
SSH IPSec Client
Models RFIPSC-1/5/10/50
Quick Start Guide


Quick Start Guide
82013151 Revision B
SSH IPSec Client Model # RFIPSC-1/5/10/50
for RouteFinder Model # RF650VPN
This publication may not be reproduced, in whole or in part, without prior expressed written permission from
Multi-Tech Systems, Inc. All rights reserved.
Copyright © 2001, by Multi-Tech Systems, Inc.
Multi-Tech Systems, Inc. makes no representations or warranties with respect to the contents
hereof and specifically disclaims any implied warranties of merchantability or fitness for any
particular purpose.
publication and to make changes from time to time in the content hereof without obligation of MultiTech Systems, Inc. to notify any person or organization of such revisions or changes.
Furthermore, Multi-Tech Systems, Inc. reserves the right to revise this
Record of Revisions
Revision Date Description
A 9/7/01 Manual released for SSH Sentinel v1.2.0.15.
B 11/21/01 Manual revised to add RFIPSC-1, license agreement text and
editorial changes.
Patents
This Product is covered by one or more of the following U.S. Patent Numbers:
5.301.274; 5.309.562 ; 5.355.365; 5.355.653; 5.452.289; 5.453.986. Other
Patents Pending.
TRADEMARKS
Trademarks of Multi-Tech Systems, Inc.: Multi-Tech, the Multi-Tech logo and
RouteFinder.
Windows is a registered trademark of Microsoft Corporation in the United States and
other countries.
SSH, ssh, SSH Secure Shell, and SSH Sentinel are trademarks or registered trademarks
of SSH Communications Security Corp.
All products or technologies are the trademarks or registered trademarks of their
respective holders.
Multi-Tech Systems, Inc.
2205 Woodale Drive
Mounds View, Minnesota 55112
(763) 785-3500 or (800) 328-9717
Fax 763-785-9874
Tech Support (800) 972-2439
Internet Address: http://www.multitech.com

iv

Contents
Chapter 1 – Introduction and Description
Introduction ......................................................................................... 7
Product Description .............................................................................. 7
Internet Protocol (IP) ............................................................................ 8
Internet Protocol Security (IPSec)......................................................... 8
About this Manual and Related Manuals ................................................ 9
Ship Kit Contents.................................................................................. 9
Chapter 2 – SSH IPSec Client Installation and Setup
Introduction ......................................................................................... 11
Pre-Installation Requirements............................................................... 11
Starting the SSH Sentinel Installation................................................... 12
Authenitcation Key Generation.............................................................. 13
Identity Information ............................................................................. 15
Choose the Enrollment Method ............................................................. 15
Enrollment Methods.............................................................................. 16
Encryption Speed Diagnostics ............................................................... 18
Completing the Installation................................................................... 19
SSH IPSec Client Setup ........................................................................ 20
Host to Net Setup................................................................................. 20
Host to Net using SSH Sentinel 1.1.1.................................................... 21
RouteFinder Configuration ........................................................ 23
Sentinel Configuration .............................................................. 24
SSH Sentinel Installation Notes............................................................. 35
SSH Sentinel Release Notes.................................................................. 35
Updating SSH Sentinel .......................................................................... 36
Removing SSH Sentinel........................................................................ 36
Chapter 3 - Service, Warranty and Tech Support
Introduction ......................................................................................... 39
Limited Warranty.................................................................................. 39
On-line Warranty Registration............................................................... 39
Recording RouteFinder Information....................................................... 40
Contacting Tech Support via E-mail....................................................... 40
Service ................................................................................................ 39
Multi-Tech on the Internet.................................................................... 39
Ordering Accessories ............................................................................ 39
Appendix A - RFIPSC-1/5/10/50 Client Software CD 41
Appendix B - Multi-User Software License Agreement 45
v

Figures
Figure Number Title Page Number
Figure 1 The SSH Sentinel installation package icon. 12
Figure 2. SSH Sentinel Welcome screen. 12
Figure 3. Licensing Agreement 13
Figure 4. Choose Destination Path. 14
Figure 5. Generating the Authentication Key. 15
Figure 6. Authentication Key Generation Done. 15
Figure 7. Inquiring Certificate Identity. 16
Figure 8. Choosing the Enrollment Method. 17
Figure 9. Online Enrollment Sett ings. 18
Figure 10. Off-line Certification Request. 19
Figure 11. Encryption Speed Diagnostics screen 20
Figure 12. SSH Sentinel Installation Completed screen. 21
Figure 13. RouteFinder Add a New Connection screen. 23
Figure 14. The Sentinel Policy Editor screen. 24
Figure 15. Sentinel Key Management select Authentication Keys. 24
Figure 16. Sentinel Add a new Authentication Key. 25
Figure 17. Sentinel Select Primary Identifier and Host IP Address. 25
Figure 18. Sentinel Preshared Key Information screen. 26
Figure 19. Sentinel Select VPN Connection screen. 27
Figure 20. Sentinel Select Security Gateway and Intranet IP Address. 29
Figure 21. Sentinel Probing IPSec connection parameters screen 30
Figure 22. Sentinel Probe Results .. unsuccessful screen. 30
Figure 23. Sentinel IP Address Settings, Proposal Parameters, & Rule Comment 31
Figure 24. Sentinel Connection Properties | Advanced Options screen 32
Figure 25. Sentinel Probe Results | IPSec Connection working correctly . 33
Figure 26. Sentinel Probing Result Details screen 34
Figure 27. Sentinel Updating Security Policy screen. 35
Figure 28. Sentinel Diagnostics ... Ping the new connection screen. 36
vi

RFIPSC Quick Start Guide
Chapter 1 – Introduction and
Description
Introduction
Welcome to Multi-Tech’s new RouteFinder, model RF650VPN. The RF650VPN is an
Internet security appliance that lets you use data encryption and the Internet to
securely connect to telecommuters, remote offices, customers or suppliers while
avoiding the cost of expensive private leased lines.
