Page 1
Novell®
www.novell.com
Reference Guide
novdocx (en) 7 January 2010
AUTHORIZED DOCUMENTATION
Sentinel
6.1 SP2
February 2010
TM
Sentinel 6.1 Reference Guide
Page 2

Legal Notices
Novell, Inc., makes no representations or warranties with respect to the contents or use of this documentation, and
specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose.
Further, Novell, Inc., reserves the right to revise this publication and to make changes to its content, at any time,
without obligation to notify any person or entity of such revisions or changes.
Further, Novell, Inc., makes no representations or warranties with respect to any software, and specifically disclaims
any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc.,
reserves the right to make changes to any and all parts of Novell software, at any time, without any obligation to
notify any person or entity of such changes.
Any products or technical information provided under this Agreement may be subject to U.S. export controls and the
trade laws of other countries. You agree to comply with all export control regulations and to obtain any required
licenses or classification to export, re-export or import deliverables. You agree not to export or re-export to entities
on the current U.S. export exclusion lists or to any embargoed or terrorist countries as specified in the U.S. export
laws. You agree to not use deliverables for prohibited nuclear, missile, or chemical biological weaponry end uses.
See the Novell International Trade Services Web page (http://www.novell.com/info/exports/) for more information
on exporting Novell software. Novell assumes no responsibility for your failure to obtain any necessary export
approvals.
novdocx (en) 7 January 2010
Copyright © 1999-2010 Novell, Inc. All rights reserved. No part of this publication may be reproduced, photocopied,
stored on a retrieval system, or transmitted without the express written consent of the publisher.
Novell, Inc., has intellectual property rights relating to technology embodied in the product that is described in this
document. In particular, and without limitation, these intellectual property rights may include one or more of the U.S.
patents listed on the Novell Legal Patents Web page (http://www.novell.com/company/legal/patents/) and one or
more additional patents or pending patent applications in the U.S. and in other countries.
Novell, Inc.
404 Wyman Street, Suite 500
Waltham, MA 02451
U.S.A.
www.novell.com
Online Documentation: To access the latest online documentation for this and other Novell products, see
the Novell Documentation Web page (http://www.novell.com/documentation).
Page 3

Novell Trademarks
For Novell trademarks, see the Novell Trademark and Service Mark list (http://www.novell.com/company/legal/
trademarks/tmlist.html).
Third-Party Materials
All third-party trademarks are the property of their respective owners.
novdocx (en) 7 January 2010
Page 4

novdocx (en) 7 January 2010
4 Sentinel 6.1 Reference Guide
Page 5

Contents
Preface 13
novdocx (en) 7 January 2010
1Sentinel
TM
User Reference Introduction 15
2 Sentinel Event Fields 17
2.1 Event Field Labels and Tags . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
2.1.1 Free-Form Filters and Correlation Rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
2.1.2 Actions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
2.1.3 Proprietary Collectors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
2.1.4 JavaScript Collectors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
2.2 List of Fields and Representations. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
3 Sentinel Control Center User Permissions 31
3.1 General . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
3.1.1 General – Public Filters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
3.1.2 General – Manage Private Filters of Other Users . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
3.1.3 General – Integration Actions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
3.2 Active Views. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
3.2.1 Active Views – Menu Items . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
3.2.2 Active Views – Active Views . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
3.3 iTRAC. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
3.3.1 iTRAC - Template Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
3.3.2 iTRAC - Process Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
3.4 Incidents. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
3.5 Integrators . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
3.6 Actions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
3.7 Event Source Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
3.8 Analysis Tab. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
3.9 Advisor Tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
3.10 Administration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
3.10.1 Administration – Global Filters. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
3.10.2 Administration – Server Views. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
3.11 Correlation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
3.12 Solution Pack . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
3.13 Identity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
4 Sentinel Correlation Engine RuleLG Language 41
4.1 Correlation RuleLG Language Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
4.2 Event Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
4.3 Event Operations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
4.3.1 Filter Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
4.3.2 Window Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
4.3.3 Trigger Operation. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
4.4 Rule Operations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
4.4.1 Gate Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
4.4.2 Sequence Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
Contents 5
Page 6

4.5 Operators . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
4.5.1 Flow Operator . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
4.5.2 Union Operator . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
4.5.3 Intersection Operator . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
4.5.4 Discriminator Operator. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
4.6 Order of Operators . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
4.7 Differences between Correlation in 5.x and 6.x . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
5 Sentinel Data Access Service 51
5.1 DAS Container Files. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
5.1.1 Reconfiguring Database Connection Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
5.1.2 DAS Logging Properties Configuration Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
5.1.3 Certificate Management for DAS_Proxy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
6 Sentinel Accounts and Password Changes 59
6.1 Sentinel Default Users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
6.1.1 Native Database Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
6.1.2 Windows Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
6.2 Password Changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60
6.2.1 Changing Password. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60
6.2.2 Sentinel Updates After a Password Change . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61
novdocx (en) 7 January 2010
7 Sentinel Database Views for Oracle 65
7.1 Views . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 65
7.1.1 ACTVY_PARM_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 65
7.1.2 ACTVY_REF_PARM_VAL_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 65
7.1.3 ACTVY_REF_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
7.1.4 ACTVY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
7.1.5 ADV_NXS_FEED_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
7.1.6 ADV_NXS_PRODUCTS_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 68
7.1.7 ADV_NXS_SIGNATURES_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
7.1.8 ADV_NXS_MAPPINGS_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
7.1.9 ADV_OSVDB_DETAILS_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70
7.1.10 ADV_NXS_KB_PATCH_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73
7.1.11 ADV_NXS_KB_PRODUCTSREF_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
7.1.12 ASSET_CATEGORY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
7.1.13 ASSET_HOSTNAME_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
7.1.14 ASSET_IP_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
7.1.15 ASSET_LOCATION_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
7.1.16 ASSET_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76
7.1.17 ASSET_VALUE_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76
7.1.18 ASSET_X_ENTITY_X_ROLE_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 77
7.1.19 ASSOCIATIONS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 77
7.1.20 ATTACHMENTS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
7.1.21 AUDIT_RECORD_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
7.1.22 CONFIGS_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
7.1.23 CONTACTS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
7.1.24 CORRELATED_EVENTS_RPT_V (legacy view) . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
7.1.25 CORRELATED_EVENTS_RPT_V1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
7.1.26 CRITICALITY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
7.1.27 CUST_HIERARCHY_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
7.1.28 CUST_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
7.1.29 ENTITY_TYPE_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
7.1.30 ENV_IDENTITY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
6 Sentinel 6.1 Reference Guide
Page 7

7.1.31 ESEC_CONTENT_GRP_CONTENT_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
7.1.32 ESEC_CONTENT_GRP_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
7.1.33 ESEC_CONTENT_PACK_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
7.1.34 ESEC_CONTENT_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
7.1.35 ESEC_CTRL_CTGRY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
7.1.36 ESEC_CTRL_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
7.1.37 ESEC_DISPLAY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
7.1.38 ESEC_PORT_REFERENCE_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
7.1.39 ESEC_PROTOCOL_REFERENCE_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
7.1.40 ESEC_SEQUENCE_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
7.1.41 ESEC_UUID_UUID_ASSOC_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
7.1.42 EVENTS_ALL_RPT_V (legacy view) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
7.1.43 EVENTS_ALL_RPT_V1 (legacy view) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
7.1.44 EVENTS_RPT_V (legacy view) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
7.1.45 EVENTS_RPT_V1 (legacy view). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
7.1.46 EVENTS_RPT_V2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
7.1.47 EVENTS_RPT_V3. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92
7.1.48 EVT_AGENT_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
7.1.49 EVT_AGENT_RPT_V3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97
7.1.50 EVT_ASSET_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97
7.1.51 EVT_ASSET_RPT_V3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 98
7.1.52 EVT_DEST_EVT_NAME_SMRY_1_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
7.1.53 EVT_DEST_SMRY_1_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
7.1.54 EVT_DEST_TXNMY_SMRY_1_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
7.1.55 EVT_NAME_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
7.1.56 EVT_PORT_SMRY_1_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
7.1.57 EVT_PRTCL_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
7.1.58 EVT_PRTCL_RPT_V3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
7.1.59 EVT_RSRC_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
7.1.60 EVT_SEV_SMRY_1_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
7.1.61 EVT_SRC_COLLECTOR_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
7.1.62 EVT_SRC_GRP_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
7.1.63 EVT_SRC_MGR_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104
7.1.64 EVT_SRC_OFFSET_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104
7.1.65 EVT_SRC_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104
7.1.66 EVT_SRC_SMRY_1_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
7.1.67 EVT_SRC_SRVR_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106
7.1.68 EVT_TXNMY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106
7.1.69 EVT_USR_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106
7.1.70 EVT_XDAS_TXNMY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107
7.1.71 EXTERNAL_DATA_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107
7.1.72 HIST_CORRELATED_EVENTS_RPT_V (legacy view) . . . . . . . . . . . . . . . . . . . . . 108
7.1.73 HIST_EVENTS_RPT_V (legacy view). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
7.1.74 IMAGES_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
7.1.75 INCIDENTS_ASSETS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
7.1.76 INCIDENTS_EVENTS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
7.1.77 INCIDENTS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
7.1.78 INCIDENTS_VULN_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110
7.1.79 L_STAT_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110
7.1.80 LOGS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110
7.1.81 MSSP_ASSOCIATIONS_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
7.1.82 NETWORK_IDENTITY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
7.1.83 ORGANIZATION_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
7.1.84 PERSON_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 112
7.1.85 PHYSICAL_ASSET_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 112
7.1.86 PRODUCT_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
7.1.87 ROLE_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
7.1.88 RPT_LABELS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
7.1.89 SENSITIVITY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
novdocx (en) 7 January 2010
Contents 7
Page 8

7.1.90 SENTINEL_HOST_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
7.1.91 SENTINEL_PLUGIN_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
7.1.92 SENTINEL_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
7.1.93 STATES_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
7.1.94 UNASSIGNED_INCIDENTS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
7.1.95 USERS_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
7.1.96 USR_ACCOUNT_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
7.1.97 USR_IDENTITY_EXT_ATTR_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
7.1.98 USR_IDENTITY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
7.1.99 VENDOR_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
7.1.100 VULN_CALC_SEVERITY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
7.1.101 VULN_CODE_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
7.1.102 VULN_INFO_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
7.1.103 VULN_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
7.1.104 VULN_RSRC_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
7.1.105 VULN_RSRC_SCAN_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122
7.1.106 VULN_SCAN_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122
7.1.107 VULN_SCAN_VULN_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122
7.1.108 VULN_SCANNER_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
7.1.109 WORKFLOW_DEF_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
7.1.110 WORKFLOW_INFO_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 124
7.2 Deprecated Views . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 124
novdocx (en) 7 January 2010
8 Sentinel Database Views for Microsoft SQL Server 125
8.1 Views . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
8.1.1 ACTVY_PARM_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
8.1.2 ACTVY_REF_PARM_VAL_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
8.1.3 ACTVY_REF_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
8.1.4 ACTVY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
8.1.5 ADV_NXS_FEED_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127
8.1.6 ADV_NXS_PRODUCTS_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127
8.1.7 ADV_NXS_SIGNATURES_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 128
8.1.8 ADV_NXS_MAPPINGS_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
8.1.9 ADV_OSVDB_DETAILS_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
8.1.10 ADV_NXS_KB_PATCH_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 132
8.1.11 ADV_NXS_KB_PRODUCTSREF_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
8.1.12 ANNOTATIONS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
8.1.13 ASSET_CATEGORY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
8.1.14 ASSET_HOSTNAME_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
8.1.15 ASSET_IP_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
8.1.16 ASSET_LOCATION_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135
8.1.17 ASSET_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135
8.1.18 ASSET_VALUE_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 136
8.1.19 ASSET_X_ENTITY_X_ROLE_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 136
8.1.20 ASSOCIATIONS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
8.1.21 ATTACHMENTS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
8.1.22 AUDIT_RECORD_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
8.1.23 CONFIGS_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
8.1.24 CONTACTS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
8.1.25 CORRELATED_EVENTS_RPT_V (legacy view) . . . . . . . . . . . . . . . . . . . . . . . . . . 139
8.1.26 CORRELATED_EVENTS_RPT_V1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
8.1.27 CRITICALITY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 140
8.1.28 CUST_HIERARCHY_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 140
8.1.29 CUST_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
8.1.30 ENTITY_TYPE_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
8.1.31 ENV_IDENTITY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
8.1.32 ESEC_CONTENT_GRP_CONTENT_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 142
8 Sentinel 6.1 Reference Guide
Page 9

8.1.33 ESEC_CONTENT_GRP_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 142
8.1.34 ESEC_CONTENT_PACK_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
8.1.35 ESEC_CONTENT_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
8.1.36 ESEC_CTRL_CTGRY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
8.1.37 ESEC_CTRL_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 144
8.1.38 ESEC_DISPLAY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 144
8.1.39 ESEC_PORT_REFERENCE_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 145
8.1.40 ESEC_PROTOCOL_REFERENCE_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 146
8.1.41 ESEC_SEQUENCE_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 146
8.1.42 ESEC_UUID_UUID_ASSOC_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
8.1.43 EVENTS_ALL_RPT_V (legacy view) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
8.1.44 EVENTS_ALL_RPT_V1 (legacy view) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
8.1.45 EVENTS_ALL_V (legacy view) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
8.1.46 EVENTS_RPT_V (legacy view) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
8.1.47 EVENTS_RPT_V1 (legacy view). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
8.1.48 EVENTS_RPT_V2. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
8.1.49 EVENTS_RPT_V3. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 152
8.1.50 EVT_AGENT_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 156
8.1.51 EVT_AGENT_RPT_V3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
8.1.52 EVT_ASSET_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
8.1.53 EVT_ASSET_RPT_V3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
8.1.54 EVT_DEST_EVT_NAME_SMRY_1_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 159
8.1.55 EVT_DEST_SMRY_1_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 159
8.1.56 EVT_DEST_TXNMY_SMRY_1_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 160
8.1.57 EVT_NAME_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 161
8.1.58 EVT_PORT_SMRY_1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 161
8.1.59 EVT_PORT_SMRY_1_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 162
8.1.60 EVT_PRTCL_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 162
8.1.61 EVT_RSRC_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 162
8.1.62 EVT_SEV_SMRY_1_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
8.1.63 EVT_SRC_COLLECTOR_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
8.1.64 EVT_SRC_GRP_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164
8.1.65 EVT_SRC_MGR_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164
8.1.66 EVT_SRC_OFFSET_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164
8.1.67 EVT_SRC_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 165
8.1.68 EVT_SRC_SMRY_1_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 165
8.1.69 EVT_SRC_SRVR_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 166
8.1.70 EVT_TXNMY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 166
8.1.71 EVT_USR_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
8.1.72 EVT_XDAS_TXNMY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
8.1.73 EXTERNAL_DATA_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 168
8.1.74 HIST_CORRELATED_EVENTS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 168
8.1.75 HIST_CORRELATED_EVENTS_RPT_V (legacy view) . . . . . . . . . . . . . . . . . . . . . 169
8.1.76 HIST_EVENTS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169
8.1.77 HIST_EVENTS_RPT_V (legacy view). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
8.1.78 IMAGES_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
8.1.79 INCIDENTS_ASSETS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
8.1.80 INCIDENTS_EVENTS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
8.1.81 INCIDENTS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
8.1.82 INCIDENTS_VULN_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
8.1.83 L_STAT_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
8.1.84 LOGS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
8.1.85 MSSP_ASSOCIATIONS_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
8.1.86 NETWORK_IDENTITY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
8.1.87 ORGANIZATION_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
8.1.88 PERSON_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
8.1.89 PHYSICAL_ASSET_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
8.1.90 PRODUCT_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 177
8.1.91 ROLE_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 177
novdocx (en) 7 January 2010
Contents 9
Page 10

8.1.92 RPT_LABELS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178
8.1.93 SENSITIVITY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178
8.1.94 SENTINEL_HOST_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178
8.1.95 SENTINEL_PLUGIN_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
8.1.96 SENTINEL_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
8.1.97 STATES_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
8.1.98 UNASSIGNED_INCIDENTS_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
8.1.99 USERS_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
8.1.100 USR_ACCOUNT_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
8.1.101 USR_IDENTITY_EXT_ATTR_RPT_V. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
8.1.102 USR_IDENTITY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
8.1.103 VENDOR_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
8.1.104 VULN_CALC_SEVERITY_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
8.1.105 VULN_CODE_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
8.1.106 VULN_INFO_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 184
8.1.107 VULN_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 184
8.1.108 VULN_RSRC_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 185
8.1.109 VULN_RSRC_SCAN_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 186
8.1.110 VULN_SCAN_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 186
8.1.111 VULN_SCAN_VULN_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 186
8.1.112 VULN_SCANNER_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
8.1.113 WORKFLOW_DEF_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
8.1.114 WORKFLOW_INFO_RPT_V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
8.2 Deprecated Views . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 188
novdocx (en) 7 January 2010
A Sentinel Troubleshooting Checklist 189
B Sentinel Service Logon Account 193
B.1 Sentinel Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 193
B.2 Introduction to Service Logon Accounts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 193
B.2.1 Disadvantages of running a service in the context of a user logon . . . . . . . . . . . . . 194
B.3 To Setup NT AUTHORITY\NetworkService as the Logon Account for Sentinel Service. . . . 195
B.3.1 Adding Sentinel Service as a Login Account to ESEC and ESEC_WF DB
Instances . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 195
B.3.2 Changing logon account . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 198
B.3.3 Setting the Sentinel Service to Start Successfully . . . . . . . . . . . . . . . . . . . . . . . . . . 199
C Sentinel Service Permission Tables 201
C.1 Advisor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
C.2 Collector Manager . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 202
C.3 Correlation Engine . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 203
C.4 Data Access Server (DAS) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 204
C.5 Sentinel Communication Server. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 205
C.6 Sentinel Service . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 206
C.7 Reporting Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 206
D Sentinel Database Users, Roles, and Access Permissions 207
D.1 Sentinel Database Instance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 207
D.1.1 ESEC . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 207
D.1.2 ESEC_WF . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 207
D.2 Sentinel Database Users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 207
D.2.1 Summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 208
10 Sentinel 6.1 Reference Guide
Page 11

D.2.2 esecadm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 208
D.2.3 esecapp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 208
D.2.4 esecdba . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 209
D.2.5 esecrpt . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 209
D.3 Sentinel Database Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 209
D.3.1 Summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 209
D.3.2 ESEC_APP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 209
D.3.3 ESEC_ETL . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 218
D.3.4 ESEC_USER . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 224
D.4 Sentinel Server Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 228
D.5 Windows Domain Authentication DB users and permissions. . . . . . . . . . . . . . . . . . . . . . . . . 228
E Sentinel Log Locations 229
E.1 Sentinel Data Manager . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 229
E.2 iTRAC. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 229
E.3 Advisor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230
E.4 Event Insertion . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230
E.5 Database Queries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230
E.6 Active Views . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230
E.7 Aggregation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
E.8 Wrapper . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
E.9 Collector Manager . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
E.10 Correlation Engine . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
E.11 Sentinel Control Center . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 232
E.12 DAS Proxy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 232
E.13 Solution Designer. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 232
E.14 Multiple Instances . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 232
novdocx (en) 7 January 2010
Contents 11
Page 12

novdocx (en) 7 January 2010
12 Sentinel 6.1 Reference Guide
Page 13

Preface
SentinelTM is a security information and event management solution that receives information from
many sources throughout an enterprise, standardizes it, prioritizes it and presents it to you to make
threat, risk and policy related decisions.
The Sentinel 6.1 Reference Guide is your reference for the following:
Chapter 1, “SentinelTM User Reference Introduction,” on page 15
Chapter 2, “Sentinel Event Fields,” on page 17
Chapter 3, “Sentinel Control Center User Permissions,” on page 31
Chapter 4, “Sentinel Correlation Engine RuleLG Language,” on page 41
Chapter 5, “Sentinel Data Access Service,” on page 51
Chapter 6, “Sentinel Accounts and Password Changes,” on page 59
Chapter 7, “Sentinel Database Views for Oracle,” on page 65
Chapter 8, “Sentinel Database Views for Microsoft SQL Server,” on page 125
novdocx (en) 7 January 2010
Audience
This documentation is intended for Information Security Professionals.
Feedback
We want to hear your comments and suggestions about this manual and the other documentation
included with this product. Please use the User Comments feature at the bottom of each page of the
online documentation and enter your comments there.
Additional Documentation
Sentinel Technical documentation is broken down into several different volumes. They are:
Sentinel 6.1 Installation Guide
Sentinel 6.1 User Guide
Sentinel 6.1 User Reference Guide
The documentation for this product is available at http://www.novell.com/documentation/
sentinel61/index.html (http://www.novell.com/documentation/sentinel61/index.html)
Additional documentation on developing collectors (proprietary or JavaScript) and JavaScript
correlation actions is available at the Novell Developer Community web site: http://
developer.novell.com/wiki/index.php?title=Develop_to_Sentinel (http://developer.novell.com/
wiki/index.php?title=Develop_to_Sentinel)
Documentation Conventions
The following are the conventions used in this manual:
Notes and Warnings
Preface 13
Page 14

