Page 1
Novell
File System Factory
1.2.1
August 30, 2005
www.novell.com
ADMINISTRATION GUIDE
Page 2

Legal Notices
Condrey Consulting Corporation makes no representations or warranties with respect to the contents of this documentation, and specifically disclaims
any express or implied warranties of merchantability or fitness for any particular purpose. Further, Condrey Consulting Corporation reserves the right
to revise this publication and to make changes to its content, at any time, without obligation to notify any person or entity of such revisions or changes.
Also, Condrey Consulting Corporation makes no representations or warranties with respect to any software, and specifically disclaims any express or
implied warranties of merchantability or fitness for any particular purpose. Further, Condrey Consulting Corporation reserves the right to make
changes to any Condrey Consulting Corporation software product described herein, at any time, without obligation to notify any person or entity of
such revisions or changes.
You may not export or re-export this product in violation of any applicable laws or regulations including, without limitation, U.S. export regulations
or the laws of the country in which you reside.
Copyright © 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
Document Version: 60105
Novell, Inc.
404 Wyman Street, Suite 500
Waltham, MA 02451
U.S.A.
www.novell.com
File System Factory 1.2.1 Administration Guide
August 30, 2005
Online Documentation: To access the online documentation for this and other Novell products, and to get updates, see
www.novell.com/documentation.
Page 3

Novell Trademarks
File System Factory is a trademark of Condrey Consulting Corporation.
AuditLogin is a trademark of Condrey Consulting Corporation.
IUAdmin is a trademark of Condrey Consulting Corporation.
Internet User Administrator is a trademark of Condrey Consulting Corporation.
Third-Party Materials
Novell is a registered trademark of Novell, Inc. in the United States and other countries.
Novell Cluster Services is a trademark of Novell, Inc.
Novell Directory Services is a trademark of Novell, Inc.
Client32 is a trademark of Novell, Inc.
ConsoleOne is a trademark of Novell, Inc.
DirXML is a trademark of Novell, Inc.
eDirectory is a trademark of Novell, Inc.
IPX is a trademark of Novell, Inc.
NetWare is a registered trademark of Novell, Inc. in the United States and other countries.
NCP is a trademark of Novell, Inc.
NLM is a trademark of Novell, Inc.
Nsure is a trademark of Novell, Inc.
eGuide is a trademark of Novell, Inc.
Windows is a trademark of Microsoft Corporation.
All other third-party trademarks are property of their respective owners.
Page 4

Contents
Novell...................................................................................................................................1
File System Factory™........................................................................................................1
Contents..............................................................................................................................4
1 Welcome...........................................................................................................................6
.............................................................................................................................................6
2 Product Mission and Key Benefits .................................................................................7
3 Overview...........................................................................................................................9
4 Components and Transaction Flow..............................................................................10
5 Product Requirements...................................................................................................11
6 New Features in Version 1.2.1......................................................................................12
New Features in Version 1.2............................................................................................13
7 Global Event Subsystem................................................................................................14
9 Installation and Configuration.....................................................................................18
Schema Extensions.......................................................................................................18
Proxy Rights.................................................................................................................18
Base Installation...........................................................................................................19
Creating a Policy..........................................................................................................19
Assigning a Policy to a Container...............................................................................20
Installation and Configuration Verification..............................................................20
Applying a Policy to Existing Users...........................................................................21
10 Management Interface................................................................................................22
Accessing the Management Interface.........................................................................22
Using the Management Interface................................................................................24
11 Policy Definitions and Application.............................................................................41
12 Backfill Operations......................................................................................................47
........................................................................................................................................51
13 Quota Manager............................................................................................................52
Enabling and Configuring Quota Management for a Policy...................................53
Setting up Rights to Use Quota Manager..................................................................53
Using the Quota Manager Interface...........................................................................54
Configuring the Executive Dashboard.......................................................................57
Executive Dashboard Security Principle Object.......................................................58
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
3
Page 5

Using the Executive Dashboard Interface.................................................................59
Configuring Workflow................................................................................................63
Setting up the Workflow Management Structure.....................................................64
Using the Workflow Interface....................................................................................64
16 Template Processing....................................................................................................66
Examples.......................................................................................................................70
Template Summary......................................................................................................73
17 Mass User Testing.......................................................................................................74
18 Universal Resource Access..........................................................................................75
19 Home Directory Deployment Scenarios......................................................................77
20 Collaborative Storage Management...........................................................................79
Collaborative Storage in Business .............................................................................79
Collaborative Storage in Education ..........................................................................80
21 Data Migration............................................................................................................82
22 Release Notes...............................................................................................................85
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
4
Page 6
1 Welcome
Welcome to the Novell File System Factory ™ 1.2 Administrator’s Guide. This
Administrator’s Guide is intended to introduce you to File System Factory™ and guide
you through the installation, configuration, and usage of the product.
During the spring of 2003 Novell introduced Novell File System Factory, a product that
revolutionizes use of the Novell File System. Novell is building on that success with the
release of Novell File System Factory 1.2 and now with version 1.2.1. File System
Factory allows for easy provisioning, management, and cleanup of user home directories
and group storage, while providing disk storage to all network users and collaborative
storage to working groups.
Designed for the real world from the inside out, Novell File System Factory is built on
procedures proven in real world environments. In the real world target servers die,
volumes dismount, routers are rebooted and backhoes dig up communication links. The
action engine in File System Factory is built on transactional state machine architecture to
ensure that policies are applied when events happen no matter what.
Novell File System Factory is a complete home directory life cycle solution for user as
well as group storage. With File System Factory, and its automated power and ease of
configuration, the perplexity of file system management is gone. Users will love true
instant access to the information they need. Administrators will love Zero Day cleanup.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
5
Page 7

2 Product Mission and Key Benefits
Novell’s File System Factory is a revolutionary policy driven file-system management
solution that unites Novell’s industry leading directory service eDirectory with the
legendary NetWare file system. The connection of eDirectory identities with directory
based storage management polices for creating personal and collaborative storage
delivers the industry’s only identity based storage management solution.
Product Mission
The mission of File System Factory™ is to unite an organization’s user identities with
their storage system to deliver a full lifecycle identity based storage management solution
that completely automates the load balanced creation, management, and deletion of
personal and collaborative disk space.
The major objective of Novell File System Factory is to create a storage management
subsystem to back these Administrator instructions:
1. Install some disk storage.
2. Point your new or existing tree at the new storage.
3. Sit back and relax.
Identity Based Storage Management Solution
Novell File System Factory is a key component of Novell’s Secure Identity Management
solution set. File System Factory provides new and dynamic levels of automation and
management for NetWare file services, which to this point have not been possible. File
System Factory enables policy-based lifecycle provisioning and de-provisioning of
personal and group storage. As a result, your business can simplify access and
management of storage, based on users' identities. Regardless of how you create, move or
delete user and group accounts in the directory, Novell File System Factory responds to
these events by automatically creating, moving or deleting disk storage on NetWare. With
File System Factory, your business can effortlessly keep pace with the storage demands of
a busy, large-scale organization and reduce support costs.
Providing personal and collaborative storage on a network can be a very valuable.
However, providing and managing storage for each user and group on your network can
become a major headache for your overburdened IT department. Fortunately, with File
System Factory™, you can provide the storage users expect (and genuinely need) while
significantly reducing the headache—and cost—of creating and managing that storage.
Storage Solution for all Environments
File System Factory™ unites the NetWare® file system that is an integral part of many
real-world eDirectory implementations with the eDirectory automation that these identity
provisioning solutions provide. File System Factory™ is designed to provide an
immediate benefit in managing network storage for any enterprise, no matter what the
current situation:
• New Tree – No User Home Directories
o If you are just starting out, File System Factory™ can give your new
users managed home directory space with little effort on your part.
• Existing Tree – No User Home Directories
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
6
Page 8

o If you already have user accounts in your tree, but have not taken the
steps to give them home directories, File System Factory™ can
automatically give your existing users managed home directory space.
• Existing Tree – Existing User Home Directories
o If you already have user accounts in your tree and they have home
directories, File System Factory™ can begin managing your existing
home directories as well as provision and manage any new ones.
Key Novell File System Factory Benefits:
• Full lifecycle, policy-driven file system management to create, manage, delete
home directories for both personal and collaborative storage.
• Unites newer identity provision solutions with the NetWare file system,
delivering identity based storage management.
• Automatic NetWare® storage with access methods to all namespaces, including
Windows, Mac, UNIX, and the Web.
• Group collaborative storage provisioning through policies.
• Automatic assignment of Disk Space Restrictions.
• Load balancing, Multi-Server Distribution & Space Balancing.
• NetWare storage control based on policies managed by eDirectory.
• Powerful automated Data Migration, including moving from traditional NetWare
file servers to Novell Storage Services™ & Cluster Services
• Automated Cleanup (everybody’s pain point) based on policy.
• Designed, built and tested to solve “real world” issues in delivering personal and
collaborative storage.
Enable Migration to New Provisioning Processes
Novell File System Factory is an invaluable resource to assist organizations in moving to
a new or adding an additional provisioning process. By using File System Factory to
make storage creation and management a separate but linked component of the user
provisioning process, organizations are now free to adopt and migrate to the new
provisioning technologies of Novell. Therefore, with File System Factory you can add file
system connectivity to your current and future provisioning solution whether it is based
on Novell Nsure Identity Manager (DirXML), LDAP applications, UIMPORT, LDIF,
ICE, custom code or another vendor’s product.
Policy Based Data Migration
Migrating home directories and group storage is a cumbersome and time consuming
process for administrators, but now Novell File System Factory is making migrating data
easy and painless for both administrators and end-users. Using Novell File System
factory can make moving to a Netware cluster as easy as changing an attribute in
eDirectory. With NetWare now supporting Clusters and SANs, many organizations want
to migrate. Data migration through dynamic policy application is one of the most
powerful features of File System Factory. If a user moves or the policy covering the user
changes, the new policy applies. If the new policy points to a different set of storage, say
another server, the user’s home directory and data will automatically moved to the new
server in a way that the user is not impacted by the move. Attributes of the policy dictate
the schedule and bandwidth used for data migrations.
In addition, File System Factory™ contains safeguards to ensure "seamless" migration of
the data by taking the necessary precautions to avoid troublesome situations and educate
the user about the migration process.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
7
Page 9

