 MIB Specications
OID Name Model
1 ident
1.1.0 identSWinitVersion String(2) read-only
1.2.0 identSWAgentVersion String(3) read-only Application Version
1.3.0 idensHWVersion String(3) read-only
4 monitor
4.1 pingServer
4.1.1.0 pingServerNumEntries INTEGER read-only
4.1.2.0 pingServerTable not-accessible
4.1.2.1.0 pingServerTableEntry not-accessible
4.1.2.1.1.(index)
4.1.2.1.2.(index)
4.1.2.1.3.(index)
4.1.2.1.4.(index) pingServerIpAddress STRING(63) read-only ping monitoring address
4.3 logDump
4.3.1.0 logDumpEventlog1 OBJECT IDENTFIER read-only
4.3.2.0 logDumpEventlog2 OBJECT IDENTFIER read-only
4.3.3.0 logDumpEventlog3 OBJECT IDENTFIER read-only
5.1 controlLight
5.1.1.0 controlLightNumEntries INTEGER read-only
5.1.2.0 controlLightTable not-accessible
5.1.2.1.0 controlLightTableEntry not-accessible
5.1.2.1.1.(index)
5.1.2.1.2.(index) controlLightControlState
5.1.2.1.3.(index) controlLightControlTimer INTEGER(-1,99) read-write
5.1.2.1.4.(index) controlLightCurrentState
5.1.3.0 controlLightSnmpClear
6 Trap
6.1 trapPatliteAlarmAdded OBJECT-IDENTIFIER not-accessible When an abnormality in the PING occurs
6.2 trapPatliteAlarmRemoved OBJECT-IDENTIFIER not-accessible
6.3 trapPatliteTrapReceived OBJECT-IDENTIFIER not-accessible When a trap is received
6.4 trapPatliteClearExecuted OBJECT-IDENTIFIER not-accessible When the clear button is pushed
6.5 trapPatliteRshExecuted OBJECT-IDENTIFIER not-accessible When an RSH command is executed
6.6 trapPatliteAppMonitorAlarmAdded OBJECT-IDENTIFIER not-accessible
6.7 trapPatliteAppMonitorAlarmRemoved OBJECT-IDENTIFIER not-accessible
6.8 trapPatliteTestSwExecuted
pingServerTableIndex INTEGER read-only
pingServerName STRING(31) read-only
pingServerAlertValue
controlLightDeviceColor
INTEGER{ normal(1),
occurred(2) }
INTEGER {red(1), amber(2), green(3), blue(4),
clear(5), buzzer(6) }
INTEGER {turn-off(1),
turn-ON(2), blinking-pat--pattern(3), nop(4), blinkingpatern2(5), soundpattern4(6) }
INTEGER { off(1), on(2),
blinking-pattern1(3),
blinking-pattern2(4),
sound-pattern4(5) }
INTEGER{ execute(1),
nop(0) }
OBJE CT-IDENTIFI-ERnot- accessi-
MAX-ACCESS
read-only
read-only
read-write
read-only
read-write
ble
Comment
ID Group
OS Version
Hardware Version
Monitor Group
ping monitoring setting
Ping monitoring count
ping monitoring table
ping monitoring index
ping monitor name
ping monitor condition
normal(1), event occurred(2)
log setting
event log from 1 to 85
event log from 86 to 170
event log from 171 to 255
signal tower control
count of control entries
signal tower table
signal tower color
R(1)/Y(2)/G(3)/B(4)/C(5)/Buz(6)
Signal Tower Status: lights and buzzer
off(1)/lighting and buzzer synchronized
withlightpattern1(2)/ashingpattern1
and buzzer synchronized with light
pattern2(3)/nochange(4)/ashingpattern2 and buzzer synchronized with light
pattern3(5)/buzzer synchronized with light
pattern 4(6). controlLightControlTimer is
set by entering values above zero.
A preset value is decremented for every
second until it is 0, then it changes to the
status designated by the controlLightControlState.
The present status is displayed.
lights and buzzer off(1)/lighting and buzzer
synchronizedwithlightpattern1(2)/ashing pattern1 and buzzer synchronized
withlightpattern2(3)/ashingpattern2and
buzzer synchronized with light pattern3(4)/
buzzer synchronized with light pattern4(5)
execute(1) setup will clear the Signal
Tower operation.
When an abnormality in the PING is
restored
When an abnormality in the application
occurs
When an abnormality in the application is
restored
When the test switch is pushed
76

