

ACCESS GATEWAY
Access Gateway
Copyright © 2015 Nomadix, Inc. All Rights Reserved.
This product also includes software developed by: The University of California,
Berkeley and its contributors; Carnegie Mellon University, Copyright © 1998 by
Carnegie Mellon University All Rights Reserved; Go Ahead Software, Inc., Copyright
© 1999 Go Ahead Software, Inc. All Rights Reserved; Livingston Enterprises, Inc.,
Copyright © 1992 Livingston Enterprises, Inc. All Rights Reserved; The Regents of the
University of Michigan and Merit Network, Inc., Copyright 1992 – 1995 All Rights
Reserved; and includes source code covered by the Mozilla Public License, Version 1.0
and OpenSSL.
This User Guide is protected by U.S. copyright laws. You may not transmit, copy,
modify, or translate this manual, or reduce it or any part of it to any machine readable
form, without the express permission of the copyright holder.

ACCESS GATEWAY
Trademarks
The symbol, and Nomadix Service Engine
®
are registered
trademarks of Nomadix, Inc. All other tradem arks and brand nam e s are marks of their
respective holders.
Product Information
Telephone: +1.818.597.1500
Fax: +1.818.597.1502
For technical support information, see the Appendix in this User Guide.
Patent Information
Please see the Nomadix website for a list of US and foreign patents covering this product
release.
Disclaimer
Nomadix, Inc. makes no warranty, either express or implied, including but not limited to any
implied warranties of merchantability and fitness for a particular purpose, regarding the
product described herein. In no event shall Nomadix, Inc. be liable to anyone for special,
collateral, incidental, or consequential damages in connection with or arising from the use of
Nomadix, Inc. products.
Write your product serial number in this box:

ACCESS GATEWAY
WARNING
Risk of electric shock; do not open; no user-serviceable
parts inside.
AVERTISSEMENT
Risque de choc electrique; ne pas ouvrir; ne pas tenter de
demontre l’appareil.
WARNUNG
Nicht öffnen; elektrische Bauteile.
AVISO
Riesgo de shock eléctrico. No abrir. No hay piezas
configurables dentro.
CAUTION
Read the instruction manual prior to operation.
ATTENTION
Lire le mode d’emploi avant utilisation.
ACHTUNG
Lesen Sie das Handbuch bevor Sie das Gerät in Betrieb
nehmen.
PRECAUCIÓN
Leer el manual de instrucciones antes de poner en
marcha el equipo.
30851 Agoura Rd, Suite 102, Agoura Hills, CA 91301 USA (head office)

ACCESS GATEWAY
v
Table of Contents
Chapter 1: Introduction .................................................................................................. 1
About this Guide....................................................................................................................... 1
Organization.............................................................................................................................. 2
Welcome to the Access Gateway.............................................................................................. 3
Product Configuration and Licensing ............................................................................... 3
Key Features and Benefits ............................................................................................. ........... 4
Platform Reliability............................................................................................................ 4
Local Content and Services ............................................................................................... 4
Transparent Connectivity .................................................. ................................................ 5
Billing Enablement ............ .......................................... ...................................................... 6
Access Control and Authentication.................................................................................... 6
Security .............................................................................................................................. 6
5-Step Service Branding .................................................................................................... 6
NSE Core Functionality............... ............................................................................................. 8
Access Control................................................................................................................... 9
Bandwidth Management .................................................................................................. 10
Billing Records Mirroring ............................................................................................... 10
Bridge Mode .................................................................................................................... 11
Class-Based Queueing..................................................................................................... 11
Command Line Interface ......................................................... ........................................ 14
Credit Card............................................................................................... ....................... 14
Dynamic Address Translation™.................................. .............................................. ...... 14
Dynamic Transparent Proxy............................................................................................ 14
End User Licensee Count ................................................................................................ 15
External Web Server Mode................. .......................................... ................................... 15
Facebook Authentication....................................................................... .......................... 15
iNAT™............................................................................................................................. 17
Information and Control Console.................................................................................... 18
Initial NSE Configuration................................................................................................ 18
Internal Web Server................. .................................................................................... .... 18
International Language Support...................................................................................... 19
IP Upsell......................................................................................................................... . 19
Load Balancing................................................................................................................ 20
Logout Pop-Up Window .................................................................................................. 20
MAC Filtering............................................................................. ..................................... 20
Multi-Level Administration Support................................................................................ 20
Multi-WAN Interface Management.................................................................................. 20
NTP Support .................................................. ........................................... ....................... 20
Portal Page Redirect ................................................... ........................................... ......... 21

ACCESS GATEWAY
vi
RADIUS-driven Auto Configuration................................................................................ 21
RADIUS Client................................................................................................................ . 22
RADIUS Proxy ............................................. .................................................................... 22
Realm-Based Routing....................................................................................................... 22
Remember Me and RADIUS Re-Authentication........................................ ....................... 23
Secure Management......................................................................................................... 23
Secure Socket Layer (SSL) ............................................................................................... 24
Secure XML API............................................................................................................... 24
Session Rate Limiting (SRL)............................................................................................. 25
Session Termination Redirect.................................. ......................................................... 25
Smart Client Support........................................................................................................ 25
SNMP Nomadix Private MIB........................................................................................... 25
Static Port Mapping ......................................................................................................... 25
Tri-Mode Authentication.................................................................................................. 25
URL Filtering.............................. .......................................... ........................................... 26
Walled Garden ................................................................................................................. 26
Web Management Interface ............................................................................................. 26
Weighted Fair Queueing.................................................................................................. 26
Optional NSE Modules............................................................................................................ 28
Load Balancing ................................................................................................................ 28
Hospitality Module........................................................................................................... 28
PMS Integration................................................................. .......................................... .... 29
High Availability Module................................................................................................. 29
Network Architecture (Sample) .............................................................................................. 30
Multiple Unit Clustering.......................................................................................................... 31
Identifying the Resident Gateway in a Cluster Environment........................................... 31
Load Balancing and Link Failover.......................................................................................... 33
Definitions and Concepts................................................................................................. 33
Load Balancing across Multiple Low Speed Links .......................................................... 36
Failover to Standby ISP Link........................................................................................... 36
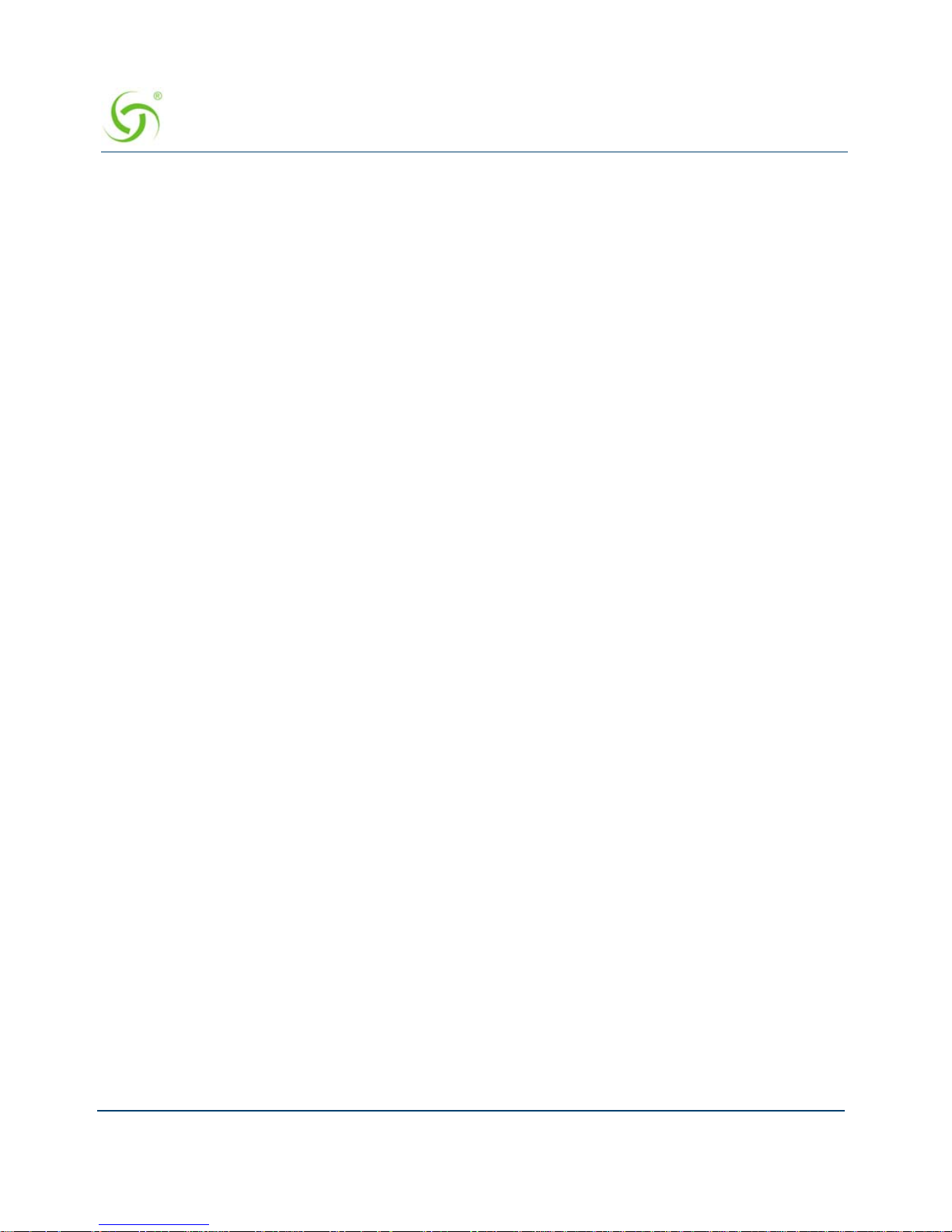
Separate Guest HSIA and Admin ISP Links, with Failover Between Each ISP Link ...... 37
Guest HSIA Failover Only, to Admin Network ............................................ .................... 38
Sharing Guest HSIA Network and Hotel Admin Network Among Multiple ISP Links .... 39
Load Balancing With Users Connected to a Preferred ISP Link..................................... 40
Online Help (WebHelp) .......................................................................................................... 42
Notes, Cautions, and Warnings............................................................................................... 42
Chapter 2: Installing the Access Gateway.................................................................... 43
Installation Workflow.............................................................................................................. 43
Powering Up the System......................................................................................................... 45
User Manual and Documentation............................................................................................ 45
Accessory Box Contents................................................................................................... 46

ACCESS GATEWAY
vii
Start Here ........................................... ..................................................................................... 46
Configuration.......................................................................................................................... 48
Step 1a: Static WAN IP Configuration............................................................................ 48
Step 1b: DHCP Client Configuration..................... .......................................... ............... 50
Step 1c: PPPoE Dynamic IP Client Configuration......................................................... 51
Step 1d: PPPoE Static IP Client Configuration.............................................................. 52
Step 2: Entering Your Location Information ........................................... ....................... 52
Step 3: Retrieving Your License Key .............................................................................. 53
Step 4: Configuring the System....................................................................................... 53
Step 5: Configuring AG DHCP Server Settings .............................................................. 54
The Management Interfaces (CLI and Web) .......................................................................... 55
Making Menu Selections and Inputting Data with the CLI ............................................. 56
Menu Organization (Web Management Interface).......................................................... 56
Inputting Data – Maximum Character Lengths............................................................... 58
Online Documentation and Help..................................................................................... 59
Quick Reference Guide........................................................................................................... 59
Establishing the Start Up Configuration................................................................................. 60
Assigning Login User Names and Passwords ................................................................. 61
Setting the SNMP Parameters (optional) .............................................. .......................... 62
Configuring the WAN interface ....................................................................................... 63
Enabling the Logging Options (recommended)............................................................... 64
Logging Out and Powering Down the System........................................................................ 67
Connecting the Access Gateway to the Customer’s Network ................................................ 67
Establishing the Basic Configuration for Subscribers ............................................................ 67
Setting the DHCP Options............................................................................................... 68
DHCP Options from RFC 2132....................................................................................... 69
DHCP Dynamic Enable and Disable .............................................................................. 72
Setting the DNS Options.................................................................................................. 73
Archiving Your Configuration Settings.................................................................................. 75
Installing the Nomadix Private MIB....................................................................................... 75
Chapter 3: System Administration............................................................................... 77
Choosing a Remote Connection.............................................................................................. 77
Using the Web Management Interface (WMI)................................................................. 78
Using an SNMP Manager................................................................................................ 79
Using a Telnet Client....................................................................................................... 79
Logging In............................ .......................................... .......................................... ............... 80
About Your Product License................................................................................................... 80
Configuration Menu................................................................................ ................................ 80
Defining the AAA Services {AAA} ................................................................................... 80
Establishing Secure Administration {Access Control}.................................................... 91
Defining Automatic Configuration Settings {Auto Configuration} ................................. 94
Setting Up Bandwidth Management {Bandwidth Management}..................................... 97

ACCESS GATEWAY
viii
Group Bandwidth Limit Policy ........................................................................................ 98
Group Bandwidth Limit Policy – Operation.................................................................... 99
Group Bandwidth Limit Policy – Enable ....................................................................... 100
Group Bandwidth Limit Policy – Current Table............................................................ 100
Establishing Billing Records “Mirroring” {Bill Record Mirroring} ............................ 101
Class-Based Queueing ................................................................................................... 102
Clustering {Clustering}.................................................................................................. 105
Configuring Destination HTTP Redirection {Destination HTTP Redirection}............. 106
Managing the DHCP service options {DHCP} ............................................................. 109
Enabling DNSSEC Support............................................................................................ 113
Managing the DNS Options {DNS}................................................................................ 114
Managing the Dynamic DNS Options {Dynamic DNS}................................................. 114
Ethernet Ports/WAN................................................ ....................................................... 116
Setting the Home Page Redirection Options {Home Page Redirect} ............................ 118
Enabling Intelligent Address Translation (iNAT™) ...................................................... 119
Defining IPSec Tunnel Settings {IPSec}........................................................................ 121
Load Balancing .............................................................................................................. 12 7
Establishing Your Location {Location} ......................................................................... 128
Managing the Log Options {Logging} ........................................................................... 129
Enabling MAC Authentication {MAC Authentication} .................................................. 134
Assigning Passthrough Addresses {Passthrough Addresses}........................................ 135
Assigning a PMS Service {PMS}.................................................................................... 136
Setting Up Port Locations {Port-Location}................................ ................................... 142
Setting up Quality of Service {QoS}............................................................................... 148
Defining the RADIUS Client Settings {RADIUS Client}................................................ 149
Defining the RADIUS Proxy Settings {RADIUS Proxy}................................................ 154
Defining the Realm-Based Routing Settings {Realm-Based Routing} ........................... 158
Managing SMTP Redirection {SMTP}..................................... ...................................... 166
Managing the SNMP Communities {SNMP} ................................................................. 167
Enabling Dynamic Multiple Subnet Support (Subnets).................................................. 168
Displaying Your Configuration Settings {Summary}..................................................... 169
Setting the System Date and Time {Time}...................................................................... 170
Setting up Traffic Descriptors........................................................................................ 172
Setting Up URL Filtering {URL Filtering}.................................................................... 173
Selecting User Agent Filtering Settings......................................................................... 174
Zone Migration............................................................................................................... 1 75
Defining IPSec Tunnel Settings...................................................................................... 177
Network Info Menu.............................. ................................................................................. 179
Displaying ARP Table Entries {ARP}............................................................................ 179
Displaying DAT Sessions {DAT} ................................................................................... 179
Displaying the Host Table {Hosts} ................................................................................ 180
Displaying ICMP Statistics {ICMP}.............................................................................. 181
Displaying the Network Interfaces {Interfaces}............................................................. 181
Interface Monitoring ...................................................................................................... 183

