Page 1

HOTWIRE DSL ROUTERS
USER’S GUIDE
Document No. 6371-A2-GB20-10
August 2000
Page 2

Copyright E 2000 Paradyne Corporation.
All rights reserved.
Printed in U.S.A.
Notice
This publication is protected by federal copyright law. No part of this publication may be copied or distributed,
transmitted, transcribed, stored in a retrieval system, or translated into any human or computer language in any form
or by any means, electronic, mechanical, magnetic, manual or otherwise, or disclosed to third parties without the
express written permission of Paradyne Corporation, 8545 126th Ave. N., Largo, FL 33773.
Paradyne Corporation makes no representation or warranties with respect to the contents hereof and specifically
disclaims any implied warranties of merchantability or fitness for a particular purpose. Further, Paradyne Corporation
reserves the right to revise this publication and to make changes from time to time in the contents hereof without
obligation of Paradyne Corporation to notify any person of such revision or changes.
Changes and enhancements to the product and to the information herein will be documented and issued as a new
release to this manual.
Warranty, Sales, Service, and Training Information
Contact your local sales representative, service representative, or distributor directly for any help needed. For
additional information concerning warranty , sales, service, repair , installation, documentation, training, distributor
locations, or Paradyne worldwide office locations, use one of the following methods:
H Internet: Visit the Paradyne World Wide Web site at www.paradyne.com. (Be sure to register your warranty
at www.paradyne.com/warranty.)
H Telephone: Call our automated system to receive current information by fax or to speak with a company
representative.
— Within the U.S.A., call 1-800-870-2221
— Outside the U.S.A., call 1-727-530-2340
Document Feedback
We welcome your comments and suggestions about this document. Please mail them to Technical Publications,
Paradyne Corporation, 8545 126th Ave. N., Largo, FL 33773, or send e-mail to userdoc@paradyne.com. Include
the number and title of this document in your correspondence. Please include your name and phone number if you
are willing to provide additional clarification.
Trademarks
ACCULINK, COMSPHERE, FrameSaver, Hotwire, and NextEDGE are registered trademarks of Paradyne
Corporation. MVL, OpenLane, Performance Wizard, and TruePut are trademarks of Paradyne Corporation. All other
products and services mentioned herein are the trademarks, service marks, registered trademarks, or registered
service marks of their respective owners.
A
August 2000
6371-A2-GB20-10
Page 3

Contents
About This Guide
H Document Purpose and Intended Audience v. . . . . . . . . . . . . . . . . . . . . . . . .
H Document Summary vi. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Product-Related Documents vii. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Document Conventions viii. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
1 Introduction to Hotwire DSL Routers
H What is a Hotwire DSL Router? 1-1. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
DSL Technologies Supported 1-1. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Typical DSL Router System 1-2. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Hotwire DSL Router Features 1-3. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Service Subscriber 1-4. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
2 Accessing the DSL Router
H Access Control to the DSL Router 2-1. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Levels of Access 2-1. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Changing Access Session Levels 2-2. . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Local Console Access 2-2. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Setting Up the New User’s Login 2-3. . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Telnet Access 2-4. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Determining the Current Access Level 2-4. . . . . . . . . . . . . . . . . . . . . . . . .
Determining the Available Commands 2-4. . . . . . . . . . . . . . . . . . . . . . . . . .
Using the List Command 2-5. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Changing the System Identity 2-5. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Exiting from the System 2-5. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Manually Logging Out 2-6. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Automatically Logging Out 2-6. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
6371-A2-GB20-10
August 2000
i
Page 4

Contents
3 Configuring the DSL Router
H Overview of DSL Router Configuration 3-1. . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Interfaces for the DSL Router 3-1. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Ethernet and DSL Interface Identifiers 3-2. . . . . . . . . . . . . . . . . . . . . . . . . .
Service Domain IP Address Assignments 3-2. . . . . . . . . . . . . . . . . . . . . . .
Numbered DSL Interface 3-3. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Unnumbered DSL Interface 3-3. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H IP Routing 3-4. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Network Considerations 3-4. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Address Resolution Protocol (ARP) 3-5. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Proxy ARP 3-5. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Network Address Translation (NAT) 3-6. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Basic NAT 3-6. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Network Address Port Translation (NAPT) 3-6. . . . . . . . . . . . . . . . . . . . . .
IP Options Processing 3-7. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Applications Supported by NAT 3-7. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Dynamic Host Configuration Protocol (DHCP) Server 3-7. . . . . . . . . . . . . . . .
H DHCP Relay Agent 3-8. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Security 3-9. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
IP Filtering 3-9. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Land Bug/Smurf Attack Prevention 3-9. . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Routed vs. Bridged PDUs 3-10. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
4 DSL Router Configuration Examples
H Configuration Examples 4-1. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Basic Configuration Example 4-2. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Basic NAT Configuration Example 4-3. . . . . . . . . . . . . . . . . . . . . . . . . . . . .
NAPT Configuration Example 4-4. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Unnumbered DSL Interface with Proxy ARP Configuration Example 4-5
DHCP Relay with Proxy ARP Configuration Example 4-6. . . . . . . . . . . . .
DHCP Server with Basic NAT Configuration Example 4-7. . . . . . . . . . . .
Downstream Router Configuration Example 4-8. . . . . . . . . . . . . . . . . . . . .
ii
August 2000
6371-A2-GB20-10
Page 5

5 Monitoring the DSL Router
H What to Monitor 5-1. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Detecting Problems 5-1. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Status of Interfaces 5-2. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Interface Statistics 5-3. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Clearing Statistics 5-4. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H List of Discard Reasons 5-4. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
6 Diagnostics and Troubleshooting
H Diagnostics and Troubleshooting Overview 6-1. . . . . . . . . . . . . . . . . . . . . . . . .
H Device Restart 6-1. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Alarms Inquiry 6-1. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H System Log 6-2. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
SYSLOG Events 6-3. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
SYSLOG Message Display 6-4. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Ping 6-5. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Ping Test Results 6-5. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H TraceRoute 6-6. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
TraceRoute Test Results 6-6. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Contents
A Command Line Interface
H Command Line Interface Feature A-1. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Navigation A-2. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Command Recall A-2. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Document Conventions A-2. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Command Line Interface Commands A-3. . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Configuration Control Commands A-3. . . . . . . . . . . . . . . . . . . . . . . . . . . . .
RFC 1483 Encapsulation A-3. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Ethernet Frame Format A-3. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Interface and Service Domain IP Address A-4. . . . . . . . . . . . . . . . . . . . . .
IP Routing Table A-5. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
ARP Table A-7. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Proxy ARP A-7. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
NAT A-8. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
DHCP Server A-10. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
DHCP Relay Agent A-11. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
IP Packet Processing A-12. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Traps A-12. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Show Command Outputs A-13. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
6371-A2-GB20-10
August 2000
iii
Page 6

Contents
B Configuration Defaults & Command Line Shortcuts
H Configuration Default Settings B-1. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Command Line Input Shortcuts B-3. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
C Traps & MIBs
H SNMP Overview C-1. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Traps Overview C-1. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
DSL Router Traps C-2. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H MIBs Overview C-3. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Standard MIBs C-3. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
MIB II (RFC 1213) C-3. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
System Group C-3. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Interfaces Group (RFC 1573) C-5. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Extension to Interfaces Table (RFC 1573) C-7. . . . . . . . . . . . . . . . . . . . . .
IP Group (RFC 1213) C-7. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
IP CIDR Route Group (RFC 2096) C-8. . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Transmission Group C-9. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
SNMP Group C-10. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Ethernet-Like MIB (RFC 2665) C-10. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
H Paradyne Enterprise MIBs C-11. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Device Control MIB C-11. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Device Diagnostics MIB C-12. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Health and Status MIB C-15. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Configuration MIB C-16. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Interface Configuration MIB C-17. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
ARP MIB C-17. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
NAT MIB C-17. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
DHCP MIB C-18. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
DSL Endpoint MIB C-19. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
SYSLOG MIB C-20. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Interface Configuration MIB C-20. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
D DSL Router Terminal Emulation
H DSL Router Terminal Emulation D-1. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Accessing the List Command Output D-1. . . . . . . . . . . . . . . . . . . . . . . . . . .
Terminal Emulation Programs D-2. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Index
iv
August 2000
6371-A2-GB20-10
Page 7

About This Guide
Document Purpose and Intended Audience
This guide describes how to configure and operate Hotwire DSL routers. This
document addresses the use of the following Hotwire DSL Router models:
H Hotwire 6301/6302 IDSL Router
H Hotwire 6341/6342 Symmetric DSL Router
H Hotwire 6371 RADSL Router
This document is intended for administrators and operators who maintain the
endpoints at customer premises. A basic understanding of internetworking
protocols and their features is assumed. Specifically, you should have familiarity
with the following internetworking concepts:
H TCP/IP applications
H IP and subnet addressing
H IP routing
H Bridging
It is also assumed that you have already installed a Hotwire DSL Router. If not,
refer to
Product-Related Documents
on page vii for installation documents.
6371-A2-GB20-10
August 2000
v
Page 8

About This Guide
Document Summary
Section Description
Chapter 1
Chapter 2
Chapter 3
Chapter 4
Chapter 5
Chapter 6
Appendix A
Appendix B
Introduction to Hotwire DSL Routers.
of the Hotwire DSL Routers.
Accessing the DSL Router.
Routers access control and provides instructions on how to
log in and log out of the system.
Configuring the DSL Router.
interfaces, Domain Types, IP Routing, and network
considerations.
Describes the Hotwire DSL
Describes the DSL router
DSL Router Configuration Examples.
common DSL router configuration examples.
Monitoring the DSL Router.
that monitor the Hotwire system.
Describes operator programs
Diagnostics and Troubleshooting.
Hotwire operational problems and solutions. Contains
SysLog information.
Command Line Interface.
router’s Command Line Interface and command syntax with
examples.
Provides explanation of the DSL
Provides an overview
Presents several
Describes common
Configuration Defaults & Command Line Shortcuts.
Provides a list of all configuration options with factory
default settings and a list of all command line shortcuts with
the abbreviated command line input.
Appendix C
Appendix D
Index Lists key terms, acronyms, concepts, and sections in
A master glossary of terms and acronyms used in Paradyne documents is
available on the Web at www.paradyne.com. Select
→
Manuals
Technical Glossary.
Traps & MIBs.
supported by the DSL routers.
DSL Router Terminal Emulation.
setup procedures for two common text file programs.
alphabetical order.
Summarizes the MIBs and SNMP traps
Provides configuration
Library → Technical
vi
August 2000
6371-A2-GB20-10
Page 9

Product-Related Documents
Contact your sales or service representative to order additional product
documentation.
Document Number Document Title
About This Guide
6301-A2-GN10
6341-A2-GN10
6371-A2-GN10
8000-A2-GB22
8000-A2-GB26
Contact your sales or service representative to order additional product
documentation.
Paradyne documents are also available on the World Wide Web at
www.paradyne.com. Select
Hotwire DSL & MVL
Hotwire 6301/6302 IDSL Routers Installation
Instructions
Hotwire 6341/6342 Symmetric DSL Routers
Installation Instructions
Hotwire 6371 RADSL Router Installation Instructions
Hotwire Management Communications Controller
(MCC) Card, IP Conservative, User’s Guide
Hotwire IP MVL, RADSL, IDSL, and SDSL Cards,
Models 8310/8312/8314, 8510/8373/8374, 8303/8304,
and 8343/8344, User’s Guide
Library → Technical Manuals →
.
6371-A2-GB20-10
August 2000
vii
Page 10

About This Guide
Document Conventions
The following syntax is used throughout this document.
Syntax Translation
[ ]
{ }
|
Italics
Bold
x.x.x.x
xx:xx:xx:xx:xx:xx
Square brackets represent an optional element.
Braces represent a required entry.
Vertical bar separates mutually exclusive elements.
Entry is a variable to be supplied by the operator.
Enter (type) as shown.
32-bit IP address and mask information where x is an
8-bit weighted decimal notation.
MAC address information where x is a hexadecimal
notation.
viii
August 2000
6371-A2-GB20-10
Page 11

Introduction to Hotwire DSL Routers
What is a Hotwire DSL Router?
The Hotwirer DSL (Digital Subscriber Line) Router operates as an IP router
connecting a DSL link to an Ethernet network. This system provides high-speed
access to the Internet or a corporate network over a traditional twisted-pair
copper telephone line to the end user.
DSL Technologies Supported
1
Paradyne’s Hotwire DSL network supports the following types of technologies:
H Hotwire IDSL (ISDN DSL) products provide IDSL multirate symmetric packet
transport and can operate over a connection with an ISDN repeater or digital
facilities. Data rates of 64 kbps, 128 kbps, or 144 kbps can be configured.
H Hotwire RADSL (Rate Adaptive DSL) products are applicable for both
asymmetric and symmetric applications. The 1 Mbps symmetric operation is
ideal for traditional business applications while the 7 Mbps downstream with
1.1 Mbps upstream asymmetric operation provides added bandwidth for
corporate Internet access. RADSL products can also save line costs by
optionally supporting simultaneous data and voice over the same line.
H Hotwire SDSL (Symmetric DSL) packet-based products provide high-speed
symmetric DSL services with bandwidth for business applications. These
products are configurable from 144 kbps up to 2.3 Mbps. This gives service
providers the opportunity to sell multiple services with a single product.
6371-A2-GB20-10
August 2000
1-1
Page 12
Introduction to Hotwire DSL Routers
Typical DSL Router System
DSL is a local loop technology that uses standard twisted-pair copper wire to
support high-speed access over a single pair of twisted copper wires. DSL
applications are point-to-point, requiring DSL devices at the central site and at the
end-user site.
The Hotwire DSL routers interoperate with the following types of Hotwire IP DSL
cards (at the DSLAM/GranDSLAM chassis) to deliver applications at high speeds
in support of packet services over a DSL link:
H The Hotwire 8303 or 8304 IP IDSL Cards interoperate with two Hotwire IDSL
Routers:
— Hotwire 6301 IDSL Router with one Ethernet port
— Hotwire 6302 IDSL Router with a 4-port Ethernet hub
H The Hotwire 8343 or 8344 SDSL Cards interoperate with two Hotwire
Symmetric DSL Routers:
— Hotwire 6341 SDSL Router with one Ethernet port
— Hotwire 6342 SDSL Router with a 4-port Ethernet hub
H The Hotwire 8510, 8373, and 8374 IP RADSL Cards interoperate with the
Hotwire 6371 RADSL Router with one Ethernet port
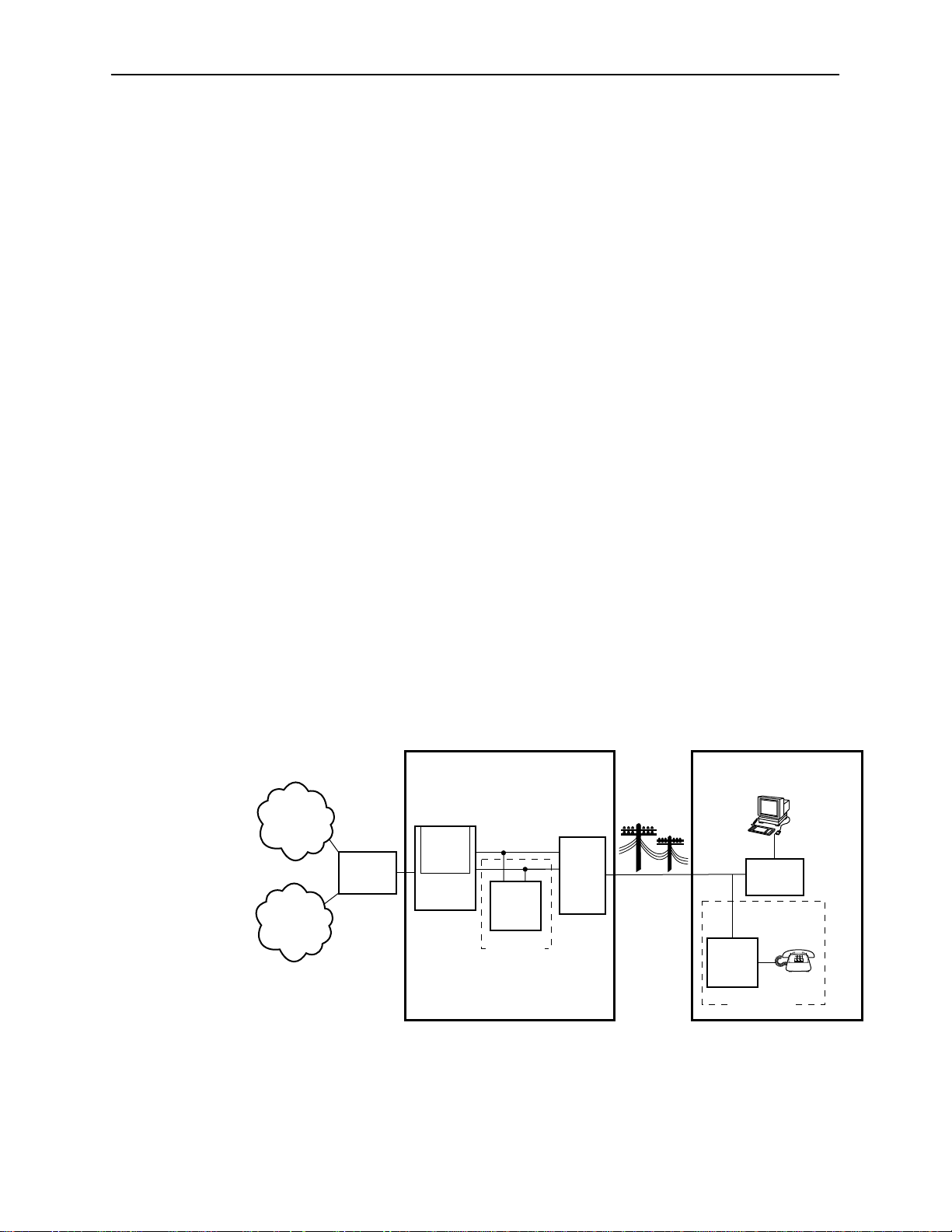
The following illustration shows a typical Hotwire system with a Hotwire DSL
Router. All Hotwire DSL routers transport data. The Hotwire 6371 RADSL Router
can transport data and POTS simultaneously.
Network Access Provider (NAP) Service Subscriber
Customer Premises (CP)
DSL
Router
*
POTS
CP
POTS
Splitter
Optional
Network
Service
Provider
Corporate
Intranet
Core
Router
Central Office (CO)
IP DSL
Line
Card
DSLAM
POTS
Splitter
Optional
CO
MDF
POTS/DSL
Data
Interface
1-2
Legend: DSL – Digital Subscriber Line POTS– Plain Old Telephone Service
* 6371 RADSL Router Only
MDF – Main Distribution Frame
August 2000
6371-A2-GB20-10
00-16576-02
Page 13

