Page 1

Operating Manual
IPn3G / IPn3Gb
3G/HSPA/HSPA+ Cellular Ethernet/Serial/USB Gateway
Revision 3.1 - March 2014
Firmware: v2.2.0-r2102
150 Country Hills Landing N.W.
Calgary, AB, Canada T3K 5P3
Phone: (403) 248-0028
Fax: (403) 248-2762
www.microhardcorp.com
Page 2

Important User Information
Warranty
Microhard Systems Inc. warrants that each product will be free of defects in material and workmanship for a period of one (1)
year for its products. The warranty commences on the date the product is shipped by Microhard Systems Inc. Microhard Systems
Inc.’s sole liability and responsibility under this warranty is to repair or replace any product which is returned to it by the Buyer
and which Microhard Systems Inc. determines does not conform to the warranty. Product returned to Microhard Systems Inc. for
warranty service will be shipped to Microhard Systems Inc. at Buyer’s expense and will be returned to Buyer at Microhard Systems Inc.’s expense. In no event shall Microhard Systems Inc. be responsible under this warranty for any defect which is caus ed
by negligence, misuse or mistreatment of a product or for any unit which has been altered or modified in any way. The warranty
of replacement shall terminate with the warranty of the product.
Warranty Disclaims
Microhard Systems Inc. makes no warranties of any nature of kind, expressed or implied, with respect to the hardware, software,
and/or products and hereby disclaims any and all such warranties, including but not limited to warranty of non-infringement,
implied warranties of merchantability for a particular purpose, any interruption or loss of the hardware, software, and/or product,
any delay in providing the hardware, software, and/or product or correcting any defect in the hardware, software, and/or product,
or any other warranty. The Purchaser represents and warrants that Microhard Systems Inc. has not made any such warranties to
the Purchaser or its agents MICROHARD SYSTEMS INC. EXPRESS WARRANTY TO BUYER CONSTITUTES MICRO-
HARD SYSTEMS INC. SOLE LIABILITY AND THE BUYER’S SOLE REMEDIES. EXCEPT AS THUS PROVIDED, MI-
CROHARD SYSTEMS INC. DISCLAIMS ALL WARRANTIES, EXPRESS OR IMPLIED, INCLUDING ANY WARRANTY
OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PROMISE.
MICROHARD SYSTEMS INC. PRODUCTS ARE NOT DESIGNED OR INTENDED TO BE USED IN
ANY LIFE SUPPORT RELATED DEVICE OR SYSTEM RELATED FUNCTIONS NOR AS PART OF
ANY OTHER CRITICAL SYSTEM AND ARE GRANTED NO FUNCTIONAL WARRANTY.
Indemnification
The Purchaser shall indemnify Microhard Systems Inc. and its respective directors, officers, employees, successors and assigns
including any subsidiaries, related corporations, or affiliates, shall be released and discharged from any and all manner of action,
causes of action, liability, losses, damages, suits, dues, sums of money, expenses (including legal fees), general damages, special
damages, including without limitation, claims for personal injuries, death or property damage related to the products sold hereunder, costs and demands of every and any kind and nature whatsoever at law.
IN NO EVENT WILL MICROHARD SYSTEMS INC. BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL,
INCIDENTAL, BUSINESS INTERRUPTION, CATASTROPHIC, PUNITIVE OR OTHER DAMAGES WHICH MAY BE
CLAIMED TO ARISE IN CONNECTION WITH THE HARDWARE, REGARDLESS OF THE LEGAL THEORY BEHIND
SUCH CLAIMS, WHETHER IN TORT, CONTRACT OR UNDER ANY APPLICABLE STATUTORY OR REGULATORY
LAWS, RULES, REGULATIONS, EXECUTIVE OR ADMINISTRATIVE ORDERS OR DECLARATIONS OR OTHERWISE, EVEN IF MICROHARD SYSTEMS INC. HAS BEEN ADVISED OR OTHERWISE HAS KNOWLEDGE OF THE
POSSIBILITY OF SUCH DAMAGES AND TAKES NO ACTION TO PREVENT OR MINIMIZE SUCH DAMAGES. IN THE
EVENT THAT REGARDLESS OF THE WARRANTY DISCLAIMERS AND HOLD HARMLESS PROVISIONS INCLUDED
ABOVE MICROHARD SYSTEMS INC. IS SOMEHOW HELD LIABLE OR RESPONSIBLE FOR ANY DAMAGE OR INJURY, MICROHARD SYSTEMS INC.'S LIABILITY FOR ANYDAMAGES SHALL NOT EXCEED THE PROFIT REALIZED BY MICROHARD SYSTEMS INC. ON THE SALE OR PROVISION OF THE HARDWARE TO THE CUSTOMER.
Proprietary Rights
The Buyer hereby acknowledges that Microhard Systems Inc. has a proprietary interest and intellectual property rights in the
Hardware, Software and/or Products. The Purchaser shall not (i) remove any copyright, trade secret, trademark or other evidence
of Microhard Systems Inc.’s ownership or proprietary interest or confidentiality other proprietary notices contained on, or i n, the
Hardware, Software or Products, (ii) reproduce or modify any Hardware, Software or Products or make any copies thereof, (iii)
reverse assemble, reverse engineer or decompile any Software or copy thereof in whole or in part, (iv) sell, transfer or otherwise
make available to others the Hardware, Software, or Products or documentation thereof or any copy thereof, except in accordance
with this Agreement.
© Microhard Systems Inc. 2
Page 3

Important User Information (continued)
About This Manual
It is assumed that users of the products described herein have either system integration or
design experience, as well as an understanding of the fundamentals of radio communications.
Throughout this manual you will encounter not only illustrations (that further elaborate on the
accompanying text), but also several symbols which you should be attentive to:
Caution or Warning
Usually advises against some action which could result in undesired or
detrimental consequences.
Point to Remember
Highlights a key feature, point, or step which is noteworthy. Keeping
these in mind will simplify or enhance device usage.
Tip
An idea or suggestion to improve efficiency or enhance usefulness.
Information
Information regarding a particular technology or concept.
© Microhard Systems Inc. 3
Page 4
Important User Information (continued)
Regulatory Requirements / Exigences Réglementaires
To satisfy FCC RF exposure requirements for mobile transmitting devices, a separation distance of 23cm or more should be maintained
between the antenna of this device and persons during device operation. To ensure compliance, operations at closer than this distance is not
recommended. The antenna being used for this transmitter must not be co-located in conjunction with any other antenna or transmitter.
Pour satisfaire aux exigences de la FCC d'exposition RF pour les appareils mobiles de transmission, une distance de séparation de 23cm ou
WARNING
WARNING
plus doit être maintenue entre l'antenne de cet appareil et les personnes au cours de fonctionnement du dispositif. Pour assurer le respect,
les opérations de plus près que cette distance n'est pas recommandée. L'antenne utilisée pour ce transmetteur ne doit pas être co-localisés
en conjonction avec toute autre antenne ou transmetteur.
MAXIMUM EIRP
FCC Regulations allow up to 36dBm Effective Isotropic Radiated Power (EIRP). Therefore, the sum of the transmitted power (in dBm), the
cabling loss and the antenna gain cannot exceed 36dBm.
Réglementation de la FCC permettra à 36dBm Puissance isotrope rayonnée équivalente (EIRP). Par conséquent, la somme de la puissance
transmise (en dBm), la perte de câblage et le gain d'antenne ne peut pas dépasser 36dBm.
EQUIPMENT LABELING / ÉTIQUETAGE DE L'ÉQUIPEMENT
This device has been modularly approved. The manufacturer, product name, and FCC and Industry Canada identifiers of this product must
appear on the outside label of the end-user equipment.
WARNING
Ce dispositif a été approuvé de façon modulaire. Le fabricant, le nom du produit, et la FCC et de l'Industrie du Canada identifiants de ce
produit doit figurer sur l'étiquette à l'extérieur de l'équipement de l'utilisateur final.
SAMPLE LABEL REQUIREMENT / EXIGENCE D'ÉTIQUETTE :
IPn3G Version 2 IPn3G Version 1
FCCID: RI7T56KL1
IC: 5131A-KL1
This device complies with Part 15 of the FCC Rules.
Operation is subject to the following two conditions:
(1) this device may not cause harmful interference,
and (2) this device must accept any interference
received including interference that may cause
undesired operation.
FCCID: IHDT56KL1
IC: 109O-KL1
This device complies with Part 15 of the FCC Rules.
Operation is subject to the following two conditions:
(1) this device may not cause harmful interference,
and (2) this device must accept any interference
received including interference that may cause
undesired operation.
IPn3Gb
FCCID: XPYLISAU230
IC: 8595A-LISAU230
This device complies with Part 15 of the FCC Rules.
Operation is subject to the following two conditions:
(1) this device may not cause harmful interference,
and (2) this device must accept any interference
received including interference that may cause
undesired operation.
Please Note: These are only sample labels; different products contain different identifiers. The actual identifiers should
be seen on your devices if applicable.
S'il vous plaît noter: Ce sont des exemples d'étiquettes seulement; différents produits contiennent des identifiants
différents. Les identifiants réels devrait être vu sur vos périphériques le cas échéant.
© Microhard Systems Inc. 4
Page 5

Revision History
Revision Description Initials Date
1.0 Initial Release PEH July 2010
1.1 Updated drawings (SMA), screen shots, pictures PEH Sept 2010
1.2 Updated drawings (Diversity, GPS) PEH Sept 2010
1.3 Updated graphics, drawings to reflect new enclosure design PEH Oct 2010
1.4 Update to Quick Start & WebUI menu changes PEH Jan 2011
1.5 Updates to screen shots as required PEH Feb 2011
1.6 Added GPS specs and antenna info PEH Feb 2011
1.7 NTP moved to system configuration, timezone added, phone number added to stats page, ICMP
description updated (v1.1.6-r026)
1.8 Updated VPN IPSec, GPS, Firewall, Misc Updates (v1.1.8-r1032h PEH June 2011
2.0 New menu format, Added AT Commands, UDP Reporting (v1.1.10-r1036) PEH Sept 2011
2.1 Added AT Command Syntax for each command, Added SMS At Commands PEH Feb 2012
2.2 Updated to reflect changes in v1.2.2-r1045. SMS, SMS Alerts, GRE, Added info on SNMP MIB,
Backup/Restore, System conf etc
2.3 Updated FCC & IC ID’s, Misc Screen Shots, Formatting PEH Feb 2012
2.4 Updated SNMP MIB PEH Feb 2012
2.41 Removed references to Appendix D in Regulatory Info. PEH Mar 2012
2.5 Added Digital I/O, COM Logging, Event NMS Support, Management, Scheduled Reboots, SMS,
PPP, Email Updates, Screen Shots etc. v1.2.4-r1058
2.6 Added System > History (RSSI, EC/NO, Temp, VDC logs), System Reboot History, Network >
Ethernet Port Status. V2.0.0-r2002b
2.61 Fixed links in TOC PEH July 2012
2.7 Updated NMS Configuration and related info, Syslog, Static Routing, updated screen shots, etc.
V2.0.18-r2040, added Appendix on IP-Passthrough, Port Forwarding, added GPS to Serial.
2.8 Updated to reflect changes up to v2.0.28-r2070. Added History > Frequency ,Updated Network
DHCP Lease time, MAC binding, Updated Carrier > Frequency, Added Security > Certificate Management, Updated VPN, Updated GRE, Added Modbus, Added Power Saving. Misc formatting,
updated screen shots throughout.
2.81 Added PoE, for units shipped after March 1, 2013 PEH Jul 2013
2.9 Added Data Usage, Local Monitor, VPN Appendix, Firewall Appendix, Troubleshooting Appendix,
updated screen shots, added Modbus options to serial port, added SMS Control Commands, AT
Commands, misc corrections & formatting. Changes current up to firmware v2.0.44 -r2090.
3.0 Added FCC ID for IPn3Gb, Added additional spec data for IPn3Gb PEH Jan 2014
3.1 Additional updates for IPn3Gb, Updated to reflect firmware v2.2.0-r2102. Updated Carrier Config,
Added Wireless Bus to COM1.
PEH Apr 2011
PEH Feb 2012
PEH June 2012
PEH June 2012
PEH Nov 2012
PEH Mar 2013
PEH Oct 2013
PEH Mar 2014
© Microhard Systems Inc. 5
Page 6

CSA Class 1 Division 2 Option
CSA Class 1 Division 2 is Available Only on Specifically Marked Units
If marked this for Class 1 Division 2 – then this product is available for use in Class 1 Division 2, in the indicated Groups on the
product.
In such a case the following must be met:
The transceiver is not acceptable as a stand-alone unit for use in hazardous locations. The transceiver must be mounted within a
separate enclosure, which is suitable for the intended application. Mounting the units within an approved enclosure that is c ertified
for hazardous locations, or is installed within guidelines in accordance with CSA rules and local electrical and fire code, will ensure
a safe and compliant installation.
The antenna feed line; DC power cable and interface cable must be routed through conduit in accordance with the National
Electrical Code.
Do not connect or disconnect equipment unless power has been switched off or the area is known to be non-hazardous.
Installation, operation and maintenance of the transceiver should be in accordance with the transceiver’s installation manual, and
the National Electrical Code.
Tampering or replacement with non-factory components may adversely affect the safe use of the transceiver in hazardous
locations, and may void the approval.
The wall adapters supplied with your transceivers are NOT Class 1 Division 2 approved, and therefore, power must be supplied to
the units using the screw-type or locking type connectors supplied from Microhard Systems Inc. and a Class 1 Division 2 power
source within your panel.
If you are unsure as to the specific wiring and installation guidelines for Class 1 Division 2 codes, contact CSA International.
CSA Classe 1 Division 2 est disponible uniquement sur les unités particulièrement
marquées
Si marqué cette Classe 1 Division 2 - alors ce produit est disponible pour une utilisation en Classe 1 Division 2 , dans les groupes
indiqués sur le produit .
Dans un tel cas, la suivante doit être remplie:
L'émetteur-récepteur n'est pas acceptable comme une unité autonome pour une utilisation dans des endroits dangereux .
L'émetteur-récepteur doit être monté dans un boîtier séparé , qui est approprié pour l'application envisagée. Montage des unités
dans une enceinte approuvée qui est certifié pour les emplacements dangereux , ou est installé à l'intérieur des lignes directrices ,
conformément aux règles de la CSA et le code électrique local et le feu , assurera une installation sûre et conforme .
La ligne d'alimentation d'antenne , câble d'alimentation CC et le câble d'interface doivent être acheminés à travers le conduit en
conformité avec le National Electrical Code .
Ne pas connecter ou déconnecter l'équipement que l'alimentation est coupée ou que la zone est connue pour être non
dangereux .
Installation, l'exploitation et la maintenance de l'émetteur-récepteur doivent être en conformité avec le manuel d'installation de
l'émetteur-récepteur , et le National Electrical Code .
Falsification ou le remplacement des composants non - usine peut nuire à l'utilisation sécuritaire de l'émetteur-récepteur dans des
endroits dangereux , et peut annuler l'approbation .
Les adaptateurs muraux fournis avec les émetteurs-récepteurs sont PAS classe 1, division 2 ont approuvé , et par conséquent,
doit être alimenté pour les unités à l'aide des connecteurs de type vis ou verrouillage fournies par Microhard Systems Inc. et une
Division 2 source d'alimentation de classe 1 au sein de votre panneau .
Si vous n'êtes pas sûr de l' installation et de câblage des lignes directrices spécifiques pour la classe 1 Division 2 codes ,
communiquer avec la CSA International.
© Microhard Systems Inc. 6
Page 7

Table of Contents
1.0 Overview 9
1.1 Performance Features .......................................................................................................................... 9
1.2 Specifications ..................................................................................................................................... 10
1.3 Ipn3Gb RF Performance..................................................................................................................... 12
2.0 Quick Start 14
2.1 Installing the SIM Card ...................................................................................................................... 14
2.2 Getting Started .................................................................................................................................. 14
3.0 Hardware Features 18
3.1 IPn3G Hardware ................................................................................................................................ 18
3.1.1 IPn3G Mechanical Drawings ................................................................................................... 19
3.1.2 Connectors & Indicators ......................................................................................................... 20
3.1.2.1 Front ...................................................................................................................... 20
3.1.2.2 Rear ....................................................................................................................... 21
4.0 WebUI Configuration 22
4.1 Logon Window ................................................................................................................................... 23
4.2 System .............................................................................................................................................. 24
4.2.1 Summary ............................................................................................................................... 24
4.2.2 Config .................................................................................................................................... 25
4.2.3 Location ................................................................................................................................. 28
4.2.4 History ................................................................................................................................... 29
4.3 Network ............................................................................................................................................. 30
4.3.1 Summary ............................................................................................................................... 30
4.3.2 Statistics .............................................................................................................................. 31
4.3.3 Graph .................................................................................................................................... 32
4.3.4 Config .................................................................................................................................... 33
4.3.5 Static Routing ........................................................................................................................ 36
4.3.6 SNMP .................................................................................................................................... 37
4.3.7 DHCP Lease .......................................................................................................................... 40
4.3.8 Device List ............................................................................................................................. 40
4.3.9 Local Monitor ......................................................................................................................... 41
4.4 Carrier .............................................................................................................................................. 42
4.4.1 Statistics ................................................................................................................................ 42
4.4.2 Graph .................................................................................................................................... 43
4.4.3 Config .................................................................................................................................... 44
4.5 COM1 / COM2 Configuration .............................................................................................................. 50
4.5.1 Statistics ................................................................................................................................ 50
4.5.2 Config .................................................................................................................................... 51
4.6 USB Configuration ............................................................................................................................. 64
4.6.1 Statistics ................................................................................................................................ 64
4.6.2 Config .................................................................................................................................... 65
4.7 Security ............................................................................................................................................. 69
4.7.1 Password ............................................................................................................................... 69
4.7.2 Discovery ............................................................................................................................... 69
4.7.3 Access ................................................................................................................................... 69
4.7.4 Authentication ........................................................................................................................ 70
4.7.5 Certificate Management ......................................................................................................... 72
4.8 Firewall .............................................................................................................................................. 73
4.8.1 Rules ................................................................ ..................................................................... 74
4.8.2 Port Forwarding / DMZ ........................................................................................................... 76
4.8.3 MAC List .............................................................................................................................. 78
© Microhard Systems Inc. 7
Page 8

Table of Contents (continued)
4.8.4 IP List .................................................................................................................................... 79
4.8.5 Default ................................................................................................................................... 80
4.9 I/O ..................................................................................................................................................... 81
4.9.1 Status .................................................................................................................................... 81
4.10 Advanced .......................................................................................................................................... 82
4.10.1 VPN / IPsec ........................................................................................................................... 82
4.10.1.1 Gateway to Gateway (Site-to-Site) ........................................................................... 82
4.10.1.2 L2TP Server ........................................................................................................... 88
4.10.1.3 L2TP Client............................................................................................................. 90
4.10.1.4 VPN Client Status ................................................................................................... 92
4.10.2 GRE Tunneling ...................................................................................................................... 93
4.10.3 GPS ...................................................................................................................................... 97
4.10.4 Event Reporting ................................................................................................................... 102
4.10.4.1 Configuration ........................................................................................................ 102
4.10.4.2 Message Structure ................................................................................................ 103
4.10.4.3 Message Payload ................................................................................................. 104
4.10.5 SMS .................................................................................................................................... 105
4.10.6 SMS Alerts........................................................................................................................... 106
4.10.7 Netflow Report ..................................................................................................................... 108
4.10.8 Modbus................................................................................................................................ 109
4.10.8.1 TCP Modbus ................................ ........................................................................ 109
4.10.8.2 COM (Serial) Mobus ............................................................................................. 111
4.10.9 Power Saving ....................................................................................................................... 113
4.10.10 Data Usage .......................................................................................................................... 114
4.11 Tools ............................................................................................................................................... 117
4.11.1 Maintenance ........................................................................................................................ 117
4.11.1.1 Configuration Backup (WebUI/FTP) ....................................................................... 117
4.11.1.3 Configuration Restore (WebUI/FTP) ...................................................................... 119
4.11.1.5 Firmware Upgrade (WebUI/FTP) ........................................................................... 121
4.11.2 NMS Settings ....................................................................................................................... 123
4.11.3 Diagnostic Utilities (Ping/Trace Route) .................................................................................. 127
4.11.4 Reset to Default ................................................................................................................... 128
4.11.5 Reboot System .................................................................................................................... 128
4.12 Logout ............................................................................................................................................. 129
5.0 AT Commands ....................................................................................................130
5.1 AT Command Overview ................................................................................................ .................... 130
5.1.1 Serial Port Configuration....................................................................................................... 130
5.1.2 Telnet TCP/IP Configuration ................................................................................................. 131
5.2 AT Command Syntax ....................................................................................................................... 132
5.3 Supported AT Commands ................................................................................................................ 133
Appendices
Appendix A: RS485 Wiring .................................................................................................................. 178
Appendix B: Serial Interface ................................................................................................................ 179
Appendix C: IP-Passthrough ............................................................................................................... 180
Appendix D: Port Forwarding .............................................................................................................. 182
Appendix E: VPN Example .................................................................................................................. 184
Appendix F: Firewall Example ............................................................................................................. 192
Appendix G: Troubleshooting ................................ ............................................................................. 194
Appendix H: “system.conf” File Structure .......................................................................................... 197
Appendix I: SNMP MIB File Sample ................................................................................................... 222
Appendix J: Digital I/O: Driving an External Relay ............................................................................. 237
© Microhard Systems Inc. 8
Page 9

