Page 1

dsPIC30F2010
Data Sheet
High-Performance, 16-Bit
Digital Signal Controllers
© 2006 Microchip Technology Inc. DS70118G
Page 2

Note the following details of the code protection feature on Microchip devices:
• Microchip products meet the specification contained in their particular Microchip Data Sheet.
• Microchip believes that its family of products is one of the most secure families of its kind on the market today, when used in the
intended manner and under normal conditions.
• There are dishonest and possibly illegal methods used to breach the code protection feature. All of these methods, to our
knowledge, require using the Microchip products in a manner outside the operating specifications contained in Microchip’s Data
Sheets. Most likely, the person doing so is engaged in theft of intellectual property.
• Microchip is willing to work with the customer who is concerned about the integrity of their code.
• Neither Microchip nor any other semiconductor manufacturer can guarantee the security of their code. Code protection does not
mean that we are guaranteeing the product as “unbreakable.”
Code protection is constantly evolving. We at Microchip are committed to continuously improving the code protection features of our
products. Attempts to break Microchip’s code protection feature may be a violation of the Digit al Millennium Copyright Act. If suc h a c t s
allow unauthorized access to your software or other copyrighted work, you may have a right to sue for relief under that Act.
Information contained in this publication regarding device
applications and t he lik e is provided only for your convenience
and may be su perseded by upda t es . It is y our responsibility to
ensure that your application meets with your specifications.
MICROCHIP MAKES NO REPRESENTATIONS OR
WARRANTIES OF ANY KIND WHETHER EXPRESS OR
IMPLIED, WRITTEN OR ORAL, STATUTORY OR
OTHERWISE, RELATED TO THE INFORMATION,
INCLUDING BUT NOT LIMITED TO ITS CONDITION,
QUALITY, PERFORMANCE, MERCHANTABILITY OR
FITNESS FOR PURPOSE. Microchip disclaims all liability
arising from this information and its use. Use of Microchip
devices in life supp ort and/or safety ap plications is entir ely at
the buyer’s risk, and the buyer agrees to defend, indemnify and
hold harmless M icrochip from any and all dama ges, claims,
suits, or expenses re sulting from such use. No licens es are
conveyed, implicitly or otherwise, under any Microchip
intellectual property rights.
Trademarks
The Microchip name and logo, the Microchip logo, Accuron,
dsPIC, K
EELOQ, microID, MPLAB, PIC, PIC, PICSTAR T,
PRO MATE, PowerSmart, rfPIC and SmartShunt are
registered trademarks of Microchip Technology Incorporated
in the U.S.A. and other countries.
AmpLab, FilterLab, Migratable Memory, MXDEV, MXLAB,
SEEVAL, SmartSensor and The Embedded Control Solutions
Company are registered trademarks of Microchip Technology
Incorporated in the U.S.A.
Analog-for-the-Digital Age, Application Maestro, CodeGuard,
dsPICDEM, dsPICDEM.net, dsPICworks, ECAN,
ECONOMONITOR, FanSense, FlexROM, fuzzyLAB,
In-Circuit Serial Programming, ICSP, ICEPIC, Linear Active
Thermistor, Mindi, MiWi, MPASM, MPLIB, MPLINK, PICkit,
PICDEM, PICDEM.net, PICLAB, PICtail, PowerCal,
PowerInfo, PowerMate, PowerTool, REAL ICE, rfLAB,
rfPICDEM, Select Mode, Smart Serial, SmartT el, Total
Endurance, UNI/O, WiperLock and ZENA are trademarks of
Microchip Technology Incorporated in the U.S.A. and other
countries.
SQTP is a service mark of Microchip Technology Incorporated
in the U.S.A.
All other trademarks mentioned herein are property of their
respective companies.
© 2006, Microchip Technology Incorporated, Printed in the
U.S.A., All Rights Reserved.
Printed on recycled paper.
Microchip received ISO/TS-16949:2002 certification for its worldwide
headquarters, design and wafer fabrication facilities in Chandler and
Tempe, Arizona, Gresham, Oregon and Mountain View, California. The
Company’s quality system processes and procedures are for its
PICmicro
EEPROMs, microperipherals, nonvolatile memory and analog
products. In addition, Microchip’s quality system for the design and
manufacture of development systems is ISO 9001:2000 certified.
®
8-bit MCUs, KEELOQ
®
code hopping devices, Serial
DS70118G-page ii © 2006 Microchip Technology Inc.
Page 3

dsPIC30F2010
28-Pin dsPIC30F2010 Enhanced Flash
16-Bit Digital Signal Controller
Note: This data sheet summarizes features of this g roup
of dsPIC30F devices and is not intended to be a complete
reference source. For more information on the CPU,
peripherals, register descriptions and general device
functionality, refer to the “dsPIC30F Family Reference
Manual” (DS70046). For more informat ion on the device
instruction set and programming, refer to the “dsPIC30F/
33F Programmer’s Reference Manual” (DS70157).
High-Performance Modified RISC CPU:
• Modified Harvard architecture
• C compiler optimized instruction set architecture
• 83 base instructions with flexible addressing
modes
• 24-bit wide instructions, 16-bit wide data path
• 12 Kbytes on-chip Fla sh program space
• 512 bytes on-chip data RAM
• 1 Kbyte nonvolatile data EEPROM
• 16 x 16-bit working register array
• Up to 30 MIPs operation:
- DC to 40 MHz external clock input
- 4 MHz-10 MHz oscillator input with
PLL active (4x, 8x, 16x)
• 27 interrupt sources
• Three external interrupt sources
• 8 user-selectable priority levels for each interrupt
• 4 processor exceptions and software traps
DSP Engine Features:
• Modulo and Bit-Reversed modes
• Two 40-bit wide accumulators with optional
saturation logic
• 17-bit x 17-bit single-cycle hardw are frac tio nal /
integer multiplier
• Single-cycle Multiply-Accumulate (MAC)
operation
• 40-stage Barrel Shifter
• Dual data fetch
Peripheral Features:
• High current sink/source I/O pins: 25 mA/25 mA
• Three 16-bit timers/counters; optionally pair up
16-bit timers into 32-bit timer modules
• Four 16-bit capture input functions
• Two 16-bit compare/PWM output functions
- Dual Compare mode available
• 3-wire SPI modules (supports 4 Frame modes)
2
•I
CTM module supports Multi-Master/Slave mode
and 7-bit/10-bit addressing
• Addressable UART modules with FIFO buffers
Motor Control PWM Module Features:
• 6 PWM output channels
- Complementary or Independent Output
modes
- Edge and Center-Aligned modes
• 4 duty cycle generators
• Dedicated time base with 4 modes
• Programmable output polarity
• Dead-time control for Complementary mode
• Manual output control
• Trigger for synchron iz ed A/D conv ersion s
Quadrature Encoder Interface Module Features:
• Phase A, Phase B and Index Pulse input
• 16-bit up/down position counter
• Count direction status
• Position Measurement (x2 and x4) mode
• Programmable digital noise filters on inputs
• Alternate 16-bit Timer/Counter mode
• Interrup t on position counter rollover/underflow
Analog Features:
• 10-bit Analog-to-Digital Converter (ADC) with:
- 1 Msps (for 10-bit A/D) conversion rate
- Six input channels
- Conversion available during Sleep and Idle
• Programmable Brown-out Reset
© 2006 Microchip Technology Inc. DS70118G-page 1
Page 4

dsPIC30F2010
Special Digital Signal Controller Features:
• Detects clock failure and switches to on-chip lowpower RC oscillator
• Programmable code protection
• Enhanced Flash program memory:
- 10,000 erase/write cycle (min.) for
industrial temperature range, 100K (typical)
• Data EEPROM memory:
- 100,000 erase/write cycle (min.) for
industrial temperature range, 1M (typical)
• Self-reprogrammable under software control
• Power-on Reset (POR), Power-up Timer (PWRT )
and Oscillator Start-up Timer (OST)
• Flexible Watchdog Timer (WDT) with on-chip lowpower RC oscillator for reliable operation
• In-Circuit Serial Programming™ (ICSP™)
programming capability
• Selectable Power Management modes
- Sleep, Idle and Alternate Clock modes
CMOS Technology:
• Low-power, high-speed Flash technology
• Wide operating voltage range (2.5V to 5.5V)
• Industrial and Extended temperature ranges
• Low power consumption
• Fail-Safe clock monitor operation
dsPIC30F Motor Control and Power Conversion Family*
Program
Device Pins
dsPIC30F2010 28 12K/4K 512 1024 3 4 2 6 ch 6 ch Yes 1 1 1 –
dsPIC30F3010 28 24K/8K 1024 1024 5 4 2 6 ch 6 ch Yes 1 1 1 –
dsPIC30F4012 28 48K/16K 2048 1024 5 4 2 6 ch 6 ch Yes 1 1 1 1
dsPIC30F3011 40/44 24K/8K 1024 1024 5 4 4 6 ch 9 ch Yes 2 1 1 –
dsPIC30F4011 40/44 48K/16K 2048 1024 5 4 4 6 ch 9 ch Yes 2 1 1 1
dsPIC30F5015 64 66K/22K 2048 1024 5 4 4 8 ch 16 ch Yes 1 2 1 1
dsPIC30F6010 80 144K/48K 8192 4096 5 8 8 8 ch 16 ch Yes 2 2 1 2
dsPIC30F6010A 80 144K/48K 8192 4096 5 8 8 8 ch 16 ch Yes 2 2 1 2
Mem. Bytes/
Instructions
SRAM
Bytes
EEPROM
Bytes
Timer
16-bit
Input
* This table provi des a summ ary of the ds PIC30F 2010 p eriphe ral feat ures. Ot her a vailable de vices in the ds PIC30 F
Motor Control and Power Conversion Family are shown for feature comparison.
Cap
Output
Comp/Std
PWM
Motor
Control
PWM
A/D 10-bit
1 Msps
Quad
Enc
TM
C
SPI
2
UART
I
CAN
DS70118G-page 2 © 2006 Microchip Technology Inc.
Page 5

Pin Diagrams
dsPIC30F2010
28-Pin SDIP and SOIC
EMUD3/AN0/VREF+/CN2/RB0
EMUC3/AN1/V
AN2/SS1/LVDIN/CN4/RB2
EMUD1/SOSCI/T2CK/U1ATX/CN1//RC13
EMUC1/SOSCO/T1CK/U1ARX/CN0/RC14
EMUD2/OC2/IC2/INT2/RD1
REF-/CN3/RB1
AN3/INDX/CN5/RB3
AN4/QEA/IC7/CN6/RB4
AN5/QEB/IC8/CN7/RB5
OSC1/CLKI V
28-Pin QFN
MCLR
VDD
1
2
3
4
5
6
7
SS
8
9
10
11
12
13
14
28
AV
DD
AVSS
27
PWM1L/RE0
26
dsPIC30F2010
PWM1H/RE1
25
PWM2L/RE2
24
PWM2H/RE3
23
PWM3L/RE4
22
PWM3H/RE5V
21
DD
20
SSOSC2/CLKO/RC15
V
19
PGC/EMUC/U1RX/SDI1/SDA/RF2
18
PGD/EMUD/U1TX/SDO1/SCL/RF3
17
FLTA/INT0/SCK1/OCFA/RE8
16
15
EMUC2/OC1/IC1/INT1/RD0
AN2/SS1/LVDIN/CN4/RB2
AN3/INDX/CN5 RB3
AN4/QEA/IC7/CN6/RB4
AN5/QEB/IC8/CN7/RB5
V
OSC1/CLKI
OSC2/CLKO/RC15
SS
EMUD3/AN0/VREF+/CN2/RB0
EMUC3/AN1/VREF- /CN3/RB1
27
28
1
2
3
dsPIC30F2010
4
5
6
7
8
9
EMUD1/SOSCI/T2CK/U1ATX/CN1/RC13
EMUC1/SOSCO/T1CK/U1ARX/CN0/RC14
AVDD
AVSS
PWM1L/RE0
MCLR
23
24
25
26
1011121314
DD
V
/INT0/SCK1/OCFA/RE8
EMUD2/OC2/IC2/INT2/RD1
EMUC2/OC1/IC1/INT1/RD0
FLTA
PWM1H/RE1
22
21
PWM2L/RE2
20
PWM2H/RE3
PWM3L/RE4
19
PWM3H/RE5
18
V
DD
17
VSS
16
PGC/EMUC/U1RX/SDI1/SDA/RF2
15
PGD/EMUD/U1TX/SDO1/SCL/RF3
© 2006 Microchip Technology Inc. DS70118G-page 3
Page 6
dsPIC30F2010
Table of Contents
1.0 Device Overview..........................................................................................................................................................................5
2.0 CPU Architecture Overview..........................................................................................................................................................9
3.0 Memory Organization................................................................................................................................................................. 19
4.0 Address Generator Units............................................................................................................................................................ 31
5.0 Interrupts.................................................................................................................................................................................... 37
6.0 F la sh Program Memory..............................................................................................................................................................43
7.0 Data EEPROM Memory............................................................................................................................................................. 49
8.0 I /O Po rts.....................................................................................................................................................................................53
9.0 Timer1 Module ........................................................................................................................................................................... 57
10.0 Timer2/3 Module ...................................... .. .. .... .. ..... .... .. .. .. .. .... ..... .. .. .... .. .. .. .. ....... .. .. .. .... .............................................................61
11.0 Input Capture Module........................................................................................ .. .... .. .. .... ........................................................... 67
12.0 Output Compare Module............................................................................ ................................................................................ 71
13.0 Quadrature Encoder Interface (QEI) Module ............................................................................................................................. 75
14.0 Motor Control PWM Module....................................................................................................................................................... 81
15.0 SPI Module.................................................................................................................................................................................91
16.0 I2C Module.................................................................................................................................................................................95
17.0 Universal Asynchronous Receiver Transmitter (UART) Module .............................................................................................. 103
18.0 10-bit High-Speed Analog-to-Digital Converter (ADC) Module ................................................................................................111
19.0 System Integration.............. ................................................................. ....................................................................................123
20.0 Instruction Set Summary..........................................................................................................................................................137
21.0 Development Support. .............................................................................................................................................................. 145
22.0 Electrical Characteristics..........................................................................................................................................................149
23.0 Packaging Information...................................................................... ........................................................................................187
The Microchip Web Site..................................................................................................................................................................... 199
Customer Change Notification Service ..................................... ...... ............. ...... ............... ...... ...........................................................199
Customer Support..............................................................................................................................................................................199
Reader Response.............................................................................................................................................................................. 200
Product Identification System.............................................................................................................................................................201
TO OUR VALUED CUSTOMERS
It is our intention to provide our valued customers with the best documentation possible to ensure successful use of your Microchip
products. To this end, we will continue to improve our pu blications to better s uit your needs. Our publications will be refined and
enhanced as new volumes and updates are introduced.
If you have any questions or c omm ents regarding t his publication, p lease c ontact the M arket ing Co mmunications Department via
E-mail at docerrors@microchip.com or fax the Reader Response Form in the back of this data sheet to (480) 792-4150. We
welcome your feedback.
Most Current Data Sheet
To obtain the most up-to-date version of this data sheet, please register at our Worldwide Web site at:
http://www.microchip.com
You can determine the version of a data sheet by examining its literature number found on the bottom outside corner of any page.
The last character of the literature number is the version number, (e.g., DS30000A is version A of document DS30000).
Errata
An errata sheet, describing minor operational differences from the data sheet and recommended workarounds, may exist for current
devices. As device/documentation issues become known to us, we will publish an errata sheet. The errata will specify the revision
of silicon and revision of document to which it applies.
To determine if an errata sheet exists for a particular device, please check with one of the following:
• Microchip’s Worldwide Web site; http://www.microchip.com
• Your local Microchip sales office (see last page)
When contacting a sales office, please specify which device, revision of silicon and data sheet (include literature number) you are
using.
Customer Notification System
Register on our web site at www.microchip.com to receive the most current information on all of our products.
DS70118G-page 4 © 2006 Microchip Technology Inc.
Page 7

dsPIC30F2010
1.0 DEVICE OVERVIEW
Note: This data sheet summarizes features of this g roup
of dsPIC30F devices and is not intended to be a complete
reference source. For more information on the CPU,
peripherals, register descriptions and general device
functionality, refer to the “dsPIC30F Family Reference
Manual” (DS70046). For more informat ion on the device
instruction set and programming, refer to the “dsPIC30F/
33F Programmer’s Reference Manual” (DS70157).
This document contains device specific information for
the dsPIC30F2010 device. The dsPIC30F devices
contain extensive Digital Signal Processor (DSP) functionality within a high-performance 16-bit mic rocontroller
(MCU) architecture. Figure 1-1 shows a device block
diagram for the dsPIC30F2010 device.
© 2006 Microchip Technology Inc. DS70118G-page 5
Page 8

dsPIC30F2010
4
FIGURE 1-1: dsPIC30F2010 BL OC K DIAGR AM
Interrupt
Controller
24
Address Latch
Program Memory
(12 Kbytes)
Data EEPROM
(1 Kbyte)
Data Latch
Instruction
Decode &
24
24
16
Control
PSV & Table
Data Access
Control Block
Control
16
24
Y Data Bus
8
16
PCH PCL
PCU
Program Counter
Stack
Logic
Loop
Control
Logic
ROM Latch
IR
Decode
16
16
Y Data
RAM
(256 bytes)
Address
Latch
Y AGU
Effective Address
16
X Data Bus
16
Data LatchData Latch
X Data
(256 bytes)
Address
16
16
X RAGU
X WAGU
16
16 x 16
W Reg Array
16
16
RAM
Latch
16
16
EMUD3/AN0/VREF+/CN2/RB0
EMUC3/AN1/VREF-/CN3/RB1
AN2/SS1/LVDIN/CN4/RB2
AN3/INDX/CN5/RB3
AN4/QEA/IC7/CN6/RB4
AN5/QEB/IC8/CN7/RB5
PORTB
16
PORTC
EMUD1/SOSCI/T2CK/U1A T X/CN1/RC1 3
EMUC1/SOSCO/T1CK/U1ARX/CN0/RC1
OSC2/CLKO/RC15
Control Signals
to Various Blocks
OSC1/CLKI
Generation
Timing
MCLR
10-bit ADC
Timers
Power-up
Timer
Oscillator
Start-up Timer
POR/BOR
Reset
Watchdog
Timer
Input
Capture
Module
QEI
DSP
Engine
16
Output
Compare
Module
Motor Control
PWM
Divide
Unit
ALU<16>
16
UART1SPI1
I2C™
PORTD
PORTE
PORTF
EMUC2/OC1/IC1/INT1/RD0
EMUD2/OC2/IC2/INT2/RD1
PWM1L/RE0
PWM1H/RE1
PWM2L/RE2
PWM2H/RE3
PWM3L/RE4
PWM3H/RE5
/INT0/SCK1/OCFA/RE8
FLTA
PGC/EMUC/U1RX/SDI1/SDA/RF2
PGD/EMUD/U1TX/SDO1/SCL/RF3
DS70118G-page 6 © 2006 Microchip Technology Inc.
Page 9
dsPIC30F2010
Table 1-1 provides a brief description of device I/O
pinouts and the functions that may be multiplexed to a
port pin. Multiple functions may exist on one port pin.
When multiplexing occurs, the peripheral module’s
functional requirements may force an override of the
data direction of the port pin.
TABLE 1-1: PINOUT I/O DESCRIPTIONS
Pin Name
AN0-AN5 I Analog Analog input channels.
DD P P Positive supply for analog module.
AV
AVSS P P Ground reference for analog module.
CLKI
CLKO
CN0-CN7 I ST Input change notification inputs.
EMUD
EMUC
EMUD1
EMUC1
EMUD2
EMUC2
EMUD3
EMUC3
IC1, IC2, IC7,
IC8
INDX
QEA
QEB
INT0
INT1
INT2
FLTA
PWM1L
PWM1H
PWM2L
PWM2H
PWM3L
PWM3H
MCLR
OCFA
OC1-OC2
OSC1
OSC2
Legend: CMOS = CMOS compatible input or output Analog = Analog in put
Pin
Type
I
O
I/O
I/O
I/O
I/O
I/O
I/O
I/O
I/O
I ST Capture inputs. The dsPIC30F2010 has 4 capture inputs. The inputs are
I
I
I
I
I
I
I
O
O
O
O
O
O
I/P ST Master Clear (Reset) input or programming voltage input. This pin is an active-
I
O
I
I/O
ST = Schmitt Trigger input with CMOS levels O = Output
I = Input P = Power
Buffer
Type
ST/CMOS—External clock source input. Always associated with OSC1 pin function.
Oscillator crystal output. Connects to crystal or resonator in Crystal
Oscillator mode. Optionally functions as CLKO in RC and EC modes. Always
associated with OSC2 pin function.
Can be software programmed for internal weak pull-ups on all inputs.
ST
ST
ST
ST
ST
ST
ST
ST
ST
ST
ST
ST
ST
ST
ST
—
—
—
—
—
—
ST
—
ST/CMOS—Oscillator crystal input. ST buffer when configured in RC mode; CMOS
ICD Primary Communication Channel data input/output pin.
ICD Primary Communication Channel clock input/output pin.
ICD Secondary Communication Channel data input/output pin.
ICD Secondary Communication Channel clock input/output pin.
ICD Tertiary Communication Channel data input/output pin.
ICD Tertiary Communication Channel clock input/output pin.
ICD Quaternary Communication Channel data input/output pin.
ICD Quaternary Communication Channel clock input/output pin.
numbered for consistency with the inputs on larger device variants.
Quadrature Encoder Index Pulse inpu t.
Quadrature Encoder Phase A input in QEI mode.
Auxiliary Timer External Clock/Gate input in Timer mode.
Quadrature Encoder Phase A input in QEI mode.
Auxiliary Timer External Clock/Gate input in Timer mode.
External interrupt 0
External interrupt 1
External interrupt 2
PWM Fault A input
PWM 1 Low output
PWM 1 High output
PWM 2 Low output
PWM 2 High output
PWM 3 Low output
PWM 3 High output
low Reset to the device.
Compare Fault A input (for Compare channels 1, 2, 3 and 4).
Compare outputs.
otherwise.
Oscillator crystal output. Connects to crystal or resonator in Crystal Oscillator
mode. Optionally functions as CLKO in RC and EC modes.
Description
© 2006 Microchip Technology Inc. DS70118G-page 7
Page 10
dsPIC30F2010
TABLE 1-1: PINOUT I/O DESCRIPTIONS (CONTINUED)
Pin Name
PGD
PGC
RB0-RB5 I/O ST PORTB is a bidirectional I/O port.
RC13-RC14 I/O ST PORTC is a bidirectional I/O port.
RD0-RD1 I/O ST PORTD is a bidirectional I/O por t.
RE0-RE5,
RE8
RF2, RF3 I/O ST PORTF is a bidirectional I/O port.
SCK1
SDI1
SDO1
SS1
SCL
SDA
SOSCO
SOSCI
T1CK
T2CK
U1RX
U1TX
U1ARX
U1ATX
VDD P — Positive supply for logic and I/O pins.
SS P — Ground reference for logic and I/O pins.
V
VREF+ I Analog Analog Voltage Reference (High) input.
VREF- I Analog Analog Voltage Reference (Low) input.
Legend: CMOS = CMOS compatible input or output Analog = Analog in put
Pin
Type
I/O
I
I/O ST PORTE is a bidirectional I/O port.
I/O
I
O
I
I/O
I/O
O
I
I
I
I
O
I
O
ST = Schmitt Trigger input with CMOS levels O = Output
I = Input P = Power
Buffer
Type
ST
ST
ST
ST
—
ST
ST
ST
—
ST/CMOS
ST
ST
ST
—
ST
—
Description
In-Circuit Serial P rogramming™ data input/output pin .
In-Circuit Serial Programming clock input pi n.
Synchronous serial clock input/output for SPI #1.
SPI #1 Data In.
SPI #1 Data Out.
SPI #1 Slave Synchronization.
2
Synchronous serial clock input/output for I
Synchronous serial data input/output for I
32 kHz low-power oscillator crystal output.
32 kHz low-power oscillator crystal input. ST buffer when configured in RC
mode; CMOS otherwise.
Timer1 external clock input.
Timer2 external clock input.
UART1 Receive.
UART1 Transmit.
UART1 Alternate Receive.
UART1 Alternate Transmit.
2
C™.
C.
DS70118G-page 8 © 2006 Microchip Technology Inc.
Page 11

dsPIC30F2010
2.0 CPU ARCHITECTURE OVERVIEW
Note: This data sheet summarizes features of this g roup
of dsPIC30F devices and is not intended to be a complete
reference source. For more information on the CPU,
peripherals, register descriptions and general device
functionality, refer to the “dsPIC30F Family Reference
Manual” (DS70046). For more informat ion on the device
instruction set and programming, refer to the “dsPIC30F/
33F Programmer’s Reference Manual” (DS70157).
This document provides a summary of the
dsPIC30F2010 CPU and peripheral function. For a
complete description of this functionality, please refer
to the “dsPIC30F Family Reference Manual”
(DS70046).
2.1 Core Overview
The core has a 24-bit instruction word. The Program
Counter (PC) is 23 bits wide with the Least Significant
bit (LSb) always clear (see Section 3.1 “Program
Address Space ”), and the Most Significant bit (MSb)
is ignored during no rmal program exec ution, exce pt for
certain specialized instructions. Thus, the PC can
address up to 4M instruction words of user program
space. An instruction prefetch mechanism is used to
help maintain throughput. Program loop constructs,
free from loop count management overhead, are supported usin g the DO and REPEAT instructions, both of
which are interruptible at any point.
The working register array consists of 16x16-bit registers, each of which can act as data, address or offset
registers. One working register (W15) operates as a
software Stack Pointer for interrupts and calls.
The data space is 64 Kbytes (32K words) and is split
into two blocks, referred to as X and Y data memory.
Each block has its own independent Address Generation Unit (AGU). Most instructions operate solely
through the X memory AGU, which provides the
appearance of a single unified data space. The
Multiply-Accu mulate (MAC) class of dual s ource DSP
instructions operate through both the X and Y AGUs,
splitting the data address space into two parts (see
Section 3.2 “Data Address Space”). The X and Y
data space boundary is device specific and cannot be
altered by the user . Each dat a word consis ts of 2 bytes,
and most instruct ions can address data eith er as words
or bytes.
There are two methods of accessing data stored in
program memory:
• The upper 32 Kbytes of data sp ace memory can b e
mapped into the lower half (user space) of program
space at any 16K program word bound ary, defined
by the 8-bit Program Space Visibility Page
(PSVP AG) register. This le ts any instruction access
program space as if it were data space , with a lim itation that the access requires an additional cycle.
Moreover, only the lower 16 bits of eac h instruction
word can be accessed using this method.
• Linear indirect access of 32K word pages within
program space is als o possibl e using any work ing
register, via table read and write instructions.
Table read and write instructions can be used to
access all 24 bits of an instruction word.
Overhead-free circular buffers (Modulo Addressing)
are supported in both X and Y address spaces. This is
primarily intended to remove the loop overhead for
DSP algorithms.
The X AGU also supports Bit-Reversed Addressing on
destination ef fective addres ses, to greatly simplify inp ut
or output data reordering for radix-2 FFT algorithms.
Refer to Section 4.0 “Address Generator Units” for
details on Modulo and Bit-Reversed Addressing.
The core supports In here nt (n o op era nd), Relative, Literal, Memory Direct, Register Direct, Register Indirect,
Register Offset and Literal Offset Addressing modes.
Instructions are a ssociated w ith pred efined Addr essing
modes, depending upon their functional requirements.
For most i ns tru c ti o ns , the c or e i s c apa bl e of e xe c ut i ng
a data (or program data) memory read, a working register (data) read, a data memory write and a program
(instruction) memory read per instruction cycle. As a
result, 3-operand instructions are supported, allowing
C = A + B operations to be executed in a single cycle.
A DSP engine has been included to significantly
enhance the core arithmetic capability and throughput.
It features a high-speed 17-bit by 17-bit multiplier, a
40-bit ALU, two 40-bit saturating accumulators and a
40-bit bidirectional b arre l s hi fter. Data in the accumulator or any wor kin g regi ste r can be sh ifted up to 15 bi ts
right or 16 bits left in a single cycle. The DSP instructions operate seamles sly with all other in struct ion s and
have been desi gned for o ptimal re al-time p erformanc e.
The MAC class of instructions can concurrently fetch
two data operands from memory, while multiplying two
W registers. To enable this concurrent fetching of data
operands, the data space has been split for these
instructions and linear for all others. This has been
achieved in a transparent and flexible manner, by
dedicating certain working registers to each address
space for the MAC class of instructions.
The core does not support a multi-stage instruction
pipeline. However, a single stage instruction prefetch
mechanism is used, which accesses and partially
decodes instructions a cycle ahead of execution, in
order to maximize available execution time. Most
instructions execute in a single cycle, with certain
exceptions.
The core features a vectored exception processing
structure for traps and interrupts, with 62 independent
vectors. The exceptions consist of up to 8 traps (of
which 4 are reserved ) an d 54 int errup ts. Each interrupt
is prioritized based on a us er-assigned priority betwee n
1 and 7 (1 being the lowest priority and 7 being the
highest) in conjunction with a predetermined ‘natural
order’. Traps have fi xed prio rities, ranging from 8 to 15.
© 2006 Microchip Technology Inc. DS70118G-page 9
Page 12