Hotwire DSL Router Features
The Hotwire DSL routers contain the following features.
H IP routing with:
— NAT (Network Address Translation)
— NAPT (Network Address Port Translation)
— DHCP Server (Dynamic Host Configuration Protocol) and DHCP Relay
Agent
— A full set of IP filters
— SNMP Set/Get capability
H High-speed Internet or intranet access.
H Diagnostics. Provides the capability to diagnose device and network
problems and perform tests.
H Device and Test Monitoring. Provides the capability of tracking and
evaluating the unit’s operation.
Introduction to Hotwire DSL Routers
H Remote Firmware Download. Provides easy setup and activation of
firmware upgrades from a remote location.
H Security. Provides multiple levels of security, which prevents unauthorized
access to the DSL router.
H Console Terminal Interface. Provides an interface for:
— Configuring and managing the DSL router.
— Remote terminal access via Telnet.
— Management from an NMS using SNMP.
6371-A2-GB20-10
August 2000
1-3
Page 14

Introduction to Hotwire DSL Routers
Service Subscriber
The Service Subscriber is the user (or set of users) that has contracted to receive
networking services (e.g., Internet access, remote LAN access) for the end-user
system from an NSP (Network Service Provider). Service subscribers may be:
H Residential users connected to public network services (e.g., the Internet)
H Work-at-home users connected to their corporate intranet LAN
H Commercial users at corporate locations (e.g., branch offices) connected to
other corporate locations or connected to public network services
The Hotwire DSL Router must be installed at the customer premises to provide
the end user with access to any of the above services.
NOTE:
If you would like more information on DSL-based services, applications, and
network deployment, refer to Paradyne’s
may be downloaded or ordered through Paradyne’s World Wide Web site at
www.paradyne.com/library.
The DSL Sourcebook.
The book
1-4
August 2000
6371-A2-GB20-10
Page 15

Accessing the DSL Router
Access Control to the DSL Router
The Hotwire DSL Router can be managed from an NMS using SNMP or from the
command line interface. There are two methods to access the command line
interface:
H Local access at the DSL router through the Console port, or
H Access by a Telnet session (controlled through the management interface at
the Hotwire chassis).
2
Levels of Access
When a local console connection is first established, a login prompt appears. The
Hotwire DSL Router accepts only one login session at a time. The DSL Router is
configured at the factory with a default login ID and password. However, to
provide login security to the DSL system, configure a new login ID and password.
There is one login ID and two levels of privileges on the Hotwire DSL system.
Your user account can be configured with one user name and different
passwords for:
H Administrator. The Administrator has two levels of access to the DSL router.
— Administrator, non-configuration mode: Provides read-only capabilities.
This is the same level of access as Operator.
— Administrator, configuration mode: Provides complete write access to the
DSL router. However, MIB sets are done from the NMS vs. the command
line.
H Operator. The Operator has read-only access to display device information
with no modification permission and no access to management functions.
Refer to Appendix A,
command line entry.
Command Line Interface
, for access level details for each
6371-A2-GB20-10
August 2000
2-1
Page 16

Accessing the DSL Router
Changing Access Session Levels
H You can change the Administrator access level by entering:
admin enable
This command provides Administrator access level privileges. The DSL
router will respond with a prompt to enter the password for Administrator
access.
H You can end the Administrator access level by entering:
admin disable
This command results in ending the Administrator access level session. No
password is needed.
Entering exit has the same results. Refer to
page 2-5 for further details on ending a session.
The Operator and Administrator have the same Login ID with different passwords
for their access level. To determine the level of access for a session, refer to
Determining the Current Access Level
on page 2-4.
Exiting from the System
on
Local Console Access
The DSL router ships with the local console enabled. After login, the local console
can be disabled with the command console disable. After saving this change
and ending the session, there is no local access through the console port. Any
access must be through a Telnet session or the NMS.
NOTE:
Entering console disable results in NO local access to the DSL router.
If you attempt to log in, you will receive an error message.
To determine via a Telnet session if a console is enabled, enter:
show console
The display returned for the show console command will be:
H console enabled – Command line management at the console is
available, or
H console disabled – No command line management is available at the
console.
For steps to set up the new user’s login, refer to
on page 2-3.
Setting Up the New User’s Login
2-2
August 2000
6371-A2-GB20-10
Page 17

Setting Up the New User’s Login
The DSL router will provide the login prompt when the local console connection is
first established. When the login prompt appears, a locally connected console
defaults to Console Enabled with Operator access only.
" Procedure
For first-time access to the Hotwire DSL Router’s command line interface:
1. At the initial login> prompt, type the default login ID paradyne and press
Enter.
2. At the password> prompt (for Operator), type the default password abc123
and press Enter.
The login ID and password fields are validated together.
3. At the system identity of CUSTOMER> prompt, type admin enable and press
Enter.
4. At the password> prompt (for Administrator), type the default password
abc123 and press Enter.
Accessing the DSL Router
5. The system identity will change to the Administrator display mode of
CUSTOMER#>. Type configure terminal and press Enter.
6. The system identity will change to the Administrator configuration mode of
CUSTOMER - CONFIG#>.
7. To change the login ID, enter text to replace the default of paradyne:
name
your new login ID
NOTE:
The Login ID and Password fields are NOT case-sensitive.
8. Enter a new password and specify the level:
password
Example: type password operator 238clrd3 and press Enter.
Both the Login ID and the Password fields are 1–31 printable alphanumeric
ASCII characters in the ASCII hex range of 0x21–0x7E. No spaces are
allowed. The following table lists the invalid characters.
Invalid Characters
# Number sign 0x23
$ Dollar sign 0x24
level password
Value ASCII Hex T ranslation
6371-A2-GB20-10
% Percentage 0x25
& Ampersand 0x26
August 2000
2-3
Page 18
Accessing the DSL Router
9. At the prompt, enter the new Administrator-level password to replace abc123:
password admin
save
and press Enter
new password
and press Enter
NOTE:
Any input during an Administrator configuration session must be saved
while still in configuration mode.
For more information regarding the system identity, refer to
Current Access Level,
If you are denied access during a Telnet session, the session stops and an error
is logged. If you accessing the DSL router locally and a Telnet session is active,
you will receive a message:
Local console disabled by conflict
Telnet Access
The Telnet access defaults to Administrator level. If the login is at the Operator
level, then Operator level access is available. Telnet access is always enabled.
Determining the Current Access Level
The command line prompt displays the access level. The factory default for
System identity is CUSTOMER>. You can set your own system identity name to
replace CUSTOMER. See the example below.
If the prompt format
appears as . . .
below.
Then the DSL router
access level is . . .
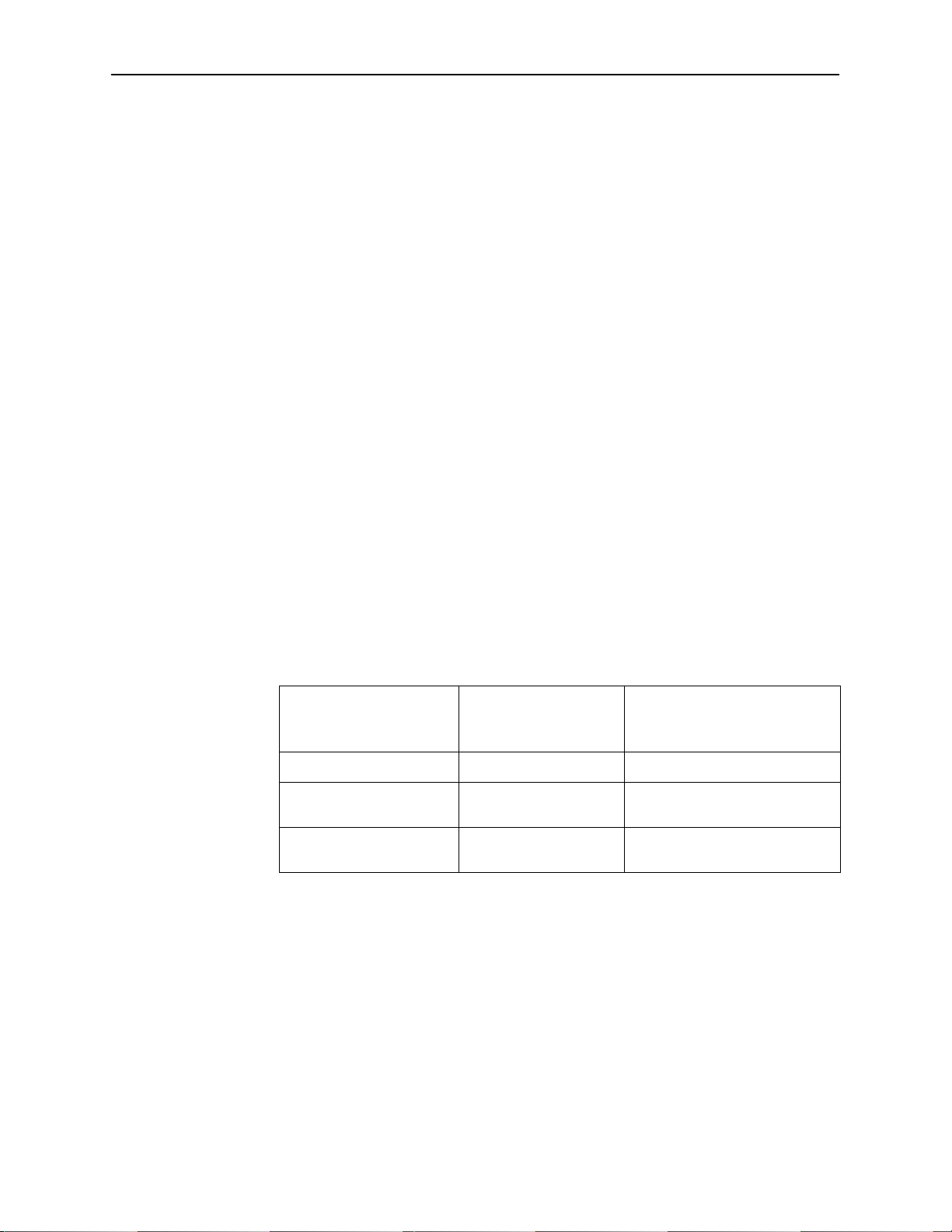
Determining the
And if you entered a System
identity of PARADYNE, the
prompt displays . . .
CUSTOMER> Operator, display mode P ARADYNE>
CUSTOMER #> Administrator, display
CUSTOMER – CONFIG#> Administrator,
Determining the Available Commands
To determine the commands available at the current login access level, enter:
H help or
H ? (question mark)
H the command without any parameters
2-4
mode
configuration mode
August 2000
PARADYNE #>
PARADYNE – CONFIG#>
6371-A2-GB20-10
Page 19

Using the List Command
The list command displays a sequence of commands, in the form of ASCII
strings, that would have the effect of setting all configuration settings to the
current values. (The two passwords are not output.)
To determine the commands available, enter the Administrator configuration
mode and enter either:
H list
Displays the output in on-screen page mode. In on-screen page mode, the
user interface displays 23 lines of information. When the 24th line is reached,
More... is displayed. Pressing any key will display the next page.
H list config
Displays the output in scroll mode as a text file. Scroll mode captures and
displays all command strings in a text file for use with a terminal emulation
program. Refer to Appendix D,
Changing the System Identity
Accessing the DSL Router
DSL Router Terminal Emulation.
Procedure
"
To change the System Identity from the factory default of CUSTOMER>:
1. Login and enter the ADMIN-configuration mode.
2. At the CUSTOMER-CONFIG#> prompt, type the new System identity
(no spaces allowed), press Enter, type save, and press Enter.
system identity
For example:
system identity PARADYNE and press Enter
save
3. In this example, after saving the entry and ending the configuration mode, the
System identity will display:
PARADYNE #>
The System identity is the same as the MIB entry of sysName. The
sysContact and SysLocation MIB entries are not displayed.
Exiting from the System
You can manually log out of the system, or let the system automatically log you
out. The DSL router will log you out immediately if you disconnect the Console
cable. Any unsaved configuration input will be lost.
and press Enter
new system identity
6371-A2-GB20-10
August 2000
2-5
Page 20
Accessing the DSL Router
Manually Logging Out
To log out, there are two commands: logout and exit.
" Procedure
To log out of the Hotwire DSL Router command line session or Telnet session:
" Procedure
To exit the Hotwire DSL Router’s current access level:
1. At the > prompt, type logout and press Enter.
2. The system ends the session immediately. Any configuration updates must
be saved before exiting or the updates will be lost.
1. At the > prompt, type exit and press Enter. If there are any unsaved
configuration changes, you will be prompted to save changes before exiting.
2. The exit command has the following effect:
If you are accessing the DSL router . . .
At the Local console and logged in at the
Administrator level, configuration mode
At the Local console and logged in at the
Administrator level, non-configuration
mode
At the Local console and logged in at the
Operator level
Via a Telnet session and logged in at any
access level
Automatically Logging Out
The DSL router has an automatic timeout feature that logs you out of the system
after five minutes of inactivity. Any input that is not saved is lost. You will need to
log back in.
At the console, press Enter to display the login> prompt to log back in. The
autologout {enable | disable} command default is enabled. Unsaved
configuration input is lost.
Then . . .
You are placed at the Operator level
and any configuration updates must be
saved or the updates will be lost.
You are placed at the Operator level.
The Exit command responds exactly
like the Logout command.
Entering either of the following ends
the Telnet session immediately:
H Exit
H Ctrl + ] (right bracket)
2-6
When autologout is:
H Enabled, the current configuration is retained through a power recycle.
H Disabled, the system inactivity timer is disabled.
August 2000
6371-A2-GB20-10
Page 21

Configuring the DSL Router
Overview of DSL Router Configuration
The Hotwire DSL Routers support various customer premises distribution
networks that contain IP forwarding devices or routers, in addition to locally
attached hosts or subnets. The Hotwire DSL Router has an IP Routing Table that
contains IP address and subnet mask information.
The DSL router supports Internet Protocol as specified in RFC 791 and Internet
Control Message Protocol (ICMP) as specified in RFCs 792 and 950. The DSL
router acts as a router (or gateway) as defined in RFC 791.
3
For more information on supported RFCs, refer to Appendix C,
Interfaces for the DSL Router
The Hotwire DSL Router has two interfaces:
H DSL Interface
The Hotwire DSL Router interface type is determined by the model number:
— 6301 and 6302 are Hotwire IDSL Routers
— 6341 and 6342 are Hotwire SDSL Routers
— 6371 is a Hotwire RADSL Router
The DSL interface has a unique MAC address assigned before shipping.
Traps & MIBs.
6371-A2-GB20-10
August 2000
3-1
Page 22

Configuring the DSL Router
H Ethernet Interface
— All DSL routers have an Ethernet interface with a unique MAC address
assigned before shipping.
— The Ethernet interface is a 10/100BaseT interface that automatically
negotiates the rate. If all attached Ethernet devices support 100BaseT,
the DSL router will default to 100BaseT. Otherwise, the DSL router
operates at 10BaseT.
— The DSL router can be configured for either DIX format or IEEE 802.3
format. When the DSL router is configured to use IEEE 802.3 format, the
DSL router uses SNAP encapsulation as specified in RFC 1042.
— The Hotwire 6302 IDSL and the 6342 SDSL Routers each have a hub
configuration with four Ethernet connectors. The hub acts as a bit-level
repeater. There is logically one Ethernet communications interface and
one single collision domain.
— The DSL router only accepts frames on the Ethernet interface with its
own MAC address or a broadcast or multicast MAC address.
Ethernet and DSL Interface Identifiers
The following are the naming conventions used for the Hotwire DSL Router
interfaces:
H eth1 (or e0) – Ethernet interface name.
H dsl1 (or d0) – DSL interface name.
Service Domain IP Address Assignments
H Multiple Service Domains can be defined using network addresses and
subnet masks.
H For both the DSL interface and the Ethernet interface, four Service Domain
IP Addresses and subnet masks can be defined.
3-2
August 2000
6371-A2-GB20-10
Page 23
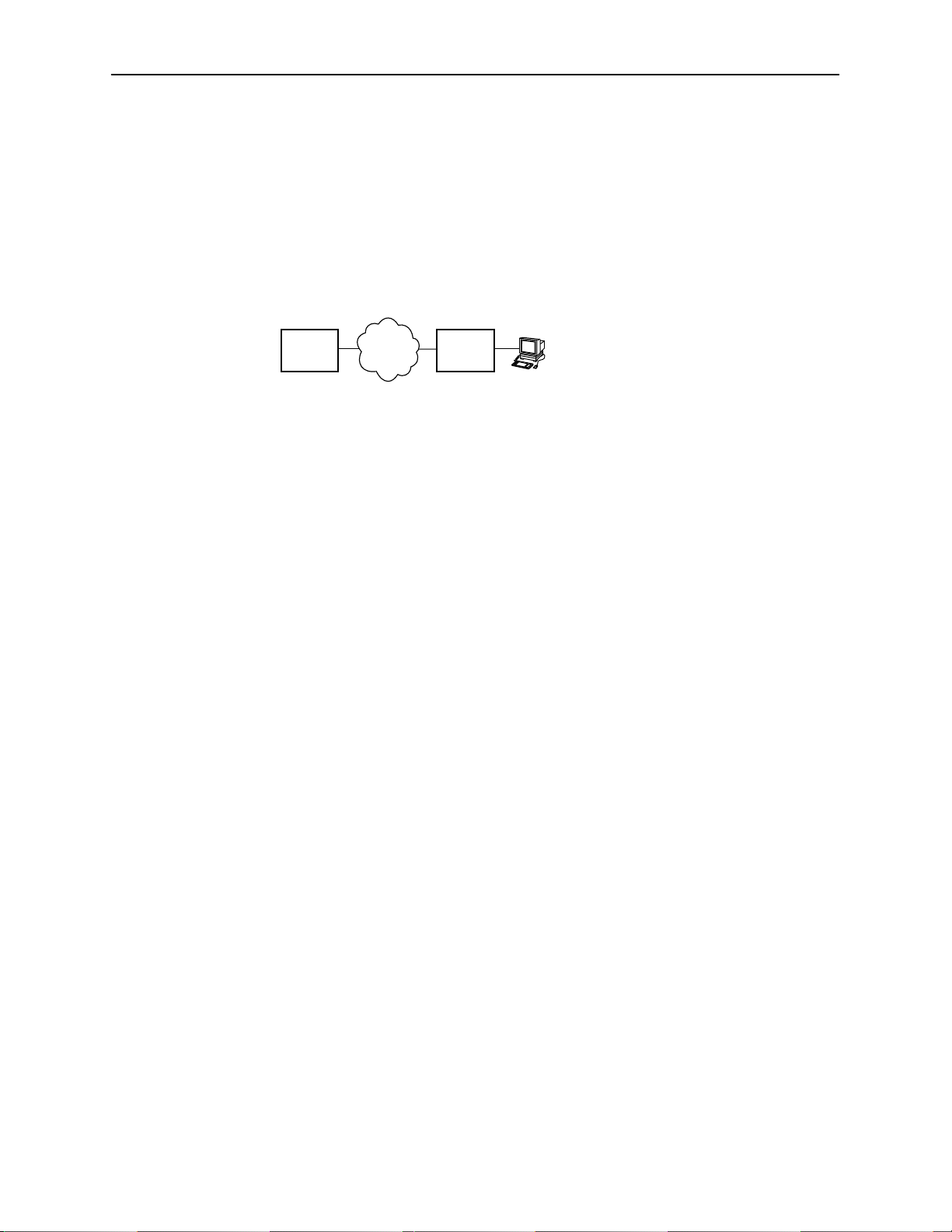
Numbered DSL Interface
In this scenario, the hosts attached to the DSL router’s Ethernet interface are on
a different logical network than the core router. The DSL router is the next hop
router for the hosts. The upstream next hop router for the DSL router is the core
router.
Configuring the DSL Router
Simplified Network Topology
Core
Router
The hosts can be assigned IP addresses on the network attached to the DSL
router’s Ethernet interface. The upstream next hop router is assigned an address
on a different logical network than the hosts.
Actions required to configure the DSL router interfaces in this scenario:
H Assign IP address to Ethernet interface: eth1
H Assign IP address to DSL interface: dsl1
H Assign upstream next hop router
Unnumbered DSL Interface
In this LAN extension application scenario, the hosts connected to a corporate
network for virtual office connection or teleworkers want to look like they are on
the same network as the core router. The core router will be the next hop router
for the hosts.
WAN
DSL
Router
Host
(End Users)
99-16609
6371-A2-GB20-10
Actions required to configure the DSL router interfaces in this scenario:
H Assign IP address to Ethernet interface: eth1
H Specify the DSL interface as unnumbered: dsl1
H Assign upstream next hop router
H Enable Proxy ARP for both the eth1 and dsl1 interfaces
H Disable scoping on the DSL card at the DSLAM/GranDSLAM chassis
August 2000
3-3
Page 24

