Page 1
Copyright © 2021 Moxa Inc.
Released on March 26, 2021
About Moxa
Moxa is a leading provider of edge connectivity, industrial computing, and network
infrastructure solutions for enabling connectivity for the Industrial Internet of Things
(IIoT). With over 30 years of industry experience, Moxa has connected more than 57
m
customers in more than 70 countries. Moxa delivers lasting business value by
empowering industries with reliable networks and sincere service. Information about
Moxa’s solutions is available at www.moxa.com.
How to Contact Moxa
Tel : +886-2-8919-1230
The Security Hardening Guide for the NPort 5000 Series
Moxa Technical Support Team
support@moxa.com
Contents
1. Introduction .................................................................................... 2
2. General System Information ........................................................... 3
2.1. Basic Information About the Device ............................................................ 3
2.2. Deployment of the Device ......................................................................... 4
3. Configuration and Hardening Information ...................................... 4
3.1. TCP/UDP Ports and Recommended Services ................................................. 5
3.2. HTTPS and SSL Certificates ....................................................................... 9
3.3. Account Management ..............................................................................10
3.4. Accessible IP List .....................................................................................12
3.5. Logging and Auditing ...............................................................................13
4. Patching/Upgrades ....................................................................... 15
4.1. Patch Management Plan ...........................................................................15
4.2. Firmware Upgrades .................................................................................15
5. Security Information and Vulnerability Feedback ......................... 16
illion devices worldwide and has a distribution and service network that reaches
Page 2

Moxa Tech Note
The Security Hardening Guide for the NPort 5000
Series
Copyright © 2021 Moxa Inc.
Page 2 of 16
1. Introduction
This document provides guidelines on how to configure and secure the NPort 5000 Series. The
recommended steps in this document should be considered as best practices for security in
most applications. It is highly recommended that you review and test the configurations
thoroughly before implementing them in your production system in order to ensure that your
application is not negatively impacted.
Page 3
Moxa Tech Note
The Security Hardening Guide for the NPort 5000
Series
Copyright © 2021 Moxa Inc.
Page 3 of 16
2. General System InformationBasic Information About the
Device
Model Function Operating System Firmware Version
NPort 5000A Series General purpose Moxa Operating
System
NPort 5110 General purpose Moxa Operating
System
NPort 5130/5150 General purpose Moxa Operating
System
NPort 5200 Series General purpose Moxa Operating
System
NPort 5400 Series General purpose Moxa Operating
System
NPort 5600-DT Series General purpose Moxa Operating
System
NPort 5600-DTL Series Entry level Moxa Operating
System
NPort 5600 Series Rackmount Moxa Operating
System
NPort 5000AI-M12
Series
NPort IA5000 Series Industrial automation Moxa Operating
NPort IA5000A Series Industrial automation Moxa Operating
Railway Moxa Operating
System
System
System
Version 1.6
Version 2.10
Version 3.9
Version 2.12
Version 3.14
Version 2.8
Version 1.6
Version 3.10
Version 1.5
Version 1.7
Version 1.7
The NPort 5000 Series is a device server specifically designed to allow industrial
devices to be directly accessible from the network. Thus, legacy devices can be
transformed into Ethernet devices, which then can be monitored and controlled from
any network location or even the Internet. Different configurations and features are
available for specific applications, such as protocol conversion, Real COM drivers, and
TCP operation modes, to name a few.
Moxa Operating System (MOS) is an embedded proprietary operating system, which is
only executed in Moxa edge devices. Because the MOS operating system is not freely
available, the chances of malware attacks are significantly reduced.
Page 4
Moxa Tech Note
The Security Hardening Guide for the NPort 5000
Series
Copyright © 2021 Moxa Inc.
Page 4 of 16
2.2. Deployment of the Device
You should deploy the NPort 5000 Series
behind a secure firewall network that has
sufficient security features in place to
ensure that networks are safe from
internal and external threats.
Make sure that the physical protection of
the MGate devices and/or the system
meets the security needs of your
application. Depending on the
environment and the threat situation, the
form of protection can vary significantly.