ACCESS GATEWAY
ix
Displaying the IP Statistics {IP}.................................................................................... 184
Viewing IPSec Tunnel Status {IPSec}............................................................................ 185
Viewing NAT IP Address Usage {NAT IP Usage}......................................................... 185
Displaying the Routing Tables {Routing}...................................................................... 186
Modifying the Routing Tables {Routing}....................................................................... 187
Displaying the Active IP Connections {Sockets}........................................................... 188
Displaying the Static Port Mapping Table {Static Port-Mapping}............................... 189
Displaying TCP Statistics {TCP}................................................................................... 190
Displaying UDP Statistics {UDP}................................................................................. 191
Port-Location Menu.............................................................................................................. 191
Adding and Updating Port-Location Assignments {Add} ............................................. 192
Exporting Port-Location Assignments {Export}............................................................ 195
Finding Port-Location Assignments by Description {Find by Description}................. 196
Finding Port-Location Assignments by Location {Find by Location} .. ........................ 197
Finding Port-Location Assignments by Port {Find by Port}......................................... 198
Importing Port-Location Assignments {Import}............................................................ 199
Displaying the Port-Location Mappings {List} ............................................................. 201
Deleting Port-Location Assignments............................................................................. 201
Enabling Facebook Login for a Port Location.............................................................. 201
Subscriber Intra-Port Communication.......................................................................... 202
Subscriber Administration Menu.......................................................................................... 203
Adding Subscriber Profiles {Add}................................................................................. 203
Displaying Current Subscriber Connections {Current}................................................ 209
Deleting Subscriber Profiles by MAC Address {Delete by MAC}................................. 210
Deleting Subscriber Profiles by User Name {Delete by User}...................................... 211
Displaying the Currently Allocated DHCP Leases {DHCP Leases} ............................ 212
Deleting All Expired Subscriber Profiles {Expired} ..................................................... 212
Finding Subscriber Profiles by MAC Address {Find by MAC}..................................... 213
Finding Subscriber Profiles by User Name {Find by User}.......................................... 214
Listing Subscriber Profiles {List Profiles} .................................................................... 214
Viewing RADIUS Proxy Accounting Logs {RADIUS Session History}......................... 216
Displaying Current Profiles and Connections {Statistics}............................................ 217
Subscriber Interface Menu.................................................................................................... 217
Defining the Billing Options {Billing Options} ............................................................. 217
Setting Up the Information and Control Console {ICC Setup} ..................................... 224
Defining Languages {Language Support}..................................................................... 231
Enable Serving of Local Web Pages {Local Web Server}............................................. 233
Defining the Subscriber’s Login UI {Login UI}............................................................ 235
Defining the Post Session User Interface (Post Session UI) ......................................... 239
Defining Subscriber UI Buttons {Subscriber Buttons}.................................................. 242
Defining Subscriber UI Labels {Subscriber Labels}..................................................... 243
Defining Subscriber Error Messages {Subscriber Errors}........................................... 245
Defining Subscriber Messages {Subscriber Messages} ................................................ 247

ACCESS GATEWAY
x
System Menu.................................................... .......................................... ........................... 250
Adding and Deleting ARP Table Entries........................................................................ 250
Configurable Gateway ARP Refresh Interval................................................................ 251
Enabling the Bridge Mode Option {Bridge Mode}........................................................ 251
Exporting Configuration Settings to the Archive File {Export}.............................. ....... 252
Importing the Factory Defaults {Factory}..................................................................... 253
Defining the Fail Over Options {Fail Over}.................................................................. 254
Viewing the History Log {History} ................................................................................ 255
Establishing ICMP Blocking Parameters {ICMP} ........................................................ 256
Importing Configuration Settings from the Archive File {Import} ................................ 257
Establishing Login Access Levels {Login}..................................................................... 258
Defining the MAC Filtering Options {MAC Filtering}.................................................. 261
Utilizing Packet Capturing {Packet Capture} ............................................................... 262
Rebooting the System {Reboot}...................................................................................... 264
Routing Tables {Routing}............................................................................................... 264
Establishing Session Rate Limiting {Session Limit} ...................................................... 266
Adding/Deleting Static Ports {Static Port-Mapping} .................................................... 267
Updating the Access Gateway Firmware {Upgrade} .................................................... 269
Chapter 4: The Subscriber Interface.......................................................................... 271
Overview ............................................................................................................................... 271
Authorization and Billing...................................................................................................... 272
The AAA Structure.......................................................................................................... 273
Process Flow (AAA)....................................................................................................... 276
Internal and External Web Servers................................................................................ 277
Language Support .......................................................................................................... 277
Home Page Redirection .............. .......................................... ......................................... 277
Subscriber Management........................................................................................................ 278
Subscriber Management Models.................................................................................... 278
Configuring the Subscriber Management Models ......................................................... 279
Information and Control Console (ICC)................................................................................ 280
ICC Pop-Up Window ......................................................... ............................................ 280
Logout Console .............................................................................................................. 281
Chapter 5: Quick Reference Guide............................................................................. 283
Web Management Interface (WMI) Menus.......................................................................... 283
Configuration Menu Items ............................................................................................. 284
Network Info Menu Items............................................................................................... 287
Port-Location Menu Items ............................................................................................. 289
Subscriber Administration Menu Items .......................................................................... 289
Subscriber Interface Menu Items ................................................................................... 291
System Menu Items................ ..................................................................................... .... 292

ACCESS GATEWAY
xi
Alphabetical Listing of Menu Items (WMI)......................................................................... 294
Default (Factory) Configuration Settings ............................................................................. 296
Product Specifications........................................................................................................... 298
Sample AAA Log................................. ... ........................................... ................................... 313
Message Definitions (AAA Log) .................................................................................... 313
Sample SYSLOG Report ......................................... ............................................................. 314
Sample History Log ......................................... ..................................................................... 315
Keyboard Shortcuts............................................................................................................... 316
HyperTerminal Settings........................................................................................................ 316
RADIUS Attributes............................................................................................................... 317
Authentication-Request.................................................................................................. 318
Authentication-Reply (Accept)....................................................................................... 318
Accounting-Request....................................................................................................... 319
Selected Detailed Descriptions...................................................................................... 320
Nomadix Vendor-Specific RADIUS Attributes .............................................................. 322
Setting Up the SSL Feature................................................................................................... 325
Prerequisites.................................................................................................................. 325
Obtain a Private Key File (cakey.pem) ......................................................................... 325
Installing Cygwin and OpenSSL on a PC............ .......................................................... 326
Private Key Generation ................................................................................................. 329
Create a Certificate Signing Request (CSR) File .......................................................... 332
Create a Public Key File (server.pem).......................................................................... 333
Setting Up Access Gateway for SSL Secure Login ........................................................ 336
Setting Up the Portal Page............................................................................................ 337
Mirroring Billing Records..................................................................................................... 338
Sending Billing Records................................................................................................. 338
XML Interface................................................................................................................ 339
Chapter 6: Troubleshooting........................................................................................ 343
General Hints and Tips ......................................................................................................... 343
Management Interface Error Messages................................................................................. 344
Common Problems................................................................................................................ 346
Appendix A: Technical Support................................................................................. 349
Contact Information.............................................................................................................. 349
Appendix B: Glossary of Terms.................................................................................. 351
ACCESS GATEWAY
xii

ACCESS GATEWAY
1
Introduction 1
Introduction
About this Guide
This User Guide provides information and procedures that will enable system administrators to
install, configure, manage, and use the Access Gateway product successfully and efficiently.
Use this guide to take full advantage of the Access Gateway’s functionality and features.
Refer to “Product Specifications” on page 298 for a list of Access Gateway Products that this
document supports.
The Nomadix Access Gateway hardware is configured and controlled by Nomadix Service
Engine (NSE) software. The NSE 7.4 is the last Software Release that supports the AG2300,
AG3100, and AG5500.
NSE 8.5 series software releases support the AG2400, AG5600, AG5800 and AG5900.

ACCESS GATEWAY
2 Introduction
Organization
This User Guide is organized into the following sections:
Chapter 1 – Introduction. The current chapter; an introduction to the features and benefits of
the Nomadix Access Gateway.
Chapter 2 – Installing the Access Gateway. Provides instructions for installing the Access
Gateway and establishing the start-up configuration.
Chapter 3– System Administration. Provides all the instructions and procedures necessary to
manage and administer the Access Ga teway on the customer’ s network, following a successful
installation.
Chapter 4– The Subscriber Interface. Provides an overview and sample scenario for the
Access Gateway’s subscriber interface. It also includes an outline of the authorization and
billing processes utilized by the system, and the Nomadix Information and Control Console.
Chapter 5 – Quick Reference Guide. Contains product reference information, organized by
topic and functionality. It also contains a full listing of all product configuration elements,
sorted alphabetically and by menu.
Chapter 6 – Troubleshooting. Provides information to help you resolve common hardware and
software problems. It also contains a list of error messages associated with the management
interface.
Technical Support. Informs you how to obtain technical support. Refer to Troubleshooting
before contacting Nomadix, Inc. directly.
Glossary of Terms. Provides an explanation of terms directly related to Nomadix product
technology. Glossary entries are organized alphabetically.

ACCESS GATEWAY
Introduction 3
Welcome to the Access Gateway
The Access Gateway is a freestanding, fully featured network appliance that enables public
access service providers to offer broadband Internet connectivity to their customers.
The Access Gateway handles transparent connectivity, advanced security, policy-based traffic
shaping, and service placement supporting thousands of users simultaneously in a broadband
environment. The Access Gateway also offers a unique set of security and connectivity
features for deploying metro wireless 802.11 networks, including Mesh and WiMAX
technologies.
The Access Gateway yields a complete solution to a set of complex issues in the Enterprise,
Public-LAN, and Residential segments.
Product Configuration and Licensing
All Nomadix Access Gateway products are powered by our patented and patent-pending suite
of embedded software, called the Nomadix Service Engine™ (NSE). The Access Gateway
employs our NSE core software package and comes pre-packaged with the option to purchase
additional modules to expand the product’s functionality.
This User Guide covers all features and functionality provided with the NSE core package, as
well as additional optional modules. Your product license must support the optional NSE
modules if you want to take advantage of the expanded functionality. The following note will
preface procedures that directly relate to optional modules.
See also:
NSE Core Functionality
Optional NSE Modules
Access Gateway

ACCESS GATEWAY
4 Introduction
Key Features and Benefits
The Access Gateway is a 1U high, free-standing or rack-mountable device that provides
Ethernet ports to interface with the router and the aggregation equipment within the network. It
also incorporates an RS232 serial port for connecting to a Property Management System
(PMS) and for system management and administration, while maintaining one bil ling
relationship with their chosen provider.
The Access Gateway enables a wide variety of network deployment options for different venue
types. For example:
Allows for flexible WAN Connectivity (T1/E1, Cable, xDSL, and ISDN).
Supports 802.11a/b/g and hybrid networks utilizing wired Ethernet.
Supports key requirements needed to be compliant with the Wi-Fi ZONE™ program.
Allows you to segment your existing network into public and private sections using
VLANs, then leverage your existing network investment to create new revenue
streams.
Enables you to provide Wi-Fi access as a billable service or as an amenity to augment
the main line of business for your venue.
Contains an advanced XML interface for accepting and processing XML commands,
allowing the implementation of a variety of service plans and offerings.
Offers three user-friendly ways of remote management—through a Web interface,
SNMP MIBs, and Telnet interfaces—allowing for scalable, large public access
deployments.
Provides capabilities for load balancing and fail-over management across m ulti ple
ISPs.
Platform Reliability
The Access Gateway is designed as a network appliance, providing maximum uptime and
reliability unlike competitive offerings that use a server-based platform.
Local Content and Services
The Access Gateway’s Portal Page feature intercepts the user’s browser settings and directs
them to a designated Web site to securely sign up for service or log in if they have a preexisting account.
Allows the provider to present their customers with local services or have the user
sign up for service at zero expense.

ACCESS GATEWAY
Introduction 5
Offers both pre and post authentication redirects of the user’s browser, providing
maximum flexibility in service branding .
Transparent Connectivity
Resolving configuration conflicts is difficult and time consuming for network users who are
constantly on the move, and costly to the solution provider. In fact, most users are reluctant to
make changes to their computer’s network settings and won’t even bother. This fact alone has
prevented the widespread deployment of broadband network services.
Our patented Dynamic Address Translation™ (DAT) functionality offers a true “plug and
play” solution by enabling a seamless and transparent experience and the tools to acquire new
customers on-site.
DAT greatly reduces provisioning and technical support costs and enables providers to deliver
an easy to use, customer-friendly service.

ACCESS GATEWAY
6 Introduction
Billing Enablement
The Access Gateway supports billing plans using credit cards, scratch cards, or monthly
subscriptions, or direct billing to a hotel’s Property Management System (PMS) and can base
the billable event on a number of different parameters such as time, volume, IP address type, or
bandwidth.
Access Control and Authentication
The Access Gateway ensures that all traffic to the Internet is blocked until authentication has
been completed, creating an additional level of security in the network. Also, the Access
Gateway allows service providers to create their own unique “walled garden,” enabling users
to access only certain predetermined Web sites before they have been authenticated.
Nomadix simultaneously supports the secure browser-based Universal Access Method (UAM),
IEEE 802.1x, and Smart Clients for companies such as Adjungo Networks, Boingo Wireless,
GRIC and iPass. MAC-based authentication is also available.
Security
The patented iNAT™ (Intelligent Network Address Translation) feature creates an intelligent
mapping of IP Addresses and their associated VPN tunnels—by far the most reliable multisession VPN passthrough to be tested against diverse VPN termination servers from companies
such as Cisco, Checkpoint, Nortel and Microsoft. Nomadix’ iNAT feature allows multiple
tunnels to be established to the same VPN server, creating a seamless connection for all users
on the network.
The Access Gateway provides fine-grain management of DoS (Denial of Service) attacks
through its Session Rate Limiting (SRL) feature, and MAC filtering for improved network
reliability.
5-Step Service Branding
A network enabled with the Nomadix Access Gateway offers a 5-Step service branding
methodology for service providers and their partners, comprising:
1. Initial Flash Page branding.
2. Initial Portal Page Redirect (Pre-Authentication). T ypically, this is used to redirect the user
to a venue-specific Welcome and Login page.
3. Home Page Redirect (Post-Authentication). This redirect page can be tailored to the
individual user (as part of the RADIUS Reply message, the URL is received by the NSE)
or set to re-display itself at freely configurable intervals.

ACCESS GATEWAY
Introduction 7
4. The Information and Control Console (ICC) contains multiple opportunities for an
operator to display its branding or the branding of partners during the user’s session. As an
alternative to the ICC, a simple pop-up window provides the opportunity to display a
single logo.
5. The “Goodbye” page is a post-session page that can be defined either as a RADIUS VSA
or be driven by the Internal Web Server (IWS) in the NSE. Using the IWS option means
that this functionality is also available for other post-paid billing mechanisms (for
example, post-paid PMS).

ACCESS GATEWAY
8 Introduction
NSE Core Functionality
Powering Nomadix’ family of Access Gateways, the Nomadix Service Engine (NSE) delivers
a full range of features needed to successfully deploy public access networks. These “core”
features solve issues of connectivity, security, billing, and roaming in a Wi-Fi public access
network.
The NSE’s core package of features includes:
Access Control
Bandwidth Management
Billing Records Mirroring
Bridge Mode
Class-Based Queueing
Command Line Interface
Credit Card
Dynamic Address Translation™
Dynamic Transparent Proxy
End User Licensee Count
External Web Server Mode
Facebook Authentication
“Adding and Updating Port-Location Assignments {Add}” on page 192Home Page
Redirect
iNAT™
Information and Control Console
Internal Web Server
International Language Support
IP Upsell
Logout Pop-Up Window
MAC Filtering
Multi-Level Administration Support
Multi-WAN Interface Management
NTP Support

ACCESS GATEWAY
Introduction 9
Portal Page Redirect
RADIUS Client
RADIUS-driven Auto Configuration
RADIUS Proxy
Realm-Based Routing
Remember Me and RADIUS Re-Authentication
Secure Management
Secure Socket Layer (SSL)
Secure XML API
Session Rate Limiting (SRL)
Session Termination Redirect
Smart Client Support
SNMP Nomadix Private MIB
Static Port Mapping
Tri-Mode Authentication
URL Filtering
Walled Garden
Web Management Interface
Weighted Fair Queueing
Access Control
For IP-based access control, the NSE incorporates a master access control list that checks the
source (IP address) of administrator logins. A login is permitted only if a match is made with
the master list contained within the NSE. If a match is not made, the login is denied, even if a
correct login name and password are supplied.
The access control list supports up to 50 (fifty) entries in the form of a specific IP address or
range of IP addresses.
The NSE also offers access control based on the interface being used. This feature allows
administrators to block access from Telnet, Web Management, and FTP sources.

