Moxa MGate 5101, MGate 5102, MGate 5103, MGate 5105, MGate 5109 Security Hardening Guide
...Page 1
Copyright © 2021 Moxa Inc.
Released on March 26, 2021
About Moxa
Moxa is a leading provider of edge connectivity, industrial computing, and network
infrastructure solutions for enabling connectivity for the Industrial Internet of Things
(IIoT). With over 30 years of industry experience, Moxa has connected more than 57
m
customers in more than 70 countries. Moxa delivers lasting business value by
empowering industries with reliable networks and sincere service. Information about
Moxa’s solutions is available at www.moxa.com.
How to Contact Moxa
Tel : +886-2-8919-1230
The Security Hardening Guide for the MGate 5000 Series
Moxa Technical Support Team
support@moxa.com
Contents
1. Introduction .................................................................................... 2
2. General System Information ........................................................... 3
2.1. Basic Information About the Device ............................................................ 3
2.2. Deployment of the Device ......................................................................... 4
3. Configuration and Hardening Information ...................................... 4
3.1. TCP/UDP Ports and Recommended Services ................................................. 5
3.2. HTTPS and SSL Certificates ....................................................................... 8
3.3. Account Management ..............................................................................11
3.4. Accessible IP List .....................................................................................14
3.5. Logging and Auditing ...............................................................................15
3.6. DoS Defense ..........................................................................................17
4. Patching/Upgrades ....................................................................... 18
4.1. Patch Management Plan ...........................................................................18
4.2. Firmware Upgrades .................................................................................18
5. Security Information and Vulnerability Feedback ......................... 19
illion devices worldwide and has a distribution and service network that reaches
Page 2

Moxa Tech Note
The Security Hardening Guide for the MGate
5000 Series
Copyright © 2021 Moxa Inc.