NOTE: Notes provide additional information that may be useful or for reference.
WARNING: Warnings provide additional information that helps you identify and stop performing
actions in the system that cause damage or loss of data.
Commands appear in courier font. For example:
useradd –g dba –d /export/home/oracle –m –s /bin/csh oracle
Go to Start > Program Files > Control Panel to perform this action: Multiple actions in a step.
References
For more information, see “Section Name” (if in the same Chapter).
For more information, see “Chapter Name” (if in the same Guide).
For more information, see “Section Name” in “Chapter Name”, Name of the Guide (if in a
different Guide).
In Novell documentation, a greater-than symbol (>) is used to separate actions within a step and
items in a cross-reference path.
®
A trademark symbol (
, TM, etc.) denotes a Novell trademark. An asterisk (*) denotes a third-party
trademark.
novdocx (en) 7 January 2010
When a single pathname can be written with a backslash for some platforms or a forward slash for
other platforms, the pathname is presented with a backslash. Users of platforms that require a
forward slash, such as Linux or UNIX, should use forward slashes as required by your software.
Contacting Novell
Web Site: http://www.novell.com (http://www.novell.com)
Novell Technical Support: http://support.novell.com/
phone.html?sourceidint=suplnav4_phonesup (http://support.novell.com/
phone.html?sourceidint=suplnav4_phonesup)
Self Support: http://support.novell.com/
support_options.html?sourceidint=suplnav_supportprog (http://support.novell.com/
support_options.html?sourceidint=suplnav_supportprog)
Patch Download Site: http://download.novell.com/index.jsp (http://download.novell.com/
index.jsp)
24x7 support: http://www.novell.com/company/contact.html (http://www.novell.com/
company/contact.html)
For Collectors/Connectors/Reports/Correlation/Hotfixes/TIDS: http://support.novell.com/
products/sentinel (http://support.novell.com/products/sentinel)
14 Sentinel 6.1 Reference Guide
Page 15

1
SentinelTM User Reference
novdocx (en) 7 January 2010
Introduction
The Sentinel User Reference Guide is your reference for:
Collector administrator functions
Collector and Sentinel meta tags
Sentinel console user permissions
This guide assumes that you are familiar with Network Security, Database Administration and
UNIX operating systems.
This guide discusses about:
Sentinel Meta tags
Sentinel User Permissions
Correlation Engine RuleLG Language
Sentinel Data Access Service
Sentinel Accounts and Password Changes
Sentinel Database Views for Oracle
Sentinel Database Views for Microsoft SQL Server
Sentinel correlation engine
Sentinel command line options
Sentinel server database views
1
SentinelTM User Reference Introduction
15
Page 16

novdocx (en) 7 January 2010
16 Sentinel 6.1 Reference Guide
Page 17

2
Sentinel Event Fields
Every Sentinel event or correlated event has certain fields that are automatically populated (such as
Event Time and Event UUID) and other fields that may or may not be populated, depending on the
type of event, the collector parsing, and the mapping service configuration. This event data is visible
in Active Views, historical queries, and reports. They are stored in the database and can be accessed
via the report views. They can also be used in actions available through the right-click event menu,
correlation actions, and iTRAC workflow actions.
2.1 Event Field Labels and Tags
Each field can be referred to by a user-friendly label or a short tag. The user-friendly label is visible
throughout the Sentinel Control Center interface, for example:
Column headers for Active Views, historical event queries, and the Active Browser
Correlation wizard drop-down menus
novdocx (en) 7 January 2010
2
Active View configuration drop-down menus
Each field has a default label, but that label is user-configurable using the Event Configuration
option on the Admin tab. For more information, see “Admin Tab” section in Sentinel 6.1 User
Guide. InitUserName is the default label to represent the account name of the user who initiated the
event, but this can be changed by the administrator. When a user changes the default label, the
changes are reflected in most areas of the interface, including any correlation rules, filters, and rightclick menu options.
WARNING: Changing the default label for any variables other than Customer Variables may cause
confusion when working with Novell Technical Services or other parties who are familiar with the
default names. In addition, JavaScript Collectors built by Novell refer to the default labels described
in this chapter and are not automatically updated to refer to new labels.
Each field also has a short tag name that is always used for internal references to the field and is not
user-configurable. This short tag name may not correspond exactly to the default label; Sentinel
labels have changed over the years, but the underlying short tags remain the same for backward
compatibility. (For example, InitUserName is the default label for the account name of the user who
initiated the event. The default label was previously SourceUserName, and the underlying short tag
is “sun”.)
NOTE: Many of the default labels were updated for clarity in the Sentinel 6.1 release. Because all
filters, actions, and correlation rule definitions are defined using the short tags (even though the
label may be visible in the interface), there is no change in functionality due to the label renaming.
Each field is associated with a specific data type, which corresponds to the data type in the database:
string: limited to 255 characters (unless otherwise specified)
integer: 32 bit signed integer
UUID: 36 character (with hyphens) or 32 character (without hyphens) hexadecimal string in
the format XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX (For example, 6A5349DA-7CBF-1028-9795-000BCDFFF482)
Sentinel Event Fields
17
Page 18
date: Collector Variable must be set with date as number of milliseconds from January 1, 1970
00:00:00 GMT. When displayed in Sentinel Control Center, meta-tags of type date are
displayed in a regular date format.
IPv4: IP address in dotted decimal notation (that is – xxx.xxx.xxx.xxx)
2.1.1 Free-Form Filters and Correlation Rules
Users can use either the tag or the label when they write free-form language in the Sentinel Control
Center. The Sentinel interface shows the user-friendly label.
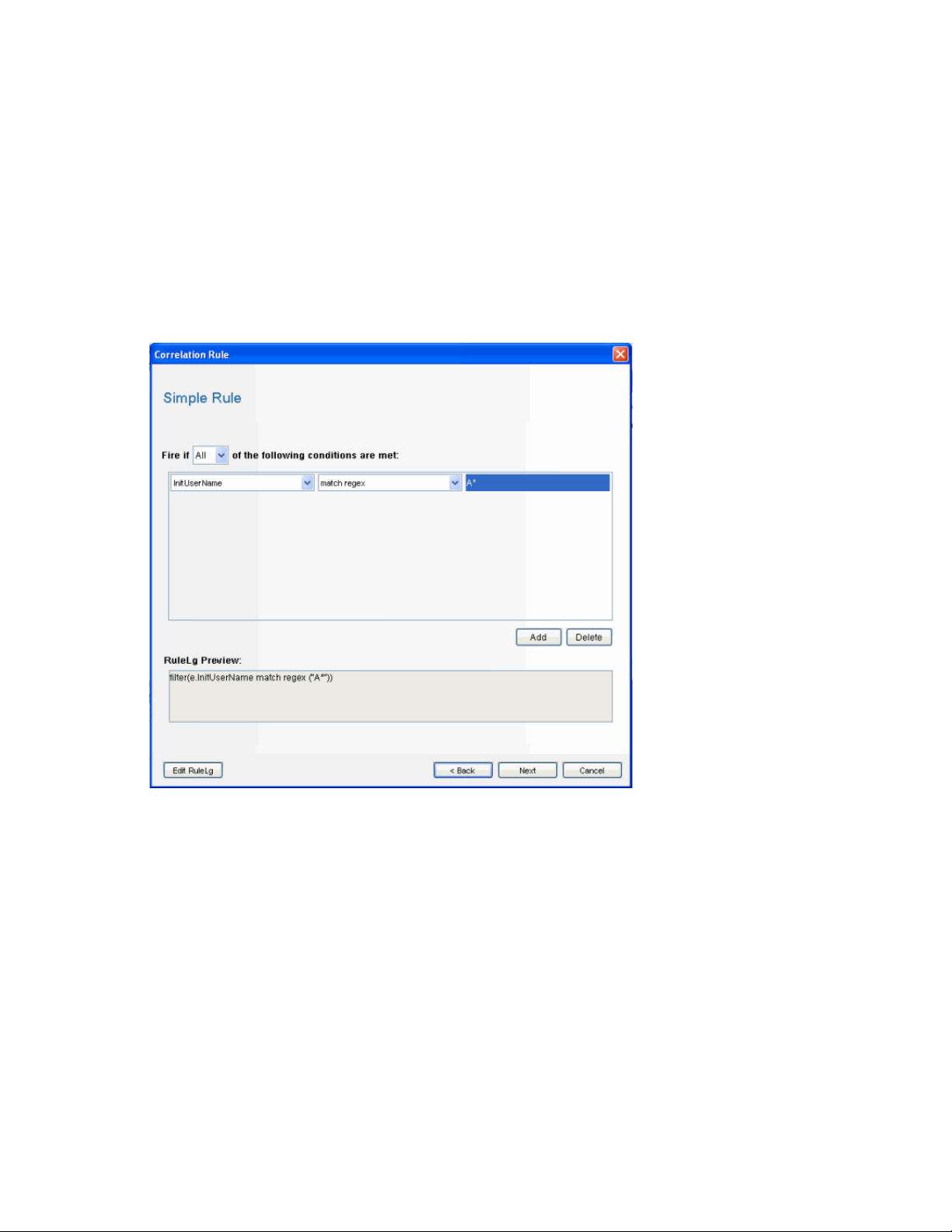
Figure 2-1 Correlation Wizard displaying labels in drop-down and free-form language
novdocx (en) 7 January 2010
18 Sentinel 6.1 Reference Guide
Page 19
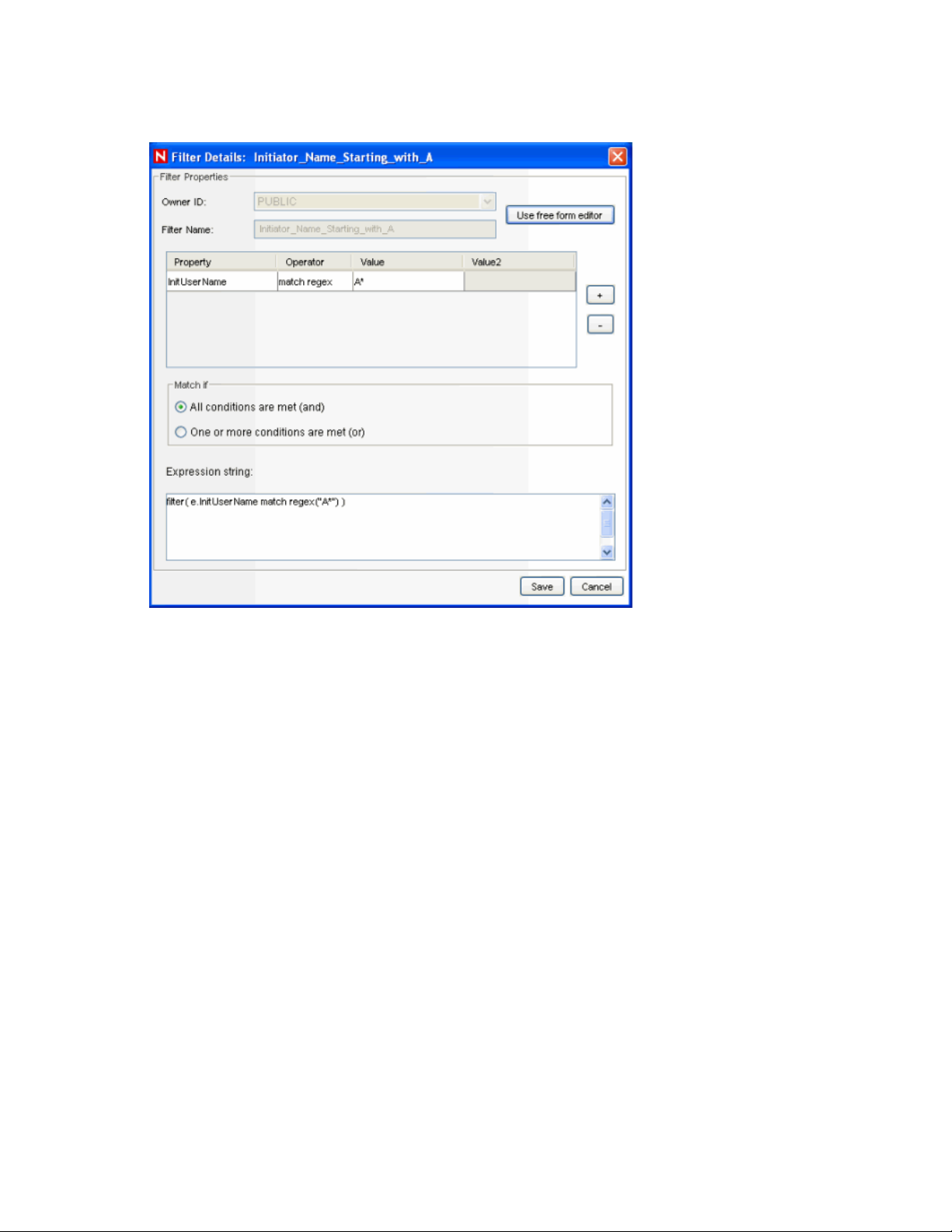
Figure 2-2 Filter Wizard displaying labels in drop-down and free-form language
novdocx (en) 7 January 2010
The representation of fields in the free-form RuleLG language is usually prefaced by “e.” for
example, “e.InitUserName” or “e.sun” can refer to the Initiator User Name for the incoming or
current event. In special cases, “w.” may be used to refer to a field in a past event (for example,
“w.InitUserName”). For more information about the RuleLG language, see Chapter 4, “Sentinel
Correlation Engine RuleLG Language,” on page 41.
2.1.2 Actions
Users can use either the tag or the label when they define parameters to be sent to right-click Event
Menu actions, correlation actions, and iTRAC workflow actions.
To pass a field value to an action, you may use a checklist that shows the labels or type the
parameter name directly into the configuration.
Sentinel Event Fields 19
Page 20
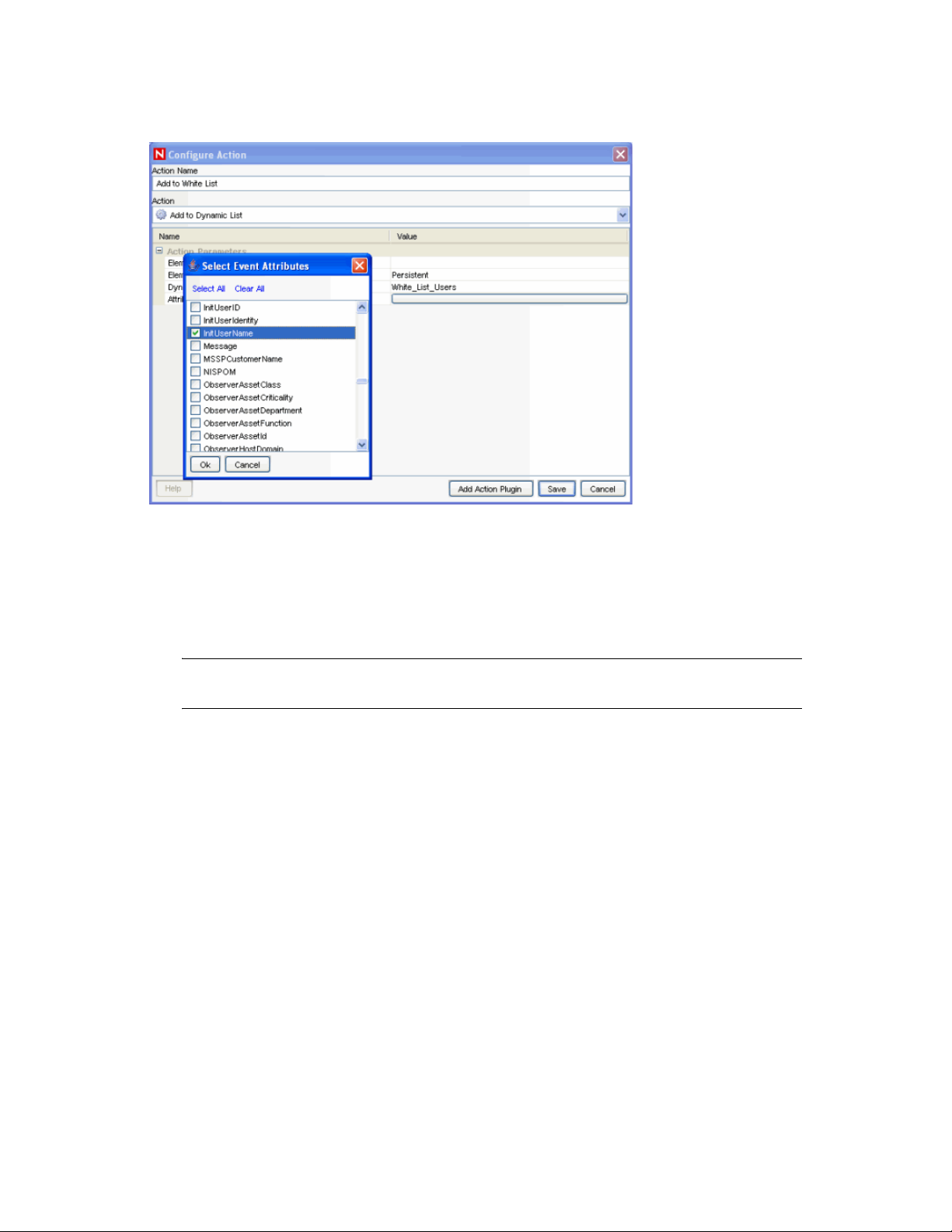
Figure 2-3 Configuration Action - Select Event Attributes window
novdocx (en) 7 January 2010
When you type the label or short tag for a field to be used in an action, the name can be enclosed in
percent signs (%tag%) or dollar signs ($tag$). For example:
%sun% in a correlation action refers to the value of InitUser in the correlated event
$sun$ in a correlation action refers to the value of InitUser in the current, “trigger” event (the
final event that caused the correlation rule to fire)
NOTE: In a right-click menu event operating on a single event, there is no functional
difference between %sun% and $sun$.
For example, to pass the Initiator User Name to a command line action to look up information from
a database about that user, you could use %InitUserName% or %sun%. For more information about
Actions, see “Actions and Integrators” section in Sentinel 6.1 User Guide.
20 Sentinel 6.1 Reference Guide
Page 21
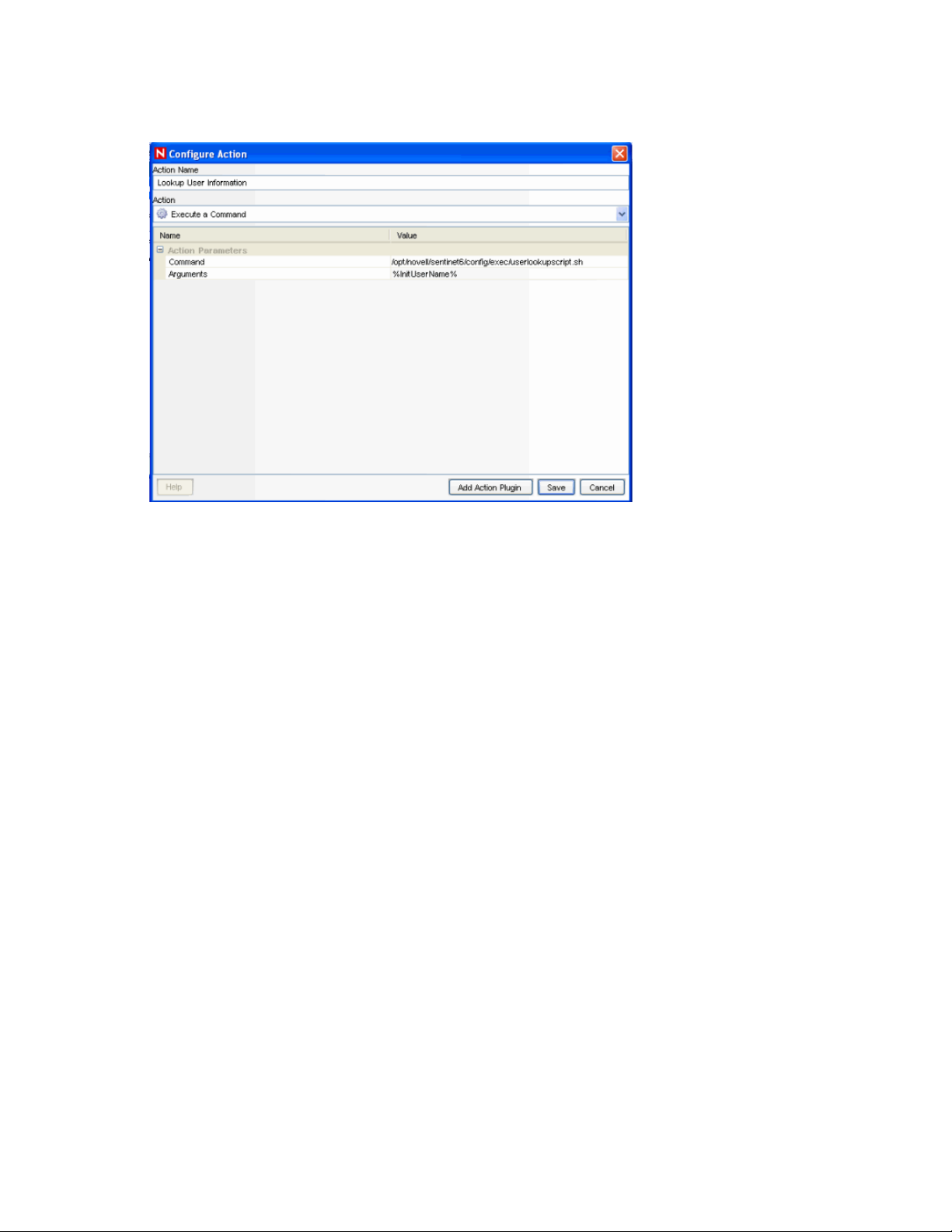
Figure 2-4 Configuration Action window
novdocx (en) 7 January 2010
2.1.3 Proprietary Collectors
Proprietary Collectors, written in Novell’s own language, always use variables based on the short
tag to refer to event fields. The short tag name must be prefaced by a letter and underscore, where
the letter indicates the data type for the field (i_ for integer, s_ for string).
2.1.4 JavaScript Collectors
JavaScript Collectors usually refer to event fields using an “e.” followed by the same user-friendly
label set in Event Configuration in the Sentinel Control Center. For a Sentinel system with a default
configuration, for example, the Initiator User Name would be referred to as “e.InitUserName” in the
JavaScript Collector. There are some exceptions to this general rule. Refer to the Sentinel Collector
SDK (http://developer.novell.com/wiki/index.php?title=Develop_to_Sentinel) for more details.
2.2 List of Fields and Representations
The table on the following pages shows the default labels, descriptions and data types for the
Sentinel event fields, along with the proper way to refer to the tags in filters, correlation rules,
actions, and proprietary collector scripts. Fields that cannot or should not be manipulated in the
Collector parsing do not have a Collector variable.
Sentinel Event Fields 21
Page 22

