Page 1

ESET Mail Security
Installation Manual and User Guide
Linux, BSD and Sol ari s
Page 2

Contents
1. Introduction
2. Terminology and abbreviations
3. Installation
4. Architecture Overview
5. Integration with Email Messaging System
5.4
6. Important ESET Mail Security mechanisms
..................................................................3
.........................................................................................3
Mai n functionality1.1
.........................................................................................3
Key features of the sys tem1.2
..................................................................5
..................................................................7
..................................................................8
..................................................................10
.........................................................................................11
Bi-directional email message scanning in MTA5.1
.........................................................................................11
Scanni ng of inbound email messages5.2
.........................................................................................11
Scanni ng of outbound emai l mess a ges5.3
Scanni ng of email messages downloaded from
.........................................................................................11
POP3/IMAP server
.........................................................................................12
Alternative methods of content filteri ng5.5
5.5.1
Scanning email mess ages in CommuniGa te Pro
................................................................................12
using esets_cgp
................................................................................13Scanning email mess ages using AMaViS5.5.2
..................................................................14
.........................................................................................14
Handle Object Policy6.1
.........................................................................................14
User Speci fic Configuration6.2
.........................................................................................15
Blacklist and Whi teli s t6.3
.........................................................................................15
Anti-Spam Control6.4
.........................................................................................16
Sampl es Submission System6.5
.........................................................................................17
Web Interface6.6
Remote Administration6.7
Logging6.8
................................................................................17License mana gement6.6.1
................................................................................18SMTP+Postfix configura tion exampl e6.6.2
................................................................................19Statis tics6.6.3
.........................................................................................19
................................................................................20Remote Administra tion usage example6.7.1
.........................................................................................22
ESET Mail Security
Copyright ©2011 by ESET, spol. s r. o.
ESET Mail Security was developed by ESET, spol. s r. o.
For more information visit www.eset.com.
All rights reserved. No part of this documentation may be reproduced,
stored in a retrieval sys tem or transmitted in any form or by any
mea ns , electroni c, mecha nical, photocopying, recording, scanning, or
otherwise without permis sion in writing from the author.
ESET, spol. s r. o. res erves the right to change any of the described
application softwa re without prior notice.
Custome r Care Worldwide: www.es et.eu/support
Custome r Care North Ameri ca : www.eset.com/support
7. ESET Security system update
8. Let us know
..................................................................23
.........................................................................................23
ESETS update util i ty7.1
.........................................................................................23
ESETS update process description7.2
.........................................................................................23
ESETS mirror http daemon7.3
..................................................................24
9. Appendix A. ESETS setup and
..................................................................25
configuration
.........................................................................................25
Setting ESETS for MTA Postfix9.1
.........................................................................................26
Setting ESETS for MTA Sendmail9.2
.........................................................................................26
Setting ESETS for MTA Qmai l9.3
.........................................................................................27
Setting ESETS for MTA Exim versi on 39.4
.........................................................................................28
Setting ESETS for MTA Exim versi on 49.5
.........................................................................................28
Setting ESETS for MTA ZMai l er9.6
.........................................................................................29
Setting ESETS for outbound emai l mess age scanning9.7
.........................................................................................29
Setting ESETS for s canning of POP3 communica tion9.8
.........................................................................................29
Setting ESETS for s canning of IMAP communica tion9.9
10. Appendix B. PHP License
..................................................................31
REV. 2011-02-08
Page 3

1. Introduction
Dear user, you have acquired ESET Mail Security - the premier security sys tem runni ng under the Linux, BSD and Solaris OS. As
you will soon fi nd out, ESET's state-of-the-art scanni ng engine has unsurpas s ed scanni ng speed and detection rates combi ned
with a very s mall footpri nt that makes i t the ideal choice for any Linux, BSD and Sol ari s OS server.
1.1 Main functionality
Post Office Protocol filter (POP3)
The POP3 fi l ter scans communication between POP3 cl i ents and servers for virus es.
Simple Mail Transfer Protocol filter (SMTP)
The SMTP filter scans communication between SMTP cl i ents and servers for virus es. In addi tion i t can al s o serve as a content
filter for the Postfix MTA.
Internet Message Access Protocol filter (IMAP)
The IMAP filter s cans communication between IMAP cl i ents and servers for virus es.
Sendmail content filter
Sendmail content filter accesses mail messages process ed by MTA Sendmail and scans them for vi ruses. It examines a nd
modifies content and meta-information of mess ages. If an infection cannot be removed from an emai l mess age, the message wil l
be rejected.
External filter plugin for Communigate Pro
The CGP module is an external filter pl ugin for CommuniGate Pro. It reads email filenames from stdin, then requests a s can by
ESETS daemon and fi nal l y returns a status. It examines (but does not modify) email content and bl ocks messages with
infiltrations in the emai l body.
PIPE module
The PIPE is a simple email scanner, that reads emai l from the standard (s tdi n) i nput, then requests a n ESETS daemon sca n. In
case content is accepted, it is submitted to the standa rd (stdout) output.
1.2 Key features of the system
Advanced engine algorithms
The ESET antivirus s canning engine al gorithms provide the highest detection ra te and the fastest scanning times.
Multi-processing
ESET Mai l Securi ty is developed to run on s i ngle- as well as multi-processor units.
Advanced Heuristics
ESET Mai l Securi ty includes unique advanced heuri s tics for Wi n32 worms, backdoor infections and other forms of malware.
Built-In features
Built-in archivers unpack archi ved objects without the need for any external programs.
Speed and efficiency
To increase the speed and efficiency of the system, its architecture is based on the running daemon (resident program) where
al l s canning requests a re sent.
Enhanced security
All executive daemons (except esets_dac) run under non-privi l eged user account to enhance security.
Selective configuration
The system supports selective confi gurati on bas ed on the user or cl i ent/server.
Multiple logging levels
Multiple logging l evels can be confi gured to get information about system activity and infiltrations.
3
Page 4

Web interface
Configuration, administration and license management are offered through an intuitive and us er-friendly Web interface.
Remote administration
The system supports ESET Remote Administration for management in large computer networks.
No external libraries
The ESET Mail Security installation does not require external l i brari es or programs except for LIBC.
User-specified notification
The system can be configured to notify s peci fi c users in the event of a detected infiltration or other important events.
Low system requirements
To run effici ently, ESET Mail Securi ty requires j ust 16MB of hard-disk space and 32MB of RAM. It runs smoothly under the 2.2.
x, 2.4.x and 2.6.x Linux OS kernel versions as well a s under 5.x, 6.x FreeBSD OS kernel versi ons.
Performance and scalability
From lower-powered, small office servers to enterprise-class I SP servers with thous ands of users, ESET Mail Security deli vers
the performance and scalability you expect from a UNIX ba s ed solution, in addi tion to the unequal ed s ecurity of ESET products.
4
Page 5

2. Terminology and abbreviations
In this s ection we wil l review the terms and abbreviations used in this document. Note that a boldface font is reserved for
product component names and also for newly defined terms a nd abbreviati ons . Terms a nd abbreviations defined i n thi s chapter
are expanded upon later in this document.
ESETS
ES E T S ecurity
operating sys tems. It is also the name (or i ts part) of the software package contai ni ng the products.
RSR
Abbreviation for ‘RedHat/Novell (SuSE) Ready’. Note that we also support RedHat Ready and Novell(SuSE) Ready va riations of
the product. The RSR package differs from the ‘standard’ Linux vers i on in that it meets the FHS (File-sys tem Hierarchy Standard
defined as a part of Linux Standard Bas e) criteria required by the RedHat Ready and Novell(SuSE) Ready certificate. This means
that the RSR package is ins talled as an add-on a pplication - the primary instal l a tion di rectory i s ‘/opt/eset/esets’.
ESETS daemon
The mai n ESETS system control and scanni ng daemon:
ESETS base directory
The directory where ESETS loadable modules contai ni ng the virus signature databas e are stored. The abbrevi ation
@ BA SED IR@
listed below:
Linux: /var/lib/esets
Linux RSR: /var/opt/eset/esets/lib
FreeBSD: /var/lib/esets
NetBSD: /var/lib/esets
Solaris: /var/opt/esets/lib
is a s tandard acronym for all securi ty products developed by ESET, spol . s r. o. for Linux, BSD and Sol a ris
esets_d aem on
wil l be used for future references to this di rectory. The
.
@ BA SED IR@
value for the following Operating Systems is
ESETS configuration directory
The directory where al l files related to the ESET Mai l Security configuration are stored. The abbrevi ation
used for future references to this directory. The
Linux: /etc/esets
Linux RSR: /etc/opt/eset/esets
FreeBSD: /usr/local/etc/esets
NetBSD: /usr/pkg/etc/esets
Solaris: /etc/opt/esets
@ ETCD IR@
value for the following Operating Systems is l i s ted below:
ESETS configuration file
Mai n ESET Mai l Security configuration file. The absolute path of the file is as fol l ows:
@ETCDIR@/esets.cfg
ESETS binary files directory
The directory where the relevant ESET Mai l Security binary files are stored. The abbrevi ation
references to this di rectory. The
Linux: /usr/bin
Linux RSR: /opt/eset/esets/bin
FreeBSD: /usr/local/bin
NetBSD: /usr/pkg/bin
Solaris: /opt/esets/bin
@ BINDIR @
value for the following Operating Systems is l i s ted below:
@ BINDIR @
ESETS system binary files directory
The directory where the relevant ESET Mai l Security system binary fi l es are stored. The abbreviation
for future references to this directory. The
@ SB INDIR @
value for the following Operating Systems is l i s ted below:
@ ETCD IR@
wil l be
wil l be used for future
@ SB INDIR @
wil l be used
Linux: /usr/sbin
Linux RSR: /opt/eset/esets/sbin
FreeBSD: /usr/local/sbin
NetBSD: /usr/pkg/sbin
Solaris: /opt/esets/sbin
5
Page 6

ESETS object files directory
The directory where the relevant ESET Mai l Security object files and l i brari es are stored. The abbreviation
used for future references to this directory. The
Linux: /usr/lib/esets
Linux RSR: /opt/eset/esets/lib
FreeBSD: /usr/local/lib/esets
NetBSD: /usr/pkg/lib/esets
Solaris: /opt/esets/lib
@ LIBD IR@
value for the following Operating Systems is l i s ted below:
@ LIBD IR@
wil l be
6
Page 7