1.0 Overview
A SERIAL GATEWAY
allows asynchronous
serial data to enter (as
through a gate) the
realm of IP
communications.
The serial data is
encapsulated within
UDP or TCP packets.
The IPn3G is a high-performance 3G Cellular Ethernet/Serial/USB Gateway. Equipped with 2
serial data ports, 1 USB, and 1 Ethernet Port, the IPn3G provides complete access to remote
devices. Using the vast established infrastructure of cellular networks, the IPn3G can provide
data services anywhere coverage is provided.
While private wireless networks can provide wireless data services, using FHSS ISM bands, or
secure dedicated licensed radio’s, coverage is only available where radio’s, repeaters, and other
equipment is deployed. Achieving a wide coverage area generally involves many radio units,
antennas, possibly private or shared towers and large amounts of planning.
The IPn3G/IPn3Gb operates on HSPA & Quad Band GSM cellular networks, using 3G/HSPA//
HSPA+/EDGE/GPRS technology to provide fast and reliable data transfer.
The small size and superior performance of the IPn3G makes it ideal for many applications.
Some typical uses for this modem:
SCADA
remote telemetry
traffic control
industrial controls
remote monitoring
LAN extension
GPS
wireless video
robotics
display signs
fleet management
1.1 Performance Features
Key performance features of the IPn3G/IPn3Gb include:
communicates with virtually all PLCs, RTUs, and serial devices through either one of
two available RS232 interface, RS422, or RS485
fastest serial rates: 300 baud to 921kbps
advanced serial port supports legacy serial devices, including RTS, CTS, DSR, DTR,
and DCD.
Easy to manage through web- or text-based user interface, or SNMP
wireless firmware upgrades
system wide remote diagnostics
advanced security features
industrial temperature specifications
DIN rail mountable
Optional Class 1 Div 2
Available as OEM solution
Supporting co-located independent networks and with the ability to carry both serial and IP traffic, the IPn3G supports not only network growth, but also provides the opportunity to migrate
from asynchronous serial devices connected today to IP-based devices in the future.
© Microhard Systems Inc. 9
Page 10

1.0 Overview
Caution: Using a
power supply that
does not provide
proper voltage or
current may damage
the modem.
1.2 IPn3G / IPn3Gb Specifications
Electrical/General
IPn3G Supported Bands: HSPA & Quad Band GSM
850/1900/1700-2100 (HSPA)
850/900/1800/1900 MHz (GSM)
IPn3Gb Supported Bands: UMTS/HSPA FDD Bands [MHz] - Six band
Band I (2100MHz), Band II (1900MHz), Band IV (1700MHz), Band V
(850MHz), Band VI (800MHz), Band VIII (900Hz)
3GPP Release 7
5.76 Mb/s uplink, 21.1 Mb/s downlink
or 5.76 Mb/s uplink, 7.2 Mb/s downlink
IPn3G Data Features: HSPA
Up to 7.2 Mbps downlink
Up to 5.76 Mbps uplink
EDGE/GPRS
Multi-Slot Class 12
IPn3Gb Data Features: HSDPA cat 14, up to 21.1 Mb/s DL for LISA-U230
GPRS multi-slot class 125, coding scheme CS1-CS4, up to 85.6 kb/s DL/UL
EDGE multi-slot class 125, coding scheme MCS1-MCS9, up to 236.8 kb/s DL/UL
CSD GSM max 9.6 kb/s
UMTS max 64 kb/s
IPn3G TX Power: HSPA - Class 3 (0.25W)
GSM 850/900 MHz - Class 4 (2W)
GSM 1800/1900 MHz - Class 1 (1W)
EDGE 850/900 MHz - Class E2 (0.5W)
EDGE 1800/1900 MHz - Class E2 (0.4W)
IPn3Gb TX Power: WCDMA/HSDPA/HSUPA Power Class
· Power Class 3 (24 dBm) for WCDMA/HSDPA/HSUPA mode
GSM/GPRS Power Class
· Power Class 4 (33 dBm) for GSM/E-GSM bands
· Power Class 1 (30 dBm) for DCS/PCS bands
EDGE Power Class
· Power Class E2 (27 dBm) for GSM/E-GSM bands
· Power Class E2 (26 dBm) for DCS/PCS bands
IPn3Gb Current Consumption:
UMTS Active Connection Current:
Avg Serial Data: 75mA
Avg Ethernet: 94mA
Peak Tx: 275mA
Serial Interface: RS232, RS485, RS422
Serial Baud Rate: 300bps to 921kbps
USB: USB 2.0
USB Console Port
USB to Serial Data Routing
USB to Ethernet Data Routing
© Microhard Systems Inc. 10
Page 11

1.0 Overview
1.2 IPn3G / IPn3Gb Specifications (Continued)
Ethernet: 10/100 BaseT, Auto - MDI/X, IEEE 802.3
SIM Card: 1.8 / 3.0V
PPP Characteristics: Dial on Demand
Idle Time
Network Protocols: TCP, UDP, TCP/IP, TFTP, ARP, ICMP, DHCP, HTTP, HTTPS*, SSH*, SNMP,
FTP, DNS, Serial over IP, QoS
Management: Local Serial Console, Telnet, WebUI, SNMP, FTP &
Wireless Upgrade, RADIUS authentication, IPsec VLAN
Diagnostics: Temperature, RSSI, remote diagnostics
Input Voltage: 7-30 VDC
Power over Ethernet: Passive PoE on Ethernet Port (Units shipped after March 1, 2013)
GPS: Sensitivity: - Autonomous acquisition: -145 dBm
- Tracking Sensitivity: -158 dBm (50% valid fixes)
Position Accuracy: - Tracking L1, CA code
- 12 Channels
- Max. update rate 1 Hz
Error calculated location less than 11.6 meters 67% of the time, and
less than 24.2 meters 95% of the time.
Environmental
Operation Temperature: -40
Humidity: 5% to 95% non-condensing
o
F(-40oC) to 185oF(85oC)
Mechanical
Dimensions: 2.21” (56mm) X 3.85” (97mm) X 1.46” (37mm)
Weight: Approx. 245 grams
Connectors: Antenna(s): Main TX/RX: SMA Female
Diversity: SMA Female
GPS: SMA Female
Data, etc: Data: DE-9 Female
Ethernet : RJ-45
GPS Antenna Requirements:
- Frequency Range: 1575.42 MHz (GPS L1 Band)
- Bandwidth: +/- 2 MHz
- Total NF < 2.5dB
- Impedance 50ohm
- Amplification (Gain applied to RF connector): 19dB to 23dB
- Supply voltage 1.5V to 3.05V
- Current consumption - Typical 20mA (100mA max)
- Cellular Power Antenna Rejection + Isolation:
- 824 - 915 MHz > 10dB
- 1710 - 1785 MHz > 19dB
- 1850 - 1980 MHz > 23dB
© Microhard Systems Inc. 11
Page 12

1.0 Overview
1.3 IPn3Gb RF Performance
Frequency Range Min. (MHz) Max. (MHz) Remarks
GSM 850
E-GSM 900
DCS 1800
PCS1900
UMTS 800 (band VI)
UMTS 850 (band V)
UMTS 900 (band VIII)
UMTS 1700 (band VIII)
UMTS 1900 (band II)
UMTS 2100 (band 1)
Uplink 824 849 Module transmit
Downlink 869 894 Module receive
Uplink 880 915 Module transmit
Downlink 925 960 Module receive
Uplink 1710 1785 Module transmit
Downlink 1805 1880 Module receive
Uplink 1850 1910 Module transmit
Downlink 1930 1990 Module receive
Uplink 830 840 Module transmit
Downlink 875 885 Module receive
Uplink 824 849 Module transmit
Downlink 869 894 Module receive
Uplink 880 915 Module transmit
Downlink 925 960 Module receive
Uplink 1710 1755 Module transmit
Downlink 2110 2155 Module receive
Uplink 1850 1910 Module transmit
Downlink 1930 1990 Module receive
Uplink 1920 1980 Module transmit
Downlink 2110 2170 Module receive
Table 1-1: IPn3Gb Operating RF Frequency Bands
Receiver Input Sensitivity Min. (dBm) Typ. (dBm) Max. (dBm) Remarks
GSM 850 / E-GSM 900 -102.0 -110.0 Downlink RF level @ BER Class II < 2.4%
DCS 1800 / PCS 1900 -102.0 -109.0 Downlink RF level @ BER Class II < 2.4%
UMTS 800 (band VI) -106.7 -111.0 Downlink RF level for RMC @ BER < 0.1%
UMTS 850 (band V) -104.7 -112.0 Downlink RF level for RMC @ BER < 0.1%
UMTS 900 (band VIII) -103.7 -111.0 Downlink RF level for RMC @ BER < 0.1%
UMTS 1700 (band VIII) -106.7 -111.0 Downlink RF level for RMC @ BER < 0.1%
UMTS 1900 (band II) -104.7 -111.0 Downlink RF level for RMC @ BER < 0.1%
UMTS 2100 (band 1) -106.7 -111.0 Downlink RF level for RMC @ BER < 0.1%
Condition: 50 Ω source
© Microhard Systems Inc. 12
Table 1-2: IPn3Gb Receiver sensitivity performance
Page 13

1.0 Overview
1.3 IPn3Gb
Maximum Output
Power
GSM 850 / E-GSM 900
DCS 1800 / PCS 1900
UMTS 800 (band VI) 23.0 Uplink continuous RF power for RMS at maximum power
UMTS 850 (band V) 23.0 Uplink continuous RF power for RMS at maximum power
UMTS 900 (band VIII) 23.0 Uplink continuous RF power for RMS at maximum power
UMTS 1700 (band VIII) 23.0 Uplink continuous RF power for RMS at maximum power
UMTS 1900 (band II) 23.0 Uplink continuous RF power for RMS at maximum power
UMTS 2100 (band 1) 23.0 Uplink continuous RF power for RMS at maximum power
Condition for all parameters: 50 Ω output load
Condition for GPRS/EDGE multi-slot output power: Multi-Slot Power Reduction profile 2
RF Performance (continued…)
Min.
32.5 Uplink burst RF power for GSM or GPRS 1-slot TCH at PCL 5 or Gamma 3
32.5 Uplink burst RF power for GPRS 2-slot TCH at Gamma 3
31.7 Uplink burst RF power for GPRS 3-slot TCH at Gamma 3
30.5 Uplink burst RF power for GPRS 4-slot TCH at Gamma 3
27.0 Uplink burst RF power for EDGE 8PSK 1-slot TCH at PCL 8 or Gamma 6
27.0 Uplink burst RF power for EDGE 8PSK 2-slot TCH at Gamma 6
26.2 Uplink burst RF power for EDGE 8PSK 3-slot TCH at Gamma 6
25.0 Uplink burst RF power for EDGE 8PSK 4-slot TCH at Gamma 6
29.5 Uplink burst RF power for GSM or GPRS 1-slot TCH at PCL 0 or Gamma 3
29.5 Uplink burst RF power for GPRS 2-slot TCH at Gamma 3
28.7 Uplink burst RF power for GPRS 3-slot TCH at Gamma 3
27.5 Uplink burst RF power for GPRS 4-slot TCH at Gamma 3
26.0 Uplink burst RF power for EDGE 8PSK 1-slot TCH at PCL 2 or Gamma 5
26.0 Uplink burst RF power for EDGE 8PSK 2-slot TCH at Gamma 5
25.2 Uplink burst RF power for EDGE 8PSK 3-slot TCH at Gamma 5
24.0 Uplink burst RF power for EDGE 8PSK 4-slot TCH at Gamma 5
Typ.
(dBm)
Table 1-3: IPn3Gb Transmitter maximum output power
Max. Remarks
© Microhard Systems Inc. 13
Page 14
RS485/422
TxB -
TxA -
RxB -
RxA -
GND -
Vin+ -
U
S
B
D
I
A
G
N
O
S
T
I
C
R
F
R
S
S
I
S
G
N
L
S
T
A
T
U
S
C
O
N
F
I
G
m
i
c
r
o
h
a
r
d
S
Y
S
T
E
M
S
I
N
C
.
S
I
M
C
A
R
D
2.0 Quick Start
This QUICK START guide will walk you through the setup and process required to
access the WebUI configuration window and to establish a basic wireless connection
to your carrier.
Note that the units arrive from the factory with the Local Network setting configured
as ‘Static’ (IP Address 192.168.0.1, Subnet Mask 255.255.255.0, and Gateway
192.168.0.1), in DHCP server mode. (This is for the Ethernet Adapter on the back
of the IPn3G unit.
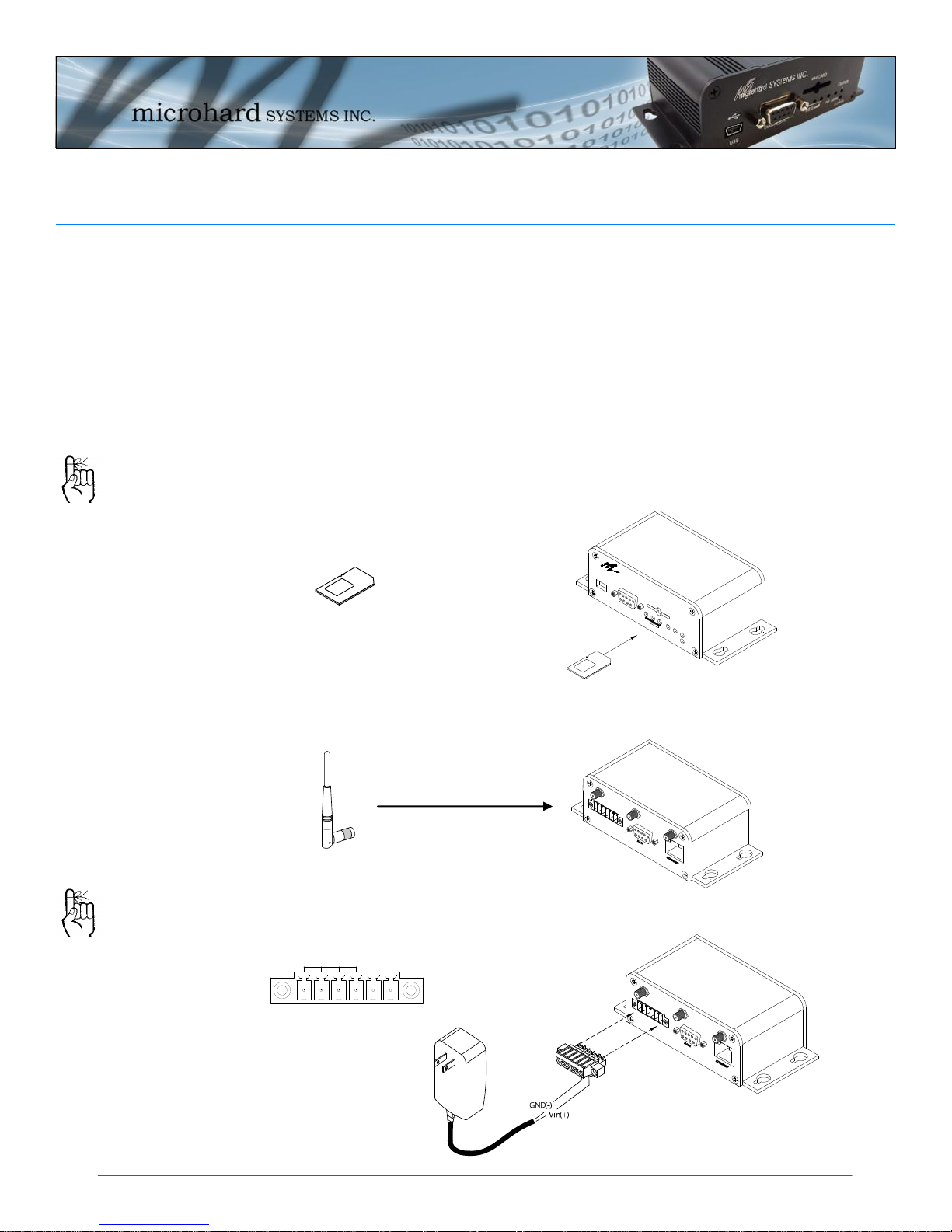
2.1 Installing the SIM Card
Before the IPn3G can be used on a cellular network a valid SIM Card for your
Wireless Carrier must be installed. Insert the SIM Card into the slot as shown
To reset to factory
defaults, press and
hold the CFG button
for 8 seconds with the
IPn3G powered up.
The LED’s will flash
quickly and the IPn3G
will reboot with factory
defaults.
below.
SIM Card Slot
2.2 Getting Started
Connect the Antenna’s to the applicable ANTENNA jack’s of the IPn3G.
Connect the Phoenix-Type Connector to the power adapter as shown below and
apply power to the
Use the MHS-supplied
power adapter or an
equivalent power
source.
© Microhard Systems Inc. 14
Main Antenna (SMA)
(GPS & Diversity not shown)
unit.
Page 15

2.0 Quick Start
Connect A PC configured for DHCP directly to the ETHERNET port of the IPn3G,
using an Ethernet Cable. If the PC is configured for DHCP it will acquire a IP Address from the IPn3G.
Open a Browser Window and enter the IP address 192.168.0.1 into the address
bar.
The factory default
network settings:
IP: 192.168.0.1
Subnet: 255.255.255.0
Gateway: 192.168.0.1
The factory default login:
User name: admin
Subnet: admin
It is always a good idea to
change the default admin
login for future security.
The IPn3G will then ask for a Username and Password. Enter the factory de-
faults listed below.
192.168.0.1
The Factory default login:
User name: admin
Password: admin
© Microhard Systems Inc. 15
Page 16
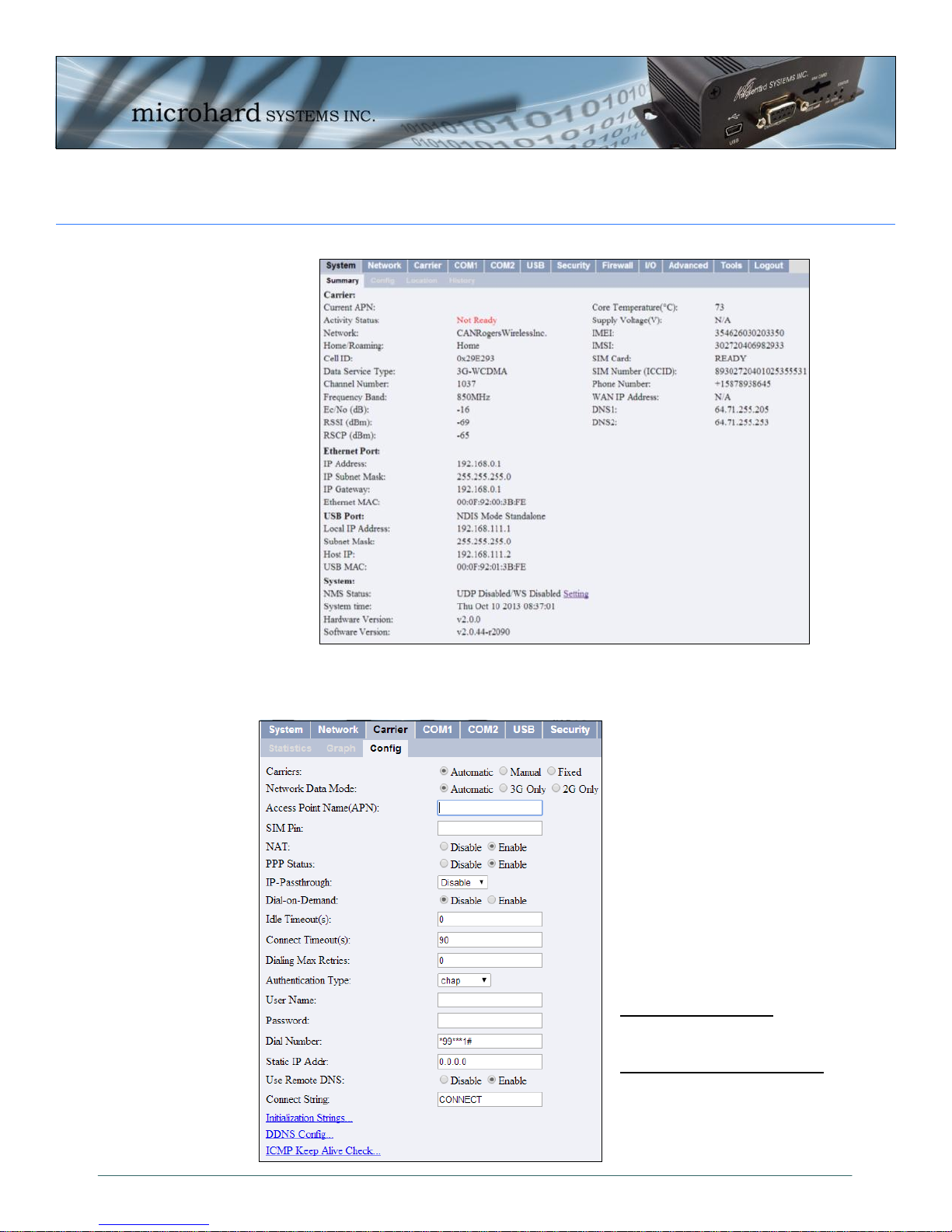
2.0 Quick Start
Once successfully logged in, the System Summary Window will be displayed.
To establish basic wireless connectivity with your carrier, the information in the
Carrier > Config menu must be completed as provided by your carrier.
Carriers may require different
information to be filled out.
Contact them for specific connection information.
For SIM Cards issued with Dynamic IP addresses most carriers simply require the correct
APN. SIM Cards assigned Static
public IP address often require
additional login details.
Wireless Carriers require the
following information:
Always Required:
Access Point Name (APN)
Some Carriers Require:
Authentication Type
User Name
Password
© Microhard Systems Inc. 16
Page 17
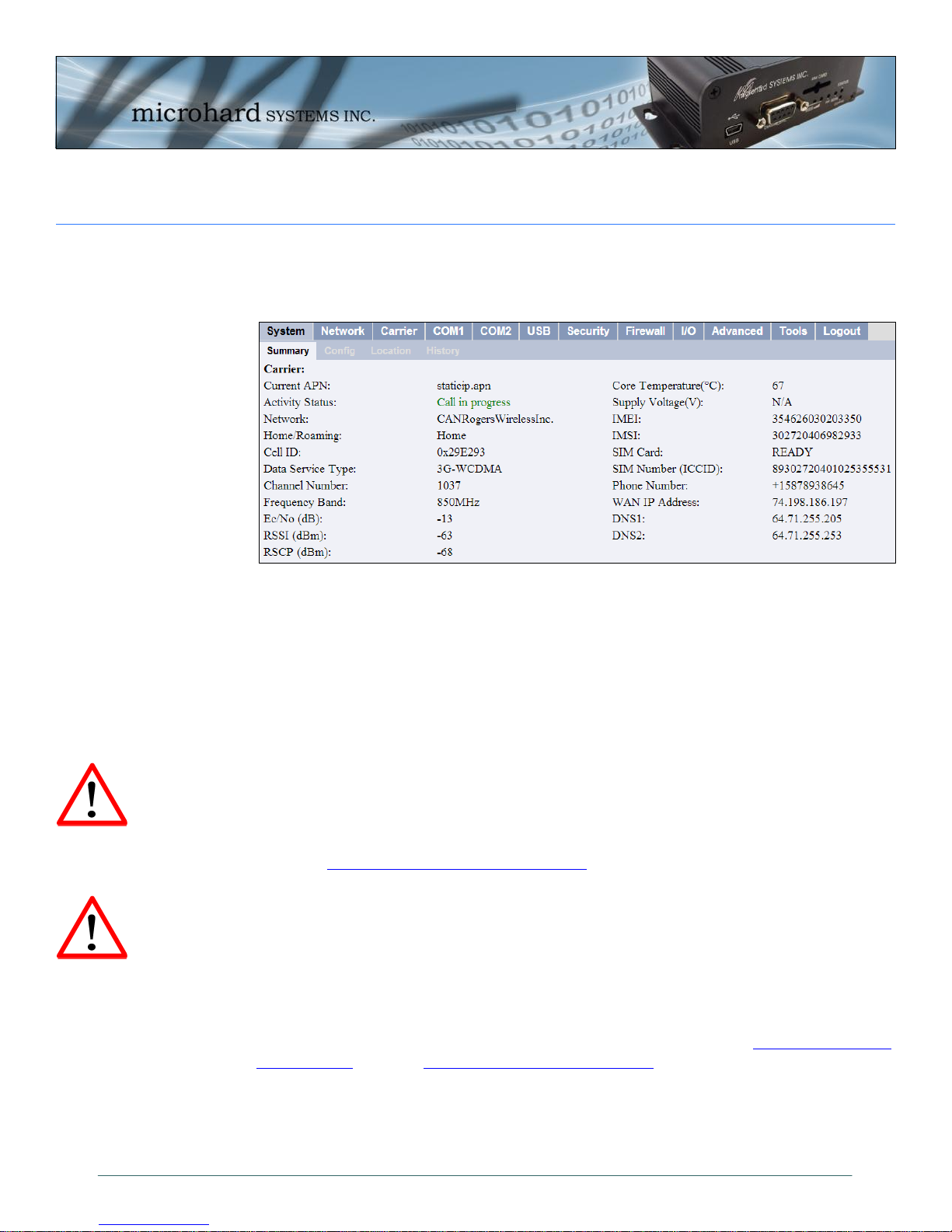
2.0 Quick Start
Verify connectivity with your Wireless Carrier by selecting Carrier > Statistics
or System > Summary. Your carriers name should appear next to the Network
entry and the Activity Status should read as: Call in progress
If you do not see “Call in Progress” you are not connected to or communicating
with your wireless carrier.
Check that the SIM card is installed correctly.
Verify that the proper antennas are installed correctly
Verify the APN assigned by the carrier.
Re-Enter the login details, if required by the carrier, to ensure any typing
You see “Call in Progress”, but no Internet Access. Check the WAN IP Address in
the Carrier > Statistics or System > Summary screens. If an IP Address is
not shown, check the APN and login details for errors.
Ensure the default
passwords are changed.
Set up appropriate firewall
rules to block unwanted
incoming data.
Refer to Section 4.0 WebUI Configuration to configure serial ports, USB, or any
security or firewall features required on the IPn3G.
Ensure that all default passwords are changed to limit access to the modem.
For best practices and to limit data charges it is critical to properly set up the
firewall. (Especially important for Public Static IP addresses.)
To access devices attached to the IPn3G remotely, see Appendix C: IP-
Passthrough, and/or Appendix D: Port Forwarding for working examples of how
to configure your devices and the IPn3G to provide remote connectivity.
errors.
© Microhard Systems Inc. 17
Page 18