The SSH Sentinel IPSec VPN Client software is available in 1-, 5-, 10- and 50-user
packages. The RF650VPN provides SSH Sentinel version 1.1.1 client software (30-day
trial Internet Pilot version with Static IP support). It allows client computer connection
to the RF650VPN using PSK (Pre Shared Keys) in a Host-to-Net connection.
Chapter 2 of this manual describe the SSH IPSec VPN client installation and setup
process for the full 1-, 5-, 10- or 50-user Sentinel SSH IPSec VPN client packages with
these Multi-Tech model numbers:
Model Description
RFIPSC-1 SSH IPSec VPN Client 1-User License
RFIPSC-5 SSH IPSec VPN Client 5-User License
RFIPSC-10 SSH IPSec VPN Client 10-User License
RFIPSC-50 SSH IPSec VPN Client 50-User License
Product Description
SSH Sentinel is a software product for securing Internet Protocol (IP) based traffic using
the IPSec protocol - as specified by Internet Engineering Task Force (IETF) standards.
SSH Sentinel is an easy-to-use product designed for end users. It allows you to encrypt
and authenticate important network connections, like remote access to corporate
networks remote administration, file transfer, sending and receiving email (SMTP, POP)
and IP telephony.
SSH Sentinel software currently supports the following Microsoft Windows operating
systems: Windows 95, Windows 98, Windows NT4, Windows Me and Windows 2000.
SSH Sentinel is designed to be a client type IPSec application. The features are
designed for a single user workstation using a single network adapter and the Internet
Protocol (IP). SSH Sentinel supports all network connection types, including dial-up.
The product is designed to be secure and robust, easy to use, and quick to adapt to the
environment at hand.
Key characteristics include intuitive installation and configuration, as well as an easy
way to use certificates for authentication.
7

PN 82013151
Internet Protocol (IP)
The open architecture of the Internet Protocol (IP) makes it a highly efficient, costeffective and flexible communications protocol for local and global communications.
IP is widely adopted, not only on the global Internet, but also in the internal networks
of large corporations.
The Internet Protocol was designed to be highly reliable against random network errors.
However, it was not designed to be secure against a malicious attacker. In fact, it is
vulnerable to a number of well-known attacks. This is preventing it from being used to
its fullest for business and other purposes involving confidential or mission-critical data.
The most common types of attacks include:
• Eavesdropping on a transmission, for example, looking for passwords, credit card
numbers, or business secrets.
• Taking over communications, or hijacking communications, in such a way that the
attacker can inspect and modify any data being transmitted between the
communicating parties.
• Faking network addresses, also known as IP spoofing, in order to fool access control
mechanisms based on network addresses, or to redirect connections to a fake
server.
Internet Protocol Security (IPSec)
Internet Engineering Task Force (IETF) has developed the Internet Protocol Security
(IPSec) protocol suite to prevent misuse and attacks on IP. IETF is an international
standards body with representation from hundreds of leading companies, universities,
and individuals developing Internet-related technologies. Its track record includes the
Internet Protocol itself and most of the other protocols and technologies that form the
backbone of the Internet.
The IPSec protocol suite adds security to the basic IP version 4 protocol and is
supported by all leading vendors of Internet products. IPSec is a mandatory part of the
next generation of IP protocol, IP version 6. The IPSec protocol works on the network
level. It adds authentication and encryption to each data packets transmitted. It
protects each packet against eavesdropping and modification, and provides
authentication of the origin of the packet.
IPSec works independently of any application protocol. Thus, all applications that use IP
protocol for data transfer are equally and transparently protected. IPSec makes it safe
to use the Internet for transmitting confidential data. By doing so, it solves the main
obstacle that is slowing down the adoption of the Internet for business use.
8
RFIPSC Quick Start Guide
About this Manual and Related Manuals
This Quick Start Guide manual contains four chapters and one appendix, and is
intended to provide the experienced client user or system administrator with the
information needed to quickly get the SSH IPSec Client software up and running. The
full Sentinel SSH IPSec Client User Guide manual is provided on the SSH IPSec Client
CD-ROM included in the license pak.
Please address comments about this manual to the Multi-Tech Publications Dept.
Related manuals may include add-on product documentation for options such as the
Windows PPTP client, the E-Mail Anti-Virus Upgrade, etc.