Table 2-1 Labels and Meta-tags used in Sentinel Control Center and proprietary Collector language
novdocx (en) 7 January 2010
Default Label
Filters and
Correlation
Rules
Menu and
Correlation
Actions
Proprietary
Collector
Language
Data
Typ e
Description
DeviceEventTimeString e.et %et% s_ET string The normalized date and
time of the event, as
reported by the sensor.
DeviceEventTime e.det %det% date The normalized date and
time of the event, as
reported by the sensor.
SentinelProcessTime e.spt %spt% date The date and time
Sentinel received the
event.
BeginTime e.bgnt %bgnt% s_BGNT date The date and time the
event started occurring
(for repeated events).
EndTime e.endt %endt% s_ENDT date The date and time the
event stopped occurring
(for repeated events).
RepeatCount e.rc %rc% s_RC integer The number of times the
same event occurred if
multiple occurrences were
consolidated.
EventTime e.dt %dt% date The normalized date and
time of the event, as given
by the Collector.
SentinelServiceID e.src %src% UUID Unique identifier for the
Sentinel service which
generated this event.
Severity e.sev %sev% i_Severity integer The normalized severity
of the event (0-5).
Vulnerability e.vul %vul% s_VULN integer The vulnerability of the
asset identified in this
event. Set to 1 if Sentinel
detects an exploit against
a vulnerable system.
Requires Advisor.
Criticality e.crt %crt% s_CRIT integer The criticality of the asset
identified in this event.
InitIP e.sip %sip% s_SIP IPv4 IPv4 address of the
initiating system.
TargetIP e.dip %dip% s_DIP IPv4 IPv4 address of the target
system.
Collector e.port %port% string Name of the Collector that
generated this event.
22 Sentinel 6.1 Reference Guide
Page 23

novdocx (en) 7 January 2010
Default Label
Filters and
Correlation
Rules
Menu and
Correlation
Actions
Proprietary
Collector
Language
Data
Typ e
Description
CollectorScript e.agent %agent% string The name of the Collector
Script used by the
Collector to generate this
event.
Resource e.res %res% s_Res string Compliance monitoring
hierarchy level 1
SubResource e.sres %sres% s_SubRes string Subresource name
ObserverHostName e.sn %sn% s_SN string Unqualified hostname of
the observer (sensor) of
the event.
SensorType e.st %st% s_ST string The single character
designator for the sensor
type (N, H, O, V, C, W, A,
I, P, T).
N: Network events
H: Host events
O: Other events
V: Vulnerability
events
C: Correlated events
W: Watchlist events
A: Audit events
I: Internal events
P: Performance
statistics events
T: Realtime events
Protocol e.prot %prot% s_P string Protocol used between
initiating and target
services.
InitHostName e.shn %shn% s_SHN string Unqualified hostname of
the initiating system.
InitServicePort e.spint %spint% s_SPINT integer Port used by service/
application that initiated
the connection.
InitServicePortName e.sp %sp% s_SP string Name of the initiating
service that caused the
event.
TargetHostName e.dhn %dhn% s_DHN string Unqualified hostname of
the target system.
TargetServicePort e.dpint %dpint% s_DPINT integer Network port accessed on
the target.
Sentinel Event Fields 23
Page 24

novdocx (en) 7 January 2010
Default Label
Filters and
Correlation
Rules
Menu and
Correlation
Actions
Proprietary
Collector
Language
Data
Typ e
Description
TargetServicePortName e.dp %dp% s_DP string Name of the target
service affected by this
event.
InitUserName e.sun %sun% s_SUN string Initiating user's account
name. Example jdoe
during an attempt to su.
TargetUserName e.dun %dun% s_DUN string Target user's account
name. Example root
during a password reset.
FileName e.fn %fn% s_FN string The name of the program
executed or the file
accessed, modified or
affected.
ExtendedInformation e.ei %ei% s_EI string Stores additional
collector-processed
information. Values within
this variable are
separated by semi-colons
(;).
ReporterHostName e.rn %rn% s_RN string Unqualified hostname of
the reporter of the event.
ProductName e.pn %pn% s_PN string Indicates the type, vendor
and product code name of
the sensor from which the
event was generated.
Message e.msg %msg% s_BM string Free-form message text
for the event.
DeviceAttackName e.rt1 %rt1% s_RT1 string Device specific attack
name that matches attack
name known by Advisor.
Used in Exploit Detection.
Rt2 e.rt2 %rt2% s_RT2 string Reserved by Novell for
expansion.
Ct1 thru Ct2 e.ct1 thru
e.ct2
%ct1%
thru
%ct2%
s_CT1
and
string Reserved for use by
customers for customerspecific data.
s_CT2
Rt3 e.rt3 %rt3% integer Reserved by Novell for
expansion.
Ct3 e.ct3 %ct3% s_CT3 integer Reserved for use by
customers for customerspecific data.
24 Sentinel 6.1 Reference Guide
Page 25

novdocx (en) 7 January 2010
Default Label
Filters and
Correlation
Rules
Menu and
Correlation
Actions
Proprietary
Collector
Language
Data
Typ e
Description
CorrelatedEventUuids e.ceu %ceu% s_RT3 string List of event UUIDs
associated with th
correlated event. Only
relevant for correlated
events.
CustomerHierarchyId e.rv1 %rv1% s_RV1 integer Used for MSSPs.
ReservedVar2 thru
ReservedVar10
ReservedVar11 thru
ReservedVar20
e.rv2 thru
e.rv10
e.rv11 thru
e.rv20
%rv2%
thru
%rv10%
%rv11%
thru
%rv20%
s_RV2
thru
s_RV10
s_RV11
thru
s_RV20
integer Reserved by Novell for
expansion.
date Reserved by Novell for
expansion.
CollectorManagerId e.rv21 %rv21% s_RV21 UUID Unique identifier for the
Collector Manager which
generated this event.
CollectorId e.rv22 %rv22% s_RV22 UUID Unique identifier for the
Collector which generated
this event.
ConnectorId e.rv23 %rv23% S_RV23 UUID Unique identifier for the
Connector which
generated this event.
EventSourceId e.rv24 %rv24% S_RV24 UUID Unique identifier for the
Event Source which
generated this event.
RawDataRecordId e.rv25 %rv25% S_RV25 UUID Unique identifier for the
Raw Data Record
associated with this event.
ControlPack e.rv26 %rv26% S_RV26 string Sentinel control
categorization level 1 (for
Solution Packs).
EventMetricClass e.rv28 %rv28% s_RV28 string Class of the event-
dependent numeric value.
InitIPCountry e.rv29 %rv29% s_RV29 string Country where the IPv4
address of the initiating
system is located.
TargetIPCountry e.rv30 %rv30% s_RV30 string Country where the IPv4
address of the target
system is located.
Sentinel Event Fields 25
Page 26

novdocx (en) 7 January 2010
Default Label
Filters and
Correlation
Rules
Menu and
Correlation
Actions
Proprietary
Collector
Language
Data
Typ e
Description
DeviceName e.rv31 %rv31% s_RV31 string Name of the device
generating the event. If
this device is supported
by Advisor, the name
should match the name
known by Advisor. Used
in Exploit Detection.
DeviceCategory e.rv32 %rv32% s_RV32 string Device category (FW,
IDS, AV, OS, DB).
EventContext e.rv33 %rv33% s_RV33 string Event context (threat
level).
InitThreatLevel e.rv34 %rv34% s_RV34 string Initiator threat level.
InitUserDomain e.rv35 %rv35% s_RV35 string Domain (namespace) in
which the initiating
account exists.
DataContext e.rv36 %rv36% s_RV36 string Data context.
InitFunction e.rv37 %rv37% s_RV37 string Initiator function.
InitOperationalContext e.rv38 %rv38% s_RV38 string Initiator operational
context.
MSSPCustomerName e.rv39 %rv39% s_RV39 string MSSP customer name.
VendorEventCode e.rv40 %rv40% s_RV40 string Event code reported by
device vendor.
TargetHostDomain e.rv41 %rv41% s_RV41 string Domain portion of the
target system's fullyqualified hostname.
InitDomain e.rv42 %rv42% s_RV42 string Domain portion of the
initiating system's fullyqualified hostname.
ReservedVar43 e.rv43 %rv43% s_RV43 string Reserved by Novell for
expansion.
TargetThreatLevel e.rv44 %rv44% s_RV44 string Target threat level.
TargetUserDomain e.rv45 %rv45% s_RV45 string Domain (namespace) in
which the target account
exists..
VirusStatus e.rv46 %rv46% s_RV46 string Virus status.
TargetFunction e.rv47 %rv47% s_RV47 string Target function.
TargetOperationalContext e.rv48 %rv48% s_RV48 string Target operational
context.
TaxonomyLevel4 e.rv53 %rv53% s_RV53 string Sentinel event code
categorization - level 4.
26 Sentinel 6.1 Reference Guide
Page 27

novdocx (en) 7 January 2010
Default Label
Filters and
Correlation
Rules
Menu and
Correlation
Actions
Proprietary
Collector
Language
Data
Typ e
Description
CustomerHierarchyLevel2 e.rv54 %rv54% s_RV54 string Customer Hierarchy Level
2 (used by MSSPs).
VirusStatus e.rv56 %rv56% s_RV56 string Virus Status.
InitMacAddress e.rv57 %rv57% s_RV57 string Initiator Mac Address.
Part of initiator host asset
data.
InitNetworkIdentity e.rv58 %rv58% s_RV58 string Initiator Network Identity.
Part of initiator host asset
data.
InitAssetFunction e.rv60 %rv60% s_RV60 string Function of the initiating
system (fileserver,
webserver, etc.).
InitAssetValue e.rv61 %rv61% s_RV61 string Initiator Asset Value. Part
of initiator host asset data.
InitAssetCriticality e.rv62 %rv62% s_RV62 string Criticality of the initiating
system (0-5).
Variables reserved for future
use by Novell
e.rv63 thru
e.rv75
%rv63%
thru
s_RV63
thru s_rv75
string Variables not currently in
use
%rv75%
InitAssetDepartment e.rv76 %rv76% s_RV76 string Department of the
initiating system.
InitAssetId e.rv77 %rv77% s_RV77 string Internal asset identifier of
the initiator.
Variables reserved for future
use by Novell
e.rv78 thru
e.rv80
%rv78%
thru
s_RV78
thru s_rv80
string Variables not currently in
use
%rv80%
TargetAssetClass e.rv81 %rv81% s_RV81 string Class of the target system
(desktop, server, etc.).
TargetAssetFunction e.rv82 %rv82% s_RV82 string Function of the target
system (fileserver,
webserver, etc.).
TargetAssetValue e.rv83 %rv83% s_RV83 string Target Asset Value. Part
of target host asset data.
Variables reserved for future
use by Novell
e.rv84 thru
e.rv97
%rv84%
thru
s_RV84
thru s_rv97
string Variables not currently in
use.
%rv97%
TargetDepartment e.rv98 %rv98% s_RV98 string Target Department. Part
of target host asset data.
TargetAssetId e.rv99 %rv99% s_RV99 string Internal asset identifier of
the target.
CustomerHierarchyLevel4 e.rv100 %rv100% s_RV100 string Customer Hierarchy Level
4 (used by MSSPs)
Sentinel Event Fields 27
Page 28

novdocx (en) 7 January 2010
Default Label
Variables reserved for future
use by Novell
CustomerVar1
thru
CustomerVar10
CustomerVar11 thru
CustomerVar20
CustomerVar21 thru
CustomerVar89
Filters and
Correlation
Rules
e.rv101
thru
e.rv200
e.cv1 thru
e.cv10
e.cv11 thru
e.cv20
e.cv21 thru
e.cv89
Menu and
Correlation
Actions
%rv101%
thru
%rv200%
%cv1%
thru
%cv10%
%cv11%
thru
%cv20%
%cv21%
thru
%cv89%
Proprietary
Collector
Language
s_rv101
thru
s_rv200
s_CV1
thru
s_CV10
s_CV11
thru
s_CV20
s_CV21
thru
s_CV29
Data
Typ e
Description
various Variables not currently in
use
integer Number variable reserved
for customer use. Stored
in database.
date Date variable reserved for
customer use. Stored in
database.
string String variable reserved
for customer use. Stored
in database.
SARBOX e.cv90 %cv90% s_CV90 string Set to 1 if the asset is
governed by SarbanesOxley.
HIPAA e.cv91 %cv91% s_CV91 string Set to 1 if the asset is
governed by the Health
Insurance Portability and
Accountability Act
(HIPAA) regulation.
GLBA e.cv92 %cv92% s_CV92 string Set to 1 if the asset is
governed by the GrammLeach Bliley Act (GLBA)
regulation.
FISMA e.cv93 %cv93% s_CV93 string Set to 1 if the asset is
governed by the Federal
Information Security
Management Act (FISMA)
regulation.
NISPOM e.cv94 %cv94% s_CV94 string Set to 1 via an asset map
if the target asset is
governed by the National
Industrial Security
Program Operating
Manual (NISPOM)
CustomerVar95 thru
CustomerVar100
e.cv95 thru
e.cv100
%cv95%
thru
%cv100%
s_CV95
thru
s_CV100
string String variable reserved
for customer use. Stored
in database.
CustomerVar101 thru
CustomerVar110
28 Sentinel 6.1 Reference Guide
e.cv101
thru
e.cv110
%cv101%
thru
%cv110%
s_CV101
thru
s_CV110
string Integer variable reserved
for customer use. Stored
in database.
Page 29

novdocx (en) 7 January 2010
Default Label
CustomerVar111 thru
CustomerVar120
CustomerVar121 thru
CustomerVar130
CustomerVar131 thru
CustomerVar140
CustomerVar141 thru
CustomerVar150
CustomerVar151 thru
CustomerVar160
CustomerVar161 thru
CustomerVar170
CustomerVar171 thru
CustomerVar180
Filters and
Correlation
Rules
e.cv111
thru
e.cv120
e.cv121
thru
e.cv130
e.cv131
thru
e.cv140
e.cv141
thru
e.cv150
e.cv151
thru
e.cv160
e.cv161
thru
e.cv170
e.cv171
thru
e.cv180
Menu and
Correlation
Actions
%cv111%
thru
%cv120%
%cv121%
thru
%cv130%
%cv131%
thru
%cv140%
%cv141%
thru
%cv150%
%cv151%
thru
%cv160%
%cv161%
thru
%cv170%
%cv171%
thru
%cv180%
Proprietary
Collector
Language
s_C V111
thru
s_CV120
s_CV121
thru
s_CV130
s_CV131
thru
s_CV140
s_CV141
thru
s_CV150
s_CV151
thru
s_CV160
s_CV161
thru
s_CV170
s_CV171
thru
s_CV180
Data
Typ e
Description
string Date variable reserved for
customer use. Stored in
database.
string UUID variable reserved
for customer use. Stored
in database.
string IPv4 variable reserved for
customer use. Stored in
database.
string String variable reserved
for customer use. Stored
in database.
string Integer variable reserved
for customer use. Not
stored in database.
string Date variable reserved for
customer use. Not stored
in database.
string UUID variable reserved
for customer use. Not
stored in database.
CustomerVar181 thru
CustomerVar190
CustomerVar191 thru
CustomerVar200
e.cv181
thru
e.cv190
e.cv191
thru
e.cv200
%cv181%
thru
%cv190%
%cv191%
thru
%cv200%
s_CV181
thru
s_CV190
s_CV191
thru
s_CV200
string IPv4 variable reserved for
customer use. Not stored
in database.
string String variable reserved
for customer use. Not
stored in database.
Sentinel Event Fields 29
Page 30

novdocx (en) 7 January 2010
30 Sentinel 6.1 Reference Guide
Page 31

3
Sentinel Control Center User
novdocx (en) 7 January 2010
Permissions
Sentinel allows administrators to set user permissions in the Sentinel Control Center at a granular
level. The only user created by default is the esecadm, or Sentinel Administrator. All other users are
created by the Sentinel Administrator, or someone with similar permissions.
To change user permissions:
1 Log into the Sentinel Control Center as a user with “User Management” permissions.
2 Click the Admin tab.
3 Select User Configuration from Admin tab. Alternatively, Select User Manager from User
Configuration in the Navigator.
4 Right click user and select User Details.
3
5 Select the Permissions tab.
Sentinel Control Center User Permissions
31
Page 32

novdocx (en) 7 January 2010
6 Uncheck the checkboxes for which you want to restrict user.
7 Click OK.
The permissions in the User Manager are grouped into several major categories:
General (page 33)
Active Views (page 34)
iTRAC (page 35)
Incidents (page 35)
Integrators (page 36)
Sentinel Control Center User Permissions (page 31)
Event Source Management (page 37)
Analysis Tab (page 37)
Advisor Tab (page 37)
Administration (page 38)
Correlation (page 39)
32 Sentinel 6.1 Reference Guide
Page 33

Solution Pack (page 39)
Identity (page 39)
Each of these groups of setting is described in more detail below.
3.1 General
Table 3-1 Permissions-General
Permission Name Description
Save Workspace Allows user to save preferences. If this permission is unavailable, user
will never be prompted to save changes to preferences when logging out
or exiting the Sentinel Control Center.
Column Management Allows user to manage the columns in the Active View tables.
Snapshot Allows user to take a snapshot of Active View tables.
novdocx (en) 7 January 2010
3.1.1 General – Public Filters
Table 3-2 Permissions-General-Public Filters
Permission Name Description
Create Public Filters Allows user to create a filter with an owner ID of PUBLIC. If user does
not have this permission, then the value PUBLIC will not be listed as
one of the owner IDs that user can create a filter for.
Modify Public Filters Allows user to modify a public filter.
Delete Public Filters Allows user to delete a public filter.
3.1.2 General – Manage Private Filters of Other Users
Table 3-3 Permissions-General-Manage Private Filters of Other Users
Permission Name Description
Create Private Filters for Other Users Allows user to create private filters for themselves or for
other users.
Modify Private Filters of Other Users Allows user to modify their own private filters and private
filters created by other users.
Delete Private Filters of Other Users Allows user to delete their own private filters and private
filters created by other users.
View/Use Private Filters of Other Users Allows user to view/use their own private filters and private
filters crated by other users.
Sentinel Control Center User Permissions 33
Page 34