3. Installation
After purchasing ESET Mail Security, you wil l receive your authorization data (username, pas s word and license key). This data
is necess ary for both identifyi ng you as our customer and a l l owing you to download updates for ESET Mail Securi ty. The
username/password data i s a l so required for downloading the ini tial instal l a tion package from our web si te. ESET Mai l Security
is distributed as a bi na ry file:
esets.i386.ext.bin
In the binary file shown above,
‘ex t’
is a Linux, BSD and Solari s OS distribution dependent suffi x, i.e., ‘deb’ for Debian, ‘rpm’ for
RedHat and SuSE, ‘tgz’ for other Linux OS di s tri butions, ‘fbs 5.tgz’ for FreeBSD 5.x, ‘fbs6.tgz’ for FreeBSD 6.x, ‘nbs4.tgz’ for NetBSD 4.
xx a nd ‘sol 10.pkg.gz‘ for Sol ari s 10.
Note that the Linux RSR binary fi l e format is:
esets-rsr.i386.rpm.bin
To install or upgra de the product, use the following command:
sh ./esets.i386.ext.bin
For the Linux RSR vari a tion of the product, use the command:
sh ./esets-rsr.i386.rpm.bin
to display the product’s User License Acceptance Agreement. Once you have confirmed the Acceptance Agreement, the
instal l ation packa ge is placed into the current working directory and relevant informati on regarding the package’s instal l ation,
un-instal l a tion or upgrade is di s pl ayed ons creen.
Once the package is i nstalled, you ca n verify that the main ESETS servi ce is runni ng by using the following command:
Linux OS:
ps -C esets_daemon
BSD OS:
ps -ax | grep esets_daemon
Solaris:
ps -A | grep esets_daemon
After pressing ENTER, you shoul d s ee the following (or simil ar) message:
PID TTY TIME CMD
2226 ? 00:00:00 esets_daemon
2229 ? 00:00:00 esets_daemon
At least two ESETS daemon processes are running in the background. The first PID represents the process and threads manager
of the sys tem. The other represents the ESETS scanning process.
7
Page 8
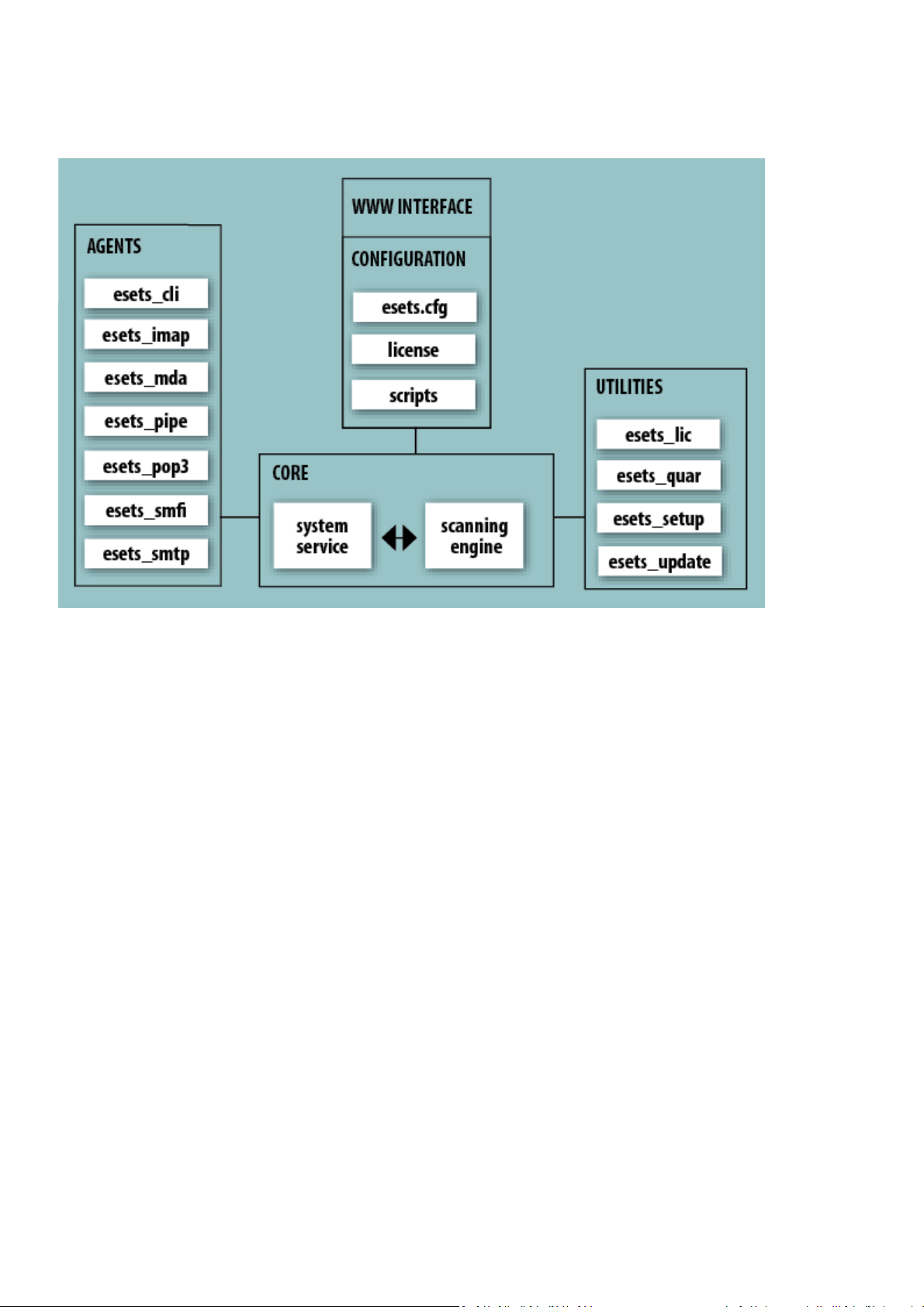
4. Architecture Overview
Once ESET Mail Security is successful l y i nstalled, you shoul d become famil i a r with i ts architecture.
Figure 4-1. Structure of ESET Mail Security.
The structure of ESET Mail Securi ty i s s hown i n Figure 4-1. The system is compri s ed of the following parts:
CORE
The Core of ESET Mai l Securi ty is the ESETS daemon (esets_daemon). The daemon uses ESETS API l i brary l i besets.so and ESETS
loading modules em00X_xx.dat to provide base sys tem tas ks s uch as scanni ng, maintenance of the agent daemon processes,
maintenance of the samples submission s ys tem, logging, notification, etc. Please refer to the
details.
AGENTS
The purpose of ESETS agent modules is to integrate ESETS with the Linux, BSD and Solari s Server envi ronment.
UTILITIES
The utility modules provi de simple and effective management of the system. They are respons i bl e for relevant system tasks
such a s l i cense mana gement, quarantine management, system setup and update.
CONFIGURATION
Proper configuration is the most important aspect of a smooth-running securi ty system - the remainder of thi s chapter is
dedicated to expl aining all related components. A thorough understandi ng of the
this fi l e contai ns i nformation essential to the confi guration of ESET Mail Securi ty.
After the product is successful l y i nstalled, al l i ts configuration components are stored in the ESETS confi guration directory.
The directory consists of the foll owi ng fi l es:
@ETCDIR@/esets.cfg
This i s the most important configuration file, as i t controls all major as pects of the product‘s functional i ty. The esets.cfg fi l e is
made up of s everal sections, each of which contai ns various pa rameters. The fil e contai ns one globa l and s everal “agent“
sections, with all section names enclosed in square brackets. Parameters in the global s ecti on a re used to define confi guration
options for the ESETS daemon as well as default values for the ESETS scanning engine confi guration. Parameters i n agent sections
are used to define configuration options of modul es used to intercept various data fl ow types in the computer and/or its
neighborhood, and prepare it for s canning. Note that in addi tion to the various parameters us ed for system confi gurati on, there
are al s o rules governing the organization of the file. For detai l ed information on the most effective way to orga ni ze this file,
esets.cfg
esets_d aem on (8 )
file is also hi ghl y recommended, as
man pa ge for
8
Page 9

please refer to the
esets.cfg (5 )
and
esets_d aem on (8 )
man pa ges, as well a s relevant agents‘ man pages.
@ETCDIR@/certs
This directory is used to store the certificates used by the ESETS web interface for authentication. Pleas e see the
esets_w ww i(8 )
man pa ge for detai l s .
@ETCDIR@/license
This directory is used to store the product(s) license key(s) you have acquired from your vendor. Note that the ESETS daemon
wil l check only this directory for a valid l i cense key, unless the
‘licen se_d ir’
parameter in the ESETS confi guration file is redefined.
@ETCDIR@/scripts/license_warning_script
If enabled by the ESETS configuration file parameter
‘licen se_w a rn _en ab led ’
, this s cri pt will be executed 30 days (once per day)
before product license expiration, sending an emai l notification about the expi rati on s tatus to the system admini s tra tor.
@ETCDIR@/scripts/daemon_notification_script
If enabled by the ESETS configuration file parameter
‘ex ec_scrip t’
, this s cri pt is executed in the event of a detected infi l tra tion
by the antivi rus system. It is used to send email noti fi cation a bout the event to the system administrator.
9
Page 10
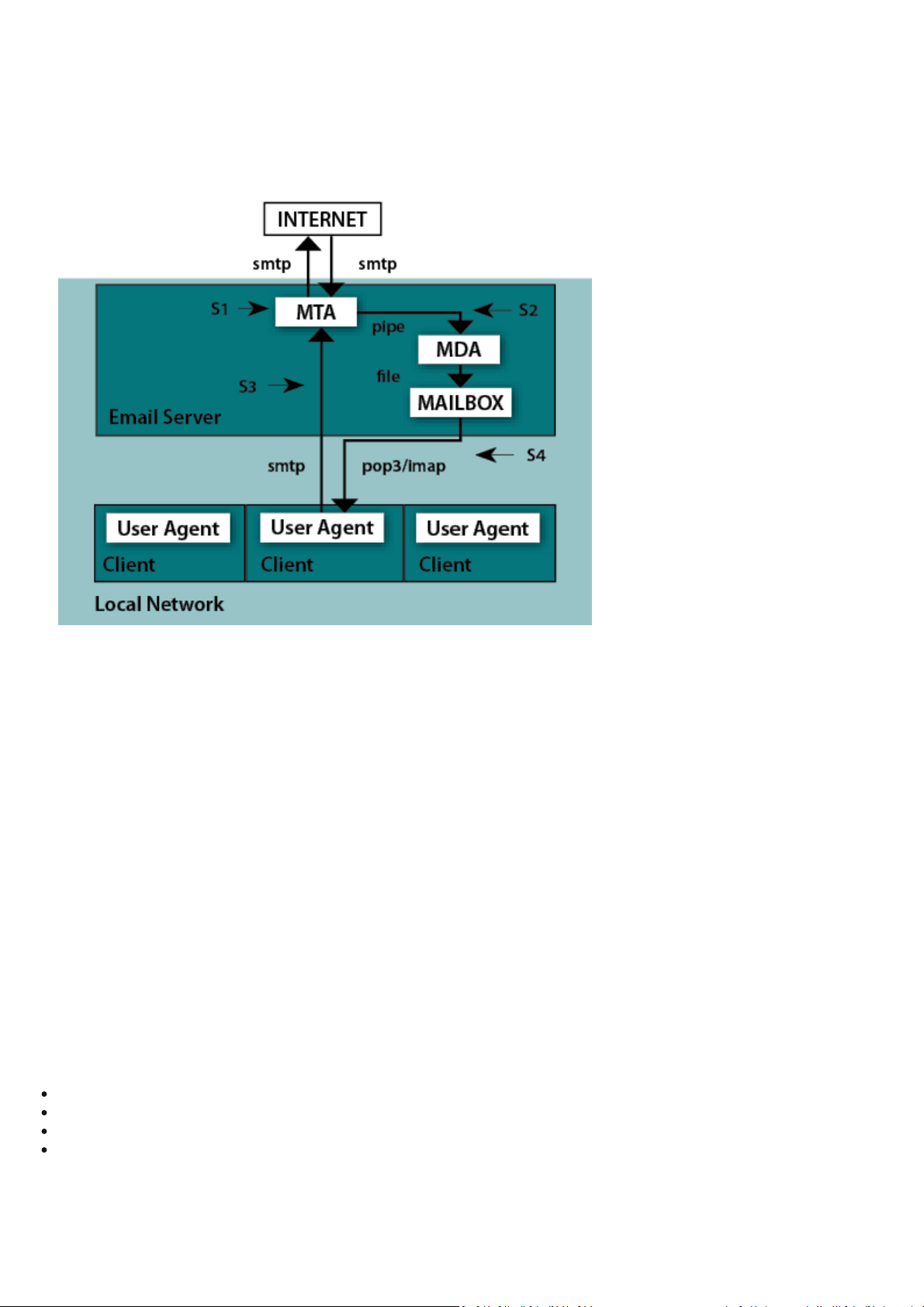
5. Integration with Email Messaging System
This chapter descri bes the integration of ESET Mail Security with a vari ety of known emai l mess aging systems. It is extremely
important to understand the basic princi ples of a n emai l mess aging system (see figure 5-1) and how ESET Mail Security
integrates with it.
Figure 5-1. Scheme of UNIX OS email messaging system.
MTA - Mail Transport Agent
A program (e.g., sendmail, postfix, qmail, exim, etc.) that enables the transfer of email messages between local and remote
domai ns .
MDA - Mail Delivery Agent
A program (e.g., maildrop, procmai l , deliver, loca l .mai l , etc.) that enables the deli very of loca l l y address ed email messages
into particul a r mailboxes.
MUA - Mail User Agent
A program (e.g., Micros oft Outlook, Mozilla Thunderbird, Eudora, etc.) that provi des access to and management of email
messages, such as reading, compos i ng, printing, etc.
MAILBOX
A fil e or file structure on a disk servi ng as the storage space for emai l mess a ges.
The email server receives data communication using SMTP (Simple Mail Transfer Protocol ) communication. The received
message is transferred by MTA either to another remote email messagi ng s ys tem or is delivered using local MDA into a
particul ar MAILBOX. In most ca ses, each l ocal network user owns a MAILBOX loca ted on the server. Note that it is the
responsibility of the user’s l ocal MUA to provide the function of downl oadi ng a nd correctly interpreting the message at the
user’s computer. When retrieving data from MAILBOX, the MUA typical l y us es POP3 (Post Office Protocol ) or IMAP (Internet
Message Access Protocol ) to communicate with the MTA. The SMTP protocol i s used to send data to the Internet.
The ESETS operating princi ple is based on data communication interception and scanning at the various phas es of its transfer.
The interception l ocations a re marked in fi gure 5-1 by symbols S1, S2, S3 a nd S4.
S1 - Bi -di rectional email message scanni ng, i .e. content fil tering in MTA.
S2 - Scanning of i nbound emai l mess ages, i.e. mess ages with a target address which i s l ocated inside the local domai n.
S3 - Scanning of outbound email messages, i.e. messages bound to a remote Internet domai n.
S4 - Scanning of emai l mess ages being downl oa ded from POP3/IMAP server.
The remai nder of this chapter reviews methods for i ntegrating ESETS with a va riety of supported messagi ng s ys tems.
10
Page 11

