Microhard Systems BulletPlus, BulletPlus + Serial Data, BulletPlus + Ethernet, BulletPlus Peak Operating Manual
Page 1

Operating Manual
BulletPlus
4G/LTE Dual SIM Ethernet/Serial/USB Gateway w/WIFI
Document: BulletPlus.Operating Manual.v1.3.1.pdf
FW: v1.3.0 Build 1014
June 2016
150 Country Hills Landing NW
Calgary, Alberta
Canada T3K 5P3
Phone: (403) 248-0028
Fax: (403) 248-2762
www.microhardcorp.com
Page 2

Important User Information
Warranty
Microhard Systems Inc. warrants that each product will be free of defects in material and workmanship for a
period of one (1) year for its products. The warranty commences on the date the product is shipped by Micro-
hard Systems Inc. Microhard Systems Inc.’s sole liability and responsibility under this warranty is to repair or
replace any product which is returned to it by the Buyer and which Microhard Systems Inc. determines does
not conform to the warranty. Product returned to Microhard Systems Inc. for warranty service will be shipped
to Microhard Systems Inc. at Buyer’s expense and will be returned to Buyer at Microhard Systems Inc.’s ex-
pense. In no event shall Microhard Systems Inc. be responsible under this warranty for any defect which is
caused by negligence, misuse or mistreatment of a product or for any unit which has been altered or modified
in any way. The warranty of replacement shall terminate with the warranty of the product.
Warranty Disclaims
Microhard Systems Inc. makes no warranties of any nature of kind, expressed or implied, with respect to the
hardware, software, and/or products and hereby disclaims any and all such warranties, including but not limited to warranty of non-infringement, implied warranties of merchantability for a particular purpose, any interruption or loss of the hardware, software, and/or product, any delay in providing the hardware, software, and/
or product or correcting any defect in the hardware, software, and/or product, or any other warranty. The Purchaser represents and warrants that Microhard Systems Inc. has not made any such warranties to the Purchaser or its agents MICROHARD SYSTEMS INC. EXPRESS WARRANTY TO BUYER CONSTITUTES MICROHARD
SYSTEMS INC. SOLE LIABILITY AND THE BUYER’S SOLE REMEDIES. EXCEPT AS THUS PROVIDED, MICROHARD
SYSTEMS INC. DISCLAIMS ALL WARRANTIES, EXPRESS OR IMPLIED, INCLUDING ANY WARRANTY OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PROMISE.
MICROHARD SYSTEMS INC. PRODUCTS ARE NOT DESIGNED OR INTENDED TO BE USED IN
ANY LIFE SUPPORT RELATED DEVICE OR SYSTEM RELATED FUNCTIONS NOR AS PART OF
ANY OTHER CRITICAL SYSTEM AND ARE GRANTED NO FUNCTIONAL WARRANTY.
Indemnification
The Purchaser shall indemnify Microhard Systems Inc. and its respective directors, officers, employees, successors and assigns including any subsidiaries, related corporations, or affiliates, shall be released and discharged from any and all manner of action, causes of action, liability, losses, damages, suits, dues, sums of
money, expenses (including legal fees), general damages, special damages, including without limitation,
claims for personal injuries, death or property damage related to the products sold hereunder, costs and demands of every and any kind and nature whatsoever at law.
IN NO EVENT WILL MICROHARD SYSTEMS INC. BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL,
INCIDENTAL, BUSINESS INTERRUPTION, CATASTROPHIC, PUNITIVE OR OTHER DAMAGES WHICH MAY BE
CLAIMED TO ARISE IN CONNECTION WITH THE HARDWARE, REGARDLESS OF THE LEGAL THEORY BEHIND
SUCH CLAIMS, WHETHER IN TORT, CONTRACT OR UNDER ANY APPLICABLE STATUTORY OR REGULATORY
LAWS, RULES, REGULATIONS, EXECUTIVE OR ADMINISTRATIVE ORDERS OR DECLARATIONS OR OTHERWISE,
EVEN IF MICROHARD SYSTEMS INC. HAS BEEN ADVISED OR OTHERWISE HAS KNOWLEDGE OF THE POSSIBILITY OF SUCH DAMAGES AND TAKES NO ACTION TO PREVENT OR MINIMIZE SUCH DAMAGES. IN THE EVENT
THAT REGARDLESS OF THE WARRANTY DISCLAIMERS AND HOLD HARMLESS PROVISIONS INCLUDED ABOVE
MICROHARD SYSTEMS INC. IS SOMEHOW HELD LIABLE OR RESPONSIBLE FOR ANY DAMAGE OR INJURY, MICROHARD SYSTEMS INC.'S LIABILITY FOR ANYDAMAGES SHALL NOT EXCEED THE PROFIT REALIZED BY MICROHARD SYSTEMS INC. ON THE SALE OR PROVISION OF THE HARDWARE TO THE CUSTOMER.
Proprietary Rights
The Buyer hereby acknowledges that Microhard Systems Inc. has a proprietary interest and intellectual property rights in the Hardware, Software and/or Products. The Purchaser shall not (i) remove any copyright, trade
secret, trademark or other evidence of Microhard Systems Inc.’s ownership or proprietary interest or confiden-
tiality other proprietary notices contained on, or in, the Hardware, Software or Products, (ii) reproduce or modify any Hardware, Software or Products or make any copies thereof, (iii) reverse assemble, reverse engineer or
decompile any Software or copy thereof in whole or in part, (iv) sell, transfer or otherwise make available to
others the Hardware, Software, or Products or documentation thereof or any copy thereof, except in accordance with this Agreement.
© Microhard Systems Inc. 2
Page 3

Important User Information (continued)
About This Manual
It is assumed that users of the products described herein have either system integration or
design experience, as well as an understanding of the fundamentals of radio communications.
Throughout this manual you will encounter not only illustrations (that further elaborate on the
accompanying text), but also several symbols which you should be attentive to:
Caution or Warning
Usually advises against some action which could result in undesired or
detrimental consequences.
Point to Remember
Highlights a key feature, point, or step which is noteworthy. Keeping
these in mind will simplify or enhance device usage.
Tip
An idea or suggestion to improve efficiency or enhance usefulness.
Information
Information regarding a particular technology or concept.
© Microhard Systems Inc. 3
Page 4

Important User Information (continued)
Regulatory Requirements / Exigences Réglementaires
To satisfy FCC RF exposure requirements for mobile transmitting devices, a separation distance of 23cm or more should be maintained
between the antenna of this device and persons during device operation. To ensure compliance, operations at closer than this distance is not
recommended. The antenna being used for this transmitter must not be co-located in conjunction with any other antenna or transm itter.
WARNING
WARNING
WARNING
Pour satisfaire aux exigences de la FCC d'exposition RF pour les appareils mobiles de transmission, une distance de séparatio n de 23cm ou
plus doit être maintenue entre l'antenne de cet appareil et les personnes au cours de fonctionnement du dispositif. Pour assurer le respect,
les opérations de plus près que cette distance n'est pas recommandée. L'antenne utilisée pour ce transmetteur ne doit pas être co-localisés
en conjonction avec toute autre antenne ou transmetteur.
MAXIMUM EIRP
FCC Regulations allow up to 36dBm Effective Isotropic Radiated Power (EIRP). Therefore, the sum of the transmitted power (in dBm), the
cabling loss and the antenna gain cannot e xceed 36dBm.
Réglementation de la FCC permettra à 36dBm Puissance isotrope rayonnée équivalente (EIRP). Par conséquent, la somme de la pui ssance
transmise (en dBm), la perte de câblage et le gain d'antenne ne peut pas dépasser 36dBm.
EQUIPMENT LABELING / ÉTIQUETAGE DE L'ÉQUIPEMENT
This device has been modularly approved. The manufacturer, product name, and FCC and Industry Canada identifiers of this product must
appear on the outside label of the end-user equipment.
Ce dispositif a été approuvé de façon modulaire. Le fabricant, le nom du produit, et la FCC et de l'Industrie du Canada identifiants de ce
produit doit figurer sur l'étiquette à l'extérieur de l'équipement de l'utilisateur final.
SAMPLE LABEL REQUIREMENT / EXIGENCE D'ÉTIQUETTE :
BulletPlus (Contains):
FCCID: NS915PX2
IC: 3142A-15PX2
This device complies with Part 15 of the FCC Rules.
Operation is subject to the following two conditions:
(1) this device may not cause harmful interference,
and (2) this device must accept any interference
received including interference that may cause
undesired operation.
Please Note: These are only sample labels; different products contain different identifiers. The actual identifiers should be seen on
your devices if applicable. S'il vous plaît noter: Ce sont des exemples d'étiquettes seulement; différents produits contiennent des
identifiants différents. Les identifiants réels devrait être vu sur vos périphériques le cas échéant.
© Microhard Systems Inc. 4
Page 5

CSA Class 1 Division 2 Option
CSA Class 1 Division 2 is Available Only on Specifically Marked Units
If marked this for Class 1 Division 2 – then this product is available for use in Class 1 Division 2, in the indicated Groups on the
product.
In such a case the following must be met:
The transceiver is not acceptable as a stand-alone unit for use in hazardous locations. The transceiver must be mounted within a
separate enclosure, which is suitable for the intended application. Mounting the units within an approved enclosure that is c ertified
for hazardous locations, or is installed within guidelines in accordance with CSA rules and local electrical and fire code, w ill ensure
a safe and compliant installation.
The antenna feed line; DC power cable and interface cable must be routed through conduit in accordance with the National
Electrical Code.
Do not connect or disconnect equipment unless power has been switched off or the area is known to be non-hazardous.
Installation, operation and maintenance of the transceiver should be in accordance with the transceiver’s installation manual , and
the National Electrical Code.
Tampering or replacement with non-factory components may adversely affect the safe use of the transceiver in hazardous
locations, and may void the approval.
The wall adapters supplied with your transceivers are NOT Class 1 Division 2 approved, and therefore, power must be supplied to
the units using the screw-type or locking type c onnectors supplied from Microhard Systems Inc. and a Class 1 Division 2 power
source within your panel.
If you are unsure as to the specific wiring and installation guidelines for Class 1 Division 2 codes, contact CSA Internation al.
CSA Classe 1 Division 2 est disponible uniquement sur les unités particulièrement
marquées
Si marqué cette Classe 1 Division 2 - alors ce produit est disponible pour une utilisation en Classe 1 Division 2 , dans les groupes
indiqués sur le produit .
Dans un tel cas, la suivante doit être remplie:
L'émetteur-récepteur n'est pas acceptable comme une unité autonome pour une utilisation dans des endroits dangereux .
L'émetteur-récepteur doit être monté dans un boîtier séparé , qui est approprié pour l'application envisagée. Montage des unités
dans une enceinte approuvée qui est certifié pour les emplacements dangereux , ou est installé à l'intérieur des lignes direc trices ,
conformément aux règles de la CSA et le code électrique local et le feu , assurera une installation sûre et conforme .
La ligne d'alimentation d'antenne , câble d'alimentation CC et le câble d'interface doivent être acheminés à travers le conduit en
conformité avec le National Electrical Code .
Ne pas connecter ou déconnecter l'équipement que l'alimentation est coupée ou que la zone est connue pour être non
dangereux .
Installation, l'exploitation et la maintenance de l'émetteur-récepteur doivent être en conformité avec le manuel d'installation de
l'émetteur-récepteur , et le National Electrical Code .
Falsification ou le remplacement des c omposants non - usine peut nuire à l'utilisation sécuritaire de l'émetteur-récepteur dans des
endroits dangereux , et peut annuler l'approbation .
Les adaptateurs muraux fournis avec les émetteurs-récepteurs sont PAS classe 1, division 2 ont approuvé , et par conséquent,
doit être alimenté pour les unités à l'aide des connecteurs de type vis ou verrouillage fournies par Microhard Systems Inc. et une
Division 2 source d'alimentation de classe 1 au sein de votre panneau .
Si vous n'êtes pas sûr de l' installation et de câblage des lignes directrices spécifiques pour la classe 1 Division 2 codes ,
communiquer avec la CSA International.
© Microhard Systems Inc. 5
Page 6
Revision History
Revision Description Initials Date
1.0 Preliminary. (Firmware v1.3.0-r1009-28) PEH Nov 2015
1.1 Updated to firmware v1.3.0-r1010. Added Bandwidth, Cloud Filter,
Webfilter, MultiWAN, GRE. Misc updates to screenshots & formatting.
1.2 Updated to firmware v1.3.0-r1012. Misc corrections, added VRRP,
updated Data Usage, Carrier Settings.
1.3 Updated to firmware v1.3.0-r1014. PEH May 2016
1.3.1 Misc. correcstions. PEH June 2016
PEH Dec 2015
PEH Apr 2016
© Microhard Systems Inc. 6
Page 7

Table of Contents
1.0 Overview ......................................................................................................... 10
1.1 Performance Features ................................................................................................... 10
1.2 Specifications ................................................................................................................ 11
2.0 QUICK START ................................................................................................. 13
2.1 Installing the SIM Card .................................................................................................. 13
2.2 Getting Started with Cellular .......................................................................................... 13
3.0 Hardware Features ......................................................................................... 17
3.1 BulletPlus ...................................................................................................................... 17
3.1.1 BulletPlus Mechanical Drawings .......................................................................... 18
3.1.2 BulletPlus Mounting Bracket (Optional) ................................................................ 19
3.1.2 BulletPlus Connectors & Indicators ...................................................................... 20
3.1.2.1 Front & Top ........................................................................................... 20
3.1.2.2 Rear & Side ........................................................................................... 21
4.0 Configuration.................................................................................................. 22
4.0 Web User Interface ...................................................................................................... 22
4.0.1 Logon Window ..................................................................................................... 23
4.1 System ......................................................................................................................... 24
4.1.1 Summary ............................................................................................................. 24
4.1.2 Settings ............................................................................................................... 25
Host Name .......................................................................................................... 25
Console Timeout.................................................................................................. 25
Date/Time ............................................................................................................ 26
NTP Server Settings ............................................................................................ 27
4.1.3 Services .............................................................................................................. 28
FTP ..................................................................................................................... 28
Telnet .................................................................................................................. 28
HTTP/HTTPS ...................................................................................................... 28
4.1.4 Keepalive............................................................................................................. 29
4.1.5 Maintenance ........................................................................................................ 31
Firmware Upgrade ............................................................................................... 31
Reset to Default ................................................................................................... 31
Backup & Restore Configurations ........................................................................ 32
4.1.6 Reboot ................................................................................................................. 33
4.2 Network ....................................................................................................................... 34
4.2.1 Summary ............................................................................................................. 34
4.2.2 LAN ..................................................................................................................... 35
LAN DHCP .......................................................................................................... 37
VLAN Configuration ............................................................................................. 39
4.2.3 WAN .................................................................................................................... 40
4.2.4 DHCP (MAC Binding) .......................................................................................... 42
4.2.5 DDNS .................................................................................................................. 43
4.2.6 Routes ................................................................................................................. 44
4.2.7 VRRP (Virtual Router Redundancy Protocol) ....................................................... 46
4.2.8 Ports (Switch) ...................................................................................................... 47
4.2.9 Bandwidth (Throttling Control) .............................................................................. 48
4.2.10 Device List.......................................................................................................... 49
4.2.11 Cloud Filter (Content/Security Filter) ................................................................... 50
4.2.12 WebFilter (MAC/Network Content Filter) ............................................................. 51
4.2.13 MultiWAN ........................................................................................................... 53
© Microhard Systems Inc. 7
Page 8

Table of Contents
4.3 Carrier .......................................................................................................................... 56
4.3.1 Status .................................................................................................................. 56
4.3.2 Settings ............................................................................................................... 57
Dual Cards Management ..................................................................................... 58
APN ..................................................................................................................... 59
4.3.3 SMS .................................................................................................................... 61
4.3.4 SMS Config ......................................................................................................... 61
SMS Commands.................................................................................................. 61
SMS Alerts .......................................................................................................... 63
4.3.5 Data Usage ......................................................................................................... 65
Data Usage History .............................................................................................. 68
4.4 Wireless ....................................................................................................................... 69
4.4.1 Status .................................................................................................................. 69
4.4.2 Radio1 ................................................................................................................. 70
Radio1 Phy Configuration .................................................................................... 70
Radio Virtual Interface ......................................................................................... 73
4.4.3 Hotspot ................................................................................................................ 76
4.5 Firewall ....................................................................................................................... 80
4.5.1 Summary ............................................................................................................. 80
4.5.2 General ............................................................................................................... 81
4.5.3 Port Forwarding ................................................................................................... 83
4.5.4 MAC-IP List ......................................................................................................... 85
4.5.5 Rules ................................................................................................................... 87
4.5.6 Firewall Default .................................................................................................... 89
4.6 VPN ............................................................................................................................ 90
4.6.1 Summary ............................................................................................................. 90
4.6.2 Gateway to Gateway............................................................................................ 91
4.6.3 Client to Gateway (L2TP Client) ........................................................................... 96
4.6.4 OpenVPN ............................................................................................................ 98
OpenVPN Server ................................................................................................. 98
OpenVPN Client .................................................................................................. 101
4.6.4 GRE .................................................................................................................... 103
4.6.5 VPN Users ........................................................................................................... 106
4.6.6 Certificate Managment ......................................................................................... 107
4.7 Router .......................................................................................................................... 108
4.7.1 RIPV2 .................................................................................................................. 108
4.7.2 OSPF .................................................................................................................. 109
4.8 Serial ............................................................................................................................ 110
4.8.1 Summary ............................................................................................................. 110
4.8.2 Settings ............................................................................................................... 111
USB ..................................................................................................................... 111
Data Baud Rate ................................................................................................... 112
IP Protocol Config ................................................................................................ 114
TCP Client ...................................................................................................... 114
TCP Server ..................................................................................................... 114
TCP Client/Server ........................................................................................... 115
UDP Point-to-Point .......................................................................................... 115
SMTP Client .................................................................................................... 115
PPP ................................................................................................................ 116
GPS Transparent Mode .................................................................................. 117
4.9 I/O ................................................................................................................................ 118
4.9.1 Settings ............................................................................................................... 118
© Microhard Systems Inc. 8
Page 9

Table of Contents
4.10 GPS .............................................................................................................................. 120
4.10.1 Location ............................................................................................................. 120
4.10.2 Settings .............................................................................................................. 121
4.10.3 Report ................................................................................................................ 122
4.10.4 GPSGate ............................................................................................................ 124
4.10.5 Recorder ............................................................................................................ 127
4.10.6 Load Record ....................................................................................................... 129
4.10.7 TAIP ................................................................................................................... 131
4.11 Apps ............................................................................................................................ 133
4.11.1 Modbus .............................................................................................................. 133
4.11.1.1 TCP Modbus ........................................................................................ 133
4.11.1.2 Serial (COM) Modbus........................................................................... 135
4.11.1.3 Modbus Data Map ................................................................................ 136
4.11.2 Netflow Report ................................................................................................... 137
4.11.3 Local Monitor ..................................................................................................... 138
4.11.4 Event Report ...................................................................................................... 140
4.11.4.1 Configuration ....................................................................................... 140
4.11.4.2 Message Structure ............................................................................... 141
4.11.4.2 Message Payload................................................................................. 142
4.11.5 Websocket ......................................................................................................... 143
4.12 Diag .............................................................................................................................. 145
4.12.1 Ping.................................................................................................................... 145
4.12.2 Traceroute .......................................................................................................... 145
4.12.3 Iperf.................................................................................................................... 146
4.13 Admin .......................................................................................................................... 148
4.13.1 Users ................................................................................................................. 148
4.13.2 Authentication (RADIUS) .................................................................................... 150
4.13.3 NMS .................................................................................................................. 151
4.13.4 SNMP ................................................................................................................ 155
4.13.5 Discovery ........................................................................................................... 158
4.13.6 Logout ................................................................................................................ 159
5.0 AT Command Line Interface........................................................................... 160
5.1 AT Command Overview .............................................................................................. 160
5.1.1 Serial Port .......................................................................................................... 160
5.1.2 Telnet................................................................................................................. 161
5.2 AT Command Syntax .................................................................................................. 162
5.3 Supported AT Commands .......................................................................................... 163
Appendices .......................................................................................................... 212
Appendix A: Serial Interface .................................................................................................. 212
Appendix B: IP-Passthrough Example ................................................................................... 213
Appendix C: Port Forwarding Example .................................................................................. 215
Appendix D: VPN (Site to Site) Example ............................................................................... 217
Appendix E: Firewall Rules Example ..................................................................................... 219
Appendix F: Port Forwarding w/IP-Passthrough (Iperf) .......................................................... 221
Appendix G: Troubleshooting ................................................................................................ 223
© Microhard Systems Inc. 9
Page 10