Page 2 of 19
1. Introduction
This document provides guidelines on how to configure and secure the MGate 5000 Series.
The recommended steps in this document should be considered as best practices for security
in most applications. It is highly recommended that you review and test the configurations
thoroughly before implementing them in your production system in order to ensure that your
application is not negatively impacted.
Page 3
Moxa Tech Note
The Security Hardening Guide for the MGate
5000 Series
Copyright © 2021 Moxa Inc.
Page 3 of 19
2. General System InformationBasic Information About the
Device
Model Function
MGate 5101 Series PROFIBUS-to-Modbus TCP Gateway Linux Version v2.2
MGate 5102 Series PROFIBUS-to-PROFINET Gateway Linux Version v2.3
MGate 5103 Series
MGate 5105 Series
MGate 5109 Series
MGate 5111 Series
MGate 5114 Series
MGate 5118 Series
MGate W5108/W5208
Series
Modbus RTU/ASCII/EtherNet/IP-to-PROFINET
Gateway
Modbus RTU/ASCII/TCP-to-EtherNet/IP
Gateway
Modbus RTU/ASCII/TCP-to-DNP3 serial/TCP
Gateway
Modbus/PROFINET/EtherNet/IP-to-PROFIBUS
Gateway
Modbus RTU/ASCII/TCP/IEC101-to-IEC104
Gateway
CAN-J1939-to-
Modbus/PROFINET/EtherNet/IP Gateway
IEEE 802.11 a/b/g/n wireless Modbus/DNP3
Gateway
Operating
System
Linux Version v2.2
Linux Version v4.3
Linux Version v2.3
Linux Version v1.3
Linux Version v1.3
Linux Version v2.2
Linux Version v2.4
Firmware
Version
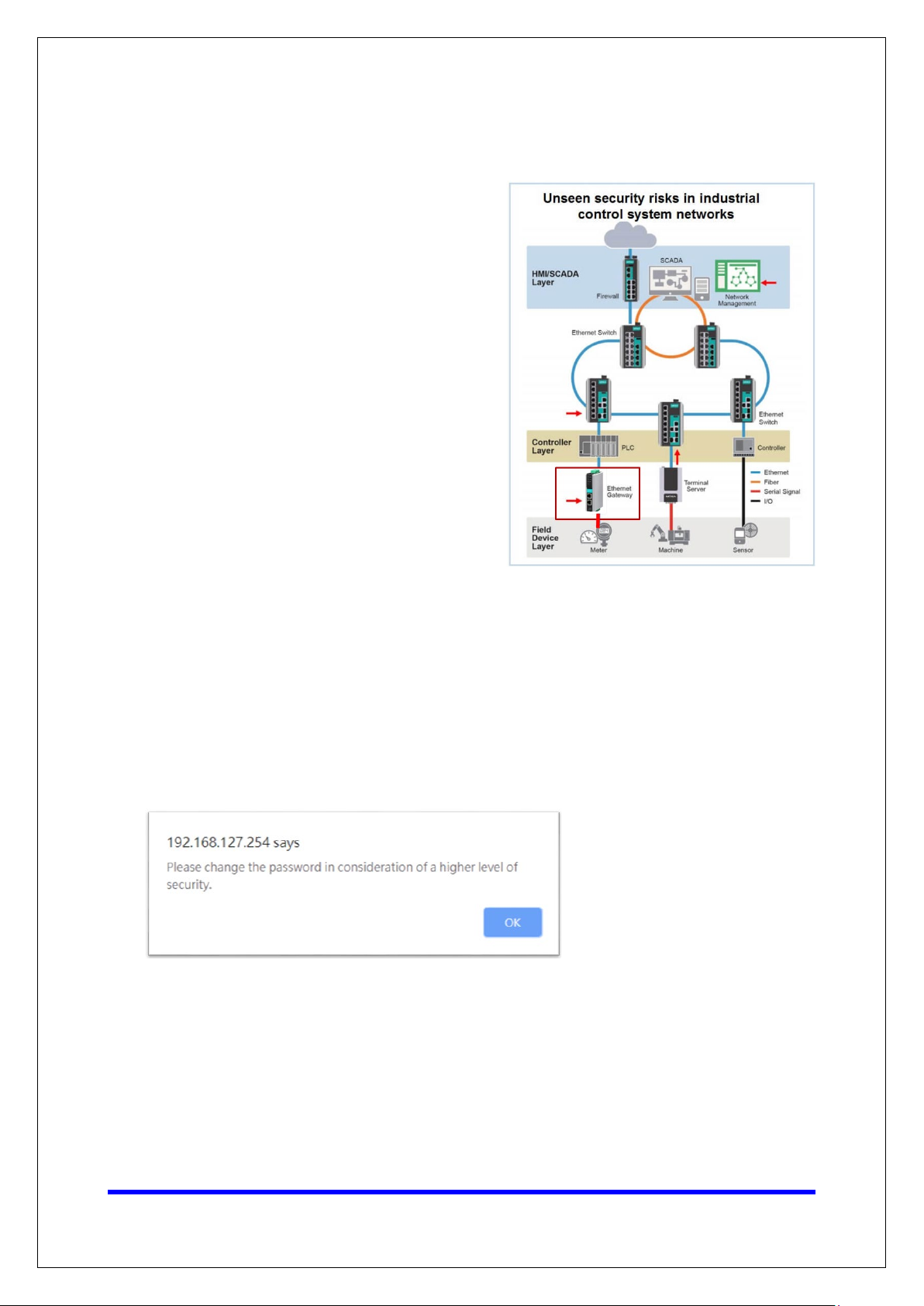
The MGate 5000 Series is a protocol gateway specifically designed to allow industrial
devices to be directly accessed from a network. Thus, legacy fieldbus devices can be
transformed into different protocols, which can be monitored and controlled from any
network location or even the Internet.
To harden the security of this proprietary operating system, the open source HTTPS
library, openSSL v1.1.1b, is also included and periodically reviewed for cybersecurity
enhancement.
Page 4
Moxa Tech Note
The Security Hardening Guide for the MGate
5000 Series
Copyright © 2021 Moxa Inc.
Page 4 of 19
2.2. Deployment of the Device
You should deploy the MGate 5000 Series
behind a secure firewall network that has
sufficient security features in place to
ensure that networks are safe from
internal and external threats.
Make sure that the physical protection of
the MGate devices and/or the system
meets the security needs of your
application. Depending on the
environment and the threat situation, the
form of protection can vary significantly.
