Nortel Meridian Mail, Meridian Mail Reporter 2.0 User Manual
Meridian Mail Reporter 2.0
User’s Guide
Product release: 2.0
Document version: Standard 2.0
Date: October 1996
© 1996 Northern Telecom
All righ t s re s e rv e d
Printed in the United States of America
Information is subject to change without notice. Northern Telecom reserves the right to make
changes in design or components as progress in engineering and manufacturing may warrant.
AdminPlus, Nortel, Meri dian Mail, Meridian Mail Reporter, ACCESS, and Meridian-1 are
trademarks of Northern Telecom. Thi nkJet is a trademark of Hewlet t-Packard. Microsoft Access,
Microsof t Windows, Microsoft Wi ndows 3.1, Windows 3.11, Windo ws for Workgroups 3.11,
Windows NT, Micro soft Windows Termi nal, and MS-DOS are trade marks of Microsof t Corporation.
Racal-Datacom is a trademark of Racal Data Communications Incorpora ted. OS/2 is a tradema rk
of Internati onal Business Machines Incorporated. Hayes Optima 144 is a trademar k of Hayes
Microcomput er Product s, Inc orp orated. pcANYWHERE is a trade mark of Dynam ic Micr oprocess or
Associates. RoboHELP is a trademark of Blue Sky Software Corporation.

Chapter 1 - Introducing MMR
Table of Contents
Introducing MMR................................. ......... .......... ......... .......... ......... ... 1-1
Overview ....................................................................................................1-1
Components of Meridian Ma il R eporter .....................................................1-2
MMR Setup ........................................................................................1-2
MMR Communications .......................................................................1-2
MMR Reports .....................................................................................1-3
Benefi ts of U s ing Meridia n M ail Reporter ..... .............................................1-4
Security ..............................................................................................1-4
Convenience ......................................................................................1-4
Flexibility ............................................................................................1-4
Centralization .....................................................................................1-5
Visual Information ..............................................................................1-5
Ability to Bill Service U sa ge ...............................................................1-6
Historical informat ion .........................................................................1-6

Chap ter 2 - Getting Started
Table of Contents
Getting Started...................................................................................... 2-1
Introduction ................................................................................................2-1
Background Information ............................................................................. 2-1
MMR Configuration ....................................................................................2-2
MMR Hardware and Software Requirements ............................................2-4
Hardware ...........................................................................................2-4
Optional Hardware .............................................................................2-5
Software .............................................................................................2-5
Virtual Memory Settings for Windows 3.1 ..................................2-7
Windows 3.1 Protection and Multitasking ......... ........... ..............2-7
Windows 95 and Windows NT Protection ..................................2-8
MMR Package Contents ............................................................................2-8
Setting up Meridian Mail ............................................................................2-9
Overview of Converting to Meridian Mail Release 10 ........................2-9
Overview of Converting to Meridian Mail Release 11 ......................2-10
Proced ures for Converting to M eridian Mail Release 10 or 11 ........2 -10
Cabling In f orm ation ..........................................................................2 -13

Chapter 3 - Installing MMR
Table of Contents
Installing MMR....................................................................................... 3-1
Introduction................................................................................................ 3-1
Before Installation...................................................................................... 3-1
Installation Disks................................................................................ 3-1
Online Instructions ............................................................................. 3-2
MMR Setup........................................................................................ 3-2
Configuration Options........................................................................ 3-2
Installation Checklist .......................................................................... 3-3
Installin g t he Software................................................................................ 3-4
After Installation....................................................................................... 3 -19
Changing Your Password ................................................................ 3 -19
When to Use the Three MMR Programs .......................................... 3-22
MMR Setup.............................................................................. 3 -22
MMR Communications............................................................. 3 -23
MMR Reports ...........................................................................3-23

Chapter 4 - Using MMR and its Online Help
Table of Contents
Using MMR and its Online Help........................................................... 4-1
Introduction................................................................................................ 4-1
Using MMR........................ ................................. ................................. ...... 4-1
Installation Disk Setup ....................................................................... 4-2
MMR Setup........................................................................................ 4-2
MMR Communications....................................................................... 4-3
Download Process..................................................................... 4-3
Download Schedules ................................................................. 4-5
Critical Errors ......... ...................... ................................. ............. 4-6
Log File ...................................................................................... 4-7
MMR Reports..................................................................................... 4-8
Reports, Alerts, and Palettes ..................................................... 4-8
Reporting Interval....................................................................... 4-9
Print Preview............................................................................ 4 -11
Triggered Alerts....................................... ................................ . 4-16
Customization.......................................................................... 4-17
Backup..................................................................................... 4-36
Other Functions of MMR Reports ............................................ 4-36
MMR Loader.................................................................................... 4-37
MMR Upgrade.................................................................................. 4-38
Guidelines for Operating MMR ........................................................ 4-39
All programs....... ...................... ................................. ............... 4-39
MMR Setup.............................................................................. 4 -39
MMR Communications............................................................. 4 -39
MMR Reports........................................................................... 4-39
Using Online Help.................................................................................... 4-41
Why MMR Help is helpful ................................................................. 4-41
Before you begin.............................................................................. 4 -42
Using Windows 95 Help..................................... .............................. 4-42
How MMR Help is structured ................................................... 4-42
How you access MMR Help..................................................... 4-42
Using Windows 3.1 Help.................................................................. 4-44
How MMR Help is structured ................................................... 4-45
How you access MMR Help..................................................... 4-47
How you find MMR Help's information..................................... 4-48
How you find procedural information........................................ 4-49

How you fin d referential informat ion......................................... 4-50
How you navigate through MMR Help's information................ 4 -52
Tutorial..................................................................................... 4-53