3.1.3 General – Integration Actions
Table 3-4 Permissions-General-Integration Actions
Permission Name Description
Send to Remedy Help Desk Allows user to send events, incident and associated objects to
Remedy. (requires the optional Remedy integration component)
3.2 Active Views
Table 3-5 Permissions-Active Views
Permission Name Description
View Active Views Tab Allows user to see and use the Active Views tab, menu and other
related functions associated with the Active Views tab.
novdocx (en) 7 January 2010
3.2.1 Active Views – Menu Items
Table 3-6 Permissions-Active Views-Menu Items
Permission Name Description
Use Assigned Menu Items Allows user to use assigned menu items in the
Active Views Events table (the right-click menu).
Add to Existing Incident Allows user to add events to existing incidents
using the Active Views Events table (the right-click
menu).
Remove from Incident Allows user to remove events from an existing
incident using the Events tab Events table (the
right-click menu).
Email Events Allows user to e-mail events using the Active Views
Events table (the right-click menu).
View Advisor Attack Data Allows user to view the Advisor Attack Data stream.
View Vulnerability Allows user to view the vulnerabilities present in the
Sentinel database
3.2.2 Active Views – Active Views
Table 3-7 Permissions-Active Views-Active Views
Permission Name Description
Use/View Active Views Allows user to access the Active Views charts.
34 Sentinel 6.1 Reference Guide
Page 35

3.3 iTRAC
Table 3-8 Permissions-iTRAC
Permission Name Description
View iTRAC Tab Allows user to see and use the iTRAC tab, menu and other related
functions associated with the iTRAC tab.
Activity Management Allows user to access the Activity Manager.
Manage Work Items Of Users Gives user administrative control over all workitems, including
those assigned to other users
3.3.1 iTRAC - Template Management
Table 3-9 Permissions-iTRAC-Template Management
novdocx (en) 7 January 2010
Permission Name Description
View/Use Template Manager Allows user to access the Template Manager.
Create/Modify Templates Allows user to create and modify templates.
3.3.2 iTRAC - Process Management
Table 3-10 Permissions-iTRAC-Process Management
Permission Name Description
View/Use Process Manager Allows user to access the Process View Manager.
Start/Stop Processes Allows user to use the Process View Manager.
3.4 Incidents
Table 3-11 Permissions-Incidents
Permission Name Description
View Incidents Tab Allows user to see and use the Incidents tab, menu and other related
functions associated with the View Incidents tab.
Incident Administration Allows user to modify an incident.
View Incident(s) Allows user to view/modify the details of an incident. If the user does not
have this permission, then the Incident Details window will not be displayed
when the user either double-clicks an Incident in the Incident View window
or right-clicks the incident or selects the Modify option.
Sentinel Control Center User Permissions 35
Page 36

Permission Name Description
Create Incident(s) Allows user to create Incidents in the in the Incident View window or by right
clicking on the incident and select Modify option. Alternatively you can
select Create Incident menu item in the Incidents menu bar and clicking
Create Incident option in the tool bar.
Modify Incident(s) Allows user to modify an incident in the Incident Details window.
Delete Incident(s) Allows user to delete incidents.
Assign Incident(s) Allows user to assign an incident in the Modify and Create Incident window.
Email Incidents Allows user to e-mail Incidents of interest.
Incident Actions Allows user to view Execute Incident Action menu option in an Incident and
to execute actions.
Add Notes Allows user to add any number notes to an incident.
3.5 Integrators
novdocx (en) 7 January 2010
Table 3-12 Permissions-Integrators
Permission Name Description
View Integrator Allows user to view Integrators, open Integrator Manager, use
update, refresh, help, test buttons and view integrator event details.
Manage Integrator Allows user to manage (add/modify/delete) the configured
Integrators.
Manage Integrator Plugins Allows user to manage (add/modify/delete) the Integrators plugins.
3.6 Actions
Table 3-13 Permissions-Action Manager
Permission Name Description
View Actions Allows user to use Action Manager and view Actions.
Manage Actions Allows user to add/edit/delete actions of type "Execute Action
Plugins"
Manage Action Plugins Allows user to add/edit/delete Action Plugins.
36 Sentinel 6.1 Reference Guide
Page 37

3.7 Event Source Management
Table 3-14 Permissions-Event Source Management
Permission Name Description
View Status Allows user to view the status of ESM components.
View Scratchpad Allows user to design and configure ESM components.
Configure ESM Components Allows you to configure ESM components.
Control ESM Components Allows you to control and manage ESM components.
Manage Plugins Allows you to manage Collector and Connector Plugins.
View Raw Data Allows you to view/parse raw data.
Debug Collector Allows you to debug Collector.
Command and Control consists of:
novdocx (en) 7 January 2010
start/stop individual ports
start/stop all ports
restart hosts
rename hosts
3.8 Analysis Tab
Table 3-15 Permissions-Analysis Tab
Permission Name Description
View Analysis Tab Allows user to see and use the View Analysis tab, menu and other
related functions associated with the View System Overview tab.
3.9 Advisor Tab
Table 3-16 Permissions-Advisor Tab
Permission Name Description
View Advisor Tab Allows user to view and use the Advisor tab and the Advisor Status
window.
Sentinel Control Center User Permissions 37
Page 38

3.10 Administration
Table 3-17 Permissions-Administration
Permission Name Description
View Administration Tab Allows user to see and use the View Administration tab, menu and
other related functions associated with the View Administration tab.
DAS Statistics Allows user to view DAS activity (DAS binary and query).
Event Configuration Allows user to rename columns, set mappings from mapping files.
This function is associated with Mapping Configuration.
Map Data Configuration Allows user to add, edit and delete mapping files.
Event Menu Configuration Allows user to access the Menu Configuration window and add new
options that display on the Event menu when you right-click an
event.
Report Data Configuration Allows user to enable or disable summary tables used in
aggregation.
novdocx (en) 7 January 2010
User Management Allows user to add, modify and delete user details
User Session Management Allows user to view, lock and terminate active users (logins to
Sentinel Control Center).
iTRAC Role Management Allows user to view and use the role manager in the Admin Tab.
Download Manager Allow user to configure download manager in the Admin Tab.
Advisor Configuration Allow user to configure Advisor settings.
3.10.1 Administration – Global Filters
Table 3-18 Permissions-Administration-Global Filters
Permission Name Description
View/Use Global Filters Allows user to access the Global Filter Configuration window.
Modify Global Filters Allows user to modify the global filters configuration.
NOTE: To access this function, View Global Filters permission must
also be assigned.
3.10.2 Administration – Server Views
Table 3-19 Permissions-Administration-Server Views
Permission Name Description
View Servers Allows user to monitor the status of all processes.
38 Sentinel 6.1 Reference Guide
Page 39

Permission Name Description
Control Servers Allows user to start, restart and stop processes.
3.11 Correlation
Table 3-20 Permissions-Correlation
Permission Name Description
View Correlation Tab Allows user to use the Correlation functions.
View/Use Correlation Rule Manager Allows user to start or stop the Correlation Rules.
View/Use Correlation Engine Manager Allows user to deploy/undeploy the Correlation Rules.
View/Use Dynamic Lists Allows user to Create, use, view, modify the Dynamic
Lists.
novdocx (en) 7 January 2010
3.12 Solution Pack
Table 3-21 TPermissions-Solution Pack
Permission Name Description
Solution Designer Allows user to access Solution Designer.
Solution Manager Allows user to access Solution Manager.
3.13 Identity
Table 3-22 Permissions-Action Manager
Permission Name Description
View/Use Identity Address Book Allows user to view and use Identity Browser.
Sentinel Control Center User Permissions 39
Page 40

novdocx (en) 7 January 2010
40 Sentinel 6.1 Reference Guide
Page 41

4
Sentinel Correlation Engine
novdocx (en) 7 January 2010
RuleLG Language
This section is about Sentinel correlation engine Rule LG language.
4.1 Correlation RuleLG Language Overview
The Sentinel Correlation Engine runs rules that are written in the Correlation RuleLg language.
Rules are created in the Sentinel Control Center. Users can create rules using a wizard for the
following rule types:
Simple Rule
Composite Rule
Aggregate Rule
Sequence Rule
These rules are converted to the Correlation RuleLg language when the rules are saved. The same
rule types, plus even more complex rules, can be created in the Sentinel Control Center using the
Custom/Freeform option. To use the Custom/Freeform option, the user must have a good
understanding of the Correlation RuleLg language.
RuleLg uses several operations, operators, and event field short tags to define a rule. The Correlation
Engine loads the rule definition and uses the rules to evaluate, filter, and store in memory events that
meet the criteria specified by the rule. Depending on the rule definition, a correlation rule might fire
based on
4
the value of one field or multiple fields
the comparison of an incoming event to past events
the number of occurrences of similar events within a defined time period
one or more subrules firing
one or more subrules firing in a particular order
Each of these constructs is represented by an operation in RuleLg.
4.2 Event Fields
All operations function on event fields, which can be referred to by their labels or by their short tags
within the correlation rule language. For a full list of labels and short tags, see “Sentinel Event
Fields” section. The label or metatag must also be combined with a prefix to designate whether the
event field is part of the incoming event or a past event that is stored in memory.
Examples:
e.DestinationIP (Destination IP for the current event)
e.dip (Destination IP for the current event)
w.dip (Destination IP for any stored event)
Sentinel Correlation Engine RuleLG Language
41
Page 42

WARNING: If you rename the label of a metatag, do not use the original label name when creating
a correlation rule.
4.3 Event Operations
Event operations evaluate, compare, and count events. They include the following operations:
Filter: Evaluates the current to determine whether they could potentially trigger a rule to fire
Window: Compares the current event to past events that have been stored in memory
Trig ger: Counts events to determine whether enough events have occurred to trigger a rule
Each operation works on a set of events, receiving a set of events as input and returning a set of
events as output. The current event processed by a rule often has a special meaning for the semantic
of the language. The current event is always part of the set of events in and out of an operation
unless the set is empty. If an input set of an operation is empty, then the operation is not evaluated.
4.3.1 Filter Operation
novdocx (en) 7 January 2010
Filter consists of a Boolean expression that evaluates the current event from the real-time event
stream. It compares event attributes to user-specified values using a wide set of operators
The Boolean expression is a composite of comparison and match instructions.
The syntax for filter is:
Filter <Boolean expression 1> [NOT|AND|OR <Boolean expression 2] […]
[NOT|AND|OR <Boolean expression n>]
Where
<Boolean expressions 1…n> are expressions using one or more event field names
and filter operators
For example, this rule detects whether the current event has a severity of 4 and the resource event
field contains either “FW” or “Comm.”
filter(e.sev = 4 and (e.res match regex ("FW") or e.res match regex ("Comm")))
Boolean Operators
Filter expressions can be combined using the Boolean operators AND, OR and NOT. The filter
boolean operator precedence (from highest [top] to lowest [bottom] precedence) is:
Table 4-1 Boolean Operators
Operator Meaning Operator Type Associativity
Not logical not unary None
And logical and binary left to right
Or logical or binary left to right
42 Sentinel 6.1 Reference Guide
Page 43

In addition to Boolean operators, filter supports the following operators.
Standard Arithmetic Operators
Standard arithmetic operators can be used to build a condition that compares the value of a Sentinel
metatag and a user-specified value (either a numeric value or a string field). The standard arithmetic
operators in Sentinel are =, <, >, !=, <=, and >=.
Examples:
filter(e.Severity > 3)
filter(e.BeginTime < 1179217665)
filter(e.SourceUserName != “Administrator”)
Match Regex Operators
The match regex operator can be used to build a condition where the value of a metatag matches a
user-specified regular expression value specified in the rule. This operator is used only for string
tags, and the user-specified values for this operator are case-sensitive.
Examples:
novdocx (en) 7 January 2010
filter(e.Collector match regex ("IBM"))
filter(e.EventName match regex ("Attack"))
Match Subnet Operators
The match subnet operator can be used to build a condition where the value of a metatag maches a
user-specified subnet specified in the rule in CIDR notation. This operator is used only for IP
address fields.
Example:
filter(e.DestinationIP match subnet (10.0.0.1/22))
Inlist Operator
The inlist operator is used to perform a lookup on an existing dynamic list of string values, returning
true if the value is present in the list. For more information on Dynamic Lists, see “Correlation Tab”
in Sentinel 6.1 User Guide.
For example, this filter expression is used to evaluate whether the Source IP of the current event is
present on a dynamic list called MailServerList. If the Source IP is present in this list, the expression
evaluates to TRUE.
filter(e.sip inlist MailServerList)
As another example, this filter expression combines the NOT and the INLIST operator. This
expression evaluates to TRUE if the Source IP is not present in the dynamic list called
MailServerList.
filter(not (e.sip inlist MailServerList))
This filter expression is used to evaluate whether the event name of the current event equals “File
Access” and the Source User Name is also not present on a dynamic list called AuthorizedUsers. If
both conditions are true for the current event, the expression evaluates to TRUE.
Sentinel Correlation Engine RuleLG Language 43
Page 44

filter(e.evt="File Access" and not(e.sun inlist AuthorizedUsers))
ISNULL Operator
The isnull operator returns true if the metatag value is equal to NULL.
Example:
Filter(isnull(e.SIP))
Output Sets
The output of a filter is either the empty set (if the Boolean expression evaluates to false) or a
set containing the current event and all of the other events from the incoming set (if the
Boolean expression evaluates to true).
If filter is the last or only operation of a correlation rule, then the output set of the filter is used
to construct a correlated event. The trigger events are the filter operation output set of events
with the current event first.
If filter is not the last operation of a correlation rule (that is, filter is followed by a flow
operatior), then the output set of a filter is used as the input set to other operations (through the
flow operator).
novdocx (en) 7 January 2010
Additional Information
The filter operator can be used to compare metatag values with other metatag values, for
example:
e.SourceIP=e.DestinationIP
4.3.2 Window Operation
Window compares the current event to a set of past events that are stored in a “window.” The events
in the window can be all past events for a certain time period, or they can be filtered.
The Boolean expression is a composite of comparison instructions and match instructions with the
Boolean operators AND, OR and NOT.
The syntax for window is:
Window (<Boolean expression>[, <filter expression>, <evaluation period>)
Where
<Boolean expression> is an expression comparing a metatag value from the
current event to a metatag value from a past event (or a user-specified
constant)
<filter expression> is optional and specifies filter criteria for the past
events
<evaluation period> specifies the duration for which past events matching the
filter expression are maintained, specified in seconds (s), minutes (m), or
hours (h). If no letter is specified, seconds are assumed.
For example, this rule detects whether the current event has a source IP address in the specified
subnet (10.0.0.10/22) and matches an event(s) that happened within the past 60 seconds.
window(e.sip = w.sip, filter(e.sip match subnet (10.0.0.10/22),60)
44 Sentinel 6.1 Reference Guide
Page 45

As another example, this rule is a domino type of rule. An attacker exploits a vulnerable system and
uses it as an attack platform.
window((e.sip = w.dip AND e.dp = w.dp AND e.evt = w.evt), 1h)
This rule identifies a potential security breach after a denial of service attack. The rule fires if the
destination of a denial of service attack has a service stopped within 60 seconds of the attack.
filter(e.rv51="Service" and e.rv52="Stop" and e.st = "H") flow window (e.sip =
w.dip, filter(e.rv52="Dos"), 60s) flow trigger(1,0))
Output Sets
If any past event evaluates to true with the current event for the simple boolean expression, the
output set is the incoming event plus all matching past events.
If no events in the window match the current event for the simple boolean expression, the
output set is empty.
If a window is the last or only operation of a correlation rule, then the output set of the window
is used to construct a correlated event (the correlated events being the window operation output
set of events with the current event first).
novdocx (en) 7 January 2010
Additional Information
You must prepend a metatag name with "e." to specify the current event or with "w." to specify
the past events
All window simple Boolean expressions must include a metatag in the form w.[metatag].
For more information about valid filter expressions, see Section 4.3.1, “Filter Operation,” on
page 42.
Every event coming in to the Correlation Engine that passes this filter is put into the window of
past events
If no filter expression exists, then all events coming into the Correlation Engine are maintained
by the window. With extremely high event rates or long durations, this might require a large
amount of memory.
The current event is not placed into the window until after the current event window evaluation
is complete
To minimize memory usage, only the relevant parts of the past events, not all metatag values,
are maintained in memory.
4.3.3 Trigger Operation
Trigger is used to specify a number of events for a user-specified duration.
The syntax for trigger is:
Trigger (<number of events>, <evaluation period>[, discriminator (<list of
tags>))
Where
Sentinel Correlation Engine RuleLG Language 45
Page 46

<number of events> is an integer value specifying the number of matching
events that are necessary for the rule to fire
<evaluation period> specifies the duration for which past events matching the
filter expression are maintained, specified in seconds (s), minutes (m), or
hours (h). If no letter is specified, seconds are assumed.
discriminator is a field to group by
For example, this rule detects if 5 events with the same source IP address happen within 10 seconds.
trigger(5,10,discriminator(e.sip))
Output Sets
If the specified count is reached within the specified duration, then a set of events containing all
of the events maintained by the trigger is output; if not, the empty set is output.
When receiving a new input set of events, a trigger first discards the outdated events (events
that have been maintained for more than the duration) and then inserts the current event. If the
number of resulting events is greater than or equal to the specified count, then the trigger
outputs a set containing all of the events.
If a trigger is the last operation (or the only operation) of a correlation rule, then the output set
of the trigger is used to construct a correlated event (the correlated events being the trigger
operation output set of events with the current event first).
If a trigger is not the last operation of a correlation rule (that is, it is followed by a flow
operator), then the output set of a trigger is used as the input set to other operations (through the
flow operator).
The discriminator (meta-tag list) is a comma-delimited list of meta-tags. A trigger operation
keeps different counts for each distinct combination of the discriminator meta-tags.
novdocx (en) 7 January 2010
4.4 Rule Operations
Rule operations work on subrules that have been combined into a compound rule. They include:
Gate
Sequence
4.4.1 Gate Operation
The gate operation is used to create a composite rule which is used in identifying complex situations
from the occurrence of simple situations.
The composite rule is made up of one or more nested subrules and can be configured to fire if some,
any or all of the subrules fire within a specified time window. The subrules can be a simple rule or
another composite rule. For more information on Composite Rule, see “Correlation Tab” in Sentinel
6.1 User Guide.
The syntax for gate is:
Gate(<subrule 1 rulelg>, <subrule 2 rulelg>…<subrule n ruleLg>, <mode>,
<evaluation period>, discriminator(<list of tags>))
Where
46 Sentinel 6.1 Reference Guide
Page 47

Subrule Rulelgs are the rulelg definitions for 1 to n subrules
mode = all | any | 1 | 2 | … | n, which is the number of subrules that must be
triggered in order for the gate rule to trigger
<evaluation period> specifies the duration for which past events matching the
filter expression are maintained, specified in seconds (s), minutes (m), or
hours (h). If no letter is specified, seconds are assumed.
discriminator is a field to group by
For example, this rule is a typical perimeter security IDS inside/outside rule
filter(e.sev > 3) flow gate(filter(e.sn = "in"), filter(e.sn = "out"), all,
60s, discriminator(e.dip, e.evt))
4.4.2 Sequence Operation
Sequence rules are similar to gate rules, except that all child rules must fire in time order for the
sequenced rule to evaluate to true.
The subrules can be a simple rule or another composite rule.
The syntax for sequence is:
novdocx (en) 7 January 2010
Sequence(<subrule 1 rulelg>, <subrule 2 rulelg>…<subrule n ruleLg>,
<evaluation period>, discriminator(<list of tags>))
Where
Subrule Rulelgs are the rulelg definitions for 1 to n subrules
<evaluation period> is a time period expressed in seconds (s), minutes (m), or
hours (h)
discriminator is a field to group by
For example, this rule detects three failed logins by a particular user in 10 minutes followed by a
successful login by same user.
sequence (filter(e.evt="failed logins") flow trigger(3, 600,
discriminator(e.sun,e.dip)), filter(e.evt="goodlogin"), 600,
discriminator(e.sun, e.dip))
4.5 Operators
Operators are used to transition between operations or expressions. The fundamental operators used
between operations are:
Flow operator
Union operator
Intersection operator
Discriminator operator
4.5.1 Flow Operator
The output set of events of the left-hand side operation is the input set of events for the right-hand
side operation. Flow is typically used to transition from one correlation operation to the next.
For example:
Sentinel Correlation Engine RuleLG Language 47
Page 48

filter(e.sev = 5) flow trigger(3, 60)
The output of the filter operation is the input of the trigger operation. The trigger only counts events
with severity equal to 5.
4.5.2 Union Operator
The union of the left side operation output set and the right side operation output set. The resulting
output set contains events from either the left-hand side operation output set or the right-hand side
operation output set without duplicates.
For example:
filter(e.sev = 5) union filter(e.sip = 10.0.0.1)
is equivalent to
filter(e.sev = 5 or e.sip = 10.0.0.1)
4.5.3 Intersection Operator
novdocx (en) 7 January 2010
The intersection of the left side operation output set and the right side operation output set. The
resulting output set contains events that are common in both the left-hand side operation output set
and the right-hand side operation output set without duplicates.
For example:
filter(e.sev = 5) intersection filter(e.sip = 10.0.0.1)
is equivalent to
filter(e.sev = 5 and e.sip = 10.0.0.1)
4.5.4 Discriminator Operator
The discriminator operator allows users to group by event fields within other event operations.
Discriminator can be used within the trigger, gate, or sequence operations. This is the last operation
when executing a condition. The input for this operator will generally be the output of other
operations, if any.
For example, this filter expression is used to identify five severity 5 events within 60s that all have
the same Source IP. Note that the attribute (SIP in this example) can be any value, even a NULL, but
it must be the same for all five events in order for the rule to fire.
filter(e.sev=5 ) flow trigger(5, 60s, discriminator(e.sip)
4.6 Order of Operators
The operator precedence (from highest (top) to lowest (bottom)) are:
48 Sentinel 6.1 Reference Guide
Page 49

