Page 1

i
E-47-V Dome Camera Operation Manual
Page 2

ii
Table of Contents
1 Product Overview ........................................................................................................................ 1
2 Initial Config ................................................................................................................................. 2
2.1
2.2
Device Initialization ....................................................................................................... 2
Login and Logout .......................................................................................................... 3
2.2.1 Log in WEB Interface ............................................................................................ 3
2.2.2 Logout ...................................................................................................................... 4
3 Live ................................................................................................................................................ 5
3.1
3.2
3.3
3.4
Encode Setup ................................................................................................................ 5
System Menu ................................................................................................................. 6
Video Window Function Option .................................................................................. 6
Video Window Setup .................................................................................................... 7
3.4.1 Image Adjustment ..................................................................................................... 7
3.4.2 Original Size ............................................................................................................. 8
3.4.3 Full Screen ................................................................................................................ 8
3.4.4 Width and Height Ratio ............................................................................................ 9
3.4.5 Fluency Adjustment .................................................................................................. 9
3.4.6 Rules Info ................................................................................................................. 9
3.4.7 Zoom and Focus ....................................................................................................... 9
4 Playback ..................................................................................................................................... 10
4.1
Playback ....................................................................................................................... 10
4.1.1 Function of Play ...................................................................................................... 10
4.1.2 Playback File .......................................................................................................... 11
4.1.3 Playback Cut ........................................................................................................... 14
4.1.4 Record Type ........................................................................................................... 14
4.1.5 Progress Bar ............................................................................................................ 14
4.1.6 Assistant Function .................................................................................................. 15
4.2
Picture Playback ......................................................................................................... 15
4.2.1 Play ......................................................................................................................... 16
4.2.2 Playback File .......................................................................................................... 16
4.2.3 Snapshot Type ........................................................................................................ 18
5 Setup ........................................................................................................................................... 20
5.1
Camera ......................................................................................................................... 20
5.1.1 Conditions ............................................................................................................... 20
5.1.2 Video ...................................................................................................................... 30
5.1.3 Audio ...................................................................................................................... 38
5.2
Network ......................................................................................................................... 40
5.2.1 TCP/IP .................................................................................................................... 40
Page 3

iii
5.2.2 Port .......................................................................................................................... 41
5.2.3 PPPoE ..................................................................................................................... 44
5.2.4 DDNS ..................................................................................................................... 45
5.2.5 IP filter .................................................................................................................... 46
5.2.6 SMTP (e-mail) ..................................................................................................... 47
5.2.7 UPnP ....................................................................................................................... 48
5.2.8 SNMP ..................................................................................................................... 49
5.2.9 Bonjour ................................................................................................................... 51
5.2.10 Multicast ................................................................................................................. 52
5.2.11 802.1x ..................................................................................................................... 53
5.2.12 QoS ......................................................................................................................... 53
5.2.13 HTTPs ..................................................................................................................... 54
5.3
Event ............................................................................................................................. 63
5.3.1 Video detection ....................................................................................................... 63
5.3.2 Audio Detection ...................................................................................................... 69
5.3.3 Smart Plan ............................................................................................................... 71
5.3.4 Intelligence Behavior Analytics ............................................................................. 71
5.3.5 Face Detection ........................................................................................................ 79
5.3.6 Alarm ...................................................................................................................... 81
5.3.7 Abnormity ............................................................................................................... 82
5.4
Storage Management ................................................................................................. 84
5.4.1 Schedule .................................................................................................................. 84
5.4.2 Destination .............................................................................................................. 88
5.4.3 Record control ........................................................................................................ 90
5.5
System .......................................................................................................................... 91
5.5.1 General .................................................................................................................... 91
5.5.2 Account ................................................................................................................... 94
5.5.3 Default .................................................................................................................... 97
5.5.4 Import/Export ......................................................................................................... 98
5.5.5 Auto Maintenance ................................................................................................... 98
5.5.6 Upgrade .................................................................................................................. 99
5.6
Information ................................................................................................................... 99
5.6.1 Version .................................................................................................................... 99
5.6.2 Log ........................................................................................................................ 100
5.6.3 Online User ........................................................................................................... 101
6 Alarm ......................................................................................................................................... 102
7 Log out ...................................................................................................................................... 104
Page 4

iv
Important
The following functions are for reference only. Some series products may not support all the functions
listed below.
Cybersecurity Recommendations
1. Change Passwords and Use Strong Passwords
The number one reason systems get “hacked” is due to having weak or default passwords. It is
recommended to change default passwords immediately and choose a strong password whenever
possible. A strong password should be made up of at least 8 characters and a combination of special
characters, numbers, and upper and lower case letters.
2. Update Firmware
As is standard procedure in the tech-industry, we recommend keeping IP camera firmware up-to-date to
ensure the system is current with the latest security patches and fixes.
“Nice to have” recommendations to improve your network security
1. Change Passwords Regularly
Regularly change the credentials to your devices to help ensure that only authorized users are able to
access the system.
2. Change Default HTTP and TCP Ports:
● Change default HTTP and TCP ports for systems. These are the two ports used to communicate and
to view video feeds remotely.
● These ports can be changed to any set of numbers between 1025-65535. Avoiding the default ports
reduces the risk of outsiders being able to guess which ports you are using.
3. Enable HTTPS/SSL:
Set up an SSL Certificate to enable HTTPS. This will encrypt all communication between your devices
and recorder.
4. Enable IP Filter:
Enabling your IP filter will prevent everyone, except those with specified IP addresses, from accessing
the system.
5. Change ONVIF Password:
Page 5

v
On older IP Camera firmware, the ONVIF password does not change when you change the system’s
credentials. You will need to either update the camera’s firmware to the latest revision or manually
change the ONVIF password.
6. Forward Only Ports You Need:
● Only forward the HTTP and TCP ports that you need to use. Do not forward a huge range of numbers
to the device. Do not DMZ the device's IP address.
● You do not need to forward any ports for individual cameras if they are all connected to a recorder on
site; just the NVR is needed.
7. Limit Features of Guest Accounts:
If your system is set up for multiple users, ensure that each user only has rights to features and
functions they need to use to perform their job.
8. UPnP:
● UPnP will automatically try to forward ports in your router or modem. Normally this would be a good
thing. However, if your system automatically forwards the ports and you leave the credentials defaulted,
you may end up with unwanted visitors.
● If you manually forwarded the HTTP and TCP ports in your router/modem, this feature should be
turned off regardless. Disabling UPnP is recommended when the function is not used in real
applications.
9. SNMP:
Disable SNMP if you are not using it. If you are using SNMP, you should do so only temporarily, for
tracing and testing purposes only.
10. Multicast:
Multicast is used to share video streams between two recorders. Currently there are no known issues
involving Multicast, but if you are not using this feature, deactivation can enhance your network security.
11. Check the Log:
If you suspect that someone has gained unauthorized access to your system, you can check the system
log. The system log will show you which IP addresses were used to login to your system and what was
accessed.
12. Physically Lock Down the Device:
Page 6

vi
Ideally, you want to prevent any unauthorized physical access to your system. The best way to achieve
this is to install the recorder in a lockbox, locking server rack, or in a room that is behind a lock and key.
13. Connect IP Cameras to the PoE Ports on the Back of an NVR:
Cameras connected to the PoE ports on the back of an NVR are isolated from the outside world and
cannot be accessed directly.
14. Isolate IP Camera Network
The network your NVR and IP camera resides on should not be the same network as your public
computer network. This will prevent any visitors or unwanted guests from getting access to the same
network the security system needs in order to function properly.
Electrical safety
All installation and operation should conform to your local electrical safety codes.
The power source shall conform to the requirement of the Safety Extra Low Voltage (SELV)
standard, and supply power with voltage rated by DC 12 V or AC 24 V according to the Limited
power Source requirement of IEC60950-1. Please note that the power supply requirement is
subject to the device label.
Make sure the power supply is correct before operating the device.
A readily accessible disconnect device shall be incorporated in the building installation wiring
Prevent the power cable from being trampled or pressed, especially the plug, power socket and the
junction extruded from the device.
We assume no liability or responsibility for all the fires or electrical shock caused by improper
handling or installation.
Environment
Do not aim the device at strong light to focus, such as lamp light and sun light, otherwise it might
cause over brightness or light marks, which are not the device malfunction, and affect the longevity
of Charge Coupled Device (CCD) or Complementary Metal-Oxide Semiconductor (CMOS).
Do not place the device in a damp or dusty environment, extremely hot or cold temperatures, or the
locations with strong electromagnetic radiation or unstable lighting.
Keep the camera away from water or other liquid to avoid damages to the internal components.
Keep the indoor device away from rain or damp to avoid fire or lightning.
Keep sound ventilation to avoid heat accumulation.
Transport, use and store the device within the range of allowed humidity and temperature.
Heavy stress, violent vibration or water splash are not allowed during transportation, storage and
installation.
Page 7

vii
Pack the device with standard factory packaging or the equivalent material when transporting the
device.
Page 8
1
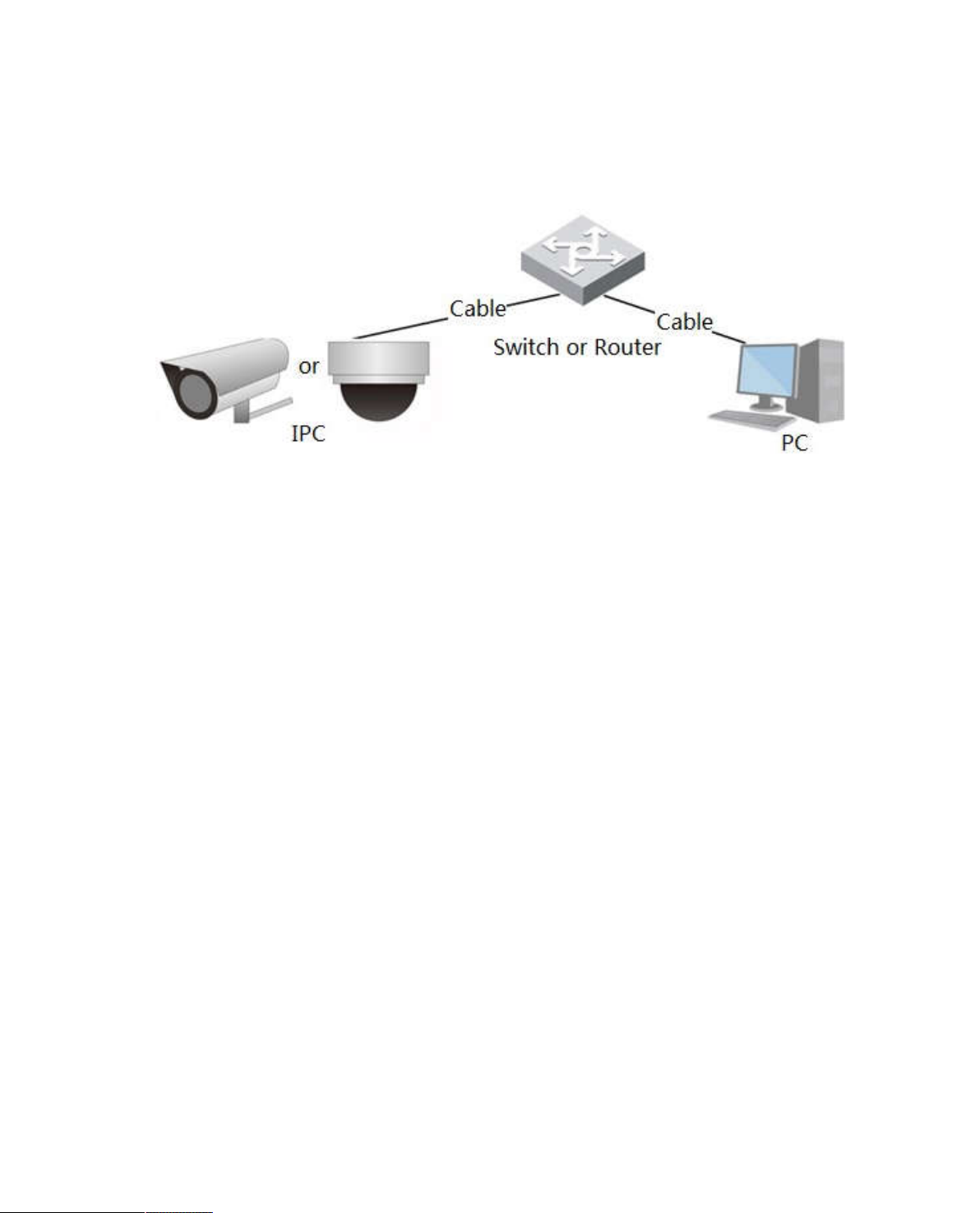
1 Product Overview
The common networking mode for IPC is to connect IPC to PC via switch or router. The common
network mode is shown in Figure 1-1
Figure1-1
Before you have access to network camera via the Internet, you need to acquire its IP address. Users
can search IP address of network camera via Quick Config Tool.
Page 9
2
2 Initial Config
In this chapter it is to introduce the device initial config operation, which includes device initialization,
login device, log out WEB interface and password reset.
2.1 Device Initialization
It needs to implement device initialization when you use the device for the first time. Here it is to take
WEB operation as an example to introduce device initialization. You can also initialize device via Quick
Config Tool, NVR and platform etc.
Note
In order to guarantee device safety, please keep admin login password properly after device
initialization, and modify the password regularly.
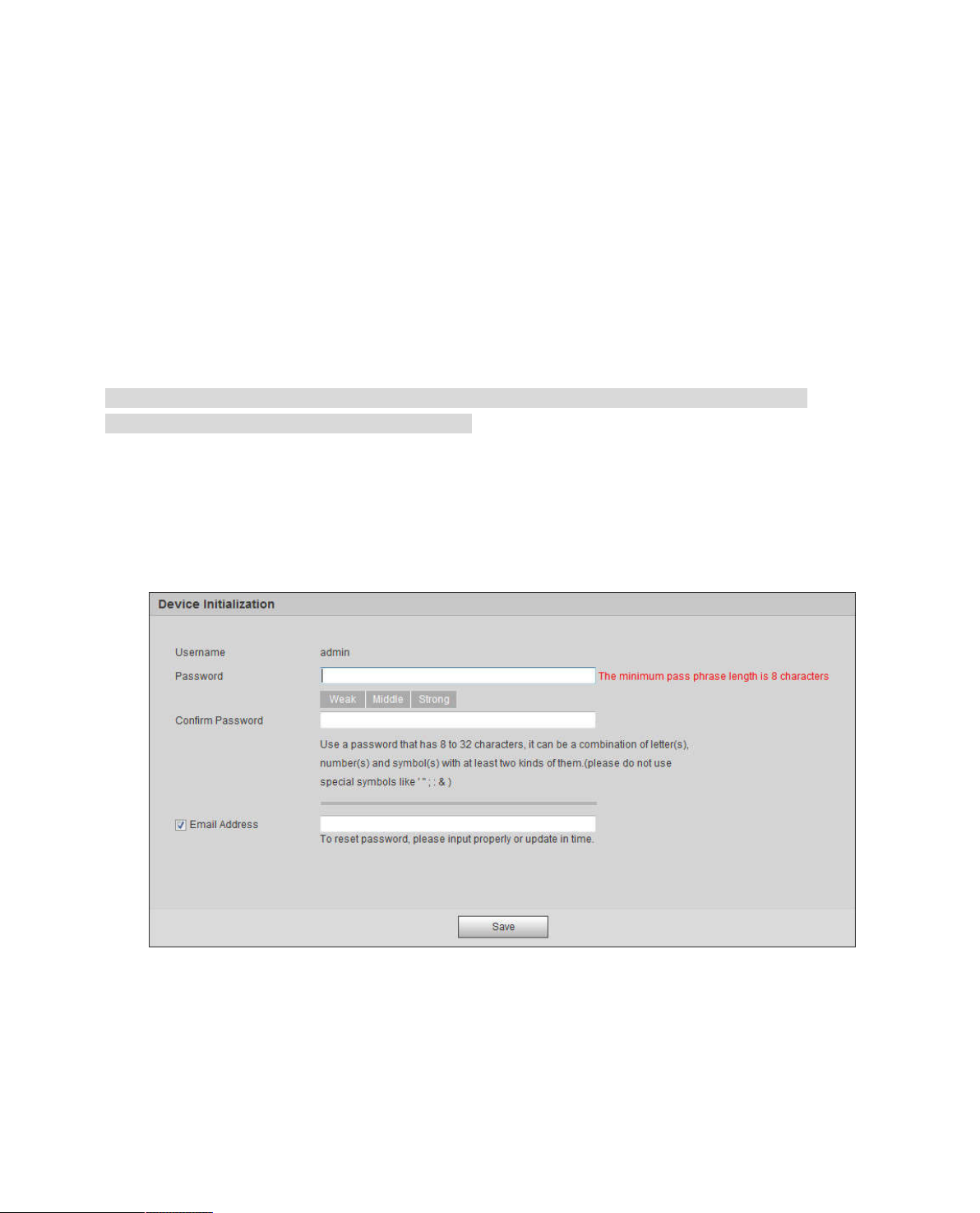
Step 1
Open IE browser, input camera IP address in the address bar and click Enter.
The system will display the interface of Device Initialization after it is connected successfully, which is
shown in Figure 2-1
Note
The default IP address is 192.168.1.108.
Figure 2-1
Step 2
It is to set admin login password, please refer to Table 2-1 for more details.
Page 10