3 Overview
File System Factory™ is an event-driven file system management solution for eDirectory
and NetWare. Ultimately, it creates, manages, and deletes disk storage based on events in
the Directory. It is designed to provide these services for user home directories (personal
storage) as well as shared disk space (group storage).
These actions are performed based on File System Factory™ management Policies that
are defined and associated with containers in the tree. Policy definitions allow separate
management methods for storage for users and groups in the same part of the tree. A
single Policy may be assigned to multiple objects in the tree for unified management. A
policy may be assigned to a container, a group, or directly to an individual user object.
Standard inheritance determines which policy, if any, is applied for a given object.
File System Factory™ contains selectable algorithms for load-balancing storage across
multiple servers and volumes. These may be traditional NetWare volumes, volumes based
on Novell Storage Services (NSS), or volumes backed by Novell Cluster Services.
When an event occurs in the tree, the event-monitoring component of File System
Factory™ immediately intercepts the event. Because File System Factory™ contains a
Global Event Subsystem; multiple instances of the event monitor can be run
simultaneously on multiple servers without concern for replica location collisions and
duplicate event processing.
The intercepted Directory events are sent to a server running the File System Factory™
action engine component. If the engine determines that a Policy has been associated
directly or indirectly with the object being created, modified, or deleted; the engine then
applies the Policy.
Policies contain provisions for having File System Factory™ not only create the file
systems, but also apply quotas, set trustee assignments, and copy a given template
directory containing files and subdirectories with trustees. Directory cleanup can be
managed such that file system deletions may occur immediately after object deletion or be
deferred for a specified amount of time.
File System templates may be applied to users or groups or both users and groups. File
System Factory™ can copy in a specified template directory from anywhere on the
network for each user or group home directory created. Files and directories may be
copied as well as trustee assignments and attributes.
The engine contains an internal transactional state machine architecture that allows the
engine to deal with transient waits with eDirectory synchronization issues. The state
machine architecture also allows 100% recovery from any failure involving network
communications, a target server or a server running a component of File System
Factory™ (including the engine itself).
File System Factory™ will work with any version of NDS or eDirectory. Components
will run on any 5.x or 6.x NetWare server. File systems can be created and managed on
any supported version of NetWare that works with NDS or eDirectory (4.x, 5.x, 6.x).
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
8
Page 10
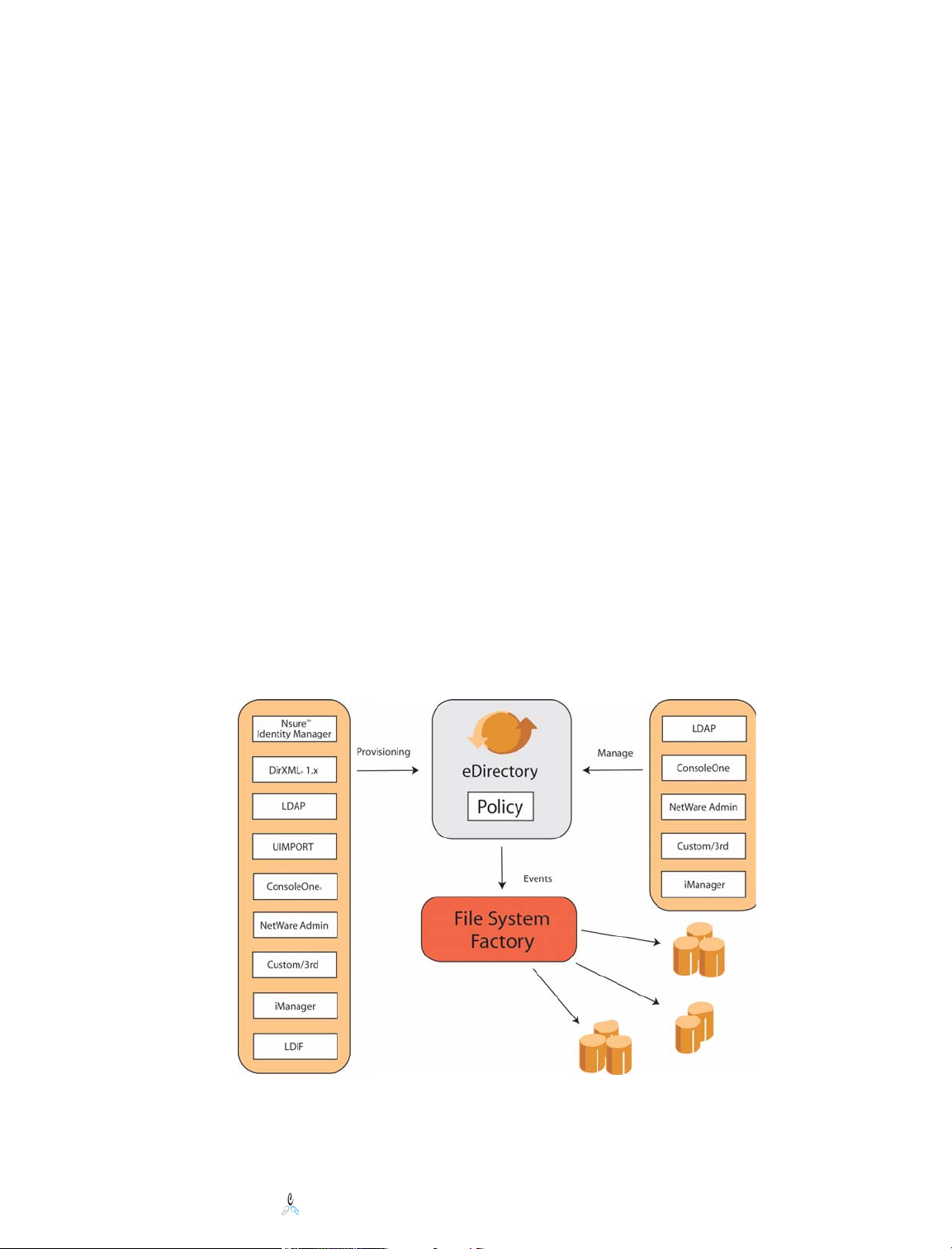
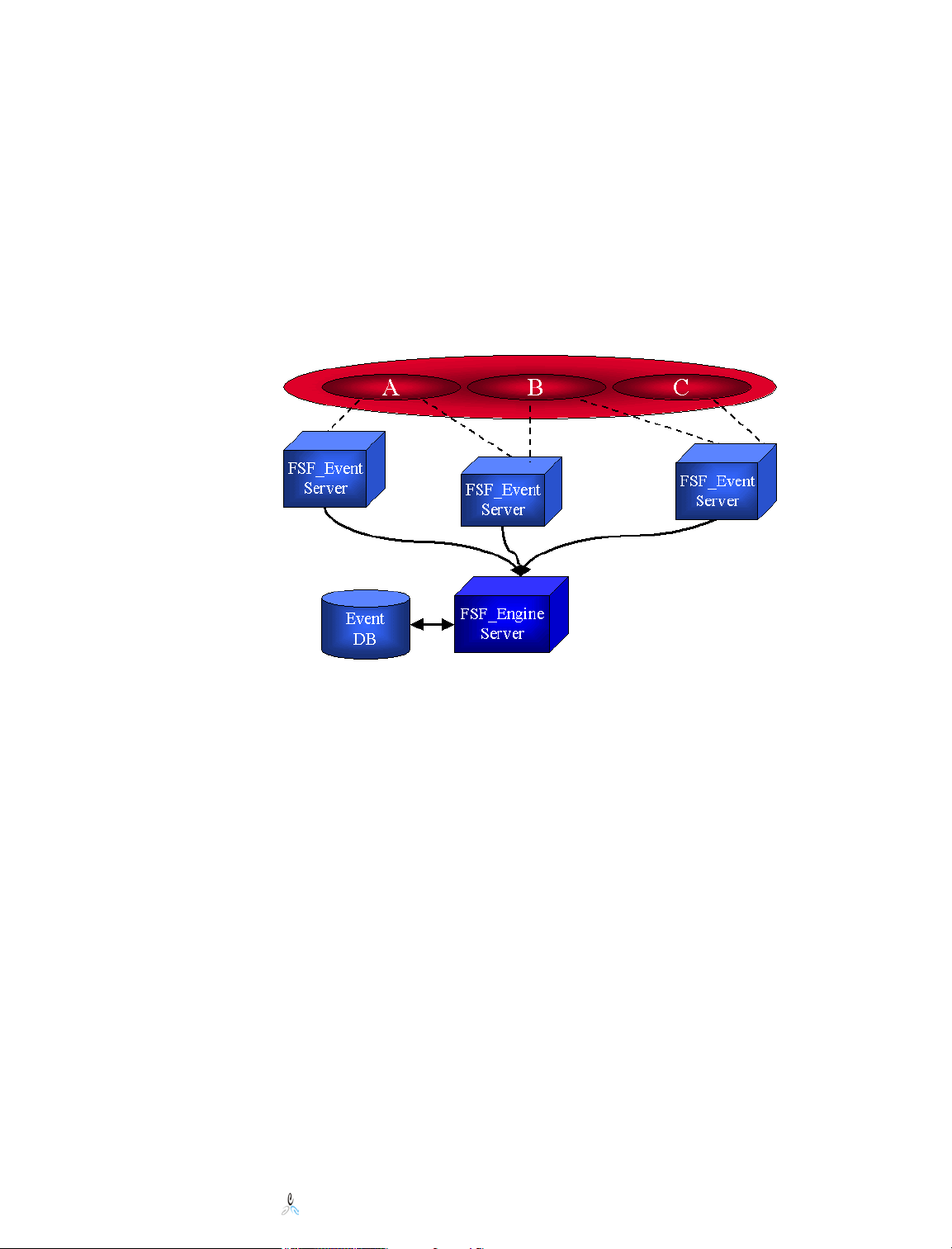
4 Components and Transaction Flow
The following diagram illustrates the command and controls as well as data flow within a
File System Factory™ system.
Generally, this is how File System Factory™ is put into action:
1. An Administrator uses a browser to create a File System Factory™ Policy. Here,
the Policy is directed to one or more target data paths on NetWare volumes. A
load-balancing algorithm is specified as well as a default trustee assignment and
optionally an initial quota and copy template path.
2. Then the Policy is assigned or associated with one or more objects in the tree,
such as a container.
3. The event monitoring NLM intercepts events for the container associated with
the Policy and sends the events in to the Engine NLM.
4. The Engine NLM contains a process queue and event database on the local
system. It applies the Policy to the event and acts on the target file system
pointed to by the Policy.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
9
Page 11
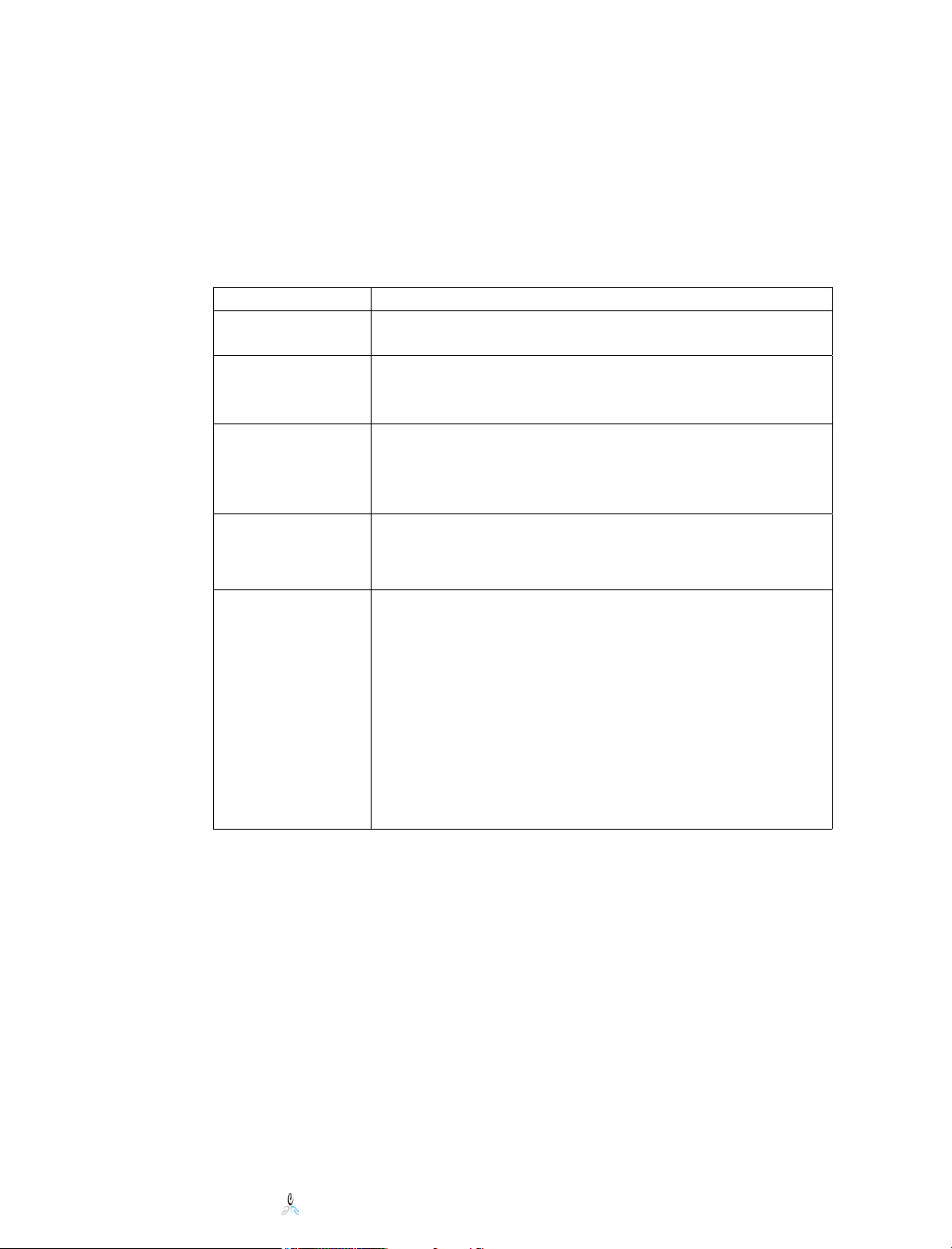
5 Product Requirements
The following table defines all requirements to run File System Factory™.
Component Requirement
NDS/eDirectory Any Novell supported version of NDS or eDirectory
(6.xx, 7.xx, 8.xx, 85.xx, 8.6.x. and 8.7.x)
Replica
Placement
Event
Monitoring
NLM
FSF_EVENT
Action Engine
NLM
FSF_ENGINE
Target Home
Directory Server
for Users or
Groups
There are no replica location requirements. Because
File System Factory™ contains a Global Event
Subsystem, replicas can be held on any server.
Supported on the following platforms:
• NetWare 5.1 SP6 or later
• NetWare 6.0 SP4 or later
Supported on the following platforms:
• NetWare 6.0 SP4 or later
• NetWare 6.5 SP1 or later
File System Factory™ performs server-to-server
communication from the server running the Action
Engine NLM to manage user and group file systems on
target servers. These target servers can be at any of
these levels of NetWare:
• NetWare 4.x SP9 or later
• NetWare 5.0 SP6a or later
• NetWare 5.1 SP6 or later
• NetWare 6.0 SP4 or later
• NetWare 6.5 SP1 or later
4.x
4.x
5.0
5.0
5.1
5.1
6.0
6.0
5.1
5.1
6.0
6.0
6.5
6.5
6.0
6.0
6.5
6.5
6.5
6.5
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
10
Page 12

6 New Features in Version 1.2.1
Novell File System Factory™ 1.2.1 resolves several known issues and enhances
the existing feature set.
Resolved issues include
• Functionality added to prevent events from queuing, and not clearing
• Case matching issue which caused unnecessary moves
• Unusual characters in object names including underscores in server and volume names not
working in the admin Dashboard, “&”, “.” and other unusual characters in common names.
• Domain objects now displayed in selection interface
• New return code added to correctly process –member- and –owner- events
New features and enhancement include
Changes and additions to backfill operations (see chapter 12 for details)
• Separation between user home directory management and group storage management
• Group storage management backfill operations added
• New operation to assign the home directory attribute when directories exist but eDirectory
attribute is not set
• New operation to copy or update a user directory structure (template)
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
11
Page 13

• New operation to set rights on home directories
New consistency check operations added to provide a diagnostic look at
whether users and group are correctly cataloged for management through File
System Factory. This is available through the Management FSF Policies
interface (browsing objects) or from the backfill options pages.
New configuration option which provides the ability to set up a security user
to restrict access to the management interface
Rename functionality added for changes to user names with member
directories in group storage
Operation to perform abort of multiple pending events. This is a restricted
access operation, which will require contact with support to use. To gain access,
send an email request to fsfdev@novell.com
.
New Features in Version 1.2
Novell File System Factory™ 1.2 has been updated to the Novell common web
interface skin. It also has many new features to further enhance the experience
of identity based file system provisioning. This section identifies and gives
reference to sections in this guide which provide detail on the use and access of
the new features.
Status indicator for user storage available; see section 10, Management Interface.
Priority Event status for create user events; see section 7, Global Event
Subsystem.
New Executive and Administrator Dashboards for easily accessible statistics,
status and reports; see section 10, Management Interface for Admin Dashboard,
and chapter 14, Executive Dashboard.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
12
Page 14

Auditing Access quickly calculates and displays the rights to any file or
directory, and how those rights were assigned; see section 10, Management
Interface.
File Browse capability; see section 10, Management Interface.
Ability to assign a deleted user’s files to a manager and manage using workflow,
based on Novell eGuide; see section 15, Workflow.
New backfill options including group and template backfill; see section 12,
Backfill Operations.
Increased accessibility for group template processing, including sample
templates; see section 16, Template Processing.
Quota Manager is a role based service feature allowing a help-desk user or
support personnel to quickly and easily manage and raise user disk space quota
based on policy, without having to give them rights to the file system; see section
13, Quota Manager.
7 Global Event Subsystem
Description
File System Factory™ contains an event services component (FSFEVENT.NLM) that
intercepts relevant User and Group events in the Directory and sends them to the action
engine component (FSFENGIN.NLM) for processing.
The event subsystem is built on top of the AuditLogin™ event and transactional
consolidation engine which has years of proven reliability and performance. The event
consolidation engine provides the ability to receive events from multiple sources
simultaneously and make sense of them.
The event services component of the system contains a caching subsystem so that events
will be cached locally if they cannot immediately be sent into the consolidation
component. This system assures that all events eventually make it to the consolidation
component in the correct order.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
13
Page 15
Therefore, you may run the event auditing NLM (FSFEVENT.NLM) on multiple servers
simultaneously and have them all send their events into a single server running the action
engine NLM (FSFENGIN.NLM) and be assured that the events will be delivered.
The problem of auditing Directory events on multiple servers simultaneously usually
arises when multiple audited servers hold a replica of the same partition. The result is that
the same event will be intercepted by each of the instances of the event monitor that is on
a server auditing the same replica ring and be sent in to the consolidator engine multiple
times. The problem is exacerbated by delays in Directory synchronization and network
outages.
The File System Factory™ engine global event system component contains proprietary
analysis methodologies along with an event database on the local system that ensures that
any event is only acted on only once.
Why Global Events?
An alternative to implementing a Global Event System is to require the event-monitoring
component to run on a server that holds a replica of every partition that contains relevant
objects.
NDS/eDirectory is a scalable, replicated database that allows administrators to define
partitions and replicate the database in ways that make sense for the given network
topology and hardware that is in place. This flexibility is one of the attributes of NDS and
eDirectory that makes it a winner. The introduction of a software product requiring at
least one server to hold a replica of all partitions removes some of this flexibility and is
often a challenge in customer environments where the tree and network is not designed to
facilitate this.
You may already have a network that can support a single replica server requirement. If
so, you have the option of only running one instance of FSFEVENT.NLM. However, you
may find that running multiple instances results in faster actions on events and the
insurance policy that says you will not miss any events even if a server fails or a replica
becomes corrupted.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
14
Page 16