Table 4-2 Operator Precedence
Operator Meaning Operator Type Associativity
flow Output set becomes input set binary left to right
intersection Set intersection (remove duplicates) binary left to right
union Set union (remove duplicates) binary left to right
4.7 Differences between Correlation in 5.x and
6.x
There are several new functionalities updated / included in 6.0 to widen the usage of Correlation to
meet user’s requirements and for the ease-of-use.
Gate Operation: This is new in 6.0.
Sequence Operation: This is new in 6.0.
Inlist Operator and Dynamic Lists: These are new in 6.0.
novdocx (en) 7 January 2010
Isnull Operator: This is new in 6.0. For metatag values equal to null, Sentinel 5.x supported the
following syntax which is replaced by the ISNull operator in Sentinel 6.0
e.SIP= “ ”
Update Window: This is new in Sentinel 6.0
Sentinel 6.0 merges the C (Correlated Events) and W (watchlist events) SensorTypes. All
events generated by the Correlation Engine are now labeled C in the SensorType field.
Correlation Actions and Correlation Rules: Correlation Actions and Correlation Rules are
decoupled in Sentinel 6.0
Although the filter operation supported AND and OR Boolean expressions in Sentinel 5.x, the
window operation supports Boolean expressions for the first time in Sentinel 6.0. For example:
OR: window(e.dip=w.dip OR e.sip=w.sip, filter(e.sev>2),60)
AND: window(e.evt=w.evt AND e.sun=w.sun, filter(e.sev>2),60)
Sentinel 6.0 no longer has the GUI option to create a rule from a PUBLIC filter. The filter
criteria must be defined in the correlation wizard or language.
The update functionality for a rule that is triggered more than once is configurable in Sentinel
6.0. In Sentinel 5.1.3, updates to a rule were based on a sliding window based on the trigger
time period. In Sentinel 6.0, the update functionality can be set when the rule is deployed; the
rule actions might happen every time the rule is triggered, or they can be set to occur once and
then wait for some period of time before the action occurs again. This prevents multiple
notifications on a single, ongoing event.
The in, not in, and difference operators are deprecated in Sentinel 6.0. Correlation rules using
these operators must be modified before running them in Sentinel 6.0.
The e.all metatag has been deprecated. Correlation rules using this operator should be updated
to use specific short tags before running them in Sentinel 6.0.
Sentinel Correlation Engine RuleLG Language 49
Page 50

novdocx (en) 7 January 2010
50 Sentinel 6.1 Reference Guide
Page 51

5
Sentinel Data Access Service
The Data Access Service (DAS) process is Sentinel Server's persistence service and provides a
message bus interface to the database. Some of the services it provides are event storage, Historical
Query, event drill down, vulnerability and Advisor data retrieval, and configuration manipulation.
5.1 DAS Container Files
DAS is a collection of services provided by five different processes. Each process is a container
responsible for different types of database operations. These processes are:
DAS Query: Performs general Sentinel Service operations including Login and Historical
Query.
DAS Binary: Performs event database insertion.
DAS RT: Provides the server-side functionality for Active Views.
DAS Aggregation: Calculates event data summaries that are used in reports.
novdocx (en) 7 January 2010
5
DAS iTRAC: Provides the server-side functionality for the Sentinel iTRAC functionality.
DAS CMD: Provides a command line interface to certain DAS services. Used primarily for
third-party integration.
DAS Proxy: Provides the server-side of the SSL proxy connection to Sentinel Server.
DAS Proxy is not directly part of the DAS collection of services. It is part of the Communication
Server and does not directly connect to the database.
5.1.1 Reconfiguring Database Connection Properties
The primary settings in these configuration files that can be configured using the dbconfig utility are
related to the database connection, including:
username
password
hostname
port number
database (database name)
server (oracle, oracle10g, or mssql)
If any of these database connection settings need to be changed, they must be changed in every
das_*.xml
the same time (For example, update all files in the %ESEC_HOME%\config or $ESEC_HOME/
config directory). Alternately, using the –n argument, this utility can update a single file’s contents if
only one file need to be updated. Typically, all files should be updated at the same time.
file using the
dbconfig
utility. Using the –a argument, this utility can update all files at
WARNING: Do not manually edit the database connection properties. Use the
change any database connection values within these files.
Sentinel Data Access Service
dbconfig
utility to
51
Page 52

To Reconfigure Database Connection Properties:
1 Login to the machine where DAS is installed as the esecadm user on UNIX or a user with
administrative rights on Windows.
2 Go to:
For Windows:
%ESEC_HOME%\bin
For UNIX:
$ESEC_HOME/bin
3 Provide the following command:
For Windows:
dbconfig –a %ESEC_HOME%\config [[-u username] [-p password] | [-winAuth]]
[-h hostname] [-t portnum] [-d database] [-s server] [-help] [-version]
For UNIX:
dbconfig –a $ESEC_HOME/config [-u username] [-p password] [-h hostname] [t portnum] [-d database] [-s server] [-help] [-version]
novdocx (en) 7 January 2010
NOTE: The -winAuth argument is available only on Windows and should be used instead of the –u
and –p arguments if the Sentinel Application User is a Windows Authentication user.
Other settings in the files can be adjusted manually (without using dbconfig):
maxConnections
batchSize
loadSize
Changing these settings might affect database performance and should be done with caution
5.1.2 DAS Logging Properties Configuration Files
The following files are used to configure logging of the DAS process. These files are typically
changed when troubleshooting the DAS process.
das_query_log.prop
das_binary_log.prop
das_rt_log.prop
das_itrac_log.prop
das_aggregation_log.prop
das_cmd_log.prop
das_proxy_log.prop
They are located in the following locations:
For Windows:
%ESEC_HOME%\config
52 Sentinel 6.1 Reference Guide
Page 53

For UNIX:
$ESEC_HOME/config
These files contain the configuration that determines how the DAS processes will log messages. The
most important part of the configuration is the logging levels, which indicate how verbose the log
messages should be. The section of the file to configure these settings is:
###### Configure the logging levels
# Logging level rules are read from the top down.
# Start with the most general, then get more specific.
#
# Defaults all loggers to INFO (enabled by default)
.level=INFO
#
# < Set level of specific loggers here >
#
# Turns off all logging (disabled by default)
#.level=OFF
######
novdocx (en) 7 January 2010
NOTE: The logger
.level
is a wildcard logger name that refers to all loggers. Setting this logger’s
level will affect all loggers.
The available logging levels are:
OFF: disables all logging
SEVERE (highest value): indication that a component has malfunctioned or there is a loss/
corruption of critical data
WARNING: if an action can cause a component to malfunction in the future or if there is non-
critical data loss/corruption
INFO: audit information
CONFIG: for debugging
FINE: for debugging
FINER: for debugging
FINEST: (lowest value) – for debugging
ALL: will log all levels
When one specifies a logging level, all log messages of that level and higher (in the above list) will
actually be logged. For example, if one specifies the INFO level, then all INFO, WARNING and
SEVERE message will be logged.
NOTE: At 10 second intervals, the logging properties file will be checked to see if any changes
have occurred since it was last read. If the file has changed, the LogManagerRefreshService will reread the logging properties file. Therefore, it is not necessary to restart the processes to begin using
the updated logging levels.
Log messages are written to ESEC_HOME%\log (for Windows) or $ESEC_HOME/log (for UNIX),
in the following files:
Sentinel Data Access Service 53
Page 54

das_query_0.*.log
das_binary_0.*.log
das_itrac_0.*.log
das_aggregation0.*.log
das_rt0.*.log
das_cmd0.*.log
das_proxy0.*.log
The 0 indicates the unique number to resolve conflicts and the * indicates a generation number to
distinguish rotated logs. For example,
das_query0.0.log
is the log with index 0 (latest) file in a
rotated set of log files for the DAS Query process.
Log messages are also written to the process’s console (standard output). However, since the
processes are running as services, users do not have access to the console output. It is possible,
however, to capture the console output in the
sentinel0.*.log file
. This is useful, for example,
if the process is producing an error that is not printed to the process’s own log file. This can be
enabled by adding the following line to the
esecurity.base.process.MonitorableProcess.level=FINEST
sentinel_log.prop
file:
5.1.3 Certificate Management for DAS_Proxy
novdocx (en) 7 January 2010
The DAS_Proxy SSL Server uses an asymmetric key pair, consisting of a certificate (or public key)
and a private key, to encrypt communications. When the Sentinel Communication Server is started
for the first time, it automatically creates a self-signed certificate which is used by the DAS_Proxy
SSL Server.
You can replace the self-signed certificate with a certificate signed by a major Certificate Authority
(CA), such as Verisign, Thawte (http://www.thawte.com/), or Entrust (http://www.entrust.com/).
You can also replace the self-signed certificate with a certificate signed by a less common CA, such
as a CA within your company or organization.
This section describes several certificate management tasks that you can perform in Sentinel:
Replace the default certificate with a certificate signed by a Certificate Authority (CA)
Change default keystore and keyEntry passwords. This is recommended on all Sentinel
systems.
Change the location of the .proxyServerKeystore file
Change the default keyEntry alias to avoid potential conflicts with other keys in the keystore or
for simplicity
Replacing the default certificate with a CA-signed certificate
Novell provides a self-signed certificate for the DAS_Proxy SSL Server to use. To improve security,
you can replace the default, self-signed certificate that gets installed with a certificate signed by a
Certificate Authority (CA). The CA may be a major CA, such as Verisign, Thawte (http://
www.thawte.com/), or Entrust (http://www.entrust.com/), or it may be a less widely-known CA,
such as one that is within your organization.
54 Sentinel 6.1 Reference Guide
Page 55
The basic steps are to get a CA to sign your certificate and then import that certificate into the
keystore for DAS_Proxy to use. To import the certificate, the CA that signed the certificate must be
“known” to the keytool utility. Keytool usually recognizes the major certificate authorities, but for
other CA’s you may need to import a certificate or chain of certificates for the certificate authority
before you can successfully import the certificate that DAS_Proxy uses.
NOTE: These instructions are based on the user guide for keytool. For more information, see http://
java.sun.com/j2se/1.5.0/docs/tooldocs/solaris/keytool.html (http://java.sun.com/j2se/1.5.0/docs/
tooldocs/solaris/keytool.html)
To use a CA-signed certificate:
1 Execute the following command in the console:
$ESEC_HOME/jre/bin/keytool -list -keystore $ESEC_HOME/config/
.proxyServerKeystore
2 Provide the keystore password (star1111 by default). The contents of the keystore file display:
Keystore type: jks
Keystore provider: SUN
Your keystore contains 1 entry
10.0.0.1, Jan 8, 2008, keyEntry,
Certificate fingerprint (MD5):
22:B4:19:63:AC:2D:F9:C0:66:7F:7C:64:85:68:89:AB
The keyEntry alias, which is used in the following step, is the IP address in the example above.
By default, the keyEntry alias can be the IP address or the host name of the local machine.
novdocx (en) 7 January 2010
3 Execute the following command in the console using the keyEntry alias from
.proxyServerKeystore:
$ESEC_HOME/jre/bin/keytool -certreq -alias <keyEntry alias> -keystore
$ESEC_HOME/config/.proxyServerKeystore -file <csr_filename.csr>
The .csr file is saved in the specified location.
4 Provide the
.csr
file to the CA. The CA will return a signed
.cer
file. (These exact steps will
vary based on the Certificate Authority.)
5 If the CA is not well known, you must add the CA's certificate to the "cacerts" keystore using
the following steps:
5a Open a command prompt and go to $ESEC_HOME/jre/lib/security. There should be a
cacerts file in this directory.
5b Run the following command to import:
$ESEC_HOME/jre/bin/keytool -import -trustcacerts -alias
<a_ca_cert_alias_of_your_choosing> -keystore $ESEC_HOME/jre/lib/
security/cacerts -file <ca_cert_filename>
NOTE: The default password for this keystore file is “changeit”.
5c Execute the preceding steps on the Sentinel Server machine, all Collector Manager
systems that are connecting to the Sentinel Server through the SSL Proxy, and all Sentinel
Control Center systems.
6 To enable the use of CA signed certificate, edit das_proxy.xml file available on the Sentinel
Server. Change the property value to true:
<property name="usecacerts">true</property>
Sentinel Data Access Service 55
Page 56

7 Edit the configuration.xml file on all system with Sentinel Control Center and add the
following attribute to the “ssl” element of the “proxied_client” and “proxied_trusted_client”
strategies:
usecacerts="true"
For example:
<strategy active="yes" id="proxied_client"
location="com.esecurity.common.communication.strategy.proxystrategy.Proxi
edClientStrategyFactory">
<transport type="ssl">
<ssl host="hostname" keystore=”Path of .proxyClientKeystore” port="10013"
usecacerts="true"/>
</transport>
</strategy>
<strategy active="yes" id="proxied_trusted_client"
location="com.esecurity.common.communication.strategy.proxystrategy.Proxi
edClientStrategyFactory">
<transport type="ssl">
<ssl host="hostname" keystore=”Path of .proxyClientKeystore” port="10014"
usecacerts="true"/>
</transport>
</strategy>
novdocx (en) 7 January 2010
NOTE: The default property of
usecacerts
8 Import the
$ESEC_HOME/jre/bin/keytool -import -trustcacerts -alias <keyEntry alias> keystore $ESEC_HOME/config/.proxyServerKeystore -file <cer_filename.cer>
to true.
.cer
file into keystore file by executing the following command:
usecacerts
is false. You must change the property of
This will replace the self-signed certificate installed with Sentinel.
9 Restart Sentinel Server.
Novell also recommends that you change the keystore and keyEntry passwords after replacing the
certificate.
Changing default keystore and keyEntry passwords
By default, the passwords used for keystore and the keyEntry are both set to star1111. It is a good
practice to change these to something new.
NOTE: DAS_Proxy requires that the keystore and keyEntry passwords to be identical.
To change the keystore and the keyEntry password:
1 Execute the following command in the console to change the keystore password:
$ESEC_HOME/jre/bin/keytool -storepasswd -keystore $ESEC_HOME/config/
.proxyServerKeystore
2 Enter the old keystore password (star1111 by default) and a new keystore password. The
following example depicts this:
Enter keystore password: <old_pass>
New keystore password: <new_pass>
Re-enter new keystore password: <new_pass>
56 Sentinel 6.1 Reference Guide
Page 57

3 Verify the keyEntry alias using the following command:
$ESEC_HOME/jre/bin/keytool -list -keystore $ESEC_HOME/config/
.proxyServerKeystore
Provide the current keystore password. The contents of the keystore file display:
Keystore type: jks
Keystore provider: SUN
Your keystore contains 1 entry
10.0.0.1, Jan 8, 2008, keyEntry,
Certificate fingerprint (MD5):
22:B4:19:63:AC:2D:F9:C0:66:7F:7C:64:85:68:89:AB
The keyEntry alias is the IP address in the example above. By default, the keyEntry alias is
either set to the IP address or the hostname of the local machine.
4 Execute the following command in the console to change the keyEntry password to the same
password as the new keystore password:
$ESEC_HOME/jre/bin/keytool -keypasswd -alias <keyEntry alias> -keystore
$ESEC_HOME/config/.proxyServerKeystore
5 Enter the existing password and the new password. The following example depicts this:
Enter keystore password: <new_pass>
Enter key password for <keyEntry alias> <old_pass>
New key password for <keyEntry alias>: <new_pass>
Re-enter new key password for <keyEntry alias>: <new_pass>
novdocx (en) 7 January 2010
NOTE: Remember that the keyEntry password and keystore password must be identical.
6 Get the encrypted, Base64 value of the new password using the following steps:
Copy ESEC_HOME/config/das_rt.xml to a file named t
emp.xml
:
Execute the following command to add an encrypted, Base 64 form of the password to
temp.xml
$ESEC_HOME/bin/dbconfig -n $ESEC_HOME/config/temp.xml -p <new password
for keystore and keyEntry>
Open
Copy the value of “password” from the following section of the file:
name="password">BSEU8ew2JYsxtOt4hYcYNA==</property>
Delete the
file:
temp.xml
temp.xm
file.
<property
l file when you are confident that you have successfully copied the
encrypted password.
7 Open the das_proxy.xml file.
8 Paste the copied value of the new password to the “keystorePassword” property in the
“ProxyService” component property as shown below:
<obj-component id="ProxyService">
<class>esecurity.ccs.comp.clientproxy.ClientProxyService</class>
<property name="clientports">ssl:10013</property>
<property name="certclientports">ssl:10014</property>
<property name="keystore"> ../config/.proxyServerKeystore</property>
<property name="keystorePassword"> BSEU8ew2JYsxtOt4hYcYNA==</
property>
</obj-component>
9 Save the
das_proxy.xml
file.
10 Restart Sentinel Server.
Sentinel Data Access Service 57
Page 58

Using a new .proxyServerKeystore location
novdocx (en) 7 January 2010
By default the certificate and private key are stored in the file
$ESEC_HOME/config
value of the property “keystore” in the file
. To change the location of
$/ESEC_HOME/config/das_proxy.xml.
.proxyServerKeystore
.proxyServerKeystore
file, you can edit the
located at
You must restart Sentinel Server after making changes.
Using a new keyEntry alias
The default keyEntry alias is either the IP address or the hostname of the local machine. To use a
different keyEntry alias, open the das_proxy.xml file and set the value of “certificateAlias” in the
component “ProxyService” to the new value.
You must restart Sentinel Server after making changes.
58 Sentinel 6.1 Reference Guide
Page 59

6
Sentinel Accounts and Password
novdocx (en) 7 January 2010
Changes
This section discusses users that are created or used during Sentinel installation and normal Sentinel
operations. Unless you create domain users in advance in order to use Windows Authentication,
these users are created by the Sentinel installer. These user accounts are used for Sentinel’s normal
operations, such as event inserts into the Sentinel database.
The administrator might select to occasionally change the passwords for these accounts. To ensure
continued normal Sentinel operations, there are special procedures necessary to update the
passwords in all necessary locations.
6.1 Sentinel Default Users
This section discusses about Sentinel default users.
6.1.1 Native Database Authentication
Installer creates several users during installation if you use native database authentication (Oracle or
Microsoft SQL Server). These users are all created as database users in the Oracle or SQL Server
database, and the passwords are configurable at install time. The installer will create the users with
the following default names:
6
esecdba: Schema owner
esecadm: Sentinel administrator
esecrpt: Reporter user, same password as the admin user
esecapp: Sentinel application user. Used by Sentinel Server to connect to the database
In addition to creating a database user for the Sentinel administrator, the installer also creates a
Sentinel user with the same username and password for the Sentinel Control Center. For UNIX only,
the installer creates an operating system user with no password set. To log in as this user, the UNIX
administrator must set a password or su to the user as root.
6.1.2 Windows Authentication
If you use Windows authentication, the Windows administrator must create several domain accounts
before the installation is started. The credentials for these accounts must be given during the
Sentinel installation:
Sentinel DB Administrator: Schema owner
Sentinel Administrator: Sentinel administrator
Sentinel Report User: Reporter user, same password as the admin user.
Sentinel Application User: Sentinel application username for connecting to the database.
Windows Authentication users are supported only when SQL Server is being used and DAS is
running on Windows.
Sentinel Accounts and Password Changes
59
Page 60