This document may contain links to sites on the Internet, which are owned and
operated by third parties. Multi-Tech Systems, Inc. is not responsible for the content of
any such third-party site.
Ship Kit Contents
The SSH IPSec Client License Pak is shipped with the following:
· one SSH IPSec CD-ROM
· one SSH IPSec Client License
· one printed Quick Start Guide manual
· one Multi-User Software License Agreement
· one Registration Card
If any of these items are missing, contact Multi-Tech Systems or your dealer or
distributor. Inspect the contents for signs of any shipping damage. If damage is
observed, do not install the software; contact Multi-Tech’s Tech Support for advice.
9

PN 82013151
10

RFIPSC Quick Start Guide
Chapter 2 - SSH IPSec Client
Installation and Setup
Introduction
This section describes the SSH Sentinel software, an IPSsec client product by SSH
Communications Security Corp, providing secure communications over a TCP/IP
connection. The Sentinel SSH software is used by client devices for secure connection
to the Multi-Tech RouteFinder model RF650VPN. The SSH Sentinel client installation
and setup procedures are described in the following sections.
The installation of the SSH Sentinel software is a straightforward process guided by an
installation wizard, and you should be able to complete it without studying this manual.
This beginning of this section describes the first installation of the SSH Sentinel
software. During the installation, you create an authentication key pair and a matching
certificate to be used for authentication. However, if a previous version of the software
is already installed on your computer, then launching the installation only updates the
existing software to the new version. The security policy rules and the authentication
keys that you have configured with the previous version of the software are preserved.
You can always remove the software completely and then reinstall it.
Pre-Installation Requirements
SSH Sentinel client software works on the following Microsoft Windows platforms and
versions:
Platform Version Build Notes
Windows 95 OSR1, OSR2 Winsock2 required
Windows 98 SE Windows NT 4.0 SP3 to SP6 Windows Me Windows 2000 SP1 -
SSH Sentinel is a client-type implementation of IPSec; it is not IPSec gateway software,
even though some of the Windows platforms are capable of functioning as routers.
