Page 1

Publication#:
Document Release:
Release Date:
PeriProducer CTI T oolkit User’s Guide
for M1
(Peri-IPML V2.1)
P0606089
1.1
October 17, 2003
Page 2

PeriProducer CTI Toolkit User’s Guide for M1
Page ii Nortel Networks Confidential # P0606089 Ver: 1.1
Important Notice
Nortel Networks reserves the right to make cha nges in the content s of this publ icat ion
including functions and specifications identified herein without notice.
The material contained in this document is intended for Nortel Networks Certified
personnel and licensed customers with a non-disclosure agreement or standard
contract.
In the absence of a written agreement to the contrary, Nortel Networks assumes no
liability for applications assistance, customer’s product/application/concepts, or
infringements of patents or copyrights of third parties arising from the use of systems
and architectures described herein. Nor does Nortel Networks warrant or represent
that any license, either expressed or implied, is granted under any patent right,
copyright, or other combina tion of technolo gy, archit ecture, or soft ware as mi ght be or
is already in use.
This document should not be reproduced, disseminated, or otherwise disclosed
without prior written consent from an officer of Nortel Networks.
This document has been copyrighted by Nortel Networks and may not be duplicated.
Copyright © 2003 Nortel Networks, All Rights Reserved
Page 3

Table of Contents
# P0606089 Ver: 1.1 Nortel Networks Confidential Page iii
Table of Contents
Preface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . v
Scope . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . vi
Intended Audience . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . vi
How To Use This Manual . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . vi
Organization of This Manual . . . . . . . . . . . . . . . . . . . . . . . . . . . vii
Conventions Used in This Manual . . . . . . . . . . . . . . . . . . . . . . . viii
Solaris and Windows 2000 Conventions . . . . . . . . . . . . . . . . . . . ix
Trademark Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ix
Overview of CTI Features . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Overview of CTI Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
Toolkit Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
CTI, RSM, TAPI, and TAPISCCS Blocks. . . . . . . . . . . . . . 13
Toolkit Usage for Specific Product Features . . . . . . . . . . . . . . . . 15
Product Features and Resources . . . . . . . . . . . . . . . . . . . . . . 15
Product Features Application Development. . . . . . . . . . . . . 15
Toolkit Installation and Removal Procedures . . . . . . . . . . . 21
Installing and Removing the Toolkit on Windows 2000
Systems . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Link Server Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Installing the CTI Toolkit. . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Removal of the CTI Toolkit on 2000 . . . . . . . . . . . . . . . . . . 22
Installation of the CTI Toolkit on Solaris Systems . . . . . . . . . . . 23
Link Server Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Installing the CTI Toolkit. . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Removal of the CTI Toolkit on Solaris . . . . . . . . . . . . . . . . 24
Adding the CTI Folders and Data Cards . . . . . . . . . . . . . . . . . . . 25
CTI Toolkit Blocks Reference . . . . . . . . . . . . . . . . . . . . . . . . 27
CTI Toolkit Blocks Reference . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
CTI Programming . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Configuration Requirements. . . . . . . . . . . . . . . . . . . . . . . . . 28
Folders and Data Cards. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Error Condition Handling. . . . . . . . . . . . . . . . . . . . . . . . . . . 28
CTI Toolkit Blocks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Agent Function . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
CTI Initialize. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Device Parameter Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Register Device. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Set Event Handling. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
Telephony Event Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Page 4

PeriProducer CTI Toolkit User’s Guide for M1
Page iv Nortel Networks Confidential # P0606089 Ver: 1.1
Telephony Request . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
User Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Device Statistics Data. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
Send TAPI Call Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
Send TAPI SCCS Call Data . . . . . . . . . . . . . . . . . . . . . . . . . 51
GetTAPIData . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
CSTAPILS Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
Log Message. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Example Applications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
Example Applications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
Agent Function . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
CTI Initialize . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
Device Parameter Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
Register Device . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
Set Event Handling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
Telephony Event Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
Telephony Request . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 65
User Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 68
Device Statistics Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
Send TAPI CallData/Send TAPIsccs CallData . . . . . . . . . . . . . . 70
Log Message . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
Example Log Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73
Example Log Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
Agent Function CSVAPI Log File . . . . . . . . . . . . . . . . . . . . . . . . 74
CTI Initialize CSVAPI Log File . . . . . . . . . . . . . . . . . . . . . . . . . 74
Register Device CSVAPI Log File . . . . . . . . . . . . . . . . . . . . . . . 74
Set Event Handling CSVAPI Log File . . . . . . . . . . . . . . . . . . . . 75
Telephony Event Data CSVAPI Log File . . . . . . . . . . . . . . . . . . 76
Telephony Request CSVAPI Log File . . . . . . . . . . . . . . . . . . . . . 78
User Data CSVAPI Log File . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
Device Statistics Data CSRSM and CSRSMLS Log Files . . . . . 86
Send TAPI Call Data CSTAPI and CSTAPILS Log Files . . . . . 89
Send TAPI SCCS Call Data CSTAPI and CSTAPILS
Log Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92
Log Message Example Application Log File . . . . . . . . . . . . . . . 95
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
Glossary of CTI Terminology . . . . . . . . . . . . . . . . . . . . . . . 101
Page 5

Preface
Page 6

PeriProducer CTI Toolkit User’s Guide for M1
Page vi Nortel Networks Confidential # P0606089 Ver: 1.1
Scope
The PeriProducer CTI Toolkit User’s Gu ide for M1 document provides product
descriptions, installation procedures, and usage information for using the CTI Toolkit
to develop applications for Nortel Networks Media Processing Server (MPS)
platforms.
In this document, Nortel Networks MPS (MPS500 and MPS1000) systems are both
referred to as Processing Server (PS) systems or Interactive Voice Response (IVR)
systems.
Intended Audience
This document is intended to assist CTI applic at ion developers with using the CTI
T oolkit . Knowle dge of conf igurati on settings of eleme nts withi n a Call Center , such as
a PBX, and application development is recommended.
How To Use This Manual
This manual uses many standard terms relating to computer system and software
application functions. However, it contains some terminology that can only be
explained in the context of the MPS system. Refer to the Glossary of MPS
Terminology for definitions of MPS specific terms.
Initially, you should read this manual at least onc e, fr om sta rt to fi ni sh. Lat er, you can
use the Table of Contents to locate topics of interest for reference and review.
If you are reading this document online, use the cross-reference links (shown in blue)
to quickly locate related topics. <L
EFT> click once with your mouse while positioned
with your cursor over the cross-reference link. Click on any point in a Table of
Contents entry to move to that topic. Click on the page number of any Index entry to
access that topic page.
T o familiar ize yourself with va rious special ized textual ref erences withi n the manual, ,
see Conventions Used in This Manual on page viii.
Periphonics is part of Nortel Networks. The name Peripho nics, an d varia tions the reof,
appear in this manual only where it is referred to in a product. (For examples, a
PeriProducer application, the
PERImps package, the perirev command, etc.)
Page 7

Preface
# P0606089 Ver: 1.1 Nortel Networks Confidential Page vii
Organization of This Manual
This manual is separated into chapters that describe the installation, configuration, and
usage of the CTI Toolkit.
Chapter 1 — Overview of CTI Features
A description of the CTI functions and an overview of the PeriProducer CTI Toolkit.
Chapter 2 — Toolkit Installation and Removal Procedures
Detailed instructions for installating and removing the CTI Toolkit on the Windows
platform.
Chapter 3 — CTI Toolkit Blocks Reference
Detailed usage instructions for all the CTI Toolkit blocks.
Appendix A — Example Applications
References to example applications that demonstrate the use of each CTI Toolkit
block and their major functions.
Appendix B — Example Log Files
Examples of log file output from each of the CTI Toolkit blocks.
Page 8
PeriProducer CTI Toolkit User’s Guide for M1
Page viii Nortel Networks Confidential # P0606089 Ver: 1.1
Conventions Used in This Manual
This manual uses different fonts and symbols to differentiate between document
elements a nd types of information. These c onventions are summarized in th e
following table.
Conventions Used in This Manual page 1 of 2
Notation Description
Normal text
Normal text font is used for most of the document.
important term
The Italics font is used to introduce new terms, to highlight
meaningful words or phrases, or to distinguish specific term s from
nearby text.
system
command
This font indicates a sy st em com mand and/or its argume nt s . Suc h
keywords are to be entered exactly as shown (i.e., users are not to
fill in their own values).
command,
condition
and alarm
Command, Condition and Alarm references appear on the screen
in magenta text and reference the Command Reference Manual,
the PeriProducer User’s Guide, or the Alarm Reference Man ual,
respectively. Refer to these documents for detailed information
about Commands, Conditions, and Alarms.
file name /
directory
This font is used for highlig hting the names of disk directories , files,
and extensions for file names. It is also used to show displays on
text-based screens (e.g., to show the contents of a file.)
on-screen field
This font is used for field labels, on-screen menu buttons, and
action buttons.
<KEY NAME>
A term that appears within angled brackets denotes a terminal
keyboard key, a telephone keypad button, or a system mouse
button.
Book Reference
This font indicates the names of other publications referenced
within the document.
cross refer ence
A cross reference appears on the screen in blue text. Click on the
cross reference to access the referenced location. A cross
reference that refers to a section name accesses the first page of
that section.
The Note icon identifies notes, important facts, and other keys to
understanding.
!
The Caution icon identifies procedures or events that require
special attention. The icon indicates a warning that serious
problems may arise if the stated instructions are improperly
followed.
Page 9

Preface
# P0606089 Ver: 1.1 Nortel Networks Confidential Page ix
Solaris and Windows 2000 Conventions
This manual depicts examples (command line syntax, configuration files, and screen
shots) in Solaris format. In certain instances Windows 2000 specific commands,
procedures, or screen shots are shown where required. The following table lists
examples of general operating system conventions to keep in mind when using this
manual with either the Solaris or 2000 operating system.
Trademark Conventions
The following trademark information is presented here and applies throughout for
third party products discussed within this manual. Trademarking information is not
repeated hereafter.
Solaris is a tr adema rk or r egist ered trade mark of Su n Micro systems , Inc. in t he United
States and other countries.
Microsoft, W indows, W i ndows 2000, Inte rnet Explore r , and the Fly ing W indows logo
are either trademarks or registered trademarks of Microsoft Corporation.
Netscape
®
and Netscape Navigator® are registered trademarks of Netscape
Communications Corporation in the United States and other countries. Netscape’s
The flying Window icon identifies procedures or events that apply
to the Windows operating system only.
a
The Solaris icon identifies procedures or events that apply to the
Solaris operating system only.
b
a. Windows 2000 and the flying Window logo are either trademarks or registered
trademarks of the Microsoft Corp orat ion .
b. Solaris is a trademark or registered trademark of Sun Microsystems, Inc. in the
United States and other countries.
Conventions Used in This Manual page 2 of 2
Notation Description
Solaris Windows 2000
Environment $VPSHOME %VPSHOME%
Paths $VPSHOME/common/etc %VPSHOME%\common\etc
Command <command> & start /b <command>
Page 10

PeriProducer CTI Toolkit User’s Guide for M1
Page x Nor tel Networks Confidential # P0606089 Ver: 1.1
logos and Netscape product and service names are also trademarks of Netscape
Communications Corporation, which may be registered in other countries.
Page 11
This chapter covers:
Overview of CTI
Features
1. CTI Description
2. Toolkit Overview
3. Product Features and Resources
Page 12

PeriProducer CTI Toolkit User’s Guide for M1
Page 12 Nortel Networks Confidential #P0606089 – Ver: 1.1
Overview of CTI Features
The PeriProducer package with Computer Telephony Integration (CTI) Toolkit is a
development environment for crea ti ng Interactive Voice Response (IVR) applications
to use with the Peri-IPML or PeriICM software. With PeriProducer and the CTI
Toolkit, users can create CTI applications without having specific knowledge of the
low-level functions of phone systems or IVR programming.
The CTI Toolkit version 2.1.0 is compatible with PeriProducer version 3.0 and
above.
CTI and PeriProducer use a graphical user interface (GUI) with icons, drag-and-drop
placement, pull-down menus, fill-in-the-blanks data entry, default parameter values,
and other features that make application development straightforward. The various
application functions are represented with icons (referred to as blocks). The
application is constructed by selecting and sequencing the blocks. The completed
application is represented by the graphical layout of the blocks both during
development and at run time.
The CTI Toolkit is used to create customer-specific applications to interface with the
M1-Meridian Link, SCCS Interface (RSM & HDX), and IVR.DLL for the TAPI
server. Using the CTI Toolkit , fu nctions from specific swit che s (PBXs) ar e accessible
to PeriProducer applications. During the run of an application, PeriProducer executes
a function and the system software translates the requests in to a format the P BX can
process. Messages from the PBX are translated by the syste m into a format that
applications can interpret.
Page 13
Overview of CTI Features
#P0606089 – Ver: 1.1 Nortel Networks Confidential Page 13
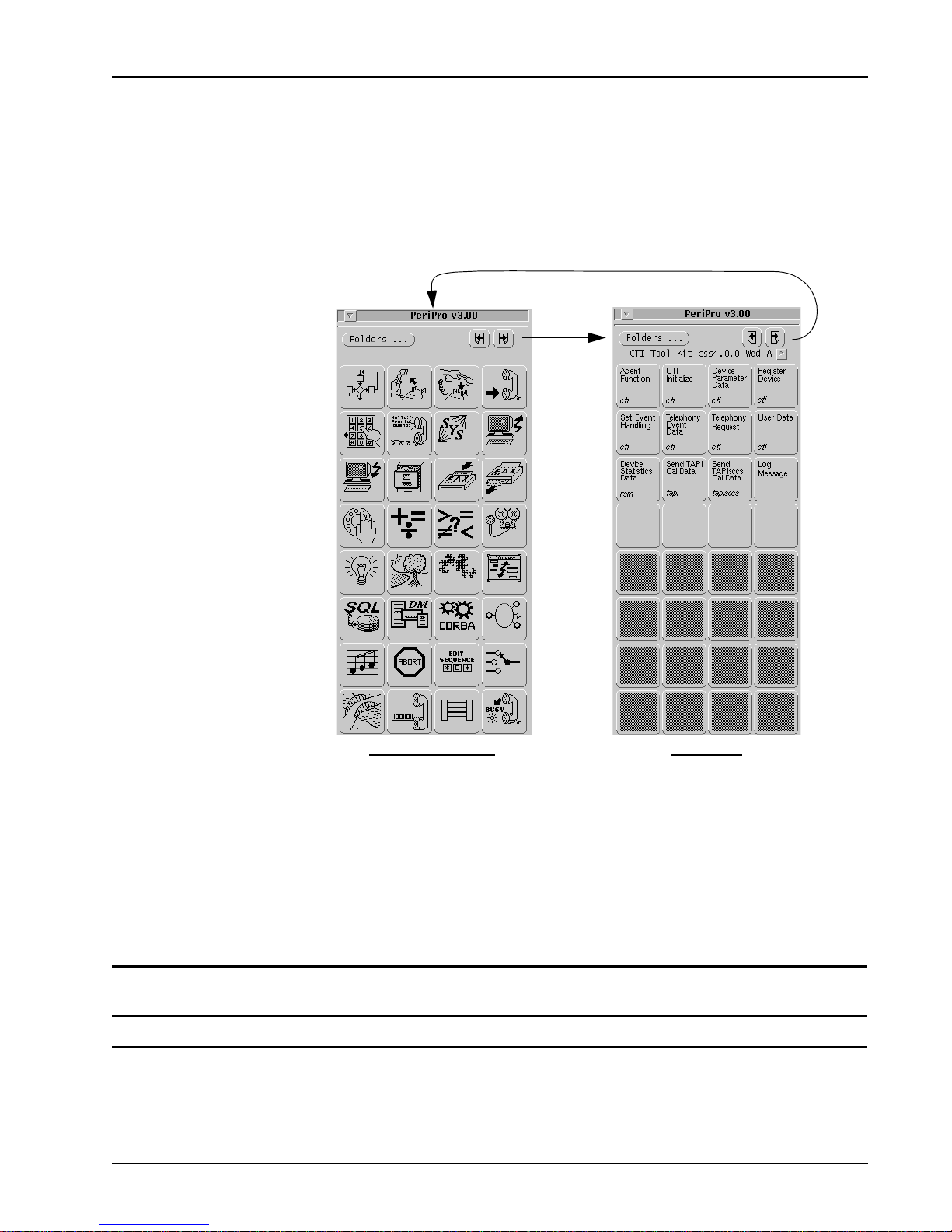
Toolkit Overview
The CTI Toolkit allows access to functions that are specific to CTI programming.
These functions are not accessible from the standard PeriProducer Toolkit.
The arrows in the upper right corner of each Toolkit switch between the CTI and the
PeriProducer Toolkit (and any other Toolkit installed).
Brief descriptions of the CTI Toolkit blocks follow. Detailed descriptions are in
chapter 3, CTI Toolkit Blocks Refe rence. The Per iProducer Toolkit i s descri bed in the
PeriProducer User’s Guide.
CTI, RSM, TAPI, and TAPISCCS Blocks
PeriProducer Too lkit CTI Toolkit
Block Resource Description
$JHQW)XQFWLRQ
CTI Sets the Agent’s state, for example: Login, Ready, Work Not Ready,
Logout, etc. See page 30.
&7,,QLWLDOL]H CTI Initializes handlers for CTI-related conditions. See page 32.
'HYLFH
3DUDPHWHU'DWD
CTI Retrieves all Device Parameter data, based on the Device name (this is
determined by Nortel Networks Certified personnel) and Parameter name,
passed as parameters. See page 33.
Page 14

PeriProducer CTI Toolkit User’s Guide for M1
Page 14 Nortel Networks Confidential #P0606089 – Ver: 1.1
5HJLVWHU'HYLFH
CTI Registers/unregisters a device with CTI resources. This tool is used when
the application needs to receive events for the specified device. See
page 35.
6HW(YHQW
+DQGOLQJ
CTI Specifies how events are handled. There are three options:
•
Wait: The application waits until the event occurs. When using
this option, no conditions are generated.
•
CtiCond: The application receives a CtiCond condition when
the event occurs.
•
Ignore: The application ignores the event.
See page 37.
7HOHSKRQ\(YHQW
'DWD
CTI Retrieves the specified event data and places the data into a CTI folder. See
page 40.
7HOHSKRQ\
5HTXHVW
CTI Answers, initiates, transfer, or releases a call. See page 42.
8VHU'DWD CTI Adds, removes, or retrieves CallData/TLink data from or to a CTI folder.
See page 45.
'HYLFH6WDWLVWLFV
'DWD
RSM Retrieves data for a statistics group, specifically one of "AgentItd",
"AgentMwnd", "ApplicIPtd", "ApplicMwnd", "SkillItd", or "SkillMwnd"
based on the Statistics Device name (this is determined by Nortel Networks
Certified personnel) and Statistics Group, passed as parameters. See
page 47.
6HQG7$3,&DOO
'DWD
TAPI Sends values in array, CTI.AVCalldata.AVpairs to Resource
Symposium TAPI Server (TAPI). See page 50.
*HW7$3,'DWD TAPI Gets data from Symposium TAPI Server based on Call ID. See page 52.
6HQG7$3,6&&6
&DOO'DWD
TAPISCCS Sends values in array, CTI.AVCalldata.AVpairs to Symposium Call
Center Server TAPI interface (TAPISCCS). Also known as IVR.DLL
interface. This block is used only in the DMS SCCS environment. See
page 51.
/RJ0HVVDJH Misc. Prints a message, with TimeStamp, to a log file designated for the
application’s line. See page 53.
Block Resource Description
Page 15

Overview of CTI Features
#P0606089 – Ver: 1.1 Nortel Networks Confidential Page 15
Toolkit Usage for Specific Product Features
The following sections provide information to determine the best CTI tool(s) to use
when designing an application for a particular product feature or resource.
Product Features and Resources
The table below correlates product features, CTI resources, and Toolkit blocks.
Product Features Application Development
The following table shows which Toolkit blocks to use for accessing CTI product
features. For each feature, references are made to example applications that illustrate
the use of these blocks. Blocks that are part of the standard PeriProducer Toolkit are
Product Feature Resource Toolkit Blocks
Peri-IPML (M1) CTI
$JHQW)XQFWLRQ (page 30)
&7,,QLWLDOL]H (page 32 )
'HYLFH3DUDPHWHU'DWD (page 33)
5HJLVWHU'HYLFH (page 35)
6HW(YHQW+DQGOLQJ (page 37)
7HOHSKRQ\(YHQW'DWD (page 40)
7HOHSKRQ\5HTXHVW (page 42)
8VHU'DWD (page 45)
Call Data Attachment CTI
8VHU'DWD (page 45)
IVR-SCCS (CS-HDX) CTI
8VHU'DWD (page 45)
IVR-SCCS (RSM) rsm 'HYLFH6WDWLVWLFV'DWD (page 47)
IVR-SCCS
(IVR-DLL interface)
tapisccs
6HQG7$3,6&&6&DOO'DWD (page 51)
IVR-TAPI tapi
6HQG7$3,&DOO'DWD (page 50)
Page 16