Monitored Events
For improved performance, the event monitor in File System Factory™ streamlines the
process by only monitoring for and sending events to the Engine that might be relevant to
a Policy or template. Currently, the following events are monitored:
• User
o Add Object
o Delete Object
o Rename Object
o Move Object
o File System Factory™ Policy Assignment
o Modify Manager attribute from Novell eGuide
• Group
o Add Object
o Delete Object
o Rename Object
o Member Attribute
Add Member
Delete Member
o Owner Attribute
Add Owner
Delete Owner
Priority Events
New in File System Factory 1.2, user create events received by the FSF engine will be
assigned a higher priority than other events. This will allow them to be processed first,
instead of having to wait for lower priority events, such as data migration (move) events.
High priority events will be processed first, in chronological order, and when complete,
the other events will be processed in chronological order. If there is a delay causing a
high priority event to be unable to complete, it will be assigned a non-priority status, and
processed with the regular queue rotation.
.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
15
Page 17

8 Transactions and the Engine State Machine
“Neither rain, nor snow, nor sleet, nor gloom of delayed DS synchronization shall stay
this system from the swift completion of its appointed tasks…”
Because NDS/eDirectory is a replicated, loosely consistent database, taking live action on
NDS events in real-world network situation is challenging. For example, the engine may
be notified of the creation of a new user, but the replica that the engine NLM is using for
referrals may not know about the user yet. Or maybe he does and the engine can go ahead
and use server-to-server communications to create the home directory on a target server,
but the application of the quota or the ACL fails because the replica being used by the
target server does not know about the user yet.
There are other potential problems in the real world. Target servers die, volumes
dismount, routers are rebooted, and backhoes dig up communication links.
Because of this real world that most customers live in, the action engine in File System
Factory™ is built on transactional state machine architecture to ensure that Policies are
applied when events happen, no matter what.
Each transaction consists of a series of steps or states. The engine contains a Process
Queue that is backed by the file system of the local server. Each transaction on the
Process Queue contains the state or progress of the given transaction. If there is some
situation that is holding up completion of a particular transaction, the engine will move on
to the next transaction in the list. When it comes back around to the transaction that was
experiencing the delay and processing will continue. The process queue is rebuilt from
the file system each time the engine is restarted.
In the end, File System Factory™ is built so that you can trigger several thousand
transactions and then disconnect the net connection or even push the reset button on any
server running any File System Factory™ component or any target server without cause
for concern.
Note: In the event of large numbers of events queuing, which for some reason cannot
clear through regular engine processing, there is a new multiple event abort feature
available for restricted use by contacting support at fsfdev@novell.com.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
16
Page 18
9 Installation and Configuration
The following sections present step-by-step instructions on the initial installation of File
System Factory™. It also includes instructions for defining a new Policy and associating
it with a container in the tree. There are sections on verifying the installation and load
testing the product in your environment as well.
Schema Extensions
File System Factory™ requires that the schema be extended. The schema extensions
include several attributes that make up the new class cccFSFactoryPolicy. There is one
new attribute that added to the optional attributes list of the Organization, Organizational
Unit, and User classes. For Quota Manager there is one attribute called
cccFSFactoryHomeDirectoryQuota added to Organizational Person class.
The schema is extended during the installation or upgrade process.
Proxy Rights
The File System Factory™ engine (FSFENGIN.NLM) needs the appropriate rights to
manage the file systems of target volumes as well as manipulate certain attributes of
objects in the tree. The engine authenticates to the tree as the NDS server object of the
server it is running on.
Before you start this section, you should take a look at the rights your server already has
in the tree. Novell gives some server objects Supervisor rights to the root of the tree by
default. If your server already has these rights, you may skip the remainder of this section.
There are two approaches to choose from here:
1. As a matter of practicality, you should give the server object Supervisor rights to
any containers that might (now or in the future) hold users, servers, or File
System Factory™ Policy objects.
2. OR, if you want to micro-manage the rights the server object has, the server
object needs to be given the following rights:
Type Right Class Attribute Target
NDS Read /
Write
(Property)
NDS Read /
Write
(Property)
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
Organization,
Organizational
Unit
Organization,
Organizational
Unit
Home Directory Containers associated with
a File System Factory™
Policy that may contain
User objects. All user
objects below the ACL
assignment will inherit this
right.
ccFSFactory*** Containers that may hold
File System Factory™
Policies. This will allow
the Engine server to
manage all Policies created
in containers below the
ACL assignment.
17
Page 19
NDS Create
(Object)
File
Sys
Supervisor N/A File Systems pointed to by
Organization,
Organizational
Unit
The Engine Server must
have the right to create
cccFSFactoryPolicy
objects anywhere in the
tree that an administrator
might wish.
File System Factory™
Policies.
Base Installation
Before you begin, you will need the following items:
1. The File System Factory™ is distribution package. This is a single EXE that
may be downloaded from the web site.
2. A license file, LICENSE.DAT, is also required for the specific tree into which
you intend to install.
Running the distribution package executable will guide you through the entire installation
and initial configuration of the product. The first step of the installation allows the option
to view Installation Best Practices. It also has a Check for updates option which is
strongly recommended.
.
If you have completed this step, you are now running File System Factory™.
Creating a Policy
Note: There is a computer-based video that describes the policy creation and assignment
process in the \factory\videos subdirectory on the Engine server.
The following details the creation and association of a File System Factory™ Policy:
1. Attach to the NetWare Remote Manager on the server running the Engine using a
browser. If you are unsure of how to do this, see section 12 of this document, which
describes the management interface and how to attach to it.
2. At the bottom of the page you will see an entry for File System Factory™. Click on
the “Manage” menu link
3. Click on Policy Administration menu link.
4. Select a container into which you have Create rights to hold a Policy object. After
being created, a given Policy may be applied to any container, so the location of the
object in the tree is not very important.
5. Type in the name for a new Policy and click the “Create Policy” button. This will
create the new Policy.
6. When the new Policy is displayed on the screen, click the Policy name. This will
result in the display of the Policy configuration menu. You may define policy
management attributes for users or groups here. We will configure for users.
7. Click on the “User Paths” menu link.
8. Enter the volume and path information for one or more targets. This identifies where
the user home directories will be stored. The paths that you enter here must exist.
9. Click on the “User Properties” menu link.
10. Select or enter the given criteria:
o Algorithm: Select the distribution algorithm that you would like to use.
o Quota: Enter the number of megabytes that you would like to be applied to
each home directory as a quota.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
18
Page 20

o Trustee: Select the rights that you would like for each user to have to his
home directory.
o Template: If you would like for each home directory to be primed with a set
of files and directories, enter the volume and path information that holds the
directory to be copied from. Trustee assignments will be copied as well.
11. Click “Save” to save the criteria.
12. If you would like for this policy to apply to groups, repeat steps 7-10 to specify
Policy criteria related to file systems for Groups, except click on the “Group Paths”
and “Group Properties” links as appropriate.
13. Now you must assign the Policy with one or more objects in the tree. The following
example shows show to assign a policy to a container.
Assigning a Policy to a Container
For a Policy to have any effect, you must assign it to one or more containers in the tree.
There are two methods to choose from:
A. Browse to the container and assign the given policy to the container.
B. Go to the given policy configuration page and add containers to the "Associated
Containers" list.
Since we have just been editing the Policy, we will simply add the container to the Policy
that we are already editing.
1. Click on the “Associated Containers” menu link.
2. Browse to the appropriate container and select it.
3. Click “Add Container”.
Installation and Configuration Verification
At this point, all components are installed and you have created a Policy and assigned it
to a container. The children of the container a Policy was originally associated with
inherit that Policy. File System Factory™ is monitoring the NDS for events. If an event
occurs in a container covered by a Policy, then action will be taken.
You may verify operation of File System Factory™ by adding a user to the container or
any sub-container. You can use NWAdmin or ConsoleOne to do this.
After the user is created, inspect the FSFEVENT screen to verify that the event was
received. If not, verify that the server in question holds a replica of the partition
containing the object.
Then inspect the FSFENGIN screen to verify that the event made it from FSFEVENT. If
not, verify that the name of the server running the Engine was correctly specified on the
FSFEVENT LOAD command and check the FSFEVENT screen for connectivity errors.
If there are connectivity errors, each transaction will cause FSFEVENT to attempt to
reconnect to the Engine server, therefore adding another user is one way to precipitate a
reconnection.
Then using NWAdmin or ConsoleOne, look at the “Environment” tab for the user. If the
event has processed, the home directory attribute will reflect the location of the user’s
home directory. Depending on replica location and synchronization, the update may take
a minute. As with all things DS, wait “an appropriate amount of time.”
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
19
Page 21

Verify the quota, trustee assignment, and copy file system template results as applicable.
Applying a Policy to Existing Users
If the container to which you apply a Policy already contains users, you may instruct File
System Factory™ to begin managing these users.
1. Click on Policy Management menu link.
2. Browse to the container (or any sub-container).
3. Click on the backfill icon beside the name of the container. The container
management page will be shown.
4. Select the “Backfill” option.
5. Click on the “Apply Policy” button.
The engine will then apply the appropriate policy to any users in that container or any
sub-containers. Those users that do not already have a home directory will be queued up
as events for the Engine to process.
.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
20
Page 22