3. Configuration and Hardening Information
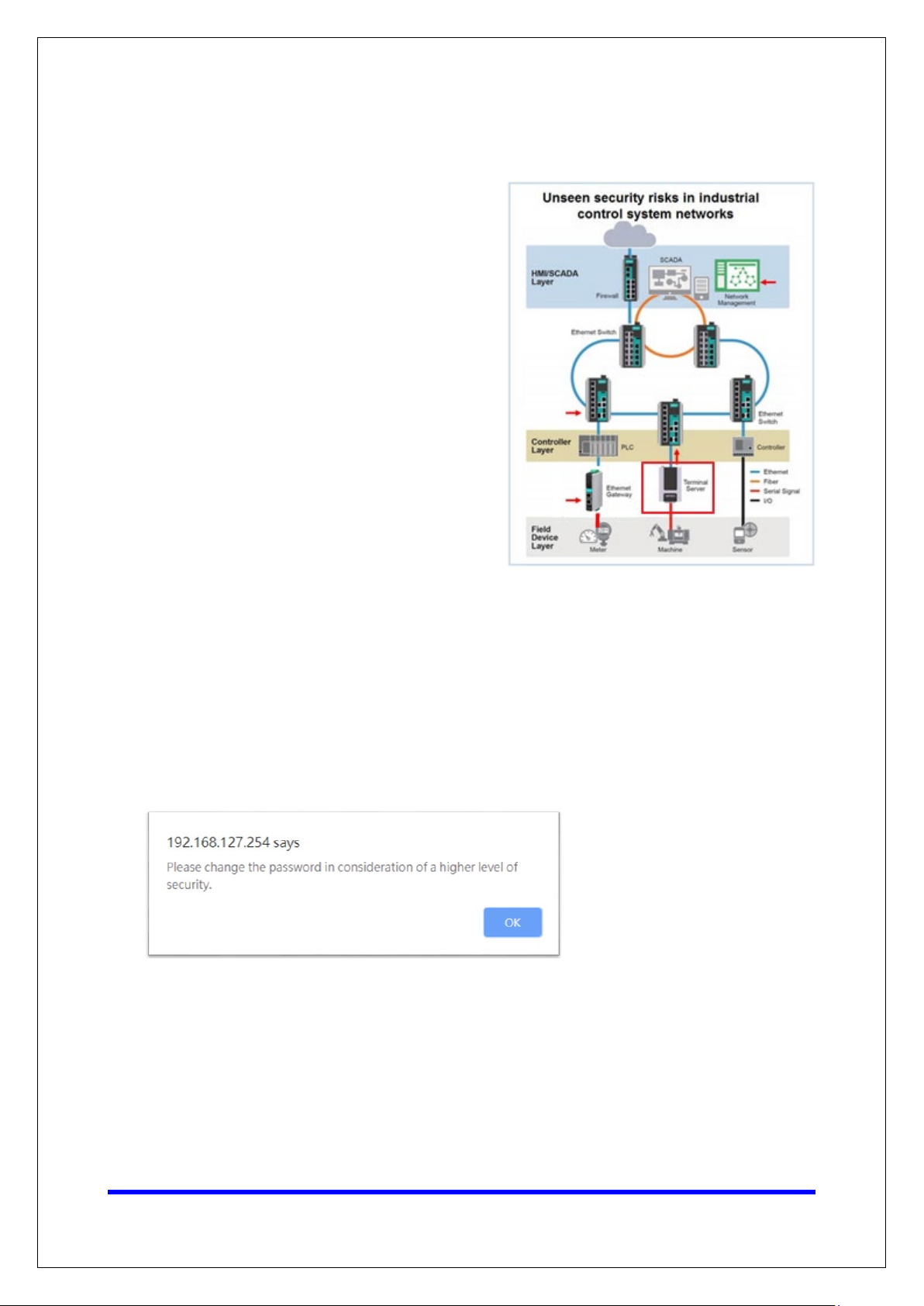
For security reasons, account and password protection is enabled by default, so you must
provide the correct account and password to unlock the device before entering the web
console of the gateway.
The default account and password are admin and moxa (both in lowercase letters),
respectively. Once you are successfully logged in, a pop-up notification will appear to remind
you to change the password in order to ensure a higher level of security.
Page 5
Moxa Tech Note
The Security Hardening Guide for the NPort 5000
Series
Copyright © 2021 Moxa Inc.