PeriProducer CTI Toolkit User’s Guide for M1
Page 16 Nortel Networks Confidential #P0606089 – Ver: 1.1
documented in the PeriProducer User’s Guide.
Product Feature / Function / Toolkit Blocks
Example
Apps
Peri-IPML/M1 l ink
or SCCS
Login/Logout the IVR agent ports under IVR application control.
Logon IVR Port
1. &7,,QLWLDOL]Hpage 32
2. (QYLURQPHQW
3. +DQGOH
4. $JHQW)XQFWLRQpage 30
AF-8 (page 57)
Logoff IVR Port
(Same as above, followed by another $JHQW)XQFWLRQ.)
AF-8 (page 57)
Retrieve call information such as Current Locati on, Calling Line ID, DNIS, IVR T reatmen t DN,
and Call Arrival Time.
Get ANI
1. &7,,QLWLDOL]Hpage 32
2. (QYLURQPHQW
3. +DQGOH
4. $QVZHU
5. 6HW(YHQW+DQGOLQJpage 37
6. 7HOHSKRQ\(YHQW'DWDpage 40
TE-2 (page 63)
Get DNIS
1. &7,,QLWLDOL]Hpage 32
2. (QYLURQPHQW
3. +DQGOH
4. $QVZHU
5. 6HW(YHQW+DQGOLQJpage 37
6. 7HOHSKRQ\(YHQW'DWDpage 40
TE-2 (page 63)
Get IVR Treatment
1. &7,,QLWLDOL]Hpage 32
2. (QYLURQPHQW
3. +DQGOH
4. $QVZHU
5. 6HW(YHQW+DQGOLQJpage 37
6. 8VHU'DWDpage 45
UD-4 (page 68)
Get Arrival Time
1. &7,,QLWLDOL]Hpage 32
2. (QYLURQPHQW
3. +DQGOH
4. $QVZHU
5. 6HW(YHQW+DQGOLQJpage 37
6. 8VHU'DWDpage 45
UD-4 (page 68)
Page 17
Overview of CTI Features
#P0606089 – Ver: 1.1 Nortel Networks Confidential Page 17
Peri-IPML/M1 link
or SCCS (continued)
Perform Consultation Transfer - Initiate and Complete Two Step Transfer. IVR application
initiates the transfer, places the caller on hold, and the connects the IVR to the destination
DN. When the complete transfer is issued, the caller is connected to the Destination DN and
the IVR port is disconnected.
Initiate Two-Step Transfer
1. &7,,QLWLDOL]Hpage 32
2. (QYLURQPHQW
3. +DQGOH
4. $QVZHU
5. 6HW(YHQW+DQGOLQJpage 37
6. 7HOHSKRQ\5HTXHVWpage 42
TR-4 (page 65)
Complete Two Step Transfer
(Same as above followed by another 7HOHSKRQ\5HTXHVW.)
TR-4 (page 65)
Perform Blind Transfer (one-step Transfer) – When the transfer is completed, the Caller is
connected to the destination DN and IVR is disconnected.
Initiate Blind Transfer
1. &7,,QLWLDOL]Hpage 32
2. (QYLURQPHQW
3. +DQGOH
4. $QVZHU
5. 6HW(YHQW+DQGOLQJpage 37
6. 7HOHSKRQ\5HTXHVWpage 42
TR-2 (page 65)
Perform Consultation Conference - Initiate and Complete Conference. IVR application
initiates the conference, places the caller on hold, and connects the IVR to the destination
DN. When the complete conferenc e is is sue d, the ca lle r is conn ec ted to the Desti nation DN
and the IVR port.
Initiate Conference
1. &7,,QLWLDOL]Hpage 32
2. (QYLURQPHQW
3. +DQGOH
4. $QVZHU
5. 6HW(YHQW+DQGOLQJpage 37
6. 7HOHSKRQ\5HTXHVWpage 42
TR-3 (page 65)
Complete Conference
(Same as above followed by another 7HOHSKRQ\5HTXHVW.)
TR-3 (page 65)
Retrieve held Call by a Consultation Transfer or Consultation Conference.
Hold Call
1. &7,,QLWLDOL]Hpage 32
2. (QYLURQPHQW
3. +DQGOH
4. $QVZHU
5. 6HW(YHQW+DQGOLQJpage 37
6. 7HOHSKRQ\5HTXHVWpage 42
TR-5 (page 65)
Retrieve Call
(Same as above followed by another 7HOHSKRQ\5HTXHVW.)
TR-5 (page 65)
Product Feature / Function / Toolkit Blocks
Example
Apps
Page 18
PeriProducer CTI Toolkit User’s Guide for M1
Page 18 Nortel Networks Confidential #P0606089 – Ver: 1.1
IVR-SCCS
(CS-HDX links to
SCCS for
M1/DMS100)
The HDX (Host Data Exchange) interface sends info rma tio n to CSDA and waits for CSDA to
return information related to the sent information. For example, the SCCS can send an
account number to CSDA, and CSDA returns a skillset relevant to that account type.
Receive Call Data from SCCS
(Total Call Count/Average Wait Time)
1. &7,,QLWLDOL]Hpage 32
2. (QYLURQPHQW
3. +DQGOH
4. 'LVFRQQHFW
5. $JHQW)XQFWLRQpage 30
6. $QVZHU
7. 6HW(YHQW+DQGOLQJpage 37
8. 8VHU'DWDpage 45
UD-3 (page 68)
Send Call Data (Skills) to SCCS
1. &7,,QLWLDOL]Hpage 32
2. (QYLURQPHQW
3. +DQGOH
4. 'LVFRQQHFW
5. $JHQW)XQFWLRQpage 30
6. $QVZHU
7. 6HW(YHQW+DQGOLQJpage 37
8. 8VHU'DWDpage 45
UD-3 (page 68)
IVR-SCCS
(IVR-DLL Interface)
Provides application data to SCCS from IVR system.
Send Call Data to SCCS/IVR.DLL
1. &7,,QLWLDOL]Hpage 32
2. (QYLURQPHQW
3. +DQGOH
4. 'LVFRQQHFW
5. $JHQW)XQFWLRQpage 30
6. $QVZHU
7. 6HW(YHQW+DQGOLQJpage 37
8. 6HQG7$3,6&&6&DOO'DWDpage 51
ST -1 (page 70)
IVR-SCCS (CS-RSM
links to SCCS for
M1)
Provides Skillset, Applicat ion, Agent Statisti cs from SCCS to the IVR appl ication. Info rmatio n
flow is one way, from the SCCS to the IVR application.
Receive Skill Stats from SCCS/RSM
1. &7,,QLWLDOL]Hpage 32
2. (QYLURQPHQW
3. +DQGOH
4. 'LVFRQQHFW
5. $JHQW)XQFWLRQpage 30
6. $QVZHU
7. 6HW(YHQW+DQGOLQJpage 37
8. 'HYLFH6WDWLVWLFV'DWDpage 47
DS-1 (page 69)
Product Feature / Function / Toolkit Blocks
Example
Apps
Page 19

Overview of CTI Features
#P0606089 – Ver: 1.1 Nortel Networks Confidential Page 19
IVR-TAPI (TAPI
Server CSTAPI
Links for M1)
IVR T API allo ws IVR a pplic ations to send c all da ta t o TAPI server fo r scree n pop s. It uses t he
IVR.DLL socket inte rface. T he IVR applicati on atta ches Ca ll Da ta t o the D N using cstapils
process. The IVR Applications sends Call Data Attachment Request to cstapi and then
from cstapi to cstapils. cstapils does not store the request, it creates an IVR Caller
Data message and sends it to the TAPI Server. The Call Data is stored in the TAPI Server
until SCCS has routed the c all to an agen t. The data flow is on e way, from the IVR app lication
to the TAPI Server.
Send Call Data to Symposium TAPI Server/IVR.DLL
1. &7,,QLWLDOL]Hpage 32
2. (QYLURQPHQW
3. +DQGOH
4. 'LVFRQQHFW
5. $JHQW)XQFWLRQpage 30
6. $QVZHU
7. 6HW(YHQW+DQGOLQJpage 37
8. 6HQG7$3,&DOO'DWDpage 50
ST -1 (page 70)
Product Feature / Function / Toolkit Blocks
Example
Apps
Page 20

PeriProducer CTI Toolkit User’s Guide for M1
Page 20 Nortel Networks Confidential #P0606089 – Ver: 1.1
Page 21
This chapter covers:
Toolkit Installation and
Removal Procedures
1. Install ation of the CTI T oolkit for W indows 2000
and Solaris
2. Removal of the CTI Toolkit for Windows 2000
and Solaris
3. Adding the CTI Folders and Data cards
Page 22

PeriProducer CTI Toolkit User’s Guide for M1
Page 22 Nortel Networks Confidential # P0606089 Ver: 1.1
Installing and Removing the Toolkit on Windows 2000 Systems
Installation of t he CTI Toolkit on a Windows 2000 syste m can onl y be pe rf ormed by a
user with Administrator privileges.
Link Server Configuration
First, the 2000 server running the Peri-IPML, Peri-ICM, IVR TAPI, and IVR SCCS
(or Link Server) must have the latest patches installed. The file
PERIrel5Patch_Bundle_XX.exe contains the required patches (where XX
denotes the latest patch bundle) and is found on the CD in the
Patches-nt
directory.
Next, the
vrc.vrp and services files, located on the Link Server must be the
same as the
vrc.vrp and services files on all the MPS systems. For detailed
instructions describing how to copy the
vrc.vrp and services files to the Link
Server, see the MPS Interface to M1 document.
Finally, the machine(s) running the PeriProducer application development tool must
contain the latest PeriProducer patch(es) (which includes the
ppro.conf file).
Installing the CTI Toolkit
Perform the following steps:
1. Insert the CD into the drive. Locate and open the
PERIctitk-nt
directory.
2. Click
Setup.exe to run the installation.
3. When the Installation Complete message appears, the CTI Toolkit
installation process is finished.
To use the CTI Toolkit, s tar t Peri Pro duce r. Then cl ick the left arrow in the upp er r ig ht
hand corner of the Toolkit window until the CTI Toolkit becomes active.
Removal of the CTI Toolkit on 2000
You do not need to uninstall the previous Toolkit before installing a new version on
2000 systems. When upda ting the CTI To olkit on a 2 000 syste m, any pr evious Toolk it
program and configuration files are automatically overwritten by the new version.
(PeriProducer application and
vex files are preserved.)
To remove the CTI Toolkit:
1. Open the Windows Control Panel and launch the Add/Remove Programs
utility.
2. Highlight
PERIctitk and click ADD/REMOVE.
Page 23

Toolkit Installation and Removal Procedures
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 23
3. Confirm the uninstallation by clicking Yes.
4. When the message "Uninstall sucessfully completed" appears, the CTI
Toolkit is uninstalled. Click OK.
Installation of the CTI Toolkit on Solaris Systems
Installation of the CTI Toolkit on a Solaris system can only be performed by a user
with superuser privileges .
When updating the CTI Toolkit on a Solaris system, existing Toolkit program and
configuration files are not automatically overwritten. It is necessary to explicitly
uninstall the previous Toolkit when installing a new version on Windows systems.
(See Removal of the CTI Toolkit on Solaris on page 24.)
Link Server Configuration
First, the server running the Peri-IPML, Peri-ICM, IVR TAPI, and IVR SCCS
products (referred to as the "Link Server"), must have the latest patches installed.
Next, the
vrc.vrp and services files, located on the Link Server must be the
same as the
vrc.vrp and services files on all the VPS/is systems. F or detailed
instructions describing how to copy the
vrc.vrp and services files to the Link
Server, see the MPS Interface to M1 manual.
Finally, the machine(s) running the PeriProducer application development tool must
also contain the latest PeriProducer patch(es) (which includes the
ppro.conf file).
Installing the CTI Toolkit
To install the CTI Toolkit on a Solaris system, use the FTP uti l it y to copy the package
from the CD of Windows 2000 machine to the Solaris machine.
1. From a DOS prompt on a Windows 2000 machine,
cd to the
PERIctitksolaris directory on the CD.
2. Enter
ftp hostname (where hostname is the name of the Solaris node)
3. Change the directory to:
temp
4. Enter bin
5. Enter put PERIctitk.tar.Z (for the package)
6. Issue the following commands (as shown below) to uncompress and untar
the
PERIctitk-solaris package:
pkginfo | grep PERIctitk
uncompress PERIctitk.tar.Z
tar -xvf PERIctitk.tar
Page 24

PeriProducer CTI Toolkit User’s Guide for M1
Page 24 Nortel Networks Confidential # P0606089 Ver: 1.1
The monitor will show several screens of output. Wait for the command
prompt to return.
7. Enter
pkgadd -d . PERIctitk to install the CTI Toolkit. The monitor
will show several screens of output.
8. The following confirmation message will appear:
Do you want to continue with the installation of
<PERIctitk> [y,n,?] y
Enter Y
9. After the pa ckage is installed, the following message appea r s:
Installation of <PERIctitk> was successful.
10. Reboot the machine.
11. Enter the following command to ensure the CTI Toolkit exists on the
system:
pkginfo | grep PERIctitk
The following message should appear:
application PERIctitk CallSPONSOR CTI PERIPRO TOOLS
Removal of the CTI Toolkit on Solaris
Perform the following steps to uninstall the CTI Toolkit from a Solaris system.
1. Enter the following command to remove the CTI Toolkit from the system:
pkgrm PERIctitk
2. One or more confirmation messages such as the following will appear:
Do you want to remove this package? y
Enter Y to all confirmation prompts.
3. The following message should appear:
Removal of <PERIctitk> was successful.
Page 25

Toolkit Installation and Removal Procedures
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 25
Adding the CTI Folders and Data Cards
To manipulate data with the blocks of the CTI Toolkit, the CTI folder must first be
installed. The CTI folder is a hierarchy of folders, subfolders, and data cards that are
used to transfer data to and from CTI specific resources.
The include folders path is determined by the environment variable PPROPATH,
which is automatically set during installation. PPROPATH contains a list of directory
names separated by semicolons. The directories are searched in the order they are
listed.
Before adding the CTI folders, modify the PPROPAT H variable to include the
$
PPROHOME/ctitools and $PPROHOME/ctitools/folders directories.
To view the current PPROPATH value, issue the following command:
echo $PPROPATH
The CTI.resource data card defaults to cti. If the CTI resource nam e is cti, the
CTI.resource data card does not have to be changed. Otherwise, the CTI.resource
data card ha s to be set to the name of the CTI res ource.
Gencti is useful if the CTI
resource name (VAPI’s service name) is different.
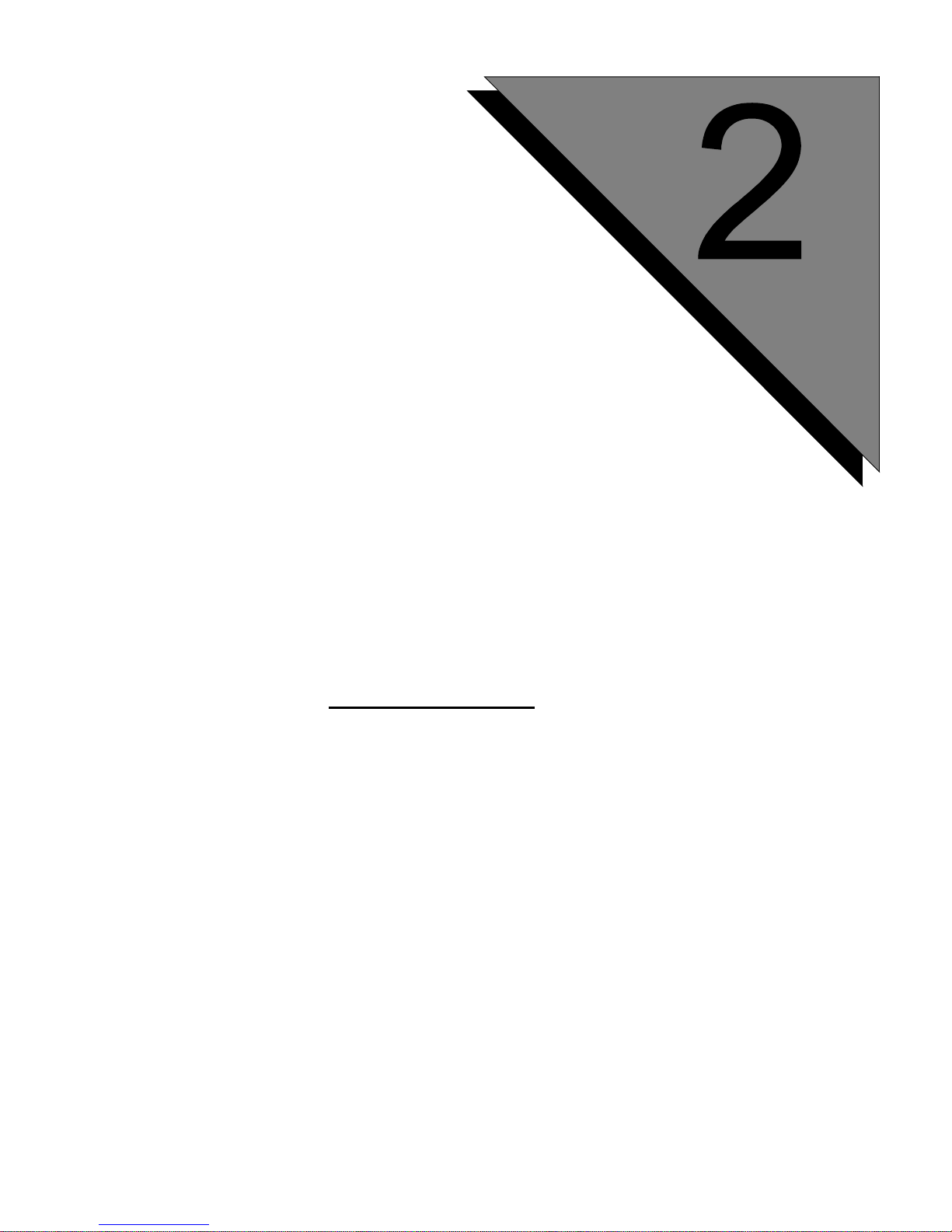
To import the CTI folder:
1. Click the Folders... bu tton i n the Toolkit window to display the Manage
Data Folders window. System is the default folder.
2. Add a CTI folder:
a. Remove
System from the Name field and type CTI.
Page 26
PeriProducer CTI Toolkit User’s Guide for M1
Page 26 Nortel Networks Confidential # P0606089 Ver: 1.1
b. Click
INCLUDE FILES and ADD to expand the CTI folder. CTI is
shown as the parent folder in the Available Folders panel.
3. Double-click on
CTI to displ ay the lower-level CTI entries in the
Current Folder panel.
Page 27
This chapter covers:
CTI Toolkit Blocks
Reference
1. CTI Toolkit
2. CTI Blocks
3. RSM Block
4. TAPI Block
5. TAPISCCS Block
Page 28
PeriProducer CTI Toolkit User’s Guide for M1
Page 28 Nortel Networks Confidential # P0606089 Ver: 1.1
CTI Toolkit Blocks Reference
This chapter describ es the f uncti ons of e ach CTI Tool kit bl ock. For mor e inf ormati on,
see Example Applications on page 56 and Example Log Files on page 74.
CTI Programming
Configuration Requirements
The following pertains to the development of PeriProducer CTI applications. See the
MPS Interfa ce to M1 manual for specific information about software configuration.
• To allow the ACD (M1 or SCCS) to transfer a call to an IVR port, that IVR
phone line must be configured in the switch as an agent phone.
• To allow call transfers to a live agent, the agent's ph one li ne also has to be set
up in the switch and/or SCCS to be part of an ACD queue or CDN (but
usually a different ACD queue or CDN than is used for IVR ports).
• All CDNs, queues, and IVR port agent phones must be register ed in the IP ML
using the Periview IPML Configuration tool as Agent Position IDs.
Folders and Data Cards
The following symbols indicate how data for each parameter is transferred within
each CTI block.
Although informat ion gathe red fro m calls is stor ed in s ystem fol ders, Nort el Networ ks
recommends that critical information be copied to local folders and data cards to
ensure that the data is not overwritten by other operations.
Error Condition Handling
Typically, when a block is executed, it makes data requests of the switch or SCCS
system. If a request succeeds, the application receives an
oc (output complete)
condition. If a request fails, the application receives an
of (output failure) condition.
These conditions are generated from CSVAPI for the set of CTI blocks, or from
CSTAPI for the two TAPI blocks. Normally, both the
oc and of conditions are
handled internally. However, they can be handled explicitly at the discretion of the
application developer.
Signifies that data is being sent to a data card.
Signifies that data is being received from a data card.
Page 29

CTI Toolkit Blocks Reference
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 29
You can also use a CTI.Status data card to determine whether a request succeeds or
fails. Afte r a block is executed, the value of the CTI.Status data card is assigned the
value 0 if the block’s execution was successful, or is set to a non-zero value if there
was a problem. Normally, applications must only check the value of CTI.status to
determine the success or failure of an operation such as transferring a call, receiving
data, etc.
In the case of a general failure (one which is not a direct result of executing a
particular block), a
ctifail condition can be asynch ronousl y genera ted. In gen era l,
it is recommended that the application explicitly handle the
ctifail condition.
Generally speaking, requests can fai l for different re as ons. The most common incl ude :
• unavailable resources
• invalid parameter specifications in a block
• timer expiration.The maxi mum a mount of time that an app li cat i on wa it s for a
response is determined by the value of the Environment block variable
vpsrcvtime. If a request times out, the application receives a vrto
condition (instead of
of). This is another condi tion that the application should
handle.
• unregistered ports. The ports used to run an IVR application or Agent phone
have to be registered using the IPML Configurator. The switch and/or SCCS
must be configured properly to identify Agent Position IDs and CDNs.
• invalid configuration file entries. To use the functions in the CTI Toolkit, the
IPML packages must be properly configured by following the procedures in
the MPS Interface to M1 publication. The following are some configuration
essentials that should be verified if particular blocks produce problems when
executed:
• CTI blocks— Use the IPML Configurator to set up communications
between CSVAPI and VMS, CSVAPI and TLS, and TLS and SCCS (or
the switch).
• TAPI blocks— Use the IPML Configurator to set up communications
between CSTAPILS and VMS, CSTAPI and CSTAPILS, and CSTAPILS
and the Symposium TAPI server.
• RSM block— The configuration files mus t be set up to allow
communications between CSRSM and VMS, CSRSM and CSRSMLS,
and TLS and SCCS (or the switch). Skill levels, agent names, and
application (SCCS script names) must be entered in IPML Configurator
in PeriView.
Page 30
PeriProducer CTI Toolkit User’s Guide for M1
Page 30 Nortel Networks Confidential # P0606089 Ver: 1.1
CTI Toolkit Blocks
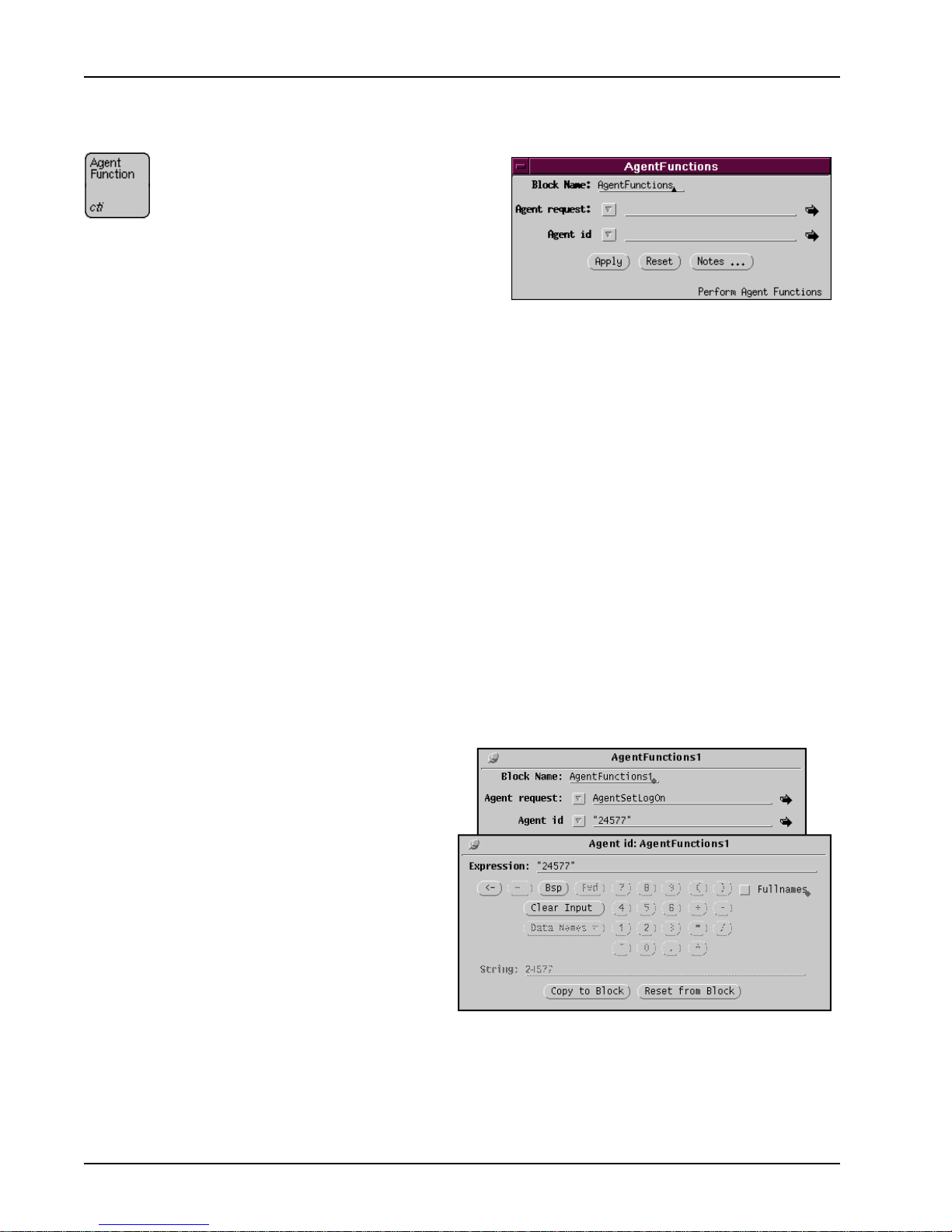
The Agent Function block outputs two parameters:
1. Agent request: Assigns a value from CTI.Requests.Agent.
Applicable values for this field are under the Agent folders menu. To set
the Agent request field:
• Set the agent state to
AgentSetLogon to log on to the ACD and start
the agent's work period. (Only one logon is required at IVR application
startup or whenever the CTI resource has been reacquired.)
• Once the logon process is s uccessful , the IVR port must be changed to the
ready state. The switch can be setup to have the IVR port go ready by
default.
• Before any calls can be received, the phone line has to be set to
MakeReady.
• Set the state to
AgentSetWorkNotReady to allow the agent to ta ke a
break. When the agent is ready to return to work, set the state to
AgentSetWorkReady.
• Finally, at the end of the work period, set the state to
MakeNotReady
and then
AgentSetLogOff.
2. Agent id: The
agent ID should be
assigned the
position ID of the
phone line. The
only applicable
value for the
Agent id field is a
character st ring.
Agent Function
The Agent Function block sets the
state of an agent phone, which is
either a live agent or an IVR
application running on the IVR port.
Page 31