10 Management Interface
File System Factory™ is very powerful, but requires little in the way of management.
The following are operations that must be performed to manage a File System Factory™
installation:
• Define Policies.
• Associate Policies with objects in the tree.
• Configure Parameters.
• Perform backfill operations.
There are also some management tools available to help administrators track and report
statistics, activity and trends in the storage managed by File System Factory™. These are
available in the Admin Dashboard. There is also an Executive Dashboard designed to
provide access to reports and statistics from a separate interface for individuals who need
easy access to the data, but who don’t need daily access to the actual management of File
System Factory™. See Chapter 14, Executive Dashboard.
Accessing the Management Interface
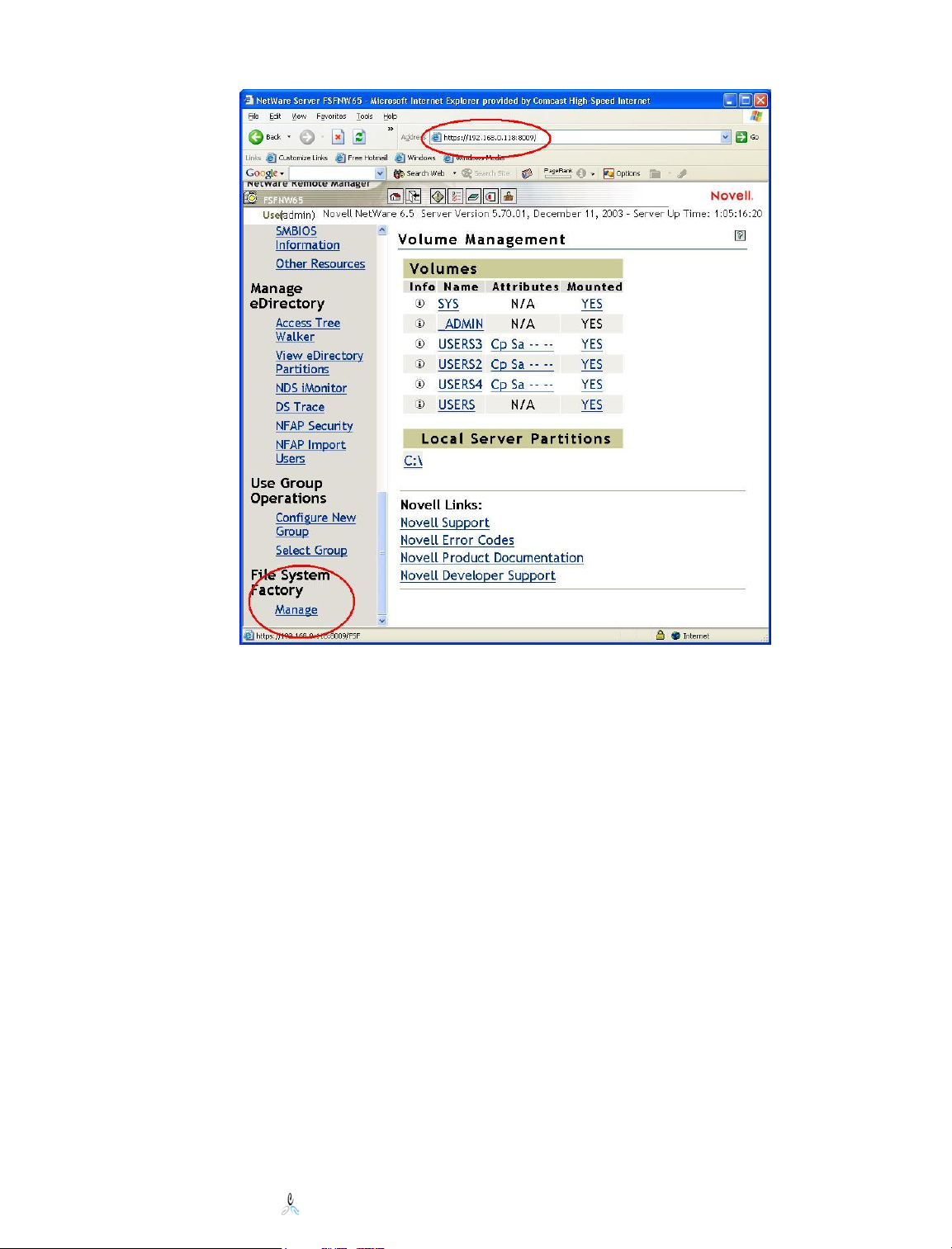
File System Factory™ is managed using a browser. The management interface is
accessible through the NetWare Remote Manager (NRM) web portal that is available on
all NetWare 5.x and 6.x servers.
PORTAL.NLM provides the NRM interface. It runs on top of HTTPSTK.NLM, which
provides the communications layer. The File System Factory™ Engine also runs on top of
HTTPSTK.NLM, and is linked from the main menu of the NRM interface.
Be aware that in some versions of the NetWare Remote Management (Portal) interface,
you must login in order to see the “Manage” link under the File System Factory™ menu
item.
Access NetWare Remote Manager by going to the default page:
(Ex: http://your.server.name.or.ip.address:8008)
Via SSL:
(Ex: https://your.server.name.or.ip.address:8009)
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
21
Page 23
Depending on whether or not another web server is running on the system, the HTTPSTK
NLM may be listening on the standard HTTP port 80 as well. By default HTTPSTK
listens on port 8008 for standard HTTP connections and on port 8009 for SSL encrypted
connections. The NetWare Remote Manager, which also runs on HTTPSTK, provides an
interface for configuring which ports HTTPSTK is listening on. You may specify the
ports on the HTTPSTK.NLM LOAD command as well. Also, you can force the
HTTPSTK to always use SSL connections, which will secure the use of the interface on a
public network.
Clicking on the “Manage” link will take you to the File System Factory™ Management
Interface. Navigate using the buttons at the top. The functions of these buttons are
described in the next section, “Using the Management Interface.”
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
22
Page 24
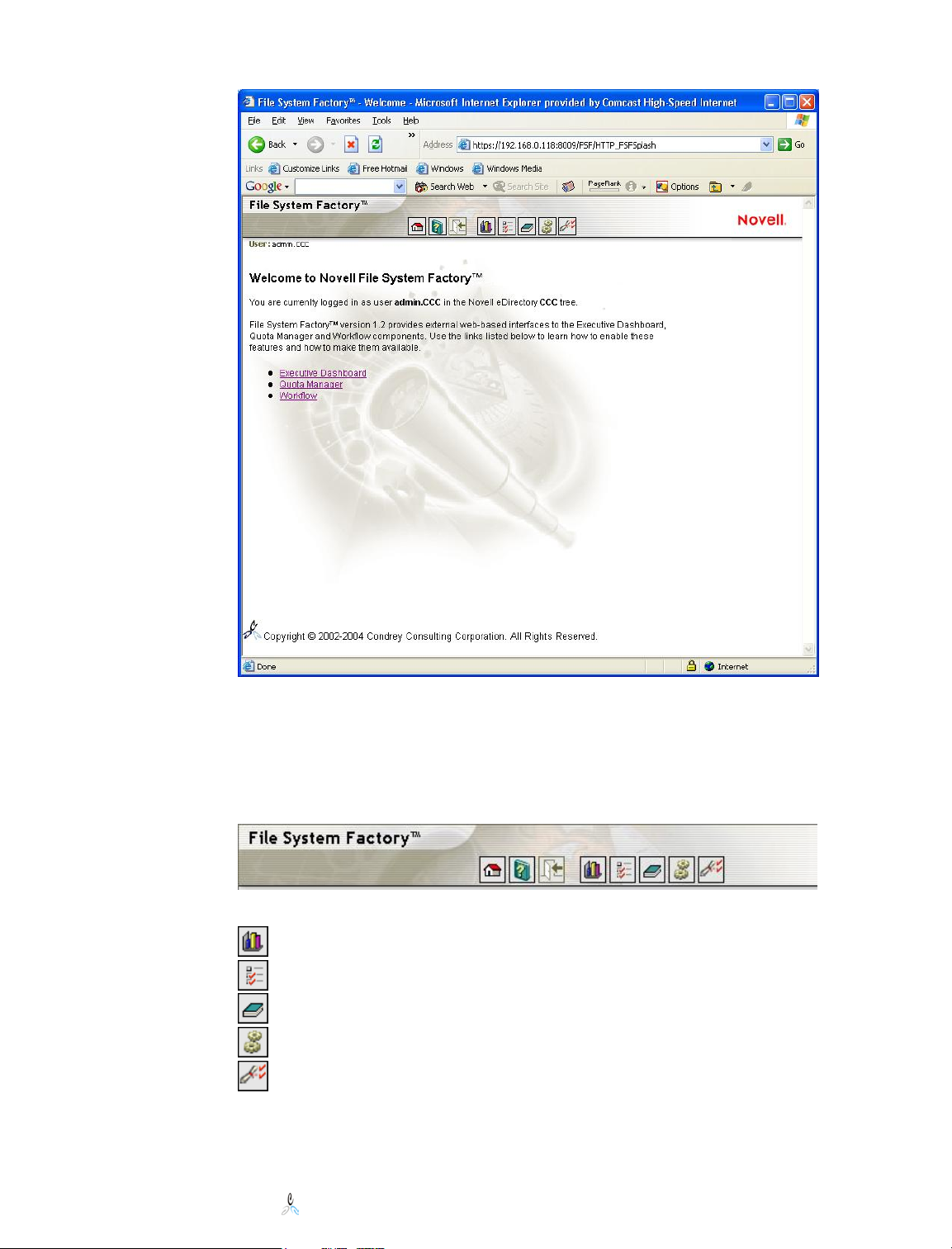
The welcome screen has links that will help in getting started in the three external
interface pieces, “Executive Dashboard,” “Quota Manger,” and “Workflow.” See
chapters 13, 14 and 15 for more details on these interfaces.
Using the Management Interface
The options available from the management interface include:
Admin Dashboard
Configure FSF Engine
Reports/Logfiles
Manage FSF Engine
Manage FSF Policies.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
23
Page 25
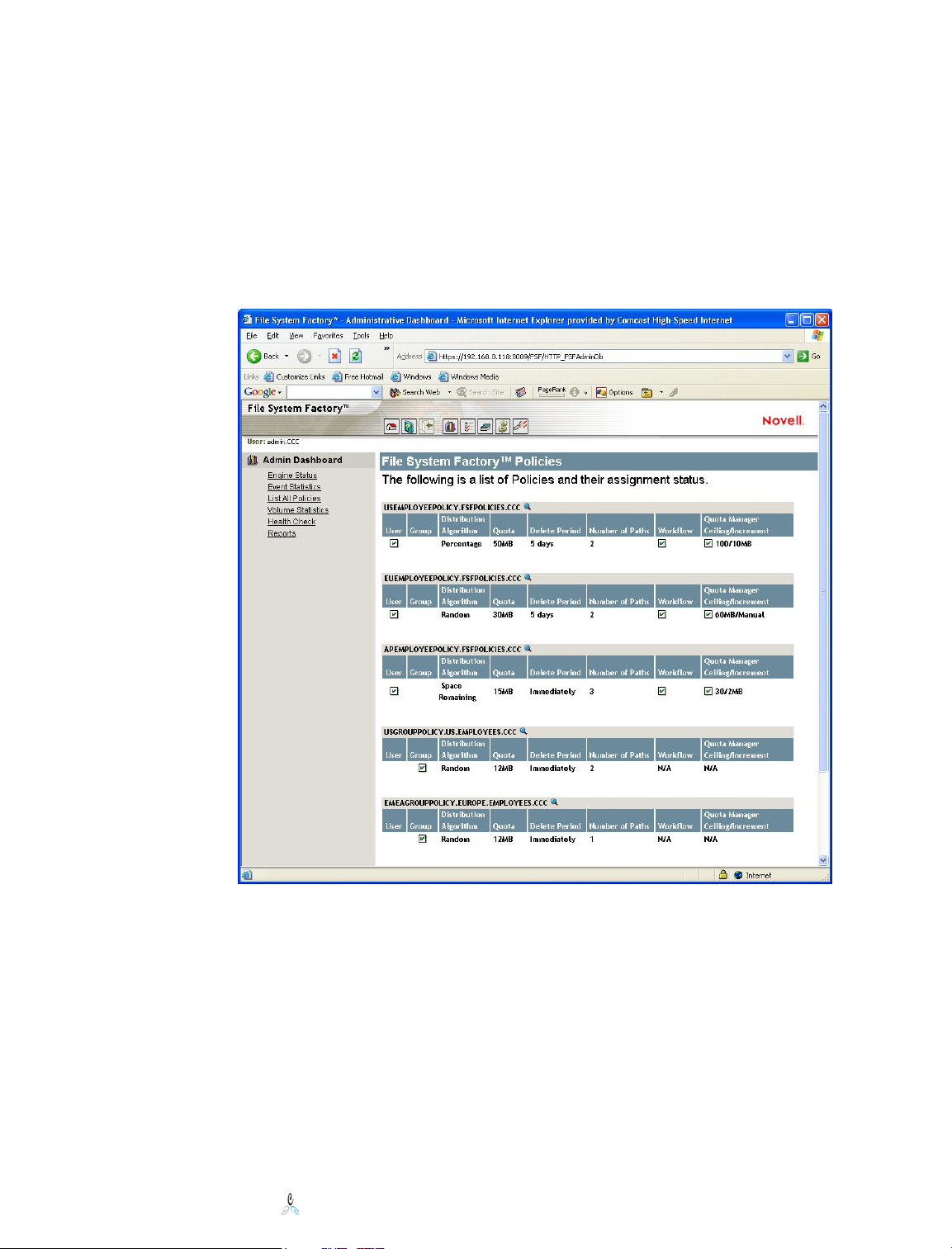
Admin Dashboard
Admin Dashboard is a feature new to version 1.2. The purpose of this option is to have a
quick access point to reports, statistics and data managed by File System Factory™. The
options are available on a left menu, with the option “List All Policies” the default
starting point. The other options include “Engine Status,” “Event Statistics,” “Volume
Statistics,” “Health Check” and “Reports.”
List All Policies
The “List All Polices” page gives a summary list of all the policies in the tree. Policies
are eDirectory objects and can exist anywhere in the tree.
This view provides an easily accessible summary of where policies are and some of the
properties settings, for easier policy comparison. Elements include the policy Full
Distinguished Name, which the administrator may click on and go immediately to the
properties of that policy. The summary includes whether the user and/or group properties
are in use, the selected distribution algorithm, the default directory quota, the number of
paths defined, the selected deletion period, workflow options, and whether quota
management is active, along with the specified quota ceiling, and predetermined
increment (if specified.) Additional detail on workflow options are found in chapter 15,
Workflow, and further detail on Quota Manager is found in chapter 13, Quota Manager.
Engine Status
The Engine Status Page provides the same information that can be seen on the File
System Factory™ Engine Console. The engine status indicates whether the engine is
accepting and/or processing events. General information includes version information,
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
24
Page 26
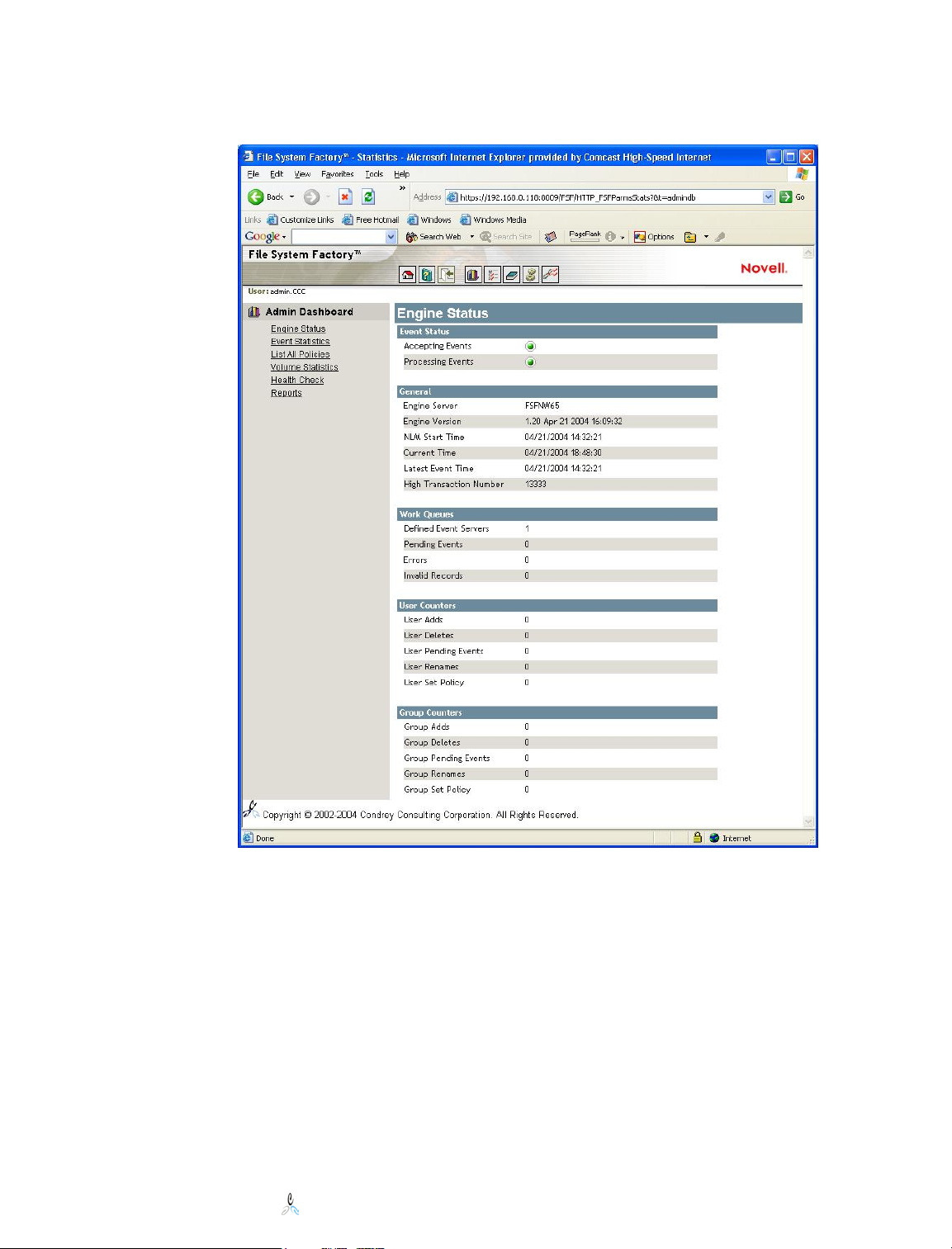
the NLM start time, number of event server, and events in the queues. It also shows
counts of specific operations that have been performed on Group and User objects. These
counts are from the time of load.
This same information is available in the “Manage FSF Engine” option. However, this
view does not have the controls to turn process and accept events on, nor does it have the
option to view the details of the pending events. Those operations are available in the
“Manage FSF Engine” option.
Event Statistics
The Event statistics page gives a daily view of the same event statistics that are tracked on
the Engine Console. The current day and the previous three days are shown. Counts will
be different from the engine status counts as that view counts from engine load time.
Events tracked include user and group add, delete, deferred delete, rename, user move
and user set policy.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
25
Page 27

Volume Statistics
The Volume statistics page lists all the paths in use in File System Factory™ policies.
The amount of space on the volume, the amount of space in use, the amount of space
available and the percentage free are displayed. A status “stoplight” indicates where
space is getting low.
Health Check
The server health check indicates whether the server running the File System Factory™
Engine is able to communicate with other servers. The areas of concern are the servers
running the event NLM, and any servers which host storage pointed to by policy paths.
Status is indicated as a “green light” when connectivity is good, and a “red light” when
there is a problem.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
26
Page 28

Reports
Reports are generated every night a little after midnight. One report is stored for each
day.
The report page allows configuration and generation of reports for various statistics
related to objects managed by File System Factory™. The reports that can be generated
are as follows:
□ Disk space usage reports relative to
o Users
o A specific Policy
o Groups
o A specific Volume
These graphical reports provide information on how much file space is available to
the given entity, and how much is actually in use. It is possible to select multiple
time periods to be able to observe change over time.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
27
Page 29

To generate one of these reports, select the subject for the report (Policy, Volume,
User or Group.) If Policy or Volume is selected, the appropriate drop down list box
will be enabled. Select an item from the list. Select one or more time frame, and
press submit to generate the report.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
28
Page 30

□ Number of users managed by File System Factory™ policies by
o Individual policy
o All policies
This report will give a listing of one or all policies and the number of users managed
by that policy.
To generate this report select either Individual Policy, or All Policies. If Individual
Policy is selected, the drop down list box will be activated. Select the desired policy
and press submit.
Configure FSF Engine
This option allows access to the areas of the product that require configuration. The
default page is the engine configuration which includes Administration management
configuration and Log file management.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
29
Page 31