3. Configuration and Hardening Information
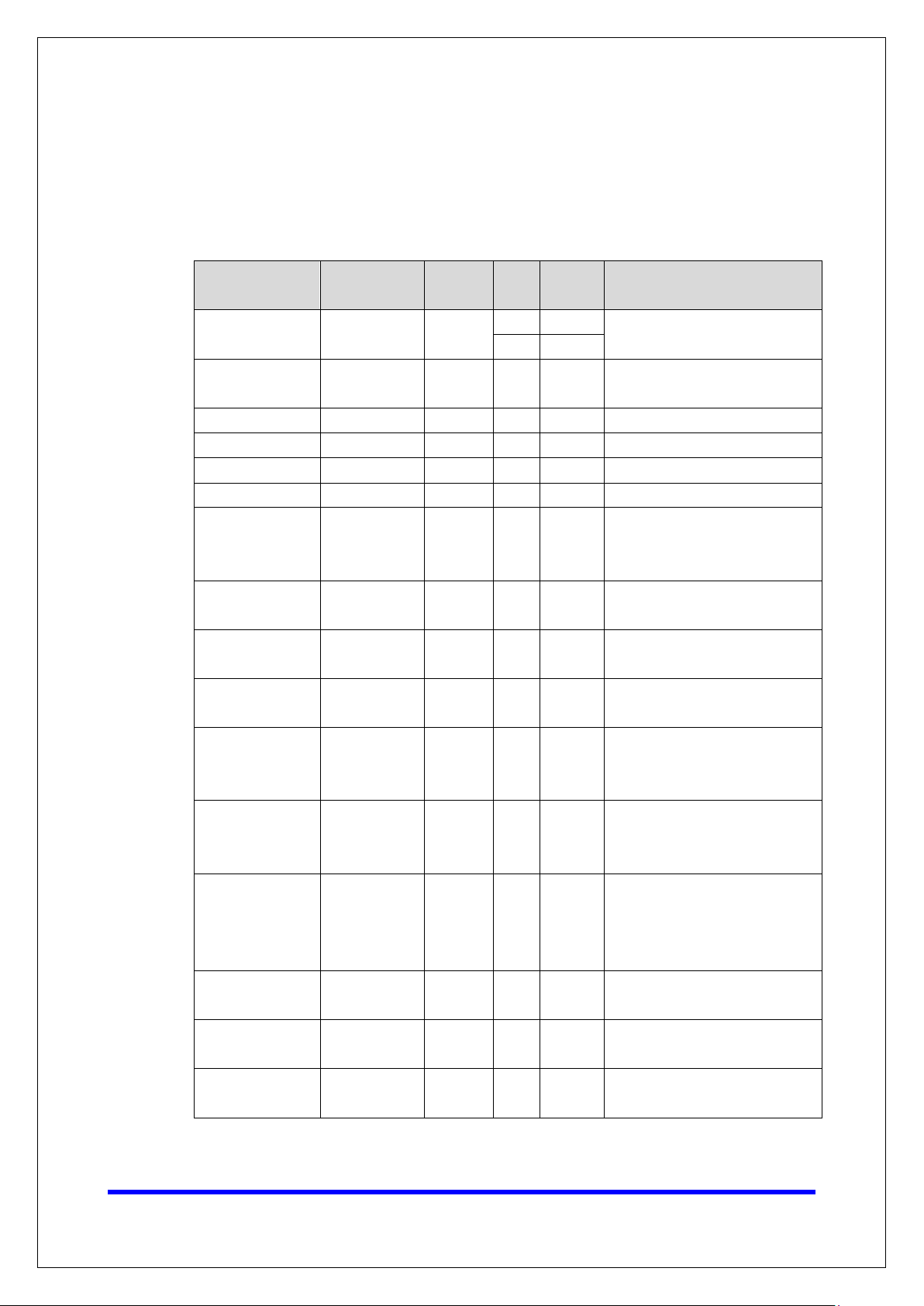
For security reasons, account and password protection is enabled by default, so you must
provide the correct account and password to unlock the device before entering the web
console of the gateway.
The default account and password are admin and moxa (both in lowercase letters),
respectively. Once you are successfully logged in, a pop-up notification will remind you to
change the password to ensure a higher level of security.
Page 5
Moxa Tech Note
The Security Hardening Guide for the MGate
5000 Series
Copyright © 2021 Moxa Inc.