3.0 Hardware Description
3.1 IPn3G Hardware
The IPn3G provides a fully enclosed, stand alone modem, requiring only cabled connections.
The IPn3G can be used on a table top like surface, or using the mounting holes provided can be
mounted anywhere for a permanent solution.
Power
Data (Serial) Interface
Ethernet Interface
USB Interface
LED Indicators
Antenna’s (Main, GPS, Diversity)
Image 3-1: IPn3G Front View
Image 3-2: IPn3G Back View
© Microhard Systems Inc. 18
Page 19
IPn3G-ENC
Top View
microhard SYSTEMS INC.
SIM CARD
RSSI
DIAGNOSTIC
RF SGNL
STATUS
CONFIG
USB
RS485/422
Vin+
GND
RxA
RxB
TxA
TxB
DATA
ETHERNET
ANTENNA
GPS
RX DIV
3.0 Hardware Description
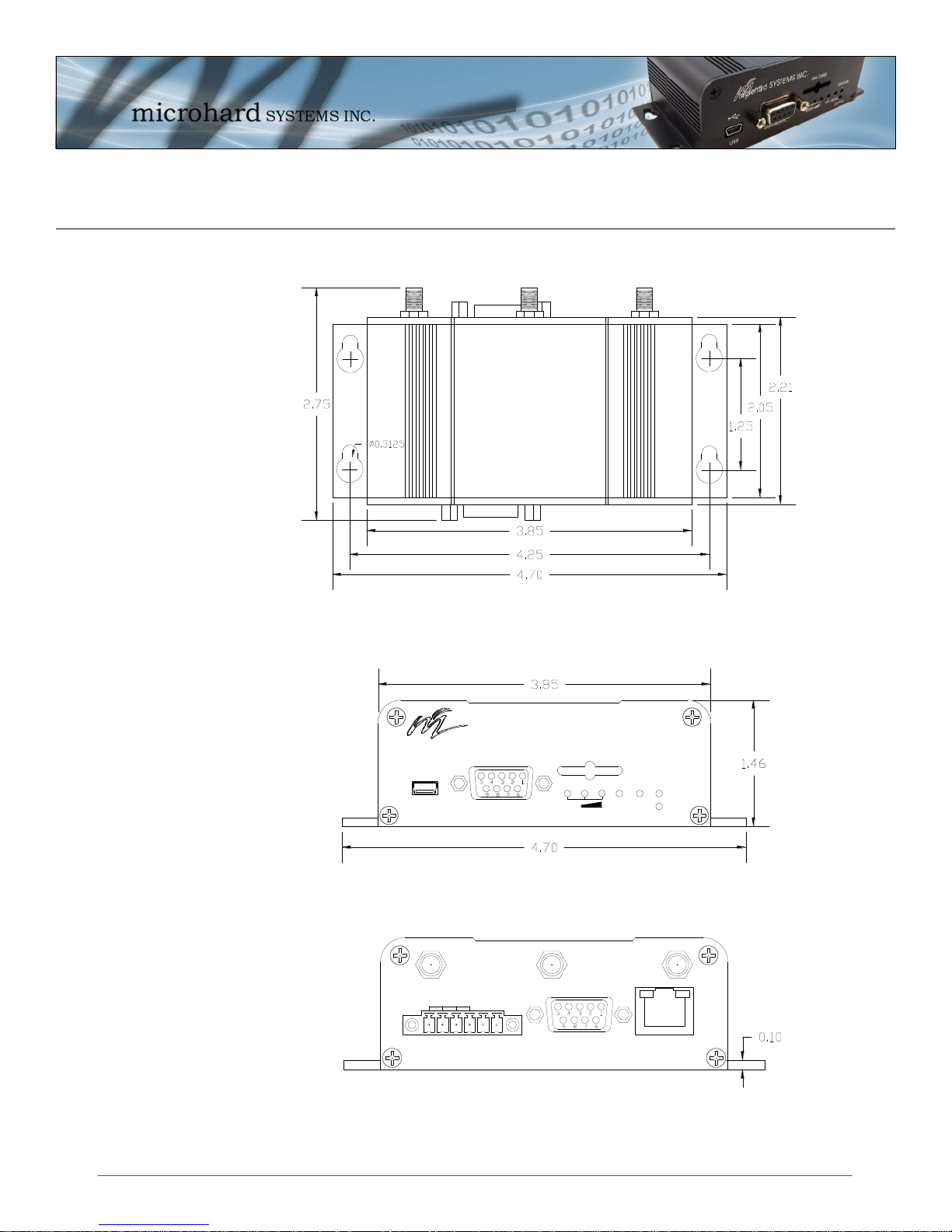
3.1.1 IPn3G Mechanical Drawings
Drawing 3-1: IPn3G Top View
© Microhard Systems Inc. 19
Drawing 3-2: IPn3G Front View
Image 3-3: IPn3G Back View
Notes: The dimension unit is inches.
Page 20
microhard SYSTEMS INC.
SIM CARD
RSSI
DIAGNOSTIC
RF SGNL
STATUS
CONFIG
USB
3.0 Hardware Description
3.1.2 Connectors and Indicators
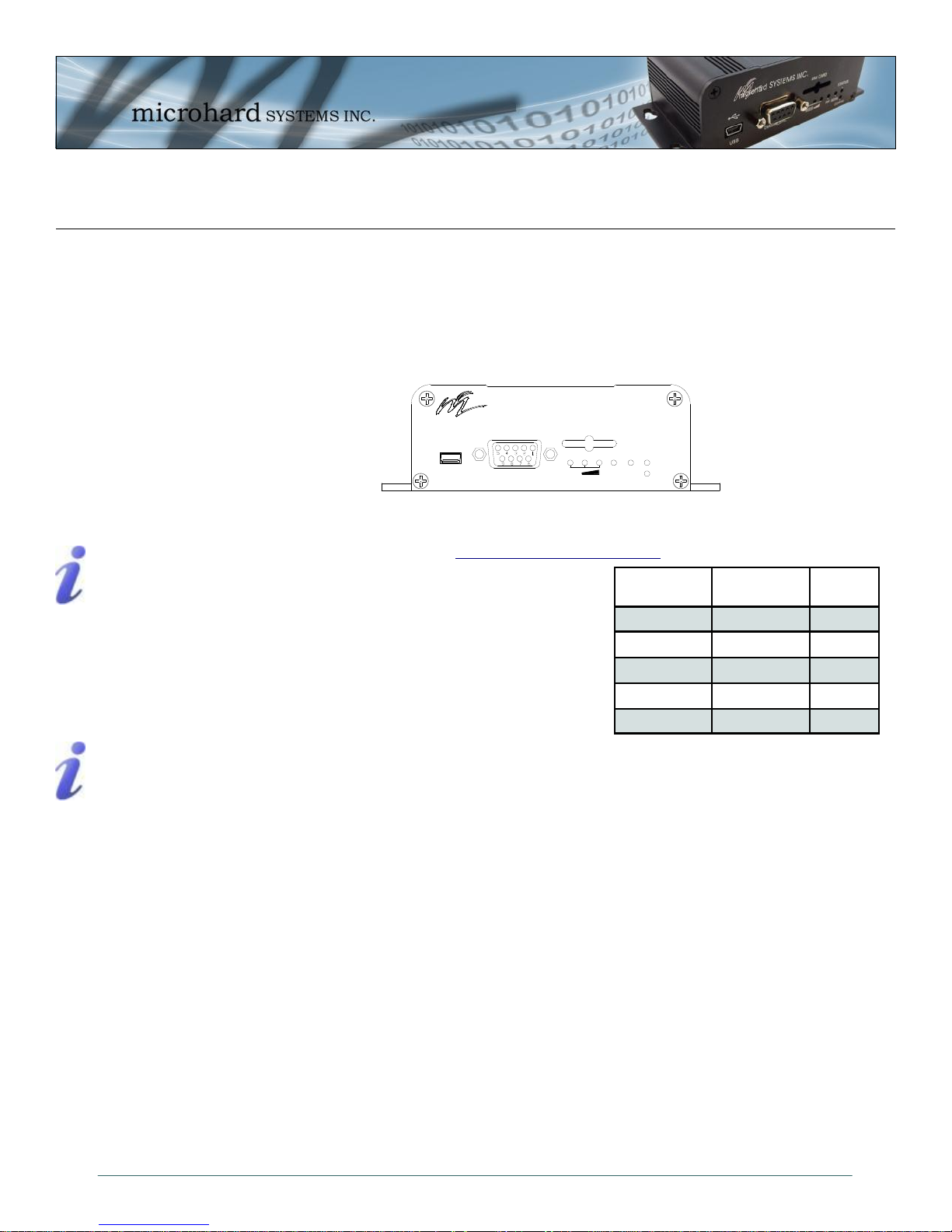
3.1.2.1 Front
On the front of the IPn3G is the USB port, DIAGNOSTIC port, CONFIG Button, RSSI, STATUS, RF and
SGNL LED’s as described below:
The USB port can be used for: (See Section 4.1.7 USB Configuration)
Console Port
Data Mode
Windows USB driver
downloads are available
to registered users
from:
microhardcorp.com/
support
The Diagnostic port (RS232) is used for:
NDIS Mode
AT Command Interface at 115.2kbps and
HyperTerminal (or equivalent).
User data (RS232 - RxD, TxD, and SG)
Digital I/O—Input Pin 7, Output Pin 8
CONFIG (Button) - Holding this button depressed while powering-up the IPn3G will boot the unit into
FLASH FILE SYSTEM RECOVERY mode. The default IP address for system recovery (only - not for nor-
Digital I/O is only
available and has been
implemented on units
shipped after June 1,
2012
mal access to the unit) is static: 192.168.1.39.
If the unit has been powered-up for some time (>1 minute), depressing the CFG Button for 8 seconds will
result in FACTORY DEFAULTS being restored, including a static IP address of 192.168.0.1. This IP address is useable in a Web Browser for accessing the Web User Interface.
RF LED (Red) - When connected to a 2G/EDGE or 3G-WCDMA Network, the RF LED indicates
a transmission burst. When connected to a 3G/HSPA Network the LED has no function.
SGNL LED (Green) - When illuminated, the SGNL LED indicates that the modem is connected and syn-
chronized with a wireless carrier.
Receive Signal Strength Indicator (RSSI) (3x Green) - As the received signal strength increases,
starting with the furthest left, the number of active RSSI LEDs increases. If the measured signal strength is
less than –110dBm no LED’s will be illuminated. If the signal is greater than –105dBm, 1 LED will be on, -
100dBm equals 2 LED’s, and any signal greater than –95dBm will show all 3 RSSI LED’s to be ON.
STATUS LED (Red) - Upon initial application of power the STATUS LED will be illuminated for approxi-
© Microhard Systems Inc. 20
mately 20 seconds, after which time it will being to blink slowly (loading) for an additional 25 seconds, then
stay ON ‗solid‘ (indicating it has achieved its specific operational status).
Drawing 3-4: IPn3G Front View
Table 3-1: Diagnostic Port RS232 Pin Assignment
Signal
Name
RXD 2 O
TXD 3 I
SG 5
Digital In 7 I
Digital Out 8 O
PIN
#
Input or
Output
Page 21
RS485/422
TxB -
TxA -
RxB -
RxA -
GND -
Vin+ -
RS485/422
Vin+
GND
RxA
RxB
TxA
TxB
DATA
ETHERNET
ANTENNA
GPS
RX DIV
3.0 Hardware Description
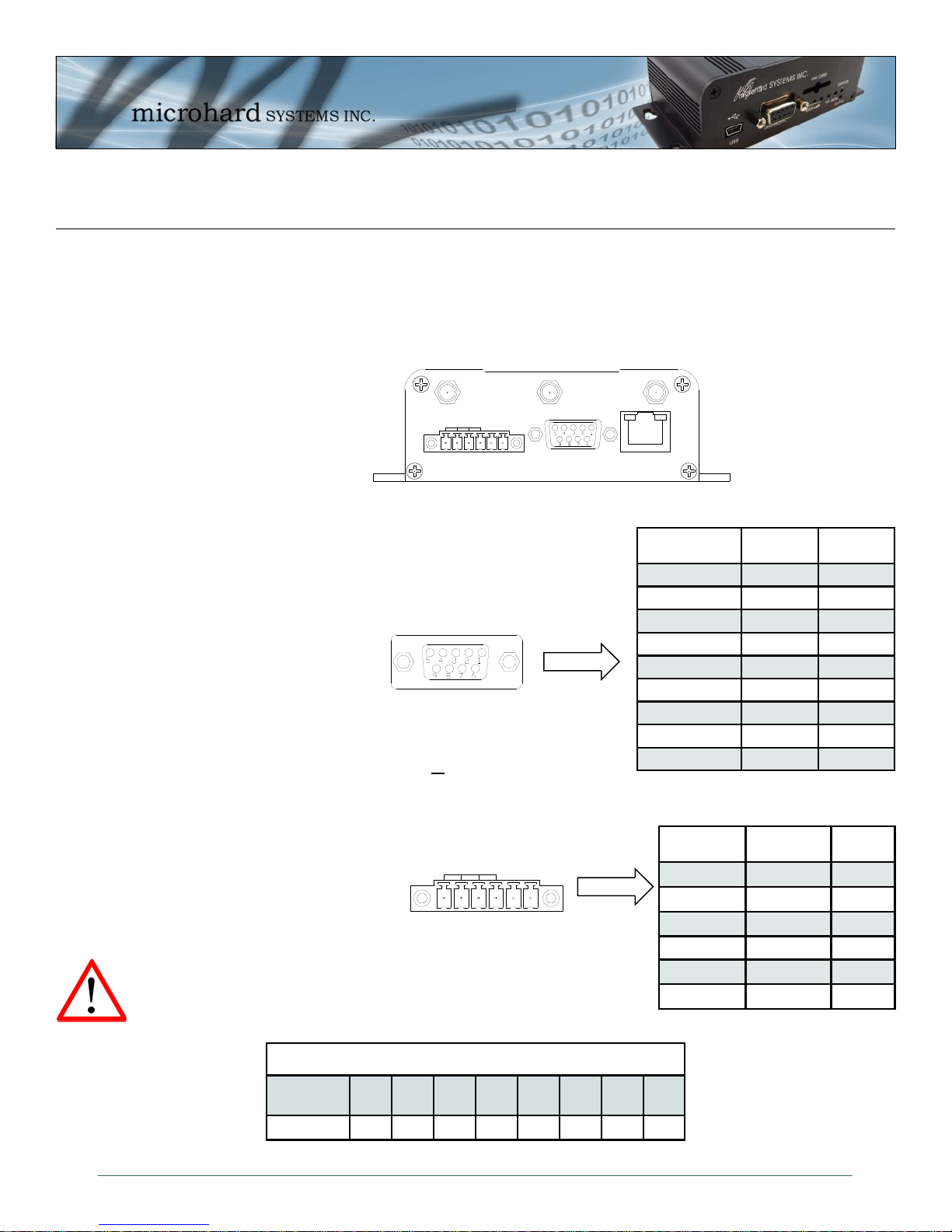
3.1.2 Connectors and Indicators
3.1.2.2 Rear
On the back of the IPn3G is the Data port, RS485/422 interface, as well as the power connections. The
unit also has the SMA(F) connectors for the Main (TX/RX), GPS and the Diversity (RX) antenna’s.
The DATA (RS232 Port (DCE)) on the rear
of the circuit board is used for:
RS232 serial data (300-921kbps).
The RS422/485 Port is used to interface the Nano
Development Board to a DTE with the same
interface type. Either the RS232 or RS422/485 interface is used
for data traffic.
Vin+/Vin– is used to power the unit. The input Voltage range
is 7-30 Vdc.
PoE*– The IPn3G can also be powered using Passive PoE on the
Ethernet Port, via a PoE injector.
Caution: Using a
power supply that
does not provide
proper voltage may
damage the modem.
© Microhard Systems Inc. 21
Source
Voltage
9 - 30 Vdc Data Data Data DC+ DC+ Data DC- DC-
Drawing 3-5: IPn3G Rear View
Table 3-3: Data RS422/485 / Vin Pin Assignment
Ethernet RJ45 Connector Pin Number
1 2 3 4 5 6 7 8
Table 3-4: Ethernet PoE Connections
Name Data Port Input or
DCD 1 O
RXD 2 O
TXD 3 I
DTR 4 I
SG 5
DSR 6 O
RTS 7 I
CTS 8 O
RING 9 O
Table 3-2: Data RS232 Pin Assignment
Green Conn.
Pin No.
6 TxB (D+) O
5 TxA (D-) O
4 RxB (R+) I
3 RxA (R-) I
2 Vin -
1 Vin + I
Name Input or
Output
Output
*PoE only available on models shipped after March 1,
2013*
Page 22