1.0 Overview
The BulletPlus is a high-performance Cellular Dual Ethernet/Serial/USB Gateways w/WiFi,
equipped with 3x RJ45 Ethernet Ports, dual SIM capability, 2x Programmable Analog I/O,
Standalone GPS, 802.11b/g/n WiFi, and an RS232 serial communication port.
The BulletPlus utilizes the cellular infrastructure to provide network access to wired or wireless devices anywhere cellular coverage is supported by a cellular carrier. The BulletPlus
supports 4G/LTE connections with blazing fast speeds.
Providing reliable Cellular Ethernet bridge functionality as well gateway service for most
equipment types which employ an RS232, RJ45 or WiFi interface, the BulletPlus can be used
in a limitless types of applications such as:
High-speed backbone
IP video surveillance
Voice over IP (VoIP)
Facilitating internetwork
wireless communications
Legacy network/device
migration
SCADA (PLC’s, Modbus,
Hart)
1.1 Performance Features
Key performance features of the BulletPlus include:
Fast, reliable connection speeds to 4G, 3G, LTE, and HSPA Networks (varies by
model)
2x Programmable Analog/Digital Inputs OR up to 8 Digital Outputs
DMZ and Port Forwarding
3x 10/100 Ethernet Ports (WAN/2LAN)
Standalone GPS (TCP Server/UDP/SMTP Reporting)
User interface via local console, telnet, web browser
Compatibility with virtually all PLCs, RTUs, and other RS232 serial devices.
Local & remote wireless firmware upgradable
User configurable Firewall with IP/MAC ACL
IP/Sec secure VPN and GRE Tunneling
Industrial Temperature Rating (-40oC to +85oC)
© Microhard Systems Inc. 10
Page 11
1.0 Overview
1.2 Specifications
BulletPlus
BulletPlus Supported Bands: LTE FDD (Bands 1-5,7,8,13,17,18,19,20)
(North America) UMTS | DC-HSPA+ (Bands 1,2,4,5,8)
GSM | GPRS | EDGE (Bands 2,3,5,8)
3GPP Protocol Stack Release 9
BulletPlus Supported Bands: LTE FDD: Band 1, 3, 8, all bands with diversity
(China) LTE TDD: Band 39, 40, 41(38), all bands with diversity
DC-HSPA+/HSPA+/HSPA/UMTS: Band 1, 5, 8, 9, all bands
with diversity
TD-SCDMA: Band 34, 39, all bands with diversity
GSM/GPRS/EDGE: 1800 MHz/900 MHz
BulletPlus Data Features: LTE: DL 100 Mbps, UL 50 Mbps
(North America) HSPA+: DL 42 Mbps, UL 5.7 Mbps
HSPA+: DL 21 Mbps, UL 5.7 Mbps
WCDMA: DL/UL 384 kbps
EDGE Class 33: DL/UL 236.8 kbps
GPRS Class 33: DL/UL 85.6kbps
BulletPlus Data Features: LTE FDD: UL 50Mbit/s, DL 150Mbit/s @20M BW cat4
(China) LTE TDD: UL 10Mbit/s; DL 112Mbit/s @20M BW cat4
TD-SCDMA PS: UL 384 kbit/s; DL 384 kbit/s
TD-HSPA+: UL 2.2 Mbit/s; DL 4.2 Mbit/s
DC-HSPA+: UL 5.76 Mbit/s; DL 42 Mbit/s
HSPA+: UL 5.76 Mbit/s; DL 21.6 Mbit/s
WCDMA PS: UL 384 kbit/s; DL 384 kbit/s
WCDMA CS: UL 64 kbit/s; DL 64 kbit/s
EDGE: UL 236.8 kbit/s; DL 236.8 kbit/s
GPRS: UL 85.6 kbit/s; DL 85.6 kbit/s
General
Serial Interface: RS232, RS485, RS422
Serial Baud Rate: 300bps to 921kbps
USB*: USB 2.0
(*Future) USB Console Port
USB to Serial Data Routing
USB to Ethernet Data Routing (NDIS)
Current Consumption:
(@12VDC)
BulletPlus 120 170
BulletPlus + Serial Data 142 180
BulletPlus + Ethernet 155 195
BulletPlus Peak 230 305
Model AVG (mA) w/WiFi (AP)
© Microhard Systems Inc. 11
Page 12

1.0 Overview
General Specifications (Continued)
Ethernet: 2 x LAN 10/100 BaseT, Auto - MDI/X, IEEE 802.3
1 x WAN 10/100 BaseT, Auto - MDI/X, IEEE 802.3
I/O: 2x Programmable Analog/Digital Inputs or up to 2x Digital Outputs
60mA current sink on open drain
SIM Card: Dual: 1.8 / 3.0V Standard/2FF size
PPP Characteristics: Dial on Demand/Idle Time
Network Protocols: TCP, UDP, TCP/IP, TFTP, ARP, ICMP, DHCP, HTTP, HTTPS*, SSH*, SNMP,
FTP, DNS, Serial over IP, QoS
Management: Local Serial Console, Telnet, WebUI, SNMP, FTP &
Wireless Upgrade, RADIUS authentication, IPsec VLAN
Diagnostics: Temperature, RSSI, remote diagnostics
Input Voltage: 7-30 VDC
Power over Ethernet: Passive PoE on Ethernet Port (WAN)
GPS: Sensitivity: - Autonomous acquisition: -145 dBm
- Tracking Sensitivity: -158 dBm (50% valid fixes)
Position Accuracy: - Tracking L1, CA code
- 12 Channels
- Max. update rate 1 Hz
Error calculated location less than 11.6 meters 67% of the time, and
less than 24.2 meters 95% of the time.
Environmental
Operation Temperature: -40
Humidity: 5% to 95% non-condensing
o
F(-40oC) to 185oF(85oC)
Mechanical
Dimensions: 2.21” (56mm) X 3.85” (97mm) X 1.46” (37mm)
Weight: Approx. 245 grams
Connectors: Antenna(s): CELL, DIV, GPS: SMA Female
ANT3: RP-SMA Female
Data, etc: Data: DE-9 Female (Front RS232)
Ethernet : 2x RJ-45
GPS Antenna Requirements:
- Frequency Range: 1575.42 MHz (GPS L1 Band)
- Bandwidth: +/- 2 MHz
- Total NF < 2.5dB
- Impedance 50ohm
- Amplification (Gain applied to RF connector): 19dB to 23dB
- Supply voltage 1.5V to 3.05V
- Current consumption - T ypical 20mA (100mA max)
- Cellular Power Antenna Rejection + Isolation:
- 824 - 915 MHz > 10dB
- 1710 - 1785 MHz > 19dB
- 1850 - 1980 MHz > 23dB
© Microhard Systems Inc. 12
Page 13
2.0 Quick Start
This QUICK START guide will walk you through the setup and process required to access the
WebUI configuration window and to establish a basic wireless connection to your carrier.
Note that the units arrive from the factory with the Local Network setting configured as
‘Static’ (IP Address 192.168.168.1, Subnet Mask 255.255.255.0, and Gateway
192.168.168.1), in DHCP server mode. (This is for the LAN Ethernet Adapter on the back of
the BulletPlus unit.)
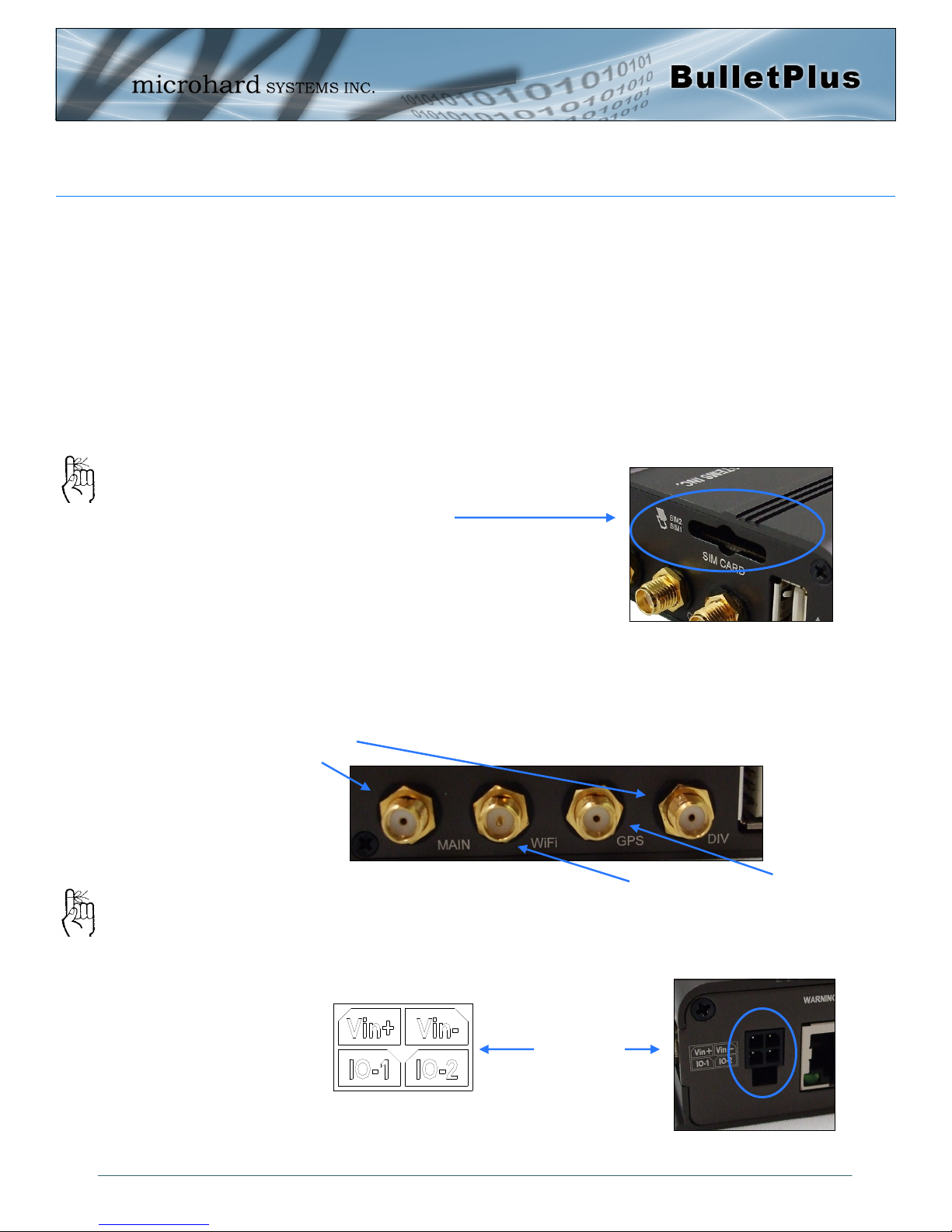
2.1 Installing the SIM Card
Before the BulletPlus can be used on a cellular network a valid SIM Card for your Wire-
less Carrier must be installed. Insert the SIM Card into the slot as shown, the bottom
SIM slot is for SIM1: (The contacts should face down, and the notch to the right)
To reset to factory
defaults, press and hold
the CFG button for 8
seconds with the
BulletPlus powered up.
The LED’s will flash
quickly and the modem
will reboot with factory
defaults.
Use the MHS-supplied
power adapter or an
equivalent power source.
The unit can also be powered
via PoE using a MHS PoE
injector.
2.2 Getting Started with Cellular
Connect the Antenna’s to the applicable ANTENNA jack’s of the BulletPlus.
Connect the power connector to the power adapter and apply power to the unit, the CPU
LED will flash during boot-up, once on solid, proceed to the next step.
SIM Card Slot (s)
Cellular
Antenna’s
7-30VDC
WiFi Antenna
GPS Antenna
© Microhard Systems Inc. 13
Page 14

2.0 Quick Start
Connect A PC configured for DHCP directly to a LAN port of the BulletPlus, using an
Ethernet Cable. If the PC is configured for DHCP it will automatically acquire a IP Address
from the BulletPlus.
Open a Browser Window and enter the IP address 192.168.168.1 into the address bar.
The factory default network
settings:
IP: 192.168.168.1
Subnet: 255.255.255.0
Gateway: 192.168.168.1
The factory default login:
User name: admin
Subnet: admin
It is always a good idea to
change the default admin
login for future security.
The BulletPlus will then ask for a Username and Password. Enter the factory defaults listed
below.
192.168.168.1
The Factory default login:
User name: admin
Password: admin
As of Firmware version v1.3.0r1014 you will be required to
change the default password
when you login for the first time.
© Microhard Systems Inc. 14
Page 15
2.0 Quick Start
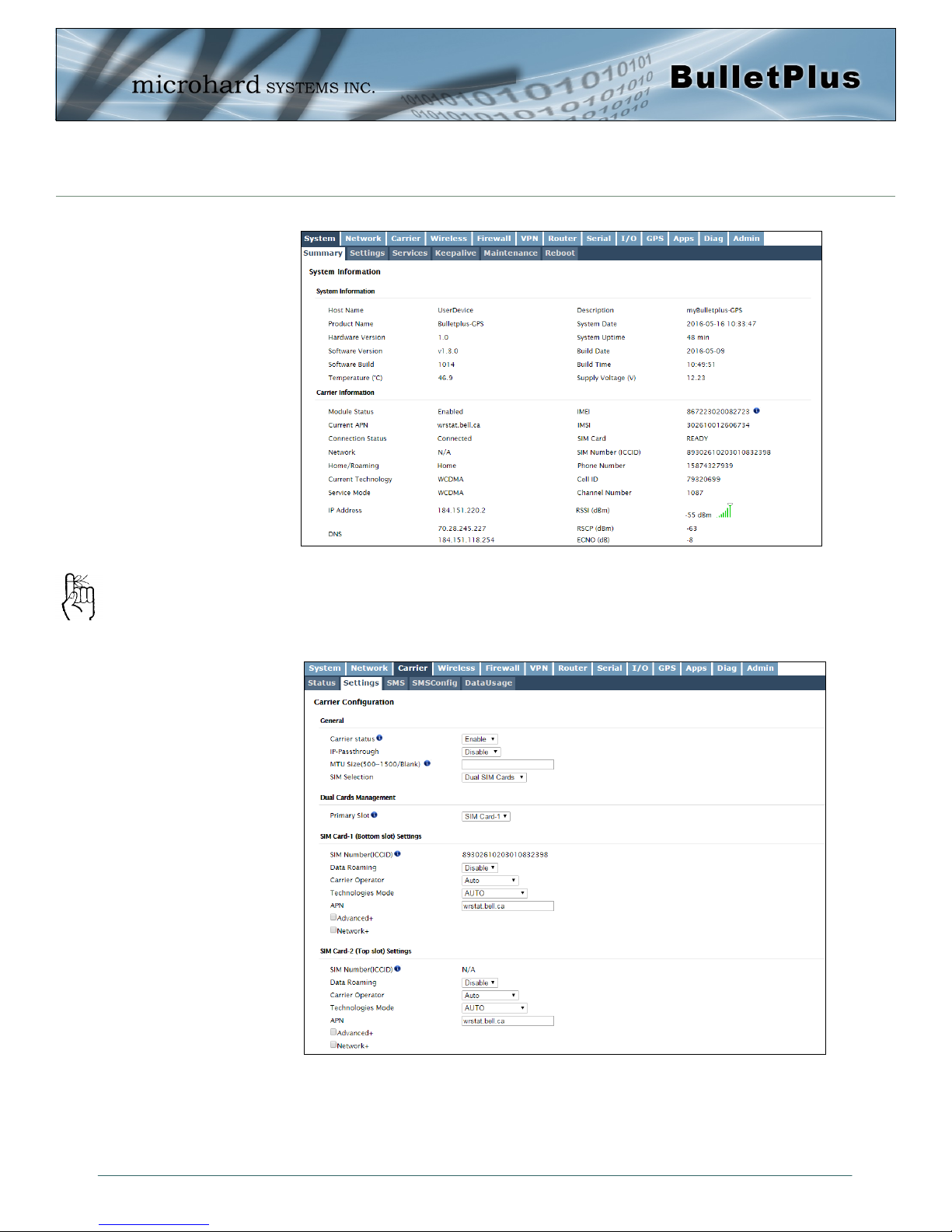
Once successfully logged in, the System Summary page will be displayed.
As seen above under Carrier Status, the SIM card is installed, but an APN has not been
specified. Setting the APN to auto (default) may provide quick network connectivity, but
may not work with some carriers, or with private APN’s. To set or change the APN, click
on the Carrier > Settings tab and enter the APN supplied by your carrier in the APN field.
Auto APN: The BulletPlus
will attempt to detect the
carrier based on the SIM card
installed and cycle through a
list of commonly used APN’s
to provide quick network
connectivity.
Some carriers may also require a Username and Password.
Once the APN and any other required information is entered to connect to your carrier,
click on “Submit”.
© Microhard Systems Inc. 15
Page 16
2.0 Quick Start
On the Carrier > Status Tab, verify that a WAN IP Address has been assigned by your
carrier. It may take a few minutes, so try refreshing the page if the WAN IP Address
doesn’t show up right away. The Activity Status should also show “Connected”.
If you have set a static IP on your PC, you may need to add the DNS Servers shown in
the Carrier Status Menu to you PC to enable internet access.
Congratulations! Your BulletPlus is successfully connected to your Cellular Carrier.
Ensure the default
passwords are changed.
Set up appropriate firewall
rules to block unwanted
incoming data.
To access devices connected to BulletPlus remotely, one or more of the following must be
configured: IP-Passthrough, Port Forwarding, DMZ. Another option would be to set up a
VPN.
Ensure that all default passwords are changed to limit access to the modem.
(Firmware version v1.3.0-r1014 requires the defaults passwords are changed
upon initial login).
For best practices and to limit data charges it is critical to properly set up the
firewall. (Especially important for Public Static IP addresses.)
© Microhard Systems Inc. 16
Page 17

