查询COP87L88EK Family供应商
COP87L88EK/RK Family
8-Bit CMOS OTP Microcontrollers with 8k or 32k
Memory, Comparator, and Single-slope A/D Capability
General Description
The COP87L88EK/RK Family OTP (One Time Programmable) microcontrollers are highly integrated COP8
ture core devices with 16k or 32k memory and advanced
features including a Multi-Input Comparator and
Single-slope A/D capability. These multi-chip CMOS devices
are suited for applications requiring a full featured, low EMI
controller with an analog comparator, current source, and
voltage reference, and as pre-production devices for a
masked ROM design. Lower cost pin and software compatible 8k ROM versions (COP888EK) are available forusewith
a range of COP8 software and hardware development tools.
COP87L88EK/RK Family, 8-Bit CMOS OTP Microcontrollers with 8k or 32k Memory, Comparator,
and Single-slope A/D Capability
July 1999
Family features include an 8-bit memory mapped architecture, 10 MHz CKI (-XE=crystal oscillator) with 1 µs instruc-
™
tion cycle, three multi-function 16-bit timer/counters with
Fea-
PWM, MICROWIRE/PLUS
parator with seven input multiplexor, an analog current
source and V
modes, idle timer, MIWU, high current outputs, software selectable I/O options, WATCHDOG
2.7V to 5.5V operation and 28/40/44 pin packages.
Devices included in this datasheet are:
/2 reference, two power saving HALT/IDLE
CC
™
serial I/O, one analog com-
™
timer and Clock Monitor,
Device Memory (bytes) RAM (bytes) I/O Pins Packages Temperature
COP87L84EK 16k OTP EPROM 256 24 28 DIP/SOIC -40 to +85˚C
COP87L88EK 16k OTP EPROM 256 36/40 40 DIP, 44 PLCC -40 to +85˚C
COP87L84RK 32k OTP EPROM 256 24 28 DIP/SOIC -40 to +85˚C
COP87L88RK 32k OTP EPROM 256 36/40 40 DIP, 44 PLCC -40 to +85˚C
Key Features
n Analog function block with
— Analog comparator with seven input multiplexor
— Constant current source and V
n Three 16-bit timers, each with two 16-bit registers
supporting:
— Processor Independent PWM mode
— External Event counter mode
— Input Capture mode
n 8 or 32 kbytes on-board EPROM with security feature
n 256 bytes on-board RAM
/2 reference
CC
Additional Peripheral Features
n Idle Timer
n Multi-Input Wake Up (MIWU) with optional interrupts (8)
n WATCHDOG and Clock Monitor logic
n MICROWIRE/PLUS serial I/O
I/O Features
n Software selectable I/O options ( TRI-STATE™Output,
Push-Pull Output, Weak Pull-Up Input, High Impedance
Input)
n Packages:
— 44 PLCC with 40 I/O pins
— 40 DIP with 36 I/O pins
— 28 DIP/SO with 24 I/O pins
n Schmitt trigger inputs on Port G and L
CPU/Instruction Set Feature
n 1 µs instruction cycle time
n Twelve multi-source vectored interrupts servicing
— External Interrupt with selectable edge
— Idle Timer T0
— Three Timers (Each with 2 interrupts)
— MICROWIRE/PLUS
— Multi-Input Wake Up
— Software Trap
— Default VIS (default interrupt)
n Versatile and easy to use instruction set
n 8-bit Stack Pointer (SP)—stack in RAM
n Two 8-bit Register Indirect Data Memory Pointers
(B, X)
Fully Static CMOS
n Two power saving modes: HALT and IDLE
n Single supply operation: 2.7V to 5.5V
n Temperature ranges: −40˚C to +85˚C
Development Support
n Emulation devices for the COP888EK/COP884EK
n Real time emulation and full program debug offered by
MetaLink Development System
COP8™is a trademark of National Semiconductor Corporation.
MICROWIRE/PLUS
TRI-STATE
WATCHDOG
iceMASTER
© 1999 National Semiconductor Corporation DS101133 www.national.com
™
is a trademark of National Semiconductor Corporation.
®
is a registered trademark of National Semiconductor Corporation.
™
is a trademark of National Semiconductor Corporation.
™
is a trademark of MetaLink Corporation.
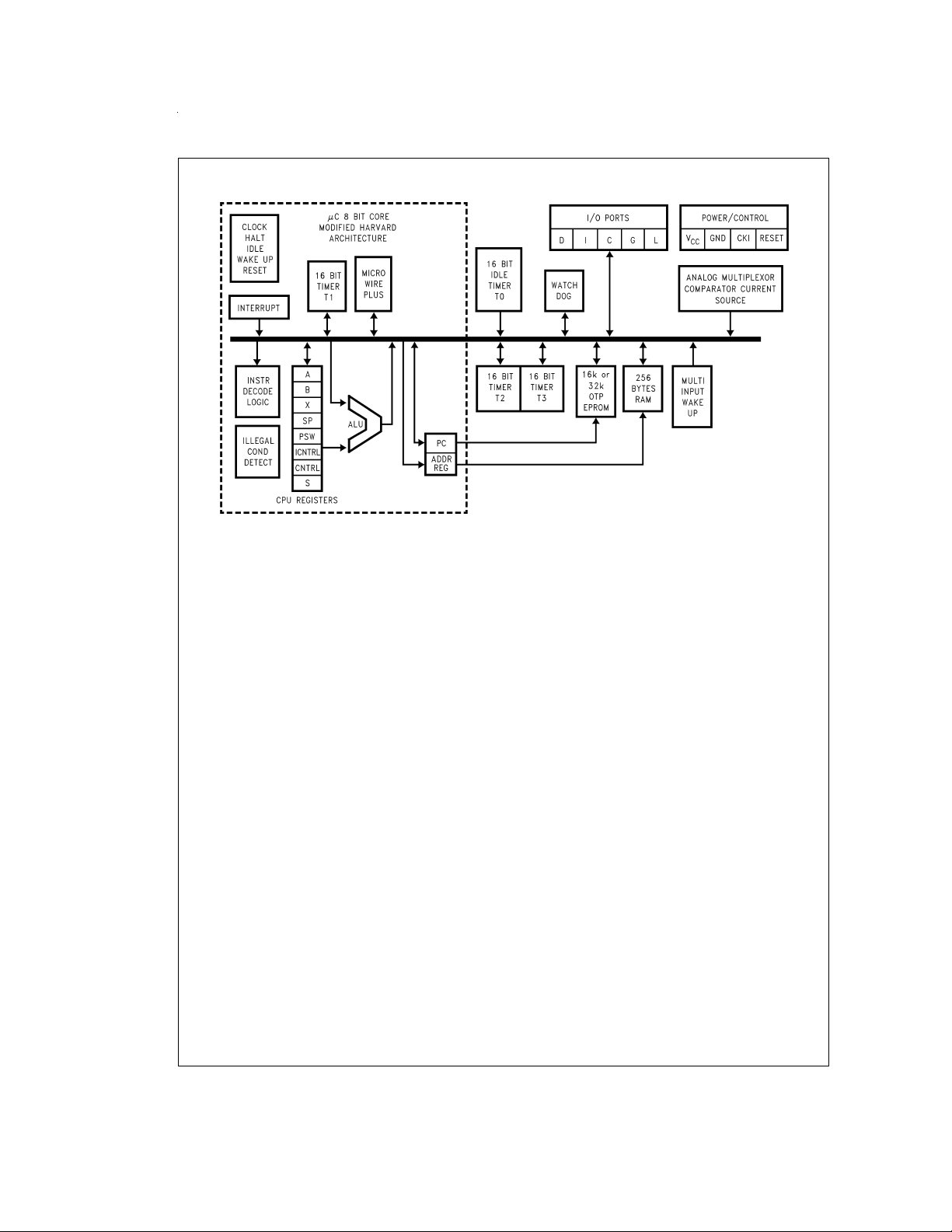
Block Diagram
DS101133-1
FIGURE 1. Block Diagram
www.national.com 2
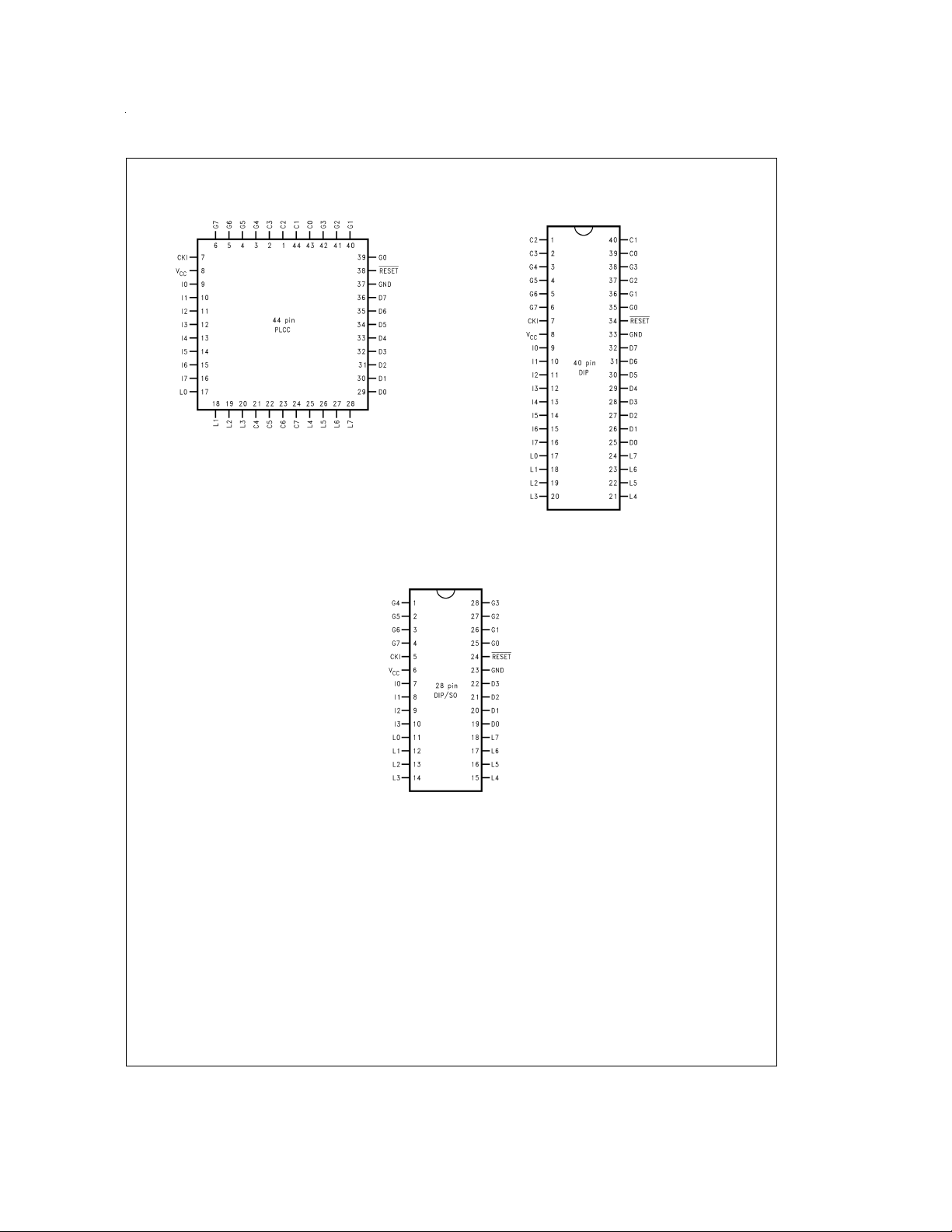
Connection Diagrams
Plastic Chip Carrier
DS101133-2
Top View
Order Number COP87L88EKV-XE or COP87L88RKV-XE
See NS Plastic Chip Package Number V44A
Dual-In-Line Package
Dual-In-Line Package
DS101133-3
Top View
Order Number COP87L84EKN-XE or COP87L84RKN-XE
See NS Molded Package Number N40A
Note: -X Crystal Oscillator
-E Halt Mode Enabled
DS101133-4
Top View
Order Number COP87L84EKN-XE or COP87L84RKN-XE
See NS Molded Package Number N28B
Order Number COP87L84EKM-XE or COP87L84RKM-XE
See NS Molded Package Number M28B
FIGURE 2. Connection Diagrams
www.national.com3
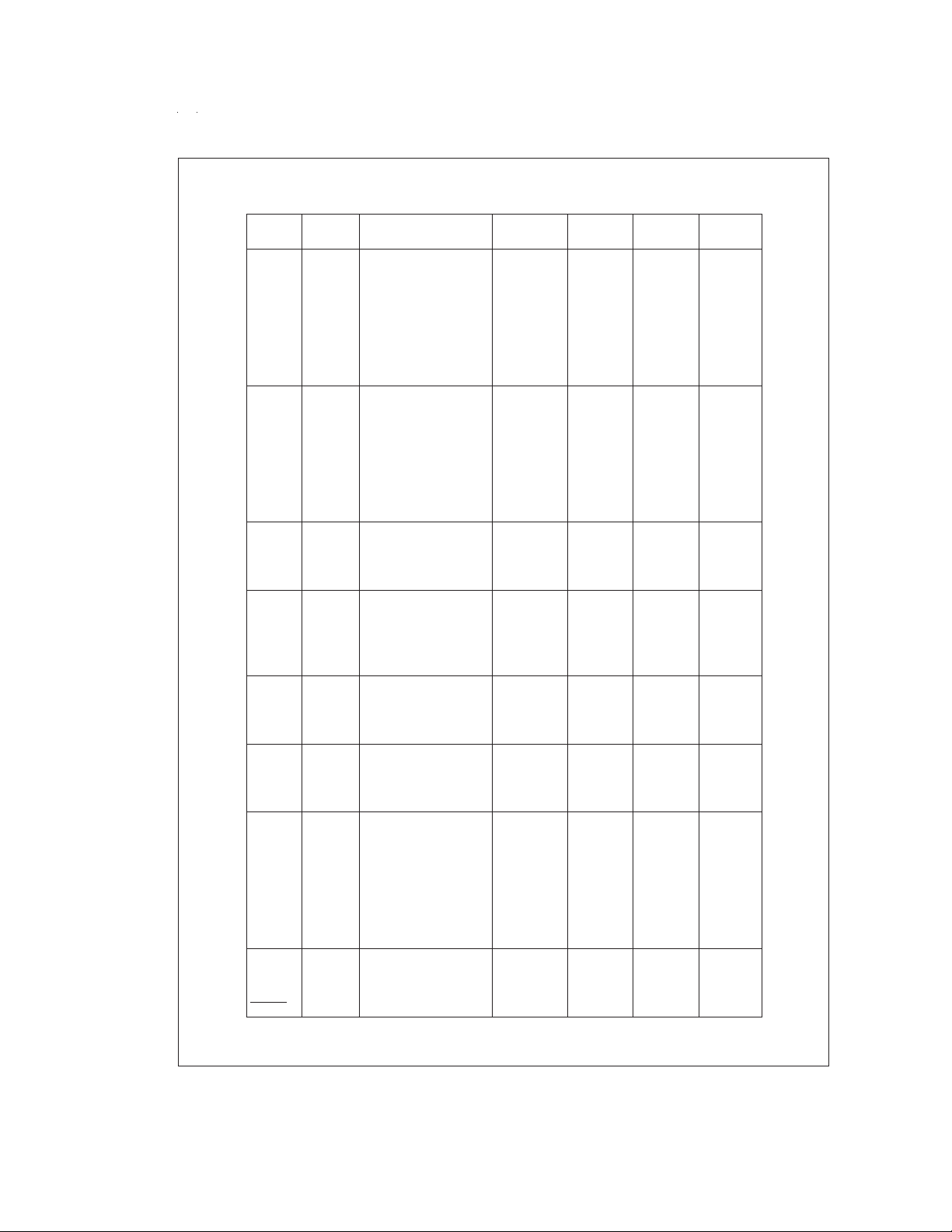
Connection Diagrams (Continued)
Pinouts for 28-, 40-, and 44-Pin Packages
Port Type Alt. Fun Alt. Fun
L0 I/O MIWU 11 17 17
L1 I/O MIWU 12 18 18
L2 I/O MIWU 13 19 19
L3 I/O MIWU 14 20 20
L4 I/O MIWU T2A 15 21 25
L5 I/O MIWU T2B 16 22 26
L6 I/O MIWU T3A 17 23 27
L7 I/O MIWU T3B 18 24 28
G0 I/O INT 25 35 39
G1 WDOUT 26 36 40
G2 I/O T1B 27 37 41
G3 I/O T1A 28 38 42
G4 I/O SO 1 3 3
G5 I/O SK 2 4 4
G6ISI 355
G7 I/CKO HALT Restart 4 6 6
D0O 192529
D1O 202630
D2O 212731
D3O 222832
I0 I COMPIN1+ 7 9 9
I1 I COMPIN−/Current 8 10 10
Source Out
I2 I COMPIN0+ 9 11 11
I3 I COMPOUT/COMPIN2+ 10 12 12
I4 I COMPIN3+ 13 13
I5 I COMPIN4+ 14 14
I6 I COMPIN5+ 15 15
I7 I COMPOUT 16 16
D4 O 29 33
D5 O 30 34
D6 O 31 35
D7 O 32 36
C0 I/O 39 43
C1 I/O 40 44
C2 I/O 1 1
C3 I/O 2 2
C4 I/O 21
C5 I/O 22
C6 I/O 23
C7 I/O 24
V
CC
GND 23 33 37
CKI 5 7 7
RESET
28-Pin 40-Pin 44-Pin
Pack. Pack. Pack.
688
24 34 38
www.national.com 4