Configuring the DSL Router
IP Routing
The DSL router uses destination-based routing for downstream traffic. An IP
Routing Table is maintained to specify how to forward IP datagrams downstream.
The DSL router is capable of supporting 32 entries in the IP Routing Table. This
table can be viewed by both Operator and Administrator access levels.
The DSL router uses source-based forwarding for upstream traffic to ensure that
packets are forwarded to the upstream router specified for the configured Service
Domain.
Refer to Chapter 4,
Network Considerations
The DSL routers can be configured to function in a variety of network
environments. The following sections provide descriptions of some of the DSL
router features:
Address Resolution Protocol (ARP)
H
H
Proxy ARP
H
Network Address Translation (NAT)
—
Basic NA T
—
Network Address Port Translation (NAPT)
—
IP Options Processing
—
Applications Supported by NAT
H
Dynamic Host Configuration Protocol (DHCP) Server
H
DHCP Relay Agent
H
Security
DSL Router Configuration Examples,
for further details.
3-4
—
IP Filtering
—
Land Bug/Smurf Attack Prevention
H
Routed vs. Bridged PDUs
August 2000
6371-A2-GB20-10
Page 25

Address Resolution Protocol (ARP)
Address Resolution Protocol, as specified in RFC 826, is supported in the DSL
router. The DSL router provides for a total of 265 ARP table entries. The timeout
for completed and uncompleted ARP table entries is configurable.
NOTE:
The DSL router does not process ARP requests and ARP responses on its
DSL interface when it is configured to support RFC 1483 PDU routing
(Standard mode). See
information. The operating mode (Standard or VNET) can be changed from
the DSL card without requiring any reconfiguration of the DSL router. If any
static ARP entries have been configured, they will remain in the database
and can be displayed with the show arp command. You can create static
ARP entries regardless of the current operating mode.
The Command Line Interface provides the ability to:
H Create up to 64 static ARP table entries to be retained across power cycles.
Routed vs. Bridged PDUs
Configuring the DSL Router
on page 3-10 for more
Proxy ARP
H Display the ARP table.
H Delete ARP table entries.
H Display and delete automatically added static ARP table entries by the DHCP
server and relay functions. Refer to
(DHCP) Server
The DSL router supports Proxy ARP. Proxy ARP responses are based on the IP
Routing table contents. The IP Routing table must have an entry for every host
that is reachable on the Ethernet interface, including hosts for which the DSL
router will not forward packets because of IP filters. If an ARP request is received
on one interface for an IP address that is reachable on the other interface, the
DSL router will respond with its own MAC address.
on page 3-7.
Dynamic Host Configuration Protocol
NOTE:
The Proxy ARP option is not available on the DSL interface when the DSL
router is configured to support RFC 1483 PDU routing. See
Bridged PDUs
The Command Line Interface provides the ability to enable and disable Proxy
ARP for each interface.
on page 3-10 for more information.
Routed vs.
6371-A2-GB20-10
NOTES:
— When Basic NAT is enabled, the DSL interface (dsl1) must have Proxy
ARP enabled if the dsl1 interface address is part of the Basic NAT global
IP network address.
— Proxy ARP and NAPT cannot be enabled at the same time.
August 2000
3-5
Page 26

Configuring the DSL Router
Network Address Translation (NAT)
Network Address Translation is used when a private network’s internal IP
addresses cannot be used outside the private network. The IP addresses may be
restricted for privacy reasons or they may not be valid public IP addresses.
Basic NAT
The DSL router provides NAT as described in
Translator (NAT)
public (global) external IP addresses.
Two variations of traditional NAT are supported:
H Basic NA T
H Network Address Port Translation (NAPT)
. NAT allows the private (local) hosts to transparently access
RFC 1631 The IP Network Address
NOTE:
Basic NAT and NAPT cannot be enabled at the same time.
Basic NAT allows hosts in a private network to transparently access the external
network by using a block of public addresses. Static mapping enables access to
selected local hosts from the outside. Basic NAT is often used in a large
organization with a large network setup for internal use and the need for
occasional external access.
Basic NAT provides a one-to-one mapping by translating a range of assigned
public IP addresses to a similar-sized pool of private addresses (typically from the
x.x.x
10.
host appears to have an unique IP address. Up to 256 IP addresses can be
allocated for use with Basic NAT.
address space). Each local host currently communicating with a external
Network Address Port Translation (NAPT)
NAPT allows multiple clients in a local network to simultaneously access remote
networks using a single IP address. This benefits telecommuters and SOHO
(Small Office/Home Office) users that have multiple clients in an office running
TCP/UDP applications. NAPT is sometimes referred to as PAT (Port Address
Translation).
NAPT provides a many-to-one mapping and uses one public address to interface
numerous private users to an external network. All hosts on the global side view
all hosts on the local side as one Internet host. The local hosts continue to use
their corporate or private addresses. When the hosts are communicating with
each other, the translation is based on the IP address and the IP port numbers
used by TCP/IP applications.
3-6
August 2000
6371-A2-GB20-10
Page 27

IP Options Processing
Configuring the DSL Router
The NAT and NAPT functions handle and process the IP datagrams with options
set as described below. No command is available to set IP options.
The DSL Router does not process (and drops) any IP datagrams with the
following IP options:
H Loose source and record route (type 131)
H Strict source and record route (type 133)
H Security (type 130)
H Stream ID (type 136)
The DSL Router does process IP datagrams with the following IP options, but
does not provide its IP address or timestamp information in the response
message:
H Record route (type 7)
H Timestamp (type 68)
Applications Supported by NAT
The DSL routers support the following applications and protocols:
H FTP
H HTTP
H NetMeeting
H Ping
H RealPlayer
H Telnet
H TFTP
Dynamic Host Configuration Protocol (DHCP) Server
The DSL router provides a DHCP Server feature as specified in RFC 2131,
Dynamic Host Configuration Protocol, and RFC 2132, DHCP Option and BOOTP
Vendor Extensions. DHCP is the protocol used for automatic IP address
assignment.
DHCP setup considerations:
6371-A2-GB20-10
H The range of IP addresses to be used by the DHCP server must be
configured. The maximum number of clients is 256.
H The DHCP server must be enabled.
August 2000
3-7
Page 28

Configuring the DSL Router
H When the DHCP IP address range is changed, all binding entries,
H When the DHCP Server is enabled, there can be only one service domain
H The IP address for the next hop router that is provided to the hosts in the
H The subnet mask can be configured along with the IP address range
H The DHCP server domain name can be configured (optional).
H The Domain Name Server (DNS) IP address can be configured (optional).
H The minimum and maximum lease time settings can be configured.
automatically added routes, and ARP table entries for the clients configured
with the old address range are removed.
(Ethernet interface) configured.
DHCP reply must be configured.
(optional).
For additional information, refer to Chapter 4,
Examples.
DHCP Relay Agent
The DSL router provides the capability of serving as a DHCP Relay Agent, as
specified in RFC 2131, Dynamic Host Configuration Protocol. The DSL router
provides the capability to enable and disable the DHCP Relay Agent and to
configure the IP address of the DHCP server to which the DHCP requests are to
be forwarded.
The DHCP server assigns an IP address to the end-user system. When DHCP
Relay is enabled, it is possible to limit the number of DHCP clients. The DSL
router’s IP Routing table and ARP table are automatically updated. The DHCP
relay agent in the DSL router should be used when there is a DHCP server
upstream in the service domain. DHCP relay agent setup considerations:
H DHCP server IP address must be configured.
H DHCP relay must be enabled.
H The number of DHCP clients can be limited to 1—256.
H DHCP server and DHCP relay functions cannot be enabled at the same time.
H NAT and DHCP relay cannot be enabled at the same time.
DSL Router Configuration
3-8
August 2000
6371-A2-GB20-10
Page 29

Security
IP Filtering
Configuring the DSL Router
The DSL router offers security via the following:
H IP Filtering – Can be enabled or disabled.
H Land Bug/Smurf Attack Prevention – Always present.
NOTE:
All Hotwire DSL Router filters are configured on the Hotwire DSL card.
By default, filtering is disabled on the Hotwire DSL card for the DSL router.
If enabled, filtering provides security advantages on LANs by restricting traffic on
the network and hosts based on the IP source and/or destination addresses.
IP packets can be filtered based on:
H Destination IP Address
H IP Protocol Type
H Source and Destination Port Number (if applicable)
H Source IP Address
H TCP Filter (prevents the receipt of downstream TCP connect requests)
NOTE:
If the Source IP Address filter is enabled on the Hotwire card and an
IP address is assigned to the DSL interface, there must also be an entry
configured in the Hotwire Client Table for the DSL interface’s IP address.
For more information about IP filtering, see the
SDSL Cards, Models 8310/8312, 8510/8373/8374, 8303/8304, and 8343/8344,
User’s Guide.
Land Bug/Smurf Attack Prevention
Land Bug and Smurf Attack prevention are enhanced firewall features provided
by the DSL Router:
H Land Bug – The DSL router drops all packets received on its DSL interface
or Ethernet interface when the source IP address is the same as the
destination IP address. This prevents the device from being kept busy by
constantly responding to itself.
Hotwire MVL, RADSL, IDSL, and
6371-A2-GB20-10
H Smurf Attack – The DSL Router will not forward directed broadcasts on its
DSL and Ethernet interfaces, nor will it send an ICMP echo reply to the
broadcast address. This ensures that a legitimate user will be able to use the
network connection even if ICMP echo/reply (smurf) packets are sent to the
broadcast address.
August 2000
3-9
Page 30
Configuring the DSL Router
Routed vs. Bridged PDUs
The DSL router supports both the VNET model and the 1483 Routed model
(derived from RFC 1483) for the transportation of PDUs (Protocol Data Units)
from the DSL router to the router in the core network. When operating in
Standard mode, the DSL router supports both routed and bridged PDUs. When
operating in VNET mode, the DSL router supports bridged PDUs only.
NOTE:
Standard mode vs. VNET mode is configured on the DSL card at the
DSLAM/GranDSLAM chassis.
Both ends of the network (e.g., the DSL router and the DSL line card or the core
router) must be configured to operate the same way (i.e., routed or bridged).
If Using This Network Model . . .
1483 Routed or Bridged
(Standard Mode)
Then These DSL Cards Can Be Used . . .
Model 8303 24-port IDSL
Model 8344 24-port SDSL
Model 8374 12-port RADSL
1483 Bridged (VNET Mode) Models 8303/8304 24-port IDSL
Models 8343/8344 24-port SDSL
Models 8373/8374 12-port RADSL
Model 8510 12-port RADSL
The following diagram illustrates the 1483 Routed model (Standard mode) in the
network.
NSP's
Access
Device
POWER
NAP's
Core
Router
NSP's
Access
Device
NAP's ATM
Network
O
I
IPC Hotwire
GranDSLAM
ALARMS
MajorMinorFanBA
DSL
Router
Client
Client
3-10
Figure 3-1. 1483 Routed Network Model (Standard mode)
August 2000
IP/MACIP/1483/FUNIIP/1483/ATM
00-16802
6371-A2-GB20-10
Page 31

DSL Router Configuration Examples
Configuration Examples
The Hotwire DSL Router configuration examples include only a few of the
possible scenarios. This chapter covers some of the common configurations.
The command syntax will vary based on your network setup.
Configuration commands require the access level of Administrator-Config and
changes need to be saved while in configuration mode to take effect. Refer to
Chapter 2,
Accessing the DSL Router
4
.
The Hotwire DSL Router configuration examples include:
H Basic
H Basic NA T
H NAPT
H Unnumbered DSL Interface with Proxy ARP
H DHCP Relay with Proxy ARP
H DHCP Server with Basic NAT
H Downstream Router
Refer to Appendix A,
syntax.
Refer to Appendix B,
specific command default settings and abbreviated command line syntax.
NOTES:
— The examples in this chapter are provided to illustrate some of the
features of the Hotwire DSL Routers. Not all possible feature
configurations are covered in the examples.
Command Line Interface,
Configuration Defaults & Command Line Shortcuts
for specific commands and
, for
6371-A2-GB20-10
— The IP addresses used in the examples are for illustrative purposes only.
These addresses are not intended for use when configuring your local
network.
August 2000
4-1
Page 32

DSL Router Configuration Examples
Basic Configuration Example
Core
Router
155.1.4.253
WAN
155.1.4.254
In this basic example:
DSL
dsl1
DSL
Router
Customer Premises (CP)
Console
Port
Connection
Ethernet
eth1
155.1.3.254
Hub
End-user
Systems
155.1.3.1
155.1.3.2
155.1.3.3
155.1.3.4
00-16590-01
H There are multiple clients with statically assigned public IP addresses
configured on the Ethernet side of the DSL router.
H The IP addresses of the clients are contained within the subnet specified by
the configured Ethernet IP address and subnet mask.
H The next hop router (default gateway) of the clients is the Ethernet interface
(eth1) of the DSL router.
H The next hop router for downstream forwarding from the core router is the
DSL interface (dsl1) of the DSL router.
The command line syntax for this example is:
address eth1 155.1.3.254 255.255.255.0
ifn
ifn
address dsl1 155.1.4.254 255.255.255.0
ip route create upstream eth1 155.1.4.253
4-2
August 2000
6371-A2-GB20-10
Page 33

Basic NAT Configuration Example
Core
Router
155.1.3.1
WAN
NAT Mapping Public IP Addresses Private IP Addresses
192.128.1.1 10.1.3.2
DSL
dsl1
155.1.3.2
DSL
Router
DSL Router Configuration Examples
Customer Premises (CP)
Console
Port
Connection
Ethernet
eth1
10.1.3.1
Hub
End-user
Systems
10.1.3.2
10.1.3.3
10.1.3.4
10.1.3.5
00-16767
192.128.1.2 10.1.3.3
192.128.1.3 10.1.3.4
192.128.1.4 10.1.3.5
In this Basic NAT example:
H NAT is used for one-to-one mapping of addresses.
H There are four private IP addresses configured on the Ethernet side of the
DSL router with NAT static mappings to four public IP addresses.
H The Ethernet interface (eth1) is in the private address space and the DSL
interface is in public address space.
H The next hop router (default gateway) for the clients is the Ethernet IP
address of the DSL router, 10.1.3.1.
The command line syntax for this example is:
address eth1:1 10.1.3.1 255.255.255.248
ifn
ifn
address dsl1 155.1.3.2 255.255.255.0
ip route create upstream eth1 155.1.3.1
nat basic address 192.128.1.0
nat basic map 192.128.1.1 10.1.3.2 10.1.3.5
nat basic enable
6371-A2-GB20-10
August 2000
4-3
Page 34

DSL Router Configuration Examples
NAPT Configuration Example
Core
Router
155.1.3.1
WAN
DSL
dsl1
155.1.3.2
DSL
Router
Customer Premises (CP)
Console
Port
Connection
Ethernet
eth1
10.1.3.1
Hub
10.1.3.2
10.1.3.3
10.1.3.4
10.1.3.
End-user
Systems
n
NAPT Mapping Public IP Addresses Private IP Addr esses
155.1.3.2 Port 23 10.1.3.4
155.1.3.2 Port 23 10.1.3.2
155.1.3.2 Port 23 10.1.3.3
155.1.3.2 Port
n
10.1.3.
n
In this NAPT example:
00-16611-02
H The DSL router is configured for NAPT using a single public IP address.
H When using NAPT, the DSL interface (dsl1) must be numbered because the
Ethernet interface will be configured within the private address space.
H NAPT static mapping is configured for a server (Telnet port 23) on the
Ethernet interface but publicly available.
The command line syntax for this example is:
ifn address eth1 10.1.3.1 255.255.255.0
ifn address dsl1 155.1.3.2 255.255.255.0
ip route create upstream eth1 155.1.3.1
nat napt address 155.1.3.2
nat napt map tcp 10.1.3.4 23
nat napt enable
4-4
August 2000
6371-A2-GB20-10
Page 35

DSL Router Configuration Examples
Unnumbered DSL Interface with Proxy ARP Configuration Example
Customer Premises (CP)
Core
Router
155.1.3.253
WAN
DSL
dsl1
Unnumbered
DSL
Router
Console
Port
Connection
Ethernet
eth1
155.1.3.254
Hub
155.1.3.1
155.1.3.2
155.1.3.3
End-user
Systems
00-16768
In this Unnumbered DSL Interface with Proxy ARP example:
H The clients are statically configured and use the core router as the next hop
router (default gateway) in order to create the LAN extension configuration.
H The DSL interface is unnumbered.
H The DSL line is configured (at the DSLAM/GranDSLAM chassis) for VNET
mode.
H Proxy ARP and NAPT cannot be enabled at the same time.
H If Basic NAT was enabled, the DSL interface (dsl1) must have Proxy ARP
enabled if the dsl1 interface address is part of the Basic NAT global IP
network address.
6371-A2-GB20-10
H The clients, the DSL router’s Ethernet interface, and the core router interface
are all on the same logical network.
The command line syntax for this example is:
address eth1 155.1.3.254 255.255.255.0
ifn
ifn
address dsl1 unnumbered
ip route create upstream eth1 155.1.3.253
proxy arp eth1 enable
proxy arp dsl1 enable
August 2000
4-5
Page 36