3.0 Hardware Features
3.1 BulletPlus
The BulletPlus is a fully-enclosed unit ready to be interfaced to external devices with standard connectors
as discussed below. An optional mounting bracket can be ordered to allow the BulletPlus to be mounted
for a fixed installation.
The BulletPlus Hardware Features Include:
Standard Connectors for:
3x 10/100 Ethernet Ports (RJ45 - 1xWAN / 2xLAN)
Data Port (RS232/DB9)
4-Pin: MATE-N-LOK Type Connector for Power / I/O 1/2
Cellular Antenna (SMA Female Antenna Connection x2)
GPS Antenna (SMA Female Antenna Connection)
WiFi Antenna (RP-SMA Female Antenna Connection)
Status/Diagnostic LED’s for RSSI(x3), Tx, Rx, GPS, CPU
Dual SIM (Mini-SIM (2FF)) Card Slots
CFG Button for factory default / firmware recovery operations
USB 2.0 Connector
Image 3-1: BulletPlus
© Microhard Systems Inc. 17
Page 18
3.0 Hardware Features
55.2
12.5 14.5 14.5 14.5 25.0
17.5
37.7
81.0
81.0
78.0
28.0
13.0
15.0
55.2
63.2
28.0
8.5
19.5
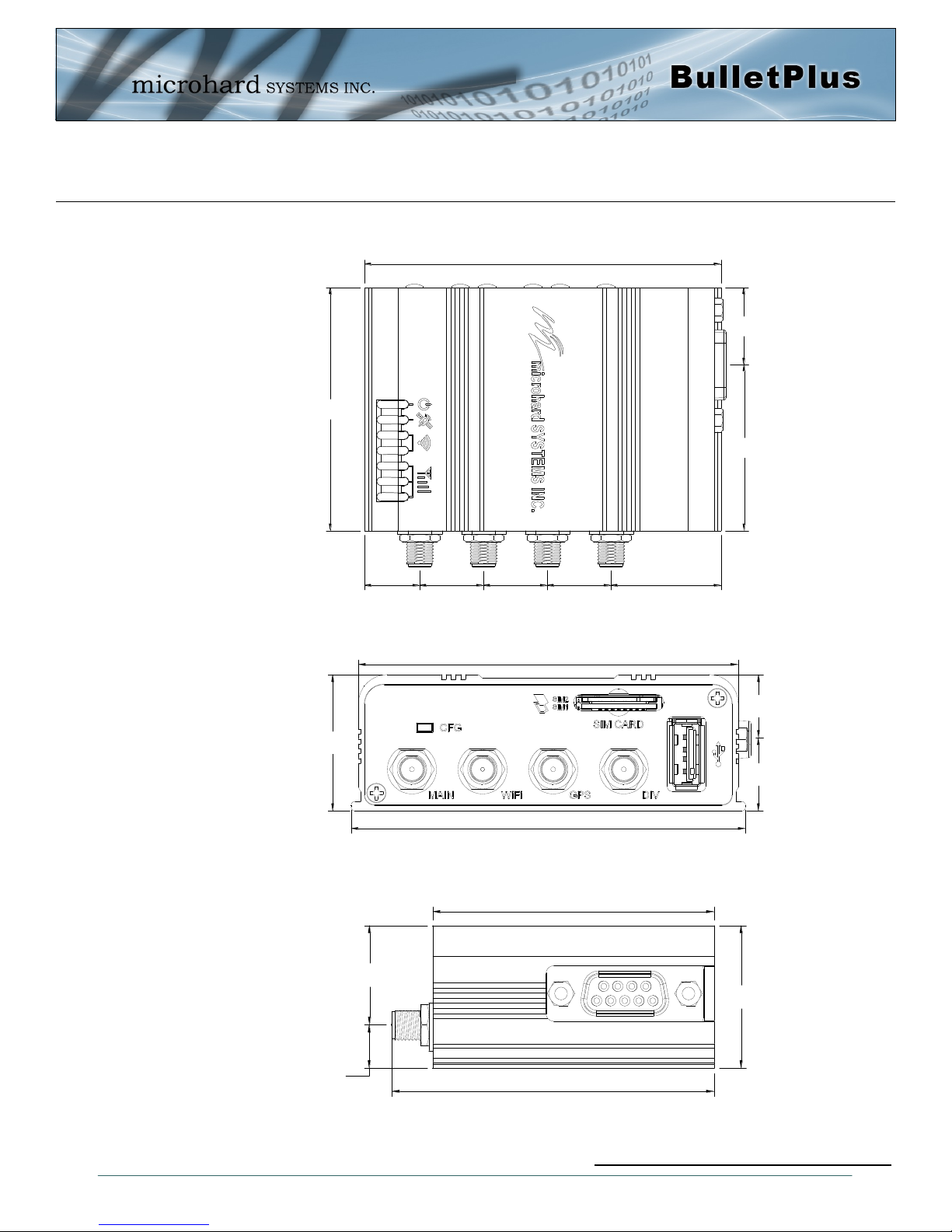
3.1.1 Mechanical Drawings
Drawing 3-1: BulletPlus Top View Dimensions
© Microhard Systems Inc. 18
Drawing 3-2: BulletPlus Back View Dimensions
Drawing 3-3: BulletPlus Side View Dimensions
Note: All dimension units: Millimeter
Page 19
3.0 Hardware Features
58.0
62.4
16.0
13.0
3.2
57.255.2
12.6
12.6
12.5
12.5
16.1
16.1
32.0
4.0
4.0
16.832.0
15.2
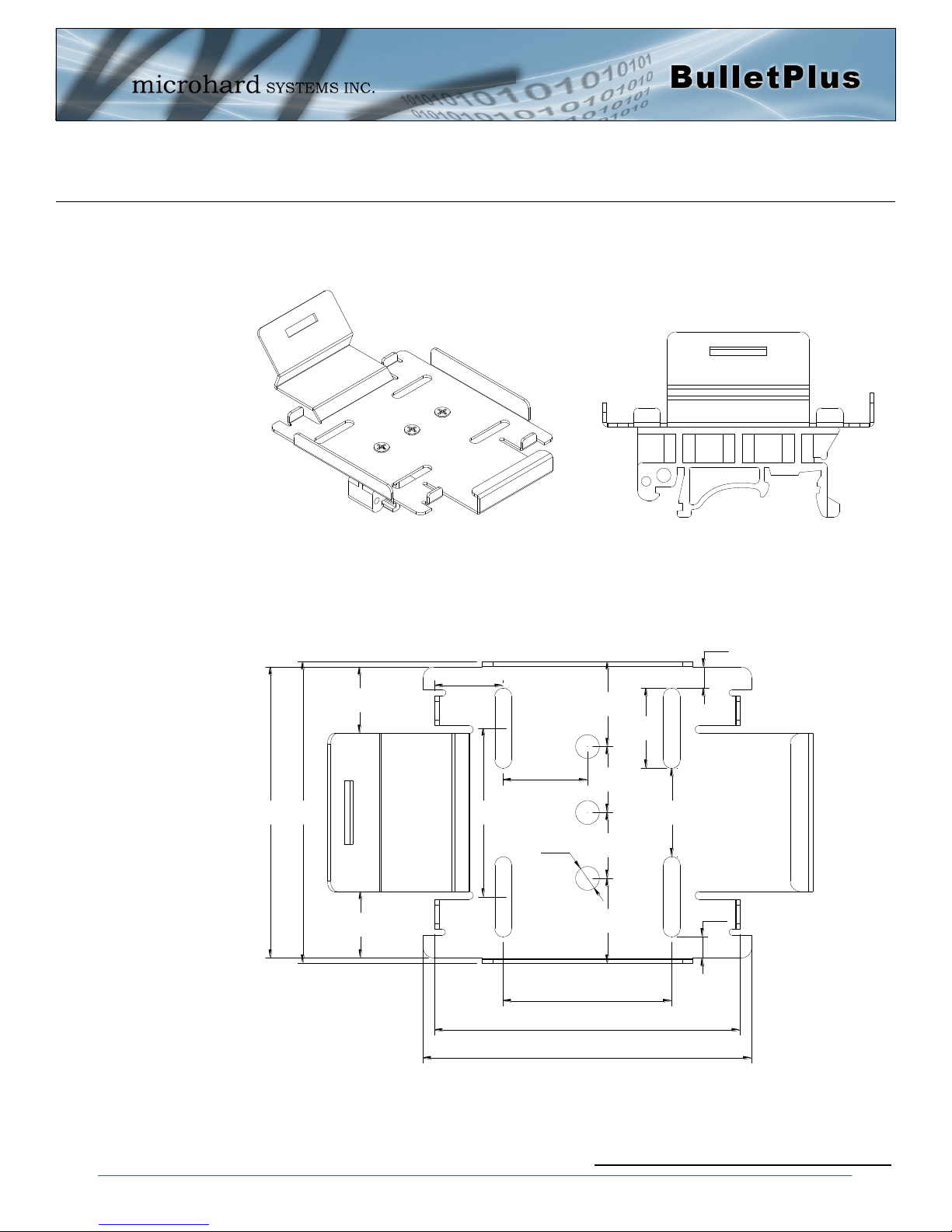
3.1.2 BulletPlus Mounting Bracket (Order Option)
Drawing 3-4: BulletPlus Top View Dimensions (Shown with removable TS35 DIN Rail Mount)
© Microhard Systems Inc. 19
Drawing 3-5: BulletPlus Mounting Bracket Dimensions
Note: All dimension units: Millimeter
Page 20
3.0 Hardware Features
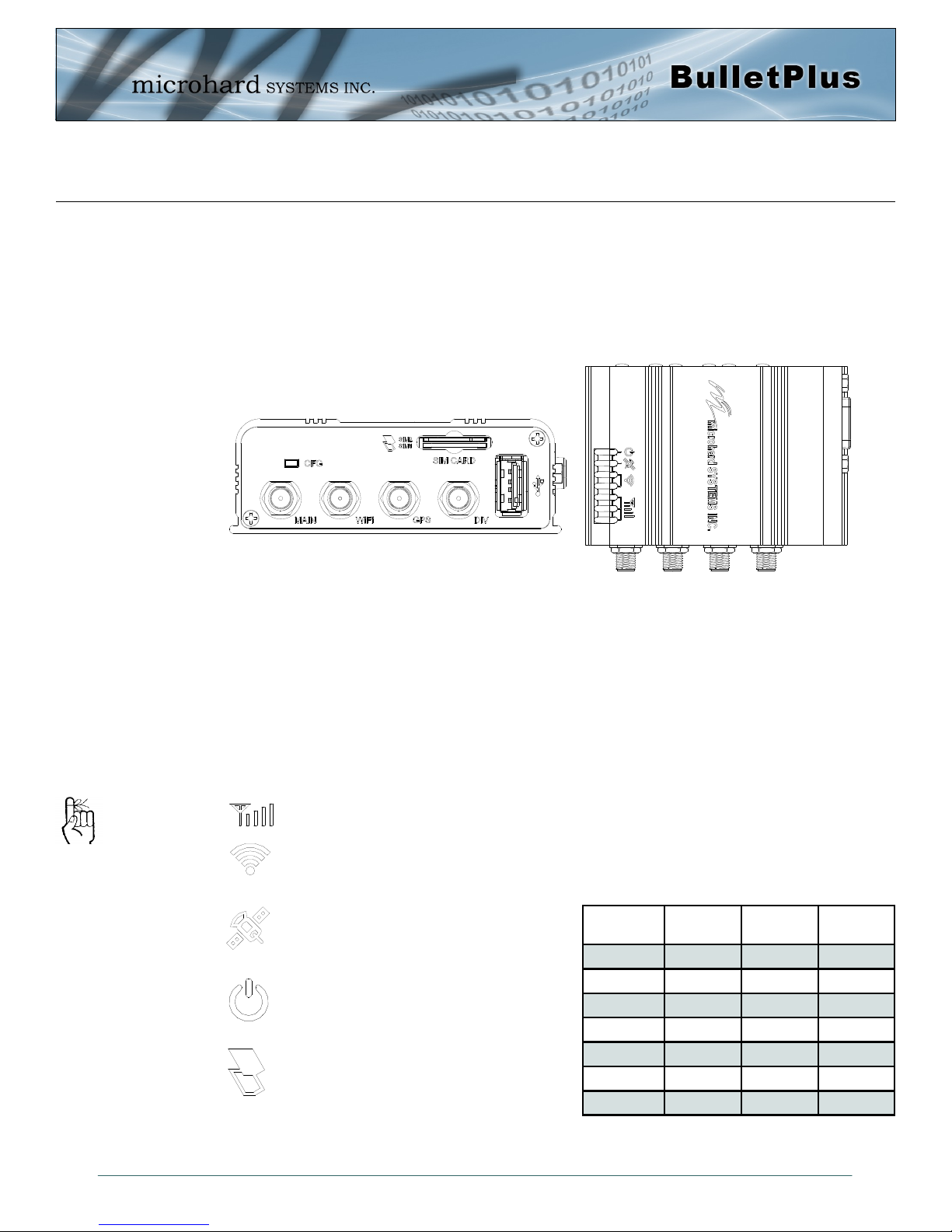
3.1.3 Connectors and Indicators
3.1.3.1 Front & Top
On the front of the Bullet is the CFG Button, USB Port, Main, GPS & Diversity, GPS & WIFI Antenna
Connectors and SIM Card Slot. The top of the Bullet are the status indicators, RSSI, Tx, RX, GPS and
PWR.
Drawing 3-6: Bullet Front & Top View
The factory default network
settings:
IP: 192.168.168.1
Subnet: 255.255.255.0
Gateway: 192.168.168.1
The USB port is a future development to be available in later releases of firmware.
CFG (Button) - Holding this button while powering-up the Bullet will boot the unit into FLASH FILE SYS-
TEM RECOVERY mode. The default IP address for system recovery (only - not for normal access to the
unit) is static: 192.168.1.39. Hold for 1 second for httpd recovery mode, 5 seconds for tftp recovery mode,
or 10 seconds for master reset. If button is held for longer than 15 seconds the button will be ignored.
If the unit has been powered-up for some time (>1 minute), depressing the CFG Button for ~10 seconds
(unit will reboot) will result in FACTORY DEFAULTS being restored, including the static factory IP address.
This IP address is useable in a Web Browser for accessing the Web User Interface.
Receive Signal Strength Indicator (RSSI) - As the received signal strength increases, starting
with the furthest left, the number of active RSSI LEDs increases.
Tx(Red)/Rx(Green) LED’s - The Tx/Rx LED’s indicate carrier (cellular) traffic.
GPS - Indicates that the optional standalone
GPS module has synchronized and is ready
for use.
PWR LED - The Power LED indicates that
power has been applied to the module.
Flashing indicates a bootup process.
SIM Card - This slot is used to install SIM
card(s) provided by the cellular carrier. Ensure
that the SIM card is installed properly by pay-
ing attention to the diagram printed next the
SIM card slot. The Bottom slot is SIM1, the contact
should face down, and the notch should be to the
Signal
(dBm)
(-85, 0] ON ON ON
(-90, -85] ON ON FLASH
(-95, -90] ON ON OFF
(-100, -95] ON FLASH OFF
(-105, -100] ON OFF OFF
(-109, -105] FLASH OFF OFF
Other SCANNING SCANNING SCANNING
RSSI1 RSSI2 RSSI3
Table 3-1: RSSI LED’s
right.
© Microhard Systems Inc. 20
Page 21
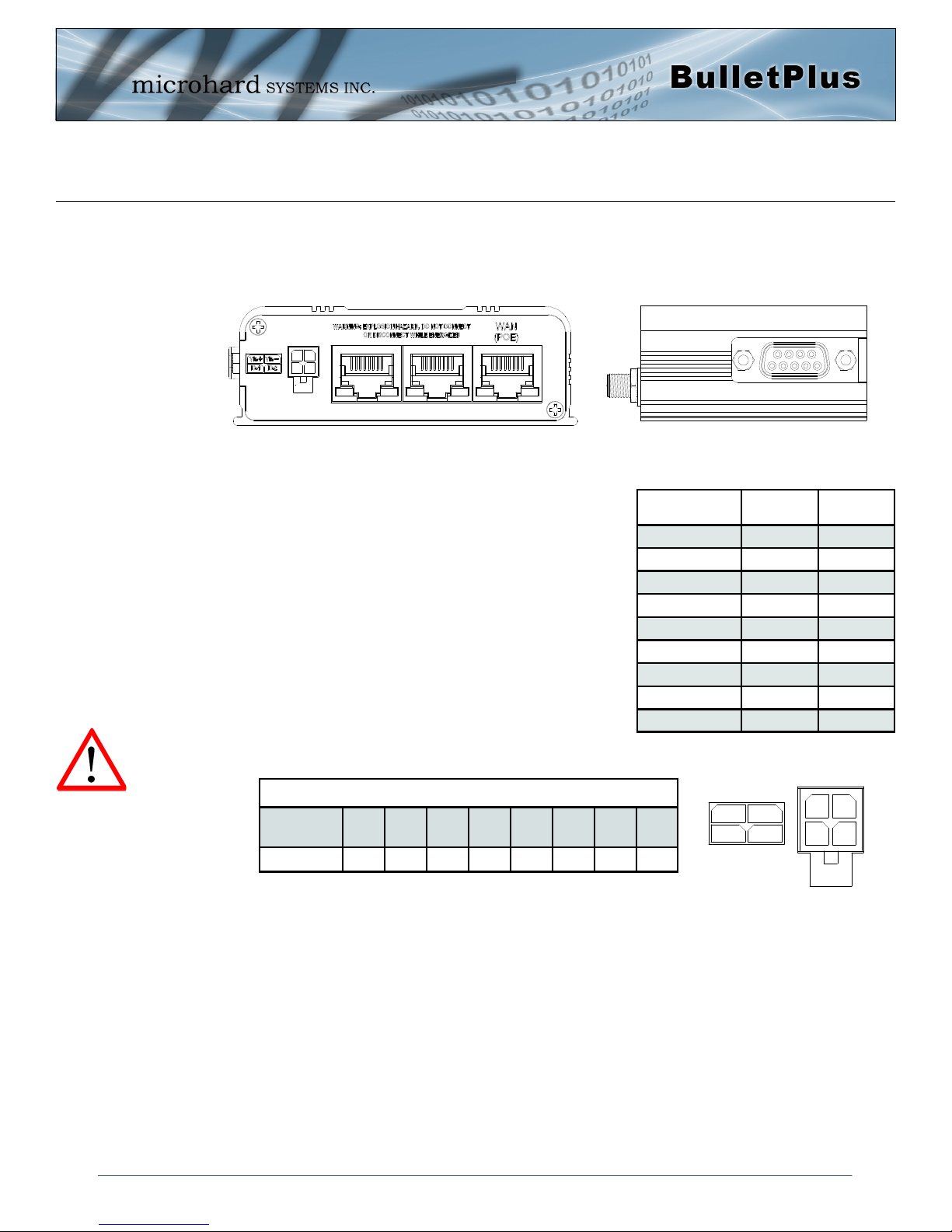
3.0 Hardware Features
Vin+
Vin-
IO-1
IO-2
3.1.3.2 Rear & Side View
On the side of the Bullet is the Data Port (RS232) and on the back are the Power and Ethernet(PoE)
interfaces and the 2x Programmable I/O.
Drawing 3-7: BulletPlus Rear & Side View
Caution: Using a power
supply that does not
provide proper voltage
may damage the modem.
The Data Port (RS232 DCE) on the side of the unit is used for
RS232 Serial Data based field devices at 300 bps to 921kbps.
The Ethernet Ports (2LAN/WAN) are 10/100 Mbps RJ-45
interfaces used to connect devices Ethernet based field devices.
Programmable I/O– The Bullet has 2 programmable Analog/
Digital Inputs or 2 Digital Outputs. Maximum recommended load
for the output pin is 150mA @ 30 Vdc (Vin).
Vin+/Vin– is used to power the unit. The input Voltage range is
7-30 Vdc.
PoE– The Bullet can also be powered using Passive PoE on the
Ethernet Port (WAN), via a PoE injector.
Ethernet RJ45 Connector Pin Number
Source
Voltage
9 - 30 Vdc Data Data Data DC+ DC+ Data DC- DC-
1 2 3 4 5 6 7 8
Table 3-3: Ethernet PoE Connections
Name Data Port Input or
DCD 1 O
RXD 2 O
TXD 3 I
DTR 4 I
SG 5
DSR 6 O
RTS 7 I
CTS 8 O
RING 9 O
Table 3-2: Data RS232 Pin Assignment
Output
© Microhard Systems Inc. 21
Page 22
4.0 Configuration
4.0 Web User Interface
The factory default network
settings:
IP: 192.168.168.1
Subnet: 255.255.255.0
Gateway: 192.168.168.1
Image 4-0-1: WebUI
Initial configuration of an BulletPlus using the Web User (Browser) Interface (Web UI) method involves the
following steps:
configure a static IP Address on your PC to match the default subnet or if your PC is configured for
DHCP, simply connect a PC to a LAN port of the BulletPlus and it will be assigned a IP address
automatically.
connect the BulletPlus ETHERNET(LAN) port to PC NIC card using an Ethernet cable
apply power to the BulletPlus and wait approximately 60 seconds for the system to load
open a web browser and enter the factory default IP address(192.168.168.1) of the unit:
logon window appears; log on using default Username: admin Password: admin
use the web browser based user interface to configure the BulletPlus as required.
refer to Section 2.0: Quick Start for step by step instructions.
In this section, all aspects of the Web Browser Interface, presented menus, and available configuration
options will be discussed.
© Microhard Systems Inc. 22
Page 23
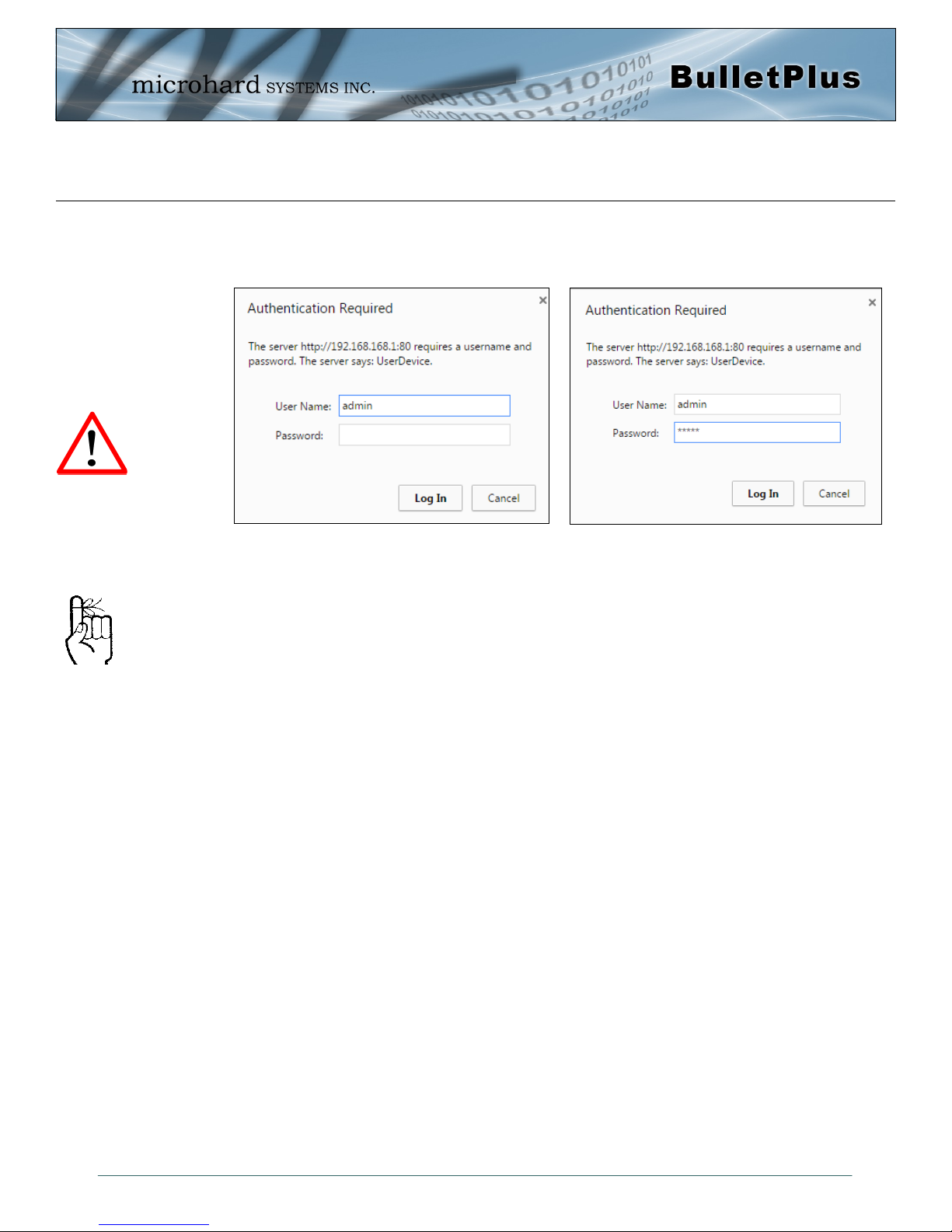
4.0 Configuration
4.0.1 Logon Window
Upon successfully accessing the BulletPlus using a Web Browser, the Logon window will appear.
For security, do not allow the
web browser to remember the
User Name or Password.
The factory default User Name is: admin
The default password is: admin
Note that the password is case sensitive. It should be changed (discussed further along in this section),
It is advisable to change the
login Password. Do not
FORGET the new password
as it cannot be recovered.
but once changed, if forgotten, may not be recovered.
When entered, the password appears as ’dots’ as shown in the image below. This display format prohibits
others from viewing the password.
The ‘Remember my password’ checkbox may be selected for purposes of convenience, however it is
recommended to ensure it is deselected - particularly once the unit is deployed in the field - for one
primary reason: security.
If the BulletPlus is restored to factory defaults the password is also restored to the original default
password.
As of firmware version v1.3.0-r1014 it is required to change the password upon initial login, once
the password is changed, it will be required to login to the unit once again with the updated
password.
Image 4-0-2: Logon Window
© Microhard Systems Inc. 23
Page 24
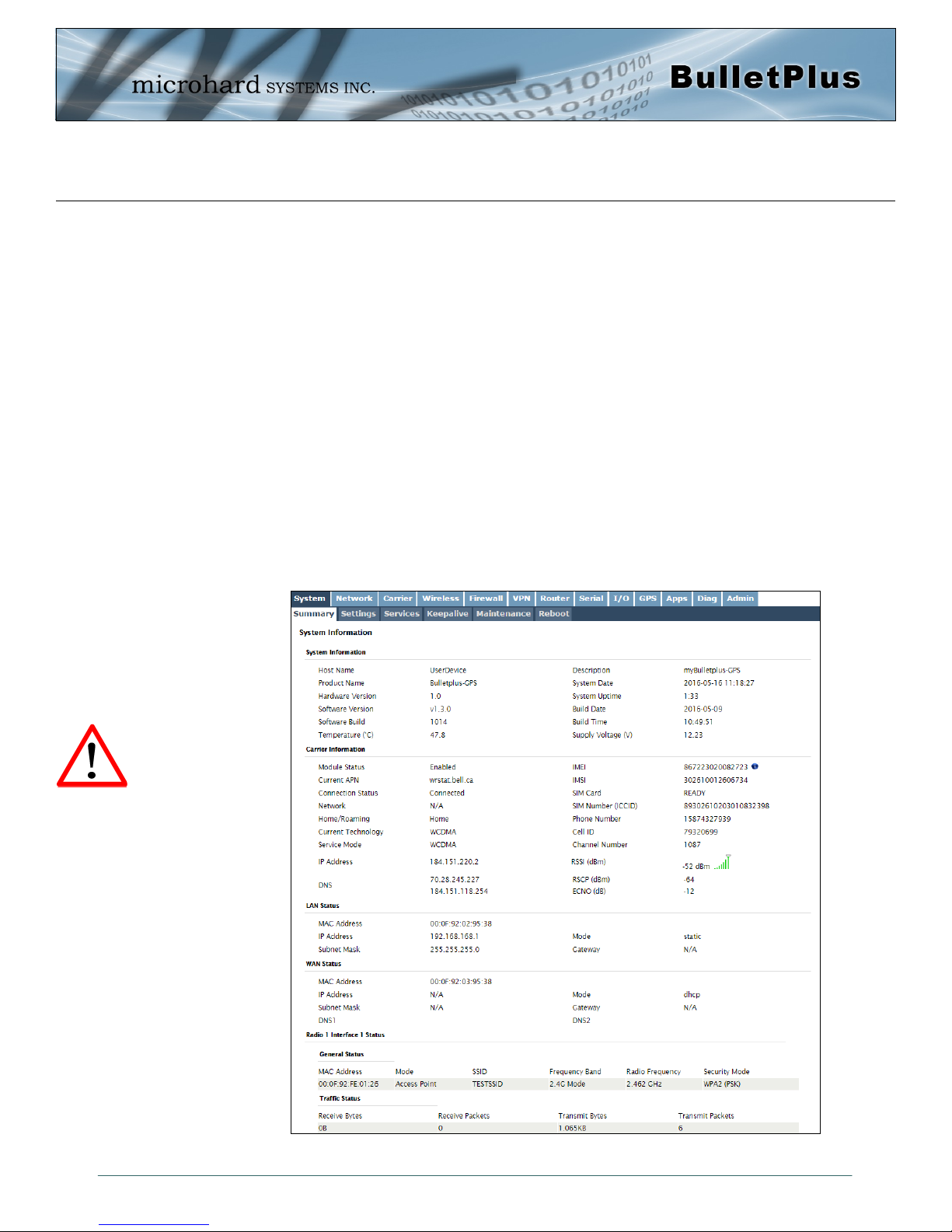
4.0 Configuration
4.1 System
The main category tabs located at the top of the navigation bar separate the configuration of the BulletPlus
into different groups based on function. The System Tab contains the following sub menu’s:
Summary - Status summary of entire radio including network settings,
version information, and radio connection status
Settings - Host Name, System Log Settings, System Time/Date
Services - Enable/Disable and configure port numbers for SSH, Telnet, HTTP
and HTTPS services
Keepalive - Configure System keep alive to ensure network/internet access.
Maintenance - Remote firmware Upgrades, reset to defaults, configuration backup
and restore.
Reboot - Schedule reboots and/or immediately reboot the system.
4.1.1 System > Summary
The System Summary screen is displayed immediately after initial login, showing a summary and status of
all the functions of the BulletPlus in a single display. This information includes System Status, Carrier
Status, Cellular & LAN/WAN network information, version info, etc.
The System Summary page
will Auto Refresh, each time
this happens a small amount
of data is used. If viewing
over the Cellular Network this
data could add up to a
significant amount over a long
period of time.
© Microhard Systems Inc. 24
Image 4-1-1: System Info Window
Page 25
4.0 Configuration
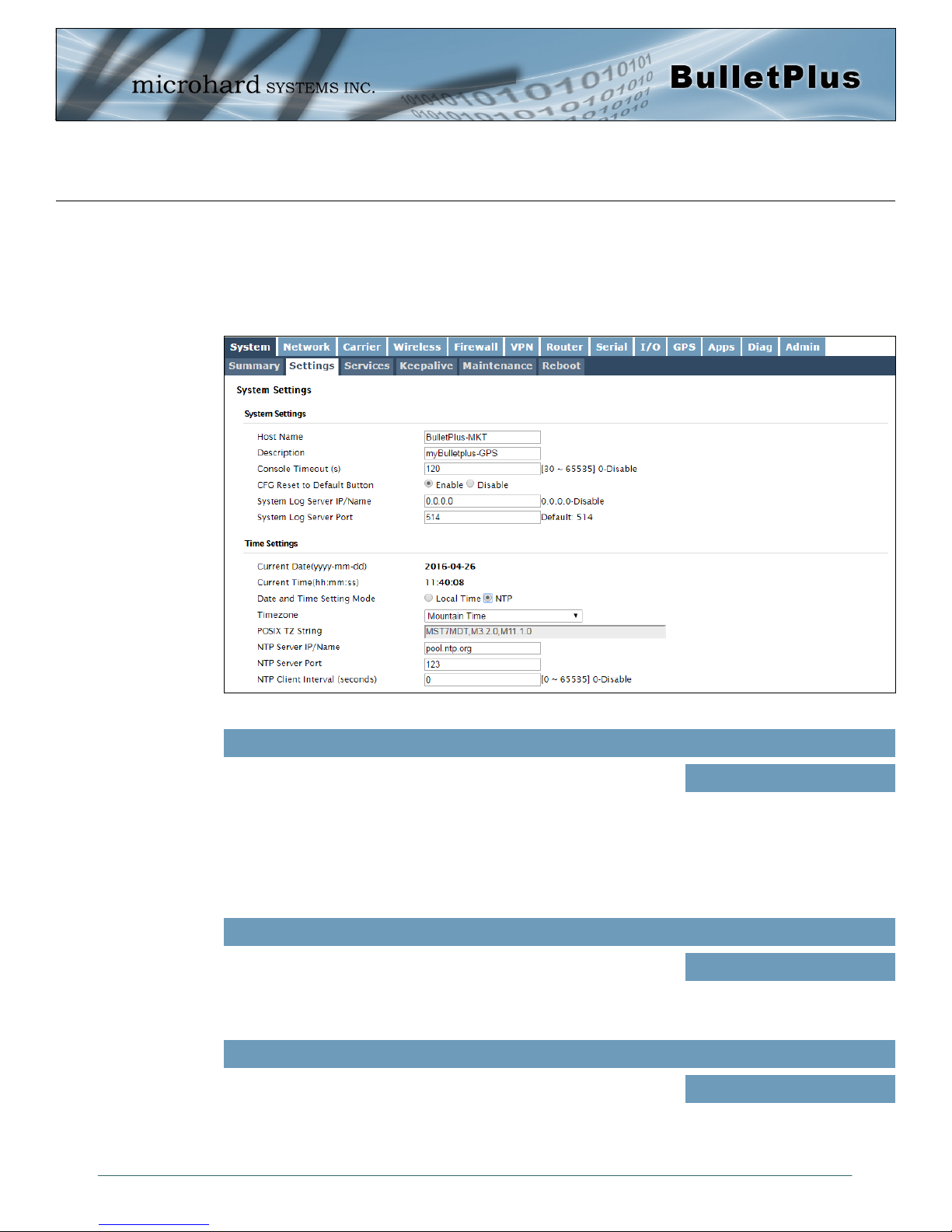
4.1.2 System > Settings
System Settings
Options available in the System Settings menu allow for the configuration of the Host Name, Description,
Console Timeout and System Log server settings.
Image 4-1-2: System Settings > System Settings
Host Name/Description
The Host Name is a convenient identifier for a specific BulletPlus unit.
This feature is most used when accessing units remotely: a convenient
cross-reference for the unit’s WAN/Carrier IP address. This name
appears when logged into a telnet session, or when the unit is
reporting into Microhard NMS System.
The description provides an additional field for text characters, but is
not displayed anywhere but in this field.
Console Timeout (s)
This value determines when a console connection (made via Console
Port or Telnet) will timeout after becoming inactive.
CFG Reset to Default Button
Enabled by default, when the CFG button on the front of the BulletPlus
is held down for 10s while the unit is powered up, the unit will reset
and all settings will be reset to factory defaults. When disabled the unit
will reset, but the settings will not be overwritten.
Values (characters)
BulletPlus (varies)
up to 30 characters
Values (seconds)
60
0-65535
Values (Selection)
Enable
Disable
© Microhard Systems Inc. 25
Page 26
4.0 Configuration
System Syslog Server IP
Network Time Protocol (NTP)
can be used to synchronize the
time and date or computer
systems with a centralized,
referenced server. This can
help ensure all systems on a
network have the same time
and date.
The BulletPlus can report system level events to a third party Syslog
server, which can be used to monitor events reported by the BulletPlus.
IP Address
0.0.0.0
System Syslog Server Port
Enter the UDP listening port of the Syslog Server. The default port number
is generally 514, but could vary from Server to Server.
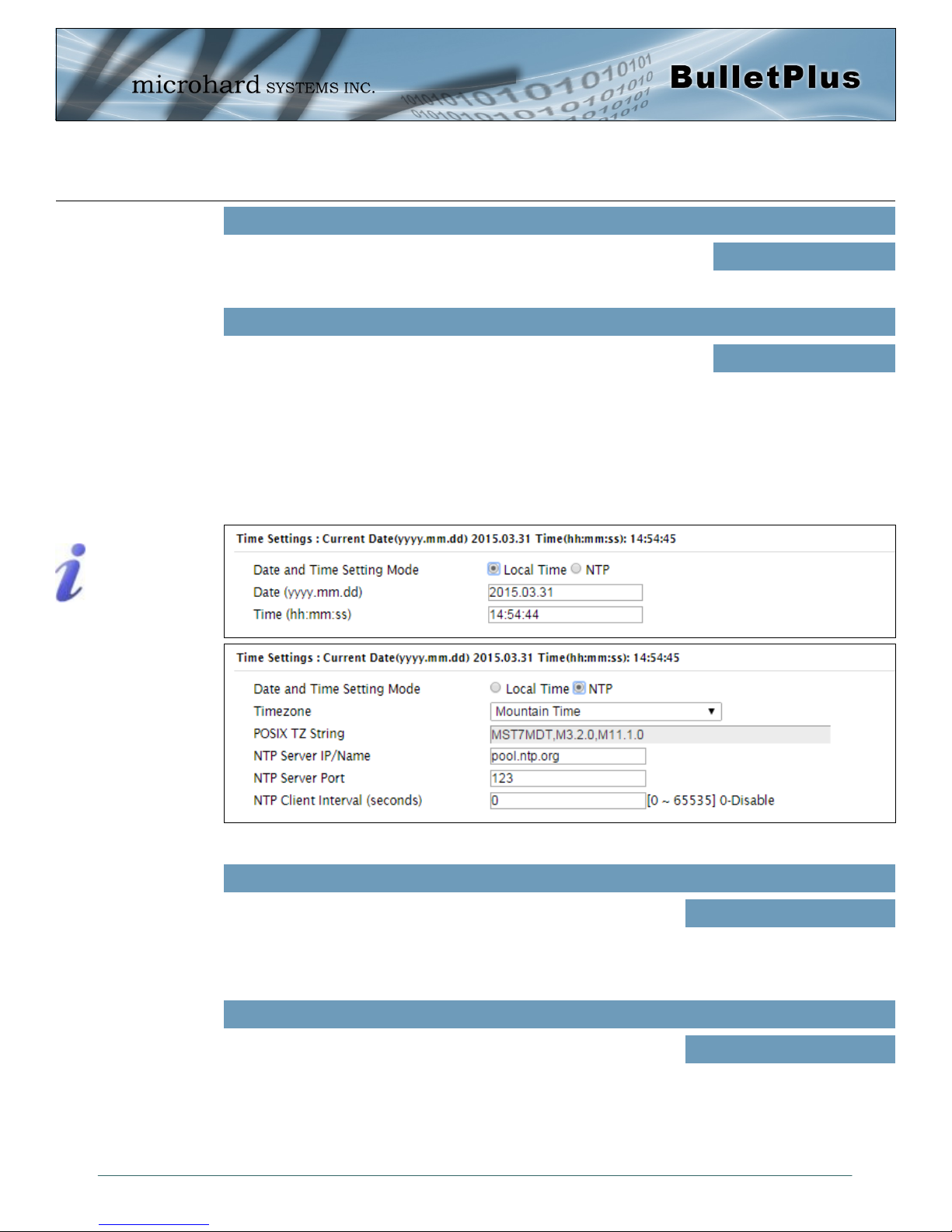
Time Settings
The BulletPlus can be set to use a local time source, thus keeping time on its own, or it can be configured
to synchronize the date and time via a NTP Server. The options and menus available will change
depending on the current setting of the Date and Time Setting Mode, as seen below.
UDP Port
514
Select the Date and Time Setting Mode required. If set for ‘Use
Local Time’ the unit will keep its own time and not attempt to
synchronize with a network server. If ‘Synchronize Date And
Time Over Network’ is selected, a NTP server can be defined.
The calendar date may be entered in this field. Note that the
entered value is lost should the BulletPlus lose power for some
reason.
© Microhard Systems Inc. 26
Image 4-1-3: System Settings > Time Settings
Date and Time Setting Mode
Values (selection)
Use Local Time Source
Synchronize Date And Time
Over Network
Date
Values (yyyy-mm-dd)
2015.04.01 (varies)
Page 27

