Page 1

Oracle TimesTen
In-Memory Database
Installation Guide
Release 7.0
B31679-01
For last-minute updates, see the TimesTen release notes.
Page 2

Copyright ©1996, 2007, Oracle. All rights reserved.
ALL SOFTWARE AND DOCUMENTATION (WHETHER IN HARD
COPY OR ELECTRONIC FORM) ENCLOSED AND ON THE
COMPACT DISC(S) ARE SUBJECT TO THE LICENSE
AGREEMENT.
The documentation stored on the compact disc(s) may be printed by
licensee for licensee’s internal use only. Except for the foregoing, no
part of this documentation (whether in hard copy or electronic form)
may be reproduced or transmitted in any form by any means, electronic
or mechanical, including photocopying, recording, or any information
storage and retrieval system, without the prior written permission of
TimesTen Inc.
Oracle, JD Edwards, PeopleSoft, Retek, TimesTen, the TimesTen icon,
MicroLogging and Direct Data Access are trademarks or registered
trademarks of Oracle Corporation and/or its affiliates. Other names may
be trademarks of their respective owners.
The Programs (which include both the software and documentation)
contain proprietary information; they are provided under a license
agreement containing restrictions on use and disclosure and are also
protected by copyright, patent, and other intellectual and industrial
property laws. Reverse engineering, disassembly, or decompilation of
the Programs, except to the extent required to obtain interoperability
with other independently created software or as specified by law, is
prohibited.
The information contained in this document is subject to change without
notice. If you find any problems in the documentation, please report
them to us in writing. This document is not warranted to be error-free.
Except as may be expressly permitted in your license agreement for
these Programs, no part of these Programs may be reproduced or
transmitted in any form or by any means, electronic or mechanical, for
any purpose.
February 2007
Printed in the United States of America
Page 3

Contents
About this Guide
TimesTen documentation . . . . . . . . . . . . . . . . . . . . . 1
Background reading . . . . . . . . . . . . . . . . . . . . . . . 2
Conventions used in this guide . . . . . . . . . . . . . . . . . . . 3
Technical Support . . . . . . . . . . . . . . . . . . . . . . . . 5
1 Access Control
Introduction. . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Access Control . . . . . . . . . . . . . . . . . . . . . . . . 7
Limitations of Access Control and non-root installs . . . . . . . . . . . 7
General . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Cache Connect . . . . . . . . . . . . . . . . . . . . . . . . 8
Replication . . . . . . . . . . . . . . . . . . . . . . . . . 8
Client/Server . . . . . . . . . . . . . . . . . . . . . . . . . 8
Instance access . . . . . . . . . . . . . . . . . . . . . . . . . 8
Instance startup/shutdown. . . . . . . . . . . . . . . . . . . . 8
Instance data store. . . . . . . . . . . . . . . . . . . . . . . 9
TimesTen users . . . . . . . . . . . . . . . . . . . . . . . . . 9
TimesTen instance administrator . . . . . . . . . . . . . . . . . 9
TimesTen instance users . . . . . . . . . . . . . . . . . . . .10
Before installation . . . . . . . . . . . . . . . . . . . . . . . .11
TimesTen administrators group. . . . . . . . . . . . . . . . . . 11
Instance registry directory. . . . . . . . . . . . . . . . . . . .11
Installation directories, files and the daemon port . . . . . . . . . . . .12
Installation directories . . . . . . . . . . . . . . . . . . . . .12
Instance home directory . . . . . . . . . . . . . . . . . . . .12
Daemon home directory . . . . . . . . . . . . . . . . . . . .12
Password file. . . . . . . . . . . . . . . . . . . . . . . . .12
Daemon port . . . . . . . . . . . . . . . . . . . . . . . . .13
Authenticating users and privileges . . . . . . . . . . . . . . . . .13
Privileges . . . . . . . . . . . . . . . . . . . . . . . . . .13
GroupRestrict . . . . . . . . . . . . . . . . . . . . . . . .13
Maintaining users and privileges . . . . . . . . . . . . . . . . .14
Listing of defined users and privileges . . . . . . . . . . . . . . .14
Enabling Access Control after installation on UNIX . . . . . . . . . . .14
2 TimesTen Installation
Platforms and configurations . . . . . . . . . . . . . . . . . . . .19
iii
Page 4

Platform support . . . . . . . . . . . . . . . . . . . . . . . 19
JDK support. . . . . . . . . . . . . . . . . . . . . . . . . 20
Client/Server configurations . . . . . . . . . . . . . . . . . . 21
Cache Connect to Oracle . . . . . . . . . . . . . . . . . . . . 21
Replication configurations . . . . . . . . . . . . . . . . . . . 22
Installation instances . . . . . . . . . . . . . . . . . . . . . . . 23
Instance names. . . . . . . . . . . . . . . . . . . . . . . . 23
Instance port numbers . . . . . . . . . . . . . . . . . . . . . 23
Choosing the appropriate TimesTen components . . . . . . . . . . . . 24
Components available on Windows. . . . . . . . . . . . . . . . 24
Components available on UNIX . . . . . . . . . . . . . . . . . 24
Installation prerequisites . . . . . . . . . . . . . . . . . . . . . 25
UNIX requirements . . . . . . . . . . . . . . . . . . . . . . 25
Default installation directories. . . . . . . . . . . . . . . . . . 34
Cache Connect. . . . . . . . . . . . . . . . . . . . . . . . 35
Operating system security considerations . . . . . . . . . . . . . . . 35
Prerequisites for non-root installations
on UNIX systems. . . . . . . . . . . . . . . . . . . . . . . 37
Installation prerequisites for non-root installs . . . . . . . . . . . . 37
Create the TimesTen instance
administrators group . . . . . . . . . . . . . . . . . . . . . 37
Create the TimesTen registry . . . . . . . . . . . . . . . . . . 38
Post-installation requirements . . . . . . . . . . . . . . . . . . 38
Configure the syslog messages . . . . . . . . . . . . . . . . . 39
Changing the daemon port number on UNIX . . . . . . . . . . . . . 39
UNIX libraries . . . . . . . . . . . . . . . . . . . . . . . . . 39
Installing TimesTen on Windows systems. . . . . . . . . . . . . . . 40
Installing TimesTen . . . . . . . . . . . . . . . . . . . . . . 40
Installing TimesTen in silent mode . . . . . . . . . . . . . . . . 41
Verifying installation . . . . . . . . . . . . . . . . . . . . . 42
Verifying TimesTen Client and Server installation . . . . . . . . . . 42
Working with the Data Manager Service
and the Server . . . . . . . . . . . . . . . . . . . . . . . 43
Uninstalling TimesTen. . . . . . . . . . . . . . . . . . . . . 44
Installing TimesTen on Solaris systems. . . . . . . . . . . . . . . . 44
Installing TimesTen . . . . . . . . . . . . . . . . . . . . . . 45
Working with the daemon and Server . . . . . . . . . . . . . . . 48
Uninstalling TimesTen. . . . . . . . . . . . . . . . . . . . . 49
Installing TimesTen on HP-UX systems . . . . . . . . . . . . . . . 49
Installing TimesTen . . . . . . . . . . . . . . . . . . . . . . 49
Working with the TimesTen daemon and Server. . . . . . . . . . . 53
Uninstalling TimesTen. . . . . . . . . . . . . . . . . . . . . 54
iv Oracle TimesTen In-Memory Dat abase Installation Guide
Page 5

Installing TimesTen on HP-UX Memory Windows . . . . . . . . . . .54
Use a separate instance for each memory window . . . . . . . . . .54
Using TimesTen in a memory window . . . . . . . . . . . . . . .55
Address Space Considerations . . . . . . . . . . . . . . . . . .55
Troubleshooting. . . . . . . . . . . . . . . . . . . . . . . .56
Installing TimesTen on AIX systems . . . . . . . . . . . . . . . . .57
Installing TimesTen . . . . . . . . . . . . . . . . . . . . . .5 7
Working with the TimesTen daemon and server . . . . . . . . . . .61
Uninstalling TimesTen . . . . . . . . . . . . . . . . . . . . .6 1
Installing TimesTen on Linux systems . . . . . . . . . . . . . . . .62
Installing TimesTen . . . . . . . . . . . . . . . . . . . . . .6 2
Working with the TimesTen daemon and Server . . . . . . . . . . .65
Uninstalling TimesTen . . . . . . . . . . . . . . . . . . . . .6 5
Installing TimesTen on Tru64 UNIX systems . . . . . . . . . . . . .66
Installing TimesTen . . . . . . . . . . . . . . . . . . . . . .6 6
Working with the TimesTen daemon and Server . . . . . . . . . . .69
Uninstalling TimesTen . . . . . . . . . . . . . . . . . . . . .7 0
Using the Cache Administrator . . . . . . . . . . . . . . . . . . .7 0
Informational messages on Windows systems . . . . . . . . . . . . .71
Informational messages on UNIX systems. . . . . . . . . . . . . . .72
Incremental install and uninstall of Cache Connect . . . . . . . . . . .73
ODBC installation . . . . . . . . . . . . . . . . . . . . . . . .73
Environment modifications. . . . . . . . . . . . . . . . . . . . .74
PATH environment variable . . . . . . . . . . . . . . . . . . .75
ODBCINI environment variable . . . . . . . . . . . . . . . . .75
SYSODBCINI environment variable . . . . . . . . . . . . . . .76
SYSTTCONNECTINI environment variable . . . . . . . . . . . .76
CLASSPATH environment variable . . . . . . . . . . . . . . . .77
ORACLE_HOME environment variable . . . . . . . . . . . . . .77
Shared library path environment variable. . . . . . . . . . . . . .77
Web server configuration . . . . . . . . . . . . . . . . . . . . .79
Migrating data stores to TimesTen 7.0 . . . . . . . . . . . . . . . .80
Using the ttMigrate utility. . . . . . . . . . . . . . . . . . . .80
Using the ttBulkCp utility. . . . . . . . . . . . . . . . . . . .82
Building and running the demo applications . . . . . . . . . . . . . .8 3
Defining data sources for the demo applications . . . . . . . . . . .83
Building the demo applications. . . . . . . . . . . . . . . . . .84
Problems running the demo programs . . . . . . . . . . . . . . .84
Building and running the JDBC demo applications . . . . . . . . . .85
Viewing the online documentation . . . . . . . . . . . . . . . . . .85
Installation problems . . . . . . . . . . . . . . . . . . . . . . .86
Contents v
Page 6

3 Data Store Upgrades
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Data store compatibility . . . . . . . . . . . . . . . . . . . . 87
Data type compatibility . . . . . . . . . . . . . . . . . . . . 87
Data store character set . . . . . . . . . . . . . . . . . . . . 88
Data type conversion . . . . . . . . . . . . . . . . . . . . . . . 89
Converting data types to Oracle data types . . . . . . . . . . . . . 90
Upgrading data types as TimesTen data types . . . . . . . . . . . . 90
Data store character set conversion . . . . . . . . . . . . . . . . . 91
Converting from the TIMESTEN8 character set. . . . . . . . . . . 91
Converting from a character set
other than TIMESTEN8 . . . . . . . . . . . . . . . . . . . 92
Upgrade modes . . . . . . . . . . . . . . . . . . . . . . . . . 93
In-place upgrades. . . . . . . . . . . . . . . . . . . . . . . 93
Offline upgrades . . . . . . . . . . . . . . . . . . . . . . . 93
Online upgrades with replication. . . . . . . . . . . . . . . . . 94
Online upgrades with Client/Server. . . . . . . . . . . . . . . . 94
Performing an in-place data store upgrade . . . . . . . . . . . . . . 95
Unloading a data store . . . . . . . . . . . . . . . . . . . . . 95
Moving to a new patch release of TimesTen . . . . . . . . . . . . 96
Performing an offline upgrade . . . . . . . . . . . . . . . . . . . 97
Moving to a different directory . . . . . . . . . . . . . . . . . 98
Moving to a different machine. . . . . . . . . . . . . . . . . . 98
Reducing data store size . . . . . . . . . . . . . . . . . . . 100
Moving between 32-bit and 64-bit data stores. . . . . . . . . . . 101
Moving to a different major release of TimesTen . . . . . . . . . 101
Performing an online upgrade with replication . . . . . . . . . . . . 104
Overview . . . . . . . . . . . . . . . . . . . . . . . . . 104
Limitations . . . . . . . . . . . . . . . . . . . . . . . . 107
Requirements . . . . . . . . . . . . . . . . . . . . . . . 107
Online upgrade example . . . . . . . . . . . . . . . . . . . 108
Performing a Client/Server online upgrade from a TimesTen version prior to 6.0
113
Overview . . . . . . . . . . . . . . . . . . . . . . . . . .113
Limitations . . . . . . . . . . . . . . . . . . . . . . . . .114
Client/Server online upgrade example. . . . . . . . . . . . . . .114
Performing a Client/Server online upgrade from TimesTen version 6.0 and
above . . . . . . . . . . . . . . . . . . . . . . . . . . .116
Client/Server online upgrade . . . . . . . . . . . . . . . . . .116
Client/Server online upgrade with continuous access to the data store . .117
Record of Upgrades . . . . . . . . . . . . . . . . . . . . . . .117
vi Oracle TimesTen In-Memory Database Installation Guide
Page 7

Index
Contents vii
Page 8

viii Oracle TimesTen In-Memory Database Installation Guide
Page 9

About this Guide
This document contains all necessary information for installing the
Oracle TimesTen® In-Memory Database (TimesTen) Data Manager,
Client and Server components.
The TimesTen CD contains a
notes. These notes list product information and late changes to the
printed documentation. The release notes are also available in PDF
format. The PDF file is named
TimesTen documentation
TimesTen documentation is available on the product distribution media
and on the Oracle Technology Network:
http://www.oracle.com/technology/documentation/timesten_doc.html.
Including this guide, the TimesTen documentation set consists of these
documents:
Book Titles Description
README.TXT file that holds the release
README.pdf.
Oracle TimesTen In-Memory
Database Installation Guide
Oracle TimesTen In-Memory
Database Introduction
Oracle TimesTen In-Memory
Database Operations Guide
Oracle TimesTen In-Memory
Database C Developer’s and
Reference Guide
and the
Oracle TimesTen In-Memory
Database Java Developer’s
and Reference Guide
Oracle TimesTen In-Memory
Database API Reference
Guide
Contains information needed to install and configure
TimesTen on all supported platforms.
Describes all the available features in the Oracle
TimesTen In-Memory Database.
Provides information on configuring TimesTen and
using the ttIsql utility to manage a data store. This
guide also provides a basic tutorial for TimesTen.
Provide information on how to use the full set of
available features in TimesTen to develop and
implement applications that use TimesTen.
Describes all TimesTen utilities, procedures, APIs and
provides a reference to other features of TimesTen.
1
Page 10

Oracle TimesTen In-Memory
Database SQL Reference
Guide
Contains a complete reference to all TimesTen SQL
statements, expressions and functions, including
TimesTen SQL extensions.
Oracle TimesTen In-Memory
Database Error Messages
and SNMP Traps
Oracle TimesTen In-Memory
Database TTClasses Guide
TimesTen to TimesTen
Replication Guide
TimesTen Cache Connect to
Oracle Guide
Oracle TimesTen In-Memory
Database Troubleshooting
Procedures Guide
Contains a complete reference to the TimesTen error
messages and information on using SNMP Traps with
TimesTen.
Describes how to use the TTClasses C++ API to use
the features available in TimesTen to develop and
implement applications.
Provides information to help you understand how
TimesTen Replication works and step-by-step
instructions and examples that show how to perform
the most commonly needed tasks.
This guide is for application developers who use and
administer TimesTen and for system administrators
who configure and manage TimesTen Replication.
Describes how to use Cache Connect to cache Oracle
data in TimesTen data stores. This guide is for
developers who use and administer TimesTen for
caching Oracle data.
Provides information and solutions for handling
problems that may arise while developing applications
that work with TimesT en, or while configuring or
managing TimesTen.
Background reading
For a Java reference, see:
• Horstmann, Cay and Gary Cornell. Core Java(TM) 2, Volume I--
Fundamentals (7th Edition) (Core Java 2). Prentice Hall PTR; 7
edition (August 17, 2004).
A list of books about ODBC and SQL is in the Microsoft ODBC manual
included in your developer’s kit. Your developer’s kit includes the
appropriate ODBC manual for your platform:
• Microsoft ODBC 3.0 Programmer’s Reference and SDK Guide
provides all relevant information on ODBC for Windows developers.
2 Oracle TimesTen In-Memory Database Installation Guide
Page 11
• Microsoft ODBC 2.0 Programmer’s Reference and SDK Guide,
included online in PDF format, provides information on ODBC for
UNIX developers.
For a conceptual overview and programming how-to of ODBC, see:
• Kyle Geiger. Inside ODBC. Redmond, WA: Microsoft Press. 1995.
For a review of SQL, see:
• Melton, Jim and Simon, Alan R. Understanding the New SQL: A
Complete Guide. San Francisco, CA: Morgan Kaufmann Publishers.
1993.
• Groff, James R. / Weinberg, Paul N. SQL: The Complete Reference,
Second Edition. McGraw-Hill Osborne Media. 2002.
For information about Unicode, see:
• The Unicode Consortium, The Unicode Standard, Version 5.0,
Addison-Wesley Professional, 2006.
• The Unicode Consortium Home Page at http://www.unicode.org
Conventions used in this guide
TimesTen supports multiple platforms. Unless otherwise indicated, the
information in this guide applies to all supported platforms. The term
Windows refers to Windows 2000, Windows XP and Windows Server
2003. The term UNIX refers to Solaris, Linux, HP-UX, Tru64 and AIX.
TimesTen documentation uses these typographical conventions:
If you see... It means...
code font
Code examples, filenames, and pathnames.
For example, the
italic code
font
A variable in a code example that you must replace.
For example:
Driver=install_dir/lib/libtten.sl
Replace install_dir with the path of your TimesT en
installation directory.
.odbc.ini. or ttconnect.ini file.
About this Guide 3
Page 12

TimesTen documentation uses these conventions in command line
examples and descriptions:
If you see... It means...
fixed width
italics
[ ]
Variable; must be replaced with an appropriate value.
Square brackets indicate that an item in a command line
is optional.
{ }
Curly braces indicated that you must choose one of the
items separated by a vertical bar ( | ) in a command line.
|
A vertical bar (or pipe) separates arguments that you may
use more than one argument on a single command line.
...
An ellipsis (. . .) after an argument indicates that you may
use more than one argument on a single command line.
%
#
The percent sign indicates the UNIX shell prompt.
The number (or pound) sign indicates the UNIX root
prompt.
TimesTen documentation uses these variables to identify path, file and
user names:
If you see... It means...
install_dir
The path that represents the directory where the current
release of TimesTen is installed.
TTinstance
The instance name for your specific installation of
TimesTen. Each installation of TimesTen must be
identified at install time with a unique alphanumeric
instance name. This name appears in the install path. The
instance name “giraffe” is used in examples in this guide.
bits or bb T wo digits, either 32 or 64, that represent either the 32-bit
or 64-bit operating system.
release or rr T wo digits that represent the first two digits of the current
TimesTen release number, with or without a dot. For
example, 70 or 7.0 represents TimesTen Release 7.0.
jdk_version
Two digits that represent the version number of the
major JDK release. Specifically, 14 represent JDK 1.4;
5 represents JDK 5.
4 Oracle TimesTen In-Memory Database Installation Guide
Page 13

timesten
A sample name for the TimesTen instance administrator.
You can use any legal user name as the TimesTen
administrator. On Windows, the TimesTen instance
administrator must be a member of the Administrators
group. Each TimesTen instance can have a unique
instance administrator name.
DSN
The data source name.
Technical Support
For information about obtaining technical support for TimesTen
products, go to the following Web address:
http://www.oracle.com/support/contact.html
About this Guide 5
Page 14