3
Parameter
Note
User name
The default user name is admin
Password
password.
email to reset the password of admin.
The password ranges from 8 to 32 digitals. It can contain letters, numbers
Confirm
password
Email
Step 3
Click Save and device initialization is completed.
and special characters (excluding “'”,“"”,“;”,“:”,“&”) . The password shall
contain at least two categories. Usually we recommend the strong
Input an email address for reset password purpose. In case you forgot
password in the future, input the security code you got on the assigned
Table 2-1
2.2 Login and Logout
Here it is to introduce device login and WEB interface logout via browser, it is to take IE Explorer 8 as
an example to make introduction.
2.2.1 Log in WEB Interface
Users can make operations such as live, playback and config upon the device after logging in device
WEB interface via browser.
Note
It can log in WEB interface after device initialization is completed.
It will prompt to install plug-in when logging in the system for the first time, please download and
install plug-in according to prompt.
Step 1
Open IE browser, input camera IP address in the address bar and click Enter button.
The system will display the Login interface after it is successfully connected, which is shown in Figure 2-
2.
Figure 2-2
Page 11
4
Step 2
Input the password of admin user.
Step 3
Click Login.
It will display the Live interface after it logged in successfully, which is shown in Figure 2-3.
Note
Different devices have different functions with different interface display; please refer to the actual
interface for more details.
Figure 2-3
2.2.2 Logout
Click Logout and return to WEB login interface. After logging in the device WEB, the system will
hibernate automatically if it fails to operate the device for a period of time. It can recover to normal
working status quickly after entering password.
Page 12

5
to disable it. Generally for storage and monitor.
2 3 1
4
3 Live
After you logged in, you can see the live monitor window. See Figure 3-1.
Figure 3-1
There are four sections:
Section 1: Encode setup bar
Section 2: System menu
Section 3: Window function option bar
Section 4: Window adjust bar
3.1 Encode Setup
Note: Some series don’t support sub stream 2.
The encode setup interface is shown as in Figure 3-2
Figure 3-2
Please refer to the following sheet for detailed information.
Parameter Function
Main stream
Click it to enable main stream video monitoring and click again
Page 13
6
substitutes main stream for monitoring.
substitutes main stream for monitoring.
There are three options: TCP/UDP/Multicast
Click on the button to force alarm to be on or off.
zoom in/out the video size.
Sub Stream 1
Sub Stream 2
Protocol
Click it to enable Sub Stream 1 video monitoring and click again
to disable it. When network bandwidth is insufficient, it
Click it to enable Sub Stream 2 video monitoring and click again
to disable it. When network bandwidth is insufficient, it
You can select stream media protocol from the dropdown list.
3.2 System Menu
System menu is shown as in Figure 3-3
Please refer to chapter 3 Live, chapter 4 Playback, chapter 5 Setup, chapter 6 Alarm, chapter 7 Log out
for detailed information.
Figure 3-3
3.3 Video Window Function Option
The interface is shown as below. See Figure 3-1.
1 2 3 4 5 6 7 8 9
Figure 3-1
Please refer to the following sheet for detailed information.
SN Parameter Function
1 Relay-out
2 Digital
Zoom
It shows if there is any alarm output, status description is as
follows:
Red: means there is alarm output.
Grey: means alarm is over.
When the video is in the original status, click it you can
select any zone to zoom in. In the non-original status,
you can drag the zoom-in zone in specified range. Right
click mouse to restore previous status.
Click it; you can use the middle button of the mouse to
Page 14
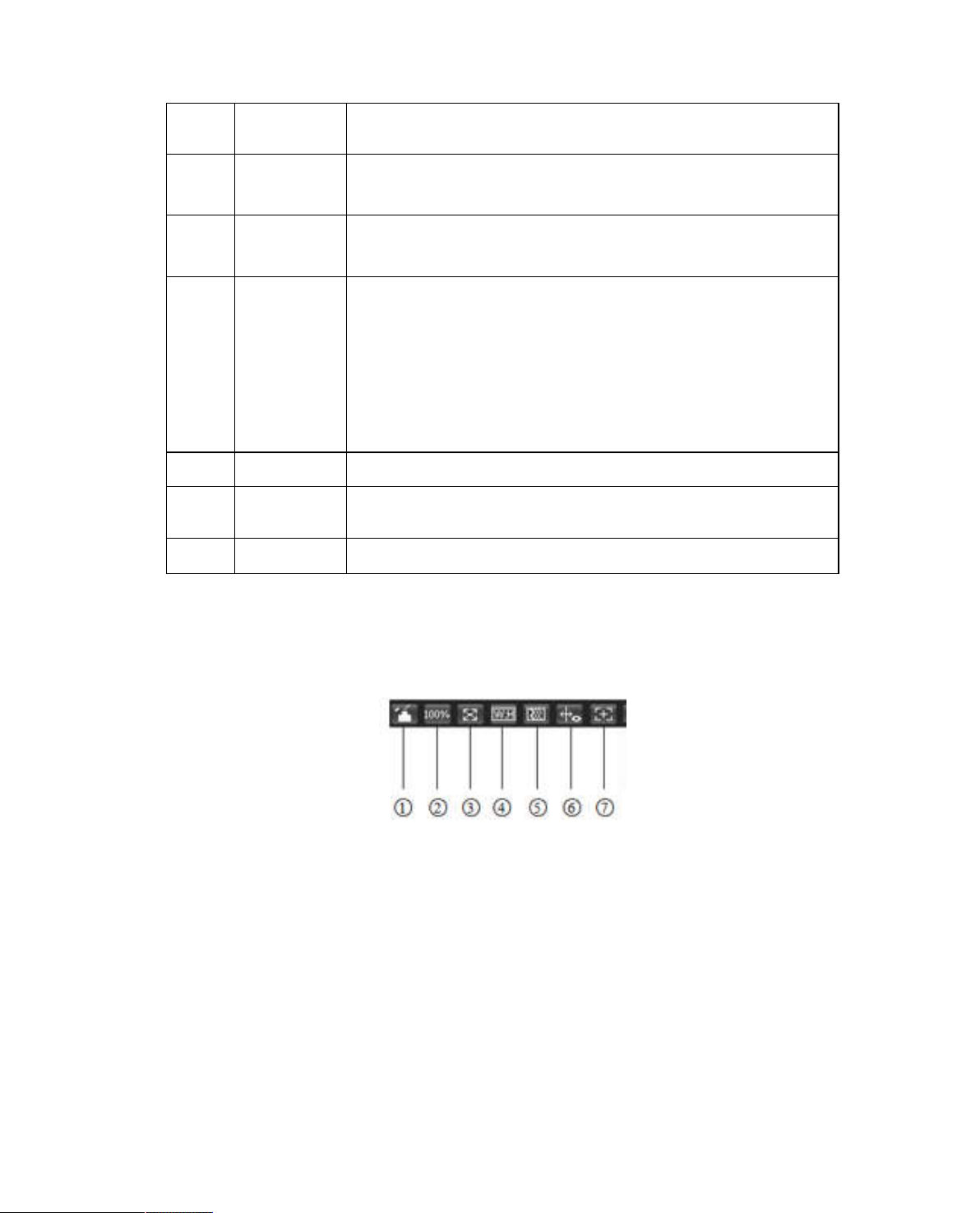
7
5.1.2.5.
3 Snapshot
4 Triple
snapshot
5 Record
6 Easy focus Click it, you can see there are two parameters on the preview
7 Audio
8 Talk Click it to start or end bidirectional talk.
9 Help Click it to open help file.
Click on the button to snapshot, save picture to path in Ch.
5.1.2.5.
Click it to take snapshot upon the video at the frequency of
one picture per second. All images are saved to path in Ch
Click it to record the video. All videos are saved to path in
Chapter 5.1.2.5.
video:AF Peak and AF Max.
AF Peak: It is to display the video definition during the focus
process.
AF Max: It is the most suitable value for the video definition.
The close the AF Peak and AF Max is, the better the focus
effect is.
Turn on or off audio when you are monitoring.
3.4 Video Window Setup
The interface is shown as in Figure 3-2.
3.4.1 Image Adjustment
See Figure 3-3 for image adjustment.
Figure 3-2
Page 15
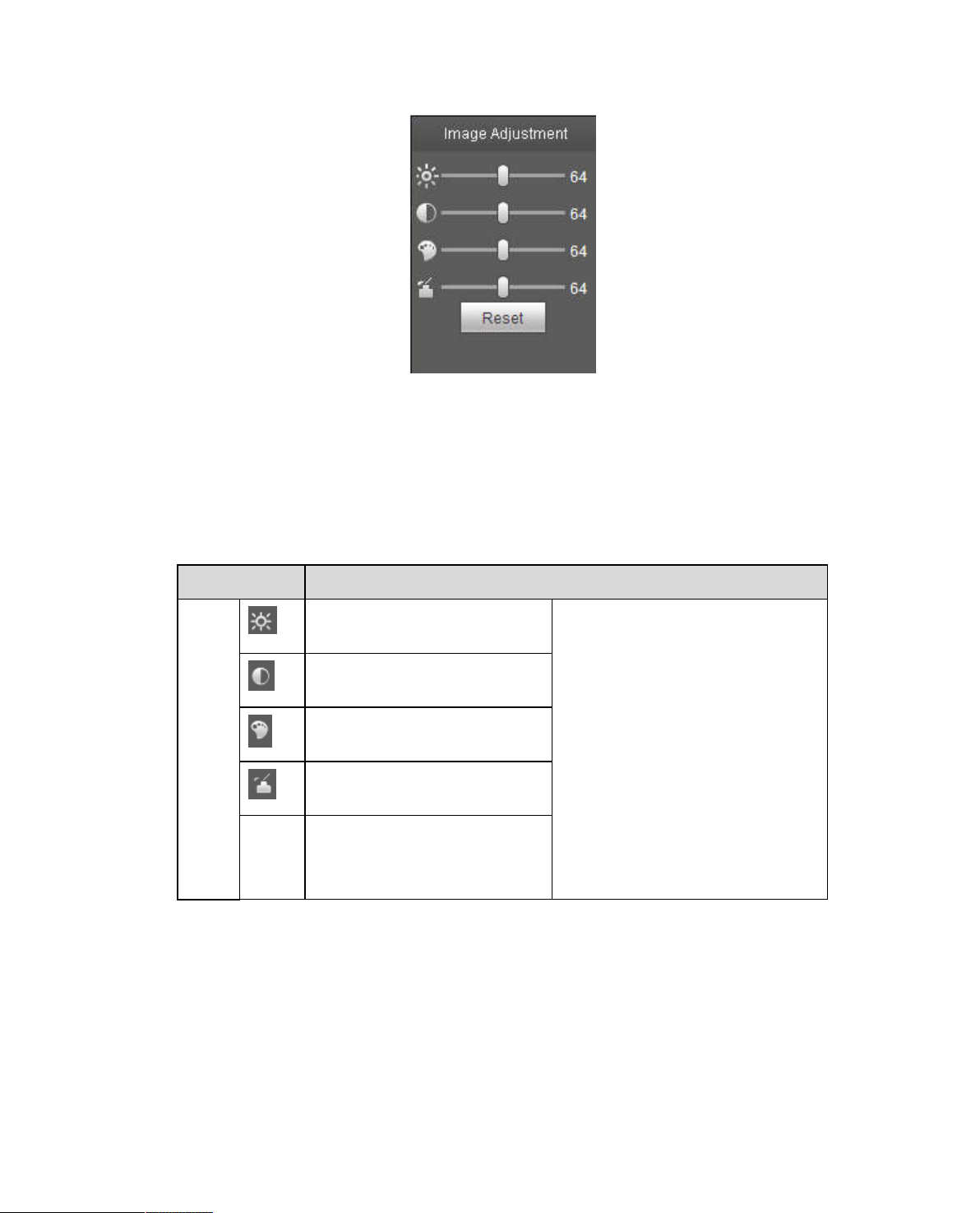
8
Figure 3-3
Click this button to display/hide image control interface. Click it to open picture setup interface. This
interface is on the top right pane.
Please refer to the following sheet for detailed information.
Parameter Function
Video
setup
Reset Restore brightness,
It is to adjust monitor video
brightness.
It is to adjust monitor video
contrastness.
It is to adjust monitor video
hue.
It is to adjust monitor video
saturation.
contrastness saturation and
hue to system default setup.
Note:
All the operations here apply
to WEB end only.
Please go to Setup-
>Camera->Conditions to
adjust corresponding items.
3.4.2 Original Size
Click this button to go to original size. It is to display the actual size of the video stream. It depends on
the resolution of the bit stream.
3.4.3 Full Screen
Click it to go to full-screen mode. Double click the mouse or click the Esc button to exit the full screen.
Page 16