Chapter 5 - Alerts
Table of Contents
Alerts...................................................................................................... 5-1
Overview.................................................................................................... 5-1
SEER A lert................................................................................................. 5-2
Critical SEERs Alert........................................................................... 5-2
Displayed Report Fields............................................................. 5-2
Analysis and Corrective Actions ................................................. 5-3
Application Alerts....................................................................................... 5-3
Failed O ut c alls Alert........................................................................... 5-3
Displayed Report Fields............................................................. 5-3
Analysis and Corrective Actions ................................................. 5-4
Remot e N ot if ic at ion Target Problem A lert . ........................................ 5-4
Displayed Report Fields............................................................. 5-5
Analysis and Corrective Actions ................................................. 5-5
Failed Networking Sessions Alert ...................................................... 5-6
Displayed Report Fields............................................................. 5-6
Analysis and Corrective Actions ................................................. 5-7
Failed Fax Delivery Alert.................................................................... 5-7
Displayed Report Fields............................................................. 5-8
Analysis and Corrective Actions ................................................. 5-8
Security Alerts............................................................................................ 5-8
Excessive After-Hour Logons Alert......... ........... ........... ..................... 5-8
Displayed Report Fields............................................................. 5-9
Analysis and Corrective Actions ............................................... 5-11
Excessive Thru-Dialer Access Alert................................................. 5-12
Displayed Report Fields........................................................... 5 -12
Analysis and Corrective Actions ............................................... 5-12
Excessive Failed Logons Alert .........................................................5-13
Displayed Report Fields .......... ........... ........... ........... ................5-14
Analysis and Corrective Actions ...............................................5-14
Excessive Incomplete Voice Mail Accesses Alert ............................5-14
Displayed Report Fields .......... ........... ........... ........... ................5-15
Analysis and Corrective Actions ...............................................5-15

Chapter 6 - System Status Reports
Table of Contents
System Status Reports......................................................................... 6-1
Overview.................................................................................................... 6-1
SEER Query Report........................................................................... 6-1
Report Filters.............................................................................. 6-1
Displayed Report Fields............................................................. 6-2
Analysis and Corrective Actions ................................................. 6-2
Channel Problem Identification Report ...............................................6-2
Report Filters ..............................................................................6-3
Displayed Report Fields .......... ........... ........... ........... ..................6-3
Analysis and Corrective Actions .................................................6-4
Disk Usage Monitor Report ................. ........... ........... ..................... ....6-5
Displayed Report Fields .......... ........... ........... ........... ..................6-6
Analysis and Corrective Actions .................................................6-6

Chapter 7 - Traffic Reports
Table of Contents
Traffic Reports....................................................................................... 7-1
Overview.................................................................................................... 7-1
System Traffic Summary Report........................................................ 7-1
Report Filters.............................................................................. 7-2
Displayed Report Fields............................................................. 7-5
Analysis and Corrective Actions ................................................. 7-6
Meridia n M ail Produ c ti vi ty R eport ...................................................... 7-8
Displayed Report Fields............................................................. 7-8
Analysis and Corrective Actions ............................................... 7-10

Chapter 8 - Voice Mail Reports
Table of Contents
Voice Mail Reports................................................................................ 8-1
Overview.................................................................................................... 8-1
Voice Messaging Activity Report ....................................................... 8-2
Report Filter ............................................................................... 8-2
Displayed Report Fields............................................................. 8-2
Analysis and Corrective Actions ................................................. 8-3
Mailbox Counts Report ...................................................................... 8-4
Displayed Report Fields (Class of Service)................................ 8-4
Displayed Report Fields (Department).......................... .......... ... 8-5
Displayed Report Fields (NMS Location ID) .............................. 8-5
Displayed Report Fields (Customer Number)............................ 8-6
Analysis and Corrective Actions ................................................. 8-6
Messaging Usage Report .................................................................. 8-7
Report Filters.............................................................................. 8-7
Displayed Report Fields............................................................. 8-7
Analysis and Corrective Actions ................................................. 8-8
Call Answering/User Responsiveness Report ................................... 8-9
Report Filters.............................................................................. 8-9
Displayed Report Fields............................................................. 8-9
Analysis and Corrective Actions ............................................... 8-10
Mailbox Session Analysis Report..................................................... 8-11
Report Filters............................................................................ 8-12
Displayed Report Fields........................................................... 8 -12
Analysis and Corrective Actions ................................................8-13
Inactive User Report ........................................................................ 8-13
Report Filter ............................................................................. 8-14
Displayed Report Fields........................................................... 8 -14
Analysis and Corrective Action ................................................ 8-15
Top Users of Storage Report........................................................... 8 -15
Report Filters............................................................................ 8-16
Displayed Report Fields........................................................... 8 -16
Analysis and Corrective Actions ............................................... 8-16
Users Exceeding COS Storage Limit Report............. ..................... . 8-17
Report Filters............................................................................ 8-17
Displayed Report Fields........................................................... 8 -17
Analysis and Corrective Actions ............................................... 8-18

User Directory Report...................................................................... 8-18
Report F ilt ers............................................................................ 8-19
Display ed Report Fi elds........................................................... 8-19
Analysis and Correc t iv e Actions............................................... 8-19
Class of Service Report ................................................................... 8 -20
Report F ilt er ............................................................................. 8 -20
Display ed Report Fi elds........................................................... 8-20
Report F ilt er ............................................................................. 8 -21
Display ed Report Fi elds........................................................... 8-21
Analysis and Correc t iv e Actions............................................... 8-22

Chapter 9- Networking Reports
Table of Contents
Networking Reports.............................................................................. 9-1
Overview.................................................................................................... 9-1
Network Activity Report...................................................................... 9-1
Report Filters.............................................................................. 9-2
Displayed Report Fields............................................................. 9-2
Analysis and Corrective Actions ................................................. 9-3
AMIS Open Networking Activity Report............................................. 9-4
Report Filters.............................................................................. 9-5
Displayed Report Fields............................................................. 9-5
Analysis and Corrective Actions ................................................. 9-6