dsPIC30F2010
2.2 Programmer’s Model
The programmer’s model is shown in Figure 2-1 and
consists of 16x16-bit working registers (W0 through
W15), 2x40-bit accumulators (ACCA and ACCB),
STATUS Register (SR), Data Table Page register
(TBLPAG), Program Space Visibility Page register
(PSVPAG), DO and REPEAT registers (DOSTART,
DOEND, DCOUNT and RCOUNT) and Program
Counter (PC). The working registers can act as data,
address or offset registers. All registers are memory
mapped. W0 acts as the W register for file register
addressing.
Some of these registers have a shadow register associated with each of them, as shown in Figure 2-1. The
shadow register is used as a temp orary holding reg ister
and can transfer it s con ten ts to or from its host reg is ter
upon the occurrence of an event. None of the shadow
registers are accessible directly. The following rules
apply for transfer of registers into and out of shadows.
• PUSH.S and POP.S
W0, W1, W2, W3, SR (DC, N, OV, Z and C bits
only) are transferred.
• DO instruction
DOSTART, DOEND, DCOUNT shadows are
pushed on loop start, and popped on loop end.
When a byte operation is performed on a working register , o nly th e L eas t S ign ifi can t By te of t he target register is affected. However, a benefit of memory mapped
working registers is that both the Least and Most Significant B ytes can be manipulate d through byte wide
data memory space accesses.
2.2.1 SOFTWARE STACK POINTER/ FRAME POINTER
The dsPIC® DSC devices contain a software stack.
W15 is the dedicated software Stack Pointer (SP), and
will be automatically modified by exception processing
and subroutine ca lls and return s. However , W15 can be
referenced by any instruction in the same manner as all
other W registers. This simplifies the reading, writing
and manipulation of the Stack Pointer (e.g., creating
stack frames).
Note: In order to protect against misaligned
stack accesses, W15<0> is always clear.
W15 is initialized to 0x0800 during a Reset. The user
may reprogram the SP during initialization to any
location within data space.
W14 has been dedicated as a Stack Frame Pointer as
defined by the LNK and ULNK instructions. However,
W14 can be referenced by any instruction in the same
manner as all other W registers.
2.2.2 STATUS REGISTER
The dsPIC DSC core has a 16-b it STATUS Register
(SR), the LSB of which is referred to as the SR Low
Byte (SRL) and the MSB as the SR High Byte (SRH).
See Figure 2-1 for SR layout.
SRL contains all the MCU ALU operation status flags
(including the Z bit), as wel l as the CPU Inter rupt Pri ority Level status bits, IPL<2:0>, and the REPEAT active
status bit, RA. During exception processing, SRL is
concatenated with the MSB of the PC to form a
complete word value which is then stacked.
The upper byte of the STATUS register contains the
DSP adder/subtracter status bits, the DO Loop Active
bit (DA) and the Digit Carry (DC) status bit.
2.2.3 PROGRAM COUNTER
The Program Counter is 23 bi ts wide. Bit 0 is a lways
clear. Therefore, the PC can address up to 4M
instruction words.
DS70118G-page 10 © 2006 Microchip Technology Inc.
Page 13
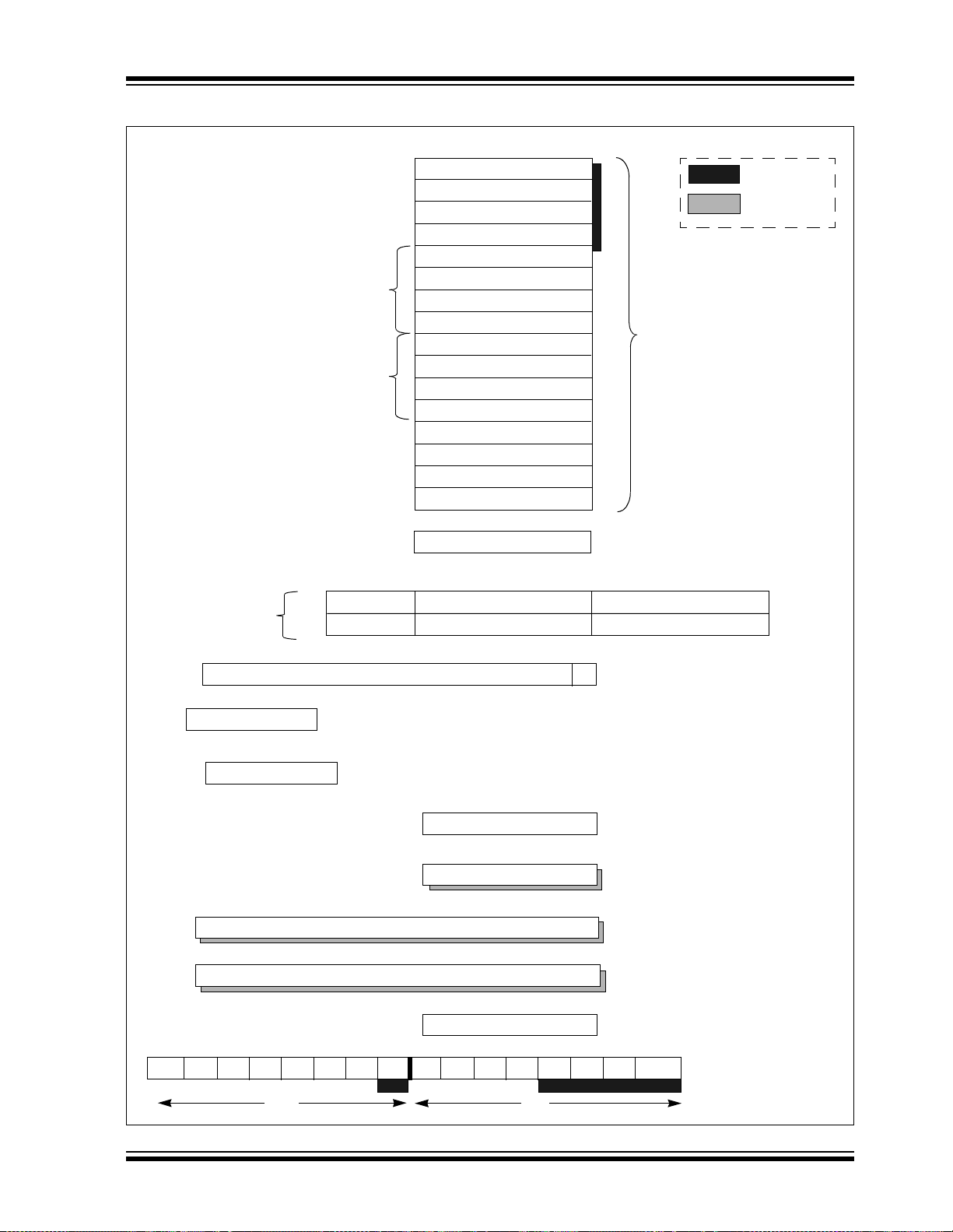
FIGURE 2-1: PROGRAMMER’S MODEL
DSP Operand
Registers
DSP Address
Registers
W0/WREG
W1
W2
W3
W4
W5
W6
W7
W8
W9
W10
W11
W12/DSP Offset
W13/DSP Write-Back
W14/Frame Pointer
W15/Stack Pointer
dsPIC30F2010
D0D15
PUSH.S Shadow
DO Shadow
Legend
Working Registers
DSP
Accumulators
PC22
7
22
22
TABPAG
TBLPAG
7
PSVPAG
PSVPAG
AD39 AD0AD31
ACCA
ACCB
0
Data Table Page Address
0
SPLIM Stack Pointer Limit Register
Program Space Visibility Page Address
15
RCOUNT
15
DCOUNT
DOSTART
DOEND
PC0
AD15
Program Counter
0
0
REPEAT Loop Counter
0
DO Loop Counter
0
DO Loop Start Address
DO Loop End Address
15
CORCON
OA OB SA SB
© 2006 Microchip Technology Inc. DS70118G-page 11
OAB SAB
SRH
DA DC
IPL2 IPL1
RA
IPL0 OV
SRL
N
0
Core Configuration Register
C
Z
STATUS Register
Page 14
dsPIC30F2010
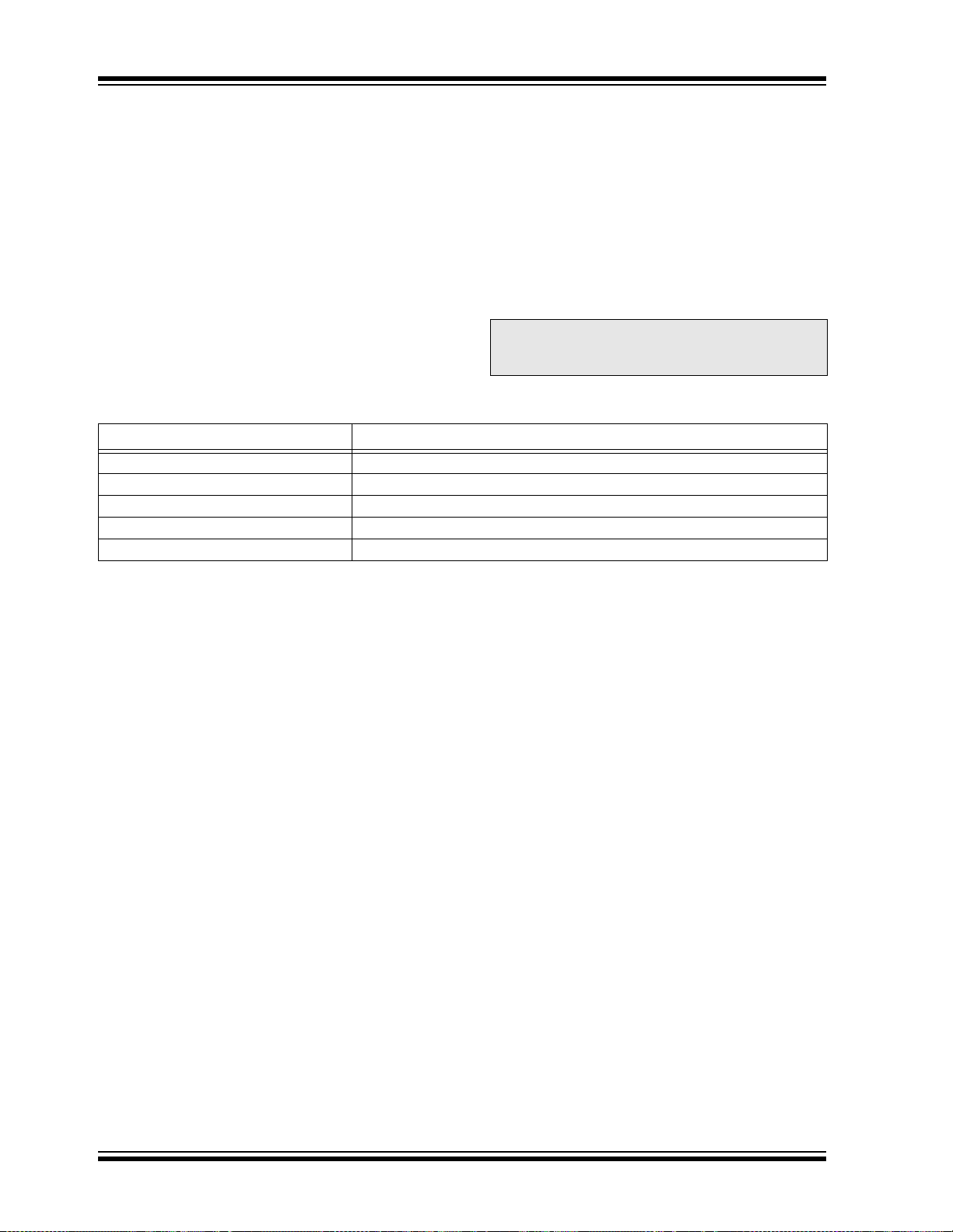
2.3 Divide Support
The dsPIC DSC devices feature a 16/16-bit signed
fractional divide ope rati on , as w ell as 32/16-bit and 16/
16-bit signed an d unsigned intege r divide operati ons, in
the form of single instruction iterative divides. The following instructions and data sizes are supported:
1. DIVF – 16/16 signed fractional divide
2. DIV.sd – 32/16 signed divide
3. DIV.ud – 32/16 unsigned divide
4. DIV.sw – 16/16 signed divide
5. DIV.uw – 16/16 unsigned divide
The 16/16 divides are similar to the 32/16 (same number
of iterations), but the dividend is either zero-extended or
sign-extended during the first iteration.
The divide instructions must be executed within a
REPEAT loop. Any other form of exec ution (e.g. a serie s
of discrete divide instruc tions) w ill not function c orrectly
because the instruction flow depends on RCOUNT.
The divide instru ction does not automat icall y set up the
RCOUNT value, and it must, therefore, be explicitly
and correctly specified in the REPEAT instruction, as
shown in Table 2-1 (REPEAT will execute the target
instruction {operand value + 1} times). The REPEAT
loop count must be set up for 18 iterati ons of the DIV/
DIVF instruction. Thus, a complete divide operation
requires 19 cycles.
Note: The Divide flow is interruptible. However,
the user needs to save the context as
appropriate.
TABLE 2-1: DIVIDE INSTRUCTIONS
Instruction Function
DIVF Signed fractional divide: Wm/Wn → W0; Rem → W1
DIV.sd Signed divide: (Wm + 1:Wm)/Wn → W0; Rem → W1
DIV.ud Unsigned divide: (Wm + 1:Wm)/Wn → W0; Rem → W1
DIV.sw (or DIV.s) Signed divide: Wm/Wn → W0; Rem → W1
DIV.uw (or DIV.u) Unsigned divide: Wm/Wn → W0; Rem → W1
DS70118G-page 12 © 2006 Microchip Technology Inc.
Page 15

dsPIC30F2010
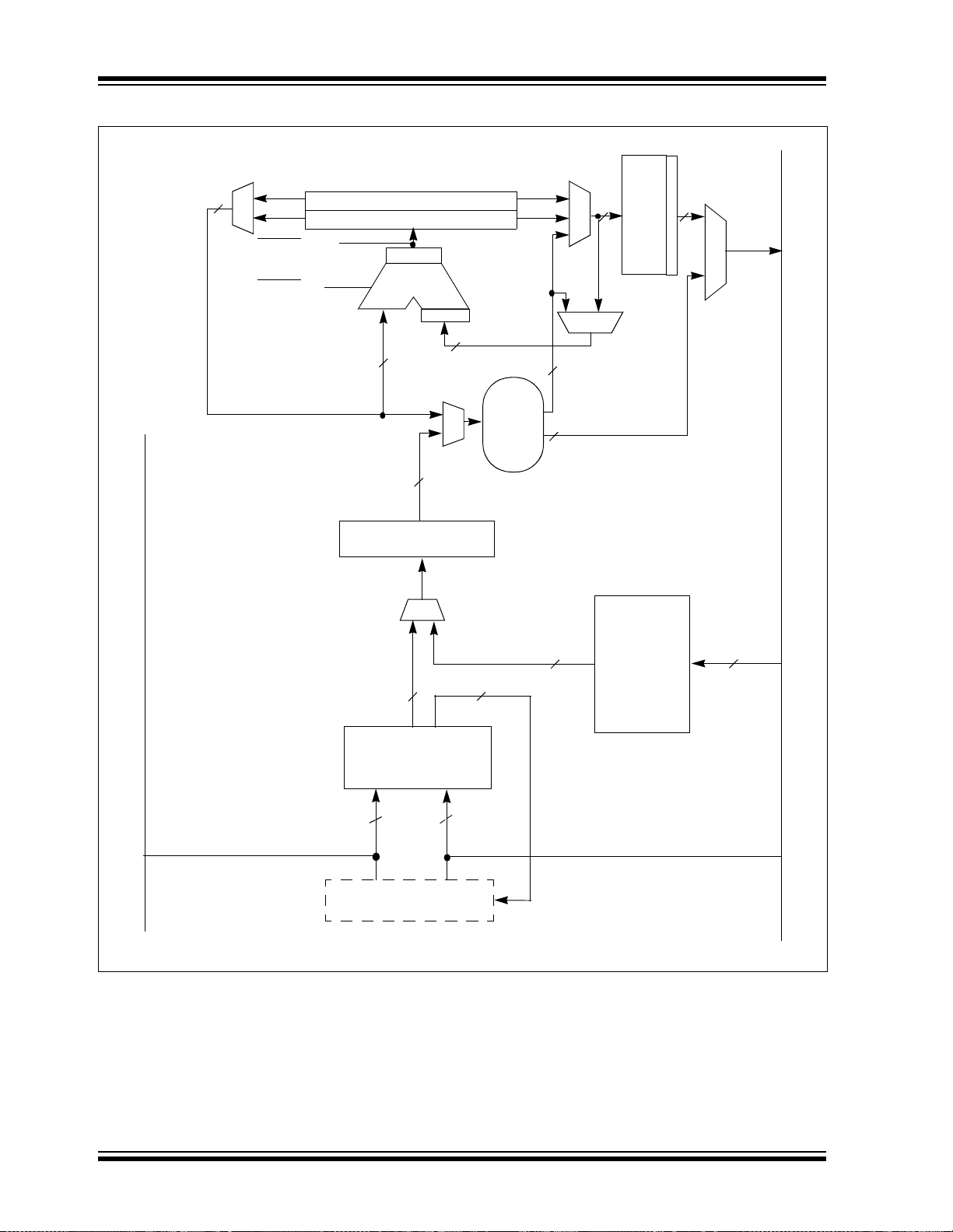
2.4 DSP Engine
The DSP engine consists of a high-speed 17-bit x
17-bit multiplier , a barrel s hifter , and a 40-bit adde r/subtracter (with two target accumulators, round and
saturation logic).
The DSP engine also has the capability to perform inherent accumulator-to-accumulator operations, which
require no additional data. These instructions are ADD,
SUB and NEG.
The DSP engine has various options selected through
various bits in the CPU Core Configuration Register
(CORCON), as listed below:
1. Fractional or integer DSP multiply (IF).
2. Signed or unsigned DSP multiply (US).
3. Conventional or convergent rounding (RND).
4. Automatic saturation on/off for ACCA (SATA).
5. Automatic saturation on/off for ACCB (SATB).
6. Automatic saturation on/off for writes to data
memory (SATDW).
7. Accumulator Saturation mode selection
(ACCSAT).
Note: For CORCON layout, see Table 3-3.
A block diagram of the DSP engine is shown in
Figure 2-2.
TABLE 2-2: DSP INSTRUCTION SUMMARY
Instruction Algebraic Operation ACC WB?
CLR A = 0 Yes
ED A = (x – y)
EDAC A = A + (x – y)
MAC A = A + (x * y) Yes
MAC A = A + x
MOVSAC No change in A Yes
MPY A = x * y No
MPY.N A = – x * y No
MSC A = A – x * y Yes
2
2
2
No
No
No
© 2006 Microchip Technology Inc. DS70118G-page 13
Page 16
dsPIC30F2010
FIGURE 2-2: DSP ENGINE BLOCK DI AGR AM
40
Carry/Borrow Out
Carry/Borrow In
40-bit Accumulator A
40-bit Accumulator B
Saturate
Adder
Negate
40
Round
Logic
S
a
16
t
u
r
a
t
e
40
40
Barrel
Shifter
32
32
40
16
X Data Bus
16
Zero Backfill
40
Sign-Extend
Y Data Bus
33
17-bit
Multiplier/Scaler
16
To/From W Array
DS70118G-page 14 © 2006 Microchip Technology Inc.
16
Page 17

dsPIC30F2010
2.4.1 MULTIPLIER
The 17x17-bit multiplier is capable of signed or
unsigned operati on and can mul tiplex i ts ou tput usi ng a
scaler to support either 1.31 fractional (Q31) or 32-bit
integer results. Unsigned operands are zero-extended
into the 17th bit of the multiplier input value. Signed
operands are sign-exten ded into the 17th bit of the mu ltiplier input value. The output of t he 17x17-bit multip lier/
scaler is a 33-bit value, which is sign-extended to 40
bits. Intege r data is inherently rep resented as a signed
two’s complement value, where the MSB is defined as
a sign bit. Generally speaking, the range of an N-bit
two’s complement integer is -2
bit integer, the data range is -32 76 8 (0x 800 0) to 3276 7
(0x7FFF), including 0. For a 32-bit integer, the data
range is -2,147,483,648 (0x8000 0000) to
2,147,483,645 (0x7FFF FFFF ).
When the multiplier is configured for fractional multiplication, the data is represented as a two’s complement
fraction, where the M SB is defined as a sign b it and the
radix point is impl ied to lie just after the sign b it (QX format). The range of an N-bit two’s complement fraction
with this implied radix point is -1.0 to (1-2
16-bit fraction, the Q15 data range is -1.0 (0x8000) to
0.999969482 (0x7FFF), including ‘0’ and has a precision of 3.01518x1 0
tiply operation generates a 1.31 product, which has a
precision of 4.65661x10
The same multiplier is used to support the MCU multiply instructions, which include integer 16-bit signed,
unsigned and mixed sign multiplies.
The MUL instruction may be directed to use byte or
word-sized operands. Byt e operands will direct a 16-bit
result, and word operands will direct a 32-bit result to
the specified register(s) in the W array.
-5
. In Fractional mode, a 16x16 mu l-
-10
N-1
N-1
to 2
– 1. For a 16-
1-N
). For a
.
2.4.2 DATA ACCUMULATORS AND ADDER/SUBTRACTER
The data accumulator consists of a 40-bit adder/subtracter with automatic si gn extension logic. It can selec t
one of two accumulators (A or B) as its preaccumulation source and post-accumulation destination. For the ADD and LAC instructions, the data to be
accumulated or load ed ca n be optio nally sca led v ia th e
barrel shifter, prior to accumulation.
2.4.2.1 Adder/Subtracter, Overflow and
Saturation
The adder/subtracter is a 40-bit adder with an optional
zero input into one side and either true or complement
data into the other input. In the case of addition, the
carry/borrow
true data (not complemented), whereas in the case of
subtraction, the carry/bo rrow
other input is complemented. The adder/subtracter
generates overflow status bits SA/SB and OA/OB,
which are latched and reflected in the STATUS
Register.
• Overflow from bit 39: this is a catastrophic
overflow in which the sign of the accumulator is
destroyed.
• Overflow into guard bits 32 through 39: this is a
recoverable overflow. This bit is set whenever all
the guard bits are not identical to each other.
The adder has an additional saturation block which
controls accumulator data saturation, if selected. It
uses the result of the adder, the overflow status bits
described above, and the SATA/B (CORCON<7:6>)
and ACCSAT (CORCON<4>) mode control bits to
determine when and to what value to saturate.
Six STATUS register bits have been provided to
support saturation and overflow; they are:
1. OA:
ACCA overflowed into guard bits
2. OB:
ACCB overflowed into guard bits
3. SA:
ACCA saturated (bit 31 overflow and sa turation)
or
ACCA overflowed into guard bits and saturated
(bit 39 overflow and s aturation)
4. SB:
ACCB saturated (bit 31 overflow and sa turation)
or
ACCB overflowed into guard bits and saturated
(bit 39 overflow and s aturation)
5. OAB:
Logical OR of OA and OB
6. SAB:
Logical OR of SA and SB
The OA and OB bits are modified each time data
passes through the adder/subtracter. When set, they
indicate that the most recent operation has overflowed
into the accumulator guard bits (bits 32 through 39).
The OA and OB bits can also optionally generate an
arithmetic warning trap when set and the corresponding overflow trap flag enable bit (OVATE, OVBTE) in
the INTCON1 register (refer to Section 5.0 “Inter-
rupts”) is set. This allows the user to take immediate
action, for example, to correct system gain.
input is active high and the other input is
input is active low and the
© 2006 Microchip Technology Inc. DS70118G-page 15
Page 18

