Page 1

ESET Gateway Security
Installation Manual and User Guide
Linux, BSD and Sol ari s
Page 2

Contents
1. Introduction
2. Terminology and abbreviations
3. Installation
4. Architecture Overview
5. Integration with Internet Gateway services
..................................................................3
.........................................................................................3
Mai n functionality1.1
.........................................................................................3
Key features of the sys tem1.2
..................................................................5
..................................................................7
..................................................................8
..................................................................9
.........................................................................................9
Transparent HTTP/FTP proxy configura tion5.1
.........................................................................................10
Manual HTTP/FTP proxy confi guration5.2
5.2.2
Internet Content Adaptation configuration5.3
Large HTTP Objects Handli ng5.4
ESETS plug-in fi l ter for SafeSqui d Proxy Cache5.5
................................................................................10Manua l proxy configura ti on of Mozilla Firefox5.2.1
Manua l proxy configura ti on of Squid Web Proxy
................................................................................11
Cache
.........................................................................................11
.........................................................................................12
.........................................................................................13
................................................................................13Opera tion principle5.5.1
................................................................................13Installation and configuration5.5.2
6. Important ESET Gateway Security
..................................................................15
mechanisms
.........................................................................................15
Handle Object Policy6.1
.........................................................................................15
User Speci fic Confi guration6.2
.........................................................................................16
Blacklist and Whi teli s t6.3
Sampl es Submissi on System6.4
Web Interface6.5
Remote Admini s tra tion6.6
Logging6.7
................................................................................16URL Whitelist6.3.1
.........................................................................................16
.........................................................................................17
................................................................................18License mana gement6.5.1
................................................................................18Agent HTTP configuration example6.5.2
..........................................................................19HTTP Agent tes ti ng with the Mozilla Fire fox6.5.2.1
................................................................................20Statis tics6.5.3
.........................................................................................20
................................................................................21Remote Administra tion usage example6.6.1
.........................................................................................23
ESET Gateway Security
Copyright ©2011 by ESET, spol. s r. o.
ESET Gateway Security was developed by ESET, spol. s r. o.
For more information visit www.e set.com.
All rights reserved. No part of this documentation may be reproduced,
stored in a retrieval sys tem or transmitted in any form or by any
mea ns , electroni c, mecha nical, photocopying, recording, scanning, or
othe rwise without permis sion in writing from the author.
ESET, spol. s r. o. res erves the right to change any of the described
application softwa re without prior notice.
Custome r Care Worldwi de: www.es et.eu/support
Custome r Care North America : www.eset.com/support
REV. 2011-02-08
7. ESET Security system update
8. Let us know
..................................................................24
.........................................................................................24
ESETS update utility7.1
.........................................................................................24
ESETS update process descri ption7.2
.........................................................................................24
ESETS mirror http daemon7.3
..................................................................25
9. Appendix A. ESETS setup and
..................................................................26
configuration
Setting ESETS for s canning of HTTP communica tion -
9.1
.........................................................................................26
transparent mode
Setting ESETS for s canning of FTP communication -
9.2
.........................................................................................26
transparent mode
Setting ESETS for s canning of ICAP encapsulated HTTP
9.3
.........................................................................................26
messages
10. Appendix B. PHP License
..................................................................27
Page 3

1. Introduction
Dear user, you have acquired ESET Gateway Securi ty - the premier securi ty system running under the Linux, BSD and Sol ari s OS.
As you wil l s oon find out, ESET's state-of-the-art sca nning engine has unsurpass ed sca nning speed and detection rates combi ned
with a very s mall footpri nt that makes i t the ideal choice for any Linux, BSD and Solari s OS server.
1.1 Main functionality
Hypertext Transfer Protocol filter (HTTP)
The HTTP filter module is an HTTP 1.1 compliant speci al proxy s erver used to sca n communication between HTTP cl i ents a nd
HTTP servers for viruses. The module receives HTTP messages from an HTTP cli ent (a web browser application or other proxy
cache) and forwards them to the HTTP server (a web server appl i cation) and vice versa. The body of the mess age (if ava i l able)
wil l be scanned for vi ruses by the
The
esets_h ttp
module into the environment.
File Transfer Protocol filter (FTP)
The FTP fil ter module is a s peci a l trans parent proxy s erver that scans communica tion between an ftp client and a n ftp s erver
for vi ruses. The FTP gateway modul e is used to scan both incoming and outgoing data transfers. Depending on the scanning
results a transferred object will be cl eaned, deleted or blocked.
SafeSquid filter
The SSFI modul e is a plugin accessing all objects process ed by the SafeSqui d Proxy ca che. Once an object is accessed by the
plugin, it wil l be sca nned for infi l trations by the ESETS daemon. In ca se of positive detection SSFI blocks the appropri ate source
and sends a predefined template page instead. The
higher.
is able to act as both a transparent and a non-transparent proxy server depending on the integration of the
esets_h ttp
module.
esets_ssfi.so
module is s upported by SafeSquid Advanced version 4.0.4.2 and
Internet Content Adaptation Protocol filter (ICAP)
The ICAP filter module i s an ICAP 1.0 compliant s peci al server that scans ICAP enca ps ul a ted HTTP messages from ICAP cl i ents
for vi ruses.
1.2 Key features of the system
Advanced engine algorithms
The ESET antivirus s canning engine algori thms provide the highest detection rate and the fas test s canning times.
Multi-processing
ESET Gateway Security is developed to run on single- as well as multi-process or uni ts.
Advanced Heuristics
ESET Gateway Security incl udes uni que adva nced heuristics for Win32 worms, backdoor infections and other forms of
malware.
Built-In features
Built-in archi vers unpack a rchi ved obj ects without the need for any external programs.
Speed and efficiency
To increase the speed and effici ency of the sys tem, its archi tecture is based on the runni ng da emon (resident progra m) where
al l s canning requests a re sent.
Enhanced security
All executive daemons (except esets_dac) run under non-privileged user a ccount to enhance securi ty.
Selective configuration
The system supports s elective confi guration bas ed on the user or client/server.
Multiple logging levels
Multipl e l ogging l evels can be confi gured to get information about system activi ty and i nfil trations .
3
Page 4

Web interface
Configuration, administrati on a nd license management are offered through a n i ntuitive and user-fri endl y Web interface.
Remote administration
The system supports ESET Remote Admini s tra tion for mana gement in large computer networks .
No external libraries
The ESET Gateway Securi ty instal l a tion does not requi re external libra ries or programs except for LIBC.
User-specified notification
The system can be configured to notify s peci fi c users in the event of a detected infiltration or other i mportant events.
Low system requirements
To run effici ently, ESET Gateway Security requires just 16MB of hard-di s k s pace and 32MB of RAM. It runs s moothly under the
2.2.x, 2.4.x and 2.6.x Linux OS kernel vers i ons a s well a s under 5.x, 6.x FreeBSD OS kernel versi ons.
Performance and scalability
From lower-powered, small office servers to enterprise-clas s ISP s ervers with thousands of us ers, ESET Gateway Security
deli vers the performance and s cal a bi l i ty you expect from a UNIX based sol ution, in addition to the unequaled securi ty of ESET
products.
4
Page 5