Administration management allows restriction to be set up to limit access of the
management interface tools. The default is to allow the users with rights to the server
object access to the interface. The alternate option is to set an object as the security
principle which will allow users with security equivalence to that object access to the
interface.
Log file management default values are set for the length of time to keep logged data.
The default for both Audit logs and Detail reports is 30 days. These values can be set to
any value that meets the needs of the organization. Realize that keeping log files for long
periods will occupy more disk space.
The other configurable items are Executive Dashboard, Quota Manger and Workflow.
Both Quota Manager and Workflow are enabled on the policy level. Details on how to
set up these features and use the external interfaces for them are available from the links
on the configuration page. This information is also available in Chapter 13, Quota
Manager and chapter 15, Workflow. The details of the Executive Dashboard
configuration are available in Chapter 14, Executive Dashboard.
Reports/Logfiles
This option provides access to the detailed Daily Reports, and to the Backfill Reports.
The Daily reports include all the transactions logged each day. The reports are generated
each night, just after midnight. Past reports are checked and cleaned up when necessary.
Backfill reports contain the actions that were carried out during each backfill call. These
reports are a stored and named by date and time, as more than one backfill is likely to
occur in one day.
Manage FSF Engine
This option allows the administrator to view active processes related to the File System
Factory Engine. The default screen is the Engine Status, but from this view the
administrator can exercise some control on events occurring. The menu options include:
Engine Status
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
30
Page 32

Event Servers
Pending Events
Stop/Start Accepting New Events
Stop/Start Processing Events
Engine Status
The engine status is the same screen as in Administrative Dashboard. From this view the
other menu items perform actions related to the engine status.
Event Server
The engine status shows how many engine servers are providing data. This option allows
the administrator to view details on those event servers. The version of each event server
is show, along with the last time that event server delivered events to the engine. The
event count shown for each server is the number of events sent from that server from the
last time the event NLM was loaded.
Selecting the radio button next to a server and pressing “List Partitions” will return a list
of the partitions stored on the server, and the replica type of each.
Pending Events
Also on the engine status screen is the count of pending events in the engine. To see what
types of events are pending, select this option. All of the pending events are listed, with
details on the status of those events. A green light shows the event the engine was
processing at the time pending events was selected. Some events process very quickly
and may actually have completed before they can be viewed. Others may remain in the
queue for a long time, waiting for some condition to be met before they can be completed.
For example, if a user is deleted, and the policy on that user indicated that the home
directory should not be deleted for 30 days, that event will remain in the queue until the
time is up before it can be completed.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
31
Page 33

Each event also has a transaction number associated with it. Clicking on the transaction
number provides additional information about the event and the object it is working on,
and some additional options for troubleshooting purposes. Each option is explained in
detail on the page to assist with troubleshooting.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
32
Page 34

Stop/Start Accepting Events and Start/Stop Processing Events
The two status stoplights at the top of the Engine status screen show at a glance whether
the engine is in a processing mode or not. If both lights are green the engine is in full
operation mode. If the light for accepting events is not green, no further events will
accumulate in the pending event queue.
The event servers will store the events received until the engine is set to accept events
again. If the light for processing events is not green, no events in the queue will be
processed. If accept is on, additional events will be added to the queue. The menu items
toggle between start and stop the operations. When stop is selected for either one, a
screen will come up with a field to enter text which can describe the reason for stopping
the operation. This can be helpful if multiple people monitor or administer File System
Factory™.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
33
Page 35

Once turned off, the menu item will change from Stop to Start. To turn the function back
on, select the Start Accepting Events or Start Processing Events option from the left
menu.
Manage FSF Policies
From this option you can
□ Create, manage, modify and assign FSF policies - These operations are
described in chapter 9, Installation and Configuration, and further policy details
are available in Chapter 11, Policy Definitions and Applications
□ Perform Backfill operations – Backfill operations are described in detail in
Chapter 12, Backfill Operations
□ Browse the tree
□ Add Organizational Units
□ View or set a home directory quota
□ Browse the file system
□ View Trustee assignments in the file system
□ Perform Consistency Check for user or groups
These last six operations are described here.
Browse the Tree
This is the starting point of the Manage FSF Policies option. Beginning from the root of
the tree, it is possible to navigate the tree. Object displayed include container objects,
group objects and user objects. To browse into a container object, click on the blue arrow
on the left. To browse back up the tree, click on the portion of the context to go to.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
34
Page 36

When users are listed in the browser, a status “stoplight” has been added to show the
amount and percentage of disk space left available to them based on the disk space quota
set. The administrator can see at a glance which users are getting close to their limit. The
stoplights are based on directory space available and go from green to yellow to red based
on the following percentages:
Green = space available > 25% of quota
Yellow = space available < 25% of quota
Red = space available < 10% of quota
Add Organizational Units
While browsing the tree, it is possible to create an Organizational Unit. Under the list of
all the container objects is an edit field and the “AddOrgUnit” button. Enter the name of
the Organizational Unit to add, and click the button. The organizational unit is created
and can be used immediately.
To have access to the last three options described here, select the manage icon on a
user object. Details of the home directory are displayed, which include the volume name
and the path of the home directory. A summary by suffix and file size is also displayed,
with details of the size of the largest file, the number of files and the number of
subdirectories in the user’s home directory.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
35
Page 37

The three buttons on this page, Quota, Trustees and Files, provide the next three features.
View and Set a Home Directory Quota
Clicking on the Quota Button provides the disk space quota information. The current
disk space limit is displayed, as is the amount of space the user has left.
If “Restrict Size” is checked, a quota is set. For unlimited disk space, uncheck “Restrict
Size.” To change the limit, type it in the edit field “Limit.” The screen should update to
show the amount of space left available to the user. Press “Back” to return to the
previous screen.
Browse the File System
Selecting the “File” button from the “Object Management” page allows the administrator
to view the files and directories in the selected user’s home directory. This may be
helpful in deciding whether or not to increase a user’s quota, or in seeing if a user has
needed files. The sub-directories are listed, followed by the files in the current directory.
Choosing a subdirectory changes the view to that subdirectory. The “Trustees” button
initiates the security analysis option described next.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
36
Page 38

View Trustee Assignments in the File System
Sometimes for security auditing purposes it is helpful to know who has rights at a
particular directory level, and how they got those rights. Selecting the “Trustees” button,
either from the file browse view or the “Object Management” view, provide an analysis of
the rights all eDirectory objects have to the selected directory. It provides a list of each
object with effective rights and identifies how those rights were given, i.e. through a
direct trustee assignment, thought inheritance, or via security equivalence. Inherited
rights filters (IRFs) can be discovered through this analysis as well.
When the analysis is run, the list is displayed, and the following legend is displayed as
well, to help the administrator to understand the results.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
37
Page 39

Perform Consistency Check on User or Groups
To fully take advantage of File System Factory, it is important to know whether objects
are correctly cataloged by File System Factory and being managed properly. New to
version 1.2.1, a consistency check has been added to show what is being managed and
where problems or inconsistencies might exist. The consistency reports can be accessed
from the backfill options, or from the object selection management interface.
The user report identifies potential problems or inconsistencies with a set of users and
home directory management, and the group report shows this information with groups and
group storage management. The report shows which users are properly cataloged for
management with File System Factory, and then shows volume and path information,
rights, quotas and status for each user. The report also provides details on collective
information, including volumes, paths, rights and quotas, identifying potential problems
where possible.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
38
Page 40

Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
39
Page 41

11 Policy Definitions and Application
File System Factory™ Policies are where the Administrator defines how disk space is to
be managed for the objects in the container(s) associated with that Policy. Typically, an
Administrator will perform these actions:
1. Designate some disk storage for File System Factory™ to use for a given Policy.
2. Define a Policy, pointing the policy at the disk space.
3. Associate the Policy with one or more objects in the tree.
File System Factory™ then handles all the disk allocation, management, and cleanup for
objects that inherit or are directly assigned those policies.
How is a Policy Assigned and Inherited?
A user storage policy may be assigned to the following object types:
• Organization
• Organizational Unit
• Group
• User
When File System Factory™ performs an analysis on an individual user object, it must
determine which policy, if any, to use. It determines this by searching in the following
order until a policy is located or the list is exhausted:
1. Direct assignment to the user itself.
2. An assignment to a group that the user is a member of. The groups are
searched in the order that the user was added to them in eDirectory.
3. The parent container of the user object.
4. The parent’s parent container and so on up to the [Root].
Assigning a Policy Directly to a User
As mentioned above a user storage policy may be assigned to the user object directly
instead of having the policy be inherited from a container or group that the user is a
member of. This policy assignment may be done using the File System Factory™ web
interface, or the attribute may be set using any tool or program that can write to
eDirectory. For example, an LDAP application or a Novell Identity Manager (formerly
DirXML) driver might set this attribute as part of the user provisioning process.
In some provisioning solutions, the user may be created before there is an opportunity to
set this attribute. This is not an issue unless there is another policy that may be assigned to
a container or group that may affect the user.
To guard against premature application of a container or group assigned policy, File
System Factory™ contains a configurable parameter for delaying evaluation of new user
events.
You should plan based on your account creation and provisioning process before creating
a situation where multiple policies may apply to any single user.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
40
Page 42

Policy Attribute Changes
The attributes of a Policy may be modified at anytime using the File System Factory™
web interface; after which any eDirectory events on objects that use that policy will result
in the new values being applied. No policy attribute change will be automatically
retroactive against files systems affected by the policy. Backfill operations may be used to
retroactively apply certain policy changes.
Policy Assignment Changes
Policy assignments to objects in the tree may be set and changed at any time. However,
the policy is only immediately applied against existing user objects if the policy is applied
directly to the user. Changes in policy assignments to groups and containers require a
backfill operation. The following table describes operation in these cases:
New Policy Assigned
Via
Previous Policy
Assigned Via
None
User
Group
Container
None User Group Container
No action. Apply
Immediate
No action. Apply
Immediate
No action. Apply
Immediate
No action. Apply
Immediate
Apply via
Backfill
Apply via
Backfill
Apply via
Backfill
Apply via
Backfill
Apply via
Backfill
Apply via
Backfill
Apply via
Backfill
Apply via
Backfill
Policy changes against groups and containers require a backfill as a safety precaution.
Inadvertent changes in policy assignments at these levels have the capability of triggering
data movement for hundreds or even thousands of users which could be gigabytes or even
terabytes of data. Backfill operations constitute a direct request from the administrator to
take these actions.
See the chapter on Data Migration for more information about data movement after a
policy change.
Policy Re-Evaluation and Group Membership Changes
Because an individual user may inherit a policy from a group, changes in membership
may affect the policy that needs to be applied. If a user object is added or removed from a
group in the Directory, and that group has a policy associated with it, the user object is reevaluated by the File System Factory™ Engine. If it is determined that a new policy
applies to the user as a result, the new policy is applied immediately.
As with any immediate policy change, data movement may result. See the chapter on Data
Migration for more information about data movement.
Policy Re-Evaluation and Object Moves
If a user object is moved in the Directory, the object is re-evaluated by the File System
Factory™ Engine. If it is determined that a new policy applies to the user as a result of
the move, the new policy is applied immediately. A new policy will only apply if policies
are assigned to containers. In other words, if a policy was assigned directly to a user or to
a group the user was in, there would be no effective policy change as a result of a user
move since the group memberships and policy assignment attribute would move with the
user.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
41
Page 43

As with any immediate policy change, data movement may result. See the chapter on Data
Migration for more information about data movement.
What Makes Up a Policy?
In this section we will describe the contents of a Policy in detail.
A Policy is an object in the tree that has attributes that define it. Conceptually, a Policy
consists of two parts:
1. One set of attributes that define management for Users.
Item Multi-Valued Description
Path Yes Points to one or more target locations to hold
file systems for Users.
Maximum
Unreachable
Paths
Algorithm No Specifies the Load-Balancing algorithm to be
ACL No Specifies the trustee rights that each USER
Quota No Specifies the default quota that should be
Quota
Ceiling
Quota
Increment
Template No Points to a directory that should be copied into
Move
Throttle
Move
Schedule
DelWait No Specifies how to manage File System Cleanup
No The point at which new object or set policy
events affected by this policy should be held
pending availability of paths specified in the
policy.
used in selecting between the defined paths.
should be granted to their home directory.
Rights may be given to other objects
automatically by using the Template option.
See the section on Template Processing for
more information.
placed on the each User’s home directory.
No If Quota Management is enabled for the policy,
this specifies the maximum disk space quota
the user can have through quota management.
If zero, there is no maximum specified. See
the section on Quota Management for more
information.
No If Quota Management is enabled for the policy,
this specifies the incremental increase of disk
space quota the user can be given through
quota management. If zero, the quota manager
can manually set the new quota amount. See
the section on Quota Management for more
information.
each new User home directory. See the section
on Template Processing for more information.
No Specifies how fast data is to be moved from
one location to another during a data migration
operation which may occur as the result of a
policy assignment change, object move, or
backfill operation. See the chapter on Data
Migration for more information.
No Specifies a weekly schedule for when data may
be moved during a data migration operation.
for User Home Directories.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
42
Page 44

Workflow No Specifies that the user home directory should
be assigned to the manager upon user delete.
See the chapter on Workflow for more
information.
2. One set of attributes that define management for Groups.
Item Multi-Valued Description
Path Yes Points to one or more target locations to hold file
systems for collaborative disk space.
Algorithm No Specifies the Load-Balancing algorithm to be
used in selecting between the defined paths.
ACL No Specifies the trustee rights that each Group
should be granted to the root of its disk space.
You have granular control over rights within the
shared file system by making use of a template.
See the section on Template Processing for more
information.
Quota No Specifies the default quota that should be placed
on the directory allocated for each group.
Template No Points to a directory that should be copied into
each new group directory. See the section on
Template Processing for more information.
DelWait No Specifies how to manage File System Cleanup
for group disk space.
There is no requirement that you define management for both Users and Groups in a
single Policy, but you may do so if you like. File System Factory™ regards a Policy with
no target paths defined as “not managed”. So, if you create a Policy and assign target
paths in the “User Properties” section, but do not assign any paths in the “Group
Properties” section, then the Policy has no effect on group events in containers where the
Policy is applied.
Policies inherit down the tree. Therefore, if you associate a Policy that has user paths
defined with the “Atlanta.Acme” container, then it will apply for users created in the
“Sales.Atlanta.Acme” container. You can block inheritance by assigning another Policy
with no path defined to a container below the one where the original Policy was defined.
Algorithms and Target Selection
One of the most important elements of File System Factory™ is its ability to load-balance
disk allocations across a set of server volumes. When a new user home directory or piece
of group storage is created, File System Factory™ must decide on the location.
One of the attributes in a Policy definition is the load-balancing algorithm to be used is
when selecting the location from the list of target paths also defined in the Policy.
Currently there are three algorithms to choose from:
Algorithm Description
Random A path is selected from the target path list at random.
The random distribution method is quite effective and in our tests
has proven to be a good selection for most installations unless the
target volumes are not close to the same size at installation.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
43
Page 45