Before starting SSH Sentinel client installation, make sure that there are no other IPSec
implementations, network sniffers, NAT applications, firewalls, or third party
intermediate network drivers installed. SSH Sentinel may affect the functionality of such
software.
The SSH Sentinel installation requires that you have full access rights for the system
files on your computer. On a Windows NT system, you must log in with administrator
rights.
11
PN 82013151
To run the SSH Sentinel client software, you need a personal computer with at least the
following configuration:
• Processor Pentium 100 MHz
• Memory (RAM) 32 MB for Windows 9x, or 64 MB for Windows NT4/2000
• Hard disk space 10 megabytes of free disk space
• Network connection TCP/IP network protocol
Starting the SSH Sentinel Installation
The SSH Sentinel installation requires that you have full access rights for the system
files on your computer. On a Windows NT system, you must log in with administrator
rights.
1. In Windows Explorer, double click the SSH Sentinel installation package icon
Sentinel.exe. The Sentinel.exe file is included on the RFIPSC-5/10/50 SSH Sentinel IPSec Client
CD (refer to Appendix A of this manual for more information on the CD).
Figure 1. The SSH Sentinel installation package icon.
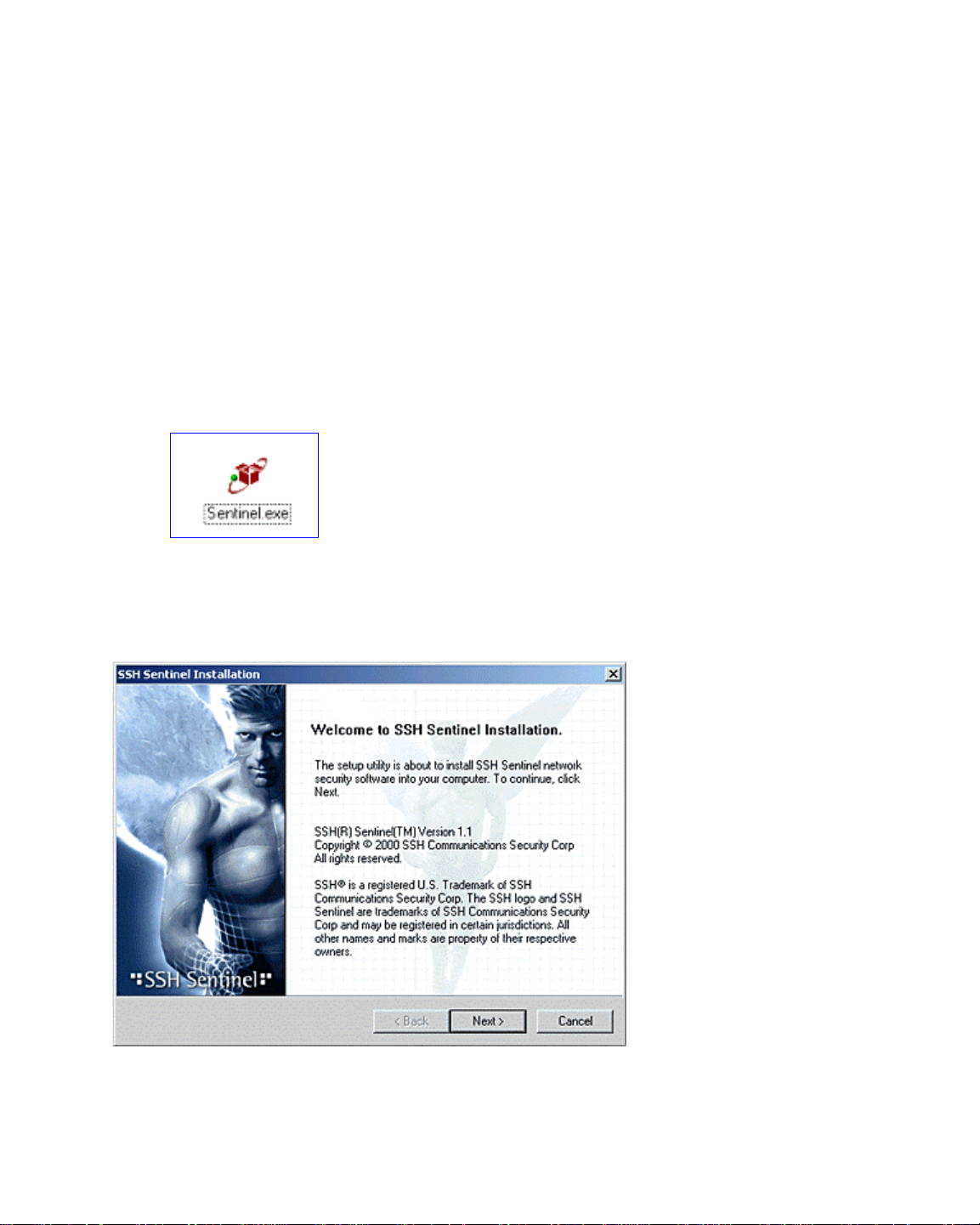
The self-extracting package automatically initiates InstallShield software to install and
set up SSH Sentinel Client software.
Figure 2. SSH Sentinel Welcome screen.
12
RFIPSC Quick Start Guide
The installer will run Installation Wizard, which creates the initial configuration and sets
up the SSH Sentinel client software.
Note: If a previous version of the SSH Sentinel software is installed on your computer
and you try to install a new version, the wizard updates the software and the steps
described here are skipped.
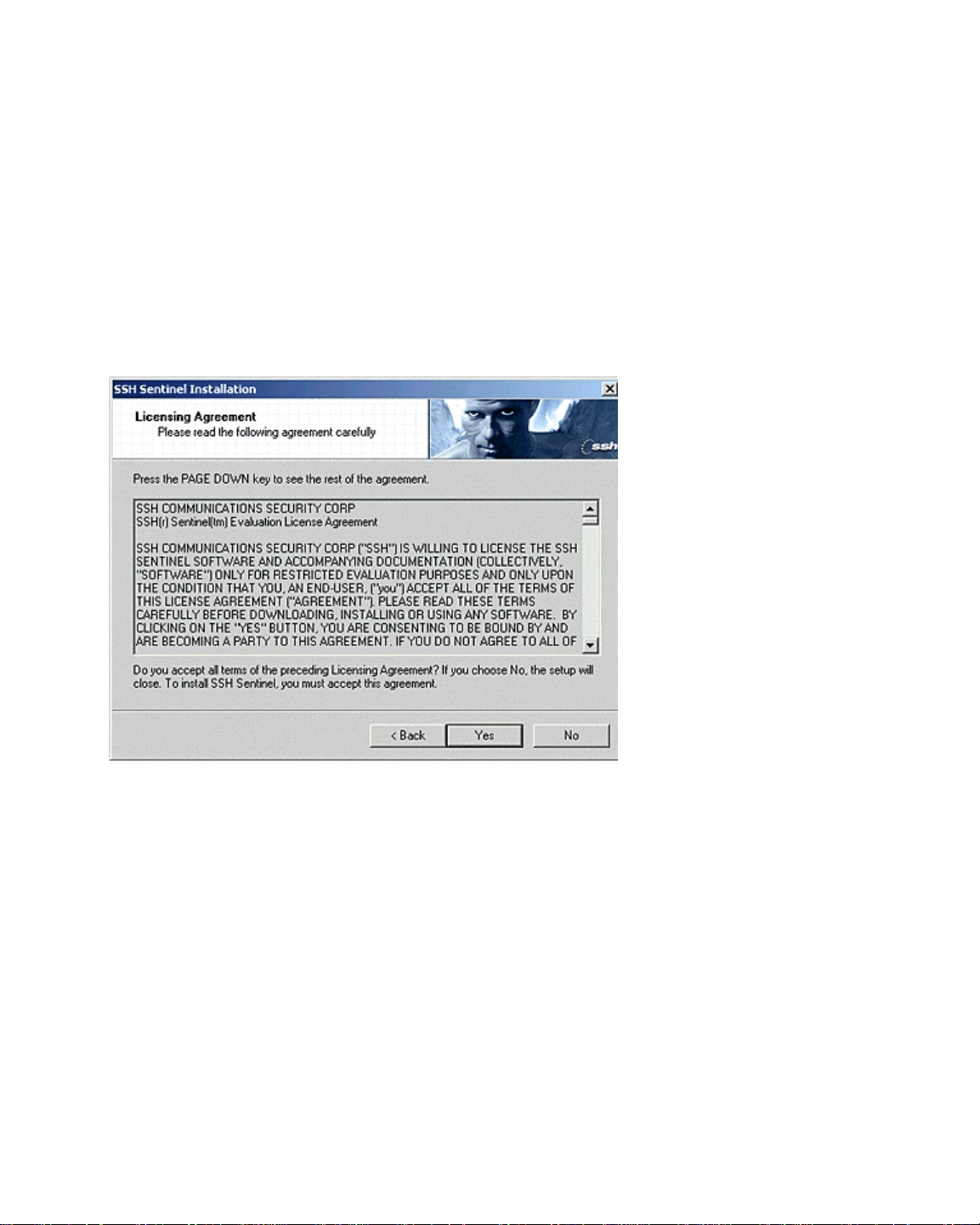
3. When started, the Installation Wizard goes through a sequence of basic installation
dialogs, displaying the licensing agreement and allowing you to select the installation
directory and the program folder. The installation can only be performed on a local
computer. Remote installation of SSH Sentinel is not possible, because the installation
program updates kernel mode components related to networking and remote access.
