
BayStack 600 Series
Wireless LAN
Security
September 1998

BayStack 600 Series Wireless LAN Security
Copyright © 1998 Nortel Networks (Nortel). All rights reserved. The information contained in this document
represents the current view of Nortel, on the issues discusses as of the date of publication. Because Nortel must
respond to the changing market conditions, it should not be interpreted to be a commitment on the part of Nortel
and Nortel can not guarantee the accuracy of any information presented after the date of publication.
This document is for information purposes only. Nortel makes no warranties, express or implied, in this document.
©9-1998
BayStack 600 Series Wireless LAN Security 2
1. Overview
Many people have extra concerns about wireless data transmission due in part to the lack
of security for wireless voice systems. Although wireless LANs, like voice systems, utilize
radio signals to send data, non-digital wireless LANs are sophisticated digital systems and
can be made quite secure. The 802.11 wireless LAN standard specifies a “Wired
Equivalent Privacy” option for maximum integrity of data being sent over the air.
But there are also other aspects of the BayStack Wireless LAN system that also contribute
to the security of the overall system.
First, wireless LANs are in essence an extension of the wired infrastructure, providing
portable PC users with LAN access just like a wired network adapter. As a result, the
overall password and login in protection schemes are handled by IT and MIS network
administrators for their wired local area networks (LAN) apply to their wireless local area
networks as well.
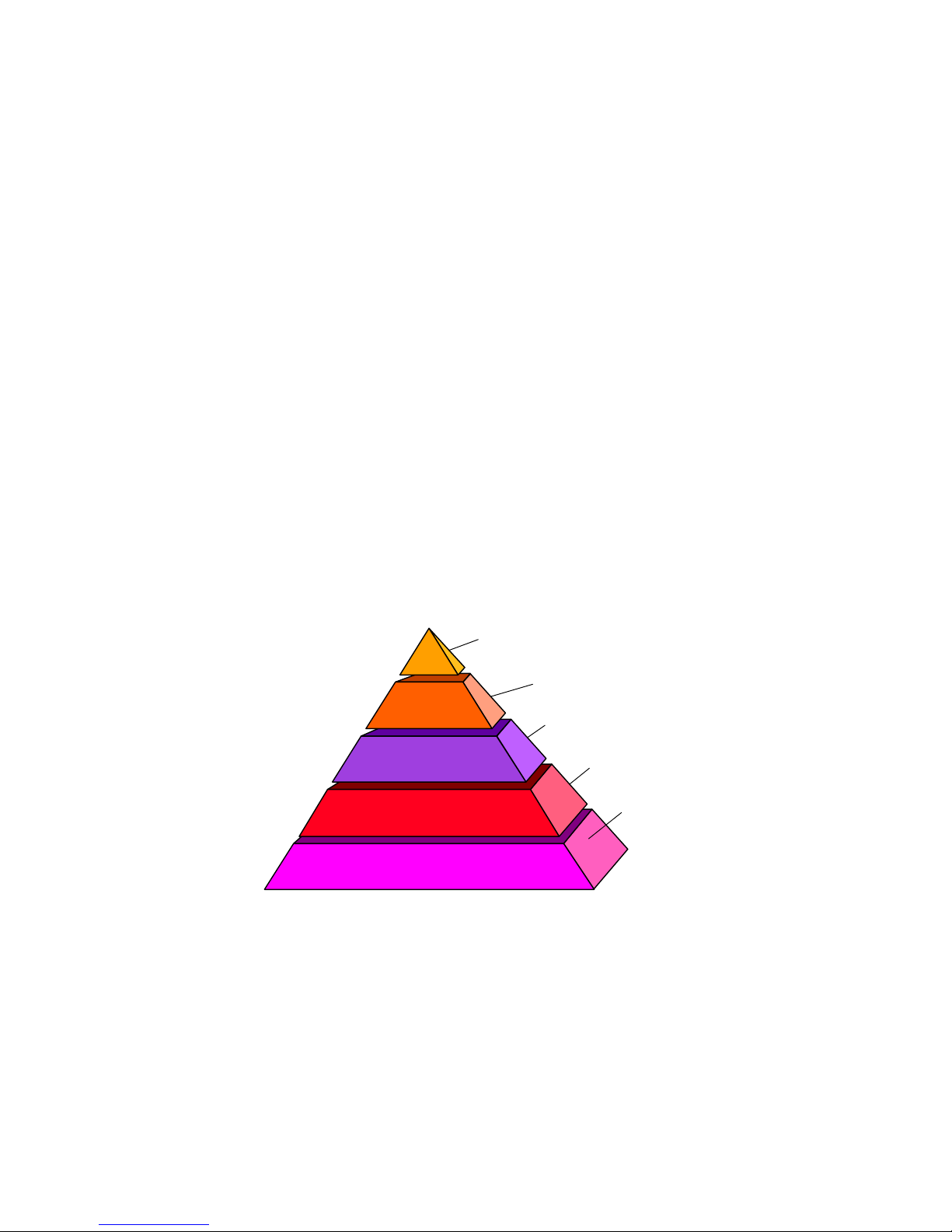
The BayStack wireless LAN system security can be viewed as five layers: radio design and
operation, WLAN segmentation and identification, over-the-air data scrambling,
authentication of users by adapter MAC address and security over the access point
configuration utilities.
5 Levels of Security
APs: Password protected and configurable
AP
Locking
User
Authentication
Data Scrambling
Unique Keys
Virtual WLAN Segments
“SSIDs”
Spread Spectrum Radios
Spread Spectrum Radios
Secure Radio Links
Secure Radio Links
The balance of this paper describes these security features in more detail and provides
recommendations for implementing them.
over the wire only
Each AP contains a registry list
of authorized PC Card serial#s
Optional data encryption
RSAs RC4 ...
Independent co-located
“logical” networks
Secure Radio
Transmission
Sales Training - Field Sales - 1
BayStack 600 Series Wireless LAN Security 3