4.0 WebUI Configuration
The Web User Interface (WebUI) is a browser based configuration method that allows a user to use a
graphical interface to configure, test and troubleshoot a IPn3G unit. Any standard web browser can be
used and no additional software is required. Using the Web User Interface a user can:
Remotely or locally configure a IPn3G unit, including:
Network settings
Radio configuration
Serial Port configuration
Security
USB
Firewall
I/O
VPN
Retrieve unit revisions
Update system firmware
Much more...
In this section, all aspects of the Web Browser Interface, presented menus, and available configuration
options will be discussed.
© Microhard Systems Inc. 22
Page 23
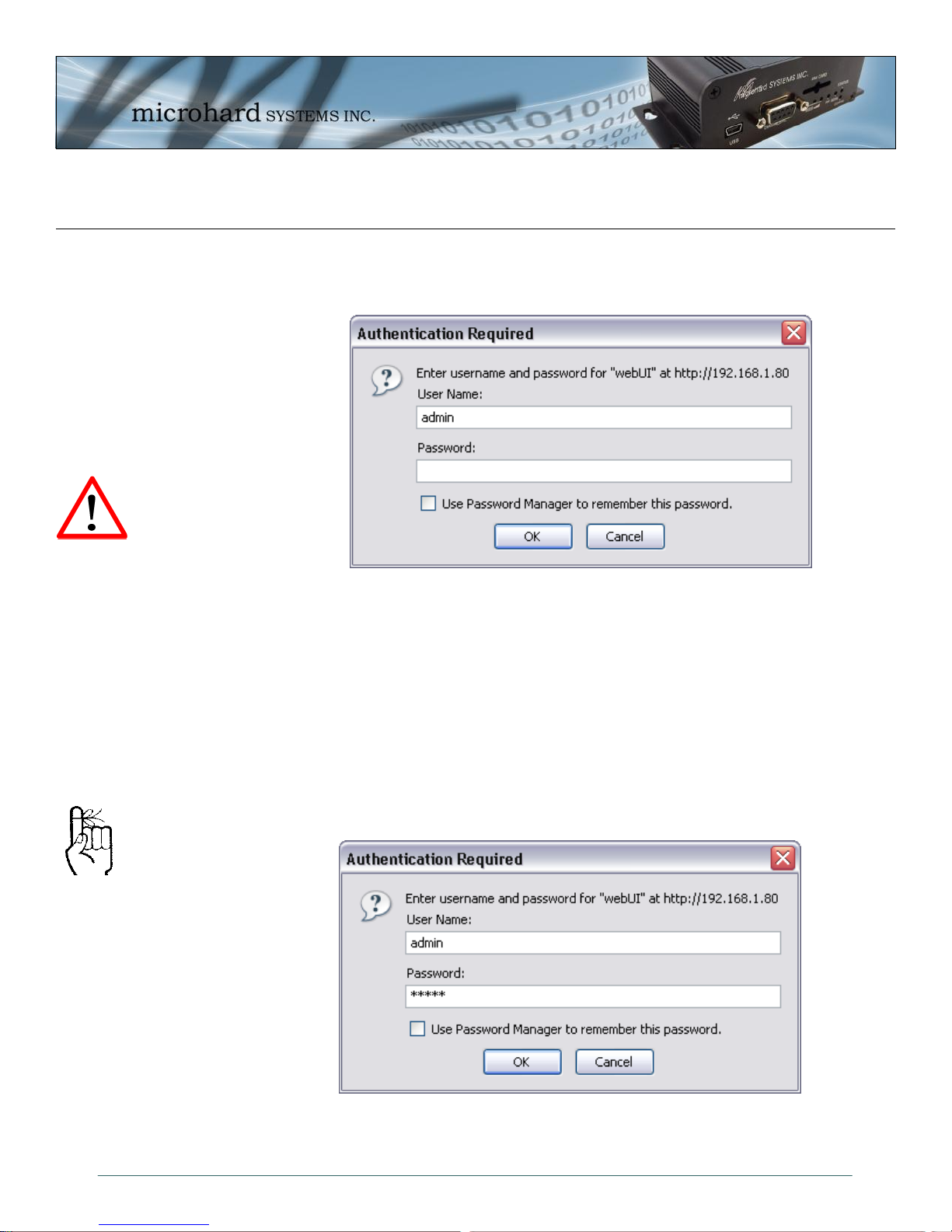
4.0 WebUI Configuration
4.1 Logon Window
Upon successfully accessing the IPn3G using a Web Browser, the Logon window will appear.
For security, do not
allow the web browser
to remember the User
Name or Password.
It is advisable to
change the login
Password (see Section
4.1.8.1). Do not
FORGET the new
password as it cannot
be recovered.
The factory default User Name is: admin
The default password is: admin
Note that the password is case sensitive. It may be changed (discussed further along in this section), but
once changed, if forgotten, may not be recovered.
When entered, the password appears as ’dots’ as shown in the image below. This display format prohibits
others from viewing the password.
The ‘Remember my password’ checkbox may be selected for purposes of convenience, however it is
recommended to ensure it is deselected - particularly once the unit is deployed in the field - for one
primary reason: security.
Image 4-1: Logon Window
© Microhard Systems Inc. 23
Image 4-2: Logon Window With Password Input
Page 24
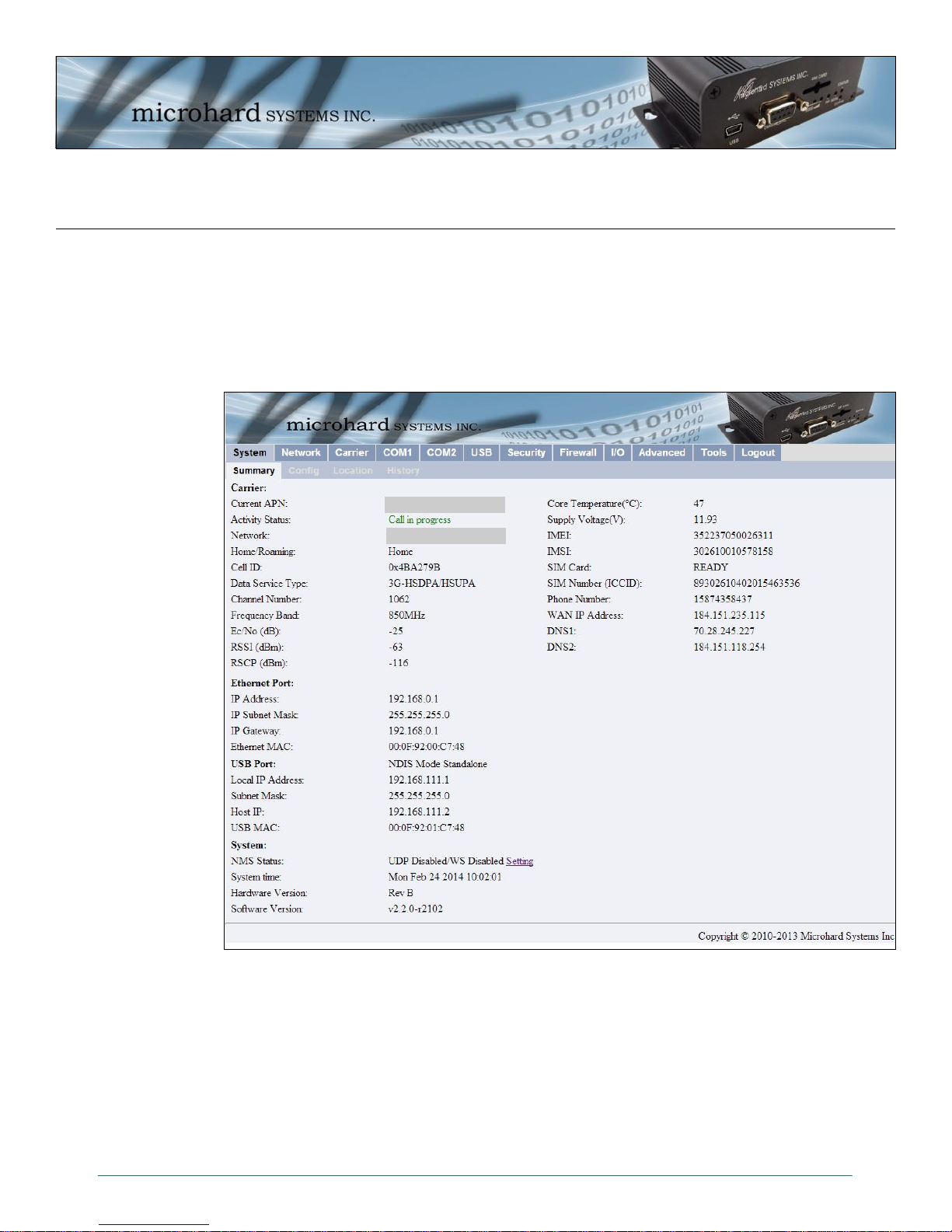
4.0 WebUI Configuration
4.2 System
4.2.1 System > Summary
The System Summary window displays an overview of the current IPn3G configuration. When initially
logging into the unit, this will be the first window displayed, allowing a user to quickly identify configuration
information.
Carrier APN
Carrier Name
The System Summary window displays information about the wireless carrier as well as local network,
USB and System information:
Carrier: Activity Status, Network, WAN IP, Phone Number, SIM Card info etc
Ethernet Port: Local Ethernet Port information of rear RJ45 Connector.
USB Port: USB Port information, NDIS IP Address etc.
System: Hardware and Software versions and System time.
© Microhard Systems Inc. 24
Image 4-3: System Summary Window
Page 25
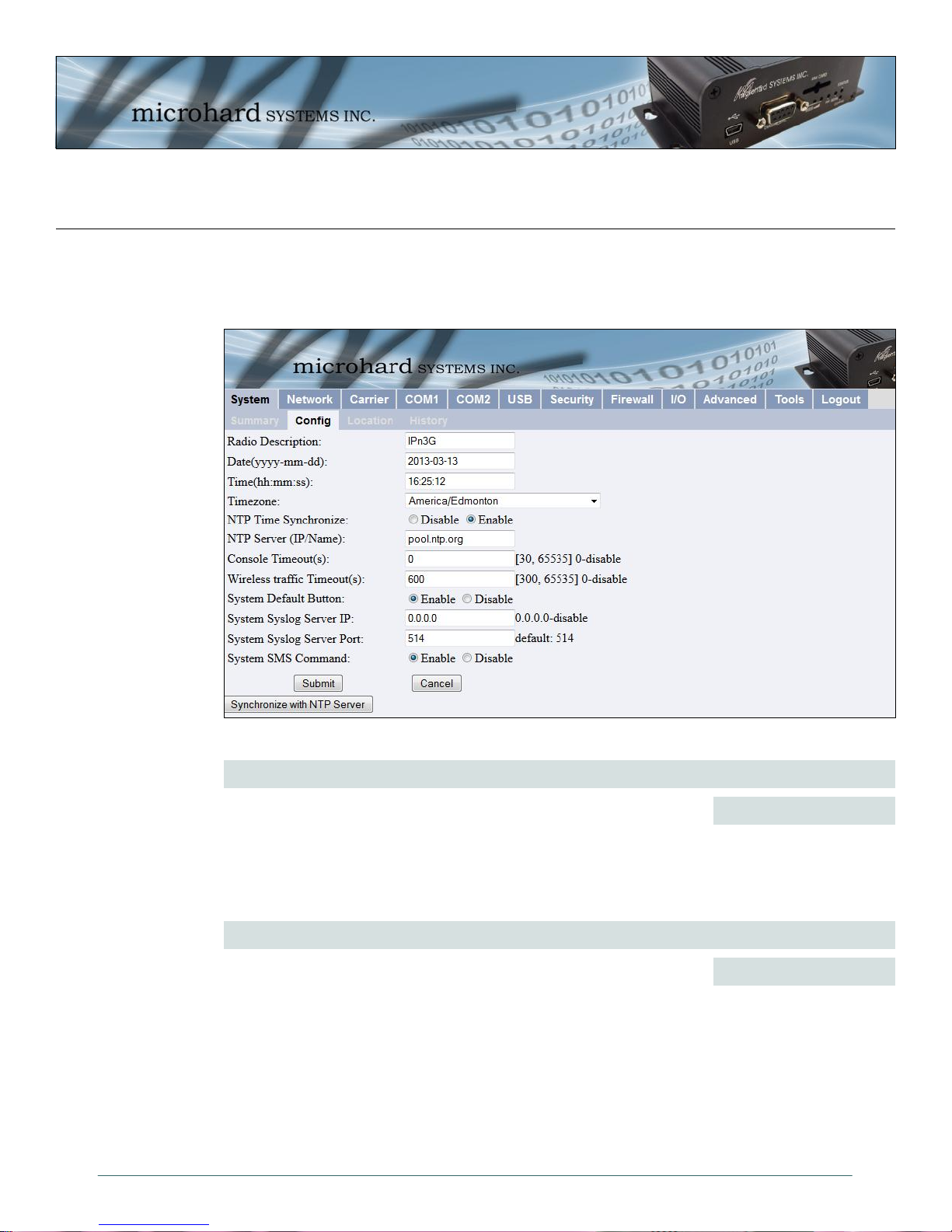
4.0 WebUI Configuration
4.2.2 System > Config
The System Config submenu allows the configuration of the Radio Description, the Time and Date,
including NTP time server parameters. As well as the Console and Wireless Traffic timeouts.
Image 4-4: System Config Window
Radio Description
The Radio Description is simply a convenient identifier for a specific IPn3G,
e.g. Pump Station 5, 123 Main Street, etc. This feature is most welcome
when accessing units remotely: a convenient cross-reference for the unit’s
IP address. This ‘name’ appears in all menu windows. It has no bearing
on the unit’s operation.
Date (yyyy-mm-dd)
The calendar date may be entered in this field. Note that the entered value
is lost should the IPn3G lose power for some reason.
Values (Characters)
Default is model-dependent
up to 30 characters
Values (2010-08-05)
valid date values, where
yyyy = 4-digit year
mm = 2-digit month
dd = 2-digit day
© Microhard Systems Inc. 25
Page 26