9
3.4.4 Width and Height Ratio
Click it to restore original ratio or suitable window.
3.4.5 Fluency Adjustment
There are three levels of fluency for you to select (Realtime, Normal, and Fluency). The default is
normal.
3.4.6 Rules Info
Click the button, preview image will display intelligent rules after enabling; it is “enable” by default.
3.4.7 Zoom and Focus
Click this button and the focus zooming interface appears on the right of preview interface, as shown in
Figure 2-7, click left mouse button to adjust focus zooming configuration.
Note:
· The product series which support motorized zoom, synchronous focus and back focus have this
button.
· Auto-focus after zoom and focus adjustment.
Page 17
10
3
1 6 5
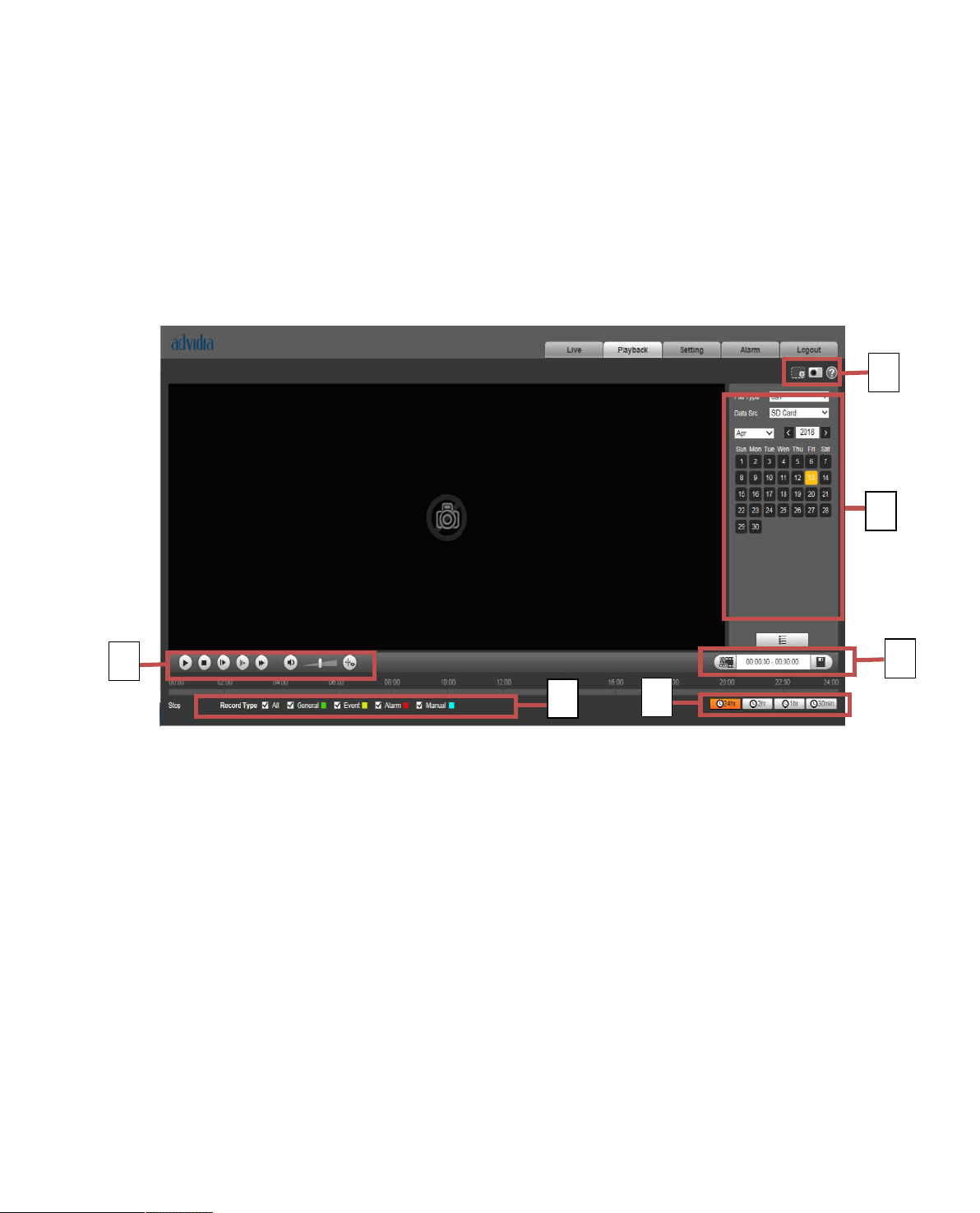
4 Playback
Web client playback supports video playback and picture playback.
Note:
Before playback, user shall set storage management as in Ch. 5.4.
4.1 Playback
The playback interface is shown as in Figure 4-1.
2
4
Figure 4-1
There are four sections:
Section 1: Function of play
Section 2: Playback file
Section 3: Play time cut
Section 4: Record type
Section 5: Progress bar
Section 6: Assistant function
4.1.1 Function of Play
The function of play is shown as in Figure 4-2 and Figure 4-3.
Page 18
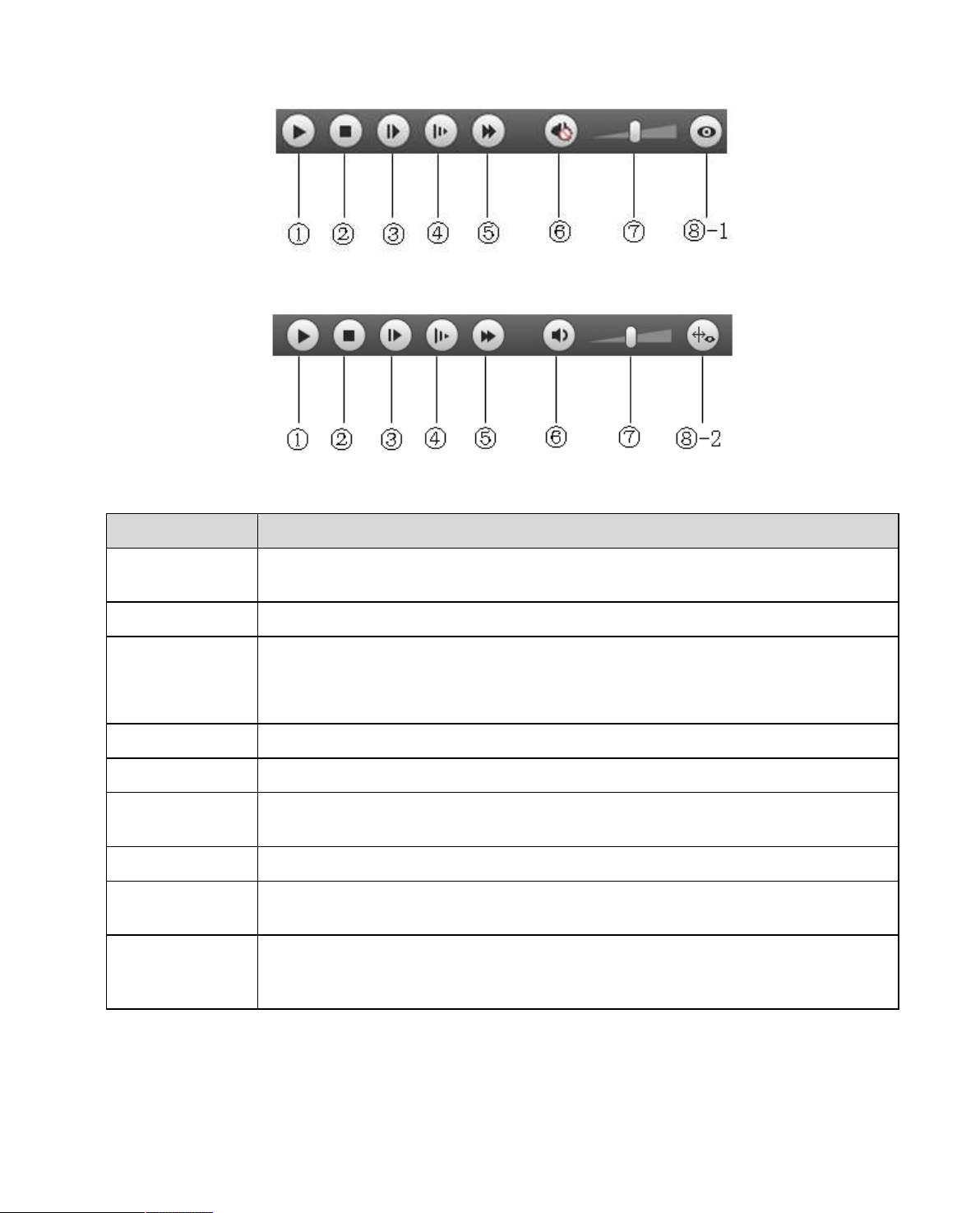
11
①
②
③
④
⑤
⑥
⑦
⑧
Parameter Function
Figure 4-2
Figure 4-3
Play
Stop
Play by
frame
Slow
Quick Click on this button to play quickly.
Silent
Volume
-1 Fisheye
⑧ -2 Rule Info
When you see this button, it means pause or not played record. Click on this
button, switch to normal play status.
Click this button to stop playing.
Click on this button to go to next frame.
Note:
You shall pause record when you use this function.
Click on this button to play slowly.
When this button displays, it means audio is silent. Click on this button to switch
back to normal.
Click on left mouse to adjust volume.
Click this button and fisheye device can adjust display mode according to
different installation mode during the process of playback.
Click the button and it will playback and display intelligent rules and object
detection box if the video is equipped with intelligent rule info after the function is
enabled, it is off by default.
4.1.2 Playback File
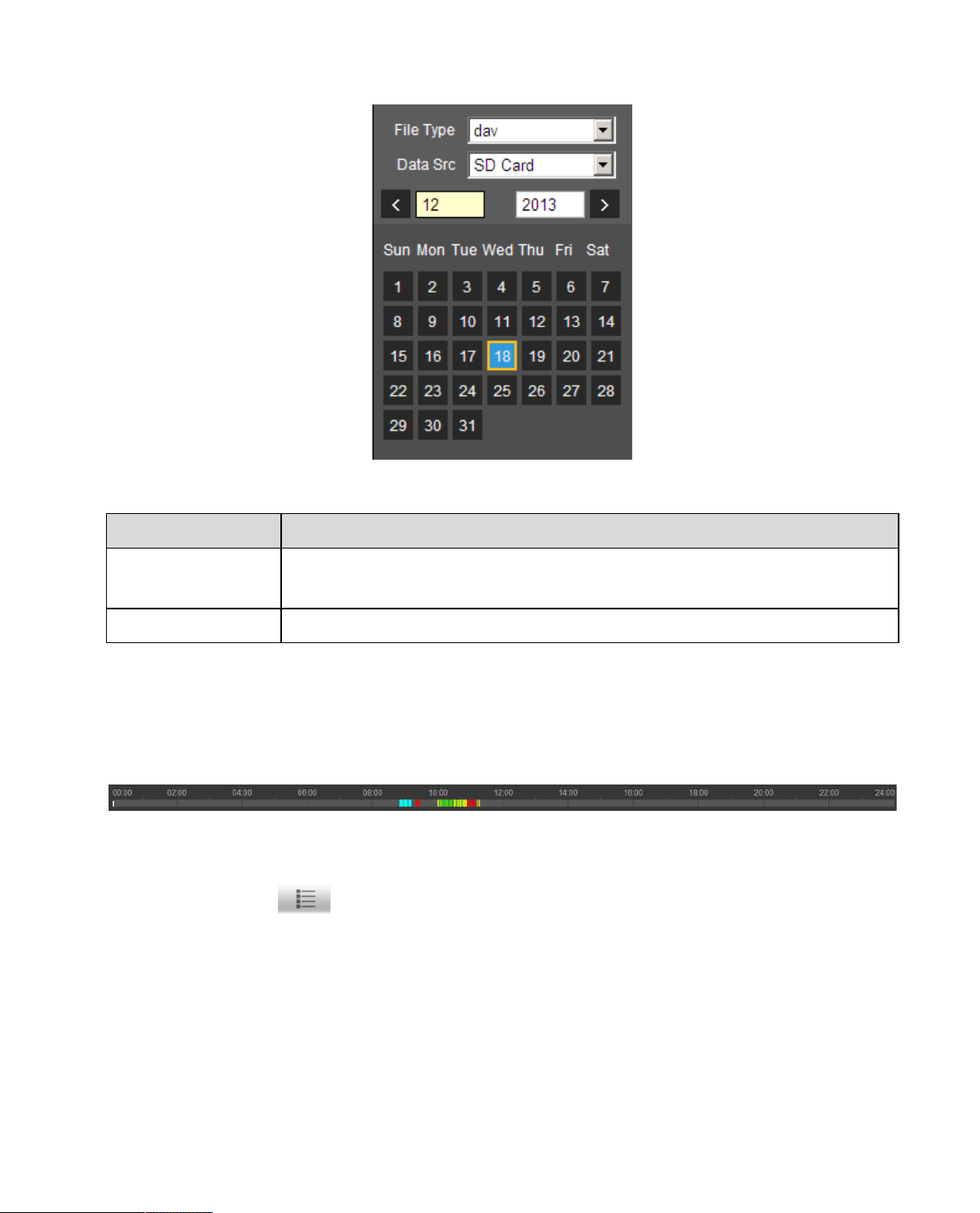
In calendar, blue date represents data currently has video record or snapshot. See Figure 4-4.
Page 19
12
Figure 4-4
Parameter Function
File Type
Data Source Default is SD card.
Step 1. Click on data in blue, time axis displays record file progress bar in color. While, green represents
normal record, yellow represents motion detect record, red represents alarm record, and blue
represents manual record.
Step 2. Click on certain time on progress bar, playback starts from this time. See Figure 4-5.
Select “dav”, as video playback.
Select “jpg” as picture playback.
Figure 4-5
Step 3. Click on file list , select date file will be displayed in list.
Step 4. Double click on file in list, playback this file and display file size, start time and end time.
See Figure 4-6.
Page 20
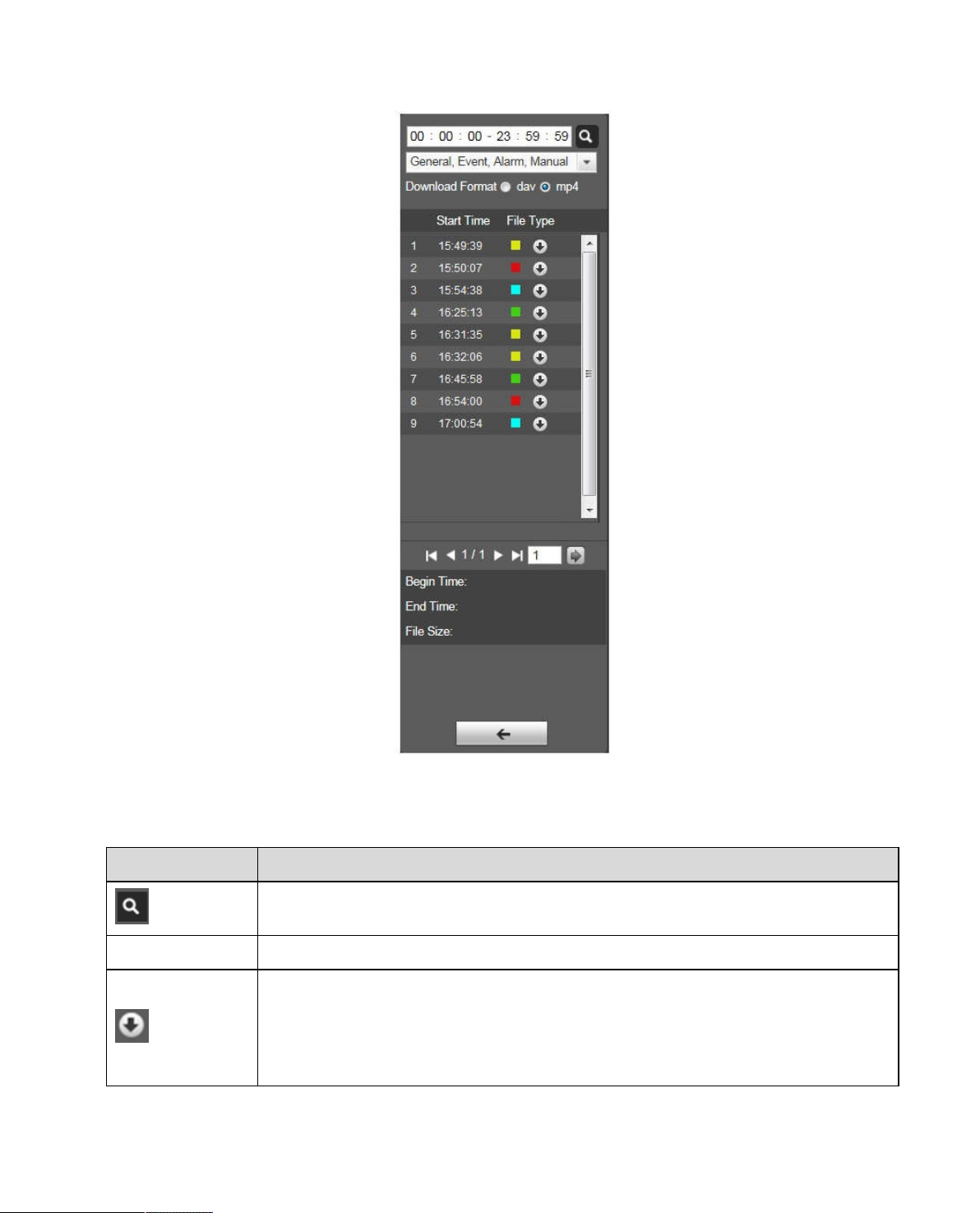
13
Figure 4-6
Parameter Function
Search
Record Format There are two formats: dav, mp4.
Download
It means records within searched start time and end time on the date.
Click the download button and download file to path in Ch. 5.1.2.5.
System does not support download and playback at the same time.
Page 21
14
Parameter Function
Back
Click on back button to go to calendar interface.
4.1.3 Playback Cut
Note:
Playback cut function will automatically pause playing record as playback cut and playback cannot be at
the same time.
Step 1. Click on start time to cut on time axis. This time must be within progress bar range.
Step 2. Move mouse to cut icon . You will be ask to select start time. Click on cur icon as
finish cutting.
Step 3. Click on playback cut end time on time axis. This time must be within progress bar range.
Step 4. Move mouse to cut icon you will be asked to select end time. Click on cut icon as
finish cutting.
Step 5. Click on Save button to save file cut to path in Ch 5.1.2.5. See Figure 4-7.
Figure 4-7
4.1.4 Record Type
After checking record file type, only selected file will be displayed in progress bar and file list. Users can
also select the record type to be displayed via the dropdown box which is above the file list. See Figure
4-8.
Figure 4-8
4.1.5 Progress Bar
Page 22