4.0 Configuration
Time
The time may be entered in this field. Note that the entered
value is lost should the BulletPlus lose power for some reason.
If connecting to a NTP time server, specify the timezone from
the dropdown list.
This displays the POSIX TZ String used by the unit as
determined by the timezone setting.
Enter the IP Address or domain name of the desired NTP time
server.
Enter the IP Address or domain name of the desired NTP time
server.
Values (hh:mm:ss)
11:27:28 (varies)
Timezone
Values (selection)
User Defined (or out of date)
POSIX TZ String
Values (read only)
(varies)
NTP Server
Values (address)
pool.ntp.org
NTP Port
Values (port#)
123
NTP Client Interval
By default the modem only synchronizes the time and date during
system boot up (default: 0), but it can be modified to synchronize at a
regular interval. This process does consume data and should be set
accordingly.
© Microhard Systems Inc. 27
0
Values (seconds)
Page 28
4.0 Configuration
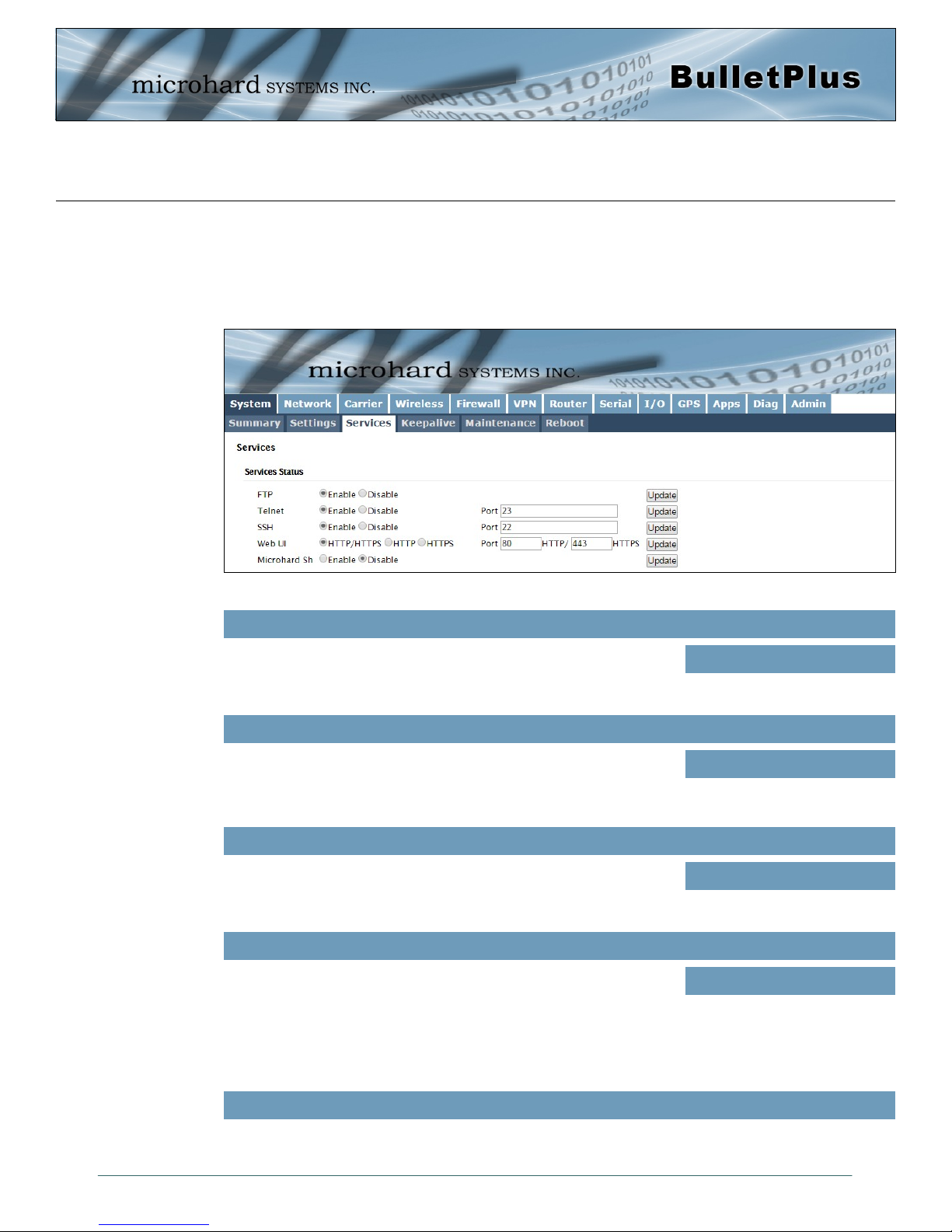
4.1.3 System > Services
Certain services in the BulletPlus can be disabled or enabled for either security considerations or resource/
power considerations. The Enable/Disable options are applied after a reboot and will take affect after each
start up. The Start/Restart/Stop functions only apply to the current session and will not be retained after a
power cycle.
Image 4-1-5: System > Services
The FTP service can be enabled/disabled using the Services Status
Menu. The FTP service is used for firmware recovery operations.
Using the Telnet Service Enable/Disable function, you can disable the
Telnet service from running on the modem. The port used by the
Telnet service can also be modified. The default is 23.
Using the SSH Service Enable/Disable function, you can disable the
SSH service (Port 22) from running on the modem. The port used by
the SSH service can also be modified. The default is 22.
The default web server port for the web based configuration tools used
in the modem is port 80 (http) and port 443 (HTTPS).
Change as required, but keep in mind that if a non standard port is
used, it must be specified in a internet browser to access the unit.
(example: http://192.168.168.1:8080).
FTP
Values (port)
Enable / Disable
Telnet
Values (port)
23
SSH
Values (port)
22
Web UI
Values (selection)
HTTP/HTTPS
HTTP
HTTPS
Reserved for internal use.
© Microhard Systems Inc. 28
Microhard Sh
Page 29
4.0 Configuration
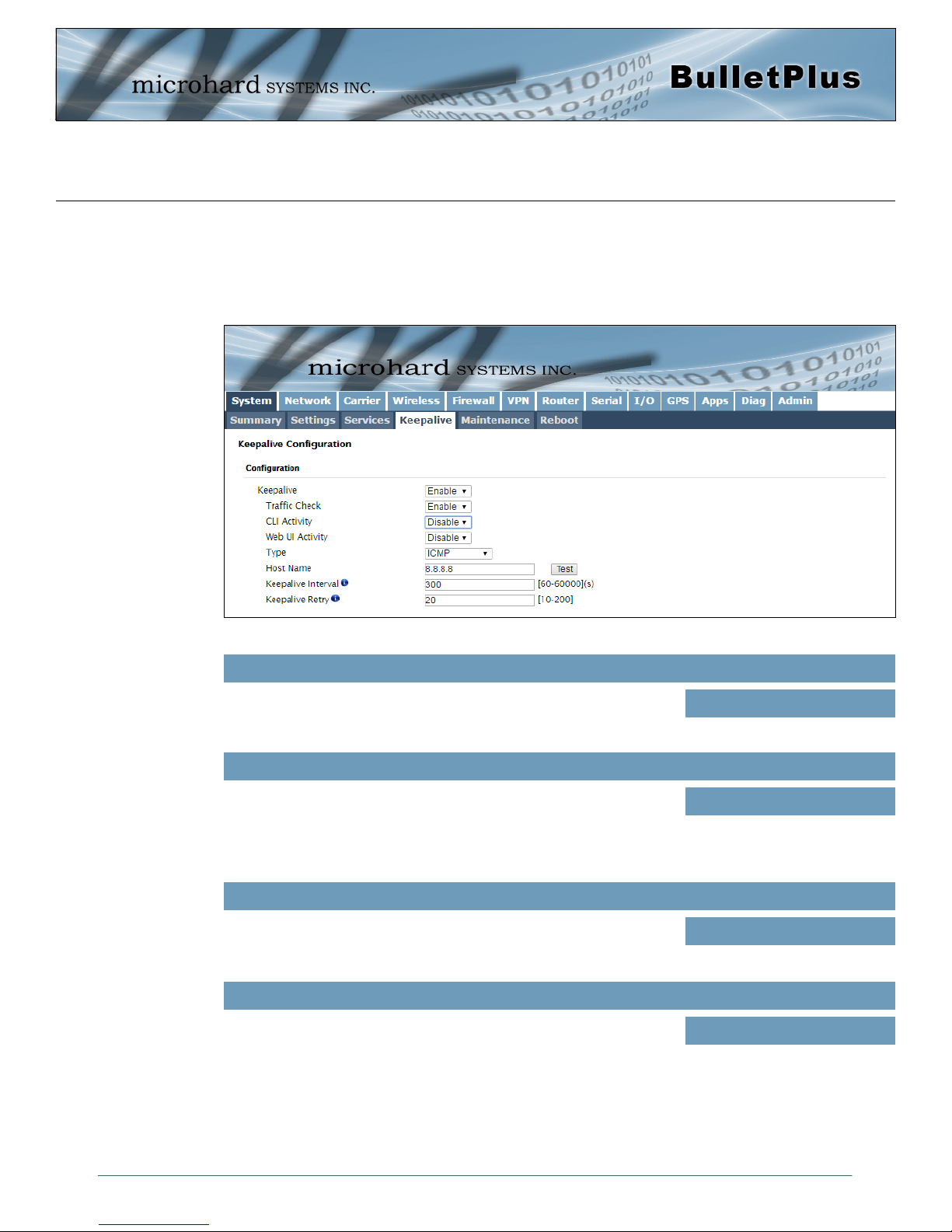
4.1.4 System > Keepalive
The Keep alive tab allows for the configuration of the keep alive features of the BulletPlus. The BulletPlus
can check for activity on the Wireless Interface, The CLI (Command Line Interface), The WEBUI, and
ensure that they are working as expected. In the event that the BulletPlus does not detect activity on a
interface it will reboot to attempt to resolve any issues that may have occurred.
Image 4-1-6: Carrier > Keepalive
Enable or Disable the keep alive functions of the modem. If it is
disabled, the user can configure the Traffic Check separately. The unit
will monitor traffic on the Cell interface.
Monitors traffic on the Cell interface as well as the WAN interface if the
WAN port is configured as independent in the Network Settings. If the
Bullet detects that there is no activity on the above interfaces it will
attempt a ICMP, HTTP or DNS Lookup as configured below to
determine if service has been lost.
Monitors the activity of CLI. If the console isn't accessed within the
certain period which is specified by Console Timeout in SystemSettings web page, the modem will send out the connection request.
Monitors the activity of Web UI. If the Web UI isn't accessed or
refreshed within the certain period which is specified by Console
Timeout in System-Settings web page, the modem will send out the
connection request.
Keep Alive
Values (Selection)
Enable / Disable
Traffic Check
Values (Selection)
Enable / Disable
CLI Activity
Values (Selection)
Enable / Disable
Web UI Activity
Values (Selection)
Enable / Disable
© Microhard Systems Inc. 29
Page 30
4.0 Configuration
Type
Once the connection is lost, the modem will send one of the requests
to the remote host to determine the connection status. If the modem
fails to get the response, it will re-send the request within the seconds
specified by Keepalive Interval below:
ICMP: Send a "ping" request
HTTP: Send a "wget" request to a HTTP server
DNS Lookup: Send a "dslookup" request to a DNS server
Specify a IP Address or Domain that is used to test the modems
connection. The modem will send out the connection requests to the
specified Host.
The Interval value determines the frequency, or how often, the unit will
send out PING messages to the Host. The BulletPlus will first attempt
to re-initialize the cellular model before performing a full system
reboot, thus the interval may be delayed by up to 120 seconds)
The Keepalive Retry is the maximum number of connection failures
such as “Host unreachable” the unit will attempt before the unit will
reboot itself to attempt to correct connection issues. The default
number is 20, and valid value is from 10 to 200.
Values (Selection)
ICMP
HTTP
DNS Lookup
Host Name
Values (IP or Domain)
8.8.8.8
Keepalive Interval
Values (seconds)
300
Keepalive Retry
Values (number)
20
© Microhard Systems Inc. 30
Page 31