DSL Router Configuration Examples
DHCP Relay with Proxy ARP Configuration Example
DHCP
Server
Core
Router
155.1.3.252
WAN
155.1.3.253
Unnumbered
DSL
dsl1
DSL
Router
Customer Premises (CP)
Console
Port
Connection
Ethernet
eth1
155.1.3.254
Hub
End-user
Systems
155.1.3.1
155.1.3.2
155.1.3.3
00-16612-01
In this DHCP Relay with Proxy ARP example:
H The clients are using dynamic IP address assignment and use the core router
as the next hop router (default gateway) in order to create the LAN extension
configuration.
H The DSL line is configured (at the DSLAM/GranDSLAM chassis) for VNET
mode.
H The DSL interface (dsl1) is unnumbered.
H The clients, the Ethernet interface (eth1), and the core router interface are all
on the same logical network.
H IP Scoping must be disabled at the DSL card.
H The DSL router is configured as a DHCP relay.
The command line syntax for this example is:
address eth1 155.1.3.254 255.255.255.0
ifn
ifn
address dsl1 unnumbered
ip route create upstream eth1 155.1.3.253
proxy arp eth1 enable
proxy arp dsl1 enable
dhcp relay enable
dhcp relay address 155.1.3.252
4-6
August 2000
6371-A2-GB20-10
Page 37

DHCP Server with Basic NAT Configuration Example
Customer Premises (CP)
Core
Router
DSL
Router
Console
Port
Connection
Ethernet
eth1
10.1.3.10
155.1.3.1
WAN
DSL
dsl1
155.1.3.2
Public IP Addresses for Basic NAT Private IP Addresses
192.128.1.1 10.1.3.2
DSL Router Configuration Examples
End-user
Systems
10.1.3.2
10.1.3.3
Hub
10.1.3.9
00-16613-01
192.128.1.2 10.1.3.3
. . . . . .
192.128.1.8 10.1.3.9
In this DHCP Server with Basic NAT example:
H The clients are using dynamic IP address assignment and use the Ethernet
interface (eth1) of the DSL router as the next hop router (default gateway).
H The DSL interface (dsl1) must be numbered.
H The DSL router is configured as the DHCP server giving the private IP
addresses to the clients.
H The Ethernet interface is in private address space. NAT is used for
one-to-one mapping of addresses.
The command line syntax for this example is:
address eth1 10.1.3.10 255.255.255.240
ifn
ifn
address dsl1 155.1.3.2 255.255.255.0
ip route create upstream eth1 155.1.3.1
nat basic address 192.128.1.0
nat basic enable
dhcp server addresses 10.1.3.2 10.1.3.9
dhcp server router 10.1.3.10
dhcp server enable
6371-A2-GB20-10
August 2000
4-7
Page 38

DSL Router Configuration Examples
Downstream Router Configuration Example
Customer Premises (CP)
End-user
Systems
120.26.7.1
Core
Router
155.1.3.1
WAN
120.26.7.2
130.26.7.1
130.26.7.2
130.26.7.3
DSL
dsl1
155.1.3.2
DSL
Router
Console
Port
Connection
Ethernet
eth1
120.26.7.5
Hub
120.26.7.3
120.26.7.100
Router Hub
In this downstream router example:
H There are clients statically configured and connected to the DSL router.
H There are also clients connected behind a downstream router.
H The DSL interface (dsl1) is numbered.
The command line syntax for this example is:
ifn
address eth1 120.26.7.5 255.255.255.0
ifn
address dsl1 155.1.3.2 255.255.255.0
ip route create upstream eth1 155.1.3.1
ip route create 130.26.7.0 255.255.255.0 120.26.7.100
End-user
Systems
00-16591-01
4-8
August 2000
6371-A2-GB20-10
Page 39

Monitoring the DSL Router
What to Monitor
This chapter presents information on how to access and monitor the Hotwire DSL
Router’s status and performance statistics. You can monitor DSL router
operations by viewing:
H LEDs on the DSL router’s front panel.
H DSL Router Interfaces Status, including DSL and Ethernet LED status.
H DSL Router Statistics, including DSL Service Domain, DSL Management
Domain, Ethernet, and IP statistics.
5
H DSL Router SNMP traps.
Detecting Problems
The DSL router can detect and report problem conditions and the user can
perform diagnostic tests. The DSL router offers a number of indicators to alert
you to possible problems:
H LEDs provide status. Refer to
H Status messages for both the Ethernet and DSL links. Refer to
H Network performance statistics for both the Ethernet and DSL links. Refer to
H Current status of DSL Router SNMP traps, if enabled. Refer to Appendix C,
For additional information regarding diagnostic tests, System Log messages, and
troubleshooting, refer to Chapter 6,
Status LEDs
Installation Instructions for LED indications and troubleshooting of the
hardware installation.
Interfaces
Interface Statistics
Traps & MIBs
on page 5-2.
on page 5-3.
.
Diagnostics and Troubleshooting.
in the Hotwire DSL Router
Status of
6371-A2-GB20-10
August 2000
5-1
Page 40

Monitoring the DSL Router
Status of Interfaces
From the Command Line Interface, the current status of the Ethernet (eth1)
Interface and the DSL (dsl1) Interface can be obtained with one command:
The information displayed for Ethernet and DSL Interfaces is presented below.
show interface {eth1 | dsl1}
Use to request status statistics for the named interface, eth1 or dsl1.
Minimum access level: Operator
eth1 – Ethernet interface
dsl1 – DSL interface
eth1 status – Fields included in the display of Ethernet status: eth1
dsl1 status – Fields included in the display of DSL status: dsl1
show interface
– Ethernet Link: { up | down }
This is the same status as reflected by the Ethernet LED.
– MAC address:
– proxy ARP eth1 { enabled | disabled }
– ifn eth1:1 – ip-addr
– ifn eth1:2 – ip-addr
– ifn eth1:3 – ip-addr
– ifn eth1:4 – ip-addr
– DSL Link: { up | down }
This is the same status as reflected by the DSL LED.
– MAC address:
– proxy ARP dsl1 { enabled | disabled }
– ifn dsl1:1 – ip-addr
– ifn dsl1:2 – ip-addr
– ifn dsl1:3 – ip-addr
– ifn dsl1:4 – ip-addr
xx:xx:xx:xx:xx:xx
x.x.x.x
mask
x.x.x.x
mask
x.x.x.x
mask
x.x.x.x
mask
xx:xx:xx:xx:xx:xx
x.x.x.x
mask
x.x.x.x
mask
x.x.x.x
mask
x.x.x.x
mask
x.x.x.x
x.x.x.x
x.x.x.x
x.x.x.x
x.x.x.x
x.x.x.x
x.x.x.x
x.x.x.x
*
*
5-2
* The Primary designation of a numbered interface marks that interface as the one
whose IP address is used as a Router ID. If no interface is defined as Primary , the last
numbered interface created becomes the Primary IP Address.
August 2000
6371-A2-GB20-10
Page 41

Interface Statistics
From the Command Line Interface, statistics are available for DSL, Ethernet, and
IP processing. Statistics are available for all three selections, eth1, dsl1, and
ip, with one command:
The format of the statistics information display is presented below.
show statistics [ eth1 | dsl1 | ip ]
Use to request statistics for the named interface, eth1 or dsl1, or IP processing statistics.
Minimum access level: Operator
eth1 – Ethernet interface statistics
dsl1 – DSL interface statistics
ip – IP processing statistics
Information displayed for show statistics eth1:
Monitoring the DSL Router
show statistics
– Total Bytes Received
– Total Bytes Transmitted
– Total Frames Received
– Total Frames Transmitted
– Total Frames Discarded: Each Discard Reason will display with # of frames
discarded for each specific Discard Reason.
Refer to Table 5-1, Discard Reasons for the Ethernet Interface (eth1).
. . . . . . . . . . . . . .
. . . . . . . . . . . .
. . . . . . . . . . . .
. . . . . . . . . .
nnnn
nnnn
nnnn
nnnn
Information displayed for show statistics dsl1:
H Service Domain Statistics (end-user traffic):
– Total Bytes Received
– Total Bytes Transmitted
– Total Frames Received
– Total Frames Transmitted
H Management Domain Statistics (management traffic):
– Total Bytes Received
– Total Bytes Transmitted
– Total Frames Received
– Total Frames Transmitted
H Total Frames Discarded: This total is for both the Service Domain and the
Management Domain. Each Discard Reason will display with # of frames discarded
for each specific Discard Reason.
Refer to Table 5-2, Discard Reasons for the DSL Interface (dsl1)
Information displayed for show statistics ip:
– Total Packets Received
– Total Packets Transmitted
– Total Packets Discarded: Each Discard Reason will display with # of packets
discarded for each specific Discard Reason.
Refer to Table 5-3, Discard Reasons for IP.
. . . . . . . . . . . . . .
. . . . . . . . . . . .
. . . . . . . . . . . .
. . . . . . . . . .
. . . . . . . . . . . . . .
. . . . . . . . . . . .
. . . . . . . . . . . .
. . . . . . . . . .
. . . . . . . . . . . .
. . . . . . . . . .
nnnn
nnnn
nnnn
nnnn
nnnn
nnnn
nnnn
nnnn
.
nnnn
nnnn
6371-A2-GB20-10
August 2000
5-3
Page 42

Monitoring the DSL Router
Clearing Statistics
From the Command Line Interface, the statistics can be cleared.
clear statistics [ eth1 | dsl1 | ip ]
Clears the statistics for the named interface. If no interface is entered, ALL statistics for
all interfaces are cleared.
Minimum access level: Administrator
eth1
– Ethernet interface statistics
dsl1
– DSL interface statistics
ip
– IP processing statistics
Example: clear statistics eth1
List of Discard Reasons
The Discard Statistics represents the number of frames or packets discarded.
The display includes the reason for the discard. The following tables list discard
reasons for:
H Ethernet Interface (Table 5-1)
H DSL Interface (Table 5-2)
H IP (Table 5-3)
Table 5-1. Discard Reasons for the Ethernet Interface (eth1) (1 of 2)
Discard Reasons for the Ethernet Interface (eth1)
Alignment Error
CRC Error
Excessive Collisions
Excessive Defers on TX
FIFO Overflow Error
Frame Length Greater than Max
Late Collision on TX
5-4
No Carrier Detect on TX
Parity Error
Receive Buffer Pool Depletion
Receiver Halted
August 2000
6371-A2-GB20-10
Page 43

Monitoring the DSL Router
Table 5-1. Discard Reasons for the Ethernet Interface (eth1) (2 of 2)
Discard Reasons for the Ethernet Interface (eth1)
Receiver Missed Frame
Signal Quality Error on TX
Srv Domain Phy TX Queue Overflows
Srv Domain Receive Queue Overflows
Srv Domain Wrpr TX Queue Overflows
TX Halted
TX Parity Error
TX Underflow
Unsupported Encapsulation Protocol
Unsupported SNAP Network Protocol
Unsupported TypeII Network Protocol
Table 5-2. Discard Reasons for the DSL Interface (dsl1) (1 of 2)
Discard Reasons for the DSL Interface (dsl1)
Alignment Error
Mgmt Domain Phy TX Queue Overflows
Mgmt Domain Rcv Queue Overflows
Mgmt Domain TX Link Queue Overflows
Mgmt Domain Wrpr TX Queue Overflows
Receive Aborts
Receive Buffer Pool Depletion
Receive CRC Errors
Receive Frame Too Short or Too Long
Receive Interrupt Errors
6371-A2-GB20-10
Receive Overruns
Receive Unknown Errors
Service Domain Rcv Queue Overflows
Srv Domain Phy TX Queue Overflows
Srv Domain TX Link Down Discards
August 2000
5-5
Page 44

Monitoring the DSL Router
Table 5-2. Discard Reasons for the DSL Interface (dsl1) (2 of 2)
Table 5-3. Discard Reasons for IP
Discard Reasons for the DSL Interface (dsl1)
Srv Domain Wrpr TX Queue Overflows
Unknown Frame Type Errors
Unrecognized VNID
Unsupported Encapsulation Protocol
Unsupported Network Protocol
Discard Reasons for IP
Bad Port to Destination
Bad Port to Source
DSL Receive Packets Filtered
DSL Transmit Packets Filtered
Ethernet Receive Packets Filtered
Ethernet Transmit Packets Filtered
Fragmentation Failures
ICMP Errors
IP Processing Disabled
No Route to Destination
No Route to Source
No Upstream Route
Other Reassembly Failures
Other Receive Errors
Other Transmit Errors
Packets Pending on ARP Discarded
5-6
Reassembly Timeout
TCP Errors
Time to Live Expired
Transport Protocol Not Handled
UDP Errors
August 2000
6371-A2-GB20-10
Page 45

Diagnostics and Troubleshooting
Diagnostics and Troubleshooting Overview
There are several features available to assist in evaluating the Hotwire DSL
Router. The following sections are covered in this chapter:
H Device Restart
H Alarms Inquiry
H System Log
H Ping
6
Device Restart
Alarms Inquiry
H TraceRoute
The DSL router can be restarted locally or remotely. From the Command Line
Interface, type Restart and press Enter.
The DSL router reinitializes itself, performing a power-on self-test and resetting
the local System Log (SYSLOG).
show alarms
This command allows the operator to display the list of current alarm conditions, if any .
Minimum access level: Operator
The possible output lines are:
Alarm: Management Address Conflict
Alarm: Failed Selftest
Alarm: System Error
No alarm condition is set
Alarm condition reverts to Normal when the offending problem has been corrected.
6371-A2-GB20-10
August 2000
6-1
Page 46

Diagnostics and Troubleshooting
System Log
The Hotwire DSL Router can log significant system events (SYSLOG). The
SYSLOG can be maintained locally on the DSL router and can also be sent to a
remote SYSLOG server , preferably in the management domain. To activate:
H The DSL router must be configured to enable the output of SYSLOG
messages via the syslog enable command. (The Management Controller
Card (MCC) has SYSLOG always enabled.)
H An IP address (loopback or remote) must be supplied.
H The SYSLOG can also be captured by a remote SYSLOG server running the
UNIX daemon
IP address where the
is using.
The advantage of using a remote SYSLOG server is that ALL events will be
maintained upon restart of the DSL router. The local SYSLOG is cleared
upon restart.
Events are classified by severity level and the system administrator can specify
the minimum severity to be logged.
syslogd
or an equivalent program. It is necessary to know the
syslogd
resides and the UDP port number the
syslogd
show syslog
Displays the current status of system as enabled or disabled. If enabled, the severity
level, management IP address, and UDP port will be displayed.
syslog { enabled | disabled }
level { emer | err | norm | info }
management ip-addr
port
nnn
x.x.x.x
syslog {enable | disable}
Allows the user to enable or disable SYSLOG output. The SYSLOG IP address must be
entered (next command) and saved to complete enabling SYSLOG.
Minimum access level: Administrator/Config
enable – Enables SYSLOG output.
disable – Disables SYSLOG output.
syslog ip
Specifies the IP address for the host to send system log entries to.
Minimum access level: Administrator/Config
ip-addr – The IP address for SYSLOG (typically loopback address of 127.0.0.1).
syslog port [
ip-addr
port-number
]
6-2
Specifies the UDP port number on the server to which the system events will be sent.
Minimum access level: Administrator/Config
port-number – The UDP port number. Default = 514.
August 2000
6371-A2-GB20-10
Page 47

Diagnostics and Troubleshooting
gy
unusable
SYSLOG Events
syslog level
Specifies the minimum severity level to be logged. Refer to Table 6-1, SYSLOG
Messages, for a list of messages by severity level.
Minimum access level: Administrator/Config
level – The minimum level to be logged. The default is NORM.
The choices for severity level (displayed as high severity to low severity) are as follows:
EMER – emergency, the system is unusable
ERR – error conditions reported
NORM – normal or administrative reporting
INFO – informational reporting
Example: To log EMER and ERR severity levels, enter syslog level ERR
show log [
Displays the contents of the local system error log. (The 100 most recent SYSLOG
entries are kept locally .) The user specifies how many entries they wish to view. Entries
are displayed in reverse order from most recent to oldest.
number – The number of local entries to be seen. Default = 10. Range = 1–100.
NOTE: The SYSLOG retained locally will be reset at the DSL router if the restart
level
number
command is issued. External logs are retained after a DSL router restart.
]
The following are some of the SYSLOG events that will be reported for defined
severity levels.
Table 6-1. SYSLOG Messages (1 of 2)
Level
EMER Emergency and
ERR Error conditions
Description Event
the system is
unusable
reported
Alarm Cleared
Alarm Set
System Abort
ARP Table size exceeded
Executable image in flash invalid
Frame received in error
6371-A2-GB20-10
August 2000
6-3
Page 48

Diagnostics and Troubleshooting
p
g
reporting
Table 6-1. SYSLOG Messages (2 of 2)
Level EventDescription
NORM Normal or
administrative
ortin
re
INFO Informational
reporting
Admin enable
Admin enable failure
Any configuration change command
Configuration changes saved
Download completed
Download failure
Login
Login failure
Logout
Statistics cleared
Switch program LMC message received
System started
ARP table entry created due to packet arrival
ARP table entry created for DHCP address assignment
ARP table entry deleted due to time out
Device information LMC message received
Packet filter action
Routing table entry created for DHCP address
assignment
VNID update LMC message received
SYSLOG Message Display
The SYSLOG message displays the following fields:
H Date
H Time
H Severity Level
H DSLAM Slot #/Port #
H System Identifier
H SYSLOG Event Description
This is an example of a SYSLOG message:
01/06/00 21:22:38 5 03/01 CUSTOMER Console logout complete
6-4
August 2000
6371-A2-GB20-10
Page 49

Ping
Diagnostics and Troubleshooting
The Ping program is an IP-based application used to test reachability to a specific
IP address by sending an ICMP echo request and waiting for a reply. From the
Command Line Interface, Ping can test connectivity upstream or downstream.
ping
dest-ip
[mgt | -x
Pings the specified destination IP address. Once Ping starts, the input prompt will not
redisplay until either the Ping finishes or the Ping command is aborted with Ctrl-c.
Minimum access level: Administrator
dest-ip – The destination IP address of the device to ping.
mgt – Specifies that the IP address is in the management domain (through the MCC).
Do not use with –x source-ip selection.
source-ip – The source IP address to be used. The default source address is from the
service domain in which the test is being done. The IP address is validated to verify that
it is an interface IP address.
bytes – Bytes of data (l = length). Default = 64 bytes. Range = 0–15,000.
time – Number of seconds to wait before ending ping attempt. Default = 10 seconds.
Range = 0–60.
interface – The target interface for the command (eth1|dsl1). Do not use with –x
source-ip selection.
Example: ping 135.300.41.8 –l 144 –w 30 -i eth1
source-ip
] [-l
bytes
] [-w
time
] [-i {eth1 | dsl1}]
Ping Test Results
Ping test results display in the following formats.
H Ping successful:
Ping reply [
x.x.x.x]:
bytes of data=
nn
H Ping timeout:
Ping reply [
x.x.x.x]:
REQUEST TIMED OUT
H ICMP echo response of an unreachable destination:
Ping reply [
x.x.x.x]:
DESTINATION UNREACHABLE
6371-A2-GB20-10
August 2000
6-5
Page 50