15
Parameter Function
Figure 4-9
24 hours
2 hours
1 hour
30 min
Click on it, means video in past 24 hours.
Click on it, means video in past 2 hours.
Click on it, means video in past 1 hour.
Click on it, means video in past 30 min.
4.1.6 Assistant Function
Video playback assistant function is shown in Figure 4-10.
Figure 4-10
Parameter Function
Click on it, video in playback status if is in original size, user can
zoom in any area, If it is not in its original size, right click mouse to
Digital Zoom
restore its original size.
Click on this button, you can scroll to zoom in.
Snapshot
Click on this button, you can snapshot video under playback status.
Snapshot will be saved to path in Ch. 5.1.2.5.
4.2 Picture Playback
Web client picture playback interface has the following three functions:
Parameter Function
1 Play function bar
2 Playback file bar
3 Snapshot type bar
See Figure 4-11.
Page 23
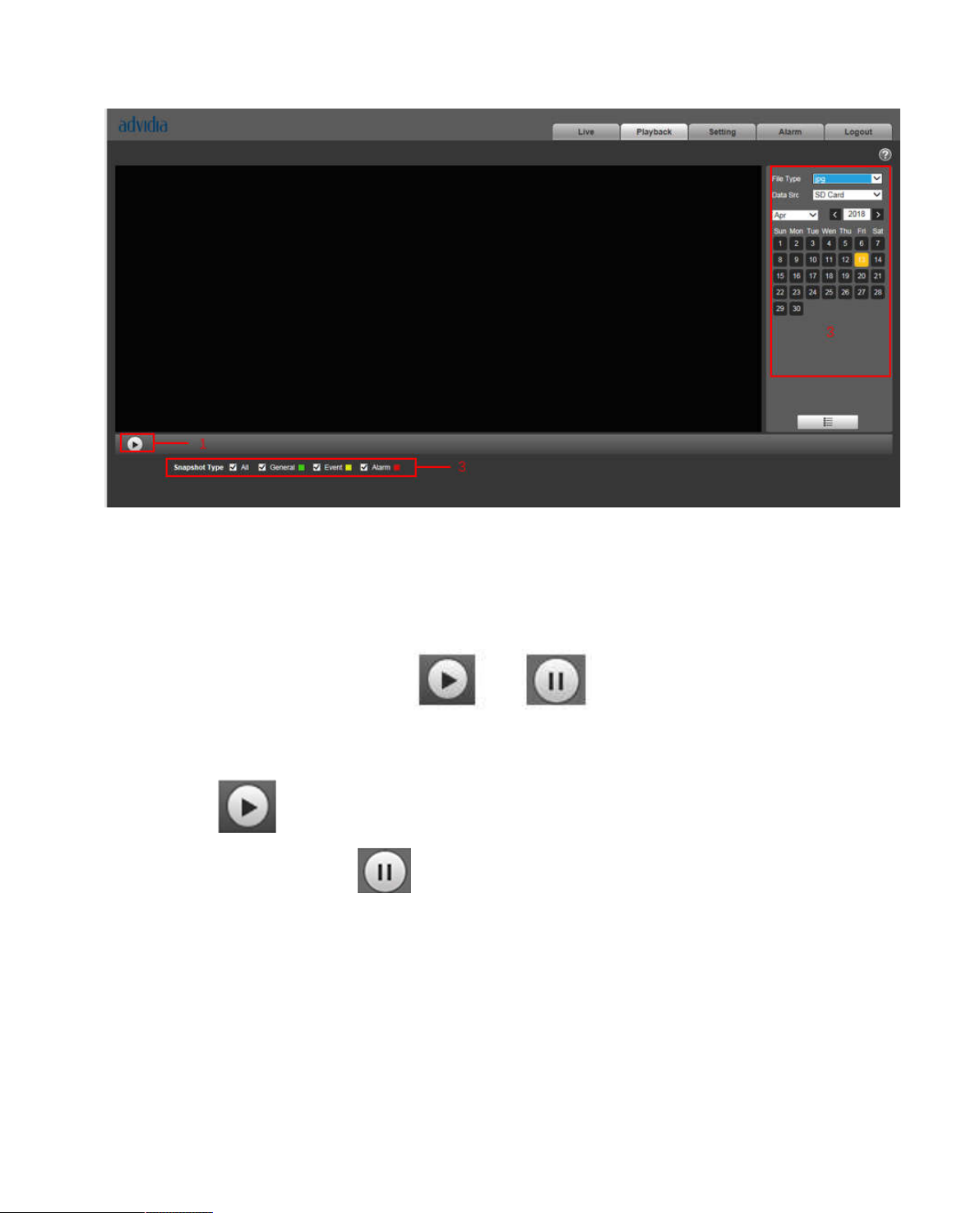
16
Figure 4-11
4.2.1 Play
Figure 4-12
Default icon is and it means pause or not played picture. Click on play button to switch to
normal play status. Icon become
Click on it to pause.
4.2.2 Playback File
Page 24
17
Figure 4-13
Step 1. Click on file list , select snapshot file of the date.
Step 2. Double click on file in list, to play this snapshot.
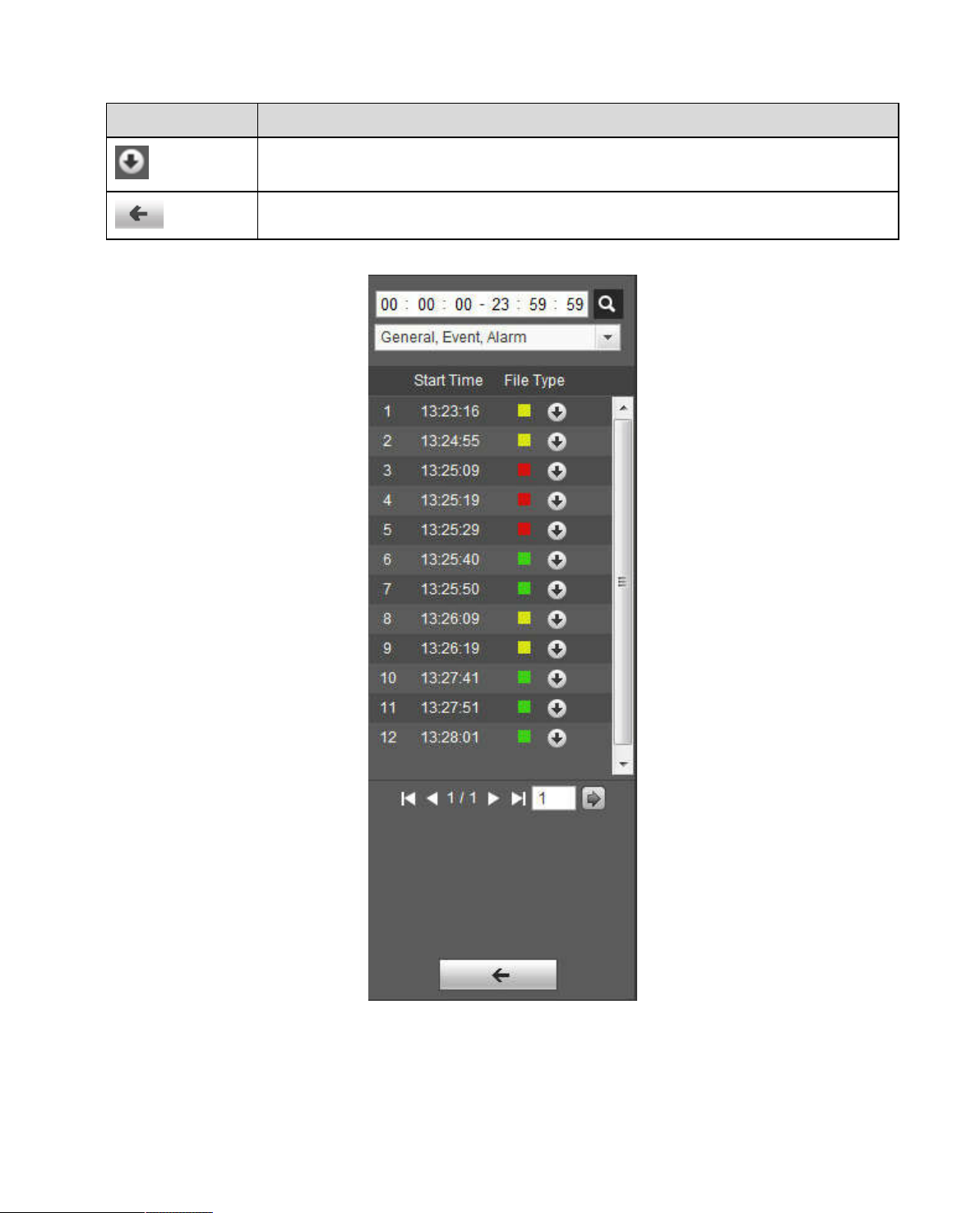
Parameter Function
Search
It means all snapshot files within the start time and end time of selected date.
Page 25
18
Parameter Function
Click the download button to open snapshot file or directly download to local
Download
according to the browser types.
Back
Click on back button to return to calendar interface and re-select time.
Figure 4-14
4.2.3 Snapshot Type
Page 26
19
After checking snapshot file type, in file list only display file of selected type. Users can also select the
snapshot type to be displayed via the dropdown box above the file list. See Figure 4-15.
Figure 4-15
Page 27
20
5 Setup
Web client setup support camera, network, time, storage, system and system info view.
5.1 Camera
The camera setting includes conditions, profile management, zoom and focus.
5.1.1 Conditions
Note:
The camera parameter may be different according to different models, please refer to the actual product
for more details.
5.1.1.1 Picture
Note:
The device which supports true WDR fails to support long exposure when true WDR is enabled.
Step 1
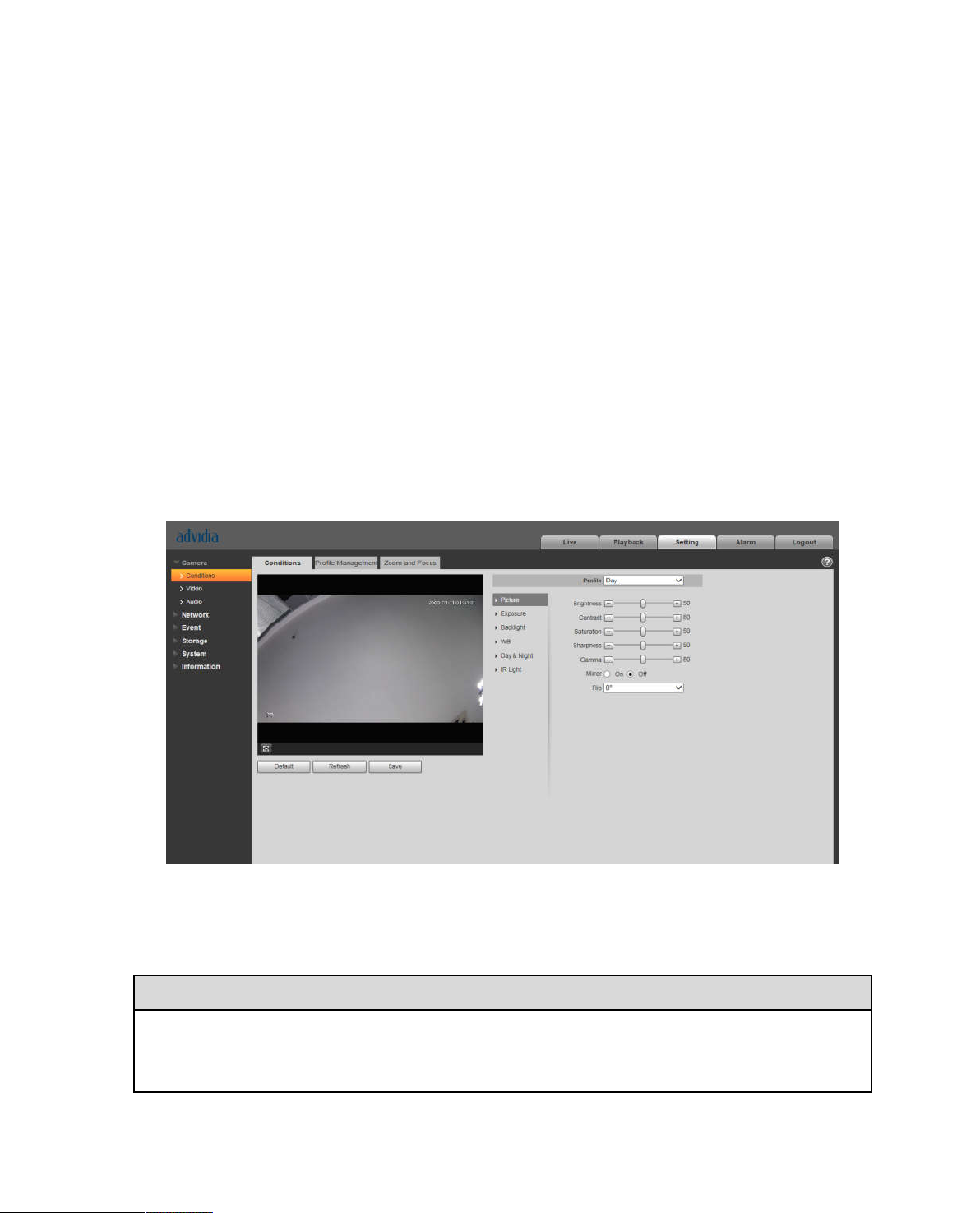
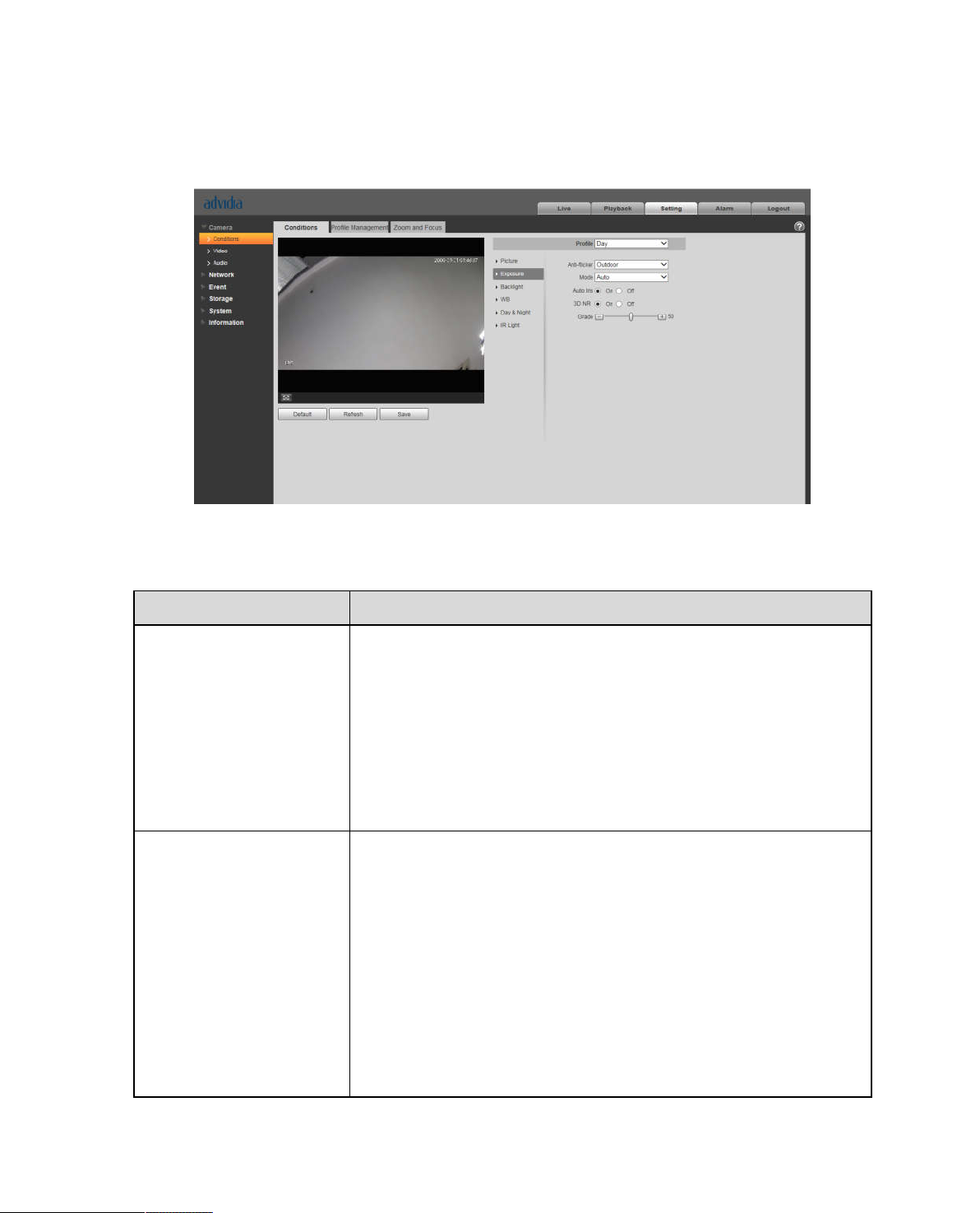
Select “Setup > Camera > Conditions > Picture” and the system will display the “Picture” image which is
shown in Figure 5-1.
Figure 5-1
Step 2
Set picture parameters; please refer to the following sheet for more details about parameter setting.
Parameter Note
Brightness
It is to adjust the image overall brightness via linear adjustment mode.
The larger the number is, the brighter the picture is, and on the contrary it
Page 28
21
Parameter Note
is opposite. The picture get blurry easily when the value is set too big.
It is to adjust the picture contrast. The bigger the value is, the bigger the
bright contrast becomes, and on the contrary it is smaller. The dark area
Contrast
Saturation
Sharpness
Gamma
becomes darker and the bright area becomes overexposed easily when
the value is set too big. The picture becomes blurry when the value is set
too small.
It is to adjust the color darkness and lightness. The color becomes darker
when the value is bigger; on the contrary it becomes lighter. The value
causes no influence to the overall brightness of the image.
It is to adjust the sharpness level of the picture edge. The bigger the
sharpness value is, the more obvious the image edge becomes, the image
is likely to generate noise more easily when the value is set too big.
It is to change image brightness and improve the dynamic display range of
the image via nonlinear adjustment mode. The bigger the value is, the
brighter the picture becomes, and on the contrary it is opposite.
Mirror After mirror is enabled, the monitoring image will be displayed invertedly.
It is to change the display direction of the monitoring image.
It includes following options:
Normal: The monitoring picture is normally displayed.
Flip mode 1: The monitoring picture is displayed with clockwise
rotation 90°
Flip
Flip mode 2: The monitoring picture is displayed with anticlockwise
rotation 90°
180°: The monitoring picture is displayed upside down.
Note:
Please set the video resolution as 1080P or lower when applying
flip mode for some devices.
Step 3
Click “Save” and complete the image parameter config of the camera.
5.1.1.2 Exposure
Page 29
22
gain range which is set by priority during normal exposure
Step 1
Select “Setup > Camera > Conditions > Exposure”. The system will display the “Exposure” interface
which is shown in Figure 5-2.
Step 2
It is to set the exposure parameter, please refer to the following sheet for more details.
Figure 5-2
Parameter Note
Outdoor: You can switch to exposure mode when it is in
50Hz: When the current is 50Hz, system can auto adjust the
Anti-flicker
60Hz: When the current is 60Hz, system can auto adjust the
It is the camera exposure mode.
Note:
When “Anti-flicker” is “Outdor”, the “exposure mode” can be
Different devices have different exposure modes; please
Mode
It includes the following options:
Auto: It can auto adjust the image brightness according to
Gain priority: The device can auto adjust according to the
outdoor mode, it can realize the result in the corresponding
exposure mode.
exposure according to the environment brightness in case
there is any stripe.
exposure according to the environment brightness in case
there is any stripe.
set as “gain priority” or “shutter priority” mode.
refer to the actual interface.
the environment.
Page 30
23
Parameter Note
Shutter priority: The device can auto adjust according to the
Iris priority: Iris value is fixed, the device can auto adjust the
Manual: It is to manually set gain value and shutter value,
It can set the parameter when the camera installs auto iris.
The lens iris can auto adjust the size according to the
Auto Iris
The iris value reaches the max when disabling auto iris, the
range according to the different scene brightness. The device
will auto adjust shutter value if the image brightness fails to
reach the effect and the gain value has reached to upper limit
or lower limit, which is to make the image reach the best
brightness.
shutter range which is set by priority during normal exposure
range according to the different scene brightness. The device
will auto adjust shutter value if the image brightness fails to
reach the effect and the shutter value has reached to upper
limit or lower limit, which is to make the image reach the best
brightness.
shutter value if the image brightness fails to reach effect and
the shutter value has reached the upper limit or lower limit,
the device can auto adjust the gain value to make the image
reach the best brightness.
adjust the the displayed brightness of the image.
environment after auto iris is enabled, then the image
brightness will change accordingly.
lens iris will not change according to the environment
brightness.
It is to process the image with multiframe (at least two frames), it
3D NR
Grade
Step 3
Click “Save” to complete the parameter config of camera exposure.
5.1.1.3 Backlight
Backlight mode can be divided into BLC, WDR and HLS.
BLC: it can avoid cucoloris phenomenon of the darker area in the backlight environment.
WDR: It can suppress the overbright area and compensate darker area by enabling WDR, which can
make the overall image clear.
can realize noise reduction of the image by using the interframe
information between the previous and latter frame.
It can set the parameter when “3D NR” is enabled.
The bigger the grade is, the better NR effect it can realize.
Page 31