5.1 Bi-directional email message scanning in MTA
Bi-directional email message scanning mode al l ows the user to s can inbound email messages as well as outbound, us i ng the
same implementation al gorithm. The bi-directiona l content filter method i s MTA dependent. ESET Mail Security comes with five
content filters that are built for the most common MTA programs, such as MTA Sendmai l , Postfi x, Exi m, QMail and ZMai l er.
Check that your MTA is properl y confi gured and running. Then, configure ESET Mail Securi ty for bi -di rectional emai l message
scanni ng by running the foll owi ng s cript:
/usr/sbin/esets_setup
Select MTA and content fil ter instal l options. The ESETS module being used is also di s pl a yed.
Note that the installer backs up all modified confi guration fi l es and can display every command that it wil l execute after your
approva l . It can also be used for uni nstalling. Detailed steps for a l l poss i bl e scenari os are described in appendix A of this
documentation.
5.2 Scanning of inbound email messages
Inbound emai l mess age scanning i s performed duri ng mess age trans fer between MTA and MDA. Incoming emai l s a re
intercepted by the
in figure 5-1, virus s canning ca n be enabled by setting the proper configuration of MTA and the
Securi ty supports most common MTA programs, such a s MTA Sendmail, Postfix, Exim, QMail and ZMailer. ESETS supports any
MDA. In particul a r, the following MDAs were tested: procmai l , maildrop, deliver and l ocal.mail.
Check that your MTA is properl y confi gured using the original MDA and that the MTA is running. Then confi gure ESET Mai l
Securi ty for inbound email message sca nning by running the following script:
esets_m d a
module, scanned by the ESETS daemon and delivered to MAILBOX using the original MDA. As s hown
esets_m d a
module. ESET Mail
/usr/sbin/esets_setup
Select MDA and inbound install options . The ESETS module used i s also di s pl ayed.
Note that the installer backs up all modified confi guration fi l es and can display every command that it wil l execute after your
approva l . Als o use it for uninstal l . Detai l ed steps for all possible scenarios are descri bed in the appendix A of this
documentation.
5.3 Scanning of outbound email messages
Outbound email message scanni ng is performed duri ng transfer of email messages between the local MUA and the MTA.
Configure ESET Mail Security for outbound email message scanning by runni ng the following script:
/usr/sbin/esets_setup
Select the SMTP install option. This wil l set the
packets. Check the newly a dded firewall rule to see if any changes are necessary.
Note that the installer backs up all modified confi guration fi l es and can display every command that it wil l execute after your
approva l . It can also be used for uni nstalling. Detailed steps for a l l poss i bl e scenari os are described in appendix A of this
documentation.
esets_sm tp
module to li s ten on a predefined port and redirect applicabl e IP
5.4 Scanning of email messages downloaded from POP3/IMAP server
POP3/IMAP mess ages s canning is performed during message trans fer between MAILBOX and MUA. All emai l s requested by
POP3/IMAP clients are intercepted by the
infiltrations. ESET Mai l Security supports most common MUA programs, s uch as Microsoft Outlook, Evolution, Mozilla
Thunderbi rd and others. Note that there is restri ction in ESET Mail Security functionality when emai l s downloaded by Mozilla
Thunderbi rd using IMAP communication protocol . An email in this case is requested and downloaded part by part and built
directly by Mozil l a Thunderbird. For this reas on it is not possi ble to write proper information about the infi l tra tions found into
the header and body of the emai l and thus the functional i ty i s deactivated for this MUA.
esets_p op 3
(or
esets_im a p
) agent module and scanned by the ESETS daemon for
To confi gure ESET Mai l Security for scanning of emai l mess ages downloaded from POP3 or IMAP server, run the following
scri pt:
/usr/sbin/esets_setup
Select the POP3 or I MAP instal l option. This will set the given ESETS module to li sten on a predefined port and redirect
applicabl e IP packets. Check the newly added firewall rule to see if any changes are necessary.
Note that the installer backs up all modified confi guration fi l es and can display every command that it wil l execute after your
11
Page 12

approva l . It can also be used for uni nstalling. Detailed steps for a l l poss i bl e scenari os are described in appendix A of this
documentation.
5.5 Alternative methods of content filtering
5.5.1 Scanning email messages in CommuniGate Pro using esets_cgp
CommuniGate Pro i s the powerful and reliable Unifi ed Communica tions server and
virus a nd a nti-spam filtering).
esets_cg p
is used for content fil tering (anti-
Es ets_cg p
messages and denies ESETS access to clean or delete infected emai l attachments. As a result, the ESETS footnote with log and
status dependent header fields will not be written into the emai l message. Also,
information. Thus, us er s pecific configura tions are unavailable and advanced mai l ha ndling features (accept, defer, dis card,
reject) are li mited.
Integrating the antivirus Plugin with CommuniGate Pro
Pleas e see the Virus Scan section of the CommuniGate Pro manual .
Open the
create new filter with fol l owed values:
Figure 5-2. Setting of Content Filtering.
only allows scanni ng of incoming email messages.
Gen er a l
page in the
Set t ing s
section of the WebAdmin Interface and click the
Es ets_cg p
does not al l ow modi fi cation of scanned email
esets_cg p
does not provi de mail sender/recipient
Helper s
link. In panel
Co n t ent Filt er in g
Next, open the Mail page in the
12
Set t ing s
section of the WebAdmin Interface, click the
Rules
link and add a new rul e as follows:
Page 13

Figure 5-3. Rule Settings.
5.5.2 Scanning email messages using AMaViS
AMaViS (A Mail Virus Scanner) is a tool that interfaces your MTA with several a ntivi rus scanners . It supports vari ous MTAs
and comes in three branches:
with ESET Mail Security by using
functi ona l i ty method is described. AMaViS does not allow modifica tion of s canned email messages and denies ESETS access to
cl ean or delete infected emai l a ttachments. As a result, the ESETS footnote with l og and s tatus dependent header fi elds will not be
written into the emai l mess age. Also, AMaViS does not provi de mai l s ender/recipient information. Thus, user speci fi c
confi gurations are unavai l a bl e and advanced mail handling features (accept, defer, disca rd, reject) are limited for
Lastly, AMaViS only scans fil es, it cannot use the ESETS anti-s pa m engine.
Taki ng i nto account these drawbacks, content fil tering us i ng AMaViS i s recommended only i f the system admini strator does
not require the features discus s ed above.
amavisd-new configuration
To install the product with
Next, confi gure the product with the newly instal l ed
replace the claus e for ‘ESET Software ESETS - Cli ent/Server Versi on’ in the fil e ‘amavisd.conf’ with the following one:
### http://www.eset.com/
['ESET Software ESETS Command Line Interface',
'@BINDIR@/esets_cli', '--subdir {}',
[0], [1, 2, 3], qr/virus="([^"]+)"/ ],
You may need to install addi tional Perl modul es Archive-Tar, Archive-Zip, BerkeleyDB, Compress-Zlib, Convert-TNEF, ConvertUUlib, IO-stringy, MailTools, MIME-Bas e64, MIME-tools , Net-Server and Uni x-Syslog from:
www.cpan.org/modul es
a ma vis, a ma visd
esets_cli
a ma visd-n ew
. Before expl aini ng the AMaViS confi gurations, the impact of the ESET Mail Security
, unpack a nd i nstall the source amavi s d-new-2.x.y.tgz in your instal l ation di rectory.
and
a ma visd-n ew
a ma visd-n ew
. Only the amavisd-new branch is supported. AMaViS cooperates
esets_cli
.
. To do this, delete the clause for ‘ESET Software ESETS’ and then
The procedure to ins tall is as follows:
perl Makefile.PL; make; make install
After configuration, pleas e follow the recommendations for confi guring
Amavisd-new directory according your mai l s erver.
a ma visd-n ew
in the README.mta loca ted in the
13
Page 14