4.0 WebUI Configuration
NTP may be used to
synchronize the time in
the IPn3G within a
network to a reference
time source.
The calendar date may be entered in this field. Note that the entered value
is lost should the IPn3G lose power for some reason.
The Timezone field allows you to set the time zone in the IPn3G. Select the
time zone from the dropdown list that matches your location. Time zones
are sorted by UTC (+/-) offset.
Note that if NTP Server Status is ENABLED, the ‘Synchronize with NTP
Server’ soft button on the System Configuration menu will be available for
use.
Leave as DISABLED (default) if a server is not available.
IP address or domain name for NTP server (on local LAN or website
(provided that Internet access is available)) is to be entered in this field if
the NTP Server Status is configured as ENABLED.
Time (hh:mm:ss)
Values (11:27:28)
hh = 2-digit hours
mm = 2-digit minutes
ss = 2-digit seconds
Timezone
Values (List)
Select the applicable time
zone from the dropdown
list.
NTP Time Synchronize
Values (Selection)
Disable
Enable
NTP Server (IP/Name)
Values (0.0.0.0)
valid NTP server IP
address or ‘name’
This value determines when the console connection (made via COM2) will
timeout after becoming inactive.
The Wireless Traffic Timeout will reset the unit if there has been no RF
activity in the configured time. 0 = Disabled (default)
Enabled by default, when the CONFIG button on the front of the IPn3G is
held down for 10s while the unit is powered up, the unit will reset and all
settings will be reset to factory defaults. When disabled the unit will reset,
but the settings will not be overwritten.
© Microhard Systems Inc. 26
Console Timeout (s)
Values (seconds)
60
0-65535
Wireless Traffic Timeout (s)
Values (seconds)
600
300-65535
System Default Button
Values (Selection)
Enable
Disable
Page 27
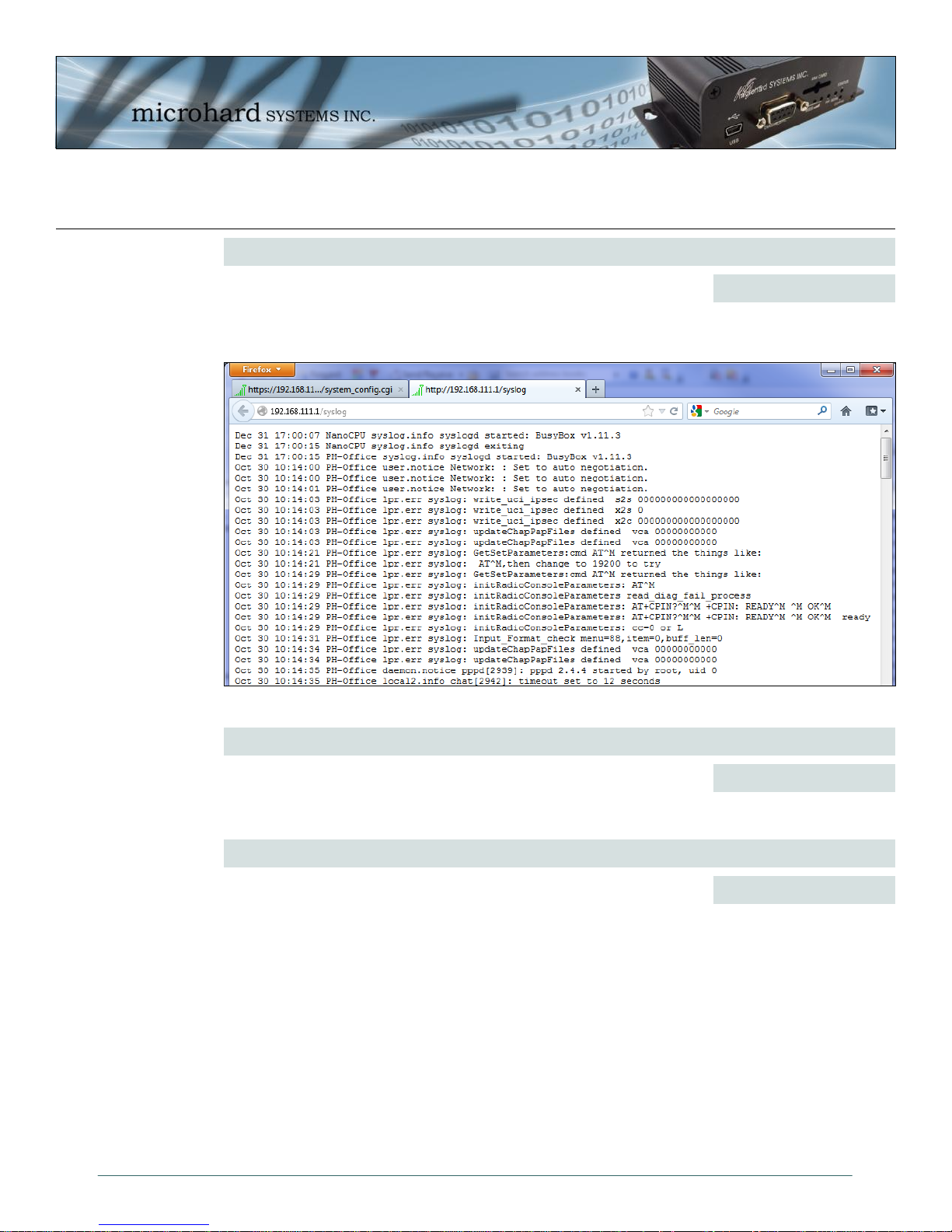
4.0 WebUI Configuration
System Syslog Server IP
The IPn3G can report system level events to a third party Syslog server,
which can be used to monitor events reported by the IPn3G. The raw event
syslog can be view by entering the following URL into the web browser
http://X.X.X.X/syslog, Where X.X.X.X is the IP address of the IPn3G.
Image 4-5: Syslog
IP Address
0.0.0.0
System Syslog Server Port
Enter the UDP listening port of the Syslog Server. The default port number
is generally 514, but could vary from Server to Server.
UDP Port
514
System SMS Command
This option allows a user to enable or disable to use of the following SMS
commands to reboot or trigger events in the IPn3G:
MSC#REBOOT Reboot system
MSC#MIOP1 open I/O ouput1
MSC#MIOC1 close I/O ouput1
MSC#EURD0 trigger event report0
MSC#EURD1 trigger event report1
MSC#EURD2 trigger event report2
MSC#NMS trigger NMS UDP report
MSC#WEB trigger NMS webclient service immediately
MSC#PSCLOSE close power saving mode
MSC#PSVOL enable/switch to supply voltage power mode
MSC#PSTIMER enable/switch to timer power mode
MSC#PSSNIFF enable/switch to sniff power mode
MSC#APN set APN and reconnect. MSC=apn[,usr][,pwd]
© Microhard Systems Inc. 27
MSC#GPSR0 trigger gps report0
MSC#GPSR1 trigger gps report1
MSC#GPSR2 trigger gps report2
MSC#GPSR3 trigger gps report3
Values (Selection)
Enable / Disable
Page 28
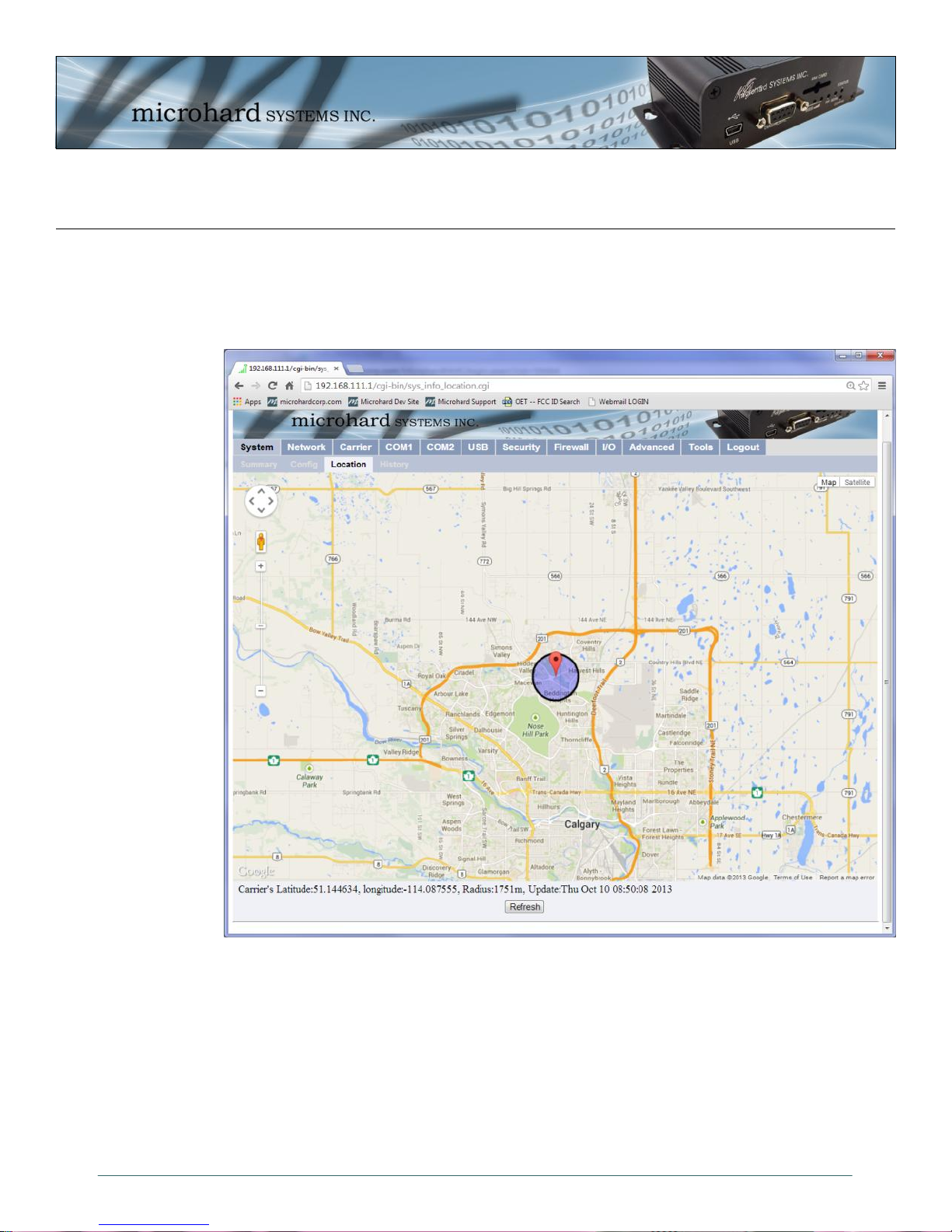
4.0 WebUI Configuration
4.2.3 System > Location
The Location menu shows current modem location with online map and exact GPS Coordinate. If the GPS
is not valid, it uses the Cell Tower ID that the unit is currently connect to, to approximate the general
location of the IPn3G.
© Microhard Systems Inc. 28
Image 4-6: System > Location
Page 29
4.0 WebUI Configuration
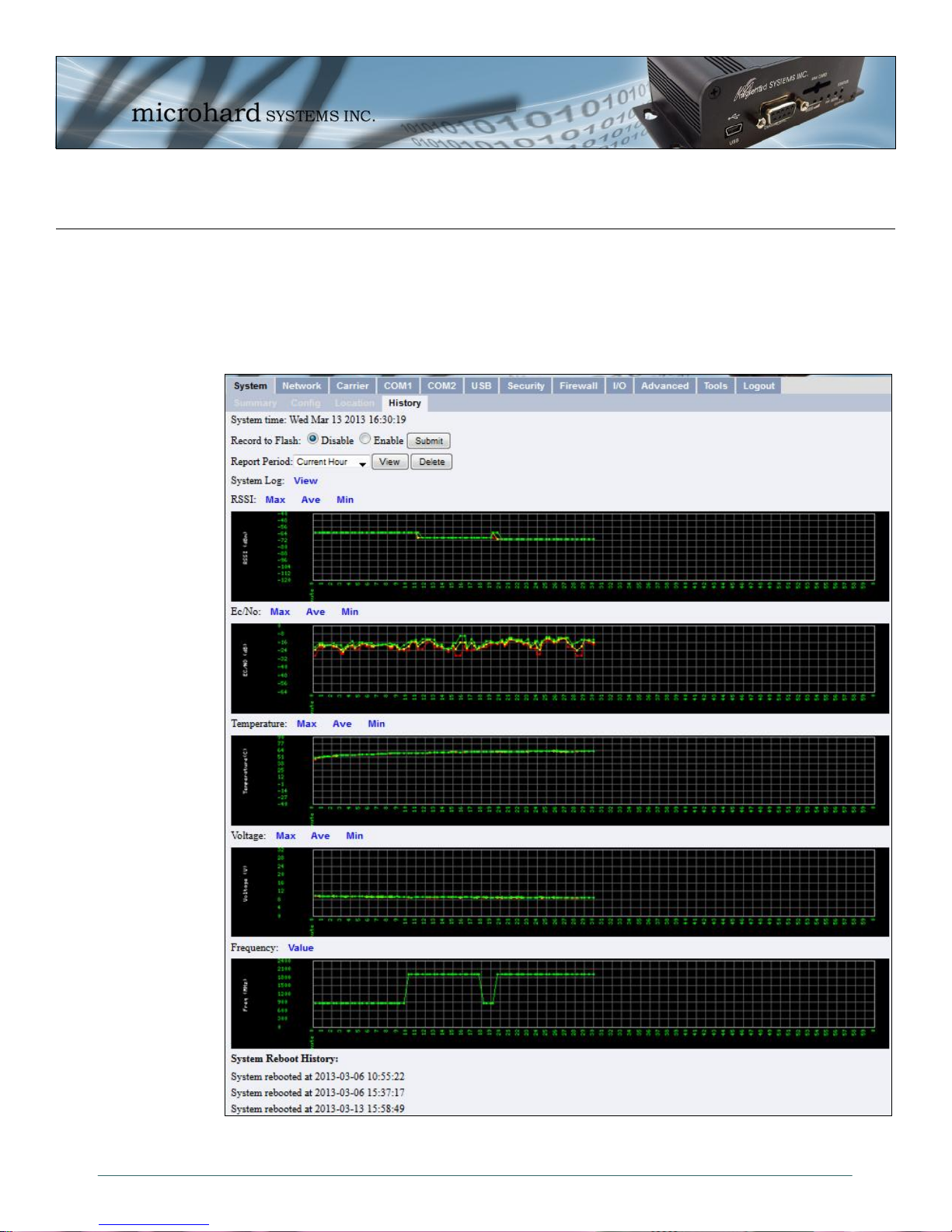
4.2.4 System > History
The History menu shows a graphical history of RSSI, Ec/No, Temperature, Voltage and Frequency of the
Cellular module. Data for the current hour, as well as a specific 24 hour period of a calendar date. Clicking
the Max, Ave and Min links will show the raw data used to plots the points on the graphs. The data points
are optionally stored in non-volatile (flash) memory, so data is saved even when the IPn3G is restarted or
power is lost.
© Microhard Systems Inc. 29
Image 4-7: System > Location
Page 30
4.0 WebUI Configuration
4.3 Network
4.3.1 Network > Summary
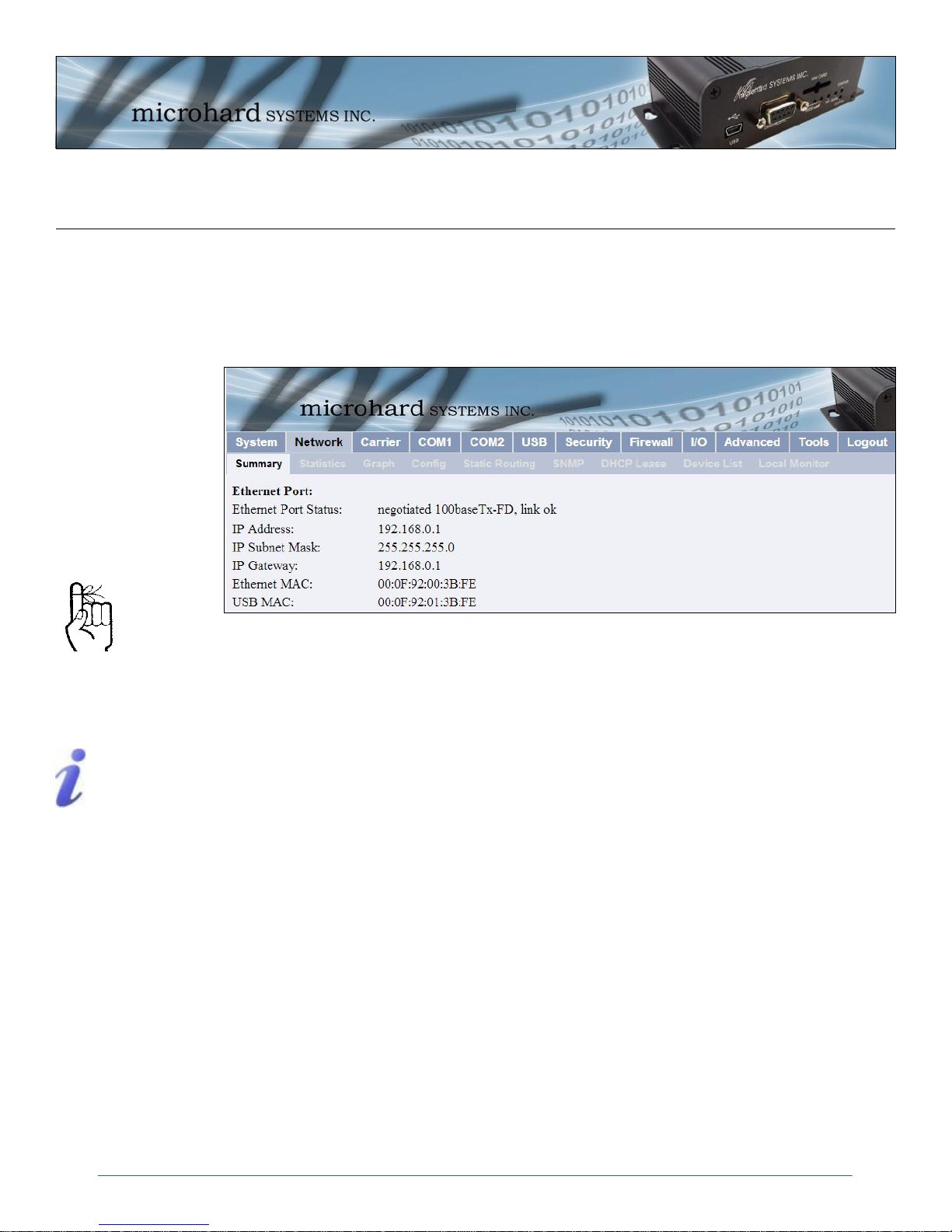
The Network > Summary tab gives an overview of the configuration of the Ethernet port on the IPn3G. This
port is the RJ45 port located on the back of the IPn3G.
Within any IP network,
each device must have its
own unique IP address.
A SUBNET MASK is a bit
mask that separates the
network and host (device)
portions of an IP address.
The ‘unmasked’ portion
leaves available the
information required to
identify the various
devices on the subnet.
Image 4-8: Network Configuration , Local IP Configuration Submenu
Ethernet Port Status: The Ethernet port status shows the type and status of the local Ethernet Link.
IP Address: This is the currently configured logical IP address of the IPn3G. This IP address must
be set statically in the Network > Config tab. This is generally set to a Private IP
address for a local network.
IP Subnet Mask: The IP Subnet Mask is the current Subnet Mask being used by the unit to define the
subnet and host address of the IPn3G.
IP Gateway: The IP Gateway sets the default gateway for traffic leaving the IPn3G.
Ethenet MAC: This is the physical MAC address of the RJ45 Ethernet Port of the back of the IPn3G
USB MAC: For quick reference, this is the physical MAC address of the USB port on the front of
the IPn3G, when it is configured as a NDIS Ethernet Interface. See the USB section
for more information.
© Microhard Systems Inc. 30
Page 31

4.0 WebUI Configuration
4.3.2 Network > Statistics
The Network > Statistics tab displays a variety of parameters which apply to the traffic through, and status
of, the physical Ethernet port (hardware interface) on the rear of the IPn3G.
Received and Transmitted information are applicable to the local data traffic into and out of the IPn3G,
respectively. Errors which are counted include alignment, frame check sequence (FCS), frame too long,
and internal MAC. The dropped packet count could increment if, for example, the network layer was too
busy to accept the data.
The FIFO errors are related to interface-specific hardware.
Collisions occur on all Ethernet networks being that Ethernet operates as a logical bus. The amount of
collisions is typically related to the number of devices on the attached network and the amount of data
being moved.
The Transmit Carrier count relates to carrier sense errors.
© Microhard Systems Inc. 31
Image 4-9: Network Statistics
Page 32

4.0 WebUI Configuration
4.3.3 Network > Graph
The Network > Graph tab displays a graphical display of the Ethernet Traffic on the Ethernet interface of
the IPn3G.
LAN (eth0) Shows an overview of all data sent or received by the IPn3G at the physical
LAN (eth0) / hourly Shows the traffic volumes (TX = green, RX = grey) at hourly intervals during
LAN (eth0) / daily Shows the total data received and transmitted for the day, as well as the
LAN (eth0) / monthly Shows the total data received and transmitted for the current month, as well as
LAN (eth0) / Top 10 Show the top 10 days with the most data sent or received.
Ethernet port on the rear of the unit. A summary of the data of the current day
and the current month is shown.
the current 24 hour period. This could be useful to see when the most or least
amount of traffic is present.
average rate of data.
the average rate of data.
© Microhard Systems Inc. 32
Image 4-10: Network Graph
Page 33

4.0 WebUI Configuration
4.3.4 Network > Config
The Network > Config tab allows the configuration of the Ethernet port on the IPn3G (Rear RJ45). This port
is configured as static port and must be configured by the user if the default values are not to be used. By
default this port acts as a simple DHCP server, allowing the IPn3G to assign IP addresses and enable
communication to attached devices. Caution must be taken not to connect the IPn3G to an existing
network where a DHCP server may already be running.
Within any IP network,
each device must have its
own unique IP address.
A SUBNET MASK is a bit
mask that separates the
network and host (device)
portions of an IP address.
The ‘unmasked’ portion
leaves available the
information required to
identify the various
devices on the subnet.
A GATEWAY is a point
within a network that acts
as an entrance to another
network.
In typical networks, a
router acts as a gateway.
Image 4-11: Network Configuration , Local IP Configuration Submenu
Enter a valid IP Address. The default IP address for the Ethernet Port on
the IPn3G is 192.168.0.1.
For a small private network with IP addresses appearing similar to
192.168.1.xx (Class C address), the standard 255.255.255.0 subnet mask
may be applicable.
If the IPn3G units are integrated into a network which has a defined
gateway, then, as with other hosts on the network, this gateway’s IP
address will be entered into this field.
IP Address
Values
192.168.0.1
IP Subnet Mask
Values
255.255.255.0
IP Gateway
Values
192.168.0.1
© Microhard Systems Inc. 33
Page 34

4.0 WebUI Configuration
Ethernet Port Mode
This option allows a user to select between Auto Negotiation (10/100), or
Fixed. If fixed is selected, additional options appear below.
This option allows a user to select between Auto Negotiation (10/100), or
Fixed. If fixed is selected, additional options appear below.
Choose between full and half duplex.
The ARP Cache timeout allows the configuration of how long a ARP entry
stays in the ARP table.
Values (selection)
Auto Negotiation
Fixed
Ethernet Port Speed
Values (selection)
100MBit/s / 10MBit/s
Ethernet Port Duplex
Values (selection)
Full / Half
ARP Cache Timeout(s)
Values (seconds)
60
DHCP Server Status
Prior to enabling this
service, verify that there
are no other devices either wired (e.g. LAN) or
wireless (e.g. another
unit) with an active DHCP
SERVER service.
(The Server issues IP
address information at the
request of a DHCP Client,
which receives the
information.)
Choose to enable or disabled the DHCP Server service. Devices on the
network, which are intended to receive IP address information from this
DHCP Server, must have their local IP settings set for ‘DHCP’ (as opposed
to ‘static’). The default is Enabled.
DHCP Starting/Ending Address
Use the Starting and Ending Address fields to define the range that the
DHCP server will assign IP Addresses. (also known as the address pool).
Values
Disable
Enable
Values
192.168.0.100 to
192.168.0.200
DHCP Lease Time
This is the amount of time a device can lease an IP Address from the
IPn3G before it must renew or obtain a new IP address. This option allows
the user to specify if the lease time specified in in seconds, minutes, hours
etc.
© Microhard Systems Inc. 34
Values (selection)
Seconds
Minutes
Hours
Days
Weeks
Page 35

4.0 WebUI Configuration
DNS Mode
Select between Static (user must specify DNS server addresses), or
Automatic (the DNS servers are assigned by the Carrier).
If set for Static, a user would enter the IP Address of the desired primary
DNS server in this field. If set for automatic, this field will be populated by
the currently assigned DNS address.
If set for Static, a user would enter the IP Address of the desired alternate
DNS server in this field. If set for automatic, this field will be populated by
the currently assigned DNS address.
It may be desirable to ensure specific devices always obtain the same IP
address from the DHCP service. Enter the MAC address of that device in
this field.
Values (selection)
Static
Automatic
Preferred DNS Server
Values (IP Address)
(current DNS Server)
Alternate DNS Server
Values (IP Address)
(current DNS Server)
Binding MAC
Values (MAC)
00:00:00:00:00:00
Binding IP
It may be desirable to ensure specific devices always obtain the same IP
address from the DHCP service. Enter the IP Address to be assigned to
that device here.
© Microhard Systems Inc. 35
Values (IP Address)
0.0.0.0
Page 36

4.0 WebUI Configuration
4.3.5 Network > Static Routing
The Network > Static Routing Menu, allows for the user to add static routes to the IPn3G. Static routes can
be used to inform IPn3G of networks that are not directly attached.
Enter the destination IP Address and subnet mask of the remote network
for which the data is intended.
Enter the IP Address of the next hop to the destination network.
Select the interface from which the destination network is available. LAN
refers to the network attached locally through the RJ45, and the WAN is
the Cellular network.
© Microhard Systems Inc. 36
Image 4-12: Network Configuration , Local IP Configuration Submenu
Destination IP / Subnet Mask
Values (IP Address)
0.0.0.0 / 255.255.255.0
Default Gateway
Values
0.0.0.0
Interface
Values (selection)
WAN / LAN
Page 37

4.0 WebUI Configuration
4.3.6 Network > SNMP
The IPn3G may be configured to operate as a Simple Network Management Protocol (SNMP) agent.
Network management is most important in larger networks, so as to be able to manage resources and
measure performance.
SNMP may be used in several ways:
SNMP: Simple Network
Management Protocol
provides a method of
managing network
devices from a single PC
running network
management software.
Managed networked
devices are referred to as
SNMP agents.
A SNMP management system (a PC running SNMP management software) is required for this service to
operate. An SNMP MIB Browser can be also be used to provision the IPn3G, these utilities are not supplied
by Microhard Systems, but many free and premium types of browsers are available on the market. This system must have full access to the IPn3G network. Communications is in the form of queries (information
requested by the management system) or traps (information initiated at, and provided by, the SNMP agent
in response to predefined events).
Objects specific to the IPn3G are hosted under private enterprise number 21703.
An object is a variable in the device and is defined by a Management Information Database (MIB). Both the
management system and the device have a copy of the MIB. The MIB in the management system provides
for identification and processing of the information sent by a device (either responses to queries or devicesourced traps). The MIB in the device relates subroutine addresses to objects in order to read data from, or
write data to, variables in the device. Contact Microhard Systems Inc, for the most recent MIB file.
An SNMPv1 agent accepts commands to retrieve an object, retrieve the next object, set and object to a
specified value, send a value in response to a received command, and send a value in response to an event
(trap).
SNMPv2c adds to the above the ability to retrieve a large number of objects in response to a single request.
SNMPv3 adds strong security features including encryption; a shared password key is utilized. Secure device monitoring over the Internet is possible. In addition to the commands noted as supported above, there
is a command to synchronize with a remote management station.
Custom MIBs can be obtained by contacting Microhard Systems Inc. Appendix F: SNMP MIB Sample con-
tains the first few pages of the IPn3G MIB to be used as a reference The MIB file can change when new
features are added, so it is best to contact us for the complete and latest MIB file for the IPn3G.
configure remote devices
monitor network performance
detect faults
audit network usage
detect authentication failures
© Microhard Systems Inc. 37
Page 38

4.0 WebUI Configuration
Image 4-13: Network > SNMP
If disabled, no SNMP service is provided from the device. Enabled, the
device - now an SNMP agent - can support SNMPv1, v2, & v3.
Read Only Community Name
Effectively a plain-text password mechanism used to weakly authenticate
SNMP queries. Being part of the community allows the SNMP agent to
process SNMPv1 and SNMPv2c requests. This community name has only
READ priority.
Read Write Community Name
Effectively a plain-text password mechanism used to weakly authenticate
SNMP queries. Being part of the community allows the SNMP agent to
process SNMPv1 and SNMPv2c requests. This community name has only
READ/WRITE priority.
Defines the user name for SNMPv3.
SNMP Operation Mode
Values
Disable / V1&V2&V3
Values (char string)
public
Values (char string)
private
SNMP V3 User Name
Values (char string)
© Microhard Systems Inc. 38
V3user
Page 39

4.0 WebUI Configuration
V3 User Read Write Limit
Defines accessibility of SNMPv3; select either Read Only or Read/Write
priority. If Read Only is selected, the SNMPv3 user may only read
information; if Read Write is selected, the SNMPv3 user may read and
write (set) variables.
V3 User Authentication Level
Defines SNMPv3 user’s authentication level.
NoAuthNoPriv: No authentication, no encryption.
AuthNoPriv: Authentication, no encryption.
AuthPriv: Authentication, encrpytion.
V3 Authentication Password
SNMPv3 user’s authentication password. Only valid when V3 User
Authentication Level set to AuthNoPriv or AuthPriv (see above).
V3 Authentication Password
SNMPv3 user’s encryption password. Only valid when V3 User
Authentication Level set to AuthPriv (see above).
Values
Read Only
Read Write
Values
NoAuthNoPriv
AuthNoPriv
AuthPriv
Values (char string)
00000000
Values (char string)
00000000
Select which version of trap will be sent should a failure
or alarm condition occur.
If enabled, an authentication failure trap will be generated upon
authentication failure.
The community name which may receive traps.
Defines a host IP address where traps will be sent to (e.g. SNMP
management system PC IP address).
Values
V1 Traps
V2 Traps
V3 Traps
SNMP Trap Version
V1&V2 Traps
V1&V2&V3 Traps
Auth Failure Traps
Values
Disable / Enable
Trap Community Name
Values (char string)
TrapUser
Trap Manage Host IP
Values
0.0.0.0
© Microhard Systems Inc. 39
Page 40

4.0 WebUI Configuration
4.3.7 Network > DHCP Lease
The Network > DHCP Lease tab shows a summary of IP Addresses assigned by the IPn3G’s DHCP
server. As seen below the MAC address, IP Address, Name and the amount of time remaining on the
DHCP lease is shown.
Image 4-14: Network Configuration , Local IP Configuration Submenu
4.3.8 Network > Device List
The Network > Device List shows the current ARP table for the local network adapter. Similar to the DHCP
list the MAC address and IP address are shown, however not only DHCP assigned devices are listed in the
device list, any devices, even those statically assigned, that are connected through the local network
interface (RJ45) are displayed, including those connected through a hub or switch.
Image 4-15: Network Configuration , Device List
© Microhard Systems Inc. 40
Page 41