6 Replacement and Option Parts
The following explains the repair and maintenance parts of this product. Signal Tower tiers can be increased
or decreased by the customer by purchasing the necessary parts.
6.1 Replacement Parts
The following is the replacement part list for the NHL, NHP and NHS Series. When inquiring, please ask
the store where you purchased this product. Rubber feet, AC Adaptor, and adhesive seal are common
accessories.
Table 6.1.1 NH Series Replacement Parts
Model Name Part Name Part Number
Head Cover B32310027-1F1
Center Shaft 5 Tier S33552120-04225F1
Center Shaft 4 Tier S33552120-04180F1
Center Shaft 3 Tier S33552120-04140F1
Center Shaft 2 Tier S33552120-04100F1
NHL (φ60 Type)
Center Shaft 1 Tier S33552120-0455F1
LED Unit Red B72100168-1F1
LED Unit Amber B72100168-2F1
LED Unit Green B72100168-3F1
LED Unit Blue B72100168-4F1
LED Unit White B72100167-7F1
Table 6.1.2 Compatable Replacement Parts
Part Name Part Number
Cover Seal T93190007-1F1
Rubber Feet T81800007-F1
Bottom Seal T93130009-F1
Support Base (Screws Included) T81800019-F1
6
77

6.2 Signal Tower Unit Color Arrangement
Snaps
Snaps
Align sna ps with Tab s
Align sna ps with Tab s
Connector s
The following explains the method when rearranging or repairing the LED units from customer purchased
parts.
6.2.1 NHL Signal Tower Unit (Color) Rearrangement Method
Turn the power off before changing the color sequence.
1.
Carefully peel off the cover sticker, then loosen the center shaft and remove the head cover and shaft.
2.
Because the upper and lower LED units are secured to each other by two snaps, carefully remove the
LED unit by gently pushing the snaps inward.
When increasing or decreasing tiers, be sure to replace the center shaft with the proper length to match
3.
the number of tiers when changing.
After the center shaft is properly xed, place the static-free cover sticker back on.
4.
6
Please
Fig. 6.2.1 NHL Signal Tower Unit (Color) Rearrangement Figure
• Do not attempt to forcibly detach an LED unit. Failure to comply may damage the unit.
• The LED unit falling and breaking may result if the center shaft is not properly tightened.
• Overtightening the center shaft may cause damage to the threads or tapping hole, causing
possible malfunction or damage to the LED units.
• Be sure to torque the center screw no more than 0.68 N-m. Failure to do so may cause
damage to the unit
• Be careful of the contact pins when handling the LED unit, they may be sharp.
78

6.3 Option Parts
The following explains the mounting instructions of this product for the option parts available that customers
had purchased.
6.3.1 Wall Mount Bracket
This product can be attached to a wall with the wall mount bracket. One wall mount bracket can be used to
attach this product on either the left-side or right-side of the wall.
C
R
L
A
E
RESET
TEST
HIGH
LOW
VOL.
OFF
RX/TX
LINK
24VDC
C
R
L
A
E
RESET
TEST
HIGH
LOW
VOL.
OFF
RX/TX
LINK
24VDC
Fig. 6.3.1 Wall Mount Surface Bracket Figure
(Figure to the left indicates the left-sided attachment; gure to the right indicates the right-sided attachment)
Please
The installation direction for this product is only for the front attachment direction.
6
79

Installation Method
[
]
1. After deciding on the attachment direction of the wall mount bracket, assemble this product to the bracket.
(Use the same installation screw enclosed for assembling the Support Base).
113
16
NHL Unit
62
4-φ6
70
38
NH-WST
Mounting Screws
Bracket
Mounting
79
Location
NHL Underside View NH-WST Outside Appearance Installation Procedure
Fig. 6.3.2 Wall Mount Bracket Installation Diagram
2. Fix the wall mount bracket to the wall surface. Please select the proper screw when installing the wall
mount bracket to the customer's wall in accordance to the quality of the wall material to be mounted upon.
Tighten the screws between this product and the bracket with a torque of about 0.39 N-m.
Please
Failure to do so may cause damage to the unit.
Verify the installation is securely clamped to ensure there is no fear of detachment and falling
after installation. Apply the power after checking that it has been installed correctly.
6
Option Name Part Number
Wall Mounting Bracket NH-WST
6.3.2 Partition Mounting Bracket
The partition mounting bracket is an optional item for attaching to partition walls in environments which cannot
be attached to walls or other positions. The partition mounting bracket is designed to be attached with the front
of this product facing to the right or left when fastening it to the partition.
C
R
L
A
E
RESET
TEST
HIGH
LOW
VOL.
OFF
RX/TX
LINK
24VDC
C
R
L
A
E
RESET
TEST
HIGH
LOW
VOL.
OFF
RX/TX
LINK
24VDC
80
Please
Fig. 6.3.3 Partition mounting bracket installation example
(Left image is for the left-side and the right image is for the right-side installations)
The installation direction for this product is only for the front attachment direction.