Chapter 10 - Outcalling Reports
Table of Contents
Outcalling Reports.............................................................................. 10-1
Overview.................................................................................................. 10-1
Outcalling Activit y R eport .................................................................10-1
Report Filters............................................................................ 10-2
Displayed Report Fields........................................................... 1 0-2
Analysis and Corrective Actions ............................................... 10-2
Outcalling Audi t Trail Summary Repo rt.. .......................................... 10-3
Report Filters............................................................................ 10-3
Displayed Report Fields........................................................... 1 0-3
Analysis and Corrective Actions ............................................... 10-6
Outcalling Audi t Trail Detail R eport.................................................. 1 0-6
Report Filters............................................................................ 10-6
Displayed Report Fields........................................................... 1 0-7
Analysis and Corrective Actions ............................................. 10-12

Chapter 11 - Multimedia Application Reports
Table of Contents
Multimedia Applications Reports...................................................... 11-1
Overview.................................................................................................. 11-1
Multimedia Application Caller Analysis Report................................. 1 1-1
Report Filters............................................................................ 11-2
Displayed Report Fields........................................................... 1 1-2
Analysis and Corrective Actions ............................................... 11-3
Fax Deliveries Activity Report.......................................................... 11-5
Report Filters............................................................................ 11-5
Displayed Report Fields........................................................... 1 1-5
Graph....................................................................................... 11-7
Analysis and Corrective Actions ............................................... 11-7
Fax Audit Trail Summary Report...................................................... 11-9
Report Filters............................................................................ 11-9
Displayed Report Fields........................................................... 1 1-9
Analysis and Corrective Actions ............................................. 11-10
Fax Audit Trail Detail Report.......................................................... 11-11
Report Filters.......................................................................... 11-11
Displayed Report Fields......................................................... 11-11
Analysis and Corrective Actions ............................................. 11-14

Chapter 12 - Bill-Back Files
Table of Contents
Bill-Back Files.......... ......... .......... ......... ............................ .......... ......... . 12-1
Overview.................................................................................................. 12-1
800 Access Bill-B ac k F ile. ................................................................ 1 2-1
Report Filters............................................................................ 12-2
Displayed Report Fields........................................................... 1 2-2
Analysis and Corrective Actions ............................................... 12-3
Voice Mail Usage Bill-Back Fil e ....................................................... 12-3
Report Filters............................................................................ 12-3
Displayed Report Fields........................................................... 1 2-3
Analysis and Corrective Actions ............................................... 12-4
Outcalling Bill-B ac k F ile ... ................................................................ 1 2-5
Report Filters............................................................................ 12-5
Displayed Report Fields........................................................... 1 2-5
Analysis and Corrective Actions ............................................... 12-6
Networking Usage Bill-Back File...................................................... 1 2-6
Report Filters............................................................................ 12-6
Displayed Report Fields........................................................... 1 2-7
Analysis and Corrective Actions ................................................12-7
Faxback Outcalls Bill-Back File........................................................ 1 2-8
Report Filters............................................................................ 12-8
Displayed Report Fields........................................................... 1 2-8
Analysis and Corrective Action ................................................ 12-9

Chapter 13 - Troubleshooting
Table of Contents
Troubleshooting.................................................................................. 13-1
Overview.................................................................................................. 13-1
Using the MMR Disks.............................................................................. 13-1
Recovering from Mishaps and Errors ............. ...................... ........... ........ 13-3
To recover from a missed download................................................ 1 3-3
To recover from a time-out during file transfer................................. 13-4
To merge files into the database if an error occurs
after file transfer............................................................................... 13-4
To fix a corrupted database............................................................. 13-5
To stop interference from another newly installed program............. 13-7
To recover from hard disk problems or a virus................................. 1 3-8
Error Me s s ages Durin g I ns t allation. . ... ..................................................... 1 3-9
Error Me s s ages After I ns t allation. .......................................................... 13-10
Critical Errors.......... ........... ........... ........... ...................... ........... ........... .. 13-16
To troubleshoot a critical error ....................................................... 13-16
Critical Error Messages.................................................................. 13-16
Fatal Error Messages............................................................................. 13-45