Page 5 of 16
3.1. TCP/UDP Ports and Recommended Services
Refer to the table below for all the ports, protocols, and services that are used to
communicate between the NPort 5000 Series and other devices.
Service Name Option
Moxa Command
(DSCI)
DNS_wins Enable Enable UDP 53, 137, 949
SNMP agent Enable/Disable Enable UDP 161 SNMP handling routine
HTTP server Enable/Disable Enable TCP 80 Web console
HTTPS server Enable/Disable Enable TCP 443 Secured web console
Telnet server Enable/Disable Disable TCP 23 Telnet console
DHCP client Enable/Disable Disable UDP 68
SNTP Enable/Disable Disable UDP Random Port
Remote System
Log
Enable/Disable Enable
Enable/Disable Disable UDP Random Port
Default
Setting
Type Port Number Remark & Description
TCP 14900, 4900
UDP 4800
For Moxa utility
communication
Processing DNS and WINS
(Client) data
The DHCP client needs to
acquire the system IP
address from the server
Synchronize time settings
with a time server
This function is not
available for the NPort
5100/5100A/5200/
5200A Series.
Send the event log to a
remote log server
Operation Mode Option
Real COM Mode Enable/Disable Enable TCP
RFC2217 Mode Enable/Disable Disable TCP
TCP Server Mode Enable/Disable Disable TCP
Default
Setting
Type Port Number
950+ (Serial port No. -
1)
966+ (Serial port No. -
1)
User-defined (default:
4000+Serial port No.)
User-defined (default:
4000+Serial port No.)
User-defined (default:
966+Serial port No.)
Remark &
Description
Only available in
certain models
Page 6

Moxa Tech Note
The Security Hardening Guide for the NPort 5000
Series
Copyright © 2021 Moxa Inc.
Page 6 of 16
Operation Mode Option
UDP Mode Enable/Disable Disable UDP
Pair Connection
Master Mode
Pair Connection
Slave Mode
Ethernet Modem
Mode
Reverse Telnet
Mode
Disabled Mode Enable/Disable Disable N/A N/A
Enable/Disable Disable TCP
Enable/Disable Disable TCP
Enable/Disable Disable TCP
Enable/Disable Disable TCP
Default
Setting
Type Port Number
User-defined (default:
4000+Serial port No.)
User-defined (default:
4000+Serial port No.)
User-defined (default:
4000+Serial port No.)
User-defined (default:
4000+Serial port No.)
User-defined (default:
4000+Serial port No.)
Remark &
Description
Only available in
certain models
Only available in
certain models
For security reasons, you should consider disabling unused services. After initial setup,
use services with stronger security for data communication. Refer to the table below for
the suggested settings.
Service Name
Moxa Command
(DSCI)
DNS_wins Enable UDP 53, 137, 949
SNMP Disable UDP 161
HTTP Server Disable TCP 80
HTTPS Server Enable TCP 443
Telnet Server Disable TCP 23
DHCP Client Disable UDP 67, 68
SNTP Client Disable UDP Random Port
Remote System
Log
Suggested
Setting
Disable
Enable UDP Random Port
Type Port Number Security Remark
TCP 14900, 4900
UDP 4800
Disable this service as it is not commonly
used
A necessary service to get IP; cannot be
disabled
Suggest to manage NPort via HTTPS
console
Disable HTTP to prevent plain text
transmission
Encrypted data channel with trusted
certificate for NPort configuration
Disable this service as it is not commonly
used
Assign an IP address manually for the
device
Suggest to use the SNTP server for
secure time synchronization
Suggest using a system log server to
store all the logs from all the devices in
the network
Page 7
Moxa Tech Note
The Security Hardening Guide for the NPort 5000
Series
Copyright © 2021 Moxa Inc.