24
HLC: It is to weaken the high light, which can be applied in the areas such as toll gate, entrance and exit
of the parking lot and etc. As for extreme light, it can snapshot the human face in the dark environment
and it can realize better effect for the details of the plate number.
Step 1
Select “Setup > Camera > Condition > Backlight”, the system will display the interface of “Backlight”
which is shown in Figure 5-3.
Figure 5-3
Step 2
Set the backlight parameter.
When the “Mode” is set as “Scene Self-adaptation”, the system will auto adjust the image
brightness according to the environmental brightness, which is to make the object display clearly in
the scene.
When the “Mode” is set as “BLC”, it can select default mode or customized mode.
When selecting “Default” mode, the system can realize auto exposure according to the
environment, which is to make the image in the darkest area clear to be seen.
When selecting “Customized” mode, the system can realize exposure upon the selected area
after it set customized area, which is to make the image of the selected area reach
appropriate brightness.
When the “Mode” is set as “WDR”, it will lower the brightness of the area with high brightness and
enhance the brightness of the area with low brightness, which is to make the objects in both high
brightness and low brightness area display clearly.
Note:
There may be video loss of a few seconds when the camera is switched from non WDR mode to WDR
mode.
Page 32

25
When the “Mode” is set as “HLC”, the system will constrain the brightness of the area with high
brightness and decrease the size of the halo area, which is to lower the brightness of the whole
image.
Step 3
Click “Save” to complete the config of the backlight mode.
5.1.1.4 WB
WB is used to restore the white object in the scene by the camera, after WB mode is set, it can make
the white object look white in different environments.
Step 1
Select “Setup > Camera > Conditions > WB”, the system will display the interface of “WB”, which is
shown in Figure 5-4.
Figure 5-4
Step 2
Set WB mode.
When the “Mode” is set as “Auto”, the system can auto compensate white balance upon different
color temperatures, which is to make the image color normal.
When the “Mode” is set as “Natural”, the system can auto compensate white balance to the scene
without artificial light, which is to make the image color normal.
When the “Mode” is set as “Street Lamp”, the system can auto compensate white balance to the
outdoor scene at night, which is to make the image color normal.
When the “Mode” is set as “Outdoor”, the system can auto compensate white balance to the most
outdoor scenes with natural light and artificial light, which is to make the image color normal.
When the “Mode” is set as “Manual”, it can manually set the value of red gain and blue gain; the
system can compensate the different color temperatures in the environment according to the
settings.
Page 33

26
Black & white: The camera image is displayed as black & white image.
It is to set the sensitivity of the switch between image color display and
When the “Mode” is set as “Regional Custom”, it is to set customized area, the system can
compensate white balance to different color temperature of the images in the area, which is to
make the image color normal.
Step 3
Click “Save” to complete the config of WB mode.
5.1.1.5 Day & Night
It is to set the switch between color mode and black & white mode.
Step 1
Select “Setup > Camera > Conditions > Day & Night” and the system will display the interface of “Day &
Night”, which is shown in Figure 5-5.
Figure 5-5
Step 2
Set day & night parameter; please refer to the following sheet for more details.
Parameter Note
It is to set the camera image displayed as color or black & white mode.
Note:
The setting of “Day/Night Mode” is not affected by the setting of “Profile
Management”.
Mode
Sensitivity
It includes the following options:
Color: The camera image is displayed as color image.
Auto: The camera can auto select color image or black & white image
to be displayed according to the environmental brightness.
The parameter can be set when the “Day/Night Mode” is “Auto”.
Page 34

27
color display and black & white display.
Parameter Note
black & white display.
The parameter can be set when the “Day/Night Mode” is “Auto”.
Delay
Step 3
Click “Save” to complete the config of day/night mode.
5.1.1.6 IR Light
You can directly set the mode of IR light if the device is equipped with IR light.
Step 1
Select “Setup > Camera > Conditions > IR Light” and the system will display the interface of “IR Light”
which is shown in Figure 5-6.
It is to set the switch delay between image color display and white & black
display. The smaller the delay is, the faster of the switch becomes between
Step 2
It is to set IR light mode according to the actual scene.
When the “Mode” is set as “Manual”, it can manually set the brightness of IR light; the system will
realize light compensation to the image according to the IR light intensity.
When the “Mode” is set as “Smart IR”, the system can adjust the light brightness according to the
actual scene.
When the “Mode” is set as “Zoomprio”, the system can auto adjust the IR light according to the
brightness change of the actual scene.
Figure 5-6
Page 35

28
The system will enable near light by priority when the actual scene becomes dark, the system
will enable the far light when the near light fails to meet the requirement of scene brightness
even if it is adjusted to the brightest.
The system will adjust far light brightness by priority to off and then adjust the brightness of
near light when the actual scene becomes bright. The system will always disable far light
when the focal length of the lens is adjusted to a certain wide angle, which is to avoid near
overexposure. Meanwhile, it can manually set light compensation to slightly adjust the
brightness of IR light.
When the “mode” is set as “Off”, it will not enable the IR light.
Step 3
Click “Save” and complete the config of IR light.
5.1.1.7 Profile Management
Step 1
Select “Setup > Camera > Conditions > Profile Management” and the system will display the interface of
“Profile Management”.
Step 2
Set profile management.
When the “Profile Management” is set as “Normal”, the system will monitor according to the normal
config.
Figure 5-7
When the “Profile Management” is set as “Full Time”, you can select “Always Enable” in “Day” or
“Night’, the system will monitor according to the config of “always enable”.
Figure 5-8
Page 36

29
When the “Profile Management” is set as “Schedule”, you can set some period as day and another
period as night, for example, if it sets 0:00~12:00 as day, 12:00~24:00 as night, then the system will
monitor by adopting corresponding config in different periods.
Step 3
Click “Save” to complete the settings of profile management.
Note:
Click “Default” to restore the device to default config; click “Refresh” to check the latest config file of the
device.
5.1.1.8 Zoom and Focus
Note:
Only motorized vari-focal devices support focus and zoom function.
Step 1
Select “Setup > Camera > Conditions > Zoom and Focus” and the system will display the interface of
“Zoom and Focus” which is shown in Figure 5-10.
Figure 5-9
Figure 5-10
Page 37

30
Step 2
Adjust the focal length of the lens.
After it is zoomed, set “Speed” and press “+”, “-“or drag the sliding block directly to adjust.
Step 3
Adjust the lens definition.
After it is focused, set “Speed” and press “+”, “-“or drag the sliding block directly to adjust.
Note:
Speed is used to set the length by pressing “+” and “-“.
After adjusting the focal length of the lens or click “Auto Focus”, the device will auto adjust the
image definition, it is not allowed to implement other lens operation during auto focus.
After several times of zoom and focus, the image fails to be adjusted clear, click “Restore All’ to
reset the lens to zero and remove the accumulative error of the lens.
Click “Refresh” and the device will automatically synchronize the hardware to the location of sliding
block of lens zoom and focus.
5.1.2 Video
5.1.2.1 Video
Step 1
Select “Setup > Camera > Video > Video” and the system will display the interface of “Video” which is
shown in Figure 5-11.
Figure 5-11
Step 2
Set video bit stream, please refer to the following sheet for more details about the parameters.
Page 38

31
display the dewarped image on the third-party platform.
Parameter Function
Installation Mode
It will display the parameter when the device is fisheye.
There are three installation modes for fisheye which are
ceiling, wall mount and ground installation, please
select installation mode according to the actual
installation scene of the fisheye.
The system will begin to switch after switching
installation mode, it will prompt successfully saved after
it is switched successfully.
Note:
The device end will output the dewarped video stream
after configuring installation and record mode, when the
device is accessed to third-party platform, it will directly
Record Mode
It will display the parameter when the device is fisheye.
The system will begin to switch after record mode is
switched, it will prompt saved successfully after it is
switched successfully.
The record mode will change according to the different
installation modes.
1O: the original picture which is not dewarped.
1P: 360°rectangular panorama.
2P: The mode can be set when the “Installation
Mode” is set as “Ceiling” or “Ground”. It is the 2
related 180°rectangular image, the two
subwindows can both form 360°panorama anytime.
1O+3R: original image + 3 independent sub
images, both the sub image and sub boxes in the
original image can support zoom and movement.
1R: Original image + independent sub image, the
sub boxes of the original image support zoom and
movement.
4R: original image + 4 independent sub images,
both the sub image and sub boxes in the original
image support zoom and movement.
2R: Original image + 2 independent sub images,
the sub boxes of the original image can support
zoom and movement, the sub image supports up
and down movement, which can change the
vertical angle of view.
Note:
The device end will output dewarped video stream after
configuring installation and record mode, when the
device is accessed to the third-party platform, it will
directly display the dewarped image on the third-party
platform.
Page 39

32
stream 2 at the same time.
please refer to the actual interface for more details.
code stream setting.
recommend bit to get the better video output effect.
Under MJPEG mode, only CBR is available.
Parameter Function
Sub Stream Enable
Select “Enable” to enable sub stream.
The device supports enabling sub stream 1 and sub
Smart Codec
Code-Stream Type
Encode mode
It can enhance image compression performance and
reduce storage space by enabling intelligent encoding.
Note:
After intelligent encoding is enabled, the device will not
support third stream, ROI or intelligent event detection,
ACF means using different fps to record.
There are two options: VBR and CBR.
Please note you can set video quality in VBR mode.
Note:
WEB interfaces don’t support motion detect and alarm
There are five options: H.264 (main profile standard,
H.264H (high profile standard), H.264B (Baseline
Profile), H.265 (main profile standard) and MJPEG
encode.
The H.264, H.264H both are H264 bit stream.
H.264 is the Main Profile encode and you need to
enable the sub stream function in your camera and
set the resolution as CIF. Then you can monitor via
the Blackberry cell phone.
The H.265 is the main profile encode mode.
MJPEG: In this encode mode, the video needs to
large bit stream to guarantee the video definition.
You can use the max bit stream value in the
Resolution There are multiple resolutions. You can select from the
Frame Rate (FPS)
Bit Rate Type
Recommended Bit Recommended bit rate value according to the resolution
dropdown list.
For each resolution, the recommended bit stream value
is different.
Note: When video is under rotating status, you cannot
set resolution higher than 1080P (excluding 1080P).
PAL: 1~25f/s,1-50f/s NTSC: 1~30f/s or 1~60f/s.
The frame rate may vary due to different resolutions.
There are two options: VBR and CBR.
Please note, you can set video quality in VBR mode.
and frame rate you have set.
Page 40

33
information.
Parameter Function
Bit Rate
SVC Frame rate can be encoded by layer. It is a flexible
I Frame Here you can set the P frame amount between two I
Watermark Settings Select “Watermark Setting” and enable watermark
Watermark Character It is the character of watermark verification, it is
In CBR, the bit rate here is the max value. In
dynamic video, system needs to low frame rate or
video quality to guarantee the value.
The value is null in VBR mode.
Please refer to recommend bit rate for the detailed
encoding method. By default, it is 1 as 1 layer. You also
can set 2/3/4 layers.
frames. The value ranges from 1 to 150. Default value
is 50.
Recommended value is frame rate *2.
function. After the watermark function is enabled, you
can check if the video is tampered via verifying
watermark character.
DigitalCCTV by default.
5.1.2.2 Snapshot
The snapshot interface is shown as in Figure 5-13.
Figure 5-13
Please refer to the following sheet for detailed information.
Parameter Function
Snapshot type
Image size It is the same as the resolution of main stream.
There are two modes: general (schedule) and Event (activation).
Quality
It is to set the image quality. There are six levels.
Page 41

34
Interval
5.1.2.3 Video Overlay
The video overlay interface is shown as in Figure 5-14.
It is to set snapshot frequency. Optional1~7s/picture, customized.
Figure 5-14
Figure 5-15
Page 42

35
Figure 5-16
Figure 5-17
Page 43

36
System max supports 4 privacy mask zones.
You can use the mouse to drag the time tile position.
You can use the mouse to drag the channel tile position.
position. Alignment include align left and align right.
You cannot enable text and picture overlay at the same time.
type and left align and right align for OSD info.
Figure 5-18
Please refer to the following sheet for detailed information.
Parameter Function
Privacy Masking
Time Title
Channel Title
Text Overlay
Picture Overlay
Counting
Here you can privacy mask the specified video in the
monitor video.
You can enable this function so that system overlays time
information in video window.
You can enable this function so that system overlays
channel information in video window.
You can enable this function to overlay text in video
window.
You can use the mouse to drag location box to adjust its
You can enable this function to display overlay picture.
Click on disable to turn it off.
Click on Upload Picture to overlay local picture into
monitoring window. You can drag the yellow box to move
it.
Note:
Check “Enable” to display the counting statistics data in
the video monitoring window; check “Disable” not to
display.
There are enter number and leave number for statistics
Page 44