Installation Method
[
]
1. After deciding on the attachment direction of the partition mounting bracket, assemble this product to the
bracket. (Use the screws include when assembling).
100
100
NHL Unit
45
NH-WST
70.2
Mounting Screws
Bracket
Mounting
Location
NHL Underside View NH-WST Outside Appearance Installation Procedure
Fig. 6.3.4 Partition mounting bracket installation method
Please
Tighten the screws between this product and the partition mounting bracket with a
torque of about 0.39 N-m. Failure to do so may cause damage to the unit.
2. Check the width of the partition, then select the proper clamping screw to thread through the bracket. Attach the
pressure plate and ttings.
RESET
TEST
VOL.
HIGH
LOW
OFF
RESET
TEST
VOL.
HIGH
LOW
OFF
Long clamping screw application Short clamping screw application
6
Fig. 6.3.5 Installation Method 1
3. Turn the clamping screw clockwise to tighten.
RESET
TEST
HIGH
LOW
VOL.
OFF
The long clamping screw is effective
for thicknesses of 18 to 48mm.
Fig. 6.3.6 Installation Method 2
Option Name Part Number
Partition Mounting Bracket NH-PST
Please
The partition mounting bracket may break if too much torque is applied.
RESET
TEST
HIGH
LOW
VOL.
OFF
The short clamping screw is effective
for thicknesses of 48 to 58mm.
81

7
7 Troubleshooting
Problem Check the following
The power does not turn on. • Check whether the AC Adaptor is connected correctly.
• Check whether the LAN connector is connected correctly.
The Web setup tool does not
display.
The Web setup tool does not
display correctly.
The Signal Tower does not turn
on.
The buzzer does not sound.
Socket communication does not
work.
The RSH command data is
unreceivable.
I want to return it to the factory
settings.,
The E-mail transmission cannot
be sent.
The SNMP SET/GET does not
work.
• Check the setup for the IP address on this product.
• Check the setup for the IP address on the PC side.
• Refer to 2.5 "Network Setup" for the IP address set up procedure.
• Make sure the browser information has been recently updated.
• Check whether the AC Adaptor is connected correctly.
• Check the setup of the Signal Tower operation with the Web setup tool.
Refer to "4.13 Normal Mode Setting Screen" for the procedure to set up for the
normal operation mode.
• After any recombination of tiers to the Signal Tower has been done, check whether
the Signal Tower lights up by accessing the Signal-Tower Output Control screen. If
the light does not turn on, it may not be installed correctly.
Refer to "4.15 Signal-Tower Output Control Screen" for the procedure to control
the Signal-Tower output.
• Check whether the volume switch has been set in the "OFF" position.
• After each setup, check the buzzer operation.
Refer to "4.15 Signal-Tower Output Control Screen" for the procedure to setup the
buzzer output.
• Check whether the correct communication port has been set.
Refer to "4.5 Socket Communication Conguration Screen" for the setup procedure
of the Socket Communication.
• Check whether the data had been sent correctly.
For data transmitted by the Socket Communication, refer to "3.5 PHN Command
Reception Function" and "3.6 PNS Command Reception Function".
• Check the command reception setup.
Refer to "4.8 Command Reception Conguration Screen" for the setup procedure
of the command reception.
• Check whether the security settings for the PC has granted permission.
• Refer to "3.13 Reinitialization".
• Check whether the setup for the server is correct.
• Check the SET Community name and GET Community name.
The status LED is ashing. • It may be in the factory-shipment inspection mode. Please reboot this product.
82