Figure 3. Licensing Agreement
Note that the installation will terminate immediately if you do not accept the licensing
agreement.
13
PN 82013151
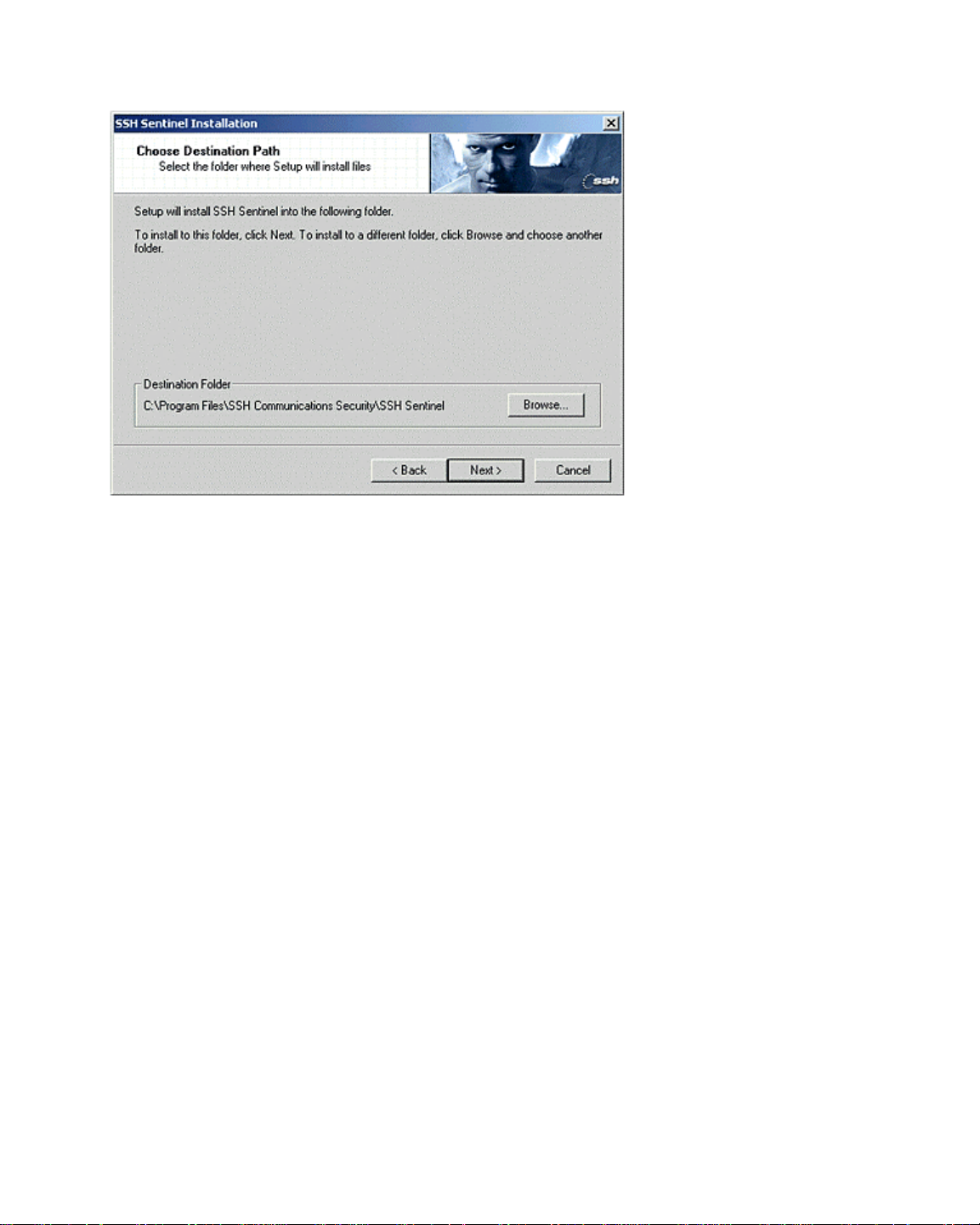
Figure 4. Choose Destination Path.