4.0 Configuration
4.1.5 System > Maintenance
Firmware Upgrade
Occasional firmware updates may be released by Microhard Systems which may include fixes and/or new
features. The firmware can be updated wirelessly using the WebUI.
Check this box to erase the configuration of the BulletPlus unit during
the upgrade process. This will upgrade, and return the unit to factory
defaults, including the default IP Addresses and passwords. Not
checking the box will retain all settings during a firmware upgrade
procedure.
Use the Browse button to find the firmware file supplied by Microhard
Systems. Select “Upgrade Firmware” to start the upgrade process.
This can take several minutes.
Reset to Default
The BulletPlus may be set back to factory defaults by using the Reset to Default option under System >
Maintenance > Reset to Default. *Caution* - All settings will be lost!!!
© Microhard Systems Inc. 31
Image 4-1-7: Maintenance > Firmware Upgrade
Erase Current Configuration
Values (check box)
unchecked
Firmware Image
Values (file)
(no default)
Page 32

4.0 Configuration
Backup & Restore Configuration
The configuration of the BulletPlus can be backed up to a file at any time using the Backup Configuration
feature. The file can the be restored using the Restore Configuration feature. It is always a good idea to
backup any configurations in case of unit replacement. The configuration files cannot be edited offline, they
are used strictly to backup and restore units.
Image 4-1-8: Maintenance > Reset to Default / Backup & Restore Configuration
Name this Configuration / Backup Configuration
Use this field to name the configuration file. The .config extension will automatically be added to the
configuration file.
Restore Configuration file / Check Restore File / Restore
Use the ‘Browse’ button to find the backup file that needs to be restored to the unit. Use the ‘Check
Restore File’ button to verify that the file is valid, and then the option to restore the configuration is
displayed, as seen above.
The Keep Carrier Settings box can be selected before the restore process is started, if it is selected the
BulletPlus will retain the current carrier settings and not overwrite them with the settings contained in the
backup file.
© Microhard Systems Inc. 32
Page 33

4.0 Configuration
4.1.6 System > Reboot
The BulletPlus can be remotely rebooted using the System > Reboot menu. As seen below a button
‘Reboot now’ is provided. Once pressed, the unit immediately reboots and starts its boot up procedure. The
BulletPlus can also be restarted on a regular basis by setting up a daily/weekly/monthly schedules.
Image 4-1-9: System > Reboot
Status
Use this option to enable or disabled schooled reboots. If enabled the
BulletPlus is reboot at the interval defined below.
Schedule daily, weekly or monthly reboots. Setting up a reboot
schedule can help keep the modem connected to the cellular carrier
and prevent physically rebooting the modem if located at a remote
destination.
Values (selection)
Disable / Enable
Values (selection)
Reboot Daily
Reboot Weekly
Reboot Monthly
Days / Time
If set for weekly, days are counted from Sunday to Saturday (0 to 6),
and if set to monthly the days are counted 1 to 31. Multiple days can
be specified by separating with a comma ‘,’.
Set the time of day (24hr clock) for which to reboot the device.
© Microhard Systems Inc. 33
Values (selection)
1,
Type
Page 34

4.0 Configuration
4.2 Network
4.2.1 Network > Summary
The Network Summary display gives a overview of the currently configured network interfaces including
the Connection Type (Static/DHCP), IP Address, Net Mask, Default Gateway, DNS, and IPv4 Routing
Table.
© Microhard Systems Inc. 34
Image 4-2-1: Network > Network Status
Page 35

4.0 Configuration
4.2.2 Network > LAN
LAN Port Configuration
The BulletPlus features 2x LAN ports that can be used for connection of devices on a local network. The
WAN port can also be bridged with the LAN therefore providing up to 3 LAN ports. By default the has a
static IP Address assigned, 192.168.168.1. Also, by default the LAN is running a DHCP server to provide
IP Addresses to devices that are connected to the physical LAN port (s) (directly or via a switch).
DHCP: Dynamic Host
Configuration Protocol may
be used by networked
devices (Clients) to obtain
unique network addresses
from a DHCP server.
Advantage:
Ensures unique IP addresses
are assigned, from a central
point (DHCP server) within a
network.
Disadvantage:
The address of a particular
device is not ‘known’ and is
also subject to change.
STATIC addresses must be
tracked (to avoid duplicate
use), yet they may be
permanently assigned to a
device.
Within any IP network, each
device must have its own
unique IP address.
Image 4-2-2: Network > Network LAN Configuration
LAN Add/Edit Interface
The BulletPlus has the capability to have multiple SSID’s for the WiFi radio. New Interfaces can be added
for additional SSID’s, providing, if required, separate subnets for each SSID. By default any additional
interfaces added will automatically assign IP addresses to connecting devices via DHCP. Additional
interfaces can only be used by additional WIFI SSID’s (virtual interfaces).
Image 4-2-3: Network > LAN Port Configuration
Spanning Tree (STP)
This option allows the BulletPlus to participate in the Spanning Tree
protocol with other devices to prevent local loops. By default this is
disabled.
Values (selection)
Off
On
© Microhard Systems Inc. 35
Page 36

4.0 Configuration
Connection Type
The factory default
network settings:
IP: 192.168.168.1
Subnet: 255.255.255.0
Gateway: 192.168.168.1
A SUBNET MASK is a bit
mask that separates the
network and host (device)
portions of an IP address.
The ‘unmasked’ portion
leaves available the
information required to
identify the various devices
on the subnet.
This selection determines if the BulletPlus will obtain an IP address
from a DHCP server on the attached network, or if a static IP address
will be entered. If a Static IP Address is chosen, the fields that follow
must also be populated.
If ‘Static’ Connection Type is selected, a valid IPv4 Address for the
network being used must be entered in the field. If ‘DHCP’ is chosen
this field will not appear and it will be populated automatically from the
DHCP server.
If ‘Static’ Connection Type is selected, the Network Mask must be
entered for the Network. If ‘DHCP’ is chosen this field will not appear
and it will be populated automatically from the DHCP server.
If the Connection Type is set to DHCP, you can use Auto for the DNS
Mode and a DNS server will automatically be defined. If the connection
type is set as static, DNS servers can be manually specified.
Values (selection)
DHCP
Static
IP Address
Values (IP Address)
192.168.168.1
Netmask
Values (IP Address)
255.255.255.0
DNS Mode
Values (selection)
Auto
Manual
Within any IP network, each
device must have its own
unique IP address.
Primary DNS / Secondary DNS
Set the primary and alternate DNS (Domain Name Server) for use by
devices on the LAN port, if required.
Values (selection)
Auto
Manual
© Microhard Systems Inc. 36
Page 37

4.0 Configuration
LAN DHCP
A BulletPlus may be configured to provide dynamic host control protocol (DHCP) service to all attached
(either wired or wireless (WiFi)-connected) devices. By default the DHCP service is enabled, so devices
that are connected to the physical Ethernet LAN ports, as well as any devices that are connected by WiFi
will be assigned an IP by the BulletPlus. The LAN DHCP service is available for each interface, and is
located in the add/edit interface menus.
Image 4-2-4: Network > DHCP Server
DHCP Server
Prior to enabling this service,
verify that there are no other
devices - either wired (e.g.
LAN) or wireless with an
active DHCP SERVER
service. (The Server issues
IP address information at the
request of a DHCP Client,
which receives the
information.)
The option is used to enable or disable the DHCP service for devices
connected to the LAN Port(s).
Select the starting address DHCP assignable IP Addresses. The first
octets of the subnet will be pre-set based on the LAN IP configuration,
and can not be changed.
Set the maximum number of IP addresses that can be assigned by the
BulletPlus.
The DHCP lease time is the amount of time before a new request for a
network address must be made to the DHCP Server.
Specify an alternate gateway for DHCP assigned devices if the default
gateway is not to be used.
Values (selection)
Enable / Disable
Start
Values (IP Address)
192.168.168.100
Limit
Values (integer)
150
Lease Time
Values (minutes)
720
Alternate Gateway
Values (IP Address)
(IP Address)
© Microhard Systems Inc. 37
Page 38

4.0 Configuration
Preferred DNS Server
DNS: Domain Name Service
is an Internet service that
translates easilyremembered domain names
into their not-so-easilyremembered IP addresses.
Being that the Internet is
based on IP addresses,
without DNS, if one entered
the domain name
www.microhardcorp.com (for
example) into the URL line of
a web browser, the website
‘could not be found’).
Specify a preferred DNS server address to be assigned to DHCP
devices.
Specify the alternate DNS server address to be assigned to DHCP
devices.
Enter the address of the WINS/NBNS (NetBIOS) Server. The WINS
server will translate computers names into their IP addresses, similar
to how a DNS server translates domain names to IP addresses.
Select the method used to resolve computer names to IP addresses.
Four name resolution methods are available:
B-node: broadcast
P-node: point-to-point
M-node: mixed/modified
H-node: hybrid
Values (IP Address)
(IP Address)
Alternate DNS Server
Values (IP Address)
(IP Address)
WINS/NBNS Servers
Values (IP/Domain)
(no default)
WINS/NBT Node Type
Values (selection)
none
b-node
p-node
m-node
h-node
© Microhard Systems Inc. 38
Page 39

4.0 Configuration
VLAN Configuration
The BulletPlus has the capability to add multiple network interfaces, as such it may be desirable to
segment these different subnets. The BulletPlus features 802.1Q VLAN. 802.1Q VLAN uses tagging to
allow separation of network segments. Ports can belong to multiple VLANs. A Trunk port can be configured
to communicate with other VLAN switch by adding all configured VLANs to a single port. The native
VLAN1 is used by default, it is important that any connected VLAN switch use the same Native VLAN.
Image 4-2-5: Network > VLAN
VLAN names can be added to aid in VLAN identification (purpose, I,e
Engineering, Accounting, etc).
When adding a VLAN you must select a VLAN ID. Select between 2
and 127 for valid VLAN IDs.
Assign port to the current VLAN.
Excluded: Not part of the current VLAN
Tagged: In 802.1Q this assigns the current VLAN to the port,
Untagged: In port based VLAN this assigns a port to the current
VLAN.
VLAN Name
Values
(no default)
VLAN ID
Values
2 (2-127)
Port 1 - 2
Values (selection)
Excluded
Tagged
Untagged
Network
Allows the user the ability to assign specific configured network
interfaces to a specific VLAN. (802.1Q)
© Microhard Systems Inc. 39
Values (selection)
None
LAN
(additional network interfaces)
Page 40

4.0 Configuration
4.2.3 Network > WAN
WAN Configuration
The WAN configuration refers to the wired WAN connection on the BulletPlus. The WAN port can be used
to connect the BulletPlus to other networks, the internet and/or other network resources.
DHCP: Dynamic Host
Configuration Protocol may
be used by networked
devices (Clients) to obtain
unique network addresses
from a DHCP server.
Advantage:
Ensures unique IP addresses
are assigned, from a central
point (DHCP server) within a
network.
Disadvantage:
The address of a particular
device is not ‘known’ and is
also subject to change.
STATIC addresses must be
tracked (to avoid duplicate
use), yet they may be
permanently assigned to a
device.
Image 4-2-6: Network > WAN Configuration
Use this to set the function of the physical WAN RJ45 port. If set to
independent WAN , the physical WAN port will operate as a standard
WAN port. Alternatively it can be configured to be bridged to the LAN,
and operate as a second LAN port, or even as an independent LAN.
This selection determines if the BulletPlus will obtain an WAN IP
address from a DHCP server, or if a static IP address will be entered.
If a Static IP Address is chosen, the fields that follow must also be
populated.
If ‘Static’ Connection Type is selected, a valid IPv4 Address for the
network being used must be entered in the field. If ‘DHCP’ is chosen
this field will not appear and it will be populated automatically from the
DHCP server.
If ‘Static’ Connection Type is selected, the Network Mask must be
entered for the Network. If ‘DHCP’ is chosen this field will not appear
and it will be populated automatically from the DHCP server.
Working Mode
Values (selection)
Independent WAN
Bridged with LAN Port
Independent LAN
Connection Type
Values (selection)
DHCP
Static
IP Address
Values (IP Address)
(no default)
Netmask
Values (IP Address)
(no default)
© Microhard Systems Inc. 40
Page 41

4.0 Configuration
Default Gateway
If the BulletPlus is integrated into a network which has a defined
gateway, then, as with other hosts on the network, this gateway’s IP
address will be entered into this field. If there is a DHCP server on the
network, and the Connection Type (see previous page) is selected to
be DHCP, the DHCP server will populate this field with the appropriate
gateway address.
The Default Route parameter allows you to set this interface as the
default route in the routing table. This is result in all data being sent to
the WAN interface if there the destination network is not directly
connected (LAN, WIFI etc), and no other route has been specified
(4G). In cases where the WAN is the primary connection this would be
set to Yes.
Select between Manual or Auto for DNS server(s) for the WAN
interface. If set to Auto the BulletPlus will try to automatically detect the
DNS servers to use, which is normally the case when the WAN is
DHCP. Manual required the DNS addresses to be known and entered
below.
DNS (Domain Name Service) Servers are used to resolve domain
names into IP addresses. If set to auto and the Connection Type is set
for DHCP the DHCP server will populate this field and the value set
can be viewed on the Network > Status page. To add additional static
servers, enter them here.
Values (IP Address)
(no default)
Default Route
Values (selection)
No / Yes
DNS Mode
Values (selection)
Manual / Auto
Primary DNS
Values (IP Address)
(no default)
DNS (Domain Name Service) Servers are used to resolve domain
names into IP addresses. If set to auto and the Connection Type is set
for DHCP the DHCP server will populate this field and the value set
can be viewed on the Network > Status page. To add additional static
servers, enter them here.
© Microhard Systems Inc. 41
Secondary DNS
Values (IP Address)
(no default)
Page 42

4.0 Configuration
4.2.4 DHCP (MAC Binding)
In some applications it is important that specific devices always have a predetermined IP address. This
menu allows for MAC Address binding to a IP Address, so that whenever the device that has the specified
MAC address, will always get the selected IP address from the DHCP service. In this situation, all attached
(wired or wireless) devices can all be configured for DHCP, but still get a known IP address.
Image 4-2-7: Network > MAC Address Binding
Name
The name field is used to give the device a easily recognizable name.
Values (characters)
(no default)
MAC Address
Enter in the MAC address of the device to be bound to a set IP
address. Set the IP Address in the next field. Must use the format:
AB:CD:DF:12:34:D3. It is not case sensitive, but the colons must be
present.
Values (MAC Address)
(no default)
IP Address
Enter the IP Address to be assign to the device specified by the MAC
address above.
Static Addresses
This section displays the IP address and MAC address currently assigned through the DCHP service, that
are bound by it’s MAC address. Also shown is the Name, and the ability to remove the binding by clicking
“Remove _______”.
Values (IP Address)
(minutes)
Active DHCP Leases
This section displays the IP Addresses currently assigned through the DCHP service. Also shown is the
MAC Address, Name and Expiry time of the lease for reference. The ‘Release All’ button terminates all
active leased and requires all connected devices to request new network information (IP/Subnet/etc)
© Microhard Systems Inc. 42
Page 43