dsPIC30F2010
The SA and SB bits are modified each ti me data pass es
through the adder/subtracter, but can only be cleared by
the user. When set, they indicate that the accumulator
has overflowed its maximum range (bit 31 for 32-bit saturation, or bit 39 for 40-bit saturation) and will be saturated (if saturation is enabled). When saturation is not
enabled, SA and SB default to bit 39 overflow and thus
indicate that a catastrophic overflow has occurred. If the
COVTE bit in the INTCON1 register is set, SA and SB
bits will generate an arithmetic warning trap when
saturation is disabled.
The overflow and saturation status bits can optionally
be viewed in the S tat us Register (SR) as the logical OR
of OA and OB (i n bit OAB) , and the lo gical OR of SA
and SB (in bit SAB). This allows programmers to check
one bit in the STATUS register to determine if either
accumulator has overflowed, or one bit to determine if
either accumulator has s aturated. T his w ould be us eful
for complex number arithmetic which typically uses
both the accumulators.
The device supports three Saturation and Overflow
modes.
1. Bit 39 Overflow and Saturation:
When bit 39 overflow and saturation occurs, the
saturation logic loads the maximally positive 9.31
(0x7FFFFFFFFF) or maximally negative 9.31
value (0x8000000000) into the target accumulator. The SA or SB bit is set and remains set until
cleared by the user. This is referred to as ‘super
saturation’ and provides protection against erroneous data or unexpected algorithm problems
(e.g., gain calculations).
2. Bit 31 Overflow and Saturation:
When bit 31 overflow and saturation occurs, the
saturation logic then loads the maximally positive
1.31 value (0x007FFFFFFF) or maximally negative 1.31 value (0x0080000000) into the target
accumulator . The SA or SB bit is set and rem ains
set until cleared by the user . When this Saturation
mode is in effect, the guard bits are not used (so
the OA, OB or OAB bits are never set).
3. Bit 39 Catastrophic Overflow
The bit 39 overflow status bit from the adder is
used to set the SA or SB bit, which remain set
until cleared by the user. No saturation operation
is performed and the accumulator is allowed to
overflow (destroying it s sign). If the C OVTE bit in
the INTCON1 register is set, a catastrophic
overflow can initiate a trap exception.
2.4.2.2 Accumulator ‘Write-Back’
The MAC class of instructions (with the exception of
MPY, MPY.N, ED and EDAC) can optionally write a
rounded version of the high word (bits 31 through 16)
of the accumulator that is not targeted by the instructio n
into data spac e memory. The write is performed across
the X bus into combined X and Y address space. The
following addressing modes are supported:
1. W13, Regi ster Direct:
The rounded contents of the non-target
accumulator are written into W13 as a 1.15
fraction.
2. [W13]+=2, Register Indirect with Post-Increment:
The rounded conten ts of the non- target accumulator are written into the address pointed to by
W13 as a 1.15 fraction. W13 is then
incremented by 2 (for a word write).
2.4.2.3 Round Logic
The round logic is a combinational block, which performs a conventional (biased) or convergent (unbiased)
round function during an accumulator write (store). The
Round mode is determined by the state of the RND bit
in the CORCON register. It generates a 16-bit, 1.15 data
value which is passed to the data space write saturation
logic. If rounding is not indicated by the instruction, a
truncated 1.15 data value is stored and the least
significant word (lsw) is simply discarded.
Conventional rounding takes bit 15 of the accumulator,
zero-extends it and ad ds it to the AC CxH w ord (bi t s 16
through 31 of the accumulato r). If the ACCxL word (bit s
0 through 15 of the accumulator) is between 0x8000
and 0xFFFF (0x8000 included), ACCxH is incremented. If ACCxL is between 0x0000 and 0x7FFF,
ACCxH is left unchanged. A consequence of this
algorithm is that over a succ ession of ran dom roundin g
operations, the value will tend to be biased slightly
positive.
Convergent (or unbiased) rounding operates in the
same manner as conventional rounding, except when
ACCxL equals 0x8000 . If this is the case, the Least Significant bit (bit 16 of the accumulator) of ACCxH is
examined. If it is ‘1’, ACCxH is incremented. If it is ‘0’,
ACCxH is not modified. Assuming that bit 16 is effectively random in nature, this scheme will remove any
rounding bias that may accumulate.
The SAC and SAC.R instructions store either a truncated (SAC) or rounded (SAC.R) version of the c ontents
of the target accumul ator to data mem ory , via the X bu s
(subject to data saturation, see Section 2.4.2.4 “Data
Space Write Saturation”). Note that for the MAC cl as s
of instructions, the accumulator write-back operation
will function in the s ame mann er , a ddressing co mbine d
MCU (X and Y) data space though the X bus. For this
class of instructions, the data is always subject to
rounding.
DS70118G-page 16 © 2006 Microchip Technology Inc.
Page 19

dsPIC30F2010
2.4.2.4 Data Space Write Saturation
In addition to adder/subtrac ter saturation, writes to dat a
space may also be saturated, but without affecting the
contents of the source accumulator. The data space
write saturation logic block accepts a 16-bit, 1.15 fractional value from the round logic block as its input,
together with overflow status from the original source
(accumulator) and the 16-bit round adder. These are
combined and used t o sele ct the a ppr opriate 1.15 fra ctional value as output to write to data space memory.
If the SATDW bit in the CORCON register is set, data
(after rounding or truncation) is tes te d for ove rflo w and
adjusted accordingly. For input data greater than
0x007FFF, data written to memory is fo rced to the ma ximum positi ve 1. 15 val ue, 0x 7FFF. For input data less
than 0xFF8000, da ta wr itten to me mory i s forced to th e
maximum negative 1.15 value, 0x8000. The Most Significant bit of the source (bit 39) is used to determine
the sign of the operand being tested.
If the SA TDW bi t in the CORCON regis ter is not set , the
input data is always passed through unmodified under
all conditions.
2.4.3 BARREL SHIFTER
The barrel shifter is capable of performing up to 15-bit
arithmetic or logic right shifts, or up to 16-bit left shifts
in a single c ycle. The sou rce can be ei ther of th e two
DSP accumulators or the X bus (to support multi-bit
shifts of register or memory data).
The shifter requi res a signed binary val ue to de term in e
both the magnitude (num ber of bits) and direction of the
shift operation. A positive value will shift the operand
right. A negative value will shift the operand left. A
value of 0 will not modify the operand.
The barrel shifter is 40 bits wide, thereby obtaining a
40-bit result for DSP shift operati ons and a 16- bit result
for MCU shift operations. Data from the X bus is presented to the barrel shifter between bit positions 16 to
31 for right shifts, and bit positio ns 0 to 15 for left shift s.
© 2006 Microchip Technology Inc. DS70118G-page 17
Page 20

dsPIC30F2010
NOTES:
DS70118G-page 18 © 2006 Microchip Technology Inc.
Page 21

dsPIC30F2010
3.0 MEMORY ORGANIZATION
Note: This data sheet summa rizes features o f this
group of dsPIC30 F devi ces and is not inte nded to be
a complete reference source. For more information
on the CPU, peripherals, register descriptions and
general device functionality, refer to the “dsPIC30F
Family Reference Manual” (DS70046). For more
information on the device instruction set and programming, refer to the “dsPIC30F/33F
Programmer’s Reference Manual” (DS70157).
3.1 Program Address Space
The program address space is 4M instruction words. It
is addressable by a 24-bit value from either the 23-bit
PC, table instruction Effective Address (EA), or data
space EA, when program space is mapped into data
space, as defined by Table 3-1. Note that the program
space address i s incr ement ed by two betw een suc cessive program words, in order to provide compatibility
with data space addressing.
User program space access is restricted to the lower
4M instruction word address range (0x000000 to
0x7FFFFE), for all acce sses other than TBLRD/TBLWT,
which use TBLPAG<7> to determine user or configuration space access. In Table 3-1, Read/Write instructions, bit 23 allows a ccess to the De vice ID, the User ID
and the Configuration bits. Otherwise, bit 23 is always
clear.
FIGURE 3-1:
Space
User Memory
PROGRAM SPACE MEMORY
MAP FOR dsPIC3 0F2010
Reset - GOTO Instruction
Reset - Target Address
Reserved
Ext. Osc. Fail Trap
Address Error Trap
Stack Error Trap
Arithmetic Warn. Trap
Reserved
Reserved
Reserved
Vector 0
Vector 1
Vector 52
Vector 53
Alternate Vector Table
User Flash
Program Memory
(4K instructions)
Reserved
(Read 0’s)
Data EEPROM
(1 Kbyte)
000000
000002
000004
000014
00007E
000080
0000FE
000100
001FFE
002000
7FFBFE
7FFC00
7FFFFE
800000
Vector Tables
Note: The address map shown in Figure 3-1 is
conceptual, and the actual memory configuration may vary across individual
devices depending on available memory.
Reserved
8005BE
Space
Configuration Memory
UNITID (32 instr.)
Reserved
Device Configuration
Registers
Reserved
DEVID (2)
8005C0
8005FE
800600
F7FFFE
F80000
F8000E
F80010
FEFFFE
FF0000
FFFFFE
© 2006 Microchip Technology Inc. DS70118G-page 19
Page 22

dsPIC30F2010
TABLE 3-1: PROGRAM SPACE ADDRESS CONSTRUCTION
Access Type
Access
Space
<23> <22:16> <15> <14:1> <0>
Instruction Access User 0 PC<22:1> 0
TBLRD/TBLWT User
TBLPAG<7:0> Data EA <15:0>
(TBLPAG<7> = 0)
TBLRD/TBLWT Configuration
TBLPAG<7:0> Data EA <15:0>
(TBLPAG<7> = 1)
Program Space Visibility User 0 PSVPAG<7:0> Data EA <14:0>
FIGURE 3-2: DATA ACCESS FROM PROGRAM SPACE ADDRESS GENERATION
23 bits
Using
Program
Counter
0
Program Space Address
0Program Counter
Select
Using
Program
Space
Visibility
Using
Table
Instruction
Note: Program Space Visibility cannot be used to access bits <23:16> of a word in program memory.
0
1/0
User/
Configuration
Space
Select
PSVPAG Reg
8 bits
TBLPA G Reg
8 bits
1
24-bit EA
EA
15 bits
EA
16 bits
Byte
Select
DS70118G-page 20 © 2006 Microchip Technology Inc.
Page 23
dsPIC30F2010
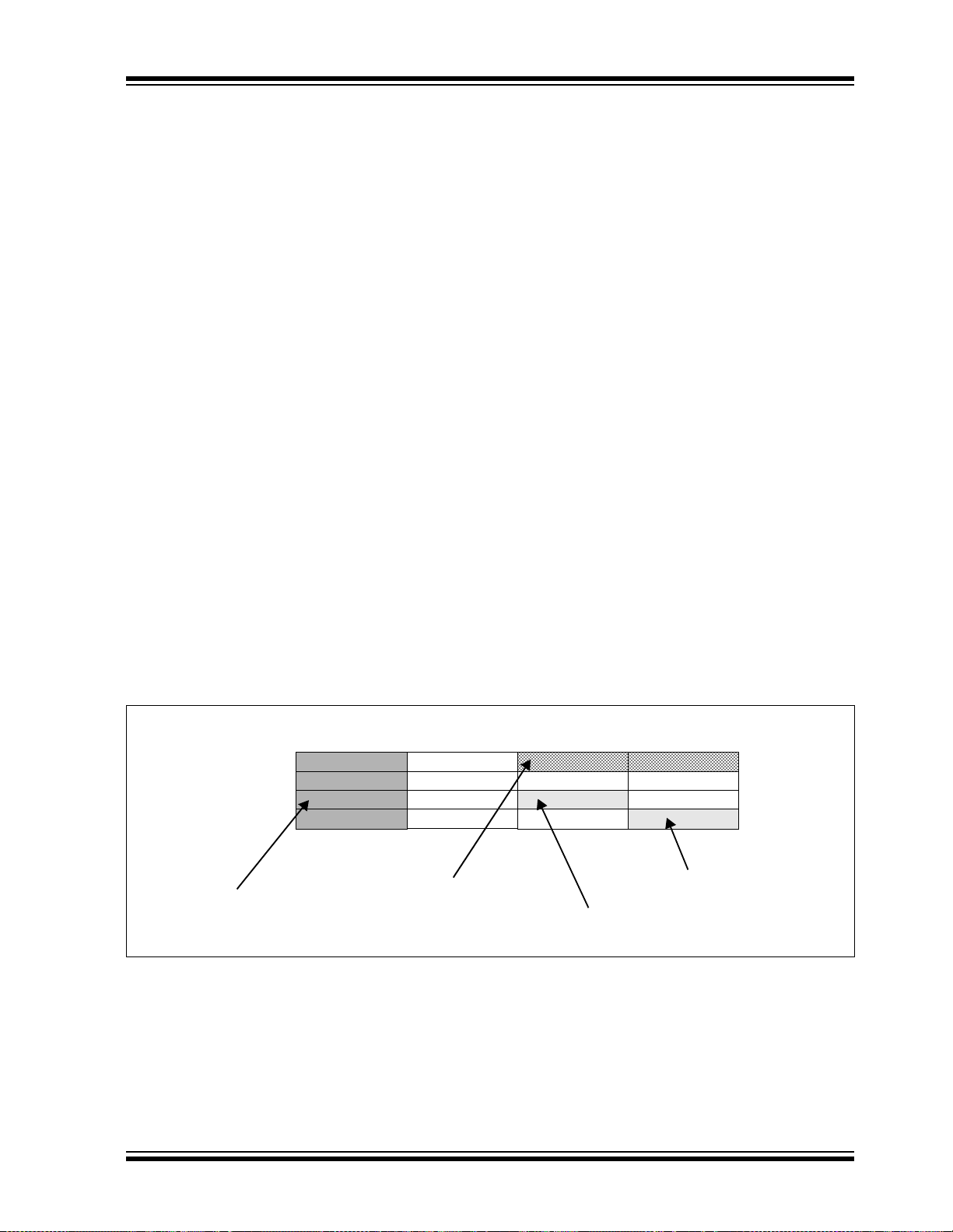
3.1.1 DATA ACCESS FROM PROGRAM MEMORY USING TABLE INSTRUCTIONS
This architecture fetc hes 24 -bi t w ide prog ram me mo ry.
Consequently, instructions are always aligned. However, as the architecture is modified Harvard, data can
also be present in program space.
There are two methods by which program space can
be accessed: via special table instructions, or through
the remapping of a 16 K word program space p age in to
the upper half o f da ta space (see Section 3.1.2 “Data
Access from Program Memory Using Program
Space Visibility”). The TBLRDL and TBLWTL instruc-
tions offer a direct method of reading or writing the lsw
of any address within program space, without going
through data sp ac e. The TBLRDH and TBLWTH instruc-
tions are the only method wh ereby the upp er 8 bits of a
program space word can be accessed as data.
The PC is incremented by two for each successive
24-bit program word. This allows program memory
addresses to directly map to data space addresses.
Program memory can thus be regarded as two 16-bit
word wide address sp ac es , res id ing sid e by si de, each
with the same address range. TBLRDL and TBLWTL
access the space which contains the least significant
data word, and TBLRDH a nd TBLWTH ac cess the sp ace
which contains the Most Significant data Byte.
Figure 3-2 shows h ow th e EA is created for table op erations and data space accesses (PSV = 1). Here,
P<23:0> refers to a program space word, whereas
D<15:0> refers to a data space word.
A set of T able Instruction s are provided to move byte or
word-sized data to and from program space.
1. TBLRDL: Table Re ad Low
Word: Read the least significant word of the
program address;
P<15:0> maps to D<15:0>.
Byte: Read one of the LSBs of the program
address;
P<7:0> maps to the destination byte when byte
select = 0;
P<15:8> maps to the d estination b yte when byte
select = 1.
2. TBLWTL: Table Write Lo w (ref er t o Section 6.0
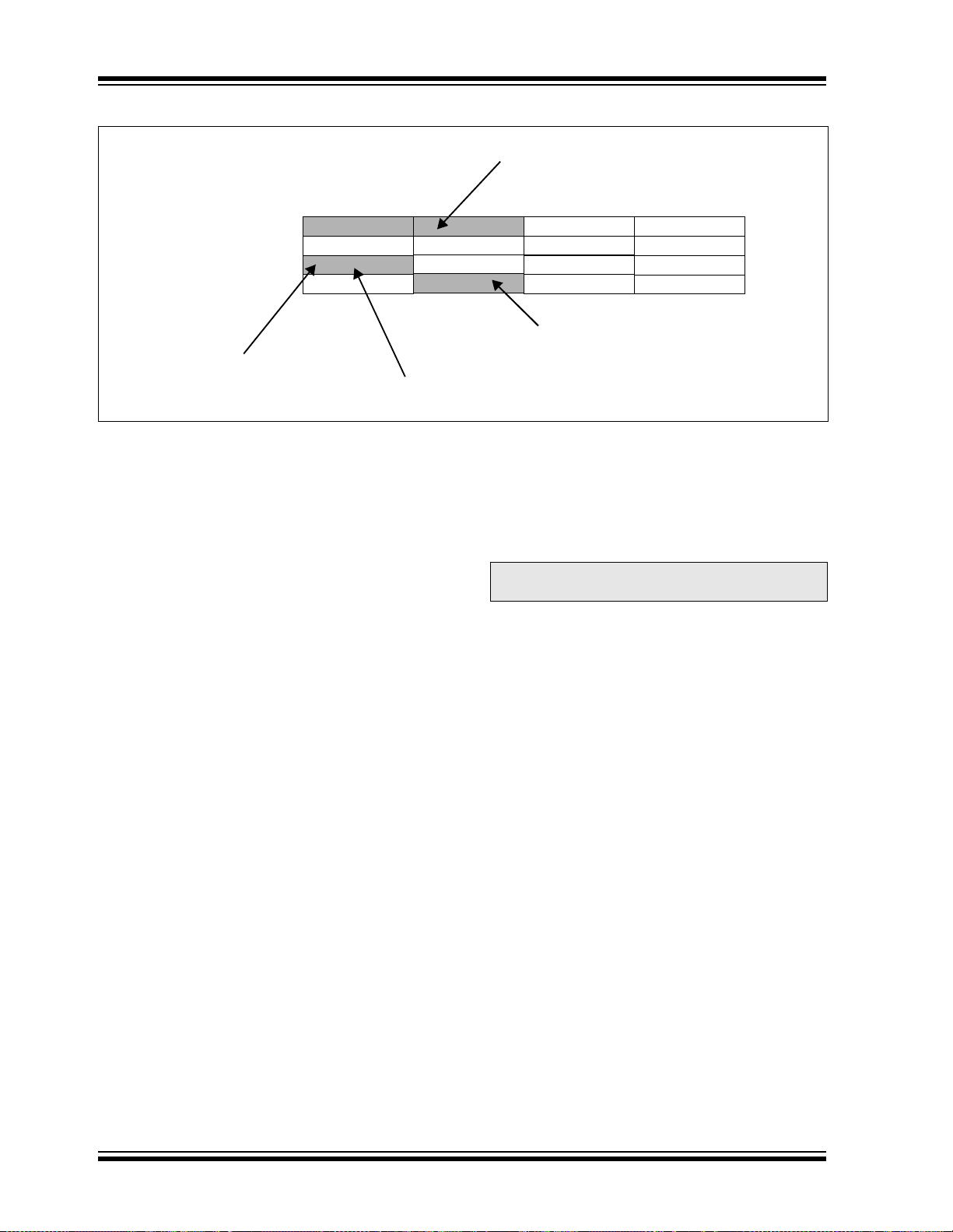
“Flash Program Memory” for details on Flash
Programming).
3. TBLRDH: Table Re ad High
Word: Read the most significant word of the
program address;
P<23:16> maps to D<7:0>; D<15:8> always
be = 0.
Byte: Read one of the MSBs of the program
address;
P<23:16> maps to the destination byte when
byte select = 0;
The destination byte will always be = 0 when
byte select = 1.
4. TBLWTH: Table Write High (ref er to Section 6.0
“Flash Program Memory” for details on Flash
Programming).
FIGURE 3-3: PROGRAM DATA T ABLE A CCESS (LEAST SI GNIFICANT WO RD)
PC Address
0x000000
0x000002
0x000004
0x000006
Program Memory
‘Phantom’ Byte
(Read as ‘0’).
00000000
00000000
00000000
00000000
23
TBLRDL.W
16
8
TBLRDL.B (Wn<0> = 0)
TBLRDL.B (Wn<0> = 1)
0
© 2006 Microchip Technology Inc. DS70118G-page 21
Page 24
dsPIC30F2010
FIGURE 3-4: PROGRAM DATA T ABLE ACCESS (M OST SI GNIFICANT BYTE)
TBLRDH.W
PC Address
0x000000
0x000002
0x000004
0x000006
Program Memory
‘Phantom’ Byte
(Read as ‘0’)
00000000
00000000
00000000
00000000
23
TBLRDH.B (Wn<0> = 1)
3.1.2 DATA ACCESS FROM PROGRAM MEMORY USING PROGRAM SPACE VISIBILITY
The upper 32 Kbytes of data space may optionally be
mapped into any 16K word program space page. This
provides transparent access of stored constant data
from X data space, without the need to use special
instructions (i.e., TBLRDL/H, TBLWTL/H instructions).
Program space access through the data space occurs
if the MSb of the data space EA is set and program
space visibility is enabled, by setting the PSV bit in the
Core Control register (CORCON). The functions of
CORCON are discussed in Section 2.4 “DSP
Engine”, DSP Engine.
Data accesses to this area add an additional cycle to
the instruction being executed, since two program
memory fetches are required.
Note that the upper half of addressable data space is
always part of the X data space. Therefore, when a
DSP operation uses program sp ace mapp ing to acc ess
this memory region , Y d at a space should ty pic al ly contain state (variable) data for DSP operations, whereas
X data space should typically contain coefficient
(constant) data.
Although each da ta sp ace addres s, 0x8000 and higher ,
maps directly into a corresponding program memory
address (see Figure 3-5), only the lower 16-bits of the
24-bit program word are used to contain the data. The
upper 8 bits shoul d be progra mmed to forc e an illeg al
instruction to maintain machine robustness. Refer to
the “dsPIC30F/33F Programmer’s Reference Manual”
(DS70157) for details on instruction encoding.
16
TBLRDH.B (Wn<0> = 0)
Note that by incrementing the PC by 2 for each program memory word, the Least Significant 15 bits of
data space addresses directly map to the Least Significant 15 bits in the corresponding program space
addresses. The rem aining b its a re provid ed by th e Program Space Vis ibilit y Page regi ster, PSVPAG<7:0>, as
shown in Figure 3-5.
Note: PSV access is tempor arily dis abled d uring
table reads/writes.
For instructions that use PSV which are executed
outside a REPEAT loop:
• The following instructions will require one instruction cycle in addition to the specified execution
time:
- MAC class of instructions with data operand
prefetch
- MOV instructions
- MOV.D instructions
• All other instructions will require two instruction
cycles in addition to the specified execution time
of the instruction.
For instructions that use PSV which are executed
inside a REPEAT loop:
• The following inst ances wi ll require two ins truction
cycles in addition to the specified execution time
of the instruction:
- Execution in the first iteration
- Execution in the last iteration
- Execution prior to exiting the loop due to an
interrupt
- Execution upon re-entering the loop after an
interrupt is serviced
• Any other iteration of the REPEAT loop will allow
the instruction, accessing data using PSV, to
execute in a single cycle.
8
0
DS70118G-page 22 © 2006 Microchip Technology Inc.
Page 25

dsPIC30F2010
FIGURE 3-5 : DATA S PACE WIND O W I NT O P ROG R AM SPACE OPER AT ION
Data Space Program Space
0x0000
EA<15> =
Data
Space
EA
BSET CORCON,#2 ; PSV bit set
MOV #0x00, W0 ; Set PSVPAG register
MOV W0, PSVPAG
MOV 0x9200, W0 ; Access program memory location
16
EA<15> = 1
Upper half of Data
Space is mapped
into Program Space
15
0
15
; using a data space access
0x8000
15
0xFFFF
PSVPAG
0x00
8
Address
Concatenat i on
(1)
23 15 0
23
Data Read
0x100100
0x001200
0x001FFE
Note: PSVPAG is an 8-bit register, containing bits <22:15> of the program space address
(i.e., it defines the page in program space to which the upper half of data space is being mapped).
3.2 Data Address Space
The core has two data spaces. The data spaces can be
considered either separate (for some DSP instructions), or as one unified linear address range (fo r MCU
instructions). The dat a spaces are accessed using tw o
Address Generation Units (AGUs) and separate data
paths.
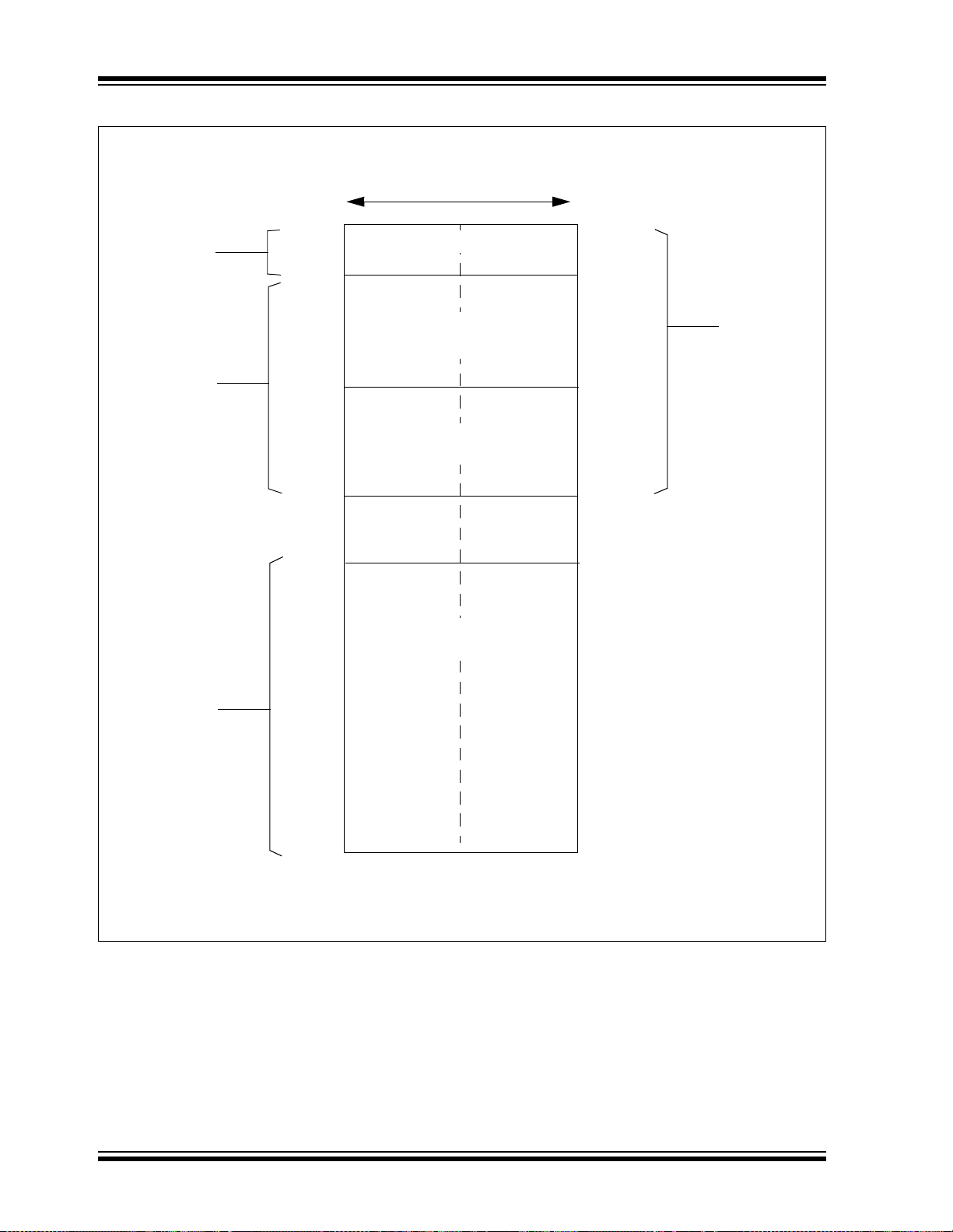
3.2.1 DATA SPACE MEMORY MAP
The data space memory is split into two blocks, X and
Y data space. A key element of this architectur e is th at
Y space is a subset of X space, and is fully contained
within X space. In order to provide an apparent linear
addressing space, X and Y spaces have contiguous
addresses.
When executing any instruction other than one of the
MAC class of instructions, the X block consists of the
256 byte data address space (including all Y
addresses). When executing one of the MAC class of
instructions, the X block consists of the 256 bytes data
address space excluding the Y address block (for data
reads only). In other word s, all other i nstructions rega rd
the entire data memory as one composite address
space. The MAC class instructions extract the Y
address space from data space and address it using
EAs sourced from W10 and W11. The remaining X data
space is addressed using W8 and W9. Both address
spaces are concurrently accessed only with the MAC
class instructions.
A data space memory map is shown in Figure 3-6.
© 2006 Microchip Technology Inc. DS70118G-page 23
Page 26
dsPIC30F2010
FIGURE 3-6: DA TA SPA CE MEM OR Y MA P
SFR Space
(Note)
512 bytes
SRAM Space
MSB
Address
0x0001
0x07FF
0x0801
0x08FF
0x0901
0x09FF 0x0A00
(Note)
0x8001
16 bits
LSBMSB
SFR Space
X Data RAM (X)
256 bytes
Y Data RAM (Y)
256 bytes
LSB
Address
0x0000
0x07FE
0x0800
2560 bytes
Near
Data
Space
0x08FE
0x0900
0x8000
X Data
Unimplemented (X)
Optionally
Mapped
into Program
Memory
0xFFFF
Note: Unimplemented SFR or SRAM locations read as ‘0’.
0xFFFE
DS70118G-page 24 © 2006 Microchip Technology Inc.
Page 27
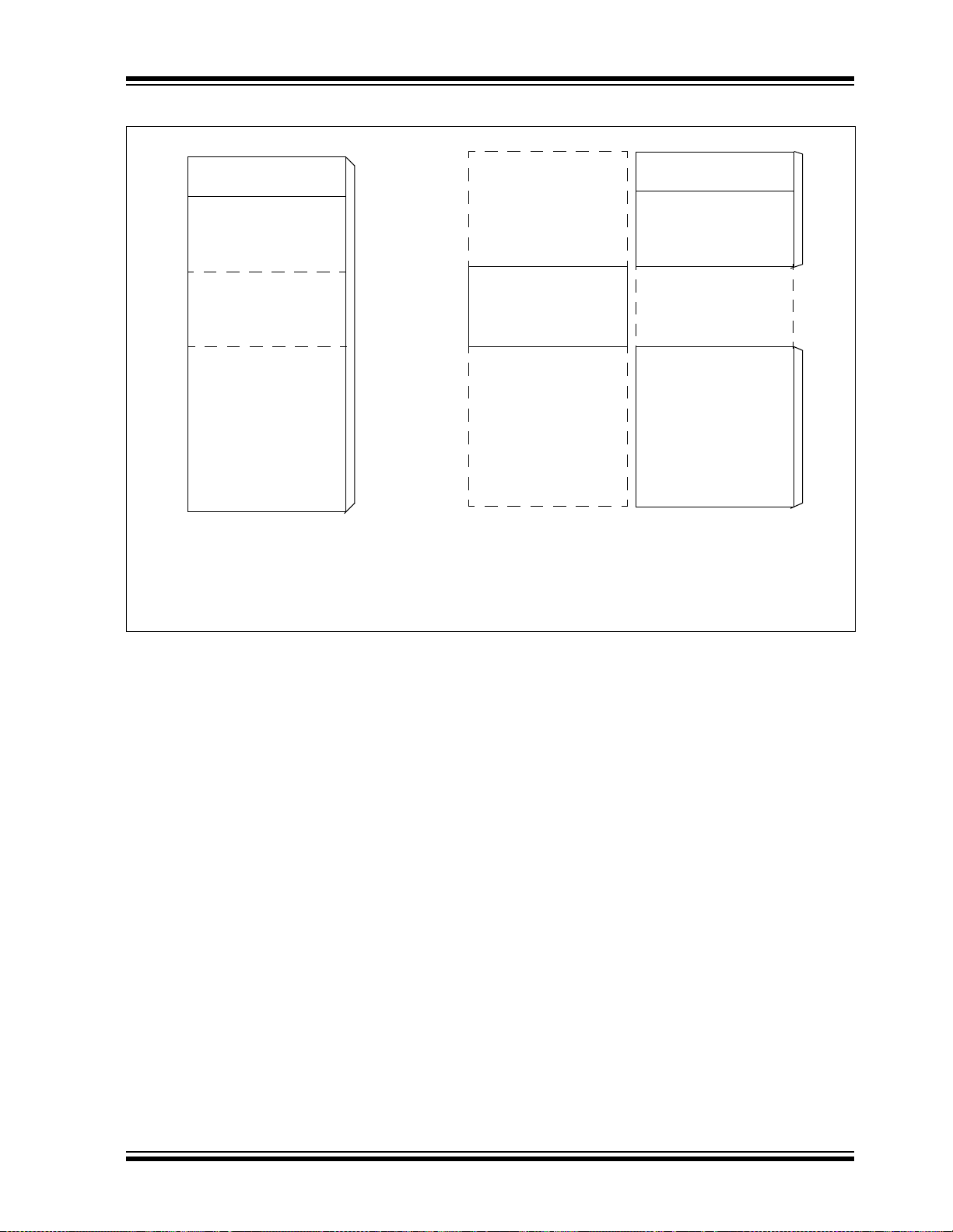
dsPIC30F2010
FIGURE 3-7: DATA SPACE FOR MCU AND DSP (MAC CLASS) INSTRUCTIONS
SFR SPACE
UNUSED
(Y SPACE)
X SPACE
Non-MAC Class Ops (Read/Write) MAC Class Ops Read-Only
MAC Class Ops (Wr i te)
Indirect EA using any W Indirect EA using W8, W9 Indirect EA using W10, W11
Y SPACE
UNUSED
SFR SPACE
UNUSED
X SPACE
X SPACE
© 2006 Microchip Technology Inc. DS70118G-page 25
Page 28