6.2 Password Changes
Corporate policy might require that passwords be changed on a regular schedule. Sentinel user
passwords can be changed using database utilities. After changing a password, some Sentinel
components need to be updated to use the new password.
6.2.1 Changing Password
This section discusses about changing password
SQL Server Accounts
On Windows, this procedure can be used to change the password for the Sentinel Application User,
the Sentinel Database User, or the Sentinel Report User. To change the password for the Sentinel
Administrator or other Sentinel Control Center user, see Section 6.2.1, “Changing Password,” on
page 60.
To change password in MS SQL Server Management Studio:
novdocx (en) 7 January 2010
1 Open the MS SQL Enterprise Manager/ MS SQL and select Security > Logins.
2 Right-click a username from the right pane and select properties.
3 Change the password. Click OK.
Follow the procedures in Sentinel updates after a password change.
Oracle Accounts
This procedure can be used to change the password for the Sentinel Application User, the Sentinel
Database User, or the Sentinel Report User. To change the password for the Sentinel Administrator
or other Sentinel Control Center user, see Section 6.2.1, “Changing Password,” on page 60.
To change password in Oracle:
1 Connect to Oracle Enterprise Manager with user having sysdba privilege.
2 Select your specific database from the left pane.
3 In Database > Security > Users, select a user for which you want to change the password.
4 Provide new password and confirm the password. Click Apply.
Follow the procedures in Sentinel updates after a password Change.
Windows Domain Accounts
If the Sentinel system uses domain user accounts and Windows Authentication, use the following
password change procedures. These procedures can be used for the Sentinel Administrator, the
Sentinel Database User, the Sentinel Report User, and the Sentinel Application User. It can also be
used for any Sentinel Control Center account that uses Windows Authentication.
To change the password for Windows domain accounts:
1 Log into a machine using the account and use standard Windows password change procedures
or
60 Sentinel 6.1 Reference Guide
Page 61

Request a password change from a Windows administrator.
2 Follow the procedures in Sentinel updates after a password change.
Sentinel Control Center Accounts (Native DB Authentication)
This procedure can be used to change the password for the Sentinel Administrator account or any
other Sentinel Control Center user.
To change the Sentinel Administrator password:
1 Login to the Sentinel Control Center as the Sentinel Administrator or another user with User
Management permissions.
2 Click Admin > User Configuration. The User Manager window displays.
3 Double-click esecadm user account or right-click User Details.
4 Modify the account password and confirm password. Click OK.
No additional updates are needed in the Sentinel system.
Sentinel Control Center Accounts (Windows Authentication)
novdocx (en) 7 January 2010
Use standard procedures for changing the password for Windows domain accounts.
6.2.2 Sentinel Updates After a Password Change
The passwords for certain Sentinel users, such as the Sentinel Database User and the Sentinel
Application User, are encrypted and stored in configuration files and used in normal Sentinel
operations. These configuration files must be updated after the passwords are changed.
Updating Sentinel Application User Password
The Sentinel Application User credentials are stored encrypted in the container xml files. After a
password change, these files must be updated for Sentinel to continue working.
The procedures are different depending on whether the Sentinel Application User uses Native
Database Authentication or Windows Authentication.
To update the Sentinel Application User password (Native DB Authentication):
1 Change the password for the Sentinel Application User (esecapp by default) using database
utilities as described in Section 6.2.1, “Changing Password,” on page 60.
2 Using the dbconfig utility, update all container xml files. This is required because these xml
files store the (encrypted) esecapp password to allow DAS and Advisor to connect to the
database.
The container xml files are located in the following locations:
For Windows:
%ESEC_HOME%\config
For Oracle:
$ESEC_HOME/config
Sentinel Accounts and Password Changes 61
Page 62

For more information on usage of the dbconfig utility, see Chapter 5, “Sentinel Data Access
Service,” on page 51.
dbconfig –a {$ESEC_HOME/config | %ESEC_HOME%\config} -p <password>
To update the Sentinel Application User password (Windows Authentication):
1 Change the password for the Sentinel Application User domain account as described in
Section 6.2.1, “Changing Password,” on page 60.
2 On your DAS machine, open Windows Services (Control Panel > Administrative Tools >
Services).
3 Right-click Sentinel > Properties. Click the Log On tab and update Log on as password. Click
Apply and click OK.
novdocx (en) 7 January 2010
4 If you have Advisor installed, you will need to update the Run as property (Control Panel >
Scheduled Tasks > right-click Properties) of the Advisor Scheduled task(s).
62 Sentinel 6.1 Reference Guide
Page 63

novdocx (en) 7 January 2010
5 Click Set password. Provide the new password twice and click OK. Click Apply and click OK.
Updating Sentinel Database User Password
These password change procedures are only necessary if extra Sentinel Data Manager jobs have
been created and scheduled or the Sentinel Data Manager command line interface is being used.
To change Sentinel DB Administrator password (Windows Authentication):
1 Use the Windows Operating System to change the password as described in Section 6.2.1,
“Changing Password,” on page 60.
2 If you are running any SDM command line scheduled tasks in your environment, you will need
to update the Run as property (Control Panel > Scheduled Tasks > right-click Properties).
3 Click Set password. Provide the new password twice and click OK. Click Apply and click OK.
To update the Sentinel DB Administrator password (Native DB Authentication):
1 Change the password for the Sentinel DB Administrator User (esec by default) using database
utilities password as described in Section 6.2.1, “Changing Password,” on page 60.
Sentinel Accounts and Password Changes 63
Page 64

2 In order for automated SDM command line tasks to continue to work (if applicable in your
environment), update the dbPass in the sdm.connect file with the new esecdba password using
the SDM GUI or command line. For more information, see “Sentinel Data Manager” in
Sentinel 6.1 User Guide.
sdm -action saveConnection -server <oracle/mssql> -host <hostIp/hostName>
-port <portnum> -database <databaseName/SID> [-driverProps
<propertiesFile>] {-user <dbUser> -password <dbPass>} -connectFile
<filenameToSaveConnection>
Updating Sentinel Report User Password
This procedure is only necessary for Crystal on Windows. For Crystal on Linux, no changes are
necessary.
To update the Sentinel Report User password for Crystal on Windows:
1 Change the password for the Sentinel Report User (esecrpt by default) using database utilities
as described in Section 6.2.1, “Changing Password,” on page 60.
2 Log into the Crystal Server machine.
3 Go to Control Panel > Administrative Tools >Data Sources (ODBC) to update the ODBC Data
Source Name (DSN).
4 Under the System DSN tab, highlight sentineldb and click Configure.
5 Click Next. Update the password.
novdocx (en) 7 January 2010
6 Click Next until you get a Finish button. Click Finish.
64 Sentinel 6.1 Reference Guide
Page 65

7
Sentinel Database Views for
novdocx (en) 7 January 2010
Oracle
This section lists the SentinelTM schema views for Oracle*. The views provide information for
developing your own reports (Crystal Reports*). Sentinel defines an event schema that is used to
hold the parsed data received from event sources. For more information on the Sentinel Event
schema, see Event schema (http://developer.novell.com/wiki/index.php/Event_schema).
7.1 Views
Listed below are the views available with Sentinel.
7.1.1 ACTVY_PARM_RPT_V
This view contains information about iTRACTM activities.
Column Name Datatype Comment
ACTVY_PARM_ID varchar2(36) Activity parameter identifier
ACTVY_ID varchar2(36) Activity identifier
PARM_NAME varchar2(255) Activity Parameter name
7
PARM_TYP_CD varchar2(1) Activity parameter type code
DATA_TYP varchar2(50) Activity parameter data type
DATA_SUBTYP varchar2(50) Activity parameter data subtype
RQRD_F number (1,0) Required flag
PARM_DESC varchar2(255) Activity parameter description
PARM_VAL varchar2(1000) Activity parameter value
FORMATTER varchar2(255) Activity parameter formatter
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number (38,0) User who created the object
MODIFIED_BY number (38,0) User who last modified the object
7.1.2 ACTVY_REF_PARM_VAL_RPT_V
This view contains information about iTRACTM activities.
Sentinel Database Views for Oracle
65
Page 66
Column Name Datatype Comment
ACTVY_ID varchar2(36) Activity identifier
ACTVY_PARM_ID varchar2(36) Activity parameter identifier
CREATED_BY number(38,0) User who created the object
DATE_CREATED Date Date the entry was created
DATE_MODIFIED Date Date the entry was modified
MODIFIED_BY number(38,0) User who last modified the object
PARM_VAL varchar2(1000) Activity parameter value
SEQ_NUM number(38,0) Sequence number
7.1.3 ACTVY_REF_RPT_V
This view contains information about iTRAC activities.
novdocx (en) 7 January 2010
Column Name Datatype Comment
ACTVY_ID varchar2(36) Activity identifier
SEQ_NUM number(38,0) Sequence number
REFD_ACTVY_ID varchar2(36) Referenced activity identifier
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38,0) User who created object
MODIFIED_BY number(38,0) User who last modified object
7.1.4 ACTVY_RPT_V
This view contains information about iTRAC activities.
Column Name Datatype Comment
ACTVY_ID varchar2(36) Activity identifier
ACTVY_NAME varchar2(255) Activity name
ACTVY_TYP_CD varchar2(1) Activity type code
ACCESS_LVL varchar2(50) Access level
EXEC_LOC varchar2(50) Execution location
ACTVY_DESC varchar2(255) Activity description
PROCESSOR varchar2(255) Processor
INPUT_FORMATTER varchar2(255) Input formatter
66 Sentinel 6.1 Reference Guide
Page 67

Column Name Datatype Comment
OUTPUT_FORMATTER varchar2 (255) Output formatter
APP_NAME varchar2 (25) Application name
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number (38,0) User who created object
MODIFIED_BY number (38,0) User who last modified object
7.1.5 ADV_NXS_FEED_V
This view contains information about the Advisor feed files that are processed on a regular schedule.
Column Name Datatype Comment
FILE_NAME varchar (256) The filename of the Advisor feed file.
novdocx (en) 7 January 2010
HASH_VALUE varchar (256) The hash value of the Advisor feed
file.
RECORDS_INSERTED number (18,0) The number of records inserted into
the database.
RECORDS_UPDATED number (18,0) The number of records updated into
the database.
PROCESSING_START_TIME date Time stamp indicating when the
processing of the feed files started.
PROCESSING_END_TIME date Time stamp indicating when the
processing of the feed files ended.
GENERATION date The unique ID to which each feed file
belongs.
DATE_CREATED date Time stamp indicating when the feed
file information was entered in the
Sentinel database.
DATE_MODIFIED date Time stamp indicating when the feed
file information was modified in the
Sentinel database.
CREATED_BY number ID of the user who entered the feed
file information in the Sentinel
database.
MODIFIED_BY number ID of the user who modified the feed
file information in the Sentinel
database.
Sentinel Database Views for Oracle 67
Page 68

7.1.6 ADV_NXS_PRODUCTS_V
This view contains information about all the products that are supported by Novell® for Advisor,
which include the Intrusion Detection System (IDS), Vulnerablility Scanners, and Knowledge Base
(OSVDB, CVE, and Bugtraq).
Column Name Datatype Comment
PRODUCT_ID number The unique ID of the product.
PRODUCT_NAME varchar2 (256 char) Name of the product. For example, Cisco*
Secure IDS, Enterasys* Dragon* Network
Sensor, or McAfee* IntruShield*.
INTERNAL_NAME varchar2 (256 char) Short name of the product that is used in
generating the
file. This name is used by Collectors for
exploit detection. For example, if the
product name is Cisco Secure IDS, the
internal name is
exploitdetection.csv
Secure
.
novdocx (en) 7 January 2010
IS_ATTACK number (1,0) This value is
Otherwise, this value is 0.
IS_VULN number (1,0) This value is
Scanner. Otherwise, this value is 0.
IS_KB number (1,0) This value is
Base. Otherwise, this value is 0.
IS_ACTIVE number (1,0) This value is
exploit detection in the Advisor window of
Sentinel Control Center. If the value is
attacks from this product are not populated
in the
IS_POPULATE_ATTACK_NAME number (1, 0) This value is 1 by default. If the value is
the attack name is not populated in the
exploitDetection.csv
IS_POPULATE_ATTACK_CODE number (1, 0) This value is
the attack code is not populated in the
exploitDetection.csv
DATE_CREATED date Time stamp indicating when the product
information was entered in the Sentinel
database.
DATE_MODIFIED date Time stamp indicating when the product
information was modified in the Sentinel
database.
1
if the product is IDS.
1
if the product is Vulnerability
1
if the product is Knowledge
1
if the product is selected for
exploitdetection.csv
file.
1
by default. If the value is 0,
file.
file.
0
,
0
,
CREATED_BY number ID of the user who entered the product
MODIFIED_BY number ID of the user who modified the product
68 Sentinel 6.1 Reference Guide
information in the Sentinel database.
information in the Sentinel database.
Page 69

7.1.7 ADV_NXS_SIGNATURES_V
This view contains the information about the list of signatures for each product that is supported by
Novell for Advisor.
Column Name Datatype Comment
PRODUCT_ID number The unique ID of the product.
SIGNATURE_ID number The unique ID of the signature.
SIGNATURE_NAME varchar2 (256 char) Name of the signature.
PUBLISHED date Time stamp indicating when the signature
was published for the product by the
vendor.
INSERTED date Time stamp indicating when the signature
information was entered in the vendor
database.
UPDATED date Time stamp indicating when the signature
information was updated in the vendor
database.
novdocx (en) 7 January 2010
DATE_CREATED date Time stamp indicating when the signature
information was entered in the Sentinel
database.
DATE_MODIFIED date Time stamp indicating when the signature
information was modified in the Sentinel
database.
CREATED_BY number ID of the user who entered the signature
information in the Sentinel database.
MODIFIED_BY number ID of the user who modified the signature
information in the Sentinel database.
7.1.8 ADV_NXS_MAPPINGS_V
This view contains the mapping information for the products supported by Novell for Advisor. It
provides information about the type of mapping between each product including the IDS product
signatures, Vulnerability product signatures, and Knowledge Base product signatures.
Column Name Datatype Comment
SOURCE_PRODUCT_ID number The unique ID of the source product.
SOURCE_SIGNATURE_ID number The unique ID of the source signature.
TARGET_PRODUCT_ID number The unique ID of the target product.
TARGET_SIGNATURE_ID number The unique ID of the target signature.
MAPPING_DIRECT number (1, 0) This value is
MAPPING_INDIRECT number (1, 0) This value is
1
if the mapping is direct.
1
if the mapping is indirect.
Sentinel Database Views for Oracle 69
Page 70

Column Name Datatype Comment
MAPPING_NGRAM number (1, 0) This value is 1 if the mapping is n-gram.
INSERTED date Time stamp indicating when the mapping
information was entered in the vendor
database.
UPDATED date Time stamp indicating when the mapping
was updated in the vendor database.
novdocx (en) 7 January 2010
IS_DELETED number (1, 0) This value is
invalid.
DELETED date Time stamp indicating when the mapping
was marked as invalid.
DATE_CREATED date Time stamp indicating when the mapping
information was entered in the Sentinel
database.
DATE_MODIFIED date Time stamp indicating when the mapping
information was modified in the Sentinel
database.
CREATED_BY number ID of the user who entered the mapping
information in the Sentinel database.
MODIFIED_BY number ID of the user who modified the mapping
information in the Sentinel database.
1
if the mapping is marked as
7.1.9 ADV_OSVDB_DETAILS_V
This view contains information about the known vulnerablities from the OSVDB for the products
supported by Novell for Advisor. It also stores the classifications to which the vulnerability applies.
Column Name Datatype Comment
OSVDB_ID number The unique ID of the vulnerability in the
OSVDB_TITLE clob The normalized name of the vulnerability.
DESCRIPTION clob A brief description of the vulnerability.
URGENCY number Indicates the urgency of the vulnerability.
SEVERITY number Indicates the severity of the vulnerability.
ATTACK_TYPE_AUTH_MANAGE number (1, 0) This value is
70 Sentinel 6.1 Reference Guide
OSVDB.
The rating is 1- 10. The higher the
number, the more urgent the vulnerability.
The rating is 1- 10. The higher the
number, the more urgent the vulnerability.
1
if the attack type is
authentication management. For
example, brute force attack, default
password, and cookie poisoning.
Page 71

Column Name Datatype Comment
ATTACK_TYPE_CRYPT number (1, 0) This value is 1 if the attack type is
cryptographic. For example, weak
encryption (implementation or algorithm),
no encryption (plaintext), and sniffing.
ATTACK_TYPE_DOS number (1, 0) This value is 1 if the attack type is denial
of service. For example, saturation flood,
crash, lock up, and forced reboot.
ATTACK_TYPE_HIJACK number (1, 0) This value is 1 if the attack type is hijack.
For example, man-in-the-middle attacks,
IP spoofing, session timeout or take-over,
and session replay.
1
ATTACK_TYPE_INFO_DISCLOSE number (1, 0) This value is
information disclosure. For example,
comments, passwords, fingerprinting, and
system information.
ATTACK_TYPE_INFRASTRUCT number (1, 0) This value is 1 if the attack type is
infrastructure. For example, DNS
poisoning and route manipulation.
if the attack type is
novdocx (en) 7 January 2010
1
ATTACK_TYPE_INPUT_MANIP number (1, 0) This value is
manipulation. For example, XSS, SQL
injection, file retrieval, directory traversal,
overflows, and URL encoding.
ATTACK_TYPE_MISS_CONFIG number (1, 0) This value is 1 if the attack type is
misconfiguration. For example, default
files, debugging enabled, and directory
indexing.
ATTACK_TYPE_RACE number (1, 0) This value is 1 if the attack type is race
condition. For example, symlink.
ATTACK_TYPE_OTHER number (1, 0) This value is
fall under any of the above attack types.
ATTACK_TYPE_UNKNOWN number (1, 0) This value is
unknown.
IMPACT_CONFIDENTIAL number (1, 0) This value is
attack(s) is loss of confidential
information. For example, passwords,
server information, environment
variables, confirmation of file existence,
path disclosure, file content access, and
SQL injection.
IMPACT_INTEGRITY number (1, 0) This value is
attack(s) is loss of integrity, which results
in data modifications by unauthorized
persons. For example, unauthorized file
modification, deletion, or creation, remote
file inclusion, and arbitrary command
execution.
if the attack type is input
1
if the attack type does not
1
if the attack type is
1
if the impact of the
1
if the impact of the
Sentinel Database Views for Oracle 71
Page 72

Column Name Datatype Comment
IMPACT_AVAILABLE number (1, 0) This value is 1 if the impact of the attack
is loss of availability of a service or
information.
1
IMPACT_UNKNOWN number (1, 0) This value is
is unknown.
if the impact of the attack
novdocx (en) 7 January 2010
EXPLOIT_AVAILABLE number (1, 0) This value is
the vulnerability.
EXPLOIT_UNAVAILABLE number (1, 0) This value is
for the vulnerability.
EXPLOIT_RUMORED number (1, 0) This value is
exist for the vulnerability.
EXPLOIT_UNKNOWN number (1, 0) This value is
the vulnerability.
VULN_VERIFIED number (1, 0) This value is
vulnerability has been verified.
VULN_MYTH_FAKE number (1, 0) This value is
or a false alarm.
VULN_BEST_PRAC number (1, 0) This value is
result of not following the best practices in
the configuration or usage of the
vulnerable system or software.
VULN_CONCERN number (1, 0) This value is 1 if the vulnerability requires
additional concern for remediation.
VULN_WEB_CHECK number (1, 0) This value is
common problem in Web servers or Web
applications.
1
if an exploit is available for
1
if an exploit is not available
1
if an exploit is rumored to
1
if an exploit is unknown for
1
if the existence of the
1
if the vulnerability is a myth
1
if the vulnerability is a
1
if the vulnerability is a
ATTACK_SCENARIO clob Description of how a vulnerability can be
SOLUTION_DESCRIPTION clob Description of the solution that is used to
FULL_DESCRIPTION clob The complete description of the
LOCATION_PHYSICAL number (1, 0) This value is
LOCATION_LOCAL number (1, 0) This value is
LOCATION_REMOTE number (1, 0) This value is
LOCATION_DIALUP number (1, 0) This value is 1 if the vulnerability can be
LOCATION_UNKNOWN number (1, 0) This value is
72 Sentinel 6.1 Reference Guide
exploited.
fix the vulnerability.
vulnerability.
1
if the vulnerability can be
exploited with only physical system
access.
1
if the vulnerability can be
exploited on a local system.
1
if the vulnerabilitycan be
exploited on a remote system.
exploited using a dial-up connection.
1
if the vulnerability is
exploited in an unknown location.
Page 73