Page 7 of 16
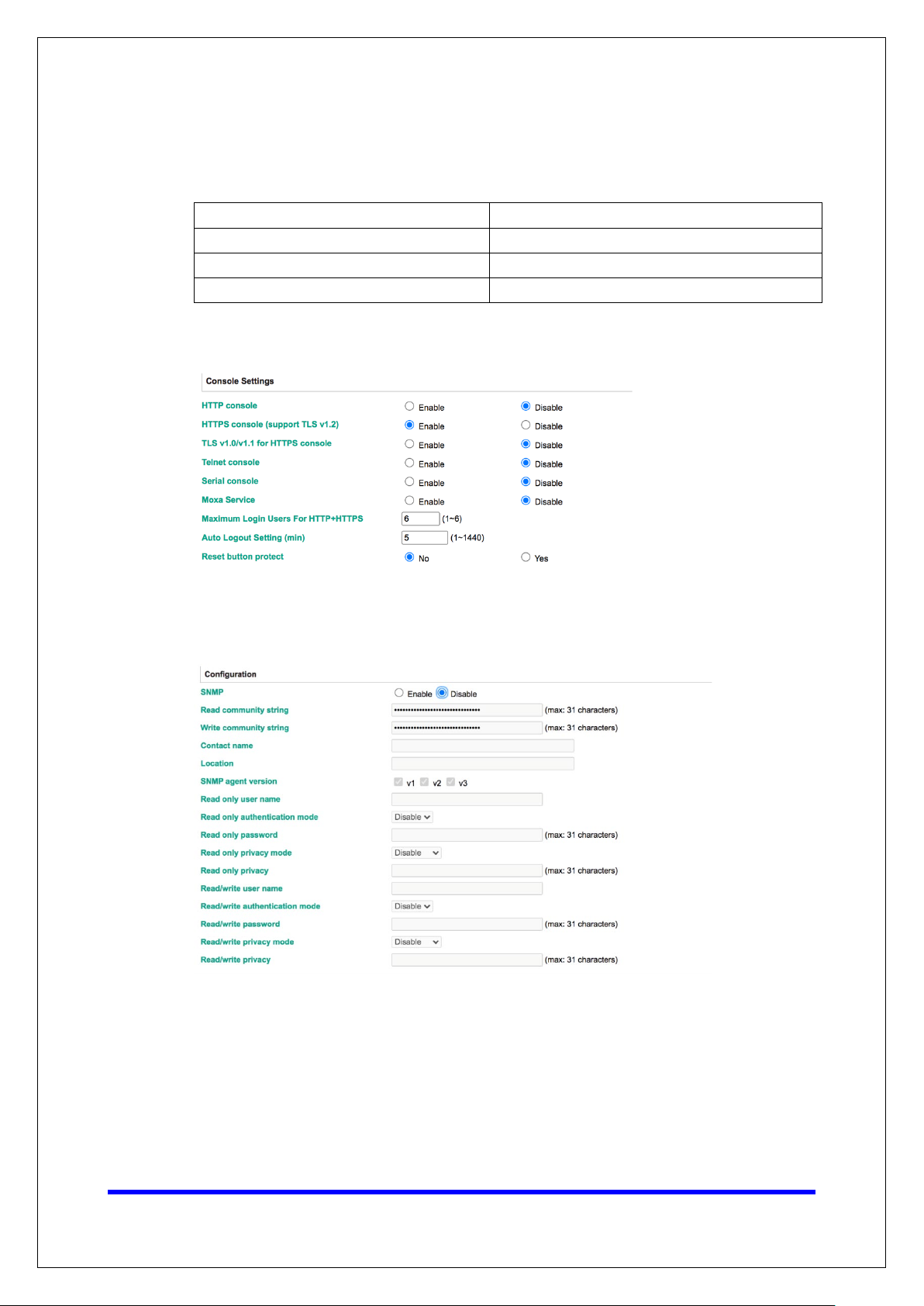
For console services, we recommend the following:
HTTP Disable
HTTPS Enable
Telnet Disable
Moxa Command Disable
To enable or disable these services, log in to the HTTP/HTTPS console and select Basic
Settings
For the SNMP agent service, log in to the HTTP/HTTPS console and select
Administration
SNMP agent service.
Console Settings.
SNMP Agent, select Disable for SNMP, and select Disable for the
Page 8

Moxa Tech Note
The Security Hardening Guide for the NPort 5000
Series
Copyright © 2021 Moxa Inc.
Page 8 of 16
Note:
For
the
To disable the SNTP service server, log in to the HTTP/HTTPS/SSH/Telnet console and
select Basic Settings, and keep the Time server setting empty. This will disable the
SNTP service. Then, keep the Time server empty as Disable for the SNTP Server.