CTI Toolkit Blocks Reference
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 31
Keep in mind the following when using the Agent Function block:
• When any of these agent state change requests are used, a message is sent to
the CTI resource (CSVAPI process). F or each different request, the message
sent to CSVAPI reads the same, but with CtiFunction and Set Wait Event
values for t hat particular f unction. The following table shows these values.
• The CTI.status data card is the only value in the CTI folder that is affected by
this CTI Toolkit block. CTI.status is set to 0 if the request is successful and
set to 1 if the request fails.
• The Agent Function bl ock requ ir es prio r use of th e CTI Initialize block (see
page 32) block to obtain the
CTI resource.
• For examples of applications that use t his bl ock, see Agent Function on page
56.
• For example log files showing the internal functions of this block, see Agent
Function CSVAPI Log File on page 74.
CTI Function
SetWaitEvent (what VENGINE waits for as an
indicator of success)
AgentSetLogon LoggedOn
AgentSetLogOff LoggedOff
MakeReady Ready
MakeNotReady NotReady
AgentSetWorkNotReady WorkNotReady
AgentSetWorkReady WorkReady
Page 32

PeriProducer CTI Toolkit User’s Guide for M1
Page 32 Nortel Networks Confidential # P0606089 Ver: 1.1
CTI Initialize should always be one of the first blocks of the application because it
sets up conditio n ha ndling for the rest o f t he application. It o nly has to be called again
if the application has terminated or freed the
CTI resource.
CTI Initialize sends a mes sage to an y of se veral CSVAPI services to reserve memo ry
for managing CTI events and requests for the IVR port the application is running on.
For each resource request, the message sent is the same, but appears only in the
appropriate log file for services such as CSRSM, CSTAPI, CSVAPI (CTI), and so on.
The only output generated by CTI Initialize is the condition handlers set up for the
ctiup/ctidown conditions.
There are certain input values that have to be assigned in the CTI folder structure in
order for the CTI Initialize block to acquire resources:
The CTI.Resource.Status folder values are affected by CTI Initialize. The values
are set to True if the request to get a resource succee ds and set to False if that request
fails. If they are not set to False to start with, CTI Initialize does not change them.
For examples of applications that use this block, see Appendix Example
Applications—CTI Initialize on page 58. For example log files showing the internal
functions of this block, see Appendix Example Log Files—CTI Initialize CSVAPI
Log File on page 74.
CTI Resource Status Indicator Usage
CTI.ResourceStatus.TIIsOk not used
CTI.ResourceStatus.CSrouterIsOK not used
CTI.ResourceStatus.CSRsmIsOk not used by RSM block
CTI.ResourceStatus.CSTAPISccsIsOk not used by TAPISCCS bloc k
CTI.ResourceStatus.CSSentryIsOk not used
CTI.ResourceStatus.CSTapiIsOk not used by TAPI block
CTI.ResourceStatus.CSTIsOk must be set to false to hav e the
CTI Initialize block
reserve the resource
CTI Initialize
The CTI Initialize block sets handlers for the ctiup,
ctidown, and cticond conditions. This block also
acquires any
CTI resource required by the application.
The CSRSM, CSTAPI, and CSTAPISCCS processes do not need to
useCTI Initialize since their respective blocks (Device Statistics Data,
Send TAPI Call Data, and Send TAPI SCCS Call Data) get and free the
appropriate resources. However, when using any of the other blocks in the
CTI Toolkit (i.e., those that have an italicized cti in the lower left corner of the bl ock
icon), the application has to execute CTI Initialize to acquire the resource.
Page 33

CTI Toolkit Blocks Reference
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 33
The Device Parameter Data block has two parameters:
• Device Number: Specifies a value (usually a DN) on which this CTI block
is to report. Valid values for this field are the numb ers of registered devices
relevant to the application’s requirements, such as agent IVR ports regi stered
in the IPML Configurator.
• Param Name: Use one of the nine constants in the
CTI.Requests.DeviceParams folder to specify the particular information
required. (S elect the value fr om the DeviceParams menu.)
Device Parameter Data
The Device Parameter Data block
acquires information (often switch
specific) from a specified telephony
device connected to the switch.
Page 34

PeriProducer CTI Toolkit User’s Guide for M1
Page 34 Nortel Networks Confidential # P0606089 Ver: 1.1
Each of the parameter names cause s a dif ferent mess age to be sent to CSVAPI
requesting information from the CSDA service. For each request, the
CtiFunction parameter is set to
getdeviceparam, and the device and
specific parameter are set to values passed into the Device Parameter Data
block. These values are:
The following is impor tant info rmation per taining t o the use of the Device Parameter
Data block:
• The CTI.status data card value is affected by this block. It is set to 0 for
success an d 1 for failure. O ther areas that may get written to are the
CTI.EventData.paramname and the CTI.EventData.paramvalue
including the CTI.EventData.tlinkdata.datakey() and
CTI.EventData.tlinkdata.datavalue() arrays.
• To use the Device Parameter Data block in an application, the CTI
Initialize block (see page 32) block has to be used first to obtain the CTI
resource. Also the Set Event Handling block (see page 37) is used to wait for
a connecti on to be establish ed to guarantee that data is available.
• For examples of applications that use this block, see Appendix Example
Applications—Device Parameter Data on page 58.
• ACDGroupStatus
• AgentBreakTime
• AgentID
• AgentLogonTime
• AgentMode
• AgentTalkTime
• AgentTimeInMode
• AgentWorkTime
• CallerETA
Page 35

CTI Toolkit Blocks Reference
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 35
This block sends a r egister/unregister m es sage to the CTI resource to reserve mem or y
for the specified DN. The request includes a DN, a device type, and whether to
register or unregister it .
The Register Device block has three parameters:
• Register DN request: assigned either CTI.Requests.Registration.
Register or CTI.Requests.Registration.UnRegister. The value is selected
from the Registration menu:
• Destination number:
specifies the destination
number to register or
unregister. The only
applicable value for the
Destination number field
is a character string.
Register Device
The Register Device block
registers or unregisters a
destination number (DN). A DN
must be registered before any
other CTI Toolkit operations can
be performed using that DN.
Page 36

PeriProducer CTI Toolkit User’s Guide for M1
Page 36 Nortel Networks Confidential # P0606089 Ver: 1.1
• Device Type To Register: specifies the type of device you are registering.
The following is important information pertaining to the use of the Register Device
block:
• The calling application obtains the CTI resource via the CTI Initialize block
(see page 32) block or the Resource block. No other blocks are needed befo re
Register Device.
• Use the Register Device block as one of the first blocks of the application.
• Call this block only to re-register the DN if th is application (or another) has
unregistered the DN.
• The CTI.Status value is set to 0 for success and 1 for failure.
• For examples of applications that use this block, see Appendix Example
Applications—Register Device on page 58.
• For example log files showing the internal functions of this block, see
Appendix Example Log Files—Reg ister Device CS VAPI Log File on page
74.
Page 37

CTI Toolkit Blocks Reference
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 37
The Set Event Handling block has two parameters:
• Event: Assign a value to this field from CTI.Constants.Events folder,
which is accessed from the Events menu.
• Application Event Handling: Use any of the type of methods of handling
an event as defined in the CTI.Requests.SetEventType folder, which is
accesed from the SetEventType menu.
Set Event Handling
The Set Event Handling
block controls the re sponse
of an IVR application to
the events coming from the
switch for the agent-IVRport on which the
application is running. Use this block to synchronize event handling between an IVR
application and resources.
Page 38

PeriProducer CTI Toolkit User’s Guide for M1
Page 38 Nortel Networks Confidential # P0606089 Ver: 1.1
The SetWaitEvent, SetIgnoreEvent and SetCtiCondEvent functions can
be performed for the any of the available events:
AgentEvents, All,
CallData, Dequeued, CallCleared, CallEvents, Conferenced,
Dialing, Forwarding, Held, Established, LoggedOff,
LoggedOn, NotReady, Queued, Ready, Retrieved, Ringing,
RouteRequest, ServiceComplete, ServiceInitiated,
Transferred, WorkNotReady, and WorkReady.
The following is important information pertaining to the use of the Set Event
Handling block:
• The Set Event Handling block is often used to synchronize the application
and the Answer block with CSVAPI. Many of the Example Applications
listed in Appendix A show ho w this block ca n be used to wait for the call to be
established after the application "falls out" of the Answer block. Depending
on the situation, the waiting event could also be ringing, which allows all
other subsequent data or telephony requests to the CTI resource to function
properly.
• It is generally best if the first use of Set Event Handling in the application
ignores all events, thus clearing the wait conditions of anything leftover from
a previous call.
• The CTI resource must be obta ine d via t he CTI In itial ize b loc k (see page 32)
before Set Event Handling is executed.
• Depending on the parameter specified in the Application Event Handling
field, the a pplication may receive either a
vrto or cticond condition. The
application can eit her a sk CSVAPI to send a
CTI condition when i t rec eives a
particular event or (as is usually done) the application waits until a needed
event occurs or until the
vpsrcvtime value times out with a vrto error . If
a
CTI condition is used, the application must handle the condition
appropriately. Handling of conditions is essential if SetCTICondEvent is
specified in the Application Event Handling field.
• The CTI.status p arameter is set t o 0 if the reques t i s successful and set to 1 if
the request fails.
• In the event that an applicat ion’s request comes to the VAPI before it receives
any events from the switch, synchronize the application’s requests with the
call’s events by doing the following:
a. Answer the call.
b. Get CTI resources.
c. Use SetWaitEvent on an
Established event.
d. Retrieve the
EventData or perform the AttachData.
• SetWaitEvent is useful when the applicaiton’s execution has to be
synchronized with even ts. The applicat ion’s execution will pause at this block
until it is notified that the event occurred (or until a condition occurs). For
example:
• If the application is setting an Agent to a Ready state using the Agent
Page 39

CTI Toolkit Blocks Reference
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 39
Function block, it might set a Wait block for the Ready event, and only
then assume that the Agent is Ready.
• If the application originates a call using the Te le phony Reques t block
(see page 42), it can set a Wait block for an established event and then
proceed because the agent is in the Ready state.
• A Set Event Handling block is used to request a CTI condition when a
certain event occurs. After a specified time, the application proceeds with
execution. If the specified event occurs, a CTI condition is sent to the
application. To find out what generated the condition, check the value of
System.ConditionData, which is a string consisting of the causal event and
possible additional data (depending on the event). This is useful when the
application has to respond to an even t as ynchronously and not wait for it. For
example, if the application initiates a call, it can set a CTI condition for a
CallCleared event so it can proceed wit h execut ion, and be not ifie d when
the call is cleared.
• For examples of applications that use this block, see Appendix Example
Applications—Set Event Handling on page 59.
• For example log files showing the internal functions of this block, see
Appendix Example Log Files—Set Event Handling CSVAPI Log File on
page 75.
Page 40

PeriProducer CTI Toolkit User’s Guide for M1
Page 40 Nortel Networks Confidential # P0606089 Ver: 1.1
Telephone data types is the only parameter in thi s CTI block. It s value is assigned
from the CTI.Requests.EventData folder, which is accessed from the EventData
menu.
.
Four types of event data ca n be ret riev ed usin g this CTI bloc k: the e nt ire event re cord,
DNIS, ANI, or ETA. If the whole event record is requested, it may include any of the
following, depending on availability: (
agentid, agentstate, ani,
attributedata (a structured array[folder] that includes Key, Value and Level in
each of 40 elements),
callid, calldata (a structured array[folder] that includes
datakey and datavalue in each of 40 elements),
csrsmstatdata (a structured
array[fold er] that includes datakey and datavalue in each of 40 elements),
devicelist (a structured array[folder] that includes device in each of 40
elements),
dnis, eta, othercallid, otherdevice, paramname,
paramvalue, qtime, route, status, thisobjectkey, thispathkey,
tlinkdata (a structured array[folder] that includes datakey and datavalue in each
of 40 elements) and
tlservername.
Telephony Event Data
The Telephony Event Data
block obtains specific event
data for the IVR application
running on the IVR port.
Page 41

CTI Toolkit Blocks Reference
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 41
The following is important information pertaining to the use of the Telephony Event
Data block:
• This block requires several prerequisites. The CTI Initialize block (see page
32) or the Resource block must be used to first obtain the CTI resource. The
IVR application has to be Logged In to the Queue or CDN. Also the Set
Event Handling block (see page 37) should be used to wait for
Established to guarantee that the data is available to be retrieved. Set
Event Handling is best used right after the call is answered to synchronize
the CTI services and their data stores with the actual phone device state. The
usual state to wait for is
Established.
• The CTI.status parameter is set to 0 if the request is successful. It is set to 1
or 9 if the request fails. Also, various parts of the CTI.EventData folder can
be written to based on the data ret ri eved from the specifi ed Telephone data
type.
• For examples of applications that use this block, see Appendix Example
Applications—Te lephony Event Data on page 63.
• For example log files showing the internal functions of this block, see
Appendix Example Log Files—Telephony Event Data CSVAPI Log File on
page 76.
Page 42

PeriProducer CTI Toolkit User’s Guide for M1
Page 42 Nortel Networks Confidential # P0606089 Ver: 1.1
The Telephony Request block has two parameters:
• Call Processing Request: This field indicates the desired call processing
operation. Valid values are selected from the Telephony menu.
• Destination number: This
field specifies the phone
number of the destination
for the desired operation
(selected in the Call
Processing Request
field). The destination
number is entered as a
character st ring.
• There are 12 possible functions that this block can request IPML to perform on
behalf of the IVR application. Some functions require that the Destination
Telephony Request
This block makes requests to
the switch to perform
telephony actions on behalf
of the IVR application
running on the IVR port.
Page 43

CTI Toolkit Blocks Reference
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 43
number parameter be assigned to a valid DN while others do not. The table
below shows how it works:
Call Processing
Request
Description
AnswerCall • CTI.Requests.ThisDevice is assigned to the DN for the
IVR-agent port.
• CTI.Requests.CallID i s set to the cal l ID as obtai ned from a
Telephony Event Data request.
• The Destination number parameter is assigned spaces.
BlindTrans fer The Destination Num ber for the bli nd transfer to send t he call to
(from the current IVR-agent port) must be placed in the
Destination number parameter part of the CTI block.
ClearCall The Destination number part of the CTI block par ameter is
assigned spaces.
CompleteConference • No parameters or CTI folder values are used.
• The Destination num be r p art of the CTI block param ete r is
assigned spaces.
CompleteTransfer • No parameters or CTI folder values are used.
• The Destination num be r p art of the CTI block param ete r is
assigned spaces.
ConsultationConference The Destination Number for the consultation conference must
be placed in the Destination number parameter part of the CTI
block.
Consultati onTransfer The Destination number parameter part of the CT I block is
assigned the number to which transfers are made.
InitiateConference The Destination number parameter part of the CTI block is
assigned the number to which conferences are connected.
InitiateTransfer The Destination number parameter part of the CTI block is
assigned the number to which transfers are made.
HoldCall The Destination number parameter part of the CTI block is
assigned spaces.
MakeCall • CTI.Requests.ThisDevice is assigned to the DN for the
IVR-agent port.
• The Destination number parameter part of the CTI block is
assigned the number to make a call to.
RetrieveCall The Destination number parameter part of the CTI block is
assigned spaces.
Page 44

PeriProducer CTI Toolkit User’s Guide for M1
Page 44 Nortel Networks Confidential # P0606089 Ver: 1.1
The following is important information pertaining to the use of the Telephony
Request block:
• To use the Telephony Re quest bloc k severa l other blocks hav e to b e execute d
first. The CTI Initialize block (see page 32) should be used to obtain the CTI
resource. Also, th e Set Event Handling block (se e page 37) should be used to
wait for the
Established state (in most cases) to guarantee that CSV API is
ready to process the request.
• It is generally best if the first use of the Set Event Handling is ignores all
events, thus clearing the wait conditions of anything left over from a previous
circumstance. The application should use Set Event Handling a second time
before trying to make a tele phony request . This is u sually best done right aft er
the call is a nswer ed to synchronize the CTI services and t heir data stores wi th
the actual phone device state.
• The CTI.status data card is the only value in the CTI folder that is affected by
this CTI toolkit block. The CTI.status parameter is set to 0 if the request is
successful. It is set to 1 if the request fails.
• When using a Telephony Request block to transfer a call, the
cticond
should be handled. After the block is executed, the val ue of CTI.status can be
checked to verfiy whether or not the transfer was successful. If the transfer
fails due to a problem with the CTI resource, a regular transfe r might still be
successful. If the failure is related to the switch, all transfe rs will be
unsuccessful.
• For examples of applications that use this block, see Appendix Example
Applications—Telephony Request on page 65.
• For example log files showing the internal functions of this block, see
Appendix Example Log Files—Telephony Request CSVAPI Log File on
page 78.
Use of the Answer Call function of the Telephony Request block requires that the
application use the Set Event Handling block to wait for
Ringing.
Page 45

CTI Toolkit Blocks Reference
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 45
The User Data block has two parameters:
• Data function: Valid values (Add, Remove, or Retrieve) are assigned
from the CTI.Requests.UsrDataFunc folder via the UsrDataFunc menu.
• Data type: Valid values (Calldata or Tlinkdata) are assigned from the
CTI.Requests.UsrDataFunc folder via the UsrDataType menu.
User Data
This block obtains, modifies, or
removes specific call data or
obtains telephony link data (often
switch specific) for the IVR
application running on the agentIVR-port.
Page 46

PeriProducer CTI Toolkit User’s Guide for M1
Page 46 Nortel Networks Confidential # P0606089 Ver: 1.1
The following is important information pertaining to the use of the User Data block:
• The User Data bl ock requ ires se veral prereq uisite bl ock s. The CTI Init iali ze
block (see page 32) should be used to obtain the CTI resource. The IVR
application has to be Logged In to the Queue or CDN on DMS systems (but
not on M1 systems). Also the Set Event Handling block ( see pag e 37) should
be used to wa it for the
Established state to guarantee that the data is
available to retrieve.
• For the User Data block to perform read-only operations, no special input
values need to be assigned in any part of the CTI folder structure. To use the
block to get a specific key, place the fieldname of that item in the Key(1)
array position.
User Data returns the value of the first key it encounters. In
environments where you need to retrieve values of duplicate keys, do not
specify a value in the Key(1) array position. This tells the User Data
block to return all key-value pairs, including duplicate keys.
• CTI.EventData.Calldata (a structured array[folder] that includes datakey
and datavalue in each of 40 elements) and CTI.EventData.tlinkdata (a
structured array[folder] that includes datakey, datavalue in each of 40
elements) are the two places where the data is returned.
• If data is being removed or added, the CTI.AVCalldata.Avpairs.Key() and
CTI.AVCalldata.Avpairs.Value() ca rds hav e to be populated accordingly. In
either case, use the Key() array to name the data items to delete or add.
• Call data can be added to by either the IVR application or SCCS. Telephony
link data (tlink data) can only be added to by the switch (or SCCS as a front
end for the switch). Data can always be obtained from either; but can only be
removed from the CallData. The Call Data and Tlink data are both discarded
after the call expires. Thus the application does not have to maintain it on it's
own.
• The CTI.status parameter is set to 0 if the request was successful and set to 1
if the reque st failed.
• For examples of applications that use this block, see Appendix Example
Applications—User Data on page 68.
• For example log files showing the internal functions of this block, see
Appendix Example Log Files—User Data CSVAPI Log File on page 83.
Page 47