Absolute Maximum Ratings (Note 1)
If Military/Aerospace specified devices are required,
please contact the National Semiconductor SalesOffice/
Distributors for availability and specifications.
Supply Voltage (V
Voltage at Any Pin −0.3V to V
)7V
CC
CC
+ 0.3V
Total Current into V
Pin (Source) 100 mA
CC
Total Current out of GND Pin (Sink) 110 mA
Storage Temperature Range −65˚C to +140˚C
Note 1:
Absolute maximum ratings indicate limits beyond which damage to
the device may occur. DC and AC electrical specifications are not ensured
when operating the device at absolute maximum ratings.
DC Electrical Characteristics
−40˚C ≤ TA≤ +85˚C unless otherwise specified
Parameter Conditions Min Typ Max Units
Operating Voltage 2.7 5.5 V
Power Supply Ripple (Note 3) Peak-to-Peak 0.1 V
CC
Supply Current (Note 4)
CKI=10 MHz V
CKI=4 MHz V
HALT Current (Note 5) V
=
CC
=
CC
=
CC
=
V
CC
=
5.5V, t
4.0V, t
1 µs 16.5 mA
c
=
2.5 µs 6.5 mA
c
5.5V, CKI=0 MHz 12 µA
4.0V, CKI=0 MHz 8 µA
IDLE Current (Note 4)
CKI=10 MHz V
CKI=4 MHz V
Input Levels (V
IH,VIL
)
=
CC
=
CC
5.5V, t
4.0V, t
=
1 µs 3.5 mA
c
=
10 µs 0.7 mA
c
RESET
Logic High 0.8 V
Logic Low 0.2 V
CC
CC
CKI, All Other Inputs
Logic High 0.7 V
Logic Low 0.2 V
Hi-Z Input Leakage V
Input Pullup Current V
=
5.5V −2 +2 µA
CC
=
5.5V, V
CC
=
0V −40 −250 µA
IN
G and L Port Input Hysteresis (Note 8) 0.35 V
CC
CC
CC
Output Current Levels
D Outputs
Source V
Sink V
=
4.5V, V
CC
=
4.5V, V
CC
=
3.3V −0.4 mA
OH
=
1V 10 mA
OL
All Others
Source (Weak Pull-Up Mode) V
Source (Push-Pull Mode) V
Sink (Push-Pull Mode) V
TRI-STATE Leakage V
=
4.5V, V
CC
=
4.5V, V
CC
=
4.5V, V
CC
=
6.0V −2 +2 µA
CC
=
2.7V −10 −110 µA
OH
=
3.3V −0.4 mA
OH
=
0.4V 1.6 mA
OL
Allowable Sink/Source Current per Pin
(Note 8)
D Outputs (Sink) 15 mA
All others 3mA
Maximum Input Current Room Temp
±
200 mA
without Latchup (Note 6)
RAM Retention Voltage, V
r
500 ns Rise 2 V
and Fall Time (min)
Input Capacitance 7pF
Load Capacitance on D2 1000 pF
V
V
V
V
V
V
www.national.com5

AC Electrical Characteristics
−40˚C ≤ TA≤ +85˚C unless otherwise specified
Parameter Conditions Min Typ Max Units
Instruction Cycle Time (t
Crystal, Resonator, 4.5V ≤ V
R/C Oscillator 4.5V ≤ V
Inputs
t
SETUP
t
HOLD
Output Propagation Delay (Note 7) R
t
PD1,tPD0
SO, SK 4.5V ≤ VCC≤ 5.5V 0.7 µs
All Others 4.50V ≤ V
MICROWIRE Setup Time (t
MICROWIRE Hold Time (t
MICROWIRE Output Propagation Delay (t
Input Pulse Width (Note 8)
Interrupt Input High Time 1.0 t
Interrupt Input Low Time 1.0 t
Timer 1, 2, 3 Input High Time 1.0 t
Timer 1, 2, 3 Input Low Time 1.0 t
Reset Pulse Width 1.0 µs
=
Note 2: t
Note 3: Maximum rate of voltage change must be
Note 4: Supply and IDLE currents are measured with CKI driven with a square wave Oscillator, CKO driven 180˚ out of phase with CKI, inputs connected to V
and outputs driven low but not connected to a load.
Note 5: The HALT mode will stop CKI from oscillating in the RC and the Crystal configurations. Measurement of I
sinking current; with L, C, G0, and G2–G5 programmed as low outputs and not driving a load; all outputs programmed low and not driving a load; all inputs tied to
V
in crystal clock mode.
Note 6: Pins G6 and RESET are designed with ahighvoltageinput network. These pins allow input voltages
biased at voltages>VCC(the pins do not have source current when biased at a voltage below VCC). The effective resistance to VCCis 750Ω (typical). These two
pins will not latch up. The voltage at the pins must be limited to
cludes ESD transients.
Note 7: The output propagation delay is referenced to the end of the instruction cycle where the output change occurs.
Note 8: Parameter characterized but not tested.
Instruction Cycle Time
c
; clock monitor and comparator disabled. Parameter refers to HALTmode entered via setting bit 7 of the G Port data register.Part will pull up CKI during HALT
CC
)
c
≤ 5.5V 1.0 DC µs
CC
≤ 5.5V 3.0 DC µs
CC
4.5V ≤ VCC≤ 5.5V 200 ns
4.5V ≤ VCC≤ 5.5V 60 ns
=
L
) (Note 7) VCC≥ 4.5V 20 ns
UWS
) (Note 7) VCC≥ 4.5V 56 ns
UWH
)V
UPD
<
0.5 V/ms.
<
14V.WARNING: Voltages in excess of 14V will cause damage to the pins. This warning ex-
=
2.2k, C
100 pF
L
≤ 5.5V 1.0 µs
CC
≥ 4.5V 220 ns
CC
HALTis done with device neither sourcing nor
DD
>
VCCand the pins will have sink current to VCCwhen
c
c
c
c
CC
www.national.com 6
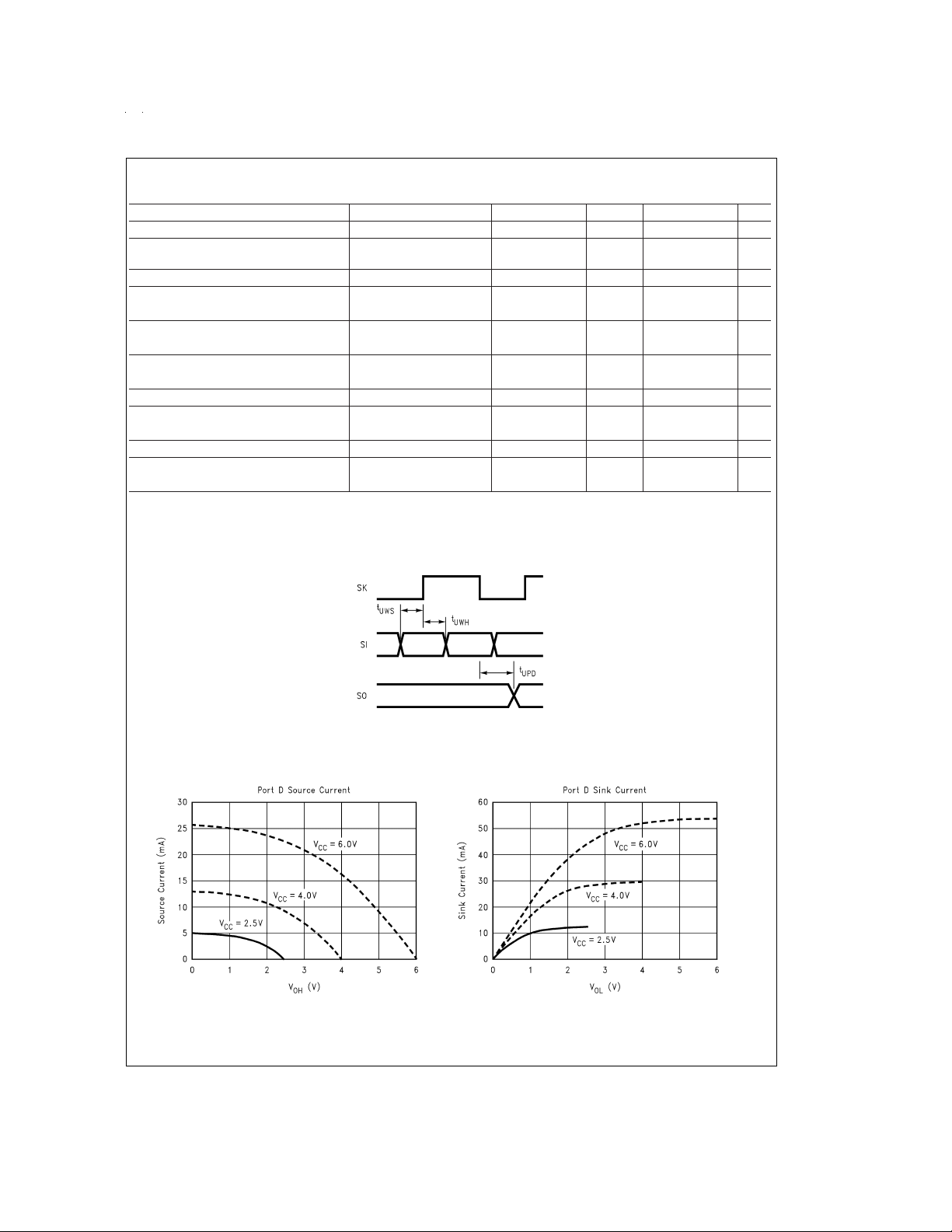
Analog Function Block AC and DC Characteristics
=
V
5.0V, −40˚C ≤ T
CC
Parameter Conditions Min Typ Max Units
Input Offset Voltage 0.4V
Input Common Mode Voltage Range
(Note 10)
V
/2 Reference 4.5V<V
CC
DC Supply Current for
Comparator (when enabled)
DC Supply Current for
V
/2 Reference (when enabled)
CC
DC Supply Current for
Constant Current Source (when enabled)
Constant Current Source 4.5V
Current Source Variation over 4.5V
Common Mode Range Temp=Constant
Current Source Enable Time 1.5 2 µs
Comparator Response Time 100 mV Overdrive, 1 µs
Note 9: While performance characteristics are given at V
/2 reference and the constant current source is not guaranteed beyond the specified limits.
V
CC
Note 10: The device is capable of operating over a common mode voltage range of 0 to V
and 0.4V.
≤ +85˚C
A
<
<
V
VCC− 1.5V
IN
0.4 V
<
5.5V 0.5 VCC− 0.04 0.5 V
CC
=
V
5.5V
CC
=
V
5.5V
CC
=
V
5.5V
CC
<
<
V
5.5V 10 20 40 µA
CC
<
<
V
5.5V
CC
100 pF Load
=
5.0V, the analog function block will operate over the entire 2.5V–6.0V V
CC
− 1.5V, however increased offset voltage will be observed between 0V
CC
±
10
CC
±
25 mV
− 1.5 V
CC
0.5 VCC+ 0.04 V
250 µA
50 80 µA
200 µA
±
2µA
range. Accuracy of the
CC
FIGURE 3. MICROWIRE/PLUS Timing
Typical Performance Characteristics (−55˚C ≤ T
DS101133-19 DS101133-20
DS101133-18
=
A
+125˚C)
www.national.com7
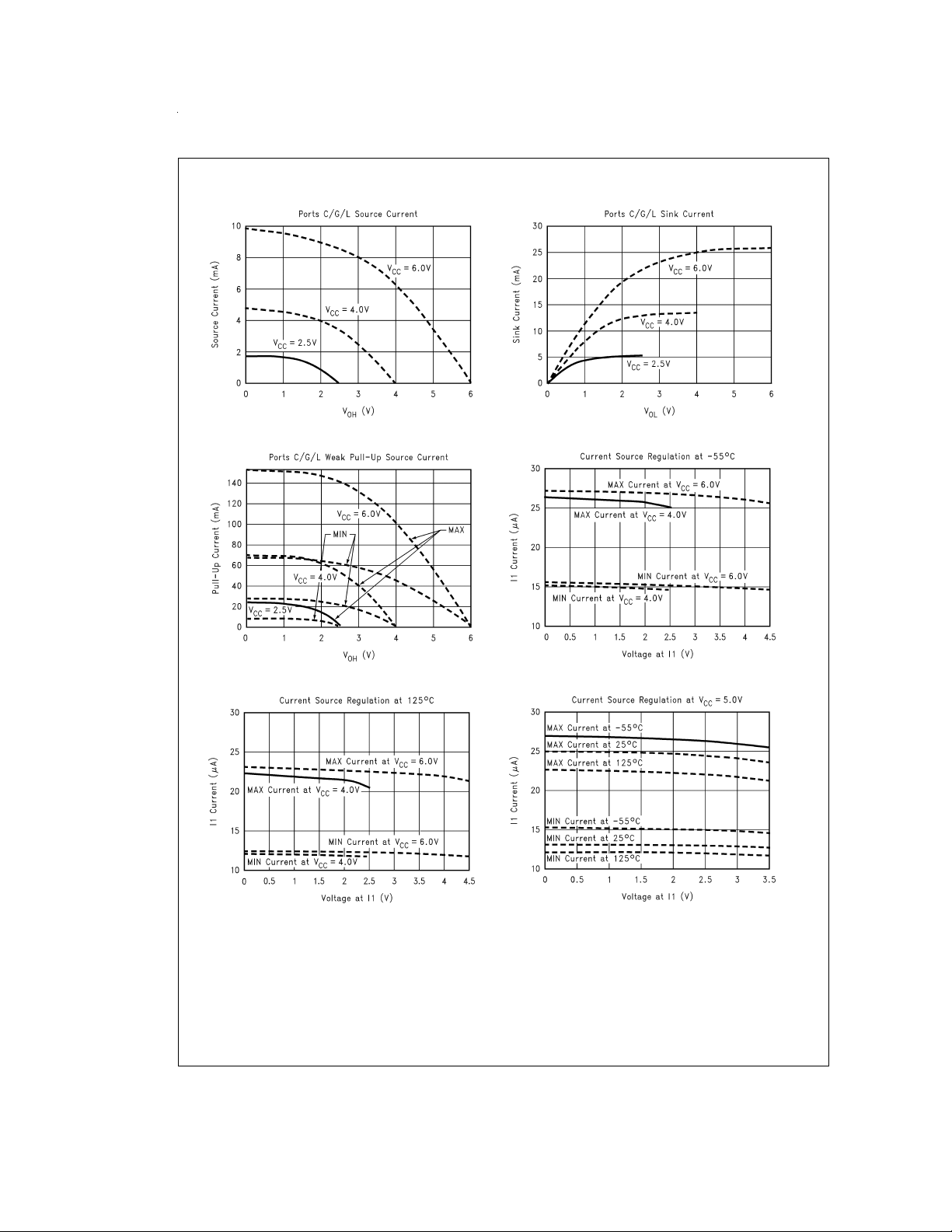
Typical Performance Characteristics (−55˚C ≤ T
DS101133-21 DS101133-22
=
+125˚C) (Continued)
A
DS101133-23
DS101133-28
www.national.com 8
DS101133-27
DS101133-29
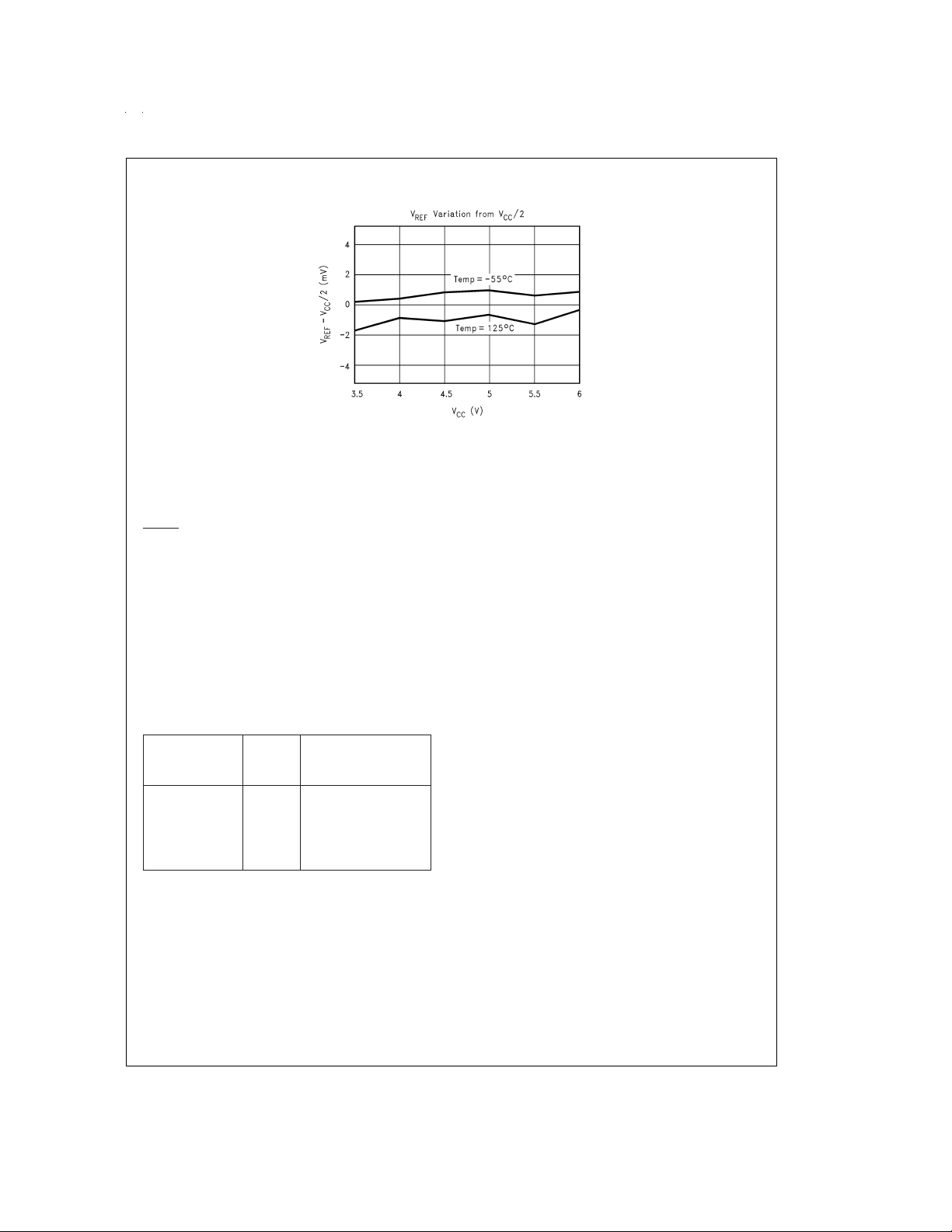
Typical Performance Characteristics (−55˚C ≤ T
Pin Descriptions
VCCand GND are the power supply pins. All VCCand GND
pins must be connected.
CKI is the clockinput. This can come from an R/C generated
oscillator, or a crystal oscillator (in conjunction with CKO).
See Oscillator Description section.
RESET is the master reset input. See ResetDescription section.
The device contains three bidirectional 8-bit I/O ports (C, G
and L), where each individual bit may be independently configured as an input(Schmitt Trigger inputs on ports Land G),
output or TRI-STATE under program control. Three data
memory address locations are allocated for each of these
I/O ports. Each I/O port has two associated 8-bit memory
mapped registers, the CONFIGURATION register and the
output DATAregister. A memory mapped address is also reserved for the input pins of each I/O port. (See the memory
map for the various addresses associated with theI/O ports.)
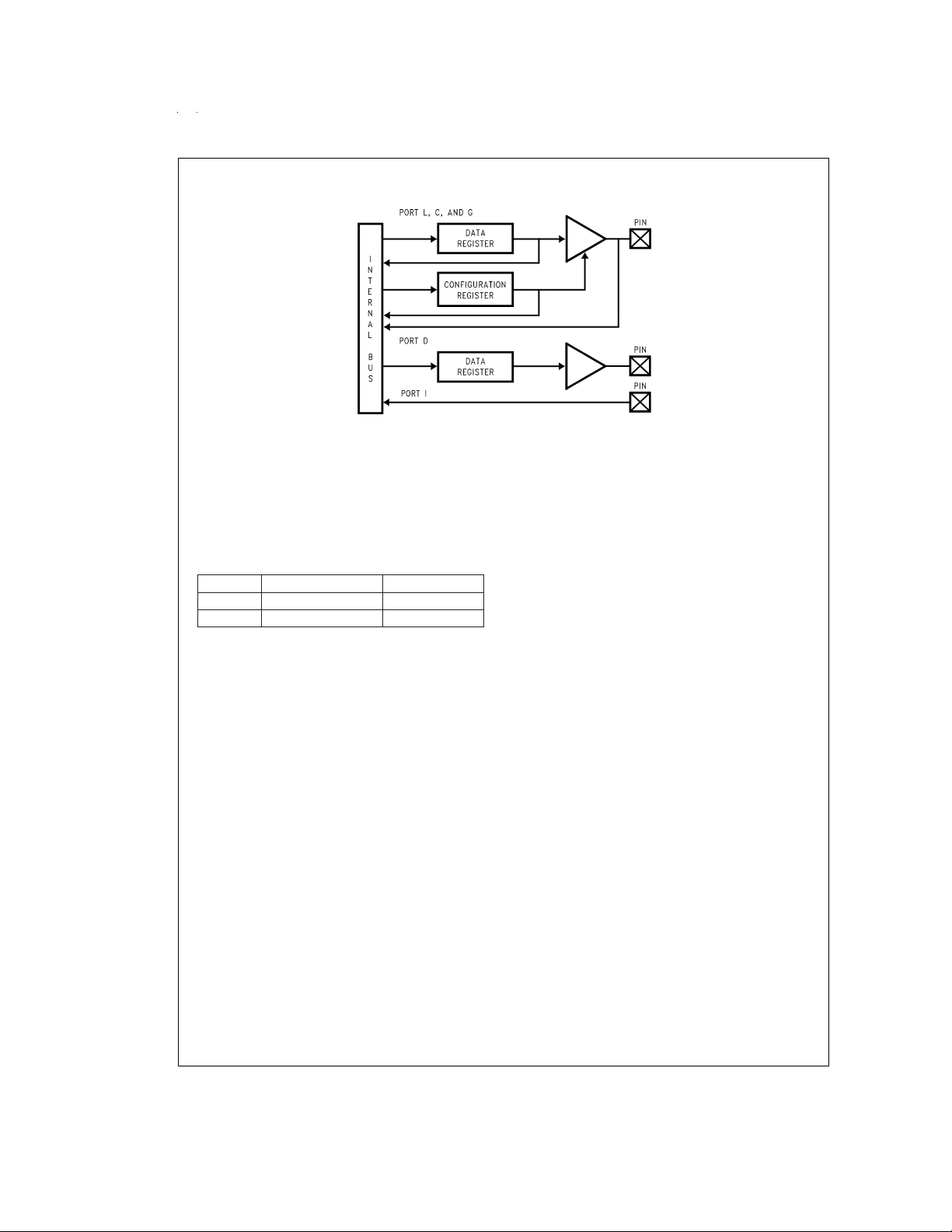
Figure 4
shows the I/O port configurations. The DATA and
CONFIGURATION registers allow for each port bit to be individually configured under software control as shown below:
CONFIGURA-
TION
Register Register
0 0 Hi-Z Input
0 1 Input with Weak Pull-Up
1 0 Push-Pull Zero Output
1 1 Push-Pull One Output
PORT L is an 8-bit I/O port. All L-pins have Schmitt triggers
on the inputs.
The Port L supports Multi-Input Wake Up on alleight pins. L4
and L5 are used for the timer input functions T2A and T2B.
L6 and L7 are used for the timer input functions T3A and
T3B.
DATA
Port Set-Up
(TRI-STATE Output)
The Port L has the following alternate features:
L7 MIWU or T3B
L6 MIWU or T3A
L5 MIWU or T2B
L4 MIWU or T2A
L3 MIWU
L2 MIWU
L1 MIWU
L0 MIWU
Port G is an 8-bit port with 5 I/O pins (G0, G2–G5), an input
pin (G6), and a dedicated output pin (G7). Pins G0 and
G2–G6 all have Schmitt Triggers on their inputs. Pin G1
serves as the dedicated WDOUT WATCHDOGoutput, while
pin G7 is either input or output depending on the oscillator
mask option selected. With the crystal oscillator option selected, G7 serves as the dedicated output pin for the CKO
clock output. With the single-pin R/C oscillator mask option
selected, G7 serves as a general purpose input pin but is
also used to bring the device out of HALT mode with alow to
high transition on G7. There are two registers associated
with the G Port, a data register and a configuration register.
Therefore, each of the 5 I/O bits (G0, G2–G5) can be individually configured under software control.
Since G6 is an input only pin and G7 is the dedicated CKO
clock output pin (crystal clock option) or general purpose input (R/C clock option), the associated bits in the data and
configuration registers for G6 and G7 are used for special
purpose functions as outlined on the nextpage. Reading the
G6 and G7 data bits will return zeros.
=
+125˚C) (Continued)
A
DS101133-30
www.national.com9
Pin Descriptions (Continued)
FIGURE 4. I/O Port Configurations
Note that the chipwill beplaced inthe HALT mode by writing
a “1” to bit 7 of the Port G Data Register. Similarly the chip
will be placed inthe IDLEmode bywriting a “1” to bit 6 of the
Port G Data Register.
Writing a “1” to bit 6 of the Port G Configuration Register enables the MICROWIRE/PLUS to operate with the alternate
phase of the SK clock. The G7 configuration bit, if set high,
enables the clock start up delay after HALT when the R/C
clock configuration is used.
Config Reg. Data Reg.
G7 CLKDLY HALT
G6 Alternate SK IDLE
Port G has the following alternate features:
G6 SI (MICROWIRE Serial Data Input)
G5 SK (MICROWIRE Serial Clock)
G4 SO (MICROWIRE Serial Data Output)
G3 T1A (Timer T1 I/O)
G2 T1B (Timer T1 Capture Input)
G0 INTR (External Interrupt Input)
Port G has the following dedicated functions:
G7 CKO Oscillator dedicated output or general purpose
input
G1 WDOUT WATCHDOG and/or Clock Monitor dedi-
cated output
Port C is an 8-bit I/O port. The 40-pin device does not have
a full complement of Port C pins. The unavailable pins are
not terminated. A read operation for these unterminated pins
will return unpredicatable values.
PORTI is aneight-bit Hi-Z input port. The 28-pin device does
not have a full complement of Port I pins. The unavailable
pins are not terminated i.e., they are floating. A read operation for these unterminatedpins will return unpredictable values. The user must ensure that the software takes this into
account by either masking or restricting the accesses to bit
operations. The unterminated Port I pins will draw power
only when addressed.
Port I is an eight-bit Hi-Z input port.
Port I0–I7 are used for the analog function block.
The Port I has the following alternate features:
I7 COMPOUT (Comparator Output)
I6 COMPIN5+ (Comparator Positive Input 5)
www.national.com 10
DS101133-5
I5 COMPIN4+ (Comparator Positive Input 4)
I4 COMPIN3+ (Comparator Positive Input 3)
I3 COMPOUT/COMPIN2+ (Comparator Output/
Comparator Positive Input 2))
I2 COMPIN0+ (Comparator Positive Input 0)
I1 COMPIN− (Comparator Negative Input/Current
Source Out)
I0 COMPIN1+ (Comparator Positive Input 1)
Port D is an 8-bitoutput port thatis presethigh when RESET
goes low. The user can tie two or more D port outputs (except D2) together in order to get a higher drive.
Note: Care must be exercised with the D2 pin operation. At RESET, the ex-
ternal loads on this pin must ensure that the output voltages stay
above 0.8 V
keep the external loading on D2 to
to prevent the chip from entering special modes. Also
CC
<
1000 pF.
Functional Description
The architecture of the device is modified Harvard architecture. With the Harvard architecture, the control store program memory (ROM) is separated from the data store
memory (RAM). Both ROM and RAM have their own separate addressing space with separate address buses. The architecture, though based on Harvard architecture, permits
transfer of data from ROM to RAM.
CPU REGISTERS
The CPU can do an 8-bitaddition, subtraction,logical or shift
operation in one instruction (t
There are six CPU registers:
A is the 8-bit Accumulator Register
PC is the 15-bit Program Counter Register
PU is the upper 7 bits of the program counter (PC)
PL is the lower 8 bits of the program counter (PC)
B is an 8-bit RAM address pointer, which can be optionally
post auto incremented or decremented.
X is an 8-bit alternate RAM address pointer, which can be
optionally post auto incremented or decremented.
SP is the 8-bit stack pointer, which points to the subroutine/
interrupt stack (in RAM). The SP is initialized to RAM address 06F with reset.
) cycle time.
c