2. Terminology and abbreviations
In this s ection we wil l review the terms a nd a bbreviati ons us ed i n thi s document. Note that a bol dface font is reserved for
product component names and also for newly defi ned terms and a bbreviations . Terms and abbrevia tions defined in this cha pter
are expanded upon later in this document.
ESETS
ES E T S ecu rity
operating s ys tems. It is also the name (or i ts part) of the software packa ge containing the products.
RSR
Abbreviation for ‘RedHat/Novell (SuSE) Ready’. Note that we al s o support RedHat Ready and Novell (SuSE) Ready vari ations of
the product. The RSR package differs from the ‘standa rd’ Linux version i n that it meets the FHS (Fil e-system Hierarchy Standard
defined as a part of Linux Standard Bas e) criteria required by the RedHat Ready and Novell(SuSE) Ready certifi cate. This means
that the RSR package is instal l ed as an add-on appl i cation - the primary instal l ation directory is ‘/opt/eset/esets’.
ESETS daemon
The mai n ESETS system control a nd scanning da emon:
ESETS base directory
The directory where ESETS loadable modules containi ng the virus s i gna ture databa se are stored. The abbreviation
@ BA SE D IR@
listed below:
Linux: /var/lib/esets
Linux RSR: /var/opt/eset/esets/lib
FreeBSD: /var/lib/esets
NetBSD: /var/lib/esets
Solaris: /var/opt/esets/lib
is a s tandard a cronym for all securi ty products developed by ESET, spol . s r. o. for Linux, BSD and Sol ari s
esets_d a em on
wil l be used for future references to this di rectory. The
.
@ BA SE D IR@
value for the following Operating Systems i s
ESETS configuration directory
The directory where al l fi l es related to the ESET Gateway Securi ty confi guration a re stored. The abbrevia tion
used for future references to this directory. The
Linux: /etc/esets
Linux RSR: /etc/opt/eset/esets
FreeBSD: /usr/local/etc/esets
NetBSD: /usr/pkg/etc/esets
Solaris: /etc/opt/esets
@ ETCD IR@
value for the following Operating Systems i s l i s ted below:
ESETS configuration file
Mai n ESET Gateway Security confi guration file. The abs ol ute path of the fil e is as follows:
@ETCDIR@/esets.cfg
ESETS binary files directory
The directory where the relevant ESET Gateway Security bi nary files are stored. The abbreviation
future references to thi s di rectory. The
Linux: /usr/bin
Linux RSR: /opt/eset/esets/bin
FreeBSD: /usr/local/bin
NetBSD: /usr/pkg/bin
Solaris: /opt/esets/bin
@ BINDIR @
value for the following Operating Systems i s l i s ted below:
@ BINDIR @
ESETS system binary files directory
The directory where the relevant ESET Gateway Security s ys tem bina ry files are stored. The abbrevia tion
used for future references to this directory. The
@ SB INDIR @
value for the following Operating Systems i s l i s ted below:
@ ETCD IR@
wil l be used for
@ SB INDIR @
wil l be
wil l be
Linux: /usr/sbin
Linux RSR: /opt/eset/esets/sbin
FreeBSD: /usr/local/sbin
NetBSD: /usr/pkg/sbin
Solaris: /opt/esets/sbin
5
Page 6

ESETS object files directory
The directory where the relevant ESET Gateway Security object fil es and libra ries are stored. The abbreviation
be used for future references to this directory. The
Linux: /usr/lib/esets
Linux RSR: /opt/eset/esets/lib
FreeBSD: /usr/local/lib/esets
NetBSD: /usr/pkg/lib/esets
Solaris: /opt/esets/lib
@ LIBD IR@
value for the following Operating Systems i s l i s ted below:
@ LIBD IR@
wil l
6
Page 7

3. Installation
After purchasing ESET Gateway Securi ty, you will receive your authorizati on data (username, password and l i cense key). This
data is necessa ry for both identifyi ng you as our customer and al l owi ng you to download upda tes for ESET Gateway Security. The
username/pass word data i s also requi red for downloadi ng the ini tial installation package from our web site. ESET Gateway
Securi ty i s di s tri buted as a binary fi l e:
esets.i386.ext.bin
In the bina ry file shown a bove,
‘ex t’
is a Linux, BSD and Solaris OS distribution dependent suffi x, i.e., ‘deb’ for Debian, ‘rpm’ for
RedHat and SuSE, ‘tgz’ for other Linux OS di stri buti ons , ‘fbs5.tgz’ for FreeBSD 5.x, ‘fbs6.tgz’ for FreeBSD 6.x, ‘nbs4.tgz’ for NetBSD 4.
xx a nd ‘sol 10.pkg.gz‘ for Sol ari s 10.
Note that the Linux RSR binary fi l e format is:
esets-rsr.i386.rpm.bin
To install or upgra de the product, use the following command:
sh ./esets.i386.ext.bin
For the Linux RSR vari a tion of the product, use the command:
sh ./esets-rsr.i386.rpm.bin
to display the product’s User License Acceptance Agreement. Once you have confirmed the Acceptance Agreement, the
instal l ation package is placed into the current worki ng directory and relevant information regardi ng the packa ge’s i ns tallation,
un-instal l a tion or upgra de is di spl ayed onscreen.
Once the package is i ns talled, you can veri fy tha t the main ESETS service i s running by usi ng the foll owing command:
Linux OS:
ps -C esets_daemon
BSD OS:
ps -ax | grep esets_daemon
Solaris:
ps -A | grep esets_daemon
After pressing ENTER, you should s ee the following (or s i milar) mess age:
PID TTY TIME CMD
2226 ? 00:00:00 esets_daemon
2229 ? 00:00:00 esets_daemon
At least two ESETS daemon processes are running in the background. The first PI D represents the process and threads manager
of the sys tem. The other represents the ESETS sca nning process .
7
Page 8