6 Oracle TimesTen In-Memory Database Installation Guide
Page 15

Access Contr ol
Introduction
Access Control
With TimesTen you can optionally install a layer of internal security,
which throughout the TimesTen documentation set and in the
installation scripts is referred to as “Access Control.”
The Access Control feature of TimesTen provides an environment of
basic control for applications that use the internally defined privileges.
In TimesTen, user privileges are granted on a instance wide-basis. A
user’s privileges apply to all data stores in a given TimesTen instance or
installation.
Limitations of Access Control and non-root installs
General
You can enable Access Control when you install TimesTen. You can
also choose to enable it after installation by using the ttmodinstall
utility. See “Enabling Access Control after installation on UNIX” on
page 14. Access Control cannot be disabled after installation of
TimesTen. You must uninstall and re-install TimesTen if you want to
disable Access Control.
The instance administrator owns all files in the installation directory
tree. Only the instance administrator can administer the TimesTen
instance. See “TimesTen instance administrator” on page 9. All
TimesTen daemon processes are owned by the instance administrator.
1
Prior to installing TimesTen as non-root, certain tasks must be
performed by the user
for non-root installations on UNIX systems” on page 37. You cannot
root. Those tasks are outlined in “Prerequisites
7
Page 16

Cache Connect
For Cache Connect, the TimesTen internal user must match the Oracle
user. External Client/Server users must match the Oracle user. If you are
using the Cache Connect Administrator interface, the user must be an
internal TimesTen user.
Replication
If Access Control is enabled, replication daemon administration and
replication schema changes are restricted to users having the ADMIN
privilege. See “Privileges” on page 13.
Changes are applied to a replicated subscriber data store regardless of
the settings or presence of Access Control on the subscriber.
Instance user configuration commands are not replicated.
Client/Server
If a TimesTen client connects to a Timesten server, and the server side
data store has Access Control enabled, the server’s Authenticate
attribute must be enabled.
T o use Access Control with Client/Server applications, when the user is
identified externally, the Client and the Server processes must be on the
same machine. When Access Control is enabled, remote Client/Server
access is only supported with TimesTen internal users.
TimesTen ignores the values of UID, PWD and PWDCrypt if specified
in the Server DSN. These are client-side only attributes. The user name
and password must be explicitly declared on the Client side.
When Access Control is enable, if PWD or PWDCrypt is specified in
Client/Server applications, TimesTen assumes that the user is internally
identified, otherwise TimesTen assumes that the user is externally
identified and authenticated by the operating system.
Instance access
Instance startup/shutdown
Permission to start and stop the main TimesTen daemon is restricted to
the TimesTen instance administrator.
To start the TimesTen main daemon:
8 Oracle TimesTen In-Memory Database Installation Guide
Page 17

% ttDaemonAdmin -start
To stop an instance:
% ttDaemonAdmin -stop
Instance data store
A DSN for a minimal instance-wide data store is defined by TimesTen
at install time to guarantee that TimesTen always has something with
which to connect.
The following is the definition of the instance DSN for a root
installation:
[TT_instance]
Driver=install_dir/lib/libtten.suffix
DataStore=/var/TimesTen/instance/TT_instance
The following is the definition of the instance DSN for a non-root
installation:
[TT_instance]
Driver=install_dir/lib/libtten.suffix
DataStore=install_dir/info/TT_instance
This data store gets special treatment from the daemon, and has special
access restrictions placed on it. Any user can connect to the instance
data store to change their own password. However, users other than the
instance administrator have only SELECT privileges on the instance
data store.
TimesTen users
TimesTen instance administrator
The owner of a TimesTen installation is the “TimesTen instance
administrator.”
Only a member of the TimesTen administrators group can install
TimesTen because only the instance administrator user can administer
TimesTen. The user installing the instance automatically becomes the
administrator for that instance. Only that user may start or stop the
instance, and only that user may administer the other users in that
instance. If the GroupRestrict attribute is set, the instance
administrator user must have corresponding group membership.
Access Control 9
Page 18

Note: All examples in the TimesTen documentation set use the name
timesten to represent the instance administrator.
For details on establishing the TimesTen instance administrators group,
see “Create the TimesTen instance administrators group” on page 37.
On Windows systems, the user
TimesTen instance administrator when Access Control is selected at
install time.
On UNIX systems, a TimesTen instance administrator user is the OS
user who installs that instance of Timesten.
System automatically becomes the
TimesTen instance users
TimesTen instance users are user names that have been identified to the
instance. They are defined at the instance level and apply to all data
stores in an instance. Initially, only one user name is known to the
instance: the instance administrator.
Only the instance administrator has permission to create or delete users.
Individual users have permission to change their own passwords.
Instance users may be internal user names or external user names.
Internal user
A user name that has been defined within the TimesTen instance is
referred to as an “internal user.” It has no significance outside of the
particular instance of TimesTen in which it was defined. Internal users
are authenticated by the TimesTen instance. See "CREATE USER"in
the Oracle TimesTen In-Memory Database SQL Reference Guide.
TimesTen user names (as specified in the UID DSN attribute) are
automatically converted to upper case (case insensitive).
External user
A user name that is identified by the operating system or some other
external mechanism is referred to as an “external user.” In this release
only the operating system user name is recognized as an external user.
External users are assumed to have been authenticated by some external
mechanism. See "CREATE USER"in the Oracle TimesTen In-Memory
Database SQL Reference Guide. A password is not required by
TimesTen since the user was authenticated by the operating system at
login time.
UNIX external user names are case sensitive. Windows external user
names are not. When connecting from UNIX platforms, TimesTen
10 Oracle TimesTen In-Memory Database Installation Guide
Page 19

automatically converts the external user name to upper case, rendering it
case insensitive.
The PWDCrypt attribute allows you to encrypt a password rather to use
cleartext passwords, and it also provides a way to deal with the special
characters and case sensitivity used in passwords that might create
difficulties if specified in clear text within the PWD DSN attribute.
Before installation
Several steps must be taken to prepare a machine for TimesTen
installation. These steps are needed once per machine and require root
permission. See “Installation prerequisites” on page 25. Additional steps
must be performed before installation if either Access Control is to be
enabled or you plan to install as non-root.
TimesTen administrators group
An operating system group needs to be defined for those users who will
be allowed to install and administer TimesTen instances. This can be an
existing group, but we suggest that a group named “timesten” be created
specifically for this purpose. “Create the TimesTen instance
administrators group” on page 37. The member of the TimesTen
administrators group who installs the TimesTen instance becomes the
TimesTen instance administrator for that instance.
Instance registry directory
TimesTen maintains a “registry” of all TimesTen instances installed on a
given machine. The instance registry itself is not required for operation,
but it is essential for correct installation and uninstallation of TimesT en.
It is not accessible by TimesTen users including the instance
administrator user.
On Unix platforms, for root user installs, the instance registry is located
in the directory
TimesTen/
is a once per machine, pre-installation step. See “Create the TimesTen
registry” on page 38. The disk space required for the files in this
directory is less than 2k bytes.
On Windows the instance registry is contained in the operating system
registry. No action is required by users including the instance
administrator user.
/etc/TimesTen/. Initial creation of the /etc/
directory may require root access. Creation of this directory
Access Control 11
Page 20

Installation directories, files and the daemon port
Installation of TimesTen must be performed by the chosen instance
administrator user. The instance administrator owns all files in the
installation directory tree. Only the instance administrator can operate
the instance.
Installation directories
The installer suggests default destination directories, based on the user
performing the installation.
Instance home directory
The instance may be installed in any directory to which the instance
administrator has sufficient permission.
On Unix, the installer suggests
releases. For non-root users, the installer suggests the home directory of
the user, usually defined by the environment variable $HOME.
On Windows, the installer suggests the directory pattern as used in
previous releases of TimesTen,
The TimesTen documentation refers to the installation directory as
install_dir.
/opt/TimesTen/tt70 as in previous
C:\TimesTen\tt70.
Daemon home directory
The “home” or current working directory of the running the main
TimesTen daemon is known as the daemon home directory. This
directory must be owned by the instance administrator, with
permissions on UNIX systems. The daemon verifies both the
permissions and ownership of this directory when it starts up.
On UNIX, the installer suggests the use of
installed as non-root or
On Windows, the
purpose, just as in previous releases.
/var/TimesTen/tt70 if running as root.
install_dir\srv\info directory is used for this
install_dir/info if
rwxr-xr-x
Password file
If access control is selected at installation time, user and password data
is stored in the file
Initially, this file contains a single entry for the instance administrator.
The presence of this file indicates to the daemon that Access Control has
install_dir/srv/info/ttpasswd.
12 Oracle TimesTen In-Memory Database Installation Guide
Page 21

been selected. If this file is missing, an error occurs after Access Control
is enabled.
This file is readable and writable only by the instance administrator.
Passwords are stored in encrypted form and are not known to the
instance administrator as one way hashes, so they cannot be recovered.
Daemon port
Though the instance registry enforces portTCP/IP uniqueness for
TimesTen instances, the possibility of the TimesTen main daemon port
conflicting with ports used by non-TimesTen applications always exists.
See “Changing the daemon port nu mber on UNIX” on page 39 for ways
to change the demon port number after installation.
Authenticating users and privileges
When Access Control is enabled, certain TimesTen utility APIs, XLA
operations, utilities, procedures and SQL operations require user
authentication. For details on each operation, see the specific chapters of
the Oracle T imes Ten In-Memory Database API Reference Guide and the
Oracle TimesTen In-Memory Database Operations Guide.
All TimesTen utilities prompt for a password if needed. See Chapter 2,
“Utilities” in the Oracle TimesTen In-Memory Database API Reference
Guide.
Client/Server utilities always prompt for a password if no PWD attribute
is specified, since they must always use Authenticate.
Scripts built on utilities requiring passwords may want to use the
PWDCrypt attribute, rather than embedding a cleartext password in the
script.
Privileges
For a description of the TimesTen Access Control privileges, see
“Access Control Privileges” in the Oracle TimesTen In-Memory
Database SQL Reference Guide,
GroupRestrict
The instance administrator must be included in the GroupRestrict
groups being used.
Access Control 13
Page 22

Maintaining users and privileges
TimesTen allows the instance administrator to create, drop and alter
users when Access Control is enabled. It also allows the instance
administrator to grant and revoke privileges for users. For details see
Chapter 5, “SQL Statements in the Oracle TimesTen In-Memory
Database SQL Reference Guide.
Administration of users is done at the instance level by establishing a
connection to any data store and using the SQL commands to create and
modify users. These commands are not transactional and cannot be
rolled back.
Listing of defined users and privileges
The ttUserPrivileges built-in procedure lists the privileges granted to
users defined in the instance.
The ttSchema utility allows user definitions and privilege information
to be output in the form of SQL statements that can be used to recreate
the user environment within a different instance.
Enabling Access Control after installation on UNIX
On UNIX, the ttmodinstall utility allows the instance administrator to
enable Access Control if it was not enabled at install time. If you have
not stopped the TimesT en daemon before using ttmodinstall, the utility
stops the daemon before changing the port number. After the port
change, the daemon is automatically restarted. If you have not stopped
the entire TimesTen instance, then ttmodinstall will stop the instance,
make the necessary changes, then restart the instance.
This is useful, if you install TimesTen and later determine that you want
to enable Access Control.
The utility is run from the command line and takes the
Control
% ttmodinstall -enableAccessControl
Note: Disabling Access Control can only be done by uninstalling and
re-installing the same or a differently release of TimesTen.
The ttmodinstall utility can also modify the path supplied to the
ORACLE_HOME environment variable that provides Cache Connect
to Oracle with the knowledge of where Oracle is installed.
option. For example:
14 Oracle TimesTen In-Memory Database Installation Guide
-enableAccess
Page 23

All other changes to the TimesTen instance can only be made by
uninstalling and re-installing the same or a differently release of
TimesTen. (See “Changing the daemon port number on UNIX” on page
39 and “ORACLE_HOME environment variable” on page 77.)
Access Control 15
Page 24

16 Oracle TimesTen In-Memory Database Installation Guide
Page 25

2
T imesTen Installation
This chapter contains configuration information that you will need to
review before installing TimesTen on your system, in the sections:
• Platforms and configurations
• Installation instances
• Choosing the appropriate TimesTen components
• Installation prerequisites
• Operating system security considerations
• Prerequisites for non-root installations on UNIX systems
• Changing the daemon port number on UNIX
You will find a description of the procedures to install TimesTen on
your platform:
• Installing TimesTen on Windows systems
• Installing TimesTen on Solaris systems
• Installing TimesTen on HP-UX systems
• Installing TimesTen on HP-UX Memory Windows
• Installing TimesTen on AIX systems
• Installing TimesTen on Linux systems
• Installing TimesTen on Tru64 UNIX systems
This chapter also contains information to help you configure TimesTen
after installation, work with the demo applications, migrate data stores
to this release and view the TimesTen documentation:
• Using the Cache Administrator
• Informational messages on Windows systems
• Informational messages on UNIX systems
• ODBC installation
• Environment modifications
• Web server configuration
• Migrating data stores to TimesTen 7.0
17
Page 26

• Building and running the demo applications
• Viewing the online documentation
Finally, this chapter contains information that helps you troubleshoot
any problems that may arise during the installation process:
• Installation problems
18 Oracle TimesTen In-Memory Database Installation Guide
Page 27