Functional Description (Continued)
S is the 8-bit Data Segment Address Register used toextend
the lower half of the address range (00 to 7F) into 256 data
segments of 128 bytes each.
All the CPU registers are memory mapped with the exception of the Accumulator (A) and the Program Counter (PC).
The device can be configured to inhibit external reads of the
program memory. This is done by programming the Security
Byte.
PROGRAM MEMORY
The program memory consists of 8192 bytes of OTP
EPROM. These bytes mayhold program instructions or constant data (data tables for the LAID instruction, jump vectors
for the JID instruction, and interrupt vectors for the VIS instruction). The program memory is addressed by the 15-bit
program counter (PC). All interrupts in the devices vector to
program memory location 0FF Hex.
The device can be configured to inhibit external reads of the
program memory. This is done by programming the Security
Byte.
SECURITY FEATURE
The program memory array has an associate Security Byte
that is located outside of the program address range. This
byte can be addressed only from programming mode by a
programmer tool.
Security is an optional feature andcan onlybe asserted after
the memory array has been programmed and verified. A secured part will read all 00(hex) by a programmer. The part
will fail Blank Check and will fail Verify operations. A Read
operation will fill the programmer’s memory with 00(hex).
The Security Byte itself is always readable with value of
00(hex) if unsecure and FF(hex) if secure.
DATA MEMORY
The data memory address space includes the on-chip RAM
and data registers, the I/O registers(Configuration, Data and
Pin), the control registers, the MICROWIRE/PLUS SIO shift
register, and the various registers, and counters associated
with the timers (with the exception of the IDLE timer). Data
memory is addressed directly by the instruction or indirectly
by the B, X, SP pointers and S register.
The data memory consists of 256 bytes of RAM. Sixteen
bytes of RAM are mappedas “registers”at addresses0F0 to
0FF Hex. These registers can be loaded immediately, and
also decremented and tested with the DRSZ (decrement
register and skip if zero) instruction. The memory pointer
registers X, SP,B andS arememory mappedinto thisspace
at address locations 0FC to 0FF Hex respectively, with the
other registers being available for general usage.
The instruction set permitsany bit in memory to be set, reset
or tested. All I/O and registers (except A and PC) are
memory mapped; therefore, I/O bits and register bits can be
directly and individually set,reset andtested. The accumulator (A) bits can also be directly and individually tested.
Note: RAM contents are undefined upon power-up.
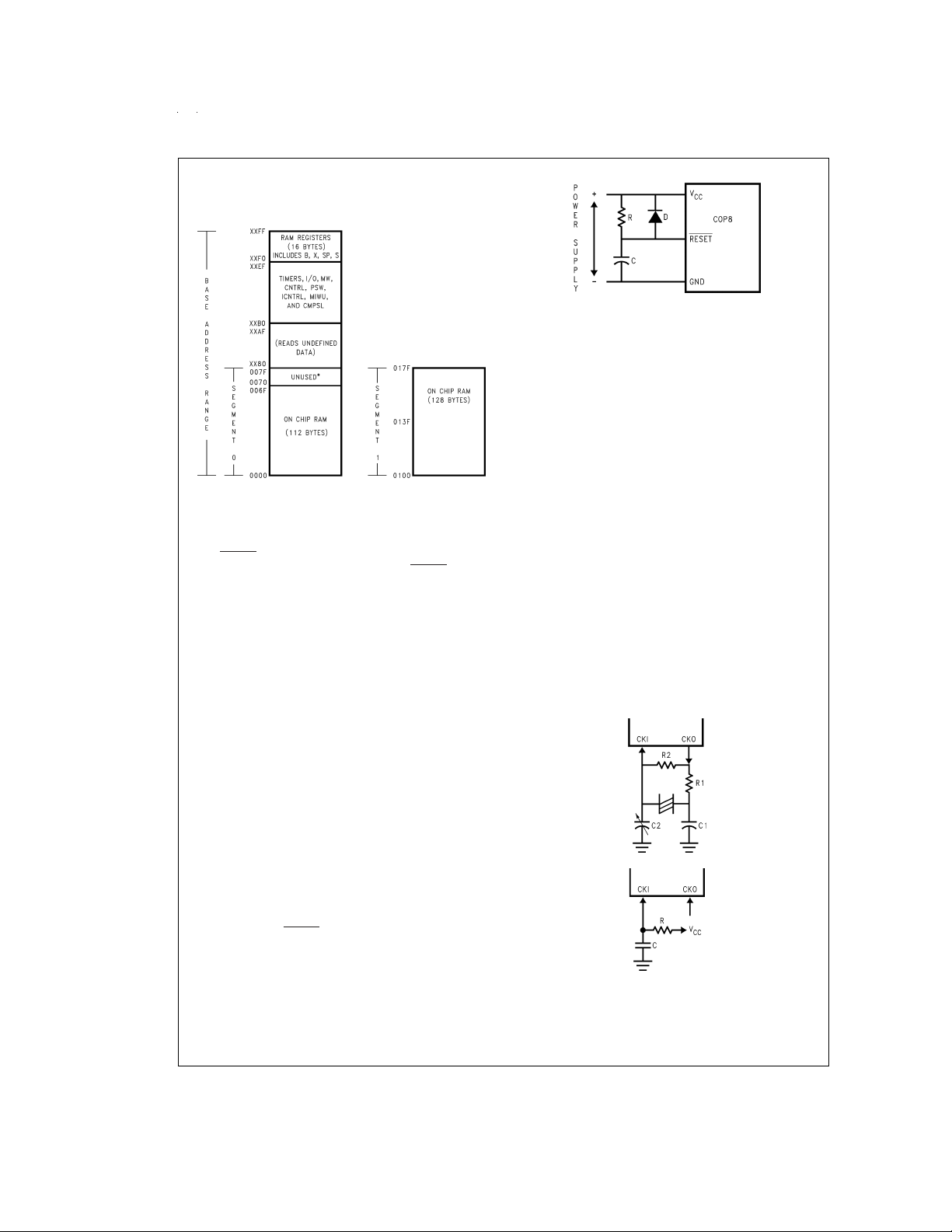
Data Memory Segment RAM
Extension
Data memory address 0FF is used as a memory mapped location for the Data Segment Address Register (S).
The data store memory is either addressed directly by a
single byte address within the instruction, or indirectly relative to the reference of the B, X, or SP pointers (each contains a single-byte address). This single-byte address allows
an addressing range of256 locationsfrom 00to FFhex. The
upper bit of this single-byte address divides the data store
memory into two separate sections as outlined previously.
With the exception of the RAM register memory from address locations 00F0 to 00FF, all RAM memory is memory
mapped with the upper bit of the single-byte address being
equal to zero. This allows the upper bit ofthe single-byte address to determine whether or not the base address range
(from 0000 to 00FF) is extended. If this upper bit equals one
(representing address range 0080 to 00FF), then address
extension does not take place. Alternatively, if this upper bit
equals zero, then the data segment extension register S is
used to extend the base address range (from 0000 to 007F)
from XX00 to XX7F, where XX represents the 8 bits from the
S register. Thus the 128-byte data segment extensions are
located from addresses 0100 to 017F for data segment 1,
0200 to 027F for data segment 2, etc., up to FF00 to FF7F
for data segment 255.The base address range from 0000 to
007F represents data segment 0.
Figure 5
illustrates how the S register data memory extension is used in extending the lower half of the base address
range (00 to 7F hex) into 256 data segments of 128 bytes
each, with a total addressing range of 32 kbytes from XX00
to XX7F. This organization allows a total of 256 data segments of 128 bytes each with an additional upper base segment of 128 bytes. Furthermore, all addressing modes are
available for all data segments. The S register must be
changed under program control to move from one data segment (128 bytes) to another. However, the upper base segment (containing the 16 memory registers, I/O registers,
control registers, etc.) is always available regardless of the
contents of the S register, since the upper base segment
(address range 0080 to 00FF) is independent of data segment extension.
The instructions that utilize thestack pointer (SP)always reference the stack as part of the base segment (Segment 0),
regardless of the contents of the S register. The S register is
not changed by these instructions. Consequently, the stack
(used with subroutine linkage and interrupts) is always located in the base segment. The stack pointer will be intitialized to point at data memory location 006F as a result of reset.
The 128 bytes of RAM contained in the base segment are
split between the lower and upper base segments. The first
112bytes ofRAM are resident from address 0000 to 006F in
the lower base segment, while the remaining 16 bytes of
RAM represent the 16 data memory registers located at addresses 00F0 to 00FF of the upper base segment. No RAM
is located at the upper sixteen addresses (0070 to 007F) of
the lower base segment.
Additional RAM beyond these initial 128 bytes, however, will
always be memory mapped in groups of 128 bytes (or less)
at the data segment address extensions (XX00 to XX7F) of
the lower base segment. The additional 128 bytes of RAM
are memory mapped at address locations 0100 to 017F hex.
www.national.com11
Data Memory Segment RAM
Extension
(Continued)
*Reads as all ones.
DS101133-6
FIGURE 5. RAM Organization
Reset
The RESET input when pulled low initializes the microcontroller. Initialization will occur whenever the RESET input is
pulled low. Upon initialization, the data and configuration
registers for ports L, G and C are cleared, resulting in these
Ports being initialized to the TRI-STATE mode. Pin G1 of the
G Port is anexception (asnoted below)since pinG1 is dedicated as the WATCHDOGand/or Clock Monitor error output
pin. Port D is set high. The PC, PSW, ICNTRL, CNTRL,
T2CNTRL and T3CNTRL control registers are cleared. The
Comparator Select Register is cleared. The S register is initialized to zero. The Multi-Input Wakeup registers WKEN and
WKEDG are cleared. Wakeup register WKPND is unknown.
The stack pointer, SP, is initialized to 6F hex.
The device comes out of reset with both the WATCHDOG
logic and the Clock Monitor detector armed, with the
WATCHDOG service window bits set and the Clock Monitor
bit set. The WATCHDOG and Clock Monitor circuits are inhibited during reset. The WATCHDOG service window bits
being initialized high default to the maximum WATCHDOG
service window of 64k t
being initialized high will cause a Clock Monitor error following reset if the clock has not reached the minimum specified
frequency at the termination of reset. A Clock Monitor error
will cause an active low error output on pin G1. This error
output will continue until 16 t
the clock frequency reaching the minimum specified value,
at which time the G1 output will enter the TRI-STATE mode.
The external RC network shown in
to ensure that the RESETpin is heldlow until thepower supply to the chip stabilizes.
clock cycles. The Clock Monitor bit
C
–32 tCclock cycles following
C
Figure 6
should be used
RC>5 x Power Supply Rise Time
DS101133-7
FIGURE 6. Recommended Reset Circuit
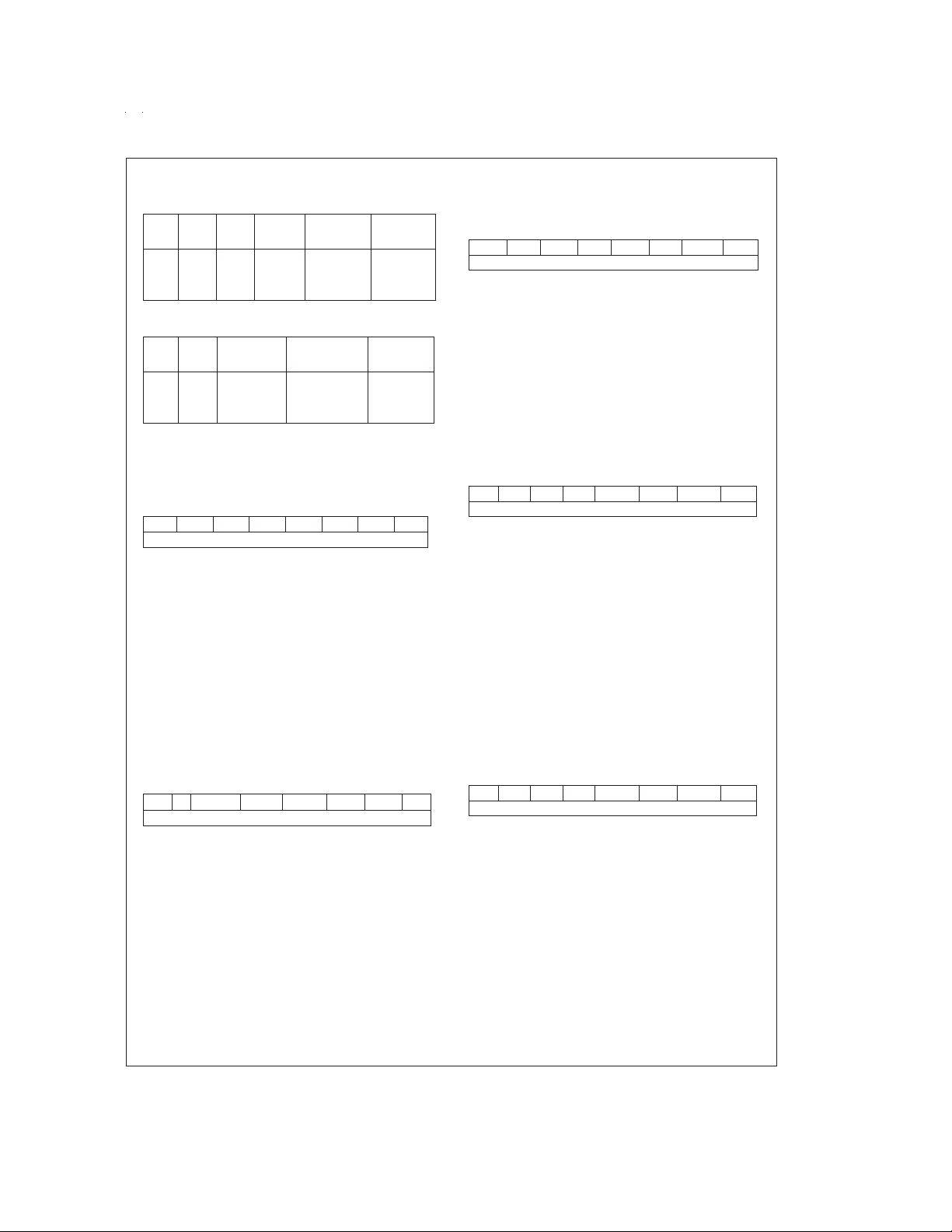
Oscillator Circuits
The chip can be driven by a clock input on the CKI input pin
which can be between DC and 10 MHz. The CKO output
clock is on pin G7 (crystal configuration). The CKI input frequency is divided down by 10 to produce the instruction
cycle clock (1/t
Note: External clocks with frequencies above about 4 MHz require the user
to drive the CKO (G7) pin with a signal 180 degrees out of phase with
CKI.
Figure 7
CRYSTAL OSCILLATOR
CKI and CKO can be connected to make a closed loop crystal (or resonator) controlled oscillator.
Table 1
standard crystal values.
R/C OSCILLATOR
By selecting CKI as a single pin oscillator input, a single pin
R/C oscillator circuit can beconnected toit. CKOis available
as a general purpose input, and/or HALT restart input.
Note: Use of the R/C oscillator option will result in higher electromagnetic
emissions.
Table 2
functions of the component (R and C) values.
).
c
shows the Crystal and R/C oscillator diagrams.
shows the component values required for various
shows the variation in the oscillator frequencies as
DS101133-8
www.national.com 12
DS101133-9
FIGURE 7. Crystal and R/C Oscillator Diagrams
Oscillator Circuits (Continued)
TABLE 1. Crystal Oscillator Configuration, T
R1 R2 C1 C2 CKI Freq
(kΩ)(MΩ) (pF) (pF) (MHz)
0 1 30 30–36 10 V
0 1 30 30–36 4 V
0 1 200 100–150 0.455 V
TABLE 2. RC Oscillator Configuration, T
R C CKI Freq Instr. Cycle
(kΩ) (pF) (MHz) (µs)
3.3 82 2.2 to 2.7 3.7 to 4.6 V
5.6 100 1.1 to 1.3 7.4 to 9.0 V
6.8 100 0.9 to 1.1 8.8 to 10.8 V
Note 11: 3k ≤ R ≤ 200k
50 pF ≤ C ≤ 200 pF
=
25˚C
A
Conditions
=
CC
=
CC
=
CC
=
25˚C
A
Conditions
=
CC
=
CC
=
CC
5V
5V
5V
5V
5V
5V
Control Registers
CNTRL Register (Address X'00EE)
T1C3 T1C2 T1C1 T1C0 MSEL IEDG SL1 SL0
Bit 7 Bit 0
The Timer1 (T1) and MICROWIRE/PLUS control register
contains the following bits:
T1C3 Timer T1 mode control bit
T1C2 Timer T1 mode control bit
T1C1 Timer T1 mode control bit
T1C0 Timer T1 Start/Stop control in timer
modes 1 and 2, T1 Underflow Interrupt
Pending Flag in timer mode 3
MSEL Selects G5 and G4 as MICROWIRE/PLUS
IEDG External interrupt edge polarity select
SL1 & SL0 Select the MICROWIRE/PLUS clock divide
PSW Register (Address X'00EF)
HC C T1PNDA T1ENA EXPND BUSY EXEN GIE
Bit 7 Bit 0
The PSW register contains the following select bits:
HC Half Carry Flag
C Carry Flag
T1PNDA Timer T1 Interrupt Pending Flag (Autoreload
T1ENA Timer T1 Interrupt Enable for Timer Underflow
EXPND External interrupt pending
BUSY MICROWIRE/PLUS busy shifting flag
EXEN Enable external interrupt
GIE Global interrupt enable (enables interrupts)
The Half-Carry flag is also affectedby all the instructionsthat
affect the Carry flag. The SC (Set Carry) and R/C (Reset
Carry) instructions will respectively set or clear boththe carry
signals SK and SO respectively
(0 = Rising edge, 1 = Falling edge)
by (00 = 2, 01 = 4, 1x = 8)
RA in mode 1, T1 Underflow in Mode 2, T1A
capture edge in mode 3)
or T1A Input capture edge
flags. In addition to the SC and R/C instructions, ADC,
SUBC, RRC and RLC instructions affect the Carry and Half
Carry flags.
ICNTRL Register (Address X'00E8)
Rsvd LPEN T0PND T0EN µWPND µWEN T1PNDB T1ENB
Bit 7 Bit 0
The ICNTRL register contains the following bits:
Rsvd This bit is reserved and must be zero
LPEN L Port Interrupt Enable (Multi-Input Wakeup/
Interrupt)
T0PND Timer T0 Interrupt pending
T0EN Timer T0 Interrupt Enable (Bit 12 toggle)
µWPND MICROWIRE/PLUS interrupt pending
µWEN Enable MICROWIRE/PLUS interrupt
T1PNDB Timer T1 Interrupt Pending Flag for T1B cap-
ture edge
T1ENB TimerT1 InterruptEnable for T1B Inputcapture
edge
T2CNTRL Register (Address X'00C6)
T2C3 T2C2 T2C1 T2C0 T2PNDA T2ENA T2PNDB T2ENB
Bit 7 Bit 0
The T2CNTRL control register contains the following bits:
T2C3 Timer T2 mode control bit
T2C2 Timer T2 mode control bit
T2C1 Timer T2 mode control bit
T2C0 Timer T2 Start/Stop control in timer
modes 1 and 2, T2 Underflow Interrupt Pending Flag in timer mode 3
T2PNDA Timer T2 Interrupt Pending Flag (Autoreload
RA in mode 1, T2 Underflow in mode 2, T2A
capture edge in mode 3)
T2ENA Timer T2 Interrupt Enable for Timer Underflow
or T2A Input capture edge
T2PNDB Timer T2 Interrupt Pending Flag for T2B cap-
ture edge
T2ENB Timer T2 Interrupt Enable for Timer Underflow
or T2B Input capture edge
T3CNTRL Register (Address X'00B6)
T3C3 T3C2 T3C1 T3C0 T3PNDA T3ENA T3PNDB T3ENB
Bit 7 Bit 0
The T3CNTRL control register contains the following bits:
T3C3 Timer T3 mode control bit
T3C2 Timer T3 mode control bit
T3C1 Timer T3 mode control bit
T3C0 Timer T3 Start/Stop control in timer
modes 1 and 2, T3 Underflow Interrupt Pending Flag in timer mode 3
T3PNDA Timer T3 Interrupt Pending Flag (Autoreload
RA in mode 1, T3 Underflow in mode 2, T3A
capture edge in mode 3)
T3ENA Timer T3 Interrupt Enable for Timer Underflow
or T3A Input capture edge
T3PNDB Timer T3 Interrupt Pending Flag for T3B cap-
ture edge
T3ENB Timer T3 Interrupt Enable for Timer Underflow
or T3B Input capture edge
www.national.com13