8 Freeware Terms of Agreement
The following chapter clearly outlines the copyrights for the freeware software used with this product.
8.1 GNU GENERAL PUBLIC LICENCE
GNU GENERAL PUBLIC LICENSE
Version 2, June 1991
Copyright (C) 1989, 1991 Free Software Foundation, Inc.
675 Mass Ave, Cambridge, MA 02139, USA
Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not
allowed.
Preamble
The licenses for most software are designed to take away your freedom to share and change it. By contrast, the
GNU General Public License is intended to guarantee your freedom to share and change free software--to make sure
the software is free for all its users. This General Public License applies to most of the Free Software Foundation’s
software and to any other program whose authors commit to using it. (Some other Free Software Foundation
software is covered by the GNU Library General Public License instead.) You can apply it to your programs, too.
When we speak of free software, we are referring to freedom, not price. Our General Public Licenses are
designed to make sure that you have the freedom to distribute copies of free software (and charge for this service if
you wish), that you receive source code or can get it if you want it, that you can change the software or use pieces of
it in new free programs; and that you know you can do these things.
To protect your rights, we need to make restrictions that forbid anyone to deny you these rights or to ask you
to surrender the rights. These restrictions translate to certain responsibilities for you if you distribute copies of the
software, or if you modify it.
For example, if you distribute copies of such a program, whether gratis or for a fee, you must give the recipients
all the rights that you have. You must make sure that they, too, receive or can get the source code. And you must
show them these terms so they know their rights.
We protect your rights with two steps:
(1) copyright the software, and
(2) offer you this license which gives you legal permission to copy, distribute and/or modify the software.
Also, for each author’s protection and ours, we want to make certain that everyone understands that there is no
warranty for this free software. If the software is modied by someone else and passed on, we want its recipients to
know that what they have is not the original, so that any problems introduced by others will not reect on the original
authors’ reputations.
Finally, any free program is threatened constantly by software patents. We wish to avoid the danger that
redistributors of a free program will individually obtain patent licenses, in effect making the program proprietary. To
prevent this, we have made it clear that any patent must be licensed for everyone’s free use or not licensed at all.
The precise terms and conditions for copying, distribution and modication follow.
8
83

8
GNU GENERAL PUBLIC LICENSE
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
0. This License applies to any program or other work which contains a notice placed by the copyright holder saying
it may be distributed under the terms of this General Public License. The "Program", below, refers to any such
program or work, and a "work based on the Program" means either the Program or any derivative work under
copyright law: that is to say, a work containing the Program or a portion of it, either verbatim or with modications
and/or translated into another language. (Hereinafter, translation is included without limitation in the term
"modication".) Each licensee is addressed as "you".
Activities other than copying, distribution and modication are not covered by this License; they are outside its
scope. The act of running the Program is not restricted, and the output from the Program is covered only if its
contents constitute a work based on the Program (independent of having been made by running the Program).
Whether that is true depends on what the Program does.
1. You may copy and distribute verbatim copies of the Program's source code as you receive it, in any medium,
provided that you conspicuously and appropriately publish on each copy an appropriate copyright notice and
disclaimer of warranty; keep intact all the notices that refer to this License and to the absence of any warranty; and
give any other recipients of the Program a copy of this License along with the Program.
You may charge a fee for the physical act of transferring a copy, and you may at your option offer warranty
protection in exchange for a fee.
2. You may modify your copy or copies of the Program or any portion of it, thus forming a work based on the Program,
and copy and distribute such modications or work under the terms of Section 1 above, provided that you also
meet all of these conditions:
a) You must cause the modied les to carry prominent notices stating that you changed the les and the date of
any change.
b) You must cause any work that you distribute or publish, that in whole or in part contains or is derived from the
Program or any part thereof, to be licensed as a whole at no charge to all third parties under the terms of this
License.
c) If the modied program normally reads commands interactively when run, you must cause it, when started
running for such interactive use in the most ordinary way, to print or display an announcement including an
appropriate copyright notice and a notice that there is no warranty (or else, saying that you provide a warranty)
and that users may redistribute the program under these conditions, and telling the user how to view a copy of
this License. (Exception: if the Program itself is interactive but does not normally print such an announcement,
your work based on the Program is not required to print an announcement.)
These requirements apply to the modied work as a whole. If identiable sections of that work are not derived
from the Program, and can be reasonably considered independent and separate works in themselves, then this
License, and its terms, do not apply to those sections when you distribute them as separate works. But when
you distribute the same sections as part of a whole which is a work based on the Program, the distribution of the
whole must be on the terms of this License, whose permissions for other licensees extend to the entire whole,
and thus to each and every part regardless of who wrote it.
Thus, it is not the intent of this section to claim rights or contest your rights to work written entirely by you;
rather, the intent is to exercise the right to control the distribution of derivative or collective works based on the
Program.
In addition, mere aggregation of another work not based on the Program with the Program (or with a work
based on the Program) on a volume of a storage or distribution medium does not bring the other work under the
scope of this License.
84