Diagnostics and Troubleshooting
TraceRoute
The TraceRoute program is an IP diagnostic tool that allows you to learn the path
a packet takes from the service domain local host to its remote host.
If you are unable to ping a device in a Hotwire network configuration, you may
want to run TraceRoute to identify the link (destinations up to 64 hops) between
the DSL router and the device that is not forwarding the Ping message.
traceroute
[-i {eth1 | dsl1}]
Performs TraceRoute to the specified destination IP address. Once T raceRoute starts,
the input prompt will not redisplay until either TraceRoute finishes or the T raceRoute
command is aborted with Ctrl-c.
Minimum access level: Administrator
dest-ip – The destination IP address for TraceRoute.
source-ip – The source IP address used. The default source address is from the
service domain in which the test is being done. The IP address is validated to verify that
it is an interface IP address.
bytes – Bytes of data (l = length). Default = 64 bytes. Range = 0–15,000.
time – Time (in seconds) before the TraceRoute is abandoned. Default = 10 seconds.
Range = 0–60.
hops – Decimal number that specifies the maximum number of hops to be tested.
Default = 8. Range = 0–128.
interface – The target interface for the command (eth1 | dsl1). Do not use with the
–x source-ip selection.
Example: traceroute 135.300.41.8 –w 80 -i eth1
TraceRoute Test Results
TraceRoute results display in the following format:
dest-ip
[-x
source-ip
Tracing route to [
byte packet
] [-l
bytes
] [-w
time
] [-h
x.x.x.x
] over a max of nn hops with
hops
]
nnn
6-6
Round T rip Time
IP Address of
Hop #
1 <100ms <100ms <100ms
2 <100ms <100ms <100ms
3 <200ms <200ms <200ms
4 <200ms <200ms <200ms
Try #1 Try #2 Try #3
Responding System
x.x.x.x
x.x.x.x
x.x.x.x
x.x.x.x
The Hop # is the Time to Live (TTL) value set in the IP packet header. The Round
Trip Time contains the time in 100ms intervals for each attempt to reach the
destination with the TTL value.
August 2000
6371-A2-GB20-10
Page 51

Command Line Interface
Command Line Interface Feature
The Hotwire DSL router is managed with text commands from the Command Line
Interface. The Command Line Interface can be accessed:
H Locally with an ASCII terminal connected to the Console port, or
H Remotely via a Telnet session.
The Command Line Interface is ASCII character-based and provides the
capability to:
A
H Display the syntax of commands.
H Change the operational characteristics of the DSL router by setting
configuration values.
H Restore all configuration values to the initial factory defaults.
H Display DSL router hardware and identification information.
H Display system status, including DSL link status and Ethernet status.
H Display a sequence of commands that would have the effect of setting all
configurable parameters to their current value.
Refer to Appendix B,
Configuration Defaults & Command Line Shortcuts.
6371-A2-GB20-10
August 2000
A-1
Page 52

Command Line Interface
Navigation
Command Recall
The Hotwire DSL router uses the following keys (as do most terminal emulation
programs):
H Enter or Return – Accepts the input.
H Ctrl-c – Aborts the entry or clears the input line.
H Down Arrow – Repeats an entry within the last five entered.
H Up Arrow – Displays the last entry.
H Left Arrow – Moves the insertion point one space to the left.
H Right Arrow – Moves the insertion point one space to the right.
The Hotwire DSL router keeps a history of the last several commands entered on
the command line interface. For example, if you press the Up Arrow key, the most
recently entered command will appear on the command line, where it can be
edited and reentered by pressing Enter. If you press the Up Arrow key again, the
next most recent command will appear, etc.
After pressing the Up Arrow key one or more times, pressing the Down Arrow key
moves down the list of recent commands, wrapping past the end of the list in
either direction.
Commands appearing in the command line can be edited. Use the Left and Right
Arrow keys to move the insertion point, enter the new characters or use the
Delete key to delete the character just to the left of the insertion point.
Document Conventions
This syntax is used throughout this manual. The Command Line Interface is not
case-sensitive, with the exception of the Login ID and Password fields.
Syntax Translation
[ ]
{ }
|
Italics
Bold
x.x.x.x
xx:xx:xx:xx:xx:xx
Square brackets represent an optional element.
Braces represent a required entry.
Vertical bar separates mutually exclusive elements.
Entry is a variable to be supplied by the operator.
Enter (type) as shown.
32-bit IP address and mask information where x is an
8-bit weighted decimal notation.
MAC address information where x is a hexadecimal
notation.
A-2
6371-A2-GB20-10August 2000
Page 53

Command Line Interface Commands
Configuration Control Commands
configure {terminal | factory}
Enables the Administrator configuration mode. Configuration mode will remain in effect
until the exit or logout command has been entered. While in configuration mode, the
show commands are unavailable.
Minimum access level: Administrator
configure terminal – Configuration mode is in effect and all changes entered by the
Administrator are made on top of the current running configuration. When finished
entering the commands needed to configure the DSL router, the save command must
be input to save the configuration changes or the exit command can be used to
discard the configuration changes and leave the configuration mode.
configure factory – Causes the configuration mode to be entered and the factory
default settings to be loaded. The save command must be used to save the
configuration factory defaults as the active configuration.
CAUTION: All previously set interface IP address assignments, IP route table
entries, ARP cache entries, NAT static entries, and DHCP server entries
will be purged when the save command is executed.
save
Saves configuration changes to the active configuration in NVRAM. No configuration
changes are effect until the save command is issued. If the save command is entered
and there are changes that require a reboot of the DSL router, a prompt states that a
reset is necessary for changes to take effect and prompts for verification.
Minimum access level: Administrator/Config
yes – Changes are stored and the DSL router resets automatically if interface addresses
have been changed.
no – DSL router is left in configuration mode.
Command Line Interface
RFC 1483 Encapsulation
1483encap [LLC | VC]
Specifies the method for carrying the routed PDUs.
Minimum access level: Administrator/Config
LLC – LLC encapsulation. Default = LLC.
VC – VC-based multiplexing.
Ethernet Frame Format
frame [802.3 | DIX]
Specifies the Ethernet frame format that is to be used.
Minimum access level: Administrator/Config
format – 802.3 or DIX. Default = DIX.
6371-A2-GB20-10
August 2000
A-3
Page 54

Command Line Interface
Interface and Service Domain IP Address
ifn address {eth1[:ifn] | dsl1[:ifn]}
ip-address mask
[primary]
ifn {dsl1[:ifn] | eth1[:ifn]} primary
ifn address dsl1 unnumbered
Specifies the IP address associated with either the Ethernet interface or the DSL
interface. Up to four (4) IP addresses may be assigned on each interface. An interface
address and mask cannot be changed while there is a static route (upstream or
downstream) that uses it. Interface IP address ranges must not overlap.
Minimum access level: Administrator/Config
eth1, eth1:1, eth1:2, eth1:3, eth1:4 – Ethernet interface. eth1 is the same as eth1:1.
dsl1, dsl1:1, dsl1:2, dsl1:3, dsl1:4 – DSL interface. dsl1 is the same as dsl1:1.
ip-address – The IP address associated with the specified interface.
mask – Mask for the associated subnet.
primary – The Primary designation of a numbered interface marks that interface as the
one whose IP address will be used as the Router ID. (The Router ID is important when
the DSL interface is unnumbered.) If no interface is defined as Primary , the last
numbered interface created will become the Primary IP Address.
unnumbered – Specifies that the DSL interface is to be unnumbered.
NOTES: – For each defined Ethernet interface, a corresponding upstream next hop
Examples: ifn address dsl1 135.300.41.8 255.255.255.0
router IP address must be configured for routing of packets received on
that interface. See ip route create upstream command on page
A-6 for more details.
– When the eth1 is assigned an IP address, this section also defines the
logical network (subnet) containing the locally attached hosts. An IP
route table entry will automatically be created to correspond to the
subnet defined by the mask.
– When the DSL interface is numbered, multiple logical Ethernet interfaces
can be assigned to the same DSL logical interface by configuring the
same upstream next hop router.
– The configured DSL logical interfaces must be either all numbered or a
single unnumbered interface.
– When NAT is being used, the DSL interface must be numbered. Only
one logical interface must be defined for each physical interface, i.e.,
one IP address to each interface.
– When NAT, DHCP Server, or DHCP Relay is enabled, there can be only
one service domain configured.
ifn dsl1 primary
A-4
6371-A2-GB20-10August 2000
Page 55

IP Routing Table
Command Line Interface
delete {eth1[:ifn] | dsl1[:ifn]}
Deletes any of the assignments that are configured for the interface. Only the specific
Ethernet or DSL interface number needs to be specified.
An interface address and mask cannot be deleted while there is a static route (upstream
or downstream) that uses it. First, delete the IP route with the ip route delete
command (see IP Routing Table).
Minimum access level: Administrator/Config
eth1, eth1:1, eth1:2, eth1:3, eth1:4 – Ethernet interface. eth1 is the same as eth1:1.
dsl1, dsl1:1, dsl1:2, dsl1:3, dsl1:4 – DSL interface. dsl1 is the same as dsl1:1.
Only dsl1 or dsl1:1 are acceptable inputs for an unnumbered interface.
Example: delete eth1:4
ip route create
ip route delete
Configures the downstream static routes. Downstream routes cannot be created unless
at least one Ethernet interface has been configured. To configure upstream routers, refer
to the next set of entries.
create – Create a downstream IP route table entry . To configure a downstream default
gateway , enter a destination IP address and a subnet mask of 0.0.0.0.
delete – Delete a downstream IP route table entry. This will delete an IP route placed in
the table by the DHCP server, the DHCP relay, or manually entered static entries.
NOTE: An interface route is created automatically when an address and mask are
assigned to an Ethernet interface with the ifn address command. The
Ethernet interface route can be deleted with the ip route purge or the
ip route delete command. Once deleted, the interface route can be
entered manually using ip route create or a new ifn address
command.
dest-ip – IP address of the destination. The destination IP address must be within the
address range of a configured Ethernet interface or the next-hop-ip address must be
provided.
dest-mask – IP mask for the destination IP address.
next-hop-ip – IP address of the next hop downstream router used to reach the
destination. A next hop with an IP address of 0.0.0.0 specifies a directly reachable client.
A nonzero next-hop-ip address must be within the address range of an Ethernet
interface.
remote – Indicates that the device specified by the destination IP and destination mask
is logically within a local subnet route but is not on the physical Ethernet and resides
upstream from the DSL router. A remote route cannot be created unless at least one
DSL interface has previously been configured.
Example: Refer to Chapter 4,
dest-ip dest-mask
dest-ip dest-mask
DSL Router Configuration Examples
{next-hop-ip | remote}
.
6371-A2-GB20-10
August 2000
A-5
Page 56

Command Line Interface
ip route create upstream eth1[:
ip route delete upstream eth1[:
Enter or delete upstream IP routing table entries. When the DSL interface is
unnumbered, an IP routing table entry will be created automatically with the next hop
router as remote. To configure downstream routers, refer to the previous set of entries.
Minimum access level: Administrator/Config
create – Create an upstream IP route table entry .
delete – Delete an upstream IP route table entry .
eth1, eth1:1, eth1:2, eth1:3, eth1:4 – Ethernet interface. eth1 is the same as eth1:1.
Specified logical Ethernet interface.
next-hop-ip – IP address of the next hop upstream router used to reach the remote
destination or the downstream default gateway .
NOTE: When the DSL interface is numbered, the next hop router IP address must
Example: Refer to Chapter 4,
fall into one of the service domain IP subnets configured for the DSL
interface.
DSL Router Configuration Examples
ifn] next-hop-ip
ifn
]
.
ip route purge
Deletes all IP route table entries, including interface routes and those automatically
added by DHCP Server and DHCP Relay agent.
NOTE: An interface route is created automatically when an IP address and mask
Minimum access level: Administrator/Config
are assigned to an Ethernet interface with the ifn address command.
The Ethernet interface route can be deleted with the ip route purge or
the ip route delete command. Once deleted, the interface route can
be entered manually using ip route create or a new ifn address
command.
A-6
6371-A2-GB20-10August 2000
Page 57

ARP Table
Command Line Interface
arp timeout incomplete [
Specifies the ARP table timeout value in seconds for incomplete ARP table entries.
Default = 5 seconds.
Minimum access level: Administrator/Config
arp timeout complete [
Specifies the ARP table timeout value in minutes for complete ARP table entries.
Default = 20 minutes.
Minimum access level: Administrator/Config
arp { create | delete }
Creates or deletes a single, static ARP table entry . Static ARP entries created with this
command are retained across resets/power cycles.
Minimum access level: Administrator/Config
create – Create an ARP table entry.
delete – Delete an ARP table entry.
ip-address – The IP address of the ARP entry to be created or deleted.
mac-address – MAC address (valid for create command).
Examples: arp create 132.53.4.2 00:10:4b:97:6c:44
arp delete 132.53.4.2
time
]
time
]
ip-address mac-address
Proxy ARP
arp purge
Deletes ALL static and dynamic ARP table entries.
Minimum access level: Administrator/Config
proxy arp {eth1 | dsl1 } [ enable | disable ]
Enables or disables proxy ARP for the specified interface.
Minimum access level: Administrator/Config
eth1 – The Ethernet interface.
dsl1 – The DSL interface.
enable – Enable Proxy ARP. Default = Enable.
disable – Disable Proxy ARP.
NOTE: Proxy ARP and NAPT cannot be enabled at the same time. When Basic
NAT is enabled, Proxy ARP is allowed on the dsl1 interface.
Example: proxy arp dsl1 disable
6371-A2-GB20-10
August 2000
A-7
Page 58

Command Line Interface
NAT
nat basic enable
Enables the one-to-one mapping function of Basic NA T. Enabling Basic NAT
automatically disables NA T NAPT. If Basic NAT is enabled, Proxy ARP must be enabled
on the dsl1 interface when the dsl1 interface address is part of the Basic NA T global IP
network address.
Minimum access level: Administrator/Config
nat napt enable
Enables the many-to-one mapping function of NAPT. Enabling NAT NAPT automatically
disables Basic NAT.
Minimum access level: Administrator/ Config
NOTE: Proxy ARP and NAPT cannot be enabled at the same time.
nat basic address
Defines the public IP addresses used in the one-to-one mapping function of Basic NA T
Up to 256 addresses can be allocated with Basic NA T.
Minimum access level: Administrator/Config
ip-addr ip-mask – Any valid public IP address/IP mask. Default = 255.255.255.0.
Example: nat basic address 192.128.1.1
nat napt address
Defines the public IP addresses used in the public IP address of a single host for use in
the many to one mapping function of NAPT. NAPT cannot accept incoming requests,
unless a static NA T entry has been configured.
Minimum access level: Administrator/Config
ip-addr – Any valid public IP address.
Example: nat napt address 192.128.1.1
nat timeout
Specifies the NA T timeout value for mappings set up dynamically.
Minimum access level: Administrator/Config
time – The timeout value in minutes. Default = 20 minutes.
Example: nat timeout 90
time
ip-addr [ip-mask
ip-addr
]
A-8
nat napt map { udp | tcp }
Permits global access to a local server, such as a Web server. Port-based static entries
can be configured for NAPT. This allows a global host to access a server behind the
DSL router without exposing the local server’s IP address.
Minimum access level: Administrator/Config
udp, tcp – Specify the protocol to which the mapping applies.
server-ip – Enter the IP address of a local server. Only one server of a particular type
(FTP, Telnet, SMPT, TFTP , gopher, finger, http, etc.) can be supported at one time.
port – The destination port number for the specified server.
Example: nat napt map tcp 192.128.1.1 102
server-ip port
6371-A2-GB20-10August 2000
Page 59

Command Line Interface
nat basic map public-ip private-ip
nat basic map lower-public-ip lower-private-ip upper-private-ip
Statically maps public to private IP addresses for the one-to-one mapping function of
Basic NAT. In the first command, a single address pair is mapped. In the second
command, a range of IP addresses will be contiguously mapped starting at the pair
defined by the lower-public-ip and lower-private-ip argument.
Minimum access level: Administrator/Config
public-ip – IP address of the public address space which is to be mapped to the IP
address of a local host.
private-ip – IP address of a local host which is to be mapped to an IP address in the
public IP address space.
lower-public-ip – Lowermost IP address of a range of public addresses which are to be
mapped to a range of IP addresses of local hosts.
lower-private-ip – Lowermost IP address of a range of local host IP addresses which
are to be mapped to a range of IP addresses in the public IP address space.
upper-private-ip – Uppermost IP address of a range of local IP addresses which are to
be mapped to a range of IP addresses of local hosts.
Example: nat basic map 192.128.1.1 10.1.3.2
nat basic delete private-ip
nat basic delete lower-private-ip upper-private-ip
In the first command, the command deletes static mapping entry associated with the
specified one-to-one mapping of Basic NA T. In the second command, a range of
mappings will be contiguously deleted starting at the pair defined by the lower-private-ip
and ending with the upper-private-ip argument.
Minimum access level: Administrator/Config
private-ip – Statically mapped IP address of the local host.
lower-private-ip – Lowermost IP address of a range of local host IP addresses which
are to be deleted.
upper-private-ip – Uppermost IP address of a range of local IP addresses which are to
be deleted.
Example: nat basic delete 192.128.1.1
nat napt delete {udp | tcp} port
Deletes static mapping entries which identify a local server.
Minimum access level: Administrator/Config
udp, tcp – Specify the protocol used.
port – The port number associated with the server-ip.
Example: nat napt delete tcp 102
6371-A2-GB20-10
August 2000
A-9
Page 60

Command Line Interface
DHCP Server
nat disable
Disables the currently enabled NAT, either Basic NAT or NAPT.
Minimum access level: Administrator/Config
nat purge
Purges all mapping entries.
Minimum access level: Administrator/Config
The DHCP Server can be enabled and disabled. Based on RFC 2131 and
RFC 2132, supported options are:
H Domain Name
H Domain Name Server
H Router
H Subnet Mask
dhcp server {enable
Enables or disables the DHCP server. For the DHCP Server to be enabled, one (and
only one) address must be assigned to the Ethernet interface. The DHCP Server and
the DHCP Relay Agent cannot be enabled at the same time.
Minimum access level: Administrator/Config
enable – Enable the DHCP Server.
disable – Disable the DHCP Server. Default = disable.
Example: dhcp server enable
dhcp server addresses
Specifies the range of IP addresses to be used by the DHCP server. When the DHCP
address range is changed, all binding entries, automatically added routes, and ARP
entries are removed.
Minimum access level: Administrator/Config
Example: dhcp server address 132.53.4.2 132.53.4.250
| disable}
lower-ip-address upper-ip-address [mask
]
A-10
6371-A2-GB20-10August 2000
Page 61

Command Line Interface
dhcp server leasetime
Specifies the lease-time settings used by the DHCP server.
Minimum access level: Administrator/Config
min-lease-time – Default = 120 minutes (2 hours)
max-lease-time – Default = 4320 minutes (72 hours)
Example: dhcp server leasetime 120 320
dhcp server router
Specifies the router IP address used by the DHCP server.
Minimum access level: Administrator/Config
Example: dhcp server router 132.53.4.2
dhcp server name
Specifies the domain name used by the DHCP server.
Minimum access level: Administrator/Config
Example: dhcp server name Clearwater7
domain name
dhcp server nameserver
Specifies the DNS IP address used by the DHCP server.
Minimum access level: Administrator/Config
Example: dhcp server nameserver 132.53.4.2
min-lease-time max-lease-time
ip-address
ip-address
DHCP Relay Agent
dhcp relay {enable | disable}
Enables or disables the DHCP relay agent. The DHCP relay agent will maintain up to
256 DHCP clients.
Minimum level access: Administrator/Config
enable – Enable the DHCP relay.
disable – Disable the DHCP relay. Default = disable.
Example: dhcp relay enable
dhcp relay address
Use this command to specify the DHCP server to forward DHCP requests to.
Minimum level access: Administrator/Config
Example: dhcp relay address 132.23.4.2
dhcp relay max
Use this command to specify the maximum number of DHCP clients.
Minimum level access: Administrator/Config
number – 1 — 256
Example: dhcp relay max 133
ip-address
number
6371-A2-GB20-10
August 2000
A-11
Page 62