CTI Toolkit Blocks Reference
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 47
The Device Statistics Data block has two parameters:
• Stati stics Device: Should
be assigned a value specific
to the application, such as
"LinuxDeveloper" as a type
of operator skill. The only
applicable value for this field
is a character string.
• Stati stic Group: Should be assigned a value from the
CTI.Requests.CSRSMStatisticGroup folder (su ch as SkillItd for skil l
information provide d on an "interv al to date" basis). Valid values for this field
are accessed from the CSRSMStatisticGroups menu.
Device Statistics Data
This block obtains statistics
information from SCCS through
the RSM interface on various
devices su ch as agents,
applications, or skill sets. This
block uses the
csrsm resource.
Page 48

PeriProducer CTI Toolkit User’s Guide for M1
Page 48 Nortel Networks Confidential # P0606089 Ver: 1.1
The statistical information denoted by the values in the
CTI.Requests.CSRSMStatisticGroup folder (su ch as
SkillItd for skill
information provided on an "interval to date" basis) represent the types of statistics
available for various "devices." The table below explains their use.
The following is important information pertaining to the use of the Device Statistics
Data block:
• This block requires t wo pre re qui sites. The CTI Initialize block (see page 32)
should be used early in the application to set up appropriate error handling.
The application should use the Set Event Handling block (see page 37)
before trying to obtain data. This is usually best done right after the call is
answered to synchronize th e CTI se rvice s and thei r data stores with the ac tual
phone device state. The usual state to wait for is
Established.
• The CTI.status p arameter is set t o 0 if the reques t i s successful and set to 1 if
the request fails.
• For examples of applications that use this block, see Appendix Example
Applications—Device Statistics Data on page 69.
• For example log files showing the internal functions of this block, see
Appendix Example Log Files—Device Statistics Data CSRSM and
CSRSMLS Log Files on page 86.
Statistical Groups Device Type for the Statistics
AgentItd
Agent information on an interval-to-date
basis.
Agents under SCCS control.
AgentMwnd
Agent information on a moving-window
basis.
ApplicItd
Application information on an interval-todate basis.
Applicati on refers to a script name running
under SCCS usually controlling a CDN.
ApplicMwnd
Application (refers to a script name running
under SCCS usually controlling a CDN)
information on a moving window-basis.
SkillItd
Skill information on an interval-to-date basis.
Skills are defined within SCCS by
associating particular agent groups
(usually in queues) with this skill.
SkillMwnd
Skill information on a moving-window basis.
Page 49

CTI Toolkit Blocks Reference
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 49
• CTI.EventData.csrsmstatdata is a structured ar ray[folder] that includes
datakey and datavalue in each of 40 elements. It is the location of the returned
data.
• The data structu re re turns key/va lue pa irs. T he f ollowi ng are the k eys th at ca n
be returned based on the selected statistics group:
Statistical
Groups
Statistics re turned in CTI.Eve ntData.csrsmstatdat a
AgentItd
- and AgentMwnd
AgentID_High
AgentID_Low
AnsweringSkillset
DNInTimeInState
DNOutTimeInState
PositionID
State
SupervisorID_High
SupervisorID_Low
SupervisorUserID
TimeInState
ApplicItd
- and ApplicMwnd
ApplicationID
CallsAbandoned
CallsAbandonedAfterThreshold
CallsAbandonedDelay
CallsAnswered
CallsAnsweredAfterThreshold
CallsAnsweredDelay
CallsAnsweredDelayAtSkillset
CallsGivenTerminationTreatment
CallsOfferedApp
CallsWaiting
MaxWaitingTime
NetworkOutCalls
NetworkOutCallsAbandoned
NetworkOutCallsAbandonedDelay
NetworkOutCallsAnswered
NetworkOutCallsAnsweredDelay
NetworkOutCallsRequested
NetworkOutCallsWaiting
TimeBeforeInterflow
WaitingTime
SkillItd
- and SkillMwnd
AgentOnACDDNCall
AgentOnNACDDNCall
AgentOnNetworkSkillsetCall
AgentOnOtherSkillsetCall
AgentsAvailable
AgentsInService
AgentsNotReady
AgentsOnDNCalls
AgentsOnSkillsetCall
AgentsUnavailable
CallsAnsweredAfterThreshold
CallsOfferedSkill
CallsWaiting
ExpectedWaitTime
LongestWaitingTimeSinceLastCall
LongestWaitingTimeSinceLogin
MaxWaitingTime
NetworkCallsAnswered
NetworkCallsOffered
NetworkCallsWaiting
QueuedCallAnswered
SkillsetAbandoned
SkillsetAbandonedAfterThreshold
SkillsetAbandonedDelay
SkillsetID
SkillsetState
TotalCallsAnswered
TotalCallsAnsweredDelay
WaitingTime
Page 50

PeriProducer CTI Toolkit User’s Guide for M1
Page 50 Nortel Networks Confidential # P0606089 Ver: 1.1
The following information pertains to the use of the Send TAPI Call Data block:
• This block requires two prerequisites as it manages its own resource needs.
The CTI Initialize block (see page 32) should be used early in the appli cation
to set up appropriate error handling. Also, the Set Event Handling block (see
page 37) should be used before trying to send data. This is usually best done
right after the call is answered to synchronize the CTI services and their data
stores with the actual phone device state. The usual state to wait for is
Established.
• The values required for the this CTI block are stored in the folders
CTI.AVCalldata.Avpairs.Key() and CTI.AVCalldata.Avpairs.Value().
• CTI.EventData.csrsmstatdata (a structured array[folder] that includes
datakey and datavalue in each of 40 elements) is the return location for the
data.
• The CTI.status parameter is set to 0 if the request was successful and set to 1
if the reque st fails.
• For examples of applications that use this block, see Appendix Example
Applications—Send TAPI CallData/Send TAPIsccs CallData on page 70.
• For example log files showing the internal functions of this block, see
Appendix Example Log Files—Send TAPI Call Data CSTAPI and
CSTAPILS Log Files on page 89.
Send TAPI Call Data
The TAPI block sends screen pop information about the
current call from the IVR application to the Symposium
TAPI Server via the
IVR.DLL protocol. This block uses
the
cstapi resource.
Page 51

CTI Toolkit Blocks Reference
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 51
The following information pertains to the use of the Send TAPI SCCS Call Data
block:
• This block requires two prerequisites as it manages its own resource needs.
The CTI Initialize block (see page 32) should be used early in t he applica tion
to set up appropriate error handling. Also, the Set Event Handling block (see
page 37) should be used before trying to send data. This is usually best done
right after the call is answered to synchronize the CTI services and their data
stores with the actual phone device state. The usual state to wait for is
Established.
• The values required for the this CTI block are stored in the folders
CTI.AVCalldata.Avpairs.Key() and CTI.AVCalldata.Avpairs.Value().
• CTI.EventData.csrsmstatdata (a structured array[folder] that includes
datakey and datavalue in each of 40 elements) is the location for the returned
data.
• The CTI.status p ara m ete r is set to 0 if t he request is suc ces sf ul and set to 1 if
the request fails.
• For examples of applications that use this block, see Appendix Example
Applications—Send TAPI CallData/Send TAPIsccs CallData on page 70.
• For example log files showing the internal functions of this block, see
Appendix Example Log Files—Send TAPI SCCS Call Data CSTAPI and
CSTAPILS Log Files on page 92.
Send TAPI SCCS Call Data
This TAPISCCS block sends screen pop information
about the current call from the IVR application to the
Symposium TAPI Serv er vi a the IVR.DLL pro tocol . This
block uses the
cstapisccs resource.
Page 52

PeriProducer CTI Toolkit User’s Guide for M1
Page 52 Nortel Networks Confidential # P0606089 Ver: 1.1
The GetTapiData block has no Parameters. Before executing the block, the callid for
the active call must be retrieved by the peripro application. The general procedure to
get data fro m the Symposium Tapi Server is as follows:
• Obtain the Callid from vapi using the User Data block.
• Use an assignment block to populate the
CTI.requests.callid
datacard with the callid obtained from csvapi.
• Execute the GetTapiData block.
• Data is returned in
CTI.AVCalldata.AVPairs folder.
• 40 Pairs of 40 byte keys and 40 byte values are available for calldata
storage.
A test application has been included in the ctitoolkit,
/samples/SCCS-
Integrate/get_tapi_calldata.ppr
, which illustrates the procedure.
CSTAPILS Settings
The Periview configuration tool provides access to two values that are used for the
ReverseIVR feature.
• SendCallDataKey true/false - Indicates whether retrieved data is expected to
be delimited. Example using `&` as delimeter:
customerid&5544332211&firstname&henry&lastname&smith
• CallDataField delimiter - delimiter to expect.
If SendCallDataKey is set false, then cstapils will send attac hed data in the form of a
single key/valu e pa ir where the the key is TAPIDATA and t he value is the data as sent
from the tapi server, with a maximum length of 40 bytes.
GetTAPIData
The Get Tapi CallData block is used to retrieve call data
which has been previously attached by another application
connected to the Symposium Tapi Server, such as
CallCenter agent's desktop softphone.
Page 53

CTI Toolkit Blocks Reference
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 53
The Log Message block has two parameters:
• filename: A character string (less than or equal to 50 characters) specifying part
of the name for the application’s log file. Log file names are assigned by the
system using the format filename
VnnnLmmm.log, where:
• filename is user specified.
• nnn is the number of t he IVR syst em running the appl ication, padded wit h
zeroes ("0") to make it three digits.
• mmm is number of the IVR phone port running the application, padded
with zeroes ("0") to make it three digits.
• Log message: A character
string (less than or equal to 1 00
characters) specifying the
message to be logged.
The following information pertains to the use of the Log Message block:
• If this bloc k executes suces sfully, a new log file is created or t he specified
message is appended to an existing file.
• Log file lines are prefixed with date and time information. For example:
03/16/01 09:56:33 application starts
• If the operation is unsuccessful, it is usually due to illegal file name
characters, inappropriate write permissions, or disk space problems.
• For examples of applications that use this block, see Appendix Example
Applications—Log Message on page 71.
• For example log files showing the inter nal functions of this bl ock, see page 74
through page 95.
Log Message
Log Message is used to
place information into a log
file based on specified
parameters. It logs any text
that meets the size
limitations. It does not use
any resources.
Page 54

PeriProducer CTI Toolkit User’s Guide for M1
Page 54 Nortel Networks Confidential # P0606089 Ver: 1.1
This page has been intentionally left blank.
Page 55

Example Applications
Page 56

PeriProducer CTI Toolkit User’s Guide for M1
Page 56 Nortel Networks Confidential # P0606089 Ver: 1.1
Example Applications
The example PeriProducer applications lis ted in this appendix exist in the installation
directory of the
PERIctitk package. For 2000 platforms, prefix the directories
listed with
C:\Program Files\Nortel\PERIctitk.
Agent Function
App. # Example Application Name, Location, Function, and Usage
AF-1
/samples/CS-AD/ACDAgent.ppr
1. CTI init; read config file for agent DN and this device; get cti resource
2. Log agent in (trap vrto if request times out)
3. Set agent ready (trap vrto if request times out)
4. Wait 5 minutes to answer call via cti calls; not traditional Answer block; wait for release
5. Set agent not ready (trap vrto if request times out)
6. Log agent out (trap vrto if request times out) works on all Nortel switches.
AF-2
/samples/CS-AD/ACDPhoneLoginLogout.ppr
1. CTI init; read config file for agent DN and this device; get cti resource
2. Log agent in (trap vrto if request times out)
3. Set agent ready (trap vrto if request times out)
4. Set agent not ready (trap vrto if request times out)
5. Log agent out (trap vrto if request times out)
AF-3
/samples/CS-AD/Anologue.ppr
1. Read config file for agent DN and this device (logging only)
2. Get cti resource
3. Log agent in (trap vrto if request times out)
4. Delay to simulate phone conversation
5. Hang up
6. Log agent out (trap vrto if request times out)
AF-4
/samples/CS-AD/Nortel-iccm/ACDAgent.ppr
This is a duplicate of the application in the CS-AD directory.
AF-5
/samples/CS-AD/Nortel-iccm/ACDPhoneLoginLogout.ppr
1. Set up to handle "of" by logging out and restarting
2. CTI init; read config file for agent DN and this device; get cti resource
3. Log agent in (trap vrto if request times out)
4. Set agent ready (trap vrto if request times out)
5. Set agent not ready (trap vrto if request times out)
6. Log agent out (trap vrto if request times out)
AF-6
/samples/CS-AD/Nortel-iccm/AgentLogout.ppr
1. CTI init; read config file for agent DN and this device (for logging); get cti resource
2. Log agent out
Page 57

Example Applications
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 57
AF-7
/samples/CS-AD/Nortel-iccm/dmsloginlogout.ppr
1. CTI init
2. Read config file for agent DN, this device (for logging)
3. Get cti resource
4. Log agent in (trap vrto if request times out)
5. Use Answer block to wait for call, then wait for established
6. Short delay
7. Set agent ready (vrto trap from login taked control if request times out)
8. Set agent not ready (vrto trap from login taked control if request times out)
9. Log agent in (trap vrto if request times out)
AF-8
/samples/CS-AD/Nortel-ipml/AnaloguePhoneLoginLogout.ppr
1. CTI init
2. Read config file for this device (for logging) and Agent DN
3. Get cti resource
4. Log agent in (trap vrto if request times out)
5. Short delay to simulate phone co nve rsation
6. Log agent out (trap vrto if request times out)
7. Delay 15 seconds
8. Free cti resource
9. Force connect
10. Loop to get cti resource
App. # Example Application Name, Location, Function, and Usage
Page 58

PeriProducer CTI Toolkit User’s Guide for M1
Page 58 Nortel Networks Confidential # P0606089 Ver: 1.1
CTI Initialize
Device Parameter Data
Register Device
App. # Example Application Name, Location, Function, and Usage
CI-1
/samples/SCCS-integrate/tapi_da_ivr_agent.ppr
1. In container Library.GetCTIRes, the CTI.ResourceStatus.CTIIsOk tells the CTI Init block
that the calling application wants to get the CTI resource.
2. In the container Startup.Inits. Check immediately following the call to the CTI Init block,
the value CTI.st atus is checked to see if it is 0 and the value CT I.Resourc eS tatu s.CTIIsOk
is checked to see if it is true. If both conditions are met, then the code proceeds,
otherwise it exits the application.
3. Later, after the application concludes, it’s work in the Wrapup container, the resource is
freed and the Library.GetCTIRes is called again before the application starts at the
Answer block again to wait for a new call.
4. Note tha t this applicat ion uses a Resource block in the Wrapup container to free the CTI
resource, since the application requires that the resource is freed after every cycle.
CI-2
/samples/SCCS-integrate/acdagentwithcalldata.ppr
1. In the container, Initiate, the CTI Init block is called to set the condition handling.
2. In the container, Initiate.GetCTI, the application uses the Resource block to get the CTI
resource on it’s own, without help from the CTI Init block.
3. Note that this ap plication allows the terminati on of the a pplicati on to automati cally fre e the
CTI resource.
App. # Example Application Name, Location, Function, and Usage
DP-1
/samples/CS-AD/Nortel-iccm/GetACDGroupStatus.ppr
1. CTI init; config file read; but not used except for logging purposes
2. CTI resource gotten
3. A hard coded DN is used to get ACDGroupStatus information
4. The CTI.EventData.paramname and the CTI.EventData.paramvalue are ignored while
the CTI.EventData.t linkdata.dat akey() and CTI.EventD ata.tlinkdat a.datavalue () arrays are
logged.
DP-2
/samples/CS-AD/testrequestdeviceparams.ppr
1. Error trapping is set up, cti resource is obtained and this device is registered.
2. A loop is st arted tha t s end s e ach ty pe o f Para m Na me to c t i f or th e s am e Dev ic e Num be r.
3. The loop exits and the cti resource is free d as the appl ic ati on te rmi nat es . No te th at at the
end of an IVR application’s execution, the cti resource is freed automatically.
App. # Example Application Name, Location, Function, and Usage
RD-1
/samples/CS-AD/testrequestdeviceparams.ppr
1. Error trapping is set up, cti resource is obtained and this device is registered.
2. A loop is st arted tha t s end s e ach ty pe o f Para m Na me to c t i f or th e s am e Dev ic e Num be r.
3. The loop exits and the cti resource is free d as the appl ic ati on te rmi nat es . No te th at at the
end of an IVR application’s execution, the cti resource is freed automatically.
Page 59

Example Applications
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 59
Set Event Handling
App. # Example Application Name, Location, Function, and Usage
SE-1
/samples/CS-AD/ACDAgent.ppr
1. CTI init; read config file for agent DN and this device; get cti resource
2. Log agent in (trap vrto if request times out)
3. Set agent ready (trap vrto if request times out)
4. Wait 5 minutes to answer call via cti calls; not traditional Answer block; wait for release
5. Set agent not ready (trap vrto if request times out)
6. Log agent out (trap vrto if request times out)
SE-2
/samples/CS-AD/AniAndDnis.ppr
1. CTI init; get cti resource
2. Use Answer block to wait for call, then wait for established
3. Get ANI & DNIS
4. Get Telephony Link Data
5. Wait for release
SE-3
/samples/CS-AD/Anologue.ppr
1. Read config file for agent DN and this device (logging only)
2. Get cti resource
3. Log agent in (trap vrto if request times out)
4. Delay to simulate phone conversation
5. Hang up
6. Log agent out (trap vrto if request times out)
SE-4
/samples/CS-AD/BlindXfer.ppr
1. CTI init
2. Get cti resource
3. Read config file for number to transfer to
4. Use Answer block to wait for call, then wait for established
5. Make blind transfer request
SE-5
/samples/CS-AD/Conference.ppr
1. CTI init
2. Get cti resource
3. Use Answer block to wait for call, then wait for established
4. Handle vrto if time out occurs
5. Read config file for number to conference to
6. Initiate conference using config file number to connect to
7. Complete conference
8. Delay to simulate phone conversation
9. Hang up
SE-6
/samples/CS-AD/ConsultXfer.ppr
1. CTI init
2. Get cti resource
3. Read config file for number to consult transfer to
4. Use Answer block to wait for call, then wait for established
5. Handle vrto if time out occurs
6. Make consult transfer using config file number to connect to
7. Complete conference
8. Hang up as application terminates
Page 60

PeriProducer CTI Toolkit User’s Guide for M1
Page 60 Nortel Networks Confidential # P0606089 Ver: 1.1
SE-7
/samples/CS-AD/cticondition.ppr
SE-8
/samples/CS-AD/HoldAndRetrieve.ppr
1. CTI init
2. Get cti resource
3. Use Answer block to wait for call, then wait for established
4. Make hold call request
5. Delay 3 seconds
6. Make retrieve call request
7. Use cti to wait for release
SE-9
/samples/CS-AD/Nortel-iccm/ACDAgent.ppr
1. CTI init
2. Answer call
3. Wait for Established with a blocking wait
4. Wait for Call Cleared via cti condition
5. Use System services to wait for 5 minutes to get the call cleared
6. Log the reception of cti event, it’s condition data and then exit
SE-10
/samples/CS-AD/Nortel-iccm/anianddnisagent.ppr
1. CTI init & get cti resource
2. Trap error and cticond
3. Read config file for this device (for logging) and Agent DN
4. Log agent in (trap vrto if request times out)
5. Answer call
6. Get ANI & DNIS; speak the values and log them
7. Get tlink data and log it
8. Wait for the call cleared event
9. Log agent out (trap vrto if request times out)
SE-11
/samples/CS-AD/Nortel-iccm/BlindXferAgent.ppr
1. CTI init
2. Read config file for agent DN, this device (for logging) and number to transfer to
3. Get cti resource
4. Log agent in (trap vrto if request times out)
5. Use Answer block to wait for call, then wait for established
6. Make blind transfer request
7. Log agent out (trap vrto if request times out)
8. Free cti re source
SE-12
/samples/CS-AD/Nortel-iccm/ConferenceAgent.ppr
1. CTI init
2. Read config file for agent DN, this device (for logging) and number to conference to
3. Get cti resource
4. Log agent in (trap vrto if request times out)
5. Use Answer block to wait for call, then wait for established
6. Make conference request
7. Log agent out (trap vrto if request times out)
8. Free cti re source
App. # Example Application Name, Location, Function, and Usage
Page 61

Example Applications
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 61
SE-13
/samples/CS-AD/Nortel-iccm/ConsultXferAgent.ppr
1. CTI init
2. Read config file for agent DN, this device (for logging) and number to consult transfer to
3. Ret cti resource
4. Log agent in (trap vrto if request times out)
5. Use Answer block to wait for call, then wait for established
6. Make consult transfer request
7. Log agent out (trap vrto if request times out)
8. Free cti re source
SE-14
/samples/CS-AD/Nortel-iccm/HoldAndRetrieveAgent.ppr
1. CTI init
2. Read config file for agent DN, this device (for logging)
3. Get cti resource
4. Log agent in (trap vrto if request times out)
5. Use Answer block to wait for call, then wait for established
6. Make hold call request
7. Short delay to simulate phone conversation
8. Make retrieve call request
9. Wait for release (trap vrto if request times out)
10. Log agent out (trap vrto if request times out)
(Note that an unexpected disc causes application to log out agent too.)
SE-15
/samples/CS-AD/Nortel-ipml/AnalogueCtiDialer.ppr
1. CTI init
2. Read config file for this device and the number to dial
3. Get cti resource
4. Toggle phone line state on/off
5. Make call request
6. Wait for established
7. Set up cti cond to arrive for release
8. Short delay to simulate phone conversation
9. Make release call request
10. Either arriving cticond or arriving disc terminates application
SE-16
/samples/SCCS-integrate/acdagentwithcalldata.ppr
1. CTI init
2. Read config file for this device and Agent DN
3. Get cti resource
4. Log agent in (trap vrto if request times out)
5. Set agent ready (trap vrto if request times out)
6. Wait for ringing (trap vrto if request times out)
7. Takes call as transferred from tapi_da_ivr_agent.ppr
8. Get callid
9. Make an answer call request
10. Retrieve and log all call data via CSDA
11. Set agent not ready (trap vrto if request times out)
12. Log agent out (trap vrto if request times out)
App. # Example Application Name, Location, Function, and Usage
Page 62

PeriProducer CTI Toolkit User’s Guide for M1
Page 62 Nortel Networks Confidential # P0606089 Ver: 1.1
SE-17
/samples/SCCS-integrate/tapi_da_ivr_agent.ppr
1. CTI init
2. Read config file for this device and Agent DN
3. Get cti resource
4. Log agent out (trap vrto if request times out)
5. Wait 1 second
6. Log agent in (trap vrto if request times out)
7. Answer call
8. Generate call data; send to cti resource
9. Delay to simulate phone conversation
10. Hang up
11. Loop to Answer block and wait for call
App. # Example Application Name, Location, Function, and Usage
Page 63