Authentication Key Generation
The SSH Sentinel Installation Wizard generates a primary authentication key for IPSec
peer (host) authentication purposes. The primary authentication key is a 1024-bit RSA
key pair that is used for digital signatures and strong authentication.
Authentication key generation begins with random seed generation. A random pool of
data is collected from the user moving the mouse or typing in random text. The data is
then used as a seed to ensure that all authentication keys will be unique. With this
method, the likelihood of generating two identical authentication keys is infinitesimal.
The general level of security that can be provided with 1024-bit RSA authentication
keys is considered military strength. The Internet Key Exchange (IKE) protocol used in
key negotiation is better by design and security than most of the other solutions that
currently exist.
The SSH Sentinel key generation process will take some 30 seconds and may
momentarily use most of the computer’s CPU resources.
4. Once the authentication key generation is complete, proceed with the installation.
14
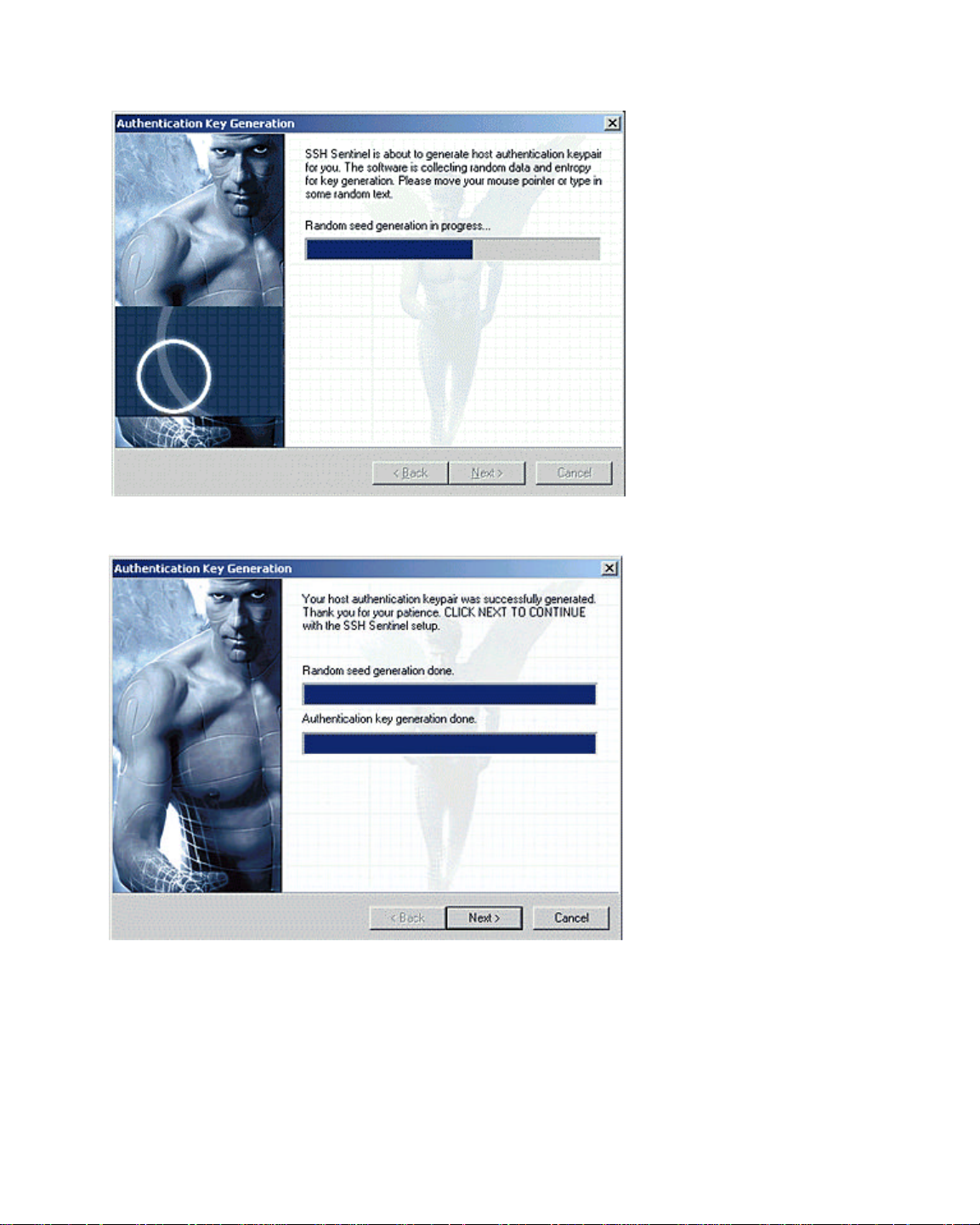
Figure 5. Generating the Authentication Key.