3. You may copy and distribute the Program (or a work based on it, under Section 2) in object code or executable
form under the terms of Sections 1 and 2 above provided that you also do one of the following:
a) Accompany it with the complete corresponding machine-readable source code, which must be distributed under
the terms of Sections 1 and 2 above on a medium customarily used for software interchange; or,
b) Accompany it with a written offer, valid for at least three years, to give any third party, for a charge no more than
your cost of physically performing source distribution, a complete machine-readable copy of the corresponding
source code, to be distributed under the terms of Sections 1 and 2 above on a medium customarily used for
software interchange; or,
c) Accompany it with the information you received as to the offer to distribute corresponding source code. (This
alternative is allowed only for noncommercial distribution and only if you received the program in object code or
executable form with such an offer, in accord with Subsection b above.)
The source code for a work means the preferred form of the work for making modications to it. For
an executable work, complete source code means all the source code for all modules it contains, plus
any associated interface denition les, plus the scripts used to control compilation and installation of the
executable. However, as a special exception, the source code distributed need not include anything that is
normally distributed (in either source or binary form) with the major components (compiler, kernel, and so on) of
the operating system on which the executable runs, unless that component itself accompanies the executable.
If distribution of executable or object code is made by offering access to copy from a designated place, then
offering equivalent access to copy the source code from the same place counts as distribution of the source
code, even though third parties are not compelled to copy the source along with the object code.
4. You may not copy, modify, sublicense, or distribute the Program except as expressly provided under this License.
Any attempt otherwise to copy, modify, sublicense or distribute the Program is void, and will automatically
terminate your rights under this License. However, parties who have received copies, or rights, from you under
this License will not have their licenses terminated so long as such parties remain in full compliance.
5. You are not required to accept this License, since you have not signed it. However, nothing else grants you
permission to modify or distribute the Program or its derivative works. These actions are prohibited by law if
you do not accept this License. Therefore, by modifying or distributing the Program (or any work based on the
Program), you indicate your acceptance of this License to do so, and all its terms and conditions for copying,
distributing or modifying the Program or works based on it.
6. Each time you redistribute the Program (or any work based on the Program), the recipient automatically receives a
license from the original licensor to copy, distribute or modify the Program subject to these terms and conditions.
You may not impose any further restrictions on the recipients’ exercise of the rights granted herein. You are not
responsible for enforcing compliance by third parties to this License.
7. If, as a consequence of a court judgment or allegation of patent infringement or for any other reason (not limited
to patent issues), conditions are imposed on you (whether by court order, agreement or otherwise) that contradict
the conditions of this License, they do not excuse you from the conditions of this License. If you cannot distribute
so as to satisfy simultaneously your obligations under this License and any other pertinent obligations, then as a
consequence you may not distribute the Program at all. For example, if a patent license would not permit royaltyfree redistribution of the Program by all those who receive copies directly or indirectly through you, then the only
way you could satisfy both it and this License would be to refrain entirely from distribution of the Program.
If any portion of this section is held invalid or unenforceable under any particular circumstance, the balance of the
section is intended to apply and the section as a whole is intended to apply in other circumstances.
It is not the purpose of this section to induce you to infringe any patents or other property right claims or to
contest validity of any such claims; this section has the sole purpose of protecting the integrity of the free software
distribution system, which is implemented by public license practices. Many people have made generous
contributions to the wide range of software distributed through that system in reliance on consistent application
of that system; it is up to the author/donor to decide if he or she is willing to distribute software through any other
system and a licensee cannot impose that choice.
This section is intended to make thoroughly clear what is believed to be a consequence of the rest of this License.
8
85

8. If the distribution and/or use of the Program is restricted in certain countries either by patents or by copyrighted
interfaces, the original copyright holder who places the Program under this License may add an explicit
geographical distribution limitation excluding those countries, so that distribution is permitted only in or among
countries not thus excluded. In such case, this License incorporates the limitation as if written in the body of this
License.
9. The Free Software Foundation may publish revised and/or new versions of the General Public License from time
to time. Such new versions will be similar in spirit to the present version, but may differ in detail to address new
problems or concerns.
Each version is given a distinguishing version number. If the Program species a version number of this License
which applies to it and “any later version”, you have the option of following the terms and conditions either of that
version or of any later version published by the Free Software Foundation. If the Program does not specify a
version number of this License, you may choose any version ever published by the Free Software Foundation.
10. If you wish to incorporate parts of the Program into other free programs whose distribution conditions are different,
write to the author to ask for permission. For software which is copyrighted by the Free Software Foundation, write
to the Free Software Foundation; we sometimes make exceptions for this. Our decision will be guided by the two
goals of preserving the free status of all derivatives of our free software and of promoting the sharing and reuse of
software generally.
NO WARRANTY
11. BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY FOR THE
PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN OTHERWISE STATED
IN WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES PROVIDE THE PROGRAM “AS IS”
WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED
TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE.
THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD
THE PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING, REPAIR
OR CORRECTION.
8
12. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING WILL ANY
COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR REDISTRIBUTE THE PROGRAM
AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES, INCLUDING ANY GENERAL, SPECIAL,
INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR INABILITY TO USE THE
PROGRAM (INCLUDING BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING RENDERED INACCURATE
OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE
WITH ANY OTHER PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE
POSSIBILITY OF SUCH DAMAGES.
86