Appendix A - Modem and Cable Specifications
Table of Contents
Modem and Cable Specifications........................................................A-1
Modems and Modem Settings.................................................................. A-1
Defining Modem Settings in MMR Setup.......................................... A-1
Change Settings for Modems Connected to the MMR PC................ A-3
Change Settings for Modems Connected to Meridian Mail............... A-6
Cable Requirements................................................................................. A-9
Chapter 1: Introducing MMR
Overview
Meridian Mail Reporter (MMR) is a PC software package developed to run under
Microsoft Windows 3.1, Microsoft Windows NT, or Windows 95. MMR enables a
Meridian Mail administrator to produce and print both summary and detailed
reports for use in managing Meridian Mail systems. MMR uses periodic downloads
of Operational Measurements (OM) Þles received from one or more Meridian Mail
systems, and incorporates this information into a Microsoft Windows-based
relational database on the PC.
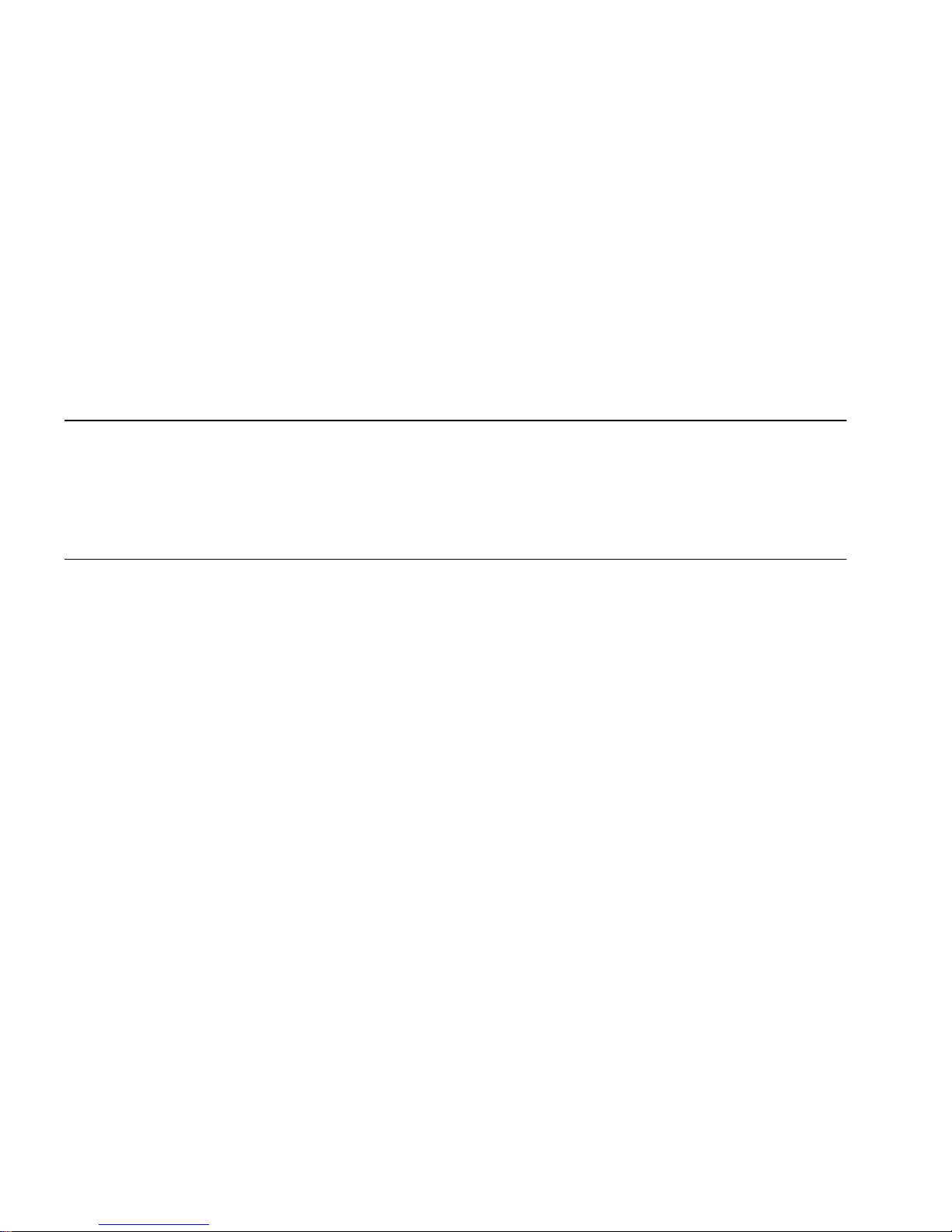
Figure 1-1
Meridian Mail Reporter System
ESC
F1
F2
F3
F4
!
`
1
@
TAB
F5
2
F6
#
3
F7
$
QWERT YU I OP
4
%
CAPS LOCK
SHIFT
CTRL
ASDFGHJKL
ZXCVBNM
ALT
F8
5
^
F9
6
&
F10
7
*
F11
8
(
F12
9
)
PRINT
_
SCREEN
0
SYS RQ
SCROLL
_
+
P
LOCK
A
U
S
E
=
B
R
E
BACKSPACE
A
K
N
U
{
[
:
<
;
,
>
"
.
'
?
/
SHIFT
ALT
CTRL
M
L
O
C
K
C
A
P
S
}
]
ENTER
L
O
C
S
K
C
R
O
L
INSERT
L
L
I
I
O
C
K
HOME
PAGE
DELETE
UP
NUM
END
LOCK
PAGE
DOWN
/
789
*
-
456
PG DNHOME
+
1
END PG DN
2
3
INS
E
N
.
T
DEL
E
R
Meridian Mail Meridian Mail Reporter PC Printer
The administrator can easily produce and print the following information:
¥ Alert reports that notify you of critical problems that require immediate attention
¥ System Status reports used for troubleshooting hardware or software conÞguration
problems, as well as providing capacity analysis information useful for
balancing your system
1 - 1

Meridian Mail Reporter 2.0 UserÕs Guide
¥ TrafÞc reports that provide information regarding busy hours for all, or individual,
services
¥ Voice Mail reports that are used to analyze trends and usage of the messaging
application of Meridian Mail
¥ User Information reports used to provide a directory of users and classes of service
(COS)
¥ Networking reports used for analyzing network usage and for providing indicators
of potential networking problems
¥ Outcalling reports used to analyze outcalling activity and for providing indicators
of potential outcalling problems
¥ Multimedia Application Caller Analysis and Fax Delivery reports used for
analyzing service activity for voice menus, announcements, and fax on demand
¥ Bill-Back Þles used for billing system usage back to the appropriate users and
departments
Components of Meridian Mail Reporter
Meridian Mail Reporter consists of three main components: Setup,
Communications, and Reports.
MMR Setup
MMR Setup is used for installing and conÞguring the MMR system on your
computer. MMR Setup is invoked from the installation diskettes when you are
doing a new installation or an upgrade (for example, from single site to multisite).
After installing MMR, you can use the MMR Setup program to add, delete, or
change your systemÕs site information. The MMR Setup installation process is
discussed in detail in Chapter 3, ÒInstalling MMR.Ó
MMR Communications
MMR Communications is a stand-alone program that provides the interface
between the Meridian Mail system and your computer. Once MMR is installed, this
program starts automatically whenever Windows is started. MMR Communications
runs in the background where it starts downloads according to the download
schedule, activates MMR Reports to merge the download data, checks
1 - 2

alerts, and prints reports. Also, MMR Communications provides system monitoring
capabilities such as displaying link status and recording all link activity in log Þles.
Note: MMR Communications must always be active or automatic downloads and
scheduled reports will fail to occur.
MMR Reports
MMR Reports allows you to view and manage alerts and reports. Both alerts and
reports analyze performance metrics on the systemÕs hardware, application, and
security. However, alerts and reports are distinct: alerts have thresholds and reports
have Þlters. Due to their thresholds, alerts indicate problems which need immediate
attention. MMR tests for alert conditions after a download; when a predeÞned
threshold is met or exceeded, an alert is triggered. ReportsÕ Þlters allow you to set
speciÞc parameters for queries. As a result, you can deÞne the scope of information
that a report contains. In the main window of MMR Reports, alerts and reports
appear in the Alert and Report palettes.
Introducing MMR
MMR Reports gives you the capabilities to view and print reports, customize the
Alert and Report palettes, create a schedule for printing reports, and modify the
download schedules of Operation Measurements.
These capabilities are explained in Chapter 4, ÒUsing MMR and its Online Help,Ó
as well as in the online help provided with MMR.
In Chapters 5 through 12, you will Þnd overviews of each report including
¥ Þeld deÞnitions
¥ an example of the report
¥ output sort keys
¥ analysis and corrective actions
These eight report chapters will be very useful for analyzing Meridian Mail usage
patterns and for preventing potential problems.
1 - 3

