Nortel BayStack 650, BayStack 660, BayStack 600 Reference Manual

BayStack 600 Series
Wireless LAN
Security
September 1998

BayStack 600 Series Wireless LAN Security
Copyright © 1998 Nortel Networks (Nortel). All rights reserved. The information contained in this document
represents the current view of Nortel, on the issues discusses as of the date of publication. Because Nortel must
respond to the changing market conditions, it should not be interpreted to be a commitment on the part of Nortel
and Nortel can not guarantee the accuracy of any information presented after the date of publication.
This document is for information purposes only. Nortel makes no warranties, express or implied, in this document.
©9-1998
BayStack 600 Series Wireless LAN Security 2
1. Overview
Many people have extra concerns about wireless data transmission due in part to the lack
of security for wireless voice systems. Although wireless LANs, like voice systems, utilize
radio signals to send data, non-digital wireless LANs are sophisticated digital systems and
can be made quite secure. The 802.11 wireless LAN standard specifies a “Wired
Equivalent Privacy” option for maximum integrity of data being sent over the air.
But there are also other aspects of the BayStack Wireless LAN system that also contribute
to the security of the overall system.
First, wireless LANs are in essence an extension of the wired infrastructure, providing
portable PC users with LAN access just like a wired network adapter. As a result, the
overall password and login in protection schemes are handled by IT and MIS network
administrators for their wired local area networks (LAN) apply to their wireless local area
networks as well.
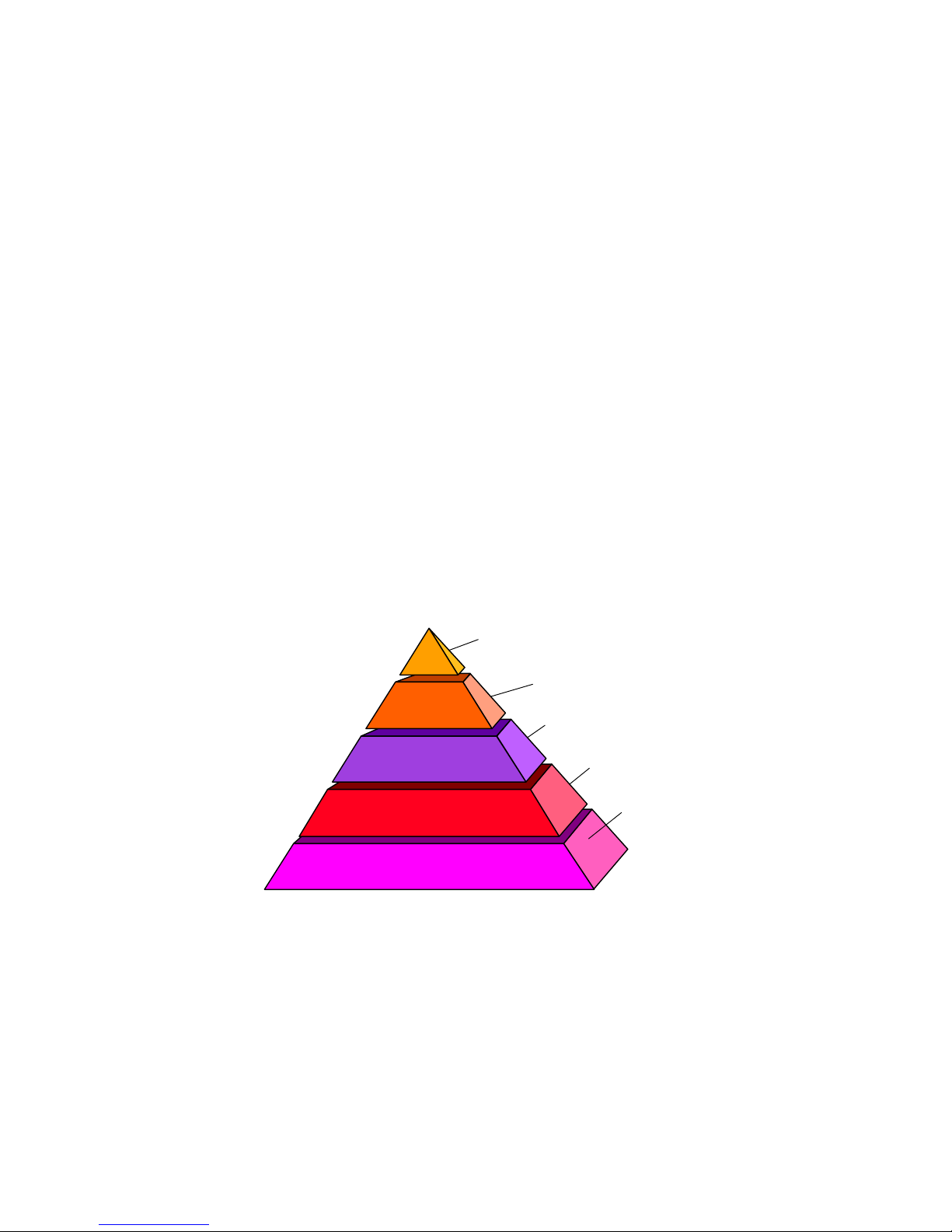
The BayStack wireless LAN system security can be viewed as five layers: radio design and
operation, WLAN segmentation and identification, over-the-air data scrambling,
authentication of users by adapter MAC address and security over the access point
configuration utilities.
5 Levels of Security
APs: Password protected and configurable
AP
Locking
User
Authentication
Data Scrambling
Unique Keys
Virtual WLAN Segments
“SSIDs”
Spread Spectrum Radios
Spread Spectrum Radios
Secure Radio Links
Secure Radio Links
The balance of this paper describes these security features in more detail and provides
recommendations for implementing them.
over the wire only
Each AP contains a registry list
of authorized PC Card serial#s
Optional data encryption
RSAs RC4 ...
Independent co-located
“logical” networks
Secure Radio
Transmission
Sales Training - Field Sales - 1
BayStack 600 Series Wireless LAN Security 3
 Loading...
Loading...