For the remote system log server, it depends on your network architecture. We
recommend your network administrator to have a Log Server to receive the log
messages from the device. In this case, log in to the HTTP/HTTPS/SSH/Telnet console,
select Remote Log Server, and input the IP address of the Log Server in the SYSLOG
server field. If your network doesn't have one, keep it empty (disable Remote
System Log Server).
For the operation mode services, it depends on how you bring your serial device to the
Ethernet network. For example, if your host PC uses a legacy software to open a COM
port to communicate with the serial device, then the NPort will enable the Real COM
mode for this application. If you don't want the NPort to provide such a service, log in
to the HTTP/HTTPS/SSH/Telnet console, select Serial Port Settings Port #
Operation Modes, and then select Disable.
each instruction above, click the Submit button to save your changes, then restart
NPort device so the new settings will take effect.
Page 9

Moxa Tech Note
The Security Hardening Guide for the NPort 5000
Series
Copyright © 2021 Moxa Inc.
Page 9 of 16
3.2. HTTPS and SSL Certificates
HTTPS is an encrypted communication
channel. As TLS v1.1 or lower has severe
vulnerabilities that can easily be hacked,
the NPort 5000 Series uses TLS v1.2 for
HTTPS to ensure data transmissions are
secured. Make sure your browser has TLS
v1.2 enabled.
Page 10

Moxa Tech Note
The Security Hardening Guide for the NPort 5000
Series
Copyright © 2021 Moxa Inc.
Page 10 of 16
3.3. Account Management
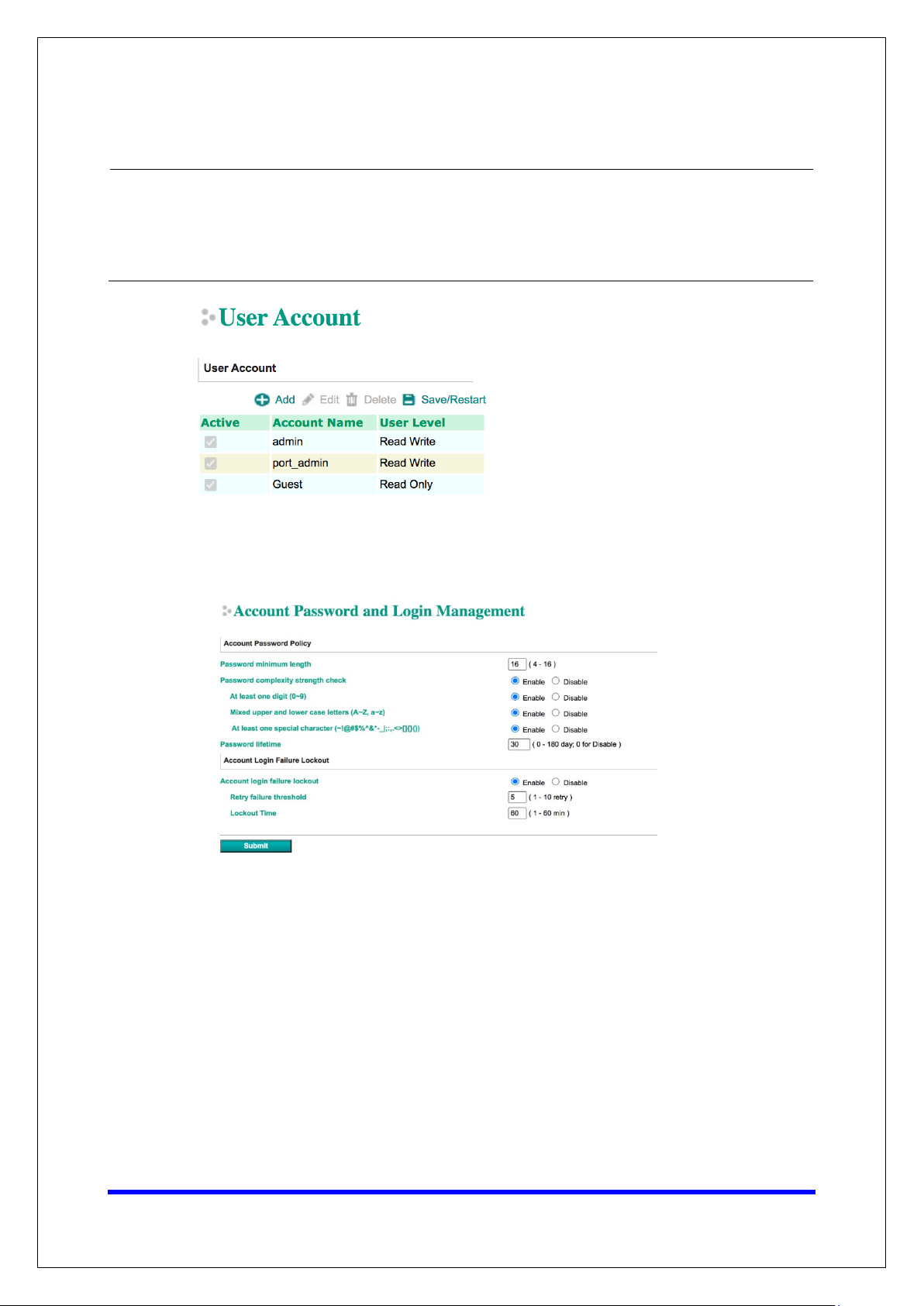
• The NPort 5000 Series provides two different user levels, Read Write (admin) and
Read Only (user). With a Read Write account, you can access and modify all settings
through the web console. With a Read Only account, you can only view settings.