2. The BayStack 600 Wireless System Radio Design and Operation
2.1 FCC 2.4 GHz Spectrum
The BayStack 600 Series wireless LAN
systems operate in the 2.4GHz range of
the unlicensed Industrial, Scientific, and
Medical (ISM) bands. See Figure 1 for an
overview of the spectrum assignments.
This ranges falls into the Super High
category of telecommunications.
Transmissions in this range are difficult to
intercept or jam as a result of the
extremely high frequency involved. This in
itself presents a certain level of security.
Figure 1. Spectrum Assignments
2.2 Radio Design
The BayStack 600 Wireless LAN products use a low power radio design. The BayStack
600 Series radios only outputs 50 milliwatts of power and supports a smaller radio range
compared to other wireless LAN products with more powerful radios outputting in excess of
200 milliwatts of power. For security reasons, this is desirable, because the radio signals
are restricted to a limited range. The BayStack 650’s radio range is about 225 feet in a
typical office environment, while the BayStack 660’s radio range is about 300 feet in the
same environment. These ranges permit each access point to service an optimum sized
cell of users while not posing the security risks inherent in excessively large cells.
The BayStack 600 Series’ low-power radio design also makes the system scaleable and
contributes to better overall system performance. Each access point adds additional data
throughput capacity to the overall system. Because the system supports a smaller radio
range, it allows users to add more access points to increase capacity in the same area
without concerns about airwave pollution. The cellular phone industry has found this to be
important and is also moving to the “smaller cells” concept.
2.3 Frequency Hopping Spread Spectrum Radio
The IEEE 802.11 Specification defines two types of RF modulation standards for
transmissions in the 2.4 GHz range, both employing spread spectrum technology:
Frequency Hopping Spread Spectrum and Direct Sequence Spread Spectrum. Spread
spectrum technology was originally developed for the military in order to dramatically reduce
BayStack 600 Series Wireless LAN Security 4

the ability of an enemy to intercept the signals.
Figure 3. Direct Sequence
Frequency Hopping Spread Spectrum (FH) is a
process whereby a radio transmits and receives
on one frequency for a short period of time
(called dwell time) and then changes, or hops, to
another frequency, transmits and receives, and
hops to another and so on. Nortel Networks'
BayStack 650 products are based on frequency
hopping technology. This technique carves the
ISM band into 78 separate 1 MHz channels.
Figure 2. Frequency Hopping
Every 10th of a second, the signal moves from
one frequency to another, transmitting short bursts of data (see Figure 2.) The choice of
channels is based on a pseudo-random hopping algorithm.
The constantly shifting nature of frequency hopping systems make them very difficult to
intercept or to jam. All mobile units accessing the network must use the same hopping
sequence and must also synchronize their hop timing. An intruder must know, at any
precise 10th of a second, both the current transmission frequency and the hopping pattern
that dictates the next frequency to which the system will jump next in order to intercept the
signal or jam the transmission.
2.4 Direct Sequence Spread Spectrum Radios
The second type of RF modulation in the 802.11 specification is Direct Sequence Spread
Spectrum. The BayStack 660 products operate within the same 2.4 MHz band as the
BayStack 650 products. However, the BayStack 660 products utilize a completely different
radio modulation technique than used with Frequency Hopping. This technique is called
Direct Sequence. With Direct Sequence, the original data stream is multiplied by a
spreading factor or “chipping code”. This process
actually breaks down each data bit into multiple
“sub-bits” or chips, represented by a “0” or a “1”
within a set pattern and transmits those chips over
a frequency range much broader than the “normal”
range of the data stream (see Figure 3). (The FCC
actually requires that the resulting bit rate exceed
the original rate by at least a factor of 10). A
receiver (having the same chipping code “key”)
would then take in the transmitted range of chips,
reprocess them through a “decoder”, and
reassemble the original date stream. Instead of
using a discrete signal for any given slice of
BayStack 600 Series Wireless LAN Security 5