Example Applications
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 63
Telephony Event Data
App. # Example Application Name, Location, Function, and Usage
TE-1
/samples/CS-AD/ACDAgent.ppr
1. CTI init; read config file for agent DN and this device; get cti resource
2. Log agent in (trap vrto if request times out)
3. Set agent ready (trap vrto if request times out)
4. Wait 5 minutes to answer call via cti calls (not traditional vrto if request times out);
Answer block; wait for release
5. Set agent not ready (trap vrto if request times out)
6. Log agent out (trap)
TE-2
/samples/CS-AD/AniAndDnis.ppr
1. CTI init; get cti resource
2. Use Answer block to wait for call, then wait for established
3. Get ANI & DNIS
4. Get Telephony Link Data
5. Wait for release
TE-3
/samples/CS-AD/HoldAndRetrieve.ppr
1. CTI init
2. Get cti resource
3. Use Answer block to wait for call, then wait for established
4. Make hold call request
5. Delay 3 seconds
6. Make retrieve call request
7. Use cti to wait for release
TE-4
/samples/CS-AD/Nortel-iccm/ACDAgent.ppr
Duplicate storage for samples/CS-AD/ACDAgent.ppr
TE-5
/samples/CS-AD/Nortel-iccm/anianddnisagent.ppr
1. CTI init
2. Read config file for agent DN and this device (for logging)
3. Get cti resource
4. Log agent in (trap vrto if request times out)
5. Use Answer block to wait for call, then wait for established
6. Get ANI & DNIS
7. Get Telephony Link Data
8. Wait for release
TE-6
/samples/CS-AD/Nortel-iccm/GetACDGroupStatus.ppr
1. CTI init
2. Read config file for agent DN and this device (for logging)
3. Get cti resource
4. Get acdgroupstatus for a hardcoded device , log data received
5. Termina te app lic ati on
Page 64

PeriProducer CTI Toolkit User’s Guide for M1
Page 64 Nortel Networks Confidential # P0606089 Ver: 1.1
TE-7
/samples/CS-AD/Nortel-iccm/HoldAndRetrieveAgent.ppr
1. CTI init
2. Read config file for agent DN, this device (for logging)
3. Get cti resource
4. Log agent in (trap vrto if request times out)
5. Use Answer block to wait for call, then wait for established
6. Make hold call request
7. Short delay to simulate phone conversation
8. Make retrieve call request
9. Wait for release (trap vrto if request times out)
10. Log agent out (trap vrto if request times out)
11. Note that an unexpected disc causes application to log out agent too
TE-8
/samples/CS-AD/testrequestdeviceparams.ppr
1. Error trapping is set up, cti resource is obtained and this device is registered.
2. A loop is st arted tha t s end s e ach ty pe o f Para m Na me to c t i f or th e s am e Dev ic e Num be r.
3. The loop exits and the cti resource is free d as the appl ic ati on te rmi nat es . No te th at at the
end of an IVR application’s execution, the cti resource is freed automatically.
TE-9
/samples/SCCS-integrate/acdagentwithcalldata.ppr
1. CTI init
2. Read config file for this device and Agent DN
3. Get cti resource
4. Log agent in (trap vrto if request times out)
5. Set agent ready (trap vrto if request times out)
6. Wait for ringing (trap vrto if request times out)
7. Takes call as transferred from tapi_da_ivr_agent.ppr
8. Get callid
9. Make an answer call request
10. Retrieve and log all call data via CSDA
11. Set agent not ready (trap vrto if request times out)
12. Log agent out (trap vrto if request times out)
TE-10
/samples/SCCS-integrate/tapi_da_ivr_agent.ppr
1. Log start of application
2. CTI init & get cti resource
3. Trap vrto, error and cticond
4. Read config file for this device (for logging & call data), Agent DN and number to blind
transfer to
5. Log agent out (trap vrto if request times out)
6. Wait 1 second
7. Log agent in (trap vrto if request times out)
8. Answers call from Dialer.ppr
9. Waits for established
10. Get ANI/DNIS and other call data; log it
11. Gets statistical group data via SCCS RSM
12. Generates call data, sends it to CSTAPI and in turn Symposium TAPI Server
13. Regenerates similar call data, sends it to CSS via CSDA
14. Either disconnect so that SCCS CDN can take over routing of call (if number =####) OR
make a blind transfer
15. Log end of application, wait in Answer block
App. # Example Application Name, Location, Function, and Usage
Page 65
Example Applications
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 65
Telephony Request
App. # Example Application Name, Location, Function, and Usage
TR-1
/samples/CS-AD/ACDAgent.ppr
1. CTI init; read config file for agent DN and this device; get cti resource
2. Log agent in (trap vrto if request times out)
3. Set agent ready (trap vrto if request times out)
4. Wait 5 minutes to answer call via cti calls; not traditional Answer block; wait for release
5. Set agent not ready (trap vrto if request times out)
6. Log agent out (trap vrto if request times out)
TR-2
/samples/CS-AD/BlindXfer.ppr
1. CTI init
2. Get cti resource
3. Read config file for number to transfer to
4. Use Answer block to wait for call, then wait for established
5. Make blind transfer request
TR-3
/samples/CS-AD/Conference.ppr
1. CTI init
2. Get cti resource
3. Use Answer block to wait for call, then wait for established
4. Handle vrto if time out occurs
5. Read config file for number to conference to
6. Initiate conference using config file number to connect to
7. Complete conference
8. Delay to simulate phone conversation
9. Hang up
TR-4
/samples/CS-AD/ConsultXfer.ppr
1. CTI init
2. Get cti resource
3. Read config file for number to consult transfer to
4. Use Answer block to wait for call, then wait for established
5. Handle vrto if time out occurs
6. Make consult transfer using config file number to connect to
7. Complete conference
8. Hang up as application terminates
TR-5
/samples/CS-AD/HoldAndRetrieve.ppr
1. CTI init
2. Get cti resource
3. Use Answer block to wait for call, then wait for established
4. Make hold call request
5. Delay 3 seconds
6. Make retrieve call request
7. Use cti to wait for release
TR-6
/samples/CS-AD/Nortel-iccm/ACDAgent.ppr
Duplicate storage for samples/CS-AD/ACDAgent.ppr
Page 66

PeriProducer CTI Toolkit User’s Guide for M1
Page 66 Nortel Networks Confidential # P0606089 Ver: 1.1
TR-7
/samples/CS-AD/Nortel-iccm/BlindXferAgent.ppr
1. CTI init
2. Read config file for agent DN, this device (for logging) and number to transfer to
3. Get cti resource
4. Log agent in (trap vrto if request times out)
5. Use Answer block to wait for call, then wait for established
6. Make blind transfer request
7. Log agent out (trap vrto if request times out)
8. Free cti re source
TR-8
/samples/CS-AD/Nortel-iccm/ConferenceAgent.ppr
1. CTI init
2. Read config file for agent DN, this device (for logging) and number to conference to
3. Get cti resource
4. Log agent in (trap vrto if request times out)
5. Use Answer block to wait for call, then wait for established
6. Make conference request
7. Log agent out (trap vrto if request times out)
8. Free cti re source
TR-9
/samples/CS-AD/Nortel-iccm/ConsultXferAgent.ppr
1. CTI init
2. Read config file for agent DN, this device (for logging) and number to consult transfer to
3. Get cti resource
4. Log agent in (trap vrto if request times out)
5. Use Answer block to wait for call, then wait for established
6. Make consult transfer request
7. Log agent out (trap vrto if request times out)
8. Free cti re source
TR-10
/samples/CS-AD/Nortel-iccm/HoldAndRetrieveAgent.ppr
1. CTI init
2. Read config file for agent DN, this device (for logging)
3. Get cti resource
4. Log agent in (trap vrto if request times out)
5. Use Answer block to wait for call, then wait for established
6. Make hold call request
7. Short delay to simulate phone conversation
8. Make retrieve call request
9. Wait for release (trap vrto if request times out)
10. Log agent out (trap vrto if request times out)
11. Note that an unexpected disc causes application to log out agent too
App. # Example Application Name, Location, Function, and Usage
Page 67

Example Applications
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 67
TR-11
/samples/CS-AD/Nortel-ipml/AnalogueCtiDialer.ppr
1. CTI init
2. Read config file for this device and the number to dial
3. Get cti resource
4. Toggle phone line state on/off
5. Make call request
6. Wait for established
7. Set up cti cond to arrive for release
8. Short delay to simulate phone conversation
9. Make release call request
10. Either arriving cticond or arriving disc terminates application
TR-12
/samples/SCCS-integrate/acdagentwithcalldata.ppr
1. CTI init
2. Read config file for this device and Agent DN
3. Get cti resource
4. Log agent in (trap vrto if request times out)
5. Set agent ready (trap vrto if request times out)
6. Wait for ringing (trap vrto if request times out)
7. Takes call as transferred from tapi_da_ivr_agent.ppr
8. Get callid
9. Make an answer call request
10. Retrieve and log all call data via CSDA
11. Set agent not ready (trap vrto if request times out)
12. Log agent out (trap vrto if request times out)
TR-13
/samples/SCCS-integrate/tapi_da_ivr_agent.ppr
1. Log start of application
2. CTI init & get cti resource
3. Trap vrto, error and cticond
4. Read config file for this device (for logging & call data), Agent DN and number to blind
transfer to
5. Log agent out (trap vrto if request times out)
6. Wait 1 second
7. Log agent in (trap vrto if request times out)
8. Answers call from Dialer.ppr
9. Waits for established
10. Get ANI/DNIS and other call data; log it
11. Gets statistical group data via SCCS RSM
12. Generates call data, sends it to CSTAPI and in turn Symposium TAPI Server
13. Regenerates similar call data, sends it to CSS via CSDA
14. Either disconnect so that SCCS CDN can take over routing of call (if number =####) OR
make a blind transfer
15. Log end of application, wait in Answer block
App. # Example Application Name, Location, Function, and Usage
Page 68

PeriProducer CTI Toolkit User’s Guide for M1
Page 68 Nortel Networks Confidential # P0606089 Ver: 1.1
User Data
App. # Example Application Name, Location, Function, and Usage
UD-1
/samples/CS-AD/AniAndDnis.ppr
1.
2. CTI init; get cti resource
3. Use Answer block to wait for call, then wait for established
4. Get ANI & DNIS
5. Get Telephony Link Data
6. Wait for release
UD-2
/samples/CS-AD/Nortel-iccm/anianddnisagent.ppr
1. CTI init
2. Read config file for agent DN and this device (for logging)
3. Get cti resource
4. Log agent in (trap vrto if request times out)
5. Use Answer block to wait for call, then wait for established
6. Get ANI & DNIS
7. Get Telephony Link Data
8. Wait for release
UD-3
/samples/SCCS-integrate/acdagentwithcalldata.ppr
1. CTI init
2. Read config file for this device and Agent DN
3. Get cti resource
4. Log agent in (trap vrto if request times out)
5. Set agent ready (trap vrto if request times out)
6. Wait for ringing (trap vrto if request times out)
7. Takes call as transferred from tapi_da_ivr_agent.ppr
8. Get callid
9. Make an answer call request
10. Retrieve and log all call data via CSDA
11. Set agent not ready (trap vrto if request times out)
12. Log agent out (trap vrto if request times out)
UD-4
/samples/SCCS-integrate/ad.ppr
1. CTI init
2. Read config file for this device and Agent DN
3. Get cti resource
4. Log agent out (trap vrto if request times out)
5. Wait 1 second
6. Log agent in (trap vrto if request times out)
7. Answer call
8. Generate call data; send to cti resource
9. Delay to simulate phone conversation
10. Hang up
11. Loop to Answer block and wait for call
Page 69

Example Applications
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 69
Device Statistics Data
UD-5
/samples/SCCS-integrate/tapi_da_ivr_agent.ppr
1. Log start of application
2. CTI init & get cti resource
3. Trap vrto, error and cticond
4. Read config file for this device (for logging & call data), Agent DN and number to blind
transfer to
5. Log agent out (trap vrto if request times out)
6. Wait 1 second
7. Log agent in (trap vrto if request times out)
8. Answers call from Dialer.ppr
9. Waits for established
10. Get ANI/DNIS and other call data; log it
11. Gets statistical group data via SCCS RSM
12. Generates call data, sends it to CSTAPI and in turn Symposium TAPI Server
13. Regenerates similar call data, sends it to CSS via CSDA
14. Either disconnect so that SCCS CDN can take over routing of call (if number =####) OR
make a blind transfer
15. Log end of application, wait in Answer block
App. # Example Application Name, Location, Function, and Usage
DS-1
/samples/SCCS-integrate/tapi_da_ivr_agent.ppr
1. Log start of application
2. CTI init & get cti resource
3. Trap vrto, error and cticond
4. Read config file for this device (for logging & call data), Agent DN and number to blind
transfer to
5. Log agent out (trap vrto if request times out)
6. Wait 1 second
7. Log agent in (trap vrto if request times out)
8. Answers call from Dialer.ppr
9. Waits for established
10. Get ANI/DNIS and other call data; log it
11. Gets statistical group data via SCCS RSM
12. Generates call data, sends it to CSTAPI and in turn Symposium TAPI Server
13. Regenerates similar call data, sends it to CSS via CSDA
14. Either disconnect so that SCCS CDN can take over routing of call (if number =####) OR
make a blind transfer
15. Log end of application, wait in Answer block
App. # Example Application Name, Location, Function, and Usage
Page 70

PeriProducer CTI Toolkit User’s Guide for M1
Page 70 Nortel Networks Confidential # P0606089 Ver: 1.1
Send TAPI CallData/Send TAPIsccs CallData
App. # Example Application Name, Location, Function, and Usage
ST-1
/samples/SCCS-integrate/tapi_da_ivr_agent.ppr
1. Log start of application
2. CTI init & get cti resource
3. Trap vrto, error and cticond
4. Read config file for this device (for logging & call data), Agent DN and number to blind
transfer to
5. Log agent out (trap vrto if request times out)
6. Wait 1 second
7. Log agent in (trap vrto if request times out)
8. Answers call from Dialer.ppr
9. Waits for established
10. Get ANI/DNIS and other call data; log it
11. Gets statistical group data via SCCS RSM
12. Generates call data, sends it to CSTAPI and in turn Symposium TAPI Server
13. Regenerates similar call data, sends it to CSS via CSDA
14. Either disconnect so that SCCS CDN can take over routing of call (if number =####) OR
make a blind transfer
15. Log end of application, wait in Answer block
Page 71

Example Applications
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 71
Log Message
Example Application Name, Location, Function, and Usage
The following example applications illustrate the use of the Log Message block:
/samples/CS-AD/ACDAgent.ppr
/samples/CS-AD/ACDPhoneLoginLogout.ppr
/samples/CS-AD/AniAndDnis.ppr
/samples/CS-AD/Anologue.ppr
/samples/CS-AD/BlindXfer.ppr
/samples/CS-AD/Conference.ppr
/samples/CS-AD/ConsultXfer.ppr
/samples/CS-AD/cticondition.ppr
/samples/CS-AD/Dialer.ppr
/samples/CS-AD/HoldAndRetrieve.ppr
/samples/CS-AD/Nortel-iccm/ACDAgent.ppr
/samples/CS-AD/Nortel-iccm/ACDPhoneLoginLogout.ppr
/samples/CS-AD/Nortel-iccm/AgentLogout.ppr
/samples/CS-AD/Nortel-iccm/anianddnisagent.ppr
/samples/CS-AD/Nortel-iccm/BlindXferAgent.ppr
/samples/CS-AD/Nortel-iccm/ConferenceAgent.ppr
/samples/CS-AD/Nortel-iccm/ConsultXferAgent.ppr
/samples/CS-AD/Nortel-iccm/Dialer.ppr
/samples/CS-AD/Nortel-iccm/dmsloginlogout.ppr
/samples/CS-AD/Nortel-iccm/GetACDGroupStatus.ppr
/samples/CS-AD/Nortel-iccm/HoldAndRetrieveAgent.ppr
/samples/CS-AD/Nortel-ipml/AnalogueCtiDialer.ppr
/samples/CS-AD/Nortel-ipml/AnaloguePhoneLoginLogout.ppr
/samples/CS-AD/testrequestdeviceparams.ppr
/samples/SCCS-integrate/acdagentwithcalldata.ppr
/samples/SCCS-integrate/ad.ppr
/samples/SCCS-integrate/analogueivragent.ppr
/samples/SCCS-integrate/Dialer.ppr
/samples/SCCS-integrate/tapi_da_ivr_agent.ppr
Page 72

PeriProducer CTI Toolkit User’s Guide for M1
Page 72 Nortel Networks Confidential # P0606089 Ver: 1.1
This page has been intentionally left blank.
Page 73

Example Log Files
Page 74

PeriProducer CTI Toolkit User’s Guide for M1
Page 74 Nortel Networks Confidential # P0606089 Ver: 1.1
Example Log Files
This appendix provides example log files for each of the CTI Toolkit blocks.
Agent Function CSVAPI Log File
CTI Initialize CSVAPI Log File
Register Device CSVAPI Log File
Request from the Tool Kit
12/04/200 0 17:21:05 option SendRespo nse value No
12/04/2000 17:21:05 option AgentId value 1503
12/04/2000 17:21:05 option SetWaitEvent value LoggedOn
12/04/2000 17:21:05 option CtiFunction value AgentSetLogOn
Response was ignored by CSVAPI (due to SendResponse value being No)
12/04/2000 17:21:05 clm-tlsdefault: Sending CsSetAgentState Response to Client 9
12/04/2000 17:21:05 This Device => 2103
12/04/2000 17:21:05 Status => Success
12/04/2000 17:21:05 csvapi: SetAgentState ignored for phoneline 52
OC was sent to Tool Kit Module
12/04/2000 17:21:06 clm_C op yL as tClnt Event: event queueing is turned on for client 9, dn ’2103’
12/04/2000 17:21:06 clm_CopyLastClntEvent: creating new event queue
12/04/2000 17:21:06 clm-tlsdefault: Sending CsLoggedOn Event to client 9
12/04/2000 17:21:06 This Device => 2103
12/04/2000 17:21:06 Agent ID => 1503
12/04/2000 17:21:06 TLinkData => "AgentSetFeature,4353", "Split,6400", "ThisDN,6400", "TN_This,11",
"PBXTimeStamp,7:58:14"
12/04/2000 17:21:06 send_apmi_msg: Sent ’oc’ to vms 1, phoneline 52 with data <LoggedOn>
Request from the Tool Kit for CTI resource in CSVAPI.log
10/26/2000 07:01:09 apmi_issue_get_resource: vms 1, phoneline 51 get resource request
Request from the Tool Kit for cstapi resource in CSVAPI.log
12/08/2000 15:52:11 apmi_issue_get_resource: vms 1, phoneline 54 get resource request
Request from the Tool Kit for registration of a DN
12/04/200 0 17:21:05 option SendRespo nse value Yes
12/04/2000 17:21:05 option DirectoryNumber value 1503
12/04/2000 17:21:05 option CtiFunction value RegisterAddress
Page 75

Example Log Files
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 75
Set Event Handling CSVAPI Log File
CSVAPI Receive Set Wait Event for Established after it answers the call. Until CSVAPI receives a Set Wait Event
Option, it will queue up 10 messages for each Phone Line.
12/04/2000 17:21:29 apmi_got_send_resource: vms 1, phoneline 52 message converted to v-shell options =>
12/04/200 0 17:21:29 option SendRespo nse value No
12/04/200 0 17:21:29 option SetWaitEvent value established
12/04/2000 17:21:29 option CtiFunction value ProcessEvent
12/04/2000 17:21:29 ProcessEvent: clm get ting last event callid 0
12/04/2000 17:21:29 clm-CSVAPI: Received CsSetWaitEvent Request from Client 9
12/04/2000 17:21:29 Device => 2103
12/04/2000 17:21:29 CsEventList => Established
12/04/2000 17:21:30 clm-C SVAPI: Sending CsSetWaitEvent Respon se to Client 9
12/04/2000 17:21:30 This Device => 2103
12/04/2000 17:21:30 Status => Success
12/04/2000 17:21:30 CSVAPI: SetWaitEvent ignored for phoneline 52
CSVAPI ignores all of the events and waits until the Established Event has arrived. At that time, it sends "oc" to
IVR application:
12/04/2000 17:21:26 clm-tlsdefault: Ignoring/Queueing CsQueued Event for client 2
12/04/2000 17:21:26 This Device => 6400
12/04/2000 17:21:26 Call ID => 24
12/04/2000 17:21:26 Other Device(s) => 6702, 5008
12/04/2000 17:21:26 Que ue Coun t => 0
12/04/2000 17:21:26 CallData => "queue_pos_AMEX,0", "queue_pos_NT,0", "queue_pos_UNIX,0",
"queue_pos_VISA,0", "expected_wait_AMEX,0", "expected_wait_NT,0",
"expected_wait_UNIX,0 ", "expe cte d_wa it_ VISA,0"
12/04/2000 17:21:26 OldState => Null
12/04/2000 17:21:26 NewState => Queued
12/04/2000 17:21:26 TLinkData => "DNIS,6702", "ANI,5008", "ArrivalTime,12/04/00 17:21:12.968",
"Treatment,9999", "DeviceType,2", "ACDLine,0", "InternalCall,1"
12/04/2000 17:21:26 clm_C op yL as tClnt Event: event queueing is turned on for client 9, dn ’2103’
CSVAPI Sends "oc" when it receives Established Event:
12/04/2000 17:21:30 clm-tlsdefault: Sending CsEstablished Event to client 9
12/04/2000 17:21:30 This Device => 2103
12/04/2000 17:21:30 Call ID => 24
12/04/2000 17:21:30 Other Device(s) => 6702, 5008
12/04/2000 17:21:30 DNIS => 6702
12/04/2000 17:21:30 ANI => 5008
12/04/2000 17:21:30 CallData => "queue_pos_AMEX,0", "queue_pos_NT,0", "queue_pos_UNIX,0",
"queue_pos_VISA,0", "expected_wait_AMEX,0", "expected_wait_NT,0",
"expected_wait_UNIX,0 ", "expe cte d_wa it_ VISA,0"
12/04/2000 17:21:30 OldState => Alerting
12/04/2000 17:21:30 NewState => Connected
Page 76