ACCESS GATEWAY
10 Introduction
Administration can now be performed after unblocking the interfaces for the Subscriber side of
the NSE. The Administrative ports are configurable as well. See “Establishing Secure
Administration {Access Control}” on page 91.
Bandwidth Management
The NSE optimizes bandwidth by limiting bandwidth usage symmetrically or asymmetrically
on a per device (MAC address / User) basis, and manages the WAN Link traffic to provide
complete bandwidth management over the entire network. You can ensure that every user has a
quality experience by placing a bandwidth ceiling on each device accessing the network, so
every user gets a fair share of the available bandwidth.
With the Nomadix ICC feature enabled, subscribers can increase or decrease their own
bandwidth and pricing plans for their service dynamically.
Billing Records Mirroring
NSE-powered devices can send copies of credit card billing records (and optional ly, PMS) to
external servers that have been previously defined by system administrators. The NSE assumes
control of billing transmissions and the saving of billing records. By effectively “mirroring”
the billing data, the NSE can send copies of billing records to predefined “carbon copy”
servers. Additionally, if the primary and secondary servers are not responding, the NSE can
store up to 2,000 billing records. The NSE regularly attempts to connect with the primary and
secondary severs. When a connection is re-established (with either server), the NSE sends the
cached information to the server. Customers can be confident that their billing information is
secure and that no transaction records are lost.
Information and Control Console (ICC)
Bandwidth selection (pull down)

ACCESS GATEWAY
Introduction 11
Bridge Mode
This feature allows complete and unconditional access to devices. When Bridge Mode is
enabled, your NSE-powered product is effectively transparent to the network in which it is
located.
The NSE forwards any and all packets (except those addressed to the NSE network interface).
The packets are unmodified and can be forwarded in both directions. The Bridge Mode
function is a very useful feature when troubleshooting your entire network as it allows
administrators to effectively “remove” your product from the network without physically
disconnecting the unit.
Class-Based Queueing
The Nomadix Class-Based Queueing feature provides the ability to define multiple groups
(classes) of users. You can prioritized groups and guarantee minimum bandwidth on a pergroup basis.
Users are added to classes, and rules are applied across the entire class. Each class has three
configurable attributes:
Priority
Minimum Bandwidth
Maximum Bandwidth
Class-based queueing does not apply rules to individual users. You may use bandwidth limits
to restrict individual users, if desired.
Class-based queueing does not provide application-level (layer 7) throttling or class of service.
Rules are applied when there is contention for bandwidth (i.e. when link is saturated).
In NSE 8.5, Class Based Queueing and Weighted Fair Queueing are mutually
exclusive. Weighted Fair Queueing is enabled by default.

ACCESS GATEWAY
12 Introduction
Use Case: Property has 100 Mbps WAN Link
In this scenario, a property wishes to provide guaranteed minimum bandwidth and prioritize
traffic across three groups: Conference, Guest Room, Public Areas. The property can configure
class-based queuing according to the following table.
The sum of minimums across all classes should not exceed the total available bandwidth.
It is generally recommended to set the Maximum to equal the total available bandwidth across
all classes. This allows all classes to take advantage of the full bandwidth when there is no
contention.
With the above configuration, each of the three classes may utilize the entire available
bandwidth when there is no contention. But whenever contention occurs, bandwidth will be
allocated according to priority and minimum guarantee.
For example, if there are no users in the Conference Class, then the Guest Room and Public
Classes can use 100% of the bandwidth. If there is contention between the two, then the Guest
Room class will be allocated up to 80Mbps (because it has a higher priority), with 20Mbps
taken by the Public class (its minimum guarantee). If, however, there were no users in the
Public class, then the Guest Room class could take 100% of the bandwidth (100Mbps).
If users are introduced into the Conference class (Priority 1), and this creates contention, then
they will take bandwidth away from each of the other two classes until each reaches its
minimum.
Example Illustration of Class-Based Queueing
The following diagram demonstrates the effect of Class Based Queueing with a saturated link
of 200Mbps, and three classes defined with minimum guarantees of 100Mbps (Meeting
Room), 60Mpbs (VIP Guests), and 40Mbps (Lobby).
Note the following over time:
Class Priority Minimum Maximum
User Bandwidth
Limit**
Conference 1 30 Mbps 100 Mbps 5 Mbps
Guest Room 2 50 Mbps 100 Mbps 5 Mbps
Public 3 20 Mbps 100 Mbps 3 Mbps
User Bandwidth Limit is not an attribute of Class Based Queueing, but can be
applied (if desired) using existing Bandwidth Limit functionality.

ACCESS GATEWAY
Introduction 13
When only Lobby class subscribers are on the network, all available bandwidth is
allocated to Lobby class subscribers.
As VIP Guests join the network, bandwidth is allocated from Lobby class to VIP
Guests, until the Lobby bandwidth drops to its minimum guarantee of 40Mbps.
As Meeting Room subscribers join the network, the Lobby bandwidth is already at its
minimum guarantee. Bandwidth is allocated from VIP Guests to Meeting Room
subscribers, until bandwidth for VIP Guests reaches the minimum guarantee of
60Mbps and Meeting Room reaches its minimum guarantee of 100Mbps.
Notes and Cautions
Exercise caution in mixing subscribers with and without class membership. Subscribers with
no class membership are automatically assigned a priority of eight the lowest priority and have
no minimum bandwidth.
If higher priority classes are not assigned a maximum bandwidth cap, it is possible that
unassigned subscribers will be completely starved fo r ban dwidth.

ACCESS GATEWAY
14 Introduction
In a mixed user environment, care should be taken to ensure top priority classes have sensible
maximum thresholds. To take advantage of the class bandwidth queuing one should assign
subscribers to a minimum bandwidth and specific class.
See also “Class-Based Queueing” on page 102.
Command Line Interface
The Command Line Interface (CLI) is a character-based user interface that can be accessed
remotely or via a direct cable connection. Until your Nomadix product is up and running on the
network, the CLI is the Network Administrator’s window to the system. Software upgrades can
only be performed from the CLI.
See also “The Management Interfaces (CLI and Web)” on page 55.
Credit Card
The Credit Card provides a secure interface over SSL to enable billing via a credit card for
High Speed Internet Access (HSIA). This module also includes the Bill Mirror functionality
for posting of billing records to multiple sources.
See also:
“Secure Socket Layer (SSL)” on page 24.
“Billing Records Mirroring” on page 10.
Dynamic Address Translation™
Dynamic Address Translation (DAT) enables transparent broadband network connectivity,
covering all types of IP configurations (static IP, DHCP, DNS), regardless of the platform or
the operating system used—ensuring that everyone gets access to the network without the need
for changes to their computer’s configuration settings or client-side software. The NSE
supports both PPTP and IPSec VPNs in a manner that is transparent to the user and that
provides a more secure standard connection. See also, “Transparent Connectivity” on page 5.
Dynamic Transparent Proxy
The NSE directs all HTTP and HTTPS proxy requests through an internal proxy which is
transparent to subscribers (no need for users to perform any reconfiguration tasks). Uniquely,
the NSE also supports clients that dynamically change their browser status from non-proxy to
proxy, or vice versa. In addition, the NSE supports proxy ports 80, 800-900, 911 and 990 as
well as all unassigned ports (for example, ports above 1024), thus ensuring far fewer proxy
related support calls than competitive products.

ACCESS GATEWAY
Introduction 15
End User Licensee Count
The NSE supports a range of simultaneous user counts depending on the Nomadix Access
Gateway you choose. In addition, depending on your platform, various user count upgrades are
available for each of our NSE-powered products that allow you to increase the simultaneous
user count.
External Web Server Mode
The External Web Server (EWS) interface is for customers who want to develop and use their
own content. It allows you to create a “richer” environment than is possible with your
product’s embedded Internal Web Server.
The advantages of using an External Web Server are:
Manage frequently changing content from one location.
Serve different pages depending on site, sub-location (for example, VLAN), and user.
Take advantage of the comprehensive Nomadix XML API to implement more
complex billing plans.
Recycle existing Web page content for the centrally hosted portal page.
If you choose to use the EWS interface, Nomadix Technical Support can provide you with
sample scripts. See also, “Contact Information” on page 349.
Facebook Authentication
NSE 8.5 provides the option of Facebook authentication for facility guests. Login with
Facebook is a 2-step process. A user must first click the New User button on the Nomadix
splash screen:

ACCESS GATEWAY
16 Introduction
Then the user must click the “Log in with Facebook” button:
Several configuration steps are required to support Facebook authentication. See the following
sections for specific instructions:
“Defining the AAA Services {AAA}” on page 80
“Assigning Passthrough Addresses {Passthrough Addresses}” on page 135
“Defining the Billing Options {Billing Options}” on page 217
“Adding and Updating Port-Location Assignments {Add}” on page 192Home Page
Redirect

ACCESS GATEWAY
Introduction 17
The NSE supports a comprehensive HTTP redirect logic that allows network administrators to
define multiple instances to intercept the browser’s request and replace it with freely
configurable URLs.
Portal page redirect enables redirection to a portal page
before the authentication process. This
means that anyone will get redirected to a Web page to establish an account, select a service
plan, and pay for access. Home Page redirect enables redirection to a page
after the
authentication process (for example, to welcome a specific user to the service—after the user
has been identified by the authentication process. See also, “Portal Page Redirect” on page 21.
iNAT™
Nomadix invented a new way of intelligently supporting multiple VPN connecti ons to the
same termination at the same time (iNAT™), thus solving a key problem of many public
access networks.
Nomadix’ patented iNAT™ (intelligent Network Address Translation) feature contains an
advanced, real-time translation engine that analyzes all data packets being communicated
between the private address realm and the public address realm.
The NSE performs a defined mode of network address translation based on packet type and
protocol (for example, ISAKMP, etc.). UDP packet fragmentation is supported to provide more
seamless translation engine for certificate-based VPN connections.
If address translation is needed to ensure the success of a specific application (for example,
multiple users trying to access the same VPN termination server at the same time), the packet
engine selects an IP address from a freely definable pool of publicly routable IP addresses. The
same public IP address can be used as a source IP to support concurrent tunnels to different
termination devices—offering unmatched efficiency in the utilization of costly public IP
addresses. If the protocol type can be supported without the use of a public IP (for example,
HTTP, FTP), our proven Dynamic Address Translation™ functionality continues to be used.
Some of the benefits of iNAT™ include:
Improves the success rate of VPN connectivity by misconfigured users, thus reducing
customer support costs and boosting customer satisfaction.
Maintains the security benefits of traditional address translation technologies while
enabling secure VPN connections for mobile workers accessing corporate resources
from a public access location.
Dynamically adjusts the mode of address translation during the user's session,
depending on the packet type.
Supports users with static private IP addresses (for example, 192.168.x.x) or public
(different subnet) IP addresses without any changes to the client IP settings.
Dramatically heightens the reusability factor of costly public IP addresses.

ACCESS GATEWAY
18 Introduction
Information and Control Console
The Nomadix ICC is a HTML-based pop-up window that is presented to subscribers with their
Web browser. The ICC allows subscribers to select their bandwidth and billing options quickly
and efficiently from a simple pull-down menu. For credit card accounts, the ICC displays a
dynamic “time” field to inform subscribers of the time remaining on their account.
Additionally, the ICC contains multiple opportunities for an operator to display its branding or
the branding of partners during the user’s session, as well as display advertising banners and
present a choice of redirection options to their subscribers.
See also:
5-Step Service Branding
Logout Pop-Up Window
Information and Control Console
Initial NSE Configuration
See “Installing the Access Gateway” on page 43 for initial installation and configuration
instructions.
Internal Web Server
The NSE offers an embedded Internal Web Server (IWS) to deliver Web pages stored in flash
memory. These Web pages are configurable by the system administrator by selecting various
parameters to be displayed on the internal pages. When providers or HotSpot owners do no t
want to develop their own content, the IWS is the answer. A banner at the top of each IWS
page is configurable and contains the customer's company logo or any other image file they
desire.
To support PDAs and other hand-held devices, the NSE automatically formats the IWS pages
to a screen size that is optimal for the particular device being used.
Information and Control Console (ICC)

ACCESS GATEWAY
Introduction 19
See also:
5-Step Service Branding.
International Language Support.
International Language Support
The NSE allows you to define the text displayed to your users by the IWS without any HTML
or ASP knowledge. The language you select determines the language encoding that the IWS
instructs the browser to use. See also, “Internal Web Server” on page 18.
You can change the language of the Web Management Interface text. See “Selecting the
language of the Web Management Interface” on page 78.
The available language options are:
English
Chinese (Big 5)
French
German
Japanese (Shift_JIS)
Spanish
Other, with drop-down menu
IP Upsell
System administrators can set two different DHCP pools for the same physical LAN. When
DHCP subscribers select a service plan with a public pool address, the NSE associates their
MAC address with their public IP address for the duration of the service level agreement. The
opposite is true if they select a plan with a private pool address. This feature enables a
competitive solution and is an instant revenue generator for ISPs.
The IP Upsell feature solves a number of connectivity problems, especially with regard to
certain video conferencing and online gaming applications.
You have additional flexibility for configuring up sell scenarios. Users can be assigned WAN’s
of different bandwidth capabilities; for example, hotel guests with loyalty memberships can
qualify for premium services.

ACCESS GATEWAY
20 Introduction
Load Balancing
Load balancing is available as an optional module. See “Load Balancing and Link Failover” on
page 33 for a more complete description and typical use cases.
Logout Pop-Up Window
As an alternative to the ICC, the NSE delivers a HTML-based pop-up window with the
following functions:
Provides the opportunity to display a single logo.
Displays the session’s elapsed/count-down time.
Presents an explicit Logout button.
See also, “Information and Control Console” on page 18.
MAC Filtering
MAC Filtering enhances Nomadix' access control technology by allowing system
administrators to block malicious users based on their MAC address. Up to 50 MAC addresses
can be blocked at any one time. See also, “Session Rate Limiting (SRL)” on page 25.
Multi-Level Administration Support
The NSE allows you to define 2 concurrent access levels to differentiate between managers and
operators, where managers are permitted read/write access and operators are restricted to read
access only.
Once the logins have been assigned, managers have the ability to perform all write commands
(Submit, Reset, Reboot, Add, Delete, etc.), but operators cannot change any system settings.
When Administration Concurrency is enabled, one manager and three operators can access the
Access Gateway platform at any one time.
Multi-WAN Interface Management
The NSE supports multiple independently configurable WAN interfaces, to optimize ISP
resource allocation, and provide load balancing (optional), fail-o ver and upsell capabilities.
NTP Support
The NSE supports Network Time Protocol (NTP), an Internet standard protocol that assures
accurate synchronization (to the millisecond) of computer clock times in a network of
computers. NTP synchronizes the client’s clock to the U.S. Naval Observatory master clocks.

ACCESS GATEWAY
Introduction 21
Running as a continuous background client program on a computer, NTP sends periodic time
requests to servers, obtaining server time stamps and using them to ad just the client's clock.
Portal Page Redirect
The NSE contains a comprehensive HTTP page redirection logic that allows for a page redirect
before (Portal Page Redirect) and/or after the authentication process (Home Page Redirect).
As part of the Portal Page Redirect feature, the NSE can send a defined set of parameters to the
portal page redirection logic that allows an External Web Server to perform a redirection based
on:
Access Gateway ID and IP Address
Origin Server
Port Location
Subscriber MAC address
Externally hosted RADIUS login failure page
This means that the network administrator can now perform location-specific service branding
(for example, an airport lounge) from a centralized Web server.
See also, ““Adding and Updating Port-Location Assignments {Add}” on page 192Home Page
Redirect” on page 16.
RADIUS-driven Auto Configuration
Nomadix’ unique RADIUS-driven Auto Configuration functionality utilizes the existing
infrastructure of a mobile operator to provide an effortless and rapid method for configuring
devices for fast network roll-outs. Once configured, this methodology can also be effectively
used to centrally manage configuration profiles for all Nomadix devices in the public access
network.
Two subsequent events drive the automatic configuratio n of Nomadix devices:
1. A flow of RADIUS Authentication Request and Reply messages between the Nomadix
gateway and the centralized RADIUS server that specifies the location of the meta
configuration file (containing a listing of the individual configuration files and their
download frequency status) are downloaded from an FTP server into the flash of the
Nomadix device.
2. Defines the automated login into the centralized FTP server and the actual download
process into the flash.
Optionally, the RADIUS authentication process and FTP download can be secured by sending
the traffic through a peer-to-peer IPSec tunnel established by the Nomadix gateway and

ACCESS GATEWAY
22 Introduction
terminated at the NOC (Network Operations Center). See also, “Secure Management” on
page 23.
The NSE provides a Radius VSA that supports assigning specific users to specific WAN
interface. See “Defining Automatic Configuration Settings {Auto Configuration}” on page 94.
RADIUS Client
Nomadix offers an integrated RADIUS (Remote Authentication Dial-In User Service) client
with the NSE allowing service providers to track or bill users based on the number of
connections, location of the connection, bytes sent and received, connect time, etc. The
customer database can exist in a central RADIUS server, along with associated attributes for
each user. When a customer connects into the network, the RADIUS client authenticates the
customer with the RADIUS server, applies associated attributes stored in that customer's
profile, and logs their activity (including bytes transferred, connect time, etc.). The NSE's
RADIUS implementation also handles vendor specific attributes (VSAs), required by WISPs
that want to enable more advanced services and billing schemes, such as a per device/per
month connectivity fee. See also, “RADIUS Proxy” on page 22.
RADIUS Proxy
The RADIUS Proxy feature relays authentication and accounting packets between the parties
performing the authentication process. Different realms can be set up to directly channel
RADIUS messages to the various RADIUS servers. This functionality can be ef fectively
deployed to:
Support a wholesale WISP model directly from the edge without the need for any
centralized AAA proxy infrastructure.
Support EAP authenticators (for example, WLAN APs) on the subscriber-side of the
NSE to transparently proxy all EAP types (TLS, SIM, etc.) and to allow for the
distribution of per-session keys to EAP authenticators and supplicants.
Complementing the RADIUS Proxy functionality is the ability to route RADIU S m essages
depending on the Network Access Identifier (NAI). Both prefix-based (for example, ISP/
username@ISP.net) and suffix-based (username@ISP.net) NAI routing mechanisms are
supported. Together, the RADIUS Proxy and Realm-Based Routing further support the
deployment of the Wholesale Wi-Fi™ model allowing multiple providers to service one
location. See also, “RADIUS Client” on page 22.
Realm-Based Routing
Realm-Based Routing provides advanced NAI (Network Access Identifier) routing
capabilities, enabling multiple service providers to share a HotSpot location, further supporting