Command Line Interface
IP Packet Processing
Traps
IP multicast {enable | disable}
Enables or disables the forwarding of IP multicast packets. This setting is retained
across power cycles.
Minimum access level: Administrator
enable – Enable forwarding of IP multicast packets.
disable – Disable forwarding of IP multicast packets. Default = disable.
IP processing {enable | disable}
Enables or disables the processing of IP packets in the service domain. This setting is
retained across power cycles.
Minimum access level: Administrator
enable – Enable processing of IP packets. Default = enable.
disable – Disable processing of IP packets.
trap {disable | enable}
Use this command to enable or disable traps. Default = disable.
Minimum access level: Administrator/Config
Name of Traps:
all
authen fail
ccn
devfail
link up
link down
selftest
test start
test stop
warmstart
For additional information, refer to Appendix C,
name of trap
Traps & MIBs
.
A-12
6371-A2-GB20-10August 2000
Page 63

Show Command Outputs
show console
Displays: console enabled or console disabled
show system
Sample show system display:
May 21 09:53:26 2000
System ID: xxxxxxxx
Model #: xxxx, Serial #: xxxxxxxxxxxx, HW-Rev: xxx
Boot: FW-Version xxxxxxxx
2nd Stage Boot: FW-Version xxxxxxxx
Image 0: FW-Version xxxxxxxx, [active]
Image 1: FW-Version xxxxxxxx
DSP: FW-Version xxx
Selftest Result: [0xxxxx] (if failed) { pass | fail }
Command Line Interface
show config
Sample show config display:
syslog { enabled | disabled }
eth1 frame { DIX | 802.3 }
proxy ARP eth1 { enabled | disabled }
proxy ARP dsl1 { enabled | disabled }
NAT disabled or NAT enabled { basic NAT | NAPT }
DHCP server { enabled | disabled }
DHCP relay { enabled | disabled }
IP multicast { enabled | disabled }
IP processing { enabled | disabled }
1483 encapsulation { LLC | VC Muxing }
autologout { enabled | disabled }
6371-A2-GB20-10
August 2000
A-13
Page 64

Command Line Interface
show ip route [ip-address ]
If an IP address is not provided, the entire table will be displayed with the upstream
routes displayed first and the downstream routes next. If the IP address is provided, only
the specific entry will be displayed. If the next hop IP address = 0.0.0.0, the host is
directly reachable on the Ethernet interface (eth1).
Minimum access level: Operator
Sample show ip route display:
source ip-addr
x.x.x.x x.x.x.x x.x.x.x dsl1
source subnet-mask nexthop ip-addr interface
dest ip-addr
x.x.x.x x.x.x.x x.x.x.x eth1
dest subnet-mask nexthop ip-addr interface
show arp
Sample show arp display:
ip-addr
x.x.x.x xx:xx:xx:xx:xx:xx xxxx xxxx
MAC addr timeout (min) status
NOTES: – The timeout value shown is the actual time left for the specific entry.
– The timeout value shown will be Static for configured static entries.
– Status is Complete or Incomplete.
show arp timeout
ARP – timeout for complete = 20 min.
timeout for incomplete = 5 sec.
show nat basic
Sample show nat basic display:
NAT basic – { disabled | enabled }
NAT basic – public network address: xxx.xxx.xxx.xxx
NAT basic – public network mask: xxx.xxx.xxx.xxx
NAT timeout: xx minutes
NAT basic mappings:
public ip
x.x.x.x x.x.x.x
private-ip
A-14
6371-A2-GB20-10August 2000
Page 65

show NAT napt
Sample show NAT napt display:
NAT NAPT – { disabled | enabled }
NAT NAPT – public IP-address:
NAT timeout: xx minutes
NAT NAPT mappings:
private-ip
private-port mapped-port protocol
x.x.x.x
x.x.x.x xxxx xxxx
show traps
Sample show traps display:
warmstart { disabled | enabled }
authen fail { disabled | enabled }
selftest { disabled | enabled }
devfail { disabled | enabled }
test start { disabled | enabled }
test stop { disabled | enabled }
ccn { disabled | enabled }
link up { disabled | enabled }
link down { disabled | enabled }
For additional information, refer to Appendix C,
Traps & MIBs
Command Line Interface
{ udp | tcp }
.
show dhcp server
Displays the DHCP relay’s current status and configuration.
Minimum access level: Administrator
Sample show dhcp server display:
DHCP server { disabled | enabled }
DHCP server – router ip-addr:
DHCP server – name: domain name.com
DHCP server – nameserver ip-addr:
DHCP server – address range:
lower ip-addr
upper ip-addr
DHCP server – subnet mask:
DHCP server – leasetime:
minimum
maximum
DHCP server bindings:
ip-addr
MAC addr Leasetime (min.)
xxxx
xxxx
x.x.x.x xx:xx:xx:xx:xx:xx nnnn
x.x.x.x
x.x.x.x
x.x.x.x
x.x.x.x
x.x.x.x
minutes
minutes
6371-A2-GB20-10
August 2000
A-15
Page 66

Command Line Interface
show DHCP relay
Displays the DHCP relay agent’s current status and configuration.
Minimum level access: Administrator
Sample show dhcp relay display:
DHCP relay – { disabled | enabled }
DHCP relay – server ip-addr:
Maximum number of DHCP relay clients:
x.x.x.x
xxx
show interface
show statistics
Refer to Chapter 5,
show alarms
show syslog
show log #
Refer to Chapter 6,
Monitoring the DSL Router.
Diagnostics and Troubleshooting.
A-16
6371-A2-GB20-10August 2000
Page 67

Configuration Defaults & Command Line Shortcuts
Configuration Default Settings
All configuration options and factory default settings are listed alphabetically in
Table B-1, Default Configuration Settings. Refer to Table B-2, Command Line
Shortcuts, for abbreviated command line input.
Table B-1. Default Configuration Settings (1 of 2)
B
Configuration Option
1483 encap LLC
ARP cache entries purged
ARP timeout for complete entries 20 minutes
ARP timeout for incomplete entries 5 seconds
authen fail (trap) disabled
ccn (trap) disabled
console access locally enabled
devfail (trap) disabled
dsl1 interface IP address (DSL) purged
DHCP relay disabled
DHCP relay address assignment purged
DHCP server disabled
DHCP server address assignment purged
DHCP server max-lease-time 4320 minutes
DHCP server min-lease-time 120 minutes
DHCP server name assignment purged
Factory Default Setting
6371-A2-GB20-10
DHCP server nameserver assignment purged
DHCP server router assignment purged
August 2000
B-1
Page 68

Configuration Defaults & Command Line Shortcuts
Table B-1. Default Configuration Settings (2 of 2)
Configuration Option Factory Default Setting
Ethernet frame DIX
eth1 interface IP address (Ethernet) purged
IP multicast disabled
IP processing enabled
link up (trap) disabled
link down (trap) disabled
login-ID paradyne
NAT disabled
NAT basic static IP address mappings purged
NAT IP address purged
NAT NAPT static port mappings purged
NAT timeout 20 minutes
password abc123
ping data size 64 bytes
ping time-out 10 seconds
proxy ARP disabled
selftest (trap) disabled
system identity string customer
syslog IP address purged
syslog level norm
syslog messages purged
syslog port 514
syslog status disabled
test start (trap) disabled
test stop (trap) disabled
traceroute data size 64 bytes
traceroute time-out 10 seconds
traceroute max number of hops 8
warmstart (trap) disabled
B-2
6371-A2-GB20-10August 2000
Page 69

Command Line Input Shortcuts
Text in bold is the minimum input for each command line entry.
Table B-2. Command Line Input Shortcuts (1 of 3)
1483encap [llc | vc]
admin {disable | enable}
arp create <ip–addr> <mac–addr>
arp delete <ip–addr>
arp timeout complete [<time>]
arp timeout incomplete [<time>]
arp purge
autologout {disable | enable}
configure {factory | terminal}
Configuration Defaults & Command Line Shortcuts
console {disable | enable}
clear statistics [dsl1 | eth1 | ip]
delete {dsl1[:ifn] | eth1[:ifn]}
dhcp relay {disable | enable}
dhcp relay address <ip–addr>
dhcp server {disable | enable}
dhcp server address <lower–ip> <upper–ip> [<ip–mask>]
dhcp server leasetime <min–time> <max–time>
dhcp server name <name>
dhcp server nameserver <ip–addr>
dhcp server router <ip–addr>
exit
frame [dix | 802.3]
help
ifn address {dsl1[:ifn] | eth1[:ifn]} <ip–addr> <ip–mask> [primary]
6371-A2-GB20-10
ifn address dsl1 unnumbered
ifn {dsl1[:ifn] | eth1[:ifn]} primary
ip multicast {disable | enable}
ip processing {disable | enable}
ip route create <dest–ip> <dest–mask> <next–hop–ip>
August 2000
B-3
Page 70

Configuration Defaults & Command Line Shortcuts
Table B-2. Command Line Input Shortcuts (2 of 3)
ip route create <dest–ip> <dest–mask> remote
ip route create upstream eth1[:ifn] <next–hop–ip>
ip route delete <dest–ip> <dest mask>
ip route delete upstream eth1[:ifn]
ip route purge
list [config]
logout
name <name>
nat basic address <ip–addr> [<ip–mask>]
nat basic delete <private–ip>
nat basic delete <lower–private–ip> <upper–private–ip>
nat basic enable
nat basic map <public–ip> <private–ip>
nat basic map <lower–public–ip> <lower–private–ip> <upper–private–ip>
nat disable
nat napt address <ip–addr>
nat napt delete {udp | tcp} <port>
nat napt enable
nat napt map {udp | tcp} <server–ip> <port>
nat purge
nat timeout <time>
password {admin | operator} <password>
ping <dest–ip> [mgt | –x <source-ip> ] [–l <bytes>] [–w <time>] [–i {eth1 | dsl1}]
proxy arp {dsl1 | eth1} [disable | enable]
restart
save
show alarms
B-4
show arp [<ip–addr>]
show arp timeout
show config
show console
6371-A2-GB20-10August 2000
Page 71

Configuration Defaults & Command Line Shortcuts
Table B-2. Command Line Input Shortcuts (3 of 3)
show dhcp {relay | server}
show interface {dsl1 | eth1}
show ip route [<ip–addr>]
show log [<number of entries>]
show nat {basic | napt}
show statistics [dsl1 | eth1 | ip]
show syslog
show system
syslog {disable | enable}
syslog ip <ip–addr>
syslog level {emer | err | norm | info | debug}
syslog port <port>
system identity <identity>
traceroute <dest–ip> [–x <src–ip>] [–l <bytes>] [–w <time>] [–h <hops>] [–i {eth1 | dsl1}]
trap {disable | enable}
name of trap
6371-A2-GB20-10
August 2000
B-5
Page 72

Configuration Defaults & Command Line Shortcuts
B-6
6371-A2-GB20-10August 2000
Page 73

Traps & MIBs
SNMP Overview
The Simple Network Management Protocol (SNMP) is an application-level
protocol used in network management to gather information from network
devices. Each DSL router runs an SNMP agent that collects data. The network
management station in the NAP domain can exercise all the management
functions remotely from the Network Operations Center (NOC).
There is no discovery of the DSL router, and it does not appear on the
Management Domain map. SNMP security is configured on the MCC card and all
SNMP requests to the DSL router are authenticated at the MCC. The MCC is the
destination for all traps originated by the DSL router.
C
Traps Overview
See the
Conservative, User’s Guide
Traps inform the NMS of an alert occurring in the system (e.g. threshold
exceeded). Traps are sent at the start and completion of a test or alarm condition.
The MCC is the destination for all traps originated by the DSL router. These traps
are then rebuilt with the trap destination information stored on the MCC and
forwarded to the appropriate trap managers.
Traps are configured via a Telnet session, terminal session, or via SNMP, and are
based on community names. Traps are included in the MIB II, Entity and Hotwire
Enterprise MIB definitions. MIBs can be accessed through the Paradyne Web site
at www.paradyne.com. Select
The DSL system can send traps to three IP addressable destinations per
community (for a total of 12 destinations).
Hotwire Management Communications Controller (MCC) Card, IP
for more information on SNMP.
NOTE:
There are several SNMP Sets that result in resetting the DSL router. When
this happens, the NMS that sent the Set command may not receive a
response from the DSL router and will time out. This is not an error.
Technical Support
→
MIBS.
6371-A2-GB20-10
August 2000
C-1
Page 74

Traps & MIBs
DSL Router Traps
The table below lists the traps supported by the DSL router. All traps are defined
with a severity of Critical, Major, Minor, Warning, or Normal. By default, all traps
are initially disabled.
Table C-1. DSL Router Traps
T rap Event(Trap #)
authenticationFailure Minor The authenticationFailure trap
cCN(7) Warning The configuration has changed
deviceFailure(2) Major An internal device failure has
devSelfTestFailure(1) Minor A hardware failure of the unit
diagApplTestStart(2) Normal At least one test has been
Severity Description MIB Variable Binding*
signifies an event where access
has been attempted and failed.
There are several conditions
that can cause an
Authentication Failure trap, such
as three failed attempts to login.
via the user interface or an
SNMP Manager. The trap is
sent immediately , providing
there has been no CCN trap for
30 minutes. This suppresses the
sending of numerous traps
when multiple changes are
made in a short period of time.
been detected by the operating
software for the DSL router.
was detected as part of the
unit’s selftest. This trap is
generated after the unit has
completed initialization.
started on an interface; e.g.,
Ping, TraceRoute.
hot_sys.mib
(Hotwire System
MIB)
hot_sys.mib
(Hotwire System
MIB)
hot_sys.mib
(Hotwire System
MIB)
hot_xdsl.mib
(Hotwire xDSL
interface)
hot_xdsl.mib
(Hotwire xDSL
interface)
IfIndex (RFC 1573)
IfIndex (RFC 1573)
IfIndex (RFC 1573)
devFailureStatus
(pdn_HealthAndStatus)
IfIndex (RFC 1573)
devSelfTestResults
(pdn_HealthAndStatus)
IfIndex (RFC 1573)
applTestID
applTestType
diagApplTestStop(102) Normal This indicates that a test has
completed on an interface.
LinkDown(3) Normal Informational. IfIndex
LinkUp(4) Normal Informational. ifIndex
WarmStart Normal The Warm Start trap signifies
that the unit has just
re-initialized itself. This trap is
sent after the unit has been
reset (either with a reset
command or the result of a
power disruption).
* All traps have the Super Overloaded ifIndex as a variable-binding (as a minimum).
hot_xdsl.mib
(Hotwire xDSL
interface)
(RFC 1573)
(RFC 1213)
MIB II
(RFC 1213)
C-2
IfIndex (RFC 1573)
applTestId (pdn_diag)
applTestType (pdn_diag)
applTestStatus
IfIndex (RFC 1573)
IfIndex (RFC 1573)
IfIndex (RFC 1573)
6371-A2-GB20-10August 2000
Page 75

MIBs Overview
Standard MIBs
Traps & MIBs
The Hotwire DSL system supports standard as well as Paradyne Enterprise
MIBs. Various configuration, status, and statistical data within the SNMP agent is
accessible from the NMS. The content of an SNMP agent’s MIBs is defined by
various Internet Request for Comments (RFC) documents.
The following sections provide brief descriptions about supported MIBs.
Complete, up-to-date details about the content of all DSL MIBs are available on
the Paradyne Web site at www.paradyne.com. Select
MIBs.
Standard MIBs supported consist of the following:
H RFC 1213: MIB II
H RFC 1573: Evolution of the Interfaces Group
H RFC 2096: IP Forwarding Table MIB
Technical Support
→
MIB II (RFC 1213)
H RFC 2665: Ethernet-Like MIB
The objects defined by MIB II (RFC 1213) are organized into ten groups:
H System Group – fully supported. Refer to
H Interfaces Group – refer to
Interfaces Table (RFC 1573)
H Address Translation Group – not supported.
H IP Group – refer to
(RFC 2096)
H ICMP Group – fully supported.
H TCP Group – fully supported.
H UDP Group – fully supported.
H EGP Group – not supported.
H Transmission Group – refer to
H SNMP Group – refer to
IP Group (RFC 1213)
Interfaces Group (RFC 1573)
Transmission Group.
SNMP Group.
System Group
and
IP CIDR Route Group
and
Extension to
System Group
6371-A2-GB20-10
System Group objects are fully supported by the DSL router, as shown in
Table C-2.
August 2000
C-3
Page 76

Traps & MIBs
NOTE:
The System Name, System Contact, and System Location objects
can be configured via the port card (A-F). V alues will display in Monitoring
(B-E). However, the DSL router uses and displays the SNMP information set
via the System Group.
Table C-2. System Group Objects
Object
sysDescr
(system 1)
sysObjectID
(system 2)
sysContact
(system 4)
Description Setting/Contents
Provides a full name and version
identification for the Hotwire system’s
hardware and software.
Identifies the network management
subsystem for the DSL router.
Provides the contact information for
the person managing the DSL router.
The object is set to display a string in the following format:
PARADYNE Hotwire DSL; Model:
Release:
ssssssssssss
yy.yy.yy;
; Boot:
Model starts with the 4-digit model number:
H 6301 – IDSL router
H 6302 – IDSL 4-port router
H 6341 – SDSL router
H 6342 – SDSL 4-port router
H 6371 – RADSL router
OIDs (Object Identifiers):
H 1.3.6.1.4.1.1795.1.14.9.9.35 – 6301 IDSL router
H 1.3.6.1.4.1.1795.1.14.9.9.36 – 6302 IDSL 4-port router
H 1.3.6.1.4.1.1795.1.14.9.9.25 – 6341 SDSL router
H 1.3.6.1.4.1.1795.1.14.9.9.26 – 6342 SDSL 4-port router
H 1.3.6.1.4.1.1795.1.14.9.9.29 – 6371 RADSL router
ASCII character string (32 characters), as set by the user:
H badValue(3) – Field length exceeded.
H/W Revision:
bb.bb.bb;
2nd Boot:
xxxx-xx-xxx
zzz;
Serial Number:
xx.xx.xx;
; S/W
DSP:
xxx
sysName
(system 5)
sysLocation
(system 6)
sysServices
(system 7)
C-4
Provides a contact name for the DSL
router.
Provides the physical location for the
DSL router.
The DSL router provides routing and
host application services; i.e., Ping
and TraceRoute.
ASCII character string (32 characters), as set by the user:
H badValue(3) – Field length exceeded.
ASCII character string (32 characters), as set by the user:
H badValue(3) – Field length exceeded.
H physical(1) – Layer 1 functionality for DSL and Ethernet
interfaces.
H datalink/subnetwork(2) – Layer 2 functionality for:
– DSL interface and
– Ethernet interface (LLC)
H internet(4) – Layer 3 functionality (IP) for all
management links.
H end-to-end(8) – Layer 4 functionality (TCP) for all
management links.
H application(64) – Layer 7 functionality (TCP) for all
management links.
Object is set to 4+8+64 (76).
6371-A2-GB20-10August 2000
Page 77