Platforms and configurations
Platform support
Times Ten Data Manager and TimesTen Client/Server are supported in
the following environments:.
Environment 32-bit 64-bit
Microsoft Windows 2000, Windows
XP and Windows Server 2003 for
Intel IA-32 and EM64T and AMD64
CPUs.
Solaris 10 for AMD64 CPUs. Yes Yes
Solaris 8, 9 and 10 for UltraSparc
CPUs.
SuSE LINUX Enterprise Server 9
and 10 for Intel IA-32 and EM64T
and AMD64 CPUs.
SuSE LINUX Enterprise Server 10
for Itanium2 CPUs
Red Hat Enterprise Linux 3 and 4
for Intel Itanium2 CPUs.
Red Hat Enterprise Linux 3 and 4
for Intel IA-32 and EM64T and
AMD64 CPUs.
MontaVista Linux Carrier Grade
Edition Release 4.0 for Intel IA-32
and EM64T and AMD64 CPUs.
Yes Yes
Yes Yes
Yes Yes
Yes
Yes
Yes Yes
Yes Yes
HP-UX 11i and HP-UX 11i v2 for
PA-RISC
HP-UX 11i v2 for Itanium2. Yes Yes
AIX 5L 5.2 and 5.3 for POWER CPUs Yes Yes
Tru64 UNIX 5.1B for Alpha EV68
CPUs
Yes Yes
Yes
TimesTen Installation 19
Page 28
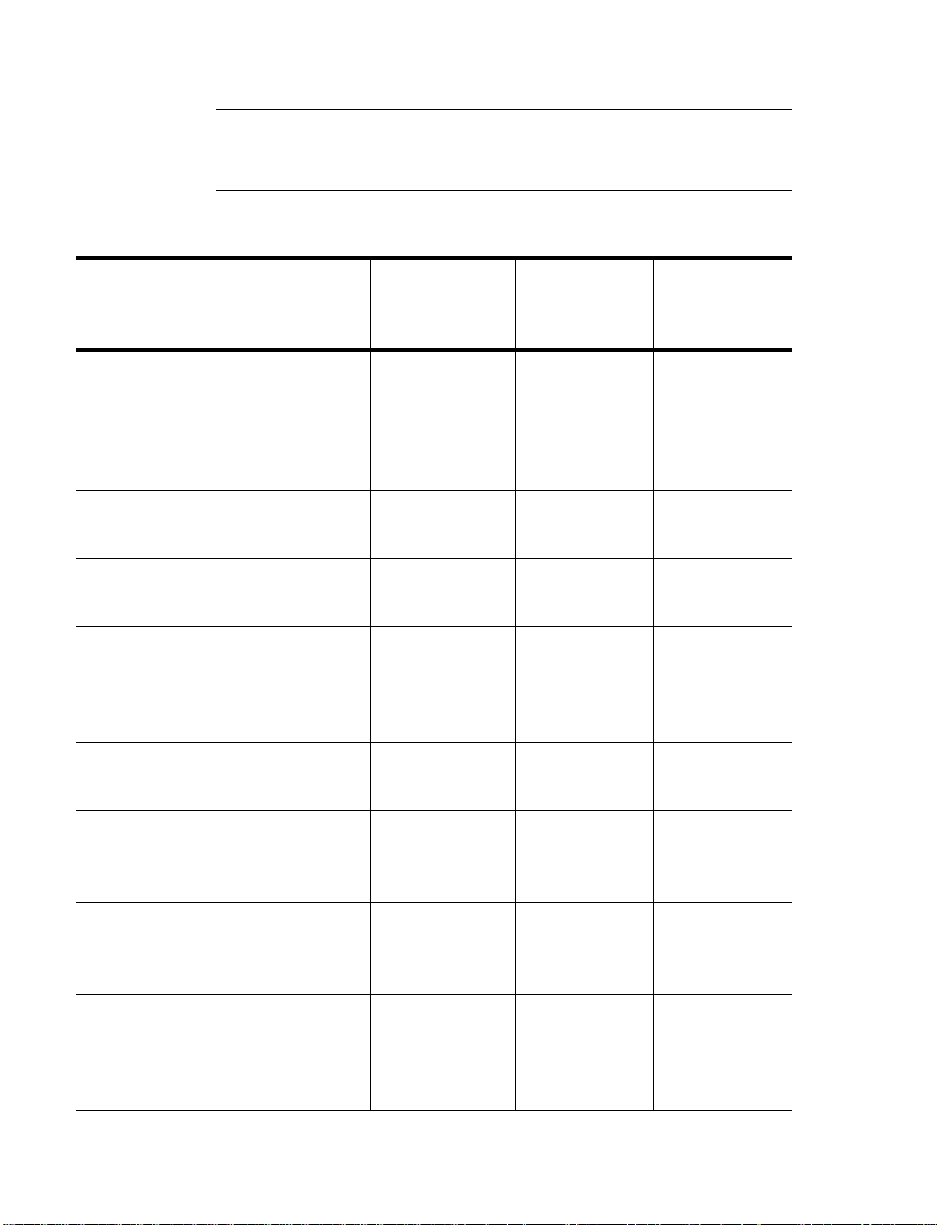
JDK support
Note: TimesTen supports the Sun JVM and the BEA WebLogic JRockit
JVM for Linux and Windows x86 systems. For details on JRockit, see
www.bea.com.
TimesTen supports the following JDKs on the specified platforms:
Environment JDK 1.4 JDK 5.0 BEA
WebLogic
JRockit 5.0
Microsoft Windows 2000,
Windows XP and Windows
Server 2003 for Intel IA-32
and EM64T and AMD64
CPUs
Solaris 10 for AMD64 CPUs Yes (32-bit
Solaris 8, 9 and 10 for
UltraSparc CPUs
SuSE LINUX Enterprise
Server 9 and 10
for Intel IA-32 and EM64T
and AMD64 CPUs
SuSE LINUX Enterprise
Server 10 for Itanium2 CPUs
Red Hat Enterprise Linux 3
and 4 for Intel Itanium2
processors
Red Hat Enterprise Linux 3
and 4 for Intel IA-32 and
EM64T and AMD64 CPUs
Yes Yes Yes
and 64-bit)
Yes (32-bit
and 64-bit)
Yes (32-bit
and 64-bit)
Yes Yes
Yes Yes
Yes Yes Yes
Yes (32-bit
and 64-bit)
Yes (32-bit
and 64-bit)
Yes (32-bit
and 64-bit)
Yes (32-bit
and 64-bit)
Yes (64-bit
only)
Yes (32-bit
and 64-bit)
MontaVista Linux Carrier
Grade Edition Release 4.0
for Intel IA-32 and EM64T
and AMD64 CPUs
Yes (32-bit
and 64-bit)
Yes (32-bit
and 64-bit)
20 Oracle TimesTen In-Memory Database Installation Guide
Yes (32-bit
and 64-bit)
Page 29
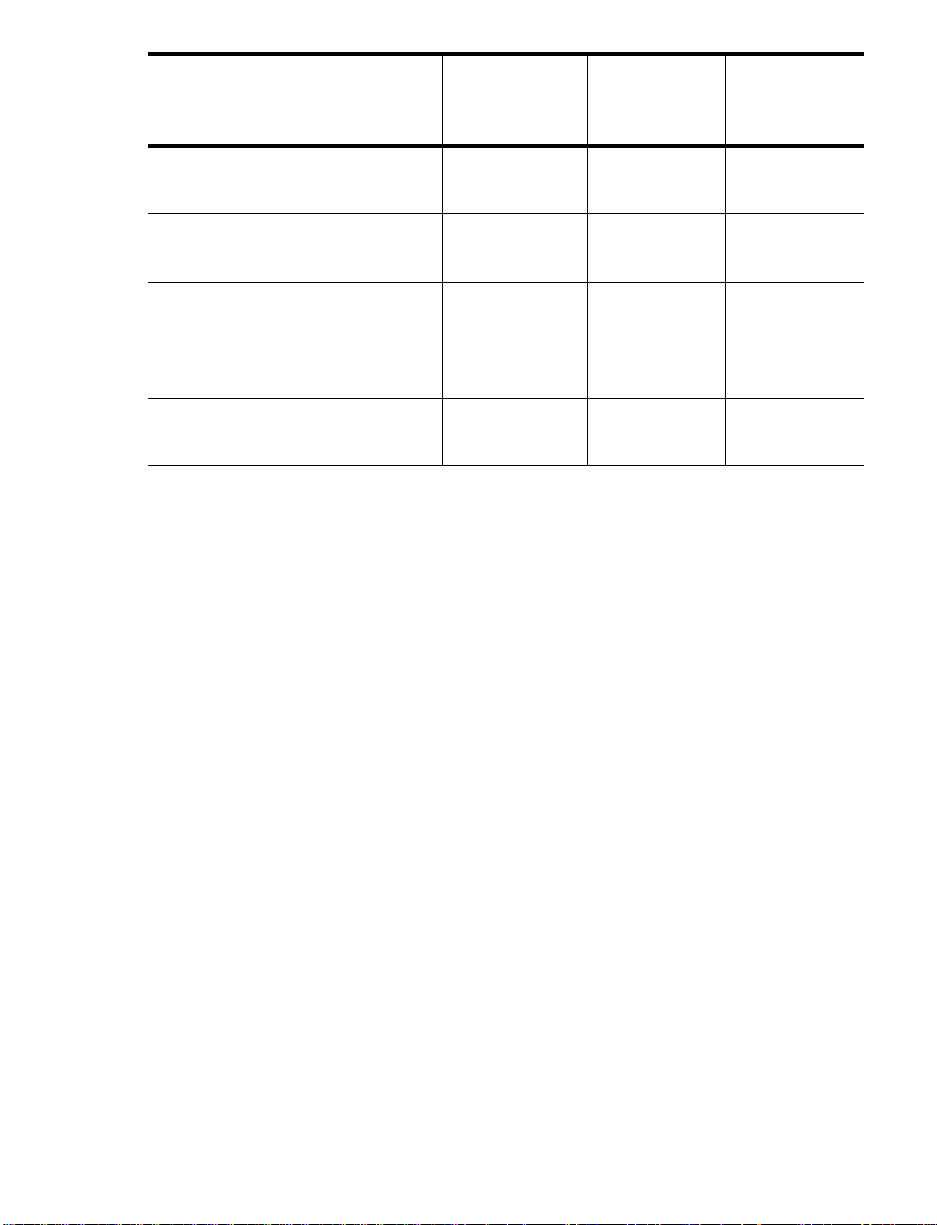
Environment JDK 1.4 JDK 5.0 BEA
WebLogic
JRockit 5.0
HP-UX 11i and HP-UX 11i v2
for PA-RISC 32- and 64-bit
HP-UX 11i v2 for Itanium2 Yes (32-bit
AIX 5L 5.2 and 5.3 for
POWER CPUs
Tru64 UNIX 5.1B for Alpha
EV68 CPUs
Yes (32-bit
and 64-bit)
and 64-bit)
Yes (32-bit
and 64-bit)
(Uses IBM
JDK)
Yes
Client/Server configurations
A TimesTen client on any supported platform can connect to a
TimesTen server on any platform where TimesTen is supported.
A TimesTen 6.0 client can connect to a 6.0 TimesTen Server of any
patch level. If the
ttendaemon.options file, a TimesTen 6.0 client can connect to a
TimesTen 7.0 or newer server, under certain configurations.
A TimesTen 7.0 or later client can connect to a TimesTen 6.0 or newer
server, under certain configurations.
For configuration details see "Configuring TimesTen Client and Server"
in the Oracle TimesTen In-Memory Database Operations Guide.
-insecure-backwards-compat option is set in the
Yes (32-bit
and 64-bit)
Yes (32-bit
and 64-bit)
Yes (32-bit
and 64-bit)
(Uses IBM
JDK)
Cache Connect to Oracle
TimesTen Cache Connect to Oracle allows you to cache Oracle
Database data in TimesT en. The following Oracle releases are supported
with this option:
• Oracle Database 10g Release 2 (Oracle 10.2.0.1.0 or above)
• Oracle Database 10g Release 1 (Oracle 10.1.0.5.0 or above)
• Oracle Database 9i Release 2 (Oracle 9.2.0.8.0 or above)
TimesTen Installation 21
Page 30

Cache Connect is supported on the 32-bit and 64-bit platforms specified
in this table:
Environment 32-bit 64-bit
Microsoft Windows 200 0, Wi ndows
XP and Windows Server 2003 for
Intel IA-32 and EM64T and AMD64
CPUs
Solaris 10 for AMD64 CPUs
systems
Solaris 8, 9 and 10 for UltraSparc
CPUs
SuSE LINUX Enterprise Server 9
and 10 for Intel IA-32, EM64T and
AMD64 CPUs
SuSE LINUX Enterprise Server 10
for Itanium2 CPUs
Red Hat Enterprise Linux 3 and 4
running on Intel Itanium2
processors
Red Hat Enterprise Linux 3 and 4
for Intel IA-32 and EM64T and
AMD64 CPUs
HP-UX 11i and HP-UX 11i v2 for PARISC 32-bit and 64-bit
Yes Yes
Yes
Yes Yes
Yes Yes
Yes
Yes
Yes Yes
Yes Yes
HP-UX 11i v2 for Itanium2 Yes Yes
AIX 5L 5.2 and 5.3 for POWER
CPUs
Tru64 UNIX 5.1B for Alpha EV68
CPUs
Replication configurations
TimesTen-to-TimesTen Replication is supported only between identical
platforms and bit-levels.
22 Oracle TimesTen In-Memory Database Installation Guide
Yes Yes
Yes
Page 31

Installation instances
On UNIX, you can install more than one instance of any TimesTen
release. By default, the instance name for this release is tt70.
If an instance of a particular release of TimesTen already exists on the
machine, and you would like to install a second instance of the same
TimesTen release, you must supply a unique instance name and port
number. The T imesTen installation script can detect if an instance of the
particular release of TimesTen already exists on the machine and will
prompt you for a new instance name and port number for the main
TimesTen daemon.
The instance name appears in the installation path and is the key used to
access all necessary information about that particular installation of
TimesTen. The instance name also appears in some TimesTen file
names.
Note: On Windows, you can only install one instance of any major and
minor release of TimesTen. The TimesTen installation script does not
prompt you to supply an instance name.
Instance names
The instance name is case-insensitive and can have up to 255 characters.
The name must be NON-NULL and can include underscores ( _ ) or
period (.), but no other special characters.
You can retrieve information about the TimesT en instance name, release
number and port settings using the ttVersion utility.
Instance port numbers
Any time that you install more than one instance of TimesTen with the
same major and minor release numbers on the same machine, the
TimesTen installation script also requires that you specify a non-default
TCP/IP port number for the main TimesTen daemon.
All TimesTen data stores that replicate to each other must use the same
daemon port number, except when the -remoteDaemonPort option is
specified in duplicate operations. This port number is set at install time
and can be verified using the ttVersion utility.
TimesTen Installation 23
Page 32

Choosing the appropriate TimesTen components
TimesTen allows you to select the components of TimesTen that you
wish to install.
Components available on Windows
Type Description
Compact Installs the TimesTen client, ODBC drivers and examples.
Typical Installs the TimesTen Data Manager, TimesTen Client, TimesTen
Server, documentation and examples.
Custom You may customize installation by selecting any of the following
components: TimesTen Data Manager, TimesTen Client and/or
TimesTen Server.
Components available on UNIX
Components Description
TimesTen Client Installs the TimesTen Client only. No other TimesTen
components are installed on the machine. Use this
installation to allow the TimesTen Client to access the
TimesTen Server on a remote machine.
TimesTen Data
Manager
TimesTen Client,
Server and Data
Manager
If you have already installed some components and you would like to
add a component, you must install a new instance of TimesTen.
Installs the TimesTen Data Manager only. Use this
installation to run the TimesTen Data Manager locally.
Installs the TimesTen Data Manager, Client and Server on a
single machine. Use this installation to:
• Allow a Client on another machine to access the
TimesTen Server on this machine.
• Allow the TimesTen Client on this machine to access the
TimesTen Server either locally or on a remote machine.
• Allow applications to access the TimesTen Data Manager
locally.
24 Oracle TimesTen In-Memory Database Installation Guide
Page 33

Installation prerequisites
Before installing Times Ten, make sure the appropriate requirements are
met for your operating system.
On platforms where JDBC is supported you must have the appropriate
version of the JDK installed on your machine to use JDBC. See
“Platforms and configurations” on page 19 to learn which JDK is
required for your platform.
UNIX requirements
In general, on UNIX systems, you must configure:
• The number of semaphores, and
• Allowable shared memory.
In addition, you may need to:
• Ensure you have the latest operating system patches
• Configure your file system to allow large files
• Configure your Java environment
• Configure your Client/Server environment
• Configure network settings for Replication
This section outlines some of the changes that may need to be made on
any UNIX system. It is followed by sections that describe changes
required for each specific UNIX platform on which TimesTen is
supported
Semaphores TimesTen consumes 1 SEMMNI per active data store, plus 1 additional
SEMMNI per TimesT en instance where Client/Server communication is
done through shared memory. For each active data store, TimesTen
consumes 100 SEMMSL if the Connections attribute is set to the default
value, and one additional SEMMSL for each connection above the
default.
Java On UNIX systems, if you are running JDBC, install the latest JDK and
any vendor required patches. Refer to the website of the OS JDK
provider for the patches you may need.
To run 64-bit Java applications on all systems except AIX systems, if
you are using the Sun 64-bit JVM, you may need to pass the
options to the Java command line.
TimesTen Installation 25
-d64
Page 34

Other Client/
Server
Settings
The maximum number of concurrent IPC connections to a TimesTen
Server allowed by TimesTen is 9,999. However, system limits can take
precedence on the number of connections to a single DSN. Client/
Server users can increase the file descriptor limit to support a large
number of connections and processes.
For example, on Solaris, you may change the file descriptor limit to
have a maximum of 1024 simultaneous server connections by adding
the line:
set rlim_fd_max = 1080
in
/etc/system.
In this case, 1080 is greater than the number of anticipated client/server
connections and allows for a few extra connections.
AIX
Replication For replication, TCP send and receive buffers should be increased to a
minimum of 512KB. You may need to embed the following commands
into a script that can be run at system boot time:
# /usr/sbin/no -p -o tcp_recvspace=524288
# /usr/sbin/no -p -o tcp_sendspace=524288
HP-UX
Semaphores
simultaneously, you must increase the value of the kernel parameter
semmns.
To view existing kernel parameter settings, log in as user root.
For HP-UX 11i, use the command:
On HP-UX systems, to connect to more than 2 data stores
# /usr/sbin/kmtune
For HP-UX 11iv2, use the command:
# /usr/sbin/kctune
Shared
memory
On HP-UX systems, you also must increase the value of the parameter
shmmax. To make these changes:
1. Use the
kmtune or kctune commands above, or run the HP System
Administration Manager to see existing kernel parameter settings:
# /usr/sbin/sam
2. Double-click Kernel Configuration, then double-click Configurable
Parameters.
26 Oracle TimesTen In-Memory Database Installation Guide
Page 35

3. Scroll down the list of parameters to semmns and change its value to a
minimum of 4096 or greater.
4. For HP-UX 11i systems, also scroll down the list of parameters to
shmmax and change its value to a maximum of 0x40000000.
Note: The value 0x240000000 (a 24 followed by seven zeroes)
indicates that the largest shared memory segment that can be created is
1024 MB. The size of the shared memory segment required for a shared
data store is larger than the requested data store size. Set this value high
enough to support the largest shared memory segment needed.
5. Recompile the kernel. Choose Create a New Kernel from the Actions
menu.
6. Reboot the system.
Large data
stores
On 64-bit HP-UX systems, if you expect to have data stores that are
larger than 2GB, you must enable large files. By default, HP-UX
supports files that are no greater than 2GB in size.
To enable large files, create the filesystems using
largefiles
% /usr/sbin/fsadm -F hfs -o largefiles device_name
option. Use the command:
newfs with the -o
For example:
% /usr/sbin/fsadm -F hfs -o largefiles \
/dev/vg02/rlvol1
Replication For replication, TCP send and receive buffers should be increased to a
minimum of 512KB. You may need to embed the following commands
into a script that can be run at system boot time:
For HP-UX 11i, 11.23 (11iv2)
#
/usr/bin/ndd -set /dev/tcp tcp_xmit_hiwater_lfp 524288
#
/usr/bin/ndd -set /dev/tcp tcp_recv_hiwater_lfp 524288
#
/usr/bin/ndd -set /dev/tcp tcp_xmit_hiwater_lnp 524288
#
/usr/bin/ndd -set /dev/tcp tcp_recv_hiwater_lnp 524288
#
/usr/bin/ndd -set /dev/tcp tcp_xmit_hiwater_max 524288
#
/usr/bin/ndd -set /dev/tcp tcp_recv_hiwater_max 524288
Linux
For Linux, TimesTen has been tested with Red Hat Enterprise Linux 3
and 3.1 and 4, the MontaVista Linux Carrier Grade Edition Release 4.0
and SuSE LINUX Enterprise Server 9 and 10 minimal configurations.
TimesTen Installation 27
Page 36

The C development tools are required if native development will be
done on the machine.
Large pages Large pages can be enabled only if the running Linux kernel supports
large pages (also called “huge pages” in Linux community).
If large pages are supported by the kernel, there should be special files
in the
/proc directory that indicate the number and size of the large
pages.
On Linux 2.4.x systems,
the /proc/sys/vm/hugetlb_pool indicates
the total size of the large pages.
On 2.6.x systems, the
/proc/sys/vm/nr_hugepages file indicates the
total number of large pages.
Y ou can change the total number and size of the large pages by changing
the contents of those files. For example, you can use:
echo "32" > /proc/sys/vm/nr_hugepages
To see the number and size of the allocated large pages use:
cat /proc/meminfo
The following output from this command would indicate that you have
16 large pages, each of the size 256MB for a total of 4GB:
HugePages_Total: 16
HugePages_Free: 16
Hugepagesize: 262144 kB
Note: Since large pages must be allocated on a contiguous memory
space, the actual large page size allocated may be smaller than
requested. Also, the large page size itself is not configurable. The value
of
Hugepagesize in /proc/meminfo indicates the system’s fixed large
page size.
You may need to change the
/etc/security/limits.conf file if PAM
(Pluggable Authentication Modules) is enabled.
The OS now is ready for the large page support. To enable this feature
on TimesTen, simply set
-linuxLargePageAlignment Size_in_MB
in the daemon options file (ttendaemon.options).
You should specify the large page alignment size in MB, which is the
Hugepagesize value in /proc/meminfo.
Once you set up large pages, TimesTen uses as many large pages as
possible. If there are not enough pages, TimesT en uses the normal pages
after consuming all available large pages.
28 Oracle TimesTen In-Memory Database Installation Guide
Page 37

When TimesTen uses large pages, the HugePages_Free file in /proc/
meminfo
changes.
Semaphores To view existing kernel parameter settings, log in as
# /sbin/sysctl -a
Shared
memory
To increase the shared memory size to 2048 MB, for example, as root,
edit the
kernel.shmmax=2147483648
/etc/sysctl.conf file by adding the line:
If your configuration is greater than 8GB, you should also increase the
value of the
to
ceil(SHMMAX/PAGE_SIZE). Page size is generally 4K on x86 systems
shmall parameter. The value is in KB and should be equal
and 16K on Itanium. For example, for a 64GB data store on Itanium,
you should specify the following parameters values:
kernel.shmmax=68719476736
kernel.shmall=4194304
T o increase the shared memory size without rebooting, use:
% /sbin/sysctl -w kernel.shmmax=2147483648
If you have your kernel configured with the /proc file system an d it is
mounted, then the current maximum shared memory segment size (in
bytes) can be viewed by the following command:
% cat /proc/sys/kernel/shmmax
You can also change this value by the following command
% echo 2147483648 > /proc/sys/kernel/shmmax
This command has the same effect as the sysctl command.
root and use:
IPC Client/
Server
Client/Server
and Cache
Administrator
On Red Hat Linux systems, to enable more than 6 ShmIpc Client/Server
connections, add the line:
kernel.sem = "250 32000 128 100"
to the /etc/sysctl.conf file and reboot.
This sets the parameter values as follows:
SEMMSL=250
SEMMNS=32000
SEMOPM=100
SEMMNI=100
If you are installing the Cache Connect to Oracle option and plan to use
the web-based Cache Administrator or if you plan to use TimesTen
client/server configurations, install the following RPM packages:
TimesTen Installation 29
Page 38