Column Name Datatype Comment
PUBLISHED date Time stamp indicating when the
vulnerability was published in the
OSVDB.
INSERTED date Time stamp indicating when the
vulnerability was inserted in the vendor
database.
UPDATED date Time stamp indicating when the
vulnerability was updated in the vendor
database.
DATE_CREATED date Time stamp indicating when the
vulnerability information was entered in
the Sentinel database.
DATE_MODIFIED date Time stamp indicating when the
vulnerability information was modified in
the Sentinel database.
CREATED_BY number The ID of the user who entered the
vulnerability information in the Sentinel
database.
novdocx (en) 7 January 2010
MODIFIED_BY number The ID of the user who modified the
vulnerability information in the Sentinel
database.
7.1.10 ADV_NXS_KB_PATCH_V
This view contains information about the patches that are required to remove the vulnerabilities.
Column Name Datatype Comment
ID number The unique ID for the row.
OSVDB_ID number The ID of the vulnerability in the OSVDB.
TYPE_NAME varchar2 (128 char) The type of the patch used to remove the
vulnerability.
TYPE_ID number The unique ID of the patch.
REF_VALUE clob The URL that has the patch information.
DATE_CREATED date Time stamp indicating when the patch
information was entered in the Sentinel
database.
DATE_MODIFIED date Time stamp indicating when the patch
information was modified in the Sentinel
database.
CREATED_BY number The ID of the user who entered the patch
information in the Sentinel database.
MODIFIED_BY number The ID of the user who modified the patch
information in the Sentinel database.
Sentinel Database Views for Oracle 73
Page 74
7.1.11 ADV_NXS_KB_PRODUCTSREF_V
This view contains the information about the products that are affected by the vulnerability.
Column Name Datatype Comment
ID number The unique ID for the row.
OSVDB_ID number The ID of the vulnerability in the OSVDB.
VENDOR_NAME varchar2 (128 char) Name of the vendor of the product that is
affected by the vulnerability.
VERSION_NAME varchar2 (128 char) Version of the product that is affected by
the vulnerability.
BASE_NAME varchar2 (128 char) Name of the product that is affected by
the vulnerability.
TYPE_NAME varchar2 (128 char) Indicates whether the product is affected
by the vulnerability or not.
DATE_CREATED date Time stamp indicating when the product
information was entered in the Sentinel
database.
novdocx (en) 7 January 2010
DATE_MODIFIED date Time stamp indicating when the product
information was modified in the Sentinel
database.
CREATED_BY number The ID of the user who entered the
product information in the Sentinel
database.
MODIFIED_BY number The ID of the user who modified the
product information in the Sentinel
database.
7.1.12 ASSET_CATEGORY_RPT_V
This iew references ASSET_CTGRY table that stores information about asset categories
Column Name Datatype Comment
ASSET_CATEGORY_ID number(38) Asset category identifier
ASSET_CATEGORY_NAME varchar2(100) Asset category name
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38) User who created object
MODIFIED_BY number(38) User who last modified object
74 Sentinel 6.1 Reference Guide
Page 75
7.1.13 ASSET_HOSTNAME_RPT_V
This view references ASSET_HOSTNAME table that stores information about alternate host names
for assets.
Column Name Datatype Comment
ASSET_HOSTNAME_ID varchar2(36) Asset alternate hostname identifier
PHYSICAL_ASSET_ID varchar2(36) Physical asset identifier
HOST_NAME varchar2(255) Host name
CUST_ID number(38) Customer identifier
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38) User who created object
MODIFIED_BY number(38) User who last modified object
novdocx (en) 7 January 2010
7.1.14 ASSET_IP_RPT_V
This view references ASSET_IP table that stores information about alternate IP addresses for assets.
Column Name Datatype Comment
ASSET_IP_ID varchar2(36) Asset alternate IP identifier
PHYSICAL_ASSET_ID varchar2(36) Physical asset identifier
IP_ADDRESS number(38) Asset IP address
CUST_ID number(38) Customer identifier
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38) User who created object
MODIFIED_BY number(38) User who last modified object
7.1.15 ASSET_LOCATION_RPT_V
This view references ASSET_LOC table that stores information about asset locations.
Column Name Datatype Comment
LOCATION_ID number(38) Location identifier
CUST_ID number(38) Customer identifier
BUILDING_NAME varchar2(255) Building name
ADDRESS_LINE_1 varchar2(255) Address line 1
Sentinel Database Views for Oracle 75
Page 76

Column Name Datatype Comment
ADDRESS_LINE_2 varchar2(255) Address line 2
CITY varchar2(100) City
STATE varchar2(100) State
COUNTRY varchar2(100) Country
ZIP_CODE varchar2(50) Zip code
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38) User who created object
MODIFIED_BY number(38) User who last modified object
7.1.16 ASSET_RPT_V
novdocx (en) 7 January 2010
This view references ASSET table that stores information about the physical and soft assets.
Column Name Datatype Comment
ASSET_ID varchar2(36) Asset identifier
CUST_ID number(38) Customer identifier
ASSET_NAME varchar2(255) Asset name
PHYSICAL_ASSET_ID varchar2(36) Physical asset identifier
PRODUCT_ID number(38) Product identifier
ASSET_CATEGORY_ID number(38) Asset category identifier
ENVIRONMENT_IDENTITY_ID number(38) Environment identify code
PHYSICAL_ASSET_IND number(1) Physical asset indicator
ASSET_VALUE_ID number(38) Asset value code
CRITICALITY_ID number(38) Asset criticality code
SENSITIVITY_ID number(38) Asset sensitivity code
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38) User who created object
MODIFIED_BY number(38) User who last modified object
7.1.17 ASSET_VALUE_RPT_V
This view references ASSET_VAL_LKUP table that stores information about the asset value.
76 Sentinel 6.1 Reference Guide
Page 77

Column Name Datatype Comment
ASSET_VALUE_ID number(38) Asset value code
ASSET_VALUE_NAME varchar2(50) Asset value name
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38) User who created object
MODIFIED_BY number(38) User who last modified object
7.1.18 ASSET_X_ENTITY_X_ROLE_RPT_V
This view references ASSET_X_ENTITY_X_ROLE table that associates a person or an
organization to an asset.
Column Name Datatype Comment
novdocx (en) 7 January 2010
PERSON_ID varchar2(36) Person identifier
ORGANIZATION_ID varchar2(36) Organization identifier
ROLE_CODE varchar2(5) Role code
ASSET_ID varchar2(36) Asset identifier
ENTITY_TYPE_CODE varchar2(5) Entity type code
PERSON_ROLE_SEQUENCE number(38) Order of persons under a particular role
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38) User who created object
MODIFIED_BY number(38) User who last modified object
7.1.19 ASSOCIATIONS_RPT_V
This view references ASSOCIATIONS table that associates users to incidents, incidents to
annotations and so on.
Column Name Datatype Comment
TABLE1 varchar2(64) Table name 1. For example, incidents
ID1 varchar2(36) ID1. For example, incident ID.
TABLE2 varchar2(64) Table name 2. For example, users.
ID2 varchar2(36) ID2. For example, user ID.
DATE_CREATED date Date the entry was created
Sentinel Database Views for Oracle 77
Page 78

Column Name Datatype Comment
DATE_MODIFIED date Date the entry was modified
CREATED_BY number User who created object
MODIFIED_BY number User who last modified object
7.1.20 ATTACHMENTS_RPT_V
This view references ATTACHMENTS table that stores attachment data.
Column Name Datatype Comment
ATTACHMENT_ID number Attachment identifier
NAME varchar2(255) Attachment name
SOURCE_REFERENCE varchar2(64) Source reference
TYPE varchar2(32) Attachment type
novdocx (en) 7 January 2010
SUB_TYPE varchar2(32) Attachment subtype
FILE_EXTENSION varchar2(32) File extension
ATTACHMENT_DESCRIPTION varchar2(255) Attachment description
DATA clob Attachment data
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number User who created object
MODIFIED_BY number User who last modified object
7.1.21 AUDIT_RECORD_RPT_V
This view references AUDIT_RECORD table that stores Sentinel internal audit data.
Column Name Datatype Comment
AUDIT_ID varchar2(36) Audit record identifier
AUDIT_TYPE varchar2(255) Audit type
SRC varchar2(255) Audit source
SENDER_HOSTNAME varchar2(255) Sender hostname
SENDER_HOST_IP varchar2(255) Sender host IP
SENDER_CONTAINER varchar2(255) Sender container name
SENDER_ID varchar2(255) Sender Identifier
CLIENT varchar2(255) Client application that requested audit
78 Sentinel 6.1 Reference Guide
Page 79

Column Name Datatype Comment
EVT_NAME varchar2(255) Event name
RES varchar2(255) Event resource
SRES varchar2(255) Event sub-resource
MSG varchar2(500) Event message
CREATED_BY number(0) User who created object
MODIFIED_BY number(0) User who last modified object
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
7.1.22 CONFIGS_RPT_V
This view references CONFIGS table that stores general configuration information of the
application.
novdocx (en) 7 January 2010
Column Name Datatype Comment
USR_ID varchar2(32) User name.
APPLICATION varchar2(255) Application identifier
UNIT varchar2(64) Application unit
VALUE varchar2(255) Text value if any
DATA clob XML data
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number User who created object
MODIFIED_BY number User who last modified object
7.1.23 CONTACTS_RPT_V
This view references CONTACTS table that stores contact information.
Column Name Datatype Comment
CNT_ID number Contact ID - Sequence number
FIRST_NAME varchar2(20) Contact first name.
LAST_NAME varchar2(30) Contact last name.
TITLE varchar2(128) Contact title
DEPARTMENT varchar2(128) Department
PHONE varchar2(64) Contact phone
Sentinel Database Views for Oracle 79
Page 80

Column Name Datatype Comment
EMAIL varchar2(255) Contact e-mail
PAGER varchar2(64) Contact pager
CELL varchar2(64) Contact cell phone
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number User who created object
MODIFIED_BY number User who last modified object
7.1.24 CORRELATED_EVENTS_RPT_V (legacy view)
This view is provided for backward compatibility. New reports should use
CORRELATED_EVENTS_RPT_V1.
novdocx (en) 7 January 2010
7.1.25 CORRELATED_EVENTS_RPT_V1
This vew contains current and historical correlated events (correlated events imported from
archives).
Column Name Datatype Comment
PARENT_EVT_ID varchar2(36) Event Universal Unique Identifier (UUID) of
parent event
CHILD_EVT_ID varchar2(36) Event Universal Unique Identifier (UUID) of child
event
PARENT_EVT_TIME date Parent event time
CHILD_EVT_TIME date Child event time
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38) User who created object
MODIFIED_BY number(38) User who last modified object
7.1.26 CRITICALITY_RPT_V
This view references CRIT_LKUP table that contains information about asset criticality.
Column Name Datatype Comment
CRITICALITY_ID number(38) Asset criticality code
CRITICALITY_NAME varchar2(50) Asset criticality name
DATE_CREATED date Date the entry was created
80 Sentinel 6.1 Reference Guide
Page 81
Column Name Datatype Comment
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38) User who created object
MODIFIED_BY number(38) User who last modified object
7.1.27 CUST_HIERARCHY_V
This view references CUST_HIERARCHY table that stores information about MSSP customer
hierarchy.
Column Name Datatype Comment
CUST_HIERARCHY_ID number(38) Customer hierarchy ID
CUST_NAME varchar2(255) Customer
CUST_HIERARCHY_LVL1 varchar2(255) Customer hierarchy level 1
novdocx (en) 7 January 2010
CUST_HIERARCHY_LVL2 varchar2(255) Customer hierarchy level 2
CUST_HIERARCHY_LVL3 varchar2(255) Customer hierarchy level 3
CUST_HIERARCHY_LVL4 varchar2(255) Customer hierarchy level 4
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number User who created object
MODIFIED_BY number User who last modified object
7.1.28 CUST_RPT_V
This view references CUST table that stores customer information for MSSPs.
Column Name Datatype Comment
CUST_ID number(38) Customer identifier
CUSTOMER_NAME varchar2(255) Customer name
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38) User who created object
MODIFIED_BY number(38) User who last modified object
7.1.29 ENTITY_TYPE_RPT_V
This view references ENTITY_TYP table that stores information about entity types (person,
organization).
Sentinel Database Views for Oracle 81
Page 82

Column Name Datatype Comment
ENTITY_TYPE_CODE varchar2(5) Entity type code
ENTITY_TYPE_NAME varchar2(50) Entity type name
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38) User who created object
MODIFIED_BY number(38) User who last modified object
7.1.30 ENV_IDENTITY_RPT_V
This view references ENV_IDENTITY_LKUP table that stores information about asset
environment identity.
Column Name Datatype Comment
novdocx (en) 7 January 2010
ENVIRONMENT_IDENTITY_ID number(38) Environment identity code
ENV_IDENTITY_NAME varchar2(255) Environment identity name
DATE_CREATED Date Date the entry was created
DATE_MODIFIED Date Date the entry was modified
CREATED_BY number(38) User who created object
MODIFIED_BY number(38) User who last modified object
7.1.31 ESEC_CONTENT_GRP_CONTENT_RPT_V
This view contains information about Solution Packs.
Column Name Datatype Comment
CONTENT_GRP_ID varchar2(36) Content group identifier
CONTENT_ID varchar2(255) Content identifier
CONTENT_TYP varchar2(100) Content type
CONTENT_HASH varchar2(255) Content hash
DATE_CREATED Date Date the entry was created
DATE_MODIFIED Date Date the entry was modified
CREATED_BY number(38,0) User who created object
MODIFIED_BY number(38,0) User who last modified object
82 Sentinel 6.1 Reference Guide
Page 83

7.1.32 ESEC_CONTENT_GRP_RPT_V
This view contains information about Solution Packs.
Column Name Datatype Comment
CONTENT_GRP_ID varchar2(36) Content group identifier
CONTENT_GRP_NAME varchar2(255) Content group name
CONTENT_GRP_DESC Clob Content group description
CTRL_ID varchar2(36) Control identifier
CONTENT_EXTERNAL_ID varchar2(255) Content external identifier
DATE_CREATED Date Date the entry was created
DATE_MODIFIED Date Date the entry was modified
CREATED_BY number(38,0) User who created object
MODIFIED_BY number(38,0) User who last modified object
novdocx (en) 7 January 2010
7.1.33 ESEC_CONTENT_PACK_RPT_V
This view contains information about Solution Packs.
Column Name Datatype Comment
CONTENT_PACK_ID varchar2(36) Content pack identifier
CONTENT_PACK_DESC Clob Content pack description
CONTENT_PACK_NAME varchar2(255) Content pack name
CONTENT_EXTERNAL_ID varchar2(255) Content external identifier
DATE_MODIFIED Date Date the entry was modified
DATE_CREATED Date Date the entry was created
CREATED_BY number(38,0) User who created object
MODIFIED_BY number(38,0) User who last modified object
7.1.34 ESEC_CONTENT_RPT_V
This view contains information about Solution Packs.
Column Name Datatype Comment
CONTENT_PACK_ID varchar2(36) Content pack identifier
CONTENT_ID varchar2(255) Content identifier
CONTENT_NAME varchar2(255) Content name
CONTENT_STATE number(38,0) Content state
Sentinel Database Views for Oracle 83
Page 84

Column Name Datatype Comment
CONTENT_TYP varchar2(100) Content type
CONTENT_DESC Clob Content description
CONTENT_CONTEXT Clob Content context
CONTENT_HASH varchar2(255) Content hash
DATE_CREATED Date Date the entry was created
DATE_MODIFIED Date Date the entry was modified
MODIFIED_BY number(38,0) User who last modified object
CREATED_BY number(38,0) User who created object
7.1.35 ESEC_CTRL_CTGRY_RPT_V
This view contains information about Solution Packs.
novdocx (en) 7 January 2010
Column Name Datatype Comment
CTRL_CTGRY_ID varchar2(36) Control category identifier
CTRL_CTGRY_DESC Clob Control category description
CTRL_CTGRY_NAME varchar2(255) Control category name
CONTENT_PACK_ID varchar2(36) Content pack identifier
CONTENT_EXTERNAL_ID varchar2(255) Content external identifier
DATE_CREATED Date Date the entry was created
DATE_MODIFIED Date Date the entry was modified
CREATED_BY number(38,0) User who created object
MODIFIED_BY number(38,0) User who last modified object
7.1.36 ESEC_CTRL_RPT_V
This view contains information about Solution Packs.
Column Name Datatype Comment
CTRL_ID varchar2(36) Control identifier
CTRL_NAME varchar2(255) Control name
CTRL_DESC clob Control description
CTRL_STATE number(38,0) Control state
CTRL_NOTES clob Control notes
CTRL_CTGRY_ID varchar2(36) Control category identifier
84 Sentinel 6.1 Reference Guide
Page 85

Column Name Datatype Comment
CONTENT_EXTERNAL_ID varchar2(255) Content external identifier
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38,0) User who created object
MODIFIED_BY number(38,0) User who last modified object
7.1.37 ESEC_DISPLAY_RPT_V
This view references ESEC_DISPLAY table that stores displayable properties of objects. Currently
used in renaming meta-tags. Used with Event Configuration (Business Relevance).
Column Name Datatype Comment
DISPLAY_OBJECT varchar2(32) The parent object of the property
novdocx (en) 7 January 2010
TAG varchar2(32) The native tag name of the property
LABEL varchar2(32) The display string of tag.
POSITION number Position of tag within display.
WIDTH number The column width
ALIGNMENT number The horizontal alignment
FORMAT number The enumerated formatter for displaying the
property
ENABLED varchar2(1) Indicates if the tag is shown.
TYPE number Indicates datatype of tag.
1 = string
2 = ulong
3 = date
4 = uuid
5 = ipv4
DESCRIPTION varchar2(255) Textual description of the tag
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number User who created object
MODIFIED_BY number User who last modified object
REF_CONFIG varchar2(4000) Referential data configuration
Sentinel Database Views for Oracle 85
Page 86

7.1.38 ESEC_PORT_REFERENCE_RPT_V
This view references ESEC_PORT_REFERENCE table that stores industry standard assigned port
numbers.
Column Name Datatype Comment
PORT_NUMBER number Per http://www.iana.org/assignments/port-numbers
(http://www.iana.org/assignments/port-numbers), the
numerical representation of the port. This port number
is typically associated with the Transport Protocol level
in the TCP/IP stack.
PROTOCOL_NUMBER number Per http://www.iana.org/assignments/protocol-
numbers (http://www.iana.org/assignments/protocolnumbers), the numerical identifiers used to represent
protocols that are encapsulated in an IP packet.
PORT_KEYWORD varchar2(64) Per http://www.iana.org/assignments/port-numbers
(http://www.iana.org/assignments/port-numbers), the
keyword representation of the port.
novdocx (en) 7 January 2010
PORT_DESCRIPTION varchar2(512) Port description.
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number User who created object
MODIFIED_BY number User who last modified object
7.1.39 ESEC_PROTOCOL_REFERENCE_RPT_V
This view references ESEC_PROTOCOL_REFERENCE table that stores industry standard
assigned protocol numbers.
Column Name Datatype Comment
PROTOCOL_NUMBER number Per http://www.iana.org/assignments/protocol-
numbers (http://www.iana.org/assignments/
protocol-numbers), the numerical identifiers used
to represent protocols that are encapsulated in
an IP packet.
PROTOCOL_KEYWORD varchar2(64) Per http://www.iana.org/assignments/protocol-
numbers (http://www.iana.org/assignments/
protocol-numbers), the keyword used to
represent protocols that are encapsulated in an
IP packet.
PROTOCOL_DESCRIPTION varchar2(512) IP packet protocol description.
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number User who created object
86 Sentinel 6.1 Reference Guide
Page 87

Column Name Datatype Comment
MODIFIED_BY number User who last modified object
7.1.40 ESEC_SEQUENCE_RPT_V
This view references ESEC_SEQUENCE table that’s used to generate primary key sequence
numbers for Sentinel tables.
Column Name Datatype Comment
TABLE_NAME varchar2(32) Name of the table.
COLUMN_NAME varchar2(255) Name of the column
SEED number Current value of primary key field.
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
novdocx (en) 7 January 2010
CREATED_BY number User who created object
MODIFIED_BY number User who last modified object
7.1.41 ESEC_UUID_UUID_ASSOC_RPT_V
This view contains information about object relationships. Used internally by Sentinel and not for
reporting purposes.
Column Name Datatype Comment
OBJECT1 varchar2(64) Object 1
ID1 varchar2(36) UUID for object 1
OBJECT2 varchar2(64) Object 2
ID2 varchar2(36) UUID for object 2
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38,0) User who created object
MODIFIED_BY number(38,0) User who last modified object
7.1.42 EVENTS_ALL_RPT_V (legacy view)
This view is provided for backward compatibility. View contains current and historical events
(events imported from archives).
Sentinel Database Views for Oracle 87
Page 88