4.0 WebUI Configuration
4.3.9 Network > Local Monitor
The Local Device Monitor allows a user to monitor a local device connected locally to the Ethernet port or
to the locally attached network. If the IPn3G cannot detect the specified IP or a DHCP assigned IP, the unit
will restart the DHCP service, and eventually restart the modem to attempt to recover the connection.
Image 4-16: Network Configuration , Local Monitor
Enable or disable the local device monitoring service.
Select the IP mode. By selecting a fixed IP address the service will monitor
the connection to that specific IP. If auto detect is selected, the IPn3G will
detect and monitor DHCP assigned IP address.
This field is only shown if Fixed Local IP is selected for the IP Mode. Enter
the static IP to be monitored in this field.
The status timeout is the maximum time the IPn3G will wait to detect the
monitored device. At this time the IPn3G will restart the DHCP service.
Status
Values (selection)
Disable / Enable
IP Mode
Values (selection)
Fixed local IP
Auto Detected IP
Local IP
Values (IP)
0.0.0.0
Status Timeout
Values (seconds)
10
This field defines the amount of time the IPn3G will wait to detect the
monitored device before it will reboot the modem.
© Microhard Systems Inc. 41
Waiting DHCP Timeout
Values (seconds)
60
Page 42

4.0 WebUI Configuration
4.4 Carrier
4.4.1 Carrier > Statistics
The Carrier Statistics window provides information related to the Wireless Carrier portion of the IPn3G. A
variety of information can be found here, such as Activity Status, Network (Name of Wireless Carrier
connected) , Data Service Type(2G/3G/HSPA etc), Frequency band, Phone Number etc.
Not all statistics parameters displayed are applicable.
The Received and Transmitted bytes and packets indicate the respective amount of data which has been
moved through the radio.
The Error counts reflect those having occurred on the wireless link.
© Microhard Systems Inc. 42
Image 4-17: Carrier Configuration Menu
Page 43

4.0 WebUI Configuration
4.4.2 Carrier > Graph
The Carrier > Graph tab displays a graphical display of the Carrier Traffic on the Wireless interface of the
IPn3G.
WAN (ppp0) Shows an overview of all data sent or received by the IPn3G on the Wireless
WAN (ppp0) / hourly Shows the traffic volumes (TX = green, RX = grey) at hourly intervals during
WAN (ppp0) / daily Shows the total data received and transmitted for the day, as well as the
WAN (ppp0) / monthly Shows the total data received and transmitted for the current month, as well as
WAN (ppp0) / Top 10 Show the top 10 days with the most data sent or received.
portion of the unit. A summary of the data of the current day and the current
month is shown.
the current 24 hour period. This could be useful to see when the most or least
amount of traffic is present.
average rate of data.
the average rate of data.
© Microhard Systems Inc. 43
Image 4-18: Carrier Graph
Page 44

4.0 WebUI Configuration
4.4.3 Carrier Configuration
The parameters within the Carrier Configuration menu must be input properly; they are the most basic
requirement required by your cellular provider for network connectivity.
This option allows for the automatic detection of available carriers, the
manual selection of detected carriers, or the fixed selection of entering a
carriers ID. Manual and Fixed are commonly used when the IPn3G is
Roaming and it is desirable to control which carrier the unit connects to.
© Microhard Systems Inc. 44
Image 4-19: Carrier Config
Carriers
Values (selection)
Automatic
Manual
Fixed
Page 45

4.0 WebUI Configuration
Carrier ID
In Manual Carrier mode, select the desired carrier from the list of available
carriers. In fixed mode, enter the Carrier ID.
When set to Automatic the modem will automatically decide on the best
signal to connect to, in some cases this may be 2G. When set to 3G Only,
the modem will continually try to connect to 3G, the same for 2G only.
Once set to operate in a specific technology, a user can then select which
frequencies within that technology to use. It is recommended to be careful,
as if no useable frequency/technology (3G/2G) is available, the modem will
not connect.
Access Point Name (APN)
The (Access Point Name) APN is required and assigned by the wireless
carrier. A Carrier will have different APNs for different service types (Static
vs Dynamic etc).
Values
Varies
Network Data Mode
Values (selection)
Automatic
3G Only
(1900/850/900/2100/1700)
2G Only
(850/900/1800/1900 MHz)
Values (String)
Carrier dependant
It is possible to have a Pin number associated with a SIM card that is
required to use the SIM card on a device. If the installed SIM card has
been set up with a SIM Pin, enter the number here.
When NAT is enabled internal addresses are not visible to external
networks. When disabled the router does not perform any address
translation on the packets passing through it.
This option allows the operation of PPP.
© Microhard Systems Inc. 45
SIM Pin
Values (String)
Carrier dependant
NAT (Network Address Translation)
Values (selection)
Disable / Enable
PPP Status
Values (selection)
Disable / Enable
Page 46

4.0 WebUI Configuration
IP-Passthrough
IP pass-through allows the WAN IP address to be assigned to the device
connected to the rear Ethernet port on the IPn3G. In this mode the IPn3G
is transparent and forwards all traffic to the device connected to the
Ethernet port. The WebUI port (Default HTTP Port:80), this port is retained
for remote management of the IPn3G. This port can be changed to a
different port under the Security > Access Menu. It is recommended to
reboot the IPn3G after changing these settings.
If disabled, the modem will always remain connected. The default is
Disabled.
The maximum amount of time to pass before modem will timeout. The
default is 0 seconds.
The maximum amount of time to wait for a connection The default is 90
seconds.
Values (selection)
Disable / Ethernet
Dial-on-Demand
Values (selection)
Disable / Enable
Idle Time Out
Values (seconds)
0-65535
Connect Time Out
Values (seconds)
0-65535
The maximum amount of attempts to dial and establish a connection. The
default is 0, which means that there is no maximum and the modem will
keep trying indefinitely.
Sets the authentication type required to negotiate with peer.
PAP - Password Authentication Protocol.
CHAP - Challenge Handshake Authentication Protocol.
User Name as required for authentication to remote peer. May not be
required for dynamically assigned IP addresses from the wireless carrier.
Usually required for static IP addresses.
© Microhard Systems Inc. 46
Dialing Max Retries
Values
0-100
Authentication Type
Values (selection)
NoAuth
pap
chap
pap-chap
User Name
Values (char string)
Carrier/peer dependant
Page 47

4.0 WebUI Configuration
Password
Password as required for authentication to remote peer. May not be
required for dynamically assigned IP addresses from the wireless carrier.
Usually required for static IP addresses.
Sets the number to be dialed. Carrier dependant, the default number is
*99***1#
In some cases the Static IP address must be entered in this field if
assigned by a wireless carrier. In most cases the IP will be read from the
SIM card and this field should be left at the default value.
Enabled by default, the IPn3G, will use the DNS server as specified
automatically by the service provider.
Sets the modems connect string if required by the carrier.
Values (char string)
Carrier/peer dependant
Dial Number
Values (String)
*99***1#
Static IP Address
Values
0.0.0.0
Use Remote DNS
Values (Selection)
Disable / Enable
Connect String
Values (String)
The modem can have up to 4 initialization strings.
© Microhard Systems Inc. 47
CONNECT
Image 4-20: Carrier Configuration Menu, DDNS Config...
Initialization 1 - 4
Values (String)
Init-string
Page 48

4.0 WebUI Configuration
Image 4-21: Carrier Configuration Menu, DDNS Config...
DDNS Status
This selection allows the use of a Dynamic Domain Name Server (DDNS),
for the IPn3G.
Unless a carrier issues a Static IP address, it may be desirable to use a
dynamic DNS service to track dynamic IP changes and automatically
update DNS services. This allows the use of a constant resolvable host
name for the IPn3G.
This is a list of supported Dynamic DNS service providers. Free and
premium services are offered, contact the specific providers for more
information.
This is the host or domain name for the IPn3G as assigned by the DDNS
provider.
Enter a valid user name for the DDNS service selected above.
Values (Selection)
Disable / Enable
Service Name
Values (Selection)
dyndns.org
changeip.com
zoneedit.com
no-ip.com
noip.com
freedns.afraid.org
dnsmax.com
thatip.com
Domain
Values
user.dyndns.org
User Name
Values
Enter a valid password for the user name of the DDNS service selected
above.
© Microhard Systems Inc. 48
username
Password
Values
username
Page 49

4.0 WebUI Configuration
Image 4-22: Carrier Configuration Menu, ICMP Keep Alive Check...
ICMP Keep Alive Check
This selection allows the use of a ICMP Keep Alive Check for the IPn3G.
The default is disabled.
A user can set up a reachable host (IP or domain) for the unit to ping
periodically to keep the WAN connection alive (Wireless Carrier) in case
the carrier shuts it down due to lack of activity. PING frequency is defined
by the Interval.
The Interval value determines the frequency, or how often, the IPn3G will
send out PING messages to the Host.
The Count field is the maximum number of PING errors such as “Host
unreachable” the IPn3G will attempt before the unit will reboot itself to
attempt to correct connection issues. If set to zero (0), the unit will never
reboot itself.
Values (selection)
Disable / Enable
HostName
Values (IP Address)
IP Address or Name of host
for ICMP PING.
Interval
Values (seconds)
30
Count
Values
10
© Microhard Systems Inc. 49
Page 50

4.0 WebUI Configuration
4.5 COM1/COM2
4.5.1 COM1/2 > Statistics
This window displays information related to the serial interfaces of the IPn3G.
COM1/2 Port Status
Enabled by default. (IF COM2 is disabled it is available as a ‘Console’ port.)
COM1/2 Connect As
Display of chosen protocol with respect to serial gateway function.
COM1/2 Connect Status
If port is enabled and there is data traffic, this will display ‘Active’.
The other displayed parameters are not all applicable. Of most use are the transmitted and received bytes/
packets: these will indicate if data is coming into and out of the COM ports.
© Microhard Systems Inc. 50
Image 4-23: COM1 Configuration Menu
Page 51

4.0 WebUI Configuration
4.5.2 COM1 and COM2 Configuration
The menus ’COM1 > Config’ and ’COM2 > Config’ are used to configure the serial device server for the
serial communications ports:
COM1 (DATA), the rear DE9 connector on the IPn3G, and
COM2 (DIAGNOSTIC), the front DE9 connector.
Serial device data may be brought into a LAN network through TCP, UDP, or multicast; it may also exit the
IPn3G network on another IPn3G ’s serial port. Ensure that the firewall allows access to the assigned ports
by either creating rules to allow it, or by setting the WAN Request to allow.
COM1 is a full-featured RS232 interface dedicated to serial data traffic. It supports hardware handshaking.
By default, this port is enabled.
COM2 is, by default, disabled. In this state, it may be used as the console port for the text user interface.
Enabled, it becomes another serial port for data traffic. It is a 3-wire (TxD, RxD, and SG) interface and
does not support hardware handshaking.
For brevity, only COM1 is fully detailed in this section; the relative limitations of COM2 are noted where
applicable.
© Microhard Systems Inc. 51
Image 4-24: COM1 Configuration Menu
Page 52

4.0 WebUI Configuration
Port Status
Note: Most PCs do not
readily support serial
communications greater
than 115200bps.
Select operational status of port. Enabled by default.
*COM2 is Disabled by default. If COM2 is Enabled and there is a desire to
switch it back to Disabled (console mode) via the serial connection to it, the
escape sequence of ‘+++’ may be entered at the Data Baud Rate for which
the port is configured.
Determines which (rear of unit) serial interface shall be used to connect to
external devices: RS232, RS485, or RS422. This option applies only to
COM1 / DATA. When an interface other than RS232 is selected, the DE9
port will be inactive.
The serial baud rate is the rate at which the modem is to
communicate with the attached local asynchronous
device.
*COM2 data baud rate maximum is 115200bps.
Values (bits per second (bps))
921600
460800
230400
115200
57600
38400
28800
19200
Values
Enable
Disable
Channel Mode
Values
RS232 / RS485 / RS422
Data Baud Rate
14400
9600
7200
4800
3600
2400
1200
600
300
Data Format
This setting determines the format of the data on the serial port.
The default is 8 data bits, No parity, and 1 Stop bit.
Values
8N1
8N2
8E1
8O1
7N1
7N2
Flow Control
Flow control may be used to enhance the reliability of
serial data communications, particularly at higher baud
rates. If the attached device does not support hardware
handshaking, leave this setting at the default value of
‘None’.
Software flow control
(XON/XOFF) is not
supported.
© Microhard Systems Inc. 52
When CTS Framing is selected, the IPn3G uses the CTS
signal to gate the output data on the serial port. Figure
3A below illustrates the timing of framed output data.
*COM2 does not support Flow Control.
Values
None / Hardware / CTS Framing
Drawing 4A: CTS Output Data Framing
7E1
7O1
7E2
7O2
Page 53

4.0 WebUI Configuration
Pre-Data Delay (ms)
Refer to Drawing 3A.
*COM2 does not support this function.
Values (ms)
100
Post-Data Delay (ms)
Refer to Drawing 3A.
*COM2 does not support this function.
Values (ms)
100
Data Mode
This setting defines the serial output data framing. In Transparent mode
(default), the received data will be output promptly from the IPn3G. When
set to Seamless, the serial port server will add a gap between data frames
to comply with the MODBUS protocol for example.
Values
Seamless
Transparent
Character Timeout
In Seamless mode (see Data Mode), this setting determines when the
serial server will consider the recently-received incoming data as being
ready to transmit. As per the MODBUS standard, frames will be marked as
‘bad’ if the time gap between frames is greater than 1.5 characters, but less
than the Character Timeout value.
The serial server also uses this parameter to determine the time gap inserted between frames. It is measured in ‘characters’ and related to baud rate.
Example: If the baud rate is 9600bps, it takes approximately 1ms to move one character. With the Character Timeout set to 4, the timeout period is 4ms. When the calculated time is less than 3.5ms, the serial
server will set the character timeout to a minimum value of 3.5ms. If the baud rate is greater than
19200bps, the minimum char acter timeout is internally set to 750us (microseconds) .
Values
characters
4
Defines the buffer size that the serial server will use to receive data from
the serial port. When the server detects that the Character Timeout criteria
has been met, or the buffer is full, it packetizes the received frame and
transmits it.
This setting effects the Quality of Service (QoS) associated with the data
traffic on the specific COM port.
© Microhard Systems Inc. 53
Maximum Packet Size
Values (Bytes)
1024
Priority
Values
Normal
Medium
High
Page 54

4.0 WebUI Configuration
Image 4-25: COM1 Modbus Config
No-Connection Data
When enabled the data will continue to buffer received on the serial data
port when the radio loses synchronization. When disabled the IPn4G will
disregard any data received on the serial data port when radio
synchronization is lost.
This option will enable or disable the MODBUS decoding and encoding
features.
Modbus TCP Protection
The field allows the Modbus TCP Protection Status flag to be enabled or
disabled. If enabled the Modbus data will be encrypted with the Modbus
Protection Key.
Modbus TCP Protection Key
MODBUS encryption key used for the MODBUS TCP Protection Status
feature.
Values (selection)
Disable
Enable
Modbus TCP Status
Values (selection)
Disable
Enable
Values (IP Address)
Disable
Enable
Values (UDP Port)
1234
© Microhard Systems Inc. 54
Page 55

4.0 WebUI Configuration
Image 4-26: COM1 Data Logging
Data Logging Status
Data Logging on the COM ports allows for the actual serial port data to be
sent to a remote host. This data can be in the Raw form or converted to
Hex before it is sent.
Select Tx&Rx to log data to/from the serial port. Select Tx to log data that is
being transmitted from the serial port, and Rx to log data being received at
the serial port.
Enter the IP Address of the where the logging data is to be sent. Generally
this is a PC listening on the specified UDP port.
Enter the UDP port of the IP Address where the data is to be sent.
Values (selection)
Disable
Raw
Hex
Logging Direction
Values (selection)
Tx&Rx
Tx
Rx
Logging Host IP
Values (IP Address)
0.0.0.0
Logging Host Port
Values (UDP Port)
30001
© Microhard Systems Inc. 55
Page 56

4.0 WebUI Configuration
This setting determines which protocol the serial server will use to transmit serial port data over the IP
Series network. Ensure that the firewall allows access to the assigned ports by either creating rules to
The protocol selected in
the Protocol Config field
will determine which
configuration options
appear in the remainder
of the COMn
Configuration Menu.
UDP: User Datagram
Protocol does not provide
sequencing information
for the packets sent nor
does it establish a
’connection’ (‘handshakin
g’) and is therefore most
suited to communicating
small packets of data.
TCP: Transmission
Control Protocol in
contrast to UDP does
provide sequencing
information and is
connection-oriented; a
more reliable protocol,
particularly when large
amounts of data are being
communicated.
Requires more bandwidth
than UDP.
allow it, or by setting the WAN Request to allow.
TCP Client: When TCP Client is selected and data is received on its serial port, the IPn3G takes the
initiative to find and connect to a remote TCP server. The TCP session is terminated by this same unit
when the data exchange session is completed and the connection timeout has expired. If a TCP
connection cannot be established, the serial port data is discarded.
Remote Server Address
IP address of a TCP server which is ready to accept serial port data through a TCP
connection. For example, this server may reside on a LAN network server.
Default: 0.0.0.0
Remote Server Port
A TCP port which the remote server listens to, awaiting a session connection request from
the TCP Client. Once the session is established, the serial port data is communicated from
the Client to the Server.
Default: 20001
Outgoing Connection Timeout
This parameter determines when the IPn3G will terminate the TCP connection if the
connection is in an idle state (i.e. no data traffic on the serial port).
Default: 60 (seconds)
TCP Server: In this mode, the IPn3G will not INITIATE a session, rather, it will wait for a Client to request
a session of it (it’s being the Server—it ‘serves’ a Client). The unit will ‘listen’ on a specific TCP port. If a
session is established, data will flow from the Client to the Server, and, if present, from the Server to the
Client. If a session is not established, both Client-side serial data, and Server-side serial data , if present,
will be discarded.
Local Listening Port
The TCP port which the Server listens to. It allows a TCP connection to be created by a TCP
Client to carry serial port data.
Default: 20001
Incoming Connection Timeout
Established when the TCP Server will terminate the TCP connection is the connection is in
an idle state.
Default: 300 (seconds)
TCP Client/Server: In this mode, the IPn3G will be a combined TCP Client and Server, meaning that it
can both initiate and serve TCP connection (session) requests. Refer to the TCP Client and TCP Server
descriptions and settings described previously as all information, combined, is applicable to this mode.
Protocol Config
© Microhard Systems Inc. 56
Page 57

4.0 WebUI Configuration
A UDP or TCP port is an
application end-point.
The IP address identifies
the device and, as an
extension of the IP
address, the port
essentially ‘fine tunes’
where the data is to go
‘within the device’.
Be careful to select a port
number that is not
predetermined to be
associated with another
application type, e.g.
HTTP uses port 80.
Multicast is a one-tomany transmission of
data over an IP network.
It is an efficient method of
transmitting the same
data to many recipients.
The recipients must me
members of the specific
multicast group.
TTL: Time to Live is the
number of hops a packet
can travel before being
discarded.
In the context of multicast,
a TTL value of 1 restricts
the range of the packet to
the same subnet.
Protocol Config (continued)
UDP Point-to-Point: In this configuration the IPn3G will send serial data to a specifically-defined point,
using UDP packets. This same IPn3G will accept UDP packets from that same point.
Remote IP Address
IP address of distant device to which UDP packets are sent when data received at serial port.
Default: 0.0.0.0
Remote Port
UDP port of distant device mentioned above.
Default: 20001
Listening Port
UDP port which the IP Series listens to (monitors). UDP packets received on this port are
Default: 20001
UDP Point-to-Multipoint (P): This mode is configured on an IPn3G which is to send multicast UDP
packets; typically, the MASTER in the IPn3G network.
Multicast IP Address
A valid multicast address this unit uses to send multicast UDP packets upon receiving data
Default: 224.1.1.1
Multicast Port
A UDP port that this IPn3G will send UDP packets to. The Multipoint (MP - see the UDP
Default: 20001
Listening Port
The UDP port that this unit receives incoming data on from multiple remote units.
Default: 20011
Time to Live
Time to live for the multicast packets.
Default: 1 (hop)
UDP Point-to-Multipoint (MP): This protocol is selected on the units which are to receive multicast UDP
packets, typically the Remote units. See the previous description of UDP Point-to-Multipoint (P).
Remote IP Address
Remote Port
forwarded to the unit’s serial port.
from the serial port. The default value is a good example of a valid multicast address.
Point-to-Multipoint (MP) description) stations should be configured to listen to this point in
order to receive multicast packets from this IPn3G.
The IP address of a distant device (IP Series or, for example, a PC) to which the unit
sends UDP packets of data received on the serial port. Most often this is the IP address
of the Master IP Series.
Default: 0.0.0.0
The UDP port associated with the Remote IP Address (above). In the case of this
‘Remote’ being the Master IPn3G, the value in this field should match the Listening Port
of the Master (see UDP Point-to-Multipoint (P)).
Default: 20011
© Microhard Systems Inc. 57
Page 58

4.0 WebUI Configuration
Multicast IP Address
A valid MULTICAST address that this unit will use to receive multicast UDP packets sent
by a UDP Point-to-Multipoint (P) unit. Note that the default value for this field matches
In a Point-to-Multipoint
(PMP) network topology
which is to utilize UDP
multicast, typically the
MASTER would be
configured as ’(P)’ (the
POINT) and the
REMOTES would be
configured as ’(MP)’ (the
MULTIPOINTS).
Multicast Port
UDP Multipoint-to-Multipoint
Multicast IP Address
A valid multicast address the unit will use to send multicast UDP packets upon receiving them
Default: 224.1.1.1
Multicast Port
UDP port that the packets are sent to. Multipoint stations should be configured to listen to
Default: 20011
Time to Live
Time to live for the multicast packets.
Default: 1 (hop)
Listening Multicast IP Address
A valid multicast address the unit is to listen to receive multicast UDP packets sent by
Default: 224.1.1.1
Listening Multicast Port
UDP port that the unit will listen to for multicast UDP packets sent by another UDP Multipoint-
the default Multicast IP Address of the UDP Point-to-Multipoint (P) configuration
described on the previous page.
Default: 224.1.1.1
The UDP port that this unit will use, along with the Multicast IP Address detailed above,
to receive the multicast UDP packets sent by the UDP Point-to-Multipoint (P) unit.
Default: 20001
at its serial port.
this port in order to receive multicast packets.
another UDP Multipoint-to-Multipoint unit.
to-Multipoint unit.
Default: 20011
Protocol Config (continued)
© Microhard Systems Inc. 58
Page 59