Actual Space A path is selected from the target path list based on the actual
free space remaining on the volume holding each of the target
paths. The path on the volume with the most disk space
remaining is selected.
If your path list consists only of multiple paths on the same
volume, you should use the Random algorithm instead.
Percentage Space A path is selected from the target path list based on the
percentage space remaining on the volume holding each of the
target paths. The path on the volume with the most disk space
remaining is selected.
If your path list consists only of multiple paths on the same
volume, you should use the Random algorithm instead.
The name of the directory created in the selected target path will be the common name
(CN) of the user or group object. If a directory by the same name already exists in the
target path (there are multiple objects with the same common name), File System
Factory™ will select the next path from the targeted list. If the list is exhausted without
finding a location for the directory, the transaction is moved into the NO_PATHS area of
the event database, a message is issued, and the NO_PATHS event counter is
incremented.
Deletion Processing Management
Another valuable aspect of File System Factory™ that makes it unique is its ability to
automatically cleanup user and group disk space based on events in the Directory. The
design of File System Factory™ is such that the engine is still able to locate a specific
user’s home directory after the user has been deleted.
A Policy definition allows the Administrator to specify when (or if) the disk space owned
by an object is to be automatically deleted when the object is deleted from the Directory.
There are three choices:
Choice Description
Never File System Factory™ never deletes the disk space owned by
objects in containers associated with this Policy.
Immediately File System Factory™ deletes the disk space owned by objects in
containers associated with this Policy as soon as the objects are
deleted from the Directory.
Deferred N days File System Factory™ deletes the disk space owned by objects in
containers associated with this Policy but allows the
Administrator to delay the deletion for a specified amount of time
after the objects are deleted from the Directory.
If the deletion management attributes of a given policy are changed and deletes being
governed are pending on the File System Factory™ process list, the administrator may
option to have those delete events modified to conform to the latest attributes. For
example, suppose a policy is configured to defer deletes for 30 days and there are 400
deletes pending because of this policy. If the policy is changed to defer deletes for 45
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
44
Page 46

days, the administrator will be prompted for approval to modify the 400 pending deletes
so that each of them adheres to the new 45 day policy.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
45
Page 47

12 Backfill Operations
In some cases, it may be necessary to retroactively apply a given policy to existing users
and file systems. Or it may be necessary to perform some administrative corrective action
or operation on a large set of users. File System Factory™ collectively refers to this type
of operation as a “Backfill”. A backfill operation is issued through the File System
Factory™ web interface. Also available from the backfill operation page, a diagnostic
consistency check report can be run. These reports can help determine what backfill
options need to be run against a given group or container. See more details on the
consistency checks in section 10.
You may perform a backfill operation against a container, a group, or an individual user
object. Backfill operations against a group will pull users from the group membership.
Backfill operations against a container will pull all users in the given container as well as
all subordinate containers.
Each user object is analyzed and worked with independently, regardless of whether the
backfill is initiated via container, group, or directly against an individual user.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
46
Page 48

Backfill Operations
There are several operations available to the administrator issuing a backfill request:
Backfill Operation Result
Full Backfill (suboption “Enforce
Paths”)
A full analysis of each user is performed. The applicable policy
for the user (if any) is determined and applied. In applying the
policy, users without home directories will have one
provisioned for them according to the policy. Pre-existing user
home directories will be cataloged for management by File
System Factory™.
This option is particularly useful for quickly provisioning home
directory storage in environments where users exist in the tree,
but to this point have not been given personal storage on the
network.
This option is also useful for seamlessly moving user data to
other volumes or servers on the network based on a schedule
defined by the administrator.
The “Enforce Paths” check box causes an additional check to
see if the home directory is located in one of the paths defined
in the policy. If it is not, the data will be moved to one of the
policy path locations.
See the section on “Enforce Paths” in the “Data Migration”
chapter for more information about using this special backfill
sub-option to trigger user data movement from unmanaged to
managed storage locations.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
47
Page 49

Recover
NDS/eDirectory
attribute
Recover Trustees Home Directory file system trustee assignments can become
Apply Quota Many user home directories are created without a disk space
Set Attributes New in File System Factory version 1.2.1, this option can be
Copy Template New in File System Factory version 1.2.1, this option can add
During the course of running eDirectory and NetWare in
production environments, if may become necessary to
repopulate the user object’s Home Directory attribute. The
reasons behind this need are many and varied.
Because the File System Factory™ catalog retains home
directory location information, it can easily restore the home
directory attribute for all users in a single backfill operation.
corrupt, lost, or inadvertently deleted in the course of day to
day operations on a production network.
File System Factory™ can easily reapply trustee assignments to
the file system storage for all users based on the ACL defined in
each user’s storage policy.
quota assignment. File System Factory™ can analyze the quota
(or lack thereof) on each user, and can apply the quota set in the
policy based on one of the following selections:
- Set quota for directories that do not currently have a quota
defined. (This will not change existing quotas.)
- All directories will have quota set or overwritten except those
with a quota larger than the one defined in the policy.
- All directories. All existing quota assignments will be
overwritten.
used to retroactively set attributes on all user home directories.
The attributes which can be set are Rename Inhibit, Delete
Inhibit, Read Only, Purge Immediate, Don’t Compress,
Immediate Compress, Archive and Hidden. Consider setting
the same flags on the policy template so that home directories
for new users will be automatically set accordingly.
or update a default directory structure for each user in the
container or group.
Select whether to use the location already specified in the
policy, or whether to specify an alternate location for use during
this backfill operation only.
Select the overwrite option from one of the following:
-Do not overwrite
-Always overwrite
-Overwrite only if newer
This option will copy the template for a given user only if the
user is covered by a policy and currently cataloged and
managed by File System Factory. As necessary, any quota that
is currently on a given directory will be temporarily removed
during the copy and then replaced after the copy completes.
Hint: This option is useful for distributing files and subdirectory
structures to user home directories or setting flags on home
directories
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
.
48
Page 50

Assign Home
Directory Attribute
Also new in File System Factory version 1.2.1, this option can
claim orphaned directories and link them to existing users and
get them ready for management.
For each user in this group, search the indicated file system
directory for a subdirectory with the same name as the common
name of the user and assign it as the home directory according
to the following rule:
-Assign only if the Home Directory attribute is currently not
set.
- Assign if the Home Directory attribute is not set or reassign if
the currently specified home directory is not found on disk.
- Overwrite any existing home directory attribute setting.
Select the volume and enter the path to be searched for existing
directories.
Unlike all other backfill options, this option can take action on
users not covered by a FSF policy. For each user whose home
directory attribute is set, a File System Factory catalog entry
will be created if the entry does not previously exist and the
user is covered by a policy. This option does not apply policybased quota and trustee assignments. These should be
introduced with additional backfill operations using those
options.
This option is useful for introducing legacy users that have a
home directory on the network, but the directory is not
specified correctly in the home directory attribute of the user's
object.
Check Mode
A backfill operation, especially one issued against a container, may cause File System
Factory™ to initiate different action events against a large number of users. The
administrator may elect to issue the backfill request in “Check Mode”, which instructs
File System Factory™ to perform the analysis portion of the request and report on the
action to be taken, but avoid taking any actions. This allows the administrator to preview
the results of his actions and prevent unintended results.
Filter Option
When running the Container or Group backfill, an option is present to enter a search filter
to limit the objects analyzed. Standard wildcard characters are supported and multiple
strings can be entered, separated by the “|” character.
Sub-container Option
When running the Container backfill, an option is present to turn off the analysis of subcontainer. When this option is selected, only the objects in the selected container are
analyzed and processed.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
49
Page 51

Group Property Backfill
New in File System Factory 1.2.1, Group backfill applies to shared storage as well as to
individual home directory management. To use these options browse to a group and
select the bacfill icon. On the left menu, select “Group Storage Management.” This
backfill has its own set of options.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
50
Page 52

Backfill Perform a full analysis on the group and apply the policy
associated with the group. If the group does not have a home
directory, the policy will be applied and a home directory will be
created. If the group has a home directory assigned in eDirectory,
the location will be cataloged and managed.
Hint: Use this option if the group does not already have storage or
if you have previously assigned storage to the home directory
attribute of the group.
Apply Group
Membership
Assign Home
Directory
Attribute
Apply the template using the group membership and owner
attributes.
View Group Membership – shows the content of the members
attribute
Hint: Use this option to apply the group membership and
ownership for -member- and -owner- processing respectively to a
group home directory that is already cataloged and managed.
Assign an existing directory as the Home Directory for this group
and begin management of the storage according to policy.
Home Directory assigned to this group in eDirectory:
<home directory path>
Select the volume to search for existing directories.
Enter the path to search for existing directories.
Note: Unlike all other backfill options, this option can take action
on groups not covered by a FSF policy.
Hint: This option is useful for introducing legacy groups that have
a home directory on the network, but the directory is not specified
correctly in the home directory attribute of the group's object. If the
group is covered by a group storage policy, FSF will catalog and
begin managing storage for this group.
13 Quota Manager
Quota Manger is a new feature in File System Factory™ 1.2. It includes a separate
external interface to allow a specified user (for example a help-desk administrator or
support personnel) to increase users’ quotas upon request, without having to have rights
to the file system.
File System Factory™ adds an attribute to the Organizational Person class called
cccFSFactoryHomeDirectoryQuota. A help-desk administrator or support person is given
the Write right to this attribute on the users he or she is to manage, and this attribute
enables them to be a quota manager on those users who have policies with quota
management enabled. The steps for using quota manager are as follows:
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
51
Page 53

1. Enable and configure Quota Manager on each policy covering users where quota
management is desired. Be sure the users are covered by the policy. If the
policy was applied after the users were created, a backfill may be required to
include those users in the FSF database.
2. Set up the rights for the user(s) to be the administrator of the disk space quotas.
3. Manage user disk space quotas using the external Quota Manager Interface
These steps are detailed here.
Enabling and Configuring Quota Management for a
Policy
Quota management is enabled at the policy level. To activate, simply go to the Quota
Manger Control, found on the user properties page of any File System Factory™ policy.
Select the check-box “Quota Manager is enabled for users covered by this policy” to
enable quota management interface for managing user quotas.
Options can then be set to determine how the quota can be managed. Choosing no
maximum will allow the quota manager to continue to increment the limit until the
volume space is exhausted. Otherwise, an upper limit maximum may be set. The other
option determines how the quota is raised by the manager. A predetermined amount can
be set, and the administrator will be able to raise a user’s quota by that amount until it
reaches the maximum (if set.) Otherwise the administrator will be able to type in the new
user quota.
Setting up Rights to Use Quota Manager
Users in eDirectory can have the rights set to use Quota Manager. Organization Roles,
groups, or other object that use security equivalence can be used as well. To make an
object the quota manager, select the portion of the tree where the users exist that the quota
manager will be allowed to manage. Remember these users must be managed by FSF
policies with quota management enabled. Set the attribute rights of the desired object for
the attribute cccFSFactoryHomeDirectoryQuota to Write. This can be set for the whole
tree, for an organization or organizational unit, or all the way down to an individual user,
if desired. Because this feature uses eDirectory rights, the traditional inheritance applies,
including the use of inherited rights filters.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
52
Page 54

Using the Quota Manager Interface
Once quota management has been enabled on a policy and a user has been identified as a
quota manager, the quota management tasks can be performed in a separate user interface.
Enter the URL for the quota manager in any web browser. The default URL is
http://your.server.name.or.ip.address:8008/FSF/HTTP_FSFQuotaMgr or for SSL:
https://your.server.name.or.ip.address:8009/FSF/HTTP_FSFQuotaMgr.
It will be necessary for the user to log in. If the user is in the File System Factory™
index, the common name will be sufficient; otherwise a fully distinguished name is
required.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
53
Page 55

Once logged in, the initial screen requires the help-desk administrator or other designated
quota manager user to enter a username to manage. This can be a full name or a standard
search string, such as bob*. This will return a list of users in the tree which match the
search spec (or username) and are managed by FSF policies which have quota
management enabled.
Each user will have a stoplight indicator showing what percentage of their directory quota
is in use. The stoplights are based on directory space available and go from green to
yellow to red based on the following percentages:
Green = space available > 25% of quota
Yellow = space available < 25% of quota
Red = space available < 10% of quota
Click on the stoplight to manage the user’s quota.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
54
Page 56

From the “Home Directory Statistics and Quota” page the quota administrator will be able
to manage the quota based on the policy settings. If an increment interval has been set,
the manager will be able to add the default amount by clicking the button. If no interval
has been set, the manager will be able to manually type in the new quota. In addition to
the quota information, the manager can view file statistics based on file extension.
Statistics include the size of the largest file, the number of files and subdirectories, and a
list indicating number of files by extension, and sorted by size.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
55
Page 57

14 Executive Dashboard
Executive Dashboard is a new feature in File System Factory™ 1.2. It includes a separate
interface to allow specified users to view statistics and generate reports based on the
storage managed by File System Factory™.
Configuring the Executive Dashboard
The configuration page for the Executive Dashboard is found in management interface
under the Configure FSF Engine option. Selecting Executive Dashboard on the left menu
will bring up the configuration page. By default, all of the options are turned off.
The first item in the configuration allows Executive Dashboard to be enabled. If this is
not selected, the external interface for Executive Dashboard will not be available. Next,
select or type in the name of the object which will have rights to use the external interface
for the Executive Dashboard. See the next section (Executive Dashboard Security
Principle Object) for more details. Three menu items can be enabled for Executive
Dashboard. These are “Event Statistics,” “Volume Statistics” and “Reports.” Enableing
“Storage Statistics on the configuration screen allows the dashboard user to see “Volume
Statistics.” The “Reports” page can have either or both of two types of reports. These
are “Policy Statistics” and “Disk Usage.” Select the appropriate check boxes to enable
the desired features. Note: The default for all the Executive Dashboard elements is
Disabled.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
56
Page 58

Executive Dashboard Security Principle Object
To secure the Executive Dashboard, File System Factory™ uses Security Equivalence to
determine who has rights to login to the Executive Dashboard. To accomplish this, File
System Factory™ supports any object type that supports security equals to (e.g. group
and organizational role objects).
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
57
Page 59

You may also designate one user as the security principle. If you choose this option, only
this user will have access to the Executive Dashboard.
Using the Executive Dashboard Interface
Enter the URL for the Executive Dashboard in any web browser. The default URL is
http://your.server.name.or.ip.address:8008/FSF/HTTP_FSFExecutiveDashboard
or for SSL:
https://your.server.name.or.ip.address:8009/FSF/HTTP_FSFExecutiveDashboard.
It will be necessary for the user to log in. If the user is in the File System Factory™
index, the common name will be sufficient; otherwise a fully distinguished name is
required.
Once logged in, the user will have access to those elements of the dashboard enabled in
the configuration.
Event Statistics
The Event statistics page gives a daily view of the same event statistics that are tracked on
the Engine Console. The current day and the previous three days are shown. Counts will
be different from the engine status counts as that view counts from engine load time.
Events tracked include user and group add, delete, deferred delete, rename, user move
and user set policy.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
58
Page 60

Reports
The report page allows configuration and generation of reports for various statistics
related to objects managed by File System Factory™. The reports that can be generated
are as follows:
□ Disk space usage reports relative to
o Users
o A specific Policy
o Groups
o A specific Volume
These graphical reports provide information on how much disk space is available to
the selected report category, and how much is actually in use. It is possible to select
multiple time periods to be able to observe change over time.
To generate one of these reports, select the subject for the report (Policy, Volume,
User or Group.) If Policy or Volume is selected, the appropriate drop down list box
will be enabled. Select an item from the list. Select one or more time frame, and
press submit to generate the report.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
59
Page 61