4. Architecture Overview
Once ESET Gateway Securi ty i s s uccessfully instal l ed, you s hould become familiar with its archi tecture.The system is
compris ed of the following parts:
CORE
The Core of ESET Gateway Security is the ESETS daemon (esets_daemon). The daemon uses ESETS API library libesets.so a nd
ESETS loading modules em00X_xx.dat to provide base sys tem tas ks s uch as scanni ng, mai ntenance of the agent daemon
process es, maintenance of the samples submission system, loggi ng, noti fi cation, etc. Please refer to the
page for details.
AGENTS
The purpos e of ESETS agent modul es is to integrate ESETS with the Linux, BSD and Sola ris Server environment.
UTILITIES
The utility modules provi de simple and effective management of the system. They are responsible for relevant sys tem tasks
such a s l i cense management, quarantine management, sys tem setup and upda te.
CONFIGURATION
Proper configuration is the most important aspect of a smooth-runni ng s ecurity system - the remai nder of this chapter is
dedicated to explaining all related components. A thorough unders tandi ng of the
this fi l e contai ns i nformati on essential to the confi guration of ESET Gateway Security.
esets.cfg
file is also hi ghl y recommended, as
esets_d a em on (8 )
man
After the product is s uccessfully i ns talled, all its confi guration components are stored in the ESETS configura tion di rectory.
The directory consists of the foll owing fi l es:
@ETCDIR@/esets.cfg
This i s the most i mportant configuration file, as it controls al l major a spects of the product‘s functionality. The esets.cfg file is
made up of s everal sections, each of which contai ns various para meters. The file contains one global and several “agent“
sections, with all section names enclosed in square bra ckets. Parameters i n the globa l section are used to define configura tion
options for the ESETS daemon as well a s default val ues for the ESETS scanning engine configura tion. Para meters in agent sections
are used to define confi guration options of modul es used to intercept vari ous data fl ow types in the computer and/or i ts
neighborhood, and prepare it for s canning. Note that in addition to the various parameters used for system configuration, there
are al s o rules governing the organization of the file. For detailed information on the most effective way to organize this fi l e,
please refer to the
@ETCDIR@/certs
This directory i s used to store the certifi cates used by the ESETS web interface for a uthentication. Please see the
man pa ge for detai l s .
@ETCDIR@/license
This directory i s used to store the product(s) license key(s) you have acquired from your vendor. Note that the ESETS daemon
wil l check only this directory for a valid l icense key, unless the
@ETCDIR@/scripts/license_warning_script
If enabl ed by the ESETS configuration file parameter
before product license expiration, sendi ng a n emai l notifi cation about the expira tion status to the sys tem administrator.
esets.cfg (5 )
and
esets_d a em on (8 )
man pa ges, as well a s relevant agents‘ man pages.
‘licen se_d ir’
‘licen se_w a rn_en a bled ’
parameter in the ESETS confi gurati on fi l e is redefined.
, this s cri pt will be executed 30 days (once per day)
esets_w w wi(8 )
@ETCDIR@/scripts/daemon_notification_script
If enabl ed by the ESETS configuration file parameter
by the antivi rus system. It is used to send email notifica tion about the event to the system admini strator.
8
‘ex ec_scrip t’
, this s cri pt is executed in the event of a detected infi l tration
Page 9
5. Integration with Internet Gateway services
ESET Gateway Security protects the organi za tion’s HTTP and FTP services a gainst virus es, worms, troj ans, spyware, phishing
and other internet threats. The term
review the process of ESET Gateway Security i ntegration with va rious services.
5.1 Transparent HTTP/FTP proxy configuration
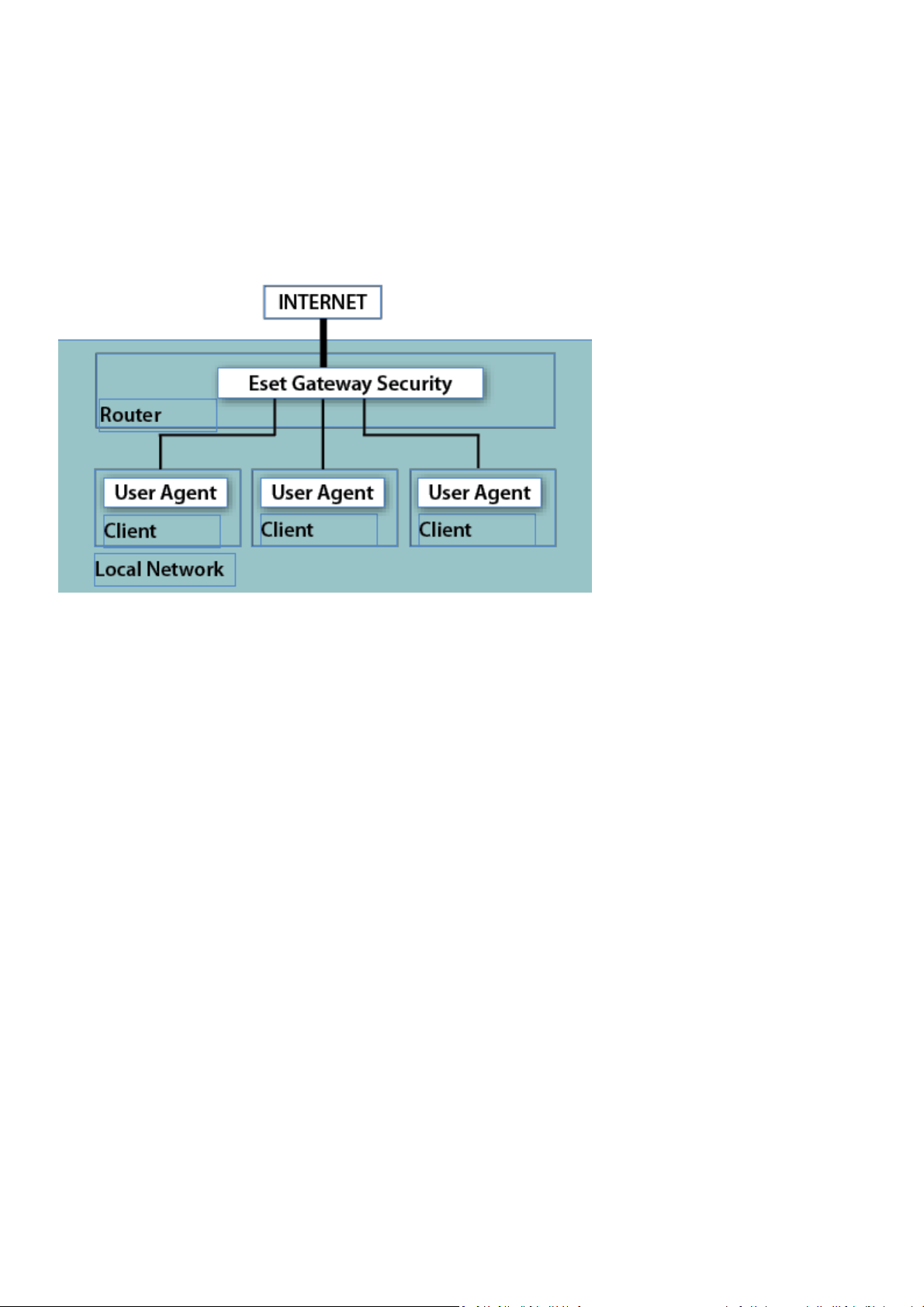
The configura tion for transparent proxying is based on a standard routing mechanism as shown i n Fi gure 5-1 below:
Figure 5-1. Scheme of ESET Gateway Security as a transparent proxy
Ga tew a y Server
refers to layer 3, or ‘router’ level of the ISO/OSI model. In this chapter we
The configura tion i s created naturally as kernel I P routing tabl es are defined on each loca l network cli ent. These routing
tabl es are used to establ i sh s tati c routes to the defaul t network gateway s erver (router). On a DHCP network, this is done
automatically. All HTTP (or FTP) communication with outbound s ervers i s then routed vi a network gateway server, where ESET
Gateway Security must be instal l ed in order to scan the communication for infiltrations. For this purpose, a generic ESETS HTTP
(or FTP) fil ter ha s been developed, called
To confi gure ESET Gateway Security to scan HTTP (or FTP) messages routed through the network gateway server, enter the
command:
/usr/sbin/esets_setup
Follow the ins tructions provided by the scri pt. When the ‘Available ins tallations /un-installations’ offer appears , choose the
‘HTTP’ (or FTP) option to display the ‘instal l /uninstal l ’ options , then choos e ‘instal l ’. This wi l l automatica l l y confi gure the
module to li s ten on a predefined port. It also redi rects IP pa ckets ori gi na ting from the selected network and wi th HTTP (or FTP)
destination port to the port where
destination ports will be scanned. If you also wis h to monitor other ports, equival ent redi rection rul es must be ass i gned.
In defaul t mode, the installer shows all steps which wi l l be performed and also creates a ba ckup of the configuration, which
can be restored at any time. The detai l ed i ns taller util i ty s teps for all pos sibl e scenarios are also descri bed i n a ppendi x A of this
document.
esets_h ttp
esets_h ttp
(or
(or
esets_ftp
esets_ftp
).
) listens. This means that onl y requests ori gi nally sent to HTTP (or FTP)
9
Page 10