For Red Hat 3.0, install:
compat-libstdc++-7.3-2.96.123
For Red Hat 4.0, install:
compat-libstdc++-296-2.96.132.7.2
These packages can be install either using the rpm command or by using
the Red Hat GUI installer found in “Legacy Software Development.”
Replication For replication, TCP send and receive buffers should be increased to a
minimum of 512KB. You may need to embed the following commands
into a script that can be run at system boot time:
# /sbin/sysctl -w net.ipv4.tcp_rmem="4096 4194304 4194304"
# /sbin/sysctl -w net. ipv4.tcp_wmem="98304 41943 04 4194304"
# /sbin/sysctl -w net.ipv4.tcp_mem="98304 4194304 4194304"
# /sbin/sysctl -w net.core.rmem_default=65535
# /sbin/sysctl -w net.core.wmem_default=65535
# /sbin/sysctl -w net.core.rmem_max=4194304
# /sbin/sysctl -w net.core.wmem_max=4194304
# /sbin/sysctl -w n
et.ipv4.tcp_window_scaling=1
Cache
Connect
Operating
system
patches
IPC
semaphores
For Cache Connect, TCP send and receive buffers should be increased
to even greater values. You may need to embed the following
commands into a script that can be run at system boot time:
#
/sbin/sysctl -w net.ipv 4.tcp_rmem="4096 4 194304 4194304"
#
/sbin/sysctl -w net.ipv4.tc p_wmem="98304 4194304 419 4304"
#
/sbin/sysctl -w net.ipv 4.tcp_mem="98304 4 194304 4194304"
#
/sbin/sysctl -w net.cor e.rmem_default=262 144
#
/sbin/sysctl -w net.cor e.wmem_default=262 144
#
/sbin/sysctl -w net.cor e.rmem_max=4194304
#
/sbin/sysctl -w net.cor e.wmem_max=4194304
#
/sbin/sysctl -w net.ipv 4.tcp_window_scali ng=1
#
/sbin/sysctl -w net.ipv 4.ip_local_port_ra nge="1024 65000"
Solaris
Solaris 8 requires patch 108827-36 or later.
To view a list of installed patches, use:
% showrev -p
On Solaris 8 and 9, TimesTen checks the IPC configuration at install
time. If either the IPC Semaphores module or the IPC Shared Memory
module is not installed, you can install them by hand. Use the
commands:
30 Oracle TimesTen In-Memory Database Installation Guide
Page 39

ryps3# modload /kernel/sys/semsys
ryps3# modload /kernel/sys/shmsys
Increase
number of
semaphores
For Solaris 10 systems, the default semaphore settings should be
sufficient without entries in
/etc/system.
On other Solaris systems, you may need to increase the number of
semaphores. TimesTen consumes 1 SEMMNI per active data store, plus
one additional SEMMNI per TimesTen instance where Client/Server
communication is done through shared memory.
For each data store, TimesTen consumes 100 SEMMSL if the
Connections attribute is set to the default value (64), and one additional
SEMMSL for each estimated connection above the default. We
recommend that you increase the number of semaphores:
1. Log in as user
2. Set or add the following lines to
set semsys:seminfo_semmni = 20
set semsys:seminfo_semmsl = 512
set semsys:seminfo_semmns = 2000
set semsys:seminfo_semmnu = 2000
root.
/etc/system:
Note: The values in this step are the minimum number of required
semaphores. You can increase these numbers as needed. You can use the
following formula as a guide, although in practice, SEMMNS and
SEMMNU can be much less than SEMMNI * SEMMSL because not
every program in the system needs semaphores.
SEMMNS=SEMMNU = (SEMMNI * SEMMSL).
Shared
memory IPC
client
connections
3. Reboot your system.
4. To view the current limits, use:
% /usr/sbin/sysdef
This command displays the limits for SEMMSL, SEMMNS, SEMOPM,
and SEMMNI, respectively.
SEMOPM is the maximum number of operations per semop call. It does
not need to be reset.
On Solaris, to have more than 6 ShmIpc-enabled Client DSN
connections per process, you must make changes to the SHMSEG
kernel parameter.
To access more than 6 data stores, you must make changes to the
SHMSEG
kernel parameter. For example, to allow a single process to
TimesTen Installation 31
Page 40

access 12 data stores, add the following line to
before using TimesTen:
set shmsys:shminfo_shmseg=12
/etc/system and reboot
Other
changes
Large data
stores
Other changes that you may need to make to your Solaris system
include the following:
• To allow a large number of connections to a data store, add the
following lines to
set rlim_fd_cur=4096
set rlim_fd_max=4096
/etc/system and reboot before using TimesTen:
• To enable large shared memory objects in Solaris, add the following
line to
/etc/system and reboot before using TimesTen:
set shmsys:shminfo_shmmax = 0x240000000
Note: The value 0x240000000 (a 24 followed by seven zeroes)
indicates that the largest shared memory segment that can be created
is 1024 MB. The size of the shared memory segment required for a
data store is larger than the data store size permanent size. Set this
value high enough to support the largest shared memory segment
needed.
If you keep data stores on a Solaris UFS file system, and are using
transaction-consistent checkpoints, you may need to change the settings
of some kernel parameters to get the best performance for you r
checkpoints. The Solaris UFS Throttle algorithm causes processes that
write a single large file to be put to sleep when a byte count threshold
exceeds the high-water mark. To disable the algorithm, add the line:
set ufs:ufs_WRITES = 0
to the /etc/system file.
Alternatively, you can increase the high-water mark by adding the line:
set ufs:ufs_HW = desired value
to the /etc/system.file
You must reboot the system for the new value to take effect.
Setting the high-water mark to the size of the checkpoint file should
provide satisfactory performance, although a lower value may as well.
More information on the UFS Throttle algorithm may be obtained in the
white paper, “Understanding Solaris Filesystems and Paging” (SMLI
TR-98-55) available from
http://www.sun.com.
32 Oracle TimesTen In-Memory Database Installation Guide
Page 41

Replication For replication, TCP send and receive buffers should be increased to a
minimum of 512KB. You may need to embed the following commands
into a script that can be run at system boot time:
# /usr/sbin/ndd -set /dev/tcp tcp xmit_hiwat=524288
# /usr/sbin/ndd -set /dev/tcp tcp_recv_hiwat=524288
Tru64 UNIX
Semaphores On Tru64 UNIX systems, to view existing kernel parameter settings, log
in as user root, and use the command:
# /sbin/sysconfig -q ipc
For each data store, TimesTen consumes 100 SEMMSL if the
Connections attribute is set to the default value (64), and one additional
SEMMSL for each estimated connection above the default.We
recommend that you increase the number of semaphores:
Shared
memory
1. Log in as user
root.
2. To view the current limits, use:
% sysconfig -q ipc
This command displays all the parameters of the IPC subsys t e m.
3. If the broadcast_wakeup semaphore parameter exists on your system, it
must be set to one:
sem_broadcast_wakeup = 1
4. Run the Tru64 UNIX dxkerneltuner:
% dxkerneltuner
5. Double-click IPC.
6. Scroll down the list of parameters and change the values of the
following parameters to at least the values indicated here:
sem_mni = 20
sem_msl = 512
sem_opm = 100
sem_ume = 100
Note: The values in this step are the minimum number of required
semaphores. You can increase these numbers as needed.
To increase the maximum address space a process may use, change the
kernel values
max_per_proc_address_space
per_proc_address_space and
TimesTen Installation 33
Page 42

To increase the maximum data segment (malloc space) a process may
use, change the kernel values
max_per_proc_data_size
per_proc_data_size and
For example, to change all of these values to 10GB:
1. Create a text file,
per_proc_address_space = 10737418240
max_per_proc_address_space = 10737418240
per_proc_data_size = 10737418240
max_per_proc_data_size = 10737418240
kernelparams, that contains the following:
2. Log in as root and run the command:
# sysconfigdb -m -f kernelparams proc
3. You may need to reboot the system after you have made these changes.
Alternatively, you can run the command:
# sysconfig -q proc
4. To view the value of the proc kernel subsystem, run the command:
% sysconfig -r subsys ttr=value
Shared
memory IPC
client
connections
On Tru64 UNIX, to have more than 6 ShmIpc-enabled Client DSN
connections per process, you must make changes to the SHMSEG
kernel parameter. Kernel parameters can be changed with either the
dxkerneltuner interface or the
sysconfigdb command.
Replication For replication, TCP send and receive buffers should be increased to a
minimum of 512KB. You may need to embed the following commands
into a script that can be run at system boot time:
# sysconfig -r inet tcp_recvspace=524288
# sysconfig -r inet tcp_sendspace=524288
Default installation directories
The TimesTen default installation directories for release 7.0 are:
• On Windows, C:\TimesTen\
• On HP-UX, Solaris and Linux, /opt/TimesTen/tt70
• On AIX, /usr/ lpp/TimesTen
TimesTen creates temporary files when large amounts of space in a data
store are freed by a transaction. In addition, other TimesTen operations,
such as
ttRepAdmin -duplicate operations and large deletes, use the
temporary directory when copying files.
tt70
/tt70
34 Oracle TimesTen In-Memory Database Installation Guide
Page 43

The temporary directory is operating system-dependent. Usually it is
located in these directories:
• On Windows,
Settings\Temp
• On Solaris, Linux and Tru64 UNIX, /tmp
• On HP-UX and AIX, /var/tmp
You can change the location of your temporary directory by setting the
TMP environment variable on Windows. On UNIX, you can change the
location of your temporary directory by setting the
variable.
Note: On Windows, the complete temporary directory path must be less
than 190 characters for the installation to complete successfully. In
addition, TimesTen does not support file path names that contain multibyte characters. Please make sure that the installation path, data store
path, transaction log path, and temporary file path do not contain any
multibyte characters.
C:\Documents and Settings\%USERNAME%\Local
TMPDIR environment
Cache Connect
If you are using the Cache Connect to Oracle option of TimesTen, you
must have at least a client installation of Oracle Database 9i or 10g on
the machine where you are installing TimesTen.
Oracle client shared libraries are required in order to cache Oracle data
in TimesTen by Cache Connect to Oracle. You must have Oracle
Database 9i client or Oracle Database 10g installed. Y ou also must have
the
ORACLE_HOME environment variable defined before running the
installer. See “ORACLE_HOME environment variable” on page 77.
Operating system security considerations
There are two mutually exclusive modes of operation for TimesTen that
have OS security implications.
1. Non-root installation (available on all non-Windows platforms). In
general, it is safer not to run any processes as a privileged user, such as
root, unless absolutely necessary. When performing non-root
installations, certain procedures must be performed once as user
See the “Prerequisites for non-root installations on UNIX systems” on
page 37.
2. GroupRestrict mode. When a data store is first created, it can be created
in GroupRestrict mode so that all of its files and shared memory
TimesTen Installation 35
root.
Page 44

segments are ownership and permissions restricted to that of a particular
operating system group. This mode only works if TimesTen is installed
and running as
API Reference Guide.
root. See the Oracle TimesTen In-Memory Database
36 Oracle TimesTen In-Memory Database Installation Guide
Page 45

Prerequisites for non-root installations on UNIX systems
As discussed in Chapter 1, “Access Control,” on UNIX systems, you
can install TimesTen as a non-root user. This entire se ction applies to all
UNIX platforms on which TimesTen is supported, unless otherwise
indicated.
However, you may need to perform certain tasks as the user
prior to installing TimesTen and after installation. This section outlines
those tasks that must be performed as the user,
Installation prerequisites for non-root installs
You must be sure that the prerequisites defined in “Installation
prerequisites” on page 25 have been met, before continuing with your
installation. Perform the pre-requisite steps for your particular platform.
The following steps are required for installations that are installed by a
non-root user, whether they use Access Control or not. These
procedures are also required for all installations that will enable Access
Control at install time.
Create the TimesTen instance administrators group
Before installing TimesT en, you must create the instance administrators
group:
1. Log in as root.
root, both
root.
2. Create an operating system group for the TimesTen administrators
group. Only members of this group can install TimesTen.
W e suggest using the name
any name that you prefer.
3. Add the user(s) who are installing and administering TimesTen to the
TimesTen administrators group.
When installing as a non-root user on HP-UX systems, the operating
system user running the TimesTen daemon must belong to an operating
system group that has been given the
the MemoryLock feature of TimesTen.
For example, if the user is a member of a group called
the following command (run as
MLOCK privilege:
timesten for the group, but you can choose
MLOCK privilege, if you want to use
timesten, then
root) gives the timesten group the
TimesTen Installation 37
Page 46

# setprivgrp timesten MLOCK
The getprivgrp command can be used to check the privileges of a
group:
$ getprivgrp timesten
timesten: MLOCK
Note: On Linux and Tru64 systems, root privileges are required to use
MemoryLock attribute. On Solaris systems, you must be installed as
root to use MemoryLock=1 or 2.Data stores in a non-root instance of
TimesTen can use settings 3 and 4 for this attribute, on Solaris systems.
Create the TimesTen registry
1. If the directory /etc/TimesTen does not already exist, create it.
# mkdir /etc/TimesTen
The disk space required for the files in this directory is less than 2k
bytes.
2. Assign ownership permissions on this directory.
For example, with a TimesTen admi nistrators group named
use:
# chmod 775 /etc/TimesTen
# chgrp timesten /etc/TimesTen
If you are upgrading from a TimesTen 5.1, you must change the existing
group ownership and permissions of the existing
/etc/TimesTen
directory on each machine that you wish to install TimesTen 7.0. In that
case the
instance_info file must be assigned write permission s for
members of the TimesTen administrators group. For example:
# chgrp -R timesten /etc/TimesTen
# chmod 664 /etc/TimesTen/*
3. You can now install TimesTen. See the section in this chapter on
installing TimesTen for your specific platform. The installer will verify
the existence and permissions of
/etc/TimesTen and will fail if not
present and correct.
timesten,
Post-installation requirements
For non-root installs, to install the TimesTen daemon start scripts in the
proper system locations, the user root must run the
located in the install_dir
# setuproot -install
/bin directory:
38 Oracle TimesTen In-Memory Database Installation Guide
setuproot script
Page 47

This step is only necessary if you want the TimesTen instance to start
each time the machine is rebooted.
Note: If you install these scripts into your system directory, you must
manually remove them in the case that you want to uninstall your
TimesTen instance, using
# setuproot -uninstall
Configure the syslog messages
For non-root installs, the default location for daemon system message
logs is to a file within the installation directory. For root installs, the
default location is the
on UNIX systems” on page 72 for details.
syslog mechanism. See “Informational messages
Changing the daemon port number on UNIX
The ttmodinstall utility allows the instance administrator to change the
port number on which the main TimesTen daemon listens. If you have
not stopped the TimesT en daemon before using ttmodinstall, the utility
stops the daemon before changing the port number. After the port
change, the daemon is automatically restarted.
This feature is useful if you install TimesTen and later find that the port
is already in use.
The utility is run from the command line and takes the
with the new port number as an argument. For example:
% ttmodinstall -port 12345
The ttmodinstall utility can also enable Access Control and modify the
path supplied to the ORACLE_HOME environment variable. All other
changes to the TimesTen instance can only be made by un instal ling
TimesTen and re-installing the same or a new product. (See “Enabling
Access Control after installation on UNIX” on page 14 and “Changing
the daemon port number on UNIX” on page 39.)
UNIX libraries
On UNIX, TimesTen installs the Data Manager library and ODBC
driver. In the
use for each available data store. See “Defining data sources for the
demo applications” on page 83 for more information on the
sys.odbc.ini file. Also see “User and system DSNs” in the TimesTen
Developers Guide.
-port option
sys.odbc.ini file, set the driver version that you want to
TimesTen Installation 39
Page 48

See the TimesTen Developer’s Guide for more information about using
TimesTen.
Installing TimesTen on Windows systems
This section discusses installation and related issues for Windows
systems. For a list of Windows platforms supported by TimesTen, see
“Platforms and configurations” on page 19.
Note: Before beginning installation, be sure that the prerequisites
defined in “Installation prerequisites” on page 25 have been met.
Installing TimesTen
An InstallShield program installs your TimesTen instance on Windows
systems. The TimesTen CD-ROM is configured to autoplay; the
installation program is automatically invoked when the CD-ROM is
inserted into the CD-ROM drive.
To install TimesTen manually, insert the CD, then run the command:
D:\WINDOWS\SETUP.EXE
where D: is the CD-ROM drive.
Note: Each time SETUP.EXE is executed, the install program checks for
previous installations. If a previous version of TimesTen exists, the
setup program starts in Maintenance Mode, which allows you to
uninstall or repair the existing TimesT en product. In order to do a install
a new version of TimesTen where the first and second version number
(e.g. 6.1.2 and 6.1.5) match, you must first uninstall TimesTen in
Maintenance Mode and then run SETUP.EXE again.
The TimesTen installation prompts you to make these choices at
installation time:
• Which component would you like to install?
See “Components available on Windows” on page 24.
• Do you want to install the Cache Connect to Oracle option?
If you intend to cache Oracle data in a TimesTen cache group, select
this option. You can incrementally install this option at a later time,
as well, using the Modify option to the installation script when the
major and minor release numbers of the TimesTen installation match
exactly.
• Do you want to enable Access Control?
40 Oracle TimesTen In-Memory Database Installation Guide
Page 49

By default, Access Control is not enabled. See Chapter 1, “Access
Control” for more details.
Custom setup also lets you choose other custom options.
The installation program adds TimesTen directories to the system
environment variables LIB and INCLUDE.
In addition, installation prompts you to add a directory to the system
environment variable PATH. If you decide not to set the PATH
environment variable at installation time, you can set the PATH
environment variable at any time after installation on a per session basis
by running the script install_dir
\bin\ttenv.bat.
Note: On Windows, TimesTen canno t be installe d in a substit uted
directory (a subdirectory that is mapped to a drive letter). Attempting to
install TimesTen in a substituted directory results in an error.
Installing TimesTen in silent mode
TimesTen allows you to save installation options to a batch file that you
can later use to install TimesTen without having to answer each option
in a dialog box. To set up silent mode:
• From a command-line, run:
C:> setup.exe -r
With this option, TimesTen walks you through a normal setup
operation with all the dialog boxes. TimesTen saves your responses
to the file
C:\WINDOWS\setup.iss.
You can now use this file to run an installation in silent mode:
• From a command-line, run:
setup.exe -s -flresponse_file.
For example:
C:> setup.exe -s -f1C:\WINDOWS\setup.iss
acquires the installation options from the response file. No dialog
boxes appear. Some information pop-up dialogs may still appear,
such as the one that informs you that the services are being started.
Note: Batch files from releases older than TimesTen Release 7.0 should
not be used to install this release. All new prompts in the installation
script for this release are assigned default answers and may produce
unexpected results when batch files from different versions are used.
TimesTen Installation 41
Page 50

Verifying installation
To verify that TimesTen has been properly installed, check that the
driver files are available and that the services are running:
1. Check that the TimesTen 7.0 Start menu shortcut has been added to the
Windows Desktop Star t > Programs menu.
2. On the Windows Desktop, choose Start > Settings > Control Panel >
Administrative T ools > Data Sources (ODBC). This opens the ODBC
Data Source Administrator.
3. Click Drivers. Check to see that the correct drivers are installed. You
should see the TimesTen Data Manager driver. If you installed
TimesTen Client, you should see the TimesTen Client 7.0 driver. Click
OK.
4. On the Windows Desktop, choose Start > Settings > Control Panel >
Administrative Tools > Services and check that the TimesTen Data
Manager 7.0 service has the word “Started” in the Status field. At this
time, you can also set Recovery options to attempt to restart the service
after a failure.
These steps verify that the system has been installed properly.
Verifying TimesTen Client and Server installation
To verify that the Client and Server have been properly installed:
1. On the Windows Desktop, choose Start > Settings > Control Panel >
Administrative Tools > Data Sources (ODBC).
This opens the ODBC Data Source Administrator.
2. Click System DSN.
3. Select the RunDataCStt70 or ShmRunDataCStt70 sample data source
and click Configure.
Note: The RunDataCStt70 DSN is used for client applications that use
TCP/IP communications with the TimesTen Server. The
ShmRunDataCStt70 DSN is used for client applications that use
shared memory to communicate with a TimesTen Server on the same
machine.
This opens the TimesTen Client Data Source Setup dialog.
4. Click Test TimesTen Server Connection to attempt a connection to the
server.
42 Oracle TimesTen In-Memory Database Installation Guide
Page 51