37
effect.
Refresh
Default
Save
5.1.2.4 ROI
Note: Some series don’t support ROI setup function.
Set privacy mask, channel title, time title, location, overlay
and save the change. You can click on Refresh to see
Click it to restore default config.
Click it to complete video settings.
Figure 5-19
Figure 5-20
Page 45

38
Parameters Note
Enable
Image
Quality
5.1.2.5 Path
The storage path interface is shown as in Figure 5-21.
Here you can set snap image saved path and the record storage path.
The default monitor image path is C:\Users\admin\WebDownload\LiveSnapshot.
The default monitor record path is C:\Users\admin\WebDownload\LiveRecord.
The default playback snapshot path is C:\Users\admin\WebDownload\PlaybackSnapshot.
The default playback download path is C:\Users\admin\WebDownload\PlaybackRecord.
The default playback cut path is: C:\Users\admin\WebDownload\VideoClips.
Note:
Admin is locally logged in PC account.
Please click the Save button to save current setup.
Check “Enable”, then it will display the ROI in the video monitoring window;
Check “Disable”, then it won’t display.
Set the image quality of ROI, ranging from 1~6, default is 6.
Note:
For fisheye device, it ranges from 1~6 (best), default is 6 (best)
Able to set area block, max 4 areas.
Figure 5-21
5.1.3 Audio
Please note some series devices do not support audio function.
5.1.3.1 Audio
The audio interface is shown as below. See Figure 5-22.
Page 46

39
Figure 5-22
Please refer to the following sheet for detailed information.
Parameter Function
Enable You can enable audio only when video is enabled.
After selecting the “Enable” of main stream or sub stream, the
network transmission stream is the audio/video composite
stream, otherwise it only includes video image.
Encode mode The encode mode of the main stream and extra stream include
G.711A, G.711Mu, G.726 and ACC. The default mode is
G.711A.
The setup here is for audio encode mode and the bidirectional
talk encode both.
Sampling
Frequency
AudioIn Type Two modes to select: LineIn, Mic. Device needs to connect
The sampling frequency of audio. It includes the following
options:
8K
16K
32K
48K
64K
external audio input source under LineIn mode, and it doesn’t
need to connect external audio input source under Mic mode.
Page 47

40
Noise Filter Enable the function and it can filter relevant noise.
Microphone
Volume
Speaker Volume
Adjust microphone volume from 0~100.
Note:
Supported by some devices.
Adjust speaker volume from 0~100.
Note:
Supported by some devices.
5.2 Network
5.2.1 TCP/IP
The TCP/IP interface is shown as in Figure 5-23. It supports IPv4 and IPv6. IPv4 supports static IP and
DHCP. IPv6 supports static IP only. When users manually modify IP address, WEB will automatically
jump to the new IP address.
Figure 5-23
Please refer to the following sheet for detailed information.
Parameter Function
Host Name It is to set current host device name. It max supports 15
characters.
Ethernet Card Please select the Ethernet port. Default is wired.
Please note you can modify the default Ethernet card if there is
more than one card.
Page 48

41
Mode There are two modes: static mode and the DHCP mode. Select
DHCP mode, it auto searches IP, and you cannot set IP/subnet
mask/gateway. Select static mode, you must manually set
IP/subnet mask/gateway.
Mac Address It is to display hose Mac address.
IP Version It is to select IP version. IPV4 or IPV6.
You can access the IP address of these two versions.
IP Address Please use the keyboard to input the corresponding number to
modify the IP address and then set the corresponding subnet
mask and the default gateway.
Preferred DNS DNS IP address.
Alternate DNS Alternate DNS IP address.
Enable
ARP/Ping set
device IP
address service.
You can use ARP/Ping command to modify or set the device IP
address if you know the device MAC address.
Before the operation, please make sure the network camera
and the PC in the same LAN. This function is on by default.
You can refer to the steps listed below.
Step 1: Get an IP address. Set the network camera and the PC
in the same LAN.
Step 2: Get the physical address from the label of the network
camera.
Step 3: Go to the Run interface and then input the following
commands.
arp –s <IP Address> <MAC>
ping –l 480 –t <IP Address>
Such as:arp -s 192.168.0.125 11-40-8c-18-10-11
ping -l 480 -t 192.168.0.125
Step 4: Reboot the device.
Step 5: You can see the setup is OK if you can see there are
output information such as “Reply from 192.168.0.125 …” from
the command output lines. Now you can close the command
line.
Step 6: Open the browse and then input http://<IP address>.
Click the Enter button, you can access now.
5.2.2 Port
5.2.2.1
The Port interface is shown as in Figure 5-24.
Port
Page 49

42
Figure 5-24
Please refer to the following sheet for detailed information.
Parameter Function
Max
connection
TCP port Port range is 1025~65534. The default value is 37777. You can input the
UDP port Port range is 1025~65534. The default value is 37778. You can input the
HTTP port Port range is 1025~65524. The default value is 80. You can input the
It is the max Web connection for the same device. The value ranges from 1
to 20. Default connection amount is 10.
actual port number if necessary.
actual port number if necessary.
actual port number if necessary.
Page 50

43
RTSP port The default value is 554. Please leave blank if use default. User uses
QuickTime or VLC can play the following formats. BlackBerry can play
too.
Real-time monitoring URL format, please require real-time RTSP
media server, require channel no., bit stream type in URL. You may
need username and password.
User uses BlackBerry need to set encode mode to H.264B, resolution
to CIF and turn off audio.
URL format is:
rtsp://username:password@ip:port/cam/realmonitor?channel=1&subtype=0
Username/password/IP and port.
The IP is device IP and the port default value is 554. You can leave it in
blank if it is the default value.
Follow standard RTP protocol and when encode mode is MJPEG, the max
resolution only supports 2040*2040.
HTTPs
Port
Note:
0~1024, 37780~37880, 1900, 3800, 5000, 5050, 9999, 37776, 39999, 42323 are all special ports.
User cannot modify them.
Avoid using default port value of other ports.
5.2.2.2
ONVIF(Open Network Video Interface Forum),this standard describes network video mode,
interface, data type and data interaction mode. ONVIF Standard’s aim is to achieve a network video
frame agreement and makes the network video products (including video front-end, video equipment,
etc.) from different manufacturers completely compatible.
ONVIF function is on by default.
ONVIF
HTTPs communication port, range is 1025~65534, default is 443.
Page 51

44
Figure 5-25
5.2.3 PPPoE
The PPPoE interface is shown as in Figure 5-26.
Enter the PPPoE username and password which are provided by ISP (Internet Service Provider), and
click “Enable”. The network camera will automatically establish network connection in the mode of
PPPoE after it is enabled, after it is successful, the IP of the “IP Address” will be automatically modified
into the dynamic IP address of the acquired WAN.
Note:
After PPPoE dial-up is successful, it needs to log in the device via the IP which is set before dial-up; in
the PPPoE setup interface, it will display the registered IP address, and then it can visit the IP address
via client.
Please disable UPnP when clicking PPPoE enable, which is to avoid causing influence to PPPoE dialup.
Figure 5-26
Page 52

45
5.2.4 DDNS
The DDNS interface is shown as in Figure 5-27.
The DDNS is to set to connect the various servers so that you can access the system via the server.
Please go to the corresponding service website to apply a domain name and then access the system
via the domain. It works even your IP address has changed. When the device connects to WLAN, you
should disable UPnP.
Figure 5-27
Please refer to the following sheet for detailed information.
Parameter Function
Server Type Click it to select DDNS protocol type, which includes: CN99
DDNS, NO-IP DDNS, Dyndns DDNS, Quick DDNS, the default is
Quick DDNS.
Server Address DDNS server IP address
CN99 DDNS
Server address: www.3322.org
NO-IP DDNS
Server address: dynupdate.no-ip.com
Dyndns DDNS
Server address: members.dyndns.org
Quick DDNS
Server address: www.quickddns.com
Mode Default is auto, it can select manual
Page 53

46
Parameter Function
Domain Name Both auto and manual are “MAC addresss.quickddns.com” by
default, it is able to set prefix manually.
Username The user name you input to log in the server, optional.
The CN99 DDNS interface is shown as in Figure 5-28.
Figure 5-28
Parameter Function
Server Type You can select CN99 DDNS protocol
Server Address Under CN99 DDNS, the default server address is “www. 3322. org”.
Domain Name Self-defined domain name
Username The user name you input to log in the server.
Password The password you input to log in the server
Refresh Period
The refresh period of the connection between the device IP and the server, default
is 10 minutes.
5.2.5 IP filter
The IP filter interface is shown as in Figure 5-29.
You can enable IP filter function so that some specified IP/MAC user can access the network camera.
You can add IP address or IP segment.
If you do not check the box here, it means there is on access limit.
Page 54

47
Here you can add IP address and MAC address. You must add these addresses before enabling the
trusted sites.
Please note: You must set MAC address in the same network segment.
Figure 5-29
5.2.6 SMTP (e-mail)
The SMTP interface is shown as in Figure 5-30.
Figure 5-30
Please refer to the following sheet for detailed information.
Page 55

48
load for the email server.
the email setup information.
Parameter Function
SMTP Server
Port Default value is 25. You can modify it if necessary.
Anonymity For the server which supports the anonymity email function, it
Input server address and then enable this function.
won’t display the information of the sender.
User Name
Password
Sender
Authentication
(Encryption
mode)
Title (Subject)
Attachment
Mail receiver
Interval
The user name of the sender email account.
The password of sender email account.
Sender email address.
You can select SSL, TLS or none.
Input email subject here.
System can send out the email of the snapshot picture once
you check the box here.
Input receiver email address here. Max three addresses.
The send interval ranges from 0 to 3600 seconds. 0 means
there is no interval.
Please note system will not send out the email immediately
when the alarm occurs. When the alarm, motion detection or
the abnormity event activates the email, system sends out the
email according to the interval you specified here. This
function is very useful when there are too many emails
activated by the abnormity events, which may result in heavy
Health mail
enable
Email test
5.2.7 UPnP
It allows you to establish the mapping relationship between the LAN and the public network.
Here you can also add, modify or remove UPnP item. For UPnP on different routers, you must disable
UPnP function. See Figure 5-31.
In the Windows OS, From Start->Control Panel->Add or remove programs. Click the “Add/Remove
Windows Components” and then select the “Network Services” from the Windows Components Wizard.
Click the Details button and then check the “Internet Gateway Device Discovery and Control client” and
“UPnP User Interface”. Please click OK to begin installation.
Please check the box here to enable this function.
The system will automatically sent out a email once to test the
connection is OK or not .Before the email test, please save
Page 56

49
Enable UPnP from the Web. If your UPnP is enabled in the Windows OS, the network camera can auto
detect it via the “My Network Places”.
Under manual mode, you can modify external port. Under auto mode, select idle port for auto port
mapping without user modification.
Figure 5-31
5.2.8 SNMP
The SNMP interface is shown as in Figure 5-32 and Figure 5-33.
The SNMP allows the communication between the network management work station software and the
proxy of the managed device. Please install the software such as MG MibBrowser 8.0c software or
establish the SNMP service before you use this function. You need to reboot the device to activate the
new setup.
Figure 5-32
Please refer to the following sheet for detailed information.
Page 57

50
Note: Only number, letter, _, and – supported.
Note: Only number, letter, _, and – supported.
event notice or status change.
1~65535.
Parameter Function
SNMP Version Check SNMP v1, device only process v1 info.
Check SNMP v2, device only process v2 info.
Check SNMP v3, can set username, password and
SNMP port The listening port of the proxy program of the device. It is a
UDP port not a TCP port. The value ranges from 1 to 65535.
The default value is 161
Community It is a string, as command between management and proxy, ,
defining a proxy, and a manager’s authentication.
encryption method. Server calibrate corresponding
username, password and encryption method too access
device and v1/v2 are unavailable.
Read community
Write community
Trap address
Trap
Trap Address
Trap Port
Read-only access to all SNMP targets, default is public.
Read/write access to all SNMP targets, default is private.
The destination address of the Trap information from the
proxy program of the device.
SNMP trap is a proxy message sent to admin as important
Address where to send Trap message.
Port which send Trap message, default is 162, range
Figure 5-33
Page 58

51
Name only can be number, letter and underline.
Name only can be number, letter and underline.
Check SNMP v3 version and SNMP port, read community, write community, Trap address, Trap port
are same with SNMP v1 and SNMP v2 versions. Only when SNMP version is SNMP v3, users need to
configure parameter in chart.
Parameter Function
SNMP Version SNMP v3
Read-only
Username
Default is public.
Note:
Read/Write
Username
Authentication You may select MD5 or SHA, default is MD5.
Authentication
Password
Encryption Default is CBC-DES.
Encryption
Password
Default is private.
Note:
Password not less than 8 characters.
Password not less than 8 characters.
5.2.9 Bonjour
The Bonjour interface is shown as below. See Figure 5-34.
Bonjour is based on the multicast DNS service from the Apple. The Bonjour device can automatically
broadcast its service information and listen to the service information from other device.
You can use the browse of the Bonjour service in the same LAN to search the network camera device
and then access if you do not know the network camera information such as IP address.
You can view the server name when the network camera is detected by the Bonjour. Please note the
safari browse support this function. Click the “Display All Bookmarks: and open the Bonjour, system can
auto detect the network camera of the Bonjour function in the LAN.
Page 59

52
Figure 5-34
5.2.10 Multicast
The multicast interface is shown as in Figure 5-35.
Multicast is a transmission mode of data packet. When there is multiple-host to receive the same data
packet, multiple-cast is the best option to reduce the broad width and the CPU load. The source host
can just send out one data to transit. This function also depends on the relationship of the group
member and group of the outer.
Note:
Open preview, streaming media protocol, select multicast, and monitor via multicast format.
Here you can set multicast address and port. You also need to go to Live interface to set the
protocol as Multicast.
Figure 5-35
Please refer to the following sheet for detailed information.
Parameter Function
Enable Select to enable multicast function. Main stream and sub stream cannot be
used at the same time.
Multicast address Main/sub stream multicast default address is 224.1.2.4 and its range is
224.0.0.0~239.255.255.255.
Port Multicast port. Main stream is 40000, sub stream1 is 40016,sub stream2 is
40032 and the range is 1025~65534.
Page 60

53
5.2.11 802.1x
802.1x (port based network access control protocol) supports manual selection of authentication
method to control if device connected to LAN can join the LAN. It well supports authentication, charging,
safety and management requirement of network.
Figure 5-36
Please refer to the following sheet for detailed information.
Parameter Function
Authentication PEAP (protected EAP protocol).
Username It needs the username to login, which is authenticated by the
server.
Password Please input password here.
5.2.12 QoS
The QoS interface is shown as below. See Figure 5-37.
Qos (Quality of Service) is network security mechanism. It is a technology to fix the network delay and
jam problem and etc. For the network service, the quality of service includes the transmission bandwidth,
delay, the packet loss and etc. We can guarantee the transmission bandwidth, lower the delay, and
reduce the loss of the data packet and anti-dither to enhance the quality.
We can set the DSCP (Differentiated Services Code Point) of the IP to distinguish the data packet so
that the router or the hub can provide different services for various data packets. It can select the
different queues according to the priority (64 different priority levels) of the packets and select the
bandwidth of the each queue. Level 0 is the lowest, and level 63 is the highest. It can also discard at the
different ratio when the broad bandwidth is jam.
Page 61

54
Figure 3-37
Please refer to the following sheet for detailed information.
Parameter Function
Real-time
monitor
Command The value ranges from 0 to 63. The router or the switcher can
Enable
Wireless QoS
The value ranges from 0 to 63. The router or the switcher can
provide different service for various data packets.
provide different service for various data packets.
Check it to enable QoS.
5.2.13 HTTPs
In the HTTPs setting interface, users can make PC log in normally via HTTPs by creating certificate or
uploading signed certificate, which is to guarantee the security of communication data and provide
safeguard for user information and device security with reliable and stable technical means.
Step 1
Create certificate or upload the signed certificate.
Please refer to the following steps if you select “Create Certificate”.
1. Select “Setup > Network > HTTPs”, and the system will display the interface of HTTPs, which is
shown in Figure 5-38.
Page 62

55
2. Click “Create” and it will pop out the dialog box of “HTTPs”, which is shown in Figure 5-39.
Figure 5-38
Figure 5-39
3. Fill in corresponding “Country”, “Province” and some other information, click “Create” after filling in.
It will show the prompt of “Create Successfully”, which means the server certificate has been
successfully created.
Page 63