Page 5 of 19
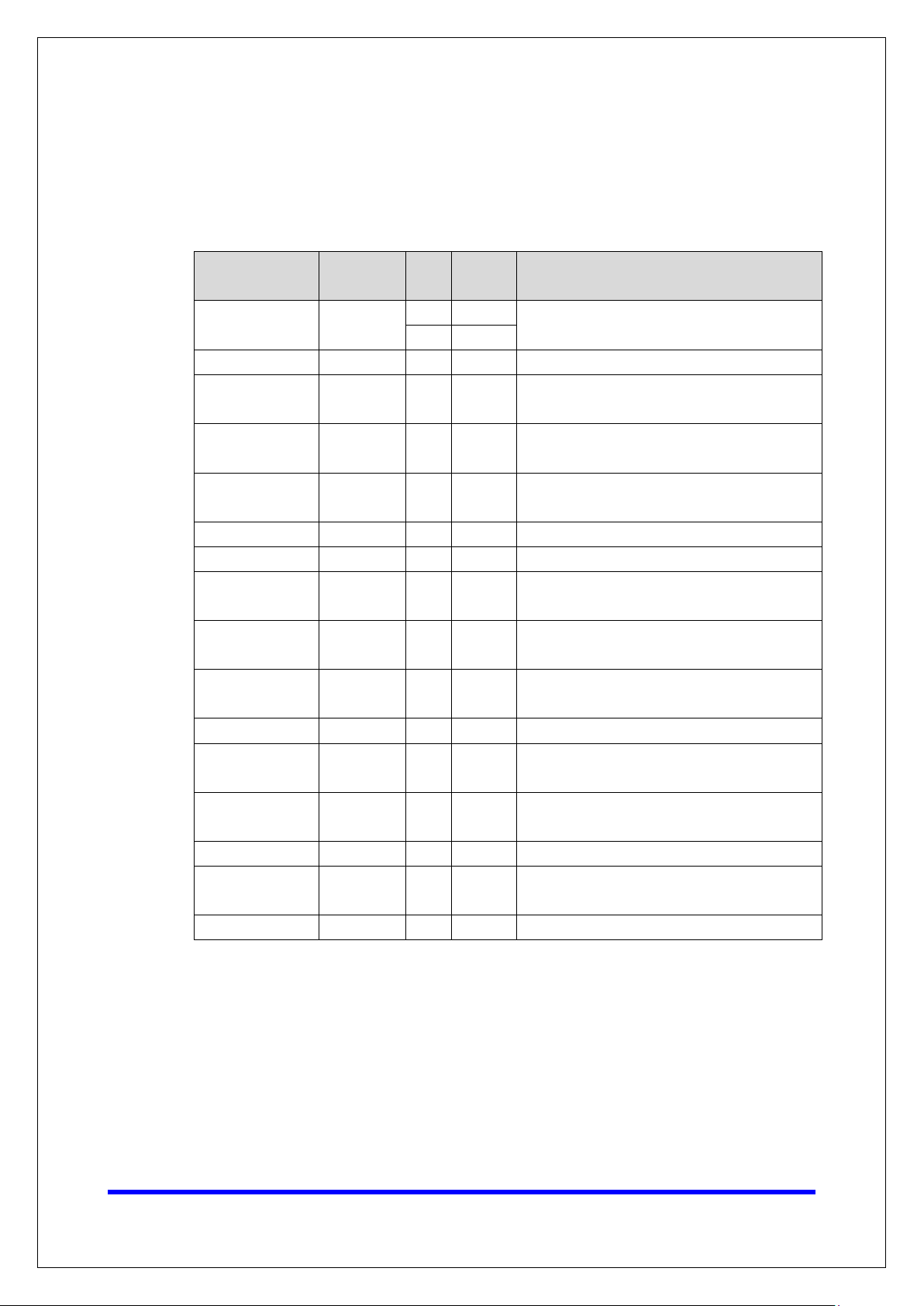
3.1. TCP/UDP Ports and Recommended Services
Please refer to the table below for all the ports, protocols, and services that are used to
communicate between the MGate 5000 Series and other devices.
Service Name Option
DSCI
(Moxa Command)
DNS client Enable/Disable Disable UDP 53
SNMP agent Enable/Disable Enable UDP 161 SNMP handling routine
HTTP server Enable/Disable Enable TCP 80 Web console
HTTPS server Enable/Disable Enable TCP 443 Secured web console
Telnet server Enable/Disable Disable TCP 23 Telnet console
DHCP client Enable/Disable Disable UDP 68
Syslog client Enable/Disable Disable UDP 514
Email client Enable/Disable Disable TCP 25
SNMP trap client Enable/Disable Disable UDP 162
NTP client Enable/Disable Disable UDP 123
Modbus TCP
client/server
EtherNet/IP Enable/Disable Enable
PROFINET Enable/Disable Enable UDP 34963
DNP3 Enable/Disable Enable
IEC-104 Enable/Disable Enable TCP 2404
Enable/Disable Enable
Enable/Disable Enable TCP
Default
Setting
Type
TCP 4900
UDP 4800
TCP,
UDP
TCP,
UDP
Port
Number
502,
7502
2222,
44818
20000
Description
For Moxa utility communication
Processing DNS and WINS
(Client) data
The DHCP client needs to acquire
the system IP address from the
server
Sending the system logs to the
remote syslog server
Sending system/config event
notifications
Sending system/config event
notifications
Network time protocol to
synchronize system time from
the server
502 for Modbus communication;
7502 for priority Modbus
communication
2222 for EtherNet/IP implicit
messaging
44818 for EtherNet/IP explicit
messaging
34963 for PROFINET protocol
communication
20000 for DNP3 protocol
communication
2404 for IEC-104 protocol
communication
Page 6
Moxa Tech Note
The Security Hardening Guide for the MGate
5000 Series
Copyright © 2021 Moxa Inc.