dsPIC30F2010
3.2.2 DATA SPACES
The X data space is used by all instructions and supports all addressing modes. There are separate read
and write data buses. The X read data bus is the return
data path for all inst ructions that view data spac e as
combined X and Y address space. It is also the X
address space data path for the dual operand read
instructions (MAC class). The X write data bus is the
only write path to data space for all instructions.
The X data space also supp orts Mod ulo Addressin g for
all instructions, subject to addressing mode restrictions. Bit-Reversed addressing is only supported for
writes to X data space.
The Y data space is used in concert with the X data
space by the MAC class of instructions (CLR, ED,
EDAC, MAC, MOVSAC, MPY, MPY.N and MSC) to provide two concurrent data read paths. No writes occur
across the Y bus. This class of instructions dedicates
two W register pointers, W10 and W11, to always
address Y data space, independent of X data space,
whereas W8 and W9 always address X data space.
Note that during accumulator write-back, the data
address space is con si dere d a c om bin ati on of X and Y
data spaces, so the write occurs across the X bus.
Consequently, the write can be to any address in the
entire data space.
The Y data space can only be used for the data
prefetch operation associated with the MAC class of
instructions. It also supports Modulo Addressing for
automated circular bu f fe rs. O f c ours e, all othe r ins tru ctions can access the Y dat a address sp ace through the
X data path, as part of the composite linear space.
The boundary between the X and Y data spaces is
defined as shown in Figure 3-6 and is not user programmable. Shoul d an EA poin t to d ata out side it s own
assigned address space, or to a location outside physical memory, an all-zero word/byte will be returned. For
example, although Y address space is visible by all
non-MAC instructions using any Addressing mode, an
attempt by a MAC instruction to fetch data from that
space, usin g W8 or W9 (X spac e point ers), wi ll ret urn
0x0000.
3.2.3 DATA SPACE WIDTH
The core data width is 16 bits. All internal registers are
organized as 16-bit wide words. Data space memory is
organized in byte addressable, 16-bit wide blocks.
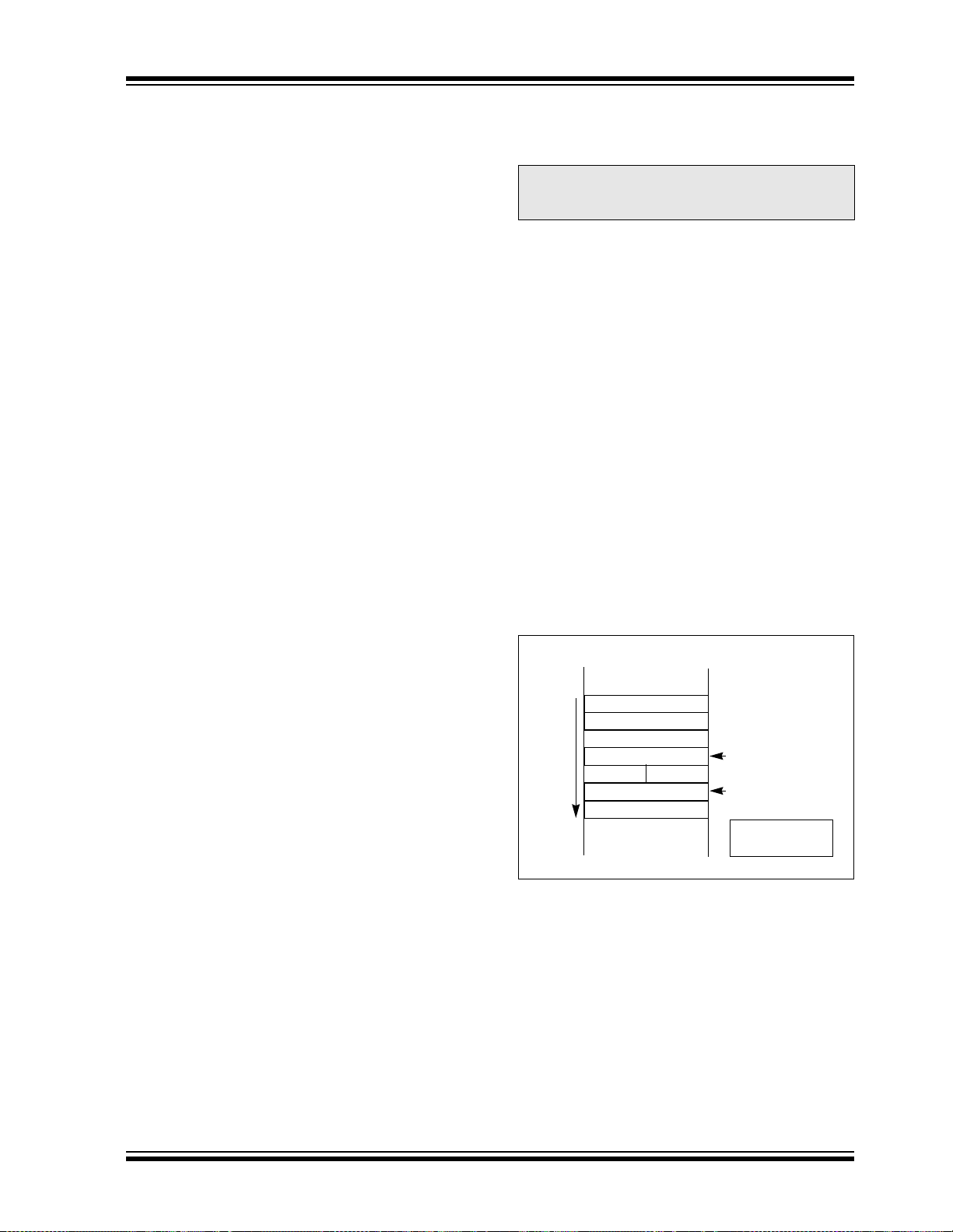
3.2.4 DATA ALIGNMENT
To help maintain backward compatibility with PIC
MCU devices and improve data space memory usage
efficiency, the dsPIC30F instruction set supports both
word and byte operation s. Data i s aligned in dat a memory and registers as words, but all data space EAs
resolve to bytes. Data byte reads will rea d the comp lete
word, which contain s the byte, usi ng the LSb of an y EA
to determine which byte to select. The selected byte is
placed onto the LSB of the X data path (no byte
accesses are possible fro m the Y data pa th as the MAC
class of instruction can only fetch words). That is, data
memory and registers are organized as two parallel
byte wide entities with shared (word) address decode,
but separate write lines. Data byte writes only write to
the corresponding side of the array or register which
matches the byte address.
As a consequence of th is byte acce ssibility, all effective
address calculatio ns (in cl udi ng tho se ge nera ted by th e
DSP operations, which are restricted to word-sized
data) are internal ly scaled to ste p through word-ali gned
memory. For example, the core would recognize that
Post-Modified Register Indirect Addressing mode,
[Ws ++], will result in a value of Ws + 1 for byte
operations and Ws + 2 for word operations.
All word accesses m ust be al igned to an even addre ss.
Misaligned word data fetches are not supported, so
care must be taken when mixing byte and word operations, or translatin g from 8-bit MCU cod e. Should a misaligned read or write be attempted, an address error
trap will be generated. If the error occurred on a read,
the instruction underway is completed, whereas if it
occurred on a write, the ins truction wil l be execu ted but
the write will not occur. In either case, a trap will then
be executed, allow ing the syste m and /or user to exam ine the machine state prior to execution of the address
fault.
®
TABLE 3-2: EFFECT OF INVALID
MEMORY ACCESSES
Attempted Operation Data Returned
EA = an unimplemented address 0x0000
W8 or W9 used to access Y data
space in a MAC instruction
W10 or W11 used to access X
data space in a MAC instruction
All effective addresses are 16 bits wide and point to
bytes within the data space. Therefore, the data space
address range is 64 Kbytes or 32K words.
DS70118G-page 26 © 2006 Microchip Technology Inc.
0x0000
0x0000
FIGURE 3-8: DATA ALIGNMENT
15 8 7 0
0001
0003
0005
Byte 1 Byte 0
Byte 3 Byte 2
Byte 5 Byte 4
LSBMSB
0000
0002
0004
Page 29
dsPIC30F2010
All byte loads into any W register are loaded into the
LSB. The MSB is not modified.
A sign-extend (SE) instruction is provided to allow
users to translate 8-bit signed data to 16-bit signed
values. Alternatively, for 16-bit unsigned data, users
can clear the MSB of any W register by executing a
zero-extend (ZE) instruction on the appropriate
address.
Although most ins truc tio ns a r e ca p ab le of operating on
word or byte data sizes, it should be noted that some
instructions, including the DSP instructions, operate
only on words.
3.2.5 NEAR DATA SPACE
An 8 Kbyte ‘near’ data space is reserved in X address
memory space between 0x0000 and 0x1FFF, which is
directly addressable via a 13- bit absolute address fiel d
within all memory direct instructions. The remaining X
address space and all of the Y address space is
addressable indirec tly. Additionally, the w hole of X da ta
space is addressable using MOV instructions, which
support memory direct addressing with a 16-bit
address field.
3.2.6 SOFTWARE STACK
The dsPIC DSC de vice cont ain s a softwa re sta ck. W15
is used as the Stack Pointer.
The Stack Pointer always points to the first available
free word, and grows from lower addresses towards
higher addresses. It pre-decrements for stack pops,
and post-increments for stack pushes, as shown in
Figure 3-9. Note that for a PC push during any CALL
instruction, the MSB of the PC is zero-ex tende d before
the push, ensuring that the MSB is always clear.
Note: A PC push during exception processing
will concatenate the SRL register to the
MSB of the PC prior to the push.
There is a Stack Pointer Limit register (SPLIM) associated with the Stack Pointer. SPLIM is uninitialized at
Reset. As is t he case f or t h e Stack Point er, SPLIM<0>
is forced to ‘0’, because all stack operations must be
word-aligned. Whenever an EA is generated using
W15 as a sour ce or destination poi nter, the address
thus generated is compa red with the value in SPLIM. If
the contents o f the Stack Pointer (W15) and the SPLIM
register are equal and a push operation is perf ormed, a
stack error trap will not occur. The stack error trap will
occur on a subsequ ent push operatio n. Thus, for exam ple, if it is desirable to cause a stac k error trap when the
stack grows beyond address 0x2000 in RAM, initialize
the SPLIM with the value, 0x1FFE.
Similarly, a stack pointer underflow (stack error) trap is
generated when the Stack Pointer address is found to
be less than 0x0800, thus preventing the stack from
interfering with the Special Function Register (SFR)
space.
A write to the SPLIM regis ter should not be im mediately
followed by an indirect read operati on usi ng W15.
FIGURE 3-9: CALL ST ACK FRAME
0x0000
015
PC<15:0>
000000000
Higher Address
Stack Grows Towards
© 2006 Microchip Technology Inc. DS70118G-page 27
PC<22:16>
<Free Word>
W15 (before CALL)
W15 (after CALL)
POP: [--W15]
PUSH: [W15++]
Page 30
DS70118G-page 28 © 2006 Microchip Technology Inc.
TABLE 3-3: CORE REGISTER MAP
SFR Name
W0 0000 W0 / WREG
W1 0002 W1
W2 0004 W2
W3 0006 W3
W4 0008 W4
W5 000A W5
W6 000C W6
W7 000E W7
W8 0010 W8
W9 0012 W9
W10 0014 W10
W11 0016 W11
W12 0018 W12
W13 001A W13
W14 001C W14
W15 001E W15
SPLIM 0020 SPLIM
ACCAL 0022 ACCAL
ACCAH 0024 ACCAH
ACCAU 0026 Sign Extension (ACCA<39>) ACCAU
ACCBL 0028 ACCBL
ACCBH 002A ACCBH
ACCBU 002C Sign Extension (ACCB<39>) ACCBU
PCL 002E PCL
PCH 0030
TBLPAG 0032
PSVPAG 0034
RCOUNT 0036 RCOUNT
DCOUNT 0038 DCOUNT
DOSTARTL 003A DOSTARTL 0
DOSTARTH 003C
DOENDL 003E DOENDL 0
DOENDH 0040
SR 0042 OA OB SA SB OAB SAB DA DC IPL2 IPL1 IPL0 RA N OV Z C
Address
(Home)
Bit 15 Bit 14 Bit 13 Bit 12 Bit 11 Bit 10 Bit 9 Bit 8 Bit 7 Bit 6 Bit 5 Bit 4 Bit 3 Bit 2 Bit 1 Bit 0 Reset State
— — — — — — — — —PCH
— — — — — — — —TBLPAG
— — — — — — — —PSVPAG
— — — — — — — — —DOSTARTH
— — — — — — — — — DOENDH
Legend: u = uninitialized bit
Note: Refer to “dsPIC30F Family Reference Manual” (DS70046) for descriptions of register bit fields.
dsPIC30F2010
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 1000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
uuuu uuuu uuuu uuuu
uuuu uuuu uuuu uuuu
uuuu uuuu uuuu uuu0
0000 0000 0uuu uuuu
uuuu uuuu uuuu uuu0
0000 0000 0uuu uuuu
0000 0000 0000 0000
Page 31
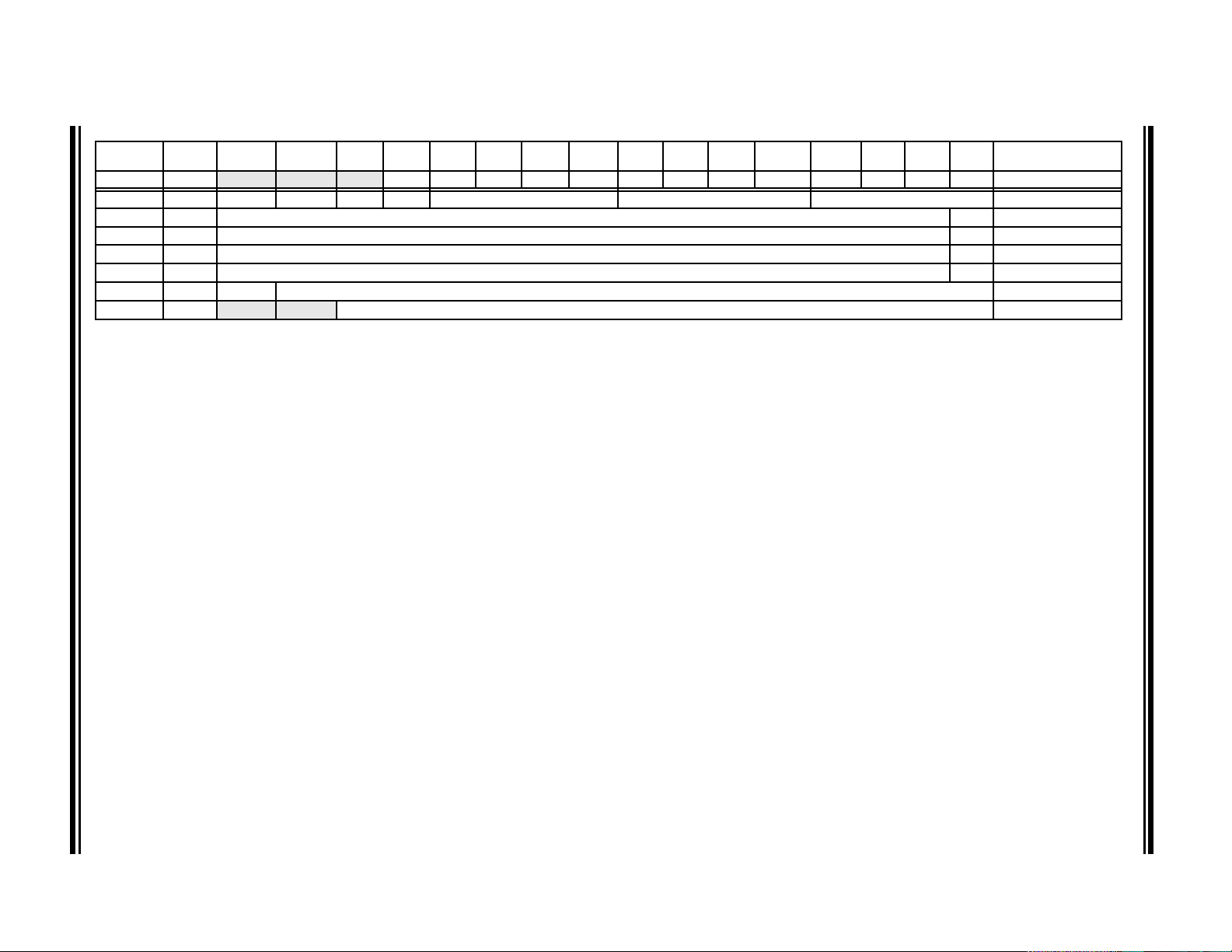
© 2006 Microchip Technology Inc. DS70118G -page 29
TABLE 3-3: CORE REGISTER MAP (CONTINUED)
SFR Name
CORCON 0044 — — — US EDT DL2 DL1 DL0 SATA SATB SATDW ACCSAT IPL3 PSV RND IF
MODCON 0046 XMODEN YMODEN — — BWM<3:0> YWM<3:0> XWM<3:0>
XMODSRT 0048 XS<15:1> 0
XMODEND 004A XE<15:1> 1
YMODSRT 004C YS<15:1> 0
YMODEND 004E YE<15:1> 1
XBREV 0050 BREN XB<14:0>
DISICNT 0052
Address
(Home)
Bit 15 Bit 14 Bit 13 Bit 12 Bit 11 Bit 10 Bit 9 Bit 8 Bit 7 Bit 6 Bit 5 Bit 4 Bit 3 Bit 2 Bit 1 Bit 0 Reset State
— — DISICNT<13:0>
Legend: u = uninitialized bit
Note: Refer to “dsPIC30F Family Reference Manual” (DS70046) for descriptions of register bit fields.
0000 0000 0010 0000
0000 0000 0000 0000
uuuu uuuu uuuu uuu0
uuuu uuuu uuuu uuu1
uuuu uuuu uuuu uuu0
uuuu uuuu uuuu uuu1
uuuu uuuu uuuu uuuu
0000 0000 0000 0000
dsPIC30F2010
Page 32

dsPIC30F2010
NOTES:
DS70118G-page 30 © 2006 Microchip Technology Inc.
Page 33

dsPIC30F2010
4.0 ADDRESS GENERATOR UNITS
Note: This data sheet summarizes features of this g roup
of dsPIC30F devices and is not intended to be a complete
reference source. For more information on the CPU,
peripherals, register descriptions and general device
functionality, refer to the “dsPIC30F Family Reference
Manual” (DS70046). For more informat ion on the device
instruction set and programming, refer to the “dsPIC30F/
33F Programmer’s Reference Manual” (DS70157).
The dsPIC DSC core contains two independent
address generator unit s: the X AGU an d Y AGU. The Y
AGU supports word-sized data reads for the DSP MAC
class of instructions only. The dsPIC DSC AGUs
support three types of data addressing:
• Linear Addressing
• Modulo (Circular) Addressing
• Bit-Reversed Addressing
Linear and Modulo Data Addressing modes can be
applied to data space or program space. Bit-Reversed
Addressing is only applicab le to dat a s pace a ddresses .
4.1 Instruction Addressing Modes
The Addressing modes in Table 4-1 form the basis of
the Addressing mode s optimized to support the sp ecific
features of individual instructions. The Addressing
modes provided in the MAC class of instructions are
somewhat different from those in the other instruction
types.
4.1.1 FILE REGISTER INSTRUCTIONS
Most file register ins truc tio ns use a 13-bit address field
(f) to directly address data present in the first 8192
bytes of data memory (near data space). Most file
register instructions employ a working register W0,
which is de noted as WREG i n these instruc tions. The
destination is typically either the same file register, or
WREG (with the exception of the MUL instruction),
which writes the re sult t o a re gister or regi ster p air. The
MOV instruction allows additional flexibility and can
access the entire data space.
TABLE 4-1: FUNDAMENTAL ADDRESSING MODES SUPPORTED
Addressing Mode Description
File Register Direct The address of the file register is specified explicitly.
Register Direct The contents of a register are accessed directly.
Register Indirect The contents of Wn forms the Effective Address (EA).
Register Indirect Post-modified The contents of Wn forms the EA. Wn is post-modified (incremented or
decremented) by a constant value.
Register Indirect Pre-modified Wn is pre-modified (incremented or decremented) by a signed constant value
to form the EA.
Register Indirect with Register Offset The sum of Wn and Wb forms the EA.
Register Indirect with Literal Offset The sum of Wn and a literal forms the EA.
© 2006 Microchip Technology Inc. DS70118G-page 31
Page 34

dsPIC30F2010
4.1.2 MCU INSTRU CTIONS
The three-operand MCU instructions are of the form:
Operand 3 = Operand 1 <function> Operand 2
where Operand 1 is alwa ys a work in g register (i.e., the
Addressing mode can only be register direct), which is
referred to as Wb. Operand 2 can be a W register,
fetched from data memory, or 5-bit literal. The result
location can be either a W register or an address
location. The following Addressing modes are
supported by MCU instructions:
• Register Direct
• Register Indirect
• Register Indirect Post-modified
• Register Indirect Pre-modif ied
• 5-bit or 10-bit Literal
Note: Not all instructions support all the
Addressing modes gi ven above. Indivi dual
instructions may support different subsets
of these Addressing modes.
4.1.3 MOVE AND ACCUMULATOR
INSTRUCTIONS
Move instructions and the DSP Accumulator class of
instructions provide a greater degree of addressing
flexibility than other instructions. In addition to the
Addressing modes supported by most MCU instructions, Move and Accumulator instructions also support
Register Indirect with Register Offset Addressing
mode, also referred to as Register Indexed mode.
Note: For the MOV instructions, the Addressing
mode specified in the instruction can differ
for the source and destination EA. However , the 4 -bit Wb (Register Offs et) fie ld is
shared between both source and
destination (but typically only used by
one).
In summary, the following Addressing modes are
supported by Move and Accumulator instructions:
• Register Direct
• Register Indirect
• Register Indirect Post-modified
• Register Indirect Pre-modif ied
• Register Indirect with Register Offset (Indexed)
• Register Indirect with Literal Offset
• 8-bit Literal
• 16-bit Literal
Note: Not all instructions support all the
Addressing modes gi ven above. Indivi dual
instructions may support different subsets
of these Addressing modes.
4.1.4 MAC INSTRUCTIONS
The dual source operand DSP instructions (CLR, ED,
EDAC, MAC, MPY, MPY.N, MOVSAC and MSC), also
referred to as MAC instruction s, utilize a simplified set of
Addressing modes to allow the user to effectively
manipulate the data pointers through register indirect
tables.
The two source operand prefetch registers must be a
member of the set {W8, W9, W10, W11}. For data
reads, W8 and W9 will always be directed to the X
RAGU and W10 and W11 will always be directed to the
Y AGU. The effective add resses generated (bef ore and
after modification) must, therefore, be valid addresses
within X data space for W8 and W9 and Y data space
for W10 and W11.
Note: Register Indirect with Register Offset
Addressing is only available for W9 (in X
space) and W11 (in Y space).
In summary, the following Addressing modes are
supported by the MAC class of instructions:
• Register Indirect
• Register Indirect Post-modified by 2
• Register Indirect Post-modified by 4
• Register Indirect Post-modified by 6
• Register Indirect with Register Offset (Indexed)
4.1.5 OTHER INSTRU CTIONS
Besides the variou s Addressing mo des outli ned above,
some instructio ns use li teral con stant s of va rious siz es.
For example, BRA (branch) instructions use 16-bit
signed literals to spe cify the branc h destination directly,
whereas the DISI instruction uses a 14-bit unsigned
literal field. In some instructi ons , suc h as ADD Acc, the
source of an operand or result is im plied by the opcod e
itself. Cert ain opera tions, su ch as NOP, do not have any
operands.
DS70118G-page 32 © 2006 Microchip Technology Inc.
Page 35