5.2 Manual HTTP/FTP proxy configuration
The manual proxy configuration (see Figure 5-2) is characterized by explici tly configuri ng the proxied user agent to listen on a
specific port and address of the parent proxy.
Figure 5-2. Scheme of ESET Gateway Security as a manual proxy
Wi th this configuration, the proxy s erver us ual l y modi fi es transferred requests a nd/or respons es, i.e., non-transparent mode.
The manual proxying functional i ty of
such a s Squi d Proxy Cache and SafeSquid, as well as web browsers s uch as Mozilla Firefox, Opera , Netscape, and Konqueror. In
general, any HTTP user agent which s upports manua l pa rent proxy s ettings will cooperate with the
section, we descri be the manual proxy configura tion setting of
these are the most common HTTP user agent applications .
esets_h ttp
has been tested with a wide range of common user agents (i.e., proxy ca ches)
esets_h ttp
esets_h ttp
with Mozi l l a Firefox and Squi d Web Proxy Cache, as
module. In the next
5.2.1 Manual proxy configuration of Mozilla Firefox
The manual HTTP/FTP proxy confi guration of
This confi gurati on a l l ows ESET Gateway Securi ty to be installed anywhere within the local network, incl udi ng the gateway
server and the user a gent’s computer.
In the example below,
192.168.1.10, by specifying the foll owing parameters i n the
agent_enabled = yes
listen_addr = ”192.168.1.10”
listen_port = 8080
The para meter
To confi gure Firefox to use
then click the
the host name or IP address in the
exampl e, IP a ddress 192.168.1.10 and port 8080 s ha l l be specifi ed). To reread the newly created configura tion, reload the ESETS
daemon.
Set t ing s...
esets_h ttp
‘listen_a dd r’
button. In the
is confi gured to listen on port 8080 of a computer with l ocal network I P a ddress
can also be the host name which is visible from the local network.
esets_h ttp
, click
Co n n ectio n S ett ing s
HTTP P r o xy
esets_h ttp
with Mozi l l a Firefox is ill ustrated on Fi gure 5-2.
To o ls > O ptio n s
window, select the
(or
FTP P r ox y
[h t tp ]
section of the ESETS confi gurati on file:
from the main menu, and click
A d v a nced
M a nu a l P r ox y Con fig ura tio n
) field, a nd enter the Port values whi ch
. Cli ck the Network tab a nd
option. Finally, enter
esets_h ttp
listens on (i n thi s
It shoul d be noted that the configuration descri bed here is not opti mal for networks with a l arge number of client computers.
This i s becaus e the HTTP ca che (if any) is present only in the user a gent - thus, the same source object i s sca nned multiple times
when requested from different user agents.
10
Page 11
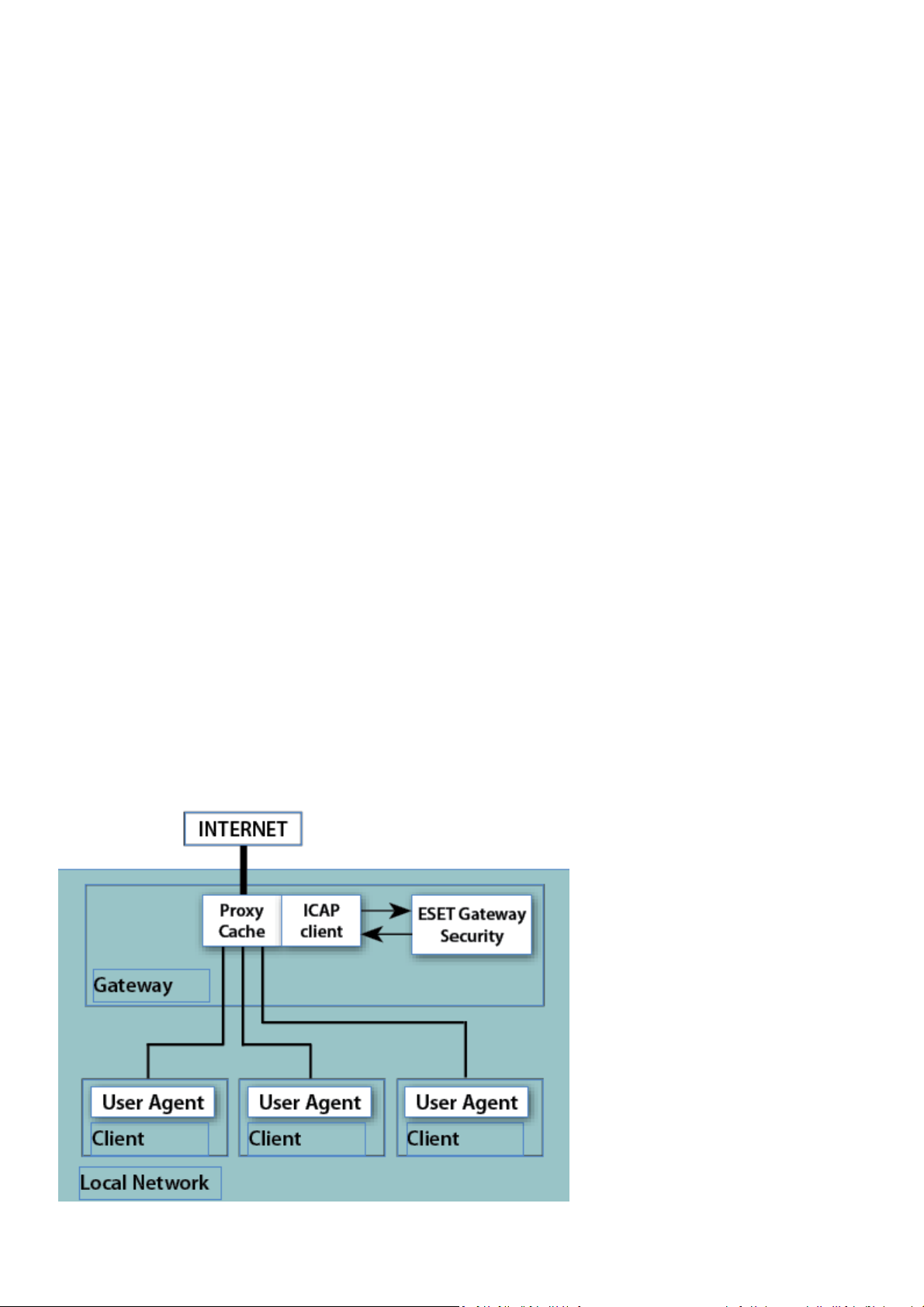
5.2.2 Manual proxy configuration of Squid Web Proxy Cache
The manual HTTP proxy confi guration of
Figure 5-2.
The signifi cant di fference from the previousl y descri bed configura tion i s that ESET Gateway Securi ty i s i ns talled on the HTTP/
FTP Gateway between the proxy cache (Squid Web Proxy in this exampl e) and the Internet. Thus, al l inbound HTTP/FTP
communica tions are firs t scanned for infiltrations and then stored in the dedicated network cache. In other words, al l previously
requested source objects present within the proxy cache are al ready checked for virus es and no addi tional checking is necessa ry
when requested again.
esets_h ttp
with the Squi d Web Proxy Cache is illustrated by the right ha nd s i de of
In the foll owing example,
of 192.168.1.10, by specifying the following parameters i n the
agent_enabled = yes
listen_addr = ”192.168.1.10”
listen_port = 8080
Note that the parameter
to al l ow
esets_h ttp
to listen to al l interfaces, by entering an address of 0.0.0.0. Use caution in the latter case, as users outside the
esets_h ttp
‘listen_a dd r’
is confi gured to listen on port 8080 of the gateway s erver, with a local network IP address
[h t tp ]
section of the ESETS confi gurati on file:
can be used to specify the host name visi ble from the local network and also can be used
local network would be allowed to use the HTTP/FTP scanner unl ess additional securi ty is added to prevent this .
To set up Squi d to use
cache_peer 192.168.1.10 parent 8080 0 no-query default
acl all src 0.0.0.0/0.0.0.0
never_direct allow all
esets_h ttp
as a pa rent proxy, add the following lines to the Squid config file (/etc/squid/squid.conf):
In the example above, Squid has been confi gured to use HTTP proxy listening at IP address 192.168.1.10 on port 8080 as a
parent proxy. All requests processed by Squi d wil l be passed to this destination. The remaini ng l i nes are used to confi gure error
message reporting i n the event that the parent proxy is down or becomes unreachable. To configure Squid to attempt direct
connections when the parent proxy is unreachabl e, add the foll owi ng pa rameters to the Squid configuration file:
cache_peer 192.168.1.10 parent 8080 0 no-query
prefer_direct off
To reread the newly created configura tion, reload the ESETS daemon.
5.3 Internet Content Adaptation configuration
The Internet Content Adaptati on i s a well known method aimed at providing object-based content vectori ng for HTTP services.
It i s based on the Internet Content Adaptation Protocol (ICAP) descri bed i n the RFC-3507 memo. Configuration for integrating the
ICAP s ervi ces i s shown i n Figure 5-3:
Figure 5-3. Scheme of ESET Gateway Security as a ICAP server.
The Proxy Cache receives the HTTP request from the User Agent and/or the respons e from the HTTP server and then
encapsulates the message into the ICAP request. The Proxy Cache must al s o work in this ca s e as the ICAP client and pas s the ICAP
11
Page 12