4.0 Configuration
4.2.5 Network > DDNS
Unless a carrier issues a Static IP address, it may be desirable to use a Dynamic DNS (DDNS) service to
track dynamic IP changes and automatically update DNS services. This allows the use of a constant
resolvable host name for the BulletPlus.
Image 4-2-8: Carrier > Traffic Watchdog
DDNS Status
This selection allows the use of a Dynamic Domain Name Server
(DDNS), for the BulletPlus.
If the BulletPlus is using a wired WAN (ISP) as well as a Cellular
carrier, specific which will use the DNS service.
This is a list of supported Dynamic DNS service providers. Free and
premium services are offered, contact the specific providers for more
information.
Enter a valid user name and password for the DDNS service selected
above.
Values (Selection)
Enable / Disable
Network
Values (Selection)
Auto / Carrier / WAN
Service
Values (selection)
changeip
dyndns
eurodyndns
hn
noip
ods
ovh
regfish
tzo
zoneedit
User Name / Password
Values (characters)
(none)
Host
This is the host or domain name for the BulletPlus as assigned by the
DDNS provider. Use the provided button to query the server (if
configured correctly)
© Microhard Systems Inc. 43
Values (domain name)
(none)
Page 44

4.0 Configuration
4.2.6 Network > Routes
Static Routes Configuration
It may be desirable to have devices on different subnets to be able to talk to one another. This can be
accomplished by specifying a static route, telling the BulletPlus where to send data.
Image 4-2-9: Network > Routes
Routes can be names for easy reference, or to describe the route
being added.
Enter the network IP address for the destination.
Specify the Gateway used to reach the network specified above.
Enter the Netmask for the destination network.
Name
Values (characters)
(no default)
Destination
Values (IP Address)
(192.168.168.0)
Gateway
Values (IP Address)
192.168.168.1
Netmask
Values (IP Address)
255.255.255.0
© Microhard Systems Inc. 44
Page 45

4.0 Configuration
Metric
In some cases there may be multiple routes to reach a destination.
The Metric can be set to give certain routes priority, the lower the
metric is, the better the route. The more hops it takes to get to a
destination, the higher the metric.
Define the exit interface. Is the destination a device on the LAN, LAN1
(If physical WAN port is bridged as an independent LAN), 3G/4G
(cellular), USB or the WAN?
Values (Integer)
255.255.255.0
Interface
Values (Selection)
LAN / LAN1 / WAN / Cell / USB
None
© Microhard Systems Inc. 45
Page 46

4.0 Configuration
4.2.7 Network > VRRP
The BulletPlus when paired with other VRRP enabled devices (another BulletPlus or compatible devices)
can provide redundant internet access for LAN devices by using VRRP (Virtual Router Redundancy
Protocol) as illustrated below. If a connected device needs to access the internet it will use whichever
virtual router has the highest priority, if that device is not available the next router with the higher priority
will router the traffic.
Internet
BulletPlus
LAN: 192.168.220.11
VRRP Router
LAN: 192.168.220.12
Virtual Router IP:
192.168.220.211
PC/LAN Device
LAN: 192.168.220.50
Gateway: 192.168.220.211
Switch
Enable or disable the VRRP service on the BulletPlus. To change
settings the VRRP service must be disabled (then submitted) and then
re-enabled.
© Microhard Systems Inc. 46
Image 4-2-10: Network > VRRP
VRRP Status
Values (Selection)
Enable / Disable
Page 47

4.0 Configuration
Virtual Router IP
This is the IP Address of the virtual router, this must be the same on all
devices participating in VRRP. This is the IP that any attached LAN
PC/device would use as its default gateway.
Values
192.168.220.211
Virtual Router ID
This is the Router ID. Each router/ participating in VRRP should have
a router ID to distinguish between them.
Values
2
Router Priority
This is the Router priority. This number to assigned to each router to
determine which router(s) will be used first or as the primary. The
higher the ID, the higher the priority.
4.2.8 Network > Ports
The Network > Ports menu can be used to determine the characteristics of the physical Ethernet interfaces
on the BulletPlus. As seen below the Mode (Auto/Manual), Auto-Negotiation, Speed (10/100Mbit/s) and the
Duplex (Full/Half) can all be configured on the BulletPlus.
Values
150
© Microhard Systems Inc. 47
Image 4-2-11: Network > Ports
Page 48

4.0 Configuration
4.2.9 Network > Bandwidth
The BulletPlus features Bandwidth Throttling, which allows the upload/download of connected networks/
users data speeds to be limited to a specified value. Network Bandwidth Throttling can be implemented by
each physical Ethernet interface as seen in the image below.
Image 4-2-12: Network > Bandwidth Throttling
The rule name is used as a reference to be able to help identify which
interface or network is attached to the affected network interface.
Select the physical interface to be affected by the Bandwidth Throttling
as defined below.
Enable or disable uploading on the specified interface. This prevent
data from being uploaded to a server. (i.e uploading/sending videos or
other files to a server).
Set the data limit (speed) for file uploads if uploads have been allowed
using the Upload Bandwidth Enable.
Rule Name
Values (chars)
rule1
Network
Values (selection)
(varies)
Upload Bandwidth Enable
Values (selection)
Enable / Disable
Upload Bandwidth
Values (kbps)
10000
© Microhard Systems Inc. 48
Page 49

4.0 Configuration
Download Bandwidth Enable
Enable or disable downloading on the specified interface. This prevent
data from being downloaded from a server. (i.e downloading files,
internet browsing etc).
Values (chars)
Enable / Disable
Download Bandwidth
Set the data limit (speed) for file downloads if downloads have been
allowed using the Download Bandwidth Enable.
4.2.10 Network > Device List
The Network > Device List shows the current ARP table for the network adapters. The MAC address and
IP address are shown, however not only DHCP assigned devices are listed in the device list, any devices,
even those statically assigned, that are connected through the local network interface (RJ45) are
displayed, including those connected through a hub or switch.
Values (kbps)
30000
© Microhard Systems Inc. 49
Image 4-2-13: Network > Device List
Page 50

4.0 Configuration
4.2.11 Network > Cloud Filter
The BulletPlus provides Cloud based content filtering and security using the third-party service by Open
DNS. OpenDNS is a service which offers free or premium DNS services with added security, phishing
protection and optional, advanced content filtering. To get started with OpenDNS an account must first be
created with OpenDNS by visiting their website.
Image 4-2-14: Network > Cloud Filtering
OpenDNS Cloud Filter
Enable or Disable the OpenDNS cloud based filtering & security.
Disable Bypassing OpenDNS
If enabled all clients connected through the BulletPlus will be forced to
use OpenDNS and is subject to any and all content filtering and
security, to prevent circumvention.
When Cloud Filter is enabled, this status will be refreshed every 30
seconds, showing the OpenDNS status. For OpenDNS to be active,
the status must be green and show "Connected to OpenDNS".
Enter the user name and password for the OpenDNS account that was
specified during registration and setup of the service.
Values (selection)
Enable / Disable
Values (selection)
Enable / Disable
Status
Values (selection)
Enable / Disable
User Name / Password
Values (selection)
Enable / Disable
© Microhard Systems Inc. 50
Page 51

4.0 Configuration
4.2.12 Network > Webfilter
The BulletPlus can provide comprehensive content filtering, limiting access to specific websites and other
content. By MAC Address, the BulletPlus allows content to be filtering regardless of the assigned IP
address. Filtering can also be applied on a entire network, limiting access to any connected device.
Enable or Disable the Webfilter of the BulletPlus.
Check Filter HTTPS will redirect all port 443 traffic into the webfilter.
(Please make sure system DNS works.)
© Microhard Systems Inc. 51
Image 4-2-15: Network > Web Filtering
Webfilter Status
Values (selection)
Enable / Disable
Filter HTTPS
Values (selection)
Enable / Disable
Page 52

4.0 Configuration
MAC Address Webfilter Default Setting
Default setting can be used for MAC addresses where all addresses
may be allowed (Allow) with a few exceptions, or where all addresses
are block (Deny), with a few exceptions.
After a Default rule has been applied, exceptions can be added by
adding MAC Webfilter Rules.
Values
00:00:00:00:00:00 Allow
MAC Webfilter Rules
Add MAC Webfilter rules to apply filtering. If a default rule has been
added these rules can be used to specify exceptions. MAC Webfilter
Rules can also be applied to limit access to just one or a few websites
by simply adding the to the MAC Webfilter list without using a default
rule.
Name: Add a name for the MAC Webfilter Rule.
MAC Address: Enter the MAC Address to apply rule to.
Domain/URL/IP: Enter the Domain Name or URL of the website control access for, i.e.
www.company.com. To ensure the full domain is blocked, enter the most inclusive domain, i.e.
.company.com will block www.company.com and images.company.com and videos.company.com.
Alternatively you can use an IP address or address range written in CIDR notation, i.e. 8.8.8.0/24.
Action: Specify if the rule Allows access or Denies access to the specified address.
Rule Priority: The Rule Priority is used to determine the order rules are evaluated. Higher priority rules
(bigger number) are evaluated first and the first one to match has its assigned action taken."
Enabled: Enable or Disable the MAC Webfilter rule.
Values
Mac1
00:00:00:00:00:00
Company.com
Deny
50
Enabled
MAC Address Webfilter Default Setting
When a network is set to Allow (Blacklist) it will allow access to all sites
not blocked in the Filter Rules. Selecting Deny (Whitelist) will only
allow access to websites with an Allow action in the Filter rules, all
other sites will be blocked.
Values (selection)
Allow / Deny
MAC Webfilter Rules
Add Network Webfilter Rules to allow or deny access to specified
content. The Network rules work with the Network Webfilter Default
Settings.
Name: Add a name for the MAC Webfilter Rule.
Network: Select the local network for which the rule applies.
Domain/URL/IP: See description in MAC Filtering Rules above.
Action: See description in MAC Filtering Rules above.
Rule Priority: See description in MAC Filtering Rules above.
Enabled: Enable or Disable the Network Webfilter rule.
© Microhard Systems Inc. 52
Values
net1
LAN
Company.com
Deny
50
Enabled
Page 53

4.0 Configuration
4.2.13 Network > MultiWAN
MultiWAN is used to manage the primary data connection used by the BulletPlus. In cases where a wired
WAN (ISP) is available it is generally used for the primary connection as data is usually cheaper (unlimited)
than a cellular connection. The BulletPlus can provide automatic failover services, switching the connection
(or default route) used for outside data.
Enable or disable the MultiWAN service on the BulletPlus. To use
MultiWAN, the WAN (wired) must be configured as independent in the
Network > WAN settings and/or the Wireless must be set to Client &
bound to the WIFI interface.
© Microhard Systems Inc. 53
Image 4-2-16: Network > MultiWAN
MultiWAN Enable
Values (selection)
Enable / Disable
Page 54

4.0 Configuration
Primary WAN
Define which connection is the primary network/internet connection for
the BulletPlus. Normally this is the wired WAN connection to an ISP.
Select which WAN connection is the secondary connection. When a
failure of the main WAN occurs this will be the first alternative.
Generally this will be the cellular connection.
The WiFi on the BulletPlus can be configured as a client and used as a
data connection to access the internet.
This is the frequency at which the BulletPlus will send ICMP packets to
the defined host to determine if the interface has failed.
It is possible for the BulletPlus to send out a notification when the
MultiWAN has switched its available connection and is routing data
through an alternate interface.
Values (selection)
WAN / Carrier / WIFI Client
Second WAN
Values (selection)
WAN / 4G / WIFI
Third WAN
Values (selection)
WAN / 4G / WIFI / Disable
Health Monitor Interval
Values (seconds)
20
Switch Notification
Values (selection)
Disable / Email / SMS / Both
Failover Settings (Same settings for WAN, WIFI Client and Carrier)
Select the type of failover detection to be used. By default ICMP is
used to ping a specified address(s), a DNS Lookup can also be
selected.
Values (selection)
ICMP / DNS Lookup
Host Name
Up to three(3) reachable addresses can be specified to test for link
health at the frequency specified above for the Health Monitor Interval.
A test button is provided to ensure that reachable address have been
entered and that there are no errors.
Advanced+ (Only shown if selected)
© Microhard Systems Inc. 54
Values (Address)
8.8.8.8
4.2.2.1
208.67.222.222
Type
Page 55

4.0 Configuration
Ping Mode
The Ping mode allows for the selected hosts to be pinged either
Sequentially or Simultaneously. This option is only displayed when the
failover mode is set to ICMP.
This is the amount of time the Health Monitor will wait for a response
from the ICMP Host (when type is configured as ICMP).
This is the number of attempts the BulletPlus will attempt to reach the
IMCP host before going into failover and switching WAN interfaces.
The BulletPlus will continue to monitor the failed interface, even after
failover has occurred. This defines the number of successful attempts
required before recovering the failed interface.
Recovery Immediate Mode / Wait
Once the preferred connection is again deemed available, it can be
specified to wait a configurable amount of time before restoring the
connection.
Values (seconds)
3
ICMP Timeout
Values (seconds)
3
Attempts Before Failover
Values (selection)
1, 3, 5, 10, 15, 20
Attempts Before Recovery
Values (selection)
1, 2, 5, 10, 15, 20
Values (selection)
Disable / Enable
© Microhard Systems Inc. 55
Page 56

4.0 Configuration
4.3 Carrier
4.3.1 Carrier > Status
The Carrier Status window provides complete overview information related to the Cellular Carrier portion of
the BulletPlus. A variety of information can be found here, such as Activity Status, Network (Name of
Wireless Carrier connected), Data Service Type (WCDMA/HSPA/HSPA+/LTE etc), Frequency band,
Phone Number etc.
Not all statistics parameters displayed are applicable.
The Received and Transmitted bytes and packets indicate the respective amount of data which has been
moved through the radio.
The Error counts reflect those having occurred on the wireless link.
© Microhard Systems Inc. 56
Image 4-3-1: Carrier > Status
Page 57

4.0 Configuration
4.3.2 Carrier > Settings
The parameters within the Carrier Configuration menu must be input properly; they are the most basic
requirement required by your cellular provider for network connectivity. The BulletPlus can support dual
SIM cards, as described below either slot can be specified as the primary slot and if a connectivity issue
occurs, the unit can be configured to automatically switch to the alternate SIM card.
Carrier Status is used to Enable or Disable the connection to the
Cellular Carrier. By default this option is enabled.
Allows a user to specify the MTU size for custom applications. In most
cases this will be left blank and the system will determine the best
value.
© Microhard Systems Inc. 57
Image 4-3-2: Carrier > Settings
Carrier Status
Values (Selection)
Enable / Disable
MTU Size
Values
(blank)
Page 58

4.0 Configuration
IP-Passthrough
IP pass-through allows the WAN IP address to be assigned to the
device connected to the LAN or WAN ports. In this mode the Bullet is
for the most part transparent and forwards all traffic to the device
connected to the selected Ethernet port except that listed below:
The WebUI port (Default Port:TCP 80), this port is retained for remote
management of the Bullet. This port can be changed to a different port under
the System > Services Menu.
The SNMP Listening Port (Default Port: UDP 161).
Port Forwarding Rules. The BulletPlus forward to other internal modem
services (Iperf etc) by using X.X.X.1 for an internal IP Address.
The virtual IP address is configurable to allow access to the unit on the
LAN/WAN connector once IP-Passthrough has been enabled.
The firewall/rules must be configured to allow traffic, all incoming
carrier traffic is blocked by default.
The BulletPlus supports one or two SIM cards to be installed. By
default the primary SIM is the top SIM, and the unit will try to connect
using SIM1 first, and then if it fails to connect, or loses connection to a
valid carrier, it will then attempt SIM2.
Dual Cards Management
Values (Selection)
Disable
Ethernet (LAN)
WAN
SIM Selection
Values (Selection)
Dual SIM Cards
SIM Card-1 Only
SIM Card-2 Only
By default the Primary SIM is the SIM installed into the SIM1 slot on
the unit. The SIM card installed into the Primary slot will be the Cellular
Carrier in which the BulletPlus will attempt to make a connection with.
This can be modified here.
SIM Card-1 Settings
This feature allows the disabling or enable of data roaming. When data
roaming is enabled the modem will be allowed to use data when in
roaming status. It is not recommended to allow roaming unless the
appropriate data plans are in place.
Primary Slot
Values (Selection)
SIM Card-1
SIM Card-2
Data Roaming
Values (Selection)
Enable / Disable
© Microhard Systems Inc. 58
Page 59

4.0 Configuration
Carrier Operator
In some cases, a user may want to lock onto a certain carrier. There
are four options to choose from: Auto, SIM based, Manual and Fixed.
Auto will allow the unit to pick the carrier automatically. Data roaming is
permitted.
SIM based will only allow the unit to connect to the network indicated by the
SIM card used in the unit.
Manual will scan for available carriers and allow a user to select from the
available carriers. It takes 2 to 3 minutes to complete a scan.
Fixed allows a user to enter the carrier code (numerical) directly and then the
unit will only connect to that carrier.
Select the valid types of Carrier connections allowed. For example if
set to auto the BulletPlus will connect to any data type. If set to
WCDMA only, the BulletPlus will only allow connection to WCDMA
related technologies, and not allow the device to connect to lesser
(slower) technologies.
APN (Access Point Name)
The APN is required by every Carrier in order to connect to their
networks. The APN defines the type of network the Bullet is connected
to and the service type. Most Carriers have more than one APN,
usually many, dependant on the types of service offered.
Values (Selection)
Auto
Based on SIM
Manual
Fixed
Technologies Mode
Values (Selection)
AUTO
WCDMA, LTE, GSM
GSM Only
WCDMA Only
LTE Only
WCDMA, GSM
LTE,WCDMA
WCDMA, LTE
LTE, GSM
Values (characters)
auto
Auto APN (default) may allow the unit to quickly connect to a carrier, by cycling through a predetermined
list of common APN’s. Auto APN will not work for private APN’s or for all carriers.
Advanced+
The SIM Pin is required for some international carriers. If supplied and
required by the cellular carrier, enter the SIM Pin here.
Sets the authentication type required to negotiate with peer.
PAP - Password Authentication Protocol.
CHAP - Challenge Handshake Authentication Protocol.
Only required if the carrier requires a User Name and Password.
© Microhard Systems Inc. 59
SIM Pin
Values (characters)
(none)
Authentication
Values (Selection)
Device decide (AUTO)
PAP
CHAP
No Auth
Page 60

4.0 Configuration
User Name
A User Name may be required for authentication to a remote peer.
Although usually not required for dynamically assigned IP addresses
from the wireless carrier. Varies by carrier.
Enter the password for the user name above. May not be required by
some carriers, or APN’s
Network+
In some cases the Static IP address must be entered in this field if
assigned by a wireless carrier. In most cases the IP will be read from
the SIM card and this field should be left at the default value.
If enabled the Bullet with use the DNS server as specified
automatically by the service provider.
Values (characters)
Carrier/peer dependant
Password
Values (characters)
Carrier/peer dependant
IP Address
Values (IP Address)
(none)
Use Remote DNS
Values (selection)
Enable / Disable
Default Route
Use this interface as the default route for all outbound traffic unless
specified in the Network > Routes table.
Values (Selection)
Yes / No
DNS-Passthrough
When enabled DNS-Passthrough will pass on the WAN assigned DNS
information to the end device.
SIM Card-2 Settings
Settings for SIM Card-2 are identical to that of SIM Card-1, refer to the previous section for information on
how to configure SIM Card-2.
Values (Selection)
Enable / Disable
© Microhard Systems Inc. 60
Page 61

4.0 Configuration
4.3.3 Carrier > SMS
SMS Command History
The SMS menu allows a user to view the SMS Command History and view the SMS messages on the SIM
Card.
Image 4-3-3: SMS > SMS Command History
4.3.4 Carrier > SMS Config
SMS messages can be used to remotely reboot or trigger events in the BulletPlus. SMS alerts can be set
up to get SMS messages based on system events such as Roaming status, RSSI,
Ethernet Link Status or IO Status.
System SMS Command
© Microhard Systems Inc. 61
Image 4-3-4: SMS > SMS Configuration
Page 62

4.0 Configuration
Status
This option allows a user to enable or disable to use of the following
SMS commands to reboot or trigger events in the BulletPlus:
MSC#REBOOT Reboot system
MSC#NMS Send NMS UDP Report
MSC#WEB Send web client inquiry
MSC#MIOP1 open I/O ouput1
MSC#MIOP2 open I/O ouput2
MSC#MIOC1 close I/O ouput1
MSC#MIOC2 close I/O ouput2
If enabled, the BulletPlus will only accept and execute commands
originating from the phone numbers in the Phone Filter List. Up to 6
numbers can be added.
MSC#EURD0 trigger event report0
MSC#EURD1 trigger event report1
MSC#EURD2 trigger event report2
MSC#EURD3 trigger event report3
MSC#GPSR0 trigger gps report0
MSC#GPSR1 trigger gps report1
MSC#GPSR2 trigger gps report2
MSC#GPSR3 trigger gps report3
Values (Selection)
Enable / Disable
Set Phone Filter
Values (Selection)
Enable / Disable
© Microhard Systems Inc. 62
Page 63