RFIPSC Quick Start Guide
Figure 6. Authentication Key Generation Done.
15
PN 82013151
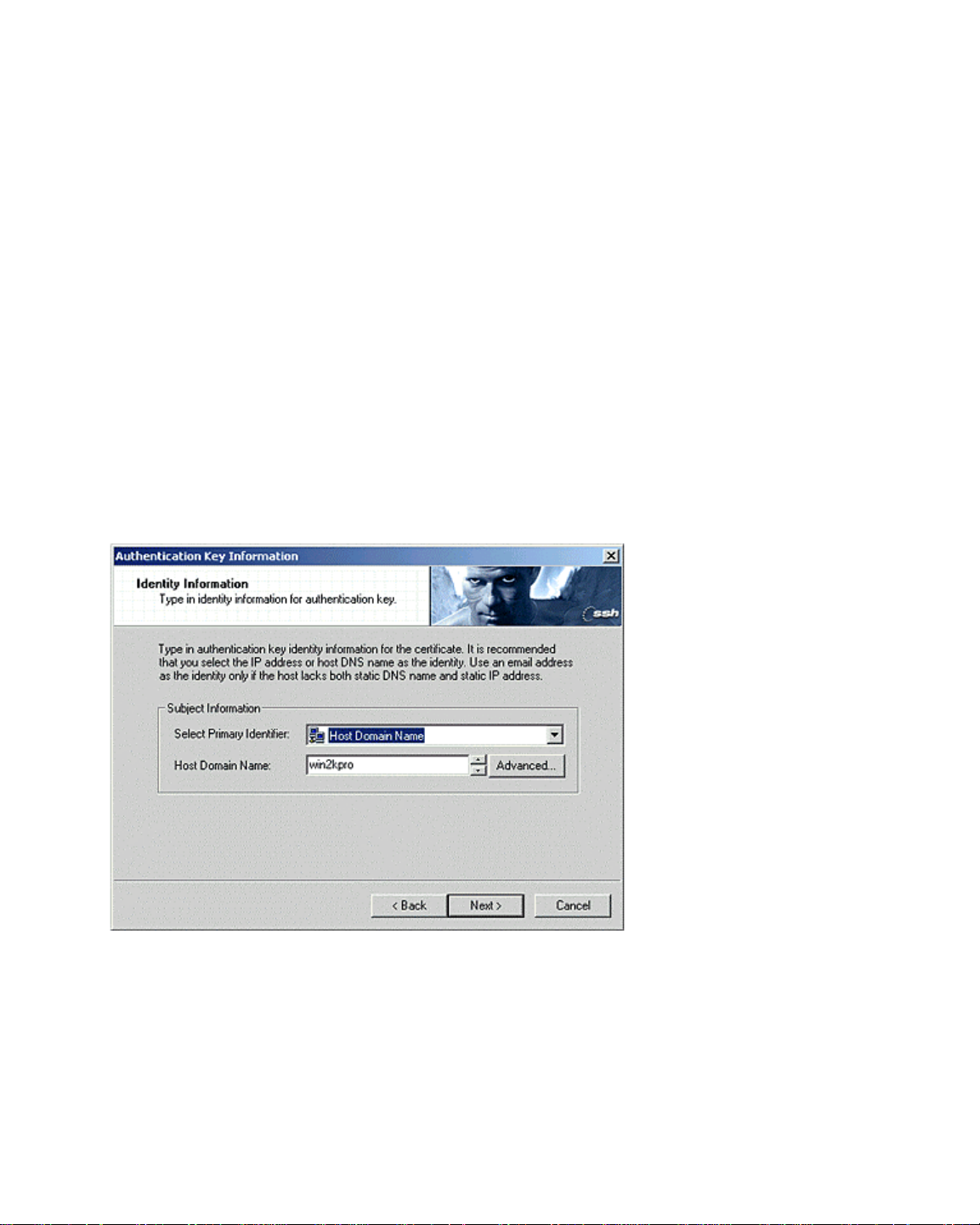
Identity Information
5. SSH Sentinel uses certificates and digital signatures as its primary authentication
method. SSH Sentinel processes certificates according to the IETF Public-Key
Infrastructure X.509v3 standards, allowing you to take advantage of the public-key
infrastructure (PKI). SSH Sentinel supports certificate revocation lists (CRLs) and
authority revocation lists (ARLs, that is, CRLs for CAs) and is very configurable.
However, you can run the software as stand-alone, separately from any public-key
infrastructure.
The setup requires host identity information that is to be associated with the
authentication key pair and its certificate. A commonly preferred identity is the host
DNS name, also referred to as the Fully Qualified Domain Name (FQDN). The DNS name
should be used as the identity whenever the host has a static DNS name and whenever
it is safe to assume that name service will be available. If the host does not have a
static DNS name, its static IP address may be used as the host identity.
If neither static DNS name nor IP address is available, you may use an email address as
the identity. However, using an email address as the identity makes it difficult for
remote hosts to bind IPSec rules for the host, since rules are normally bound to a host
name or an IP address.
Figure 7. Inquiring Certificate Identity.