ACCESS GATEWAY
Introduction 23
a Wi-Fi wholesale model. This functionality allows users to interact only with their chosen
provider in a seamless and transparent manner.
Remember Me and RADIUS Re-Authentication
The NSE’s Internal Web Server (IWS) stores encrypted login cookies in the browser to
remember logins, using usernames and passwords. This “Remember Me” functionality creates
a more efficient and better user experience in wireless networks.
The RADIUS Re-Authentication buffer has been expanded to 720 hours, allowing an even
more seamless and transparent connection experience for repeat users.
Secure Management
There are many different ways to configure, manage and monitor the performance and up-time
of network devices. SNMP, Telnet, HTTP and ICMP are all common protocols to accomplish
network management objectives. And within those objectives is the requirement to provide the
highest level of security possible.
While several network protocols have evolved that offer some level of security and data
encryption, the preferred method for attaining maximum security across all network devices is
to establish an IPSec tunnel between the NOC (Network Operations Center) and the edge
device (early VPN protocols such as PPTP have been widely discredited as a secure tunneling
method).
As part of Nomadix’ commitment to provide outstanding carrier-class network management
capabilities to its family of public access gateways, we offer secure management through the
NSE’ s standards-driven, peer-to-peer IPSec tunneling with strong data encryption.
Establishing the IPSec tunnel not only allows for the secure management of the Nomadix
gateway using any preferred management protocol, but also the secure mana gement of third
party devices (for example, WLAN Access Points and 802.3 switches) on private subnets on
the subscriber side of the Nomadix gateway . See also, “Defining IPSec Tunnel Settings” on
page 177.
T wo subsequent events drive the secure management function of the Nomadix gateway and the
devices behind it:
1. Establishing an IPSec tunnel to a centralized IPSec termination server (for example,
Nortel Contivity). As part of the session establishment process, key tunnel parameters are
exchanged (for example, Hash Algorithm, Security Association Lifetimes, etc.).
2. The exchange of management traffic, either originating at the NOC or from the edge
device through the IPSec tunnel. Alternatively, AAA data such as RADIUS
Authentication and Accounting traffic can be sent through the IPSec tunnel. See also,
“RADIUS-driven Auto Configuration” on page 21.

ACCESS GATEWAY
24 Introduction
The advantage of using IPSec is that all types of management traffic are supported, including
the following typical examples:
ICMP - PING from NOC to edge devices
Telnet - Telnet from NOC to edge devices
Web Management - HTTP access from NOC to edge devices
SNMP
SNMP GET from NOC to subscriber-side device (for example, AP)
SNMP SET from NOC to subscriber-side device (for example, AP)
SNMP Trap from subscriber-side device (for example, AP) to NOC
Secure Socket Layer (SSL)
This feature allows for the creation of an end-to-end encrypted link between your NSEpowered product and wireless clients by enabling the Internal Web Server (IWS) to display
pages under a secure link—important when transmitting AAA information in a wireless
network when using RADIUS.
SSL requires service providers to obtain digital certificates to create HTTPS pages.
Instructions for obtaining certificates are provided by Nomadix.
Secure XML API
XML (Extensible Markup Language) is used by the subscriber management module for user
administration. The XML interface allows the NSE to accept and process XML commands
from an external source. XML commands are sent over the netw ork to your NSE-powered
product which executes the commands, and returns data to the system that initiated the
command request. XML enables solution providers to customize and enhance their product
installations.
This feature allows the operator to use Nomadix' popular XML API using the built-in SSL
certificate functionality in the NSE so that parameters passed between the Gateway and the
centralized Web server are secured via SSL.
If you plan to implement XML for external billing, please contact technical
support for the XML specification of your product. Refer to “Contact
Information” on page 349.

ACCESS GATEWAY
Introduction 25
Session Rate Limiting (SRL)
Session Rate Limiting (SRL) significantly reduces the risk of “Denial of Service” attacks by
allowing administrators to limit the number sessions any one user can take over a given time
period and, if necessary, then block malicious users.
Session Termination Redirect
Once connected to the public access network, the NSE will automatically redirect the customer
to a Web site for local or personalized services if the customer logs out or the customer’s
account expires while online and the goodbye page is enabled. In addition, the NSE also
provides pre- and post-authentication redirects as well as one at session termination.
Smart Client Support
The NSE supports authentication mechanisms used by Smart Clients by companies such as
Adjungo Networks, Boingo Wireless, GRIC and iPass.
SNMP Nomadix Private MIB
Nomadix’ Access Gateways can be easily managed over the Internet with an SNMP client
manager (for example, HP OpenView or Castle Rock). See Using an SNMP Manager.
To take advantage of the functionality provided with Nomadix ’ pri vate MIB (Management
Information Base), to view and manage SNMP objects on your product , see Installing the
Nomadix Private MIB.
Static Port Mapping
This feature allows the network administrator to setup a port mapping scheme that forwards
packets received on a specific port to a particular static IP (typically private and
misconfigured) and port number on the subscriber side of the NSE. The advantage for the
network administrator is that free private IP addresses can be used to manage devices (such as
Access Points) on the subscriber side of the NSE without setting them up with Public IP
addresses.
Tri-Mode Authentication
The NSE enables multiple authentication models providing the maximum amount of flexibility
to the end user and to the operator by supporting any type of client entering their network and
any type of business relationship on the back end. For example, in addition to supporting the
secure browser-based Universal Access Method (UAM) via SSL, Nomadix is the only

ACCESS GATEWAY
26 Introduction
company to simultaneously support port-b ased authentication using IEEE 802.1x and
authentication mechanisms used by Smart Clients. MAC-based authentication is also available.
See also:
Access Control and Authentication
Smart Client Support
URL Filtering
The NSE can restrict access to specified Web sites based on URLs defined by the system
administrator . URL filtering will block access to a list of sites and/or domains entered by the
administrator using the following three methods:
Host IP address (for example, 1.2.3.4).
Host DNS name (for example, www.yahoo.com).
DNS domain name (for example, *.yahoo.com, meaning all sites under the
yahoo.com hierarchy, such as finance.yahoo.com, sports.yahoo.com, etc.).
The system administrator can dynamically add or remove up to 300 specific IP addresses and
domain names to be filtered for each property.
Walled Garden
The NSE provides up to 300 IP passthrough addresses (and/or DNS entries), allowing you to
create a “Walled Garden” within the Internet where unauthenticated users can be granted or
denied access to sites of your choosing.
Web Management Interface
Nomadix’ Access Gateways can be managed remotely via the built-in Web Management
Interface where various levels of administration can be established. See also, “Using the We b
Management Interface (WMI)” on page 78.
Weighted Fair Queueing
Weighted Fair Queueing allocates bandwidth to individual users or groups in propo rtion to
their individual or group bandwidth limits. Weighted Fair Queueing provides a fall-back in an
over-subscribed scenario.
In NSE 8.5, Class Based Queueing and Weighted Fair Queueing are mutually
exclusive. Weighted Fair Queueing is enabled by default.

ACCESS GATEWAY
Introduction 27
Example Scenario
Your facility has a 150 Mbps internet connection. You have 100 subscribers with a basic plan
with 1M up/down bandwidth limits, and 100 subscribers with a premium plan with 2M up/
down speeds
At full capacity, your 200 subscribers will consume 300 Mbps. However, the total available
bandwidth is only 150 Mbps.
When WFQ is ON, the premium subscribers will get a total bandwidth of 100 MB. And
regular subscribers will get a total bandwidth of 50MB only. The ratio of bandwidth utilization
between the premium subscribers and regular subscribers remains 2:1.

ACCESS GATEWAY
28 Introduction
Optional NSE Modules
Load Balancing
With the Load Balancing Module, Internet traffic is balanced across multiple WAN/ISP
connections to ensure that traffic is distributed based on the capability of each connection. For
example, organizations may wish to balance traffic between a low-cost DSL WAN/ISP and one
high-performance, high-capacity WAN/ISP. This is of value when multiple links are used to
optimize cost for Internet service, such as balancing traffic between one low-cost DSL WAN/
ISP and one high-performance, high-capacity WAN/ISP. Hotels may also use this capability to
provide tiered services reflecting the capacity of the WAN/ISP connection.
The Link Failover feature of the Load Balancing Module is designed to improve business
continuity. In the event that one or more links fail, traffic is seamlessly rerouted to the
remaining surviving links without lapse of service. When the failed links recover, the NSE
routes new connections toward the now-working links until a normal, balanced configuration is
reached.
For details of the Load Balancing capabilities and sample use cases, see “Load Balancing and
Link Failover” on page 33.
Hospitality Module
The optional Hospitality Module provides the widest range of Property Management System
(PMS) interfaces to enable in-room guest billing for High Speed Internet Access (HSIA)
service. This module also includes 2-Way PMS interface capability for in-room billing in a W iFi enabled network. In addition, the Hospitality Module includes the Bill Mirror functionality
for posting of billing records to multiple sources. With this module, the NSE also supports
billing over a TCP/IP connection to select PMS interfaces.
Load Balancing requires an optional NSE product license

ACCESS GATEWAY
Introduction 29
PMS Integration
By integrating with a hotel’s PMS, your NSE-powered product can post charges for Internet
access directly to a guest’s hotel bill. In this case, the guest is billed only once. The NSE
outputs a call accounting record to the PMS system whenever a subscriber purchases Internet
service and decides to post the charges to their room. Nomadix’ Access Gateways are
equipped with a serial PMS interface port to facilitate connectivity with a customer’s Property
Management System.
High Availability Module
The optional High Availability Module offers enhanced network uptime and service
availability when delivering high-quality Wi-Fi service by providing Fail-Over functionality.
This module allows a secondary Nomadix Access Gateway to be placed in the network that
can take over if the primary device fails, ensuring Wi-Fi service remains uninterrupted.
Your product license may not support this feature.
Some Property Management Systems may require you to obtain a license before
integrating the PMS with the Access Gateway. Check with the PMS vendor.
Your product license may not support this feature.

ACCESS GATEWAY
30 Introduction
Network Architecture (Sample)
The Access Gateway can be deployed effectively in a variety of wireless and wired broadband
environments where there are many users—usually mobile—who need high speed access to
the Internet.
The following example shows a potential Hospitality application:

ACCESS GATEWAY
Introduction 31
Multiple Unit Clustering
In the recent past, it was necessary to segment the network to serve a number of subscribers
that exceed the user count on a Nomadix gateway. Now with clustering all subscribers can be
on the same segment, as the subscribers are distributed across multiple gateways. A large
number of subscribers can be distributed to as many as 250 gateways, thus providing a design
capacity of 1 million subscribers being served.
One can scale the cluster up and down just by adding gateways or removing gateways.
Remember that a subscriber and the subscriber’s MAC address are positioned in a specific
gateway, so changing the number of gateways will require the gateways to reconfigure, and
their current subscriber table updated. If a prepaid subscriber exists in a radius or
authentication file, this prepayment will be lost. It is recommended that prepayment situations
should be avoided.
The cluster will distribute the subscribers MAC addresses according to a modulus calculation
based on the last three bytes of the MAC address of the subscriber. The result will determine
which gateway will support that MAC address while the other gateways ignore the traffic for
the MAC.
There is currently no failover in support of clustering. The following other NSE features are
not compatible with clustering:
Proxy ARP for device
Routed subscribers
Intra-port communication
Identifying the Resident Gateway in a Cluster Environment
To diagnose device connection problems in a cluster environment, you must identify the
resident gateway. For a given MAC address, you can determine the gateway as follows. You
will need the last three bytes of the device MAC address and the total number of gateways.
Convert the hex bytes to decimal:
1. Using the Windows Calculator in programmer mode
2. In hex mode, input the last three bytes of the MAC address
3. Convert to decimal by using that function on the calculator
The resident gateway is the (decimal bytes) modulus (the total number of gateways), plus 1.

ACCESS GATEWAY
32 Introduction
The following graphic illustrates a clustering scenario with 12,000 users and three gateways.

ACCESS GATEWAY
Introduction 33
Load Balancing and Link Failover
The NSE supports individual configuration of multiple WANs on an Access Gateway
(supported on AG2400, AG5600, and AG5800 hardware). Hotels can use this capability in a
number of ways, including load balancing, failure protection, and subscriber allo cation .
This section provides use cases and scenarios to help you consider the full advantage of these
capabilities.
Definitions and Concepts
Load Balancing
Load balancing refers to the general process of balancing user traffic across multiple ISP
connections. All load-balancing appliances, as well as the Nomadix NSE, support load
balancing.
Link Aggregation
Link aggregation refers to the process of connecting multiple ISP connections to an appliance
and having the sum of all of the ISP bandwidth available to be shared across all users.
However, one individual connection is limited to the speed of the ISP connection that is
currently being used. For example, a hotel may aggregate 5 x 1.5Mbps DSL connections
together. This means that a total of 7.5Mbps of bandwidth is available to be shared across all
users, but a single user can receive a maximum of 1.5Mbps. All load-balancing appliances, as
well as the Nomadix NSE, support link aggregation. In most cases, link aggregation and load
balancing is effectively the same thing.
Link Failover
Link failover (sometimes referred to ISP redundancy) is the process of providing a second (or
occasionally a third or more) ISP link as a back up to the primary ISP link. In the event that the
primary link fails, all traffic is re-routed to the backup link, until such time as the primary link
becomes available.
Combined Load Balancing and Link Failover
This is the process where both load balancing and link failover are combined together. It
represents the best of both worlds. Where multiple ISP links are used in load balancing mode,
in the event that one or more links fail, all traffic is automatically rerouted to the remaining
surviving links. When the failed links recover, new connections are routed toward these until
the normal balanced configuration is reached.

ACCESS GATEWAY
34 Introduction
ISP link Selection Criteria
In a load-balancing scenario, some criteria must be used to decide which ISP is selected for
outgoing traffic. There a number of factors that influence this decision, including:
Identity of the users: Is a random ISP section used or is it desirable to have certain
users steered toward a particular ISP?
For random ISP: Whether subscriber, destination address or session-based link
selection is used?
User-Based ISP Selection versus Random ISP Selection
User-based ISP selection is the process whereby the ISP link that is selected in a load-balanced
environment is based on the identity of the user. For example, all users from guest rooms may
be steered toward one ISP link, and all meeting room users steered toward another ISP link that
is only used for meetings and conferences.
The alternative is to use random ISP selection, whereby the load balancer or NSE selects the
ISP to be used according to the current load conditions. The Nomadix NSE uses random ISP
selection by default.
Link Availability Detection Method and Time
Load balancing and failover requires some form of monitoring of each ISP link to determine its
availability for executing load balancing and failover decisions. Generally, link monitoring is
accomplished by two different methods:
1. Periodic probing of predefined hosts using HTTP or ICMP ping requests.
2. Periodic DNS queries to the DNS servers provided by each ISP.
The period between successive link tests is usually configured, and is typically set to between
30 seconds and 60 seconds. This represents the maximum time for which a user will remain
connected to a failed ISP connection before being re-routed to a working ISP link in an ISP
failure scenario.
Traffic Balancing and Weighting
Load balancers have some form of weighting of traffic between links to achieve a desired
balance scenario. With the Nomadix NSE, traffic is balanced by individual subscriber numbers,
and weighted according to the speed of the ISP connected to each port. For example, if an NSE
has 2 x 10M links connected and currently has 100 active subscribers, then 50 users would be
connected to each link. If the ISP links were 10 Mbps and 40Mbps, then 20 users would be
connected to the 10M link and 80 users to the 40M link, and so on.