Meridian Mail Reporter 2.0 UserÕs Guide
BeneÞts of Using Meridian Mail Reporter
Meridian Mail Reporter provides an easier way of monitoring and maintaining your
Meridian Mail system. The following are beneÞts that can be realized by using
MMR.
Security
Computer hacker attacks on your Meridian Mail system can be disruptive and
costly to your company. Toll fraud is one result of hacker activity on a telephone
system. Toll fraud causes millions of dollars in losses each year.
Hackers use various means to try to gain access into phone systems. MMR
provides reports that notify you of
¥ excessive unsuccessful login attempts that may be a result of brute force attacks on
the systemÕs mailboxes
¥ excessive after-hours logins that might occur if a hacker penetrates a mailbox
¥ excessive thru-dialer accesses that might occur if hackers are using a thru-dialer to
make toll calls
The information provided in these reports helps in determining necessary
corrective actions to prevent further hacker activity.
Convenience
During installation, MMR automatically creates a default download schedule so
that no further conÞguration is required once the program is installed. MMR allows
the administrator to modify the download schedule and to create a schedule for
printing reports.
Flexibility
Because of its ßexibility, MMR can do the following:
¥ Transfer OM Þles from any Meridian Mail system whether it is a 4-port Card
Option on an Option 11 PBX, a 96-port Modular EC on an Option 81 PBX, or a
192-port MSM connected to an SL-100 PBX or DMS-100 central ofÞce. As
well, the MMR PC and the Meridian Mail system can be located in different
buildings or even in different cities because MMR can transfer OM Þles through
a modem. Using a single PC, MMR also can collect OM Þles from several
different Meridian Mail systems.
1 - 4

Introducing MMR
¥ Alert you of a critical problem on the Meridian Mail system which may require
immediate attention.
¥ Offer a portfolio of 38 built-in management reports. They provide a broad
spectrum of management information ranging from a simple directory of the
mailboxes on a Meridian Mail system to a comprehensive analysis of every
voice messaging and call answering session that took place on the system.
¥ Customize reportsÕ sort orders and Þlter data. The contents of the management
reports produced by MMR follow a certain sort order; however, you can create
customized reports with different sort orders. The management reports are
derived from all of the information stored in the database; however, you can
Þlter the data in order to limit the scope of a report (for example, to a speciÞc
department).
¥ Follow a schedule for printing reports on a periodic basis (for example, daily).
¥ Export the information in any report to a variety of PC Þle formats including
Microsoft Excel and Lotus 1-2-3. Also, using MMR, you can create a schedule
for exporting reports into ASCII Þles on a periodic basis. You can incorporate
these Þles into a centralized billing system.
¥ Provide you with context-sensitive online help during any operation.
Centralization
With MMR and Meridian Mail Releases 10 and 11, you can capture Operational
Measurement (OM) data from multiple sites into one centralized database. This
enables you to monitor and maintain several systems from one location. The
number of systems from which you can collect data depends on the amount of data
to be downloaded over the RS-232 link (it must be done within a 20-hour window)
and the available disk space on the MMR PC. The volume of OM data determines
the size of the MMR database.
Visual Information
Some of the reports can be displayed in graph format. Graphical format is useful
for quick analysis of data allowing you to see trends in system use. With the System
TrafÞc Summary report, for example, you can easily monitor the total amount of
trafÞc processed by your siteÕs Meridian Mail services. This graph allows you to
identify the systemÕs busy hour(s) and determine whether you have sufÞcient port
capacity to handle the load.
1 - 5

Meridian Mail Reporter 2.0 UserÕs Guide
Ability to Bill Service Usage
MMR Reports include a set of Þles that can be used to make billing of service
usage much easier. The bill-back Þles are output as either reports or as ASCII text
Þles. The ASCII text Þles can be used to feed data into an external bill-back
program. Bill-back Þles are provided for Voice Mail, 1-800 Service, Outcalling,
Networking, and Fax Outcalling services.
Historical information
MMR Reports can be scheduled to run on a daily, weekly, monthly, or on-demand
basis. MMR can keep data for up to 180 days provided that your MMR PC has
sufÞcient hard disk capacity.
1 - 6