END OF TERMS AND CONDITIONS
Appendix: How to Apply These Terms to Your New Programs
If you develop a new program, and you want it to be of the greatest possible use to the public, the best way to
achieve this is to make it free software which everyone can redistribute and change under these terms.
To do so, attach the following notices to the program. It is safest to attach them to the start of each source le to
most effectively convey the exclusion of warranty; and each le should have at least the "copyright" line and a pointer
to where the full notice is found.
<one line to give the program's name and a brief idea of what it does.>
Copyright (C) 19yy <name of author>
This program is free software; you can redistribute it and/or modify it under the terms of the GNU General Public
License as published by the Free Software Foundation; either version 2 of the License, or (at your option) any later
version.
This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the
implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General
Public License for more details.
You should have received a copy of the GNU General Public License along with this program; if not, write to the
Free Software Foundation, Inc., 675 Mass Ave, Cambridge, MA 02139, USA.
Also add information on how to contact you by electronic and paper mail.
If the program is interactive, make it output a short notice like this when it starts in an interactive mode:
Gnomovision version 69, Copyright (C) 19yy name of author
Gnomovision comes with ABSOLUTELY NO WARRANTY; for details type `show w’.
This is free software, and you are welcome to redistribute it under certain conditions; type `show c’ for details.
The hypothetical commands `show w’ and `show c’ should show the appropriate parts of the General Public
License. Of course, the commands you use may be called something other than `show w’ and `show c’; they could
even be mouse-clicks or menu items--whatever suits your program.
You should also get your employer (if you work as a programmer) or your school, if any, to sign a “copyright
disclaimer” for the program, if necessary. Here is a sample; alter the names:
Yoyodyne, Inc., hereby disclaims all copyright interest in the program
`Gnomovision’ (which makes passes at compilers) written by James Hacker.
<signature of Ty Coon>, 1 April 1989
Ty Coon, President of Vice
8
This General Public License does not permit incorporating your program into proprietary programs. If your program
is a subroutine library, you may consider it more useful to permit linking proprietary applications with the library. If
this is what you want to do, use the GNU Library General Public License instead of this License.
87

8.2 GNU LESSER GENERAL PUBLIC LICENSE
GNU LESSER GENERAL PUBLIC LICENSE
Version 3, 29 June 2007
Copyright (C) 2007 Free Software Foundation, Inc. <http://fsf.org/>
Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not
allowed.
This version of the GNU Lesser General Public License incorporates the terms and conditions of version 3 of the
GNU General Public License, supplemented by the additional permissions listed below.
0. Additional Denitions.
As used herein, “this License” refers to version 3 of the GNU Lesser General Public License, and the “GNU GPL”
refers to version 3 of the GNU General Public License.
“The Library” refers to a covered work governed by this License, other than an Application or a Combined Work
as dened below.
An “Application” is any work that makes use of an interface provided by the Library, but which is not otherwise
based on the Library. Dening a subclass of a class dened by the Library is deemed a mode of using an interface
provided by the Library.
A “Combined Work” is a work produced by combining or linking an Application with the Library. The particular
version of the Library with which the Combined Work was made is also called the “Linked Version”.
The “Minimal Corresponding Source” for a Combined Work means the Corresponding Source for the Combined
Work, excluding any source code for portions of the Combined Work that, considered in isolation, are based on the
Application, and not on the Linked Version.
The “Corresponding Application Code” for a Combined Work means the object code and/or source code for
the Application, including any data and utility programs needed for reproducing the Combined Work from the
Application, but excluding the System Libraries of the Combined Work.
8
1. Exception to Section 3 of the GNU GPL.
You may convey a covered work under sections 3 and 4 of this License without being bound by section 3 of the
GNU GPL.
2. Conveying Modied Versions.
If you modify a copy of the Library, and, in your modications, a facility refers to a function or data to be supplied
by an Application that uses the facility (other than as an argument passed when the facility is invoked), then you
may convey a copy of the modied version:
a) under this License, provided that you make a good faith effort to ensure that, in the event an Application does
not supply the function or data, the facility still operates, and performs whatever part of its purpose remains
meaningful, or
b) under the GNU GPL, with none of the additional permissions of this License applicable to that copy.
3. Object Code Incorporating Material from Library Header Files.
The object code form of an Application may incorporate material from a header le that is part of the Library. You
may convey such object code under terms of your choice, provided that, if the incorporated material is not limited
to numerical parameters, data structure layouts and accessors, or small macros, inline functions and templates (ten
or fewer lines in length), you do both of the following:
a) Give prominent notice with each copy of the object code that the Library is used in it and that the Library and its
use are covered by this License.
b) Accompany the object code with a copy of the GNU GPL and this license document.
88