The ODBC Administrator attempts to connect to the TimesTen Server
and display a message to let you know if it was successful. When you
click this button, the TimesTen Client verifies that:
• ODBC, Windows sockets, and the TimesTen Client are installed on
the machine.
• The TimesTen Server you have selected is defined.
• The host machine for the TimesTen Server is running.
• The TimesTen Server is running.
5. Click Test Data Source Connection to attempt a connection to the data
source on the TimesTen Server.
The ODBC Data Source Administrator attempts to connect to the
TimesTen data source and displays a dialog to let you know if it was
successful. When you click Test Data Source Connection, the
TimesTen Client verifies that:
• The data source you have chosen is defined on the server.
• The TimesTen Client can connect to the data source.
Working with the Data Manager Service and the Server
The TimesTen Data Manager Service starts automatically when you
install the TimesTen Data Manager. In addition, if you installed the
TimesTen Server, it is automatically started whenever the TimesTen
Data Manager service is started. You can change the startup mode for
the TimesTen Data Manager to require manual startup.
Note: You must have administrative privileges to set the startup mode
or to start and stop the TimesTen Data Manager service.
To change the startup mode:
1. On the Windows desktop, choose Start > Settings > Control Panel >
Administrative Tools > Services. This displays all currently available
services.
2. Select TimesTen Data Manager 7.0.
3. Choose either Manual or Automatic from the Startup type list.
Click OK.
If the TimesTen Data Manager startup mode is Manual, follow these
instructions to start and stop the service:
TimesTen Installation 43
Page 52

1. On the Windows desktop, choose Start > Settings > Control Panel >
Administrative Tools > Services. This displays all currently available
services.
2. Select TimesTen Data Manager 7.0.
3. Click Start to start the service. If the service is already running, click
Stop to stop the service.
Note: TimesTen writes events into the Event Log file. The Windows
Application Event Log can get full. To avoid filling the Application
Event Log, check the log settings in the Event Viewer. You can change
the size of the Event Log or control whether it overwrites old events.
Uninstalling TimesTen
To uninstall TimesTen for Windows:
• On the Windows Desktop, choose Start > Settings > Control Panel
> Add/Remove Programs.
• Alternatively, you can use the Modify option to the TimesTen
Installation script to uninstall just the Cache Connect to Oracle
option from TimesTen.
To verify that removal was successful, check that:
• The TimesTen 7.0 Start menu shortcut has been removed from the
Start > Programs menu.
• The TimesTen Data Manager 7.0 has been removed from the
Services list.
• The TimesTen 7.0 drivers have been removed from the ODBC
Drivers tab in the ODBC Control Panel.
Note: DSNs created by TimesTen installation are removed upon
TimesTen uninstall. DSNs created by users are not removed during
TimesTen uninstall.
Installing TimesTen on Solaris systems
This section discusses installation and some related topics for Solaris
systems.
Note: Before beginning installation, be sure that the prerequisites
defined in “Installation prerequisites” on page 25 have been met.
44 Oracle TimesTen In-Memory Database Installation Guide
Page 53

Installing TimesTen
To install TimesTen on your Solaris system, follow these steps:
1. Log in as the TimesTen instance administrator if installing as non-root,
or log in as user root.
2. Load the CD-ROM into the CD drive as follows:
• If the Volume Manager is installed on the system, you don’t have to
explicitly mount the CD; it may be automatically mounted at:
/cdrom/tt7.0
• Otherwise, you have to create, then mount, the cdrom
directory as follows:
# mkdir /cdrom
# /etc/mount -r -F hsfs /dev/sr0 /cdrom
3. Run the setup script by typing the following:
# cd mount_dir
# ./setup.sh
where mount_dir is the directory where the CD is mounted
(e.g.: /cdrom).
• You can run the setup script with the option
-uninstall (default is -install). When you use the -uninstall
option, the script stops the daemon if it is running and removes all
files it had installed.
• To add the Cache Connect to Oracle option to an existing TimesTen
installation, use the
-installCache option with the setup script.
• To uninstall just the Cache Connect to Oracle option from an existing
TimesTen installation, use the
-removeCache option with the setup
script.
-install or
Note: T o uninstall T imesTen, you must run setup.sh -uninstall in a
directory outside of the installation directory that you wish to uninstall.
For example to uninstall the default instance run
/opt/TimesTen/tt70/bin/setup.sh -uninstall.
TimesTen Installation 45
Page 54

In addition,
setup.sh also accepts these options:
-batch
filename
-record
filename
-doc
-help
Installs or uninstalls TimesTen without having to
respond to prompts. If filename is specified, the
installation reads all installation prompts from the
file. The batch file filename is optional. However,
TimesTen recommends that you create the batch file
and specifically indicate the instance name of the
installation.
If no batch file is provided or if the batch file does
not contain an instance name, TimesTen installs a
default instance, using “tt70” for the instance name.
If an instance with the same name already exists on
the installation machine, the install procedure fails.
On 64-bit platforms, the batch file must also specify
either the 32-bit and 64-bit version of TimesTen be
installed. If no batch file is provided or no platform is
specified in the batch file, the 32-bit version is
installed in the default instance.
Installs or uninstalls TimesTen and records responses
to prompts described in filename. The file can
then be used as the parameter to the
-batch option.
Installs documentation.
Displays the help message.
-verbose
Displays extra installation information.
The CD contains tar files of TimesTen. If the setup script cannot find the
tar files to extract from, it prompts you for their location.
4. Enter your response to the setup script prompts.
Note: To install or uninstall TimesTen without having to respond to
prompts, use the
-batch flag with the setup.sh script. Batch files from
older releases of TimesTen cannot be used to install this release. All new
prompts in the installation script for this release are assigned default
answers and may produce unexpected results when batch files from
different versions are used.
The setup script performs these actions (unless your answers resulted in
termination of the installation process):
46 Oracle TimesTen In-Memory Database Installation Guide
Page 55

• On 64-bit systems, prompts you to install one of the following
releases:
– 32-bit (default)
– 64-bit
• Prompts you to:
– Install a new instance
– Upgrade an existing instance (This option allows you to
incrementally install the Cache Connect option. The major and
minor version numbers of the TimesTen release must match
exactly.)
– Display information about an existing instance or
– Quit the installation.
• Prompts you to chose the default instance name or chose a name for
your TimesTen instance. See “Installation instances” on page 23.
• Prompts you to install TimesTen:
– Oracle TimesTen In-Memory Database
– Oracle TimesTen In-Memory Database with Cache Connect to
Oracle
• Prompts you to install one of the following components.
– Client/ Server and Data Manager
– Data Manager only
– Client only
• Prompts you for the location of your TimesTen installation and
specific files, if installing as a non-root user.
• Prompts you to specify the daemon port number. If no instances of
TimesTen are installed on the machine, or if no instances use the
default port number 17000 for 32-bit installations and 17001 for 64bit applications, prompts you to use the default port number.
• Prompts you to determine if Access Control should be enabled,
except for Client-only installs. Default answer is “No.” In that case,
no other changes are needed to your installation or your use of
TimesTen. For more details on Access Control, see Chapter 1,
“Access Control in this guide.
• Prompts you for the TimesTen Server port number.
• Removes any previous installation of this release of TimesTen if you
are installing an upgrade.
• Untars the appropriate tar file for the component(s) being installed
into the install directory, by default
/opt/TimesTen/tt70.
TimesTen Installation 47
Page 56

• Copies the daemon scripts into the appropriate directories.
• If installed by user
root, configures the system to start the daemon
when the system boots.
• Creates the directory where data stores created by the TimesTen
demo applications will reside. By default they reside in
TimesTen/
install_dir/info/DemoDataStores if installed as a non-root user.
TTinstance/DemoDataStore, if installed as root, or
/var/
• Starts the daemon.
• If there are other instances of the same patch release of TimesTen
installed on the same machine, prompts you to provide a unique port
to be used by the TimesTen daemon.
• If the TimesTen Server is being installed, prompts you to configure
the Server: server name, port number and logging options.
• Prompts you to install the TimesTen documentation.
The daemon writes a timestend.pid file into the directory the
daemon was started from:
by the user
root or install_dir/info if installed by a non-root user.
/var/TimesTen/TTinstance/ if installed
This file contains the daemon’s process ID. When the script to stop the
daemon is run, this ID is used to determine the process to terminate.
When the process terminates, the
timestend.pid file is removed.
Working with the daemon and Server
The TimesTen main daemon (timestend) starts automatically when the
operating system is booted, if the instance startup scripts have been
installed in
Application developers do not interact with the daemon directly; no
application code runs in the daemon and application developers do not,
in general, have to be concerned with it. Application programs that use
TimesTen data stores communicate with the daemon transparently by
using TimesTen internal routines.
There are situations, however, when you may have to start and stop the
daemon manually, using the T imesTen main daemon startup script. This
section explains how to start and stop the daemon. If you have installed
the TimesTen Server, it starts automatically when the T imesTen daemon
is started and stops automatically when the TimesTen daemon is
stopped.
/etc/init.d/, and operates continually in the background.
Note: You must have root privileges or be the TimesTen instance
administrator to interact with the TimesTen daemon.
48 Oracle TimesTen In-Memory Database Installation Guide
Page 57

To stop the daemon manually, use the utility command:
ttDaemonAdmin -stop
To start the daemon manually, use the utility command:
ttDaemonAdmin -start
Uninstalling TimesTen
To uninstall all TimesTen components:
1. Log in as the TimesTen instance administrator if you installed as non-
root, or log in as user root.
2. The TimesTen setup script is in the install_dir
the script with the
installation directory:
# install_dir/bin/setup.sh -uninstall
Uninstalling the system removes all TimesTen libraries and executables
and also stops and uninstalls the daemon. You can execute
that all TimesTen processes have terminated. To verify that TimesTen
has been successfully uninstalled, verified that the install_dir no
longer exists.
• To uninstall just the Cache Connect to Oracle option from an existing
TimesTen installation, use the
# install_dir/bin/setup.sh -removeCache
-uninstall option from a directory outside of the
/bin directory. Run
ps to verify
Installing TimesTen on HP-UX systems
This section discusses installation and some related topics for
HP-UX systems.
Note: Before beginning installation, be sure that the prerequisites
defined in “Installation prerequisites” on page 25 have been met.
Installing TimesTen
To install the TimesTen Data Manager on your system, follow these
steps:
1. Log in as the TimesTen instance administrator if installing as non-root,
or log in as user root.
2. Load the CD-ROM into the CD drive as follows: If the
doesn’t exist, create it:
TimesTen Installation 49
cdrom directory
Page 58

# mkdir /cdrom
Mount the CD-ROM, as follows:
• If your system is configured to mount the CD-ROM at
/cdrom, type:
# /etc/mount /cdrom
• Otherwise, mount the CD-ROM device name to the /cdrom
directory, as follows:
# /etc/mount -r cdfs CD-ROM_device_name /cdrom
where CD-ROM_device_name is the name of the CD-ROM device.
3. Run the setup script by typing the following:
# cd mount_dir
# ./setup.sh;
where mount_dir is the directory where the CD is mounted
(e.g.:
/cdrom).
You can run the setup script with the option
(default is
-install). When you use the -uninstall option, the script
-install or -uninstall
stops the daemon and Server, if they are running, and removes all files it
had installed.
• To add the Cache Connect to Oracle option to an existing TimesTen
installation, use the
-installCache option with the setup script.
• To uninstall just the Cache Connect to Oracle option from an existing
TimesTen installation, use the
-removeCache option with the setup
script.
Note: To uninstall TimesTen, you must run setup.sh -uninstall
in a directory outside of the installation directory that you wish to
uninstall. For example to uninstall the default instance run
/opt/TimesTen/tt70/bin/setup.sh -uninstall.
50 Oracle TimesTen In-Memory Database Installation Guide
Page 59

Specify the option at the end, outside the quotation marks. In addition,
setup.sh also accepts these options:
-batch
filename
-record
filename
-doc
-help
Installs or uninstalls TimesTen without having to
respond to prompts. If filename is specified, the
installation reads all installation prompts from the
file. The batch file filename is optional. However,
TimesTen recommends that you create the batch file
and specifically indicate the instance name of the
installation.
If no batch file is provided or if the batch file does
not contain an instance name, TimesTen installs a
default instance, using “tt70” for the instance name.
If an instance with the same name already exists on
the installation machine, the install procedure fails.
On 64-bit platforms, the batch file must also specify
either the 32-bit and 64-bit version of TimesTen be
installed. If no batch file is provided or not platform
is specified in the batch file, the 32-bit version is
installed in the default instance.
Installs or uninstalls TimesT en and records responses
to prompts described in filename. The file can then
be used as the parameter to the
-batch option.
Installs documentation.
Displays the help message.
-verbose
Displays extra installation information.
The CD contains tar files of TimesTen. If the setup script cannot find the
tar files to extract from, it prompts you for their location.
4. Enter your response to the setup script prompts.
Note: To install or uninstall TimesTen without having to respond to
prompts, use the
-batch flag with the setup.sh script. Batch files from
older releases of TimesTen cannot be used to install this release. All new
prompts in the installation script for this release are assigned default
answers and may produce unexpected results when batch files from
different versions are used.
The script performs these actions (unless your answers resulted in
termination of the installation process):
TimesTen Installation 51
Page 60

• On 64-bit systems, prompts you to install one of the following
releases:
– 32-bit (default)
– 64-bit
• Prompts you to:
– Install a new instance
– Upgrade an existing instance (This option allows you to
incrementally install the Cache Connect option. The major and
minor version numbers of the TimesTen release must match
exactly.)
– Display information about an existing instance or
– Quit the installation.
• Prompts you to chose the default instance name or chose a name for
your TimesTen instance. See “Installation instances” on page 23.
• Prompts you to install TimesTen:
– Oracle TimesTen In-Memory Database
– Oracle TimesTen In-Memory Database with Cache Connect to
Oracle
• Prompts you to install one of the following components.
– Client/ Server and Data Manager
– Data Manager only
– Client only
• Prompts you for the location of your TimesTen installation and
specific files, if installing as a non-root user.
• Prompts you to specify the daemon port number. If no instances of
TimesTen are installed on the machine, or if no instances use the
default port number 17000 for 32-bit installations and 17001 for 64bit applications, prompts you to use the default port number.
• Prompts you to determine if Access Control should be enabled,
except for Client-only installs. Default answer is “No.” In that case,
no other changes are needed to your installation or your use of
TimesTen. For more details on Access Control, see Chapter 1,
“Access Control in this guide.
• Prompts you for the TimesTen Server port number.
• Removes any previous installation of this release of TimesTen if you
are installing an upgrade.
• Untars the appropriate tar file for the component(s) being installed
into the install directory, by default
/opt/TimesTen/tt70.
52 Oracle TimesTen In-Memory Database Installation Guide
Page 61

• Copies the daemon scripts into the appropriate directories.
• If installed by user
root, configures the system to start the daemon
when the system boots.
• Creates the directory where data stores created by the TimesTen
demo applications will reside. By default they reside in
TimesTen/
TTinstance/DemoDataStore.
/var/
• Starts the daemon.
• If there are other instances of the same patch release of TimesTen
installed on the same machine, prompts you to provide a unique port
to be used by the TimesTen daemon.
• If the TimesTen Server is being installed, prompts you to configure
the Server: server name, port number and logging options.
• Prompts you to install the TimesTen documentation.
The daemon writes a timestend.pid file into the directory the
daemon was started from:
by the user
root or install_dir/info if installed by a non-root user.
/var/TimesTen/TTinstance/ if installed
This file contains the daemon’s process ID. When the script to stop the
daemon is run, this ID is used to determine which process to terminate.
Once the process is terminated, the
timestend.pid file is removed.
Note: When doing any compiling, use an ANSI C compiler.
Working with the TimesTen daemon and Server
The TimesTen main daemon starts automatically when the operating
system is booted and operates continually in the background.
Application developers do not interact with the daemon(timestend)
directly; no application code runs in the daemon and application
developers do not, in general, have to be concerned with it. Application
programs that use TimesTen data stores communicate with the daemon
transparently by using TimesTen internal routines.
There are situations, however, when you may have to start and stop the
daemon manually, using the T imesTen main daemon startup script. This
section explains how to start and stop the daemon. If you have installed
the TimesTen Server, it starts automatically when the T imesTen daemon
is started and stops automatically when the TimesTen daemon is
stopped.
Note: You must have root privileges or be the TimesTen instance
administrator to interact with the TimesTen daemon.
TimesTen Installation 53
Page 62

If you installed TimesTen as root, the daemon startup file on HP-UX is:
/etc/rc.config.d/tt_TTinstance
If you installed TimesTen as a non-root user, It is:
install_dir/startup
To stop the daemon manually, use the utility command:
ttDaemonAdmin -stop
To start the daemon manually, use the utility command:
ttDaemonAdmin -start
Uninstalling TimesTen
To uninstall TimesTen, follow these steps:
1. Log in as the TimesTen instance administrator if installing as non-root,
or log in as user root.
2. The TimesTen setup script is in the
the script with the
-uninstall in a directory outside of the installation
directory flag by typing:
# install_dir/bin/setup.sh -uninstall
Uninstalling the system removes all T imesTen libraries and executables
and also stops and uninstalls the daemon and Server. You can execute ps
to verify that all TimesTen processes have terminated. To verify that
TimesTen has been successfully uninstalled, verify that the
install_dir no longer exists.
• To uninstall just the Cache Connect to Oracle option from an existing
TimesTen installation, use the
# install_dir/bin/setup.sh -removeCache
install_dir/bin directory. Run
Installing TimesTen on HP-UX Memory Windows
Use a separate instance for each memory window
An instance of TimesTen can run in a memory window. A separate
instance of TimesTen is required for each memory window. During
installation, the TimesTen installer prompts you to indicate whether this
instance is to be run in a memory window.
For a memory windows installation, the installer appends th e in st ance
name and port number of the daemon to
/etc/services.window
key to the
getmemwindow(1M)command. Use the getmemwindow
allowing the instance name to be used as a
54 Oracle TimesTen In-Memory Database Installation Guide
Page 63