request for the mess age adaptation to ESET Gateway Security, namely to a generic ESETS ICAP server provides s canning of the encaps ulated message body for i nfi l tra tion. Based on the sca nning result, it then provi des an
appropriate ICAP response which is sent back to the ICAP cl i ent, or to the Proxy Cache, for further deli very.
To confi gureESET Gateway Security to scan HTTP messages which are encapsulated in ICAP requests, enter the command:
/usr/sbin/esets_setup
Follow the ins tructions provided by the scri pt. When the ‘Available ins tallations /un-installations’ offer appears , choose the
‘ICAP’ option to di spl ay the ‘ins tall/uninstal l ’ opti ons . Choose ‘instal l ’ to automatically configure the module to listen on a
predefined port and reload the ESETS daemon servi ce.
In defaul t mode, the installer shows all steps which wi l l be performed and also creates a ba ckup of the configuration, which
can be restored later at any time. The detailed installer utility steps for a l l poss i bl e scenari os a re also described in appendix A
of this documentation.
The second step of the ICAP configura tion method is a ctiva ting the ICAP cl i ent functional i ty within the Proxy Cache. The ICAP
cl i ent must be configured in order to properly request the
of the ICAP request must be entered as fol l ows:
METHOD icap://server/av_scan ICAP/1.0
In the above exampl e, METHOD i s the ICAP method used, ‘server’ is the server name (or IP address), and /av_scan is the
esets_icap i nfi l tra tions sca nning service identifi er.
esets_ica p
for the infiltration scanni ng s ervi ce. The initia l request line
esets_ica p
. The module
5.4 Large HTTP Objects Handling
Under normal conditions, objects are fi rst trans ferred from the HTTP server (or client) to
and then trans ferred to the HTTP client (or server). For large fil es (the large obj ects whose trans fer time is larger than the timeout
defined by the para meter
can caus e interrupts or even canceling of the object trans fer. Therefore, other methods of processing large objects must be
implemented. These are described in the foll owi ng two sections.
Method of deferred scan
Wi th
esets_h ttp
object transferred becomes too l arge,
as a client or server. After the last part of the object has arrived, the object is s canned for i nfiltrations . If the object ha s been
found a s i nfected, the last part of the object (last 4KB of obj ect’s data) i s not sent to the awaiting end-point and the connection to
the end-poi nt i s then dropped. Meanwhi l e, an email messa ge containing detai l s about the dangerous file trans fer i s s ent to the
Gateway administrator. This emai l notifi cati on i s s ent only i n a s erver-to-cli ent data tra ns fer. Additionall y, the URL of the source
object is stored in the
Be aware that the
file for the first time. This is because some parts of the al ready transferred data can contai n executabl e, dangerous code. For this
reas on, ESET developed a modified versi on of the
Partial scan technique
The
pa rtia l s ca n
pa rtia l s ca n
process i ng time of the object. This concept is especial l y evi dent with l a rge object HTTP transfers , as significantly more time is
needed to transfer the object than to scan it for i nfiltrations . This ass umption allows us to perform more than one scan during a
large object trans fer.
, a techni que known as the
technique has been developed as an addi tional safeguard to the
technique is bas ed on the idea that the scanning time of a large object is negligible compared to the overal l
‘lo _tim eou t’
esets_h ttp
deferred sca n
) this is not an optimal scenari o - the user agent's timeout setting or the user’s i mpatience
deferred sca n
esets_h ttp
cache in order to bl ock the source trans fer i f requested again.
technique descri bed above presents a potentia l risk to the computer requesting the infected
wil l begin to send the object trans pa rently to an awai ting HTTP end-point, such
deferred sca n
method of ha ndl i ng large fil es can be employed. This means that if the
technique, known as the ‘partial s can’ techni que.
deferred sca n
esets_h ttp
, scanned for i nfiltrations
method. The princi ple of the
To enabl e this techni que, the parameter
This wi l l cause l arge objects to be scanned for i nfi l tra tions during transfer in predefined intervals, whi l e the data which has
al ready been scanned i s sent to an awai ting end-poi nt s uch as a client or server. This method ensures that no i nfi l tra tions are
pass ed to the computer whose user a gent has requested the large infected object, because each portion of the sent data is
al ready verified to be safe.
It has been proven that in common ci rcumstances where the speed of the gateway’s local network connection is higher than
the speed of the gateway connection to the Internet, the total processing time of a large object trans fer us i ng the
technique is approximately the same as when the standard
12
‘lo _pa rtsca n_en a bled ’
deferred sca n
is entered in the
method is used.
[h t tp ]
section of the ESETS confi gurati on file.
pa rtia l s ca n
Page 13

5.5 ESETS plug-in filter for SafeSquid Proxy Cache
In previous sections we described the integration of ESET Gateway Security with HTTP and FTP servi ces us i ng
esets_ftp
. The methods described are appl i cable for the most common us er agents, incl uding the well known content filtering
esets _h ttp
and
internet proxy SafeSquid.
http://www.sa fesquid.com
However, ESET Gateway Security al s o offers an al ternative method of protecting Gateway s ervi ces, us i ng the
esets_ssfi.so
module.
5.5.1 Operation principle
The
esets_ssfi.so
module is a pl ug-i n to access al l objects processed by the SafeSquid proxy cache. Once the plug-in access es
the object, it is s canned for i nfil trations us i ng the ESETS daemon. If the object is i nfected, SafeSquid blocks the appropri ate
resource and sends the predefined templa te page instead. The
4.0.4.2 a nd later. Pleas e refer to the
esets_ssfi.so ( 1 )
man pa ges for more i nformation.
esets_ssfi.so
module is s upported by SafeSquid Advanced version
5.5.2 Installation and configuration
To integrate the module, you must create li nks from the SafeSquid modul es directory to the appropri a te installation locations
of the ESET Gateway Securi ty pa ckage. In the foll owi ng examples, it is as sumed that SafeSquid is instal l ed on a Linux OS in the ‘/
opt/sa fesquid’ di rectory.
If Sa feSqui d 4.2 or later i s instal l ed, enter the following commands:
mkdir /opt/safesquid/modules
ln -s @LIBDIR@/ssfi/esets_ssfi.so /opt/safesquid/modules/esets_ssfi.so
ln -s @LIBDIR@/ssfi/esets_ssfi.xml /opt/safesquid/modules/esets_ssfi.xml
If a n earl i er vers i on is i nstalled, enter the foll owing commands :
mkdir /opt/safesquid/modules
ln -s @LIBDIR@/ssfi/esets_ssfi.so /opt/safesquid/modules/esets_ssfi.gcc295.so
ln -s @LIBDIR@/ssfi/esets_ssfi.xml /opt/safesquid/modules/esets_ssfi.xml
/etc/init.d/safesquid restart
To complete the SafeSquid pl ug-i n i nstallation, first logon to the SafeSquid Web Administration I nterface. Select the
menu from the mai n i nterface page and browse
and create the
a nt ivir us
profi l e for the
ES ET G a tew ay S ecu r it y
Select a Sectio n t o C on fig ur e
section by cl i cking the
until you fi nd ESET Gateway Security. Cli ck
A d d
button at the bottom. Define the below
parameters wi thin the list that appears and click Submit. Remember to save the Safesquid configuration by clicki ng the
set t ing s
Comment: ESET Gateway Security
Profiles: antivirus
button.
Co n fig
Subm it
Sa v e
The SafeSquid pl ug-i n i s operati ona l i mmediately after instal l ation, but additional fine tuning s hould be performed. In the
following paragraphs , we expla i n how to configure SafeSquid to use ESETS predefined blocki ng templa tes, i n the event that a
transferred source object is i nfected (or not scanned).
Logon to the SafeSquid Web Admini s tra tion Interface. Select the
Sect ion to Con fig ur e
bottom of the
Infected template: esets_infected
Not scanned template: esets_not_scanned
After submitting the li s t of templa tes, navigate to the
until you fi nd
ESET Ga tew a y Securit y
ES ET G a tew ay S ecu r it y
. Next, edit the newly created antivi rus profi l e by clicki ng
section. Then define the following para meters in the li s t that appears:
Temp la tes
Co n fig
menu from the mai n interface page and brows e
page of the mai n
Co n fig
menu. You will see a
Ed it
Pa th
Select a
at the
parameter
that defines the SafeSquid templates directory path. Ass uming the parameter is ‘/opt/safesquid/safesqui d/templa tes’, ensure
that an appropri ate directory exi sts and if not, create it. In order to access the ESETS predefined templates from withi n thi s
directory, add the appropri ate li nks using the foll owi ng commands:
ln -s @LIBDIR@/ssfi/templates/ssfi_infected.html \
/opt/safesquid/safesquid/templates/ssfi_infected.html
ln -s @LIBDIR@/ssfi/templates/ssfi_not_scanned.html \
/opt/safesquid/safesquid/templates/ssfi_not_scanned.html
Next, cl ick
A d d
in the
Temp la tes
section to add the new templa te defini tions to the SafeSqui d confi gurati on. The following
parameters mus t be defined within the li s t that appears for the infected ESETS blocking page:
13
Page 14

Comment: ESET Gateway Security infected template
Name: esets_infected
File: ssfi_infected.html
Mime type: text/html
Response code: 200
Type: File
Parsable: Yes
For the unsca nned ESETS blocki ng page, the list is a s fol l ows :
Comment: ESET Gateway Security not scanned template
Name: esets_not_scanned
File: ssfi_not_scanned.html
Mime type: text/html
Response code: 200
Type: File
Parsable: Yes
To reread the newly created configura tion, reload SafeSquid and the ESETS daemon.
14
Page 15