ACCESS GATEWAY
Introduction 35
Load Rebalancing upon Link Recovery
Load balancing and failover with well-configured link availability detection provides fast and
effective recovery from ISP link failure occurrences. Additional consideration must be made as
to what actions should be taken when a failed ISP link recovers. The Nomadix approach is to
rebalance as the ISP links change, thus making sure the maximum level of service is always
provided. There is a small yet important waiting time to ensure changing links is kept to a
minimum.
Load Balancing and Failure Considerations
1. Is load balancing or just ISP failover required?
2. Is aggregation of multiple low-speed links required?
3. How reliable are different local ISP services?
4. What are the relative costs of different ISP services?
5. Do ISP links need to be shared between guest and back-office users?
6. Is there a requirement to have certain users connected to a particular ISP?
1. It may be a requirement to provide just a backup service to the primary ISP service in the
case that the main HSIA ISP fails. The backup service may be on a pay-to-use basis through a
3G or 4G wireless modem, or be a low-cost, lower-tier service, such as a cable modem service,
that is only used when the main ISP link is down, on the basis that providing a reduced HSIA
service is better than no service at all when the main ISP link is down. Alternatively, the
organization may have multiple ISP links, and wants to be able to fully utilize all of them
under normal conditions. The Nomadix NSE suppo rts both failover only and combined load
balancing with failover.
2. In some instances, suitable high-speed internet services required to meet the aggregate needs
of the organization may not be available or are simply too expensive. In this case it may be
desirable to aggregate multiple lower-cost, lower-speed lines together. The Nomadix AG2400
and AG5600 can aggregate services from up to three ISP links, and the AG5800 can handle up
to five links.
3. It is important to consider the relative quality of each ISP link. If a second link is much
lower quality than the main ISP link, then it should only be used as a back-up link in failover
mode, and not in a load-balanced environment. If the quality of the links is much the same,
then load balancing with failover should be used.
4. It is important to consider the relative cost of links. If all links have a fixed monthly charge,
then ideally they should be used in a load-balanced mode, so that costly links are not sitting
unused most of the time. But if an ISP link has a relatively low monthly charge with high permegabyte data usage charges, then it should only be used in failover mode as a backup to a
main ISP link.

ACCESS GATEWAY
36 Introduction
5. It may be requirement to share ISP bandwidth between Guest HSIA and Hotel Admin
networks, or have each network available as a fall-back network for the other. Both scenarios
can be handled with the Nomadix NSE.
6. It may be desirable to have certain users connected to a particular ISP link, and other users
connected to a different ISP link. The Nomadix NSE prov i des a “preferred WAN” radius
attribute (VSA). For example, paying users may be connected to an expensive high-quality
link, with free users connected to a lower-quality link, with link failover still available if the
preferred link fails.
Some examples of typical common deployment scenarios are outlined below: These are just
examples and other deployment scenarios can be handled, as well.
Load Balancing across Multiple Low Speed Links
In this example, an establishment has access to only low-speed, DSL-based ISP circuits and
wishes to aggregate five such links together. The Nomadix NSE is configured with load
balancing between all links.
Failover to Standby ISP Link
In this example, the organization has a high-quality 100M Ethernet service. But to guarantee
continuous HSIA service, the organization has a back-up ISP service from a low-cost wireless
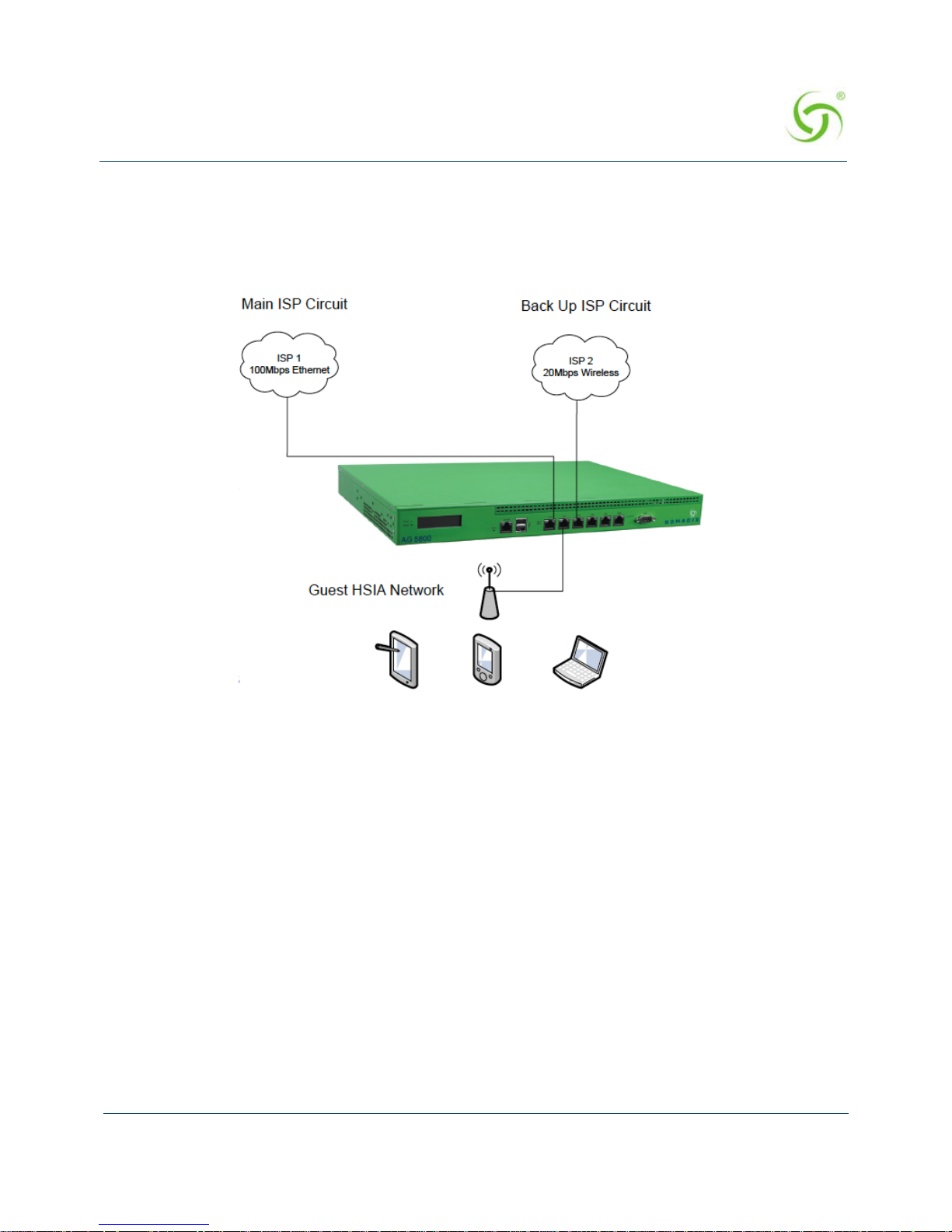
ACCESS GATEWAY
Introduction 37
provider, which charges on a data volume basis. The organization only wishes fo r thi s link to
be used when the main ISP circuit is not available.
The Nomadix NSE is configured for failover only from the WAN to port Eth2 on the NSE.
Separate Guest HSIA and Admin ISP Links, with Failover Between Each
ISP Link
In this scenario, the hotel has separate HSIA and Hotel Admin ISP circuits. Under normal
circumstances, Guests will be connected to the Guest HSIA ISP, and Hotel Admin users will
connect to the Admin ISP. If either link fails, then failover to the other link will occur. If the
Guest HSIA link fails, the guests will be connected to the Admin ISP link until the Guest HSIA
link is restored. If the Admin ISP link fails, the Admin users will be connected to the Guest
HSIA link until the Admin ISP is restored
The Nomadix NSE is configured with load balancing and failover. All Guests use ISP 1 as the
preferred WAN, the Admin network router uses ISP2 as the preferred WAN.
ACCESS GATEWAY
38 Introduction
Guest HSIA Failover Only, to Admin Network
In this scenario, the hotel has separate ISP circuits for the Guest HSIA network and Hotel
Admin network. The hotel wants the Admin network to be available as a back-up link in case
the Guest HSIA ISP link fails. There is no back-up for the Admin ISP network.
The Nomadix NSE is configured with link failover between the WAN port and port ETH2,
which is connected to the hotel Admin network router.

ACCESS GATEWAY
Introduction 39
Sharing Guest HSIA Network and Hotel Admin Network Among Multiple
ISP Links
In this scenario, multiple ISP links are connected to the Nomadix NSE, in a similar method to
the first scenario, but both the guest HSIA network and the Hotel Admin network are
connected to the NSE and share the aggregate bandwidth of the combined ISP links.
The Nomadix NSE is configured for load balancing, and the back office router's MAC address
is registered in as a device in the NSE with an appropriate band width limit.

ACCESS GATEWAY
40 Introduction
Load Balancing With Users Connected to a Preferred ISP Link
In this scenario the hotel has purchased 2 x ISP links for guest HSIA. One is a high-quality,
high-cost "business grade" ISP circuit, and the other is a low-cost, lower-grade domestic
service provided by the local cable TV operator. The hotel has a number of bill plan options
including free-to-use and pay-to-use premium plans. Under normal circumstances, the hotel
wants guests who have selected a free plan to use the low-cost link, and guests who have
selected a premium service to use the higher-cost, business-grade ISP connection. If either link
fails, guest should fail over to the other links until the preferred link is restored.

ACCESS GATEWAY
Introduction 41

ACCESS GATEWAY
42 Introduction
Online Help (WebHelp)
The Access Gateway incorporates an online Help system called “WebHelp” which is
accessible through the Web Management Interface (when a remote Internet connection is
established following a successful installation). WebHelp can be viewed on any platform (for
example, Windows, Macintosh, or UNIX-based platforms) using either Internet Explorer or
Netscape Navigator (see note).
WebHelp is useful when you have an Internet connection to the Access Gateway and you want
to access information quickly and efficiently. It contains all the information you will find in
this User Guide.
For more information about WebHelp and other online documentation resources, go to “Online
Documentation and Help” on page 59.
Notes, Cautions, and Warnings
The following formats are used throughout this User Guide:
General notes and additional information that may be useful are indicated with a
Note.
Cautions and warnings are indicated with a Caution. Cautions and warnings
provide important information to eliminate the risk of a system malfunction or
possible damage.

ACCESS GATEWAY
2
Installing the Access Gateway 43
Installing the Access Gateway
This section provides installation instructions for the hardware and software components of the
Access Gateway. It also includes an overview of the management interface, some helpful hints
for system administrators, a Quick Reference Guide, and procedures.
Nomadix Access Gateway
Installation Workflow
The following flowchart illustrates the steps that are required to install and configure your
Access Gateway successfully . Review the installatio n workflow before attempting to install the
Once you have installed your Access Gateway and established the configuration
settings, you should write the settings to an archive file. If you ever experience
problems with the system, your archived settings can be restored at any time. See
“Archiving Your Configuration Settings” on page 75.

ACCESS GATEWAY
44 Installing the Access Gateway
Access Gateway on the customer’s network.
Place the AG on a flat and stable work surface and connect the power cord.
Start a HyperTerminal session to communicate with the AG via the serial port.
Power up your computer and turn on the AG.
Log in to the Command Line Interface.
When prompted, configure your AG’s IP, DNS, and Location
settings. The AG will then prompt you to reboot the system.
Connect the AG to the customer’s network.
Power up the AG and log in via a Telnet session or the Web Management Interface.
Set the basic configuration parameters for subscribers.
Network
Connect the AG to a “live” network. Use the RJ45 to DB9 console cable
between the Access Gateway and your computer.
Export your configuration settings to an archive file.
The AG is now ready for administrators to add, delete, or
change unique subscriber profiles.
When prompted, accept to the Nomadix End User License Agreement (EULA). You
must accept the EULA before the AG can connect with the Nomadix License Key
Server. When the key is successfully received from the server, your AG will reboot.
You can now power down and connect the AG to the customer’s network.

ACCESS GATEWAY
Installing the Access Gateway 45
Powering Up the System
Use this procedure to establish a direct cable connection between the Access Gateway and
your laptop computer, and to power up the system.
1. Place the Access Gateway on a flat and stable work surface.
2. Connect the power cord.
3. Connect the RJ45 console cable between the Access Gateway’s Console port and the
female DB9 to the serial port or USB to serial adapter of your computer.
4. Turn on your computer and allow it to boot up.
5. Turn on the Access Gateway.
User Manual and Documentation
The Nomadix product user manuals, product documentation and support files including
MIB, XML DTD and sample dictionary files are located at the following URL:
http://www.nomadix.com/current_releases.php
If you have any problems, please contact our technical supp ort team at +1.818.575.2590,
or email: support@nomadix.com
.
This quick start document provides instructions and reference material for getting started
with the Nomadix Access Gateway products, specifically the AG 2400 and AG 5800.
Connect the RJ45
console cable here

ACCESS GATEWAY
46 Installing the Access Gateway
Accessory Box Contents
AG 2400
1 – U.S. (NEMA 5-15p) Power Cord
1 – EU (Schuko CEE7/7) Power Cord
1 – 6’ RJ45 – DB9 Console Cable
2 – Rack Mount Brackets and PS bracket
1 – Bumper and Screw Kit
AG 5800
1 – U.S. (NEMA 5-15p) Power Cord
1 – EU (Schuko CEE7/7) Power Cord
1 – 6’ RJ45 – DB9 Console Cable
2 – Rack Mount Brackets
1 – Bumper and Screw Kit
Start Here
1. Unpack the Nomadix Access Gateway and place the product on a flat and stable work
surface.
2. Register the gateway for support services by completing and return ing the Nomadix
Gateway Registration Form; hardcopy enclosed or obtain the form online at
http://www.nomadix.com/registration
.
3. Connect the power cord.
4. Connect to the Access Gateway (AG). There are two ways to connect to the Access
Gateway (AG):
Serial Connection:
Connect the RJ45 console cable to the product’s console port and the DB9 female to your
computer.

ACCESS GATEWAY
Installing the Access Gateway 47
Start a HyperTerminal (or equivalent) session to communicate with the AG via the
product’s console interface. Use the following configuration settings for your session:
Subscriber-side Ethernet Connection:
Connect an Ethernet cable between the product’s Eth1 port and your computer’s Ethernet
port.
5. Setup a SSH client to establish a SSH session to communicate with the NSE gateway via
the administrative IP address after the Access Gateway finishes powering up. The
administrative IP address is 172.30.30.172.
6. Power up your computer and turn on the product. You can then configure the WAN for a
static IP address, DHCP Client or PPPoE client using appropriate configuration guidelines
that follow in order to obtain the license key . Once the key has been obtained, the web
management interface (WMI) can be used to continue configuration.
LCD Messages
Some Access Gateway hardware models are equipped with an LCD panel, that displays the
following system information:
Platform and Firmware Version Installed
Primary IP Address of the NSE
NSE ID
Active Subscribers.
Bits per Second Data Bits Parity Stop Bits Flow Control
9600 8 None 1 None
IP Address 172.30.30.173
Netmask 255.255.0.0
Gateway 172.30.30.172
DNS (If Required) 4.2.2.1

ACCESS GATEWAY
48 Installing the Access Gateway
Configuration
Note: The WAN port of the AG must be connected to a live network that can access the
Internet in order to retrieve the license key from the license key server.
Log in by typing admin then password: admin. Type (y)es when prompted to configure
settings. The initial minimal WAN port configuration mode will be displayed as shown in
Figure 1.
Ready. Press enter to login.
NSE
Login: admin <Enter>
Password: ***** <Enter>
NO LICENSE KEY HAS BEEN ENTERED. A LICENSE KEY MUST BE ENTERED
IN ORDER TO PROCEED WITH INSTALLATION.
SEE USER'S GUIDE FOR LICENSE KEY INFORMATION.
INSTALLATION WILL NOW TRY TO CONTACT THE NOMADIX LICENSE KEY SERVER.
IN ORDER TO PROCEED, THE NSE MUST BE ABLE TO CONNECT TO THE INTERNET.
DO YOU WANT TO CONFIGURE THE NSE'S IP AND DNS SETTINGS? [yes/no]: y
Configuring minimal WAN interface connectivity parameters:
Configuration Mode [static] (static, dhcp, pppoe) :
Figure 1: Initial minimal WAN port configuration.
Select the desired configuration mode and use the following steps to configure the WAN
port for either Static IP, DHCP client or PPPoE.
Step 1a: Static WAN IP Configuration
Accept static as the default configuration mode and enter the following mandatory
settings shown in Figure 2.
Configuring minimal WAN interface connectivity parameters:
Configuration Mode [static ] (static, dhcp, pppoe) :
IP Address [10.0.0.10 ] : Your WAN IP address

ACCESS GATEWAY
Installing the Access Gateway 49
Subnet Mask [255.255.255.0 ] : Your subnet mask
Gateway IP [10.0.0.1 ] : Your gateway IP address
WAN 802.1Q tagging [Disabled ] :
VLAN ID [1 ] :
DNS Domain Name [nomadix.com ] :
DNS Server 1 [0.0.0.2 ] : Your primary DNS IP
DNS Server 2 [0.0.0.0 ] :
DNS Server 3 [0.0.0.0 ] :
Figure 2: Initial WAN port settings
A WAN port summary page will then be displayed as shown in Figure 3.
Port Name : WAN
Port Role : wanIf
Configuration Mode : static
IP Address : Your IP address
Subnet Mask : Your subnet mask
Gateway IP : Your gateway IP addrss
WAN 802.1Q tagging : Disabled
VLAN ID : 1
DNS Domain Name : nomadix.com
DNS Server 1 : Your primary DNS IP address
DNS Server 2 :
DNS Server 3 : 0.0.0.0
Additional NAT IP addresses : Disabled
show all - Show all WAN Interface configuration
show interface <name> - Show a single WAN Interface configuration
modify interface <name> - Modify a single WAN Interface
configuration
Type b to go back, <esc> to abort, ? for help.
Ethernet port/WAN interface configuration>
Figure 3: WAN port static IP configuration summary page.
If everything is correct in the summary, type (b)ack to return to the previous menu, and
proceed to Step 2 to enter the location information.
Otherwise, select an option from the Ethernet port configuration menu to display or make
changes to the WAN port settings. When finished with the settings, type b(ack) to return
to the previous menu, and go to Step 2.