Timers
The device contains a very versatile set of timers (T0, T1,
T2, T3). All timers and associated autoreload/capture registers power up containing random data.
TIMER T0 (IDLE TIMER)
The device supports applications that require maintaining
real time and low power with the IDLE mode. This IDLE
mode support is furnished by the IDLE timer T0, which is a
16-bit timer. The Timer T0 runscontinuously at the fixed rate
of the instruction cycle clock, t
write to the IDLE Timer T0, which is a count down timer.
The Timer T0 supports the following functions:
j
Exit out of the Idle Mode (See Idle Mode description)
j
WATCHDOG logic (See WATCHDOG description)
j
Start up delay out of the HALT mode
The IDLE Timer T0 can generate an interrupt when the thirteenth bit toggles. This toggle is latched into the T0PND
pending flag, and will occur every 4 ms at the maximum
clock frequency (t
terrupt from the thirteenth bit of Timer T0 to be enabled or
=
1 µs). Acontrol flagT0EN allows thein-
c
disabled. Setting T0EN will enable the interrupt, while resetting it will disable the interrupt.
TIMER T1, TIMER T2 AND TIMER T3
The device has a set of three powerful timer/counter blocks,
T1, T2 and T3. The associated features and functioning of a
timer block are described by referring to the timer block Tx.
Since the three timer blocks, T1, T2 and T3 are identical, all
comments are equally applicable to any of the three timer
blocks.
Each timer block consists of a 16-bit timer, Tx, and two supporting 16-bit autoreload/capture registers, RxA and RxB.
Each timer block has two pins associated with it, TxA and
TxB. The pin TxA supports I/O required by the timer block,
while the pinTxB is an input to the timer block.The powerful
and flexible timer block allows the device to easilyperform all
timer functions with minimal software overhead. The timer
block has three operating modes: Processor Independent
PWM mode, External Event Counter mode, and Input Capture mode.
The control bits TxC3, TxC2, andTxC1 allow selectionof the
different modes of operation.
Mode 1. Processor Independent PWM Mode
As the name suggests, this mode allows the device to generate a PWM signal with very minimal user intervention.The
user only has to define the parameters of the PWM signal
(ON time and OFF time). Once begun, the timer block will
continuously generate the PWM signal completely independent of the microcontroller. The user software services the
timer block only when the PWM parameters require updating.
In this mode the timer Tx counts down at a fixed rate of t
Upon every underflow the timer is alternately reloaded with
the contents of supporting registers, RxAand RxB. The very
first underflow of the timer causes the timer to reload from
the register RxA. Subsequent underflows cause the timer to
be reloaded from the registers alternately beginning with the
register RxB.
. The user cannot read or
c
The Tx Timer control bits, TxC3, TxC2 and TxC1 set up the
timer for PWM mode operation.
Figure 8
shows a block diagram of the timer in PWM mode.
The underflows can be programmed totoggle the TxA output
pin. The underflows can also be programmed to generate interrupts.
Underflows from the timer are alternately latched into two
pending flags, TxPNDA and TxPNDB. The user must reset
these pending flags under software control. Two control enable flags, TxENA and TxENB, allow the interrupts from the
timer underflow to be enabled or disabled. Setting the timer
enable flag TxENA will cause an interrupt when a timer underflow causes the RxA register tobe reloaded into the timer.
Setting the timer enable flag TxENB will cause an interrupt
when a timer underflow causes the RxB register to be reloaded into the timer. Resetting the timer enable flags will
disable the associated interrupts.
Either or both of the timer underflow interrupts may be enabled. This gives the user the flexibility of interrupting once
per PWM period on either the rising or falling edge of the
PWM output. Alternatively, the user may choose to interrupt
on both edges of the PWM output.
FIGURE 8. Timer in PWM Mode
Mode 2. External Event Counter Mode
This mode is quite similar to the processor independent
PWM mode described above. Themain differenceis that the
timer,Tx, is clockedby theinput signalfrom the TxApin. The
Tx timer control bits, TxC3, TxC2 and TxC1 allow the timerto
be clocked either on a positive or negative edge from the
TxA pin. Underflows from the timer are latched into the TxPNDA pending flag. Setting the TxENA control flag will cause
an interrupt when the timer underflows.
In this mode the input pin TxB can be used as an independent positive edge sensitiveinterrupt inputif theTxENB control flag is set. The occurrence of a positive edge on the TxB
input pin is latched into the TxPNDB flag.
Figure 9
Event Counter mode.
.
c
Note: The PWM output is not available in this mode since the TxApin is being
shows a block diagram of the timer in External
used as the counter input clock.
DS101133-10
www.national.com 14

Timers (Continued)
DS101133-11
FIGURE 9. Timer in External Event Counter Mode
Mode 3. Input Capture Mode
The device can precisely measure external frequencies or
time external events by placing the timer block, Tx, in the input capture mode.
In this mode, the timer Tx is constantly running at the fixed t
rate. The two registers, RxA and RxB, act as capture registers. Each register acts in conjunction with apin. The register
RxAacts in conjunction with theTxA pin and the register RxB
acts in conjunction with the TxB pin.
The timer value gets copied over into the register when a
trigger event occurs on its corresponding pin. Control bits,
TxC3, TxC2 and TxC1, allow the trigger events to be specified either as a positive or a negative edge. The trigger condition for each input pin can be specified independently.
The trigger conditions can also be programmed to generate
interrupts. The occurrence of the specified trigger condition
on the TxAand TxB pins will be respectively latched into the
pending flags, TxPNDA and TxPNDB. The control flag TxENA allows the interrupt on TxA to be either enabled or disabled. Setting the TxENAflag enablesinterrupts to be generated when the selected trigger condition occurs on the TxA
pin. Similarly, the flag TxENB controls the interrupts from the
TxB pin.
T2 has additional flexibility because T2B can be internally
connected to the comparator output of the Analog Function
Block. This allows the userto capture the time of a comparator event without using external pins.
Underflows from the timer can also be programmed to generate interrupts. Underflows are latched into the timer TxC0
pending flag (theTxC0 control bit serves as the timer underflow interrupt pending flag in the Input Capture mode). Consequently, the TxC0 control bit should be reset when entering the Input Capture mode. The timer underflow interrupt is
enabled with the TxENA control flag. When a TxA interrupt
occurs in the Input Capture mode, the user must check both
the TxPNDA and TxC0 pending flags in order to determine
whether a TxA input capture or a timer underflow (or both)
caused the interrupt.
Figure 10
ture mode.
shows a block diagram of the timer in Input Cap-
FIGURE 10. Timer in Input Capture Mode
TIMER CONTROL FLAGS
The control bits and their functions are summarized below.
TxC3 Timer mode control
TxC2 Timer mode control
c
TxC1 Timer mode control
TxC0 Timer Start/Stop control in Modes 1 and 2 (Pro-
cessor Independent PWM and External Event
Counter), where 1 = Start, 0 = Stop
Timer Underflow Interrupt Pending Flag in
Mode 3 (Input Capture)
TxPNDA Timer Interrupt Pending Flag
TxENA Timer Interrupt Enable Flag
1 = Timer Interrupt Enabled
0 = Timer Interrupt Disabled
TxPNDB Timer Interrupt Pending Flag
TxENB Timer Interrupt Enable Flag
1 = Timer Interrupt Enabled
0 = Timer Interrupt Disabled
DS101133-12
www.national.com15