4.0 WebUI Configuration
SMTP: Simple Mail
Transport Protocol is a
protocol used to transfer
mail across an IP
network.
Protocol Config (continued)
SMTP Client: If the IPn3G network has Internet access, this protocol may be used to send the data
received on the serial port (COM1), in a selectable format (see Transfer Mode (below)), to an e-mail
addressee. Both the SMTP Server and the e-mail addressee must be ‘reachable’ for his feature to
function. Note: COM2 does not support this mode.
Mail Subject
Enter a suitable ‘e-mail subject’ (e-mail heading).
Default: COM1 Message
Mail Server (IP/Name)
Username / Password
Mail Recipient
A valid e-mail address for the intended addressee, entered in the proper format.
Default: host@
Message Max Size
Maximum size for the e-mail message.
Default: 1024
Timeout (s)
How long the unit will wait to gather data from the serial port before sending an e-mail
Default: 10
Transfer Mode
Select how the data received on COM1 is to be sent to the email addressee. Options are:
Default: Text
PPP: COM1 can be configured as a PPP server for a serial connection with a PC or other device. The
attached PC could then use a dedicated serial (WindowsXP - dialup/modem) type PPP connection to
access the network resources of the IPn3G. Note: COM2 does not support this mode.
PPP Local IP
Enter the local PPP IP Address, the IP Address of the IPn3G COM1 Port.
Default: 192.168.0.1
PPP Host IP
PPP Idle Timeout(s)
Enter the desired PPP Idle Timeout in seconds.
IP address or ‘Name’ of SMTP (Mail) Server.
Default: 0.0.0.0
The username/password of the email account being used, if authentication is required for
outgoing email.
Default: varies/varies
message; data will be sent immediately upon reaching Message Max Size.
Text, Attached File, Hex Code.
Enter the PPP Host IP here. This is the IP of the PC or attached device.
Default: 192.168.0.99
Default: 30
© Microhard Systems Inc. 59
Page 60

4.0 WebUI Configuration
SMS Transparent Mode: Serial data from the COM1 port can be send to one or multiple destinations via
SMS text messaging. SMS messages received by the IPn3G can also be sent to the COM1 port.
Protocol Config (continued)
Image 4-27: COM > SMS Transparent Mode
Message Max Size
Enter the maximum message size. Once the number of characters has been reached the
IPn3G will package the data up and send it as a SMS message to the number(s) specified.
[1….160]. The character timeout can be used to send messages more frequently by detecting
a pause in the incoming data.
Default: 160
Reply Timeout(s)
Enter a value for the Reply Timeout.
Default: 10
Access Control
By selecting Anonymous, the IPn3G will accept a SMS message from any number. If
Control Phone List is selected, only messages from the numbers in the Access Control List
will be accepted.
Default: Anonymous
Read SMS Control
Select Keep in SIM Card to save incoming SMS messages in the SIM card, select Delete to
delete messages once they have been output to serial port.
Default: Keep in SIM Card
Access Control Phone List
Messages can be sent to up to five (5) numbers, also, this list can be used to filter incoming
© Microhard Systems Inc. 60
Page 61

4.0 WebUI Configuration
SMS AT Mode: When set to SMS AT Mode, the serial port accepts the SMS AT subset of the AT
Command Set. Only SMS AT Commands are available. For more detailed information about specific
commands, refer to the Section 5: AT Commands. The following commands are available on the COM1
serial port:
AT+CMGR - Read Message
AT+CMGL - List Message
AT+CMGD - Delete Message
AT+CMGS - Send SM to Network
AT+CGMI - Request Manufacturer ID
AT+CGMM - Request Model ID
AT+CGMR - Request Revision
AT+CSQ - Signal Strength
AT+MMGR - Read Message (Does not change Status)
AT+MMGL - List Message (Does not change Status)
AT+CMFG - Message Format
AT+CCLK - Read System Date and Time
AT+CSCA - Service Center Address
AT+CREG - Network Registration Status
AT+CNMI - New Message Indications to Terminal
AT+CMTI - Stored SMS-DELIVER Indication Unsolicited Response
GPS Transparent Mode: When in GPS Transparent Mode, GPS data is reported out of the serial port.
Sample output is shown below:
Protocol Config (continued)
© Microhard Systems Inc. 61
Image 4-28: COM > GPS Transparent Mode
Page 62

4.0 WebUI Configuration
Protocol Config (continued)
WirelessBus Mode: WirelessBus Mode can be used in systems where serial based polled SCADA
systems such as Modbus have one master/host and multiple remote/slave RTU/PLC’s located at several
different locations. The IPn3G that is connected to the Master is provided a list of IP Addresses/ports of
IPn3G’s that are connected to each of the remotes. Several Modbus (or other serial based protocols), can
be connected to each of the remote IPn3G’s (Using RS485 for multi-drop etc). WirelessBus Mode supports
Modbus RTU, and Modbus ASCII modes, as well as other protocols using broadcast mode.
Image 4-29: COM1 > Wireless Bus Mode (Host/Server)
WirelessBus Mode uses UDP packets to communicate between the Host and the Remotes. When a IPn3G
is configured as a Host/Server it retains a list of ModbusID’s and the respective IP/Port information
required to communicate with any remotes. When a Modbus poll is received by the IPn3G it looks at the
Modbus ID, then assembles a UDP packet to be sent to the corresponding IP/Port listed in the table. At the
remote side, the packet is disassembled and sent out the remote serial port as original serial data.
Listening Port
This is the UDP port used by the IPn3G configured as a Host/Server to
listen for incoming traffic from remote devices using the WirelessBus mode
and set as Remote/Clients.
Values (UDP)
20009
Timeout
The IPn3G features a configurable timeout. This timeout checks to ensure
the specified port is open and ready.
Values (seconds)
30
Bus Mode
When set to Remote/Client, and data received on the serial port will
automatically be encapsulated into an UDP packet and sent to the
configured host IP. When set to Host/Server the IPn3G will encapsulate
data received on the serial port into a UDP packet and send to the
applicable IP addresses/Ports listed.
© Microhard Systems Inc. 62
Values (selection)
Remote/Client
Host/Server
Page 63

4.0 WebUI Configuration
Protocol Config (continued)
Send Mode
When configured as Host/Server Bus Mode, this option will allow a user to
select between Modbus RTU, Modbus ASCII, or as Broadcast (for other
protocols. When set to broadcast the IPn3G will send any incoming serial
data to all the IP/Port numbers listed. When in either Modbus mode the
IPn3G will only send to the IP/Port that matches the Modbus ID.
Remote IP/ Adress Config
For each remote IPn3G enter the reachable IP address and configured
UDP port configured for serial data. The ModbusID is not required when in
broadcast mode for polled protocols other than Modbus.
Image 4-30: COM1 > Wireless Bus Mode (Remote/Client)
When the Bus Mode is configured for Remote/Client, enter the IP address
or domain address where the Host/Server is located.
Values (selection)
RTU Modbus Direct Access
ASCII Modbus Direct Access
Broadcast For Any Protocol
Values (UDP)
IP Address (required)
Port (UDP Port #)
ModbusID (if applicable)
Host IP/Domain Name
Values (IP/Domain)
192.168.168.1
Enter the UDP port number configured on the Host/Server where the
WirelessBus service is listening. By default this is configured as 20009 on
the Host/Server.
© Microhard Systems Inc. 63
Host Port
Values (UDP Port)
20009
Page 64

4.0 WebUI Configuration
4.6 USB
4.6.1 USB > Statistics
This window displays information related to the USB port located on the front of the IPn3G.
USB Port Status
Displays the status of the USB Port.
Configure via USB Configuration menu.
USB Connect As
Display of chosen protocol with respect to serial gateway function.
Configure via USB Configuration menu.
USB Connect Status
If port is enabled and there is data traffic, this will display ‘Active’.
The other displayed parameters are not all applicable. Of most use are the transmitted and received bytes/
packets: these will indicate if data is coming into and out of the USB port.
© Microhard Systems Inc. 64
Image 4-29: USB > Statistics
Page 65

4.0 WebUI Configuration
4.6.2 USB > Config
The USB Device Port Mode allows a user to define the operation of the IPn3G ’s USB Port. The port can be
configured to be used as any one of the following:
Console Mode Provides support for the USB-to-Serial console port. In this case, Mini USB port can be
used as a USB-to-Serial console port for the text user interface.
Data Mode Provides support for the USB-to-Serial port. Mini USB port can be used as a RS232
interface dedicated to serial data traffic.
NDIS Mode The USB port can be used as a network interface card. The IPn3G USB port is
configured by default in NDIS Standalone Ethernet Mode with a DHCP server running
in the background.
This means that a user can use the USB port communicate with the IPn3G via Ethernet
on the USB port of their PC’s.
Windows Drivers are available from the Support Desk on the Microhard Systems Inc website.
Please register and login into:
http://www.microhardcorp.com/support
© Microhard Systems Inc. 65
Image 4-30: USB Configuration Menu
Page 66

4.0 WebUI Configuration
Console Mode:
When the USB port in configured as Console Mode, the port acts as a console port.
Data Mode:
USB Data Mode is Disabled by default. If USB Data Mode is selected and there is a desire to switch it back
to Disabled (console mode) via the USB-to-Serial connection to it, the escape sequence of '+++' may be
entered at the Data Baud Rate for which the port is configured.
Image 4-31: USB Configuration Data Port
USB Device Port Mode
For more information about
any of the Data Port field parameters refer to COM1/COM2
Configuration.
© Microhard Systems Inc. 66
Values
Console Mode
Data Mode
NDIS Mode
Page 67

4.0 WebUI Configuration
NDIS Mode:
NDIS Standalone Mode is enabled by default. This setting will allow the USB port to act as a network
interface card.
USB Device Port Mode (Continued)
Image 4-32: USB NDIS Network Configuration
In standalone Mode the USB port will act as a separate NIC for the IPn3G.
In Bridge Mode the USB port wil use the same settings as the rear ethernet
port.
This is the IP Address of the USB NDIS adapter on the IPn3G. The IPn3G
acts as a DHCP server on this port and assigns an IP address to
connecting devices, i.e your PC.
Enter a valid subnet for the USB NIC.
Enter a valid host IP for the USB NIC.
NDIS Mode
Values (selection)
Bridge / Standalone
Local IP Address
Values
192.168.111.1
Subnet Mask
Values
255.255.255.0
Host IP
Values
192.168.111.2
© Microhard Systems Inc. 67
Page 68

4.0 WebUI Configuration
4.7 Security
4.7.1 Security > Password
For best practices and to
control unwanted access
it is critical that any
passwords not be left at
the default values.
Image 4-33: Security > Password Configuration Menu
To keep a system secure, the Administrator Password (which is prompted-for at the LogOn window,
Console, and Telnet sessions) should be modified rather than retaining the factory default value of ‘admin’.
The Upgrade Password protects the IPn3G from having firmware upgrade performed via FTP by an
unauthorized person. It is recommended that the default password be changed when the system is
deployed.
New Password/Repeat Password (admin)
Enter a new password for the Admin user. Repeat to ensure the intended
password was entered and that it was entered correctly. Do not forget the
admin password as, if lost, it cannot be recovered.
Values (char string)
admin
New Password/Repeat Password (upgrade)
Enter a new password for the Upgrade user. Repeat to ensure the intended
password was entered and that it was entered correctly.
Values (char string)
admin
© Microhard Systems Inc. 68
Page 69

4.0 WebUI Configuration
4.7.2 Security > Discovery
Image 4-34: Security Config. Menu, Discovery Service Config. Submenu
Telnet: A user command
which uses the TCP/IP
protocol to access a remote
device.
Format, from DOS prompt:
>telnet 192.168.1.50
where the IP address is that
of the target device.
If the above IP address is that
of an IPn3G accessible via
the network, the user will
arrive at the unit’s LogOn
window.
HTTP: HyperText Transfer
Protocol. The standard
protocol for transferring data
between a Web server and a
Web browser.
Allows, or disables use of the DiscoverIP utility. The discover IP utility
allows a user to scan a network for all available IPn3G units, and displays
the MAC and IP addresses as well as the unit description. The port used
for Discovery is 20077.
4.7.3 Security > Access
Image 4-35: Security Config. Menu, UI Access Config. Submenu
Discovery Service
Values (selection)
Disable
Discoverable
Changeable
User Interface (UI) Access Configuration allows the port configuration of
access services in the IPn3G, the default ports are shown below.
SSH & HTTPS: Must be
specified at the time of
order and enabled via the
factory. Once enabled,
the options can be set.
It is also possible to disable the FTP Server, and the Local DNS Server.
© Microhard Systems Inc. 69
Telnet (23)
HTTP (80)
SSH (22)
HTTPS (443)
Access
Values (selection)
Disable / Enable
Page 70

4.0 WebUI Configuration
4.7.4 Security > Authentication
There are two methods whereby a user may be authenticated for access to the IPn3G:
Local
Using the Admin or Upgrade access and associated passwords - the authentication is
done ‘locally’ within the IPn3G, and
RADIUS&Local
RADIUS authentication (using a specific user name and password supplied by your
RADIUS Server Administrator) - this authentication would be done ‘remotely’ by a
RADIUS Server; if this authentication fails, proceed with Local authentication as per
above.
RADIUS: Remote
Authentication Dial In
User Service. An
authentication,
authorization, and
accounting protocol which
may be used in network
access applications.
A RADIUS server is used
to verifying that
information is correct.
Image 4-36: Security Config. Menu, Authentication Config. Submenu
Select the Authentication Mode: Local (default) or RADIUS&Local. For
the latter selection, RADIUS authentication must be attempted FIRST; if
unsuccessful, THEN Local authentication may be attempted.
Auth Mode
Values
Local
RADIUS&Local
In this field, the IP address of the RADIUS server is to be entered if
RADIUS&Local has been selected as the Authorization Mode.
© Microhard Systems Inc. 70
RADIUS Server IP
Values
Valid RADIUS server IP
address
0.0.0.0
Page 71

4.0 WebUI Configuration
RADIUS Server Port
In this field, the applicable Port number for the RADIUS Server is to be
entered if RADIUS&Local has been selected as the Authorization Mode.
Normally, a RADIUS Server uses Port 1812 for the authentication function.
If the IP Series’ Authorization Mode has been set to RADIUS&Local, obtain
the RADIUS Secret for his particular client from your RADIUS Server
Administrator and enter it into this field, and the following field. (You will
also want to obtain the applicable RADIUS User Name from your RADIUS
Server Administrator.)
See above. Re-enter RADIUS Secret in this field.
Values
Applicable RADIUS Server
Port number
1812
RADIUS Secret
Values
Specific RADIUS Server
secret
nosecret
Repeat RADIUS Secret
Values
Specific RADIUS Server
secret
nosecret
Amount of time to wait for RADIUS authentication.
RADIUS Timeout
Values
10
1-65535
seconds
© Microhard Systems Inc. 71
Page 72

4.0 WebUI Configuration
4.7.5 Security > Certificate Management
When using the VPN features of the IPn3G, it is possible to select X.509 for the Authentication Type. If that
is the case, the IPn3G must use the required x.509 certificates in order to establish a secure tunnel
between other devices. Certificate Management allows the user a place to manage these certificates.
© Microhard Systems Inc. 72
Image 4-37: Security Config. Menu, Authentication Config. Submenu
Page 73

4.0 WebUI Configuration
4.8 Firewall
The Firewall Configuration is used to allow or disallow particular types of traffic access to and from the
network.
For best practices and to
control data usage is
critical that the firewall be
configured properly.
It is recommended to
block all WAN traffic and
create rules to open
specific ports and/or use
ACL lists to limit incoming
connections.
Image 4-38: Security Config. Menu, Firewall Configuration Submenu
When enabled, the firewall settings are in effect. When disabled, none of
the settings configured in the menu’s below have an effect, the modem is
“open”.
When Blocked the IPn3G will block at traffic on the WAN (Wireless Carrier)
unless specified otherwise in the Access Rules, MAC List, IP List
configurations. Access to ports 80 (HTTP) and 443 (HTTPS-if enabled), is
still available unless disabled in the Remote Management option.
LAN to WAN Access Control
Allows or Blocks traffic from the LAN (Ethernet, USB NDIS) accessing the
WAN unless specified otherwise using the Access Rules, MAC, and IP List
configuration.
Allow remote management of the IPn3G on the WAN side using the WebUI
on port 80(HTTP), and 443 (HTTPS). If disabled, the configuration can only
be accessed from the LAN.
Firewall Status
Values
Disable / Enable
WAN Request
Values
Block / Allow
Values
Block / Allow
Remote Management
Values
Disable / Enable
© Microhard Systems Inc. 73
Page 74

4.0 WebUI Configuration
4.8.1 Firewall > Rules
Once the firewall is turned on, rules configuration can be used to define specific rules on how local and
remote devices access different ports and services. MAC List and IP List are used for general access, and
are applied before rules are processed.
The rule name is used to identify the created rule. Each rule must have a
unique name and up to 10 characters can be used.
The Action is used to define how the rule handles the connection request.
ACCEPT will allow a connection, while REJECT (error) and DROP
(quietly dropped), will refuse connections.
This is configured based on how the WAN Request and LAN to WAN
Access Control are configured in the previous menus.
© Microhard Systems Inc. 74
Image 4-39: Firewall Configuration, Rules Config. Submenu
Rule Name
Values (10 Chars)
characters
Action
Values (selection)
ACCEPT
REJECT
DROP
Page 75

4.0 WebUI Configuration
Source Zone
Select the zone which is to be the source of the data traffic. WAN applies
to the wireless connection to the cellular carrier and the LAN refers to local
connections on the IPn3G (Ethernet, USB NDIS etc)
If a valid IP/Network address is specified, the action will apply against that
address; otherwise, leaving the default value of 0.0.0.0/0 in this field results
in the action applying to all source IP addresses.
Select the zone which is the intended destination of the data traffic. WAN
applies to the wireless connection to the cellular carrier and the LAN refers
to local connections on the IPn3G (Ethernet, USB NDIS etc)
If a valid IP/Network address is specified, the action will apply against that
address; otherwise, leaving the default value of 0.0.0.0/0 in this field results
in the action applying to all source IP addresses.
Values
WAN
LAN
none
Source IP
Values (IP Address)
0.0.0.0/0
Destination Zone
Values (selection)
WAN
LAN
none
Destination IP
Values (IP Address)
0.0.0.0/0
Protocol
The protocol field defines the transport protocol type controlled by the rule.
Values
TCP
UDP
ICMP
all
Destination Port
This field is used to define a port or service used in the rule (i.e. Port 80 =
HTTP which is generally a web server)
© Microhard Systems Inc. 75
Values (port)
0
Page 76

4.0 WebUI Configuration
4.8.2 Firewall > Port Forwarding
The IPn3G can be used to provide remote access to connected devices. To access these devices a user
must define how incoming traffic is handled by the IPn3G. If all incoming traffic is intended for a specific
connected device, DMZ could be used to simplify the process, as all incoming traffic can be directed
towards a specific IP address.
In the case where there is multiple devices, or only specific ports need to be passed, Port forwarding is
used to forward traffic coming in from the WAN (Cellular) to specific IP Addresses and Ports on the LAN.
Port forwarding can be used in combination with other firewall features, but the Firewall must be enabled
for Port forwarding to be in effect. If the WAN Request is blocked on the General Tab, additional rules and/
or IP Lists must be set up to allow the port forwarding traffic to pass through the firewall.
IP-Passthrough (Carrier > Config) is another option for passing traffic through the IPn3G, in this case all
traffic is passed to the device connected to the RJ45 port of the IPn3G, The device must be set for DHCP,
as the IPn3G assigns the WAN IP to the device, and the modem enters into a transparent mode, routing all
traffic to the RJ45 port. This option bypasses all firewall features of the IPn3G, as well as all other features
of the IPn3G such as COM, VPN, GPS etc.
Enable or disable DMZ Mode. DMZ can be used to forward all traffic to a
specific PC/Device on the LAN (DMZ Server IP listed below).
© Microhard Systems Inc. 76
Image 4-40: Firewall Configuration, Port Forwarding Config. Submenu
DMZ Mode
Values (selection)
Disable / Enable
Page 77

4.0 WebUI Configuration
If DMZ is enabled and an
exception port for the
WebUI is not specified,
remote management will
not be possible. The
default port for remote
management is TCP 80.
Enter the IP address of the destination device on the LAN side of the
IPn3G.
Enter a exception port number that will NOT be forwarded to the DMZ
server IP. Usually a configuration or remote management port that is
excluded to retain external control of the IPn3G.
Enter any additional ports that are not to be forwarded, each separated by
a comma.
This is simply a field where a convenient reference or description is added
to the rule. Each Forward must have a unique rule name and can use up to
10 characters.
DMZ Server IP
Values (IP Address)
192.168.100.100
Exception Port
Values (Port #)
none
More Exception Ports
Values (Port #)
none
Rule Name
Values (10 chars)
Forward
Enter the IP address of the intended internal (i.e. on LAN side of IPn3G)
server.
Target port number of internal server on the LAN IP entered above.
Select the type of transport protocol used. For example Telnet uses TCP,
SNMP uses UDP, etc.
Port number of incoming request (from WAN-side).
Internal Server IP
Values (IP Address)
192.168.2.1
Internal Port
Values (Port #)
3000
Protocol
Values
TCP
UDP
all
External Port
Values (Port #)
2000
© Microhard Systems Inc. 77
Page 78

4.0 WebUI Configuration
4.8.3 Firewall > MAC List
MAC List configuration can be used to control which physical LAN devices can access the ports on the
IPn3G, by restricting or allowing connections based on the MAC address. MAC List can be used alone or
in combination with LAN to WAN Access Control to provide secure access to the physical ports of the
IPn3G.
Image 4-41: Firewall Configuration, MAC List Config. Submenu
The Rule Name field is required to give the rule a convenient name for
reference. Each rule must have a unique name, up to 10 characters in
length.
Specify the MAC Address to be added to the list. Must be entered in the
correct format as seen above.
The Action is used to define how the rule handles the connection request.
ACCEPT will allow a connection, while REJECT (error) and DROP (quietly
dropped), will refuse connections.
Rule Name
Values (10 chars)
MAC_List
MAC Address
Values (MAC Address)
00:00:00:00:00:00
Action
Values (selection)
ACCEPT
DROP
REJECT
© Microhard Systems Inc. 78
Page 79