Interfaces Group (RFC 1573)
The evolution of the Interfaces Group of MIB II (RFC 1573 converted to
SNMP v1) consists of an object indicating the number of interfaces supported by
the DSL router and an interface table containing an entry for each interface.
Refer to Table C-3 for the objects supported for the DSL and Ethernet interfaces.
The Interface Stack Group table does not apply, but is required for MIB
compliance. One row will be displayed with ifStackHigherLayer=0 and
ifStackLowerLayer=0. The ifStackStatus=2 (enumerated value for notInService)
and is read-only. The Interface Test Table and the Generic Receive Address
Table are not supported.
Table C-3. Interfaces Group Objects (1 of 2)
Traps & MIBs
Object
ifNumber
(interfaces 1)
ifIndex
(ifEntry 1)
ifDescr
(ifEntry 2)
ifType
(ifEntry 3)
ifMtu
(ifEntry 4)
Description Setting/Contents
Supported as specified in
the Evolution MIB.
Provides the index into the
interface table (ifTable)
and to other MIB tables.
ifIndex calculation:
(Slot # * 1000 + local port)
* 1000 + remote ifIndex
Supplies text for each
interface:
H DSL interface
H Ethernet interface
Identifies the interface type
based on the physical/link
protocol(s).
Identifies the largest
datagram that can be sent
or received on an
interface.
Specifies the number of interfaces for this unit in the ifTable.
Remote ifIndex (DSL router ifIndex) and Interface:
H 0 – DSL router.
H 1 – Ethernet interface.
H 2 – DSL network interface.
H noSuchName – Unsupported index entered.
Text Strings for each interface:
H “DSL Interface; Card Type (IDSL, RADSL, SDSL); S/W Release:
yy.yy.yy
H “Ethernet Interface; Card Type (frame format of Type II or SNAP);
S/W Release:
Supported values:
H radsl(95) – Used for RADSL.
H sdsl(96) – Used for SDSL.
H iso88023Csmacd(6) – Used for Ethernet.
H idsl(154) – Used for IDSL.
Integer.
; H/W Release:
yy.yy.yy
zzz; [CCA part number]”
; H/W Release:
zzz; [CCA part number]”
”
ifSpeed
(ifEntry 5)
ifPhysAddress
(ifEntry 6)
ifAdminStatus
(ifEntry 7)
6371-A2-GB20-10
Provides the interface’s
current bandwidth in bits
per second (bps).
Identifies the physical
address for the interface.
Supported as read-only . H up(1) – Always displays as up.
H DSL interface – The downstream rate of the DSL interface once
trained, or zero if not trained.
H Ethernet interface – 10240000 bps (for 10 MB operation) or
102400000 (for 100 MB operation).
H DSL interface – The MAC address when operating in 1483
Bridged mode.
H Ethernet interface – The MAC address.
August 2000
C-5
Page 78

Traps & MIBs
Table C-3. Interfaces Group Objects (2 of 2)
Object Setting/ContentsDescription
ifOperStatus
(ifEntry 8)
ifLastChange
(ifEntry 9)
ifInOctets
(ifEntry 10)
ifInUcastPkts
(ifEntry 11)
ifInDiscards
(ifEntry 13)
ifInErrors
(ifEntry 14)
ifInUnknown
Protos
(ifEntry 15)
Specifies the current
operational state of the
interface.
Indicates the amount of
time the interface has
been up and running.
Input Counter objects that
collect input statistics on
data received by the
interface.
H DSL interface:
– up(1) – DSL link is established.
– down(2) – DSL link is not established.
H Ethernet interface:
– up(1) – There is a physical connection.
– down(2) – There is no physical connection.
Contains the value of sysUpTime object at the time the interface
entered its current operational state of Up or Down. If the current
state was entered prior to the last reinitialization of the local
management subsytem, then this object contains a value of 0 (zero).
Integer.
ifOutOctets
(ifEntry 16)
ifOutUcastPkts
(ifEntry 17)
ifOutDiscards
(ifEntry 19)
ifOutErrors
(ifEntry 20)
Output Counter objects
that collect output statistics
on data received by the
interface.
Integer.
C-6
6371-A2-GB20-10August 2000
Page 79

Extension to Interfaces Table (RFC 1573)
This extension contains additional objects for the Interface table. Table C-4 shows
the objects supported.
Table C-4. Extension to Interfaces Table
Traps & MIBs
Object
ifName
(ifXEntry 1)
ifHighSpeed
(ifXEntry 15)
ifConnector
Present
(ifXEntry 17)
Description Setting/Contents
Provides the name of the
interface.
Displays the downstream
speed for the DSL or
Ethernet interface in Mbps.
Indicates whether there is
a physical connector for
the interface.
IP Group (RFC 1213)
Specifies the interface name:
H dsl1 – DSL interface.
H eth1 – Ethernet interface.
Depending on the current mode of operation, displays the speed in
1 million bits per second (Mbps) of the Ethernet interface as:
H 10 Mbps
H 100 Mbps
Due to the speed displaying as Mbps, the DSL interface downstream
speed displays as 0 (zero).
The value for all interfaces is always:
H true(1)
The Internet Protocol Group objects are supported by the unit for all data paths
that are currently configured to carry IP data to/from the unit. All of the objects in
the IP Group, except for the IP Address Translation table, are fully supported.
Table C-5 provides clarification for objects contained in the IP Group.
Table C-5. IP Group Objects (1 of 2)
Object
ipForwarding
(ip 1)
ipDefaultTTL
(ip 2)
ipAddrTable
(ip 20)
6371-A2-GB20-10
Description Setting/Contents
Specifies whether the unit is acting
as an IP gateway for forwarding of
datagram received by , but not
addressed to, the DSL router.
TTL = Time To Live. Minimum value – 15. Maximum value – 255.
The address table. The device sets the object ipAdEntReasmMaxSixe to
The value is read-only and always displays: (1)
H 64 – Default.
16384. Supported as read-only.
August 2000
C-7
Page 80

Traps & MIBs
Table C-5. IP Group Objects (2 of 2)
Object Setting/ContentsDescription
ipNetToMediaTable
(ip 22)
ipNetToMediaType
This table allows access to
contents of the ARP cache.
Supported for ARP table entries. H other(1) – Entry is incomplete.
(ipNetToMediaEntry
4)
IP CIDR Route Group (RFC 2096)
This MIB obsoletes and replaces IP Group from MIB II. The IP CIDR Route
Group objects are supported for all data paths currently configured to carry IP
data to or from the device (i.e., the DSL and Ethernet interfaces). All of the
objects in this group are fully supported except as noted in Table C-6. The IP
Forwarding Group is not supported.
Table C-6. IP CIDR Route Group Objects (1 of 2)
Object
Description Setting/Contents
This table is implemented with read/write access.
H invalid(2) – Invalidates corresponding entry in the
ipNetToMediaTable.
H dynamic(3) – Results in a response with a badValue
error status. Dynamic ARP table entries will still
display with the correct dynamic (3) value, but a Set
is not allowed.
H static(4)
ipCidrRouteTable
(ipForward 4)
ipCidrRouteDest
(ipCidrRouteEntry 1)
ipCidrRouteMask
(ipCidrRouteEntry 2)
ipCidrRouteTos
(ipCidrRouteEntry 3)
ipCidrRouteNextHop
(ipCidrRouteEntry 4)
ipCidrRouteIfIndex
(ipCidrRouteEntry 5)
Replaces the ipRouteTable in
MIB II. It adds knowledge of
autonomous system of the next
hop, multiple next hops, policy
routing, and classless
inter-domain routing.
Serves as an index to the
routing table.
This is the mask that is logicalANDed with the destination
address.
The policy specifier is the IP
Table of the Service field.
The next hop route IP address
for remote routes.
Corresponds to the IfIndex
value.
This is a read/write table. If an interface route is deleted
but not the corresponding upstream route (such as with
DHCP relay), an SNMP Get for this object will still show
a table entry for the address and mask assigned to the
interface.
H reject(2) – Value for route type and the
ipCidrRouteDownstreamValid will be false.
This object cannot take a Multicast (Class D) address
value.
This is the mask before being compared to the value in
the ipCidrRouteDest field.
This object will always be 0 (zero).
If there is no router, the value is 0.0.0.0.
Identifies the local interface through which the next hop
of the route should be reached.
C-8
6371-A2-GB20-10August 2000
Page 81

Table C-6. IP CIDR Route Group Objects (2 of 2)
Object Setting/ContentsDescription
Traps & MIBs
ipCidrRouteType
(ipCidrRouteEntry 6)
ipCidrRouteProto
(ipCidrRouteEntry 7)
ipCidrRouteAge
(ipCidrRouteEntry 8)
ipCidrRouteInfo
(ipCidrRouteEntry 9)
ipCidrRouteNextHopAS
(ipCidrRouteEntry 10)
This is a read-only object. H other(1) – Not specified by this MIB (used as
Corresponds to routing
mechanisms via which this
route was learned. Inclusion of
values for gateway routing
protocols does not imply that
the host supports these
protocols.
Reflects the number of
seconds since this route was
last updated or otherwise
determined to be correct.
This object refers to the
particular routing protocol
responsible for this route.
Next hop route. Always set to a value of 0 (zero).
interface route).
H reject(2) – Entry not valid for downstream routing.
H local(3) – Route to a directly connected local host or
service network.
H remote(4) – Route to a nonlocal host or service
network.
This is a read-only object.
H other(1) – The entry is a host route set up by DHCP
or loopback route.
H local(2) – Local interface.
H netmgmt(3) – Static route.
This is a read-only object.
When displayed, a value of 0 (zero) represents a route
that will be retained permanently .
If this information is not present (determined by
ipCidrRouteProto value), the value is set to the
OBJECT IDENTIFIER (00).
ipCidrRouteMetric1 –
ipCidrRouteMetric5
(ipCidrRouteEntry 1 1 –
ipCidrRouteEntry 15)
ipCidrRouteStatus
(ipCidrRouteEntry 16)
Transmission Group
For future use. Only value accepted is -1.
Used to create or delete rows
in a table.
—
The objects in the Transmission Group are supported for the Ethernet Interface.
These objects are not defined within MIB II but rather through other
Internet-standard MIB definitions. The objects in the transmission group are
extended by RFC 2665 MIB definitions. The object dot3
(Transmission group 7)
supported on the Ethernet Interface.
is
6371-A2-GB20-10
August 2000
C-9
Page 82

Traps & MIBs
SNMP Group
The SNMP Group objects that apply to a management agent are fully supported.
The following objects apply only to an NMS and return a value of 0 (zero) if
accessed:
H snmpInTooBigs
H snmpInNoSuchNames
H snmpInBadValues
H snmpInReadOnlys
H snmpInGenErrs
H snmpInGetResponses
H snmpInTraps
H snmpOutGetRequests
H snmpOutGetNexts
H snmpOutSetRequests
Ethernet-Like MIB (RFC 2665)
Only the Ethernet-like statistics group is supported, with the following objects:
H dot3StatsIndex
H dot3StatsAlignmentErrors
(snmp 8)
(snmp 9)
(snmp 10)
(snmp 11)
(snmp 12)
(snmp 18)
(snmp 19)
(snmp 25)
(snmp 26)
(snmp 27)
(dot3StatsEntry 1)
(dot3StatsEntry 2)
H dot3StatsFCSErrors
H dot3StatsSingleCollisionFrames
H dot3StatsMultipleCollisionFrames
H dot3StatsSQETestErrors
H dot3StatsDeferredTransmissions
H dot3StatsLateCollisions
H dot3StatsExcessiveCollisions
H dot3StatsInternalMacTransmitErrors
H dot3StatsCarrierSenseErrors (
H dot3StatsFrameTooLongs
H dot3StatsInternalMacReceiverErrors
H dot3StatsSymbolErrors
H dot3StatsDuplexStatus
(dot3StatsEntry 3)
(dot3StatsEntry 4)
(dot3StatsEntry 5)
(dot3StatsEntry 6)
(dot3StatsEntry 7
(dot3StatsEntry 8)
(dot3StatsEntry 9)
dot3StatsEntry 1 1)
(dot3StatsEntry 13)
(dot3StatsEntry 18)
(dot3StatsEntry 19)
)
(dot3StatsEntry 10)
(dot3StatsEntry 16)
– always 0 (zero)
– always 0 (zero)
– always 0 (zero)
C-10
6371-A2-GB20-10August 2000
Page 83

Paradyne Enterprise MIBs
The following Paradyne Enterprise MIB Objects are supported by the unit:
Traps & MIBs
Device Control MIB
Device Control MIB
H
Device Diagnostics MIB
H
H
Health and Status MIB
Configuration MIB
H
Interface Configuration MIB
H
H
ARP MIB
NAT MIB
H
H
DHCP MIB
DSL Endpoint MIB
H
SYSLOG MIB
H
H
Interface Configuration MIB
(pdn_Arp.mib)
(pdn_NAT.mib)
(pdn_dhcp.mib)
(pdn_Control.mib)
(pdn_diag.mib)
(pdn_HealthAndStatus.mib)
(pdn_Config.mib)
(pdn_inet.mib)
(DslEndpoint.mib )
(pdn_syslog.mib)
(pdn_IfExtConfig.mib)
Objects supported by the Device Control MIB, pdn-Control.mib, include the
Device Control Group (fully supported) and the Device Control Download group.
Table C-7. Device Control Table Objects
Object
devHWControl Reset
(
control 1)
devControlDownLoadIndex
(devControlDownloadEntry 1)
devControlDownLoadRelease
(devControlDownLoadEntry 2)
devControlDownLoadOperStatus
(devControlDownLoadEntry 3)
devControlDownLoadAdminStatus
(devControlDownLoadEntry 4)
Description Setting/Contents
Initiates a hardware
power-on reset.
Represents the firmware
bank.
Indicates the software
release for the bank.
Indicates whether the
downloaded entry contains
a valid or invalid software
release.
Indicates whether the
downloaded entry is active
or inactive.
V alue from this object:
H noOp(1)
H Reset(2) – Resets the DSL router with no
warning.
H bank (1)
H bank (2)
Numeric.
H (1) – Valid software release.
H (2) – Invalid software release. Displays if
devControlDownLoadRelease is blank.
H Active(1)
H Inactive(2)
Supported as read-only .
6371-A2-GB20-10
August 2000
C-11
Page 84

Traps & MIBs
Device Diagnostics MIB
Objects supported by the Device Diagnostics MIB, pdn_diag.mib, include the
Application Test Input Group (Ping and TraceRoute) and Test Traps, providing an
NMS a trigger for a diagnostic test.
To start a test from NMS, you must obtain the Test ID by performing a Get. This
Test ID is then used as the index when setting the parameters via objects in the
Application Test Table. Refer to the
Table C-8. Application Test Group Objects (1 of 3)
applNewTestId object in Table C-8.
Object
applMaxNumberOfTests
(applTest 1)
applCurrentNumberOfTests
(applTest 2)
applStopAllTests
(
applTest 3)
applNewTestId
(applTest 4)
applTestId
(testStatusEntry 1)
applTestType
(testStatusEntry 2)
Description Setting/Contents
The number of application-based
tests that can be started on the
device.
The number of application-based
tests that are currently running on
the device.
Initiates the clearing of all
application-based tests.
To start a test from NMS,
complete a Get on this object to
obtain the test ID. Note that this
invalidates any existing test
information for Ping, TraceRoute,
and Test Status tables.
Contains identifiers that allow
NMS to find the most recent test.
Indicates the test type assigned
to this object.
The DSL router only supports one test.
The DSL router only supports one test at a
time.
H noOp – No operation.
H Stop – All tests are stopped and current
test results remain available.
H StopAndClear – All tests are stopped
and all test results are cleared.
H
nnn –
Existing unused test ID.
H 0 (zero) – A test ID cannot be assigned
at this time.
Contains applNewTestID after Get.
H 1.3.6.4.1795.1.14.5.1.3 – Ping Test
Type.
H 1.3.6.4.1795.1.14.5.1.4 – TraceRoute
Test Type.
applTestStatus
(testStatusEntry 3)
applTestErrorCode
(testStatusEntry 4)
C-12
Indicates the test status. H none(1) – No active test.
H inProgress(2) – Active test.
H success(3) – Test completed.
H failed(4) – Test failed.
H abort(5) – Test aborted.
Contains additional test details,
such as error codes.
Test Error codes:
H none – No errors.
H timeout
H icmpError
H systemError
6371-A2-GB20-10August 2000
Page 85

Table C-8. Application Test Group Objects (2 of 3)
Object Setting/ContentsDescription
Traps & MIBs
applTestOwner
(testStatusEntry 5)
applTestRowStatus
(testStatusEntry 6)
applPingTestId
(applpingTestEntry 1)
applPingTestIpAddress
(applpingTestEntry 2)
applPingTestSourceIpAddress
(applpingTestEntry 3)
applPingTestPacketSize
(applpingTestEntry 4)
applPingTestTimeout
(applpingTestEntry 5)
applPingTestMaxPings
(applpingTestEntry 6)
applPingTestPktsSent
(applpingTestEntry 7)
Identifies who started the test. 1 – 40 characters.
Use to create a new row or
delete an existing row.
Contains identifier that allows the
Network Manager to view the
results of Ping and TraceRoute
tests.
Identifies IP address to be
pinged.
Identifies the source IP address. Set source IP address.
Specifies Ping packet size.
Range includes 28 bytes of
header information.
Number of seconds between
echo request attempts.
Maximum number of Pings. H 1 – Only supported value.
Number of packets sent. H 1 – Only supported value.
Set to active(1) to create a new row.
Device supports only one at a time.
Set destination IP address.
H 28 – 15028 – Range.
H 64 – Default.
H 10 – Default.
applPingTestPktsRecv
(applpingTestEntry 8)
applPingTestMinTime
(applpingTestEntry 9)
applPingTestMaxTime
(applpingTestEntry 10)
applPingTestAvgTime
(applpingTestEntry 11)
applPingTestDomain
(applpingTestEntry 12)
applPingTestIfIndex
(applpingTestEntry 13)
applTracerouteTestId
(traceroute 1)
applTracerouteIpAddress
(traceroute 2)
applTracerouteSourceIpAddress
(traceroute 3)
Number of packets received
without error.
Minimum round trip time. H 0 – Not supported.
Maximum round trip time. H 0 – Not supported.
Average round trip time. H 0 – Not supported.
Specifies the destination IP
address’s domain as
management or service. If the
source IP address is entered,
mgmt(2) is not valid.
Specifies the interface over which
the Ping will take place.
Unique TraceRoute test ID. Contains applNewTestID after Get.
Destination IP address for
TraceRoute test.
Identifies the source IP address. Set source IP address.
H 0
H 1
H mgmt(2) – Management domain.
H service(3) – Service domain.
Defaults to the interface based upon
current routing.
Set destination IP address.
6371-A2-GB20-10
August 2000
C-13
Page 86