□ Number of users managed by File System Factory™ policies by
o Individual policy
o All policies
This report will give a listing of one or all policies and the number of users managed
by that policy.
To generate this report select either Individual Policy, or All Policies. If Individual
Policy is selected, the drop down list box will be activated. Select the desired policy
and press submit.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
60
Page 62

Volume Statistics
The Volume statistics page lists all the paths in use in File System Factory™ policies.
The amount of space on the volume, the amount of space in use, the amount of space
available and the percentage free are displayed. A status “stoplight” indicates where
space is getting low.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
61
Page 63

15 Workflow
Workflow is a new feature in File System Factory™ 1.2. It includes a separate interface
to allow managers to determine what should be done with the home directory of a deleted
user. The intent of this subsystem is to allow policy definitions by which File System
Factory™ can queue storage for deleted employees up to their manager when they leave
the organization.
This mechanism leverages the eDirectory attributes managed by the Organizational Chart
function in eGuide™. The screen shot below shows that Sue Jensen and Tom Stuart both
report to Bob Smith in the Engineering organization. If the File System Factory Policy
governing storage for Tom is configured, when Tom leaves the organization, his home
directory contents will be queued up to Bob, who can then inspect the contents, approve
the deletion, vault the data, or assign it to another individual at that point or at a later date;
perhaps when Tom’s replacement has been hired.
Configuring Workflow
When configuring a policy that will govern user home directory storage, you have the
ability enable and configure workflow processing for users covered by the given policy.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
62
Page 64

If you enable workflow for the policy, then the deletion of any user object covered by the
policy will trigger the queuing in the workflow subsystem. As the administrator, you have
the option of restricting how long the deleted employee’s manager has to do something
with the data. As shown above, a number of days or indefinitely may be specified.
When a user covered by a policy with workflow enabled is deleted, the workflow process
takes over.
If the deleted user does not have a manager defined in eGuide™, then deletion process
will proceed for that user according to the policy as if workflow were not enabled.
When workflow processing has completed, either by the manager approving the deletion
or by the approval period specified in the policy expiring, the deletion of the home
directory according to the policy will take place.
Setting up the Workflow Management Structure
As discussed above, File System Factory™ leverages the Organizational Structure
defined in eGuide™. See the eGuide™ documentation for information on configuring and
using eGuide™.
File System Factory™ monitors changes to the Organizational Structure in eDirectory and
maintains information about these relationships so that when a user is deleted, File System
Factory™ will know who the manager is for the given user and can queue it
appropriately. File System Factory only maintains this information for those users whose
home directory is managed. As with other aspects of File System Factory, you may need
to perform a backfill operation on preexisting users in order to have them managed.
Using the Workflow Interface
Much like the Executive Dashboard and Quota Manager components of File System
Factory™ 1.2, the end-user interface for the Workflow component is external to the
NetWare Remote Manager interface. Most administrators do not want end users seeing or
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
63
Page 65

touching the Remote Manager, so there is a separate interface that employee managers
will use to attach and manage data that has been queued to them.
The default URL is
http://your.server.name.or.ip.address:8008/FSF/HTTP_FSFWorkFlow
or for SSL:
https://your.server.name.or.ip.address:8009/FSF/HTTP_FSFWorkFlow
It is suggested that you add these as links in your organizational portal or on a
management web page that your users commonly access.
It will be necessary for the user to log in. If the user is in the File System Factory™ index
(which they will be if they are managed), the common name will be sufficient; otherwise a
fully distinguished name is required.
Once logged in, the employee manager will view all workflow entities which have been
assigned to him and can then perform operations on them. The documentation in the user
interface will detail these operations.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
64
Page 66

16 Template Processing
A File System Factory™ Policy object contains provisions for specifying a path to a
template for either users or groups. A template is a subdirectory that will be copied into
the home directory for each new (or backfilled) user or group covered by the Policy.
A template for user home directories may be specified in the User Properties section of
the Policy definition. Likewise, a template for group directories may be specified in the
Group Properties section of the Policy definition.
The operations involved with copying templates are the same for both user and group
templates. However, the templates are managed differently. The sections below describe
how File System Factory™ deals with both User and Group templates.
User Templates
Processing for User templates is a very simple concept. When File System Factory™
creates a home directory for a user; the Policy definition is examined to determine if a
user template has been defined. If a template has been specified, the template is copied
into the user’s home directory. That is, all the files and directories in the template are
copied as well as their attributes and trustee assignments.
During the life of the user object, File System Factory™ normally performs no further
actions on the user home directory unless specifically instructed to do so by the
administrator. No further action is taken until the directory is deleted. As is discussed
below, this is a major difference from group directory template processing.
Group Templates
Processing for Group templates is a very powerful construct in File System Factory™.
The initial processing is exactly the same as for User home directories with templates.
When File System Factory™ creates a directory for a Group; the policy is examined to
determine if a template has been defined and, if so, copies the contents of the template
directory along with all attributes and trustee assignments.
Unlike User home directories, Group disk space managed by File System Factory™ is
considered an evolving entity. File System Factory™ monitors the member and owner
attributes of Group objects so that the addition and deletion of members and owners can
have a direct impact on the structure of the individual file system of a group as well as the
rights given within the structure.
Steps for setting up Group Templates
To use the powerful abilities of group templates, there are some basic steps to follow.
Greater detail of how the elements of group templates are used follow this section, but
these are the steps to get started..
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
65
Page 67

1. Create three eDirectory objects to allow rights to be set. These object
can be anywhere in the tree, for example, in a container named
FSF.MyOrg, (just remember where they are) and can be of any type,
such as a template. The important element is the common name of the
objects. The objects must be named
-owner-
-member-
-group-.
2. In the file system, create a group template directory. This will be the
structure of the group storage that will be created. This can contain any
structure and files that will facilitate the group needs, including
personal storage areas for each member and owner of the group.
Members and owners can have different rights to different areas as well.
To create individual member directories within the directory structure,
create a directory named -member-. To create individual owner
directories within the directory structure, create a directory named
-owner-. (For more details, see “File System for Group Templates”
below.)
3. Set up the eDirectory rights for the group, members and owners using
the eDirectory objects created in step 1. Making trustee assignments on
directories for the -member- object will allow the members of the group
to have the rights specified. Making trustee assignments on directories
for the -owner- object will allow the owners of the group to have the
rights specified. Making trustee assignments on directories for the
-group- object will assign the rights to the group object. Trustee
assignments can be made where ever needed in the structure. (For more
details, see “Trustee Management with Group Templates” below.)
4. Set up a File System Factory™ policy using the group paths and
properties. Point the template setting to the template directory created.
5. Apply the policy to a container. Unlike the user properties of a policy
which can be applied at the container, group or user level, the group
properties of a policy are only applied from a container level when
groups added in that container (and its sub-containers.)
6. Create groups in the container. Directory storage will be automatically
created for each group, and personal areas will be added as owners and
members are added.
File Systems for Group Templates
In the template for Groups, there are two special directory names that receive special
processing consideration:
• “-member-“: designates that each member of the group should have their own
personal directory in the group space.
• “-owner-“: designates that each owner of the group should have their own
personal directory in the group space.
These special directory names can appear anywhere in the template directory and may
appear multiple times. However, please note that a “-member-” or “-owner-” will not take
effect if it is below another “-member-” in the directory structure. This to avoid giving
members the power to have File System Factory™ automatically create subdirectories for
each owner or member in a given member’s personal space.
Consider the following directory template designed for an educational environment:
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
66
Page 68

Suppose a new group, SPAN340-001.SPRING2003.CLASSWORK.STATEU, is created
for Spanish 340 Section 1 in a container covered by a Policy that specifies the sample
directory above for its group template. A new directory is created for the group:
Now, suppose that 10 students are added as members:
• JSmith.Students.STATEU
• MRoberts.Students.STATEU
• NFrost.Students.STATEU
• PJones.Students.STATEU
• RBrooks.Students.STATEU
• SSmith.Students.STATEU
• STimms.Students.STATEU
• TJones.Students.STATEU
• TSmythe.Students.STATEU
• WClark.Students.STATEU
And the following 2 instructors are added as owners:
• ABelcher.Staff.STATEU
• KAlesanto.Staff.STATEU
The resulting directory for Spanish 340 Section 1 would look as follows:
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
67
Page 69

Removal of members or owners of the group will not delete the disk space assigned to
that user. However, the user will no longer have rights to the disk space. This makes it
simple to add the member back and allows the data owned by that user to be retained for
the sake of the group.
Trustee Management with Group Templates
Just as member and owner modification can have an impact on the file system structure of
the disk space assigned to a group, trustee assignments can be dynamically managed.
Static trustee assignments can be made to any file or directory in the template and these
will be copied or applied to each set of directories created as a result of the application of
the Policy. For example, you may wish to have a proxy user
(APACHEUSER.SYSTEMS.STATEU) associated with a web server to have rights to a
specific directory (PUBLIC.WWW) in the file system for each group.
Static trustee assignments copied to the disk space for each group, while powerful, are
probably not sufficient for all needs you may have. Therefore, File System Factory™
supports dynamic as well as static trustee assignments to any file or directory in the
template.
With dynamic trustee management, there are two types of controls. Firstly, the group
object itself may be given specific rights within the file system associated with the group.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
68
Page 70

Secondly, changes to the members and owners attributes of the group result in changes to
the trustee assignments on the file system associated with the group.
Dynamic trustee assignments are controlled using objects with special NDS common
names for group, member, and owner. When setting up the trustee assignments on the
template, the name of the container holding the specially named objects does not matter.
If the common name of the object is “-group-”, “-member-”, or “-owner-”, then the
substitution will take place when applied to the group disk space.
The actions taken by File System Factory™ for each assignment based on a special name
common name (CN) are described in the table below:
Object CN Action Applied
-group- The group object is given the
specified trustee assignment to
At initial creation of the
file system for the group.
the given file or directory.
-member- The specific group member is
given the specified trustee
assignment to the given file or
directory.
When a member is added
to the group, the user
object of the member is
given the trustee
assignment. When the
member is removed, the
assignment to the file space
is removed.
-owner- The specific group owner is
given the specified trustee
assignment to the given file or
directory.
When an owner is added to
the group, the user object
of the owner is given the
trustee assignment. When
the owner is removed, the
assignment to the file space
is removed.
Let’s look at some examples of both static and dynamic trustee assignment in action.
Examples
Example 1: Educational
For this example, we will use the educational template sample below:
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
69
Page 71

The directory structure layout for the template is constructed so that the following can
occur:
• There is personal storage space for each instructor.
• Each class has a web presence.
• There is a common folder that everyone can see.
• Each student will have a personal directory for turning in class assignments.
• Each student will have a personal directory for receiving graded work or specific
files from the instructor(s).
We have decided that we want the following trustee assignment to be assigned for each
class:
1. The instructors should have RWCEMFA over their personal directories.
2. The proxy user for the web server should have RF over the PUBLIC.WWW
folder.
3. Everyone in the group should have RF over the PUBLIC.WWW folder.
4. Instructors should have RWCEMF over the PUBLIC.WWW folder.
5. Instructors should have RWCEMFA over the READONLY folder.
6. Everyone in the group should have RF over the READONLY folder.
7. Each student should have RWCEMF over his or her personal TURNIN folder.
8. Instructors should have RF over all students’ TURNIN folders.
9. Each student should have RF over his or her personal REVIEWED folder.
10. Instructors should have RWCEMF over all students’ REVIEWED folders.
Give the above requirements; we will set up the template with these trustee assignments:
The group, owner, and member objects shown in the diagram above are not required to be
user and group objects. The location of the objects in the tree is not a concern to File
System Factory™ either. The only thing that matters is that the CN of the objects are
“-group-”, “-member-”, and “-owner-”.
Now, let’s say that new group representing ENGL101 section 5
(ENGL101_5.classes.STATEU
associated with a Policy that is pointing to our template. As soon as the group is created
in the tree, here is what the disk space and trustee assignments will look like:
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
) is created in the tree. The container holding the group is
70
Page 72

At object creation time, the file and directory structures are copied. The only substitution
involves the -group- trustee assignment, where the name of the group is substituted.
At this point, the template itself no longer plays a part in the life of the group disk space.
The trustees and file structure of the group disk space itself will dictate how or if
member/owner changes affect things.
Now suppose that an instructor, BSmith.staff.STATEU
result:
Notice that the new owner, BSmith, now has a folder under the instructor’s directory and
now has all the same trustee assignments as the -owner- object to the other folders.
Lastly, let’s add two students as group members, ABaker.students.STATEU
TJackson.students.STATEU
. Here is the result:
, is added as an owner. Here is the
and
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
71
Page 73

Notice that the new members have their personal directories as well as rights to them.
Again, note that the member and owner changes occur based not on the template, but on
the trustee assignments and directory structure of the actual disk space for the group. This
means that a single directory for a group can be modified from what it inherited from the
template and the new custom configuration will take effect immediately.
Template Summary
Template processing is a very simple and powerful feature of File System Factory™ for
both users and groups.
You have the opportunity to dynamically populate user home directories with any file and
directory structure that you choose. This population includes trustee assignments as well
as file system attributes.
With respect to groups, the same power is there for collaborative disk space in that the
space can be initially populated with files and directories as well as trustee assignments
and attributes. You also have the ability to define templates that leverage the power of
File System Factory™ to dynamically control group disk space contents and trustee
assignments based on changes to either group members or owners, or both.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
72
Page 74

17 Mass User Testing
File System Factory™ contains an NLM named BULKADD.NLM that can add and
delete NDS/eDirectory users in mass quantities. The NLM is located in the BULKADD
directory of the File System Factory™ distribution.
The parameters for BULKADD are:
• Start: “-sNNN”
• End: “-eNNN”
• Prefix: “-pUSR”
• Action: “-a[0|1]” 1=add 0=remove
• Container “-cCONTAINER.NAME”
For example:
LOAD sys:factory\bulkadd\bulkadd.NLM –s21 –e2499 –pbob –csales.acme –a1
Would create the following users:
bob21.sales.acme
bob22.sales.acme
bob23.sales.acme
…
bob2497.sales.acme
bob2498.sales.acme
bob2498.sales.acme
Note: This NLM is not
courtesy tool to use in testing File System Factory™. If you are a licensed user of File System
Factory™, you are free to use it for other purposes at your site. You may not distribute it further.
Novell File System Factory™ Administrator’s Guide
a supported component of File System Factory™. It is included as a
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
73
Page 75