6. Important ESET Mail Security mechanisms
6.1 Handle Object Policy
The Handl e Obj ect Pol i cy (see figure 6-1) mechanism provi des fi l tering of scanned objects ba sed on their status . This
functi ona l i ty is based on the following confi guration options:
action_av
action_av_infected
action_av_notscanned
action_av_deleted
For detai l ed i nformation on these options, please refer to the
Figure 6-1. Scheme of Handle Object Policy mechanism.
esets.cfg (5 )
man pa ge.
Every object process ed is firs t handl ed according to the configuration of the
(or
‘d efer’, ‘d isca rd’, ‘reject’
scanned for virus i nfiltrations , and i f the
confi guration options
evaluate handl i ng of the object. If an
accepted. Otherwise, the object is blocked.
) the object i s accepted (or deferred, discarded, rejected). If the option is set to
‘a ctio n _a v_in f ected
‘a ccep t’
‘a v_clea n_m od e
’,
‘a ctio n _a v_no tsca nn ed
action has been taken as a resul t of these three action options, the object i s
’ option is set to
’ and
‘a ctio n _a v_deleted
‘a ctio n _a v‘
‘yes
’, the object is al s o cleaned. In addition, the
option. If this option is set to
‘sca n’
the object is
’ are taken into account to further
‘a ccep t’
6.2 User Specific Configuration
The purpose of the User Speci fi c Confi gurati on mechani s m is to provide a hi gher degree of customizati on a nd functi ona l i ty. It
al l ows the sytem admini s trator to define ESETS antivirus scanner parameters bas ed on the user who i s access i ng fi l e system
objects.
A detai l ed description of this functional i ty can be found i n the
short example of a us er-s peci fi c configuration.
14
esets.cfg (5 )
man pa ge; in thi s section we wil l provi de onl y a
Page 15

Here, the
esets_sm tp
module is used as a content filter for MTA Postfi x. The functional i ty of thi s modul e is based on the
section in the ESETS confi guration file (esets.cfg). See below:
[smtp]
agent_enabled = yes
listen_addr = "localhost"
listen_port = 2526
server_addr = "localhost"
server_port = 2525
action_av = "scan"
[smt p ]
To provi de individual parameter settings, define a
the indi vidual setting wil l be stored. In the example below, we create a reference to the speci a l configuration fi l e
esets_sm tp _spec.cf g ’
[smtp]
agent_enabled = yes
listen_addr = "localhost"
listen_port = 2526
server_addr = "localhost"
server_port = 2525
action_av = "scan"
user_config = "esets_smtp_spec.cfg"
, which is located in the ESETS confi guration directory. See below:
Once the special confi guration file is referenced from withi n the
ESETS configuration directory and add the appropriate indi vidual settings. The
[rcptuser@rcptdomain.com]
action_av = "reject"
‘u ser_co n fig ’
parameter with the path to the special configuration file where
‘
[smt p ]
section, create the
‘es ets_sm tp_sp ec.cfg ’
‘es ets_sm tp_sp ec.cfg ’
file should look l i ke this:
file in the
Note that the section header identifies the recipi ent for whi ch the individual settings have been created, and the section body
contains indi vi dual parameters for this reci pient. This confi guration wil l al l ow all other us ers attempting to access the filesystem to be processed normally. All file system objects access ed by other users wil l be scanned for infi l tra tions, except for the
user rcptuser@rcptdomai n.com, whose access will be rejected (bl ocked).
6.3 Blacklist and Whitelist
In the foll owing example we demonstrate blacklist and whi telist creation for the
confi guration. Note that the configuration described in the previous section is used for this purpos e.
esets_sm tp
content filter for MTA Postfi x
To create a blackl i s t used by
‘es ets_sm tp_sp ec.cfg ’
[black-list]
action_av = "reject"
, introduced in the previous section. See below:
esets_sm tp
, create the following group s ection within the special confi guration file
Next, add the SMTP server to the ‘bla ck-list’ group. To do this, the foll owing speci al section must be created:
[|sndrname1@sndrdomain1.com]
parent_id = "black-list"
In the example above,
messages sent from this address will now be rejected. When creati ng the ‘white-list’ used by
the foll owi ng group section in the special confi guration file
[white-list]
action_av = "accept"
action_as = "accept"
‘snd rna me1 @ sn drd om a in 1 .co m ’
is the email address of the sender added to the ‘black-list’. All emai l
‘es ets_sm tp_sp ec.cfg ’
esets_sm tp
. See below:
, it i s necessary to create
Adding the sender’s emai l a ddress to the list is s elf-explanatory.
The ‘|’ character is placed in front of the header name of the special s ecti on for the sender a ddress a nd is not placed there for
the recipient address. For information regarding the special header name syntax, refer to the man page of the appropri a te ESETS
agent module. For
esets_sm tp
, refer to the
esets_sm tp (1 )
man pa ge.
6.4 Anti-Spam Control
The anti-spam sys tem filters spam mess ages, using dynamic evaluation of the data flow of the email deli very process .
To eliminate spam, ESET Mail Security uses the anti-spam control mechani s m. This mecha ni s m ca n be enabled using the
‘a ctio n _a s’
parameter. For a ful l description of the parameter refer to the
esets.cfg (5 )
man pa ge. Note that anti-s pa m scanni ng can
be used only for emai l objects. Thus, this functional i ty is relevant only for the following modules: esets_imap, esets_mda,
esets_pipe, esets_pop3, esets_smtp and esets_smfi.
15
Page 16

Once anti-spam is enabled in any of the configuration sections, the anti-spam sca nning engine ini tializes during the main
scanni ng da emon start-up. During this process , appropriate anti -spam support modules are loaded from the anti-spam cache
directory.
To define the period (in minutes), after which ESETS wil l check for avai l a bl e anti-spam modul e updates, edit the entry shown
below i n the ESETS configura tion fi l e. If you do not set the value for this para meter, ESETS will not regularly update its anti-spam
database:
as_update_period = 60
Anti-spam functionality ca n a l so be configured us i ng the following configuration file:
@ETCDIR@/anti-spam/spamcatcher.conf
NOTE:
Spa mCa tcher
is a tool for spam detection. It tracks al l emai l communication on i ts own server and moni tors mess a ges
rejected by us ers . It evaluates this and vari ous other data to determine which email i s l i kely to contain s pam and sends users a
probabi l i ty s core for every messa ge they receive. It allows you to create your own rul es for i dentifyi ng and blacklisting spam.
Hundreds of rules can be used to evaluate spam score and bl ock the incoming s pam.
The @ETCDIR@/anti-spam/ directory contains a number of di fferent configurations stored in fi l es, that can be used to
cus tomize the anti-spam engine. If you wish to start us i ng a pa rticular configuration, replace the defaul t anti-s pam
confi guration stored in
‘spa mca tcher.co nf’
with any of the available configuration fi l es and reload the ESETS daemon.
spamcatcher.conf
Is a default confi guration file, that contains optimal configura tion recommended for typi cal server environment.
To display differences between any of the files i n the anti-spam di rectory, use the diff command. For example, if you wi sh to
compare the spamcatcher.conf and the spamcatcher.conf.accurate files use the following command:
diff spamcatcher.conf spamcatcher.conf.accurate
spamcatcher.conf.accurate
Bayesian Word Token anal ysi s (i .e. spam fi l tering using Bayesi an Analysis) is enabl ed. It improves accuracy, but uses more
memory and can therefore take sl i ghtl y more time to finish than other methods.
The limit of the number of domai ns queried against the DNS Block List server (DNSBL) is increas ed (the
‘d n sbl_m a x_d om ain s’
option). DNSBLs are most often used to publish addresses of computers or networks l i nked to spamming.
Sen der P olicy Fra mew o rk (S D K)
The value of the
‘spa m_th resh old ’
with l i ve DNS queries wil l be performed.
parameter is increased. Messages with spam scores equal to or higher than this val ue will
be rejected.
The
Spa mCo m piler
version 4 is enabl ed.
spamcatcher.conf.fast
The number of domai ns queried against the DNS Block List server is reduced.
The option
‘ta rg et_thro u gh p ut’
al l owing you to specify throughput in messages per s econd is enabl ed.
Cpu us age duri ng rule file updates is reduced by increasing the si ze of on-di s k cache fi l es.
TTL's (Time to li ve) for internal DNS and LiveFeed caches are enabled.
spamcatcher.conf.no_livefeed
The
‘liv efeed’
option speci fi es which s erver i s queried for LiveFeed requests. This option is di sabled in this configuration file.
The internal ca che for DNS requests i s di s abl ed.
6.5 Samples Submission System
The Samples submission s ys tem is an intell i gent
detected by advanced heuri s tics a nd deli vers them to the samples submis s i on system server. All virus sa mples coll ected by the
sample submiss i on system wil l be processed by the ESET virus laboratory and if necessary, added to the ESET virus signature
database.
NOTE: Accordi ng to our license agreement, by enabling sampl e submissi on system you are agreeing to allow the computer
and/or platform on which the esets_daemon is i ns talled to collect data (which may i nclude personal information about you
and/or the user of the computer) and samples of newly detected virus es or other threats and send them to our virus l ab. This
feature is turned off by defaul t. All i nformati on col l ected wil l be used onl y to analyze new threats and wi l l not be used for any
other purpose.
In order to activate the Samples Submission System, the samples submission system cache must be initia l i zed. This can be
achieved by enabl i ng the
‘sa m p les_en a bled’
option in the
deli very of samples to the ESET virus labora tory servers, the parameter
16
Th rea tS ense.Net
[g loba l]
section of the ESETS confi guration file. To allow for the actual
technology that collects infected objects which have been
‘sa m p les_send _p eriod ’
must also be specified in the same
Page 17
section.
In addition, users can choose to provi de the ESET virus l aboratory team with supplementary i nformation using the
‘sa m p les_p ro v id er_ma il’
and/or
‘sa m p les_p ro v id er_co u ntry’
configuration options. The information collected using these options
wil l a ssist in providing the ESET team with an overvi ew about a given infi l tration which may be spreading over the Internet.
For more information on the Samples Submis sion System, refer to the
esets_d aem on (8 )
man pa ge.
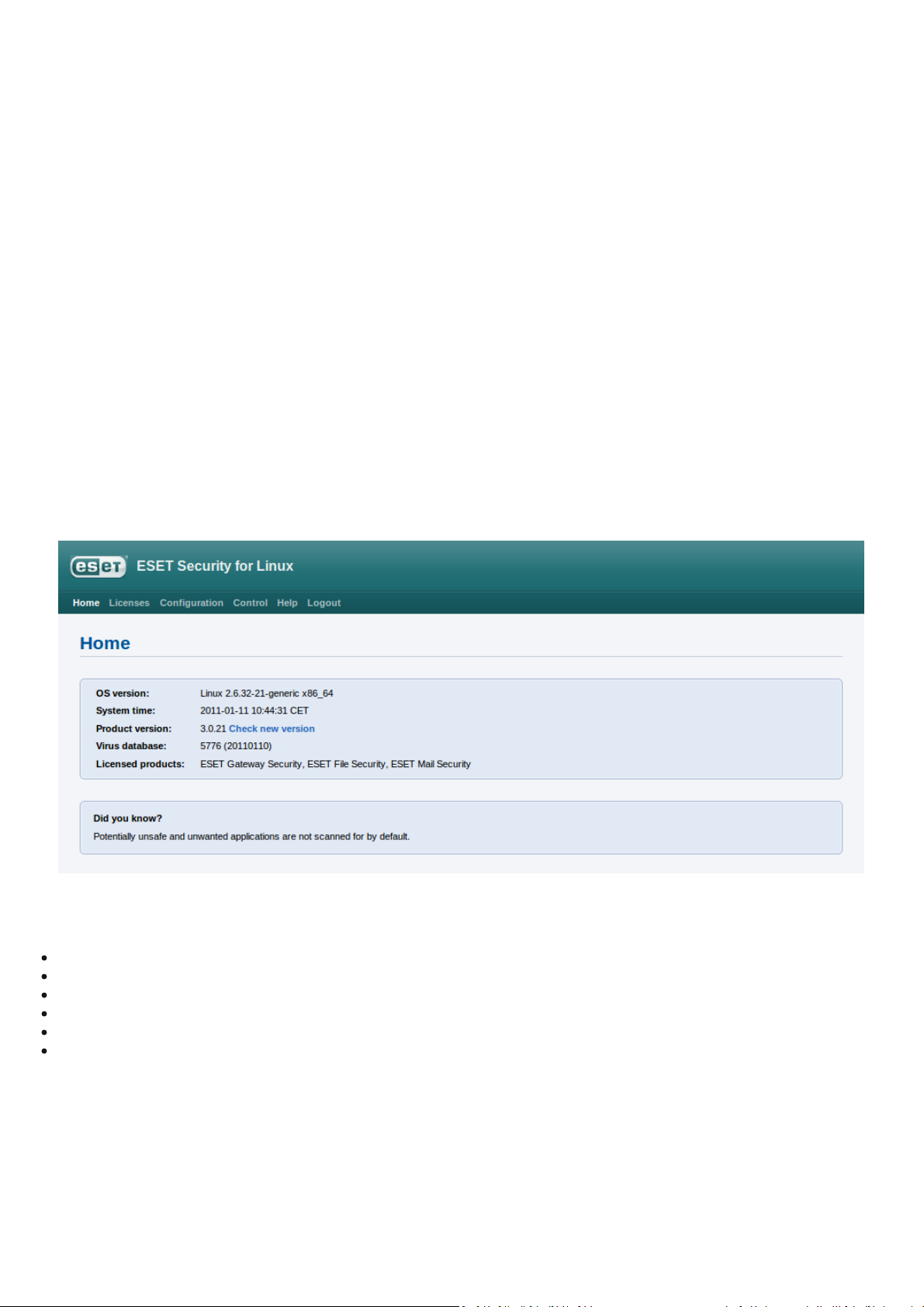
6.6 Web Interface
The Web Interface al l ows us er-friendly configuration, administration and l i cense management of ESET Security systems. This
module is a separate agent and must be expli citly enabl ed. To qui ckly configure the
the ESETS configuration fi l e and restart the ESETS daemon:
[wwwi]
agent_enabled = yes
listen_addr = address
listen_port = port
username = name
password = pass
Replace the text in ital i cs with your own val ues and di rect your browser to
‘u sern a me/p a ssw o rd’
found on the
esets_w ww i(1 )
. Basic usage instructions can be found on the help page and technica l detai l s a bout
man pa ge.
The web interface allows you to remotely access the ESETS daemon and deploy it easily. This powerful utility makes i t eas y to
read and write configuration va l ues.
Figure 6-1. ESET Security for Linux - Home screen.
W eb In terfa ce
‘h ttp s ://a dd ress :p ort’
, set the foll owing options i n
(note the https). Login with
esets_w ww i
can be
The web interface window of ESET Mai l Security is divi ded into two main s ections. The primary window, that serves to di s play
the contents of the selected menu option and the mai n menu. This hori zontal bar on the top lets you navigate between the
following mai n options:
Hom e
- provides bas i c system and ESET product information
L icen ses
Co n fig ura tion
Co n t ro l
Help
L o g out
- is a license management utility, see the foll owing chapter for mode details
- you can cha nge the ESET Mail Security system confi gurati on here
- allows you to run si mpl e tas ks and vi ew global statistics about objects process ed by esets_daemon
- provides detai l ed us age instructions for the ESET Mai l Security web interface
- use to end your current sessi on
6.6.1 License management
You can upl oad a new license using the Web interface, as shown in Figure 6-2.
If you want to dis pl a y l i censes in the cons ol e, use the following command:
/usr/sbin/esets_lic --list
If you want to import new license fil es, use the following command:
/usr/sbin/esets_lic --import *.lic
17
Page 18