4.0 Configuration
System SMS Alerts
Image 4-3-6: SMS > SMS Alerts
Enable SMS Alerts. IF enabled SMS alerts will be send when
conditions are met as configured to the phone numbers listed.
SMS Alerts can be sent to up to 6 different phone numbers that are
listed here.
SMS alerts, when active, will be sent out at the frequency defined
here.
The device Alias is text that is sent with the SMS message to provide
additional information or help identify the source of the SMS alert.
Status
Values (Selection)
Enable / Disable
Received Phone Numbers
Values (Selection)
(no default)
Time Interval(s)
Values (Seconds)
300
Device Alias
Values (30 chars)
UserDevice
© Microhard Systems Inc. 63
Page 64

4.0 Configuration
RSSI Check
Enable or disable the RSSI alerts.
Set the threshold for RSSI alerts. When the signal strength drops
below this threshold, an SMS alert will be sent to the number(s)
specified.
Enable or disable SMS Alerts for Roaming Status.
The BulletPlus can send alerts based on the roaming status. Data
rates during roaming can be expensive and it is important to know
when a device has started roaming.
Values (Selection)
Disable RSSI check
Enable RSSI check
Low Threshold (dBm)
Values (dBm)
-99
Carrier Network
Values (Selection)
Disable Roaming Check
Enable Roaming Check
Home / Roaming Status
Values (Selection)
In Roaming
Changed or In Roaming
Changed to Roaming
Enable or disable SMS Alerts for the Ethernet Link status of the LAN
RJ45 port.
The status of the Ethernet Link of the LAN (RJ45) can be used to send
SMS Alerts. The link status may indicate an issue with the connected
device.
SMS Alerts can be sent based on the state changes of the Digital I/O
lines.
Ethernet
Values (Selection)
Disable Ethernet check
Enable Ethernet check
Ethernet Link Status
Values (Selection)
Changed
In no-link
Changed or in no-link
Changed to no-link
I/O Status
Values (Selection)
Disable IO Check
Enable: INPUT Changed
Enable: Output Changed
Enable: INPUT or OUTPUT
Changed.
© Microhard Systems Inc. 64
Page 65

4.0 Configuration
4.3.5 Carrier > Data Usage
The Data Usage tool on the BulletPlus allows users to monitor the amount of cellular data consumed.
Since cellular devices are generally billed based on the amount of data used, alerts can be triggered by
setting daily and/or monthly limits. Notifications can be sent using SMS or Email, allowing a early warning if
configurable limits are about to be exceeded. The usage data reported by the Data Usage Monitor may not
match the data reported by the carrier, but it gives the users an idea of the bandwidth consumed by the
BulletPlus.
If enabled the BulletPlus will track the amount of cellular data consumed. If
disabled, data is not recorded, even in the Current Data Usage display.
© Microhard Systems Inc. 65
Image 4-3-7: Carrier > Data Usage
Status
Values (selection)
Disable
Enable
Page 66

4.0 Configuration
Monthly/Daily Over Limit
Select the notification method used to send alerts when daily or monthly
thresholds are exceeded. If none is selected, notifications will not be sent,
but data usage will be recorded for reference purposes.
Image 4-3-9: Data Usage > SMS Config
Monthly/Daily Data Unit
Select the data unit to be used for data usage monitoring.
Select the data limit for the day or month, used in connection with the data
unit is the previous field. If you want to set the limit to 250 Mbytes, select M
Bytes for the data unit, and 250 for the data limit.
Values (selection)
None
Send Notice SMS
Send Notice Email
Both SMS & Email
Values (selection)
Bytes / K Bytes / M Bytes
G Bytes
Data Limit
Values (1-65535)
500
For Monthly tracking, select the day the billing/data cycles begins. On this
day each month the BulletPlus will reset the data usage monitor numbers.
Up to two (2) additional notices can be sent based on a percentage (10500%) of the threshold value.
If SMS is selected as the notification method, enter the phone number to
send any SMS messages generated when the data usage exceeds the
configured limits.
© Microhard Systems Inc. 66
Period Start Day
Values (1-31)
1 (Day of Month)
Additional Notice 1/2
Values (10-500%)
(none)
Phone Number
Values (phone)
+1403
Page 67

4.0 Configuration
Image 4-3-10: Data Usage > Email Config
Mail Subject
If Email is selected as the notification method, enter the desired email
subject line for the notification email sent when daily and/or monthly usage
limits are exceeded.
If Email is selected as the notification method, enter the SMTP server
details for the account used to send the Email notifications. Domain or IP
address with the associated port as shown.
If Email is selected as the notification method, enter the username of the
Email account used to send Emails.
If Email is selected as the notification method, enter the password of the
Email account used to send Emails. Most email servers require
authentication on outgoing emails.
If Email is selected as the notification method, enter the password of the
Email account used to send Emails. Most email servers require
authentication on outgoing emails.
Values (string)
Daily/Monthly Data Usage
Notice
Mail Server(IP/Name)
Values (xxx:port)
smtp.gmail.com:465
Username
Values (username)
@gmail.com
Password
Values (string)
***
Authentication
Values (selection)
None
SSL/TLS
STARTTLS
SSL/TLS + STARTTLS
Enter the email address of the individual or distribution list to send the
email notification to.
© Microhard Systems Inc. 67
Mail Recipient
Values (xx@xx.xx)
host@
Page 68

4.0 Configuration
Data Usage History
The BulletPlus provides a Odometer that shows the total data used by the BulletPlus. You can also click on
the More link to get a data usage history summary as seen below.
© Microhard Systems Inc. 68
Image 4-3-11: Data Usage > Data Usage Odometer
Page 69

4.0 Configuration
4.4 Wireless (WiFi)
4.4.1 Wireless > Status
The Status window gives a summary of all radio or wireless related settings and connections.
The General Status section shows the Wireless MAC address of the current radio, the Operating Mode
(Access Point, Client), the SSID being used, frequency channel information and the type of security used.
Traffic Status shows statistics about the transmitted and received data.
The BulletPlus shows information about all Wireless connections in the Connection Info section. The
Wireless MAC address, Noise Floor, Signal to Noise ratio (SNR), Signal Strength (RSSI), The transmit and
receive Client Connection Quality (CCQ), TX and RX data rates, and a graphical representation of the
signal level or quality.
© Microhard Systems Inc. 69
Image 4-4-1: Wireless > Status
Page 70

4.0 Configuration
4.4.2 Wireless > Radio1
Radio1 Phy Configuration
The top section of the Wireless Configuration allows for the configuration of the physical radio module. You
can turn the radio on or off, and select the channel bandwidth and frequency as seen below.
Image 4-4-2: Wireless > Radio Configuration
This option is used to turn the radio module on or off. If turned off
Wireless connections can not be made. The default is On.
The Mode defines which wireless standard to use for the wireless
network. The BulletPlus supports 802.11/b/g/n modes as seen here.
Select the appropriate operating mode from the list.
The options below are dependant and vary on the operating mode
chosen here.
Only appears when using 802.11b or b/g modes. Lower channel
bandwidths may provide longer range and be less susceptible to noise
but at the trade off of data rates. Higher channel bandwidth may
provide greater data rates but will be more susceptible to noise and
shorter distance potentials.
Radio
Values (selection)
On / Off
Mode
Values (selection)
802.11B ONLY
802.11BG
802.11NG
Channel Bandwidth
Values (selection)
20MHz Normal Rate
© Microhard Systems Inc. 70
Page 71

4.0 Configuration
High Throughput Mode
Select HT20 for a 20MHz channel, or HT40 for a 40 MHz Channel.
The 40MHz channel is comprised of 2 adjacent 20MHz channels and
the + and—designate to use the higher or lower of the adjacent
channels.
Advanced Capabilities (Only shown if box is checked)
MPDU Aggregation (Enable/Disable) - Allows multiple data frames to be sent in a single transmission
block, allowing for acknowledging or retransmitting if errors occur.
Short GI (Enable/Disable) - GI (guard interval) is the time the receiver waits for any RF reflections to settle
before sampling data. Enabling a short GI (400ns) can increase throughput, but can also increase the error
rate in some installations.
HT Capabilities Info - TX-STBC RX-STBC1 DSSS_CCK-40
Maximum AMSDU (byte) - 3839
Maximum AMPDU (byte) - 65535
Values (selection)
HT20
HT40HT40+
Channel-Freq
The Channel-Freq setting allows configuration of which channel to
operate on, auto can be chosen where the unit will automatically pick a
channel to operate. If a link cannot be established it will try another
channel.
Values (selection)
Auto
Channel 01 : 2.412 GHz
Channel 02 : 2.417 GHz
Channel 03 : 2.422 GHz
Channel 04 : 2.427 GHz
Channel 05 : 2.432 GHz
Channel 06 : 2.437 GHz
Channel 07 : 2.442 GHz
Channel 08 : 2.447 GHz
Channel 09 : 2.452 GHz
Channel 10 : 2.457 GHz
Channel 11 : 2.462 GHz
This setting establishes the transmit power level which will be
presented to the antenna connectors at the rear of the BulletPlus.
Unless required, the Tx Power should be set not for maximum, but
rather for the minimum value required to maintain an adequate system
fade margin.
Refer to FCC (or as
otherwise applicable)
regulations to ascertain,
and not operate beyond,
the maximum allowable
transmitter output power
and effective isotropic
radiated power (EIRP).
© Microhard Systems Inc. 71
TX Power
Values (selection)
11 dBm
12 dBm
13 dBm
14 dBm
15 dBm
16 dBm
17 dBm
18 dBm
19 dBm
20 dBm
21 dBm
22 dBm
23 dBm
24 dBm
25 dBm
26 dBm
27 dBm
28 dBm
29 dBm
30 dBm
Page 72

4.0 Configuration
Wireless Distance
The Wireless Distance parameter allows a user to set the expected
distance the WiFi signal needs to travel. The default is 100m, so the
BulletPlus will assume that the signal may need to travel up to 100m
so it sets various internal timeouts to account for this travel time.
Longer distances will require a higher setting, and shorter distances
may perform better if the setting is reduced.
Once the RTS Threshold defined packet size is reached, the system
will invoke RTS/CTS flow control. A large RTS Threshold will improve
bandwidth, while a smaller RTS Threshold will help the system recover
from interference or collisions caused by obstructions.
Fragment Thr (256 ~ 2346)
The Fragmentation Threshold allows the system to change the
maximum RF packet size. Increasing the RF packet size reduces the
need to break packets into smaller fragments. Increasing the
fragmentation threshold slightly may improve performance if a high
packet error rate is experienced.
The Clear Channel Assessment uses carrier sense and energy
detection to determine if a channel/medium is available for
transmission. Changing the threshold will impact how the BulletPlus
Wifi determines channel availability.
Values (meters)
100
RTS Thr (256 ~ 2346)
Values (selection)
On / OFF
Values (selection)
On / OFF
CCA Power Thr (4 ~ 127)
Values (selection)
28
© Microhard Systems Inc. 72
Page 73

4.0 Configuration
Radio1 Virtual Interface
The bottom section of the Wireless Configuration provides for the configuration of the Operating Mode of
the Wireless Interface, the TX power, Wireless Network information, and Wireless Encryption. The
BulletPlus can support multiple virtual interfaces. These interfaces provide different SSID’s for different
users, and can also be assigned to separate subnets (Network Interfaces) to prevent groups from
interacting.
Image 4-4-3: Wireless > Radio Configuration
Network
Choose between LAN or WAN for the Virtual Interface. If additional
Network Interfaces have been defined in the Network > LAN section,
the Interface name will also appear here.
Values (selection)
LAN
WAN
Etc..
(Additional Interfaces…)
Mode
Access Point - An Access Point may provide a wireless data
connection to many clients, such as stations, repeaters, or other
supported wireless devices such as laptops etc.
If more than 1 Virtual Interface (more than 1 SSID) has been defined,
the BulletPlus can ONLY operate as a Access Point, and will be
locked into this mode.
Station/Client - A Station may sustain one wireless connection, i.e. to an Access Point.
Repeater - A Repeater can be connected to an Access Point to extend the range and provide a
wireless data connection to many clients, such as stations.
Values (selection)
Access Point
Client
Repeater
© Microhard Systems Inc. 73
Page 74

4.0 Configuration
This setting determines the rate at which the data is to be wirelessly transferred.
The default is ‘Auto’ and, in this configuration, the unit will transfer data at the highest possible rate in
consideration of the receive signal strength (RSSI).
Setting a specific value of transmission rate has the benefit of ‘predictability’ of that rate, but if the RSSI
drops below the required minimum level to support that rate, communications will fail.
TX bitrate
802.11 b/g
Auto
1 Mbps (802.11b,g)
2 Mbps (802.11b,g)
5.5 Mbps (802.11b,g)
11 Mbps (802.11b,g)
6 Mbps (802.11g)
9 Mbps (802.11g)
12 Mbps (802.11g)
18 Mbps (802.11g)
24 Mbps (802.11g)
36 Mbps (802.11g)
48 Mbps (802.11g)
54 Mbps (802.11g)
Disabling the SSID broadcast helps secure the wireless network.
Enabling the broadcast of the SSID (Network Name) will permit others
to ‘see’ the wireless network and perhaps attempt to ‘join’ it.
When AP Isolation is enabled wireless devices connected to this SSID
will not be able to communicate with each other. In other words if the
BulletPlus is being used as a Hot Spot for many wireless clients, AP
Isolation would provide security for those clients by not allowing
access to any other wireless device.
802.11n (HT20/HT40)
Auto
mcs-0 (7.2/15) Mbps
mcs-1 (14.4/30.0) Mbps
mcs-2 (21.7/45.0) Mbps
mcs-3 (28.9/60.0) Mbps
mcs-4 (43.3/90.0) Mbps
mcs-5 (57.8/120.0) Mbps
mcs-6 (65.0/135.0) Mbps
mcs-7 (72.2/150.0) Mbps
ESSID Broadcast
Values (selection)
On / Off
AP Isolation
Values (selection)
On / Off
WiFi Multimedia (WMM) is a feature that enhances the quality of
service on a network by prioritizing data packets according to data
type. (Video, Voice, Best Effort, Background).
© Microhard Systems Inc. 74
WMM
Values (selection)
On / Off
Page 75

4.0 Configuration
SSID
SSID: Service Set Identifier.
The ‘name’ of a wireless
network. In an open wireless
network, the SSID is
broadcast; in a closed system
it is not. The SSID must be
known by a potential client for
it to be able to access the
wireless network.
Change the default value for
the Network Name to
something unique for your
network. Do this for an
added measure of security
and to differentiate your
network from others which
may be operating nearby.
All devices connecting to the BulletPlus in a given network must use
the SSID of the BulletPlus. This unique network address is not only a
security feature for a particular network, but also allows other networks
- with their own unique network address - to operate in the same
area without the possibility of undesired data exchange between
networks.
The encryption types defines the type of security used for the Wireless
Interface, to join a network a device must know the correct password/
passphrase/key.
Security options are dependent on the version type. This section
describes all available options. Export versions may not have all
optional available to meet regulatory requirements set government
policies.
This is the password, or preshared key that is required by any device
to connect to the wireless interface of the BulletPlus. It is strongly
recommended to always have a password defined, and changed from
the factory default.
Values (string)
BulletPlus
Encryption Type
Values (selection)
Disabled
WPA (PSK)
WPA2 (PSK)
WPA+WPA2 (PSK)
WPA Enterprise (RADIUS)
WPA2 Enterprise (RADIUS)
WPA+WPA2 Enterprise(RADIUS)
WPA PSK
Values (string)
0123456789
Show Password
Check this box to show the currently configured password for WPA/
WPA2 encryption passphrase.
If using Enterprise (RADIUS) encryption, enter the IP Address of the
RADIUS authentication server here.
If using Enterprise (RADIUS) encryption, enter the port number of the
RADIUS authentication server here.
This is the password, or preshared key that is required by any device
to connect to the wireless interface of the BulletPlus. It is strongly
recommended to always have a password defined, and changed from
the factory default.
Values (selection)
unchecked
RADIUS IP Address
Values (IP Address)
(no default)
RADIUS Port
Values (port)
(no default)
RADIUS Server Key
Values (selection)
0123456789
© Microhard Systems Inc. 75
Page 76

4.0 Configuration
4.4.3 Wireless > HotSpot
The Wireless Hotspot configuration is used when providing public hotspot services and it is required to use
a server or web based authentication service to verify users, provide terms of use or other information
Image 4-4-4: Wireless > Hotspot Network Configuration
Use this option to enable or disable the hotspot authentication service.
There are three different options for the Hotspot Mode:
Simple Internal - Display a simple text based terms of use or
statement to connected users.
Simple External - Display an external webpage
RADIUS/UAM - Use a 3rd Party Authentication service to
authenticate and/or prompt users to agree to terms of
service.
If the Hotspot Mode, RADIUS/UAM is chosen, specify the hotspot URL
as given by your service provider. The address of the UAM Server, the
authentication portal.
If the Hotspot Mode, RADIUS/UAM is chosen, this is a secret
password between the Redirect URL and the Hotspot given by the
hotspot provider.
Hotspot Mode
Values (selection)
Disable
Simple Internal
Simple External
RADIUS/UAM
UAM Login URL
Values
https://
customer.hotspotsystem.com/
customer/hotspotlogin.php
UAM Secret
Values
hotsys123
© Microhard Systems Inc. 76
Page 77

4.0 Configuration
Hotspot Network Configuration
Hotspot Network
This field is used to specify which configured network is bonded to the
hotspot. Sub networks can be created in the Network > LAN menu,
which are dedicated to the hotspot devices.
*The DHCP service for the network used should be turned off as all IP
address assignments will be made by the hotspot service provider.*
Specify the IP Address of the Hotspot application. All hotspot clients
will get an IP address in the same network as the Hotspot.
Specify the Netmask of the Hotspot application. All hotspot clients will
get an IP address in the same network as the Hotspot.
Provide your service providers 1st DNS Server domain.
Values
Varies
Network IP Address
Values
192.168.182.0
Network Netmask
Values
255.255.255.0
DNS Domain
Values
Key.chillispot.info
Primary DNS
Specify the Primary DNS server to be used by devices connected to
the Hotspot network.
Values
208.67.222.222
Secondary DNS
Specify the Secondary DNS server to be used by devices connected
to the Hotspot network.
Values
208.67.222.220
DHCP Start
When devices connect to the BulletPlus Wifi and Hotspot is enabled,
the Hotspot will assign the IP addresses to the connected devices,
select the starting range here.
Values
3
DHCP End
When devices connect to the BulletPlus Wifi and Hotspot is enabled,
the Hotspot will assign the IP addresses to the connected devices,
select the ending range here.
© Microhard Systems Inc. 77
Values
250
Page 78

4.0 Configuration
Hotspot Radius Configuration
Image 4-4-5: Wireless > Hotspot Radius Configuration
Radius NAS ID
This is the RADIUS name of your Hotspot as given by your Hotspot
Service Provider.
As assigned by the Hotspot Service Provider, the name or IP address
of the primary RADIUS Server.
As assigned by the Hotspot Service Provider, the name or IP address
of the alternate RADIUS Server.
The Radius Authentication Port Number. The default is 1812. This is
provided by your Hotspot service provider.
Values
Microhard_1
Radius Server 1
Values
radius.hotspotsystem.com
Radius Server 2
Values
radius2.hotspotsystem.com
Radius Auth Port
Values
1812
Radius Acct Port
The Radius Account Port Number. The default is 1813. This is
provided by your Hotspot service provider.
Also called a shared key, this is the RADIUS password assigned by
you Hotspot provider.
© Microhard Systems Inc. 78
Values
1813
Radius Secret
Values
hotsys123
Page 79

4.0 Configuration
Radius CoA UDP Port
Specify the Radius CoA UDP Port here. This information is supplied by
the hotspot service provider.
Specify the Radius Session Timeout. In seconds, 0 = disabled.
Specify the Radius Idle Timeout. In seconds, 0 = disabled.
Values (port)
3799
Radius Session Timeout
Values (seconds)
3600
Radius Idle Timeout
Values (seconds)
900
© Microhard Systems Inc. 79
Page 80

4.0 Configuration
4.5 Firewall
4.5.1 Firewall > Summary
The Firewall Summary allows a user to see detailed information about how the firewall is operating. The
All, Filter, Nat, Raw, and Mangle options can be used to view different aspects of the firewall.
© Microhard Systems Inc. 80
Image 4-5-1: Firewall > Status
Page 81

4.0 Configuration
4.5.2 Firewall > General
The General Firewall settings allow users to enable or disable the firewall, and to decide which areas of the
modem to protect. The Firewall can also be reset to factory defaults from this area of the WebUI.
In a cellular device such as this, it is highly recommended to configure the firewall to protect any devices
connected to the modem, and to control data usage. This is especially important with units set up with a
public IP address as the modem is effectively on the public internet and is susceptible to a wide range of
threats which may severely impact the data usage. This can be avoided by blocking all Cellular traffic and
setting up specific rules to either open only used ports, or even restrict access to specific IP/networks.
For best practices and to
control data usage it is
critical that the firewall be
configured properly.
It is recommended to block
all incoming Cellular traffic
and create rules to open
specific ports and/or use
ACL lists to limit incoming
connections.
When Carrier Request is
set to ‘Allow’ the modem is
open to anyone, this is not
recommended as it may
impact data usage from
unwanted sources.
Image 4-5-2: Firewall > General
WAN Remote Management
Allow remote management of the BulletPlus on the WAN side using the
WebUI on port 80(HTTP), and 443 (HTTPS). If disabled, the configuration
can only be accessed from the LAN (or Cellular if enabled)..
Carrier Remote Management
Allow remote management of the BulletPlus from the Cellular side of using
the WebUI on port 80(HTTP), and 443 (HTTPS). If disabled, the
configuration can only be accessed from the LAN (or WAN if enabled)..
When Blocked the BulletPlus will block all requests from devices on the
WAN unless specified otherwise in the Access Rules, MAC List, IP List
configurations. Access to ports 80 (HTTP) and 443 (HTTPS-if enabled), is
still available unless disabled in the WAN Remote Management option.
When Blocked all requests from devices on the Cellular (Wireless Carrier)
side will be blocked, unless specified otherwise in the Access Rules, MAC
List, IP List configurations. Access to ports 80 (HTTP) and 443 (HTTPS-if
enabled), is still available unless disabled in the 4G Remote Management
option.
Values
Enable / Disable
Values
Enable / Disable
WAN Request
Values
Block / Allow
Carrier Request
Values
Block / Allow
© Microhard Systems Inc. 81
Page 82