time for a transmission (like we find in normal radio communications), or even discrete,
narrow signals to which a data stream would “hop” (like in Frequency Hopping), the data
stream in Direct Sequence systems is sent over a wide range within the band. The larger
the chipping sequence, the wider the transmission band over which the original signal is
spread.
The process of spreading the signal over the transmission band has a direct security
benefit. The application of the chipping code not only spreads the original bit stream, but
creates an encrypted sequence. This ensures a greater degree of security. An “intruder”
would have to first establish which part of the frequency range was used for the
transmission, and then establish the chipping code used to spread the data in order to
“decrypt” the original data stream. With Direct Sequence, the transmission amplitude is
also so small that it actually looks like noise in the radio spectrum, making interception
even more difficult.
3. BayStack Wireless LAN Segments
The IEEE 802.11 specification defines the concept of a Service Set Identifier (SSID). A
SSID is a 32 byte string that serves as an identifier for a wireless LAN segment. All access
points and mobile units that belong that a specific SSID are part of the same “logical”
network and can communicate. This can be seen as a “logical grouping” for wireless LAN
devices to communicate wirelessly. Mobile users that do not have the correct SSID
configuration cannot communicate with the other devices using the correct SSID
identification. Given the 32 byte field, there are millions of possible SSID values. This is an
extremely valuable security level.
BayStack 660 Series products do not allow the SSID values in access points to be
changed by mobile units. The access point configuration can only be changed by an
administrator on a wired LAN. In large BayStack 600 wireless infrastructures with multiple
access points, the SSIDs of all the access points would normally be the same in order to
permit mobile users to roam from one access point’s coverage area to the next without
being disconnected from the network. If desired, however, an administrator could create
different wireless domain for the exclusive use of a various groups of users. Each SSID
would only be visible by the users of that “domain,” even with the utilities.
4. Data Encryption
In addition to SSIDs, the 802.11 specification includes an optional security feature to
protect a wireless LAN from eavesdropping. A complex encryption algorithm called Wired
Equivalent Privacy is a technique that uses a 64-bit key along with the RC4 algorithm. The
BayStack 600 Series Wireless LAN Security 6

data packet is encrypted for transmission on the wireless media, and then decrypted back
to the original data stream by the receiver. Only the destination device has the key to
decrypt the data stream correctly. Nortel Networks will be including WEP security in an
upcoming release of the BayStack 600 Series products.
When data scrambling is employed, unauthorized users with the correct SSID can still not
have access to data not destined for them and will only receive scrambled, unreadable
data. The algorithm is sufficient to make it unlikely for an attacker with a commercially
available BayStack PC Card and custom software to eavesdrop on a LAN, since such a
person would need to guess the one in several million SSIDs and encryption key values.
Real end-to-end security, as with any LAN, is left to higher-layer software, which is
available from third party suppliers.
5. User Authentication and Access Point Configuration Management
The User Authentication feature optionally determines which BayStack 600 Series Wireless
LAN nodes are allowed to access the wired network through an access point. Only
authorize PC Cards whose IEEE (MAC) addresses that have been added to the access
point User List in the BayStack AP Manager utility can access the wired network through
the access point. In essence, the PC Card’s IEEE address becomes a physical key to the
network. In network environments with sensitive data or application files that require
restricted access, User Authentication ensures that the access point will grant access to
only those users whose IEEE addresses have been configured for that access point. Each
access point can be configured to store up to 128 Ethernet addresses. The BayStack AP
Manager allows for the management and propagation of Authorized User Lists across
several access points.
6. Access Point Security
The final level of security is the protection of the access point configuration. Each access
point can have its own unique password. Password locking ensures that an intruder who
gains access to the wired network and the commercially available BayStack AP Manager,
cannot modify settings within the access points, granting himself or other unauthorized
users access to network resources.
7. Summary
If security is critical in an environment, we recommend that the wireless product employ all
the security features available. Like any security measure, it is only as good as the
implementation. Access point password protection and SSIDs should be changed on a
BayStack 600 Series Wireless LAN Security 7

regular basis. Once WEP is released, it should be used extensively. In today’s high tech
society, absolute network security is difficult to achieve. With that in mind, tradeoffs
between security, mobility and productivity should be carefully evaluated for mobile users
of today’s networks.
The BayStack 600 Series product design and network management tools provide an
advanced set of progressive security features. These can be complemented by additional
security software and hardware products if required.
4401 Great America Parkway 8 Federal Street
Santa Clara, CA 95054 Billerica, MA 01821
Copyright © 1998 by Nortel Networks
All rights reserved.
Trademarks
BayStack, AirSurfer, and Netwave are all registered trademarks and the Nortel Networks logo is a trademark of
Nortel Networks
BayStack 600 Series Wireless LAN Security 8
 Loading...
Loading...