16
RFIPSC Quick Start Guide
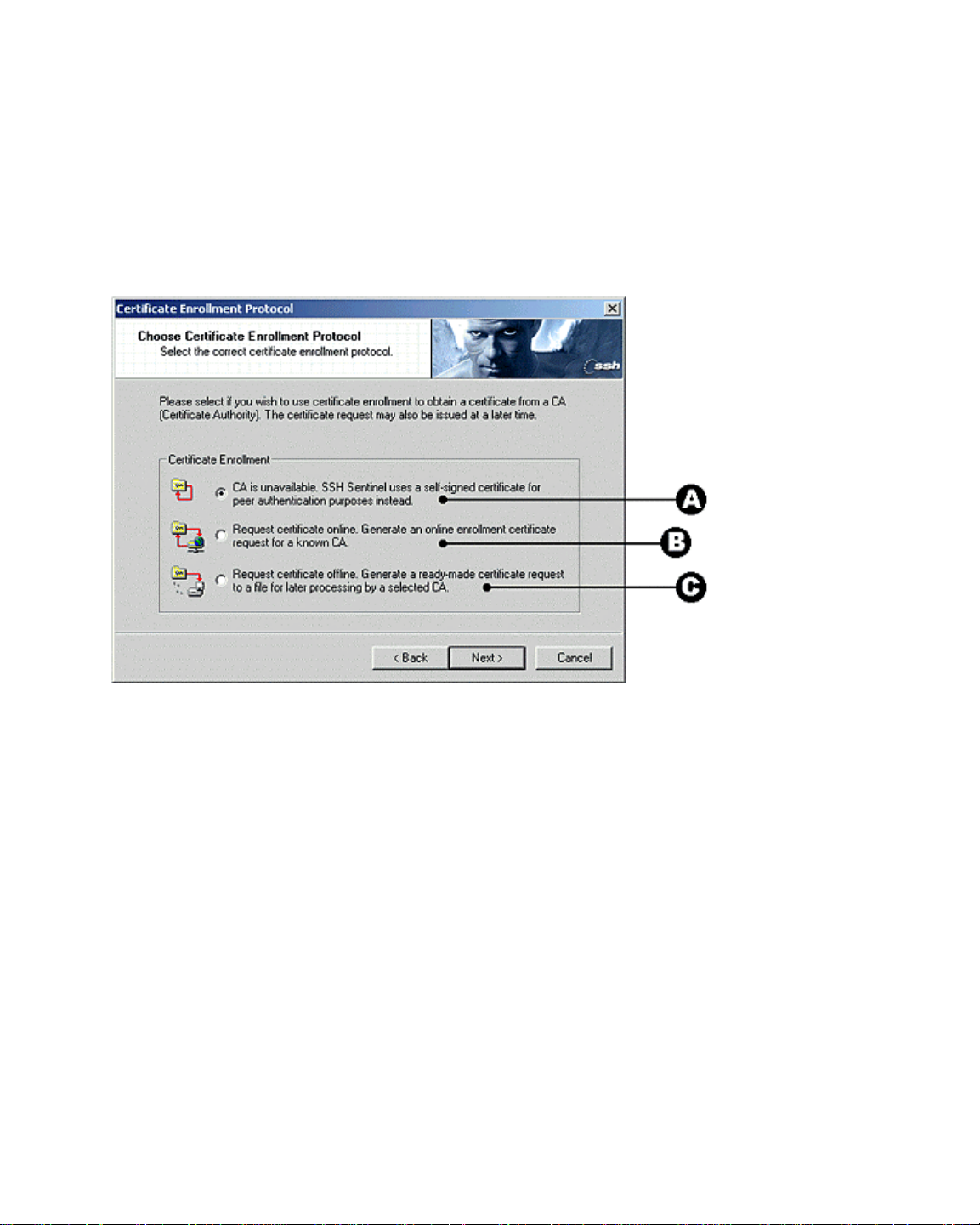
Choose the Enrollment Method
6. A certification request can be created as part of the installation process. You can
either enroll online, in other words create and send the request immediately, or save
the request in a file and deliver it later to the certification authority (CA). If there is no
certification authority available or you for some reason want to postpone the creation of
the request, create a self-signed certificate. It should be noted that once you’ve
installed the software, you can create as many certification requests as you wish with
the SSH Sentinel user interface but you cannot create a self-signed certificate with it.
Figure 8. Choosing a Certificate Enrollment Protocol.
7. Choose a Certificate EnrollmentProtocol:
A - To create a self-signed certificate, select the option CA is unavailable. SSH
Sentinel uses...
(option A in Figure 8 above). The keys created in the previous step are used when the
system creates the certificate.
B - To issue an online certification request, select the option Request certificate
online. Generate an online... (option B in Figure 8 above). The installation wizard
shows you a dialog where further information on the certification authority and the
enrollment protocol is asked for. Refer to the section entitled Online Enrollment for
reference.
C - Offline - To create a certification request and save it in a file for later processing ,
select the option Request certificate off-line. Generate a ... (option C in Figure 8
above). Refer to the section on Off-line Certification Request for the next step.
17
 Loading...
Loading...