• The default Read Write account is admin, with the default password moxa. To
manage accounts, log in to the web console and select Administration
Management
• To add a new account, click Add in the top toolbar, then enter the Account Name,
Password, Confirm Password, and select a User Level.
User Account.
Account
• To modify an existing account, click on the account name and select Edit in the top
toolbar.
• To delete an account, click on the account name and select Delete in the top
toolbar.
• After making any changes, click Save/Restart in the top toolbar.
Page 11
Moxa Tech Note
The Security Hardening Guide for the NPort 5000
Series
Copyright © 2021 Moxa Inc.
Page 11 of 16
Note:
We suggest you
level” account instead of
using the default “admin” account, as it is commonly used by embedded systems. Once
the new
“admin” account should be monitored for security
administrator level account has been created, it is suggested that the original
manage your device with another “administrator
reasons to prevent brute-force attacks.
• To improve security, the login password policy and account login failure lockout can
be configured. To configure them, log in to the HTTP/HTTPS console and select
Administration
Account Management Password & Login Policy.
• You should adjust the password policy to require more complex passwords. For
example, set the Minimum length to 16, enable all password complexity strength
checks, and enable the Password lifetime options. Also, to avoid brute-force
attack, it’s suggested that you enable the Account login failure lockout feature.
• For some system security requirements, a warning message may need to be
displayed to all users attempting to log in to the device. To add a login message, log
in to the HTTP/HTTPS console and select Administration
Management
Notification Message, and enter a Login Message to use.
Account
Page 12

Moxa Tech Note
The Security Hardening Guide for the NPort 5000
Series
Copyright © 2021 Moxa Inc.
Page 12 of 16
3.4. Accessible IP List
• The NPort 5000 Series has a feature that can limit access to specific remote host IP
addresses to prevent unauthorized access. If a host’s IP address is in the accessible
IP table, then the host will be allowed to access the NPort 5000 series. To configure
it, log in to the HTTP/HTTPS console and select Accessible IP List.
• You may add a specific address or range of addresses by using a combination of an
IP address and a netmask as follows:
− To allow access to a specific IP address: Enter the IP address in the
corresponding field, then 255.255.255.255 for the netmask.
Page 13

Moxa Tech Note
The Security Hardening Guide for the NPort 5000
Series
Copyright © 2021 Moxa Inc.
Page 13 of 16
Ensure that the IP address of the PC you are using to access the web console is in the
Accessible IP List
− To allow access to a specific IP address: Enter the IP address in the
corresponding field, then 255.255.255.255 for the netmask.
− To allow access to hosts on a specific subnet: For both the IP address and
netmask, use 0 for the last digit (e.g., “192.168.1.0” and “255.255.255.0”).
− To allow access to all IP addresses: Make sure that the Enable checkbox for
the Accessible IP List is not checked.
Additional configuration examples are shown in the following table:
Desired IP Range IP Address Field Netmask Field
Any host Disable Enable
192.168.1.120 192.168.1.120 255.255.255.255
192.168.1.1 to 192.168.1.254 192.168.1.0 255.255.255.0
192.168.1.1 to 192.168.255.254 192.168.0.0 255.255.0.0
192.168.1.1 to 192.168.1.126 192.168.1.0 255.255.255.128
192.168.1.129 to 192.168.1.254 192.168.1.128 255.255.255.128
Warning
.