4. Combined Works.
You may convey a Combined Work under terms of your choice that, taken together, effectively do not restrict
modication of the portions of the Library contained in the Combined Work and reverse engineering for debugging
such modications, if you also do each of the following:
a) Give prominent notice with each copy of the Combined Work that the Library is used in it and that the Library
and its use are covered by this License.
b) Accompany the Combined Work with a copy of the GNU GPL and this license document.
c) For a Combined Work that displays copyright notices during execution, include the copyright notice for the
Library among these notices, as well as a reference directing the user to the copies of the GNU GPL and this
license document.
d) Do one of the following:
0) Convey the Minimal Corresponding Source under the terms of this License, and the Corresponding
Application Code in a form suitable for, and under terms that permit, the user to recombine or relink the
Application with a modied version of the Linked Version to produce a modied Combined Work, in the
manner specied by section 6 of the GNU GPL for conveying Corresponding Source.
1) Use a suitable shared library mechanism for linking with the Library. A suitable mechanism is one that (a)
uses at run time a copy of the Library already present on the user’s computer system, and (b) will operate
properly with a modied version of the Library that is interface-compatible with the Linked Version.
e) Provide Installation Information, but only if you would otherwise be required to provide such information under
section 6 of the GNU GPL, and only to the extent that such information is necessary to install and execute a
modied version of the Combined Work produced by recombining or relinking the Application with a modied
version of the Linked Version. (If you use option 4d0, the Installation Information must accompany the Minimal
Corresponding Source and Corresponding Application Code. If you use option 4d1, you must provide the
Installation Information in the manner specied by section 6 of the GNU GPL for conveying Corresponding
Source.)
5. Combined Libraries.
You may place library facilities that are a work based on the Library side by side in a single library together with
other library facilities that are not Applications and are not covered by this License, and convey such a combined
library under terms of your choice, if you do both of the following:
a) Accompany the combined library with a copy of the same work based on the Library, uncombined with any other
library facilities, conveyed under the terms of this License.
b) Give prominent notice with the combined library that part of it is a work based on the Library, and explaining
where to nd the accompanying uncombined form of the same work.
6. Revised Versions of the GNU Lesser General Public License.
The Free Software Foundation may publish revised and/or new versions of the GNU Lesser General Public
License from time to time. Such new versions will be similar in spirit to the present version, but may differ in
detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Library as you received it species that a certain
numbered version of the GNU Lesser General Public License “or any later version” applies to it, you have the
option of following the terms and conditions either of that published version or of any later version published by
the Free Software Foundation. If the Library as you received it does not specify a version number of the GNU
Lesser General Public License, you may choose any version of the GNU Lesser General Public License ever
published by the Free Software Foundation.
If the Library as you received it species that a proxy can decide whether future versions of the GNU Lesser
General Public License shall apply, that proxy’s public statement of acceptance of any version is permanent
authorization for you to choose that version for the Library.
8
89

8.3 NET-SNMP
Various copyrights apply to this package, listed in various separate parts below. Please make sure that you read all
the parts.
---- Part 1: CMU/UCD copyright notice: (BSD like) -----
Copyright 1989, 1991, 1992 by Carnegie Mellon University
Derivative Work - 1996, 1998-2000
Copyright 1996, 1998-2000 The Regents of the University of California
All Rights Reserved
Permission to use, copy, modify and distribute this software and its documentation for any purpose and without fee
is hereby granted, provided that the above copyright notice appears in all copies and that both that copyright notice
and this permission notice appear in supporting documentation, and that the name of CMU and The Regents of the
University of California not be used in advertising or publicity pertaining to distribution of the software without specic
written permission.
CMU AND THE REGENTS OF THE UNIVERSITY OF CALIFORNIA DISCLAIM ALL WARRANTIES WITH REGARD
TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS. IN NO
EVENT SHALL CMU OR THE REGENTS OF THE UNIVERSITY OF CALIFORNIA BE LIABLE FOR ANY SPECIAL,
INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM THE LOSS
OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS
ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
---- Part 2: Networks Associates Technology, Inc copyright notice (BSD) -----
Copyright (c) 2001-2003, Networks Associates Technology, Inc
All Rights Reserved
8
Redistribution and use in source and binary forms, with or without modication, are permitted provided that the
following conditions are met:
* Redistributions of source code must retain the above copyright notice, this list of conditions and the following
disclaimer.
* Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
* Neither the name of the Networks Associates Technology, Inc nor the names of its contributors may be used to
endorse or promote products derived from this software without specic prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS ``AS IS’’ AND ANY
EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES
OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT
SHALL THE COPYRIGHT HOLDERS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE
USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
90