<instance> command to determine which port is being used by the
instance.
Using TimesTen in a memory window
In order to use a TimesTen instance running in a memory window, you
must launch your application using the HP-UX
setmemwindow(1M)
command.
For example, given instance
% setmemwindow -j -i `getmemwindow tt_ins1` <prog>
tt_ins1, use:
TimesTen utilities are used without the setmemwindow command, for
example:
% ttBackup ...
Address Space Considerations
The maximum size for any one data store remains 1GB with 32-bit
TimesTen.
TimesTen allocates a single shared memory segment per data store.
TimesTen may also allocate shared memory segments when configured
to use the shared memory IPC mechanism for client/server.
The daemon and utility programs (programs) provided by TimesTen are
linked with
change the TimesTen programs to be marked
2GB of shared memory within the window. Any single data store is still
limited to 1GB.
For example, to use
# chatr -M tt_instance/bin/timesten* tt_instance/bin/*Cmd
tt_instance/bin/ttcserver
To return to EXEC_MAGIC, use:
# chatr -N tt_instance/bin/timesten* tt_instance/ bin/
*Cmd tt_instance/bin/ttcserver
To determine if a program is SHMEM_MAGIC or EXEC_MAGIC, use
# chatr binary
The chatr(1M) command prints “normal executable” for EXEC MAGIC
programs. It prints “SHMEM_MAGIC” for programs so marked.
EXEC_MAGIC, using the -N option to ld(1). You may
SHMEM_MAGIC, enabling
SHMEM_MAGIC, log in as root and use:
Note: If the TimesTen programs are marked SHMEM_MAGIC, the user
application must be marked
SHMEM_MAGIC also. Failure to mark the
TimesTen Installation 55
Page 64

application
SHMEM_MAGIC may result with an Invalid Argument error
(EINVAL, errno=22) when attempting to connect to TimesTen.
If a connection is made to a data store with ExclAccess=1, then memory
windows will not be used. In this case, TimesT en does not allocate
shared memory but rather space for the data store is allocated from the
process' private data space.
Troubleshooting
TimesT en support may ask for all of the following in order to diagnose a
problem using memory windows.
• How many memory windows do you have configured?
% /usr/sbin/kmtune -q max_mem_windows
• What is the maximum shared memory segment size?
% /usr/sbin/kmtune -q shmmax
• How many windows are you using?
% cat /etc/services.window
• Do you have the correct instance in your path?
% ttVersion
% ttStatus
% getmemwindow tt_instance
• Can you connect with a utility provided by TimesTen?
% ttIsql -connStr dsn=my_dsn
• Can you successfully run a demo program? The T imesTen demos are
located under install_dir
• What other segments are in use?
% ipcs -m -a
• Does "setmemwindow(1M)" or a TimesTen utility such as ttStatus
return silently when you expected output?
• Check the error status from the “
• What do es the "
% memwin_stats -w
memwin_stats" tool show?
The memwin_stats tool may be downloaded from HP at
ftp://contrib:9unsupp8@hprc.external.hp.com/
• What error are you getting when you try to connect?
/demo/
setmemwindow” command.
The following list is not exhaustive but may help sort out the problem.
56 Oracle TimesTen In-Memory Database Installation Guide
Page 65

• Not enough core (ENOMEM, errno=12) indicates a problem
allocating the requested amount of shared memory. Can you attach
with small PermSize and TempSize attributes?
• Shared memory can be fragmented. Sometimes, you can attach with
increasingly larger segments until you allocate what you want. Are
you attempting to allocate more than 1GB within your window (2GB
if using
• Permission Denied (
SHMEM_MAGIC)?
EACCES, errno=13) indicates that you are
attempting to attach to the wrong instance or are pointing to the
wrong memory window. Which
-i argument is passed to setmemwindow(1M)?
• Invalid Argument (
EINVAL, errno=22) indicates that the shared
segment may have been allocated in another quadrant. Did you mark
the TimesTen programs
application
SHMEM_MAGIC?
• No space left on device (
SHMEM_MAGIC? Did you also mark your
ENOSPC, errno=28) may indicate that the
system is not configured for enough shared memory segments or
identifiers or that the system may have insufficient swap space to
allocate the shared segment. Check the values of
maxswapchunks and run the swapinfo(1M) command.
Installing TimesTen on AIX systems
This section discusses installation and some related topics for
AIX systems.
shmseg, shmmni,
Installing TimesTen
Before you can install the TimesTen software, you have to add and
mount the CD-ROM file system. To add the CD-ROM setup and install
TimesTen:
1. Log in as the TimesTen instance administrator if installing as non-root,
or log in as user root.
2. Insert the CD-ROM into the CD-ROM drive.
3. Enter:
# crfs -v cdrfs -p ro -d cd0 -m /usr/cdrom/
TimesTen7.0
This creates the directory into which you will mount the
CD-ROM.
4. To mount the CD-ROM, enter:
TimesTen Installation 57
Page 66

# mount /usr/cdrom/TimesTen7.0
After the CD-ROM setup is complete, you can install TimesTen as
follows:
5. Still logged in as user root or the TimesTen instance administrator, run
the setup script by typing:
# cd mount_dir
# ./setup.sh
where mount_dir is the directory where the CD is mounted
(e.g.:
/usr/cdrom/TimesTen7.0).
• To add the Cache Connect to Oracle option to an existing TimesTen
installation, use the
-installCache option with the startup script.
• To uninstall just the Cache Connect to Oracle option from an existing
TimesTen installation, use the
-removeCache option with the setup
script.
• You can run the setup script with the option -install or
-uninstall (default is install). When you use the -uninstall
option, the script stops the daemon if it is running and removes all
files it had installed. In addition, setup.sh also accepts these
options:
-batch
filename
Installs or uninstalls TimesTen without having to
respond to prompts. If filename is specified, the
installation reads all installation prompts from the
file. The batch file filename is optional. However,
TimesTen recommends that you create the batch file
and specifically indicate the instance name of the
installation.
If no batch file is provided or if the batch file does
not contain an instance name, TimesTen installs a
default instance, using “tt70” for the instance name.
If an instance with the same name already exists on
the installation machine, the install procedure fails.
On 64-bit platforms, the batch file must also specify
either the 32-bit and 64-bit version of TimesTen be
installed. If no batch file is provided or not platform
is specified in the batch file, the 32-bit version is
installed in the default instance.
-record
filename
Installs or uninstalls TimesTen and records responses
to prompts described in filename. The file can
then be used as the parameter to the
58 Oracle TimesTen In-Memory Database Installation Guide
-batch option.
Page 67

-doc
Installs documentation.
-help
-verbose
Displays the help message.
Displays extra installation information.
The CD contains tar files of TimesTen. If the setup script cannot find
the tar files to extract from, it prompts you for their location.
6. Enter your response to the setup script prompts.
Note: To install or uninstall TimesTen without having to respond to
prompts, use the
-batch flag with the setup.sh script. Batch files from
older releases of TimesTen cannot be used to install this release. All new
prompts in the installation script for this release are assigned default
answers and may produce unexpected results when batch files from
different versions are used.
The file script performs these actions (unless your answers resulted in
termination of the installation process):
• On 64-bit systems, prompts you to install one of the following
releases:
– 32-bit (default)
– 64-bit
• Prompts you to:
– Install a new instance
– Upgrade an existing instance (This option allows you to
incrementally install the Cache Connect option. The major and
minor version numbers of the TimesTen release must match
exactly.)
– Display information about an existing instance or
– Quit the installation.
• Prompts you to chose the default instance name or chose a name for
your TimesTen instance. See “Installation instances” on page 23.
• Prompts you to install TimesTen:
– Oracle TimesTen In-Memory Database
– Oracle TimesTen In-Memory Database with Cache Connect to
Oracle
• Prompts you to install one of the following components.
– Client/ Server and Data Manager
TimesTen Installation 59
Page 68

– Data Manager only
– Client only
• Prompts you for the location of your TimesTen installation and
specific files, if installing as a non-root user.
• Prompts you to specify the daemon port number. If no instances of
TimesTen are installed on the machine, or if no instances use the
default port number 17000 for 32-bit installations and 17001 for 64bit applications, prompts you to use the default port number.
• Prompts you to determine if Access Control should be enabled,
except for Client-only installs. Default answer is “No.” In that case,
no other changes are needed to your installation or your use of
TimesTen. For more details on Access Control, see Chapter 1,
“Access Control in this guide.
• Prompts you for the TimesTen Server port number.
• Removes any previous installation of this release of TimesTen if you
are installing an upgrade.
• Untars the appropriate tar file for the component(s) being installed
into the install directory, default /usr /lpp/TimesTen/tt70.
• Copies the daemon scripts into the appropriate directories.
• If installed by user
root, configures the system to start the daemon
when the system boots.
• Creates the directory where data stores created by the TimesTen
demo applications will reside. By default they reside in
TimesTen/
TTinstance/DemoDataStore.
/var/
• Starts the daemon.
• If there are other instances of the same patch release of TimesTen
installed on the same machine, prompts you to provide a unique port
to be used by the TimesTen daemon.
• If the TimesTen Server is being installed, prompts you to configure
the Server: server name, port number and logging options.
• Prompts you to install the TimesTen documentation.
The daemon writes a timestend.pid file into the directory the
daemon was started from:
by the user
root or install_dir/info if installed by a non-root user.
/var/TimesTen/TTinstance/ if installed
This file contains the daemon’s process ID. When the script to stop the
daemon is run, this ID is used to determine which process to terminate.
Once the process is terminated, the timestend.pid file is removed.
60 Oracle TimesTen In-Memory Database Installation Guide
Page 69

Working with the TimesTen daemon and server
The TimesTen daemon starts automatically when the operating system
is booted and operates continually in the background. Application
developers do not interact with timestend directly; no application
code runs in the daemon and application developers do not, in general,
have to be concerned with it. Application programs that use TimesTen
data stores communicate with the daemon transparently by using
TimesTen internal routines.
There are situations, however, when you may have to start and stop the
daemon manually, using the T imesTen main daemon startup script. This
section explains how to start and stop the daemon. If you have installed
the TimesTen Server, it starts automatically when the T imesTen daemon
is started and stops automatically when the TimesTen daemon is
stopped.
Note: You must have root privileges or be the TimesTen instance
administrator to interact with the TimesTen daemon.
To stop the daemon manually, use the utility command:
ttDaemonAdmin -stop
To start the daemon manually, use the utility command:
ttDaemonAdmin -start
To determine the status of the daemon at any time, use the ttStatus
utility.
Uninstalling TimesTen
To uninstall TimesTen, follow these steps:
1. Log in as the TimesTen instance administrator if installing as non-root,
or log in as user root.
2. The TimesTen setup script is in the install_dir/bin directory.
Run the script with the -uninstall option in a directory outside of
the installation directory:
# install_dir/bin/setup.sh -uninstall
Uninstalling the system removes all TimesTen libraries and executables
and also stops and uninstalls the daemon. You can execute ps to verify
that all TimesTen processes have terminated. To verify that TimesTen
has been successfully uninstalled, check to see that the install_dir
no longer exists.
TimesTen Installation 61
Page 70

Installing TimesTen on Linux systems
This section discusses installation and some related topics for Linux
systems.
Note: Before beginning installation, be sure that the prerequisites
defined in “Installation prerequisites” on page 25 have been met.
Installing TimesTen
To install TimesTen on your Linux system, follow these steps:
1. Log in as the TimesTen instance administrator if installing as non-root,
or log in as user root.
2. Load the CD-ROM into the CD drive as follows:
# mount/mnt/cdrom
3. Run the setup script by typing the following:
# c d / mnt/c drom
# ./setup.sh
• To add the Cache Connect to Oracle option to an existing TimesTen
installation, use the
• To uninstall just the Cache Connect to Oracle option from an existing
TimesTen installation, use the
script.
• You can run the setup script with the option
-uninstall (default is -install). When you use the -uninstall
option, the script stops the daemon and Server if they are running and
-installCache option with the startup script.
-removeCache option with the setup
-install or
62 Oracle TimesTen In-Memory Database Installation Guide
Page 71

removes all files it had installed. In addition, setup.sh also accepts
these options:
-batch
filename
Installs or uninstalls TimesTen without having to
respond to prompts. If filename is specified, the
installation reads all installation prompts from the
file. The batch file filename is optional. However,
TimesTen recommends that you create the batch file
and specifically indicate the instance name of the
installation.
If no batch file is provided or if the batch file does
not contain an instance name, TimesTen installs a
default instance, using “tt70” for the instance name.
If an instance with the same name already exists on
the installation machine, the install procedure fails.
-record
filename
-doc
-help
-verbose
Installs or uninstalls TimesT en and records responses
to prompts described in filename. The file can
then be used as the parameter to the
-batch option.
Installs documentation.
Displays the help message.
Displays extra installation information.
The CD contains tar files of TimesTen. If the setup script cannot find the
tar files to extract from, it prompts you for their location.
4. Enter your response to the setup script prompts.
Note: To install or uninstall TimesTen without having to respond to
prompts, use the
-batch flag with the setup.sh script. Batch files from
older releases of TimesTen cannot be used to install this release. All new
prompts in the installation script for this release are assigned default
answers and may produce unexpected results when batch files from
different versions are used.
The setup script performs these actions (unless your answers resulted in
termination of the installation process):
• Prompts you to:
– Install a new instance
– Upgrade an existing instance (This option allows you to
incrementally install the Cache Connect option. The major and
TimesTen Installation 63
Page 72

minor version numbers of the TimesTen release must match
exactly.)
– Display information about an existing instance or
– Quit the installation.
• Prompts you to chose the default instance name or chose a name for
your TimesTen instance. See “Installation instances” on page 23.
• Prompts you to install TimesTen:
– Oracle TimesTen In-Memory Database
– Oracle TimesTen In-Memory Database with Cache Connect to
Oracle
• Prompts you to install one of the following components.
– Client/ Server and Data Manager
– Data Manager only
– Client only
• Prompts you for the location of your TimesTen installation and
specific files, if installing as a non-root user.
• Prompts you to specify the daemon port number. If no instances of
TimesTen are installed on the machine, or if no instances use the
default port number 17000 for 32-bit installations and 17001 for 64bit applications, prompts you to use the default port number.
• Prompts you to determine if Access Control should be enabled,
except for Client-only installs. Default answer is “No.” In that case,
no other changes are needed to your installation or your use of
TimesTen. For more details on Access Control, see Chapter 1,
“Access Control in this guide.
• Prompts you for the TimesTen Server port number.
• Removes any previous installation of this release of TimesTen if you
are installing an upgrade.
• Untars the appropriate tar file for the component(s) being installed
into the install directory, by default
/opt/TimesTen/tt70.
• Copies the daemon scripts into the appropriate directories.
• If installed by user
root, configures the system to start the daemon
when the system boots.
• Creates the directory where data stores created by the TimesTen
demo applications will reside. By default they reside in
TimesTen/
TTinstance/DemoDataStore.
/var/
• Starts the daemon.
64 Oracle TimesTen In-Memory Database Installation Guide
Page 73

• If there are other instances of the same patch release of TimesTen
installed on the same machine, prompts you to provide a unique port
to be used by the TimesTen daemon.
• If the TimesTen Server is being installed, prompts you to configure
the Server: server name, port number and logging options.
• Prompts you to install the TimesTen documentation.
The daemon writes a timestend.pid file into the directory the
daemon was started from:
by the user
root or install_dir/info if installed by a non-root user.
/var/TimesTen/TTinstance/ if installed
This file contains the daemon’s process ID. When the script to stop the
daemon is run, this ID is used to determine the process to terminate.
When the process terminates, the
timestend.pid file is removed.
Working with the TimesTen daemon and Server
The TimesTen main daemon (timestend) starts automatically when the
operating system is booted and operates continually in the background.
Application developers do not interact with
application code runs in the daemon and application developers do not,
in general, have to be concerned with it. Application programs that use
TimesTen data stores communicate with the daemon transparently by
using TimesTen internal routines.
There are situations, however, when you may have to start and stop the
daemon manually, using the T imesTen main daemon startup script. This
section explains how to start and stop the daemon. If you have installed
the TimesTen Server, it starts automatically when the T imesTen daemon
is started and stops automatically when the TimesTen daemon is
stopped.
timeste nd directly; no
Note: You must have root privileges or be the TimesTen instance
administrator to interact with the TimesTen daemon.
To stop the daemon manually, use the utility command:
ttDaemonAdmin -stop
To start the daemon manually, use the utility command:
ttDaemonAdmin -start
Uninstalling TimesTen
To uninstall all TimesTen components, follow these steps:
TimesTen Installation 65
Page 74

1. Log in as the TimesTen instance administrator if you inst alled as non-
root, or log in as user root.
2. The TimesT en setup script is in the install_dir/
the script with the
-uninstall flag in a directory outside of the
bin directory. Run
installation directory, by typing:
# install_dir/bin/setup.sh -uninstall
Uninstalling the system removes all T imesTen libraries and executables
and also stops and uninstalls the daemon and Server. You can execute
to verify that all TimesTen processes have terminated. To verify that
TimesTen has been successfully uninstalled, verify that the
install_dir no longer exists.
Installing TimesTen on Tru64 UNIX systems
This section discusses installation and some related topics for Tru64
UNIX systems.
Note: Before beginning installation, be sure that the prerequisites
defined in “Installation prerequisites” on page 25 have been met.
Installing TimesTen
To install TimesTen on your Tru64 UNIX system, follow these steps:
1. Log in as the TimesTen instance administrator if installing as non-root,
or log in as user root.
ps
2. Load the CD-ROM into the CD drive.
3. Create the mount directory, if it does not already exist:
# mkdir /mnt
4. Mount the CD-ROM:
# /sbin/mount -r -t cdfs /dev/disk/cdrom0c /mnt
5. Run the setup script by typing the following:
# cd /mnt
# ./setup.sh
• To add the Cache Connect to Oracle option to an existing TimesTen
installation, use the
-installCache option with the startup script.
• To uninstall just the Cache Connect to Oracle option from an existing
TimesTen installation, use the
-removeCache option with the setup
script.
66 Oracle TimesTen In-Memory Database Installation Guide
Page 75

• You can run the setup script with the option -install or -
uninstall
(default is -install). When you use the -uninstall
option, the script stops the daemon if it is running and removes all
files it had installed.
Note: T o uninstall T imesTen, you must run setup.sh -uninstall in a
directory outside of the installation directory that you wish to uninstall.
For example to uninstall the default instance run
/opt/TimesTen/tt70/bin/setup.sh -uninstall.
In addition,
-batch
filename
-record
filename
-doc
-help
-verbose
setup.sh also accepts these options:
Installs or uninstalls TimesTen without having to
respond to prompts. If filename is specified, the
installation reads all installation prompts from the
file. The batch file filename is optional. However,
TimesTen recommends that you create the batch file
and specifically indicate the instance name of the
installation.
If no batch file is provided or if the batch file does
not contain an instance name, TimesTen installs a
default instance, using “tt70” for the instance name.
If an instance with the same name already exists on
the installation machine, the install procedure fails.
Installs or uninstalls TimesT en and records responses
to prompts described in filename. The file can
then be used as the parameter to the
-batch option.
Installs documentation.
Displays the help message.
Displays extra installation information.
The CD contains tar files of TimesTen. If the setup script cannot find the
tar files to extract from, it prompts you for their location.
6. Enter your response to the setup script prompts.
Note: To install or uninstall TimesTen without having to respond to
prompts, use the
-batch option with the setup.sh script. Batch files
from releases older than TimesTen Release7.0 should not be used to
install this release. All new prompts in the installation script for this
TimesTen Installation 67
Page 76

release are assigned default answers and may produce unexpected
results when batch files from different versions are used.
The setup script performs these actions (unless your answers resulted in
termination of the installation process):
• Prompts you to:
– Install a new instance
– Upgrade an existing instance (This option allows you to
incrementally install the Cache Connect option. The major and
minor version numbers of the TimesTen release must match
exactly.)
– Display information about an existing instance or
– Quit the installation.
• Prompts you to chose the default instance name or chose a name for
your TimesTen instance. See “Installation instances” on page 23.
• Prompts you to install TimesTen:
– Oracle TimesTen In-Memory Database
– Oracle TimesTen In-Memory Database with Cache Connect to
Oracle
• Prompts you to install one of the following components.
– Client/ Server and Data Manager
– Data Manager only
– Client only
• Prompts you for the location of your TimesTen installation and
specific files, if installing as a non-root user.
• Prompts you to specify the daemon port number. If no instances of
TimesTen are installed on the machine, or if no instances use the
default port number 17000 for 32-bit installations and 17001 for 64bit applications, prompts you to use the default port number.
• Prompts you to determine if Access Control should be enabled,
except for Client-only installs. Default answer is “No.” In that case,
no other changes are needed to your installation or your use of
TimesTen. For more details on Access Control, see Chapter 1,
“Access Control in this guide.
• Prompts you for the TimesTen Server port number.
• Removes any previous installation of this release of TimesTen if you
are installing an upgrade.
• Untars the appropriate tar file for the component(s) being installed
into the install directory, by default
/opt/TimesTen/tt70.
68 Oracle TimesTen In-Memory Database Installation Guide
Page 77