PeriProducer CTI Toolkit User’s Guide for M1
Page 76 Nortel Networks Confidential # P0606089 Ver: 1.1
Telephony Event Data CSVAPI Log File
7
12/04/2000 17:21:30 TLinkData => "TN_This,11", "TN_Other,132", "PBXCallId,24", "PBXTimeStamp,7:58:38",
"DNIS,6702", "ANI,5008", "ArrivalTime,12/04/00 17:21:12.968", "DeviceType,6",
"PositionID,2103", "AC DLine,1", "InternalCall,1"
12/04/2000 17:21:30 send_apmi_msg: Sent ’oc’ to vms 1, phoneline 52 with data <Established>
CSVAPI Sends "oc" when it receives Established Event:
CSVAPI Receive Set Wait Event for Established after it answers the call. Until CSVAPI receives a Set Wait Event
Option, it will queue up 10 messages for each Phone Line.
12/04/2000 17:21:29 apmi_got_send_resource: vms 1, phoneline 52 message converted to v-shell options =>
12/04/200 0 17:21:29 option SendRespo nse value No
12/04/200 0 17:21:29 option SetWaitEvent value established
12/04/2000 17:21:29 option CtiFunction value ProcessEvent
12/04/2000 17:21:29 ProcessEvent: clm getting last event callid 0
12/04/2000 17:21:29 clm-CSVAPI: Received CsSetWaitEvent Request from Client 9
12/04/2000 17:21:29 Device => 2103
12/04/2000 17:21:29 CsEventList => Established
12/04/2000 17:21:30 clm-CSVAPI: Sending CsSetWaitEvent Response to Client 9
12/04/2000 17:21:30 This Device => 2103
12/04/2000 17:21:30 Status => Success
12/04/2000 17:21:30 CSVAPI: SetWaitEvent ignored for phoneline 52
CSVAPI ignores all of the events and waits until the Established Event has arrived. At that time, it sends "oc" to
IVR application.
12/04/2000 17:21:26 clm-tlsdefault: Ignoring/Queueing CsQueued Event for client 2
12/04/2000 17:21:26 This Device => 6400
12/04/2000 17:21:26 Call ID => 24
12/04/2000 17:21:26 Other Device(s) => 6702, 5008
12/04/2000 17:21:26 Que ue Coun t => 0
12/04/2000 17:21:26 CallData => "queue_pos_AMEX,0", "queue_pos_NT,0", "queue_pos_UNIX,0",
"queue_pos_VISA,0", "expected_wait_AMEX,0", "expected_wait_NT,0",
"expected_wait_UNIX,0 ", "expe cte d_wa it_ VISA,0"
12/04/2000 17:21:26 OldState => Null
12/04/2000 17:21:26 NewState => Queued
12/04/2000 17:21:26 TLinkData => "DNIS,6702", "ANI,5008", "ArrivalTime,12/04/00 17:21:12.968",
"Treatment,9999", "DeviceType,2", "ACDLine,0", "InternalCall,1"
12/04/2000 17:21:26 clm_CopyLastClntEvent: event queueing is turned on for client 9, dn ’2103’
Page 77

Example Log Files
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 77
CSVAPI Sends "oc" when it receives Established Event
12/04/2000 17:21:30 clm-tlsdefault: Sending CsEstablished Event to client 9
12/04/2000 17:21:30 This Device => 2103
12/04/2000 17:21:30 Call ID => 24
12/04/2000 17:21:30 Other Device(s) => 6702, 5008
12/04/2000 17:21:30 DNIS => 6702
12/04/2000 17:21:30 ANI => 5008
12/04/2000 17:21:30 CallData => "queue_pos_AMEX,0", "queue_pos_NT,0", "queue_pos_UNIX,0",
"queue_pos_VISA,0", "expected_wait_AMEX,0", "expected_wait_NT,0",
"expected_wait_UNIX,0 ", "expe cte d_wa it_ VISA,0"
12/04/2000 17:21:30 OldState => Alerting
12/04/2000 17:21:30 NewState => Connected
12/04/2000 17:21:30 TLinkData => "TN_This,11", "TN_Other,132", "PBXCallId,24", "PBXTimeStamp,7:58:38",
"DNIS,6702", "ANI,5008", "ArrivalTime,12/04/00 17:21:12.968", "DeviceType,6",
"PositionID,2103", "AC DLine,1", "InternalCall,1"
12/04/2000 17:21:30 send_apmi_msg: Sent ’oc’ to vms 1, phoneline 52 with data <Established>
CSVAPI Sends ANI/DNIS to the Application (from Established Event)
12/04/2000 17:21:30 apmi_got_send_resource: vms 1, phoneline 52 message converted to v-shell options =>
12/04/200 0 17:21:30 option RetrieveValue value eventani
12/04/2000 17:21:30 send_apmi_msg: Queued message to vms 1, phoneline 52 with dat a <Retri eveValue ev entani
EventData:(ani:"5008")>
12/04/2000 17:21:30 apmi_got_send_resource: vms 1, phoneline 52 message converted to v-shell options =>
12/04/200 0 17:21:30 option RetrieveValue value eventdnis
12/04/2000 17:21:30 send_apmi_msg: Queued message to vms 1, phoneline 52 with data <RetrieveValue
eventdnis EventData:(dnis:"6702")>
Page 78

PeriProducer CTI Toolkit User’s Guide for M1
Page 78 Nortel Networks Confidential # P0606089 Ver: 1.1
Telephony Request CSVAPI Log File
CSVAPI Receives Blind Transfer Request and Sends the Request to TLS
01/19/2001 11:01:08 apmi_got_send_resource: vms 3, phoneline 2 message converted to v-shell options =>
01/19/2001 11:01:08 option SendResponse value No
01/19/2001 11:01:08 option SetWaitEvent value established
01/19/2001 11:01:08 option CtiFunction value ProcessEvent
01/19/2001 11:01:08 ProcessEvent: clm getting last event callid 0
01/19/2001 11:01:08 clm-CSVAPI: Received CsSetWaitEvent Request from Client 6
01/19/2001 11:01:08 Device => 2015
01/19/2001 11:01:08 CsEventList => Established
01/19/2001 1 1: 01:08 clm_CopyLastClntEvent: event queueing is turned on for clie nt 6, dn ’2015’
01/19/2001 11:01:08 clm_CopyLastClntEvent: number of events in queue = 2
01/19/2001 11:01:08 CSVAPI-clm: evnt_reseteventdata_in_clnttables
01/19/2001 11:01:08 CSVAPI-clm: evnt_reseteventdata_in_clnttables
01/19/2001 11:01:08 clm-tlsdefault: Sending CsEstablished Event to client 6
01/19/2001 11:01:08 This Device => 2015
01/19/2001 11:01:08 Call ID => 61
01/19/2001 11:01:08 Other Device(s) => 2014
01/19/2001 11:01:08 DNIS => 2015
01/19/2001 1 1: 01: 08 ANI => 2014
01/19/2001 1 1: 01: 08 OldS tate => Alerting
01/19/2001 11:01:08 NewState => Connected
01/19/2001 11:01:08 TLinkData => "TN_This,203", "TN_Other,202", "PBXCallId,61", "PBXTimeStamp,11:2:38",
"DNIS,2015", "ANI,2014", "ArrivalTime,01/19/01 11:01:05.281", "DeviceType,1", "ACDLine,0",
"InternalCall,1"
01/19/2001 11:01:08 send_apmi_msg: Sent ’oc’ to vms 3, phoneline 2 with data <Established >
01/19/2001 1 1: 01:08 clm_CopyLastClntEvent: event queueing is turned on for clie nt 5, dn ’2014’
01/19/2001 11:01:08 clm_CopyLastClntEvent: number of events in queue = 11
01/19/2001 11:01:08 clm_CopyLastClntEvent: event queue size maximum of 10 has been reached
01/19/2001 11:01:08 clm-tlsdefault: Ignoring/Queueing CsEstablished Event for client 5
01/19/2001 11:01:08 This Device => 2014
01/19/2001 11:01:08 Call ID => 61
01/19/2001 11:01:08 Other Device(s) => 2015
01/19/2001 11:01:08 DNIS => 2015
01/19/2001 1 1: 01: 08 ANI => 2014
01/19/2001 1 1: 01: 08 OldS tate => Initiated
01/19/2001 11:01:08 NewState => Connected
01/19/2001 1 1: 01:08 TLinkData => "DNIS,2015", "ANI,2014", "ArrivalTime,01/19/01 11:01:05.281", "Device Type,1",
"ACDLine,0", "InternalCall,1"
01/19/2001 11:01:08 clm-CSVAPI: Sending CsSetWaitEvent Response to Client 6
01/19/2001 11:01:08 This Device => 2015
01/19/2001 11:01:08 Status => Success
01/19/2001 11:01:08 CSVAPI: SetWaitEvent ignored for phoneline 2
01/19/2001 11:01:08 apmi_got_send_resource: vms 3, phoneline 2 message converted to v-shell options =>
01/19/2001 11:01:08 option SendResponse value No
Page 79

Example Log Files
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 79
01/19/2001 11:01:08 option DestinationNumber value 6200
01/19/2001 11:01:08 option SetWaitEvent value Dialing
01/19/200 1 11:01:08 option Ctifunct ion value BlindTransfer
01/19/2001 11:01:08 BlindTransfer: clm getting last event callid 61
01/19/2001 11:01:08 clm-CSVAPI: Received CsBlindTransfer Request from Client 6
01/19/2001 11:01:08 Calling Device => 2015
01/19/2001 11:01:08 Call ID => 61
01/19/2001 11:01:08 Called Device => 6200
01/19/2001 11:01:08 CsEventList => Dialing
CSVAPI Receives Blind Transfer Request and Sends the Request to TLS
CSVAPI Receives Blind Transfer Response from TLS and Ignores it
01/19/2001 11:01:08 clm-tlsdefault: Sending CsBlindTransfer Response to Client 6
01/19/2001 11:01:08 This Device => 2015
01/19/2001 1 1:01:08 Status => Succes s
01/19/2001 11:01:08 CSVAPI: BlindTransfer ignored for phoneline 2
Page 80

PeriProducer CTI Toolkit User’s Guide for M1
Page 80 Nortel Networks Confidential # P0606089 Ver: 1.1
CSVAPI Receive Held Event from TLS a nd Queues the Event
01/19/2001 1 1: 01:08 clm_CopyLastClntEvent: event queueing is turned on for clie nt 6, dn ’2015’
01/19/2001 11:01:08 clm_CopyLastClntEvent: creating new event queue
01/19/2001 11:01:08 clm-tlsdefault: Ignoring/Queueing CsHeld Event for client 6
01/19/2001 11:01:08 This Device => 2015
01/19/2001 11:01:08 Call ID => 61
01/19/2001 11:01:08 Other Device(s) => 2014
01/19/2001 11:01:08 DNIS => 2015
01/19/2001 1 1: 01: 08 ANI => 2014
01/19/2001 1 1:01:08 OldState => Conne cte d
01/19/2001 11:01:08 NewState => Held
01/19/2001 11:01:08 TLinkData => "TN_This,203", "TN_Other,202", "PBXCallId,61", "PBXTimeStamp,11:2:38",
"DNIS,2015", "ANI,2014", "ArrivalTime,01/19/01 11:01:05.281", "DeviceType,1", "ACDLine,0",
"InternalCall,1"
01/19/2001 1 1: 01:08 clm_CopyLastClntEvent: event queueing is turned on for clie nt 6, dn ’2015’
CSVAPI Receives Dialing Event from TLS and Send "oc" to Application
01/19/2001 11:01:08 clm_CopyLastClntEvent: number of events in queue = 2
01/19/2001 11:01:08 CSVAPI-clm: evnt_reseteventdata_in_clnttables
01/19/2001 11:01:08 clm-tlsdefault: Sending CsDialing Event to client 6
01/19/2001 11:01:08 This Device => 2015
01/19/2001 11:01:08 Call ID => 161
01/19/2001 11:01:08 Other Device(s) => 6200
01/19/2001 11:01:08 DNIS => 6200
01/19/2001 1 1: 01: 08 ANI => 2015
01/19/2001 1 1: 01:08 OldState => Null
01/19/2001 11:01:08 NewState => Initiated
01/19/2001 1 1: 01:08 TLinkData => "DNIS,6200", "ANI,2015", "ArrivalTime,01/19/01 11:01:08.686", "Device Type,1",
"ACDLine,0", "InternalCall,1"
01/19/2001 11:01:08 send_apmi_msg: Sent ’oc’ to vms 3, phoneline 2 with data <Dialing >
Page 81

Example Log Files
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 81
CSVAPI Receives Queued and Redirect Event for the CDN from TLS, No Apps are attached
01/19/2001 1 1: 01:08 clm_CopyLastClntEvent: event queueing is turned on for clie nt 2, dn ’6200’
01/19/2001 11:01:08 clm_CopyLastClntEvent: number of events in queue = 11
01/19/2001 11:01:08 clm_CopyLastClntEvent: event queue size maximum of 10 has been reached
01/19/2001 11:01:08 clm-tlsdefault: Ignoring/Queueing CsQueued Event for client 2
01/19/2001 11:01:08 This Device => 6200
01/19/2001 11:01:08 Call ID => 161
01/19/2001 11:01:08 Other Device(s) => 2015
01/19/2001 1 1: 01:08 Queue Count => 0
01/19/2001 1 1: 01:08 OldState => Null
01/19/2001 11:01:08 NewState => Queued
01/19/2001 1 1: 01:08 TLinkData => "DNIS,6200", "ANI,2 01 5", "ArrivalTim e,01 /19/01 11:01:08.686", " Devi ce Type,2",
"ACDLine,0", "InternalCall,1"
01/19/2001 1 1: 01:08 clm_CopyLastClntEvent: event queueing is turned on for clie nt 2, dn ’6200’
01/19/2001 11:01:08 clm_CopyLastClntEvent: number of events in queue = 11
01/19/2001 11:01:08 clm_CopyLastClntEvent: event queue size maximum of 10 has been reached
01/19/2001 11:01:08 clm-tlsdefault: Ignoring/Queueing CsRedirect Event for client 2
01/19/2001 11:01:08 This Device => 6200
01/19/2001 11:01:08 Call ID => 161
01/19/2001 11:01:08 Other Device(s) => 2015, 3000
01/19/2001 1 1: 01:08 OldState => Queued
01/19/2001 11:01:08 NewState => Null
01/19/2001 1 1: 01:08 TLinkData => "DNIS,6200", "ANI,2 01 5", "ArrivalT ime,01/19/01 11:01:08.686 ", " Devi ce Type,2",
"ACDLine,0", "InternalCall,1"
01/19/2001 1 1: 01:08 clm_CopyLastClntEvent: event queueing is turned on for clie nt 2, dn ’6200’
01/19/2001 11:01:08 clm_CopyLastClntEvent: number of events in queue = 11
01/19/2001 11:01:08 clm_CopyLastClntEvent: event queue size maximum of 10 has been reached
01/19/2001 11:01:08 clm-tlsdefault: Ignoring/Queueing CsQueued Event for client 2
01/19/2001 11:01:08 This Device => 6200
01/19/2001 11:01:08 Call ID => 161
01/19/2001 11:01:08 Other Device(s) => 2015, 3000
01/19/2001 1 1: 01:08 Queue Count => 0
01/19/2001 1 1: 01:08 OldState => Null
01/19/2001 11:01:08 NewState => Queued
01/19/2001 1 1: 01:08 TLinkData => "DNIS,6200", "ANI,2 01 5", "ArrivalTim e,01 /19/01 11:01:08.686", " Devi ce Type,2",
"ACDLine,0", "InternalCall,1"
01/19/2001 1 1: 01:08 clm_CopyLastClntEvent: event queueing is turned on for clie nt 2, dn ’6200’
01/19/2001 11:01:08 clm_CopyLastClntEvent: number of events in queue = 11
01/19/2001 11:01:08 clm_CopyLastClntEvent: event queue size maximum of 10 has been reached
01/19/2001 11:01:08 clm-tlsdefault: Ignoring/Queueing CsTransferred Event for client 2
01/19/2001 11:01:08 This Device => 6200
01/19/2001 11:01:08 Call ID => 61
01/19/2001 11:01:08 Other Device(s) => 2014
01/19/2001 11:01:08 Other Call ID => 161
01/19/2001 1 1: 01:08 OldState => Queued
01/19/2001 11:01:08 NewState => Queued
Page 82

PeriProducer CTI Toolkit User’s Guide for M1
Page 82 Nortel Networks Confidential # P0606089 Ver: 1.1
01/19/2001 11:01:08 TLinkData => "CallProgressEvent,112", "TN_this,203", "TN_other,4", "DNIS,2015",
"ANI,2014", "ArrivalTime,01/19/01 11:01:05.281", "DeviceType,0", "A CDL ine ,0" ,
"InternalCall,1"
01/19/2001 1 1: 01:08 clm_CopyLastClntEvent: event queueing is turned on for clie nt 6, dn ’2015’
01/19/2001 11:01:08 clm_CopyLastClntEvent: creating new event queue
01/19/2001 11:01:08 clm-tlsdefault: Ignoring/Queueing CsConnectionCleared Event for client 6
01/19/2001 11:01:08 This Device => 2015
01/19/2001 11:01:08 Call ID => 61
01/19/2001 11:01:08 Other Device(s) => 2014, 6200
01/19/2001 1 1: 01:08 OldState => Held
01/19/2001 11:01:08 NewState => Null
01/19/2001 1 1: 01:08 TLinkData => "DNIS,2015", "ANI,2014", "ArrivalTime,01/19/01 11:01:05.281", "Device Type,1",
"ACDLine,0", "InternalCall,1"
01/19/2001 1 1: 01:08 clm_CopyLastClntEvent: event queueing is turned on for clie nt 6, dn ’2015’
01/19/2001 11:01:08 clm_CopyLastClntEvent: number of events in queue = 2
CSVAPI Receives Queued and Redirect Event for the CDN from TLS, No Apps are attached
CSVAPI Receive Call Cleared Event from TLS , Queued for Application
01/19/2001 11:01:08 clm-tlsdefault: Ignoring/Queueing CsCallCleared Event for client 6
01/19/2001 11:01:08 This Device => 2015
01/19/2001 11:01:08 Call ID => 161
01/19/2001 11:01:08 Other Device(s) => 3000
01/19/2001 1 1: 01: 08 OldS tate => Initiated
01/19/2001 11:01:08 NewState => Null
01/19/2001 11:01:08 TLinkData => "CallProgressEvent,112", "TN_this,203", "TN_other,4", "DNIS,6200",
"ANI,2015", "ArrivalTime,01/19/01 11:01:08.686", "DeviceType,1", "A CDL ine ,0" ,
"InternalCall,1"
Page 83

Example Log Files
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 83
User Data CSVAPI Log File
CSVAPI Receives "Preferred Skills" from IVR application as Call-Data and Sends it to CS-DA
12/04/2000 17:23:39 apmi_got_send_resource: vms 1, phoneline 52 message converted to v-shell options =>
12/04/200 0 17:23:39 option SendRespo nse value Yes
12/04/2000 17:23:39 option thisdevice value 2103
12/04/2000 17:23:39 option attachedkey value Date-Time
12/04/2000 17:23:39 option attacheddata value 20001204 17234600
12/04/200 0 17:23:39 option attachedkey value Ivr-Line-D N
12/04/2000 17:23:39 option attacheddata value v=1 p=52 d=2103
12/04/2000 17:23:39 option attachedkey value SkillOS
12/04/200 0 17:23:39 option attacheddata value UNIX
12/04/2000 17:23:39 option attachedkey value SkillCard
12/04/200 0 17:23:39 option attacheddata value VISA
12/04/2000 17:23:39 option attachedkey value Account
12/04/2000 17:23:39 option attacheddata value ACT0000100052
12/04/2000 17:23:39 option attachedkey value Phone-Line
12/04/200 0 17:23:39 option attacheddata value 52
12/04/200 0 17:23:39 option attachedkey value CallKey #007
12/04/2000 17:23:39 option attacheddata value CallValue #007
12/04/200 0 17:23:39 option attachedkey value CallKey #008
12/04/2000 17:23:39 option attacheddata value CallValue #008
12/04/200 0 17:23:39 option attachedkey value CallKey #009
12/04/2000 17:23:39 option attacheddata value CallValue #009
12/04/200 0 17:23:39 option attachedkey value CallKey #010
12/04/2000 17:23:39 option attacheddata value CallValue #010
12/04/200 0 17:23:39 option CtiFunction value AttachData
12/04/2000 17:23:39 AttachData: clm getting last event callid 24
12/04/2000 17:23:39 clm-CSVAPI: Received CsSendAddCallData Request from Client 9
12/04/2000 17:23:39 Device => 2103
12/04/2000 17:23:39 Call ID => 24
12/04/2000 17:23:39 CallData => "Date-Time,20001204 17234600", "Ivr-Line-DN, v=1 p=52 d=2103",
"SkillOS,UNIX", "SkillCard,VISA", "Account,ACT0000100052", "Phone-Line,52", "CallKey
#007,CallValue #007", "CallKey #008,CallValue #008", "CallKey #009,CallValue #009",
"CallKey #010,CallValue #010"
12/04/2000 17:23:39 clm_C op yL as tClnt Event: event queueing is turned on for client 4, dn ’6702’
12/04/2000 17:23:39 clm_CopyLastClntEvent: number of events in queue = 4
12/04/2000 17:23:39 clm-tlsdefault: Ignoring/Queueing CsCallData Event for client 4
12/04/2000 17:23:39 This Device => 6702
12/04/2000 17:23:39 Call ID => 24
12/04/2000 17:23:39 Other Device(s) => 5008, 2103
12/04/2000 17:23:39 DNIS => 6702
12/04/2000 17:23:39 ANI => 5008
Page 84