Page 6 of 19
For security reasons, you should consider disabling unused services. After initial setup,
use services with stronger security for data communication. Refer to the table below for
the suggested settings.
Service Name
DSCI
(Moxa Command)
DNS client Disable UDP 53 Disable this service as it is not commonly used
SNMP agent Disable UDP 161
HTTP server Disable TCP 80
HTTPS server Enable TCP 443
Telnet server Disable TCP 23 Disable this service as it is not commonly used
DHCP client Disable UDP 68 Assign an IP address manually for the device
Syslog client Enable UDP 514
Email client Enable TCP 25
SNMP trap client Enable UDP 162 A service for sending important system events
NTP client Disable UDP 123 Disable this service as it is not commonly used
Modbus TCP
client/server
EtherNet/IP Enable TCP,
PROFINET Enable UDP 34963 34963 for PROFINET protocol communication
DNP3 Enable TCP,
IEC-104 Enable TCP 2404 2404 for IEC-104 protocol communication
Suggested
Setting
Disable
Enable TCP 502,
Port
Type
Number
TCP 4900
UDP 4800
7502
2222,
UDP
44818
20000 20000 for DNP3 protocol communication
UDP
Security Remark
Disable this service as it is not commonly used
Managing the MGate via HTTPS console will be
more secure
Disable HTTP to prevent plain text
transmission
Encrypted data channel with trusted certificate
for MGate configuration
A service for sending important system events
for a diagnosis of the MGate’s status
A service for sending important system events
for a diagnosis of the MGate’s status
for a diagnosis of the MGate’s status
Make sure you add your Modbus devices’ IP
addresses to the “Accessible IP list”
2222 for EtherNet/IP implicit messaging;
44818 for EtherNet/IP explicit messaging
Page 7

Moxa Tech Note
The Security Hardening Guide for the MGate
5000 Series
Copyright © 2021 Moxa Inc.
Page 7 of 19
• For console services, we recommend the following:
HTTP Disable
HTTPS Enable
Telnet Disable
Moxa Command Disable
• To enable or disable these services, log in to the HTTP/HTTPS console and select
System Management
Misc. Settings Console Settings.
•
To disable the SNMP agent service, log in to the HTTP/HTTPS console and select
System Management
SNMP Agent, then select Disable for SNMP.
Page 8

Moxa Tech Note
The Security Hardening Guide for the MGate
5000 Series
Copyright © 2021 Moxa Inc.
Page 8 of 19
Note:
For
the MGate
• To disable the NTP service, log in to the HTTP/HTTPS console, select Basic
Settings, and keep the Time server setting empty. This will disable the NTP
service.
each instruction above, click the Submit button to save your changes, then restart
device so the new settings will take effect.
3.2. HTTPS and SSL Certificates
HTTPS is an encrypted communication channel. As TLS v1.1 or lower has severe
vulnerabilities that can easily be hacked, MGate devices use TLS v1.2 for HTTPS to
ensure data transmissions are secured. Make sure your browser has TLS v1.2 enabled.
In order to use HTTPS console without a certificate warning appearing, you need to
import a trusted certificate issued by a third-party certificate authority.
• Log in to the HTTP/HTTPS console and select System Management Certificate.
You can generate an up-to-date valid certificate by importing a third-party trusted
SSL certificate or generating the “MGate self-signed” certificate.
Page 9

Moxa Tech Note
The Security Hardening Guide for the MGate
5000 Series
Copyright © 2021 Moxa Inc.
Page 9 of 19
Note:
The maximum supported key length
Behavior of the SSL Certificate on an MGate Device
− MGate devices can auto-generate a self-signed SSL certificate. It is
recommended that you import SSL certificates that are either certified by a
trusted third-party Certificate Authority (CA) or by an organization's CA.
− The length of the MGate device’s self-signed private keys is 1,024 bits, which
should be compatible with most applications. Some applications may need a
longer key, such as 2,048 bits, which would require importing a third-party
certificate. Please note that longer keys will mean browsing the web console will
be slower due to the increased complexity of encrypting and decrypting
communicated data.
MGate Self-signed Certificate
If a certificate has expired, you can regenerate the MGate self-signed certificate with
the following steps.
− Step 1. Delete the current SSL certificate issued by the MGate device.
− Step 2. Enable the NTP server and set up the time zone and local time.
− Step 3. After restarting the device, the MGate self-signed certificate will be
regenerated with a new expiration date.