ACCESS GATEWAY
50 Installing the Access Gateway
Step 1b: DHCP Client Configuration
Type (d)hcp for the configuration mode as shown in Figure 4.
Configuring minimal WAN interface connectivity parameters:
Configuration Mode [static ] (static, dhcp, pppoe) : d
WAN 802.1Q tagging [Disabled ] :
VLAN ID [1 ] :
DNS Server 3 [0.0.0.0 ] :
Figure 4: Selecting DHCP Client for WAN configuration.
A WAN port summary page will then be displayed as shown in Figure 5.
Port Name : WAN
Port Role : wanIf
Configuration Mode : dhcp
IP Address : Your IP address
Subnet Mask : Your subnet mask
Gateway IP : Your gateway IP addrss
WAN 802.1Q tagging : Disabled
VLAN ID : 1
DNS Domain Name : Your domain name
DNS Server 1 : Your primary DNS IP address
DNS Server 2 :
DNS Server 3 : 0.0.0.0
Additional NAT IP addresses : Disabled
show all - Show all WAN Interface configuration
show interface <name> - Show a single WAN Interface configuration
modify interface <name> - Modify a single WAN Interface configuration
Type b to go back, <esc> to abort, ? for help.
Ethernet port/WAN interface configuration>
Figure 5: WAN port DHCP client configuration summary page.
If everything is correct in the summary, type (b)ack to return to the previous menu, and
proceed to step 2 to enter location information.
Otherwise, select an option from the Ethernet port configuration menu to display or ma ke
changes to the WAN port settings. When finished with settings, type b(ack) to return to the
previous menu, and go to step 2.

ACCESS GATEWAY
Installing the Access Gateway 51
S tep 1c: PPPoE Dynamic IP Client Configuration
Enter (p)ppoe when prompted. Enter the following mandatory settings for a PPPoE
connection with dynamic PPP IP configuration shown in Figure 6.
Configuring minimal WAN interface connectivity parameters:
Port Role [wanIf ] (outOfService, subscriberIf, w
anIf) :
Configuration Mode [static ] (static, dhcp, pppoe) : p
PPPoE Service Name [ ] : ("none" to clear) : Your Service
LCP Echo-Request Interval [30 ] :
Maximum LCP Non-responses [6 ] :
PPP Authentication User Name [ ] : ("none" to clear) : Your User Name
PPP Authentication Password [ ] : ("none" to clear) : Your Password
PPP IP Configuation Mode [dynamic ] (dynamic, static) :
PPP Static IP Address [0.0.0.0 ] :
PPP Maximum TCP MSS [1452 ] :
WAN 802.1Q tagging [Disabled ] :
VLAN ID [1 ] :
DNS Domain Name [nomadix.com ] :
DNS Server 3 [0.0.0.0 ] :
Figure 6: Selecting PPPoE with dynamic IP configuration.
A WAN port summary page will then be displayed as shown in Figure 7.
Port Name : WAN
Port Role : wanIf
Configuration Mode : pppoe
IP Address : Your IP address
Subnet Mask : Your subnet mask
Gateway IP : Your gateway
PPPoE Service Name : Your Service Name
LCP Echo-Request Interval : 30
Maximum LCP Non-responses : 6
PPP Authentication User Name : Your user name
PPP Authentication Password : Your password
PPP IP Configuation Mode : dynamic
PPP Static IP Address : 0.0.0.0
PPP Maximum TCP MSS : 1452
WAN 802.1Q tagging : Disabled
VLAN ID : 1
DNS Domain Name : Your domain name

ACCESS GATEWAY
52 Installing the Access Gateway
DNS Server 1 : Your dns server IP address
DNS Server 2 : 0.0.0.0
DNS Server 3 : 0.0.0.0
Additional NAT IP addresses : Disabled
show all - Show all WAN Interface configuration
show interface <name> - Show a single WAN Interface configuration
modify interface <name> - Modify a single WAN Interface configuration
Type b to go back, <esc> to abort, ? for help.
Ethernet port/WAN interface configuration>
Figure 7: WAN port PPPoE client configuration summary page.
If everything is correct in the summary, type (b)ack to return to the previous menu, and
proceed to step 2 to enter location information.
Otherwise, select an option from the Ethernet port configuration menu to display or ma ke
changes to the WAN port settings. When finished with settings, type b(ack) to return to
the previous menu, and go to step 2.
Step 1d: PPPoE Static IP Client Configuration
Use the same steps for configuring dynamic PPPoE shown in Figure 6 above, but select
static for PPP IP Configuration Mode, and enter your IP address for PPP Static IP
Address. A summary page similar to Figure 7 above will be displayed.
If everything is correct in the summary, type (b)ack to return to the previous menu, and
proceed to step 2 to enter location information.
Otherwise, select an option from the Ethernet port configuration menu to display or ma ke
changes to the WAN port settings. When finished with settings, type b(ack) to return to the
previous menu, and go to step 2.
Step 2: Entering Your Location Information
You will be required to enter location information in order to obtain the license key. Enter
the following mandatory location information details shown in Figure 8.
Ethernet port/WAN interface configuration>b
Please enter your Company Name [ ]: Your company name
Please enter your Site Name [ ]: Your site name
Please enter your Address (Line 1) [ ]:
(Line 2) [ ]:

ACCESS GATEWAY
Installing the Access Gateway 53
(City) [ ]: Your site city
(State) [ ]: Your site state
(ZIP/Postal Code) [ ]:
(Country) [ ]: Your site country
Please enter your E-Mail Address [ ]: email address
Please select the venue type that most reflects your location
1. Apartment
...
25. Other
Please enter a number from the above list: Venue Type
Figure 8: Site location details.
Step 3: Retrieving Your License Key
The system will now prompt you to accept or decline the End User License Agreement
(EULA). You must accept the terms of the EULA before the AG can retrieve its license
key. To retrieve the license key, enter (y)es as shown in Figure 9. The AG retrieves the
license key from the Nomadix license key server, then reboots.
PLEASE READ THE NOMADIX END USER LICENSE AGREEMENT ('AGREEMENT') INCLUDED
WITH THE NOMADIX PRODUCT.
BY USING THIS SOFTWARE, YOU INDICATE YOUR ACCEPTANCE OF THE AGREEMENT.
I AGREE TO THE TERMS AND CONDITIONS OF THE NOMADIX END USER LICENSE
AGREEMENT.
(Y)ES (N)O
y
The system will now try to contact the Nomadix License Key Server.
Please wait...
Received key from License Key Server.
If the license key is successfully processed the unit will reboot...
Figure 9: License key retrieval
NOTE: The date and time Software License Subscription start date.
Step 4: Configuring the System
You have now established a basic configuration for the AG that enables internet
connectivity.

ACCESS GATEWAY
54 Installing the Access Gateway
Before you can log into the AG and use the graphical Web Management In terface (WMI),
you must disable subscriber-side HTTP:
1. Log in to the AG
2. Navigate to Configuration -> Access Control -> Interface
3. Press Enter until you reach Subscriber-side HTTP
4. Enter disabled
You can now use the graphical Web Management Interface (WMI) to configure the
product’s features.
Step 5: Configuring AG DHCP Server Settings
DHCP Server is enabled by default. To configure the DHCP Server, go to DHCP under the
Configuration menu. You can either modify the default DHCP pool or delete/add another
DHCP pool. The total lease pool size recommendation is 5 times more than the number of
licensed subscribers.
DHCP Parameter Your Settings Default Values
DHCP Services (Disable) no
DHCP Relay (Yes / No)
If No, skip to DHCP Server
no
DHCP Relay Server IP Address blank
DHCP Relay Agent IP Address blank
DHCP Server (Yes / No)
Only if the DHCP Relay is
disabled
yes
DHCP Server IP Address 10. 0. 0.4
DHCP Server Subnet Mask 255.255.255.0
DHCP Pool Start IP Address 10.0.0.12

ACCESS GATEWAY
Installing the Access Gateway 55
An example of a basic network including an AG is shown below.
The Management Interfaces (CLI and Web)
Until the unit is installed on the customer’ s network and a remote connection is established, the
CLI is the administrator’s window to the system. This is where you establish all the Access
Gateway start-up configuration parameters, depending on the customer’s network architecture.
The Access Gateway Menu is your starting point. From here, you access all the system
administration items from the 5 (five) primary menus available:
Configuration
DHCP Pool End IP Address 10.0.0.72
DHCP Lease Minutes 1440
The Access Gateway supports various methods for managing the system
remotely. These include, an embedded graphical Web Management Interface
(WMI), an SNMP client, or Telnet. However, until the unit is installed and
running, system management is performed from the Access Gateway’s embedded
CLI via a direct serial cable connection. The CLI can also be accessed remotely.
DHCP Parameter Your Settings Default Values

ACCESS GATEWAY
56 Installing the Access Gateway
Network Info
Port-location
Subscribers
System
Making Menu Selections and Inputting Data with the CLI
The CLI is character-based. It recognizes the fewest unique characters it needs to correctly
identify an entry . For example, in the Access Gateway Menu you need only enter
c to access the
Configuration menu, but you must enter
su to access the Subscribers menu and sy to access
the System menu (because they both start with the letter “s”).
You may also do any of the following:
Enter b (back) or press Esc (escape) to return to a previous menu.
Press Esc to abort an action at any time.
Press Enter to redisplay the current menu.
Press ? at any time to access the CLI’s Help screen.
When using the CLI, if a procedure asks you to “enter sn,” this means you must type
sn and
press the
Enter key. The system does not accept data or commands until you hit the Enter key.
Menu Organization (Web Management Interface)
When you have successfully installed and configured the Access Gateway from the CLI, you
can then access the Access Gateway from its embedded Web Management Interface (WMI).
The WMI is easier to use (point and click) and includes some items not found in the CLI. You
can use either interface, depending on your preference.
For a complete description of all features available in the WMI, see “Using the Web
Management Interface (WMI)” on page 78.
The following “composite” screen shows how the Access Gateway’ s WMI menus (folders) are
organized (shown here side-by-side for clarity and space). See also, “About Your Product
License” on page 80.
Although the basic functional elements are the same, the CLI and the WMI have
some minor content and organizational differences. For example, in the WMI the
“subscribers” menu is divided into “Subscriber Administration” and
“Subscriber Interface.” See also, “Menu Organization (Web Management
Interface)” on page 56.

ACCESS GATEWAY
Installing the Access Gateway 57
Note: Your browser preferences or
Internet options should be set to
compare loaded pages with cached
pages.

ACCESS GATEWAY
58 Installing the Access Gateway
Inputting Data – Maximum Character Lengths
The following table details the maximum allowable character lengths when inputting data:
Data Field Max. Characters
All Messages (billing options) 72
All Messages (subscriber error messages) 72
All Messages (subscriber login UI) 72
All Messages (subscriber “other” messages) 72
Description of Service (billing options Plan) 140
Home Page URL 237
Host Name and Domain Name (DNS settings) 64
IP / DNS Name (passthrough addresses) 237
Label (billing options plan) 16
Location settings (all fields) 99
Partner Image File Name 12
Password (adding subscriber profiles) 128
Port Description (finding ports by description) 63
Redirection Frequency (in minutes) 2,147,483,647
(recommend 3600)
Reservation Number 24
Username (adding subscriber profiles) 96
Valid SSL Certificate DNS Name 64

ACCESS GATEWAY
Installing the Access Gateway 59
Online Documentation and Help
The W eb Management Interface (WMI) incorporates an online help system which is accessible
from the main window.
Other online documentation resources, available from our corporate Web site
(www.nomadix.com/support), include a full PDF version of this User Guide (viewable with
Acrobat™ Reader), README files, white papers, technical notes, and business cases.
Quick Reference Guide
This section provides information to help you navigate and use the management interfaces
(CLI and Web) quickly and efficiently. It also contains the product specifications, a listing of
the factory default settings, sample log reports, listings of commands (by menu and
alphabetical), HyperTerminal settings, and some common keyboard shortcuts.
Click here to access the
online Help system

ACCESS GATEWAY
60 Installing the Access Gateway
Establishing the Start Up Configuration
The CLI allows you to administer the Access Gateway’s start-up configuration settings.
The start up configuration must be established before connecting the Access Gateway to a
customer’s network. The “start up” configuration settings include:
Assigning Login User Names and Passwords – You must assign a unique login user
name and password that enables you to administer and manage the Access Gateway
securely.
Setting the SNMP Parameters (optional) – The SNMP (Simple Network Management
Protocol) parameters must be established before you can use an SNMP client (for
example, HP OpenView) to manage and monitor the Access Gateway remotely.
Enabling the Logging Options (recommended) – Servers must be assigned and set up
if you want to create system and AAA (billing) log files, and retrieve error messages
generated by the Access Gateway.
When establishing the start-up configuration for a new installatio n, you are
connected to the Access Gateway via a direct serial connection (you do not have
remote access capability because the Access Gateway is not yet configured or
connected to a network). Once the installation is complete (see “Installation
Workflow” on page 43) and the system is successfully configured, you will have
the additional options of managing the Access Gateway remotely from the
system’s Web Management Interface, an SNMP client manager of your choice, or
a simple Telnet interface.
User names and passwords are case-sensitive.

ACCESS GATEWAY
Installing the Access Gateway 61
Assigning the Location Information and IP Addresses:
Assigning the Network Interface IP Address - This is the public IP
address that allows administrators and subscribers to see the Access Gateway
on the network. Use this address when you need to make a network connection
with the Access Gateway.
Assigning the Subnet Mask – The subnet mask defines the number of IP
addresses that are available on the routed subnet where the Access Gateway is
located.
Assigning the Default Gate w ay IP Add res s – This is the IP address of
the router that the Access Gateway uses to transmit data to the Internet.
Assigning Login User Names and Passwords
When you initially powered up the Access Gateway and logged in to the Management
Interface, the default login user name and password you used was “admin.” The Access
Gateway allows you to define 2 concurrent access levels to differentiate between managers and
operators, where managers are permitted read/write access and operators are restricted to read
access only . Once the logins have been assigned, ma nagers have the ability to perform all write
commands (Submit, Reset, Reboot, Add, Delete, etc.), but operators cannot change any system
settings. When Administration Concurrency is enabled, one manager and three operators can
access the Access Gateway at any one time (the default setting for this feature is “disabled”).
1. Enter sy (system) at the Access Gateway Menu. The System menu appears.
2. Enter lo (login).
The system prompts you for the current login. If this is the first time you are changing the
login parameters since initializing the Access Gateway, the default login name and
password is “admin.”
3. When prompted, confirm the current login parameters and enter new ones.
Sample Screen Response:
System>lo
Enable/Disable Administration Concurrency [disabled]: e
Current login: admin
Current password: *****
Enter new manager login: newmgr
Enter new password: *******
Retype new password: *******
The system accepts up to 11 characters (any character type) for user names and
passwords. All user names and passwords are case-sensitive.

ACCESS GATEWAY
62 Installing the Access Gateway
The administrative login and password were changed
Enter new operator login: newop
Enter new operator password: *****
Retype new operator password: *****
The operator login and password were changed
Enter RADIUS remote test login: rad
Enter new RADIUS remote test password: *****
Retype new RADIUS remote test password: *****
The RADIUS remote test login and password were changed
You must use the new login user name(s) and password(s) to access the system.
Setting the SNMP Parameters (optional)
You can address the Access Gateway using an SNMP client manager (for example, HP
OpenView). SNMP is the standard protocol that regulates network management over the
Internet. To do this, you must set up the SNMP communities and identifiers. For more
information about SNMP, see “Using an SNMP Manager” on page 79.
1. Enter c (configuration) at the Access Gateway Menu. The Configuration menu appears.
2. Enter sn (snmp).
3. Enable the SNMP daemon, as required. The system displays any existing SNMP contact
information and prompts you to enter new information. If this is the first time you have
initialized the SNMP command since removing the Access Gateway from its box, the
system has no information to display (there are no defaults).
4. Enter the SNMP parameters (communities and identifiers). The SNMP parameters include
your contact information, the get/set communities, and the IP address of the trap recipient.
Your SNMP manager needs this information to enable network management over the
Internet.
5. If you enabled the SNMP daemon, you must reboot the system for your changes to take
effect. In this case, enter
y (yes) to reboot your Access Gateway.
Sample Screen Response:
Configuration>sn
Enable the SNMP Daemon? [Yes]:
Enter new system contact: newname@domainname.com
[Nomadix, Newbury Park, CA]
If you want to use SNMP, you must manually turn on SNMP.