6. Important ESET Gateway Security mechanisms
6.1 Handle Object Policy
The Handl e Obj ect Pol i cy (see figure 6-1) mechanism provi des filtering of sca nned obj ects based on their status. This
functi ona l i ty is based on the foll owing confi gurati on options:
action_av
action_av_infected
action_av_notscanned
action_av_deleted
For detai l ed i nformation on these options, please refer to the
Figure 6-1. Scheme of Handle Object Policy mechanism.
Every object process ed is firs t handl ed accordi ng to the configuration of the
(or
‘d efer’, ‘d isca rd’, ‘reject’
scanned for virus i nfi l tra tions , and if the
confi guration options
eval uate handl i ng of the object. If an
accepted. Otherwise, the object is blocked.
) the object i s accepted (or deferred, dis carded, rejected). If the option i s s et to
‘a v_clea n_m od e
‘a ctio n_a v_in fected
’,
‘a ctio n_a v_n ots ca nn ed
‘a ccep t’
action has been taken as a resul t of these three action options, the object is
esets.cfg (5 )
’ option is set to
’ and
‘a ctio n_a v_d eleted
man pa ge.
‘a ctio n_a v‘
‘yes
’, the object is a l s o cleaned. In addition, the
option. If this option is set to
‘sca n’
the object i s
’ are taken into account to further
‘a ccep t’
6.2 User Specific Configuration
The purpos e of the User Speci fi c Confi gurati on mechani sm is to provi de a hi gher degree of cus tomization and functionality. It
al l ows the sytem admini strator to define ESETS anti vi rus scanner pa rameters ba sed on the user who is accessing file sys tem
objects.
A detai l ed description of this functiona l i ty can be found in the
short example of a us er-s peci fi c configuration.
In this example, the
IP address of 192.168.1.10. The functiona l i ty of
following lines:
[http]
agent_enabled = yes
listen_addr = "192.168.1.10"
listen_port = 8080
action_av = "scan"
To provi de indi vidual parameter settings, define the
where the individual setting wil l be stored. In the next example, we create a reference to the special confi gurati on fi l e
‘es ets_http_s p ec.cfg ’
esets_h ttp
module is us ed to control HTTP traffic on port 8080 of the gateway server, with a local network
esets_h ttp
is based on the
‘u ser_con f ig ’
, which is located in the ESETS confi guration directory. See below:
esets.cfg (5 )
parameter with the path to the special confi guration file
man pa ge; in thi s section we wil l provide onl y a
[h t tp ]
section of the ESETS confi gurati on file. See the
15
Page 16

[http]
agent_enabled = yes
listen_addr = "192.168.1.10"
listen_port = 8080
action_av = "scan"
user_config = "esets_http_spec.cfg"
Once the special confi guration file is referenced from within the
[h t tp ]
section, create the
‘es ets_http_s p ec.cfg ’
file in the ESETS
confi guration directory and add the appropriate indivi dua l s ettings. The next example shows the individual setting for
parameter
[|192.168.1.40]
action_av = "reject"
‘a ctio n_a v’
, for the cl i ent computer with I P a ddress 192.168.1.40. See below:
Note that the section header identifi es the HTTP cl i ent for which the individual settings have been created, and the section
body contai ns individua l para meters for that HTTP client. With this speci al configura tion, HTTP traffi c for al l l ocal network
cl i ents wi l l be processed normal l y, i .e. scanned for i nfi l trations . However, access for the HTTP cl i ent with the IP address
192.168.1.40 wi l l be rejected (blocked).
6.3 Blacklist and Whitelist
In the foll owing example we demonstrate blackl i s t and whiteli s t creation for the
scanner. Note that the confi guration descri bed i n the previous s ection i s us ed for this purpos e.
To create a blackl i s t used by
‘es ets_http_s p ec.cfg ’
[black-list]
action_av = "reject"
, introduced in the previous section. See below:
esets_h ttp
, create the foll owing group s ection within the speci a l confi guration fi l e
Next, add the HTTP server to the ‘black-l i s t’ group. To do thi s , the following special s ection must be created:
[aaa.bbb.ccc.ddd]
parent_id = "black-list"
esets_h ttp
configured as a n HTTP proxy
In the example above, ‘aaa.bbb.ccc.ddd’ is the IP a ddress of the server added to the ‘black-l i s t’. All HTTP traffic related to the
specified server wil l now be rejected, i.e. the server wil l be blocked.
To create the ‘white-li s t’ used by
confi guration file
[white-list]
action_av = "accept"
‘es ets_http_s p ec.cfg ’
esets_h ttp
it is necessary to create the foll owing group section within the speci al
which was introduced in the previous section. See below:
Adding HTTP servers to the li s t is self-expla na tory.
6.3.1 URL Whitelist
Whi teli s ting URL's can help you especial l y when you are experiencing problems with data streaming (e.g. video conferencing
dela ys ). To start creating a URL whiteli s t, that will be used by
esets_h ttp
, add the desired URL address(es) to the
wh itelist_u rl
confi guration file located in the @ETCDIR@/http directory a s fol l ows:
echo "streaming.address.com:80/*" >> @ETCDIR@/http/whitelist_url
NOTE: The syntax of the URL Whitelist compri s es a list of URL addresses (one per l i ne) as can be seen in the
esets_h ttp
output.
ESETS reads the list from the
more information please read the
wh itelist_u rl
esets_h ttp (1 )
file. After addi ng or removing URL addresses, pl ease restart the ESETS daemon. For
manpa ge.
6.4 Samples Submission System
logging
The Samples s ubmission system is an intell i gent
Th rea tSense.Net
technology that collects infected objects which have been
detected by advanced heuri s tics and delivers them to the samples s ubmission s ys tem server. All vi rus samples collected by the
sampl e submis s i on system wil l be processed by the ESET virus laboratory a nd if necess ary, added to the ESET virus signature
database.
NOTE: Accordi ng to our license agreement, by enabl i ng sa mple submis s i on s ys tem you are agreeing to al l ow the computer
and/or pla tform on which the esets_daemon is instal l ed to collect data (which may include personal information about you
and/or the user of the computer) and samples of newly detected virus es or other threats and send them to our vi rus lab. This
feature is turned off by defaul t. All i nformation collected wil l be used onl y to analyze new threats and will not be used for any
other purpose.
16
Page 17

In order to acti vate the Sampl es Submissi on System, the sampl es submis s i on system cache must be ini tialized. This can be
achieved by enabl i ng the
deli very of sampl es to the ESET virus laboratory s ervers , the parameter
‘sa mp les _en ab led ’
option in the
[g loba l]
section of the ESETS confi gurati on file. To al l ow for the actual
‘sa mp les _sen d_perio d ’
must also be specified in the same
section.
In addition, users can choose to provide the ESET virus labora tory team with suppl ementary information us i ng the
‘sa mp les _p ro vider_m a il’
and/or
‘sa mp les _p ro vider_cou n try ’
configuration options. The information collected usi ng these options
wil l a ssist in providing the ESET team with an overview about a given infiltration which may be spreadi ng over the Internet.
For more information on the Samples Submission Sys tem, refer to the
esets_d a em on (8 )
man pa ge.
6.5 Web Interface
The Web Interface al l ows us er-friendly configuration, admini s tration and l i cense mana gement of ESET Securi ty s ys tems. This
module is a separate agent and must be expl i citly enabl ed. To quickl y confi gure the
the ESETS configura tion fi l e and restart the ESETS daemon:
[wwwi]
agent_enabled = yes
listen_addr = address
listen_port = port
username = name
password = pass
Replace the text in ital i cs with your own va l ues and di rect your browser to
‘u sern a me/p a ssw o rd ’
found on the
esets_w w wi(1 )
. Basic usage instructions can be found on the help pa ge and technical detai l s about
man pa ge.
The web interface allows you to remotely access the ESETS daemon and depl oy i t eas i l y. Thi s powerful uti l i ty makes it easy to
read and write configura tion va l ues.
Figure 6-1. ESET Security for Linux - Home screen.
W eb In terf a ce
‘h ttp s ://a dd res s:p o rt’
, set the foll owi ng opti ons i n
(note the https). Login with
esets_w w wi
can be
The web interface window of ESET Gateway Security is divided into two mai n sections . The pri mary window, that s erves to
display the contents of the selected menu option a nd the mai n menu. This hori zontal bar on the top l ets you navigate between the
following mai n options:
Hom e
- provides ba s i c system and ESET product information
L icen ses
Co n fig ura tio n
Co n t ro l
Help
L o g out
- is a license management utility, see the following chapter for mode detai l s
- you can cha nge the ESET Gateway Securi ty system configuration here
- allows you to run s i mpl e tasks and vi ew global statisti cs about objects processed by esets_daemon
- provides detai l ed us age instructions for the ESET Gateway Securi ty web interface
- use to end your current sess i on
17
Page 18