• Copies the daemon scripts into the appropriate directories.
• If installed by user
root, configures the system to start the daemon
when the system boots.
• Creates the directory where data stores created by the TimesTen
demo applications will reside. By default they reside in
TimesTen/
TTinstance/DemoDataStore.
/var/
• Starts the daemon.
• If there are other instances of the same patch release of TimesTen
installed on the same machine, prompts you to provide a unique port
to be used by the TimesTen daemon.
• If the TimesTen Server is being installed, prompts you to configure
the Server: server name, port number and logging options.
• Prompts you to install the TimesTen documentation.
The daemon writes a timestend.pid file into the directory the
daemon was started from:
by the user
root or install_dir/info if installed by a non-root user.
/var/TimesTen/TTinstance/ if installed
This file contains the daemon’s process ID. When the script to stop the
daemon is run, this ID is used to determine the process to terminate.
When the process terminates, the
timestend.pid file is removed.
Working with the TimesTen daemon and Server
The TimesTen main daemon (timestend) starts automatically when the
operating system is booted and operates continually in the background.
Application developers do not interact with the daemon directly; no
application code runs in the daemon and application developers do not,
in general, have to be concerned with it. Application programs that use
TimesTen data stores communicate with the daemon transparently by
using TimesTen internal routines.
There are situations, however, when you may have to start and stop the
daemon manually, using the T imesTen main daemon startup script. This
section explains how to start and stop the daemon. If you have installed
the TimesTen Server, it starts automatically when the T imesTen daemon
is started and stops automatically when the TimesTen daemon is
stopped.
Note: You must have root privileges or be the TimesTen instance
administrator to interact with the TimesTen daemon.
To stop the daemon manually, use the utility command:
ttDaemonAdmin -stop
TimesTen Installation 69
Page 78

To start the daemon manually, use the utility command:
ttDaemonAdmin -start
Uninstalling TimesTen
To uninstall all TimesTen components:
1. Log in as the TimesTen instance administrator if you inst alled as non-
root, or log in as
root.
2. The TimesT en setup script is in the install_dir/
the script with the
-uninstall flag in a directory outside of the
installation directory, by typing:
# install_dir/bin/setup.sh -uninstall
Uninstalling the system removes all T imesTen libraries and executables
and also stops and uninstalls the daemon. You can execute
that all TimesTen processes have terminated. To verify that TimesTen
has been successfully uninstalled, verified that the install_dir no
longer exists.
• To uninstall just the Cache Connect to Oracle option from an existing
TimesTen installation, use the
# install_dir/bin/setup.sh -removeCache
Using the Cache Administrator
The Cache Administrator is a web-based tool used to set cache
definitions. This feature is available on systems where the Cache
Connect to Oracle option has been installed. See “Cache Connect to
Oracle” on page 21.
To start the Cache Administrator use the URL:
http://machine_name:port/cache
machine_name
daemon or Data Manager service is running, or localhost if using a web
browser on the same machine where TimesTen is installed.
is the host name of the machine where the TimesTen
bin directory. Run
ps to verify
port is the TimesTen web server port number that was configured
during the installation of the Cache Connect to Oracle option. Its value
is stored in the PORT variable in the
webserver.config
install_dir/info/webserver.config for non-root UNIX installs,
or the
install_dir\srv\info\webserver.config on Windows
file on UNIX systems for root installs,
/var/TimesTen/TTinstance/
systems.
70 Oracle TimesTen In-Memory Database Installation Guide
Page 79

Note: The Cache Administrator will not work if it is running on a
Windows machine with the Windows Firewall ON (this is the usual
setting). In this case, the Windows Administrator must add an exception
to allow the Cache Administrator to connect through the Windows
Firewall.
For details on setting the environment variables required to use Cache
Connect to Oracle, see “Environment modifications” on page 74.
For details on setting up the web server, see “Web server configuration”
on page 79.
The following web browsers are supported for the Cache Administrator:
• Internet Explorer 6.0
• Firefox 1.5 and greater
Informational messages on Windows systems
As the TimesTen Data Manager service operates, it generates error,
warning, informational and debug messages. These messages may be
useful for TimesTen system administration and for debugging
applications.
To view the messages, follow these steps:
1. On Windows XP, choose Start > Programs > Administrative Tools >
Event Viewer.
On Windows2000, choose Start > Settings > Control Panel >
Administrative Tools > Event Viewer.
The Event Viewer window appears.
2. From the Log menu, choose Application. The window changes to
display only log messages generated by applications.
• Messages with the phrase “TimesTen Data Manager 7.0” in the
“Source” column were generated by the TimesTen Data Manager
service.
• Messages with the phrase “TimesTen Server 7.0” in the “Source”
column were generated by the TimesTen Server service.
• Messages with the phrase “TimesTen Replication 7.0” in the
“Source” column were generated by the TimesTen Replication
Agent.
3. T o view a TimesTen message, double-click it. This displays the message
window.
TimesTen Installation 71
Page 80

4. Click Next or Previous to view additional messages.
Note: You can also use the ttDaemonLog utility to view messages
logged by the TimesTen Data Manager. For a description of the system
administration utilities, see "Utilities" in the Oracle TimesTen In-
Memory Database API Reference Guide.
Informational messages on UNIX systems
As the TimesTen daemon operates, it generates error, warning,
informational and debug messages for TimesTen system administration
and for debugging applications. At installation time, you determine
whether these messages go into a file or to the
For root installs, TimesTen logs daemon messages using the
facility defined by
syslog, by default.
To specify the syslog facility used to log TimesTen Daemon and
subdaemon messages, on a separate line of the
file add:
-facility name
Possible name values are:
mail, news, user, or uucp.
The
syslog facility allows messages to be routed in a variety of ways,
auth, cron, daemon, local0-local7, lpr,
including recording them to a file. The disposition of messages is under
the control of the configuration file,
/etc/syslog.conf
Entries in the syslog.conf file contain two columns. The first column
contains a list of the types of messages to log to a particular file. The
second column contains the name of the log file. A tab appears between
the message type and file name. Each entry in the syslog.conf file has
the format:
message_type file_name.
Message types are specified in two parts:
subsystem-facility.severity-level
syslog facility.
ttendaemon.options
LOG_USER
Depending on the configuration specified in that file, messages can be
logged into various files. For the TimesTen daemon, specify the
message types:
user.debug, user.info, user.warn and user.err.
You can also use the wildcard character * to represent the subsystemfacility. Since debug messages are ranked highest, specifying
or
user.debug is sufficient in preparing a file for the daemon log. In a
message type list, delimit items by semi-colons. For example:
72 Oracle TimesTen In-Memory Database Installation Guide
*.debug
Page 81

*.debug /var/adm/syslog/syslog.log
user.err; user.warn; user.info /var/adm/messages
To make changes to /etc/syslog.conf, you must have root privileges
or be the TimesTen instance administrator. Changes only take effect
after the
command
For further details, see your operating system's documentation for
syslog.conf or syslogd for information on configuring this file.
Note: If the /etc/syslog.conf file does not exist on your system,
create one according to the syslog.conf manual page so the daemon
can log its data to the syslog facility.
syslog daemon (syslogd) process is terminated (with the
kill -1) and restarted.
To determine if your
the TimesTen ttSyslogCheck utility. Finally, once
up correctly, you may use the TimesTen ttDaemonLog utility to view
only those messages in the system log file that TimesTen logged.
syslog configuration file is set up correctly, run
syslogd has been set
Incremental install and uninstall of Cache Connect
TimesTen allows you to incrementally install the Cache Connect to
Oracle option after having completed an installation. Likewise, you can
uninstall just the Cache Connect option of TimesTen.
T o incrementally install the Cache Connect option, use the -installCache
option when install
ODBC installation
On Windows systems, TimesTen makes use of the Microsoft ODBC 3.5
SDK. The ODBC SDK’s redistributable components are installed in
C:\WINDOWS\SYSTEM32 on Windows systems. Microsoft only permits
TimesTen to redistribute portions of the ODBC SDK; those portions are
installed automatically (if they are not already present). Other
components—Microsoft sample programs, online help files, and C
language header files—are available separately from Microsoft as part
of the Microsoft ODBC SDK, which can be installed separately as
required. Additionally, the ODBC C language header files and ODBC
online help are bundled as part of Microsoft Visual C++ 6.0, Microsoft
Visual Studio .NET or Microsoft Visual Studio 2005. Most TimesTen
developers do not need to install the SDK separately.
On UNIX systems, no separate SDK installation is required.
TimesTen Installation 73
Page 82

Environment modifications
This section describes various environment variables that you may need
to set, depending on the features of TimesT en that your application uses.
The following table summarizes, in alphabetical order, the environment
variables detailed in this section and other parts of this guide. Some of
these environment variables are platform specific.
Environment
Variable
CLASSPATH
LIB, LIBPATH,
LD_LIBRARY_PATH
or SHLIB_PATH
ODBCINI
ORACLE_HOME
PATH
What to include For settings and other
information, see:
Set to the location of the JDK
to be used by your Java
applications
“CLASSPATH environment
variable” on page 77 and
“Using the Cache
Administrator” on page 70.
On UNIX systems, include
the
lib directory under the
TimesTen installation
“Shared library path
environment variable” on
page 77.
directory
The location where the
odbc.ini file used by
“ODBCINI environment
variable” on page 75
TimesTen data stores is to be
found.
If using the Cache Connect to
Oracle option, set to the
location of the Oracle
installation. Required if you
“ORACLE_HOME
environment variable” on
page 77 and “Using the Cache
Administrator” on page 70
are using the Cache Connect
to Oracle option.
Include the bin directory
under the TimesTen
installation directory. On
Windows, also include the
path to the Oracle installation
if you are using the Cache
Connect to Oracle option.
“PATH environment
variable” on page 75, “Shared
library path environment
variable” on page 77 and
“Installing TimesTen on
Windows systems” on page
40.
74 Oracle TimesTen In-Memory Database Installation Guide
Page 83

Environment
Variable
What to include For settings and other
information, see:
SYSODBCINI
SYSTTCONNECTINI
TMP or TMPDIR
Set to the location where the
sys.
odbc.ini file used by
“SYSODBCINI environment
variable” on page 76
TimesTen system data stores
is to be found. This
environment variable should
be set in the start-up script.
Set to the location where the
sys.ttconnect.ini file
used by TimesTen Client
“SYSTTCONNECTINI
environment variable” on
page 76
applications to define logical
server names.
Set to the location of the
temporary directory.
“Default installation
directories” on page 34
TimesTen uses this directory
during recovery and other
operations.
PATH environment variable
TimesTen provides utilities for managing and debugging TimesTen
applications. To make these utilities readily available, include the
directory found in install_dir in the PATH environment variable.
bin
Note: install_dir is the directory where TimesTen is installed.
On Windows, the PATH environment variable must also contain the bin
directory of the ORACLE installation, if you are using the Cache
Connect to Oracle option.
ODBCINI environment variable
TimesTen applications use the odbc.ini file to define data sources and
their data store attributes. (For a description of data store attributes, see
Chapter 1, “Data Store Attributes in the Oracle TimesTen In-Memory
Database API Reference Guide.) By default on UNIX platforms,
TimesTen first looks for the
user running the TimesTen application. To override the name and
location of this file at run-time, set the $
to the pathname of a
.odbc.ini file before launching the TimesTen
.odbc.ini file in the home directory of the
ODBCINI environment variable
TimesTen Installation 75
Page 84

application. If TimesTen cannot locate a user DSN file, the system DSN
file located in
/var/TimesTen/sys.odbc.ini will be used. Also, see
“Defining data sources for the demo applications” on page 83 for more
information on the
also looks for the
.odbc.ini file. For non-root installations, TimesTen
sys.odbc.ini file under install_dir/info.
SYSODBCINI environment variable
TimesTen applications use the sys.odbc.ini file to define system data
sources and their data store attributes. (For a description of data store
attributes, see Chapter 1, “Data Store Attributes” in the Oracle
TimesTen In-Memory Database API Reference Guide.) A system data
source can be used by any user on the machine. On Windows, system
DSNs are defined from the System DSN tab of the ODBC Data Source
Administrator. On UNIX, system DSNs are defined in the file
TimesTen/sys.odbc.ini
at run-time, set the
of a
sys.odbc.ini file before launching the TimesTen application.
. T o override the name and location of this file
$SYSODBCINI environment variable to the pathname
If TimesTen cannot locate a user DSN file, the system DSN file located
in
/var/TimesTen/sys.odbc.ini will be used . For non-root
installations, TimesTen also looks for the
install_dir
/info.
sys.odbc.ini file under
Also, see “Defining data sources for the demo applications” on page 83
for more information on the
.odbc.ini file.
/var/
SYSTTCONNECTINI environment variable
TimesTen client applications use the sys.ttconnect.ini file to define
logical server names. For a description of logical server names, see
Chapter 2, “Working with the TimesTen Client and Server” in the
Oracle TimesTen In-Memory Database Operations Guide. By default on
UNIX platforms, TimesTen looks in
sys.ttconnect.ini
run-time, set the
. To override the name and location of this file at
SYSTTCONNECTINI environment variable before
/var/TimesTen/
launching the TimesTen Client application.
For non-root installations, TimesTen also looks for the
sys.ttconnect.ini file under install_dir/info.
On Windows systems, logical server names can be configured using the
ODBC Data Source Administrator.
76 Oracle TimesTen In-Memory Database Installation Guide
Page 85

CLASSPATH environment variable
On Windows and UNIX platforms, add install_dir/demo and
install_dir
/lib/ttjdbcjdk_version.jar. to the
CLASSPATH environment variable. For example, for JDK 5.0, set the
CLASSPATH environment variable to: install_dir
ttjdbc5.jar
.
/lib/
ORACLE_HOME environment variable
On platforms where the Cache Connect to Oracle option is supported, to
work with Oracle data, the TimesTen Oracle agent must be running.
This requires that the
path of the Oracle Database 9i or 10g installation at the time that you
install TimesTen.
The ttmodinstall utility allows the instance administrator to change the
path supplied to the ORACLE_HOME environment variable after
installation. If you have not stopped the TimesTen daemon before using
ttmodinstall, the utility stops the daemon before changing the port
number. After the change, the daemon is automatically restarted.
This feature is useful if you install TimesTen and later find that the
Oracle installation has been moved.
The utility is run from the command line and takes the
Settings
option, which will prompt you to supply the new path name.
See “Changing the daemon port number on UNIX” on page 39 and
“Enabling Access Control after installation on UNIX” on page 14.)
ORACLE_HOME environment variable be set to the
-changeOracle
Shared library path environment variable
On Solaris, and Linux systems, add install_dir/lib directory to
the LD_LIBRARY_PATH environment variable.
If you are using the Cache Connect to Oracle option, add
$ORACLE_HOME/lib to LD_LIBRARY_PATH. See “ORACLE_HOME
environment variable” on page 77.
On AIX systems, add install_dir/
environment variable.
On HP-UX 32-bit systems, add install_dir/
SHLIB_PATH environment variable. If you are using the Cache Connect
to Oracle option,
and must not contain
SHLIB_PATH must also contain $ORACLE_HOME/lib32
$ORACLE_HOME/lib. See “ORACLE_HOME
environment variable” on page 77.
lib directory to the LIBPATH
lib to the
TimesTen Installation 77
Page 86

On HP-UX 64-bit systems, add install_dir/
LD_LIBRARY_PATH environment variable. If you are using the Cache
Connect to Oracle option,
$ORACLE_HOME/lib and must not contain $ORACLE_HOME/lib32. See
SHLIB_PATH must also contain
lib to the
“ORACLE_HOME environment variable” on page 77.
On Tru64 UNIX systems, add install_dir/
LD_LIBRARY_PATH environment variable.
lib directory to the
78 Oracle TimesTen In-Memory Database Installation Guide
Page 87

Web server configuration
The TimesTen daemon contains an embedded web server, that is used
for the Cache Administrator if the Cache Connect to Oracle option is
installed. If you select to enable the web server at install time, TimesT en
enables it by setting the -webserver option in the
ttendaemon.options file.
This file is in the startup directory of the daemon:
On UNIX, if installed as
/var/TimesTen/TTinstance/
if installed by a non-root user:
install_dir/info
On Windows:
install_dir\srv\info
If you have not installed the web server and decide to enable it at a later
time, you can do so by:
1. Shutting down the TimesTen daemon.
2. Adding a separate line to the
option
-webserver.
3. Starting the TimesTen daemon.
For more details, see the chapter Chapter 3, “Working with the Oracle
TimesTen Data Manager Daemon in the Oracle TimesTen In-Memory
Database Operations Guide.
Various options for the web server are stored in the
file, also in the daemon startup directory. The TimesTen installation
scripts initially set these options. The options should only be changed at
the request of TimesTen Customer Support.
root:
ttendaemon.options file that contains the
webserver.config
The options in
webserver.config file are:
PORT — The port on which the web serv er listens. If you change this,
any scripts which start the Cache Administrator, or any links you have
saved will have to be changed.
WEBROOT — The root directory of web files.
DOCROOT — A subdirectory of
WEBROOT where the HTML files are
located. The path should begin and end with a '/' on all platforms. The
default is
/docs/. DOCROOT is prepended to the path, so if you supply a
URL, the webserver will look for a file in the indicated path.
TimesTen Installation 79
Page 88