Figure 6-2. ESET Licenses.
You can enable the license notification option i n the
Glo b a l
section options. If enabled, this functionality will notify you 30
days pri or to your license expiration.
NOTE: If you ha ve a fully functional ESET File/Gateway Security for Linux, BSD and Solaris instal l ation and you wis h to expa nd
it by adding ESET Mail Securi ty, you wil l need to set your new userna me and pas s word for ESET Mai l Security either i n the ESETS
confi guration file, or in the Web interface. This will prevent possible is s ues with updates in ESETS.
6.6.2 SMTP+Postfix configuration example
ESETS can be configured i n two ways. In this example we will demonstrate how to use both when configuring the SMTP modul e,
leaving you the choice of your preferred confi guration method:
Usi ng the ESETS configuration file:
[smtp]
agent_enabled = yes
listen_addr = "localhost"
listen_port = 2526
server_addr = "localhost"
server_port = 2525
Usi ng the web interface:
Figure 6-3. ESETS - Configuration > SMTP Agent.
Always remember to sa ve your new confi guration by cl i cking
button in the
Co n fig ura tion sect io n s
panel.
Sa v e cha ng es
. To appl y your new changes cl i ck the
A p p ly ch a ng es
There are vari ous scanner options you can us e to cus tomize the scanni ng environment: actions, li mits, modifi cation masks,
targets. Here is an exampl e of a two-way filter based on a spam subj ect prefix:
[smtp]
action_as = "defer"
as_eml_subject_prefix = "[SPAM]"
18
Page 19
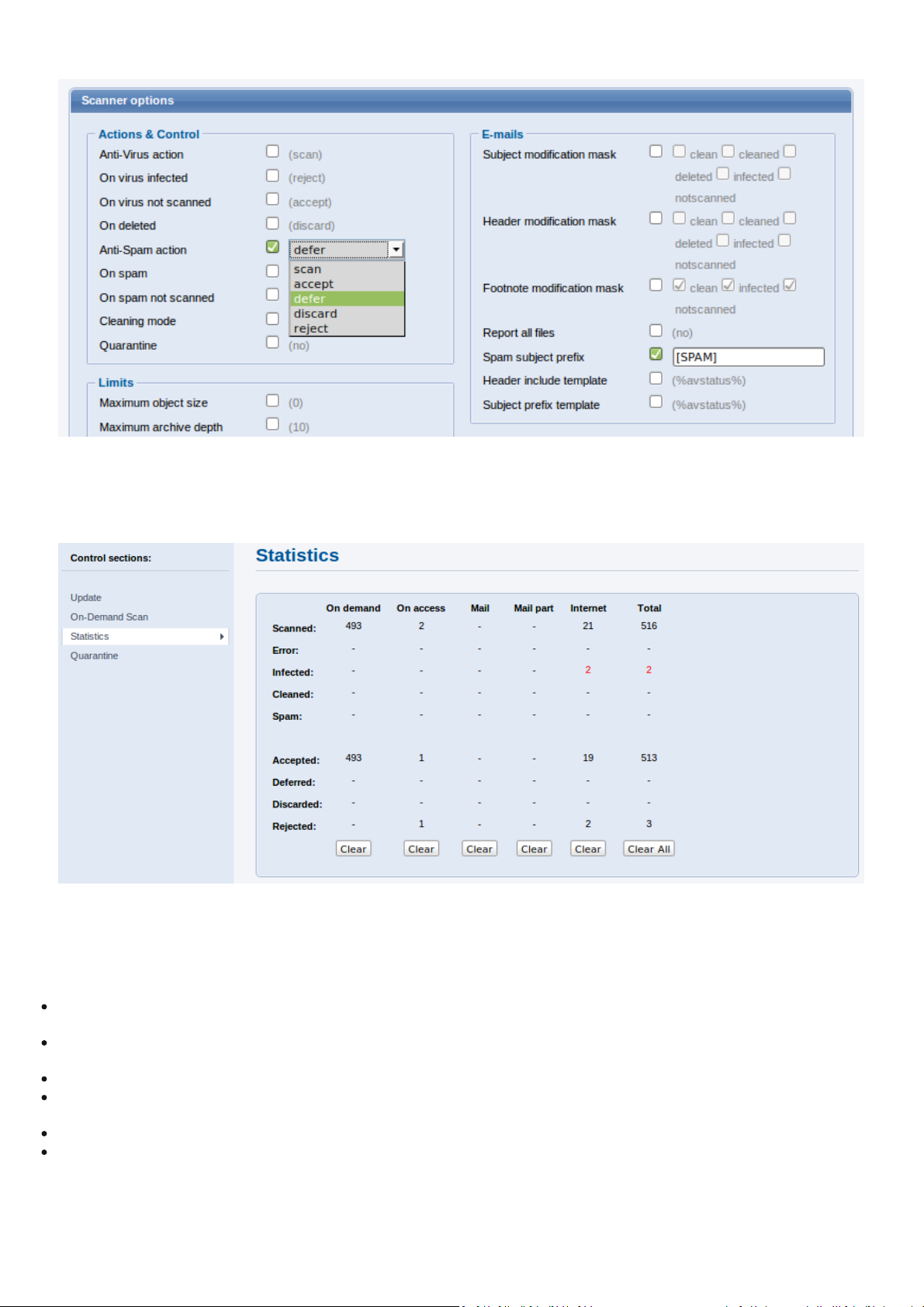
Figure 6-4. SMTP Scanner options.
6.6.3 Statistics
You can vi ew statisti cs for all of a ctive ESETS agents here.
Sta t is t ics
summary refreshes every 10 seconds.
Figure 6-5. ESETS - Control > Statistics.
6.7 Remote Administration
ESETS supports ESET Remote Admini s tra tion for mai l s ecurity management in large computer networks. The ESETS Remote
Administration Client is pa rt of the mai n ESETS daemon and performs the foll owing functions :
Communicates with ERA Server and provides you with system information, confi gurati on, protection statuses and s everal
other features
All ows cl i ent configurations to be viewed/modified usi ng the ESET Configuration Editor and implemented with the help of
confi guration tasks
Can perform
Performs On-demand scans a s requested, and s ubmi ts the resul ting back to ERA Server
NOTE: For this option to be available you must have a valid license for ESET File Security.
Adds l ogs of notable scans performed by the ESETS daemon to
Sends al l non-debug messages to
Upd a te No w
tasks
Sca n L o g
Th r ea t L og
Ev ent L o g
19
Page 20
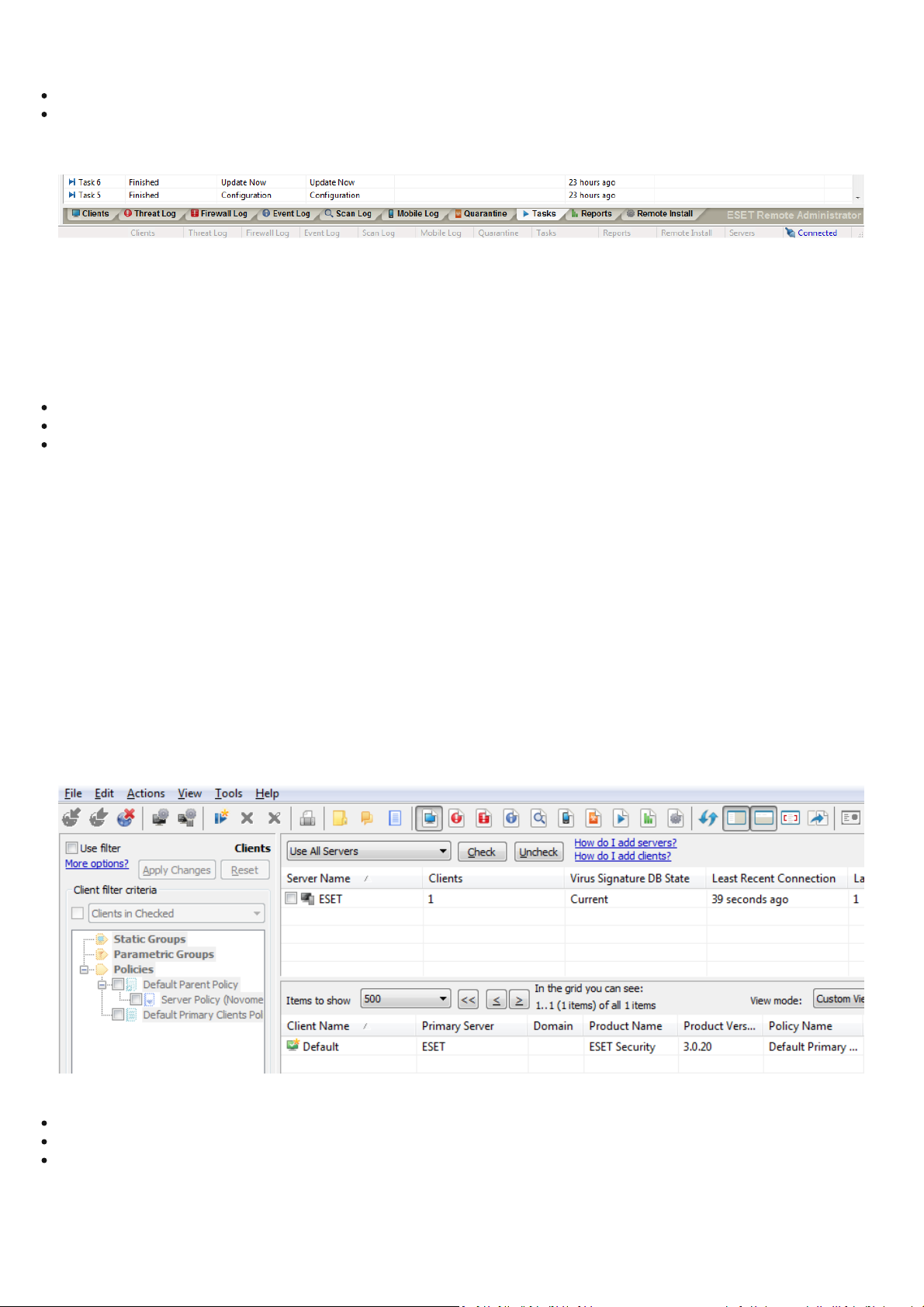
These functiona l i ties are not supported:
Firewal l Log
Remote Instal l
Figure 6-6. ERA Console tabs.
For more information, pl ease read the ESET Remote Administrator manual. This manua l i s l ocated on our web site at the
following link:
http://www.eset.com/documentation
6.7.1 Remote Administration usage example
Before commenci ng any remote admini s tration process ensure your system fulfills the three following prerequisites:
Running ERA Server
Running ERA Console
Enabl e RA Client in the ESETS daemon. Ensure that fi rewall settings do not bl ock traffic to ERA Server or vi ce versa.
To setup the bas i cs, specify the address of your ERA Server in the
to access the ERA Console password, you must edit the value of the
‘ra cl_serv er_a d d r’
‘ra cl_pa sswo rd ’
parameter first. If you are using a pass word
parameter accordi ngl y. Cha nge the val ue of
the ‘racl_interval’ parameter to adj us t the frequency of connecti ons to ERA Server (in minutes).
You can either use the web interface (see also previ ous chapter) to apply the new configuration, or you can adjus t these
parameters in the
racl_server_addr = "yourServerAddress"
racl_server_port = 2222
racl_password = "yourPassword"
racl_interval = 1
NOTE: All applicable ESET Remote Administration Cl ient vari a bl es are listed on the
[g loba l]
section of the ESETS confi guration file as fol l ows:
esets_d aem on (8 )
man pa ge.
The ESETS daemon configuration will be reloaded and RACL wil l connect to ERA Server. You will be abl e to see a newly
connected client in your ERA Console. Press the F5 button (or
M enu > V iew > Refresh
) to manually refresh the list of connected
cl i ents.
Figure 6-7. ERA Console.
By using ERA Consol e you can create a confi gurati on task to ESETS daemon from ERA Consol e:
Right click the connected
Navi gate to
Expand
N ew Ta sk > Co n fig ura tio n Ta sk > C rea t e...
Unix ES ET S ecu r it y t r ee
Clien t N a me
For an example of a confi guration task by the DAC agent, see below:
20
Page 21
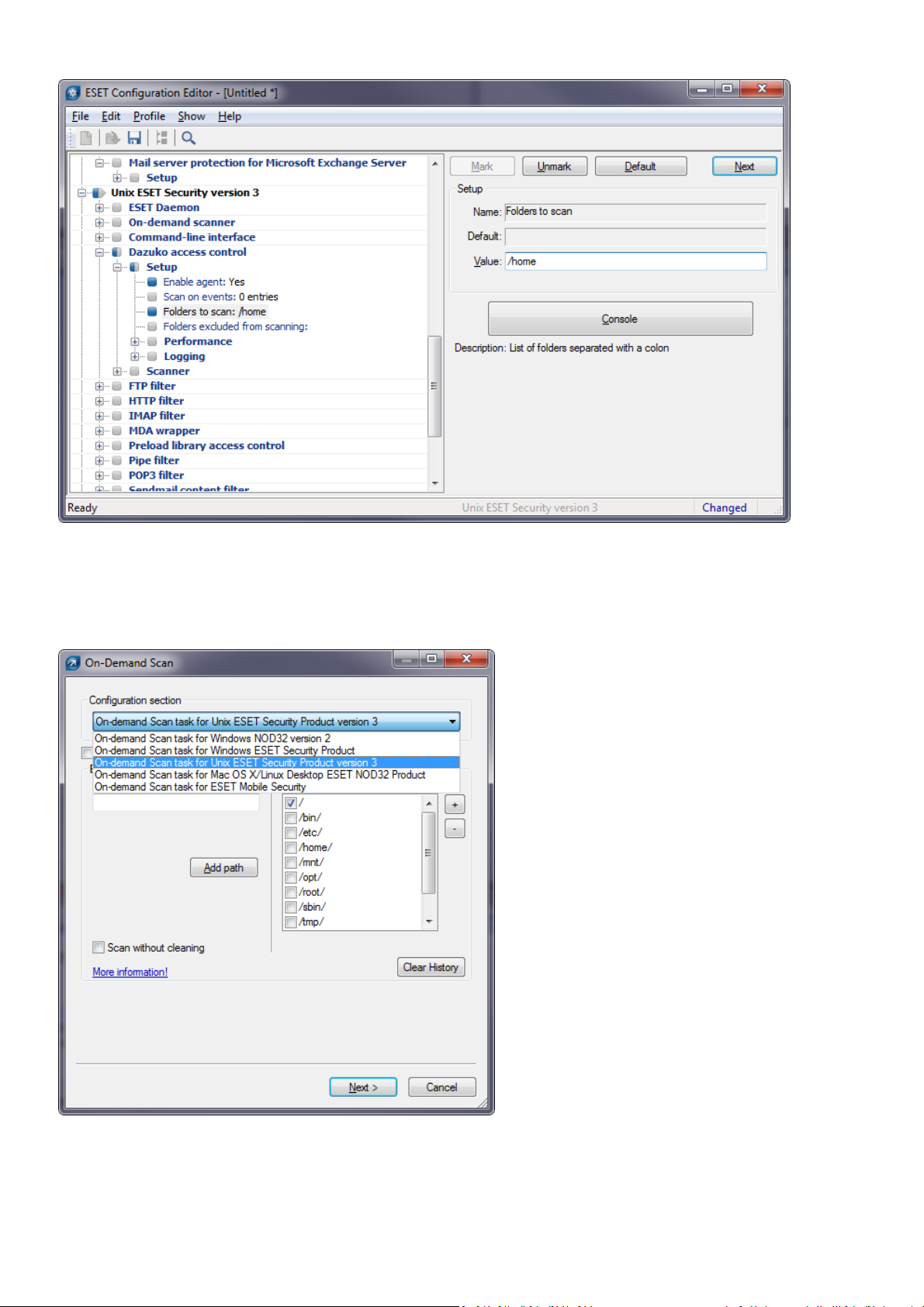
Figure 6-8. ERA Configuration Editor.
The
N ew Ta sk
context menu contains On-demand scanni ng options (enabl ed/di sabled cl eaning).
You can select the desi red product, that you wi sh to set the task for, in the
Co n fig ura tion Sect ion
drop-down menu. Make sure that you s elect the
(i.e. the product that is instal l ed on your target workstation).
Figure 6-9. ERA On-demand scan.
O n -D ema nd S ca n
pop-up window in the
O n -d ema n d S ca n ta sk fo r Unix ES ET S ecu r it y P r o du ct
option
21
Page 22