Chapter 2: Getting Started
Introduction
This chapter explains what you need to know before you begin to install MMR. As
well, you learn how to set up Meridian Mail so it can support MMR.
Background Information
Before beginning the installation of Meridian Mail Reporter (MMR), you need to
know some important things. You should understand PC and DOS terminology and
concepts. Make sure that you understand terms such as ÒÞlename,Ó Òsubdirectory,Ó
and Òdrive.Ó If you do not have a Þrm grasp of this type of information, you may
Þnd installing and using MMR difÞcult.
You should also be familiar with the Windows environment. Also, understand
concepts such as icons and clicking, and know how to print in the Windows
environment.
For information on DOS, Windows, and the PC, refer to the documentation you
received with your PC.
From a Meridian Mail perspective, you should have the
(SEERs)
Manual
Reference Manual
(NTP 555-7001-30x) available for help with problem determination.
(NTP 555-7001-501), and the
Maintenance Messages
System Administration
2 - 1
Meridian Mail Reporter 2.0 UserÕs Guide
MMR ConÞguration
Meridian Mail Reporter is available in four conÞgurations:
¥ single site Meridian Mail 10 and 11
¥ multisite Meridian Mail 10 and 11
The following diagrams show how MMR is conÞgured with Meridian Mail (MM).
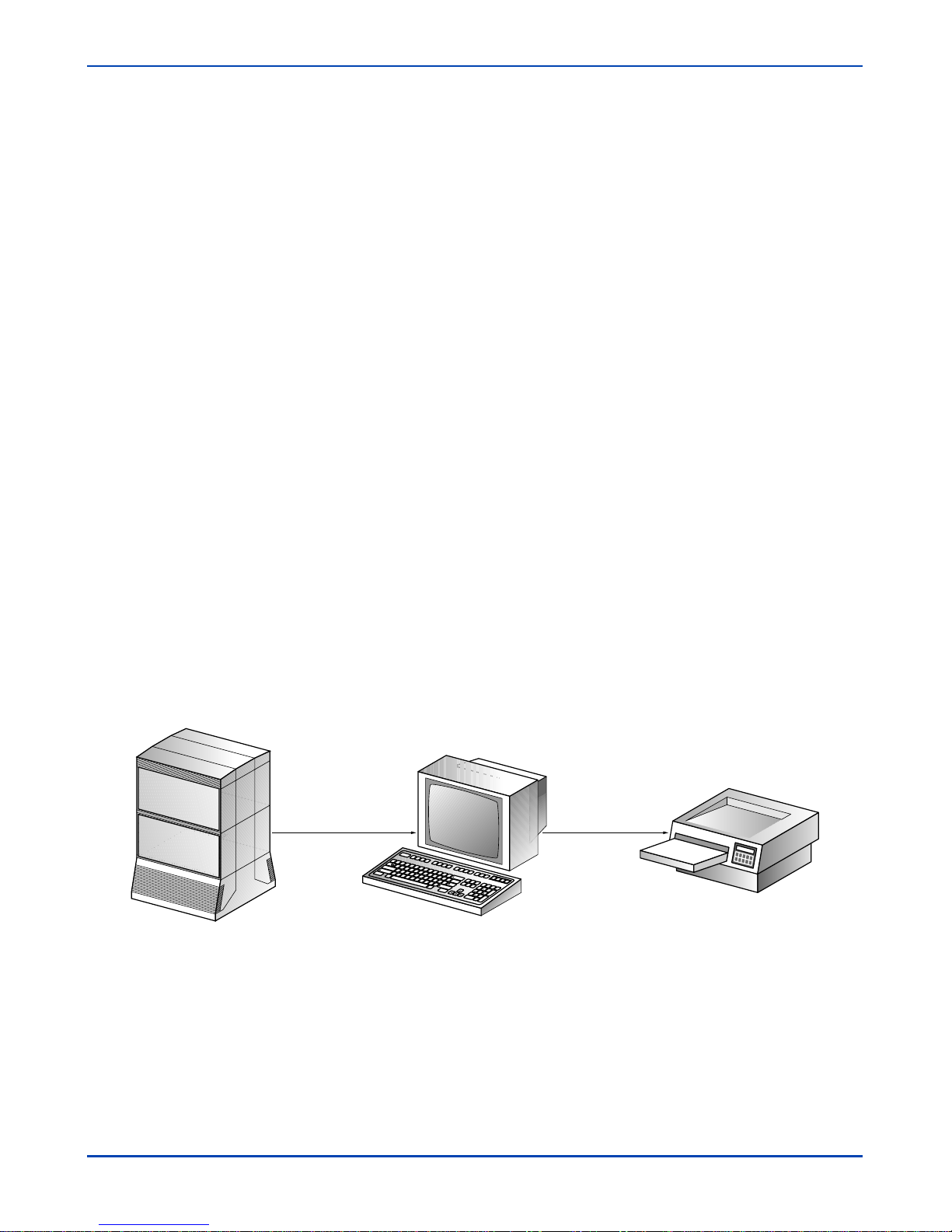
Figure 2-1
Single site conÞguration
Direct RS-232 link
or modem dial-in
ESC
F1
F2
F3
F4
!
`
1
@
TAB
F5
2
F6
#
3
F7
$
QWERT YU IO P
4
%
CAPS LOCK
SHIFT
ASDFGHJKL
CTRL
ZXCVBNM
ALT
Meridian Mail Meridian Mail Reporter (MMR)
F8
5
^
F9
6
&
F10
7
*
F11
8
(
F12
9
)
PRINT
_
SCREEN
0
SYS RQ
SCRO
_
+
LL
PAUSE
LO
CK
=
BREAK
BACKSPACE
N
UM
{
LOCK
[
:
<
;
,
>
"
.
'
?
/
SHIFT
ALT
CTRL
CAPS
LO
}
CK
SCRO
LL
INSERT
]
ENTER
LO
I
CK
H
I
O
M
E
PAG
E
DELETE
UP
NUM
END
LOC
K
PAG
E
DO
/
W
N
789
*
H
O
-
M
E
456
P
G
D
N
+
1
E
N
2
D
3
P
G
D
INS
E
N
N
.
T
DEL
E
R
Printer
Note: The dataport is connected to either an RS-232 port on an RSM or Utility card
or a Transition Module (on an MSM), or on an MMP40 card in one of the voice
nodes.
The single site conÞguration connects to Meridian Mail on an AdminPlus dataport
designated for Meridian Mail Reporter (MMR) use. This port is dedicated to
Operational Measurements (OM) download and is conÞgurable on any dataport
except for those used by the AML link and console.
2 - 2