dsPIC30F2010
4.2 Modulo Addressing
Modulo addressing is a method of providing an automated means to support circular data buffers using
hardware. The objectiv e is to re move the need for software to perform data address boundary checks when
executing tightly looped code, as is typical in many
DSP algorithms.
Modulo addressing can operate in either data or program space (since the dat a pointer mechanism is e ssentially the same for both). One circular buffer can be
supported in each of the X (which also provides the
pointers into Program space) and Y data spaces. Modulo addressing can operate on any W register pointer.
However, i t is not a dvisable to use W14 or W15 for Modulo Addressing, since these two registers are used as
the Stac k Frame Pointer and S tack Pointer , respectively.
In general, any particular circular buffer can only be
configured to ope rate in one directio n, as ther e are certain restrictions on the buffer start address (for incrementing buffers) or end address (for decrementing
buffers) based upon the dire ct ion of the buf fer.
The only exception to the usage restrictions is for buffers which have a power-of-2 length. As these buffers
satisfy the start and end address criteria, they may
operate in a Bidirectional mode, (i.e., address boundary checks will be performed on both the lower and
upper address boundaries).
4.2.1 START AND END ADDRESS
The Modulo Addressing scheme requires that a
starting and an end address be specified and loaded
into the 16-bit modulo buffer address registers:
XMODSRT, XMODEND, YMODSRT and YMODEND
(see Table 3-3).
Note: Y space Modulo Addressing EA calcula-
tions assume word-sized data (LSb of
every EA is always clear).
The length of a ci rcular buf fer is not direc tly specifi ed. It
is determined by the difference between the corresponding start and end addresses. The maximum
possible length of the circular buffer is 32K words
(64 Kbytes).
4.2.2 W ADDRESS REGISTER SELECTION
The Modulo and Bit-Rev ers ed Add ress in g Co ntro l re gister MODCON<15:0 > c on t ai ns enable flags as well a s
a W register field to specify the W address registers.
The XWM and YWM fields select which registers will
operate with Modulo Addressing. If XWM = 15, X
RAGU and X WAGU Modulo Addressing are disabled.
Similarly, if YWM = 15, Y AGU Modulo Addressing is
disabled.
The X Address Space Pointer W register (XWM) to
which Modulo Addressing is to be applied, is stored in
MODCON<3:0> (see Table 3-3). Modulo addres si ng is
enabled for X dat a space when XWM is set to any v alue
other than 15 and the XMODEN bit is set at
MODCON<15>.
The Y Address Space Pointer W register (YWM) to
which Modulo Addressing is to be applied, is stored in
MODCON<7:4>. Modulo addressing is enabled for Y
data space when YWM is set to any value other than 15
and the YMODEN bit is set at MODCON<14>.
© 2006 Microchip Technology Inc. DS70118G-page 33
Page 36

dsPIC30F2010
FIGURE 4-1: MODULO ADDRESSING OPERATION EXA MPLE
Byte
Address
0x1100
0x1163
MOV #0x1100,W0
MOV W0, XMODSRT ;set modulo start address
MOV #0x1163,W0
MOV W0,MODEND ;set modulo end address
MOV #0x8001,W0
MOV W0,MODCON ;enable W1, X AGU for modulo
MOV #0x0000,W0 ;W0 holds buffer fill value
MOV #0x1110,W1 ;point W1 to buffer
DO AGAIN,#0x31 ;fill the 50 buffer locations
MOV W0, [W1++] ;fill the next location
AGAIN: INC W0,W0 ;increment the fill value
Start Addr = 0x1100
End Addr = 0x1163
Length = 0x0032 words
DS70118G-page 34 © 2006 Microchip Technology Inc.
Page 37

4.2.3 MODULO ADDRESSING APPLICABILITY
Modulo addressing can be applied to the effective
address calculation associated with any W register. It is
important to realize that the address boundaries check
for addresses less than or greater than the upper (for
incrementing buf fers) and lo wer (for decre menting buf fers) boundary addresses (not just equal to). Address
changes may, therefore, jump beyond boundaries and
still be adjusted correctly.
Note: The modulo corrected effecti ve add res s i s
written back to the re giste r only when PreModify or Post-Modify Addressing mode is
used to compute the effective address.
When an address offset (e.g., [W7 + W2])
is used, modulo add res s c orrec ti on i s p erformed, but the contents of the register
remains unchanged.
4.3 Bit-Reversed Addressing
Bit-Reversed Addressing is intended to simplify data
reordering for radix-2 FFT algori thms. It is supported by
the X AGU fo r data writes only.
The modifier, which may be a constant value or register
contents, is regarded as having its bit order reversed.
The address source and dest ina tion are ke pt in norma l
order. Thus, the only operand requiring reversal is the
modifier.
4.3.1 BIT-REVERSED ADDRESSING IMPLEMENTATION
Bit-Reversed Addressing is enabled when:
1. BWM (W register selection) in the MODCON
register is any value other than 15 (the stack can
not be accessed using Bit-Reversed Addressing) and
2. the BREN bit is set in the XBREV register and
3. the Addressing mode used is Register Indirect
with Pre-Increment or Post-Increment.
dsPIC30F2010
N
If the length of a bit- reversed buffer is M = 2
then the last ‘N’ bits of the data b uffer start address
must be zeros.
XB<14:0> is the bit-revers ed ad dres s modifier or ‘pivot
point’ which is typically a constant. In the case of an
FFT computation, its value is equal to half of the FFT
data buffer size.
Note: All B it-Reversed EA calculations as sume
word-sized data (LSb of every EA is
always clear). The XB value is scaled
accordingly to generate compatible (byte)
addresses.
When enabled, Bit-Reversed Addressing will only be
executed for register indirect with pre-increment or
post-increment add ressing and w ord-sized dat a writes .
It will not function for an y ot her a ddressing mode or for
byte-sized data, and normal addresses will be generated instead. When Bit-Reversed Addr essin g is activ e,
the W Address Pointer will always be added to the
address modifier (XB) and the offset associated with
the register Indirect Addressing mode will be ignored.
In addition, as word-sized data is a requirement, the
LSb of the EA is ignored (and always clear).
Note: Modulo addressing and Bit-Reversed
Addressing should not be enabled
together. In the event that the user
attempts to do this, bit reversed addressing will assume priori ty when activ e for the
X WAGU, and X WAGU Modulo Addressing will be disabled. However, Modulo
Addressing will continue to function in the
X RAGU.
If Bit-Reversed Addressing has already been enabled
by setting the BREN (XBREV<15>) bit, then a write to
the XBREV register sho uld not be immedi ately followed
by an indirect read operation using the W register that
has been designated as the bit-reversed pointer.
bytes,
FIGURE 4-2: BIT-REVERSED ADDRESS EXAMPLE
Sequential Address
b15 b14 b13 b12
b15 b14 b13 b12
© 2006 Microchip Technology Inc. DS70118G-page 35
b11 b10 b9 b8
b11 b10 b9 b8
b7 b6 b5 b4
b7 b6 b5 b1
Pivot Point
b3 b2 b1 0
Bit Locations Swapped Left-to-Right
Around Center of Binary Value
b2 b3 b4 0
Bit-Reversed Address
XB = 0x0008 for a 16-word Bit-Reversed Buffer
Page 38

dsPIC30F2010
TABLE 4-2: BIT-REVERSED ADDRESS SEQUENCE (16-ENTRY)
Normal
Address
A3 A2 A1 A0 Decimal A3 A2 A1 A0 Decimal
0000 0 0000 0
0001 1 1000 8
0010 2 0100 4
0011 3 1100 12
0100 4 0010 2
0101 5 1010 10
0110 6 0110 6
0111 7 1110 14
1000 8 0001 1
1001 9 1001 9
1010 10 0101 5
1011 11 1101 13
1100 12 0011 3
1101 13 1011 11
1110 14 0111 7
1111 15 1111 15
Bit-Reversed
Address
TABLE 4-3: BIT-REVERSED ADDRESS MODIFIER VALUES FOR XBREV REGISTER
Buffer Size (Words)
32768 0x4000
16384 0x2000
8192 0x1000
4096 0x0800
2048 0x0400
1024 0x0200
512 0x0100
256 0x0080
128 0x0040
64 0x0020
32 0x0010
16 0x0008
80x0004
40x0002
20x0001
Note 1: Modifi er values greater than 256 words exceed the data memory available on the dsPIC30F2010 device
XB<14:0> Bit-Reversed Address Modifier Value
(1)
DS70118G-page 36 © 2006 Microchip Technology Inc.
Page 39

dsPIC30F2010
5.0 INTERRUPTS
Note: This data sheet summarizes features of this g roup
of dsPIC30F devices and is not intended to be a complete
reference source. For more information on the CPU,
peripherals, register descriptions and general device
functionality, refer to the “dsPIC30F Family Reference
Manual” (DS70046). For more informat ion on the device
instruction set and programming, refer to the “dsPIC30F/
33F Programmer’s Reference Manual” (DS70157).
The dsPIC30F2010 has 24 interrupt sources and 4
processor exceptions (traps), which must be arbitrated
based on a pr iority scheme.
The CPU is responsible for reading the Interrupt Vector Table (IVT) and transferring the address contained
in the interrupt vector to the program counter. The
interrupt vector is transferred from the program data
bus into the program counter, via a 24-bit wide
multiplexer on the input of the program counter.
The Interrupt Vector Table (IVT) and Alternate Interrupt Vec tor Table (AIVT) are placed near the begin ning
of program memory (0x000004). The IVT and AIVT
are shown in Figure5-1.
The interrupt controller is responsible for preprocessing the interrupts and processor exceptions,
prior to their being presented to the processor core.
The peripheral interrupts and traps are enabled, prioritized and controlled using centralized special function
registers:
• IFS0<15:0>, IFS1<15:0>, IFS2<15:0>
All interrupt request flags are maintained in these
three registers. The flags are set by their respective peripherals or external signals, and they are
cleared via software.
• IEC0<15:0>, IEC1<15:0>, IEC2<15:0>
All interrupt enable control bits are maintained in
these three registers. These control bits are used
to individually enable interrupts from the
peripherals or external signals.
• IPC0<15:0>... IPC11<7:0>
The user-assignable prio rity lev el assoc iate d with
each of these interrupts is held centrally in these
twelve registers.
• IPL<3:0> The current CPU priority level is explic-
itly stored in the IPL bits. IPL<3> is present in the
CORCON register , whereas IPL<2:0> are present
in the STATUS Register (SR) in the processor
core.
• INTCON1<15:0>, INTCON2<15 :0>
Global interrupt control func tions are deriv ed from
these two registers. INTCON1 contains the control and status flags for the processor exceptions.
The INTCON2 register controls the external interrupt request signal behavior and the use of the
alternate vector table.
Note: Interrupt flag bits get set when an interrupt
condition occurs, regar dless of the st ate of
its corresponding enable bit. User software should ensure the appropriate interrupt flag bits are clear prior to enabling an
interrupt.
All interrupt sources can be user-assigned to one of 7
priority levels, 1 through 7, via the IPCx registers.
Each interrupt source is associated with an interrupt
vector, as shown in Figure 5-1. Levels 7 and 1 represent the highest and lowest maskable priorities,
respectively.
Note: Assigning a priority level of 0 to an inter-
rupt source is equivalent to disabling that
interrupt.
If the NSTDIS bit (INTCON1<15>) is set, nesting of
interrupts is prev en ted . Th us , i f a n i nte rrupt is c urre ntl y
being serviced, processing of a new interrupt is
prevented, even if th e ne w inte rrup t is of hi ghe r priority
than the one currently being serviced.
Note: The IPL bits become read-only whenever
the NSTDIS bit has been set to ‘1’.
Certain interrupts have specialized control bits for
features like edge or level triggered interrupts, interrupt-on-change, etc. Control of these features remains
within the peripheral module which generates the
interrupt.
The DISI instruction can be used to disable the
processing of interrupts of priorities 6 and lower for a
certain number of instruc tions, during which the DISI bit
(INTCON2<14>) remains set.
When an interrupt is serviced, the PC is loaded with the
address stored in the vector locati on in Prog ram Memory that corresponds to the int errupt. There are 63 different vect ors wi thin th e IVT (ref er to F igure5-1). These
vectors are contained in locations 0x000004 through
0x0000FE of program memory (refer to Figure 5-1).
These locations contain 24-bit addresses, and in order
to preserve robustness, an address error trap will take
place should the PC attempt to fetch any of these
words during normal execution. This prevents execution of random data as a result of accidentally decrementing a PC into vector space, accidentally mapping
a data space address into vector space or the PC rolling over to 0x000000 after reaching the end of implemented program memory space. Execution of a GOTO
instructio n to this vector space wil l also generate an
address error trap.
© 2006 Microchip Technology Inc. DS70118G-page 37
Page 40

dsPIC30F2010
5.1 Interrupt Priority
The user-assignable In terrupt Prio rity (IP<2 :0>) bit s for
each individual interru pt source are located in the Least
Significant 3 bits of each nibble, within the IPCx register(s). Bit 3 of each nibble is not used and is read as a
‘0’. These bits define the priority level assigned to a
particular interrupt by the user.
Note: The user-selectable priority levels are
from 0, as the lowest pri orit y, to level 7, as
the highest priority.
Since more than one interrupt request source may be
assigned to a specific user specified priority level, a
means is provid ed to assign prio rity within a gi ven level.
This method is called “Natural Order Priority” and is
final.
Natural Order Priority is determined by the position of
an interrupt in the vector table, and only affects
interrupt operation when multiple interrupts with the
same user-assigned priority become pending at the
same time.
Table 5-1 lists the interrupt numbers and interrupt
sources for the dsPIC DSC devices and their
associated vector numbers.
Note 1: The natural o rder priority sche me has 0
as the highest priority and 53 as the
lowest priority.
2: The natural order priority number is the
same as the INT number.
The ability for the user to assign every interrupt to one
of seven priority levels means th at the user ca n as sig n
a very high overall priority level to an interrupt with a
low natural order priority. For example, the PLVD (LowVoltage Detect) can be given a priority of 7. The INT0
(external interrupt 0) may be assigned to priority level
1, thus giving it a very low effective priority.
TABLE 5-1: dsPIC30F2010 INTERRUPT
VECTOR TABLE
INT
Number
Highest Natural Order Priority
10 18 U1TX – UART1 Transm i t t er
11 19 ADC – AD C Convert Done
12 20 NVM – NVM Write Complete
13 21 SI2C – I
14 22 MI2C – I
15 23 Input Change Int er ru pt
16 24 INT1 – Extern al In te rrupt 1
17 25 IC7 – Input Captur e 7
18 26 IC8 – Input Captur e 8
19 27 Reserved
20 28 Reserved
21 29 Reserved
22 30 Reserved
23 31 INT2 - External Interrupt 2
24 32 Reserved
25 33 Reserved
26 34 Reserved
27 35 Reserved
28 36 Reserved
29 37 Reserved
30 38 Reserved
31 39 Reserved
32 40 Reserved
33 41 Reserved
34 42 Reserved
35 43 Reserved
36 44 INT3 – Extern al In te rrupt 3
37 45 Reserved
38 46 Reserved
39 47 PWM – PWM Period Match
40 48 QEI – QEI Interrupt
41 49 Reserved
42 50 Reserved
43 51 FLTA
44 52 Reserved
45-53 53 -61 Reserved
Lowest Natural Order Priority
Vector
Number
0 8 INT0 – External Interrupt 0
1 9 IC1 – Input Capture 1
2 10 OC1 – Output Compare 1
3 11 T1 – Timer 1
4 12 IC2 – Input Capture 2
5 13 OC2 – Output Compare 2
6 14 T2 – Timer 2
7 15 T3 – Timer 3
8 16 SPI1
9 17 U1RX – UART1 Receiver
Interrupt Source
2
C™ Slave Interrupt
2
C Master Interrupt
– PWM Fault A
DS70118G-page 38 © 2006 Microchip Technology Inc.
Page 41

dsPIC30F2010
5.2 Reset Sequence
A Reset is not a true exception, because the interrupt
controller is not invo lved in the Reset pro cess. The processor initializes its registers in response to a Reset,
which forces the PC to zero. The process or then begins
program execution at location 0x000000. A GOTO
instruction is stored in the first program memory location, immediatel y follo wed by th e addres s t arget for the
GOTO instruction. The processor executes the GOTO to
the specified addres s and then begi ns op erat ion at the
specified target (start) address.
5.2.1 RESE T SOURCES
In addition to External Reset and Power-on Reset
(POR), there are 6 sources of error conditions which
‘trap’ to the Reset vector.
• Watchdog Time-out:
The watchdog has timed out, indicating that the
processor is no longer executin g the corre ct flo w
of code.
• Uninitialized W Register Trap:
An attempt to use an uninitialized W register as
an Address Pointer will cause a Reset.
• Illegal Instruction Trap:
Attempted execution of any unused opcodes will
result in an illegal instruction trap. Note that a
fetch of an illegal instruction does not result in an
illegal instruction trap if that instruction is flushed
prior to execution due to a flow change.
• Brown-out Reset (BOR):
A momentary dip in the power supply to the
device has been detected, which may result in
malfunction.
• Trap Lockout:
Occurrence of multiple trap conditions
simultaneously will cause a Reset.
5.3 Traps
Traps can be considered as non-maskable interrupts
indicating a software or hardware error, which adhere
to a predefined priority as shown in Figure 5-1. They
are intended to provide the user a means to correct
erroneous operatio n d urin g debug and when opera tin g
within the application.
Note: If the user does not intend to take correc-
tive action in the event of a trap error condition, these vectors must be loaded with
the address of a default handler that simply contains the RESET instruction. If, on
the other hand, one of the vectors c ontai ning an invalid address is called, an
address error trap is generated.
Note that many of these trap conditions can only be
detected when they occur. Consequently, th e questio nable instruction is allowed to complete prior to trap
exception pr ocessing. If the user ch ooses to recover
from the error, the result of the erroneous action that
caused the trap may have to be corrected.
There are 8 fixed priority levels for traps: Level 8
through Level 15, whic h m ea ns that the IPL 3 is al w ay s
set during processing of a trap.
If the user is not cur rentl y execu tin g a trap , and h e set s
the IPL<3:0> bit s t o a va lue of ‘0111’ (Lev el 7), t hen al l
interrupts are disabled, b ut traps c an still b e processe d.
5.3.1 TRAP SOURCES
The following traps are provided with increasing priority. However, since all traps can be nested, priority has
little effect.
Math Error Trap:
The math error trap execu tes und er th e fo llowing three
circumstances:
1. Should an attempt be made to divide by zero,
the divide operation will be aborted on a cycle
boundary and the trap taken.
2. If enabled, a math error trap will be taken when
an arithmetic operation on either accumulator A
or B causes an overflow from bit 31 and the
accumulator guard bits are not utilized.
3. If enabled, a math error trap will be taken when
an arithmetic operation on either accumulator A
or B causes a catastrophic overflow from bit 39
and all saturation is disabled.
4. If the shift amount specified in a shift instruction
is greater than the maximum allowed shift
amount, a trap will occur.
© 2006 Microchip Technology Inc. DS70118G-page 39
Page 42

dsPIC30F2010
Address Error Trap:
This trap is initiated when any of the following
circumstances occurs:
1. A misaligned data word access is attempted.
2. A data fetch from an unimplemented data
memory location is attempted.
3. A data access of an unimplemented program
memory location is attempted.
4. An instruction fetch from vector space is
attempted.
Note: In the MAC class of instr uctions, wherein
the data space is split into X and Y data
space, unimplemented X space includes
all of Y space, and unimplemented Y
space includes all of X space.
5. Execution of a “BRA #literal” instruction or a
“GOTO #literal” instruction, whe re literal
is an unimplem ented progr am memo ry addr ess.
6. Executing instructions after modifying the PC to
point to unimplemented program memory
addresses. The PC may be modified by loading
a value into the stack and executing a RETURN
instruction.
Stack Error Trap:
This trap is initiated under the following conditions:
1. The Stack Pointer is loaded with a value which
is greater than the (user programmable) limit
value written into the SPLIM register (stack
overflow).
2. The Stack Pointer is loaded with a value which
is less than 0x0800 (simple stack underflow).
Oscillator Fail Trap:
This trap is initiated if the external oscillator fails and
operation becomes reliant on an internal RC backup.
5.3.2 HARD AND SOFT TRAPS
It is possible that multiple traps can become active
within the same cycle (e.g., a misaligned word stack
write to an overflowed address). In such a case, the
fixed priority shown in Figure 5-1 is implemented,
which may requ ire the user to check if ot her traps are
pending, in order to completely correct the fault.
‘Soft’ traps incl ude excepti ons of priority level 8 through
level 11, inclusive. The arithmetic error trap (level 11)
falls into this category of traps.
‘Hard’ traps include exceptions of priority level 12
through level 15, inclusive. The address error (level
12), stack error (level 13) and oscillator error (level 14)
traps fall into this category.
Each hard trap that occurs must be acknowledged
before code execution of any type may continue. If a
lower priority hard trap occurs while a higher priority
trap is pending, acknowledged, or is being processed,
a hard trap conflict will occur.
The device is automatic ally Reset in a hard trap conflict
condition. The TRAPR status bit (RCON<15>) is set
when the Reset occurs, so that the condition may be
detected in software.
FIGURE 5-1: TRAP VECTORS
Decreasing
Priority
AIVT
IVT
Reset - GOTO Instruction
Reset - GOTO Address
Reserved
Oscillator Fail Trap Vector
Address Error Trap Vector
Stack Error Trap Vector
Math Error Trap Vector
Reserved Vector
Reserved Vector
Reserved Vector
Interrupt 0 Vector
Interrupt 1 Vector
—
—
—
Interrupt 52 Vector
Interrupt 53 Vector
Reserved
Reserved
Reserved
Oscillator Fail Trap Vector
Stack Error Trap Vector
Address Error Trap Vector
Math Error Trap Vector
Reserved Vector
Reserved Vector
Reserved Vector
Interrupt 0 Vector
Interrupt 1 Vector
—
—
—
Interrupt 52 Vector
Interrupt 53 Vector
0x000000
0x000002
0x000004
0x000014
0x00007E
0x000080
0x000082
0x000084
0x000094
0x0000FE
DS70118G-page 40 © 2006 Microchip Technology Inc.
Page 43

dsPIC30F2010
)
5.4 Interrupt Sequence
All interrupt event flags are sampled in the be ginning of
each instruction cycle by the IFSx registers. A pending
interrupt request (IR Q) is indic ated by the flag bit bein g
equal to a ‘1’ in an IFSx register. The IRQ will cause an
interrupt to occur if the corresp onding bit in the interru pt
enable (IECx) register is set. For the remainder of the
instruction cycle, the priorities of all pending interrupt
requests are evaluated.
If there is a pending IRQ with a priority level greater
than the current processor priority level in the IPL bits,
the processor will be interrupted.
The processor then st acks the curren t program coun ter
and the low byte of the processor STATUS register
(SRL), as shown in Fi gu re5-2. The low byte of the s t atus registe r con tains t he pro cessor pri ority level at t he
time, prior to the beginning of the interrupt cycle. The
processor then loads the priority level for this interrupt
into the STATUS register. This action will disable all
lower priority interrupts until the completion of the
Interrupt Service Routine (ISR).
FIGURE 5-2: INTERRUPT ST ACK
FRAME
0x0000
PC<15:0>
SRL IPL3 PC<22:16>
Higher Address
Stack Grows Towards
Note 1: The user can always lower the priority
The RETFIE (Return from Interrupt) instruction will
unstack the program counter and status registers to
return the processor to its state prior to the interrupt
sequence.
<Free Word>
level by writing a new value into SR. The
Interrupt Service Routine must clear the
interrupt flag bits in the IFSx register
before lowering the processor interrupt
priority, in order to avoid recursive
interrupts.
2: The IPL3 bit (CORCON<3>) is always
clear when interrupts are being processed. It is set only during execution of
traps.
015
W15 (before CALL
W15 (after CALL)
POP : [--W15]
PUSH : [W15++]
5.5 Alternate Vector Table
In Program Memory, the Interrupt Vector Table (IVT) is
followed by the Alternate Interr upt Vector Tab le (AIVT),
as shown in Figure 5-1. Access to the Alternate Vector
Table is provided by the ALTIVT bit in the INTCON2
register . If the ALTIVT bit is set, all interrup t and exce ption processes will use the alternate vectors instead of
the default vecto rs. The alternate vectors are org anized
in the same manner as the default vectors. The AIVT
supports emulation and debugging efforts by providing
a means to switch between an application and a support environment, without requiring the interrupt vectors to be reprogrammed. This feature also enables
switching between applications for evaluation of
different software algorithms at run time.
If the AI VT is not requir ed, the p rogram m emory al located to the AIVT may be used for other purposes.
AIVT is not a protected section and may be freely
programmed by the user.
5.6 Fast Context Saving
A context saving option is available using shadow registers. Shadow registers are provided for the DC, N,
OV, Z and C bits in SR, and the re gisters W 0 through
W3. The shadows are o nly one level dee p. The shadow
registers are accessible using the PUSH.S and POP.S
instructions only.
When the processor vectors to an interrupt, the
PUSH.S instruction can be used to store the current
value of the aforementioned registers into their
respective shadow registers.
If an ISR of a certain priority uses the PUSH.S and
POP.S instructions for fast context saving, then a
higher priority I SR shou ld no t inc lude the s ame instructions. Users must save the key registers in software
during a lower priorit y interrupt, if t he higher prio rity ISR
uses fast context saving.
5.7 External Interrupt Requests
The interrupt controller supports five external interrupt
request signals, INT0-INT4. These inputs are edge
sensitive; they require a low-to-high or a high-to-low
transition to generate an interrupt request. The
INTCON2 register has thre e bits, IN T0EP-INT2EP, that
select the polarity of the edge detection circuitry.
5.8 Wake-up from Sleep and Idle
The interrupt controller may be used to wake up the
processor from either Sleep or Idle modes, if Sleep or
Idle mode is active when the interrupt is generated.
If an enabled interrupt request of sufficient priority is
received by the interrupt controller, then the standard
interrupt request is presented to the processor. At the
same time, the processor will wake-up from Sleep or
Idle and begin execution of the Interrupt Service
Routine needed to process the interrupt request.
© 2006 Microchip Technology Inc. DS70118G-page 41
Page 44