Importing a Third-party Trusted SSL Certificate
Importing the third-party trusted SSL certificate can improve security. To generate
the SSL certificate through a third party, follow these steps:
− Step 1. Create a certification authority (Root CA), such as Microsoft AD
Certificate Service (https://mizitechinfo.wordpress.com/2014/07/19/step-by-
step-installing-certificate-authority-on-windows-server-2012-r2/)
− Step 2. Find a tool to issue a certificate signing request (CSR) file. You can get
one from a third-party CA company such as DigiCert
(https://www.digicert.com/easy-csr/openssl.htm).
− Step 3. Submit the CSR file to a public certification authority to get a signed
certificate.
− Step 4. Import the certificate to the MGate device. Please note that MGate
devices only accept certificates using a “.pem” format.
for MGate devices is 2,048 bits.
Page 10

Moxa Tech Note
The Security Hardening Guide for the MGate
5000 Series
Copyright © 2021 Moxa Inc.
Page 10 of 19
Here are some well-known third-party CA (Certificate Authority) companies for your
reference (https://en.wikipedia.org/wiki/Certificate_authority):
− IdenTrust (https://www.identrust.com/)
− DigiCert (https://www.digicert.com/)
− Comodo Cybersecurity (https://www.comodo.com/)
− GoDaddy (https://www.godaddy.com/)
− Verisign (https://www.verisign.com/)
Page 11

Moxa Tech Note
The Security Hardening Guide for the MGate
5000 Series
Copyright © 2021 Moxa Inc.
Page 11 of 19
Note:
We suggest you
level” account instead of
us
the new
“admin” account should be monitored for security
3.3. Account Management
• The MGate 5000 Series provides two different user levels, admin and user, with a
maximum of 16 accounts. With an administrator account, you can access and
modify all settings through the web console. With the user account, you can only
view settings.
The default administrator account is admin, with the default password moxa. To
•
manage accounts, log in to the web console and select System Management
Misc. Settings
account, double-click the name of the account. You can change the password on the
page that opens.
• To add a new account, log in to the HTTP/HTTPS console and select System
Management
then fill in the Account name, User level, New password, and Retype
password to generate a new account.
Account Management. To change the password of an existing
Misc. Settings Account Management. Click the Add button,
ing the default “admin” account, as it is commonly used by embedded systems. Once
administrator level account has been created, it is suggested that the original
manage your device with another “administrator
reasons to prevent brute-force attacks.
Page 12
Moxa Tech Note
The Security Hardening Guide for the MGate
5000 Series
Copyright © 2021 Moxa Inc.
Page 12 of 19
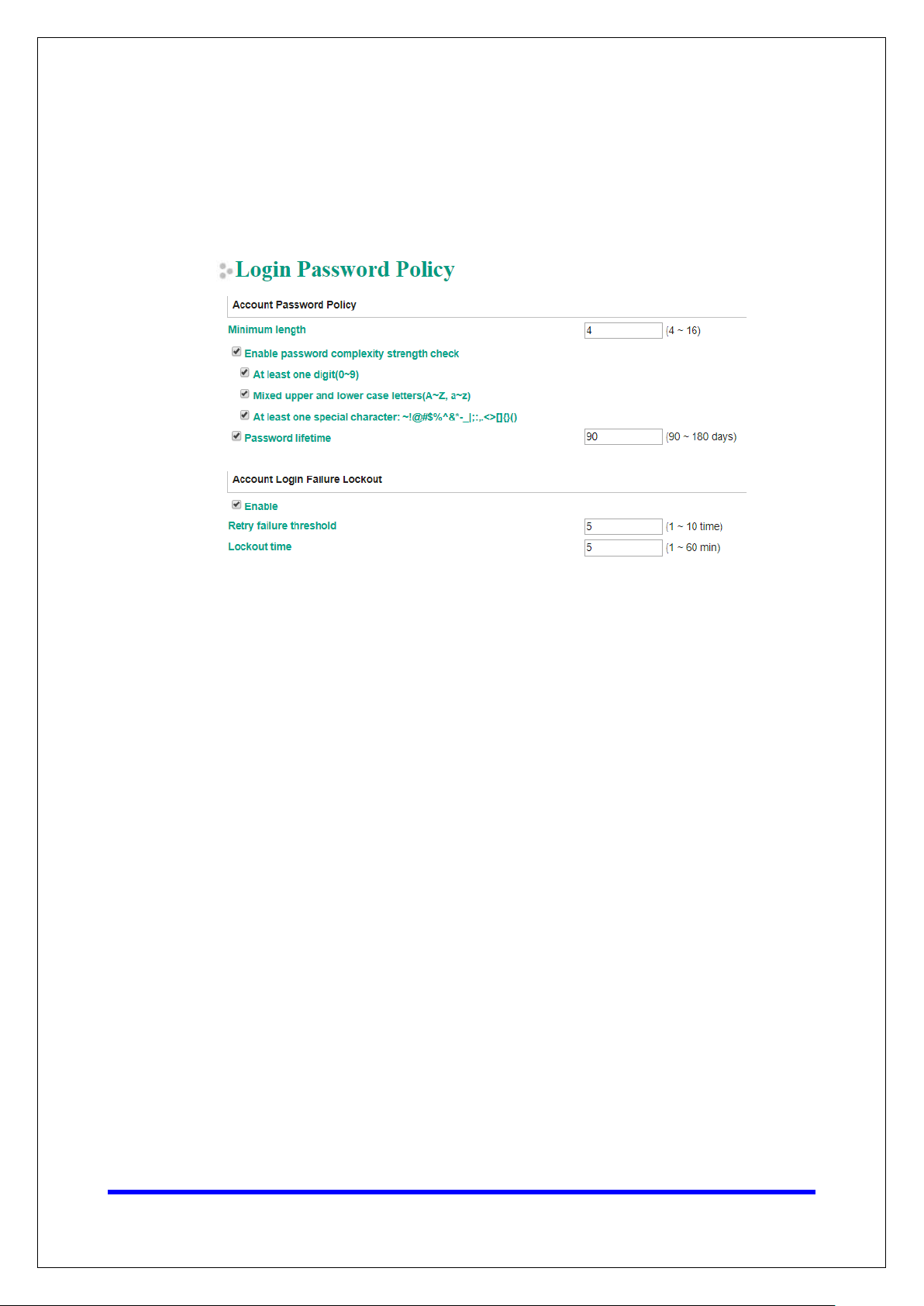
• To improve security, the login password policy and account login failure lockout can
be configured. To configure them, log in to the HTTP/HTTPS console and select