PeriProducer CTI Toolkit User’s Guide for M1
Page 84 Nortel Networks Confidential # P0606089 Ver: 1.1
12/04/2000 17:23:39 CallData => "queue_pos_AMEX,0", "queue_pos_NT,0", "queue_pos_UNIX,0",
"queue_pos_VISA,0", "expected_wait_AMEX,0", "expected_wait_NT,0",
"expected_wait_UNIX,0", "expected_wait_VISA,0", "Date-Time,20001204 17234600", "IvrLine-DN, v=1 p=52 d=2103", "SkillOS,UNIX", "SkillCard,VISA", "Account,ACT0000100052",
"Phone-Line,52", "CallKey #007,CallValue #007", "CallKey #008,CallValue #008", "CallKey
#009,CallValue #009", "CallKey #010,CallValue #010"
12/04/2000 17:23:39 OldState => Null
12/04/2000 17:23:39 NewState => Null
12/04/2000 17:23:39 clm_C op yL as tClnt Event: event queueing is turned on for client 9, dn ’2103’
12/04/2000 17:23:39 clm_CopyLastClntEvent: creating new event queue
12/04/2000 17:23:39 clm-tlsdefault: Ignoring/Queueing CsCallData Event for client 9
12/04/2000 17:23:39 This Device => 2103
12/04/2000 17:23:39 Call ID => 24
12/04/2000 17:23:39 Other Device(s) => 5008, 6702
12/04/2000 17:23:39 DNIS => 6702
12/04/2000 17:23:39 ANI => 5008
12/04/2000 17:23:39 CallData => "queue_pos_AMEX,0", "queue_pos_NT,0", "queue_pos_UNIX,0",
"queue_pos_VISA,0", "expected_wait_AMEX,0", "expected_wait_NT,0",
"expected_wait_UNIX,0", "expected_wait_VISA,0", "Date-Time,20001204 17234600", "Ivr-
Line-DN, v=1 p=52 d=2103", "SkillOS,UNIX", "SkillCard,VISA", "Account,ACT0000100052",
"Phone-Line,52", "CallKey #007,CallValue #007", "CallKey #008,CallValue #008", "CallKey
#009,CallValue #009", "CallKey #010,CallValue #010"
12/04/2000 17:23:39 OldState => Null
12/04/2000 17:23:39 NewState => Null
12/04/2000 17:23:39 clm-tlsdefault: Sending CsSendAddCallData Response to Client 9
12/04/2000 17:23:39 This Device => 2103
12/04/2000 17:23:39 Status => Success
12/04/2000 17:23:39 send_apmi_msg: Sent ’oc’ to vms 1, phoneline 52 with data <SendAddCallData>
CSVAPI Receives "Preferred Skills" from IVR application as Call-Data and Sends it to CS-DA
CSDA Receives "Preferred Skills" as Call-Data and attaches it to CallId
12/04/2000 17:23:39 clm-tlsdefault: Received CsSendAddCallData Request from Client 3
12/04/2000 17:23:39 Application ID => 9.#####
12/04/2000 17:23:39 Device => 2103
12/04/2000 17:23:39 Call ID => 24
12/04/2000 17:23:39 CallData => "Date-Time,20001204 17234600", "Ivr-Line-DN, v=1 p=52 d=2103",
"SkillOS,UNIX", "SkillCard,VISA", "Account,ACT0000100052", "Phone-Line,52", "CallKey
#007,CallValue #007", "CallKey #008,CallValue #008", "CallKey #009,CallValue #009",
"CallKey #010,CallValue #010"
CSDA Sends Call-Data Event to all Devices on the Call
12/04/2000 17:23:39 clm-csda: Sending CsCallData Event to client 3
12/04/2000 17:23:39 Application ID => 9.#####
12/04/2000 17:23:39 This Device => 2103
12/04/2000 17:23:39 Call ID => 24
12/04/2000 17:23:39 Other Device(s) => 5008, 6702
Page 85

Example Log Files
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 85
12/04/2000 17:23:39 DNIS => 6702
12/04/2000 17:23:39 ANI => 5008
12/04/2000 17:23:39 CallData => "queue_pos_AMEX,0", "queue_pos_NT,0", "queue_pos_UNIX,0",
"queue_pos_VISA,0", "expected_wait_AMEX,0", "expected_wait_NT,0",
"expected_wait_UNIX,0", "expected_wait_VISA,0", "Date-Time,20001204 17234600", "IvrLine-DN, v=1 p=52 d=2103", "SkillOS,UNIX", "SkillCard,VISA", "Account,ACT0000100052",
"Phone-Line,52", "CallKey #007,CallValue #007", "CallKey #008,CallValue #008", "CallKey
#009,CallValue #009", "CallKey #010,CallValue #010"
12/04/2000 17:23:39 OldState => Null
12/04/2000 17:23:39 NewState => Null
CSDA Sends Call-Data Event to all Devices on the Call
CSDA Sends Call-Data Response to CS-VAPI
12/04/2000 17:23:39 clm-csda: Sending Cs SendAddCallData Response to Client 3
12/04/2000 17:23:39 Application ID => 9.#####
12/04/2000 17:23:39 This Device => 2103
12/04/2000 17:23:39 Status => Success
IVR application Disconnects from the Call
12/04/2000 17:23:46 clm-tlsdefault: Sending CsConnectionCleared Event to client 3
12/04/2000 17:23:46 Application ID => 9.#####
12/04/2000 17:23:46 This Device => 2103
12/04/2000 17:23:46 Call ID => 24
12/04/2000 17:23:46 Other Device(s) => 6702, 5008
12/04/2000 17:23:46 CallData => "queue_pos_AMEX,0", "queue_pos_NT,0", "queue_pos_UNIX,0",
"queue_pos_VISA,0", "expected_wait_AMEX,0", "expected_wait_NT,0",
"expected_wait_UNIX,0", "expected_wait_VISA,0", "Date-Time,20001204 17234600", "Ivr-
Line-DN, v=1 p=52 d=2103", "SkillOS,UNIX", "SkillCard,VISA", "Account,ACT0000100052",
"Phone-Line,52", "CallKey #007,CallValue #007", "CallKey #008,CallValue #008", "CallKey
#009,CallValue #009", "CallKey #010,CallValue #010"
12/04/2000 17:23:46 OldState => Connected
12/04/2000 17:23:46 NewState => Null
12/04/2000 17:23:46 TLinkData => "TN_This,11", "PBXCallId,24", "PBXTimeStamp,8:0:54", "DNIS,6702",
"ANI,5008", "ArrivalTime,12/04/00 17:21:12.968", "DeviceType,6", "PositionID,2103",
"ACDLine,1", "InternalCall,1"
CSVAPI Receives "Free R esource" and Cleans-Up the Event Queue
12/04/2000 17:23:45 apmi_issue_free_resource: vms 1, phoneline 52 free resource request cleaning up.
12/04/200 0 17:23:45 apmi_issue_free_resource: cleared dnentry information for client 9
12/04/2000 17:23:45 clm-Admin: Preparing to complete Unregisters for Client 9
12/04/2000 17:23:45 clm-Admin: Setting timer for 100 millis econds.
12/04/2000 17:23:45 clm-CSVAPI: Device 2103 Auto-Registered.
Page 86

PeriProducer CTI Toolkit User’s Guide for M1
Page 86 Nortel Networks Confidential # P0606089 Ver: 1.1
Device Statistics Data CSRSM and CSRSMLS Log Files
CSRSM Receives Get Device Parameter from IVR Application
Statistics -Type skil litd (Skill Interval To Date), thisdevice = Skill-Name
12/04/2000 17:22:08 apmi_issue_get_resource: vms 1, phoneline 52 get resource request.
12/04/2000 17:22:08 apmi_got_send_resource: vms 1, phoneline 52 message converted to v-shell options =>
12/04/2000 17:22:08 option thisdevice value VISA
12/04/200 0 17:22:08 option param value skillitd
12/04/2000 17:22:08 option ctifuncti on va lue getdeviceparam
12/04/200 0 17:22:08 getdeviceparam: clm getting last event callid 0
12/04/2000 17:22:08 CSVAPI_extract_vmsphoneline: extracted vmsnum = 1, phoneline = 52 from clientid = 65588
12/04/2000 17:22:08 clm-csrsm: Received CsGetDeviceParam Request from Client 2
12/04/2000 17:22:08 Device => VISA
12/04/2000 17:22:08 Call ID => 0
12/04/2000 17:22:08 Parameter => Skill Interval to Date
CSRSMLS Receives Get Device Parameter from CSRSM
12/04/2000 17:22:08 clm-tlsdefault: Received CsGetDeviceParam Request from Client 1
12/04/2000 17:22:08 Application ID => 2.#####
12/04/2000 17:22:08 Device => VISA
12/04/2000 17:22:08 Call ID => 0
12/04/2000 17:22:08 Parameter => Skill Interval to Date
12/04/2000 17:22:08 clm-csrsmls: Sending CsGetDeviceParam Response to Client 1
12/04/2000 17:22:08 Application ID => 2.#####
12/04/2000 17:22:08 Device => VISA
12/04/2000 17:22:08 Parameter => Skill Interval to Date
12/04/2000 17:22:08 Status => Success
Page 87

Example Log Files
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 87
CSRSM Sends Get Device Parameter Response to IVR Application
12/04/2000 17:22:08 clm-tlsdefault: Sen ding CsGetDeviceParam Response to Client 2
12/04/2000 17:22:08 Device => VISA
12/04/2000 17:22:08 Parameter => Skill Interval to Date
12/04/2000 17:22:08 Status => Success
12/04/2000 17:22:08 send_apmi_msg: Queued message to v ms 1, phoneline 52 with data <GetD eviceParam
EventData:( csrsmstatdata:(datakey:"AgentsAvailable" datavalue:"0")
csrsmstatdata:(datakey:"AgentsInService" datavalue:"0")
csrsmstatdata:(datakey:"AgentsOnSkillsetCall" datavalue:"0")
csrsmstatdata:(datakey:"AgentsNotReady" datav alue:"0")
csrsmstatdata:(datakey:"CallsWaiting" datavalue:"0")
csrsmstatdata:(datakey:"LongestWaitingTimeSinceLastCall" datavalue:"0")
csrsmstatdata:(datakey:"MaxWaitingTime" datavalue:"0")
csrsmstatdata:(datakey:"WaitingTime" datavalue:"0")
csrsmstatdata:(datakey:"ExpectedWaitTime" datavalue:"0")
csrsmstatdata:(datakey:"CallsAnsweredAfterThreshold" datavalue:"0")
csrsmstatdata:(datakey:"LongestWaitingTimeSinceLogin" datavalue:"0")
csrsmstatdata:(datakey:"AgentsOnDNCalls" datavalue:"0")
csrsmstatdata:(datakey:"SkillsetState" datavalue:"0")
csrsmstatdata:(datakey:"AgentsUnavailable" datavalue:"0")
csrsmstatdata:(datakey:"NetworkCallsWaiting" datavalue:"0")
csrsmstatdata:(datakey:"NetworkCallsAnswered" datavalue:"0")
csrsmstatdata:(datakey:"QueuedCallAnswered" datavalue:"0")
csrsmstatdata:(datakey:"TotalCallsAnsweredDelay" datavalue:"0")
csrsmstatdata:(datakey:"TotalCallsAnswered" datavalue:"0")
csrsmstatdata:(datakey:"AgentOnNetworkSkillsetCall" datavalue:"0"))>
12/04/2000 17:22:08 apmi_issue_free_resource: vms 1, phoneline 52 free resource request cleaning up.
12/04/2000 17:22:19 CSVAPI_combine_vmsphoneline: converted vmsnum = 1, phoneline = 52 to clientid = 65588
CSRSM Receives Get Device Parameter from IVR Application
Statistics-Type skillmwnd (Skill Moving Window), thisdevice = Skill-Name
12/04/2000 17:22:19 apmi_issue_get_resource: vms 1, phoneline 52 get resource request.
12/04/2000 17:22:19 apmi_got_send_resource: vms 1, phoneline 52 message converted to v-shell options =>
12/04/2000 17:22:19 option thisdevice value VISA
12/04/2000 17:22:19 option param value skillmwnd
12/04/2000 17:22:19 option ctifuncti on value getdevicepara m
12/04/200 0 17:22:19 getdeviceparam: clm getting last event callid 0
12/04/2000 17:22:19 CSVAPI_extract_vmsphoneline: extracted vmsnum = 1, phoneline = 52 from clientid = 65588
12/04/2000 17:22:19 clm-csrsm: Received CsGetDeviceParam Request from Client 2
12/04/2000 17:22:19 Device => VISA
12/04/2000 17:22:19 Call ID => 0
12/04/2000 17:22:19 Parameter => Skill Moving Window
Page 88

PeriProducer CTI Toolkit User’s Guide for M1
Page 88 Nortel Networks Confidential # P0606089 Ver: 1.1
CSRSMLS Receives Get Device Parameter from CSRSM
12/04/2000 17:22:19 clm-tlsdefault: Received CsGetDeviceParam Request from Client 1
12/04/2000 17:22:19 Application ID => 2.#####
12/04/2000 17:22:19 Device => VISA
12/04/2000 17:22:19 Call ID => 0
12/04/2000 17:22:19 Parameter => Skill Moving Window
12/04/2000 17:22:19 clm-csrsmls: Sending CsGetDeviceParam Response to Client 1
12/04/2000 17:22:19 Application ID => 2.#####
12/04/2000 17:22:19 Device => VISA
12/04/2000 17:22:19 Parameter => Skill Moving Window
12/04/2000 17:22:19 Status => Success
CSRSM Sends Get Device Parameter Response to IVR Application
12/04/2000 17:22:19 clm-tlsdefault: Sen ding CsGetDeviceParam Response to Client 2
12/04/2000 17:22:19 Device => VISA
12/04/2000 17:22:19 Parameter => Skill Moving Window
12/04/2000 17:22:19 Status => Success
12/04/2000 17:22:19 send_apmi_msg: Queued message to v ms 1, phoneline 52 with data <Get DeviceParam
EventData:( csrsmstatdata:(datakey:"AgentsAvailable" datavalue:"0")
csrsmstatdata:(datakey:"AgentsInService" datavalue:"0")
csrsmstatdata:(datakey:"AgentsOnSkillsetCall" datavalue:"0")
csrsmstatdata:(datakey:"AgentsNotReady" datav alue:"0")
csrsmstatdata:(datakey:"CallsWaiting" datavalue:"0")
csrsmstatdata:(datakey:"LongestWaitingTimeSinceLastCall" datavalue:"0")
csrsmstatdata:(datakey:"MaxWaitingTime" datavalue:"0")
csrsmstatdata:(datakey:"WaitingTime" datavalue:"0")
csrsmstatdata:(datakey:"ExpectedWaitTime" datavalue:"0")
csrsmstatdata:(datakey:"CallsAnsweredAfterThreshold" datavalue:"0")
csrsmstatdata:(datakey:"LongestWaitingTimeSinceLogin" datavalue:"0")
csrsmstatdata:(datakey:"AgentsOnDNCalls" datavalue:"0")
csrsmstatdata:(datakey:"SkillsetState" datavalue:"0")
csrsmstatdata:(datakey:"AgentsUnavailable" datavalue:"0")
csrsmstatdata:(datakey:"NetworkCallsWaiting" datavalue:"0")
csrsmstatdata:(datakey:"NetworkCallsAnswered" datavalue:"0")
csrsmstatdata:(datakey:"QueuedCallAnswered" datavalue:"0")
csrsmstatdata:(datakey:"TotalCallsAnsweredDelay" datavalue:"0")
csrsmstatdata:(datakey:"TotalCallsAnswered" datavalue:"0")
csrsmstatdata:(datakey:"AgentOnNetworkSkillsetCall" datavalue:"0"))>
12/04/2000 17:22:19 apmi_issue_free_resource: vms 1, phoneline 52 free resource request cleaning up.
Page 89

Example Log Files
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 89
Send TAPI Call Data CSTAPI and CSTAPILS Log Files
CSTAPI Receives Add Call Data request from IVR Application
12/04/2000 17:23:39 CSVAPI_combine_vmsphoneline: converted vmsnum = 1, phoneline = 52 to clientid = 65588
12/04/2000 17:23:39 apmi_issue_get_resource: vms 1, phoneline 52 get resource request.
12/04/2000 17:23:39 apmi_got_send_resource: vms 1, phoneline 52 message converted to v-shell options =>
12/04/200 0 17:23:39 option SendRespo nse value Yes
12/04/2000 17:23:39 option thisdevice value 2103
12/04/2000 17:23:39 option attachedkey value Date-Time
12/04/2000 17:23:39 option attacheddata value 20001204 17234600
12/04/200 0 17:23:39 option attachedkey value Ivr-Line-D N
12/04/2000 17:23:39 option attacheddata value v=1 p=52 d=2103
12/04/2000 17:23:39 option attachedkey value SkillOS
12/04/200 0 17:23:39 option attacheddata value UNIX
12/04/2000 17:23:39 option attachedkey value SkillCard
12/04/200 0 17:23:39 option attacheddata value VISA
12/04/2000 17:23:39 option attachedkey value Account
12/04/2000 17:23:39 option attacheddata value ACT0000100052
12/04/2000 17:23:39 option attachedkey value Phone-Line
12/04/200 0 17:23:39 option attacheddata value 52
12/04/200 0 17:23:39 option attachedkey value CallKey #007
12/04/2000 17:23:39 option attacheddata value CallValue #007
12/04/200 0 17:23:39 option attachedkey value CallKey #008
12/04/2000 17:23:39 option attacheddata value CallValue #008
12/04/200 0 17:23:39 option attachedkey value CallKey #009
12/04/2000 17:23:39 option attacheddata value CallValue #009
12/04/200 0 17:23:39 option attachedkey value CallKey #010
12/04/2000 17:23:39 option attacheddata value CallValue #010
12/04/200 0 17:23:39 option CtiFunction value AttachData
12/04/2000 17:23:39 AttachData: clm getting last event callid 0
12/04/2000 17:23:39 clm-cstapi: Received CsSendAddCallDat a Req ues t from Clie nt 4
12/04/2000 17:23:39 Device => 2103
12/04/2000 17:23:39 Call ID => 0
12/04/2000 17:23:39 CallData => "Date-Time,20001204 17234600", "Ivr-Line-DN, v=1 p=52 d=2103",
"SkillOS,UNIX", "SkillCard,VISA", "Account,ACT0000100052", "Phone-Line,52", "CallKey
#007,CallValue #007", "CallKey #008,CallValue #008", "CallKey #009,CallValue #009",
"CallKey #010,CallValue #010"
Page 90

PeriProducer CTI Toolkit User’s Guide for M1
Page 90 Nortel Networks Confidential # P0606089 Ver: 1.1
CSTAPILS Receives Add Call Data request from CSTAPI
12/04/2000 17:23:39 clm-tlsdefault: Received CsSendAddCallData Request from Client 0
12/04/2000 17:23:39 Application ID => 4.#####
12/04/2000 17:23:39 Device => 2103
12/04/2000 17:23:39 Call ID => 0
12/04/2000 17:23:39 CallData => "Date-Time,20001204 17234600", "Ivr-Line-DN, v=1 p=52 d=2103",
"SkillOS,UNIX", "SkillCard,VISA", "Account,ACT0000100052", "Phone-Line,52", "CallKey
#007,CallValue #007", "CallKey #008,CallValue #008", "CallKey #009,CallValue #009",
"CallKey #010,CallValue #010"
12/04/2000 17:23:39 CSTAPILS::cstapils_ServiceCallback got called
12/04/2000 17:23:39 CSTAPILS::Pro cess_MT_CSREQUEST got called
12/04/2000 17:23:39 Number of bytes 258
12/04/2000 17:23:39 fe 0a 01 02 0e 00 02 02 01 00 04 08 00 02 32 31 ..............21
12/04/2000 17:23:39 30 33 07 00 f0 01 00 ec 02 44 61 74 65 2d 54 69 03.......Date-Ti
12/04/2000 17:23:39 6d 65 2c 32 30 30 30 31 32 30 34 20 31 37 32 33 me,20001204 1723
12/04/2000 17:23:39 34 36 30 30 2c 49 76 72 2d 4c 69 6e 65 2d 44 4e 4600,Ivr-Line-DN
12/04/2000 17:23:39 2c 20 76 3d 31 20 20 70 3d 35 32 20 64 3d 32 31 , v=1 p=52 d=21
12/04/2000 17:23:39 30 33 2c 53 6b 69 6c 6c 4f 53 2c 55 4e 49 58 2c 03,SkillOS,UNIX,
12/04/2000 17:23:39 53 6b 69 6c 6c 43 61 72 64 2c 56 49 53 41 2c 41 SkillCard,VISA,A
12/04/2000 17:23:39 63 63 6f 75 6e 74 2c 41 43 54 30 30 30 30 31 30 ccount,ACT000010
12/04/2000 17:23:39 30 30 35 32 2c 50 68 6f 6e 65 2d 4c 69 6e 65 2c 0052,Phone-Line,
12/04/2000 17:23:39 35 32 2c 43 61 6c 6c 4b 65 79 20 23 30 30 37 2c 52,CallKey #007,
12/04/2000 17:23:39 43 61 6c 6c 56 61 6c 75 65 20 23 30 30 37 2c 43 CallValue #007,C
12/04/200 0 17:23:39 61 6c 6c 4b 65 79 20 23 3 0 30 38 2c 43 61 6c 6c allKey #008,Call
12/04/2000 17:23:39 56 61 6c 75 65 20 23 30 30 38 2c 43 61 6c 6c 4b Value #008,CallK
12/04/2000 17:23:39 65 79 20 23 30 30 39 2c 43 61 6c 6c 56 61 6c 75 ey #009,CallValu
12/04/2000 17:23:39 65 20 23 30 30 39 2c 43 61 6c 6c 4b 65 79 20 23 e #009,CallKey #
12/04/2000 17:23:39 30 31 30 2c 43 61 6c 6c 56 61 6c 75 65 20 23 30 010,CallValue #0
12/04/200 0 17:23:39 31 30 10
12/04/2000 17:23:39 CSTAPILS::M3 Message IVRCallerData is queued at 2000.12.04-17:23:39
12/04/2000 17:23:39 CSTAPILS::Successfully sent the caller data message
12/04/2000 17:23:39 CSTAPILS::cstapils_ServiceCallback got called
12/04/2000 17:23:39 CSTAPILS::MT_CSRESPONSE not supported
12/04/200 0 17:23:39 clm-cstapils: Sending CsSendAddC allData Response to Client 0
12/04/2000 17:23:39 Application ID => 4.#####
12/04/2000 17:23:39 This Device => 2103
12/04/2000 17:23:39 Status => Success
12/04/2000 17:23:39 CSTAPILS::New host message received
12/04/200 0 17:23:39 CSTAPILS::ProcessIVRMessa ge DEFAULT TLSERVERNAME: tlsdefault
12/04/2000 17:23:39 CSTAPILS::M1 3 Processing MsgType IVRCallerDataResponse with MsgRefId: 2
12/04/2000 17:23:39 clm-tlsdefault: Received CsSendAddCallData Request from Client 0
12/04/2000 17:23:39 Device => 2103
12/04/2000 17:23:39 Call ID => 0
Page 91

Example Log Files
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 91
CSTAPI Sends "oc" to IVR Application
12/04/2000 17:23:39 clm-tlsdefault: Sending CsSendAddCallData Response to Client 4
12/04/2000 17:23:39 This Device => 2103
12/04/2000 17:23:39 Status => Success
12/04/2000 17:23:39 send_apmi_msg: Sent ’oc’ to vms 1, phoneline 52 with data <SendAddCallData >
12/04/2000 17:23:39 apmi_issue_free_resource: vms 1, phoneline 52 free resource request cleaning up.
12/04/200 0 17:23:39 apmi_issue_free_resource: cleared dnentry information for client 4
12/04/2000 17:23:39 clm-Admin: Preparing to complete Unregisters for Client 4
12/04/2000 17:23:39 clm-Admin: Setting timer for 100 millis econds.
12/04/2000 17:23:39 clm-cstapi: Device 2103 Auto-Registered.
Page 92