Figure 2-2
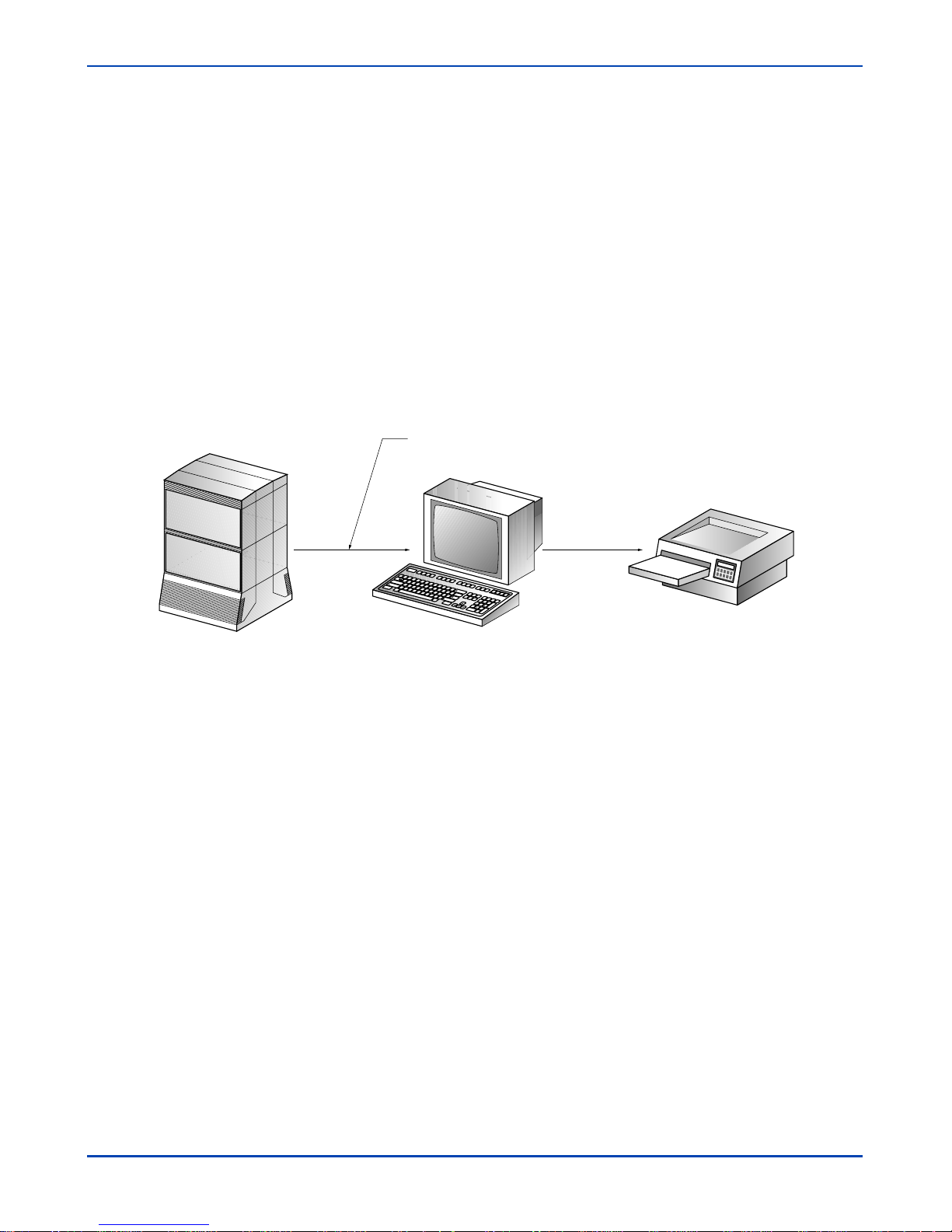
Multisite conÞguration
Modem
YES
NO TALK/DATA
MR/RI TR HS MC RD TD
Meridian Mail
Getting Started
2440
Meridian Mail
Modem
YES
NO TALK/DATA
MR/RI TR HS MC RD TD
2440
Modem
YES
NO TALK/DATA
MR/RI TR HS MC RD TD
2440
ESC
F1
F2
F3
F4
!
`
1
@
F5
TAB
2
F6
#
3
F7
$
QWERT YUIOP
4
%
F8
CAPS LOCK
5
^
F9
6
&
F10
7
SHIFT
ASDFGHJKL
*
F11
8
(
F12
9
)
CTRL
ZXCVBNM
ALT
PRINT
_
SCREEN
0
SYS RQ
SCROLL
_
+
P
LOCK
A
U
S
E
=
B
R
E
BACKSPACE
A
K
N
UM
LO
{
C
K
CAPS
[
LO
}
CK
SC
RO
LL
IN
]
LO
S
I
E
CK
R
T
:
<
H
I
O
M
;
E
,
PAGE
>
"
D
UP
E
L
.
E
ENTER
'
T
?
E
NUM
END
LOCK
/
PAGE
SHIFT
DOWN
/
ALT
789
*
H
O
-
M
E
CTRL
456
P
G
D
N
+
1
E
N
2
D
3
P
G
D
INS
E
N
N
.
T
DEL
E
R
Meridian Mail Reporter PC Report Printer
Modem
YES
NO TALK/DATA
MR/RI TR HS MC RD TD
2440
Meridian Mail
Note:
The dataport is connected to either an RS-232 port on an RSM or Utility card
or a Transition Module (on an MSM), or on an MMP40 card in one of the voice
nodes.
The multisite conÞguration is designed for customers with several MM systems
who want centralized reporting. Each Meridian Mail system must have an
AdminPlus dataport with an attached modem. The number of MM systems
supported in a multisite conÞguration is determined by the aggregate amount of
OM data to be downloaded.
The number of ports on a Meridian Mail system determines the volume of OM data
collected on a daily basis. The number of days that the data is kept on the PC
determines the size of the MMR database. Therefore, the limits for a speciÞc
conÞguration will be limited by two factors (for details, refer to the ÒMMR
Hardware and Software RequirementsÓ section in this chapter):
¥ the available disk space on the MMR PC (since the volume of OM data and days
stored determines the size of the MMR database)
2 - 3