Timers (Continued)
The timer mode control bits (TxC3, TxC2 and TxC1) are detailed below:
Mode TxC3 TxC2 TxC1 Description
1 0 1 PWM: TxA Toggle Autoreload RA Autoreload RB t
1
1 0 0 PWM: No TxA
Toggle
0 0 0 External Event
2
0 0 1 External Event
Counter
Counter
0 1 0 Captures: Pos. TxA Edge Pos. TxB Edge t
TxA Pos. Edge or Timer
TxB Pos. Edge Underflow
1 1 0 Captures: Pos. TxA Neg. TxB t
TxA Pos. Edge Edge or Timer Edge
3
0 1 1 Captures: Neg. TxA Neg. TxB t
TxB Neg. Edge Underflow
TxA Neg. Edge Edge or Timer Edge
TxB Neg. Edge Underflow
1 1 1 Captures: Neg. TxA Neg. TxB t
TxA Neg. Edge Edge or Timer Edge
TxB Neg. Edge Underflow
Power Save Modes
The device offers the user two power save modes of operation: HALT and IDLE. In the HALT mode, all microcontroller
activities are stopped. In the IDLE mode, the on-board oscillator circuitry the WATCHDOG logic, the Clock Monitor and
timer T0 are active but all other microcontroller activities are
stopped. In either mode, all on-board RAM, registers, I/O
states, and timers (with the exception of T0) are unaltered.
HALT MODE
The device can be placed in the HALT mode by writing a “1”
to the HALT flag (G7 data bit). All microcontroller activities,
including the clock and timers, are stopped. The WATCHDOG logic is disabled during the HALT mode. However, the
clock monitor circuitry if enabled remains active and will
cause the WATCHDOGoutput pin(WDOUT) togo low. If the
HALT mode is used and the user does not want to activate
the WDOUT pin, the Clock Monitor should be disabled after
the device comes out of reset (resetting the Clock Monitor
control bit with the first write to the WDSVR register). In the
HALTmode, the power requirements of the device are minimal and the applied voltage (V
=
(V
2.0V) without altering the state of the machine.
r
The device supports three different ways of exiting the HALT
mode. The first method of exiting the HALT mode is with the
Multi-Input Wakeup feature on the L port. The second
method is with a low to high transition on the CKO (G7) pin.
This method precludes the use ofthe crystal clockconfiguration (since CKO becomes a dedicated output), and so may
be used with an RC clock configuration. The third method of
exiting the HALT mode is by pulling the RESET pin low.
Since a crystal or ceramic resonator may be selected as the
oscillator, the Wakeup signal is not allowed to start the chip
running immediately since crystal oscillators and ceramic
) may be decreased to V
CC
r
Interrupt A
Source
Autoreload RA Autoreload RB
Timer
Underflow
Timer
Underflow
Interrupt B
Source
Timer
Counts On
C
t
C
Pos. TxB Edge Pos. TxA
Edge
Pos. TxB Edge Pos. TxA
Edge
C
C
C
C
resonators have a delayed start up time to reach full amplitude and frequency stability. The IDLE timer is used to generate a fixed delay to ensure that the oscillator has indeed
stabilized before allowing instruction execution. In this case,
upon detecting a valid Wakeupsignal, only the oscillator circuitry is enabled. The IDLE timer is loaded with a value of
256 and is clocked with the t
clock is derived by dividing the oscillator clock down bya fac-
instruction cycle clock. The t
c
tor of 10. The Schmitt trigger following the CKI inverter on
the chip ensures that the IDLE timer is clocked onlywhen the
oscillator has a sufficiently large amplitude to meet the
Schmitt trigger specifications. This Schmitt trigger is not part
of the oscillator closed loop. The startup timeout from the
IDLE timer enables the clock signals to be routed to the rest
of the chip.
If an RC clock option is being used, the fixed delay is introduced optionally. A control bit, CLKDLY, mapped as configuration bit G7, controls whether the delay is to be introduced
or not. The delay is included if CLKDLY is set, and excluded
if CLKDLY is reset. The CLKDLY bit is cleared on reset.
The device has two mask options associated with the HALT
mode. The firstmask option enables theHALTmode feature,
while the second mask option disables theHALT mode. With
the HALT mode enable mask option, the device will enter
and exit the HALTmode as described above. With the HALT
disable mask option, the device cannot be placed in the
HALTmode (writing a “1”to the HALT flag will have no effect,
the HALT flag will remain “0”).
The WATCHDOG detector circuit is inhibited during the
HALTmode. However, the clock monitorcircuit ifenabled remains active during HALT mode in order to ensure a clock
monitor error if the device inadvertently enters the HALT
mode as a result of a runaway program or power glitch.
c
www.national.com 16

Power Save Modes (Continued)
IDLE MODE
The device is placed in the IDLEmode by writing a “1” to the
IDLE flag (G6 databit). In this mode, all activities, except the
associated on-board oscillator circuitry, the WATCHDOG
logic, the clock monitor and the IDLE Timer T0, are stopped.
As with the HALT mode, the device can be returned to normal operation with a reset, orwith a Multi-InputWakeup from
the L Port. Alternately, the microcontroller resumes normal
operation from the IDLEmode whenthe thirteenthbit (representing 4.096 ms atinternal clockfrequency of1 MHz, t
µs) of the IDLE Timer toggles.
This toggle condition of the thirteenth bit of the IDLE Timer
T0 is latched into the T0PND pending flag.
The user has the option of being interrupted with a transition
on the thirteenth bit of the IDLE Timer T0. The interrupt can
be enabled or disabled via the T0EN control bit. Setting the
T0EN flag enables the interrupt and vice versa.
The user can enter the IDLE mode with the Timer T0 interrupt enabled. In this case, when the T0PND bit gets set, the
=
c
device will first execute theTimer T0 interrupt service routine
and then return to the instruction following the “Enter Idle
Mode” instruction.
Alternatively, the user can enter the IDLE mode with the
IDLE Timer T0 interrupt disabled. Inthis case, the device will
resume normal operation with the instruction immediately
following the “Enter IDLE Mode” instruction.
Note: It is necessary to program two NOP instructions following both the set
HALT mode and set IDLE mode instructions. These NOP instructions
are necessary to allow clock resynchronization following the HALT or
IDLE modes.
1
Multi-Input Wakeup
The Multi-Input Wakeup feature is ued to return (wakeup) the
device from either the HALT or IDLE modes. Alternately
Multi-Input Wakeup/Interrupt feature may also be used to
generate up to 8 edge selectable external interrupts.
Figure 11
shows the Multi-Input Wakeup logic.
FIGURE 11. Multi-Input Wake Up Logic
The Multi-Input Wakeup feature utilizes the L Port. The user
selects which particular L port bit (or combination of L Port
bits) will cause the device to exit the HALT or IDLE modes.
The selection is done through the Reg: WKEN. The Reg:
WKEN is an 8-bit read/write register, which contains a control bit for every L port bit. Setting a particular WKEN bit enables a Wakeup from the associated L port pin.
The user can select whether the trigger condition on the selected L Port pin is going to be either a positive edge (low to
high transition) or a negative edge (high to low transition).
This selection is made via the Reg: WKEDG, which is an
8-bit control register with a bit assigned to each L Port pin.
Setting the control bit will select the trigger condition to be a
negative edge on that particular L Port pin. Resetting the bit
selects the trigger condition to be a positive edge. Changing
DS101133-13
an edge select entails several steps in order to avoid a
pseudo Wakeup condition as a result of the edge change.
First, the associated WKEN bit should be reset, followed by
the edge select change in WKEDG. Next, the associated
WKPND bit should be cleared, followed by the associated
WKEN bit being re-enabled.
An example may serve toclarify this procedure.Suppose we
wish to change the edge select from positive (lowgoing high)
to negative (high going low) for L Port bit 5, where bit 5 has
previously been enabled for an input interrupt. The program
would be as follows:
RBIT 5, WKEN ; Disable MIWU
SBIT 5, WKEDG ; Change edge polarity
RBIT 5, WKPND ; Reset pending flag
SBIT 5, WKEN ; Enable MIWU
www.national.com17

Multi-Input Wakeup (Continued)
If the L port bits have been used as outputs and then
changed to inputs with Multi-Input Wakeup/Interrupt, a safety
procedure should also be followed to avoid inherited pseudo
wakeup conditions. After the selected L port bits have been
changed from output to input but before the associated
WKEN bits are enabled, the associated edge select bits in
WKEDG should be set or reset for the desired edge selects,
followed by the associated WKPND bits being cleared.
This same procedure should be used following reset, since
the L port inputs are left floating as a result of reset.
The occurrence of the selected trigger condition for
Multi-Input Wakeup is latched into a pending register called
WKPND. The respective bits of the WKPND register will be
set on the occurrence of the selected trigger edge onthe corresponding Port L pin. The user has the responsibility of
clearing these pending flags. Since WKPND is a pending
register for the occurrence of selected wakeup conditions,
the device will not enter the HALT mode if any Wakeupbit is
both enabled and pending. Consequently, the user has the
responsibility of clearing the pending flags before attempting
to enter the HALT mode.
WKEN, WKPND and WKEDG are all read/write registers,
and are cleared at reset.
Analog Function Block
PORT L INTERRUPTS
Port L provides the user with an additional eight fully selectable, edge sensitive interruptswhich areall vectoredinto the
same service subroutine.
The interrupt from Port L shares logic with the wake up circuitry.The registerWKEN allows interrupts from Port L to be
individually enabled or disabled. Theregister WKEDG specifies the trigger condition to be either a positive or a negative
edge. Finally, the register WKPND latches in the pending
trigger conditions.
The GIE (Global Interrupt Enable) bit enables the interrupt
function.
A control flag, LPEN, functions as a global interrupt enable
for Port L interrupts. Setting the LPEN flag will enable interrupts and vice versa. A separate global pending flag is not
needed since the register WKPND is adequate.
Since Port L is also used for waking the device out of the
HALTor IDLE modes, the user can elect to exit the HALTor
IDLE modes either with or withoutthe interruptenabled. If he
elects to disable the interrupt, then the device will restart execution from the instruction immediately following the instruction that placed the microcontroller in the HALT or IDLE
modes. In the other case, the device will first execute the interrupt service routine and then revert to normal operation.
(See HALT MODE for clock option wakeup information.)
FIGURE 12. COP888EK Analog Function Block
www.national.com 18
DS101133-14

Analog Function Block (Continued)
This device contains an analog function block with the intent
to provide a function which allows for single slope, low cost,
A/D conversion of up to 6 channels.
CMPSL REGISTER (ADDRESS X’00B7)
CMPT2B CMPISEL2 CMPISEL1 CMPISEL0 CMPOE CSEN CMPEN CMPNEG
Bit 7 Bit 0
The CMPSL register contains the following bits:
CMPT2B Selects the timer T2B input to be driven di-
CMPISEL0/1/2 Will select one of seven possible sources
CMPOE Enables the comparator output to either pin
CSEN Enables the internal constant current
RESET
The state of the Comparator Block immediately after RESET
is as follows:
1. The CMPSL Register is set to all zeros
2. The Comparator is disabled
3. The Constant Current Source is disabled
4. CMPNEG is turned off
5. The Port I inputs are electrically isolated from the comparator
6. The T2B input is as normally selected by the T2CNTRL
Register
7. CMPISEL0–CMPISEL2 are set to zero
8. All Port I inputs are selected to the default digital input
mode
The comparator outputs have the same specification as
Ports L and G except that the rise and fall times are symmetrical.
rectly by the comparator output. If the comparator is disabled (CMPEN=0), this function is disabled, i.e., the T2B input is
connected to Port L5.
(I0/I2/I3/I4/I5/I6/internal reference) as a
positive input to the comparator (see
3
for more information.) Power savings can
Table
be realized by deselecting the internal reference when it is not in actual use.
I3 or pin I7 (“1”=enable) depending on the
value of CMPISEL0/1/2.
source. This current source provides a
TABLE 3. Comparator Input Selection
Control Bit Comparator Input Source Comparator
CMPISEL2 CMPISEL1 CMPISEL0 Neg. Input Pos. Input Output
000I1 I2 I3
001I1 I2 I7
010I1 I3 I7
011I1 I0 I7
100I1 I4 I7
101I1 I5 I7
110I1 I6 I7
111I1 V
nominal 20 µA constant current at the I1
pin. This current can be used to ensure a
linear charging rate on an external capacitor. This bit has no affect and the current
source is disabled if the comparator is not
enabled (CMPEN=0).
CMPEN Enable the comparator (“1”=enable).
CMPNEG Will drive I1 to a low level. This bit can be
used to discharge an external capacitor.
This bit is disabled if the comparator is not
enabled (CMPEN=0).
The Comparator Select Register is cleared on RESET (the
comparator is disabled). To save power the program should
also disable the comparator before the µC enters the HALT/
IDLE modes. Disabling the comparator will turn off the constant current source and the V
comparator output from the T2B input andpin I3 orI7 and re-
/2 reference, disconnect the
CC
move the low on I1 caused by CMPNEG.
It is often useful for the user’s program to read the result of
a comparator operation. Since I1 is always selected to be
COMPIN− when the comparator is enabled (CMPEN=1),
the comparator output can be read internally by reading bit 1
(CMPRD) of register PORTI (RAM address 0 x D7).
The following table lists the comparator inputs and outputs
vs. the value of the CMPISEL0/1/2 bits. The output will only
be driven if the CMPOE bit is set to 1.
/2 Ref. I7
CC
Interrupts
Each device supports eleven vectored interrupts. Interrupt
sources include Timer 0, Timer 1, Timer 2, Timer 3, Port L
Wakeup, Software Trap, MICROWIRE/PLUS, and External
Input.
All interrupts force abranch tolocation 00FF Hex in program
memory. The VIS instruction may be used to vector to the
appropriate service routine from location 00FF Hex.
The Software trap has the highest priority while the default
VIS has the lowest priority.
Each of the 11 maskable inputs has a fixed arbitration ranking and vector.
Figure 13
shows the Interrupt Block Diagram.
www.national.com19

Interrupts (Continued)
FIGURE 13. Interrupt Block Diagram
MASKABLE INTERRUPTS
All interrupts other than the Software Trap are maskable.
Each maskable interrupt has an associated enable bit and
pending flag bit. The pending bit is set to1 when theinterrupt
condition occurs. The state of the interrupt enable bit, combined with the GIE bit determines whether an active pending
flag actually triggers an interrupt. All of the maskable interrupt pending and enable bits are contained in mapped control registers, and thus can be controlled by the software.
Amaskable interrupt conditiontriggers aninterrupt under the
following conditions:
1. The enable bit associated with that interrupt is set.
2. The GIE bit is set.
3. The device is not processing a non-maskable interrupt.
(If a non-maskable interrupt is being serviced, a
maskable interrupt must wait until that service routine is
completed.)
An interrupt is triggeredonly whenall of these conditions are
met at the beginning of an instruction. If different maskable
interrupts meet these conditions simultaneously, the highest
priority interrupt will be serviced first, and the other pending
interrupts must wait.
Upon Reset, all pending bits, individual enable bits, and the
GIE bit are reset to zero. Thus, a maskable interrupt condition cannot trigger an interrupt until the program enablesit by
setting both the GIE bit and the individual enable bit. When
enabling an interrupt, the user should consider whether or
not a previously activated (set) pending bit should be acknowledged. If, at the time an interrupt is enabled, any previous occurrences of the interrupt should be ignored, the associated pending bit must be reset to zero prior to enabling
the interrupt. Otherwise, the interrupt may be simply enabled; if the pendingbit isalready set,it willimmediately trigger an interrupt. A maskable interrupt is active if its associated enable and pending bits are set.
An interrupt is an asychronous event which may occur before, during, or after an instruction cycle. Any interrupt which
occurs during the execution of an instruction is not acknowl-
DS101133-15
edged until the start of the next normallyexecuted instruction
is to be skipped,the skip is performed before the pending interrupt is acknowledged.
At the start of interrupt acknowledgment, the following actions occur:
1. TheGIE bitis automatically reset to zero,preventing any
subsequent maskable interrupt from interrupting the current service routine. This feature prevents one maskable
interrupt from interrupting another one being serviced.
2. The address of the instruction about to be executed is
pushed onto the stack.
3. The program counter (PC) is loaded with 00FF Hex,
causing a jump to that program memory location.
The device requires seven instruction cycles to perform the
actions listed above.
If the user wishes to allow nested interrupts, the interrupts
service routine may set the GIE bitto 1 bywriting to the PSW
register,and thus allowother maskableinterrupts to interrupt
the current service routine. If nested interrupts are allowed,
caution must be exercised. The user must write the program
in such a way as to prevent stack overflow, loss of saved
context information, and other unwanted conditions.
The interrupt service routine stored at location 00FF Hex
should use the VIS instruction to determine the cause of the
interrupt, and jump to the interrupt handling routine corresponding to the highest priority enabled and active interrupt.
Alternately, the user may choose to poll all interrupt pending
and enable bits to determine the source(s) of the interrupt. If
more than one interrupt is active, the user’s program must
decide which interrupt to service.
Within a specific interrupt service routine, the associated
pending bit should be cleared. This is typically done as early
as possible in the service routine in order to avoid missing
the next occurrence of the same type of interrupt event.
Thus, if the same event occurs a second time, evenwhile the
first occurrence is still being serviced, the second occurrence will be serviced immediately upon return from the current interrupt routine.
www.national.com 20

Interrupts (Continued)
An interrupt service routine typically ends with an RETI instruction. This instruction sets the GIEbit backto 1,pops the
address stored on the stack, and restoresthat address to the
program counter. Program execution then proceeds with the
next instruction that would have been executed had there
been no interrupt. If there are any valid interrupts pending,
the highest-priority interrupt is servicedimmediately upon return from the previous interrupt.
VIS INSTRUCTION
The general interrupt service routine, whichstarts ataddress
00FF Hex, must be capable of handling all types of interrupts. The VIS instruction, together with an interrupt vector
table, directs the device to the specific interrupthandling routine based on the cause of the interrupt.
VIS is a single-byte instruction, typically used at the very beginning of the general interrupt service routine at address
00FF Hex, or shortly after that point, just after the code used
for context switching. The VIS instruction determines which
enabled and pending interrupt has the highest priority, and
causes an indirect jumpto theaddress correspondingto that
interrupt source. The jump addresses (vectors) for all possible interrupts sources are stored in a vector table.
The vector table may be as long as32 bytes (maximum of 16
vectors) and resides at thetop ofthe 256-byteblock containing the VIS instruction. However, if the VIS instruction is at
the very top of a 256-byte block (such as at 00FF Hex), the
vector table resides at the top of the next 256-byte block.
Thus, if the VIS instruction is located somewhere between
00FF and 01DF Hex (the usual case), the vector table is located between addresses 01E0 and 01FF Hex. If the VIS instruction is located between 01FF and 02DF Hex, then the
vector table is located between addresses 02E0 and 02FF
Hex, and so on.
Each vector is 15 bits long and points to the beginning of a
specific interrupt service routine somewhere in the 32 kbyte
memory space. Each vector occupies two bytesof the vector
table, with the higher-order byte at the lower address. The
vectors are arranged in order of interrupt priority. The vector
of the maskable interrupt with the lowest rank is located to
0yE0 (higher-order byte) and 0yE1 (lower-order byte). The
next priority interrupt is located at 0yE2 and 0yE3, and so
forth in increasing rank. The Software Trap has the highest
rank and its vector is always located at 0yFE and 0yFF. The
number of interrupts which can become active defines the
size of the table.
Table4
shows the types of interrupts,the interrupt arbitration
ranking, and the locations of the corresponding vectors in
the vector table.
The vector table should be filledby the userwith the memory
locations of the specific interrupt service routines. For example, if the Software Trap routine is located at 0310 Hex,
then the vector location 0yFE and -0yFF should contain the
data 03 and 10 Hex, respectively. When a Software Trap interrupt occurs and the VIS instruction is executed, the program jumps to the address specified in the vector table.
The interrupt sources in the vector table are listed in order of
rank, from highest to lowest priority. If two or more enabled
and pending interrupts are detected at the same time, the
one with the highest priority is serviced first. Upon return
from the interrupt service routine, the next highest-level
pending interrupt is serviced.
If the VIS instruction is executed, but no interrupts are enabled and pending, the lowest-priority interrupt vector is
used, and a jump is made to the corresponding address in
the vector table. This is an unusual occurrence, and may be
the result of an error.It can legitimately result from a change
in the enable bits or pending flags prior to the execution of
the VIS instruction, such as executing a single cycle instruction which clears an enable flag at the same time that the
pending flag is set. It canalso result,however, from inadvertent execution of the VIS command outside of the context of
an interrupt.
The default VIS interrupt vector can be useful for applications in which time critical interrupts can occur during the
servicing of another interrupt. Rather than restoring the program context (A, B, X, etc.) and executing the RETI instruction, an interrupt service routinecan be terminatedby returning to the VIS instruction. In this case, interrupts will be
serviced in turn until no further interrupts are pending and
the default VIS routine is started. After testing the GIE bit to
ensure that execution is not erroneous, the routine should
restore the program context and execute the RETI to return
to the interrupted program.
This technique can save up to fifty instruction cycles (t
more, (50µs at 10 MHz oscillator) of latency for pending interrupts with a penalty of fewer than ten instruction cycles if
no further interrupts are pending.
To ensure reliable operation, the user should always use the
VIS instruction to determine the source of an interrupt. Although it is possible to poll the pending bits to detect the
source of an interrupt, this practice isnot recommended. The
use of polling allows the standard arbitrationranking to bealtered, but the reliability of the interrupt system is compromised. The polling routine must individually test the enable
and pending bits of each maskable interrupt. If a Software
Trap interrupt should occur, it will be serviced last, even
though it should have the highest priority. Under certain conditions, a Software Trap could be triggered but not serviced,
resulting in an inadvertent “locking out” of all maskable interrupts by the Software Trap pending flag. Problems such as
this can be avoided by using VIS instruction.
c
), or
www.national.com21