System Management Misc. Settings Login Password Policy.
You should adjust the password policy to require more complex passwords. For
example, set the Minimum length to 16, enable all password complexity strength
checks, and enable the Password lifetime options. Also, to avoid brute-force
attack, it’s suggested that you enable the Account login failure lockout feature.
Page 13

Moxa Tech Note
The Security Hardening Guide for the MGate
5000 Series
Copyright © 2021 Moxa Inc.
Page 13 of 19
• For some system security requirements, a warning message may need to be
displayed to all users attempting to log in to the device. To add a login message, log
in to the HTTP/HTTPS console and select System Management Misc. Settings
Notification Message, and enter a Login Message to use.
Page 14

Moxa Tech Note
The Security Hardening Guide for the MGate
5000 Series
Copyright © 2021 Moxa Inc.
Page 14 of 19
3.4. Accessible IP List
• The MGate 5000 Series can limit access to specific host IP addresses to prevent
unauthorized access to the gateway. If a host’s IP address is in the accessible IP list,
then the host will be allowed to access the MGate 5000 Series. To configure this, log
in to the HTTP/HTTPS console and select System Management
List. The different restrictions are listed in the table below (the checkbox Apply
additional restrictions can only be activated if Activate the accessible IP list is
activated).
Accessible IP
Activate the
accessible IP list
v All protocol
v v All protocol
* HTTP, HTTPS, TELNET, SSL, SNMP, SMTP, DNS, NTP, DSU
Apply additional
restrictions
IPs on the list
(Active checked)
communication and
services* are allowed.
communication and
services* are allowed.
IPs NOT on the list
(Active NOT checked)
Protocol communication is
not allowed, but services*
are still allowed.
All services* are not
allowed.
Page 15

Moxa Tech Note
The Security Hardening Guide for the MGate
5000 Series
Copyright © 2021 Moxa Inc.
Page 15 of 19
Ensure
Accessible
• You may add a specific address or range of addresses by using a combination of an
IP address and a netmask as follows:
− To allow access to a specific IP address: Enter the IP address in the
corresponding field, then enter 255.255.255.255 for the netmask.
− To allow access to hosts on a specific subnet: For both the IP address and
netmask, use 0 for the last digit (e.g., “192.168.1.0” and “255.255.255.0”).
− To allow access to all IP addresses: Make sure that Enable the checkbox for
the accessible IP list is not checked.
Additional configuration examples are shown in the following table:
Desired IP Range IP Address Field Netmask Field
Any host Disable Enable
192.168.1.120 192.168.1.120 255.255.255.255
192.168.1.1 to 192.168.1.254 192.168.1.0 255.255.255.0
192.168.1.1 to 192.168.255.254 192.168.0.0 255.255.0.0
192.168.1.1 to 192.168.1.126 192.168.1.0 255.255.255.128
192.168.1.129 to 192.168.1.254 192.168.1.128 255.255.255.128
Warning
that the IP address of the PC you are using to access the web console is in the
IP List.