4.0 WebUI Configuration
4.8.4 Firewall > IP List
IP List configuration can be used to define who or what can access the IPn3G, by restricting or allowing
connections based on the IP Address/Subnet. Can be used alone or in combination with WAN Request
and LAN to Wan Access Control.
Image 4-42: Firewall Configuration, Blacklist Configuration Submenu
The Rule Name field is required to give the rule a convenient name for
reference. Each rule must have a unique name, up to 10 characters in
length.
Specify the specific IP or Network address (With /subnet, for example
192.168.0.0/24 will apply to all IP addresses in the 192.168.0.1 -
192.168.0.254 range (subnet /24 = 255.255.255.0).
Optional, enter a destination IP address to make the IP list more specific.
Leave as 0.0.0.0/0 to not use.
Enter the specific zone that the IP List will apply to, WAN (Wireless), LAN
(Ethernet, USB NDIS) or None (both).
Rule Name
Values (10 chars)
IP_List
Source Address
Values (IP Address)
0.0.0.0/0
Destination Address
Values (IP Address)
0.0.0.0/0
Select Zone
Values (Selection)
WAN / LAN / NONE
The Action is used to define how the rule handles the connection request.
ACCEPT will allow a connection, while REJECT (error) and DROP (quietly
dropped), will refuse connections.
© Microhard Systems Inc. 79
Action
Values (selection)
ACCEPT / DROP / REJECT
Page 80

4.0 WebUI Configuration
4.8.5 Firewall > Default
This menu provides a soft button which, when selected, will reset the firewall settings to factory defaults.
Once the button is pressed all configured firewall settings will immediately be reset to factory defaults.
Image 4-43: Reset Firewall to Default
© Microhard Systems Inc. 80
Page 81

4.0 WebUI Configuration
4.9 I/O
4.9.1 Status
On the front diagnostics (COM2) port of the IPn3G (Units shipped after June 1, 2012), 2 pins have been
set aside to be used for Digital I/O. Pin 7 is used as an INPUT, and Pin 8, is used for an OUTPUT. The
status window shows the current status of these pins.
Image 4-44: I/O > Status
Diagnostics Port (DB9 - Female)
Pin 7 - INPUT
Pin 8 - OUTPUT
Image 4-45: I/O > Pin Location
INPUT PINS
Pin 7 on the Diagnostics port of the IPn3G can be used to detect an input. Pin 7 has a small wetting
current (Vin) used to detect a contact closure, and prevent false readings by any noise or intermittent
signals, it has a threshold sensitivity of 1.8V.
OUTPUT PINS
Pin 8 on the diagnostics port of the IPn3G can be used to provide an output signal, which can be used, for
example, to drive an external relay to control an external device. Appendix G: Digital I/O: Driving an
External Relay, provides a example schematic of how this would work. Maximum recommended load for
the Output Pin is 150mA @ 32 VDC (Vin)
© Microhard Systems Inc. 81
Page 82

4.0 WebUI Configuration
4.10 Advanced
4.10.1 VPN
A Virtual Private Network (VPN) may be configured to enable a tunnel between the IPn3G and a remote
network.. The IPn3G supports VPN IPsec Gateway to Gateway (site-to-site) tunneling, meaning you are
using the IPn3G to create a tunnel between two VPN devices. The IPn3G can also operate as a L2TP
Server, allowing users to VPN into the unit from a remote PC, and a L2TP Client.
© Microhard Systems Inc. 82
Image 4-46: VPN IPsec Configuration Submenu
Page 83

4.0 WebUI Configuration
4.10.1.1 VPN > Gateway-to-Gateway
The Site to Site configuration allows the connection of two VPN devices to create a tunnel, such as a
IPn3G router at the office and a VPN capable router at a teleworker’s home. To establish a tunnel, settings
must be mirrored on the two routers. A successful connection requires that at least one router is identifiable
by a static IP address or a Server ID. If one end of the tunnel uses a dynamic IP address, the server ID can
be used to establish a connection. The two ends of the tunnel cannot be on the same subnet.
Image 4-47: VPN IPsec, Site-to-Site Submenu
Add/Edit Tunnel > Tunnel Name
Enter a name for the VPN Tunnel. Up to 16 different tunnels can be
created, each requiring a unique name. The VPN tunnel name can be
comprised of 1-0, A-Z, a-z or ‘_’. The space and dash ‘-’, are not valid
characters.
Add/Edit Tunnel > Tunnel Status
Tunnel Status is used to Enable or Disable the current tunnel.
Add/Edit Tunnel > Authentication
Select the type of Authentication. If Preshared Key is used, the same key
must be entered under IPsec Setup > Preshared Key. If X.509 is selected,
Certificate Management (Security) must be used to load the required
certificates and private keys related to X.509
Local Setup > Local Security Gateway Type
Specify the method for identifying the router to establish the VPN tunnel.
The Local Security Gateway is on this router; the Remote Security
Gateway is on the other router. At least one of the routers must have either
a static IP address or a dynamic IP with server id to make a connection.
(Continued…)
Values (chars)
tunnel1
Values (selection)
Disable / Enable
Values (selection)
Preshared Key
X.509 CA
Values (selection)
IP Only
IP + Server ID
Dynamic IP + Server ID
© Microhard Systems Inc. 83
Page 84

4.0 WebUI Configuration
IP Only: Choose this option if this router has a static WAN IP address. The WAN IP address appears
automatically. For the Remote Security Gateway Type, an extra field appears. If you know the IP address
of the remote VPN router, choose IP Address, and then enter the address.
IP + Server ID: Choose this option if this router has a static WAN IP address and a server id. The WAN IP
address appears automatically. For the Remote Security Gateway Type, an extra field appears. If you
know the IP address of the remote VPN router, choose IP Address, and then enter the address.
Dynamic IP + Server ID: Choose this option if this router has a dynamic IP address and a server id
(available such as @microhard.vpn). Enter the server id to use for authentication. The server id can be
used only for one tunnel connection.
Local Setup > Gateway IP Address
Displays the current WAN IP address of the IPn3G.
Local Setup > Local Server ID
This option appears when the Local Security Gateway Type specifies that
the Server ID is required for the connection. The Server ID must be in the
format @name, where name can be anything. Both routers must know
each others names to establish a connection.
Local Setup > Subnet IP Address
Define the local network by specifying the local subnet. Each end of the
tunnel must be on different subnets. To setup/change the local subnet on
the IPn3G, visit the Network Configuration Tab prior to setting up a VPN
tunnel.
Local Setup > Subnet Mask
Specify the subnet mask of the local network address.
Local Setup > Certificate
Values (IP Address)
Current WAN IP Address
Values (characters)
(no default)
Values (IP Address)
(no default)
Values (IP Address)
(no default)
If X.509 CA Authentication is selected, this field will appear. Enter
the certificate to be used by the current tunnel.
If X.509 CA Authentication is selected, this field will appear. Enter
the Private Key required by the X.509 protocol.
© Microhard Systems Inc. 84
Values (IP Address)
(no default)
Local Setup > Private Key
Values (IP Address)
(no default)
Page 85

4.0 WebUI Configuration
Image 4-48: VPN IPsec, Site-to-Site Submenu
Remote Setup > Remote Security Gateway Type
Specify the method for identifying the router to establish the VPN tunnel.
The Local Security Gateway is on this router; the Remote Security
Gateway is on the other router. At least one of the routers must have either
a static IP address or a dynamic IP with server id to make a connection.
(See Local Group Setup for details)
Values (selection)
IP Only
IP + Server ID
Dynamic IP + Server ID
Remote Setup > Gateway IP Address
If the remote VPN router has a static IP address, enter the IP address of
the remote VPN Gateway here.
Values (IP Address)
(no default)
Remote Setup > Remote Server ID
This option appears when the Remote Security Gateway Type specifies
that the Server ID is required for the connection. The Server ID must be in
the format @name, where name can be anything. Both routers must know
each others names to establish a connection.
© Microhard Systems Inc. 85
Values (characters)
(no default)
Page 86

4.0 WebUI Configuration
Remote Setup > Subnet IP Address
Define the remote network by specifying the subnet local to that router.
Remote Setup > Subnet Mask
Specify the subnet mask of the remote network address.
Remote Setup > Certificate
If X.509 CA Authentication is selected, this field will appear. Enter the
certificate to be used by the current tunnel.
Select the IPsec IKE (Internet Key Exchange) mode used for
authentication. Main mode is the standard mode, but aggressive mode can
be used to provide faster negotiation.
IPsec Setup > Phase 1 DH Group
Select value to match the values required by the remote VPN router.
Values (IP Address)
(no default)
Values (IP Address)
(no default)
Values (characters)
(no default)
IPsec Setup > Mode
Values (selection)
Main / Aggressive
Values (selection)
modp1024/modp1536/
modp2048
Phase 1 Encryption
Select value to match the Phase 1 Encryption type used by the remote
VPN router.
Values (selection)
3des/aes/aes128/aes256
Phase 1 Authentication
Select value to match the Phase 1 Authentication used by the remote VPN
router.
Values (selection)
md5 / sha1
Phase 1 SA Life Time
Select value to match the values required by the remote VPN router.
© Microhard Systems Inc. 86
Values
28800
Page 87

4.0 WebUI Configuration
Perfect Forward Secrecy (pfs)
Select value to match the values required by the remote VPN router.
Select value to match the values required by the remote VPN router.
Select value to match the Phase 1 Encryption type used by the remote
VPN router.
Phase 2 Authentication
Select value to match the Phase 1 Authentication used by the remote VPN
router.
Select value to match the values required by the remote VPN router.
Values (selection)
Disable / Enable
Phase 2 DH Group
Values (selection)
modp1024/modp1536/
modp2048
Phase 2 Encryption
Values (selection)
3des/aes/aes128/aes256
Values (selection)
md5/sha1
Phase 2 SA Life Time
Values
Set the Preshared Key required to authenticate with the remote VPN
router.
Set the DPD Delay required to authenticate with the remote VPN router.
Set the DPD Timeout required to authenticate with the remote VPN router.
© Microhard Systems Inc. 87
3600
Preshared Key
Values (characters)
password
DPD Delay
Values (seconds)
32
DPD Timeout
Values (seconds)
122
Page 88

4.0 WebUI Configuration
Set the DPD action required to authenticate with the remote VPN
router.
4.10.1.2 VPN > L2TP Server
DPD Action
Values (selection)
Hold / Clear
Enter a name for the L2TP VPN Tunnel. The L2TP VPN tunnel name can
be comprised of 1-0, A-Z, a-z or ‘_’. The space and dash ‘-’, are not valid
characters.
Tunnel Status is used to Enable or Disable the current tunnel.
Select the type of Authentication. If Preshared Key is used, the same key
must be entered under IPsec Setup > Preshared Key. If X.509 is selected,
Certificate Management (Security) must be used to load the required
certificates and private keys related to X.509
© Microhard Systems Inc. 88
Image 4-49: VPN, L2TP Submenu
Add/Edit Tunnel > Tunnel Name
Values (chars)
(no default)
Add/Edit Tunnel > Tunnel Status
Values (selection)
Disable / Enable
Add/Edit Tunnel > Authentication
Values (selection)
Preshared Key
X.509 CA
Page 89

4.0 WebUI Configuration
Specify the method for identifying incoming L2TP connections. Remote
systems can simply specify the IP address, or it can be configured that the
Server ID must also be known.
Local Setup > Local Security Gateway Type
Local Setup > Gateway IP Address
Displays the current WAN IP address of the IPn3G, which is the local VPN
Gateway.
Specify the Server ID if required by the Local Security Gateway Type
above. Usually this is in the format of @name.
Displays the local subnet used by the IPn3G for local devices, those
connected to the Ethernet Port. To modify the subnet used, visit the
Network Configuration menus.
Values (selection)
IP Only
IP + Server ID
Values (IP Address)
Current IP Address
Server ID
Values (characters)
(no default)
Subnet IP Address
Values (IP Address)
192.168.0.0
Subnet Mask
Displays the local subnet mask used by the IPn3G for local devices.
Values (IP Address)
255.255.255.0
Certificate / Private Key
If X.509 CA is chosen as the authentication method for the L2TP server,
then the certificates must be loaded using the Certificate Management
menu located under security. Specify which certificate / private key is being
used with this tunnel here.
Values (characters)
(no default)
Remote Setup > Start IP Address
Enter the starting range of IP Addresses that will be assigned to a remote
VPN adapter (such as a remote PC) when a VPN tunnel is created.
Values (IP Address)
192.168.0.201
End IP Address
Enter the end of the range of IP Addresses that will be assigned to a
remote VPN adapter (such as a remote PC) when a VPN tunnel is created.
IPsec Setup - Refer back to the previous section for information about IPsec parameters.
Values (IP Address)
192.168.0.210
© Microhard Systems Inc. 89
Page 90

4.0 WebUI Configuration
4.10.1.3 VPN > L2TP Client
The IPn3G can also operate as a L2TP Client, allowing a VPN connection to be made with a L2TP Server.
The Connection Name is used as a reference name for easy identification
of the connection.
Enable or disable the connection to the specified L2TP server here.
Select the type of Authentication. If Preshared Key is used, the same key
must be entered under IPsec Setup > Preshared Key. If X.509 is selected,
Certificate Management (Security) must be used to load the required
certificates and private keys related to X.509
© Microhard Systems Inc. 90
Image 4-50: VPN IPsec, VPN Client Submenu
Add New Connection > Connection Name
Values (characters)
none
Add New Connection > Tunnel Status
Values (selection)
Disable / Enable
Add New Connection > Authentication
Values (selection)
Preshared Key
X.509 CA
Page 91

4.0 WebUI Configuration
The L2TP requires that incoming connections know their IP Address and/or
the Server ID. Select which parameters are used by the L2TP server.
Local Setup > Local Security Gateway Type
Local Setup > Gateway IP Address
The current WAN IP address is shown here.
If the server ID is required, enter the ID here.
Remote Setup > Remote Security Gateway Type
The L2TP requires that incoming connections know their IP Address and/or
the Server ID. Select which parameters are used by the L2TP server. The
L2TP server must have a static, known IP address to create a tunnel.
Values (selection)
IP Only
IP + Server ID
Dynamic IP + Server ID
Values (IP Address)
Current IP Address
Local Setup > Local ID
Values (characters)
(no default)
Values (selection)
IP Only
IP + Server ID
Remote Setup > Gateway IP Address
Enter the IP address of the L2TP server that is to be connected to.
Values (IP Address)
(no default)
Remote Setup > Server ID
If the server ID is required, enter the ID here.
Values (characters)
(no default)
Remote Setup > Subnet IP Address
Enter the IP Address of the remote network.
Values (IP Address)
(no default)
Remote Setup > Subnet Mask
Enter the subnet mask of the remote network.
IPsec Setup - Refer back to the previous sections for information about IPsec
parameters.
Values (IP Address)
(no default)
© Microhard Systems Inc. 91
Page 92

4.0 WebUI Configuration
4.10.1.4 VPN > VPN Client Status
For VPN L2TP Server operation, users will be required to provide a username and password. Use VPN
Client Status to set up the required users.
Image 4-51: VPN IPsec, VPN Client Submenu
Image 4-52: VPN IPsec, VPN Client Submenu
© Microhard Systems Inc. 92
Page 93

4.0 WebUI Configuration
4.10.2 GRE
The IPn3G also supports GRE (Generic Routing Encapsulation), which can encapsulate a wide variety of
network layer protocols not supported by traditional VPN. This allows IP packets to travel from one side of
a GRE tunnel to the other without being parsed or treated like IP packets.
Image 4-53: Advanced > GRE
© Microhard Systems Inc. 93
Image 4-54: GRE Configuration
Page 94

4.0 WebUI Configuration
Image 4-55: GRE > Adding a New Tunnel
GRE Tunnel Name
Each GRE tunnel must have a unique name. Up to 10 GRE tunnels are
supported by the IPn3G. Valid characters include A-Z, a –z, 1 - 0, ‘_’.
Spaces and dashes are not allowed.
GRE Tunnel Local Status
Enable / Disable the GRE Tunnel.
Enable / Disable Multicast support over the GRE tunnel.
Enable / Disable ARP (Address Resolution Protocol) support over the GRE
tunnel.
Set the TTL (Time-to-live) value for packets traveling through the GRE
tunnel.
Values (chars(32))
gre
Values (selection)
Disable / Enable
Multicast
Values (selection)
Disable / Enable
ARP
Values (selection)
Disable / Enable
TTL
Values (value)
1 - 255
Enter the key for the GRE tunnel.
© Microhard Systems Inc. 94
Key
Values (characters)
(no default)
Page 95

4.0 WebUI Configuration
Image 4-56: GRE > Local / Remote Setup
Local Setup > Gateway IP Address
Enter the current WAN IP address of the IPn3G.
Local Setup > GRE Tunnel IP Address
This is the IP Address of the local GRE Tunnel, this must be in the same
subnet as the remote GRE tunnel. This is not the local subnet.
Local Setup > Net Mask
Set the subnet mask of the Local GRE Tunnel IP Address.
Local Setup > Subnet IP Address
Enter the IP Address of the local subnet. Each end of the GRE tunnel must
be on different subnets.
Values (IP Address)
0.0.0.0
Values (IP Address)
0.0.0.0
Values (IP Address)
0.0.0.0
Values (IP Address)
0.0.0.0
Enter the Subnet Mask of the local subnet.
Enter the WAN IP address of the remote router. This is the address to
which the tunnel will be created between.
© Microhard Systems Inc. 95
Local Setup > Subnet Mask
Values (IP Address)
0.0.0.0
Remote Setup > Gateway IP Address
Values (IP Address)
0.0.0.0
Page 96

4.0 WebUI Configuration
Specify the LAN subnet being used on the remote network. This must be a
different subnet than on the local router.
Remote Setup > Subnet IP Address
Remote Setup > Subnet Mask
Specify the LAN subnet mask being used on the remote network.
Values (IP Address)
0.0.0.0
Values (IP Address)
0.0.0.0
The setup for GRE IPsec is identical to the setup of VPN IPsec, refer to the previous section for
more information.
© Microhard Systems Inc. 96
Image 4-57: GRE > IPsec Setup
Page 97

4.0 WebUI Configuration
4.10.3 Advanced > GPS
Some models of the IPn3G support GPS and can provide GPS data to a client. The IPn3G can be polled
for GPS data via GPSD standards and/or provide customizable reporting to up to 4 different destination IP
addresses via UDP packets, or by Email.
GPS data can also be reported out the COM1 RS232/485 Serial Port. For more information, refer to the
COM1 > IP Protocol Config > GPS Transparent Mode section.
© Microhard Systems Inc. 97
Image 4-58: Advanced > GPS submenu
Page 98

4.0 WebUI Configuration
Image 4-59: GPS Polling submenu
GPS Status
Enable or disable the GPS polling function of the IPn3G. The default is
disabled.
Specify the TCP port on the IPn3G running that a remote GPS system can
connect and poll for GPSD information.
Specifies the output power supplied to the GPS antenna as required for the
specific antenna being used. Refer to your antennas manufacturer for more
information. In 0.05V intervals.
Values (selection)
Disable / Enable
TCP Port
Values (1-65535)
2947
Antenna Power (V)
Values (1.5 - 3.05)
3.05
Enable UDP and/or Email or disable GPS Reporting. Up to 4 reports can
be set up and configured independently.
If enabled local streaming will stream the GPS data selected to a device
connected to the LAN.
© Microhard Systems Inc. 98
Image 4-60: GPS Reporting submenu - UDP
GPS Reporting Report #
Values (selection)
Disable
UDP
Email
Local Streaming
Values (selection)
Disable
Enable for LAN Attached IP
Page 99

4.0 WebUI Configuration
GPS Reporting - UDP
Remote IP
Specify the IP Address of the destination of the GPS data UDP packets.
Specify the port number running the GPS services at the IP Address
specified in the IP Address field.
The repeat timer specifies the frequency at which the GPS data is reported
in seconds.
The trigger condition defines the conditions that must be met before a GPS
update is reported. If OR is chosen, the Repeater Timer OR the Distance
trigger conditions must be met before an update is sent. The AND
condition, requires that both the Repeat timer AND the Distance trigger
conditions be met before an update is sent.
Distance trigger (meters)
The distance trigger allows a specified distance to be traveled before the
GPS data is reported.
Values (IP Address)
0.0.0.0
Remote Port
Values (Port #)
0
Interval(s)
Values (seconds)
0
Trigger condition
Values (selection)
OR
AND
Values (meters)
0
The Message field allows customization of up to 4 different GPS messages
to be sent to the specified host.
None - Message is not used, no data will be sent
ALL - Sends all of the below
GGA - GPS Fix Data
GSA - Overall Satellite Data
GSV - Detailed Satellite Data
RMC - Recommended Min Data for GPS
VTG - Vector Track & Ground Speed
© Microhard Systems Inc. 99
Message#
Values (selection)
None
ALL
GGA
GSA
GSV
RMC
VTG
Page 100

4.0 WebUI Configuration
GPS Reporting - Email
Image 4-61: GPS Reporting submenu - Email
The Mail Subject field allows a user to enter a subject for the email sent by
the IPn3G.
Enter the IP Address or Domain name of the account of the outgoing mail
server used to send the message.
Enter the User Name of the email account used to send email from the
IPn3G.
Enter the Password for the email account used to send Email, only
required if the email server required outgoing authentication.
Enter the Email address of where the message is to be sent to.
Mail Subject
Values (Chars)
Report1 Message
Mail Server (IP/Name)
Values (IP/Name)
varies
User Name
Values (Chars)
varies
Password
Values (Chars)
varies
Mail Recipient
Values (Chars)
The repeat timer specifies the frequency at which the GPS data is reported
in seconds.
© Microhard Systems Inc. 100
varies
Interval(s)
Values (seconds)
0
 Loading...
Loading...