6.5.1 License management
You can upl oad a new license usi ng the Web interface, as s hown in Figure 6-2.
If you want to dis pl a y l i censes in the cons ol e, use the following command:
/usr/sbin/esets_lic --list
If you want to import new license fil es, use the following command:
/usr/sbin/esets_lic --import *.lic
Figure 6-2. ESET Licenses.
You can enable the license notifi cation option in the
Glo b a l
section options. If enabled, this functionality wil l notify you 30
days pri or to your license expiration.
6.5.2 Agent HTTP configuration example
ESETS can be configured in two ways . In this exampl e we will demonstrate how to use both when configuri ng the HTTP module,
leaving you the choice of your preferred confi guration method:
Usi ng the ESETS configuration file:
[http]
agent_enabled = yes
listen_addr = "0.0.0.0"
listen_port = 8080
18
Page 19

Usi ng the web interface:
Figure 6-3. ESETS - Configuration > HTTP Proxy.
Always remember to sa ve your new configuration by cl i cking
button in the
Co n fig ura tio n sect ions
panel.
Sa v e cha ng es
. To appl y your new changes cl i ck the
A p p ly cha ng es
6.5.2.1 HTTP Agent testing with the Mozilla Firefox
To test ESETS HTTP Agent on your local machi ne, you need to set the local proxy server to ‘localhos t:8080’. See the figure below
for a n example of such confi guration i n the Mozilla Firefox brower:
Figure 6-5. Mozilla Firefox - Network Settings.
NOTE: You do not need to configure the local machi nes connected to the ESETS server in the same manner. However, you wil l
stil l need to set a transparent http proxy vi a netfil ter (s ee section A.1 for details).
19
Page 20

If a ttempt to open an i nfected fil e, a warni ng mess a ge si mi l ar to the one on the figure below will display in your browser
window:
Figure 6-6. ESETS warning message.
6.5.3 Statistics
You can vi ew statisti cs for all of acti ve ESETS agents here.
Figure 6-5. ESETS - Control > Statistics.
Sta tist ics
summary refreshes every 10 seconds.
6.6 Remote Administration
ESETS supports ESET Remote Admini s tration for gateway security management in l a rge computer networks. The ESETS Remote
Admini stration Client is pa rt of the mai n ESETS daemon and performs the fol l owing functions:
Communicates with ERA Server and provides you with system informati on, confi guration, protection statuses and s everal
other features
All ows cl i ent configurations to be viewed/modifi ed us i ng the ESET Confi guration Edi tor and implemented with the help of
confi guration tasks
Can perform
Performs On-demand scans a s requested, and submits the resul ting back to ERA Server
NOTE: For this option to be available you must have a valid license for ESET Fil e Security.
Adds l ogs of notabl e sca ns performed by the ESETS daemon to
Sends al l non-debug messages to
20
Upd a te No w
tasks
Sca n L o g
Th r ea t L og
Ev ent L o g
Page 21

These functi ona l i ties are not supported:
Firewal l Log
Remote Instal l
Figure 6-6. ERA Console tabs.
For more information, pl ease read the ESET Remote Admini s trator manual. This manual is loca ted on our web site at the
following link:
http://www.eset.com/documentation
6.6.1 Remote Administration usage example
Before commenci ng any remote admini stration process ensure your s ys tem fulfi l l s the three foll owi ng prerequisites:
Runni ng ERA Server
Runni ng ERA Console
Enabl e RA Client in the ESETS daemon. Ensure that firewal l settings do not block traffic to ERA Server or vice vers a.
To setup the bas i cs, specify the address of your ERA Server in the
to access the ERA Console password, you must edit the value of the
‘ra cl_serv er_a dd r’
‘ra cl_pa sswo rd ’
parameter first. If you are using a pas s word
parameter accordi ngl y. Change the value of
the ‘racl_interval’ parameter to adj us t the frequency of connections to ERA Server (i n minutes).
You can either use the web interface (see also previous chapter) to appl y the new confi guration, or you can adjust these
parameters i n the
racl_server_addr = "yourServerAddress"
racl_server_port = 2222
racl_password = "yourPassword"
racl_interval = 1
NOTE: All a pplicable ESET Remote Admini s tra tion Cl i ent variables are l isted on the
[g loba l]
section of the ESETS confi gurati on file as follows:
esets_d a em on (8 )
man pa ge.
The ESETS daemon confi guration wil l be reloa ded and RACL will connect to ERA Server. You wil l be abl e to see a newly
connected client in your ERA Console. Press the F5 button (or
M enu > V iew > R efr esh
) to manua l ly refresh the list of connected
cl i ents.
Figure 6-7. ERA Console.
By using ERA Consol e you can create a confi guration task to ESETS daemon from ERA Console:
Right click the connected
Navi gate to
Expand
N ew Ta sk > Co n fig ura tio n Ta sk > C r ea te...
Unix ES ET Secu r ity t ree
Clien t N a m e
For a n example of a confi gurati on task by the DAC agent, see below:
21
Page 22

Figure 6-8. ERA Configuration Editor.
The
N ew Ta sk
context menu contains On-demand scanni ng options (enabl ed/disabled cleani ng).
You can select the desi red product, that you wish to set the task for, in the
Co n fig ura tio n S ect ion
drop-down menu. Make sure that you s elect the
(i.e. the product that is instal l ed on your target workstation).
Figure 6-9. ERA On-demand scan.
O n -D em a nd S ca n
pop-up window in the
O n -d em a nd S ca n t a sk fo r Unix ESET S ecu rit y P r o duct
option
22
Page 23

6.7 Logging
ESETS provides s ys tem daemon logging via s ys l og.
Syslo g
is a s tandard for l oggi ng program messages and ca n be us ed to log
system events s uch as network and securi ty events.
Messages refer to a facility:
auth, authpriv, daemon, cron, ftp, lpr, kern, mail, ..., local0, ..., local7
Messages are ass i gned a priori ty/level by the sender of the mess age:
Error, Warning, Summall, Summ, Partall, Part, Info, Debug
This s ection describes how to confi gure and read the logging output of s ys l og. The
‘d a em o n’
interface. Modify the value of the
) defines the sysl og facility used for l ogging. To modify syslog settings edit the ESETS confi guration file or use the web
‘syslo g _cla ss’
parameter to change the logging cl a s s. We recommend you modify these settings
‘syslo g _fa cility ’
option (default val ue
only i f you are familiar with syslog. For an example of s ys l og confi guration s ee below:
syslog_facility = "daemon"
syslog_class = "error:warning:summall"
The name and l ocation of the log file depend on your s ys l og i ns tallation a nd confi guration (e.g. rsyslog, syslog-ng, etc.).
Standa rd filenames for syslog output fi l es are for example
‘syslo g ’, 'd a em on .lo g '
, etc. To follow syslog activity, run one of the
following commands from the cons ol e:
tail -f /var/log/syslog
tail -100 /var/log/syslog | less
cat /var/log/syslog | grep esets | less
If you enable ESET Remote Administration, ERA log entries ol der than given days by the option
‘ra cl_lo g s_lifetim e’
wil l be
automatically deleted.
23
Page 24