7.1.43 EVENTS_ALL_RPT_V1 (legacy view)
This view is provided for backward compatibility. New reports should use EVENTS_RPT_V2.
View contains current events.
7.1.44 EVENTS_RPT_V (legacy view)
This view is provided for backward compatibility. New reports should use EVENTS_RPT_V2.
View contains current and historical events.
7.1.45 EVENTS_RPT_V1 (legacy view)
This view is provided for backward compatibility. New reports should use EVENT_ALL_RPT_V.
View contains current events.
7.1.46 EVENTS_RPT_V2
This is the primary reporting view for Sentinel 6.0. This view contains current event and historical
events. It is included for legacy reports but has been replaced in Sentinel 6.1 with
EVENTS_RPT_V3.
novdocx (en) 7 January 2010
Column Name Datatype Comment
EVENT_ID varchar2(36) Event identifier
RESOURCE_NAME varchar2(255) Resource name
SUB_RESOURCE varchar2(255) Subresource name
SEVERITY integer Event severity
EVENT_PARSE_TIME date Event time
EVENT_DATETIME date Event time
EVENT_DEVICE_TIME date Event device time
SENTINEL_PROCESS_TIME date Sentinel process time
BEGIN_TIME date Events begin time
END_TIME date Events end time
REPEAT_COUNT integer Events repeat count
DESTINATION_PORT_INT integer Destination port (integer)
SOURCE_PORT_INT integer Source port (integer)
BASE_MESSAGE varchar2(4000) Base message
EVENT_NAME varchar2(255) Name of the event as reported by the
sensor
EVENT_TIME varchar2(255) Event time as reported by the sensor
CUST_ID integer Customer identifier
SOURCE_ASSET_ID integer Source asset identifier
88 Sentinel 6.1 Reference Guide
Page 89

Column Name Datatype Comment
DESTINATION_ASSET_ID integer Destination asset identifier
AGENT_ID integer Collector identifier
PROTOCOL_ID integer Protocol identifier
ARCHIVE_ID integer Archive identifier
SOURCE_IP integer Source IP address in numeric format
SOURCE_IP_DOTTED varchar2(16) Source IP in dotted format
SOURCE_HOST_NAME varchar2(255) Source host name
SOURCE_PORT varchar2(32) Source port
DESTINATION_IP integer Destination IP address in numeric format
DESTINATION_IP_DOTTED varchar2(16) Destination in dotted format
DESTINATION_HOST_NAME varchar2(255) Destination host name
novdocx (en) 7 January 2010
DESTINATION_PORT varchar2(32) Destination port
SOURCE_USER_NAME varchar2(255) Source user name
DESTINATION_USER_NAME varchar2(255) Destination user name
FILE_NAME varchar2(1000) File name
EXTENDED_INFO varchar2(1000) Extended information
CUSTOM_TAG_1 varchar2(255) Customer Tag 1
CUSTOM_TAG 2 varchar2(255) Customer Tag 2
CUSTOM_TAG 3 integer Customer Tag 3
RESERVED_TAG_1 varchar2(255) Reserved Tag 1
Reserved for future use by Novell. This
field is used for Advisor information
concerning attack descriptions.
RESERVED_TAG_2 varchar2(255) Reserved for future use by Novell. Use of
this field for any other purpose might
result in data being overwritten by future
functionality.
RESERVED_TAG_3 integer Reserved for future use by Novell. Use of
this field for any other purpose might
result in data being overwritten by future
functionality.
VULNERABILITY_RATING integer Vulnerability rating
CRITICALITY_RATING integer Criticality rating
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY integer User who created object
Sentinel Database Views for Oracle 89
Page 90

Column Name Datatype Comment
MODIFIED_BY integer User who last modified object
RV01 - 10 integer Reserved Value 1 - 10
Reserved for future use by Novell. Use of
this field for any other purpose might
result in data being overwritten by future
functionality.
RV11 - 20 date Reserved Value 1 - 31
Reserved for future use by Novell. Use of
this field for any other purpose might
result in data being overwritten by future
functionality.
RV21 - 25 varchar2(36) Reserved Value 21 - 25
Reserved for future use by Novell to store
UUIDs. Use of this field for any other
purpose might result in data being
overwritten by future functionality.
novdocx (en) 7 January 2010
RV26 - 31 varchar2(255) Reserved Value 26 - 31
Reserved for future use by Novell. Use of
this field for any other purpose might
result in data being overwritten by future
functionality.
RV33 varchar2(255) Reserved Value 33
Reserved for EventContex
Use of this field for any other purpose
might result in data being overwritten by
future functionality.
RV34 varchar2(255) Reserved Value 34
Reserved for SourceThreatLevel
Use of this field for any other purpose
might result in data being overwritten by
future functionality.
RV35 varchar2(255) Reserved Value 35
Reserved for SourceUserContext.
Use of this field for any other purpose
might result in data being overwritten by
future functionality.
RV36 varchar2(255) Reserved Value 36
90 Sentinel 6.1 Reference Guide
Reserved for DataContext.
Use of this field for any other purpose
might result in data being overwritten by
future functionality.
Page 91

Column Name Datatype Comment
RV37 varchar2(255) Reserved Value 37
Reserved for SourceFunction.
Use of this field for any other purpose
might result in data being overwritten by
future functionality.
RV38 varchar2(255) Reserved Value 38
Reserved for SourceOperationalContext.
Use of this field for any other purpose
might result in data being overwritten by
future functionality.
RV40 - 43 varchar2(255) Reserved Value 40 - 43
Reserved for future use by Novell. Use of
this field for any other purpose might
result in data being overwritten by future
functionality.
novdocx (en) 7 January 2010
RV44 varchar2(255) Reserved Value 44
Reserved for DestinationThreatLevel.
Use of this field for any other purpose
might result in data being overwritten by
future functionality.
RV45 varchar2(255) Reserved Value 45
Reserved for DestinationUserContext.
Use of this field for any other purpose
might result in data being overwritten by
future functionality.
RV46 varchar2(255) Reserved Value 46
Reserved for VirusStatus.
Use of this field for any other purpose
might result in data being overwritten by
future functionality.
RV47 varchar2(255) Reserved Value 47
Reserved for future use by Novell. Use of
this field for any other purpose might
result in
data being overwritten by future
functionality.
Sentinel Database Views for Oracle 91
Page 92

Column Name Datatype Comment
RV48 varchar2(255) Reserved Value 48
Reserved for
DestinationOperationalContext.
Use of this field for any other purpose
might result in data being overwritten by
future functionality.
RV49 varchar2(255) Reserved Value 49
Reserved for future use by Novell. Use of
this field for any other purpose might
result in data being overwritten by future
functionality.
TAXONOMY_ID integer
REFERENCE_ID_01 - 20 integer Reserved for future use by Novell. Use of
this field for any other purpose might
result in data being overwritten by future
functionality.
novdocx (en) 7 January 2010
CV01 - 10 integer Custom Value 1 - 10
Reserved for use by Customer, typically
for association of Business relevant data
CV11 - 20 date Custom Value 11 - 20
Reserved for use by Customer, typically
for association of Business relevant data
CV21 - 29 varchar2(255) Custom Value 21 – 100
Reserved for use by Customer, typically
for association of Business relevant data
CV30 - 34 varchar2(4000)
CV35 – 100 varchar2(255)
7.1.47 EVENTS_RPT_V3
This is the primary reporting view for Sentinel 6.1. This view contains current event and historical
events. It is included for legacy reports.
Column Name Datatype Comment
EVENT_ID varchar2(36) Event identifier
RESOURCE_NAME varchar2(255)
SUB_RESOURCE varchar2(255) Subresource name
SEVERITY number(38,0) Event severity
EVENT_PARSE_TIME date Event time
92 Sentinel 6.1 Reference Guide
Page 93

Column Name Datatype Comment
EVENT_DATETIME date
EVENT_DEVICE_TIME date Event device time
SENTINEL_PROCESS_TIME date Sentinel process time
BEGIN_TIME date Events begin time
END_TIME date Events end time
REPEAT_COUNT number(38,0)
TARGET_SERVICE_PORT number(38,0) Target service port
INIT_SERVICE_PORT number(38,0)
BASE_MESSAGE varchar2(4000)
EVENT_NAME varchar2(255)
EVENT_TIME varchar2(255) Event time
novdocx (en) 7 January 2010
CUST_ID number(38,0)
INIT_ASSET_ID number(38,0) Initiator asset identifier
TARGET_ASSET_ID number(38,0) Target asset identifier
AGENT_ID number(38,0)
PROTOCOL_ID number(38,0)
ARCHIVE_ID number(38,0)
INIT_IP number(38,0)
INIT_IP_DOTTED varchar2(4000)
INIT_HOST_NAME varchar2(255)
INIT_SERVICE_PORT_NAME varchar2(32)
TARGET_IP number(38,0)
TARGET_IP_DOTTED varchar2(4000)
TARGET_HOST_NAME varchar2(255)
TARGET_SERVICE_PORT_NAME varchar2(32)
INIT_USER_NAME varchar2(255) The initiating user's account name
(SourceUsername).
TARGET_USER_NAME varchar2(255)
FILE_NAME varchar2(1000)
EXTENDED_INFO varchar2(1000)
CUSTOM_TAG_1 varchar2(255) Customer Tag 1
CUSTOM_TAG_2 varchar2(255) Customer Tag 2
CUSTOM_TAG_3 number(38,0) Customer Tag 3
Sentinel Database Views for Oracle 93
Page 94

Column Name Datatype Comment
RESERVED_TAG_1 varchar2(255)
RESERVED_TAG_2 varchar2(255)
RESERVED_TAG_3 number(38,0)
VULNERABILITY_RATING number(38,0)
CRITICALITY_RATING number(38,0)
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38,0) User who created object
MODIFIED_BY number(38,0) User who last modified object
RV01 number(38,0)
EVENT_METRIC number(38,0) Event metric
novdocx (en) 7 January 2010
DATA_TAG_ID number(38,0) Data tag ID
RV04-RV10 number(38,0)
RV11-RV20 date
RV21- RV28 varchar2(255)
INIT_IP_COUNTRY varchar2(255)
TARGET_IP_COUNTRY varchar2(255)
RV31 varchar2(255)
RV33 varchar2(255)
INIT_THREAT_LEVEL varchar2(255) Initiator threat level
INIT_USER_DOMAIN varchar2(255) The domain (namespace) in which the
initiating account exists.
RV36 varchar2(255)
INIT_FUNCTION varchar2(255) Initiator function
INIT_OPERATIONAL_CONTEXT varchar2(255) Initiator operational context
RV40 varchar2(255)
TARGET_HOST_DOMAIN varchar2(255) Target host domain
INIT_HOST_DOMAIN varchar2(255)
RV43 varchar2(255)
TARGET_THREAT_LEVEL varchar2(255) Target threat level
TARGET_USER_DOMAIN varchar2(255) Target user domain
RV46 varchar2(255)
TARGET_FUNCTION varchar2(255) Target function
94 Sentinel 6.1 Reference Guide
Page 95

Column Name Datatype Comment
TARGET_OPERATIONAL_CONEXT varchar2(255) Target operational context
RV49 varchar2(255)
TAXONOMY_ID number(38,0) Taxonomy identifier
novdocx (en) 7 January 2010
REFERENCE_ID_01REFERENCE_ID_20
CV01-CV10 number(38,0)
CV11-CV20 date
CV21- CV29 varchar2(255)
CV30- CV34 varchar2(4000)
CV35- CV100 varchar2(255)
INIT_USER_ID varchar2(255) The initiating account's source-specific
INIT_USER_IDENTITY varchar2(36) The internal UUID of the identity
TARGET_USER_ID varchar2(255) Target user ID
TARGET_USER_IDENTITY varchar2(36) Target user identity
EFFECTIVE_USER_NAME varchar2(255) Effective user name
EFFECTIVE_USER_ID varchar2(255) Effective user ID
EFFECTIVE_USER_DOMAIN varchar2(255) Effective user domain
number(38,0)
identifier as determined by the Collector
based on raw device data.
associated with the initiating account.
TARGET_TRUST_NAME varchar2(255) Target trust name
TARGET_TRUST_ID varchar2(255) Target trust ID
TARGET_TRUST_DOMAIN varchar2(255) Target trust domain
OBSERVER_IP number(38,0) Observer IP address in numeric format
REPORTER_IP number(38,0) Reporter IP address in numeric format
OBSERVER_HOST_DOMAIN varchar2(255) Observer host domain
REPORTER_HOST_DOMAIN varchar2(255) Reporter host domain
OBSERVER_ASSET_ID varchar2(255) Observer asset identifier
REPORTER_ASSET_ID varchar2(255) Reporter asset identifier
INIT_SERVICE_COMP varchar2(255) Initiator service component
TARGET_SERVICE_COMP varchar2(255) Target service component
EVENT_GROUP_ID varchar2(255)
CUSTOMER_VAR_101CUSTOMER_VAR_110
number(38,0)
Sentinel Database Views for Oracle 95
Page 96

Column Name Datatype Comment
novdocx (en) 7 January 2010
CUSTOMER_VAR_111CUSTOMER_VAR_120
CUSTOMER_VAR_121CUSTOMER_VAR_130
CUSTOMER_VAR_131CUSTOMER_VAR_140
CUSTOMER_VAR_141CUSTOMER_VAR_150
date
varchar2(36)
number(38,0)
varchar2(255)
7.1.48 EVT_AGENT_RPT_V
View references EVT_AGENT table that stores information about Collectors.
Column Name Datatype Comment
AGENT_ID number(38) Collector identifier
CUST_ID number(38)
AGENT varchar2(64) Collector name
PORT varchar2(64) Collector port
REPORT_NAME varchar2(255) Reporter name
PRODUCT_NAME varchar2(255) Product name
SENSOR_NAME varchar2(255) Sensor name
SENSOR_TYPE varchar2(5) Sensor type:
H - host-based
N - network-based
V - virus
O – other
DEVICE_CATEGORY varchar2(255) Device category
SOURCE_UUID varchar2(36) Source component Universal Unique
Identifier (UUID)
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38) User who created object
MODIFIED_BY number(38) User who last modified object
96 Sentinel 6.1 Reference Guide
Page 97

7.1.49 EVT_AGENT_RPT_V3
View references EVT_AGENT table that stores information about Collectors. The column names in
this view reflects the name change of Sensor to Observer. This view is designed for use in Sentinel
6.1.
Column Name Datatype Comment
AGENT_ID number(38,0) Collector identifier
CUST_ID number(38,0) Customer identifier
AGENT varchar2(64) Collector
PORT varchar2(64) Port
REPORTER_HOST_NAME varchar2(255) Reporter host name
PRODUCT_NAME varchar2(255)
OBSERVER_HOST_NAME varchar2(255)
SENSOR_TYPE varchar2(5) Sensor type:
novdocx (en) 7 January 2010
H - host-based
N - network-based
V - virus
O - other
DEVICE_CATEGORY varchar2(255) Device category
SOURCE_UUID varchar2(36) Source component Universal Unique
Identifier (UUID)
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38,0) User who created object
MODIFIED_BY number(38,0) User who last modified object
7.1.50 EVT_ASSET_RPT_V
View references EVT_ASSET table that stores asset information.
Column Name Datatype Comment
EVENT_ASSET_ID number(38) Event asset identifier
CUST_ID number(38) Customer identifier
ASSET_NAME varchar2(255) Asset name
PHYSICAL_ASSET_NAME varchar2(255) Physical asset name
REFERENCE_ASSET_ID varchar2(100) Reference asset identifier, links to source
asset management system.
Sentinel Database Views for Oracle 97
Page 98

Column Name Datatype Comment
MAC_ADDRESS varchar2(100) MAC address
RACK_NUMBER varchar2(50) Rack number
ROOM_NAME varchar2(100) Room name
BUILDING_NAME varchar2(255) Building name
CITY varchar2(100) City
STATE varchar2(100) State
COUNTRY varchar2(100) Country
ZIP_CODE varchar2(50) Zip code
ASSET_CATEGORY_NAME varchar2(100) Asset category name
NETWORK_IDENTITY_NAME varchar2(255) Asset network identity name
ENVIRONMENT_IDENTITY_NAME varchar2(255) Environment name
novdocx (en) 7 January 2010
ASSET_VALUE_NAME varchar2(50) Asset value name
CRITICALITY_NAME varchar2(50) Asset criticality name
SENSITIVITY_NAME varchar2(50) Asset sensitivity name
CONTACT_NAME_1 varchar2(255) Name of contact person/organization 1
CONTACT_NAME_2 varchar2(255) Name of contact person/organization 2
ORGANIZATION_NAME_1 varchar2(100) Asset owner organization level 1
ORGANIZATION_NAME_2 varchar2(100) Asset owner organization level 2
ORGANIZATION_NAME_3 varchar2(100) Asset owner organization level 3
ORGANIZATION_NAME_4 varchar2(100) Asset owner organization level 4
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38) User who created object
MODIFIED_BY number(38) User who last modified object
7.1.51 EVT_ASSET_RPT_V3
View references EVT_ASSET table that stores asset information. This view is designed for Sentinel
6.1.
Column Name Datatype Comment
ASSET_CRITICALITY varchar2(50)
ASSET_CLASS varchar2(100)
ASSET_FUNCTION varchar2(255)
98 Sentinel 6.1 Reference Guide
Page 99

Column Name Datatype Comment
ASSET_DEPARTMENT varchar2(100) Asset department
DATE_CREATED Date Date the entry was created
DATE_MODIFIED Date Date the entry was modified
CREATED_BY number(38,0) User who created object
MODIFIED_BY number(38,0) User who last modified object
7.1.52 EVT_DEST_EVT_NAME_SMRY_1_RPT_V
View summarizes event count by destination, taxonomy, event name, severity and event time.
Column Name Datatype Comment
DESTINATION_IP number(38) Destination IP address
DESTINATION_EVENT_ASSET_ID number(38) Event asset identifier
novdocx (en) 7 January 2010
TAXONOMY_ID number(38) Taxonomy identifier
EVENT_NAME_ID number(38) Event name identifier
SEVERITY number(38) Event severity
CUST_ID number(38) Customer identifier
EVENT_TIME date Event time
EVENT_COUNT number(38) Event count
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38) User who created object
MODIFIED_BY number(38) User who last modified object
DESTINATION_HOST_NAME varchar2(255)
7.1.53 EVT_DEST_SMRY_1_RPT_V
View contains event destination summary information.
Column Name Datatype Comment
DESTINATION_IP number(38) Destination IP address
DESTINATION_EVENT_ASSET_ID number(38) Event asset identifier
DESTINATION_PORT varchar2(32) Destination port
DESTINATION_USER_ID number(38) Destination user identifier
TAXONOMY_ID number(38) Taxonomy identifier
Sentinel Database Views for Oracle 99
Page 100

Column Name Datatype Comment
EVENT_NAME_ID number(38) Event name identifier
RESOURCE_ID number(38) Resource identifier
AGENT_ID number(38) Collector identifier
PROTOCOL_ID number(38) Protocol identifier
SEVERITY number(38) Event severity
CUST_ID number(38) Customer identifier
EVENT_TIME date Event time
EVENT_COUNT number(38) Event count
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38) User who created object
novdocx (en) 7 January 2010
MODIFIED_BY number(38) User who last modified object
DESTINATION_HOST_NAME varchar2(255)
7.1.54 EVT_DEST_TXNMY_SMRY_1_RPT_V
View summarizes event count by destination, taxonomy, severity and event time.
Column Name Datatype Comment
DESTINATION_IP number(38) Destination IP address
DESTINATION_EVENT_ASSET_ID number(38) Event asset identifier
TAXONOMY_ID number(38) Taxonomy identifier
SEVERITY number(38) Event severity
CUST_ID number(38) Customer identifier
EVENT_TIME date Event time
EVENT_COUNT number(38) Event count
DATE_CREATED date Date the entry was created
DATE_MODIFIED date Date the entry was modified
CREATED_BY number(38) User who created object
MODIFIED_BY number(38) User who last modified object
DESTINATION_HOST_NAME varchar2(255)
7.1.55 EVT_NAME_RPT_V
View references EVT_NAME table that stores event name information.
100 Sentinel 6.1 Reference Guide
 Loading...
Loading...