6.8 Logging
ESETS provides s ys tem daemon logging via sysl og.
Syslo g
is a s tandard for l oggi ng progra m messages and can be used to log
system events s uch as network and securi ty events.
Messages refer to a facility:
auth, authpriv, daemon, cron, ftp, lpr, kern, mail, ..., local0, ..., local7
Messages are ass i gned a priori ty/level by the sender of the message:
Error, Warning, Summall, Summ, Partall, Part, Info, Debug
This s ection describes how to confi gure and read the logging output of s ys l og. The
‘d a em o n ’
interface. Modify the value of the
) defines the syslog facility used for l oggi ng. To modify syslog settings edit the ESETS configuration file or us e the web
‘syslo g _cla ss’
parameter to change the logging clas s . We recommend you modi fy these settings
‘syslo g _fa cility’
option (default val ue
only i f you are familiar with syslog. For an example of sysl og confi guration see below:
syslog_facility = "daemon"
syslog_class = "error:warning:summall"
The name and l ocation of the log file depend on your s ys l og i ns tallation and configuration (e.g. rsys l og, syslog-ng, etc.).
Standa rd filenames for syslog output fi l es are for example
‘syslo g ’, 'd a emo n .lo g'
, etc. To follow syslog activity, run one of the
following commands from the cons ol e:
tail -f /var/log/syslog
tail -100 /var/log/syslog | less
cat /var/log/syslog | grep esets | less
If you enable ESET Remote Admini stration, ERA log entries ol der than gi ven da ys by the option
‘ra cl_lo g s_lifetim e’
wil l be
automatically deleted.
22
Page 23