PeriProducer CTI Toolkit User’s Guide for M1
Page 92 Nortel Networks Confidential # P0606089 Ver: 1.1
Send TAPI SCCS Call Data CSTAPI and CSTAPILS Log Files
CSTAPI Receives Add Call Data request from IVR Application
12/04/2000 17:23:39 CSVAPI_combine_vmsphoneline: converted vmsnum = 1, phoneline = 52 to clientid = 65588
12/04/2000 17:23:39 apmi_issue_get_resource: vms 1, phoneline 52 get resource request.
12/04/2000 17:23:39 apmi_got_send_resource: vms 1, phoneline 52 message converted to v-shell options =>
12/04/200 0 17:23:39 option SendRespo nse value Yes
12/04/2000 17:23:39 option thisdevice value 2103
12/04/2000 17:23:39 option attachedkey value Date-Time
12/04/2000 17:23:39 option attacheddata value 20001204 17234600
12/04/200 0 17:23:39 option attachedkey value Ivr-Line-D N
12/04/2000 17:23:39 option attacheddata value v=1 p=52 d=2103
12/04/2000 17:23:39 option attachedkey value SkillOS
12/04/200 0 17:23:39 option attacheddata value UNIX
12/04/2000 17:23:39 option attachedkey value SkillCard
12/04/200 0 17:23:39 option attacheddata value VISA
12/04/2000 17:23:39 option attachedkey value Account
12/04/2000 17:23:39 option attacheddata value ACT0000100052
12/04/2000 17:23:39 option attachedkey value Phone-Line
12/04/200 0 17:23:39 option attacheddata value 52
12/04/200 0 17:23:39 option attachedkey value CallKey #007
12/04/2000 17:23:39 option attacheddata value CallValue #007
12/04/200 0 17:23:39 option attachedkey value CallKey #008
12/04/2000 17:23:39 option attacheddata value CallValue #008
12/04/200 0 17:23:39 option attachedkey value CallKey #009
12/04/2000 17:23:39 option attacheddata value CallValue #009
12/04/200 0 17:23:39 option attachedkey value CallKey #010
12/04/2000 17:23:39 option attacheddata value CallValue #010
12/04/200 0 17:23:39 option CtiFunction value AttachData
12/04/2000 17:23:39 AttachData: clm getting last event callid 0
12/04/2000 17:23:39 clm-cstapi: Received CsSendAddCallDat a Req ues t from Clie nt 4
12/04/2000 17:23:39 Device => 2103
12/04/2000 17:23:39 Call ID => 0
12/04/2000 17:23:39 CallData => "Date-Time,20001204 17234600", "Ivr-Line-DN, v=1 p=52 d=2103",
"SkillOS,UNIX", "SkillCard,VISA", "Account,ACT0000100052", "Phone-Line,52", "CallKey
#007,CallValue #007", "CallKey #008,CallValue #008", "CallKey #009,CallValue #009",
"CallKey #010,CallValue #010"
Page 93

Example Log Files
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 93
CSTAPILS Receives Add Call Data request from CSTAPI
12/04/2000 17:23:39 clm-tlsdefault: Received CsSendAddCallData Request from Client 0
12/04/2000 17:23:39 Application ID => 4.#####
12/04/2000 17:23:39 Device => 2103
12/04/2000 17:23:39 Call ID => 0
12/04/2000 17:23:39 CallData => "Date-Time,20001204 17234600", "Ivr-Line-DN, v=1 p=52 d=2103",
"SkillOS,UNIX", "SkillCard,VISA", "Account,ACT0000100052", "Phone-Line,52", "CallKey
#007,CallValue #007", "CallKey #008,CallValue #008", "CallKey #009,CallValue #009",
"CallKey #010,CallValue #010"
12/04/2000 17:23:39 CSTAPILS::cstapils_ServiceCallback got called
12/04/2000 17:23:39 CSTAPILS::Pro cess_MT_CSREQUEST got called
12/04/2000 17:23:39 Number of bytes 258
12/04/2000 17:23:39 fe 0a 01 02 0e 00 02 02 01 00 04 08 00 02 32 31 ..............21
12/04/2000 17:23:39 30 33 07 00 f0 01 00 ec 02 44 61 74 65 2d 54 69 03.......Date-Ti
12/04/2000 17:23:39 6d 65 2c 32 30 30 30 31 32 30 34 20 31 37 32 33 me,20001204 1723
12/04/2000 17:23:39 34 36 30 30 2c 49 76 72 2d 4c 69 6e 65 2d 44 4e 4600,Ivr-Line-DN
12/04/2000 17:23:39 2c 20 76 3d 31 20 20 70 3d 35 32 20 64 3d 32 31 , v=1 p=52 d=21
12/04/2000 17:23:39 30 33 2c 53 6b 69 6c 6c 4f 53 2c 55 4e 49 58 2c 03,SkillOS,UNIX,
12/04/2000 17:23:39 53 6b 69 6c 6c 43 61 72 64 2c 56 49 53 41 2c 41 SkillCard,VISA,A
12/04/2000 17:23:39 63 63 6f 75 6e 74 2c 41 43 54 30 30 30 30 31 30 ccount,ACT000010
12/04/2000 17:23:39 30 30 35 32 2c 50 68 6f 6e 65 2d 4c 69 6e 65 2c 0052,Phone-Line,
12/04/2000 17:23:39 35 32 2c 43 61 6c 6c 4b 65 79 20 23 30 30 37 2c 52,CallKey #007,
12/04/2000 17:23:39 43 61 6c 6c 56 61 6c 75 65 20 23 30 30 37 2c 43 CallValue #007,C
12/04/2000 17:23:39 61 6c 6c 4b 65 79 20 23 30 30 38 2c 43 61 6c 6c allKey #008,Call
12/04/2000 17:23:39 56 61 6c 75 65 20 23 30 30 38 2c 43 61 6c 6c 4b Value #008,CallK
12/04/2000 17:23:39 65 79 20 23 30 30 39 2c 43 61 6c 6c 56 61 6c 75 ey #009,CallValu
12/04/2000 17:23:39 65 20 23 30 30 39 2c 43 61 6c 6c 4b 65 79 20 23 e #009,CallKey #
12/04/2000 17:23:39 30 31 30 2c 43 61 6c 6c 56 61 6c 75 65 20 23 30 010,CallValue #0
12/04/200 0 17:23:39 31 30 10
12/04/2000 17:23:39 CSTAPILS::M3 Message IVRCallerData is queued at 2000.12.04-17:23:39
12/04/2000 17:23:39 CSTAPILS::Successfully sent the caller data message
12/04/2000 17:23:39 CSTAPILS::cstapils_ServiceCallback got called
12/04/2000 17:23:39 CSTAPILS::MT_CSRESPONSE not supported
12/04/2000 17:23:39 clm-cstapils: Sending CsSendAddCallData Response to Client 0
12/04/2000 17:23:39 Application ID => 4.#####
12/04/2000 17:23:39 This Device => 2103
12/04/2000 17:23:39 Status => Success
12/04/2000 17:23:39 CSTAPILS::New host message received
12/04/200 0 17:23:39 CSTAPILS::ProcessIVRMessa ge DEFAULT TLSERVERNAME: tlsdefault
12/04/2000 17:23:39 CSTAPILS::M13 Processing MsgType IVRCallerDataResponse with MsgRefId: 2
12/04/2000 17:23:39 clm-tlsdefault: Received CsSendAddCallData Request from Client 0
12/04/2000 17:23:39 Device => 2103
12/04/2000 17:23:39 Call ID => 0
Page 94

PeriProducer CTI Toolkit User’s Guide for M1
Page 94 Nortel Networks Confidential # P0606089 Ver: 1.1
CSTAPI Sends "oc" to IVR Application
12/04/2000 17:23:39 clm-tlsdefault: Sending CsSendAddCallData Response to Client 4
12/04/2000 17:23:39 This Device => 2103
12/04/2000 17:23:39 Status => Success
12/04/2000 17:23:39 send_apmi_msg: Sent ’oc’ to vms 1, phoneline 52 with data <SendAddCallData >
12/04/2000 17:23:39 apmi_issue_free_resource: vms 1, phoneline 52 free resource request cleaning up.
12/04/200 0 17:23:39 apmi_issue_free_resource: cleared dnentry information for client 4
12/04/2000 17:23:39 clm-Admin: Preparing to complete Unregisters for Client 4
12/04/2000 17:23:39 clm-Admin: Setting timer for 100 millis econds.
12/04/2000 17:23:39 clm-cstapi: Device 2103 Auto-Registered.
Page 95

Example Log Files
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 95
Log Message Example Application Log File
03/20/01 13:38:13 application starts
03/20/01 13:38:19 Got CTI resource CTI
03/20/01 13:38:19 AgentID:1505 Agent DN:2105
03/20/01 13:38 :20 Agent 1505 logged out.
03/20/01 13:38 :21 Agent 1505 logged in
03/20/01 13:38:46 Ani is 2004
03/20/01 13:38:46 Dnis is 6702
03/20/01 13:38:46 log: [One CallData item]
03/20/01 13:38:47 EVENT DATA01: status:
03/20/01 13:38:47 EVENT DATA02: callid:
03/20/01 13:38:47 EVENT DATA03: othercallid :
03/20/01 13:38:47 EVENT DATA04: otherdevice:
03/20/01 13:38:47 EVENT DATA05: agent id:
03/20/01 13:38:47 EVENT DATA06: agent st a te:
03/20/01 13:38:47 EVENT DATA07: qtime:
03/20/01 13:38:47 EVENT DATA08: eta:
03/20/01 13:38:47 EVENT DATA09: dnis: 6702
03/20/01 13:38:47 EVENT DATA10: ani: 2004
03/20/01 13:38:47 EVENT DATA11: route:
03/20/01 13:38:47 EVENT DATA14: thisobjec tke y:
03/20/01 13:38:47 EVENT DATA13: thispath key:
03/20/01 13:38:47 EVENT DATA14: tlservernam e:
03/20/01 13:38:47 EVENT DATA15/16: paramname: paramvalue:
03/20/01 13:38:47 ATTRIBUTE DATA ARRAY DUMP STARTS
03/20/01 13:38:47 ATTRIBUTE DATA ARRAY DUMP ENDS
03/20/01 13:38:47 CALL DATA ARRAY DUMP STARTS
03/20/01 13:38:47 CTI.EventData.calldata.datakey(1 ): selected_service
03/20/01 13:38:47 CTI.EventData.calldata.datavalue(1 ):
03/20/01 13:38:47 CALL DATA ARRAY DUMP ENDS
03/20/01 13:38:47 CSRSM STAT DATA ARRAY DUMP STARTS
03/20/01 13:38:47 CSRSM STAT DATA ARRAY DUMP ENDS
03/20/01 13:38:47 TLINK DATA ARRAY DUMP STARTS
03/20/01 13:38:47 TLINK DATA ARRAY DUMP ENDS
03/20/01 13:38:47 will send: TES TDA ; applicitd
03/20/01 13:38:47 AllOK: Send/ Get of RSM data was successful.
03/20/01 13:38:47 log: [CSRSMLS: TESTDA ]
03/20/01 13:38:47 EVENT DATA01: status:
03/20/01 13:38:47 EVENT DATA02: callid:
03/20/01 13:38:47 EVENT DATA03: othercallid :
03/20/01 13:38:47 EVENT DATA04: otherdevice:
03/20/01 13:38:47 EVENT DATA05: agent id:
03/20/01 13:38:51 EVENT DATA06: agent st a te:
03/20/01 13:38:51 EVENT DATA07: qtime:
Page 96

PeriProducer CTI Toolkit User’s Guide for M1
Page 96 Nortel Networks Confidential # P0606089 Ver: 1.1
03/20/01 13:38:51 EVENT DATA08: eta:
03/20/01 13:38:51 EVENT DATA09: dnis:
03/20/01 13:38:51 EVENT DATA10: ani:
03/20/01 13:38:51 EVENT DATA11: route:
03/20/01 13:38:51 EVENT DATA14: thisobjec tke y:
03/20/01 13:38:51 EVENT DATA13: thispath key:
03/20/01 13:38:51 EVENT DATA14: tlservernam e:
03/20/01 13:38:51 EVENT DATA15/16: paramname: paramvalue:
03/20/01 13:38:51 ATTRIBUTE DATA ARRAY DUMP STARTS
03/20/01 13:38:51 ATTRIBUTE DATA ARRAY DUMP ENDS
03/20/01 13:38:51 CALL DATA ARRAY DUMP STARTS
03/20/01 13:38:51 CALL DATA ARRAY DUMP ENDS
03/20/01 13:38:51 CSRSM STAT DATA ARRAY DUMP STARTS
03/20/01 13:38:51 CTI.EventData.csrsmstatdata.datakey(1 ): CallsAbandoned
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datavalue(1 ): 4
03/20/01 13:38:51 CTI.EventData.csrsmstatdata.datakey(2 ): CallsAbandonedAfterThreshold
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datavalue(2 ): 4
03/20/01 13:38:51 CTI.EventData.csrsmstatdata.datakey(3 ): CallsAbandonedDelay
03/20/01 13:38:51 CTI.EventData.csrsmstatdata.datavalue(3 ): 4594
03/20/01 13:38:51 CTI.EventData.csrsmstatdata.datakey(4 ): CallsAnswered
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datavalue(4 ): 0
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datakey(5 ): CallsAnsweredAfterThreshold
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datavalue(5 ): 0
03/20/01 13:38:51 CTI.EventData.csrsmstatdata.datakey(6 ): CallsAnsweredDelay
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datavalue(6 ): 0
03/20/01 13:38:51 CTI.EventData.csrsmstatdata.datakey(7 ): CallsWaiting
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datavalue(7 ): 4
03/20/01 13:38:51 CTI.EventData.csrsmstatdata.da takey(8 ): MaxWaitingTime
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datavalue(8 ): 20
03/20/01 13:38:51 CTI.EventD ata.csrsmstatdata.datakey(9 ): WaitingTime
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datavalue(9 ): 80
03/20/01 13:38:51 CTI.EventData.csrsmstatdata.datakey(10): CallsAnsweredDelayAtSkillset
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datavalue(10): 0
03/20/01 13:38:51 CTI.EventData.csrsmstatdata.datakey(11): CallsGivenTerminationTreatment
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datavalue(11): 0
03/20/01 13:38:51 CTI.EventD ata.csrsmstatdata.datakey(12): CallsOffered
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datavalue(12): 4
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datakey(13): TimeBeforeInterflow
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datavalue(13): 0
03/20/01 13:38:51 CTI.EventData.csrsmstatdata.datakey(14): NetworkOutCalls
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datavalue(14): 0
03/20/01 13:38:51 CTI.EventData.csrsmstatdata.datakey(15): NetworkOutCallsAbandoned
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datavalue(15): 0
03/20/01 13:38:51 CTI.EventData.csrsmstatdata.datakey(16): NetworkOutCallsAbandonedDelay
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datavalue(16): 0
03/20/01 13:38:51 CTI.EventData.csrsmstatdata.datakey(17): NetworkOutCallsAnswered
Page 97

Example Log Files
# P0606089 Ver: 1.1 Nortel Networks Confidential Page 97
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datavalue(17): 0
03/20/01 13:38:51 CTI.EventData.csrsmstatdata.datakey(18): NetworkOutCallsAnsweredDelay
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datavalue(18): 0
03/20/01 13:38:51 CTI.EventData.csrsmstatdata.datakey(19): NetworkOutCallsWaiting
03/20/01 13:38:51 CTI.EventData.csrsmstatdata. datavalue(19): 0
03/20/01 13:38:51 CSRSM STAT DATA ARRAY DUMP ENDS
03/20/01 13:38:51 TLINK DATA ARRAY DUMP STARTS
03/20/01 13:38:51 TLINK DATA ARRAY DUMP ENDS
03/20/01 13:38:51 will send: TESTDA; applicmwnd
03/20/01 13:38:52 AllOK: Send/ Get of RSM data was successful.
03/20/01 13:38:52 log: [CSRSMLS: TESTDA ]
03/20/01 13:38:52 EVENT DATA01: status:
03/20/01 13:38:52 EVENT DATA02: callid:
03/20/01 13:38:52 EVENT DATA03: othercallid :
03/20/01 13:38:52 EVENT DATA04: otherdevice:
03/20/01 13:38:52 EVENT DATA05: agent id:
03/20/01 13:38:52 EVENT DATA06: agent st a te:
03/20/01 13:38:52 EVENT DATA07: qtime:
03/20/01 13:38:52 EVENT DATA08: eta:
03/20/01 13:38:52 EVENT DATA09: dnis:
03/20/01 13:38:52 EVENT DATA10: ani:
03/20/01 13:38:52 EVENT DATA11: route:
03/20/01 13:38:52 EVENT DATA14: thisobjec tke y:
03/20/01 13:38:52 EVENT DATA13: thispath key:
03/20/01 13:38:52 EVENT DATA14: tlservernam e:
03/20/01 13:38:52 EVENT DATA15/16: paramname: paramvalue:
03/20/01 13:38:52 ATTRIBUTE DATA ARRAY DUMP STARTS
03/20/01 13:38:52 ATTRIBUTE DATA ARRAY DUMP ENDS
03/20/01 13:38:52 CALL DATA ARRAY DUMP STARTS
03/20/01 13:38:52 CALL DATA ARRAY DUMP ENDS
03/20/01 13:38:52 CSRSM STAT DATA ARRAY DUMP STARTS
03/20/01 13:38:52 CTI.EventData.csrsmstatdata.datakey(1 ): CallsAbandoned
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datavalue(1 ): 4
03/20/01 13:38:52 CTI.EventData.csrsmstatdata.datakey(2 ): CallsAbandonedAfterThreshold
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datavalue(2 ): 4
03/20/01 13:38:52 CTI.EventData.csrsmstatdata.datakey(3 ): CallsAbandonedDelay
03/20/01 13:38:52 CTI.EventData.csrsmstatdata.datavalue(3 ): 4594
03/20/01 13:38:52 CTI.EventData.csrsmstatdata.datakey(4 ): CallsAnswered
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datavalue(4 ): 0
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datakey(5 ): CallsAnsweredAfterThreshold
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datavalue(5 ): 0
03/20/01 13:38:52 CTI.EventData.csrsmstatdata.datakey(6 ): CallsAnsweredDelay
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datavalue(6 ): 0
03/20/01 13:38:52 CTI.EventData.csrsmstatdata.datakey(7 ): CallsWaiting
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datavalue(7 ): 4
03/20/01 13:38:52 CTI.EventData.csrsmstatdata.da takey(8 ): MaxWaitingTime
Page 98

PeriProducer CTI Toolkit User’s Guide for M1
Page 98 Nortel Networks Confidential # P0606089 Ver: 1.1
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datavalue(8 ): 26
03/20/01 13:38:52 CTI.EventD ata.csrsmstatdata.datakey(9 ): WaitingTime
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datavalue(9 ): 104
03/20/01 13:38:52 CTI.EventData.csrsmstatdata.datakey(10): CallsAnsweredDelayAtSkillset
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datavalue(10): 0
03/20/01 13:38:52 CTI.EventData.csrsmstatdata.datakey(11): CallsGivenTerminationTreatment
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datavalue(11): 0
03/20/01 13:38:52 CTI.EventD ata.csrsmstatdata.datakey(12): CallsOffered
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datavalue(12): 4
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datakey(13): TimeBeforeInterflow
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datavalue(13): 0
03/20/01 13:38:52 CTI.EventData.csrsmstatdata.datakey(14): NetworkOutCalls
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datavalue(14): 0
03/20/01 13:38:52 CTI.EventData.csrsmstatdata.datakey(15): NetworkOutCallsAbandoned
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datavalue(15): 0
03/20/01 13:38:52 CTI.EventData.csrsmstatdata.datakey(16): NetworkOutCallsAbandonedDelay
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datavalue(16): 0
03/20/01 13:38:52 CTI.EventData.csrsmstatdata.datakey(17): NetworkOutCallsAnswered
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datavalue(17): 0
03/20/01 13:38:52 CTI.EventData.csrsmstatdata.datakey(18): NetworkOutCallsAnsweredDelay
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datavalue(18): 0
03/20/01 13:38:52 CTI.EventData.csrsmstatdata.datakey(19): Netw orkOutCallsWaiting
03/20/01 13:38:52 CTI.EventData.csrsmstatdata. datavalue(19): 0
03/20/01 13:38:52 CSRSM STAT DATA ARRAY DUMP ENDS
03/20/01 13:38:52 TLINK DATA ARRAY DUMP STARTS
03/20/01 13:38:52 TLINK DATA ARRAY DUMP ENDS
03/20/01 13:39:08 will send: Date-Time as 20010320 13390800 and Ivr-Line-DN as v=1 p=54 d=2105
03/20/01 13:39:09 AllOK: Send of TAPI data was suc c essful.
03/20/01 13:39:15 will send: Date-Time as 20010320 13391500 and Ivr-Line-DN as v=1 p=54 d=2105
03/20/01 13:39:15 AllOK: Send of CTI data was successful.
03/20/01 13:39:15 WRAPUP: disconnecting the call...
03/20/01 13:39:16 application loops to answer block
Page 99

Index
Page 100

PeriProducer CTI Toolkit User’s Guide for M1
Page 100 Nortel Networks Confidential # P0606089 Ver: 1.1
Index
C
conventions
manual
viii
CTI
description
12
CTI Toolkit
blocks
Agent Function
30
CTI Init
32
Device Statistics Data
47
Log Message
53
Register Device
35
Send TAPI Call Data
50
Send TAPIsccs Call Data
51, 52
Set Event Handling
37
Telephony Event Data
40
Telephony Request
42
User Data
45
installation
Solaris
23–24
Windows NT
??–22
introduction
12–15
removal
Solaris
24
Windows NT
22–??
vs. PeriProducer Toolkit 13
F
Feature Application Development Matrix 15
Feature Matrix
15
G
Get TAPI Data 52
L
log files
Agent Function
74
CTI Init
74
Device Statistics Data
86
Log Message
95
Register Device
74
Send TAPI Call Data
89
Send TAPIsccs Call Data
92
Set Event Handling
75
Telephony Event Data
76
Telephony Request
78
User Data
83
M
Menus
agent
30
CSRSMstatisticGroups
47
deviceParams
33
eventData
40
events
37
registration
35
setEventType
37
telephony
42
usrDataFunc
45
usrDataType
45
R
Removal, CTI Tool Kit
Solaris
24
Resource Matrix
15
S
Sample Applications
Agent Function
56
CTI Initialize
58
Device Parameter Data
58
Device Statistics Data
69
Log Message
71
Register Device
58
Send TAPI CallData
70
Send TAPIsccs CallData
70
Set Event Handling
59
Telephony Event Data
63
Telephony Request
65
User Data
68
 Loading...
Loading...