DS70118G-page 42 © 2006 Microchip Technology Inc.
TABLE 5-2: INTERRUPT CONTROLLER REGISTER MAP
SFR
Name
INTCON1 0080 NSTDIS
INTCON2 0082 ALTIVT DISI
IFS0 0084 CNIF MI2CIF SI2CIF NVMIF ADIF U1TXIF U1RXIF SPI1IF T3IF T2IF OC2IF IC2IF T1IF OC1IF IC1IF INT0IF
IFS1 0086
IFS2 0088
IEC0 008C CNIE MI2CIE SI2CIE NVMIE ADIE U1TXIE U1RXIE SPI1IE T3IE T2IE OC2IE IC2IE T1IE OC1IE IC1IE INT0IE
IEC1 008E
IEC2 0090
IPC0 0094
IPC1 0096
IPC2 0098
IPC3 009A
IPC4 009C
IPC5 009E
IPC6 00A0
IPC7 00A2
IPC8 00A4
IPC9 00A6
IPC10 00A8
IPC11 00AA
Addr. Bit 15 Bit 14 Bit 13 Bit 12 Bit 11 Bit 10 Bit 9 Bit 8 Bit 7 Bit 6 Bit 5 Bit 4 Bit 3 Bit 2 Bit 1 Bit 0 Reset State
— — — — OVATE OVBTE COVTE — — — MATHERR ADDRERR STKERR OSCFAIL —
— — — — — — — — — — — INT2EP INT1EP INT 0EP
— — — — — — — —INT2IF— — — — IC8IF IC7IF INT1IF
— — — —FLTAIF— —QEIIFPWMIF— — — — — — —
— — — — — — — —INT2IE— — — — IC8IE IC7IE INT1IE
— — — —FLTAIE— — QEIIE PWMIE — — — — — — —
— T1IP<2:0> — OC1IP<2:0> — IC1IP<2:0> — INT0IP<2:0>
— T31P<2:0> — T2IP<2:0> — OC2IP<2:0> —IC2IP<2:0>
—ADIP<2:0>— U1TXIP<2:0> — U1RXIP<2:0> — SPI1IP<2:0>
— CNIP<2:0> —MI2CIP<2:0>—SI2CIP<2:0> — NVMIP<2:0>
— — — — — IC8IP<2:0> — IC7IP<2:0> — INT1IP<2:0>
— INT2IP<2:0> — — — — — — — — — — — —
— — — — — — — — — — — — — — — —
— — — — — — — — — — — — — — — —
— — — — — — — — — — — — — — — —
—PWMIP<2:0>— — — — — — — — — — — —
— FLTAIP<2:0> — — — — — — — — — QEIIP<2:0>
— — — — — — — — — — — — — — — —
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0100 0100 0100 0100
0100 0100 0100 0100
0100 0100 0100 0100
0100 0100 0100 0100
0100 0100 0100 0100
0100 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0100 0000 0000 0100
0000 0000 0000 0000
dsPIC30F2010
Legend: u = uninitialized bit
Note: Refer to “dsPIC30F Family Reference Manual” (DS70046) for descriptions of register bit fields.
Page 45

dsPIC30F2010
6.0 FLASH PROGRAM MEMORY
Note: This data sheet summarizes features of this g roup
of dsPIC30F devices and is not intended to be a complete
reference source. For more information on the CPU,
peripherals, register descriptions and general device
functionality, refer to the “dsPIC30F Family Reference
Manual” (DS70046). For more informat ion on the device
instruction set and programming, refer to the “dsPIC30F/
33F Programmer’s Reference Manual” (DS70157).
The dsPIC30F family of devices contains internal
program Flash memory for executing user code. There
are two methods by which the user can program this
memory:
1. In-Circuit Serial Programming (ICSP) programming capability
2. Run-Time Self-Programming (RTSP)
6.1 In-Circuit Serial Programming
(ICSP)
dsPIC30F devices c an be s erially prog rammed while in
the end application circu it. This is simply done wit h two
lines for Programming Clock and Programming Data
(which are named PGC and PGD respectively), and
three other lines for Power (V
Master Clear (MCLR
). this allows customers to manufacture boards with unprogrammed devices, and then
program the digita l signal control ler just befo re shipping
the product. This also allows the most recent firmware
or a custom firmware to be programmed.
DD), Ground (VSS) and
6.2 Run-Time Self-Programming (RTSP)
RTSP is accomplished using TBLRD (table read) and
TBLWT (table write) instructions .
With RTSP, the user may erase program memory, 32
instructions (96 bytes ) at a time and can write program
memory data, 32 instructions (96 bytes) at a time.
6.3 Table Instruction Operation Summary
The TBLRDL and the TBLWTL instructions are used to
read or write to bits<15:0> of program memory.
TBLRDL and TBLWTL can access program memory in
Word or Byte mode.
The TBLRDH and TBLWTH i nstructio ns are used to read
or write to bits<23:16> of program memory. TBLRDH
and TBLWTH can access program memory in Word or
Byte mode.
A 24-bit program memory address is formed using
bits<7:0> of t he TBLPAG register and the EA from a W
register specified in the table instruction, as shown in
Figure 6-1.
FIGURE 6-1: ADDRESSING FOR T ABLE AND NVM REGISTERS
24 bits
Using
Program
Counter
Using
NVMADR
Addressing
Using
Table
Instruction
User/Configuration
Space Select
0
1/0
NVMADRU Reg
1/0
TBLPAG Reg
NVMADR Reg EA
8 bits 16 bits
Working Reg EA
8 bits
24-bit EA
16 bits
0Program Counter
Byte
Select
© 2006 Microchip Technology Inc. DS70118G-page 43
Page 46

dsPIC30F2010
6.4 RTSP Operation
The dsPIC30F Flash program memory is organized
into rows and panels. Each row consists of 32 instructions, or 96 bytes. Each panel consists of 128 rows, or
4K x 24 instructi ons. RTSP allo ws the user to er ase one
row (32 instructions) at a time and to program 32
instructions at one time. RTSP may be used to program
multiple program memory panels, but the table pointer
must be changed at each panel boundary.
Each panel of program memory contains write latches
that hold 32 instructions of programming data. Prior to
the actual programming operation, the write data must
be loaded into the panel write latches. The data to be
programmed into the panel is loaded in sequential
order into the write latches; instruction 0, instruction 1,
etc. The instructio n word s loaded must always b e fro m
a 32 address boundary.
The basic sequence f or RTSP program ming is to set up
a table point er, then do a s eries o f TBLWT instructions
to load the write latc hes. Prog ramming is perfo rmed b y
setting the special bits in the NVMCON register. 32
TBLWTL and four TBLWTH instructions are required to
load the 32 instructions. If multiple panel programming
is required, the table pointer needs to be changed and
the next set of multiple write latches written.
All of the table write operations are single word writes
(2 instruction cycles), because only the table latches
are written. A programming cycle is required for
programming each row.
The Flash program memory is readable, writable and
erasable during normal operation over the entire V
range.
DD
6.5 Control Registers
The four SFRs used to read and write the program
Flash memory are:
•NVMCON
• NVMADR
• NVMADRU
• NVMKEY
6.5.1 NVMCON REGISTER
The NVMCON register controls which blocks are to be
erased, which memory type is to be programmed, and
the start of the programming cycle.
6.5.2 NVMADR REGISTER
The NVMADR register is used to hold the lower two
bytes of the effective address. The NVMADR register
captures the EA<15:0> of the last tab le instruction that
has been executed and selects the row to write.
6.5.3 NVMADRU REGISTER
The NVMADRU register is used to hold the upper byte
of the effective address. The NVMADRU register captures the EA<23:16> of the last table instruction that
has been executed.
6.5.4 NVMKEY REGISTER
NVMKEY is a write-only register that is used for write
protection. To start a programming or an erase
sequence, the user must consecutively write 0x55 and
0xAA to the NVMKEY register. Refer to Section 6.6
“Programming Operations” for further details.
Note: The user can also directly write to the
NVMADR and NVMADRU registers to
specify a program memory address for
erasing or programming.
DS70118G-page 44 © 2006 Microchip Technology Inc.
Page 47

dsPIC30F2010
6.6 Programming Operations
A complete programming sequence is necessary for
programming or erasing the internal Flash in RTSP
mode. A programming operati on is nominally 2 ms ec in
duration and the processor stalls (waits) until the operation is fi nished. Setting t he WR bit (NVMCO N<15>)
starts the operation, and the WR bit is automatically
cleared when the operation is finished.
6.6.1 PROGRAMMING ALGORITHM FOR PROGRAM FLASH
The user can erase and program one row of program
Flash memory at a time. The general process is:
1. Read one row of program Flash (32 instruction
words) and store into data RAM as a data
“image”.
2. Update the data image with the desired new
data.
3. Erase program Flash row.
a) Setup NVMCON register for multi-word,
program Flash, erase and set WREN bit.
b) Write address of row to be erased into
NVMADRU/NVMDR.
c) Write ‘55’ to NVMKEY.
d) Write ‘AA’ to NVMKEY.
e) Set the WR bit. This will begin erase cycle.
f) CPU will stall for the duration of the erase
cycle.
g) The WR bit is cleared when erase cycle
ends.
4. Write 32 instruction words of data from data
RAM “image” into the program Flash write
latches.
5. Program 32 instruction words into program
Flash.
a) Setup NVMCON register for multi-word,
program Flash, program and set WREN bit.
b) Write ‘55’ to NVMKEY.
c) Write ‘AA’ to NVMKEY.
d) Set the WR bit. This will begin program
cycle.
e) CPU will stall for duration of the program
cycle.
f) The WR bit is cleared by the hardware
when program cycle ends.
6. Repeat steps 1 through 5 as needed to pro gram
desired amount of program Flash memory.
6.6.2 ERASING A ROW OF PROGRAM
MEMORY
Example 6-1 shows a co de sequenc e that can be use d
to erase a row (32 instructions) of program memory.
EXAMPLE 6-1: ERASING A ROW OF PROGR AM MEMO RY
; Setup NVMCON for erase operation, multi word write
; program memory selected, and writes enabled
; Init pointer to row to be ERASED
MOV #0x4041,W0 ;
MOV W0
MOV #tblpage(PROG_ADDR),W0 ;
MOV W0
MOV #tbloffset(PROG_ADDR),W0 ; Intialize in-page EA[15:0] pointer
MOV W0, NVMADR ; Intialize NVMADR SFR
DISI #5 ; Block all interrupts with priority <7
MOV #0x55,W0
MOV W0
MOV #0xAA,W1 ;
MOV W1
BSET NVMCON,#WR ; Start the erase sequence
NOP ; Insert two NOPs after the erase
NOP ; command is asserted
NVMCON ; Init NVMCON SFR
,
NVMADRU ; Initialize PM Page Boundary SFR
,
; for next 5 instructions
NVMKEY ; Write the 0x55 key
,
NVMKEY ; Write the 0xAA key
,
© 2006 Microchip Technology Inc. DS70118G-page 45
Page 48

dsPIC30F2010
6.6.3 LOADING WRITE LATCHES
Example 6-2 shows a sequence of instructions that
can be used to load th e 96 bytes of write lat ches. 32
TBLWTL and 32 TBLWTH instructions are needed to
load the write latches selected by the table pointer.
EXAMPLE 6-2: LOADING WRITE LATCHES
; Set up a pointer to the first program memory location to be written
; program memory selected, and writes enabled
; Perform the TBLWT instructions to write the latches
; 0th_program_word
; 1st_program_word
; 2nd_program_word
; 31st_program_word
MOV #0x0000,W0 ;
MOV W0
MOV #0x6000,W0 ; An example program memory address
MOV #LOW_WORD_0,W2 ;
MOV #HIGH_BYTE_0,W3 ;
TBLWTL W2
TBLWTH W3
MOV #LOW_WORD_1,W2 ;
MOV #HIGH_BYTE_1,W3 ;
TBLWTL W2
TBLWTH W3
MOV #LOW_WORD_2,W2 ;
MOV #HIGH_BYTE_2,W3 ;
TBLWTL W2
TBLWTH W3
•
•
•
MOV #LOW_WORD_31,W2 ;
MOV #HIGH_BYTE_31,W3 ;
TBLWTL W2
TBLWTH W3
TBLPAG ; Initialize PM Page Boundary SFR
,
[W0] ; Write PM low word into program latch
,
[W0++] ; Write PM high byte into program latch
,
[W0] ; Write PM low word into program latch
,
[W0++] ; Write PM high byte into program latch
,
[W0] ; Write PM low word into program latch
,
[W0++] ; Write PM high byte into program latch
,
[W0] ; Write PM low word into program latch
,
[W0++] ; Write PM high byte into program latch
,
Note: In Example 6-2, the contents of the upper byte of W3 has no effect.
6.6.4 INITIATING THE PROGRAMMING SEQUENCE
For protection, the w rite i nitiate sequ ence for N VMKEY
must be used to allow any erase or program operation
to proceed. After the program ming comm and has been
executed, the user must wait for the programming time
until programming is complete. The two instructions
following the start of the programming sequence
should be NOPs.
EXAMPLE 6-3: INITIATING A PROGRAMMING SEQUENCE
DISI #5 ; Block all interrupts with priority <7
MOV #0x55,W0
MOV W0
MOV #0xAA,W1 ;
MOV W1
BSET NVMCON,#WR ; Start the erase sequence
NOP ; Insert two NOPs after the erase
NOP ; command is asserted
NVMKEY ; Write the 0x55 key
,
NVMKEY ; Write the 0xAA key
,
; for next 5 instructions
DS70118G-page 46 © 2006 Microchip Technology Inc.
Page 49

© 2006 Microchip Technology Inc. DS70118G -page 47
TABLE 6-1: NVM REGISTER MAP
File Name Addr. Bit 15 Bit 14 Bit 13 Bit 12 Bit 11 Bit 10 Bit 9 Bit 8 Bit 7 Bit 6 Bit 5 Bit 4 Bit 3 Bit 2 Bit 1 Bit 0 All RESETS
NVMCON 0760 WR WREN WRERR
NVMADR 0762 NVMADR<15:0>
NVMADRU 0764
NVMKEY 0766
— — — — — — — — NVMADR<23:16>
— — — — — — — — KEY<7:0>
Legend: u = uninitialized bit
Note: Refer to “dsPIC30F Family Reference ManuaI” (DS70046) for descriptions of register bit fields.
— — — —
—PROGOP<6:0> 0000 0000 0000 0000
TWRI
uuuu uuuu uuuu uuuu
0000 0000 uuuu uuuu
0000 0000 0000 0000
dsPIC30F2010
Page 50

dsPIC30F2010
NOTES:
DS70118G-page 48 © 2006 Microchip Technology Inc.
Page 51

dsPIC30F2010
7.0 DATA EEPROM MEMORY
Note: This data sheet summarizes features of this g roup
of dsPIC30F devices and is not intended to be a complete
reference source. For more information on the CPU,
peripherals, register descriptions and general device
functionality, refer to the “dsPIC30F Family Reference
Manual” (DS70046). For more informat ion on the device
instruction set and programming, refer to the “dsPIC30F/
33F Programmer’s Reference Manual” (DS70157).
The Data EEPROM Memory is readable and writable
during normal operat ion over the enti re V
data EEPROM memory is directly mapped in the
program memory address space.
The four SFRs used to read and write the program
Flash memory are used to access data EEPROM
memory as well. As described in Section 4.0, these
registers are:
•NVMCON
• NVMADR
• NVMADRU
• NVMKEY
The EEPROM data memory allows read and write of
single words and 16-word blocks. When interfacing to
data memory, NVMADR, in conjunction with the
NVMADRU register, is used to address the EEPROM
location being accessed. TBLRDL and TBLWTL
instructions are used to read and write data EEPROM.
The dsPIC30F devices have up to 1 Kbyte of data
EEPROM, with an address range from 0x7FFC00 to
0x7FFFFE.
A word write operatio n should be preceded by an erase
of the corresponding memory location(s). The write
typically requires 2 ms to complete, but the write time
will vary with voltage and temperature.
DD range. The
A program or erase operation on the data EEPROM
does not stop t he ins truc tion fl ow. The user is re sponsible for waiting for the appropriate duration of time
before initiating another data EEPROM write/erase
operation. Attempting to read the data EEPROM while
a programming or erase o peration is in pro gress results
in unspecified data.
Control bit WR initia tes write operations, similar to program Flash writ es . Th is bi t c an not be cl eared, only set,
in software. This bit is cleared in hardware at the completion of the write operation. The inability to clear the
WR bit in software prevents the accidental or
premature termination of a write operation.
The WREN bit, when set, will allow a write operation.
On power-up, the WREN bit is c lear . Th e WRERR bit is
set when a write operation is interrupted by a MCLR
Reset, or a WDT Time-out Reset, during normal operation. In these situatio ns, foll owin g Reset, the us er can
check the WRERR bit and rewrite the location. The
address register NVMADR remains unchanged.
Note: Interrupt flag bit NVMIF in the IFS0 regis-
ter is set when write is complete. It must be
cleared in software.
7.1 Reading the Data EEPROM
A TBLRD instruction reads a word at the current program word address. This example uses W0 as a
pointer to data EEPROM. The result is placed in
register W4, as shown in Example 7-1.
EXAMPLE 7-1: DATA EEPROM READ
MOV #LOW_ADDR_WORD,W0 ; Init Pointer
MOV #HIGH_ADDR_WORD,W1
MOV W1
TBLRDL [ W0 ], W4 ; read data EEPROM
TBLPAG
,
© 2006 Microchip Technology Inc. DS70118G-page 49
Page 52

dsPIC30F2010
7.2 Erasing Data EEPROM
7.2.1 ERASING A BLOCK OF DATA EEPROM
In order to erase a block of data EEPROM, the
NVMADRU and NVMADR registers must initially
point to the block of memory to be erased. Co nfigure
NVMCON for erasing a block of data EEPROM, and
set the WR and WREN bits in NVMCON register. Setting the WR bit initiates the erase, as shown in
Example 7-2.
EXAMPLE 7-2: DATA EEPROM BLOCK ERASE
; Select data EEPROM block, ERASE, WREN bits
MOV #4045,W0
MOV W0
; Start erase cycle by setting WR after writing key sequence
DISI #5 ; Block all interrupts with priority <7
MOV #0x55,W0 ;
MOV W0
MOV #0xAA,W1 ;
MOV W1
BSET NVMCON,#WR ; Initiate erase sequence
NOP
NOP
; Erase cycle will complete in 2mS. CPU is not stalled for the Data Erase Cycle
; User can poll WR bit, use NVMIF or Timer IRQ to determine erasure complete
NVMCON ; Initialize NVMCON SFR
,
; for next 5 instructions
NVMKEY ; Write the 0x55 key
,
NVMKEY ; Write the 0xAA key
,
7.2.2 ERASING A WORD OF DATA EEPROM
The NVMADRU and NVMADR registers must point to
the block. Select er ase a bl ock of data Flas h, and set
the WR and WREN bits in NVMCON r egister. Sett ing
the WR bit initiates the erase, as shown in Example 7-
3.
EXAMPLE 7-3: DATA EEPROM WORD ERASE
; Select data EEPROM word, ERASE, WREN bits
MOV #4044,W0
MOV W0
; Start erase cycle by setting WR after writing key sequence
DISI #5 ; Block all interrupts with priority <7
MOV #0x55,W0 ;
MOV W0
MOV #0xAA,W1 ;
MOV W1
BSET NVMCON,#WR ; Initiate erase sequence
NOP
NOP
; Erase cycle will complete in 2mS. CPU is not stalled for the Data Erase Cycle
; User can poll WR bit, use NVMIF or Timer IRQ to determine erasure complete
NVMCON
,
; for next 5 instructions
NVMKEY ; Write the 0x55 key
,
NVMKEY ; Write the 0xAA key
,
DS70118G-page 50 © 2006 Microchip Technology Inc.
Page 53

dsPIC30F2010
7.3 Writing to the Data EEPROM
To write an EEPROM data location, the following
sequence must be follow ed :
1. Erase data EEPROM word.
a) Select word, data EEPROM, erase and set
WREN bit in NVMCON register.
b) Write address of word to be erased into
NVMADRU/NVMADR.
c) Enable NVM interrupt (optional).
d) Write ‘55’ to N VMKEY.
e) Write ‘AA’ to NVMKEY.
f) Set the WR bit. This will begin erase cycle.
g) Either poll NVMIF bit or wait for NVMIF
interrupt.
h) The WR bit is cleared when the era se cycl e
ends.
2. Write data word into data EEPROM write
latches.
3. Program 1 data word into data EEPROM.
a) Select word, data EEPROM, program and
set WREN bit in NVMCON register.
b) Enable NVM write done interrupt (o ptiona l).
c) Write ‘55’ to NVMKEY.
d) Write ‘AA’ to NVMKEY.
e) Set The WR bit. This will begin program
cycle.
f) Either poll NVMIF bit or wait for NVM
interrupt.
g) The WR bit is cleared when the write cycle
ends.
The write will not initiate if the above sequence is not
exactly followed (write 0x55 to NVMKEY, write 0xAA to
NVMCON, then set WR bit) for ea ch word. It is stron gly
recommended that interrupts be disabled during this
code segment.
Additionally, the WREN bit in NVMCON must be set to
enable writes. This mechanism prevents accidental
writes to data EEPROM, due to unexpected code execution. The WREN bit sho ul d be k ept clear at all times,
except when updating the EEPROM. The WREN bit is
not cleared by hardware.
After a write sequence has been initiated, clearing the
WREN bit will not aff ect the current write cycle. The WR
bit will be inhibited from being set unless the WREN bit
is set. The WREN bit must be set on a previous ins truction. Both WR and WREN c an not be se t with th e s am e
instruction.
At the completion of the write cycle, the WR bit is
cleared in hardware an d the Nonv ola til e M em ory W rite
Complete Interrupt Flag bit (NVMIF) is set. The user
may either enable this interrupt, or poll this bit. NVMIF
must be cleared by software.
7.3.1 WRITING A WORD OF DATA EEPROM
Once the user has erased the word to be pr ogrammed,
then a table write instruction is used to write one write
latch, as shown in Example 7-4.
EXAMPLE 7-4: DATA EEPROM WORD WRITE
; Point to data memory
MOV #LOW_ADDR_WORD,W0 ; Init pointer
MOV #HIGH_ADDR_WORD,W1
MOV W1
MOV #LOW(WORD),W2 ; Get data
TBLWTL W2
; The NVMADR captures last table access address
; Select data EEPROM for 1 word op
MOV #0x4004,W0
MOV W0
; Operate key to allow write operation
DISI #5 ; Block all interrupts with priority <7
MOV #0x55,W0
MOV W0
MOV #0xAA,W1
MOV W1
BSET NVMCON,#WR ; Initiate program sequence
NOP
NOP
; Write cycle will complete in 2mS. CPU is not stalled for the Data Write Cycle
; User can poll WR bit, use NVMIF or Timer IRQ to determine write complete
TBLPAG
,
[ W0] ; Write data
,
NVMCON
,
; for next 5 instructions
NVMKEY ; Write the 0x55 key
,
NVMKEY ; Write the 0xAA key
,
© 2006 Microchip Technology Inc. DS70118G-page 51
Page 54

dsPIC30F2010
7.3.2 WRITING A BLOCK OF DATA EEPROM
To write a block of data EEPROM, write to all sixteen
latches first, then set the NVMCON register and
program the block.
EXAMPLE 7-5: DATA EEPROM BLOCK WRITE
MOV #LOW_ADDR_WORD,W0 ; Init pointer
MOV #HIGH_ADDR_WORD,W1
MOV W1
MOV #data1,W2 ; Get 1st data
TBLWTL W2
MOV #data2,W2 ; Get 2nd data
TBLWTL W2
MOV #data3,W2 ; Get 3rd data
TBLWTL W2
MOV #data4,W2 ; Get 4th data
TBLWTL W2
MOV #data5,W2 ; Get 5th data
TBLWTL W2
MOV #data6,W2 ; Get 6th data
TBLWTL W2
MOV #data7,W2 ; Get 7th data
TBLWTL W2
MOV #data8,W2 ; Get 8th data
TBLWTL W2
MOV #data9,W2 ; Get 9th data
TBLWTL W2
MOV #data10,W2 ; Get 10th data
TBLWTL W2
MOV #data11,W2 ; Get 11th data
TBLWTL W2
MOV #data12,W2 ; Get 12th data
TBLWTL W2
MOV #data13,W2 ; Get 13th data
TBLWTL W2
MOV #data14,W2 ; Get 14th data
TBLWTL W2
MOV #data15,W2 ; Get 15th data
TBLWTL W2
MOV #data16,W2 ; Get 16th data
TBLWTL W2
MOV #0x400A,W0 ; Select data EEPROM for multi word op
MOV W0
DISI #5 ; Block all interrupts with priority <7
MOV #0x55,W0
MOV W0
MOV #0xAA,W1
MOV W1
BSET NVMCON,#WR ; Start write cycle
NOP
NOP
TBLPAG
,
[ W0]++ ; write data
,
[ W0]++ ; write data
,
[ W0]++ ; write data
,
[ W0]++ ; write data
,
[ W0]++ ; write data
,
[ W0]++ ; write data
,
[ W0]++ ; write data
,
[ W0]++ ; write data
,
[ W0]++ ; write data
,
[ W0]++ ; write data
,
[ W0]++ ; write data
,
[ W0]++ ; write data
,
[ W0]++ ; write data
,
[ W0]++ ; write data
,
[ W0]++ ; write data
,
[ W0]++ ; write data. The NVMADR captures last table access address.
,
NVMCON ; Operate Key to allow program operation
,
; for next 5 instructions
NVMKEY ; Write the 0x55 key
,
NVMKEY ; Write the 0xAA key
,
7.4 Write Verify
Depending on the application, good programming
practice may dictate that the value written to the memory should be verified against the original value. This
should be used in applications where excessive writes
can stress bits near the specification limit.
7.5 Protection Against Spurious Write
There are conditions when the device may not want to
write to the data EEPROM memory. To protect against
spurious EEPROM writes, various mechanisms have
been built-i n. On power-up, th e WREN bit is cleared;
also, the Power-up Ti mer prevents EEPROM write.
The write initiate sequence and the WREN bi t tog eth er
help prevent an accidental write during brown-out,
power glitch or software malfunction.
DS70118G-page 52 © 2006 Microchip Technology Inc.
Page 55

dsPIC30F2010
8.0 I/O PORTS
Note: This data sheet summarizes features of this g roup
of dsPIC30F devices and is not intended to be a complete
reference source. For more information on the CPU,
peripherals, register descriptions and general device
functionality, refer to the “dsPIC30F Family Reference
Manual” (DS70046).
All of the device pins (except VDD, VSS, MCLR and
OSC1/CLKI) are shared between the peripherals and
the parallel I/O ports.
All I/O input ports feature Schmitt Trigger inputs for
improved noise immunity.
8.1 P a ra llel I/O (PIO) Po rts
When a peripheral is enabled and the peripheral is
actively driving an associated pin, the use of the pin as
a general purpose output pin is disabled. The I/O pin
may be read, but the output driver for the parallel port
bit will be disabled. If a peripheral is enabled, but the
peripheral is not actively driving a pin, that pin may be
driven by a port.
All port pins have three registers directly associated
with the operation of the port pin. The data direction
register (TRISx) determ ines whe ther the pin is an inp ut
or an output. If the data direction bit is a ‘1’, then the pin
is an input. All port pins are defined as inputs after a
Reset. Reads from the latch (LATx), read the latch.
Writes to the latch, write the latch (LATx). Reads from
the port (PORTx), read the port pins, and writes to the
port pins, write the latch (LATx).
Any bit and its associated data and control registers
that are not valid for a particular device will be
disabled. That means the corresponding LATx and
TRISx registers and the port pin will read as zeros.
When a pin is shared with another peripheral or function that is defined as an input only, it is nevertheless
regarded as a dedicated port because there is no
other competing source of outputs. An example is the
INT4 pin.
A parallel I/O (PIO) port that shares a pin with a peripheral is, in general, subservient to the peripheral. The
peripheral’s output buffer data and control signals are
provided to a pair of multiplexers. The multiplexers
select whether the peripheral or the associated port
has ownership of the outp ut dat a and co ntro l sign als of
the I/O pad cell. Figu re 8-1 shows how po rts are shared
with other periphe rals, and th e associa ted I/O ce ll (pad)
to which they are connected. Table 8-1 shows the
formats of the registers fo r the shared po rts, PORTB
through PORTF.
FIGURE 8-1: BLOCK DIAGRAM OF A SHARED PORT STRUCTURE
Output Multiplexers
1
Output Enable
0
1
Output Dat a
0
Data Bus
WR TRIS
WR LAT +
WR Port
Peripheral Module
Peripheral Input Data
Peripheral Module Enable
Peripheral Output Enable
Peripheral Output Data
PIO Module
Read TRIS
QD
CK
TRIS Latch
QD
CK
Data Latch
I/O Cell
I/O Pad
Read LAT
Read Port
© 2006 Microchip Technology Inc. DS70118G-page 53
Input Data
Page 56

dsPIC30F2010
8.2 Configuring Analog Port Pins
The use of the ADPCFG and TRIS reg isters co ntrol the
operation of the A/D port pins. The port pins that are
desired as analog inputs must have their corresponding TRIS bit set (input). If the TRIS bit is cleared (output), the digital output level (V
converted.
When reading the POR T regist er , all pins c onfigured as
analog input channe l will read as cleare d (a low lev el).
Pins configured as digi tal inputs will not convert an an alog input. Analog levels on any pin that is defined as a
digital input (including the ANx pins), may cause the
input buffer to consume current that exceeds the
device specifications.
8.2.1 I/O PORT WRITE/READ TIMING
One instruction cycle is required between a port
direction change or port write operation and a read
operation of the same port. Typically this instruction
would be a NOP.
EXAMPLE 8-1: PORT WRITE/READ
EXAMPLE
MOV 0xFF00, W0; Configure PORTB<15:8>
; as inputs
MOV W0, TRISBB; and PORTB<7:0> as outputs
NOP ; Delay 1 cycle
btssPORTB, #13; Next Instruction
OH or VOL) will be
8.3 Input Change Notification Module
The Input Change Notification module provides the
dsPIC30F devices the ability to generate interrupt
requests to the processor in response to a change-ofstate on selected input pins. This module is capable of
detecting input change-of-states even in Sleep mode,
when the clocks are disa bled. The re are up to 22 external signals (CN0 through CN21) that may be selected
(enabled) for generating an interrupt request on a
change-of-state.
DS70118G-page 54 © 2006 Microchip Technology Inc.
Page 57