7. ESET Security system update
7.1 ESETS update utility
To maintai n the effectiveness of ESET Mail Securi ty, the virus signature database must be kept up to date. The esets_upda te
util i ty ha s been developed for this purpose. See the
options
In the event that your s erver a ccesses the Internet via HTTP proxy, the addi ti ona l confi guration options
must be defined. If access to the HTTP proxy requires a username and password, the
options must also be defined in this section. To ini tiate an update, enter the foll owi ng command:
it by adding ESET Mail Securi ty, you wil l need to set your new userna me and pas s word for ESET Mai l Security either i n the ESETS
confi guration file, or in the Web interface. This will prevent possible is s ues with updates in ESETS.
the world - new patterns are added to the virus s i gnature database in very short interval s. For this reason, we recommend that
updates be initiated on a regular ba s i s. To specify the update frequency, the
[g loba l]
virus s i gnature databa se.
‘a v_up d ate_u sern am e’
@SBINDIR@/esets_update
NOTE: If you ha ve a fully functional ESET File/Gateway Security for Linux, BSD and Solaris instal l ation and you wis h to expa nd
To provi de the highest pos sibl e securi ty for the end user, the ESET team continuous l y col l ects virus definitions from all over
section of the ESETS confi guration file. The ESETS daemon must be up and running in order to success ful l y update the
and
‘a v_up d ate_p assw ord ’
7.2 ESETS update process description
esets_u pd a te(8 )
must be defined in the
man pa ge for detai ls. To launch an update, the configuration
[g loba l]
‘a v_up d ate_p erio d’
section of the ESETS confi guration file.
‘p ro xy _u s ern a me’
‘p ro xy _a ddr’, ‘p ro xy _p o rt’
and
‘p ro xy _p a ssw o rd’
option must be defined in the
The update process consists of two stages: First, the precompil ed update modules are downloa ded from the ESET server. If the
option
‘a v_mirro r_ena bled’
modules are created in the following directory:
@BASEDIR@/mirror
If desired, the Mirror directory path can be redefined using the
confi guration file. The newly created Mirror can then serve as a fully functional update server and can be used to create lower
(chi l d) Mirror servers. See section 7.3 for detai l s .
The option
securi ty products. These modules can be mirrored from the ESET server.
NOTE: Once you set your us erna me, password a nd license for ESET Mail Security to download PCU's for ESET NOD32
Antivirus / ESET Smart Securi ty, please contact our Technica l Support and request a change, that wil l enabl e your ESET Mai l
Securi ty to downl oa d PCU's for our Wi ndows-bas ed products.
The second stage of the update process i s the compilation of modul es loadable by the ESET Mail Security scanner from those
stored in the local mirror. Typically, the foll owing ESETS loading modules are created: loa der module (em000.dat), scanner
module (em001.dat), virus signature databas e module (em002.dat), archi ves support module (em003.dat), advanced heuri s tics
module (em004.dat), etc. The modules a re created in the following directory:
@BASEDIR@
This i s the directory where the ESETS daemon loads modules from and thus can be redefined usi ng the
[g loba l]
‘a v_mirro r_p cu ’
section of the ESETS confi guration file.
is set to ‘yes’ in the
al l ows you to download Program Component Update (PCU) modules for Wi ndows-ba sed ESET
[g loba l]
section of the ESETS confi guration file, copies (or mirror) of these update
‘a v_mirro r_d ir’
option in the
[g loba l]
section of the ESETS
‘b a se_d ir’
option in the
7.3 ESETS mirror http daemon
ESETS mirror http daemon i s ins talled automatical l y with ESET Mail Security. The http mirror daemon starts i f the option
‘a v_mirro r_h ttp d_en a bled ’
Options
addresses) where the http server listens.
The option
‘a v_mirro r_h ttp d_userna me’
access the Mirror.
‘a v_mirro r_h ttp d_po rt’
‘a v_mirro r_h ttp d_a u th _mo d e’
in the
[g loba l]
and
‘a v_mirro r_h ttp d_pa sswo rd ’
section of the ESETS confi guration file is s et to
and
‘a v_mirro r_h ttp d_a d d r’
al l ows access a uthentication (default: none) to be changed to basi c. The options
‘yes’
and the Mirror is enabl ed.
define the port (default 2221) and a ddress (default: all l ocal tcp
al l ow an administrator to define the login and pas sword used to
23
Page 24

8. Let us know
Dear user, we hope this Guide has provided you wi th a thorough understanding of the requirements for ESET Mai l Securi ty
instal l ation, confi guration and mai ntenance. However, our goal i s to continually improve the quality and effectiveness of our
documentation. If you feel that any sections in this Guide are uncl ear or incomplete, pleas e let us know by contacti ng Cus tomer
Care:
http://www.eset.com/support
or us e di rectly the support form:
http://www.eset.eu/support/form
We are dedicated to provide the highest level of support and look forward to helping you s hould you experi ence any probl ems
concerni ng this product.
24
Page 25

9. Appendix A. ESETS setup and configuration
9.1 Setting ESETS for MTA Postfix
Inbound email message scanning
W arn ing :
This installation is not compatible with SELinux. Either di s a bl e SELinux or proceed to the next section.
The objective of this instal l ation is to insert
is set in the Postfix parameter
‘m a ilb ox _com m an d ’
esets_m d a
.
before the original Postfix MDA. The MDA to be used (with arguments)
NOTE: If the ‘mai l box_command‘ va l ue is empty, Postfix alone is delivering mai l . You must install and confi gure a real MDA
(e.g. procmai l ) a nd use that first for the ‘mailbox_command’ and arguments (e.g. /usr/bin/procmail -d "$USER"). Reload Pos tfix
and make sure it is deli vering mail according to your needs. You may then continue with the ESETS installation.
Take the full path to the current Postfix MDA and set the parameter ‘mda_path’ in the
[m d a ]
section of the ESETS confi guration
file to:
mda_path = "/usr/bin/procmail"
Restart the ESETS daemon. Then, replace the path to the current Postfix MDA with
esets_m d a
path and add -- --
reci pi ent="$RECIPIENT" --sender="$SENDER" to the arguments, as in the following exampl e:
mailbox_command = @BINDIR@/esets_mda -d "$USER" -- --recipient="$RECIPIENT" --sender="$SENDER"
To re-read the newly created configuration, reload Postfix.
Bi-directional email message scanning
The objective of this instal l ation is to divert all mail from Postfix to
esets_sm tp
and get them back to Postfix. In the
[smt p ]
section of the ESETS confi guration file, set the following parameters:
agent_enabled = yes
listen_addr = "localhost"
listen_port = 2526
server_addr = "localhost"
server_port = 2525
Restart the ESETS daemon;
listen _po rt’
content_filter = smtp:[127.0.0.1]:2526
NOTE: If the
esets_sm tp
and forward it to
‘co n ten t_f ilter’
(or other ESETS mail sca nning module) before or after your current ‘content_filter’.
esets_sm tp
‘serv er_a ddr:server_p ort’
wil l be started and wil l s can al l SMTP communication accepted on
. To divert all mail to
esets_sm tp
set the foll owing i n Postfix:
‘listen_a d d r:
parameter al ready has a va l ue, do not fol l ow these instructions. Ins tead, you must i ns ert
Lastly, set Postfix to accept mai l on port 2525 and continue process i ng i t. To do this, add the foll owi ng entry to the Postfix
master.cf file:
localhost:2525 inet n - n - - smtpd
-o content_filter=
-o myhostname=esets.yourdomain.com
-o local_recipient_maps=
-o relay_recipient_maps=
-o receive_override_options=no_unknown_recipient_checks,no_header_body_checks
-o smtpd_helo_restrictions=
-o smtpd_client_restrictions=
-o smtpd_sender_restrictions=
-o smtpd_recipient_restrictions=permit_mynetworks,reject
-o mynetworks=127.0.0.0/8
Replace yourdomain.com with your hostname. Make sure al l but the firs t line is indented. To re-read the newly created
confi guration, reload Postfix.
NOTE: If you ha ve SELinux enabled, it will prevent Postfix from listening on 2525 (e.g. Fedora Core >= 5), In thi s cas e, run the
following command:
semanage -a -t smtp_port_t -p tcp 2525
25
Page 26

9.2 Setting ESETS for MTA Sendmail
Inbound email message scanning
W arn ing :
This installation is not compatible with SELinux. Either di s a bl e SELinux or proceed to the next section.
The objective of this instal l ation is to insert
esets_m d a
before Sendmail’s ori gi nal MDA.
NOTE: On FreeBSD, Sendmai l may be communicating with MDA using LMTP. However, esets_mda does not unders tand LMTP. If
you have FEATURE(local _lmtp) in ‘hostname’.mc, comment it out now and recreate sendmail.cf.
The currently us ed MDA can be found i n the fil e sendmail.cf i n s ection Ml ocal: parameters ‘P’ (executable) and ‘A’ (its name
and arguments).
First, set the ‘mda_path’ in the
[m da ]
section of the ESETS confi guration file to the currently used MDA executable (Sendmail’s
‘P’ parameter). Then restart the ESETS daemon.
Next, add the li nes below to the sendmail.mc file (or `‘hos tname’.mc on FreeBSD and Solari s ) before all MAILER defini tions :
define('LOCAL_MAILER_PATH', '@BINDIR@/esets_mda')dnl
define('LOCAL_MAILER_ARGS', 'esets_mda original_arguments -- --sender $f --recipient $u@$j')dnl
In the example above, ori ginal_arguments is Sendmail’s ‘A’ parameter without the name (firs t word).
Lastly, recreate sendmail.cf a nd restart Sendmai l .
Bi-directional email message scanning
The objective of this instal l ation is to scan all mai l i n Sendmail us i ng the
esets_sm f i
filter. In the
[smfi]
section of the ESETS
confi guration file, set the following parameters:
agent_enabled = yes
smfi_sock_path = "/var/run/esets_smfi.sock"
Restart the ESETS daemon. Then, add the li nes below to the sendmail.mc file (or ‘hos tname’.mc on FreeBSD) before al l MAILER
definitions:
INPUT_MAIL_FILTER('esets_smfi', 'S=local:/var/run/esets_smfi.sock, F=T, T=S:2m;R:2m;E:5m')dnl
With these settings, Sendmail wil l communicate with
esets_sm f i
via unix s ocket ‘/var/run/esets_smfi.sock’. Flag ‘F=T’ will
result in a temporary fa i l ed connection if the filter is unavai l abl e. ‘S:2m’ defines a 2 minute timeout for sending information
from MTA to the fil ter, ‘R:2m’ defines a 2 minute timeout for readi ng replies from the filter and ‘E:5m’ sets an overall 5 minute
timeout between sending end-of-message to the fil ter and waiting for fi na l acknowledgment.
If the timeouts for the
esets_sm f i
filter are too short, Sendmail can temporarily defer the messa ge to the queue and attempt to
pass i t through later. However, this may lead to continuous deferral of the same messages. To avoi d this probl em, the timeouts
should be set properl y. You can experiment with Sendmail’s
‘co n fM AX_M E S S A GE_SIZE’
parameter, which is the maxi mum
accepted messa ge size in bytes. Taking i nto account this value and the approxi mate maximum time for MTA to process a message
of that size (this can be measured), you can determine the most effective timeout settings for the
esets_sm f i
filter.
Lastly, recreate sendmail.cf a nd restart Sendmai l .
9.3 Setting ESETS for MTA Qmail
Inbound email message scanning
The objective of this instal l ation is to insert
/var/qmai l directory, in the
mda_path = "/var/qmail/bin/qmail-esets_mda"
[m d a ]
section of the ESETS confi guration file, set the following parameter:
Restart the ESETS daemon. Create the file /var/qmai l /bin/qmai l -esets_mda with the foll owing content and run ‘chmod a +x’ on
it:
#!/bin/sh
exec qmail-local -- "$USER" "$HOME" "$LOCAL" "" "$EXT" "$HOST" "$SENDER" "$1"
esets_m d a
before Qmai l ’s local deli very a gent. Assuming Qmail i s ins talled in the
This wi l l cause esets_mda to call Qmail’s l ocal delivery agent. Next, create the file /var/qmail/bi n/qmail-start.esets with the
following content and also run 'chmod a+x' on it:
#!/bin/sh
A="$1"; shift
exec qmail-start.orig "|@BINDIR@/esets_mda '$A'"' -- --sender="$SENDER" --recipient="$RECIPIENT"' "$@"
26
Page 27