3.5. Logging and Auditing
• These are the events that will be recorded by the NPort 5000 Series:
Event Group Summary
System System cold start, system warm start
Network
Configuration
OpMode Connect, Disconnect
• To configure this setting, log in to the HTTP/HTTPS console and select System Log
Settings. Then, enable the Local Log for recording on the NPort 5000 device
and/or Remote Log for keeping records on a server. You should enable system log
settings to record all important system events in order to monitor device status and
check for security issues.
DHCP/BOOTP gets IP/renew, NTP connect failed, IP conflict, Network link
down
Login failed, IP changed, Password changed, Firmware upgraded, Certificate
imported, Configuration imported or exported, Configuration changed, Clear
event logged
Page 14

Moxa Tech Note
The Security Hardening Guide for the NPort 5000
Series
Copyright © 2021 Moxa Inc.
Page 14 of 16
• To view events in the system log, log in to the HTTP/HTTPS console and select
Monitor
System Log.
Page 15
Moxa Tech Note
The Security Hardening Guide for the NPort 5000
Series
Copyright © 2021 Moxa Inc.
Page 15 of 16
4. Patching/Upgrades
4.1. Patch Management Plan
With regards to patch management, Moxa releases version enhancements annually
with detailed release notes.
4.2. Firmware Upgrades
The process for upgrading firmware is as follows:
• Download the latest firmware for your MGate device from the Moxa website:
NPort Series URL
5100A
5100
5200A
5200
5400
5600
5600-DT
5600-DTL
IA5000A
IA5000
5000AI-M12
https://www.moxa.com/en/products/industrial-edge-connectivity/serial-
device-servers/general-device-servers/nport-5100a-series#resources
https://www.moxa.com/en/products/industrial-edge-connectivity/serial-
device-servers/general-device-servers/nport-5100-series#resources
https://www.moxa.com/en/products/industrial-edge-connectivity/serial-
device-servers/general-device-servers/nport-5200a-series#resources
https://www.moxa.com/en/products/industrial-edge-connectivity/serial-
device-servers/general-device-servers/nport-5200-series#resources
https://www.moxa.com/en/products/industrial-edge-connectivity/serial-
device-servers/general-device-servers/nport-5400-series#resources
https://www.moxa.com/en/products/industrial-edge-connectivity/serial-
device-servers/general-device-servers/nport-5600-series#resources
https://www.moxa.com/en/products/industrial-edge-connectivity/serial-
device-servers/general-device-servers/nport-5600-dt-series#resources
https://www.moxa.com/en/products/industrial-edge-connectivity/serial-
device-servers/general-device-servers/nport-5600-dtl-series#resources
https://www.moxa.com/en/products/industrial-edge-connectivity/serial-
device-servers/industrial-device-servers/nport-ia5000a-series#resources
https://www.moxa.com/en/products/industrial-edge-connectivity/serial-
device-servers/industrial-device-servers/nport-ia5000-series#resources
https://www.moxa.com/en/products/industrial-edge-connectivity/serial-
device-servers/general-device-servers/nport-5000ai-m12-series#resources
Page 16

Moxa Tech Note
The Security Hardening Guide for the NPort 5000
Series
Copyright © 2021 Moxa Inc.
Page 16 of 16
• Log in to the HTTPS console and select System Management Maintenance
Firmware Upgrade. Click the Choose File button to select the proper firmware
and click Submit to upgrade the firmware.
• If you want to upgrade the firmware for multiple units, download the Device Search
Utility (DSU) or MXconfig for a GUI interface, or the Moxa CLI Configuration Tool for
a CLI interface.
5. Security Information and Vulnerability Feedback
As the adoption of the Industrial IoT (IIoT) continues to grow rapidly, security has become
one of the top priorities. The Moxa Cyber Security Response Team (CSRT) is taking a proactive
approach to protect our products from security vulnerabilities and help our customers better
manage security risks.
You can find the latest Moxa security information here:
https://www.moxa.com/en/support/product-support/security-advisory
 Loading...
Loading...