18 Universal Resource Access
One of the challenges facing any network administrator is the task of presenting the user
with a means to access the resources available to him. For example, a user may be
assigned a home directory on the network, but unless a login script is run to map a drive
to that disk space, the user may have a difficult time locating and using the space.
File System Factory™ allocates and manages personal disk storage for users on the
network and populates the Home Directory attribute of the user object, which is accessed
by login scripts and other mechanisms. However, File System Factory™ also creates and
manages group storage on the network and users need to have a way to access that
storage. Typically a network administrator may define a drive mapping in a login script to
the group disk storage. However, a given user may be a member of many groups. There
may not be enough drive letters to map a drive for each group. Lastly, with the
automation and management provided by File System Factory™, the ability to provide
disk storage to all groups is now a real possibility.
File System Factory™ contains a workstation utility named Universal Resource Access,
or URAccess™, to provide a solution to this problem. When group disk storage is
allocated, a new attribute of the group object named cccFSFactoryHomedir is populated
with a path pointer to the storage, just as the Home Directory attribute of the user object
is populated with a path pointer to personal storage.
URAccess™ is located in the \FACTORY\URACCESS directory on the Engine server.
URAccess is a Windows utility that is supported on Client32-based Windows
workstations. Ash shown in the figure below, the utility is designed to reside in the
Windows System tray.
By invoking this utility during Windows Start-Up, the user will always have the ability to
access all personal and group storage without drive letters or login scripts. Right-clicking
on the icon will provide the user with a description-based menu of storage selections.
Clicking one of these menu items will invoke Windows Explorer with a pointer to that
storage.
URAccess works in concert with File System Factory™, as well as IUAdmin™, another
product from Condrey Consulting Corporation. Among it’s many capabilities,
IUAdmin™ allows administrators to associate many types of resources with any object in
the tree. These resources may be specific files or directories on the network or they may
be any URL accessing any page or application on the Intranet or Internet. These resource
links are all stored with the associated object in eDirectory. Then, anyone with security
equivalence or inherited rights to the associated object will see those resources in their
resource list through URAccess™.
The following diagram shows a typical user’s view of a system running both File System
Factory™ and IUAdmin™.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
74
Page 76

.
The resource list provided by URAccess™ may be rebuilt at any time by clicking the
Refresh button on the menu as shown above. URAccess™ will automatically build access
lists from all trees to which the user is currently authenticated.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
75
Page 77

19 Home Directory Deployment Scenarios
File System Factory™ is designed to fit into any provisioning process that you may
currently be using or plan to implement. The following deployment scenarios illustrate
this concept.
Note:
In the following examples, Policies are applied to containers. However, you may
also choose to apply a given Policy to Groups or individual User Objects.
Resource assistance: Look for complete sample lab exercises in the FSF Lab Training
Guide which is included with this installation.
Scenario 1: New Tree – No User Home Directories
If you are just starting out, File System Factory™ can give your new users managed home
directory space with little effort on your part. Follow these steps:
1. Decide how you are going to create the user objects and where you are going to
put them in the tree.
2. Decide which servers and volumes will hold the user home directories.
3. Create a File System Factory™ Policy and point it to the servers and volumes
that will hold the user home directories. Associate the Policy with the container
(s) that will hold the users.
4. Create the users using any method. Home Directories will be automatically
created and assigned for all users.
5. Any new accounts added to the associated containers will have the Policy
applied and be given new managed home directories.
Scenario 2: Existing Tree – No User Home Directories
If you already have user accounts in your tree, but have not taken the steps to give them
home directories, File System Factory™ can automatically give your existing users
managed home directory space. Follow these steps:
1. Decide which servers and volumes will hold the user home directories.
2. Create a File System Factory™ Policy and point it to the servers and volumes
that will hold the user home directories. Associate the Policy with the container
(s) that already hold the users.
3. Instruct File System Factory™ to do a “Backfill” operation on the containers
holding the user objects. This will apply the Policy to all users in the container as
if they were just created and a home directory will be created and assigned for
every user that does not already have one.
4. Continue using your current method of creating users in the tree.
5. Any new accounts added to the associated containers will have the Policy
applied and be given new managed home directories.
Scenario 3: Existing Tree – Existing User Home
Directories
If you already have user accounts in your tree and they have home directories, File
System Factory™ can begin managing your existing home directories as well as manage
any new ones. Follow these steps:
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
76
Page 78

1. Decide which servers and volumes will hold user home directories for any new
accounts. These can be the same servers and volumes that currently hold your
users, or an entirely new set of storage.
2. Create a File System Factory™ Policy and point it to the servers and volumes
that will hold the new user home directories. Associate the Policy with the
container(s) that already hold the users.
3. Instruct File System Factory™ to do a “Backfill” operation on the containers
holding the user objects. This will apply the Policy to all users in the container as
if they were just created. Since the users already have home directories, File
System Factory™ will catalog the location of each user’s home directory and
processing will be complete.
4. Any new accounts added to the associated containers will have the Policy
applied and be given new managed home directories.
5. When you delete any account, the Policy will be applied for cleanup operations,
even if File System Factory™ did not originally assign the space.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
77
Page 79

20 Collaborative Storage Management
The first thing that most likely comes to mind when thinking about automated storage
management in a medium to large installation is the management of user home
directories. As we have discussed, File System Factory™ can perform that duty for you
with little effort on your part and still fit into your account provisioning strategy.
However, one of the most powerful components of File System Factory™ is its ability to
create and manage collaborative (group) storage. Networks primarily exist for the purpose
of sharing information with others; making it easy for people to work together on
projects.
In a typical environment, the manager of a working group determines that it would be nice
to have a directory on the network for the group to use to share data. He or she goes to the
network administrator and makes the request. The administrator must perform a list of
actions to fulfill this request. This involves:
1. Creating the group object.
2. Adding the members to the group object.
3. Deciding where to put the storage for the group.
4. Creating the disk space for the group.
5. Optionally creating a set of subdirectories in the storage.
6. Communicating with the manager to determine which parts of the storage the
group should have access to and what access to give.
7. Giving the group appropriate access.
8. Communicating with the manager to determine which parts of the storage the
manager should have special access to.
9. Giving the manager appropriate special access.
10. Repeatedly performing steps 5-9 throughout the life of the group and storage.
File System Factory™ automates steps 3-10 of the above list though the use of Policies,
template processing, and NDS event monitoring.
Organizations can now drive collaborative storage creation, management, and deletion as
a provisioning process using any tool or process that can create groups in the Directory.
Collaborative Storage in Business
In business environments, the HR system can be used as a tool to drive the creation and
automatic membership/owner management of departmental and divisional groups. File
System Factory™ adapts to this environment where workers would be defined as
members of the group and managers would be defined as owners of the group.
Even without any automation driving group management, File System Factory™ can
relieve much of the burden of creating and maintaining shared disk space on the network
since it does all the labor intensive work in the background.
Administrators have the ability to delegate authority to create groups to departmental staff
and still provide disk space to the groups without granting staff administrative rights to
disk volumes or servers objects. The application of Policies with quotas that you define
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
78
Page 80

can keep disk usage by departments in check. Using an appropriate template definition
that you put into place can prevent rouge rights assignments targeted outside of the scope
of the working groups for increased security.
Be sure to see the section on Template Processing for a full account of the possibilities
that exist with automated workgroup storage.
Collaborative Storage in Education
In an educational environment, the student database can be used as a tool to drive the
creation and automatic membership/owner management of classes. File System Factory™
adapts to this environment where students would be defined as members of the group and
teachers/instructors would be defined as owners of the group.
K-12 Deployment
File System Factory™ is geared towards rapid deployment in a K-12 environment.
Besides giving a fast and elegant solution to giving personal disk space to all users, File
System Factory™ can also create and manage disk space for all classes in every school in
the district.
As a district or school network administrator, you have the opportunity to revolutionize
collaborative networking in your district by providing automatically managed storage for
every section of every course at your school or district by linking NDS to your student
database.
Using templates, you can customize the storage that is built for each class along grade or
school boundaries. You can provide a web presence for all classes as well as a per class
location for teachers to communicate with parents via the web. Create a “virtual desk” for
each student in the class inside the disk space. These are just a few of the possibilities.
You are limited only by your imagination in this area.
If you skipped the section above on Collaborative Storage in Business, be sure to review
that section to see how File System Factory™ can meet the collaborative storage needs of
staff working groups in local schools and district offices.
Be sure to see the section on Template Processing for a full account of the possibilities
that exist with automated storage for K-12 classes.
Higher Education Deployment
File System Factory™ is also specially geared towards deployment in a higher education
environment. The methodologies used in File System Factory™ for delivering managed
collaborative storage on a large scale stem from tried and true methodologies used for
years in a large higher education Novell environment.
As a higher education network administrator, you have the opportunity to revolutionize
collaborative networking on your campus by providing automatically managed storage for
every section of every course at your school or University by linking NDS to your student
database.
Using templates, you can design file systems where students can securely submit
assignments electronically with appropriate timestamps and where instructors can grade
and return assignments. Because the disk space management is keying off of NDS
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
79
Page 81

changes to the member attribute, you can be assured that the class disk space matches the
NDS group, which matches the actual class role in the student database. Instructors can
publish material for the entire class and the class can publish to the web. These are just a
few of the possibilities. You are limited only by your imagination in this area.
If you skipped the section above on Collaborative Storage in Business, be sure to review
that section to see how File System Factory™ can meet the collaborative storage needs of
faculty and staff working groups.
Be sure to see the section on Template Processing for a full account of the possibilities
that exist with automated workgroup storage.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
80
Page 82

21 Data Migration
Note: In release 1.20 of File System Factory™, Data Migration applies to User home directories only. A later
release of the product will introduce the ability to migrate group disk space.
In Chapter 9, “Policy Definitions and Application”, we described how File System
Factory™ policies may be applied to containers, groups, or individual users and have
detailed how changing policy associations for a given object can result in a different
policy being applicable.
We have also described how moving objects in the tree may cause a new policy to be
applied based on the new location in the tree if container-based policy assignment is used.
Remember that a given policy points to one or more storage locations on the network. If
the policy that covers a given user changes, and the new policy points to different
locations than the original policy, File System Factory™ will move the user data so that it
resides in a location pointed to by the newly applicable policy definition.
Consider the following situation and then the possible solutions:
Situation:
such that the disk storage is always available to the student as they are promoted and
move from school to school in the district. Servers are located in each school with T-1
connectivity back to the district office. The data needs to be on the server at the school
that each student attends.
Solution 1: Create a hierarchy in eDirectory such that each school is represented by its
own container. Create a policy for each school and assign it to the school container and
configure it so that it points to the server at the school. Create the students in the
appropriate container based on the school. When students are promoted, say from Middle
School A to High School A, move the user objects to High School A’s container and their
data will move from the server at the middle school to the server at the high school. This
will happen automatically with no backfill required since object moves trigger policy
reevaluation and application.
Solution 2: Create a flat structure in eDirectory where all user objects live. Create a
group representing each school. Create a policy for each school and assign it to the school
group. Add the students to the appropriate group based on their school. When students are
promoted, remove them from one school’s group and add them to another school’s group.
When you are ready for the data to move for a particular school, perform a backfill on the
group. The policy for the school will be applied and the data will be moved to the new
school server. This method is advantageous since it allows us to maintain a flat Directory
and have some manual control over the data move process.
Solution 3: Create a flat structure in eDirectory where all user objects live. Create a
policy for each school and point it to the server at the associated school. Set the policy
attribute on the user as a part of your provisioning process, perhaps a DirXML driver
connected to the student database. Then as users are promoted, the driver sets the policy
attribute to point to the new school. File System Factory™ acts on this event by applying
the new policy and moving the user data automatically to the new school server.
A school district would like to provide network disk storage for all students
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
81
Page 83

Backfill “Enforce Paths” Mode
During a full backfill operation, the administrator has the capability of selecting the
“Enforce Paths” option. This option will instruct File System Factory™ to fully analyze
the location of each user’s home directory. If the directory is not in a location pointed to
by the applicable policy, the data is moved to a location specified by the policy.
This is a very powerful feature of File System Factory™ in that it may be used to move
user data to a different volume or server.
Consider the following 2 “Enforce Paths” scenarios:
Scenario #1:
Bob has home directories for 20,000 users on 8 NetWare 4.11 servers. He would like to
move everyone to a new set of 4 NetWare 6.0 servers.
Bob should create a File System Factory™ policy that points to the 4 NetWare 6.0
servers. He should then assign that policy to the containers holding the user objects.
Finally, he should perform a full backfill operation against the containers using the
“Enforce Path” option.
All users home directories will be moved from the 4.11 servers and load balanced across
the 6.0 servers. All trustee assignments and file system attributes will be moved
seamlessly. Bob can even define a schedule for the migration and set bandwidth throttling
parameters so that network and server performance will not be affected during normal
business hours. See the section on scheduling below for more information.
Scenario #2:
Ann is the administrator of a network with 7,500 employee user accounts. Ann has not
given the majority of her user’s home directory storage. She would like to do this now
using 5 NetWare 5.1 servers that she runs. She is somewhat hesitant about doing this now
given that she anticipates installing a 3-node NetWare 6.0 server cluster connected to a
SAN in about eight months.
Part 1: Ann should not wait. She should define a Policy pointing to her 5.1 servers. Then
associate the policy with her users. Lastly, she should issue a full backfill operation
against the containers holding her users. In a flash, all of her users will have managed
disk storage on the network where they can be productive for the next eight months.
Part 2: Eight months later, Ann has her new cluster and SAN installed. She should then
modify her Policy that she defined in Part 1 above by adding path definitions so that it
points to the SAN-connected cluster. She should remove the path pointers to the 5.1
servers. Finally, she should run a full backfill operation against the user containers using
the “Enforce Path” option.
All user home directories will be moved from the 5.1 servers to the SAN-connected
cluster seamlessly. Ann can then decommission the 5.1 servers or use them for some other
purpose.
Scheduling and Throttling
During a full backfill operation, particularly against a container or large group, the
resulting application of changes in policy associations has the potential to move large
amounts of data. In some environments, this may detrimental to the network, especially at
certain times of certain days.
Given the school scenario above where data is being moved between schools over T-1
connections, it is feasible to expect that this operation could use all of the bandwidth
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
82
Page 84

available, leaving little for another work that might need to go occur. To combat this
problem, each File System Factory™ policy has a configurable throttle attribute that is
used during data migration to limit bandwidth usage.
While the throttle attribute is very useful, there may be times of the day on certain days of
the week when the administrator does not want data to migrate. In the policy definition,
the administrator has the capability of selecting the times that are valid for moving data.
This configuration is granular to the hour and is represented for each day of the week.
Therefore, the administrator could define a policy where data migrations only occur on
the weekend and Tuesday and Thursday between 1 am and 5 am.
“Seamless” Data Movement
Moving data on the network is a non-trivial operation. It must be conducted in such a
manner to ensure that the user that owns the data and the integrity of the data itself is not
impacted.
Simply copying the data to the new location and deleting the data in the old location is not
good enough. What if files are open during the move process or the user is logged in or
logs in during the process? What if others share access to the storage? How is the user
cognizant of the fact that a migration of his files is in progress?
File System Factory™ contains safeguards to ensure “seamless” migration of the data by
taking the necessary precautions to avoid these and other situations and educate the user
about the migration process.
For example, File System Factory™ will defer migration of data for a user that is logged
in to the server holding the home directory until the user is no longer logged in. Once
migration begins the user’s Home Directory attribute will be temporarily changed to point
to a PROXY location that contains information about the move process.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
83
Page 85

22 Release Notes
The following are the release notes:
• Countries, Localities and Domains are now supported.
• If Organizations and Organizational Units which have a File System Factory™
policy applied are moved or renamed, a backfill operation will have to be
performed to restore continuity in File System Factory™.
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
84
Page 86

[End of Document]
Novell File System Factory™ Administrator’s Guide
© 2002-2005 Condrey Consulting Corporation. All Rights Reserved.
85
 Loading...
Loading...