ACCESS GATEWAY
Installing the Access Gateway 63
Enter new system location: Office, Newbury Park, CA
Enter read/get community [public]:
Enter write/set community [private]:
Enter IP of trap recipient [0.0.0.0]: 10.11.12.13
SNMP Daemon: Enabled
System contact: newname@domainname.com
System location: Office, Newbury Park, CA
Get (read) community: public
Set (write) community: private
Trap recipient: 10.11.12.13
Reboot to enable new changes? [yes/no] y
Rebooting...
You can now address the Access Gateway using an SNMP client manager.
Configuring the WAN interface
If a license key is not present, you will still be directed to set up the WAN configuration as
soon as you log into the CLI. However, the subsequent steps are new and network settings are
no longer configured under Location.
The following are the steps are needed to configure the main WAN interface:
1. Enter c (configuration) at the Access Gateway Menu. The Configuration menu appears.
2. Enter eth (ethernet).
1. After you have entered “yes” to the initial prompt, enter “mod int WAN” or “m i WAN”
(“modify interface WAN”). Note that modes and interface names are case sensitive. The
configuration then steps through the settings one by one.
2. Port role for the WAN port should be already set to WAN, just hit <enter>
3. Set the configuration mode to match your network settings.
4. Set the remaining network settings .
5. Default uplink and download speed is 15 Mbps. Enter different values if desired.
Bandwidth and DNS settings are configured separately for each WAN interface. You can
configure them later in the WAN configuration dialog in the Web Management Interface.
6. If you do not wish to configure additional NAT IP addresses at this time, type “b”.
7. A summary of the WAN port settings is now displayed; if they are correct, type “b” again.
You will now see the Nomadix location configuration page. Enter contact data and agree to the
Nomadix End User License Agreement. Your license will be retrieved when you enter “y”.
The NSE will then reboot to activate your license settings.

ACCESS GATEWAY
64 Installing the Access Gateway
Enabling the Logging Options (recommended)
System logging creates log files and error messages generated at the system level. AAA
logging creates activity log files for the AAA (Authentication, Authorization, and Accounting)
functions. You can enable either of these options.
When system logging is enabled, the standard SYSLOG protocol (UDP) is used to send all
message logs generated by the Access Gateway to the specified server.
1. Enter log (logging) at the Configuration menu. The system di sp lays the current logging
status (enabled or disabled).
2. Enable or disable the system and/or AAA logging options, as required. If you enable either
option, go to Step 3, otherwise logging is disabled and you can terminate this procedure.
3. Assign a valid ID number (0-7) to each server.
4. Enter the IP addresses to identify the location of the system and AAA SYSLOG servers on
the network (the default for both is 0.0.0.0).
Although the AAA and billing logs can go to the same server, we recommend that
they have their own unique server ID number assigned (between 0 and 7). When
managing multiple properties, the properties ar e identified in the log files by their
IP addresses.

ACCESS GATEWAY
Installing the Access Gateway 65
When logging is enabled, log files and error messages are sent to these servers for future
retrieval. To see sample reports, go to “Sample SYSLOG Report” on page 314 and
“Sample AAA Log” on page 313.
Sample Screen Response:
Configuration>log
Enable/disable System Log [disabled ]: enable
Enter System Log Number (0-7) [0 ]: 2
Enter System Log Filter
0: Emergency
1: Alert
2: Critical
3: Error
4: Warning
5: Notice
6: Info
7: Debug
Select an option from above [7]: 7
Enter System Log Server IP [255.255.255.255]: 10.10.10.10
Enable/disable System Log Save to file [disabled ]: enable
Enable/disable AAA Log [disabled ]: enable
Enter AAA Log Number (0-7) [0 ]: 2
Enter AAA Log Filter
0: Emergency
1: Alert
2: Critical
3: Error
4: Warning
5: Notice
6: Info
7: Debug
Select an option from above [7]: 7
Enter AAA Log Server IP [255.255.255.255]: 10.10.10.10
Enable/disable AAA Log Save to file [disabled ]: enable
Enable/disable RADIUS History Log [disabled ]: enable
Enter RADIUS History Log Number (0-7) [0 ]: 2
Enter RADIUS History Log Filter
0: Emergency
1: Alert

ACCESS GATEWAY
66 Installing the Access Gateway
2: Critical
3: Error
4: Warning
5: Notice
6: Info
7: Debug
Select an option from above [6]: 7
Enter RADIUS History Log Server IP [255.255.255.255]: 10.10.10.10
Enable/disable RADIUS History Log Save to file [disabled ]: enable
Enable/disable System Report Log [disabled ]: enable
Enter System Report Log Number (0-7) [0 ]: 2
Enter System Report Log Server IP [255.255.255.255]: 10.10.10.10
Enter System Report Log interval (minutes) [0]: 5
Enable/disable Tracking Log [disabled ]: enable
Enter Tracking Log Number (0-7) [0 ]: 2
Enter Tracking Log Server IP [255.255.255.255]: 10.10.10.10
Enable/disable Tracking Log Save to file [disabled ]:
Enable/Disable Name Reporting [disabled ]: enable
Enable/Disable Port Reporting [disabled ]: enable
Enable/Disable Location Reporting [disabled ]: enable
Enable/Disable 500th Packet Count Reporting [disabled ]: enable
System Log Enabled
System Log Number 2
System Log Filter 7
System Log Server IP 10.10.10.10
System Log Save to file Enabled
AAA Log Enabled
AAA Log Number 2
AAA Log Filter 7
AAA Log Server IP 10.10.10.10
AAA Log Save to file Enabled
RADIUS History Log Enabled
RADIUS History Log Number 2
RADIUS History Log Filter 7
RADIUS History Log Server IP 10.10.10.10
RADIUS History Log Save to file Enabled
System Report Log Enabled
System Report Log Number 2
System Report Log Server IP 10.10.10.10
System Report Log Interval (in minutes) 5
ACCESS GATEWAY
Installing the Access Gateway 67
Tracking Log Enabled
Tracking Log Number 2
Tracking Log Server IP 10.10.10.10
Tracking Log Save to file Disabled
Tracking Name Reporting Enabled
Tracking Port Reporting Enabled
Tracking Location Reporting Enabled
Tracking Report every 500th packet Enabled
WARNING: Communication between the gateway and the syslog server may need to be
secured to comply with local laws. Consider routing communication through an IPSec tunnel.
Configuration>
Logging Out and Powering Down the System
Use this procedure to log out and power down the Access Gateway.
1. Enter l (logout) at the Access Gateway Menu. Your serial session closes automatically.
2. Turn off the Access Gateway and disconnect the power cord.
3. Disconnect the cable between the Access Gateway and your computer.
Connecting the Access Gateway to the Customer’s Network
Use this procedure to connect the Access Gateway to the customer’s network (after the start up
configuration parameters have been established).
1. Choose an appropriate physical location that allows a minimum clearance of 4cm either
side of the unit (for adequate airflow).
2. Connect the Access Gateway to the router, then connect the Access Gateway to the
customer’s subscriber port.
3. Connect the power cord and turn on the Access Gateway.
4. Go to “Establishing the Basic Configuration for Subscribers” on page 67.
Establishing the Basic Configuration for Subscribers
When you have successfully established the start up configuration and installed the uni t onto
the customer’s network, connect to the Access Gateway via Telnet. You must now set up the
basic configuration parameters for subscribers, including:

ACCESS GATEWAY
68 Installing the Access Gateway
Setting the DHCP Options – DHCP (Dynamic Host Configuration Protocol) allows
you to assign IP addresses automatically (to subscribers who are DHCP enabled). The
Access Gateway can “relay” the service through an external DHCP server or it can be
configured to act as its own DHCP server.
Setting the DNS Options – DNS (Domain Name System) allows subscribers to enter
meaningful URLs into their browsers (instead of complicated numeric IP addresses).
DNS converts the URLs into the correct IP addresses automatically.
Setting the DHCP Options
When a device connects to the network, the DHCP server assigns it a “dynamic” IP address for
the duration of the session. Most users have DHCP capability on their computer. To enable this
service on the Access Gateway, you can either enable the DHCP relay (routed to an external
DHCP server IP address), or you can enable the Access Gateway to act as its own DHCP
server. In both cases, DHCP functionali ty is necessary if you want to automatically assign IP
addresses to subscribers.
1. Enter c (configuration) at the Access Gateway Menu. The Configuration menu appears.
2. Enter dh (dhcp).
3. Follow the on-screen instructions to set up your DHCP options. For example:
The Access Gateway’s ad aptive configuration technology provides Dynamic
Address Translation (DAT) functionality. DAT is automatically configured to
facilitate “plug-and-play” access to subscribers who are misconfigured with
static (permanent) IP addresses, or subscribers that do not have DHCP capability
on their computers. DAT allows all users to obtain network access, regardless of
their computer’s network settings.
By default, the Access Gateway is configured to act as its own DHCP server and
the relay feature is “disabled.”. Please verify that your DHCP Server supports
DHCP packets before enabling the relay. Not all devices containing DHCP
servers (for example, routers) support DHCP Relay functionality.
When assigning a DHCP Relay Agent IP address for the DHCP Relay, ensure
that the IP address you use does not conflict with devices on the network side of
the Access Gateway.
Although you cannot enable the DHCP relay and the DHCP service at the
same time, it is possible to “disable” both functions from the Command Line
Interface. In this case, a warning message informs you that no DHCP services
are available to subscribers.

ACCESS GATEWAY
Installing the Access Gateway 69
Sample Screen Response:
Configuration>dh
Enable/Disable IP Upsell [disabled ]:
Enable/Disable DHCP Relay [disabled ]:
Enable/Disable DHCP Server [enabled ]:
Enable/Disable Subnet-based DHCP Service [disabled
Enable/Disable Forwarded DHCP Clients [disabled ]:
IP Upsell Disabled
DHCP Relay Disabled
External DHCP Server IP 0.0.0.0
DHCP Relay Agent IP 0.0.0.0
DHCP Server Enabled
DHCP Server Subnet-based Disabled
Forwarded DHCP Clients Disabled
Server-IP Server-Netmask Start-IP End-IP Lease Type IPUp
208.11.0.4 255.255.0.0 208.11.0.5 208.11.0.7 20 PRIV NO
10.0.0.4 255.255.255.0 10.0.0.5 10.0.0.250 30 PRIV NO *
* Default IP Pool
DHCP IP Pools Configuration:
0 - Show IP Pools
1 - Add a new IP Pool
2 - Modify an IP Pool
3 - Remove an IP Pool
4 - Exit this menu
Select the DHCP Pool configuration mode [0]:
DHCP Options from RFC 2132
You can configure DHCP options as defined in RFC 2132. The configured options are sent to
subscribers who obtain their network configuration from the NSE via DHCP.
This capability only applies to the NSE’s DHCP Server function. There is no change to the
NSE’ s operation as a DHCP client.
The options are configurable on a per-pool basis. Different sets of options can be configured
for different pools.
A given DHCP option consists of an option code and a value. RFC 2132 details the various
available options, and the data type for each. The NSE will validate the data entered to ensure
that it is type-correct for the option code in question. If it is incorrect, the option is not
accepted.
Numerical integer values can be entered in decimal format, or hex format using a “0x” prefix.

ACCESS GATEWAY
70 Installing the Access Gateway
The following DHCP option codes are supported:
Disallowed options
: Some option codes are not allowed, for one of the following reasons:
Items that are already configured elsewhere as a separate DHCP pool or NSE
configuration parameter, and/or are derived from one that is. Includes options 1
(subnet mask), 3 (router), 6 (domain name server), 15 (domain name), 51 (lease time),
54 (server identifier), 58 (renewal time), 59 (rebinding time).
Items not valid in a DHCP offer or ACK message. Includes options 50 (requested IP
address), 55 (parameter request list), 56 (error message), 57 (maximum message size),
60 (vendor class identifier), 61 (client identifier).
Items generated automatically by the mechanism of DHCP message construction,
which carry no application information. Includes options 0 (pad), 52 (option
overload), 53 (DHCP message type), 255 (end).
Unrecognized options
: Options 62-63, 77-254 are unrecognized. Some of these codes are
legitimate and are defined in other RFCs, while others are not defined. These option codes are
not explicitly disallowed on the NSE, but the NSE is “unaware” of them – that is, it will make
no attempt to validate either the code or the data. It is the administrator’s responsibility to
ensure that the option codes and data entered are legitimate.
Option Description Option Code
Single IP address 16, 28, 32
List of one or more IP addresses 3-5, 7-11, 41-42, 44-45, 48-49, 65, 69-76
List of zero or more IP addresses 68
List of one or more pairs of IP addresses (or
address/mask pairs)
21, 33
32-bit unsigned integer value 2, 24, 35, 38
16-bit unsigned integer value 13, 22, 26
8-bit unsigned integer value 23, 37, 46
List of 1 or more 16-bit unsigned integer values 25
Single octet Boolean (value may be 1 or 0) 19-20, 27, 29-31, 34, 36, 39
Sequence of 1 or more octets 43
Ascii string of 1 or more printable characters 12, 14, 17-18, 40, 47, 64, 66-67

ACCESS GATEWAY
Installing the Access Gateway 71
The following screens illustrate adding additional DHCP options to a DHCP Pool.

ACCESS GATEWAY
72 Installing the Access Gateway
DHCP Dynamic Enable and Disable
Click Configuration->DHCP. Click the Server-IP and Enable this DHCP Pool. Note that
DHCP enable/disable is dynamic, no reboot required.
Click
Configuration->DHCP. A new column under existing DHCP Pools table for DHCP
pool enable is introduced. See box in Red below.

ACCESS GATEWAY
Installing the Access Gateway 73
Click Subscriber Administration->DHCP Leases. The DHCP leases Page displays all
the current DHCP leases on the NSE.
Setting the DNS Options
DNS allows subscribers to enter meaningful URLs into their browsers (instead of complicated
numeric IP addresses) by automatically converting the URLs into the correct IP addresses. Y ou

ACCESS GATEWAY
74 Installing the Access Gateway
can assign a primary, secondary, or tertiary (third) DNS server. The Access Gateway utilizes
whichever server is currently available.
Use the following procedure to set the DNS configuration optio ns.
1. Enter c (configuration) at the Access Gateway Menu. The Configuration menu appears.
2. Enter dn (dns) at the Configuration menu. The system displays the current domain (the
default is “nomadix”).
3. Enter a valid domain name (the Internet domain that DNS requests will utilize).
4. Enter the host name (the DNS name of the Access Gateway). The host name must not
contain any spaces.
After assigning the host name, the system requests IP addresses for the primary , secondary,
and tertiary DNS servers (the default for the DNS primary address is 0.0.0.2).
5. Enter the IP addresses for the DNS servers (located at the customer’s network operating
center where DNS requests are sent).
6. You must now reboot the system for your settings to take effect. Enter y (yes) to reboot the
Access Gateway
Sample Screen Response:
Configuration>dns
NOTE: If DHCP Client or PPPoE Client is enabled, the Primary and
Secondary DNS Server may not be configured, since the DHCP/PPPoE server
may provide those items. Furthermore, if DHCP Client is configured, the
Domain may not be configured.
Enter domain [nomadix.com ]:
Enter host name (no spaces) [usg ]:
Enter primary DNS [0.0.0.2 ]: 4.2.2.2
Enter secondary DNS [0.0.0.0 ]:
Enter tertiary DNS [0.0.0.0 ]:
Enter DNS Redirection Port [1029 ]:
Enter Proxy DNS Port [1028 ]:
The system must be rebooted to function properly.
You must configure DNS if you want to enter meaningful URLs instead of numeric
IP addresses into any of the Access Gateway’s configuration screens.
The secondary and tertiary DNS servers are only utilized if the primary DNS
server is unavailable.
ACCESS GATEWAY
Installing the Access Gateway 75
The DNS options have been established. DNS will now convert subscriber browser URLs
into the correct IP addresses automatically.
Archiving Your Configuration Settings
Once you have installed your Access Gateway and established the configuration settings, you
should write the settings to an archive file. If you ever experience problems with the system,
your archived settings can be restored at any time.
Refer to the following procedures:
“Exporting Configuration Settings to the Archive File {Export}” on page 252.
“Importing Configuration Settings from the Archive File {Import}” on page 257.
Installing the Nomadix Private MIB
The Nomadix Private Management Information Base (MIB) allows you to view and manage
SNMP objects on your Access Gateway. To use the MIB, you must obtain the appropriate
nomadix.mib file for your Access Gateway. This file is available in the Support area of the
Nomadix web site.
Obtaining the Management Information Base (MIB) file
1. Visit www.nomadix.com/support.
2. Scroll to “Gateway Documentation”.
3. Click “Latest Documentation”
4. Scroll to the group for your Access Gateway model.
5. Click the link to download the MIB file for your Access Gateway.