CGIROOT — A subdirectory of
located. The path should begin and end with a '/' on all platforms. The
default is /cgi-bin/.
PERL — The path to the Perl interpreter. The path is set by the
TimesTen installation scripts. Do not change the default path unless you
are certain that the path is for a Perl version that is compatible with
TimesTen and that it contains all the required libraries. The path should
point to the Perl binary, not the Perl directory .
PERLLIB — The path to a directory containing perl modules. It is
added to the Perl search path when a perl CGI program is run.
LOG — Specifies how verbose the logging should be. Set to verbose
to log each connection.
PASSWORD_FILE — The name of a file containing user names and
passwords. If this configuration variable is set, all requests are
authenticated. The password file contains lines of the form
“
username:password” (do not use spaces around the colon, though
leading and trailing spaces and comments are allowed). Passwords are
not encrypted in the password file, and are sent only base64-encoded
from the browser to the server.
MIME — Some
form
MIMETYPE:.{extension} = {mime type}. You should not
remove the definitions for text/html.
MIME types are also specified here. They are all of the
WEBROOT where the CGI scripts are
Migrating data stores to TimesTen 7.0
TimesTen 7.0 cannot read data stores created with earlier releases of
TimesT en. T imesT en 7.0 includes two migration utilities: ttMigrate and
ttBulkCp. These utilities allow you to migrate data stores from older
TimesTen releases to TimesTen Release 7.0.
For a description of these utilities, see "Utilities" in Oracle TimesTen In-
Memory Database API Reference Guide.
On Windows, ttMigrate uses the ODBC driver manager.
On UNIX platforms, the ttMigrate utility is directly linked with the
TimesTen Data Manager ODBC driver.
Using the ttMigrate utility
The ttMigrate utility saves and restores tables from a TimesTen data
store in a binary data file. Using ttMigrate, you can save an entire data
store to a single data file. The data file includes table rows as well as
80 Oracle TimesTen In-Memory Database Installation Guide
Page 89

column and index definitions. When TimesTen restores a table in a new
data store, it also restores the table’s indexes.
Note: The ttMigrate utility cannot migrate data stores across different
hardware platforms. For example, you cannot migrate a Windows data
store to a Solaris data store. The release of ttMigrate must also match
the release of the data store you are copying from or to. In the example
in this section, use ttMigrate of the older version to save the tables of
the original data store to disk files and use ttMigrate of the new version
to migrate the files into the tables of the new data store.
For a description of the ttMigrate syntax and usage, see "Utilities" in
the Oracle TimesTen In-Memory Database API Reference Guide.
To migrate a data store from different versions:
1. Use ttMigrate to save the tables in the older version data store to a disk
file.
If, for example:
• A TimesTen 6.0 data store is called
• The data file you wish to use is called
• TimesTen 6.0 is installed in
or
C:\TimesTen\TimesTen60 on Windows.
/opt/TimesTen60 on UNIX platforms
Sales600;
sales.dat; and
On Windows, use:
C:\ > ”C:\TimesTen\tt60\bin\ttMigrate”
-c DSN=Sales600 sales.dat
On UNIX, use:
% /opt/tt60/32/bin/ttMigrate -c DSN=Sales600
sales.dat
2. Use ttMigrate to restore the saved tables in the new data store.
3. Create a new data source name,
Salestt70 for the TimesTen 7.0 data
store, and import the 6.0 data store:
If, for example:
• TimesTen 7.0 is installed in
platforms or
C:\TimesTen\tt70 on Windows.
/opt/TimesTen/tt70 on UNIX
On Windows, use:
C:\ > ”C:\TimesTen\tt70\bin\ttMigrate” -r DSN=Salestt70
sales.dat
On UNIX, use:
TimesTen Installation 81
Page 90

% /opt/TimesTen/tt70/bin/ttMigrate -rx DSN=Salestt70
sales.dat
Using the ttBulkCp utility
The ttBulkCp utility copies table data between TimesTen data stores
and ASCII files. The data files used by ttBulkCp can only contain rows
from a single table. They also do not store the table’s column or index
definitions. Therefore, when migrating from one TimesT en data store to
another with ttBulkCp, you must first create the tables and indexes in
the new data store manually. Then use ttBulkCp to copy the rows from
the original data store to the new data store. For a description of the
ttBulkCp syntax and usage, see "Utilities" in Oracle TimesTen In-
Memory Database API Reference Guide.
Note: The release of ttBulkCp must match the release of the data store
you are copying from or to. In this example, use ttBulkCp Release 6.0
to save the tables to disk files and use ttIsql and ttBulkCp Release 7.0
to copy the disk files into the tables of the new data store.
To import data from a data store created with TimesTen6.0:
1. Find all the tables you want to copy into the new release of TimesTen.
2. Use the TimesTen utility ttBulkCp to copy the data in each table to a
disk file.
3. Define a data source name for the new data store.
4. Use the CREATE TABLE and CREATE INDEX commands with ttIsql
to recreate each table and index you are importing.
5. Use the TimesTen utility ttBulkCp to copy the contents of the disk
file(s) into the table(s) of the new data store. If, for example:
• Release 6.0 is installed in:
/opt/TimesTen6.0/32 and release 7.0
is installed in /opt/TimesTen/tt70;
• Your DSN for release 6.0 is called
release 7.0 is
source_tt70.
• You have a ttIsql script named
source600 and your DSN for
create.sql that creates user tables
and indexes, or use the ttSchema utility to create the SQL statements
necessary for object creation; and
• You want to migrate the tables ABLE and BAKER from
to
source_tt70.
To copy the tables to disk files, you would execute the commands:
82 Oracle TimesTen In-Memory Database Installation Guide
source600
Page 91

% /opt/tt60/32/bin/ttBulkCp -o
DSN=source600 able able.save
% /opt/tt60/32/bin/ttBulkCp -o
DSN=source600 baker baker.save
Next create a new data source name, source_tt70 for the TimesTen 7.0
data store, and execute the commands:
% /opt/TimesTen/tt70/bin/ttIsql -connStr
DSN=source_tt70 -f create.sql
% /opt/TimesTen/tt70/bin/ttBulkCp -i
DSN=source_tt70 able able.save
% /opt/TimesTen/tt70/bin/ttBulkCp -i
DSN=source_tt70 baker baker.save
Building and running the demo applications
Source code for several demo applications is provided in the demo
directory as part of the TimesTen Data Mana ger distribution on UNIX
and Windows systems. Documentation for these demos is included
online in the file install_dir
install_dir
\demo\README.TXT on Windows.
/demo/README.TXT on UNIX or
The directory install_dir
demo/quickstart
contains files used in demos that provide examples
/demo/tutorial and install_dir/
for the TimesTen documentation. For a description of these demos, see
the README.txt file at the top of these directories.
Note: By default, the TimesTen demo applications save data store files
to
/var/TimesTen/TTinstance/demo/DemoDataStore on UNIX for
root installs, and
install_dir/info/DemoDataStores on non-root
installs. On Windows, you specify the data store directory at installation
time. Before running the demos, make sure your temporary directory
has a minimum of 100 MB of available space.
Defining data sources for the demo applications
Before the demo applications can be executed, you must create the data
source names (DSNs) that the demo applications rely on.
On Windows, the TimesTen installation program automatically creates
the appropriate data source names as System DSNs. Their configuration
can be viewed and modified via the ODBC program on the Control
Panel.
TimesTen Installation 83
Page 92

A sample file containing definitions for the DSNs required by the
TimesTen demo applications is provided in
sys.odbc.ini
non-root user the file is located in
, if your product was installed as root. If installed by a
install_dir/info/sys.odbc.ini.
/var/TimesTen/
Building the demo applications
Source code and makefiles are provided for all the demo applications.
See the README file in install_dir
the
demo directory.
/demo for more details about
Problems running the demo programs
Make sure you run the install_dir/demo/ttdemoenv.sh, .csh or
.bat file to set up your demo environment correctly. To avoid problems
with the demo programs, check the environment variables and
installation as discussed in the demo README files.
Problems running the C demo programs on UNIX
On UNIX, when running the demo programs, check the following:
•Are one or more TimesTen drivers installed? Check the
subdirectory of the installation directory for libraries beginning with
libtten.
The default installation directory for a root installation is:
–
/opt/TimesTen/TTinstance/ on Solaris, HP-UX and Linux.
–
/usr/lpp/TimesTen/TTinstance/ on AIX.
• Is the TimesTen main daemon (
timestend) running? See "Starting
and stopping the daemon on UNIX" in the Oracle TimesTen InMemory Database Operations Guide.
lib/
Problems running the C demo programs on Windows
On Windows, when running the demo programs, check the following:
• Are the correct TimesTen drivers installed? Double click on ODBC
in the Control Panel, and check the list of installed ODBC drivers.
• Are the DSNs installed correctly? Check the System DSNs in your
ODBC Data Source window. There should be several DSNs set up to
use TimesTen.
• Do you have write permission on the directory where the data store
resides?
84 Oracle TimesTen In-Memory Database Installation Guide
Page 93

• Is the TimesTen service running? To start the service, double-click
Control Panel > Administrative Tools > Services, choose the
TimesTen Data Manager service, and click Start.
Building and running the JDBC demo applications
Source code for a demo application is provided in the install_dir/
/demo/jdbc
distribution. Information about these demos is included in the
file included in the
To run the demos, source the
ttemoenv.csh on Unix or run ttdemoenv.bat on Windows, first, to set
up your demo environment correctly.
You can use the
directory on UNIX or
environment variables.
directory as part of the TimesTen Data Manager
README
demo directory.
install_dir/demo/ttdemoenv.sh or
ttdemoenv.sh or ttdemoenv.csh in the demo
ttdemoenv.bat on Windows to set these
If using
% . install_dir/demo/ttdemoenv.sh
sh, ksh, bash, zsh or a similar shell, type:
If using csh, tcsh or similar shell, type:
% source install_dir/demo/ttdemoenv.csh
Create the data source name (DSN) that the application relies on. For
details, see “Defining data sources for the demo applications” on page
83. You can use one of the demo data sources already provided by
TimesTen. See the
README file in the install_dir/demo directory to
find instructions on how to run the demo.
Viewing the online documentation
Online copies of TimesTen documentation are installed along with the
TimesTen product unless you choose not to install the documentation.
Documentation is provided in PDF format and can be viewed with the
Adobe Acrobat Reader. If you do not currently have the Adobe Acrobat
Reader installed, it is available from the Adobe Systems web page,
http://www.adobe.com.
Online documentation is installed in the
Note: The online documentation represents the most current release of
the documentation.
install_dir/doc directory.
TimesTen Installation 85
Page 94

Installation problems
To avoid problems during installation, make sure you have met all
prerequisites. Using information in the installation guide and the release
notes, check that:
• You are running a supported version of the OS.
• You have sufficient disk space.
• On UNIX, you are installing as
administrator.
• For Windows, you are installing as user
member of the local
• You have installed all required operating system patches.
• You have made all required kernel configuration changes.
root or the TimesTen instance
Administrator who is a
Administrators group.
86 Oracle TimesTen In-Memory Database Installation Guide
Page 95

Introduction
When a TimesTen data store is loaded into shared memory, many of its
attributes are fixed, including size, logging options, TimesTen software
release number, and the location of its checkpoint and log files on disk.
This chapter describes the steps required to change these attributes and
to upgrade TimesTen data stores when you install a new version of
TimesTen.
Data store compatibility
Starting with TimesTen version 7.0.0.0.0, TimesTen version numbers
consist of five components. Prior vers i on s of TimesTen used only three
numbers to indicate the version, such as 5.1.35. The first two numbers in
the version are used to indicate a major release of TimesTen, such as
5.1.x or 7.0.x.y.z. The third number indicated the patch release of a
major release of TimesTen. For example, TimesTen version number
5.1.35 indicates the 35th patch release of TimesTen version 5.1.
TimesTen data stores are not compatible between major releases, but
they are always compatible between patch releases. For example, a data
store created with TimesTen version 5.1.35 is not compatible with a
TimesTen version 7.0.0.0.0 application, but a data store created with
TimesTen 7.0.0.0.0 will be compatible with a TimesTen version
7.0.1.0.0 application.
When referring to a TimesTen version, the version number will often be
abbreviated to the major version number. For example, version 7.0.0.0.0
may be abbreviated to 7.0.
–
3
Data S tore Upgrades
Data type compatibility
Beginning with TimesT en version 7.0, T imesTen supports a selection of
Oracle data types in addition to the original TimesTen data types that are
maintained for backward compatibility. For details on both the new and
87
Page 96

backward-compatible data types, see “Type specifications” on page 8 in
the Oracle TimesTen In-Memory Database SQL Reference Guide.
Because some of the new Oracle data types have the same names as the
backward-compatible TimesTen data types, a set of aliases has been
added for addressing the data types. Which data types the aliases refer to
depends on the TypeMode that has been set for the data store. See
“TypeMode” on page 20 of the Oracle TimesTen In-Memory Database
API Reference Guide for more information.
TimesTen backward-compatible data types in version 7.0 are
replication-compatible with the data types in versions of TimesT en prior
to 7.0. However, TimesTen backward-compatible data types are not
compatible with TimesTen Cache Connect to Oracle, only the new
Oracle data types can be used with Cache Connect to Oracle. If you
wish to use Cache Connect to Oracle, you must convert any original
TimesTen data types to the new Oracle data types when performing the
data store upgrade with ttMigrate. See “Converting data types to
Oracle data types” on page 90 for details.
Oracle data types are not replication-compatible with versions of
TimesTen prior to 7.0. If you wish to perform an upgrade that requires
replication with a version of TimesTen from before 7.0, you must
upgrade the original data types as TimesT en data types. See “Upgrading
data types as TimesTen data types” on page 90 for more information.
Data store character set
Beginning with TimesTen 7.0, TimesTen requires a data store to be
configured to support a specific character set when it is created. The
character set for the data store is specified using the data store attribute
DatabaseCharacterSet. The value of this attribute is used to determine
which characters may be input to and output from character fields, and
how character data is stored and sorted. See “Choosing a database
character set” on page 74 of the Oracle TimesTen In-Memory Database
Operations Guide for more information.
Before upgrading your data store to TimesTen 7.0, you must specify a
data store character set by adding the DatabaseCharacterSet attribute
to your data store’s DSN. This attribute will be ignored by versions of
TimesTen prior to 7.0. In most cases, you will want to choose a data
store character set that makes sense for your region and that matches the
character data that is already present in your data store. However, there
are three important restrictions you must consider:
• If you plan to use the data store with TimesTen Cache Connect to
Oracle, you must specify a value for DatabaseCharacterSet that is
88 Oracle TimesTen In-Memory Database Installation Guide
Page 97

the same as the character set specified for the Oracle database that
the TimesTen data store connects to.
• Replication is not possible between data stores with different
character sets. Because data stores created with versions of TimesTen
prior to 7.0 do not have a data store character set specified, a special
data store character set, TIMESTEN8, has been created, which
allows replication compatibility between data stores created by
TimesTen 7.0 and those created by earlier releases. If you plan to
perform the data store upgrade as an online upgrade with replication
(see “Performing an online upgrade with replication” on page 104),
then you must specify a DatabaseCharacterSet of TIMESTEN8 in
your TimesTen 7.0 DSN.
• If you use TimesTen Client/Server and intend to connect to the
upgraded data store with an application linked to a Client ODBC
library from a version prior to TimesTen 7.0, you must specify a
DatabaseCharacterSet of TIMESTEN8 in your TimesTen 7.0 DSN
in order to ensure compatibility. See “Performing a Client/Server
online upgrade from a TimesTen version prior to 6.0” on page 113 or
“Performing a Client/Server online upgrade from TimesTen version
6.0 and above” on page 116.
Note: The TIMESTEN8 data store character set is intended for use
only when transitioning from a version of TimesTen prior to 7.0. When
you no longer need your data store to replicate to a pre-7.0 version of
TimesTen, or to connect to a pre-7.0 client application, you should use
ttMigrate to convert your data store to a data store character set other
than TIMESTEN8. See “Data store character set conversion” on page
91 for details.
Data type conversion
When performing an upgrade from a version prior to TimesTen 7.0, you
must choose whether to preserve the data types in your data store as
TimesTen data types, or whether to convert them to Oracle data types.
Your planned use for the data store and your preferred upgrade method
will have an impact on this decision.
Data Store Upgrades 89
Page 98

Converting data types to Oracle dat a types
Note: If you intend to use your data store with TimesTen Cache
Connect to Oracle, you must convert your data types to Oracle data
types. However, you will not be able to perform an online upgrade using
replication.
T o convert the data types from a release prior to T imesTen 7.0 to Oracle
data types, you must use the
when you restore your data store as part of your upgrade procedure. For
example, if you restore the data store
procedure, you may use the following to upgrade the data types to
Oracle data types:
ttMigrate -r -convertTypesToOra salesdata salesdata.mig
See “TimesTen to Oracle data type conversions” on page 148 in the
Oracle TimesTen In-Memory Database API Reference Guide for more
information.
Note: Because the Oracle and TimesTen versions of some data types
behave slightly differently, you should thoroughly test any applicati ons
written for versions of TimesTen prior to 7.0 with the new Oracle data
types before deploying them with TimesTen 7.0.
-convertTypesToOra option for ttMigrate
salesdata as part of an upgrade
Upgrading data types as TimesTen data types
Note: If you intend to perform an online upgrade using replication, you
must upgrade your data types as TimesTen data types. See “Online
upgrades with replication” on page 94 for more information.
If you choose to upgrade the data types in a data store from a version
prior to TimesTen 7.0 as TimesTen data types, you do not need to use
any special options when restoring the data store with ttMigrate. The
data types from a version prior to TimesTen 7.0 will automatically be
restored as TimesTen data types.
Note: The default TypeMode attribute for data stores in TimesTen 7.0
is 0, which indicates that standard data type names, such as CHAR, will
refer to the Oracle versions of the data types. In order to guarantee
compatibility with applications written for TimesTen versions before
7.0, you should configure the DSN for your data store with a TypeMode
of 1 before restoring the data store with ttMigrate as part of the upgrade
procedure.
90 Oracle TimesTen In-Memory Database Installation Guide
Page 99

Data store character set conversion
Beginning with TimesTen 7.0, a character set must be specified for each
TimesTen data store using the DSN attribute DatabaseCharacterSet.
In some cases, you may need to change the configured data store
character set as part of the upgrade process. There are two different
cases in which a data store character set conversion will be required:
• You have specified the data store character set as TIMESTEN8 in
order to upgrade your data store from a version of TimesTen prior to
7.0 using online upgrade with replication and/or client/server. After
the upgrade is complete for all data stores and client applications,
you should convert each data store from this special transitional
character set to the national character set you prefer to use for your
region. See “Converting from the TIMESTEN8 character set” on
page 91.
• You need to change your data store’s character set from the one that
you originally specified to a new one that fits your requirements
more closely. See “Converting from a character set other than
TIMESTEN8” on page 92.
Converting from the TIMESTEN8 character set
You may use ttMigrate to convert a data store from TIMESTEN8 to
any other character set by completing the following steps:
1. Save the data store to a file using ttMigrate. For example, to save the
data store
ttMigrate -c DSN=SalesData salesdata.mig
2. Destroy the data store:
ttDestroy SalesData
3. Change the value of the DSN attribute DatabaseCharacterSet for your
data store to the value specifying the new character set. For example, if
you want your data store to use the WE8ISO8859P1 character set
instead of TIMESTEN8, use the following line in your ODBCINI file:
DatabaseCharacterSet=WE8ISO8859P1
SalesData to the file salesdata.mig, use the command:
Data Store Upgrades 91
Page 100

4. Load the data store from the file using ttMigrate with the
-noCharsetConversion command line option. This option ensures that
no character values are changed when the data is loaded into the DSN
using the new character set. For example:
ttMigrate -r -noCharsetConversion
DSN=SalesData salesdata.mig
Note: If you find that you have accidentally converted your data store
from TIMESTEN8 to the wrong character set, you can use the same
procedure to convert your data store to the correct character set without
any accidental modification of the character data.
Converting from a character set other than TIMESTEN8
You may use ttMigrate to convert a data store from any character set to
any other character set by completing the following steps:
1. Save the data store to a file using ttMigrate. For example, to save the
data store
ttMigrate -c DSN=SalesData salesdata.mig
2. Destroy the data store:
ttDestroy SalesData
3. Change the value of the DSN attribute DatabaseCharacterSet for your
data store to the value specifying the new character set. For example, if
you want your data store to use the WE8ISO8859P1 character set, use
the following line in your ODBCINI file:
DatabaseCharacterSet=WE8ISO8859P1
4. Load the data store from the file using ttMigrate. TimesTen will
automatically convert the character data from the character set the file
was saved with to the character set used by the DSN. For example:
ttMigrate -r DSN=SalesData salesdata.mig
SalesData to the file salesdata.mig, use the command:
Note: It is possible that character data will be lost in the conversion
process if no mapping exists from one character set to the other for a
given character.
92 Oracle TimesTen In-Memory Database Installation Guide
 Loading...
Loading...