56
Note:
Make sure the “IP or domain name” is the same as that of the device.
4. Click “Install” and it will install the certificate on the device end.
5. Click “Download”. It will pop out the dialog box of “Save as”, save the file into the computer.
Figure 5-40
6. Double click the downloaded icon of “RootCert.cer”. The system will display the information
interface of “Certificate”, which is shown in Figure 5-41.
Page 64

57
Figure 5-41
7. Click “Install Certificate” and it will pop out the interface of “Certificate Import Wizard”, which is
shown in Figure 5-42.
Page 65

58
Figure 5-42
8. Click “Next”. Select “Trusted Root Certification Authorities”, which is shown in Figure 5-43.
Page 66

59
Figure 5-43
9. Click “Next”. The system will display the interface of “Completing the Certificate Import Wizard”,
which is shown in Figure 5-44.
Page 67

60
Figure 5-44
10. Click “Finish”, and it will pop out the dialog box of “Security Warning”, which is shown in Figure 5-45.
Page 68

61
Figure 5-45
11. Click “Yes”. It will pop out the dialog box of “Import Successful”, click “Ok” to complete downloading
certificate, which is shown in Figure 5-46.
Figure 5-46
Please refer to the following steps if you select “Install Signed Certificate”.
1. Select “Setup > Network > HTTPs”. The system will display the interface of HTTPs, which is shown
in Figure 5-47.
Page 69

62
2. Select signed certificate and certificate key path respectively via “Browse”, click “Upload”.
3. Install root certificate, please refer to step 6~11 for more details.
4. Check “Enable HTTPs”, click “Save”. The system will display the dialog box of “Need to reboot the
device”, and then the config is valid.
Figure 5-47
Figure 5-48
5. Use HTTPs
Use HTTPs to log in.
Enter https://xx.xx.xx.xx in the browser, and it will pop out normal login interface; the browser will prompt
certificate error if the certificate is not installed, which is shown in Figure 5-49.
Page 70

63
Note:
“xx.xx.xx.xx” is corresponding to your IP or domain name.
Figure 5-49
5.3 Event
5.3.1 Video detection
5.3.1.1 Motion Detection
Step 1
Select “Setup > Event > Video Detection > Motion Detection’ and the system will display the interface of
“Motion Detection” which is shown in Figure 5-50.
Figure 5-50
Step 2
Page 71

64
Select “Enable” to enable motion detection function.
Step 3
Set motion detection area.
1. Click “Setup” and the system will pop out the interface of “Setting Area”, which is shown in Figure 5-
51
Figure 5-51
2. Set area name, it is to set valid area of motion detection according to the actual situation, and it can
set the value of sensitivity and threshold respectively.
The bigger the sensitivity is, the easier it is to generate motion detection, the smaller the threshold is,
the easier it is to generate motion detection; the entire video image is the valid area of motion
detection by default.
Note:
Different colors represent different areas; each area can set different detection area.
The red line in the Oscillogram means triggering motion detection; green line means not triggering
motion detection.
3. Click “Save” to complete area setting.
Step 4
It is to set other parameters of motion detection, please refer to the following sheet for more details.
Page 72

65
3. Click “Save” to complete the setup of working period.
ranges from 0s to 100s.
3. Click “Save” to complete area setup.
interface.
System can delay the alarm output for specified time after alarm ended. The
value ranges from 10s to 300s.
alarm occurs and ends. User can set email address in Network>SMTP.
will play alarm audio file when alarm occurs. Users
>
alarm audio”.
Parameter Function
Working Period
Note:
It is to set the alarm period, it can enable alarm event only during the
period range which has been set.
1. Click “Setup” and the system will pop out the interface of “Working
Period”.
2. It is to set working period according to the following methods:
You can input time numerical value or press the left mouse button to
drag on the setup interface to set.
There are six periods to be set every day, select the check box in front
of the period, and then the period is valid.
Select week number (it selects Sunday by default, if it selects the
whole week, then it means the setup can be applied to the whole
week, you can also select the check box in front of the week number
to implement independent setting for some days).
Anti-dither
Area
Record
Record Delay System can delay the record for specified time after alarm ended. The
Relay out Enable alarm activation function. You need to select alarm output port so
Alarm Delay
System only memorizes one event during the anti-dither period. The value
1. Click “Setup” and the system will pop out the interface of “Set Area”.
2. Set the area name, it is to set the valid area of motion detection
according to the actual situation, and it can set its sensitivity and
threshold respectively. The higher the sensitivity is, the easier it is to
trigger motion detect, the smaller the area threshold is, the easier it is
to generate motion detect, the whole video image is the valid area of
the motion detect by default.
Note:
Different colors represent different areas; each area can set different
detection areas.
The red line in the Oscillogram means triggering motion detect, the green
line means not triggering motion detect.
Check it and so when alarm occurs, system will auto record. You shall set
record period in Storage>Schedule and select auto record in record control
value ranges from 10s to 300s.
that system can activate corresponding alarm device when alarm occurs.
Send Email
Audio linkage
If you enabled this function, System can send out email to alert you when
Check it and the system
can set the recorded or uploaded audio file in “camera setting > audio
Page 73

66
be off until the end of alarm after corresponding delay.
The event type includes: preset, tour and pattern.
You need to check the box here so that system can backup motion detection
snapshot file. You shall set snapshot period in Storage>Schedule.
Parameter Function
Flash linkage
Check it and the flash will be on when alarm occurs, and the flash will
PTZ
Snapshot
Here you can set PTZ movement when alarm occurs. Such as go to
preset x when there is an alarm.
Step 5
Click “Save” to complete the setting of motion detection.
5.3.1.2 Video Tampering
Step 1
Select “Setup > Event > Video Detection > Video Tampering” and the system will display the interface of
“Video Tampering” which is shown in Figure 5-52.
Figure 5-52
Step 2
Set the parameter of video tampering; please refer to the following sheet for more details.
Parameter Function
Enable video
tampering
Enable defocus
detection
You need to check the box to enable video mask detection alarm.
You need to check the box to enable defocus detection alarm.
Page 74

67
3. Click “Save” to complete the setup of working period.
interface.
m can delay the alarm output for specified time after alarm ended. The
value ranges from 10s to 300s.
alarm occurs and ends. User can set email address in Network>SMTP.
Check it and the system will play alarm audio file when alarm occurs. Users
>
alarm audio”.
be off until the end of alarm after corresponding delay.
The event type includes: preset, tour and pattern.
You need to check the box here so that system can backup motion detection
snapshot file. You shall set snapshot period in Storage>Schedule.
Parameter Function
Working Period
Note:
It is to set the alarm period, it can enable alarm event only during the
period range which has been set.
1. Click “Setup” and the system will pop out the interface of “Working
Period”.
2. It is to set working period according to the following methods:
You can input time numerical value or press the left mouse button to
drag on the setup interface to set.
There are six periods to be set every day, select the check box in front
of the period, and then the period is valid.
Select week number (it selects Sunday by default, if it selects the
whole week, then it means the setup can be applied to the whole
week, you can also select the check box in front of the week number
to implement independent setting for some days).
Record
Record Delay System can delay the record for specified time after alarm ended. The
Relay out Enable alarm activation function. You need to select alarm output port so
Alarm Delay
Send Email
Audio linkage
Flash linkage
PTZ
Snapshot
Step 3
Click “Save” to complete the setup of video tampering.
5.3.1.3 Scene Changing
Step 1
Select “Setup > Event > Video Detection > Scene Changing” and the system will display the interface of
“Scene Changing” which is shown in Figure 5-53.
Check it and so when alarm occurs, system will auto record. You shall set
record period in Storage>Schedule and select auto record in record control
value ranges from 10s to 300s.
that system can activate corresponding alarm device when alarm occurs.
Syste
If you enabled this function, System can send out email to alert you when
can set the recorded or uploaded audio file in “camera setting > audio
Check it and the flash will be on when alarm occurs, and the flash will
Here you can set PTZ movement when alarm occurs. Such as go to
preset x when there is an alarm.
Page 75

68
3. Click “Save” to complete the setup of working period.
interface.
System can delay the alarm output for specified time after alarm ended. The
value ranges from 10s to 300s.
alarm occurs and ends. User can set email address in Network>SMTP.
Step 2
Check “Enable” to enable the function of scene changing.
Step 3
It is to set the parameters of scene changing, please refer to the following sheet for more details.
Parameter Function
Working Period
Note:
It is to set the alarm period, it can enable alarm event only during the
period range which has been set.
1. Click “Setup” and the system will pop out the interface of “Working
Period”.
2. It is to set working period according to the following methods:
You can input time numerical value or press the left mouse button to
drag on the setup interface to set.
There are six periods to be set every day, select the check box in front
of the period, and then the period is valid.
Select week number (it selects Sunday by default, if it selects the
whole week, then it means the setup can be applied to the whole
week, you can also select the check box in front of the week number
to implement independent setting for some days).
Figure 5-53
Record
Record Delay System can delay the record for specified time after alarm ended. The
Relay out Enable alarm activation function. You need to select alarm output port so
Alarm Delay
Send Email
Check it and so when alarm occurs, system will auto record. You shall set
record period in Storage>Schedule and select auto record in record control
value ranges from 10s to 300s.
that system can activate corresponding alarm device when alarm occurs.
If you enabled this function, System can send out email to alert you when
Page 76

69
The event type includes: preset, tour and pattern.
You need to check the box here so that system can backup motion detection
snapshot file. You shall set snapshot period in Storage>Schedule.
Parameter Function
PTZ
Snapshot
Step 4
Click “Save” to complete the setup of scene changing.
Here you can set PTZ movement when alarm occurs. Such as go to
preset x when there is an alarm.
5.3.2 Audio Detection
Step 1
Select “Setup > Event > Audio Detection” and the system will display the interface of “Audio Detection”
which is shown in Figure 5-54.
Figure 5-54
Step 2
It is to set the parameters of audio detect, please refer to the following sheet for more details.
Parameter Function
Enable input
abnormal
Enable intensity
change
Select “Enable Input Abnormal” and it will trigger alarm when it detects
audio input abnormity.
Select “Enable Intensity Change” and it will trigger alarm when it detects
that audio intensity change exceeds the threshold.
Page 77

70
3. Click “Save” to complete the setup of working period.
ranges from 0s to 100s.
interface.
System can delay the alarm output for specified time after alarm ended. The
value ranges from 10s to 300s.
alarm occurs and ends. User can set email address in Network>SMTP.
The event type includes: preset, tour and pattern.
can backup motion detection
snapshot file. You shall set snapshot period in Storage>Schedule.
Parameter Function
Sensitivity It can be judged as audio abnormity when the input volume change
exceeds continuous environment volume; users need to adjust according
to the actual environment test.
Threshold It is to set the filtered environment volume intensity, if the environmental
noise is too big, then the value needs to be set higher, users can adjust
according to the actual environment test.
Working Period
Note:
It is to set the alarm period, it can enable alarm event only during the
period range which has been set.
1. Click “Setup” and the system will pop out the interface of “Working
Period”.
2. It is to set working period according to the following methods:
You can input time numerical value or press the left mouse button to
drag on the setup interface to set.
There are six periods to be set every day, select the check box in front
of the period, and then the period is valid.
Select week number (it selects Sunday by default, if it selects the
whole week, then it means the setup can be applied to the whole
week, you can also select the check box in front of the week number
to implement independent setting for some days).
Anti-dither
Record
Record Delay System can delay the record for specified time after alarm ended. The
Relay out Enable alarm activation function. You need to select alarm output port so
Alarm Delay
Send Email
PTZ
Snapshot
System only memorizes one event during the anti-dither period. The value
Check it and so when alarm occurs, system will auto record. You shall set
record period in Storage>Schedule and select auto record in record control
value ranges from 10s to 300s.
that system can activate corresponding alarm device when alarm occurs.
If you enabled this function, System can send out email to alert you when
Here you can set PTZ movement when alarm occurs. Such as go to
preset x when there is an alarm.
You need to check the box here so that system
Step 3
Click “Save” to complete the setup of audio detection.
Page 78

71
5.3.3 Smart Plan
Smart plan is the master switch for intelligent analysis such as “Face Detection”, “Heat Map”, “IVS”,
“People Counting” and so on, the corresponding intelligent functions can be valid after smart plan is
enabled.
Step 1
Select “Setup > Event > Smart Plan”. The system will display the interface of “Smart Plan”, which is
shown in Figure 5-55.
Figure 5-55
Step 2
Click “Save” to complete the config of smart plan.
5.3.4 Intelligence Behavior Analytics
The basic requirements of scene selection
The total proportion of the target shall not exceed 10% of the image.
The target size in the image can’t be less than 10 pixel ×10 pixel, the size of abandoned target can’t
be less than 15 pixel × 15 pixel (CIF image); The height and width of the target can’t exceed 1/3 of
the image; it is recommended that the target height is about 10% of the image height.
The difference of brightness value between target and background can’t be less than 10 gray levels.
Make sure the target appears at least over 2 seconds continuously in the field; the movement
distance has to be bigger than the width of the target itself and makes sure it is no less than 15
pixels (CIF image).
Try to lower the complexity of the monitoring scene analysis if it is possible; it is not advised to use
IVS functions in the environment where the targets are dense and light change is very frequent.
Try to keep away from the areas such as glass, ground reflected light, water surface, branch,
shadow, mosquito disturbance and etc.; try to keep away from the backlight scene to avoid direct
light.
5.3.4.1 IVS
Page 79

72
5.3.4.1.1 Tripwire
It will trigger alarm when the target crosses the warning line according to the movement direction which
has been set.
It needs some time from when the target appears to when the target is confirmed, so it has to leave
some space on both sides of the warning line when setting the warning line, please do not set the
warning line near the obstructions.
Application scene: it can be applied to the scene with sparse target and there is barely any blocks
between the targets, such as the unmanned perimeter defense.
Step 1
Select “Setup > Event > IVS > IVS” and the system will display the interface of “IVS”.
Step 2
Click “ ” to set rule name and select the rule type as “Tripwire” which is shown in Figure 5-56.
Figure 5-56
Step 3
Click “Draw Rule” to draw tripwire in the monitoring scene, click the right mouse button to complete
tripwire setting.
Step 4
Click “Draw Target” to draw the size model of filtered target in the video image.
Step 5
It is to set the parameters of tripwire, please refer to the following sheet for more details.
Page 80

73
3. Click “Save” to complete the setup of working period.
for more details.
Parameter Function
Object tracking Select “Object tracking” to enable the function, refer to “2.4 Video Window
Adjustment” for more details.
Note:
The function is only supported by some models.
Working Period
Note:
It is to set the alarm period, it can enable alarm event only during the period
range which has been set.
1. Click “Setup” and the system will pop out the interface of “Working
Period”.
2. It is to set working period according to the following methods:
You can input time numerical value or press the left mouse button to
drag on the setup interface to set.
There are six periods to be set every day, select the check box in front
of the period, and then the period is valid.
Select week number (it selects Sunday by default, if it selects the whole
week, then it means the setup can be applied to the whole week, you
can also select the check box in front of the week number to implement
independent setting for some days).
Direction
Object Track
Record
Record Delay System can delay the record for specified time after alarm ended.
Relay out Enable alarm activation function. You need to select alarm output port so
Alarm Delay
Send Email
Snapshot
Step 5
Click “Save” to complete the setup of tripwire.
It is to set the direction of tripwire, you can select A->B、B->A、A<->B.
Select “Object Track” and it will enable the function of object track; when the
moving object triggers rule and generates alarm, it will select the display
mode of object track such as 1P+3 or 1P+5 in the preview interface, the
scene of tracking window will follow the moving object till the object leaves
the view range of the camera. Please refer to “2.4.8 Fisheye/Trigger Track”
Check it and so when alarm occurs, system will auto record.
that system can activate corresponding alarm device when alarm occurs.
System can delay the alarm output for specified time after alarm ended.
If you enabled this function, System can send out email to alert you when
alarm occurs and ends. User can set email address in Network>SMTP.
Select “Snapshot” and the system will auto trigger alarm and snapshot when
alarm occurs.
5.3.4.2 Intrusion
Intrusion includes cross and appears.
Page 81

74
Cross means that it will trigger alarm when the target enters or exits the area.
Appears means that it will trigger alarm when the target appears in the area.
As for the report interval of the IVS function in the area, the system will trigger an alarm if it detects
same event happened during the interval; the alarm counter will become zero if there is no same
event happened in the interval.
It needs to leave some space for target movement for the area periphery if it is to detect enter & exit
event, which is similar to the warning line.
Application scene; it can be applied to the scene where the target is sparse and there is barely any
obstruction between the targets, such as the unmanned perimeter defense.
Step 1
Select “Setup > Event > IVS > IVS” and the system will display the interface of “IVS”.
Step 2
Click “ ” to set rule name, select the rule type as “Intrusion” which is shown in Figure 5-57.
Figure 5-57
Step 3
Click “Draw Rule” to draw an area in the monitoring image.
Step 4
Click “Draw Target” to draw the size model of filtered target in the video image.
Step 5
It is to set the parameters of intrusion, please refer the following sheet for more details.
Page 82