ACCESS GATEWAY
76 Installing the Access Gateway
Configuring the Management Information Base
1. Import the nomadix.mib file into your SNMP client manager.
2. Connect to the Access Gateway from a node on the network that is accessible via the
Access Gateway’s network port (Internet, LAN, etc.). Be sure to enable the SNMP
daemon on the Access Gateway (available on the Access Gateway’s CLI or Web
Management Interface, under the Configuration menu –
snmp).
3. All variables defined by Nomadix start with the following prefix:
iso.org.dod.internet.private.enterprises.nomadix
4. You should now be able to define queries and set the SNMP values on your Access
Gateway. If necessary, consult this User Guide or your SNMP client manager’s
documentation for further details.
We recommend that you change the predefined community strings in order to
maintain a secure environment for your Access Gateway.
Click to download the MIB file.

ACCESS GATEWAY
3
System Administration 77
System Administration
This section provides all the instructions and procedures necessary for system administrators to
manage the Access Gateway on the customer’s network (after a successful installation).
The system administration procedures in this section are organized as they are listed under their
respective Web Management Interface (WMI) menus:
“Configuration Menu” on page 80
“Network Info Menu” on page 179
“Port-Location Menu” on page 191
“Subscriber Administration Menu” on page 203
“Subscriber Interface Menu” on page 217
“System Menu” on page 250
Choosing a Remote Connection
Once installed and configured for the customer’s network, the Access Gateway can be
managed and administered remotely with any of the following interface options:
Using the Web Management Interface (WMI) - Provides a powerful and flexible Web
interface for network administrators.
Using an SNMP Manager - Allows remote “Windows” management using an SNMP
client manager (for example, HP OpenView). However, before you can use SNMP to
access the Access Gateway, you must set up the appropriate SNMP communities. For
more information, refer to “Managing the SNMP Communities {SNMP}” on
page 167.
Using a Telnet Client
Choose an interface connection, based on your preference.
Now that the Access Gateway has been installed and configured successfully, this
User Guide moves away from the Command Line Interface (CLI) and documents
the Access Gateway from the Web Management Interface (WMI) viewpoint.
To use any of the remote connections (Web, SNMP, or Telnet), the network
interface IP address for the Access Gateway must be established (you did this
during the installation process).

ACCESS GATEWAY
78 System Administration
Using the Web Management Interface (WMI)
The Web Management Interface (WMI) is a “graphical” version of the Command Line
Interface, comprised of HTML files. The HTML files are embedded in the Access Gateway
and are dynamically linked to the system’s functional command sets. You can access the WMI
from any Web browser.
To connect to the Web Management Interface, do the following:
1. Establish a connection to the Internet.
2. Open your Web browser.
3. Enter the network interface IP address of the Access Gateway (set up during the
installation process).
4. Log in as usual (supplying your user name and password).
To access any menu item from the WMI, click on the item you want. The corresponding work
screen then appears in the right side frame. From here you can control the features and settings
related to your selection. Although the appearance is very different from the Command Line
Interface, the information displayed to you is basically the same. The only difference between
the two interfaces is in the method used for making selections and applying your changes
(selections are checkable boxes, and applying your changes is achieved by pressing the
Submit
button). Pressing the
Reset button resets the screen to its previous state (clearing all your
changes without applying them).
Selecting the language of the Web Management Interface
You can click on Language Selection to change the language of the Web Management Interface
text. Currently English (U.S.) and Chinese (simplified) are provided.
Your browser preferences or Internet options should be set to compare loaded
pages with cached pages.

ACCESS GATEWAY
System Administration 79
Using an SNMP Manager
Once the SNMP communities are established, you can connect to the Access Gateway via the
Internet using an SNMP client manager (for example, HP OpenView). SNMP is the standard
protocol used in the Network Management (NM) system. This system contains two primary
elements:
Manager – The console (client) through which system administrators perform
network management functions.
Agent – An SNMP-compli ant devi ce which stor es data ab out its elf in a Manage ment
Information Base (MIB). The Access Gateway is an example of such a device.
The Access Gateway contains managed objects that directly relate to its current operational
state. These objects include hardware configuration parameters and performance statistics.
Managed objects are arranged into a virtual information database, called a Management
Information Base (MIB). SNMP enables managers and agents to communicate with each other
for the purpose of accessing these MIBs and retrieving data. See also, “Installing the Nomadix
Private MIB” on page 75.
The following example shows a (partial) SNMP screen response.
Using a Telnet Client
There are many Telnet clients that you can use to connect with the Access Gateway. Using
T elnet provides a simple terminal emulation that allows you to see and interact with the Access
Gateway’ s Command Line Interface (as if you were connected via the serial interface). As with
any remote connection, the network interface IP address for the Access Gateway must be
established (you did this during the installation process).

ACCESS GATEWAY
80 System Administration
Logging In
To access the Access Gateway’s Web Management Interface, use the Manager or Operator
login user name and password you defined during the installation process (refer to Assigning
Login User Names and Passwords).
About Your Product License
Some features included in this section will not be available to you unless you have purchased
the appropriate product license from Nomadix. In this case, the following statement will appear
either immediately below the section heading or when the feature is mentioned in the body
text:
Configuration Menu
Defining the AAA Services {AAA}
This procedure shows you how to set up the AAA (Authentication, Authorization, and
Accounting) service options. AAA Services are used by the Access Gateway to authenticate,
authorize, and subsequently bill subscribers for their use of the customer’s network. The
Access Gateway currently supports several AAA models which are discussed in “Subscriber
Management” on page 278.
1. From the Web Management Interface, click on Configuration, then AAA. The
Authentication Authorization and Accounting Settings screen appears:
User names and passwords are case-sensitive.
Your product license may not support this feature. You can upgrade your product
license at any time.

ACCESS GATEWAY
System Administration 81
2. Enable or disable AAA Services. If you enable AAA Services, go to Step 3, otherwise this
feature is disabled and you can exit the procedure.
3. Select a Logout IP address from the drop-down list. The list contains IP address that can
be used as the logout IP address. The default IP address is 1.1.1.1.
4. Enable or disable the XML Interface, as required.
XML is used by the Access Gateway’s subscriber management module for port location
and user administration. Enabling the XML interface allows the Access Gateway to accept
and process XML commands from an external source. XML commands are sent over the
network to the Access Gateway. The Access Gateway parses the query string, executes the
commands specified by the string, and returns data to the system that initiated the
command request.
5. If you enabled the XML Interface feature, enter the XML IP (server) address.

ACCESS GATEWAY
82 System Administration
6. Enable or disable Print Billing Command, as required. This feature enables NSE to
support Driverless Print servers. If this feature is enabled, you must enable the XML
interface and enter the IP address for the XML interface (Step 3 and Step 4). With Print
Billing enabled, print servers can bill subscribers’ rooms fo r printing their documents
without them having to install printers.
The DNS name print.server.com will internally resolve to the Configured Print Server
URL that is entered in the configuration. When subscribers are redirected to the Print
Server the NSE adds Parameters to that request, so that the Server is able to charge the
proper subscriber.
With these variables sent to the server it can now send the XML command to bill the users
properly.
Print Server IP needs to be entered as one of the XML server IP for the command to
successfully complete.
The XML command is:
<USG COMMAND="BILL_PRINT" IP_ADDR="">
<ROOM_NUM></ROOM_NUM>
<DOC_NAME></DOC_NAME>
<NUM_COPIES></NUM_COPIES>
<NUM_PAGES></NUM_PAGES>
<COST></COST>
<TIME_SUBMITTED></TIME_SUBMITTED>
</USG>
Subscribers could get to print.server.com by:
ICC button link
Printout in the hotel room
Link from the hotel’s HPR Page.
7. Enable or disable the AAA Passthrough Port feature, as required. System administrators
can set the Access Gateway to pass-through HTTPS traffic, in addition to standard port 80
traffic, without being redirected. When access to a non-HTTPS address (for example, a
Search Engine or News site) has been requested, the subscriber is then redirected as usual.
8. If AAA passthrough is enabled, enter the corresponding port number.
Your product license may not support this feature.
The port number must be different than 80, 2111, 1111, or 1112.

ACCESS GATEWAY
System Administration 83
9. Enable or disable the 802.1x Authentication Support feature, as required.
10. Enable or disable the Origin Server (OS) parameter encoding for Portal Page and EWS
feature, as required.
11. You can choose to Enable failover to Internal Web Server Authentication if Portal
Page/External Web Server is not reachable
by placing a check in that box.
12. Enable or disable Port Based Billing Policies.
The Port Location capabilities on the NSE have been enhanced. It is now possible to
define a policy on a port. The billing methods (RADIUS, Credit Card, PMS, L2TP
Tunneling) and the billing plans available on each port can now be individually
configured.
This ability allows for having different billing methods and billing plans on different ports
identified by VLANs or SNMP Por t Qu ery of the concentrator. A practical application of
this feature is to have a normal hotel room with a plan A that is $9.99 for a day with PMS
billing and have a meeting room with a plan of $14.99 an hour with Credit Card billing.
In order for the port-based polici es to work, you must enable Port Based Billin g Policies.
See also “Adding and Updating Port-Location Assignments {Add}” on page 192.
13. Enable or disable HTTPS Redirection.
The NSE responds to regular HTTP requests from pending subscribers with a redirection
to the login screen. The NSE does not respond to HTTPS requests from pending
subscribers (HTTP requests with a destination port = 443) with a redirect; this will result
in a timeout or invalid certificate warning.
Enabling
HTTPS Redirection adds a security exception to the user’ s browser to allow the
certificate received from the NSE to be always “valid.”
14. Enable or disable Facebook Login. If you enable Facebook login, you must provide a
Facebook App ID and Facebook App secret code. Instructions for creating these are
available from Facebook.
15. Depending on which authorization mode you choose, go to the following sub-sect ions in
this procedure:
Enabling AAA Services with the Internal Web Server – The IWS is “flashed” into the
system’s memory and the subscriber’s login page is served directly from the Access
Gateway.
Enabling AAA Services with an External W eb Server – In the EWS mode, the Access
Gateway redirects the subscriber’s login request to an external server (transparent to
Both AAA and RADIUS Authentication must be enabled for 802.1x
Authentication support.

ACCESS GATEWAY
84 System Administration
the subscriber). The login page served by the EWS reflects the “look and feel” of the
solution provider ’s network and presents more login options.
Enabling AAA Services with the Internal Web Server
You are here because you want to enable the AAA Services with the Access Gateway’s Internal
Web Server. The Access Gateway maintains an internal database of authorized subscribers,
based on their MAC (hardware address) and user name (if enabled). By referring to its database
record, also known as an authorization table, the Access Gateway instantly recognizes new
subscribers on the network.
You can configure the Access Gateway to handle new subscribers in various ways (see the
table on this page). With the IWS, you also have the option of enabling SSL support.
After selecting the Internal Web Server authorization mode, you have the option of enabling or
disabling the Usernames and New Subscribers features. These features work in conjunction
with each other to determine how new subscribers are handled. Refer to the following table:
1. Select the Internal Web Server tab.
Usernames New Subscribers System Response
Disabled Enabled Allows new subscribers to enter the system without
giving a user name and password.
Enabled
(optional)
Enabled Allows new subscribers or authen tication by their
user name and password.
Enabled Disabled New subscribers are not allowed. Only existing
subscribers are allowed after authenticating their
user name and password.
Disabled Disabled Y ou will not use this combination unless you want to
lock out all subscribers.

ACCESS GATEWAY
System Administration 85
2. Enable or disable the SSL Support feature, as required. If you enable SSL Support, you
must provide a valid
Certificate DNS Name.
For more information about setting up SSL, go to “Setting Up the SSL Feature” on
page 325.
SSL support allows for the creation of an end-to-end encrypted link between the Access
Gateway and its clients by enabling the Internal Web Server (IWS) to display pages under
a secure link—important when transmitting AAA information in a network.

ACCESS GATEWAY
86 System Administration
Adding SSL support to the Access Gateway requires service providers to obtain digital
certificates from VeriSign™ to create HTTPS pages. Instructions for obtaining certificates
are provided by Nomadix.
3. If you want to designate a portal page, you must enable the Portal Page feature, otherwise
leave this feature disabled.
4. If you enabled the Portal Page feature, provide the following supporting information:
Portal Page URL
Parameter Passing (enabled or disabled)
Parameter Signing (including Method, Parameters, and Shared Secret)
Portal XML POST URL
Portal XML Post Port
Support GIS Clients (enabled or disabled)
Block IWS Login Page (enabled or disabled)
5. Enable or disable the Usernames feature, as required (refer to the table in “Enabling AAA
Services with the Internal Web Server” on page 84).
Some subscribers may want additional account flexibility and security for their services
(for example, if they use more than one computer and their MAC address changes, or if
they move between port-locations). In this case, a subscriber can define a unique user
name and password which they can use from any machine or location (without being recharged). Subscribers who choose this option are prompted for their user name and
To enable SSL Support, your Access Gateway’s flash must include the server.pem,
cakey.pem, and cacert.pem certificate files (the “cacert.pem” file is provided
with your Access Gateway). For assistance, contact Technical Support.
The Portal Page IP or DNS address are added to the IP passthrough list
automatically.
See Redirection Parameter Signing for more information about parameter
signing.
GIS stands for Generic Interface Specification, a document written by iPass.
Enabling the Smart Client option in the Access Gateway automatically supports
all GIS compliant clients using the Internal Web Server. Enabling “Support for
GIS Clients” under the Portal Page feature means that the Access Gateway will
defer the management of the GIS clients to the Portal Page server.

ACCESS GATEWAY
System Administration 87
password whenever they try to access the Internet. Solution providers can charge a fee for
this service.
6. Enable or disable the New Subscribers feature (refer to the table in “Enabling AAA
Services with the Internal Web Server” on page 84).
7. If you enabled New Subscribers, enable or disable the Relogin After Timeout option.
8. You can now enable or disable the Credit Card Service. When this feature is enabled,
subscribers are prompted for their credit card information (for billing purposes). The
Access Gateway is configured to use Authorize.net. You will need to open a merchant
account with Authorize.net or Datacenter (Luxembourg) before this feature can be used.
Please contact Nomadix Technical Support for assistance. Refer to “Contact Information”
on page 349.
9. If you enabled the Credit Card Service, define which service you require (Authorize.net)
from the pull-down menu.
10. If the Credit Card Service is enabled, enter the information for the following fields:
Credit Card Server URL
Credit Card Server IP
Merchant ID (a valid ID issued by the credit card reconciliation service provider –
Authorize.net).
11. Check the Use NSE’s Hostname and DNS domain name box if you want the Hostname
and domain name to be sent to the Credit Card server instead of the local NSE IP address.
12. Enable or disable the SIM Compliant feature, as required. With this feature enabled, you
can change the transaction key at your discretion. To change the transaction key, simply
New Subscribers must be enabled before enabling the Credit Card and PMS
options.
All data communications between the Access Gateway and the credit card server
are encrypted by the SSL (Secure Sockets Layer) protocol. The Access Gateway
never “sees” subscriber credit card numbers.
DNS must be configured if you want to enter meaningful URLs instead of numeric
IP addresses into any of the Access Gateway’s configuration screens (for
example, the Credit Card Server URL in the following step).

ACCESS GATEWAY
88 System Administration
enter the key in the Change Transaction Key box, then re-enter the key in the Verify
Transaction Key
box.
13. Enable or disable Smart Client Support, as required.
14. You can assign a session idle timeout parameter for subscribers (see following note). To
assign an idle timeout, simply enter a numeric value (in seconds) in the Subscriber Idle
Timeout
box (the default is 1200).
15. If you enabled or disabled SSL Support on this screen, you must reboot the Access
Gateway. You can reboot the system by selection
System>Reboot in the Web
Management Interface.
16. Click on the Submit button to save your changes, or click on the Reset button if you want
to reset all the values to their previous state.
Enabling AAA Services with an External Web Server
You are here because you want to enable the AAA Services with an External Web Server
(EWS). In the EWS mode, the Access Gateway redirects the subscriber’s login request to an
external server.
1. Select the External Web Server tab.
The SIM Compliant option refers to Authorize.net's Simple Integration Method.
Subscriber Idle Timeout does not apply to RADIUS and Post Pay PMS
subscribers.
 Loading...
Loading...