---- Part 3: Cambridge Broadband Ltd. copyright notice (BSD) -----
Portions of this code are copyright (c) 2001-2003, Cambridge Broadband Ltd.
All rights reserved.
Redistribution and use in source and binary forms, with or without modication, are permitted provided that the
following conditions are met:
* Redistributions of source code must retain the above copyright notice, this list of conditions and the following
disclaimer.
* Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
* The name of Cambridge Broadband Ltd. may not be used to endorse or promote products derived from this
software without specic prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDER ``AS IS'' AND ANY EXPRESS OR IMPLIED
WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER
BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE
OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
---- Part 4: Sun Microsystems, Inc. copyright notice (BSD) -----
Copyright <A9> 2003 Sun Microsystems, Inc., 4150 Network Circle, Santa Clara,
California 95054, U.S.A. All rights reserved.
Use is subject to license terms below.
This distribution may include materials developed by third parties.
Sun, Sun Microsystems, the Sun logo and Solaris are trademarks or registered trademarks of Sun Microsystems,
Inc. in the U.S. and other countries.
Redistribution and use in source and binary forms, with or without modication, are permitted provided that the
following conditions are met:
* Redistributions of source code must retain the above copyright notice, this list of conditions and the following
disclaimer.
* Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
* Neither the name of the Sun Microsystems, Inc. nor the names of its contributors may be used to endorse or
promote products derived from this software without specic prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS ``AS IS’’ AND ANY
EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES
OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT
SHALL THE COPYRIGHT HOLDERS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF
THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
8
91

---- Part 5: Sparta, Inc copyright notice (BSD) ----Copyright (c) 2003-2008, Sparta, Inc
All rights reserved.
Redistribution and use in source and binary forms, with or without modication, are permitted provided that the
following conditions are met:
* Redistributions of source code must retain the above copyright notice, this list of conditions and the following
disclaimer.
* Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
* Neither the name of Sparta, Inc nor the names of its contributors may be used to endorse or promote products
derived from this software without specic prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS ``AS IS’’ AND ANY
EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES
OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT
SHALL THE COPYRIGHT HOLDERS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF
THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
---- Part 6: Cisco/BUPTNIC copyright notice (BSD) -----
Copyright (c) 2004, Cisco, Inc and Information Network
Center of Beijing University of Posts and Telecommunications.
All rights reserved.
8
Redistribution and use in source and binary forms, with or without modication, are permitted provided that the
following conditions are met:
* Redistributions of source code must retain the above copyright notice, this list of conditions and the following
disclaimer.
* Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
* Neither the name of Cisco, Inc, Beijing University of Posts and Telecommunications, nor the names of their
contributors may be used to endorse or promote products derived from this software without specic prior written
permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS ``AS IS’’ AND ANY
EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES
OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT
SHALL THE COPYRIGHT HOLDERS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF
THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
92

---- Part 7: Fabasoft R&D Software GmbH & Co KG copyright notice (BSD) ----Copyright (c) Fabasoft R&D Software GmbH & Co KG, 2003
oss@fabasoft.com
Author: Bernhard Penz <bernhard.penz@fabasoft.com>
Redistribution and use in source and binary forms, with or without modication, are permitted provided that the
following conditions are met:
* Redistributions of source code must retain the above copyright notice, this list of conditions and the following
disclaimer.
* Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
* The name of Fabasoft R&D Software GmbH & Co KG or any of its subsidiaries, brand or product names may
not be used to endorse or promote products derived from this software without specic prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDER ``AS IS’’ AND ANY EXPRESS OR IMPLIED
WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER
BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE
OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
8.4 BSD LICENCE
Copyright (c) 1989 The Regents of the University of California.
All rights reserved.
This code is derived from software contributed to Berkeley by Mike Muuss.
Redistribution and use in source and binary forms, with or without modication, are permitted provided that the
following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following
disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must display the following acknowledgement:
This product includes software developed by the University of California, Berkeley and its contributors.
4. Neither the name of the University nor the names of its contributors may be used to endorse or promote products
derived from this software without specic prior written permission.
THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS ``AS IS’’ AND ANY EXPRESS
OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL
THE REGENTS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY,
OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
8
93

Revision History
The upper right corner of the cover indicating the revison of this manual can be compared with previous
revisions according to the table below.
8169-A
Revision Symbol
Revision Symbol Revision Date Contents of Revision
A
June, 2011 First Publishing
B
Sep, 2011 Added text to the UL standards
94

8169-B
95
 Loading...
Loading...