© 2006 Microchip Technology Inc. DS70118G -page 55
TABLE 8-1: dsPIC30F2010 PORT REGISTER MAP
SFR Name Addr. Bit 15 Bit 14 Bit 13 Bit 12 Bit 11 Bit 10 Bit 9 Bit 8 Bit 7 Bit 6 Bit 5 Bit 4 Bit 3 Bit 2 Bit 1 Bit 0 Reset State
TRISB 02C6
PORTB 02C8
LATB 02CA
TRISC 02CC TRISC15 TRISC14 TRISC13
PORTC 02CE RC15 RC14 RC13
LATC 02D0 LATC15 LATC14 LATC13
TRISD 02D2
PORTD 02D4
LATD 02D6
TRISE 02D8
PORTE 02DA
LATE 02DC
TRISF 02DE
PORTF 02E0
LATF 02E2
— — — — — — — — — —
— — — — — — — — — —
— — — — — — — — — —
— — — — — — — — — — — — — —
— — — — — — — — — — — — — —
— — — — — — — — — — — — — —
— — — — — — —
— — — — — — —
— — — — — — —
— — — — — — — — — — — —
— — — — — — — — — — — —
— — — — — — — — — — — —
TRISB5 TRISB4 TRISB3 TRISB2 TRISB1 TRISB0
RB5 RB4 RB3 RB2 RB1 RB0
LATB5 LATB4 LATB3 LATB2 LATB1 LATB0
— — — — — — — — — — — — — 1110 0000 0000 0000
— — — — — — — — — — — — — 0000 0000 0000 0000
— — — — — — — — — — — — — 0000 0000 0000 0000
TRISD1 TRISD0
RD1 RD0
LATD1 LATD0
TRISE8
RE8
LATE8
— —
— —
— —
TRISE5 TRISE4 TRISE3 TRISE2 TRISE1 TRISE0
RE5 RE4 RE3 RE2 RE1 RE0
LATE5 LATE4 LATE3 LATE2 LATE1 LATE0
TRISF3 TRISF2
RF3 RF2
LATF3 LATF2
— — 0000 0000 0000 1100
— — 0000 0000 0000 0000
— — 0000 0000 0000 0000
0000 0000 0011 1111
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0111
0000 0000 0000 0000
0000 0000 0000 0000
0000 0001 0011 1111
0000 0000 0000 0000
0000 0000 0000 0000
Legend: u = uninitialized bit
Note: Refer to “dsPIC30F Family Reference Manual” (DS70046) for descriptions of register bit fields.
TABLE 8-2: INPUT CHANGE NOTIFICATION REGISTER MAP (BITS 15-0)
SFR Name Addr. Bit 15 Bit 14 B it 13 Bit 12 Bit 11 Bit 10 Bit 9 Bit 8 Bit 7 Bit 6 Bit 5 Bit 4 Bit 3 Bit 2 Bit 1 Bit 0 Reset State
CNEN1 00C0 CN15IE CN14IE CN13IE CN12IE CN11IE CN10IE CN9IE CN8IE CN7IE CN6IE CN5IE CN4IE CN3IE CN2IE CN1IE CN0IE
CNEN2 00C2
CNPU1 00C4 CN15PUE CN14PUE CN13PUE CN12PUE CN11PUE CN10PUE CN9PUE CN8PUE CN7PUE CN6PUE CN5PUE CN4PUE CN3PUE CN2PUE CN1PUE CN0PUE
CNPU2 00C6
— — — — — — — — — —
— — — — — — — — — —
CN21IE CN20IE CN19IE CN18IE CN17IE CN16IE
CN21PUE CN20PUE CN19PUE CN18PUE CN17PUE CN16PUE
Legend: u = uninitialized bit
Note: Refer to “dsPIC30F Family Reference Manual” (DS70046) for descriptions of register bit fields.
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
dsPIC30F2010
Page 58

dsPIC30F2010
NOTES:
DS70118G-page 56 © 2006 Microchip Technology Inc.
Page 59

dsPIC30F2010
9.0 TIMER1 MODULE
Note: This data sheet summarizes features of this g roup
of dsPIC30F devices and is not intended to be a complete
reference source. For more information on the CPU,
peripherals, register descriptions and general device
functionality, refer to the “dsPIC30F Family Reference
Manual” (DS70046).
This section describes the 16-bit general purpose
Timer1 module and associated operational modes.
Figure 9-1 depicts the simplified block diagram of the
16-bit Timer1 Module.
Note: Timer1 is a ‘Type A’ timer. Please refer to
the specifications for a Type A timer in
Section 22.0 “Electrical Characteristics” of this document.
The following sec tions provid e a detailed descripti on of
the operational modes of the timers, including setup
and control registers along with associated block
diagrams.
The Timer1 module is a 16-bit timer which can serve as
the time counter fo r the rea l-time clo ck, o r operate as a
free running interval timer/coun ter . The 16-bit timer ha s
the following modes:
• 16-bit Timer
• 16-bit Synchronous Counter
• 16-bit Asynchronous Counter
Further, the following operational characteristics are
supported:
• Timer gate operation
• Selectable prescaler settings
• Timer operation during CPU Idle and Sleep
modes
• Interrupt on 16-bit period regi ster match or falling
edge of external gate signal
These operating modes are determined by sett ing the
appropriate bit(s) in the 16-bit SFR, T1CON. Figure 9-1
presents a block diagram of the 16-bit timer module.
16-bit Timer Mode: In t he 16-bi t T imer m ode, the timer
increments on every instruction cycle up to a match
value, preloaded into the period register PR1, then
resets to ‘0’ and continues to count.
When the CPU goes into the Idle mode, the timer will
stop incrementing unless the TSIDL (T1CON<13>)
bit = 0. If TSIDL = 1, the tim er module log ic will resume
the incrementing sequence upon termination of the
CPU Idle mode.
16-bit Synchronous Counter Mode: In the 16-bit
Synchronous Counter mode, the timer increments on
the rising edge of the applied external clock signal,
which is synchronized with the internal phase clocks.
The timer counts up to a match value preloade d in PR1,
then resets to ‘0’ and continues.
When the CPU goes into the Idle mode, the timer will
stop incrementing, unless the respective TSIDL bit = 0.
If TSIDL = 1, the timer module logic will resume the
incrementing sequence upon termination of the CPU
Idle mode.
16-bit Asynchronous Counter Mode: In the 16-bit
Asynchronous Counter mode, the timer increments on
every rising edge of the applied external clock signal.
The timer counts up to a match value preloade d in PR1,
then resets to ‘0’ and continues.
When the timer is co nfigured for the As ynchronous mod e
of operation and the CPU goes into the Idle mode, the
timer will stop incrementing if TSIDL = 1.
© 2006 Microchip Technology Inc. DS70118G-page 57
Page 60

dsPIC30F2010
FIGURE 9-1: 16-BIT TIMER1 MODULE BLOCK DIAGRAM (TYPE A TIMER)
PR1
Equal
T1IF
Event Flag
SOSCO/
T1CK
0
1
TGATE
Reset
LPOSCEN
Comparator x 16
TMR1
QDCKTGATE
Q
Gate
Sync
TCS
1 X
0 1
TGATE
(3)
TON
TSYNC
1
0
Sync
TCKPS<1:0>
2
Prescaler
1, 8, 64, 256
SOSCI
9.1 Timer Gate Operation
The 16-bit timer can be pl aced in the Ga ted Ti me Accumulation mo de. This mode allow s the internal T
CY to
increment the respectiv e timer when the ga te input signal (T1CK pin) is asserted high. Control bit TGATE
(T1CON<6>) must be set to enable this mode. The
timer must be enabled (TON = 1) and the timer clock
source set to internal (TCS = 0).
When the CPU goes into the Idle mode, the timer will
stop incrementing, unless TSIDL = 0. If TSIDL = 1, the
timer will resume the incrementing sequence upon
termination of the CPU Idle mode.
9.2 Timer Prescaler
The input clock (FOSC/4 or external clock) to the 16-bit
Timer, has a prescale option of 1:1, 1:8, 1:64, and
1:256 selected by control bits TCKPS<1:0>
(T1CON<5:4>). The pres ca le r co unter is cleared when
any of the following occurs:
• a write to the TMR1 register
• clearing of the TON bit (T1CON<15>)
• device Reset such as POR and BOR
However, if the timer is disabled (TON = 0), then the
timer prescaler cannot be reset since the prescaler
clock is halt ed.
TMR1 is not cleared when T1CON is written. It is
cleared by writing to the TMR1 register.
T
CY
0 0
9.3 Timer Operation During Sleep Mode
During CPU Sleep mode, the timer will operate if:
• The timer module is enabled (TON = 1) and
• The timer clock source is selected as external
(TCS = 1) and
• The TSYNC bit (T1CON<2>) is as serted to a logic
‘0’, which defines the external clock source as
asynchronous
When all three conditions are true, the timer will
continue to count u p to the period regi ster and be Reset
to 0x0000.
When a match between the timer and the period regis ter occurs, an interrupt can be generated, if the
respective timer interrupt enable bit is asserted.
DS70118G-page 58 © 2006 Microchip Technology Inc.
Page 61

dsPIC30F2010
9.4 Timer Interrupt
The 16-bit timer has the ability to ge nera t e an in terru pt
on period mat ch. When the timer count matches the
period register , th e T1IF bit is asse rted and an in terrupt
will be generated, if enabled. The T1IF bit must be
cleared in software. The timer interrupt flag T1IF is
located in the IFS0 control register in the Interrupt
Controller.
When the Gated Time Accumulation mode is enabled,
an interrupt will also be gen erated on the f alling edge of
the gate signal (at the end of the accumulation cycle).
Enabling an interrupt is accomplished via the respective timer interrupt enable bit, T1IE. The timer interrupt
enable bit is located in the IEC0 control register in the
Interrupt Controller.
9.5 Real-Time Clock
Timer1, when operating in Real-Time Clock (RTC)
mode, provides time-of-day and event time stamping
capabilities. Key operational features of the RTC are:
• Operation from 32 kHz LP oscillator
• 8-bit prescaler
• Low power
• Real-Time Clock Interrupts
• These Operating modes are determined by
setting the appropriate bit(s) in the T1CON
Control register
9.5.1 RTC OSCILLATOR OPERATION
When the TON = 1, T CS = 1 an d TGATE = 0, the timer
increments on the rising edge of the 3 2 k H z LP os c ill ator output signal, up to the val ue spec ified in the period
register, and is then Reset to ‘0’.
The TSYNC bit must be asserted to a logic ‘0’
(Asynchronous mode) for correct operation.
Enabling LPOSCEN (OSCCON<1>) will disable the
normal Timer and Counter modes, and enable a timer
carry-out wake-up event.
When the CPU enters Sleep mode, the RTC will continue to operate, provided the 32 kHz external crystal
oscillator is active and the control bits have not been
changed. The TSIDL bit should be cleared to ‘0’ in
order for RTC to continue operati on in Idle mode .
9.5.2 RTC INTERRUPTS
When an interrupt event occurs, the respective interrupt flag, T1IF, is asserted and an interrupt will be ge nerated, if enabled. The T1IF bit must be cleared in
software. The respective Timer interrupt flag, T1IF, is
located in the IFS0 status register in the Interrupt
Controller.
Enabling an interrupt is accomplished via the respective timer interrupt enable bit, T1IE. The T im er interrupt
enable bit is located in the IEC0 control register in the
Interrupt Controller.
FIGURE 9-2: RECOMMENDED
COMPONENTS FOR
TIMER1 LP OSCILLATOR
RTC
C1
SOSCI
32.768 kHz
XTAL
C2
C1 = C2 = 18 pF; R = 100K
R
dsPIC30FXXXX
SOSCO
© 2006 Microchip Technology Inc. DS70118G-page 59
Page 62

DS70118G-page 60 © 2006 Microchip Technology Inc.
TABLE 9-1: TIMER1 REGISTER MAP
SFR Name Addr. Bit 15 Bit 14 Bit 13 Bit 12 Bit 11 Bit 10 Bit 9 Bit 8 Bit 7 Bit 6 Bit 5 Bit 4 Bit 3 Bit 2 Bit 1 Bit 0 Reset State
TMR1 0100 Timer 1 Register
PR1 0 102 Period Register 1
T1CON 0104 TON
—TSIDL— — — — — — TGATE TCKPS1 TCKPS0 —TSYNCTCS —
uuuu uuuu uuuu uuuu
1111 1111 1111 1111
0000 0000 0000 0000
dsPIC30F2010
Legend: u = uninitialized bit
Note: Refer to “dsPIC30F Family Reference Manual” (DS70046) for descriptions of register bit fields.
Page 63

dsPIC30F2010
10.0 TIMER2/3 MODULE
Note: This data sheet summarizes features of this g roup
of dsPIC30F devices and is not intended to be a complete
reference source. For more information on the CPU,
peripherals, register descriptions and general device
functionality, refer to the “dsPIC30F Family Reference
Manual” (DS70046).
This section describes the 32-bit general purpose
Timer module (Timer2/3) and associated operational
modes. Figure 10-1 depicts the simplified block diagram of the 32-bit Timer2/3 module. Figure 10-2 and
Figure 10-3 show Timer2/3 configured as two
independent 16-bit timers; Timer2 and Timer3,
respectively.
Note: Timer2 is a ‘ Type B’ time r and Timer 3 is a
‘Type C’ timer. Please refer to the appropriate timer type in Section 22.0 “Electri-
cal Characteristics” of this document.
The Timer2/3 modul e is a 32-bit timer, which can be
configured as two 16-bit tim ers, with s elect abl e operating modes. These timers are utilized by other
peripheral modules such as:
• Input Capture
• Output Compare/Simpl e PWM
The following sections provide a detailed description,
including setup and control registers, along with associated block diagrams for the ope rati ona l mod es of the
timers.
The 32-bit timer has the following modes:
• Two independent 16-bit timers (Timer2 and
Timer3) with all 16-bit operat ing modes (except
Asynchronous Counter mode)
• Single 32-bit Timer operation
• Single 32-bit Synchronous Counter
Further, the following operational characteristics are
supported:
• ADC Event Trigger
• Timer Gate Operation
• Selectable Prescaler Settings
• Timer Operation during Idle and Sleep modes
• Interrupt on a 32-bit Period Register Match
These operating modes are determined by setting the
appropriate bit(s) in the 16-bit T2CON and T3CON
SFRs.
For 32-bit timer/counter operation, Timer2 is the least
significant word and Tim er3 is the mos t significant w ord
of the 32-bit timer.
Note: For 32-bit timer operation, T3CON control
bits are ignored. Only T2CON control bits
are used for setup and control. Timer 2
clock and gate inputs are utilized for the
32-bit timer module, but an interrupt is
generated with the Timer3 interrupt flag
(T3IF), and the interrupt is enabled with
the Timer3 interrupt enable bit (T3IE).
16-bit Mode: In the 16-bit mode, Timer2 and Timer3
can be configured as two independent 16-bit timers.
Each timer can be set up in ei ther 16-bit Timer mode or
16-bit Synchronous Counter mode. See Section 9.0
“Timer1 Module” for details on these two operating
modes.
The only functional difference between Timer2 and
Timer3 is that Timer2 provides synchronization of the
clock prescaler output . This is useful for high fre quency
external clock inputs.
32-bit Timer Mode: In t he 32-bi t T imer m ode, the timer
increments on every instruction cycle up to a match
value, preloaded int o the combi ned 32-bi t period register PR3/PR2, then resets to ‘ 0’ and co nti nues to count.
For synchronous 32-bit reads of the Timer2/Timer3
pair, reading the least significant word (TMR2 register)
will cause the most significant word (msw) to be read
and latched into a 16-bit holding register, termed
TMR3HLD.
For synchronous 32-bit writes, the holding register
(TMR3HLD) must first be written to. When followed by
a write to the TMR2 regi ster, the contents of TMR3HLD
will be transferred and latched into the MSB of the
32-bit timer (TMR3).
32-bit Synchronous Counter Mode: In the 32-bit
Synchronous Counter mode, the timer increments on
the rising edge of the applied external clock signal,
which is synchronized with the internal phase clocks.
The timer counts up to a match value preloaded in the
combined 32-bit period register PR3/PR2, then resets
to ‘0’ and continues.
When the timer is configured for the Synchronous
Counter mode of operation and the CPU goes into the
Idle mode, the timer will stop incrementing, unless the
TSIDL (T2CON<13>) bit = ‘0’. If TSIDL = ‘1’, the timer
module logic will resume the incrementing sequence
upon termination of the CPU Idle mode.
© 2006 Microchip Technology Inc. DS70118G-page 61
Page 64

dsPIC30F2010
FIGURE 10- 1: 32-BIT TIMER2 /3 B LOC K DI AG R AM
Data Bus<15:0>
Write TMR2
Read TMR2
ADC Event Trigger
T3IF
Event Flag
T2CK
0
1
TGATE
(T2CON<6>)
Reset
Equal
TMR3HLD
16
16
TMR3
MSB
Comparator x 32
PR3 PR2
16
TMR2
LSB
QD
CK
Q
TGATE(T2CON<6>)
TCS
1 X
Sync
TGATE
TON
TCKPS<1:0>
2
Gate
Sync
TCY
Note: Timer Configuration bit T32, T2CON(<3>) must be set to 1 for a 32-bit timer/count er operation. All control
bits are respective to the T2CON register.
0 1
0 0
Prescaler
1, 8, 64, 256
DS70118G-page 62 © 2006 Microchip Technology Inc.
Page 65

FIGURE 10-2: 16-BIT TIMER2 BLOCK DIAGRAM (TYPE B T I MER )
dsPIC30F2010
T2IF
Event Flag
T2CK
0
1
TGATE
Equal
Reset
PR2
Comparator x 16
TMR2
QDCKTGATE
Q
Gate
Sync
CY
T
TCS
1 X
0 1
0 0
TGATE
FIGURE 10-3: 16-BIT TIMER3 BLOCK DIAGRAM (TYPE C T I MER )
TON
Sync
TCKPS<1:0>
2
Prescaler
1, 8, 64, 256
ADC Event Trigger
T3IF
Event Flag
TGATE
Equal
Reset
0
1
See
NOTE
Note: The dsPIC30F2010 does not have an external pin input to TIMER3. The following modes should not be used:
1. TCS = 1
2. TCS = 0 and TGATE = 1 (gated time accumulation)
PR3
Comparator x 16
TMR3
QDCKTGATE
Q
Sync
T
CY
TCS
1 X
0 1
0 0
TGATE
TON
TCKPS<1:0>
2
Prescaler
1, 8, 64, 256
© 2006 Microchip Technology Inc. DS70118G-page 63
Page 66

dsPIC30F2010
10.1 Timer Gate Operation
The 32-bit timer can be pl aced in the Ga ted Ti me Accumulation mo de. This mode allow s the internal T
increment the respectiv e timer when the ga te input signal (T2CK pin) is asserted high. Control bit TGATE
(T2CON<6>) must be set to en able this mode . When in
this mode, Timer2 is the originating clock source. The
TGA TE setting is ignored for T imer3. The timer must b e
enabled (TON = 1) and the timer cl ock source set to
internal (TCS = 0).
The falling edge of the external signal terminates the
count operation, but does not res et the time r. The user
must reset the timer in ord er to start count ing from zero.
CY to
10.2 ADC Event Trigger
When a match occurs between th e 32-bit timer (TMR 3/
TMR2) and the 32-bit combined period register (PR3/
PR2), a special ADC trigger event signal is generated
by Timer3.
10.3 Timer Prescaler
The input cloc k (FOSC/4 or external clock) to the timer
has a prescale option of 1:1, 1:8, 1:64, and 1:256
selected by control bits TCKPS<1:0> (T2CON<5:4>
and T3CON<5:4>). For the 32-bit timer operation, the
originating clock source is Timer2. The prescale r operation for Timer3 is not applicable in this mode. The
prescaler counter is cleared when any of the following
occurs:
• a write to the TMR2/TMR3 register
• clearing either of the TON (T2CON<15> or
T3CON<15>) bits to ‘0’
• device Reset such as POR and BOR
However, if the timer is disabled (TON = 0), then the
Timer 2 prescaler cannot be reset, since the prescaler
clock is halt ed.
TMR2/TMR3 is not cleared when T2CON/T3CON is
written.
10.4 Timer Operation During Sleep Mode
During CPU Sleep mode, the timer will not operate,
because the internal clocks are disabled.
10.5 Timer Interrupt
The 32-bit timer module can generate an interrupt on
period match, or on the fa lling edge of the external gate
signal. When the 32-bit timer count matches the
respective 32-bit period register, or the falling edge of
the external “gate” signal is detected, the T3IF bit
(IFS0<7>) is asserted a nd an interru pt will be gene rated if enabled. In this mode, the T3IF interrupt flag is
used as the source of the interrupt. The T3IF bit must
be cleared in software.
Enabling an interrupt is accomplished via the
respective timer interrupt enable bit, T3IE (IEC0<7>).
DS70118G-page 64 © 2006 Microchip Technology Inc.
Page 67