75
3. Click “Save” to complete the setup of working period.
enter&exit.
for more details.
Parameter Function
Object tracking Select “Object tracking” to enable the function, refer to “2.4 Video Window
Adjustment” for more details.
Note:
The function is only supported by some models.
Working Period
Note:
It is to set the alarm period, it can enable alarm event only during the period
range which has been set.
1. Click “Setup” and the system will pop out the interface of “Working
Period”.
2. It is to set working period according to the following methods:
You can input time numerical value or press the left mouse button to
drag on the setup interface to set.
There are six periods to be set every day, select the check box in front
of the period, and then the period is valid.
Select week number (it selects Sunday by default, if it selects the whole
week, then it means the setup can be applied to the whole week, you
can also select the check box in front of the week number to implement
independent setting for some days).
Action
Direction
Object Track
Record
Record Delay System can delay the record for specified time after alarm ended.
Relay out Enable alarm activation function. You need to select alarm output port so
Alarm Delay
Send Email
Snapshot
It is to set the action of intrusion, you can select appears and cross.
It is to set the direction of intrusion, you can select enter, exit and
Select “Object Track” and it will enable the function of object track; when the
moving object triggers rule and generates alarm, it will select the display
mode of object track such as 1P+3 or 1P+5 in the preview interface, the
scene of tracking window will follow the moving object till the object leaves
the view range of the camera. Please refer to “2.4.8 Fisheye/Trigger Track”
Check it and so when alarm occurs, system will auto record.
that system can activate corresponding alarm device when alarm occurs.
System can delay the alarm output for specified time after alarm ended.
If you enabled this function, System can send out email to alert you when
alarm occurs and ends. User can set email address in Network>SMTP.
Select “Snapshot” and the system will auto trigger alarm and snapshot when
alarm occurs.
Step 5
Click “Save” to complete the setup of intrusion.
Page 83

76
5.3.4.3 Abandoned Object
Abandoned object means the system will trigger alarm if the abandoned object in the monitoring scene
exceeds the time which has been set by the users.
Abandoned object and missing object can be confusing in a situation where both foreground and
background are complicated.
It also triggers alarm as abandoned object if there is pedestrian or vehicle staying still for too long. In
order to filter this kind of alarm, generally the abandoned object is smaller than people and vehicle;
therefore it can filter the people and vehicle via setting size. Besides, it can avoid the false alarm caused
by short stay of people via extending alarm time properly.
Application scene: It can be applied to the scene where the target is sparse and there is no obvious and
frequent light change. False alarm will be increased in the scene with high target density and frequent
blocking; false alarm will be increased in the scene where there are more people staying. As for the
detection area, try to make it simple, the function is not suitable for the area which is too complicated.
Step 1
Select “Setup > Event > IVS > IVS” and the system will display the interface of “IVS”.
Step 2
Click “ ” to set rule name, select the rule type as “Abandoned Object” which is shown in Figure 5-58.
Figure 5-58
Step 3
Click “Draw Rule” to draw an area in the monitoring area.
Step 4
Click “Draw Target” to draw the size model of filtered target in the video image.
Step 5
It is to set the parameter of abandoned object, please refer to the following sheet for more details.
Page 84

77
3. Click “Save” to complete the setup of working period.
triggers alarm.
Parameter Function
Working Period
Note:
It is to set the alarm period, it can enable alarm event only during the period
range which has been set.
1. Click “Setup” and the system will pop out the interface of “Working
Period”.
2. It is to set working period according to the following methods:
You can input time numerical value or press the left mouse button to
drag on the setup interface to set.
There are six periods to be set every day, select the check box in front
of the period, and then the period is valid.
Select week number (it selects Sunday by default, if it selects the whole
week, then it means the setup can be applied to the whole week, you
can also select the check box in front of the week number to implement
independent setting for some days).
Keep time
Record
Record Delay System can delay the record for specified time after alarm ended.
Relay out
Alarm Delay
Send Email
Snapshot
It is to set the shortest time from when the object is abandoned to when it
Check it and so when alarm occurs, system will auto record.
Enable alarm activation function. You need to select alarm output port so
that system can activate corresponding alarm device when alarm occurs.
System can delay the alarm output for specified time after alarm ended.
If you enabled this function, System can send out email to alert you when
alarm occurs and ends. User can set email address in Network>SMTP.
Select “Snapshot” and the system will auto trigger alarm and snapshot when
alarm occurs.
Step 5
Click “Save” to complete the setup of abandoned object.
5.3.4.4 Missing Object
Missing object means the system will trigger alarm if it exceeds certain amount of time after the target is
taken away from the original scene.
The system can make statistics of the still areas in the foreground area and distinguish if it is missing
object or abandoned object according to the similarity between foreground and background, it will
trigger alarm when it exceeds the time which is set by users.
Because the system distinguishes abandoned object from missing object according to the similarity of
foreground and background, it may cause error between abandoned object and missing object in a
situation where both foreground and background are complicated.
Page 85

78
Application scene: it can be applied to the scene where the target is sparse and there is no obvious and
frequent light change. False alarm will be increased in the scene where the target density is high and
there is frequent obstruction; the false alarm will be increased in the scene where there are more people
staying. As for the detection area, try to make it simple, the function is not suitable for the area which is
too complicated.
Step 1
Select “Setup > Event > IVS > IVS” and the system will display the interface of “IVS”.
Step 2
Click “ ” to set rule name and select rule type as “Missing Object”, which is shown in Figure 5-57
Figure 5-57
Step 3
Click “Draw Rule” to draw an area in the monitoring scene.
Step 4
Click “Draw Target” to draw the size model of filtered target in the video image.
Step 5
It is to set the parameters of missing object, please refer to the following sheet for more details.
Page 86

79
3. Click “Save” to complete the setup of working period.
triggers alarm.
Parameter Function
Working Period
Note:
It is to set the alarm period, it can enable alarm event only during the period
range which has been set.
1. Click “Setup” and the system will pop out the interface of “Working
Period”.
2. It is to set working period according to the following methods:
You can input time numerical value or press the left mouse button to
drag on the setup interface to set.
There are six periods to be set every day, select the check box in front
of the period, and then the period is valid.
Select week number (it selects Sunday by default, if it selects the whole
week, then it means the setup can be applied to the whole week, you
can also select the check box in front of the week number to implement
independent setting for some days).
Keep time
Record
Record Delay System can delay the record for specified time after alarm ended.
Relay out
Alarm Delay
Send Email
Snapshot
Step 5
Click “Save” to complete the setup of missing object.
It is to set the shortest time from when the object is missing to when it
Check it and so when alarm occurs, system will auto record.
Enable alarm activation function. You need to select alarm output port so
that system can activate corresponding alarm device when alarm occurs.
System can delay the alarm output for specified time after alarm ended.
If you enabled this function, System can send out email to alert you when
alarm occurs and ends. User can set email address in Network>SMTP.
Select “Snapshot” and the system will auto trigger alarm and snapshot when
alarm occurs.
5.3.5 Face Detection
Step 1
Select “Setup > Event > Face Detection” and the system will display the interface of “Face Detection”,
which is shown in Figure 5-58.
Page 87

80
3. Click “Save” to complete the setup of working period.
Step 2
Select “Enable” to enable face detection function.
Step 3
Click “Draw Target” to draw the size model of target filter in the video image.
Step 4
It is to set the parameters of face detection, please refer to the following sheet for more details.
Figure 5-58
Parameter Function
Working Period
Enable Face
Enhancement
Record
Note:
It is to set the alarm period, it can enable alarm event only during the period
range which has been set.
1. Click “Setup” and the system will pop out the interface of “Working
Period”.
2. It is to set working period according to the following methods:
You can input time numerical value or press the left mouse button to
drag on the setup interface to set.
There are six periods to be set every day, select the check box in front
of the period, and then the period is valid.
Select week number (it selects Sunday by default, if it selects the whole
week, then it means the setup can be applied to the whole week, you
can also select the check box in front of the week number to implement
independent setting for some days).
Select “Enable Face Enhancement” and it will guarantee that the face is
clear by priority when the stream is set very low.
Check it and so when alarm occurs, system will auto record.
Page 88

81
Parameter Function
Record Delay System can delay the record for specified time after alarm ended.
Relay out Enable alarm activation function. You need to select alarm output port so
that system can activate corresponding alarm device when alarm occurs.
Alarm Delay
Send Email
Snapshot
Step 5
Click “Save” to complete the setup of face detection.
System can delay the alarm output for specified time after alarm ended.
If you enabled this function, System can send out email to alert you when
alarm occurs and ends. User can set email address in Network>SMTP.
Select “Snapshot” and the system will auto trigger alarm and snapshot when
alarm occurs.
5.3.6 Alarm
5.3.6.1 Alarm
Figure 5-59
Parameter Function
Enable Check it and enable the alarm linkage.
Relay-in
Sensor Type
The default alarm 1,some products can choose alarm 2.
Two types of sensor which are normally open (NO) and normally closed (NC),
switch from normally open to normally closed, open the alarm. Switch from normally
closed to normally open, shut the alarm.
Page 89

82
5.3.7 Abnormity
Abnormity includes No SD Card, Capacity Warning, SD Card Error, Disconnection, IP Conflict and
Unauthorized Access.
Note:
Only device with SD card function has these three statuses: No SD card, capacity warning, and SD card
error. Device without SD card function does not have the above three statuses. See Figure 6-84 to
Figure 5-60.
Figure 5-60
Figure 5-61
Page 90

83
Figure 5-62
Please refer to the following sheet for detailed information.
Parameter Function
Enable
Check to alarm when SD card is abnormal.
Relay-out
Relay out
delay
Send
email
SD Card
Capacity
Limit
When device is offline or IP conflicts, the abnormal alarm is similar with case of SD card error.
Check to enable relay-out alarm.
The alarm output can delay for the specified time after alarm stops. The
value ranges from 10s to 300s.
Note:
No SD card, capacity warning, SD card error, relay-out delay all start
from alarm occurs.
After you enabled this function, the system can send out email to alarm
the specified user.
This function is invalid when network is offline or IP conflict occurs.
User can set SD card capacity that is left free. When SD card space left
is smaller than this limit, alarm occurs.
Page 91

84
Figure 5-63
When login password keep been wrong for a few times, unauthorized access alarm occurs. This
operation is similar to SD card error. Allow login error times as when it exceeds this limit, user account
will be locked.
Figure 5-64
5.4 Storage Management
5.4.1
Before schedule setup, user must set record mode is auto or manual.
Note:
If record mode in record control is off, then device will not snapshot according to schedule.
5.4.1.1 Record Schedule
Record schedule steps:
Step 1. Click on Record Schedule, see Figure 5-65.
Schedule
Page 92

85
Figure 5-65
Step 2. From Monday to Sunday select record time, click on setup on the right, see Figure 5-66.
Set period according to actual need. There are six periods available each day.
By checking or unchecking, you can add or delete three types of record schedule: General, Motion,
and Alarm.
Note:
Period setup can be done by dragging in record schedule interface while not releasing left mouse.
Figure 5-66
Step 3. Click on OK, return to record schedule interface. See Figure 5-67.
Green color stands for the general record/snapshot.
Yellow color stands for the motion detect record/snapshot.
Red color stands for the alarm record/snapshot.
Page 93

86
Figure 5-67
Step 4. In record schedule interface, click on OK. System prompts it is successfully saved.
5.4.1.2 Snapshot Schedule
Snapshot setup as:
Step 1. Click on Snapshot Schedule tab, see Figure 5-68.
Figure 5-68
Step 2. From Monday to Sunday select snapshot time, click on setup on the right. See Figure 5-68.
Set snapshot period according to actual need. There are six periods available each day.
Page 94

87
By checking or unchecking, user can add or delete three types of snapshot schedule: General,
Motion and Alarm.
Note: Period setup can be done by dragging in snapshot schedule interface while not releasing left
mouse.
Figure 5-69
Step 3. Click on OK, return to snapshot schedule interface. See Figure 5-70.
Green color stands for the general record/snapshot.
Yellow color stands for the motion detect record/snapshot.
Red color stands for the alarm record/snapshot.
Figure 5-70
Step 5. In snapshot interface, click on OK. System prompts it is successfully saved.
Page 95

88
5.4.1.3 Holiday Schedule
Holiday schedule can set specific date as holiday.
Step 1. Click on Holiday Schedule tab, see Figure 5-71.
Figure 5-71
Step 2. Select date to set as holiday. The selected date will be highlighted in yellow.
Step 3. Check Record/Snapshot, click on Save. System prompts it is successfully saved.
Step 4. Check Record Schedule/Snapshot Schedule interface, click on setup next to Holiday, and refer
to setup of Monday to Sunday.
Step 5. Complete setup of holiday, then it records/snapshots according to date in holiday schedule.
5.4.2 Destination
5.4.2.1 Path
The destination interface is shown as in Figure 5-72.
Path can config record and snapshot storage path. There are three options: Local, FTP and NAS. You
can only select one mode. System can save according to the event types. It is corresponding to the
three modes (general/motion/alarm) in the Schedule interface. Please check the box to enable the save
functions.
Note: Only device supports SD card has local.
Page 96

89
Figure 5-72
Please refer to the following sheet for detailed information.
Parameter Function
Event
Type
Local It saved in the SD card.
FTP It saved in the FTP server.
NAS It saved in NAS disk.
5.4.2.2 Local
The local interface is shown as in Figure 5-73.
Here you can view local Micro SD card or NAS disk information. You can also operate the read-only,
write-only, hot swap and format operation.
It includes: scheduled, motion detect and alarm.
Figure 5-73
5.4.2.3 FTP
The FTP interface is shown as in Figure 5-74.
Page 97

90
You need to check the box to enable the FTP function. When network disconnect occurred or there is
malfunction. Emergency storage can save the record/snapshot picture to the local SD card. Click the
test button to check if the FTP server can be connected for test.
Figure 5-74
5.4.2.4 NAS
You need to check the box to enable the NAS function. Select NAS storage, fill in NAS server address
and corresponding store path, then you can store video file or pictorial information in the NAS server.
See Figure 5-75.
Figure 5-75
Parameter Function
Server Address Set IP address of NAS server.
Remote
Directory
Set storage directory, videos and pictures can be stored in to corresponding server
directory.
5.4.3 Record control
The record control interface is shown as in Figure 5-76.
Page 98

91
previous file.
Figure 5-76
Please refer to the following sheet for detailed information.
Parameter Function
Pack
Duration
Pre-record Please input pre-record value here.
Disk Full
Here you can select file size within 1min~120min. Default setup is 8
minutes.
For example, system can record the four seconds video in the buffer.
The record begins from the fifth second.
Note:
Configure pre-record time, when alarm or motion detection occurs, if
there is no record, system will record the preceding n seconds
record.
There are two options: stop recording or overwrite the previous files
when HDD is full.
Stop: Current working HDD is overwriting or current HDD is full,
it will stop record.
Overwrite: Current working HDD is full; it will overwrite the
Record
mode
Record
stream
There are three modes: Auto/manual/close.
There are two options: main stream and sub stream.
5.5 System
5.5.1 General
The General interface is shown as in Figure 5-77.
Page 99

92
Figure 5-77
Please refer to the following sheet for detailed information.
Parameter Function
Device
Name
It is to set device name.
Note: Different devices have different names.
Video
Standard
Language You can select the language from the dropdown list.
TV Out You can open or close the function; it can only be supported by the
The date and time interface is shown as in Figure 5-78.
This is to display video standard such as PAL.
devices with TV Out.
Intelligent function will be disabled when TV Out is opened.
It will auto close TV Out when intelligent function is enabled.
Some devices support SDI and HDCVI.
Page 100

93
Figure 5-78
Please refer to the following sheet for detailed information.
Parameter Function
Date format
Here you can select date format from the dropdown list.
Time
Format
Time zone
Current
Time
Sync PC You can click this button to save the system time as your PC current
DST Enable Here you can set both begin and end time of daylight saving time.
Synchronize
with NTP
NTP server
Port
Update
period
There are two options: 24-H and 12-H.
The time zone of the device.
It is to set system time. It becomes valid after you set.
time.
You can set according to the date format or the week format.
You can check the box to enable NTP function.
You can set the time server address.
It is to set the time server port.
It is to set the sync periods between the device and the time server.
 Loading...
Loading...