Interrupts (Continued)
TABLE 4. Interrupt Vector Table
Arbitration Vector (Note 12)
Ranking Source Description Address
Hi-Low Byte
(1) Highest Software INTR Instruction 0yFE–0yFF
Reserved 0yFC–0yFD
(2) External G0 0yFA–0yFB
(3) Timer T0 Underflow 0yF8–0yF9
(4) Timer T1 T1A/Underflow 0yF6–0yF7
(5) Timer T1 T1B 0yF4–0yF5
(6) MICROWIRE/PLUS BUSY Low 0yF2–0yF3
Reserved 0yF0–0yF1
(7) Reserved 0yEE–0yEF
(8) Reserved 0yEC–0yED
(9) Timer T2 T2A/Underflow 0yEA–0yEB
(10) Timer T2 T2B 0yE8–0yE9
(11) Timer T3 T3A/Underflow 0yE6–0yE7
(12) Timer T3 T3B 0yE4–0yE5
(13) Port L/Wakeup Port L Edge 0yE2–0yE3
(14) Lowest Default VIS Instr. Execution 0yE0–0yE1
without Any Interrupts
Note 12: y is a variable which represents the VIS block. VIS and the vector table must be located in the same 256-byte block except if VIS is located at the last address of a block. In this case, the table must be in the next block.
VIS Execution
When the VIS instruction is executed it activates the arbitration logic. The arbitration logic generates an even number
between E0 and FE (E0, E2, E4, E6 etc...) depending on
which active interrupt has the highest arbitration ranking at
the time of the 1st cycle of VIS is executed. For example, if
the software trap interrupt is active, FE is generated. If the
external interrupt is active and the software trap interrupt is
not, then FAis generated and soforth. If theonly active interrupt is software trap, than E0 is generated. This number replaces the lower byte of the PC.The upper byte ofthe PC remains unchanged. The new PC is therefore pointing to the
vector of the active interruptwith the highestarbitration ranking. This vector is read from program memory and placed
into the PC which is now pointed to the 1st instruction of the
service routine of theactive interruptwith thehighest arbitration ranking.
Figure 14
instruction.
tion.
The non-maskable interrupt pending flag is cleared by the
RPND (Reset Non-Maskable Pending Bit) instruction (under
certain conditions) and upon RESET.
illustrates the different steps performed by the VIS
Figure 15
shows a flowchart for the VIS instruc-
www.national.com 22

Interrupts (Continued)
DS101133-29
FIGURE 14. VIS Operation
FIGURE 15. VIS Flowchart
DS101133-30
www.national.com23

Interrupts (Continued)
Programming Example: External Interrupt
PSW =00EF
CNTRL =00EE
RBIT 0,PORTGC
RBIT 0,PORTGD ; G0 pin configured Hi-Z
SBIT IEDG, CNTRL ; Ext interrupt polarity; falling edge
SBIT EXEN, PSW ; Enable the external interrupt
WAIT: JP WAIT ; Wait for external interrupt
INT_EXIT:
SERVICE: RBIT EXPND, PSW ; Interrupt Service Routine
SBIT GIE, PSW ; Set the GIE bit
.
.
.
.=0FF ; The interrupt causes a
VIS ; branch to address 0FF
; The VIS causes a branch to
;interrupt vector table
.
.
.
.=01FA ; Vector table (within 256 byte
.ADDRW SERVICE ; of VIS inst.) containing the ext
; interrupt service routine
.
.
RETI
.
.
; Reset ext interrupt pend. bit
.
.
.
JP INT_EXIT ; Return, set the GIE bit
www.national.com 24

Interrupts (Continued)
NON-MASKABLE INTERRUPT
Pending Flag
There is a pending flagbit associated withthe non-maskable
interrupt, called STPND. This pending flag is not memorymapped and cannot be accessed directly by the software.
The pending flag is reset to zero when a device Reset occurs. When the non-maskable interrupt occurs, the associated pending bit is set to 1. The interrupt service routine
should contain an RPNDinstruction toreset thepending flag
to zero. The RPND instruction always resets the STPND
flag.
Software Trap
The Software Trap is a special kind of non-maskable interrupt which occurs when the INTR instruction (used to acknowledge interrupts) is fetched from program memory and
placed in the instruction register. This can happen in a variety of ways, usually because of an error condition. Some examples of causes are listed below.
If the program counter incorrectly points to a memory location beyond the available program memory space, the nonexistent or unused memory location returns zeroes which is
interpreted as the INTR instruction.
If the stack is popped beyond the allowed limit (address 06F
Hex), a 7FFF will beloaded intothe PC, ifthis lastlocation in
program memory is unprogrammed or unavailable, a Software Trap will be triggered.
A Software Trap can be triggered by a temporary hardware
condition such as a brownout or power supply glitch.
The Software Trap has the highest priority of all interrupts.
When a Software Trap occurs, the STPND bit is set.The GIE
bit is not affected and the pending bit (not accessible by the
user) is used to inhibit other interrupts and to direct the program to the ST serviceroutine withthe VISinstruction. Nothing can interrupt a Software Trap service routine except for
another Software Trap. The STPND can be reset onlyby the
RPND instruction or a chip Reset.
The Software Trap indicates an unusual or unknown error
condition. Generally, returning to normal execution at the
point where the Software Trap occurred cannot be done reliably. Therefore, the Software Trap service routine should
reinitialize the stack pointer and perform a recovery procedure that restarts the software at some known point, similar
to a device Reset, but not necessarily performing all the
same functions as adevice Reset.The routinemust also execute the RPND instruction to reset the STPND flag. Otherwise, all other interrupts will belocked out.Tothe extent possible, the interrupt routine should record or indicate the
context of the device so that the cause of the Software Trap
can be determined.
If the user wishes to return to normal execution from the
point at which the Software Trap was triggered, the user
must first execute RPND, followed by RETSK rather than
RETI or RET. This is because the return address stored on
the stack is the address ofthe INTRinstruction that triggered
the interrupt. The program must skip that instruction in order
to proceed with the next one. Otherwise, an infinite loop of
Software Traps and returns will occur.
Programming a return to normal execution requires careful
consideration. If the Software Trap routine is interrupted by
another Software Trap, the RPND instruction in the service
routine for the second Software Trap will reset the STPND
flag; upon return to the first Software Trap routine, the
STPND flag will have the wrong state. This will allow
maskable interrupts to be acknowledged during theservicing
of the first Software Trap. To avoid problemssuch as this, the
user program should contain the Software Trap routine to
perform a recovery procedure rather than a return to normal
execution.
Under normal conditions, the STPND flag is reset by a
RPND instruction in the Software Trap service routine. If a
programming error or hardware condition (brownout, power
supply glitch, etc.) sets the STPND flag without providing a
way for it to be cleared, all other interrupts will be locked out.
To alleviate this condition, the user can use extra RPND instructions in the main program and in the WATCHDOG service routine (if present). There is no harm in executing extra
RPND instructions in these parts of the program.
PORT L INTERRUPTS
Port L provides the user with an additional eight fully selectable, edge sensitive interruptswhich areall vectoredinto the
same service subroutine.
The interrupt from Port L shares logic with the wake up circuitry.The registerWKEN allows interrupts from Port L to be
individually enabled or disabled. Theregister WKEDG specifies the trigger condition to be either a positive or a negative
edge. Finally, the register WKPND latches in the pending
trigger conditions.
The GIE (Global Interrupt Enable) bit enables the interrupt
function.
A control flag, LPEN, functions as a global interrupt enable
for Port L interrupts. Setting the LPEN flag will enable interrupts and vice versa. A separate global pending flag is not
needed since the register WKPND is adequate.
Since Port L is also used for waking the device out of the
HALTor IDLE modes, the user can elect to exit the HALTor
IDLE modes either with or withoutthe interruptenabled. If he
elects to disable the interrupt, then the device will restart execution from the instruction immediately following the instruction that placed the microcontroller in the HALT or IDLE
modes. In the other case, the device will first execute the interrupt service routine and then revert to normal operation.
(See HALT MODE for clock option wakeup information.)
INTERRUPT SUMMARY
The device uses the following types of interrupts, listed below in order of priority:
1. The Software Trap non-maskable interrupt, triggered by
the INTR (00 opcode) instruction. The Software Trap is
acknowledged immediately. This interrupt service routine can be interrupted only by another Software Trap.
The Software Trap should end with two RPND instructions followed by a restart procedure.
2. Maskable interrupts, triggered by an on-chip peripheral
block or an external device connected to the device. Under ordinary conditions, a maskable interrupt will not interrupt any other interrupt routine in progress. A
maskable interrupt routine in progress can be interrupted by the non-maskable interrupt request. A
maskable interrupt routine should end with an RETI instruction or, prior to restoring context, should return to
execute the VIS instruction. This is particularly useful
when exiting long interrupt service routiness if the time
between interrupts is short. In this case theRETI instruction would only be executed when the default VIS routine is reached.
www.national.com25

WATCHDOG
The device contains a WATCHDOG and clock monitor. The
WATCHDOG is designed to detect the user program getting
stuck in infinite loops resulting in loss of program control or
“runaway” programs. The Clock Monitor is used todetect the
absence of a clock or a very slow clock below a specified
rate on the CKI pin.
The WATCHDOG consists of two independent logic blocks:
WD UPPER and WD LOWER. WD UPPER establishes the
upper limit on the service window and WD LOWER defines
the lower limit of the service window.
Servicing the WATCHDOG consists of writing a specific
value to a WATCHDOG Service Register named WDSVR
which is memory mapped in the RAM. This value is composed of three fields, consisting of a 2-bit Window Select, a
5-bit Key Data field, and the 1-bit Clock Monitor Select field.
Table 5
shows the WDSVR register.
TABLE 5. WATCHDOG Service Register (WDSVR)
Window
Select
Key Data
Clock
Monitor
XX01100 Y
7654321 0
The lower limit ofthe servicewindow isfixed at2048 instruction cycles. Bits 7 and 6 of the WDSVR register allow the
user to pick an upper limit of the service window.
Table 6
shows the four possible combinations of lower and
upper limits for the WATCHDOG service window. This flexibility in choosing the WATCHDOG service window prevents
any undue burden on the user software.
Bits 5, 4, 3, 2 and 1 of the WDSVR register represent the
5-bit Key Data field. The key data is fixed at 01100. Bit 0 of
the WDSVR Register is the Clock Monitor Select bit.
TABLE 6. WATCHDOG Service Window Select
WDSVR WDSVR Clock Service Window
Bit 7 Bit 6 Monitor (Lower-Upper Limits)
0 0 x 2048–8k t
0 1 x 2048–16k t
1 0 x 2048–32k t
1 1 x 2048–64k t
C
C
C
C
Cycles
Cycles
Cycles
Cycles
x x 0 Clock Monitor Disabled
x x 1 Clock Monitor Enabled
Clock Monitor
The Clock Monitor aboard the device can be selected or deselected under program control. The Clock Monitor is guaranteed not to reject the clock if the instruction cycle clock (1/
t
) is greater or equal to 10kHz. This equates toa clock input
c
rate on CKI of greater or equal to 100 kHz.
WATCHDOG Operation
The WATCHDOG and Clock Monitor are disabled during reset. The device comes out of reset with the WATCHDOG
armed, the WATCHDOG Window Select bits (bits 6, 7 of the
WDSVR Register) set, and the Clock Monitor bit (bit 0 of the
WDSVR Register) enabled. Thus, a Clock Monitor error will
occur after coming out of reset, if the instruction cycle clock
frequency has not reached a minimum specified value, including the case where the oscillator fails to start.
The WDSVR register can be written to only once after reset
and the key data (bits 5 through 1 of the WDSVR Register)
must match to be a valid write.This writeto theWDSVR register involves two irrevocable choices: (i) the selection of the
WATCHDOG service window (ii) enabling or disabling of the
Clock Monitor. Hence, the first write to WDSVR Register involves selecting or deselecting the Clock Monitor, select the
WATCHDOG service window and match the WATCHDOG
key data. Subsequent writes to the WDSVR register will
compare the value being written by the user to the WATCHDOG service window value and the key data (bits 7 through
1) in the WDSVR Register. Table IV shows the sequence of
events that can occur.
The user must service the WATCHDOG at least once before
the upper limit of the service window expires. The WATCHDOG may not be serviced more than once in every lower
limit of the service window. The user may service the
WATCHDOG as many times aswished in thetime period between the lower and upper limits of the service window. The
first write to the WDSVR Register is also counted as a
WATCHDOG service.
The WATCHDOG has an output pin associated with it. This
is the WDOUT pin, on pin 1 of the port G. WDOUT is active
low.The WDOUT pin isin the highimpedance state inthe inactive state. Upon triggering the WATCHDOG, the logic will
pull the WDOUT (G1) pin low for an additional 16 t
cycles after the signal level on WDOUT pin goes below the
–32t
c
lower Schmitt trigger threshold. After this delay, the device
will stop forcing the WDOUT output low.
The WATCHDOG service window will restart when the
WDOUT pin goes high. It is recommended that the user tie
the WDOUT pin back to V
pull WDOUT high.
through a resistor in order to
CC
AWATCHDOGservice whilethe WDOUT signal isactive will
be ignored. The state of the WDOUT pin is not guaranteed
on reset, but if it powers up low then the WATCHDOG will
time out and WDOUT will enter high impedance state.
The Clock Monitor forces the G1 pin low upon detecting a
clock frequency error. The Clock Monitor error will continue
until the clock frequencyhas reached the minimum specified
value, after which the G1 output will enter the high impedance TRI-STATE mode following 16 t
The Clock Monitor generatesa continual Clock Monitor error
–32 tcclock cycles.
c
if the oscillator fails to start, or fails to reach the minimum
specified frequency. The specification for the Clock Monitor
is as follows:
>
1/t
10 kHz—No clock rejection.
c
<
10 Hz—Guaranteed clock rejection.
1/t
c
WATCHDOG AND CLOCK MONITOR SUMMARY
The following salient points regarding the WATCHDOG and
CLOCK MONITOR should be noted:
Both the WATCHDOG and CLOCK MONITOR detector
•
circuits are inhibited during RESET.
Following RESET, the WATCHDOG and CLOCK MONI-
•
TOR are both enabled, with the WATCHDOG having he
maximum service window selected.
The WATCHDOG service window and CLOCK MONI-
•
TOR enable/disable option can only be changed once,
during the initial WATCHDOG service following RESET.
c
www.national.com 26

WATCHDOG Operation (Continued)
The initial WATCHDOG service must match the key data
•
value in the WATCHDOG Service register WDSVR in order to avoid a WATCHDOG error.
Subsequent WATCHDOG services must match all three
•
data fields in WDSVR in order to avoid WATCHDOG errors.
The correct key data value cannot be read from the
•
WATCHDOG Service register WDSVR. Any attempt to
read this key data value of 01100 from WDSVR will read
as key data value of all 0’s.
The WATCHDOG detector circuit is inhibited during both
•
the HALT and IDLE modes.
The CLOCK MONITOR detector circuit is active during
•
both the HALT and IDLE modes. Consequently, the device inadvertently entering the HALT mode will be detected as a CLOCK MONITOR error (provided that the
CLOCK MONITOR enable option has been selected by
the program).
With the single-pin R/C oscillator mask option selected
•
and the CLKDLY bit reset, the WATCHDOG service window will resume following HALT mode from where it left
off before entering the HALT mode.
With the crystal oscillator mask option selected, or with
•
the single-pin R/C oscillator mask option selected and the
CLKDLYbit set, the WATCHDOG service window will be
set to its selected value from WDSVR following HALT.
Consequently, the WATCHDOG should not be serviced
for at least 2048 instruction cycles following HALT, but
must be serviced within the selected window to avoid a
WATCHDOG error.
The IDLE timer T0 is not initialized with RESET.
•
The user can sync in to the IDLE counter cycle with an
•
IDLE counter (T0) interrupt or by monitoring the T0PND
flag. The T0PND flag is set whenever the thirteenth bit of
the IDLE counter toggles (every 4096 instruction cycles).
The user is responsible for resetting the T0PND flag.
A hardware WATCHDOG service occurs just as the de-
•
vice exits the IDLE mode. Consequently, the WATCHDOG should not be serviced for at least 2048 instruction
cycles following IDLE, but mustbe serviced withinthe selected window to avoid a WATCHDOG error.
Following RESET, the initial WATCHDOG service (where
•
the service window and the CLOCK MONITOR enable/
disable must be selected) may be programmed anywhere within the maximum service window (65,536 instruction cycles) initialized by RESET. Note thatthis initial
WATCHDOG service may be programmed within the initial 2048 instruction cycles without causing a WATCHDOG error.
Detection of Illegal Conditions
The device can detect various illegal conditions resulting
from coding errors, transient noise, power supply voltage
drops, runaway programs, etc.
Reading of undefined ROM gets zeros. The opcode for software interrupt is zero. If the program fetches instructions
from undefined ROM, this willforce a softwareinterrupt, thus
signaling that an illegal condition has occurred.
The subroutine stack grows down for each call (jump to subroutine), interrupt, or PUSH, and grows up for each return or
POP. The stack pointer is initialized toRAM location 06F Hex
during reset. Consequently, if there are more returns than
calls, the stack pointer will point to addresses 070 and 071
Hex (which are undefined RAM). Undefined RAM from addresses 070 to 07F (Segment 0), 140 to 17F (Segment 1),
and all other segments (i.e., Segments 2 … etc.) is read as
all 1’s, which in turn will cause the program to return to address 7FFF Hex.This is an undefined ROM location and the
instruction fetched (all 0’s) from this location will generate a
software interrupt signaling an illegal condition.
Thus, the chip can detect the following illegal conditions:
1. Executing from undefined ROM
2. Over “POP”ing the stack by having more returns than
calls.
When the software interrupt occurs, the user can re-initialize
the stack pointer and do a recovery procedurebefore restarting (this recovery program is probably similar to that following reset, but might not contain the same program initialization procedures). The recovery program should reset the
software interrupt pending bit using the RPND instruction.
MICROWIRE/PLUS
MICROWIRE/PLUS is a serial synchronous communications
interface. The MICROWIRE/PLUS capability enables the device to interface with any of National Semiconductor’s MICROWIRE peripherals (i.e. A/D converters, display drivers,
2
E
PROMs etc.) and with other microcontrollers which support the MICROWIRE interface. It consists of an 8-bit serial
shift register (SIO) with serial data input (SI), serial data output (SO) and serial shift clock (SK).
diagram of the MICROWIRE/PLUS logic.
FIGURE 16. MICROWIRE/PLUS Block Diagram
The shift clock can be selected fromeither an internalsource
or an external source. Operating the MICROWIRE/PLUS arrangement with the internalclock sourceis calledthe Master
mode of operation. Similarly, operating the MICROWIRE/
PLUS arrangement with an external shift clock is called the
Slave mode of operation.
The CNTRL register is used to configure and control the
MICROWIRE/PLUS mode. To use the MICROWIRE/PLUS,
the MSEL bit in theCNTRL register is set to one. In the master mode, the SK clock rate is selected by the two bits, SL0
and SL1, in the CNTRL register. details the different clock
rates that may be selected.
Figure 16
shows a block
DS101133-16
www.national.com27