Meridian Mail Reporter 2.0 UserÕs Guide
¥ the aggregate time required to download the collected OM data on a daily basis
over an RS-232 link (no more than 12 hours is recommended, but up to 20 hours
is allowed)
Refer to the ÒMeridian Mail ConÞguration InformationÓ section in the Appendix
for tabular information on
¥ platforms supported
¥ ports
¥ modem connection
¥ the File Transfer features including platforms supported, Meridian Mail features,
and serial port speeds
MMR Hardware and Software Requirements
Meridian Mail Reporter has certain hardware and software requirements to ensure
that it runs efÞciently. Make sure that your locationÕs hardware and software meet
or exceed the following minimum mandatory requirements.
Hardware
Your PC must have the following minimum hardware requirements to run MMR:
¥ a 486 DX2 CPU, 66MHz
¥ RAM
or
a Pentium CPU, 90MHz is recommended for more than 12 Meridian Mail ports
Ñ
8 Mbytes for Windows 3.1 (16 Mbytes is recommended for more than 16
Meridian Mail ports)
12 Mbytes or Windows 95 (20 Mbytes is recommended for more than 16
Meridian Mail ports)
Ñ 16 Mbytes for Windows NT Client (24 Mbytes is recommended for more
than 16 Meridian Mail ports)
Ñ 32 Mates for Windows NT Server (40 Mbytes is recommended for more than
16 Meridian Mail ports)
¥ a hard disk drive
The space required to hold the MMR database is determined by the number of
voice ports and the number of days your site will store the information in the
2 - 4

MMR database. MMR requires 550 Mbytes as the greatest amount of free disk
space.
¥ one serial port (a serial card with 16550 UART required) for connection to
Meridian Mail
¥ one modem for the MMR PC (U.S. Robotics 14.4 is recommended) and one
modem for each Meridian Mail system for a multisite conÞguration
¥ a 3.5-inch ßoppy disk drive
¥ a VGA monitor
¥ a keyboard and a mouse
Optional Hardware
Getting Started
¥ one modem for the MMR PC and one modem for a Meridian Mail single site
For sites that require hard copy reports
¥ a laser printer (recommended) with sufÞcient memory to produce graphical reports
Software
Your PC must have the following software packages installed to run MMR:
¥ MS-DOS Version 5.0 or later
¥ Microsoft Windows 3.1, Microsoft Windows 3.11, Microsoft Windows For
Note: Dual-boot conÞgurations (such as Microsoft Windows 3.1- Microsoft
Windows NT, Microsoft Windows 3.1 - Microsoft Windows 95, Microsoft
Windows 3.1 - OS/2), are not supported.
conÞguration
(for example for an HP LaserJet with at least 2 Mbytes of RAM are required).
The printer can be connected directly to the PC or through a LAN.
Workgroups 3.11 running in 386 enhanced mode, Microsoft Windows NT 3.51,
or Microsoft Windows 95
2 - 5

Meridian Mail Reporter 2.0 UserÕs Guide
¥ an installed MS Windows printer driver
The Print Preview function, which is used to view reports on the screen, requires
the existence of an installed printer driver, even if the PC does not have access to
a printer.
Note: If you do not intend to print reports, then install the highest resolution
driver provided on your system to ensure the highest quality output of the
screens.
¥ SHARE (a utility that comes with DOS)
Important:
You require SHARE for use with only Windows 3.1 and Windows
for Workgroups.
SHARE is used by the Setup program to install MMR. To start the utility, exit
from Windows (by selecting FILE/EXIT from Windows Program Manager).
Once at the DOS prompt, type
SHARE is already installed, you will be notiÞed by the proper message, but you
can safely ignore the message. To restart Windows, type
prompt and press Enter. Follow the normal procedure to install MMR.
SHARE
and press Enter to run SHARE. If
WIN
at the DOS
It is important to note that since the installation process needs SHARE to be
loaded in memory before Windows is started, do not attempt to run a DOS
instance (MS-DOS prompt) from within Windows in order to run SHARE. This
will not work.
¥ a disk caching program (for example, SMARTDRV.EXE)
Important:
You require a disk caching program for use only with Windows 3.1
and Windows for Workgroups.
This program is part of the MS-DOS package and can be activated by inserting
the following line in the AUTOEXEC.BAT Þle:
C:\DOS\SMARTDRV.EXE
Note: The default installation of MS-DOS inserts the following line in the
AUTOEXEC.BAT Þle:
C:\DOS\SMARTDRV.EXE /X
The /X switch (which disables write caching) should be removed since write
caching provides a noticeable improvement in the performance of the merge
process.
2 - 6

Getting Started
Virtual Memory Settings for Windows 3.1
The settings for virtual memory can be changed in Microsoft Windows 3.1 through
the Control Panel, 386 Enhanced.
Make sure that, in the Virtual Memory dialog box, the following are disabled:
¥ Use 32-Bit Disk Access
¥ Use 32-Bit File Access (available in Windows For Workgroups only)
Failure to do this may result in disk access errors during the Þle conversion or
merge process.
For maximum performance, it is recommended that the current settings for the
swap Þle be set as Permanent.
Windows 3.1 Protection and Multitasking
Microsoft Windows 3.1 is not a true protected environment: it does not protect
itself fully from misbehaving applications, nor does it protect the applications
themselves from one another. As well, under Windows 3.1 you cannot multitask
because a running application is not guaranteed CPU time at regular intervals.
As a major consequence of the low level of protection in Windows 3.1, when an
application crashes with a General Protection Fault (GPF) error message or any
other Windows fatal error, the integrity of the system cannot be guaranteed
anymore. Under such circumstances, stop MMR immediately and terminate
Windows; then, restart Windows which restarts MMR. If you do not terminate and
restart Windows, all subsequent operation may encounter problems.
Because Windows 3.1 does not offer multitasking, MMR Communications is
vulnerable to other applications holding the CPU for long periods of time. MMR
Communications requires regular CPU time to download Þles from Meridian Mail.
If MMR Communications is delayed, the communications link with Meridian Mail
can terminate and cause a download in progress to fail. Consequently, you should
not run other programs, even another MMR program, while MMR
Communications downloads. For example, running reports, either scheduled or on
demand, in MMR Reports during a download can cause that download to fail. Even
using File Manager to copy between a ßoppy disk and the hard drive could cause
the download to fail.
2 - 7
 Loading...
Loading...