7. ESET Security system update
7.1 ESETS update utility
To maintai n the effectiveness of ESET Gateway Security, the virus si gnature databas e must be kept up to date. The esets_update
util i ty ha s been developed for this purpose. See the
options
In the event that your s erver access es the Internet via HTTP proxy, the addi tional configuration options
must be defined. If access to the HTTP proxy requires a us ername and pass word, the
options must also be defined in this s ecti on. To ini tiate an update, enter the following command:
the world - new patterns are added to the virus signature database in very short intervals. For thi s reason, we recommend that
updates be initiated on a regular ba sis. To specify the update frequency, the
[g loba l]
virus s i gnature databa se.
‘a v_u p d ate_u sern am e’
@SBINDIR@/esets_update
To provi de the highest pos sibl e securi ty for the end us er, the ESET team continuously collects vi rus definitions from all over
section of the ESETS confi gurati on file. The ESETS daemon must be up and runni ng in order to successfully update the
and
‘a v_u p d ate_p assw ord ’
7.2 ESETS update process description
The update process consists of two stages: First, the precompi l ed upda te modules are downloaded from the ESET server. If the
option
‘a v_mirro r_ena bled ’
modules are created in the foll owing directory:
is set to ‘yes’ in the
esets_u pd a te( 8 )
[g loba l]
section of the ESETS confi gurati on file, copies (or mirror) of these update
man pa ge for detai l s . To launch an update, the confi guration
must be defined in the
‘a v_u p d ate_p erio d ’
[g loba l]
section of the ESETS confi gurati on file.
‘p ro xy _u s ern a me’
‘p ro xy _a dd r’, ‘p ro xy _p o rt’
and
‘p ro xy _p a ssw o rd ’
option must be defined in the
@BASEDIR@/mirror
If desired, the Mirror directory path can be redefined using the
confi guration file. The newly created Mirror can then serve as a ful l y functi ona l update server and ca n be used to create lower
(chi l d) Mirror servers. See section 7.3 for detai l s .
The option
securi ty products. These modules can be mirrored from the ESET server.
NOTE: Once you set your us erna me, password a nd l i cense for ESET Gateway Security to download PCU's for ESET NOD32
Antivi rus / ESET Smart Security, please contact our Technical Support and request a change, that will enable your ESET Gateway
Securi ty to downl oa d PCU's for our Wi ndows-ba s ed products.
The second stage of the update process i s the compilation of modules l oada bl e by the ESET Gateway Security scanner from
those stored in the local mirror. Typica l l y, the following ESETS loading modules a re created: loader module (em000.da t), scanner
module (em001.dat), virus si gna ture databas e module (em002.dat), archives s upport modul e (em003.dat), adva nced heuristics
module (em004.dat), etc. The modules are created in the following directory:
@BASEDIR@
This i s the directory where the ESETS daemon loa ds modul es from and thus can be redefined us i ng the
[g loba l]
‘a v_mirro r_p cu ’
section of the ESETS confi gurati on file.
al l ows you to download Program Component Update (PCU) modules for Windows -based ESET
‘a v_mirro r_d ir’
option in the
[g loba l]
section of the ESETS
‘b a se_d ir’
option in the
7.3 ESETS mirror http daemon
ESETS mirror http daemon is instal l ed automatically with ESET Gateway Security. The http mirror daemon starts i f the option
‘a v_mirro r_h ttp d _en a bled ’
in the
[g loba l]
section of the ESETS confi gurati on file i s set to
‘yes’
and the Mirror is enabl ed.
Options
addresses) where the http server listens.
The option
‘a v_mirro r_h ttp d _usern am e’
access the Mirror.
24
‘a v_mirro r_h ttp d _po rt’
‘a v_mirro r_h ttp d _a u th_m od e’
and
and
‘a v_mirro r_h ttp d _pa ssw ord ’
‘a v_mirro r_h ttp d _a d dr’
al l ows access a uthentication (defaul t: none) to be changed to bas i c. The options
define the port (default 2221) and address (default: all local tcp
al l ow an administrator to define the login and password us ed to
Page 25

8. Let us know
Dear user, we hope this Gui de has provided you with a thorough understanding of the requirements for ESET Gateway Securi ty
instal l ation, confi guration and mai ntenance. However, our goa l i s to continual l y improve the qual i ty and effectiveness of our
documentation. If you feel that any sections in this Guide are unclear or i ncomplete, please let us know by contacting Customer
Care:
http://www.eset.com/support
or us e di rectly the support form:
http://www.eset.eu/support/form
We are dedicated to provide the highest l evel of support and l ook forward to helpi ng you shoul d you experience any problems
concerni ng this product.
25
Page 26

9. Appendix A. ESETS setup and configuration
9.1 Setting ESETS for scanning of HTTP communication - transparent mode
HTTP scanning is performed using the
esets_h ttp
daemon. In the
[h t tp ]
section of the ESETS confi gurati on file, set the following
parameters:
agent_enabled = yes
listen_addr = "192.168.1.10"
listen_port = 8080
In the example above,
step is to redirect all HTTP requests to
‘listen_a dd r’
is the address of the local network interface named ‘if0’. Restart the ESETS daemon. The next
esets_h ttp
. If IP-fi l tering is being performed by the ipcha i ns administration tool, an
appropriate rule would be:
ipchains -A INPUT -p tcp -i if0 --dport 80 -j REDIRECT 8080
If I P-fi l teri ng i s being performed by the iptables administration tool, the rul e is:
iptables -t nat -A PREROUTING -p tcp -i if0 --dport 80 -j REDIRECT --to-ports 8080
On FreeBSD, the rule is :
ipfw add fwd 192.168.1.10,8080 tcp from any to any 80 via if0 in
On NetBSD and Sol a ris, the rul e is:
echo 'rdr if0 0.0.0.0/0 port 80 -> 192.168.1.10 port 8080 tcp' | ipnat -f -
9.2 Setting ESETS for scanning of FTP communication - transparent mode
FTP scanni ng i s performed usi ng the
parameters:
esets_ftp
daemon. In the
[ftp ]
section of the ESETS confi gurati on file, set the following
agent_enabled = yes
listen_addr = "192.168.1.10"
listen_port = 2121
In the example above,
redirect all FTP requests to
‘listen_a dd r’
esets_ftp
is the address of the local network interface named ‘if0’. Restart the ESETS daemon. Then,
. If IP-fi l tering is being performed by the ipcha i ns administration tool, an a ppropriate rul e
would be:
ipchains -A INPUT -p tcp -i if0 --dport 21 -j REDIRECT 2121
If I P-fi l teri ng i s being performed by the iptables administration tool, the rul e is:
iptables -t nat -A PREROUTING -p tcp -i if0 --dport 21 -j REDIRECT --to-ports 2121
On FreeBSD, the rule is :
ipfw add fwd 192.168.1.10,2121 tcp from any to any 21 via if0 in
On NetBSD and Sol a ris, the rul e is:
echo 'rdr if0 0.0.0.0/0 port 21 -> 192.168.1.10 port 2121 tcp' | ipnat -f -
9.3 Setting ESETS for scanning of ICAP encapsulated HTTP messages
ICAP enca ps ul a ted HTTP message scanning is performed using the
confi guration file, set the following parameters:
agent_enabled = yes
listen_addr = "192.168.1.10"
listen_port = 1344
esets_ica p
daemon. In the
[ica p]
section of the ESETS
In the example above,
restart the ESETS daemon.
26
‘listen_a dd r’
is the address of the local network interface named ‘if0’. After adding these parameters,
Page 27

10. Appendix B. PHP License
The PHP License, version 3.01 Copyright (c) 1999 - 2006 The PHP Group. All rights reserved.
Redis tri bution and use in source and binary forms, with or wi thout modifica tion, is permitted provi ded that the foll owi ng
conditions a re met:
1. Redis tri butions of source code must retain the above copyri ght notice, this list of condi ti ons a nd the fol l owing di s clai mer.
2. Redis tri butions i n binary form must reproduce the above copyright notice, this l i st of conditions and the foll owing disclaimer
in the documentation and/or other material s provi ded with the dis tri bution.
3. The name “PHP” must not be used to endors e or promote products deri ved from this s oftware without prior written
permis s i on. For wri tten permission, pleas e contact group@php.net.
4. Products deri ved from this software may not be called “PHP”, nor may “PHP” appear in their name, without prior written
permis s i on from group@php.net. You may indi cate that your software works in conjunction with PHP by sayi ng “Foo for PHP”
instead of cal l i ng i t “PHP Foo” or “phpfoo”
5. The PHP Group may publ i s h revised and/or new versi ons of the li cense from time to time. Each version will be given a
distinguishing version number. Once covered code has been publ i s hed under a particul ar vers i on of the li cense, you may
al ways continue to use it under the terms of that vers i on. You may also choose to use such covered code under the terms of
any subsequent versi on of the li cense publ i s hed by the PHP Group. No one other than the PHP Group ha s the right to modify
the terms appl i cable to covered code created under thi s License.
6. Redis tri butions of any form whatsoever must retain the following acknowledgment: “This product incl udes PHP software,
freely a vailable from <http://www.php.net/software/>”.
THIS SOFTWARE IS PROVIDED BY THE PHP DEVELOPMENT TEAM "AS IS" AND ANY EXPRESSED OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
DISCLAIMED. IN NO EVENT SHALL THE PHP DEVELOPMENT TEAM OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE
GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT
OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSI BILITY OF SUCH DAMAGE.
27
 Loading...
Loading...