MICROWIRE/PLUS (Continued)
TABLE 7. WATCHDOG Service Actions
Key Window Clock Action
Data Data Monitor
Match Match Match Valid Service: Restart Service Window
Don’t Care Mismatch Don’t Care Error: Generate WATCHDOG Output
Mismatch Don’t Care Don’t Care Error: Generate WATCHDOG Output
Don’t Care Don’t Care Mismatch Error: Generate WATCHDOG Output
TABLE 8. MICROWIRE/PLUS
Master Mode Clock Select
SL1 SL0 SK
0 0 2xt
0 1 4xt
1 x 8xt
Where tcis the
instruction cycle clock
MICROWIRE/PLUS OPERATION
Setting the BUSY bit in the PSW register causes the
MICROWIRE/PLUS to start shifting the data. It gets reset
when eight data bits have been shifted. The user may reset
the BUSY bit by software to allow less than 8 bits to shift. If
enabled, an interrupt is generated when eight data bits have
been shifted. The device may enter the MICROWIRE/PLUS
mode either as a Masteror asa Slave.
two microcontroller devices and several peripherals may be
interconnected using the MICROWIRE/PLUS arrangements.
Warning:
The SIO register should only be loaded when the SK clock is
low. Loading the SIO register while the SK clock is high will
result in undefined data in the SIO register. SK clock is normally low when not shifting.
Setting the BUSY flag when the input SK clock is high in the
MICROWIRE/PLUS slave mode may cause the current SK
clock for the SIO shift register to be narrow. For safety, the
BUSY flag should only beset whenthe inputSK clockis low.
MICROWIRE/PLUS Master Mode Operation
In the MICROWIRE/PLUS Master mode of operation the
shift clock (SK) is generatedinternally by thedevice. The MICROWIRE Master always initiates all data exchanges. The
MSEL bit in the CNTRL register must be set to enable the
SO and SK functions onto the G Port. The SO and SK pins
must also be selected as outputs by setting appropriate bits
in the Port G configuration register.
bit settings required for Master mode of operation.
MICROWIRE/PLUS Slave Mode Operation
In the MICROWIRE/PLUS Slave mode of operation the SK
clock is generated by an external source. Setting the MSEL
bit in the CNTRL register enables the SO and SK functions
c
c
c
Figure 17
Table 9
shows how
summarizes the
onto the G Port. The SK pin must be selected as an input
and the SO pin is selected asan output pin bysetting and resetting the appropriate bits in the Port G configuration register.
Table 9
summarizes the settings required to enter the
Slave mode of operation.
The user must set the BUSY flag immediately upon entering
the Slave mode. This will ensure that all databits sentby the
Master will be shifted properly. After eight clock pulses the
BUSY flag will be cleared and the sequence may be repeated.
TABLE 9. MICROWIRE/PLUS Mode Settings
This table assumes that the control flag MSEL is set.
G4 (SO) G5 (SK) G4 G5
Config. Bit Config. Bit Fun. Fun.
1 1 SO Int. MICROWIRE/PLUS
SK Master
0 1 TRI- Int. MICROWIRE/PLUS
STATE SK Master
1 0 SO Ext. MICROWIRE/PLUS
SK Slave
0 0 TRI- Ext. MICROWIRE/PLUS
STATE SK Slave
Operation
Alternate SK Phase Operation
The device allows either the normal SK clock or an alternate
phase SK clock to shift data inand out of the SIO register.In
both the modes the SK is normally low. In the normal mode
data is shifted in on the rising edge of the SK clock and the
data is shifted out on the falling edge of the SK clock. The
SIO register is shifted on each falling edge of the SK clock.
In the alternate SK phase operation, data is shifted in on the
falling edge of the SK clock and shifted out on therising edge
of the SK clock.
A control flag, SKSEL, allows either the normal SK clock or
the alternate SK clock to be selected. Resetting SKSEL
causes the MICROWIRE/PLUS logic to be clocked from the
normal SK signal. Setting the SKSEL flag selects the alternate SK clock.The SKSELis mapped into the G6 configuration bit. The SKSEL flag will power up in the reset condition,
selecting the normal SK signal.
www.national.com 28

MICROWIRE/PLUS (Continued)
FIGURE 17. MICROWIRE/PLUS Application
DS101133-17
www.national.com29

Memory Map
All RAM, ports and registers (except A and PC) are
mapped into data memory address space.
Address Contents
S/ADD REG
0000 to 006F On-Chip RAM bytes (112 bytes)
0070 to 007F Unused RAM Address Space (Reads
xx80 to xxAF Unused RAM Address Space (Reads
xxB0 Timer T3 Lower Byte
xxB1 Timer T3 Upper Byte
xxB2 Timer T3 Autoload Register T3RA
xxB3 Timer T3 Autoload Register T3RA
xxB4 Timer T3 Autoload Register T3RB
xxB5 Timer T3 Autoload Register T3RB
xxB6 Timer T3 Control Register
xxB7 Comparator Select Register (CMPSL)
xxB8 to xxBF Reserved
xxC0 Timer T2 Lower Byte
xxC1 Timer T2 Upper Byte
xxC2 Timer T2 Autoload Register T2RA
xxC3 Timer T2 Autoload Register T2RA
xxC4 Timer T2 Autoload Register T2RB
xxC5 Timer T2 Autoload Register T2RB
xxC6 Timer T2 Control Register
xxC7 WATCHDOG Service Register
xxC8 MIWU Edge Select Register
xxC9 MIWU Enable Register (Reg:WKEN)
xxCA MIWU Pending Register (Reg:WKPND)
xxCB Reserved
xxCC Reserved
xxCD to xxCF Reserved
As All Ones)
Undefined Data)
Lower Byte
Upper Byte
Lower Byte
Upper Byte
Lower Byte
Upper Byte
Lower Byte
Upper Byte
(Reg:WDSVR)
(Reg:WKEDG)
Address Contents
S/ADD REG
xxD0 Port L Data Register
xxD1 Port L Configuration Register
xxD2 Port L Input Pins (Read Only)
xxD3 Reserved for Port L
xxD4 Port G Data Register
xxD5 Port G Configuration Register
xxD6 Port G Input Pins (Read Only)
xxD7 Port I Input Pins (Read Only)
xxD8 Port C Data Register
xxD9 Port C Configuration Register
xxDA Port C Input Pins (Read Only)
xxDB Reserved for Port C
xxDC Port D
xxDD to xxDF Reserved
xxE0 to xxE5 Reserved
xxE6 Timer T1 Autoload Register T1RB
Lower Byte
xxE7 Timer T1 Autoload Register T1RB
Upper Byte
xxE8 ICNTRL Register
xxE9 MICROWIRE/PLUS Shift Register
xxEA Timer T1 Lower Byte
xxEB Timer T1 Upper Byte
xxEC Timer T1 Autoload Register T1RA
Lower Byte
xxED Timer T1 Autoload Register T1RA
Upper Byte
xxEE CNTRL Control Register
xxEF PSW Register
xxF0 to xxFB On-Chip RAM Mapped as Registers
xxFC X Register
xxFD SP Register
xxFE B Register
xxFF S Register
0100 to 017F On-Chip 128 RAM Bytes
Reading memory locations 0070H–007FH (Segment 0) will return all ones.
Reading unused memory locations 0080H–00AFH (Segment 0) will return
undefined data. Reading memory locations from other unused Segments
(i.e., Segment 2, Segment 3, … etc.) will return undefined data.
www.national.com 30

Addressing Modes
There are ten addressing modes,six foroperand addressing
and four for transfer of control.
OPERAND ADDRESSING MODES
Register Indirect
This is the “normal” addressing mode. The operand is the
data memory addressed by the B pointer or X pointer.
Register Indirect (with auto post increment or
decrement of pointer)
This addressing mode is used with the LD and X instructions. The operand is the data memory addressed by the B
pointer or X pointer. This is a register indirect mode that automatically post increments or decrements the B or X register after executing the instruction.
Direct
The instruction contains an 8-bit address field that directly
points to the data memory for the operand.
Immediate
The instruction contains an8-bit immediatefield asthe operand.
Short Immediate
This addressing mode isused withthe LoadB Immediate instruction. The instruction contains a 4-bit immediate field as
the operand.
Indirect
This addressing mode is used with the LAID instruction.The
contents of the accumulator are used as a partial address
(lower 8 bits of PC) for accessing a data operand from the
program memory.
TRANSFER OF CONTROL ADDRESSING MODES
Relative
This mode is used for the JP instruction, with the instruction
field being added to the program counter to get the new program location. JP has a range from −31 to +32 to allow a
1-byte relative jump (JP + 1 is implemented by a NOP instruction). There are no “pages” when using JP, since all 15
bits of PC are used.
Absolute
This mode is used with the JMP and JSR instructions, with
the instruction field of 12 bits replacing the lower 12 bits of
the program counter (PC). This allows jumping to any location in the current 4k program memory segment.
Absolute Long
This mode is used with theJMPL and JSRL instructions, with
the instruction field of 15 bits replacing the entire 15 bits of
the program counter (PC). This allows jumping to any location in the current 4k program memory space.
Indirect
This mode is used with the JID instruction. The contents of
the accumulator are used as a partial address (lower 8bits of
PC) for accessing a location in the program memory. The
contents of this program memory location serve as a partial
address (lower 8 bits of PC) for the jump to the next instruction.
Note: The VIS is a special case of the Indirect Transfer of Control addressing
mode, where the double byte vector associated with the interrupt is
transferred from adjacent addresses in the program memory into the
program counter (PC) in order to jump to the associated interrupt service routine.
Instruction Set
Register and Symbol Definition
Registers
A 8-Bit Accumulator Register
B 8-Bit Address Register
X 8-Bit Address Register
S 8-Bit Segment Register
SP 8-Bit Stack Pointer Register
PC 15-Bit Program Counter Register
PU Upper 7 Bits of PC
PL Lower 8 Bits of PC
C 1 Bit of PSW Register for Carry
HC 1 Bit of PSW Register for Half Carry
GIE 1 Bit of PSW Register for Global Interrupt
VU Interrupt Vector Upper Byte
VL Interrupt Vector Lower Byte
[B] Memory Indirectly Addressed by B Register
[X] Memory Indirectly Addressed by X Register
MD Direct Addressed Memory
Mem Direct Addressed Memory or [B]
Meml Direct Addressed Memory or [B] or
Imm 8-Bit Immediate Data
Reg Register Memory: Addresses F0 to FF
Bit Bit Number (0 to 7)
←
↔
Enable
Symbols
Immediate Data
(Includes B, X and SP)
Loaded with
Exchanged with
www.national.com31

Instruction Set (Continued)
INSTRUCTION SET
ADD A,Meml ADD A←A + Meml
ADC A,Meml ADD with Carry A←A+Meml+C,C←Carry
HC←Half Carry
SUBC A,Meml Subtract with Carry A←A−MemI+C,C←Carry
HC←Half Carry
AND A,Meml Logical AND A←A and Meml
ANDSZ A,Imm Logical AND Immed., Skip if Zero Skip next if (A and Imm)=0
OR A,Meml Logical OR A←A or Meml
XOR A,Meml Logical EXclusive OR A←A xor Meml
IFEQ MD,Imm IF EQual Compare MD and Imm, Do next if MD=Imm
IFEQ A,Meml IF EQual Compare A and Meml, Do next if A=Meml
IFNE A,Meml IF Not Equal Compare A and Meml, Do next if A
IFGT A,Meml IF Greater Than Compare A and Meml, Do next if A
IFBNE
DRSZ Reg Decrement Reg., Skip if Zero Reg←Reg − 1, Skip if Reg=0
SBIT
RBIT
IFBIT
RPND Reset PeNDing Flag Reset Software Interrupt Pending Flag
X A,Mem EXchange A with Memory A
X A,[X] EXchange A with Memory [X] A
LD A,Meml LoaD A with Memory A←Meml
LD A,[X] LoaD A with Memory [X] A←[X]
LD B,Imm LoaD B with Immed. B←Imm
LD Mem,Imm LoaD Memory Immed Mem←Imm
LD Reg,Imm LoaD Register Memory Immed. Reg←Imm
XA,[B
XA,[X
LD A, [B
LD A, [X
LD [B
CLR A CLeaR A A←0
INC A INCrement A A←A+1
DEC A DECrement A A←A−1
LAID Load A InDirect from ROM A←ROM (PU,A)
DCOR A Decimal CORrect A A←BCD correction of A (follows ADC, SUBC)
RRC A Rotate A Right thru C C→A7→…→A0→C
RLC A Rotate A Left thru C C←A7←…←A0←C
SWAP A SWAP nibbles of A A7…A4
SC Set C C←1, HC←1
RC Reset C C←0, HC←0
IFC IF C IF C is true, do next instruction
IFNC IF Not C If C is not true, do next instruction
POP A POP the stack into A SP←SP+1,A←[SP]
PUSH A PUSH A onto the stack [SP]←A, SP←SP−1
VIS Vector to Interrupt Service Routine PU←[VU], PL←[VL]
JMPL Addr. Jump absolute Long PC←ii (ii=15 bits, 0 to 32k)
JMP Addr. Jump absolute PC9…0←i(i=12 bits)
JP Disp. Jump relative short PC←PC+r(ris−31to+32, except 1)
#
#
,Mem Set BIT 1 to bit, Mem (bit=0 to 7 immediate)
#
,Mem Reset BIT 0 to bit, Mem
#
,Mem IF BIT If bit in A or Mem is true do next instruction
±
±
±
],Imm LoaD Memory [B] Immed. [B]←Imm, (B←B±1)
If B Not Equal Do next if lower 4 bits of B≠Imm
↔
Mem
↔
[X]
±
] EXchange A with Memory [B] A↔[B], (B←B±1)
↔
A3…A0
←
±
±
] EXchange A with Memory [X] A↔[X], (X
] LoaD A with Memory [B] A←[B], (B←B±1)
] LoaD A with Memory [X] A←[X], (X←X±1)
1)
≠
>
Meml
Meml
www.national.com 32

Instruction Set (Continued)
JSRL Addr. Jump SubRoutine Long [SP]←PL, [SP−1]←PU,SP−2, PC←ii
JSR Addr Jump SubRoutine [SP]←PL, [SP−1]←PU,SP−2, PC9…0←i
JID Jump InDirect PL←ROM (PU,A)
RET RETurn from subroutine SP + 2, PL←[SP], PU←[SP−1]
RETSK RETurn and SKip SP + 2, PL←[SP],PU←[SP−1]
RETI RETurn from Interrupt SP + 2, PL←[SP],PU←[SP−1],GIE←1
INTR Generate an Interrupt [SP]←PL, [SP−1]←PU, SP−2, PC←0FF
NOP No OPeration PC←PC+1
www.national.com33

Instruction Set (Continued)
Instruction Execution Time
Most instructions are singlebyte (withimmediate addressing
mode instructions taking two bytes).
Most single byte instructions take one cycle time to execute.
Skipped instructions require x number of cycles to be
•
skipped, where x equals the number of bytes in the
skipped instruction opcode.
See the BYTES and CYCLES per INSTRUCTION table for
details.
Bytes and Cycles per Instruction
The following table shows the number of bytes andcycles for
each instruction in the format of byte/cycle.
Arithmetic and Logic Instructions
[B] Direct Immed.
ADD 1/1 3/4 2/2
ADC 1/1 3/4 2/2
SUBC 1/1 3/4 2/2
AND 1/1 3/4 2/2
OR 1/1 3/4 2/2
XOR 1/1 3/4 2/2
IFEQ 1/1 3/4 2/2
IFNE 1/1 3/4 2/2
IFGT 1/1 3/4 2/2
IFBNE 1/1
DRSZ 1/3
SBIT 1/1 3/4
RBIT 1/1 3/4
IFBIT 1/1 3/4
RPND 1/1
Instructions Using A & C
CLRA 1/1
INCA 1/1
DECA 1/1
LAID 1/3
DCOR 1/1
RRCA 1/1
RLCA 1/1
SWAPA 1/1
SC 1/1
RC 1/1
IFC 1/1
IFNC 1/1
PUSHA 1/3
POPA 1/3
ANDSZ 2/2
Transfer of Control Instructions
JMPL 3/4
JMP 2/3
JP 1/3
JSRL 3/5
JSR 2/5
JID 1/3
VIS 1/5
RET 1/5
RETSK 1/5
RETI 1/5
INTR 1/7
NOP 1/1
Memory Transfer Instructions
Register Direct Immed. Register Indirect
Indirect Auto Incr. & Decr.
[B] [X] [B+, B−] [X+, X−]
X A, (Note 13) 1/1 1/3 2/3 1/2 1/3
LD A, (Note 13) 1/1 1/3 2/3 2/2 1/2 1/3
LD B, Imm 1/1 (IF B
LD B, Imm 2/2 (IF B
LD Mem, Imm 2/2 3/3 2/2
LD Reg, Imm 2/3
IFEQ MD, Imm 3/3
Note 13: Memory location addressed by B or X or directly.
www.national.com 34
<
16)
>
15)