4.0 Configuration
LAN to WAN Access Control
Allows or Blocks traffic from the LAN accessing the WAN unless specified
otherwise using the Access Rules, MAC, and IP List configuration.
LAN to Carrier Access Control
Allows or Blocks traffic from the LAN accessing the Cell connection unless
specified otherwise using the Access Rules, MAC, and IP List
configuration.
The Anti-Spoof protection is to create some firewall rules assigned to the
external interface (WAN & Cellular) of the firewall that examines the source
address of all packets crossing that interface coming from outside. If the
address belongs to the internal network or the firewall itself, the packet is
dropped.
Packet Normalization is the normalization of packets so there are no
ambiguities in interpretation by the ultimate destination of the packet. The
scrub directive also reassembled fragmented packets, protecting some
operating systems from some forms of attack, and drops TCP packets that
have invalid flag combinations.
Values
Block / Allow
Values
Block / Allow
Anti-Spoof
Values
Enable / Disable
Packet Normalization
Values
Enable / Disable
© Microhard Systems Inc. 82
Page 83

4.0 Configuration
4.5.3 Firewall > Port Forwarding
The BulletPlus can be used to provide remote access to connected devices. To access these devices a
user must define how incoming traffic is handled by the BulletPlus. If all incoming traffic is intended for a
specific connected device, DMZ could be used to simplify the process, as all incoming traffic can be
directed towards a specific IP address.
In the case where there is multiple devices, or only specific ports need to be passed, Port forwarding is
used to forward traffic coming in from the WAN (Cellular) to specific IP Addresses and Ports on the LAN.
Port forwarding can be used in combination with other firewall features, but the Firewall must be enabled
for Port forwarding to be in effect. If the WAN Request is blocked on the General Tab, additional rules and/
or IP Lists must be set up to allow the port forwarding traffic to pass through the firewall.
IP-Passthrough (Carrier > Settings) is another option for passing traffic through the BulletPlus, in this case
all traffic is passed to a single device connected to the RJ45 port of the BulletPlus, The device must be set
for DHCP, as the BulletPlus assigns the WAN IP to the device, and the modem enters into a transparent
mode, routing all traffic to the RJ45 port. This option bypasses all firewall features of the BulletPlus, as well
as all other features of the BulletPlus such as COM, VPN, GPS etc.
If DMZ is enabled and an
exception port for the WebUI
is not specified, remote
management will not be
possible. The default port for
remote management is TCP
80.
© Microhard Systems Inc. 83
Image 4-5-3: Firewall > Port Forw arding
Page 84

4.0 Configuration
DMZ Mode
If the firewall is set to block
incoming traffic on the WAN
and/or Carrier interfaces,
additional rules or IP/MAC
lists must be configured to
allow desired traffic access.
Enable or disable DMZ Mode. DMZ can be used to forward all traffic to the
DMZ Server IP listed below.
Enter the IP address of the device on the LAN side of the BulletPlus where
all the traffic will be forwarded to.
Enter a exception port number that will NOT be forwarded to the DMZ
server IP. Usually a configuration or remote management port that is
excluded to retain external control of the BulletPlus.
Firewall Port Forwarding Configuration
This is simply a field where a convenient reference or description is added
to the rule. Each Forward must have a unique rule name and can use up to
10 characters.
Values (selection)
Disable / Enable
DMZ Server IP
Values (IP Address)
192.168.100.100
Exception Port
Values (Port #)
0
Name
Values (10 chars)
Forward
Source
Select the source for the traffic, from either the 3G/Cellular or from the
WAN.
Enter the IP address of the intended internal (i.e. on LAN side of
BulletPlus) server. This is the IP address of the device you are forwarding
traffic to.
Target port number of the internal server on the LAN IP entered above.
Select the type of transport protocol used. For example Telnet uses TCP,
SNMP uses UDP, etc.
Port number of the incoming request (from 4G/WAN-side).
Values (selection)
Carrier / WAN
Internal Server IP
Values (IP Address)
192.168.2.1
Internal Port
Values (Port #)
3000
Protocol
Values (selection)
TCP / UDP / Both
External Port
Values (Port #)
© Microhard Systems Inc. 84
2000
Page 85

4.0 Configuration
4.5.4 Firewall > MAC-IP List
MAC List configuration can be used to control which physical LAN devices can access the ports on the
BulletPlus, by restricting or allowing connections based on the MAC address. IP List configuration can be
used to define who or what can access the BulletPlus, by restricting or allowing connections based on the
IP Address/Subnet.
MAC-IP List can be used alone or in combination with LAN to WAN/4G Access Control to provide secure
access to the physical ports of the BulletPlus.
Firewall MAC List Configuration
The Rule Name field is required to give the rule a convenient name for
reference. Each rule must have a unique name, up to 10 characters in
length.
Specify the MAC Address to be added to the list. Must be entered in the
correct format as seen above. Not case sensitive.
© Microhard Systems Inc. 85
Image 4-5-5: Firewall > MAC-IP List
Rule Name
Values (10 chars)
MAC_List
MAC Address
Values (MAC Address)
00:00:00:00:00:00
Page 86

4.0 Configuration
Firewall MAC List Configuration (Continued)
Action
The Action is used to define how the rule handles the connection request.
ACCEPT will allow a connection, while REJECT (error) and DROP (quietly
dropped), will refuse connections.
Firewall IP List Configuration
The Rule Name field is required to give the rule a convenient name for
reference. Each rule must have a unique name, up to 10 characters in
length.
The Action is used to define how the rule handles the connection request.
ACCEPT will allow a connection, while REJECT (error) and DROP (quietly
dropped), will refuse connections.
Enter the specific zone that the IP List will apply to, Cellular, LAN, WAN or
None (both).
Values (selection)
ACCEPT
DROP
REJECT
Rule Name
Values (10 chars)
IP_List
Action
Values (selection)
ACCEPT / DROP / REJECT
Source
Values (Selection)
LAN/LAN1/WAN/Cell/USB
NONE
Match incoming traffic from the specified source IP range. Boxes accept
single IP Addresses without network masks, example: 192.168.1.0 to
192.168.1.255 represents all IP Addresses in the 192.168.1.0/24 network.
(Put same IP in both boxes for a single IP match.)
© Microhard Systems Inc. 86
Source IP Address
Values (IP Address)
192.168.0.0
Page 87

4.0 Configuration
4.5.5 Firewall > Rules
Once the firewall is turned on, rules configuration can be used to define specific rules on how local and
remote devices access different ports and services. MAC List and IP List are used for general access, and
are applied before rules are processed.
It is highly recommended to block as much traffic as possible from the modem, especially when using a
public IP address. The best security would to be to allow traffic only from trusted IP addresses, and only
the specific ports being used, and block everything else. Not configuring the firewall and the firewall rules
correctly could result in unpredictable data charges from the cellular carrier.
Refer to Appendix D for an
example of how to set up a
firewall to block all
connections and then add
access to only specific IP’s
and Ports.
Appendix D: Firewall
Example
Image 4-5-6: Firewall > Rules
Rule Name
The rule name is used to identify the created rule. Each rule must have a
unique name and up to 10 characters can be used.
Values (10 Chars)
characters
Action
The Action is used to define how the rule handles the connection request.
ACCEPT will allow a connection, while REJECT (error) and DROP
(quietly dropped), will refuse connections.
This is configured based on how the WAN/Carrier Request and LAN to
WAN/Carrier Access Control are configured in the previous menus.
Values (selection)
ACCEPT
DROP
REJECT
Source
Select the zone which is to be the source of the data traffic. The LAN/
LAN1 refers to local connections on the BulletPlus.
© Microhard Systems Inc. 87
Values
LAN/LAN1/WAN/Carrier
None
Page 88

4.0 Configuration
Source IPs
Match incoming traffic from the specified source IP range. Boxes accept
single IP Addresses without network masks, example: 192.168.1.0 to
192.168.1.255 represents all IP Addresses in the 192.168.1.0/24 network.
(Put same IP in both boxes for a single IP match.)
Select the zone which is the intended destination of the data traffic. 3G/4G
applies to the wireless connection to the cellular carrier and the LAN,
LAN1, USB refers to local connections on the BulletPlus.
Match incoming traffic from the specified destination IP range. Boxes
accept single IP Addresses without network masks, example: 192.168.1.0
to 192.168.1.255 represents all IP Addresses in the 192.168.1.0/24
network. (Put same IP in both boxes for a single IP match.)
Match incoming traffic directed at the given destination port or port range.
(To specify a port range use a From:To (100:200) format)
Values (IP Address)
192.168.0.0 to
192.168.0.0
Destination
Values (selection)
LAN/LAN1/Cell/WAN/USB
None
Destination IPs
Values (IP Address)
192.168.0.0 to
192.168.0.0
Destination Port
Values (port)
0
The protocol field defines the transport protocol type controlled by the rule.
Protocol
Values
TCP
UDP
Both
ICMP
© Microhard Systems Inc. 88
Page 89

4.0 Configuration
4.5.6 Firewall > Firewall Default
The Firewall Default option allows a user to return the modems firewall setting back to the default values
without having to reset the entire modem.
Image 4-4-7: Firewall > Firew all Default
© Microhard Systems Inc. 89
Page 90

4.0 Configuration
4.6 VPN
4.6.1 VPN > Summary
A Virtual Private Network (VPN) may be configured to enable a tunnel between the BulletPlus and a
remote network. The BulletPlus supports VPN IPsec Gateway to Gateway (site-to-site) tunneling, meaning
you are using the BulletPlus to create a tunnel to a network with VPN capabilities (Another BulletPlus or
VPN capable device). The BulletPlus can also operate as a L2TP Server, allowing users to VPN into the
unit from a remote PC, and a L2TP Client.
© Microhard Systems Inc. 90
Image 4-6-1: VPN > Summary
Page 91

4.0 Configuration
4.6.2 VPN > Gateway To Gateway (Site-to-Site)
A Gateway to Gateway connection is used to create a tunnel between two VPN devices such as an
BulletPlus and another device (another BulletPlus or Cisco VPN Router or another vendor…). The local
and remote group settings will need to be configured below to mirror those set on the other VPN device.
Enter a name for the VPN Tunnel. Up to 16 different tunnels can be
created, each requiring a unique name.
© Microhard Systems Inc. 91
Image 4-6-2: VPN > Gateway to Gateway
Tunnel Name
Values (chars)
tunnel1
Page 92

4.0 Configuration
Enable
Used to enable (checked) is disable (unchecked) the VPN tunnel.
Values (checkbox)
Enable (Checked)
Local Group Setup
Local Security Gateway Type
Specify the method for identifying the router to establish the VPN tunnel.
The Local Security Gateway is on this router; the Remote Security
Gateway is on the other router. At least one of the routers must have either
a static IP address or a dynamic IP with server id to make a connection.
IP Only: Choose this option if this router has a static WAN IP address. The WAN IP address appears
automatically. For the Remote Security Gateway Type, an extra field appears. If you know the IP address
of the remote VPN router, choose IP Address, and then enter the address.
IP + Server ID: Choose this option if this router has a static WAN IP address and a server id. The WAN IP
address appears automatically. For the Remote Security Gateway Type, an extra field appears. If you
know the IP address of the remote VPN router, choose IP Address, and then enter the address.
Dynamic IP + Server ID: Choose this option if this router has a dynamic IP address and a server id
(available such as @microhard.vpn). Enter the server id to use for authentication. The server id can be
used only for one tunnel connection.
Values (selection)
IP Only
IP + Server ID
Dynamic IP + Server ID
Interface IP Address
Displays the IP address of the BulletPlus, which is the local VPN Gateway.
This option appears when the Local Security Gateway Type specifies that
the Server ID is required for the connection. The Server ID must be in the
format @name, where name can be anything. Both routers must know
each others names to establish a connection.
Next-hop Gateway means the next-hop gateway IP address for the local or
remote gateway participant's connection to the public network.
Define the local network by specifying the local subnet. The local and
remote routers must use different subnets.
Values (IP Address)
Current IP Address
Server ID
Values (characters)
(no default)
Next-hop Gateway IP
Values (IP Address)
(no default)
Group Subnet IP
Values (IP Address)
(no default)
© Microhard Systems Inc. 92
Page 93

4.0 Configuration
Group Subnet Mask
Specify the subnet mask of the local network address.
Group Subnet Gateway
Enter the Gateway for the local group network.
Remote Group Setup
Remote Security Gateway Type
Specify the method for identifying the router to establish the VPN tunnel.
The Local Security Gateway is on this router; the Remote Security
Gateway is on the other router. At least one of the routers must have either
a static IP address or a dynamic IP with server id to make a connection.
(See Local Group Setup for details)
If the remote VPN router has a static IP address, enter the IP address of
the remote VPN Gateway here.
Values (IP Address)
255.255.255.0
Values (IP Address)
(no default)
Values (selection)
IP Only
IP + Server ID
Dynamic IP + Server ID
Gateway IP Address
Values (IP Address)
(no default)
This option appears when the Remote Security Gateway Type specifies
that the Server ID is required for the connection. The Server ID must be in
the format @name, where name can be anything. Both routers must know
each others names to establish a connection.
Next-hop Gateway means the next-hop gateway IP address for the local or
remote gateway participant's connection to the public network.
Define the remote network by specifying the local subnet.
Specify the subnet mask of the remote network address.
Server ID
Values (IP Address)
(no default)
Next-hop Gateway IP
Values (IP Address)
(no default)
Subnet IP Address
Values (IP Address)
(no default)
Subnet Mask
Values (IP Address)
255.255.255.0
© Microhard Systems Inc. 93
Page 94

4.0 Configuration
IPsec Setup
Phase 1 DH Group
Select value to match the values required by the remote VPN router.
Select value to match the Phase 1 Encryption type used by the remote
VPN router.
Phase 1 Authentication
Select value to match the Phase 1 Authentication used by the remote VPN
router.
Select value to match the values required by the remote VPN router.
Values (selection)
modp1024
modp1536
modp2048
Phase 1 Encryption
Values (selection)
3des
aes
aes128
aes256
Values (selection)
md5
sha1
Phase 1 SA Life Time
Values
28800
Perfect Forward Secrecy (pfs)
Select value to match the values required by the remote VPN router.
Values (selection)
Disable / Enable
Phase 2 DH Group
Select value to match the values required by the remote VPN router.
Values (selection)
modp1024
modp1536
modp2048
Phase 2 Encryption
Select value to match the Phase 1 Encryption type used by the remote
VPN router.
© Microhard Systems Inc. 94
Values (selection)
3des
aes
aes128
aes256
Page 95

4.0 Configuration
Phase 2 Authentication
Select value to match the Phase 1 Authentication used by the remote VPN
router.
Select value to match the values required by the remote VPN router.
Set the Preshared Key required to authenticate with the remote VPN
router.
Dead Peer Detection is used to detect if there is a dead peer. Set the DPD
Delay (seconds), as required.
Values (selection)
md5
sha1
Phase 2 SA Life Time
Values
3600
Preshared Key
Values (characters)
password
DPD Delay(s)
Values (seconds)
32
DPD Timeout(s)
Set the DPD (Dead Peer Detection) Timeout (seconds), as required.
Set the DPD action, hold or clear, as required.
Values (seconds)
122
DPD Action
Values (seconds)
Hold
Clear
© Microhard Systems Inc. 95
Page 96

4.0 Configuration
4.6.3 VPN > L2TP Client
The BulletPlus can operate as a L2TP Client, allowing a VPN connection to be made with a L2TP Server.
Enter a name for the VPN Tunnel. Up to 16 different tunnels can be
created, each requiring a unique name.
Used to enable (checked) is disable (unchecked) the VPN tunnel.
© Microhard Systems Inc. 96
Image 4-6-3: VPN > Client to Gateway
Tunnel Name
Values (chars)
tunnel1
Enable
Values (checkbox)
Enable (Checked)
Page 97

4.0 Configuration
Local Interface IP Address
This will display the current BulletPlus WAN (Cellular) IP Address.
Remote Gateway IP Address
Enter the IP Address of the Remote Gateway that you wish to establish a
connection with.
Some servers require that you know the Server ID as well as the IP
address. Enter the Server ID of the remote router here.
In order to communicate with the devices on the other side of the tunnel,
the BulletPlus must know which data to pass through the tunnel, to do this
enter the Remote Subnet network IP address here.
Enter the Remote Subnet Mask
Values (IP Address)
Current IP
Values (IP Address)
none
Remote Server ID
Values
none
Remote Subnet IP
Values (IP Address)
none
Remote Subnet Mask
Values (IP Address)
Idle time before hanging up
Enter the Idle time (in seconds) to wait before giving up the PPP
connection. The default is 0, which means the time is infinite. (0—65535)
Enter the Username
The preshared key is required to connect to the L2TP Server.
IPSec Setup - See previous sections for additional info.
none
Values (seconds)
0
Username
Values (chars)
0
Preshared Key
Values (chars)
0
© Microhard Systems Inc. 97
Page 98

4.0 Configuration
4.6.4 Network > OpenVPN
OpenVPN Server
The BulletPlus supports OpenVPN and can be configured as a Server or a Client. This section outlines the
configuration of a OpenVPN Server.
Enable/Disable the OpenVPN Mode by selecting the mode to operate in,
Client or Server. When the Server is enabled it will be listening for incoming
connection requests from OpenVPN Clients.
The TCP/UDP port which the server is listening on. Default is 1194
© Microhard Systems Inc. 98
Image 4-6-4: VPN > OpenVPN Server
OpenVPN Mode
Values (selection)
Client / Server / Disable
Port
Values (port)
1194
Page 99

4.0 Configuration
Tunnel Protocol
Select the Tunnel Protocol to be used. The options are TCP and UDP, the
default is UDP.
The maximum resulting UDP send packet size after the OpenVPN has
fully encapsulated data. Packets exceeding this max value will be
fragmented.
The root certificate file (CA file) that all the server and clients must have in
common.
Public Server Certificate
The Public Server Certificate which is the certificate file that resides on only
the server.
The private Server Key, which should not be disclosed.
Values (selection)
TCP / UDP
MSSFIX/Fragment size
Values (size)
1370
Root Certificate
Values (chars)
ca.crt
Values (chars)
server.crt
Private Server Key
Values (chars)
The server and each client must have a copy of this key to do TLS
authentication.
User/Password Authenication
Select the OpenVPN username as setup/defined in the VPN Users menu.
Diffie hellman parameter
Select between 1024 bit and 2048 bit Diffie Hellman keys for security.
Server Virtual Subnet / Subnet Mask
The subnet and subnet mask that the server will create to assign address
to itself and the clients.
server.key
TLS Auth Key
Values (chars)
(no default)
Values (selection)
(no default)
Values (selection)
DH2048 / DH1024
Values (IP Address)
10.8.0.0
© Microhard Systems Inc. 99
Page 100

4.0 Configuration
Push DNS to Client
If enabled (Auto) the server will push its DNS server information to the
client. Manual allows the DNS information to be manually entered.
When select yes, the clients will not see each other. Select no, it will allow
different clients to be able to "see" each other. By default, clients will only
see the server.
Keep Alive Ping Interval
The keep alive directive causes ping-like messages to be sent back and
forth over the link so that each side knows when the other side has gone
down. Default 10 seconds.
Default 120 seconds. Ping every 10 seconds, assume that remote peer is
down if no ping received during a 120 second time period. (must be at least
twice the interval specified above)
Select a cryptographic cipher. Must be the same on Server and Client.
Values (selection)
NO / Auto / Manual
Client Isolation
Values (selection)
No / Yes
Values (seconds)
10
Keep Alive Ping Period
Values (seconds)
120
Cipher
Values (selection)
DES-CBC
RC2-CBC
DES-EDE-CBC
DES-EDE3-CBC
DESX-CBC
BF-CBC
RC2-40-CBC
CAST5-CBC
RC2-64-CBC
AES-128-CBC
AES-192-CBC
AES-256-CBC
SEED-CBC
Enable/Disable LZO compression on the VPN link. Lempel–Ziv–
Oberhumer (LZO) is a lossless data compression algorithm.
OpenVPN support multiple subnet behind server/client. So that the vpn
connection can reach the subnet behind. Each subnet must be specified to
the data can be routed correctly.
© Microhard Systems Inc. 100
Use LZO Compression
Values (selection)
Enable / Disable
OpenVPN Server Network Settings
Values (selection)
(no default)
 Loading...
Loading...