This wi l l s tart Qmai l usi ng
through esets_mda. Note that in this configura tion
esets_m d a
for l ocal deliveries. However, the ori ginal delivery speci fi cati on is pas s ed to qmai l -l ocal
esets_m d a
wil l use Qmail’s recogni zed exit codes (see the
qm a il-com m an d (8 )
man pa ge). Lastly, repla ce qmail-start usi ng commands :
mv /var/qmail/bin/qmail-start /var/qmail/bin/qmail-start.orig
ln -s qmail-start.esets /var/qmail/bin/qmail-start
Restart Qmai l .
Bi-directional email messages scanning
The objective of this instal l ation is to insert esets_mda before qmail-queue, which queues a l l mails before deli very. Assuming
Qmai l i s i ns talled in the /var/qmail di rectory, in the
mda_path = "/var/qmail/bin/qmail-queue.esets"
[m da ]
section of the ESETS confi guration file, set the following parameter:
Restart the ESETS daemon. Lastly, replace qmail-queue usi ng these commands :
mv /var/qmail/bin/qmail-queue /var/qmail/bin/qmail-queue.esets
ln -s @BINDIR@/esets_mda /var/qmail/bin/qmail-queue
Restarting Qmai l i s unnecess ary. All messages enqueued from now will be scanned by ESETS. Note that i n thi s configuration
esets_m d a
wil l use qmail-queue’s exit codes (see the
qm a il-q u eu e(8 )
man pa ge).
9.4 Setting ESETS for MTA Exim version 3
Inbound email messages scanning
The objective of this instal l ation is to create an Exi m transport from
ESETS configuration file set the foll owi ng pa rameter:
esets_m d a
for l ocal users. In the
[m d a ]
section of the
mda_path = "/usr/sbin/exim"
In the above, /usr/sbi n/exi m is the full path to Exi m binary. Restart the ESETS daemon. Next, add the following transport (on
any line) to the list of Exim trans ports:
esets_transport:
driver = pipe
command = @BINDIR@/esets_mda -oi -oMr esets-scanned $local_part@$domain \
-- --sender=$sender_address --recipient=$local_part@$domain
user = mail
In the above exampl e,
‘m a il’
is one of Exim’s
‘tru sted_users ’
. Now add the following director to the top of the list of Exim
directors:
esets_director:
driver = smartuser
condition = "${if eq {$received_protocol}{esets-scanned} {0}{1}}"
transport = esets_transport
verify = false
This wi l l s end all uns canned mails for local users to
esets_m d a; esets_m d a
wil l then send them back to Exim for further
process i ng. To re-read the newly created configuration, restart Exim.
Bi-directional email message scanning
The goal of this instal l a tion i s to create an Exim trans port from
esets_m d a
for a l l mail. Perform all steps from the previous
section, but al so add thi s router to the top of the Exim router list:
esets_router:
driver = domainlist
route_list = "* localhost byname"
condition = "${if eq {$received_protocol}{esets-scanned} {0}{1}}"
transport = esets_transport
verify = false
27
Page 28

9.5 Setting ESETS for MTA Exim version 4
Inbound email message scanning
The goal of this instal l a tion i s to create an Exim trans port from
confi guration file, set this parameter:
mda_path = "/usr/sbin/exim"
or, if you are using FreeBSD, this parameter:
mda_path = "/usr/local/sbin/exim"
where /usr/sbin/exim (or /us r/local/sbi n/exi m) is the full path to the Exim binary. Then restart the ESETS daemon. Add this
router to the top of the Exim router li s t:
esets_router:
driver = accept
domains = +local_domains
condition = "${if eq {$received_protocol}{esets-scanned} {0}{1}}"
transport = esets_transport
verify = false
and this transport (at whatever location) to the li s t of Exi m transports:
esets_transport:
driver = pipe
command = @BINDIR@/esets_mda -oi -oMr esets-scanned $local_part@$domain \
-- --sender=$sender_address --recipient=$local_part@$domain
esets_m d a
for l ocal users. In the
[m d a ]
section of the ESETS
This wi l l s end all uns canned mails for local users to
esets_m d a; esets_m d a
wil l then send them back to Exim for further
process i ng. To re-read the newly created configuration, restart Exim.
Bi-directional email message scanning
The goal of this instal l a tion i s to create an Exim trans port from esets_mda for a l l mail. Perform all steps from the previous
section, but omit this line in esets_router:
domains = +local_domains
9.6 Setting ESETS for MTA ZMailer
Inbound email message scanning
The goal of this instal l a tion i s to us e
instal l ed, such a s procmail. In the
mda_path = "/path/to/procmail"
and restart the ESETS daemon. Procmail doesn‘t support the full email address as a recipient, so comment out this l i ne in
ZMai l er‘s router.cf prepending a ‘#‘:
localdoesdomain=1
Next, in the
command="sm -c $channel esets"
‘lo ca l/*’
cl ause of schedul er.conf, replace your current deli very command with:
and append this line to sm.conf (replace your.hos tname.com with your FQDN):
esets_m d a
[m d a ]
section of the ESETS confi guration file, set this para meter:
as ZMailer’s local delivery agent. However, you must have a real MDA
esets sSPfn @BINDIR@/esets_mda esets_mda -a $h -d $u -- --sender $g --recipient $u@your.hostname.com
Finally, restart ZMailer.
Bi-directional email messages scanning
The goal of this instal l a tion i s to us e
esets_zm fi
as ZMailer‘s SMTP contentfilter. Firs t start the ESETS daemon. Then add this
line to smtpserver.conf:
PARAM contentfilter @BINDIR@/esets_zmfi
and restart ZMailer.
Pleas e note that this will scan only the emai l mess a ges coming through the smtpserver. Also, make sure that your smtp-policy
is filtering a l l emai l according to your needs.
28
Page 29

9.7 Setting ESETS for outbound email message scanning
Outbound email message scanni ng is performed using the
esets_sm tp
daemon. In the
[smt p ]
section of the ESETS confi guration
file, set these para meters:
agent_enabled = yes
listen_addr = "192.168.1.0"
listen_port = 2525
where
‘listen_a d d r’
redirect all SMTP requests to
is the address of the loca l network interface named if0. Then, restart the ESETS daemon. The next step is to
esets_sm tp
. If IP-fi l tering is being performed by the ipchai ns admini s tration tool, an appropriate
rul e would be:
ipchains -A INPUT -p tcp -i if0 --dport 25 -j REDIRECT 2525
If I P-fi l teri ng i s being performed by the iptables administration tool, the rule is :
iptables -t nat -A PREROUTING -p tcp -i if0 --dport 25 -j REDIRECT --to-ports 2525
On FreeBSD, the rule is as fol l ows:
ipfw add fwd 192.168.1.10,2525 tcp from any to any 25 via if0 in
On NetBSD and Sol a ris:
echo 'rdr if0 0.0.0.0/0 port 25 -> 192.168.1.10 port 2525 tcp' | ipnat -f -
W arn ing :
Your MTA may accept all connections without extensive checking from
esets_sm tp
because those connections are
local. By using your own fi rewall rul es, make sure you do not create an open relay, i.e., al l ow someone from the outsi de to
connect to
esets_sm tp
and use it as a relay SMTP server.
9.8 Setting ESETS for scanning of POP3 communication
The POP3 communication scanni ng is performed using
file, set these para meters:
agent_enabled = yes
listen_addr = "192.168.1.10"
listen_port = 8110
where
‘listen_a d d r’
redirect all POP3 requests to
is the address of the loca l network interface named if0. Then restart the ESETS daemon. The next step is to
esets_p op 3
. If IP-fi l tering is being performed by the ipchai ns admini s tration tool, an appropriate
rul e is:
ipchains -A INPUT -p tcp -i if0 --dport 110 -j REDIRECT 8110
If I P-fi l teri ng i s being performed by the iptables administration tool, the rule would be:
iptables -t nat -A PREROUTING -p tcp -i if0 --dport 110 -j REDIRECT --to-ports 8110
On FreeBSD, the rule is as fol l ows:
ipfw add fwd 192.168.1.10,8110 tcp from any to any 110 via if0 in
On NetBSD and Sol a ris:
echo 'rdr if0 0.0.0.0/0 port 110 -> 192.168.1.10 port 8110 tcp' | ipnat -f -
esets_p op 3
daemon. In the
[p o p3 ]
section of the ESETS confi guration
9.9 Setting ESETS for scanning of IMAP communication
The IMAP communication sca nni ng is performed using the
esets_im a p
daemon. In the
file, set these para meters:
agent_enabled = yes
listen_addr = "192.168.1.10"
listen_port = 8143
where
‘listen_a d d r’
redirect all IMAP requests to
is the address of the loca l network interface named if0. Then restart the ESETS daemon. The next step is to
eset s_im a p
. If IP-fi l tering is being performed by the ipchai ns admini s tration tool an appropri ate
rul e would be:
ipchains -A INPUT -p tcp -i if0 --dport 143 -j REDIRECT 8143
If I P-fi l teri ng i s being performed by the iptables administration tool, the rule is :
[im a p]
section of the ESETS confi guration
29
Page 30

iptables -t nat -A PREROUTING -p tcp -i if0 --dport 143 -j REDIRECT --to-ports 8143
On FreeBSD, the rule is as fol l ows:
ipfw add fwd 192.168.1.10,8143 tcp from any to any 143 via if0 in
On NetBSD and Sol a ris:
echo 'rdr if0 0.0.0.0/0 port 143 -> 192.168.1.10 port 8143 tcp' | ipnat -f -
30
Page 31

10. Appendix B. PHP License
The PHP License, version 3.01 Copyright (c) 1999 - 2006 The PHP Group. All ri ghts reserved.
Redis tri bution and use in source and binary forms, with or without modifi cation, i s permitted provided that the following
conditions are met:
1. Redis tri butions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2. Redis tri butions in binary form must reproduce the above copyright notice, this l i s t of condi tions and the following discl a i mer
in the documentation and/or other materials provi ded with the distribution.
3. The name “PHP” must not be used to endors e or promote products derived from this software without prior written
permis s i on. For wri tten permission, pl eas e contact group@php.net.
4. Products deri ved from this software may not be called “PHP”, nor may “PHP” appear in their na me, without pri or wri tten
permis s i on from group@php.net. You may indi cate that your software works in conjuncti on with PHP by saying “Foo for PHP”
instead of cal l i ng it “PHP Foo” or “phpfoo”
5. The PHP Group may publ i s h revised and/or new versions of the license from time to time. Each versi on wi l l be given a
distinguishing version number. Once covered code has been published under a particul a r version of the license, you may
al ways continue to use it under the terms of that versi on. You may also choose to use such covered code under the terms of
any subsequent versi on of the li cense publ i s hed by the PHP Group. No one other than the PHP Group has the ri ght to modify
the terms appl i cable to covered code created under thi s License.
6. Redis tri butions of any form whatsoever must retain the following acknowledgment: “This product includes PHP software,
freely a vailable from <http://www.php.net/software/>”.
THIS SOFTWARE IS PROVIDED BY THE PHP DEVELOPMENT TEAM "AS IS" AND ANY EXPRESSED OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
DISCLAIMED. IN NO EVENT SHALL THE PHP DEVELOPMENT TEAM OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE
GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT
OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
31
 Loading...
Loading...