Bits 3–0
JP+19 JP+3 2
JP+20 JP+4 3
JMP
IFBNE 3 JSR
LD
*
IFBIT
IFGT
IFGT
X
X
JP+21 JP+5 4
JMP
0300–03FF
0300–03FF
IFBNE 4 JSR
B,0C
CLRA LD
3,[B]
IFBIT
ADD
A,[B]
i
#
A,
LAID ADD
A,[B−]
*
A,[X−]
0400–04FF
0400–04FF
B,0B
4,[B]
A,[B]
i
#
A,
JP+17 INTR 0
JP+18 JP+2 1
JMP
0100–01FF
0100–01FF
IFBNE 1 JSR
LD
B,0E
*
1,[B]
IFBIT
A,[B]
SUBC
i
#
A,
SC SUBC
*
JMP
IFBNE 2 JSR
LD
*
IFBIT
IFEQ
IFEQ
X
X
0200–02FF
0200–02FF
B,0D
2,[B]
A,[B]
i
#
A,
A,[B+]
A,[X+]
JMP
0000–00FF
0000–00FF
IFBNE 0 JSR
LD
B,0F
*
Bits 7–4
IFBIT
ADC
0,[B]
A,[B]
i
#
A,
RRCA RC ADC
JP+22 JP+6 5
JMP
IFBNE 5 JSR
SWAPA LD
IFBIT
AND
JID AND
*
0500–05FF
0500–05FF
B,0A
5,[B]
A,[B]
i
#
A,
JP+23 JP+7 6
JP+24 JP+8 7
JMP
JMP
0600–06FF
0600–06FF
LD B,8 IFBNE 7 JSR
*
DCORA LD B,9 IFBNE 6 JSR
6,[B]
IFBIT
IFBIT
OR
XOR
A,[B]
i
#
OR
A,
XOR
A,[B]
**
X A,[X] X
0700–07FF
0700–07FF
7,[B]
A,[B]
i
#
A,
JP+25 JP+9 8
JP+26 JP+10 9
JP+27 JP+11 A
JMP
JMP
JMP
0800–08FF
0900–09FF
0A00–0AFF
JSR
0800–08FF
0900–09FF
0A00–0AFF
0A
LD B,7 IFBNE 8 JSR
LD B,6 IFBNE 9 JSR
LD B,5 IFBNE
0,[B]
1,[B]
RBIT
i IFC SBIT
#
LD A,
*
NOP
0,[B]
2,[B]
RBIT
RBIT
1,[B]
2,[B]
IFNC SBIT
INCA SBIT
i
#
LD
[B+],
LD
A,[B+]
***
LD
A,[X+]
JP+28 JP+12 B
JMP
0B00–0BFF
JSR
0B00–0BFF
0B
LD B,4 IFBNE
3,[B]
RBIT
3,[B]
DECA SBIT
i
#
LD
[B−],
LD
A,[B−]
LD
A,[X−]
JP+29 JP+13 C
JMP
0C00–0CFF
JSR
0C00–0CFF
0C
LD B,3 IFBNE
4,[B]
RBIT
4,[B]
SBIT
*
JMPL X A,Md
i
#
LD
Md,
JP+30 JP+14 D
JMP
0D00–0DFF
JSR
0D00–0DFF
0D
LD B,2 IFBNE
5,[B]
RBIT
5,[B]
RETSK SBIT
A,Md
DIR JSRL LD
JP+31 JP+15 E
JP+32 JP+16 F
JMP
JMP
0F00–0FFF
0E00–0EFF
JSR
JSR
0F00–0FFF
0E00–0EFF
0F
0E
LD B,1 IFBNE
LD B,0 IFBNE
6,[B]
7,[B]
RBIT
RBIT
6,[B]
7,[B]
RET SBIT
RETI SBIT
i
#
LD
[B],
LD
A,[B]
***
LD
A,[X]
Opcode Table
i DRSZ
#
FE D C BA9 876 5 4 3 2 1 0
JP−15 JP−31 LD 0F0,
0F0
0F1
i DRSZ
#
JP−14 JP−30 LD 0F1,
i DRSZ
#
JP−13 JP−29 LD 0F2,
0F2
0F3
i DRSZ
#
JP−12 JP−28 LD 0F3,
0F4
i DRSZ
#
JP−11 JP−27 LD 0F4,
0F5
i DRSZ
#
JP−10 JP−26 LD 0F5,
0F6
i DRSZ
#
JP−9 JP−25 LD 0F6,
0F7
i DRSZ
#
JP−8 JP−24 LD 0F7,
0F8
i DRSZ
#
JP−7 JP−23 LD 0F8,
0F9
i DRSZ
#
JP−6 JP−22 LD 0F9,
0FA
i DRSZ
#
JP−5 JP−21 LD 0FA,
0FB
i DRSZ
#
JP−4 JP−20 LD 0FB,
0FC
i DRSZ
#
JP−3 JP−19 LD 0FC,
0FD
i DRSZ
#
JP−2 JP−18 LD 0FD,
0FE
i DRSZ
#
JP−1 JP−17 LD 0FE,
0FF
i DRSZ
#
JP−0 JP−16 LD 0FF,
www.national.com35
i is the immediate data
where,
is an unused opcode (see following table)
*
Md is a directly addressed memory location

Development Support
OVERVIEW
National is engaged withan international community of independent 3rd party vendors who provide hardware and software development tool support. Through National’s interaction and guidance, these tools cooperate to form a choice of
tools that fits each developer’s needs.
This section provides a summary of the tool and development kits currently available. Up-to-date information, selection guides, free tools, demos, updates, and purchase information can be obtained at our web site at:
www.national.com/cop8.
SUMMARY OF TOOLS
COP8 Evaluation Tools
COP8–NSEVAL: Free Software Evaluation package for
•
Windows. A fully integrated evaluation environment for
COP8, including versions of WCOP8 IDE (Integrated Development Environment), COP8-NSASM, COP8-MLSIM,
COP8C, DriveWay
information.
COP8 —NSASM: Free COP8Assembler v5 for Win32.
•
Macro assembler, linker, and librarian for COP8 software
development. Supports all COP8 devices. (DOS/Win16
v4.10.2 available with limited support).
COP8–MLSIM: Free Instruction Level Simulator tool for
•
Windows. For testing and debugging software instructions only (No I/O or interrupt support).
COP8–EPU: Very Low cost COP8 Evaluation & Pro-
•
gramming Unit. Windows based evaluation and
hardware-simulation tool, with COP8 device programmer
and erasable samples. Includes COP8-NSDEV, Driveway COP8 Demo, MetaLink Debugger, I/O cables and
power supply.
COP8–EVAL-ICUxx: Very Low cost evaluation and de-
•
sign test board for COP8ACC and COP8SGx Families,
from ICU. Real-time environment with add-on A/D, D/A,
and EEPROM. Includes software routines and reference
designs.
Manuals,Applications Notes, Literature: Available free
•
from our web site at: www.national.com/cop8.
COP8 Integrated Software/Hardware Design Development Kits
COP8-EPU: Very Low cost Evaluation & Programming
•
Unit. Windows based development and hardwaresimulation tool for COPSx/xG families, with COP8 device
programmer and samples. Includes COP8-NSDEV,
Driveway COP8 Demo, MetaLink Debugger, cables and
power supply.
COP8-DM: Moderate cost DebugModule from MetaLink.
•
A Windows based, real-time in-circuit emulation tool with
COP8 device programmer. Includes COP8-NSDEV,
DriveWay COP8 Demo, MetaLink Debugger, power supply, emulation cables and adapters.
COP8 Development Languages and Environments
COP8-NSASM: Free COP8 Assembler v5 for Win32.
•
Macro assembler, linker, and librarian for COP8 software
development. Supports all COP8 devices. (DOS/Win16
v4.10.2 available with limited support). (Compatible with
WCOP8 IDE, COP8C, and DriveWay COP8).
™
COP8, Manuals, and other COP8
COP8-NSDEV: Very low cost Software Development
•
Package for Windows. An integrated development environment for COP8, including WCOP8 IDE, COP8NSASM, COP8-MLSIM.
COP8C: Moderately priced C Cross-Compiler and Code
•
Development System from Byte Craft (no code limit). Includes BCLIDE (Byte Craft Limited Integrated Development Environment) for Win32, editor,optimizing C CrossCompiler, macro cross assembler, BC-Linker, and
MetaLink tools support. (DOS/SUN versions available;
Compiler is installable under WCOP8 IDE; Compatible
with DriveWay COP8).
EWCOP8-KS: Very Low cost ANSI C-Compiler and Em-
•
bedded Workbench from IAR (Kickstart version:
COP8Sx/Fx only with 2k code limit; No FP). A fully integrated Win32 IDE, ANSI C-Compiler, macro assembler,
editor, linker, Liberian, C-Spy simulator/debugger, PLUS
MetaLink EPU/DM emulator support.
EWCOP8-AS: Moderately priced COP8 Assembler and
•
Embedded Workbench from IAR (no code limit). Afully integrated Win32 IDE, macro assembler, editor, linker, librarian, and C-Spy high-level simulator/debugger with
I/O and interrupts support. (Upgradeable with optional
C-Compiler and/or MetaLink Debugger/Emulator support).
EWCOP8-BL: Moderately priced ANSI C-Compiler and
•
Embedded Workbench from IAR (Baseline version: All
COP8 devices; 4k code limit; no FP). A fully integrated
Win32 IDE, ANSI C-Compiler, macro assembler, editor,
linker,librarian, and C-Spy high-level simulator/debugger.
(Upgradeable; CWCOP8-M MetaLink toolsinterface support optional).
EWCOP8: Full featured ANSI C-Compiler and Embed-
•
ded Workbench for Windows from IAR (no code limit). A
fully integrated Win32 IDE, ANSI C-Compiler, macro assembler, editor, linker, librarian, and C-Spy high-level
simulator/debugger. (CWCOP8-M MetaLink tools interface support optional).
EWCOP8-M: Full featured ANSI C-Compiler and Embed-
•
ded Workbench for Windows from IAR (no code limit). A
fully integrated Win32 IDE, ANSI C-Compiler, macro assembler, editor, linker, librarian, C-Spy high-level
simulator/debugger, PLUS MetaLink debugger/hardware
interface (CWCOP8-M).
COP8 Productivity Enhancement Tools
WCOP8 IDE: Very Low cost IDE (Integrated Develop-
•
ment Environment) from KKD. Supports COP8C, COP8NSASM, COP8-MLSIM, DriveWay COP8, and MetaLink
debugger under a common Windows Project Management environment. Code development, debug, and emulation tools can be launched from the project window
framework.
DriveWay-COP8: Low cost COP8 Peripherals Code
•
Generation tool from Aisys Corporation. Automatically
generates tested and documented C or Assembly source
code modules containing I/O drivers and interrupt handlers for each on-chip peripheral. Application specific
code can be inserted for customization using the integrated editor. (Compatible with COP8-NSASM, COP8C,
and WCOP8 IDE.)
COP8-UTILS: Free set of COP8 assembly code ex-
•
amples, device drivers,and utilities to speed up code development.
www.national.com 36

Development Support (Continued)
COP8-MLSIM: Free Instruction Level Simulator tool for
•
Windows. For testing and debugging software instructions only (No I/O or interrupt support).
COP8 Real-Time Emulation Tools
COP8-DM: MetaLink Debug Module. A moderately
•
priced real-time in-circuit emulation tool, with COP8 device programmer. Includes COP8-NSDEV, DriveWay
COP8 Demo, MetaLink Debugger, power supply, emulation cables and adapters.
IM-COP8: MetaLink iceMASTER®. A full featured, real-
•
time in-circuit emulator for COP8 devices. Includes
TOOLS ORDERING NUMBERS FOR THE COP87L88EK/RK FAMILY DEVICES
Vendor Tools Order Number Cost Notes
National COP8-NSEVAL COP8-NSEVAL Free Web site download
COP8-NSASM COP8-NSASM Free Included in EPU and DM. Web site download
COP8-MLSIM COP8-MLSIM Free Included in EPU and DM. Web site download
COP8-NSDEV COP8-NSDEV VL Included in EPU and DM. Order CD from website
COP8-EPU Not available for this device
COP8-DM Contact MetaLink
Development
Devices
IM-COP8 Contact MetaLink
MetaLink COP8-EPU Not available for this device
COP8-DM DM4-COP8-888EK (10
DM Target
Adapters
IM-COP8 IM-COP8-AD-464 (-220)
IM Probe Card PC-884EK28DW-AD-10 M 10 MHz 28 DIP probe card; 2.5V to 6.0V
IM Probe Target
Adapter
ICU COP8-EVAL Not available for this device
KKD WCOP8-IDE WCOP8-IDE VL Included in EPU and DM
IAR EWCOP8-xx See summary above L - H Included all software and manuals
Byte
COP8C COP8C M Included all software and manuals
Craft
Aisys DriveWay COP8 DriveWay COP8 L Included all software and manuals
OTP Programmers
Cost: Free; VL =
<
$100; L = $100 - $300; M = $300 - $1k; H = $1k - $3k; VH = $3k - $5k
COP87L84EK
COP87L88EK
MHz), plus PS-10, plus
DM-COP8/xxx (ie. 28D)
MHW-CNV39 L DM target converters for 28SO
(10 MHz maximum)
PC-888EK40DW-AD-10 M 10 MHz 40 DIP probe card; 2.5V to 6.0V
PC-888EK44PW-AD-10 M 10 MHz 44 PLCC probe card; 2.5V to 6.0V
MHW-SOIC28 L 28 pin SOIC adapter for probe card
Contact vendors L - H For approved programmer listings and vendor
COP8-NSDEV, Driveway COP8 Demo, MetaLink Windows Debugger, and power supply. Package-specific
probes and surface mount adaptors are ordered separately.
COP8 Device Programmer Support
MetaLink’s EPU and Debug Moduleinclude development
•
device programming capability for COP8 devices.
Third-party programmers and automatic handling equip-
•
ment cover needs from engineering prototype and pilot
production, to full production environments.
Factory programming available for high-volume require-
•
ments.
VL 16k OTP devices.
M Included p/s (PS-10), target cable of choice (DIP or
PLCC; i.e. DM-COP8/28D), 16/20/28/40 DIP/SO and
44 PLCC programming sockets. Add target adapter (if
needed)
H Base unit 10 MHz; -220 = 220V; add probe card
(required) and target adapter (if needed); included
software and manuals
information, go to our OTP support page at:
www.national.com/cop8
www.national.com37

Development Support (Continued)
WHERE TO GET TOOLS
Tools are ordered directly from the following vendors. Please go to the vendor’s web site for current listings of distributors.
Vendor Home Office Electronic Sites Other Main Offices
Aisys U.S.A.: Santa Clara, CA www.aisysinc.com Distributors
1-408-327-8820 info
fax: 1-408-327-8830
Byte Craft U.S.A. www.bytecraft.com Distributors
1-519-888-6911 info
fax: 1-519-746-6751
Hilton U.S.A.: Milford, PA www.erols.com/sjg1/hilton.htm
IAR Sweden: Uppsala www.iar.se U.S.A.: San Francisco
+46 18 16 78 00 info
fax: +46 18 16 78 38 info
ICU Sweden: Polygonvaegen www.icu.se Switzeland: Hoehe
+46 8 630 11 20 support
fax: +46 8 630 11 70 support
KKD Denmark: www.kkd.dk
MetaLink U.S.A.: Chandler, AZ www.metaice.com Germany: Kirchseeon
1-800-638-2423 sales
fax: 1-602-926-1198 support
National U.S.A.: Santa Clara, CA www.national.com/cop8 Europe: +49 (0) 180 530 8585
1-800-272-9959 support
fax: 1-800-737-7018 europe.support
The following companies have approved COP8 programmers in a variety of configurations. Contact your local office
or distributor. You can link to their web sites and get the latest listing of approved programmers from National’s COP8
OTP Support page at: www.national.com/cop8.
Advantech; Advin; BP Microsystems; Data I/O; Hi-Lo Systems; ICE Technology; Lloyd Research; Logical Devices;
MQP; Needhams; Phyton; SMS; Stag Programmers; System General; Tribal Microsystems; Xeltek.
@
aisysinc.com
@
bytecraft.com
@
jhilton
warwick.net
@
iar.se 1-415-765-5500
@
iar.com fax: 1-415-765-5503
@
info
iarsys.co.uk U.K.: London
@
info
iar.de +44 171 924 33 34
fax: +44 171 924 53 41
Germany: Munich
+49 89 470 6022
fax: +49 89 470 956
@
icu.se +41 34 497 28 21
@
icu.ch
@
metaice.com 80-91-5696-0
@
metaice.com fax: 80-91-2386
bbs: 1-602-962-0013 islanger
@
metalink.de
www.metalink.de Distributors Worldwide
@
nsc.com fax: +49 (0) 180 530 8586
@
nsc.com Distributors Worldwide
Customer Support
Complete product information and technical support is available from National’s customer responses centers, and from
our on-line COP8 customer support sites.
www.national.com 38

Physical Dimensions inches (millimeters) unless otherwise noted
Order Number COP684EK-XXX/WM, COP884EK-XXX/WM,
Molded SO Wide Body Package (WM)
COP984EK-XXX/WM or COP984EKH-XXX/WM
NS Package Number M28B
Molded Dual-In-Line Package (N)
Order Number COP684EK-XXX/N, COP884EK-XXX/N,
COP984EK-XXX/N or COP984EKH-XXX/N
NS Package Number N28B
www.national.com39

Physical Dimensions inches (millimeters) unless otherwise noted (Continued)
Order Number COP688EK-XXX/N, COP888EK-XXX/N,
Order Number COP688EK-XXX/V, COP888EK-XXX/V,
Molded Dual-In-Line Package (N)
COP988EK-XXX/N or COP988EKH-XXX/N
NS Package Number N40A
Plastic Leaded Chip Carrier (V)
COP988EK-XXX/V or COP988EKH-XXX/V
NS Package Number V44A
www.national.com 40

Notes
COP87L88EK/RK Family, 8-Bit CMOS OTP Microcontrollers with 8k or 32k Memory, Comparator,
and Single-slope A/D Capability
LIFE SUPPORT POLICY
NATIONAL’S PRODUCTS ARE NOT AUTHORIZED FOR USE AS CRITICAL COMPONENTS IN LIFE SUPPORT
DEVICES OR SYSTEMS WITHOUT THE EXPRESS WRITTEN APPROVAL OF THE PRESIDENT AND GENERAL
COUNSEL OF NATIONAL SEMICONDUCTOR CORPORATION. As used herein:
1. Life support devices or systems are devices or
systems which, (a) are intended for surgical implant
into the body, or (b) support or sustain life, and
whose failure to perform when properly used in
accordance with instructions for use provided in the
2. A critical component is any component of a life
support device or system whose failure to perform
can be reasonably expected to cause the failure of
the life support device or system, or to affect its
safety or effectiveness.
labeling, can be reasonably expected to result in a
significant injury to the user.
National Semiconductor
Corporation
Americas
Tel: 1-800-272-9959
Fax: 1-800-737-7018
Email: support@nsc.com
www.national.com
National does not assume any responsibility for use of any circuitry described, no circuit patent licenses are implied and National reserves the right at any time without notice to change said circuitry and specifications.
National Semiconductor
Europe
Fax: +49 (0) 1 80-530 85 86
Email: europe.support@nsc.com
Deutsch Tel: +49 (0) 1 80-530 85 85
English Tel: +49 (0) 1 80-532 78 32
Français Tel: +49 (0) 1 80-532 93 58
Italiano Tel: +49 (0) 1 80-534 16 80
National Semiconductor
Asia Pacific Customer
Response Group
Tel: 65-2544466
Fax: 65-2504466
Email: sea.support@nsc.com
National Semiconductor
Japan Ltd.
Tel: 81-3-5639-7560
Fax: 81-3-5639-7507
 Loading...
Loading...