Traps & MIBs
Table C-8. Application Test Group Objects (3 of 3)
Object Setting/ContentsDescription
applTraceroutePacketSize
(traceroute 4)
applTracerouteTimeOut
(traceroute 5)
applTracerouteMaxHops
(traceroute 6)
applTracerouteDomain
(traceroute 7)
applTracerouteIfIndex
(traceroute 8)
applTracerouteTestOwner
(traceroute 9)
applTracerouteTestId
(applTracerouteResultsEntry 1)
applTracerouteHopCount
(applTracerouteResultsEntry 2)
applTracerouteResultsIpAddr
(applTracerouteResultsEntry 3)
applTracerouteResultsHopCount
(applTracerouteResultsEntry 4)
Specifies TraceRoute packet
size. Range + 28 bytes of header
information.
Timeout value in seconds
H 28 — 15028 – Range.
H 64 – Default.
H 10 – Default.
between echo request attempts.
Maximum number of hops to be
H 8 – Default.
tested.
Specifies the destination IP
address’s service domain.
Specifies the route for the
TraceRoute test.
H mgmt(2) – Management Domain.
H service(3) – Service Domain. Default.
If the target interface is not specified, the
default will display the calculated ifIndex.
Identifies who started the test. 1 – 40 characters.
Contains the results of a
Supports only one test per device.
TraceRoute test.
Number of hops to reach the
—
gateway .
IP address of the gateway . —
Number of hops to reach the
—
gateway .
applTracerouteResultsPacketSize
(applTracerouteResultsEntry 5)
applTracerouteResultsProbe1
(appTracerouteResultsEntry 6)
applTracerouteResultsProbe2
(applTracerouteResultsEntry 7)
applTracerouteResultsProbe3
(applTracerouteResultsEntry 8)
diagTestTrapEnable
(configure 1)
Specifies the data size of the
packets (in bytes) sent during the
TraceRoute test.
Displays roundtrip time in 100 ms
intervals of the first probe sent to
the gateway .
Displays roundtrip time in 100 ms
intervals of the second probe
sent to the gateway .
Displays roundtrip time in 100 ms
intervals of the third probe sent to
the gateway .
Use to enable or disable
diagApplTestStart and
diagApplTestStop traps.
—
H 0 – Probe has timed out.
H 0 – Probe has timed out.
H 0 – Probe has timed out.
Bit Sum.
H 1 – Test Start.
H 2 – Test Over.
C-14
6371-A2-GB20-10August 2000
Page 87

Health and Status MIB
Objects supported by the Health and Status MIB, pdn_HealthAndStatus.mib,
include the following groups:
H Device Health and Status
H Device Selftest Status
H Device Abort Status
H Device Failure Status
H Traps
Table C-9. Device Status Group Objects Table
Traps & MIBs
Object
devHealthandStatus
(devStatus1)
devSelfTestResults
(devStatus 2)
devAbortStatus
(devStatus 3)
Description Setting/Contents
This object displays alarm
messages if any alarms are
generated by the device.
This object corresponds to
self-test results. This value is
used as a binding for
devSelfTestFailure Trap.
This object is used to retrieve
the latest abort status that is
stored in the agent.
Possible alarms are:
H Alarm: Management Address Conflict.
H Alarm: Failed Selftest.
H Alarm: System Error.
H No alarm is set.
H P – Passed selftest.
H F – Failed selftest.
Possible abort codes are:
H INVALID_INTR
H INT_TIMEOUT
H O_YAMOS_FAILURE
H INIT_NOBUFS
H SYSCALL_FAILED
H G_NO_BUF
H G_BAD_CONFIG
H G_NO_ABORT
devFailureStatus
(devStatus 4)
devStatusTrapEnable
(devStatus 8)
devStatusTestFailure Signifies that the sending
deviceFailure Signifies that the sending
6371-A2-GB20-10
This object is used to retrieve
the latest failure status.
Allows user to enable or
disable the selftest failure
indication trap and the device
failure indication trap
individually .
protocol’s device failed selftest.
protocol’s device failed.
This value is used as a binding for the deviceFailure trap.
Bit Sum.
H 1 – devSelfTest failure.
H 2 – device failure.
The variable binding for this trap is the
devSelfTestResults object of the Health and Status MIB.
The reason for the failure was not selftest.
August 2000
C-15
Page 88

Traps & MIBs
Configuration MIB
The supported groups used with the DSL Configuration MIB, pdn_Config.mib,
are:
H Device Configuration Copy Group
H Trap Configuration Group
H Paradyne Device Configuration Time Group
H Traps
Table C-10. Device Configuration Copy Group Objects Table
Object
devConfigAreaCopy
(devConfigArea1)
devConfigTrapEnable
(devConfigTrap1)
devConfigTimeOfDay
(devConfigTime 1)
Description Setting/Contents
Use to configure the current configuration to the
factory defaults settings.
NOTE: ALL current configuration input is
purged when the DSL router is
resets as a result of this command.
Data purged includes:
– Interface IP addresses
– IP route table entries
– ARP cache entries
– NAT entries
– DHCP server entries
This object determines which trap types are
sent, represented by a bit map as a sum.
Allows multiple trap types to be enabled or
disabled simultaneously .
Displays the current time. —
H noOp (1) – always reads as this
value and represents:
factory1-to-active(8)
Bit positions:
H 1 – warmStart trap
H 2 – authenticationFailure trap
H 4 – enterpriseSpecific traps
H 8 – LinkUp trap
H 16 – LinkDown trap
cCN(7) Signifies a configuration change or a software
upgrade.
cCNTrapEnable
(router 28)
Use to enable or disable the configuration
change trap.
C-16
H 7 – Warning trap
H 1 – Disable trap
H 2 – Enable trap
6371-A2-GB20-10August 2000
Page 89

Interface Configuration MIB
The Paradyne proprietary Interface Configuration group, pdn_inet.mib, is
supported. Refer to Table C-11 for additional details.
Table C-11. Interface Configuration Group Objects Table
Traps & MIBs
Object
pdnInetIpAddress
(pdnInetIpAddressTableEntry 1)
pdnInetIpSubnetMask
(pdnInetIpAddressTableEntry 2)
pdnInetIpAddressType
(pdnInetIpAddressTableEntry 3)
pdnInetIpRowStatus
(pdnInetIpAddressTableEntry 4)
ARP MIB
The objects from the proxy ARP MIB group, pdn_Arp.mib, are:
H pdnNetToMediaClearAllArp
H pdnNetToMediaProxyArpTable
Description Setting/Contents
Identifies the interface IP
address.
Identifies the interface subnet
mask.
Use to view the address type
for an interface. Supported as
read-only.
Use to add/delete/modify rows
in this table.
(pdnNetToMediaConfig 2)
H Interface IP address or
H 0.0.0.0 – Unnumbered interface
H P – Passed selftest
H F – Failed selftest
H primary
H secondary
When used to add a new interface entry , the
objects specifying the table entry must be
included in the same Set PDU.
– Setting this object to
clear removes all entries from the ARP table and is equivalent to the
command: arp purge
NAT MIB
6371-A2-GB20-10
The objects in the Network Address Translation MIB group, pdn_NAT.mib, are
fully supported. The groups are:
H Network Address Translation Group – Facilitates the creation and
configuration of NAT entries. The DSL router accepts any valid public IP
address (up to 256 addresses) and subnet mask for basic NAT operation.
H NAPT Mapping Group – Facilitates the creation and configuration of NAPT
mappings. The DSL router accepts any single, public IP address for NAPT
operation. The subnet mask 255.255.255.255 is used when the NAPT
IP address configuration information is viewed.
H NAT Basic Mapping Group – Facilitates the creation and configuration of
Basic NA T mappings.
August 2000
C-17
Page 90

Traps & MIBs
DHCP MIB
The supported objects in the DHCP Server/Relay MIB, pdn_dhcp.mib, facilitates
the creation and configuration of DHCP server table entries. The following groups
are supported:
H DHCP Server Configuration Group – Fully supported. One object is
clarified below:
— dhcpServerRouterIpAddr
router IP address used by the DHCP server. This address is provided to
clients in the DHCP reply message from the DHCP server. If this value is
not set, the accepted value is 0.0.0.0.
H DHCP Binding Group – Facilitates the display of DHCP bindings. This group
is fully supported.
H DHCP Relay Group – Facilitates the display of DHCP Relay. This group is
fully supported. The following clarifies some of the DHCP Relay objects:
— dhcpRelayIpAddr
DHCP server.
— dhcpRelayEnable
DHCP relay agent.
— dhcpRelayMaxClients
the number of clients allowed to request IP address assignments from
the server.
(xdslDhcpRelayAgent 6)
(xdslDhcpRelayAgent 7)
(dhcpserv 7)
(xdslDhcpRelayAgent 8)
– Enables you to configure the
– This is the IP address of
– Use to enable or disable the
– Enables user to specify
C-18
6371-A2-GB20-10August 2000
Page 91

DSL Endpoint MIB
This DSL Endpoint MIB, pdn_DslEndpoint.mib, facilitates configuration of DSL
multirate products and is fully supported. Objects are clarified in Table C-12.
The groups in this MIB are:
H IP Routing Group – This table is an extension of the ipCidrRoute table (see
IP CIDR Route Group (RFC 2096)
H IP Multicast Group
H IP Processing Group
H Console Group
Table C-12. DSL Endpoint Configuration Group Objects Table
Traps & MIBs
on page C-8.
Object
ipCidrRouteUpstreamNextHop
(IpCidrRouteXEntry 1)
ipCidrRouteDownstreamV alid
(IpCidrRouteXEntry 2)
ipCidrClearAllRoutes
(IpCidrRouteX 2)
ipCidrRouterID
(IpCidrRouteX 3)
pdnlpMulticastEnable
(pdnRouterConfiguration 1)
pdnlpProcessingEnable
(pdnRouterConfiguration 2)
pdnConsoleEnabled
(pdnRouterConfiguration 7)
Description Setting/Contents
Corresponds to the upstream Next Hop
Router address. If the DSL interface is
numbered, each upstream Next Hop Router
address must be in a subnet defined by a
DSL interface IP address and subnet mask.
If false, the row containing it is not valid for
downstream routing.
If set to clear, all IP routes are removed from
the routing table.
Specifies the router ID (primary IP address). Must be equal to a nonzero value
Enables or disables forwarding of IP
multicast packets.
Enables or disables service domain
processing of IP packets.
Enables or disables the console port. H true(1) – Enable.
H Ethernet Interface IP address.
H 0.0.0.0 – No upstream next hop
is identified.
H true
H false
H noOp
H clear
for the interface IP address.
H enable
H disable
This setting is retained across
power cycles.
H false(2) – Disable.
6371-A2-GB20-10
August 2000
C-19
Page 92

Traps & MIBs
SYSLOG MIB
The System Log MIB (SYSLOG), pdn_syslog.mib, is fully supported.
Interface Configuration MIB
The Interface Configuration MIB, pdn_IfExtConfig.mib, is used to configure
interface-related objects and is fully supported. One object is clarified below:
H pdn_IfExtConfigIPRoutedPDUs
the IP-routed PDUs in the LLC SNAP encapsulation or VC-based
Multiplexing encapsulation (RFC1483) in the upstream direction. If neither is
configured, the value none is used.
(pdnIfExtConfigEntry 1)
– You can configure
C-20
6371-A2-GB20-10August 2000
Page 93

DSL Router Terminal Emulation
DSL Router Terminal Emulation
The Command Line Interface is available at the DSL router when the Console
cable is connected to a VT100-compatible terminal or a PC running a terminal
emulation program. Verify the terminal settings:
H Data rate set to 19.2 kbps (19200 bps)
H Character length set to 8
D
H Parity set to None
H Stop bits set to 1
H Flow control set to Off or None
Accessing the List Command Output
Use the list confg command to output command strings needed to restore
the current running configuration. Output from the List Confg command can be
captured to a text file using most terminal emulation programs. Examples of two
VT100-compatible programs are provided.
Once the text file is captured, the DSL router can be placed in configuration
mode. The text file can be fed back to configure the DSL router.
6371-A2-GB20-10
August 2000
D-1
Page 94

DSL Router Terminal Emulation
Terminal Emulation Programs
Examples of configuring two different terminal emulation programs:
H HyperTerminal – playback feature is accessed through its Transfer menu.
H Procomm+ – playback feature is accessed through its Online menu.
" Procedure
To configure the HyperTerminal:
1. Select menu option
2. Select
3. In the Properties dialog, select the Settings tab.
4. Set Emulation to VT100.
5. Select the Terminal Setup button and set to 132 column mode.
6. Select OK to exit Terminal Setup.
7. Select the ASCII Setup button.
8. Select OK to exit ASCII Setup.
9. Select OK to exit Properties.
File → Properties.
— Set Line delay to 50 ms.
— Set Character delay to 2 ms.
Transfer → Send Text File.
" Procedure
To configure Procomm+:
1. Select menu option
2. In the Send File dialog, set the protocol to ASCII.
Online → Send File.
D-2
3. Select the Setup button.
4. Select the Transfer Protocol button (on the left).
5. Select ASCII in the Current Protocol drop-down box.
— Set delay between Character to 2 ms.
— Set delay between Lines to 2 ms.
6. Check and set Use 13 for Line pace character.
7. Check display text.
8. Save the configuration.
6371-A2-GB20-10August 2000
Page 95

Index
Symbols
? for user access, commands available, 2-4
Numbers
6301/6302 IDSL Routers, 1-1
6341/6342 Symmetric DSL Routers, 1-1
6371 rate adaptive DSL Router, 1-1
A
access control, 2-1
address resolution protocol, 3-5
Administrator access, 2-2
alarms inquiry , 6-1
ARP, 3-5
enable proxy , A-7
proxy, 3-5
proxy configuration, 4-5
table, A-7
autologout, 2-6
B
basic NAT, 3-6
configuring, 4-3, A-8
C
clear statistics, 5-4
command line interface, A-1
shortcuts, B-3
command recall, command line interface, A-2
commands available, for access level, 2-4
configuration
commands, A-3
factory default settings, B-1
configure
DSL router, 4-1
terminal, 2-3
console access, 2-2
core router, 3-3
customer, system identity, 2-3
D
daemon for SYSLOG, 6-2
data rates for DSL routers, 1-3
delete, ip route, A-5
destination IP address, 3-9, A-5
device
restart, 6-1
troubleshooting, 6-1
DHCP, 3-7
DHCP relay, configuring, 4-6, A-11
DHCP server, configuring, 4-7, A-10
diagnostics, 6-1
disable, console access, 2-2
discard reasons, for interface statistics, 5-4
DNS, 3-7
downstream router, configuring, 4-8
DSL access system, 1-1
DSL interface, 3-1
configuring, 4-5
statistics, 5-3
DSL router
access, 2-1
configuring, 4-1
terminal emulation, D-1
DSL Sourcebook, 1-4
dsl1
DSL interface, 3-1
DSL interface statistics, 5-2
Dynamic Host Configuration Protocol (DHCP), 3-7
E
enable
Administrator access, 2-2
console access, 2-2
Enterprise MIBs, C-11
eth1
Ethernet interface, 3-2
Ethernet interface statistics, 5-2
Ethernet
frame format, A-3
interface, 3-2
statistics, 5-3
events in SYSLOG, 6-3
exiting the system, 2-5
6371-A2-GB20-10 August 2000
IN-1
Page 96

Index
F
factory defaults, A-3, B-1
filtering IP packets, 3-9
frame, Ethernet format, A-3
FTP and NA T, 3-7
G
glossary, vi
H
help, for current access levels, 2-4
I
ICMP, 3-1, 6-5
identifiers, for interfaces, 3-2
IDSL 6301/6302 routers, 1-1
interfaces
for DSL routers, 3-1
identifiers, 3-2
IP addresses, A-4
status, 5-1
IP addresses, 3-2, A-4
IP filtering, 3-9
IP multicast, of IP packets, A-12
IP options processing, 3-7
IP route purge, A-6
IP routing, 3-4
table, A-5
IP statistics, 5-3
M
MAC address, in ARP table, A-7
mapping, NAT function, 4-3, A-9
messages, from SYSLOG, 6-3
MIB compliance, C-3
MIB II
IP Group, C-7
System Group, C-3
mode
Standard, 3-10
VNET, 3-10
monitoring, DSL router, 5-1
N
nameserver, DHCP server, A-10
NAPT, 3-6
configuring, 4-4, A-8
NAT, 3-6
applications supported, 3-7
basic, 3-6, 4-3
command line, A-8
configuring with DHCP server, 4-7
navigation, command line interface, A-2
NetMeeting, 3-7
network address port translation (NAPT), 3-6
network address translation (NAT), 3-6
Network Management System (NMS), C-1
network performance statistics, 5-1
new user setup, 2-3
numbered DSL interface, 3-3
L
land bug, 3-9
leasetime, DHCP server, A-10
LEDs, DSL router status, 5-1
levels
of access to the DSL router, 2-4
of SYSLOG messages, 6-3
list command, 2-5
for command line output, D-1
local console access, 2-2
log system events, 6-2
login ID, 2-3
logout, automatically, 2-6
IN-2
O
Operator access, 2-2
output of show commands, A-13
August 2000
6371-A2-GB20-10
Page 97

Index
P
Packet SDSL, 6341/6342 DSL routers, 1-1
password, 2-3
P AT (Port Address Translation), see NAPT, 3-6
PDUs
Bridged, 3-10
Routed, 3-10
performance statistics, 5-1
Ping, 6-5
POTS, with 6371 DSL router, 1-1
primary IP address, A-4
printing command line input, D-1
proxy ARP, 3-5
configuring, 4-5, A-7
configuring with DHCP relay , 4-6
purge
ARP, A-7
IP route, A-6
NAT, A-10
R
RADSL 6371 router, 1-1
rate adaptive 6371 DSL router, 1-1
relay agent
configuring, A-1 1
DHCP, 3-7, 4-6
remote route, A-5
restart device, 6-1
RFC 1483, 3-10
encapsulation, A-3
router, configuring downstream, 4-8
router ID, IP address, A-4
routing table, 3-4
S
SDSL 6341/6342 routers, 1-1
security, 3-9
server, DHCP, 3-7, 4-7
service domain, IP addresses, 3-2
service subscriber, 1-4
shortcuts for command line, B-3
show
alarms, 6-1
commands, A-13
SYSLOG, 6-2
Simple Network Management Protocol (SNMP), C-1
smurf attack, 3-9
SNMP agent, overview, C-1
source IP address, 3-9
standard MIBs, C-3
statistics, 5-1
clearing, 5-4
status, of interfaces, 5-2
Symmetric DSL, 6341/6342 DSL routers, 1-1
syntax, command line interface, A-1
SYSLOG, 6-2
system identity, 2-3, 2-5
T
TCP filter, 3-9
TCP protocol, A-8
Telnet access, 2-1, 2-4
terminal emulation, settings, D-1
timeout, for NA T, A-8
TraceRoute, 6-6
traps, A-12, C-2
troubleshooting, 6-1
U
UDP protocol, A-8
unnumbered DSL interface, 3-3
upstream route, 4-3
user login, 2-3
V
VNET, 3-10
6371-A2-GB20-10 August 2000
configuring, 4-5
IP address, A-4
IN-3
 Loading...
Loading...