3.5. Logging and Auditing
• These are the events that will be recorded by the MGate 5000 Series. The SD card
access failure event and protocol events vary for the different MGate 5000 models.
Event Group Summary
System System cold start, system warm start, SD card access failure
Network DHCP/BOOTP gets IP/renew, NTP connect failed, IP conflict, Network link
down
Configuration Login failed, IP changed, Password changed, Firmware upgraded, SSL
Certificate imported, Configuration imported/exported, Configuration
changed, Clear event logged
Protocol Protocol communication logs
Page 16

Moxa Tech Note
The Security Hardening Guide for the MGate
5000 Series
Copyright © 2021 Moxa Inc.
Page 16 of 19
• To configure this setting, log in to the HTTP/HTTPS console and select System
Management
on the MGate 5000 device and/or Syslog for keeping records on a server. You
should enable system log settings to record all important system events to monitor
device status and check for security issues.
System Log Settings. Then, enable the Local Log for recording
To view events in the system log, log in to the HTTP/HTTPS console and select
•
System Monitoring
System Log.
Page 17

Moxa Tech Note
The Security Hardening Guide for the MGate
5000 Series
Copyright © 2021 Moxa Inc.
Page 17 of 19
3.6. DoS Defense
You can enable and configure a number of features to enable DoS Defense in order to
protect against denial-of-service (DoS) attacks.
Page 18

Moxa Tech Note
The Security Hardening Guide for the MGate
5000 Series
Copyright © 2021 Moxa Inc.
Page 18 of 19
4. Patching/Upgrades
4.1. Patch Management Plan
With regard to patch management, Moxa in general releases version enhancement with
thorough release notes annually.
4.2. Firmware Upgrades
The process for upgrading firmware is as follows:
• Download the latest firmware for your MGate device from the Moxa website:
− Firmware for the MGate 5101 Series:
https://www.moxa.com/en/products/industrial-edge-connectivity/protocol-
gateways/modbus-tcp-gateways/mgate-5101-pbm-mn-series#resources
− Firmware for the MGate 5102 Series:
https://www.moxa.com/en/products/industrial-edge-connectivity/protocol-
gateways/profinet-gateways/mgate-5102-pbm-pn-series
− Firmware for the MGate 5103 Series:
https://www.moxa.com/en/products/industrial-edge-connectivity/protocol-
gateways/modbus-tcp-gateways/mgate-5103-series#resources
− Firmware for the MGate 5105 Series:
https://www.moxa.com/en/products/industrial-edge-connectivity/protocol-
gateways/modbus-tcp-gateways/mgate-5105-mb-eip-series#resources
− Firmware for the MGate 5109 Series:
https://www.moxa.com/en/products/industrial-edge-connectivity/protocol-
gateways/modbus-tcp-gateways/mgate-5109-series#resources
− Firmware for the MGate 5111 Series:
https://www.moxa.com/en/products/industrial-edge-connectivity/protocol-
gateways/modbus-tcp-gateways/mgate-5111-series#resources
− Firmware for the MGate 5114 Series:
https://www.moxa.com/en/products/industrial-edge-connectivity/protocol-
gateways/modbus-tcp-gateways/mgate-5114-series#resources
− Firmware for the MGate 5118 Series:
https://www.moxa.com/en/products/industrial-edge-connectivity/protocol-
gateways/modbus-tcp-gateways/mgate-5118-series#resources
− Firmware for the MGate W5108/W5208 Series:
https://www.moxa.com/en/products/industrial-edge-connectivity/protocol-
gateways/modbus-tcp-gateways/mgate-w5108-w5208-series#resources
Page 19

Moxa Tech Note
The Security Hardening Guide for the MGate
5000 Series
Copyright © 2021 Moxa Inc.
Page 19 of 19
• Log in to the HTTP/HTTPS console and select System Management
Maintenance
proper firmware and click Submit to upgrade the firmware.
• If you want to upgrade the firmware for multiple units, then download the utility
Device Search Utility (DSU) or MXconfig for a GUI interface, or the Moxa CLI
Configuration Tool for a CLI interface.
Firmware Upgrade. Click the Choose File button to select the
5. Security Information and Vulnerability Feedback
As the adoption of the Industrial IoT (IIoT) continues to grow rapidly, security has become
one of our top priorities. The Moxa Cyber Security Response Team (CSRT) takes a proactive
approach to protect our products from security vulnerabilities and help our customers better
manage security risks.
You can find the latest Moxa security information
here:https://www.moxa.com/en/support/product-support/security-advisory
 Loading...
Loading...