© 2006 Microchip Technology Inc. DS70118G -page 65
TABLE 10-1: TIMER2/3 REGISTER MAP
SFR Name Addr. Bit 15 Bit 14 Bit 13 Bit 12 Bit 11 Bit 10 Bit 9 Bit 8 Bit 7 Bit 6 Bit 5 Bit 4 Bit 3 Bit 2 Bit 1 Bit 0 Reset State
TMR2 0106 Timer2 Register
TMR3HLD 0108 Timer3 Holding Register (For 32-bit timer operations only)
TMR3 010A Timer3 Register
PR2 010C Period Register 2
PR3 010E Period Register 3
T2CON 0110 TON
T3CON 0112 TON
—TSIDL— — — — — — TGATE TCKPS1 TCKPS0 T32 —TCS—
—TSIDL— — — — — — TGATE TCKPS1 TCKPS0 — —TCS —
Legend: u = uninitialized bit
Note: Refer to “dsPIC30F Family Reference Manual” (DS70046) for descriptions of register bit fields.
uuuu uuuu uuuu uuuu
uuuu uuuu uuuu uuuu
uuuu uuuu uuuu uuuu
1111 1111 1111 1111
1111 1111 1111 1111
0000 0000 0000 0000
0000 0000 0000 0000
dsPIC30F2010
Page 68

dsPIC30F2010
NOTES:
DS70118G-page 66 © 2006 Microchip Technology Inc.
Page 69

dsPIC30F2010
11.0 INPUT CAPTURE MODULE
The key operational features of the Input Capture
module are:
Note: This data sheet summarizes features of this g roup
of dsPIC30F devices and is not intended to be a complete
reference source. For more information on the CPU,
peripherals, register descriptions and general device
functionality, refer to the “dsPIC30F Family Reference
Manual” (DS70046).
This section describes the Input Capture module and
associated operational modes. The features provided
by this module are useful in applications requiring Frequency (Period) and Pulse measurement. Figure 11-1
• Simple Capture Event mode
• Timer2 and Timer3 mode selection
• Interrupt on input capture event
These operating modes are determined by setting the
appropriate bits in the ICxCON register (where x =
1,2,...,N). The dsPIC DSC devices contain up to 8
capture channels, (i.e., the maximum value of N is 8).
Note: The dsPIC30F2010 device has four
depicts a block diagram of the Input Capture module.
Input capture is useful for such modes as:
• Frequency/Period/Pulse Measurements
• Additional sources of External Interrupts
FIGURE 11-1: INPUT CAPTURE MODE BLOCK DIAGRAM
From General Purpose Timer Module
capture inputs – IC1, IC2, IC7 and IC8.
The naming of these four capture channels is intentional and preserves software
compatibility with other dsPIC DSC
devices.
T2_CNT
T3_CNT
16 16
ICx
Pin
Prescaler
1, 4, 16
3
Synchronizer
ICM<2:0>
Mode Select
ICBNE, ICOV
ICxCON
Data Bus
Clock
ICI<1:0>
Edge
Detection
Logic
Interrupt
Logic
Set Flag
Set Flag
ICxIF
ICxIF
10
FIFO
R/W
Logic
ICxBUF
ICTMR
Note: Where ‘x’ is shown, refere nce i s m ade to the registers or bits associated to t he res pe cti ve i npu t
capture channels 1 through N.
© 2006 Microchip Technology Inc. DS70118G-page 67
Page 70

dsPIC30F2010
11.1 Simple Capture Event Mode
The simple capture events in the dsPIC30F product
family are:
• Capture every falling edge
• Capture every rising edge
• Capture every 4th rising edge
• Capture every 16th rising edge
• Capture every rising and falling edge
These simple Input Capture modes are configured by
setting the appropriate bits ICM<2:0> (ICxCON<2:0>).
11.1.1 CAPTURE PRESCALER
There are four input capture prescaler settings, specified by bits ICM<2:0> (ICxCON<2:0>). Whenever the
capture channel is turn ed of f, the pr esc aler coun ter will
be cleared. In addition, any Reset will clear the
prescaler counter.
11.1.2 CAPTURE BUFFER OPERATION
Each capture channel has an associated FIFO buffer,
which is four 16-bit words deep. There are two status
flags, which provide status on the FIFO buffer:
• ICBNE – Input Capture Buffer Not Empty
• ICOV – Input Capture Overflow
The ICBFNE will be set on the first input capture event
and remain set until all capture events have been read
from the FIFO. As each word is read fro m the FIFO, the
remaining words are advanced by one position within
the buffer.
In the event that the FIFO is full with four capture
events and a fifth capture event occurs prior to a read
of the FIFO, an overflow conditio n will occur and the
ICOV bit will be set to a lo gic ‘1’. The fifth capture event
is lost and is not stored in the FIFO. No additional
events will be captured until all four events have been
read from the buffer.
If a FIFO read is performed after the last read and no
new capture event has been received, the read will
yield indet erminate re sults.
11.1.3 TIMER2 AND TIMER3 SELECTION
MODE
The input capture modu le c onsis ts of up to 8 input capture channels. Each ch annel can select between one of
two timers for the time base, Timer2 or Timer3.
Selection of the timer resource is accomplished
through SFR bit ICTMR (ICxCON<7>). Timer3 is the
default timer resource available for the input capture
module.
11.1.4 HALL SENSOR MODE
When the input capture module is set for capture on
every edge, rising and fal ling, ICM <2:0> = 001, the fol-
lowing operations are performed by the input capture
logic:
• The input capture interrupt flag is set on every
edge, rising and falling.
• The interrupt on Capture mode setting bits,
ICI<1:0>, is ignored, since every capture
generates an interrupt.
• A capture overflow condition is not generated in
this mode.
DS70118G-page 68 © 2006 Microchip Technology Inc.
Page 71

dsPIC30F2010
11. 2 Input Capture Operation During Sleep and Idle Modes
An input capture event will generate a device wake-up
or interrupt, if enabled, if the device is in CPU Idle or
Sleep mode.
Independent of the timer being enabled, the input
capture module will wake-up from the CPU Sleep or
Idle mode when a capture event occurs, if ICM<2:0> =
111 and the interrupt enable bit is as s erte d. The sam e
wake-up can generate an int errupt, if the conditi ons for
processing the interrupt have been satisfied. The
wake-up feature is useful as a method of adding extra
external pin interrupts.
11.2.1 INPUT CAPTURE IN CPU SLEEP
MODE
CPU Sleep mode allows input capture module operation with reduced functionality. In the CPU Sleep
mode, the ICI<1:0> bits are not applicable, and the
input capture module can only function as an external
interrupt source.
The capture module must be configured for interrupt
only on the rising edge (ICM<2:0> = 111), in order for
the input capture module to be used while the device
is in Sleep m ode. Th e presca le set ting s of 4:1 or 16:1
are not applicable in this mode.
11.2.2 INPUT CAPTURE IN CPU IDLE MODE
CPU Idle mode allows input capture module operation
with full functionality. In the CPU Idle mode, the interrupt
mode selected by the ICI<1:0> bits are applicable, as
well as the 4:1 and 16:1 capture prescale settings,
which are defined by control bits ICM<2:0>. This mode
requires the selected timer to be enabled. Moreover , the
ICSIDL bit must be asserted to a logic ‘0’.
If the inpu t capture mo dule is defi ned as ICM<2 :0> =
111 in CPU Idle mode, the input capture pin will serve
only as an external interrupt pin.
11.3 Input Capture Interrupt s
The input capture c hannels have the a bility to generate
an interrupt, based upon the selected number of capture events. The s ele ction number is set by control bits
ICI<1:0> (ICxCON<6:5>).
Each channel provides an interrupt flag (ICxI F) bit. The
respective capture channel interrupt flag is located in
the corresponding IFSx status register.
Enabling an interrupt is accomplished via the respective capture channel interrupt enable (ICxIE) bit. The
capture interrupt enable bit is located in the
corresponding IEC Control register.
© 2006 Microchip Technology Inc. DS70118G-page 69
Page 72

DS70118G-page 70 © 2006 Microchip Technology Inc.
TABLE 11-1: INPUT CAPTURE REGISTER MAP
SFR Name Addr. Bit 15 Bit 14 Bit 13 Bit 12 Bit 11 Bit 10 Bit 9 Bit 8 Bit 7 Bit 6 Bit 5 Bit 4 Bit 3 Bit 2 Bit 1 Bit 0 Reset State
IC1BUF 0140 Input 1 Capture Register
IC1CON 0142 — —ICSIDL— — — — — ICTMR ICI<1:0> ICOV ICBNE ICM<2:0>
IC2BUF 0144 Input 2 Capture Register
IC2CON 0146 — —ICSIDL— — — — — ICTMR ICI<1:0> ICOV ICBNE ICM<2:0>
IC3BUF 0148 Input 3 Capture Register
IC3CON 014A — —ICSIDL— — — — — ICTMR ICI<1:0> ICOV ICBNE ICM<2:0>
IC4BUF 014C Input 4 Capture Register
IC4CON 014E — —ICSIDL— — — — — ICTMR ICI<1:0> ICOV ICBNE ICM<2:0>
IC5BUF 0150 Input 5 Capture Register
IC5CON 0152 — —ICSIDL— — — — — ICTMR ICI<1:0> ICOV ICBNE ICM<2:0>
IC6BUF 0154 Input 6 Capture Register
IC6CON 0156 — —ICSIDL— — — — — ICTMR ICI<1:0> ICOV ICBNE ICM<2:0>
IC7BUF 0158 Input 7 Capture Register
IC7CON 015A — —ICSIDL— — — — — ICTMR ICI<1:0> ICOV ICBNE ICM<2:0>
IC8BUF 015C Input 8 Capture Register
IC8CON 015E — —ICSIDL— — — — — ICTMR ICI<1:0> ICOV ICBNE ICM<2:0>
uuuu uuuu uuuu uuuu
0000 0000 0000 0000
uuuu uuuu uuuu uuuu
0000 0000 0000 0000
uuuu uuuu uuuu uuuu
0000 0000 0000 0000
uuuu uuuu uuuu uuuu
0000 0000 0000 0000
uuuu uuuu uuuu uuuu
0000 0000 0000 0000
uuuu uuuu uuuu uuuu
0000 0000 0000 0000
uuuu uuuu uuuu uuuu
0000 0000 0000 0000
uuuu uuuu uuuu uuuu
0000 0000 0000 0000
dsPIC30F2010
Legend: u = uninitialized bit
Note: Refer to “dsPIC30F Family Reference Manual” (DS70046) for descriptions of register bit fields.
Page 73

dsPIC30F2010
12.0 OUTPUT COMPARE MODULE
The key operational features of the Output Compare
module include:
Note: This data sheet summarizes features of this g roup
of dsPIC30F devices and is not intended to be a complete
reference source. For more information on the CPU,
peripherals, register descriptions and general device
functionality, refer to the “dsPIC30F Family Reference
Manual” (DS70046).
This section describes the Output Compare module
and associated operational modes. The features provided by this modu le are useful in applications requiring
operational modes such as:
• Generation of Variable Width Output Pulses
• Power Factor Correction
Figure 12-1 depicts a block diagram of the Output
Compare module.
• Timer2 and Timer3 Selection mode
• Simple Output Compare Match mode
• Dual Output Compare Match mode
• Simple PWM mode
• Output Compare during Sleep and Idle modes
• Interrupt on Output Compare/PWM Event
These operating modes are determined by setting
the appropriate bit s in the 16-bit O CxCON SFR (where
x = 1 and 2).
OCxRS and OCxR in the figure represent the Dual
Compare registers. In the Dual Compare mode, the
OCxR register is used for th e first comp are and OCxRS
is used for the second compare.
FIGURE 12-1: OUTPUT COMPAR E MODE BL OC K DIAGR AM
Set Flag bit
OCxRS
OCxIF
From General Purpose
Timer Module
Comparator
0
TMR2<15:0>
OCxR
TMR3<15:0>
Output
Logic
3
OCM<2:0>
Mode Select
OCTSEL
1
0
T2P2_MATCH
1
T3P3_MATCH
QS
R
Output Enable
OCx
OCFA
(for x = 1 and 2)
Note: Where ‘x’ is shown, reference is made to the registers associated with the respective output compare
channels 1and 2.
© 2006 Microchip Technology Inc. DS70118G-page 71
Page 74

dsPIC30F2010
12.1 Timer2 and Timer3 Selection Mode
Each output compare channel can select between one
of two 16-bit timers: Timer2 or Timer3.
The selection of t he timers is con trolled by the O CTSEL
bit (OCxCON<3>). T imer2 is the de fault ti mer reso urce
for the Output Compare module.
12.2 Simple Output Compare Match Mode
When control bits OCM<2:0> (OCxCON<2:0>) = 001,
010 or 011, the selected output compare channel is
configured for one of three simple Output Compare
Match modes:
• Compare forces I/O pin low
• Compare forces I/O pin high
• Compare toggles I/O pin
The OCxR register is us ed in th es e m ode s. Th e O C xR
register is loaded with a value and is compared to the
selected inc rementing timer cou nt. When a compare
occurs, one of these Compare Match modes occurs. If
the counter resets to zero before reaching the value in
OCxR, the state of the OCx pin remains unchanged.
12.3 Dual Output Compare Match Mode
When control bits OCM<2:0> (OCxCON<2:0>) = 100
or 101, the selected output co mp are chan nel is co nfigured for one of two Dual Output Compare modes,
which are:
• Single Output Pulse mode
• Continuous Output Pulse mode
12.3.1 SINGLE PULSE MODE
For the user to configure the modul e for the ge ner ation
of a single output pulse, the following steps are
required (assuming timer is off):
• Determine instruction cycle time T
• Calculate desired pulse width value based on T
• Calculate time to s tart pul se from time r sta rt valu e
of 0x0000.
• Write pulse width start and stop times into OCxR
and OCxRS compare registers (x denotes
channel 1, 2).
• Set timer period register to value equal to, or
greater than, value in OCxRS compare register.
• Set OCM<2:0> = 100.
• Enable timer, TON (TxCON<15>) = 1.
To initiate another s ingle pul se, issue a nother wr ite to
set OCM<2:0> = 100.
CY.
CY.
12.3.2 CONTINUOUS PULSE MODE
For the user to configure the modul e for the ge neratio n
of a continuous stream of output pulses, the following
steps are required:
• Determine instruction cycle time T
• Calculate desired pulse value based on TCY.
• Calculate timer to start pul se width fro m timer sta rt
value of 0x0000.
• Write pulse width start and stop times into OCxR
and OCxRS (x denotes channel 1, 2) compare
registers, respectively.
• Set timer period register to value equal to, or
greater than, value in OCxRS compare register.
• Set OCM<2:0> = 101.
• Enable timer, TON (TxCON<15>) = 1.
CY .
12.4 Simple PWM Mode
When control bits OCM<2:0> (OCxCON<2:0>) = 110
or 111, the select ed outp ut comp are c hannel is confi gured for the PWM mode of operatio n. When confi gured
for the PWM mode of ope ration, OCxR is the main latch
(read-only) and OCxRS is the secondary latch. This
enables glitchless PWM transitions.
The user must perform the following steps in order to
configure the output compare module for PWM
operation:
1. Set the PWM period by writing to the appropriate
period register.
2. Set the PWM duty cycle by writing to the O CxRS
register.
3. Configure the output compare module for PWM
operation.
4. Set the TMRx prescale value and enable the
Timer, TON (TxCON<15>) = 1.
12.4.1 INPUT PIN FAULT PROTECTION
FOR PWM
When control bits OCM<2:0> (OCxCON<2:0>) = 111,
the selected output compare channel is again configured for the PWM mode of operation, with the
additional feature of input fault protection. While in this
mode, if a logic ‘0’ is detected on the OCFA/B pin, the
respective PWM outpu t pin is plac ed in the hig h-impedance input state. The OCFLT bit (OCxCON<4>)
indicates whether a Fault condition has occurred. This
state will be maintained until both of the following
events have occurred:
• The external Fault condition has been removed.
• The PWM mode has been re-enabled by writing
to the appropriate control bits.
DS70118G-page 72 © 2006 Microchip Technology Inc.
Page 75

dsPIC30F2010
12.4.2 PWM PERIOD
The PWM period is specifie d by writing to the PRx register. The PWM period can be calculated using
Equation 12-1.
EQUATION 12-1: PWM PERIOD
PWM period = [(PRx) + 1] • 4 • T
(TMRx prescale value)
PWM frequency is defined as 1 / [PWM period].
When the selected TMRx is equal to its respective
period register, PRx, the following four events occur on
the next increment cycle:
• TMRx is cleared.
• The OCx pin is set.
- Exception 1: If PWM duty cycle is 0x0000,
the OCx pin will remain low.
- Exception 2: If duty cycle is greater than PRx,
the pin will remain high.
• The PWM duty cycle is latched from OCxRS into
OCxR.
• The corresponding timer interrupt flag is set.
See Figure 12-1 for key PWM period comparisons.
Timer3 is referred to in the figure for clarity.
OSC •
12.5 Output Compare Operation During CPU Sleep Mode
When the CPU enters the Sleep mode, all internal
clocks are stopped. Therefore, when the CPU enters
the Sleep state, the output compare channel will drive
the pin to the active state that was observed prior to
entering the CPU Sleep state.
For example, if the pin was high when the CPU
entered the Sleep state, the pin will remain high. Likewise, if the pin was low when the CPU entered the
Sleep state, the pin will remain low. In either case, the
output compare module will resume operation when
the device wakes up.
12.6 Output Compare Operation During CPU Idle Mode
When the CPU enters the Idle mode, the output
compare module can operate with full functionality.
The output compare channel will operate during the
CPU Idle mode if the OCSIDL bit (OCxCON<13>) is at
logic ’0’ and the s el ect ed time base (T im er2 or Timer3)
is enabled and the TSIDL bit of the selected timer is
set to logic ‘0’.
FIGURE 12-1: PWM OUTPUT TIMING
Period
Duty Cycle
TMR3 = PR3
T3IF = 1
(Interrupt Flag)
OCxR = OCxRS
TMR3 = Duty Cycle (OCxR)
12.7 Output Compare Interrupts
The output comp are channels have the abi lity to generate an interrupt on a compare match, for whichever
Match mode has been selected.
For all modes except the PWM mode, when a compare
event occurs, the respective interrupt flag (OCxIF) is
asserted and an interru pt wil l b e ge nerated, if enabled.
The OCxIF bit is located in the corresponding IFS
status register, and must be cleared in software. The
interrupt is enabled via the respective compare interrupt enable (OCxIE) bit, located in the corresponding
IEC Control register .
TMR3 = PR3
T3IF = 1
(Interrupt Flag)
OCxR = OCxRS
TMR3 = Duty Cycle (OCxR)
For the PWM mode, when a n event occu rs, the respective timer interrupt flag (T2IF or T3IF) is asserted and
an interrupt will be generated, if enabled. The IF bit is
located in the IFS0 st atus re gister, and must be cleared
in software. The interrupt is enabled via the respective
timer interrupt enable bit (T2IE or T3IE), located in the
IEC0 Control register. The output compare interrupt
flag is never set during the PWM mode of operation.
© 2006 Microchip Technology Inc. DS70118G-page 73
Page 76

DS70118G-page 74 © 2006 Microchip Technology Inc.
TABLE 12-1: OUTPUT COMPARE REGISTER MAP
SFR Name Addr. Bit 15 Bit 14 Bit 13 Bit 12 Bit 11 Bit 10 Bit 9 Bit 8 Bit 7 Bit 6 Bit 5 Bit 4 Bit 3 Bit 2 Bit 1 Bit 0 Reset State
OC1RS 0180 Output Compare 1 Master Register
OC1R 0182 Output Compare 1 Slave Register
OC1CON 0184
OC2RS 0186 Output Compare 2 Master Register
OC2R 0188 Output Compare 2 Slave Register
OC2CON 018A
— OCFRZ OCSIDL — — — — — — — — OCFLT1 OCTSEL1 OCM<2:0>
— OCFRZ OCSIDL — — — — — — — — OCFLT2 OCTSEL2 OCM<2:0>
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
dsPIC30F2010
Legend: u = uninitialized bit
Note: Refer to “dsPIC30F Family Reference Manual” (DS70046) for descriptions of register bit fields.
Page 77

dsPIC30F2010
13.0 QUADRATURE ENCODER INTERFACE (QEI) MODULE
Note: This data sheet summarizes features of this g roup
of dsPIC30F devices and is not intended to be a complete
reference source. For more information on the CPU,
peripherals, register descriptions and general device
functionality, refer to the “dsPIC30F Family Reference
Manual” (DS70046).
This section describes the Quadrature Encoder Interface (QEI) module and associated operational modes.
The QEI module provides the interface to incremental
encoders for obtaining motor positioning data. Incremental encoders are very useful in motor control
applications.
The Quadrature Encoder Interface (QEI) is a key feature requirement for several motor con trol applicati ons,
such as Switched Reluctance (SR) and AC Induction
Motor (ACIM). The o pera tio nal fe atu res o f th e QEI are,
but not limited to:
• Three input channels for two phase signals and
index pulse
• 16-bit up/down position counter
• Count direction status
• Position Measurement (x2 and x4) mode
• Programmable digital noise filters on inputs
• Alternate 16-bit Timer/Counter mode
• Quadrature Encoder Interface interrupts
These operating modes are determined by setting the
appropriate bits QEIM<2:0> (QEICON<10:8>).
Figure 13-1 depicts the Quadrature Encoder Interface
block diagram.
FIGURE 13-1: QUADRATURE ENCOD ER IN TERF ACE BL OCK DI AGRA M
Sleep Input
Synchronize
Det
TQCS
CY
T
QEIM<2:0 >
0
1
1
0
TQCKPS<1:0>
2
Prescaler
1, 8, 64, 256
QEA
QEB
INDX
Programmable
Digita l Filter
UPDN_SRC
QEICON<11>
0
1
Programmable
Digital Filter
Programmable
Digital Filter
3
Quadrature
Encoder
Interface Logic
QEIM<2:0 >
Mode Se le ct
TQGATE
3
CK
16-bit Up/Down Counter
2
Comparator/
Zero Detect
Max Count Register
QD
Q
(POSCNT)
(MAXCNT)
Reset
Equal
QEIIF
Event
Flag
© 2006 Microchip Technology Inc. DS70118G-page 75
Page 78

dsPIC30F2010
13.1 Quadrature Encoder Interface Logic
A typical increment a l (a.k .a . opt ic al) e nc ode r has thre e
outputs: Phase A, Phase B, and an index pulse. These
signals are useful and often required in position and
speed control of ACIM and SR motors.
The two channels, Phase A (QEA) and Phase B (QEB),
have a unique relationship. If Phase A leads Phase B,
then the direction (of the motor) is deemed positive or
forward. If Phase A lags Phase B, then the direction (of
the motor) is deemed negative or reverse.
A third channel, termed index pulse, occurs once per
revolution and is used as a reference to establish an
absolute position. The index pulse coincides with
Phase A and Phase B, both low.
13.2 16-bit Up/Down Position Counter Mode
The 16-bit Up/Down Counter counts up or down on
every count pu lse, wh ich is generated by the diff erence
of the Phase A and Phase B input signals. The counter
acts as an in tegrator, whose count value is prop ortional
to position. The direction of the count is determined by
the UPDN signal, which is generated by the
Quadrature Encoder Interface Log ic.
13.2.1 POSITION COUNTER ERROR
CHECKING
Position count error checking in the QE I i s p rov ide d for
and indicated by the CNTER R bit (QEICO N<15>). The
error checking only applies when the position counter
is configured for Reset on the Index Pulse modes
(QEIM<2:0> = ‘110’ or ‘100’). In these modes, the
contents of the POSCNT register is compared with the
values (0xFFFF or MAXCNT + 1, depending on direc tion). If these value s ar e de tec ted , an e rror c ond iti on i s
generated by setting the CNTERR bit and a QEI count
error interrupt is generated. The QEI count error
interrupt can be disabled by setting the CEID bit
(DFLTCON<8>). The position counter continues to
count encoder edges after an err or has been detecte d.
The POSCNT register conti nues to count up/do wn until
a natural rollover/underflow. No interrupt is generated
for the natural rollover/underflow event. The CNTERR
bit is a read/write bit and reset in software by the user.
13.2.2 POSITION COUNTER RESET
The Position Counter Reset Enable bit, POSRES
(QEI<2>) controls wheth er the positi on co unter i s reset
when the index pulse is detected. This bit is only
applicable when QEIM<2:0> = ‘100’ or ‘110’.
If the POSRES bit is set to ‘1’, then the p osition count er
is reset when the index pulse is detected. If the
POSRES bit is set to ‘0’, then the position counter is not
reset when the index pulse is detected. The position
counter will continue counting up or down, and will be
reset on the rollover or underflow condition.
When selecting the INDX signal to reset the position
counter (POSCNT), the user has to specify the states
on QEA and QEB input pins. These states have to be
matched in order for a reset to occur. These states are
selected by the IMV<1:0> bit in the DFLTCON <10:9>
register.
The IMV<1:0> (Index Match Value) bit allows the user
to specify the state of the QEA and QEB input pins
during an index pulse when the POSCNT register is to
be reset.
In 4X Quadrature Count Mode:
IMV1 = Required state of phase B input signal for
match on index pulse
IMV0 = Required state of phase A input signal for
match on index pulse
In 2X Quadrature Count Mode:
IMV1 = Selects phase input signal for index state
0
match (
IMV0 = Required state of the selected phase input
signal for match on index pulse
The interrupt is still generated on the detection of the
index pulse and not on the position counter overflow/
underflow.
= Phase A, 1 = Phase B)
13.2.3 COUNT DIRECTION STATUS
As mentioned in the previous section, the QEI logic
generates an UPDN signal, based upon the relationship between Phase A and Phase B. In addition to the
output pin, the state of this internal UPDN signal is
supplied to a SFR bit UPDN (QEICON<1 1>) as a readonly bit.
Note: QEI pins are multiplexed with analog
inputs. User must insure that all QEI associated pins are set as digital inputs in the
ADPCFG register.
DS70118G-page 76 © 2006 Microchip Technology Inc.
Page 79

dsPIC30F2010
13.3 Position Measurement Mode
There are two Measurement modes which are supported and are termed x2 and x4. These modes are
selected by the QEIM<2:0> mo de se lect bit s locate d in
SFR QEICON<10:8>.
When control bits QEIM<2:0> = 100 or 101, the x2
Measurement mode is selected and the QEI logic only
looks at the Phase A input for the position counter
increment rate. Every rising and falling edge of the
Phase A signal caus es the posi tion coun ter to be i ncremented or decremented. The Phase B signal is still
utilized for the determination of the counter direction,
just as in the x4 mode.
Within the x2 Measurement mode, there are two
variations of how the position counter is reset:
1. Position counter reset by detection of index
pulse, QEIM<2:0> = 100.
2. Position counter reset by match with MAXCNT,
QEIM<2:0> = 101.
When control bits QEIM<2:0> = 110 or 111, the x4
Measurement mod e is selected and the QE I logic look s
at both edges of the Phase A and Phase B input signals. Every edge of both sig nals causes the position
counter to increment or decrement.
Within the x4 Measurement mode, there are two
variations of how the position counter is reset:
1. Position counter reset by detection of index
pulse, QEIM<2:0> = 110.
2. Position counter reset by match with MAXCNT,
QEIM<2:0> = 111.
The x4 Measurement mode provides for finer resolution data (more position counts) for determining motor
position.
13.4 Programmable Digital Noise
Filters
The digital noise filter section is responsible for rejecting noise on the incoming capture or quadrature signals. Schmitt Trigger inputs and a three-clock cycle
delay filter combine to reject low level noise and large,
short duration nois e s pik es tha t ty pic al ly occ ur i n noise
prone applications, such as a motor system.
The filter ensures that the filtered output signal is not
permitted to change until a stable value has been
registered for three consecutive clock cycles.
For the QEA, QEB and INDX pins, the cloc k d iv ide frequency for the digital filter is programmed by bits
QECK<2:0> (DFLTCON<6:4>) and are derived from
the base instruction cycle T
To enable the filter output for channels QEA, QEB and
INDX, the QEOUT bit must be ‘1’. The filt er netwo rk for
all channels is disabled on POR and BOR.
CY.
13.5 Alternate 16-bit Timer/Counter
When the QEI module is not configured for the QEI
mode QEIM<2:0> = 001, the module can be configured
as a simple 16-bit timer/c ou nte r. The setup and control
of the auxiliary timer is accomplished through the
QEICON SFR register. This timer functions identically
to Timer1. Th e QEA pin is used as the timer clock input.
When configured as a timer, the POSCNT register
serves as the Timer Count Register and the MAXCNT
register serves as the Period Register. When a timer/
period register match occur, the QEI interrupt flag will
be asserted.
The only exception between the general purpose timers and this timer is the added feature of external Up/
Down input select. When the UPDN pin is asserted
high, the timer will increment up. When the UPDN pin
is asserted low, the timer will be decremented.
Note: Changing the Operational mode (i.e., from
QEI to Timer or vice versa), will not affect
the Timer/Position Count Register
contents.
The UPDN control/status bit (QEICON<11>) can be
used to select the co unt direction st ate of the T imer register. When UPDN = 1, the timer will count up. When
UPDN = 0, the timer will count down.
In addition, control bit UPDN_SRC (QEICON<0>)
determines whether the timer count direction state is
based on the logi c st ate, writte n into the U PDN co ntrol/
status bit (QEICON<11>), or the QEB pin state. When
UPDN_SRC = 1, the timer count direction is co ntro lle d
from the QEB pin. Likewise, when UPDN_SRC = 0, the
timer count direction is controlled by the UPDN bit.
Note: This Timer does not support the External
Asynchronous Counter mode of operation.
If using an exte rnal clock source, t he cloc k
will automatically be synchronized to the
internal instruction cycle.
13.6 QEI Module Operation During CPU Sleep Mode
13.6.1 QEI OPERATION DURING CPU
SLEEP MODE
The QEI module will be halted during the CPU Sleep
mode.
13.6.2 TIMER OPERATION DURING CPU
SLEEP MODE
During CPU Sleep mode, the timer will not operate,
because the internal clocks are disabled.
© 2006 Microchip Technology Inc. DS70118G-page 77
Page 80

dsPIC30F2010
13.7 QEI Module Operation During CPU Idle Mode
Since the QEI module can function as a quadrature
encoder interface, or as a 16-bit timer, the following
section describes operation of the module in both
modes.
13.7.1 QEI OPERATION DURING CPU IDLE
MODE
When the CPU is placed in the Idle mode, the QEI
module will operate if the QEISIDL bit (QEICON<13>)
= 0. This bit defaults to a lo gic ‘0’ upon executing POR
and BOR. For halting the QEI module during the CPU
Idle mode, QEISIDL should be set to ‘1’.
13.7.2 TIMER OPERATION DURING CPU
IDLE MODE
When the CPU is placed in the Idle mode and the QEI
module is configured in the 16-bit Timer mode, the
16-bit timer will operate if the QEISIDL bit
(QEICON<13>) = 0. This bit defaults to a logic ‘0’ upon
executing POR and BOR . F or ha lting the timer module
during the CPU Idle mode, QEISIDL should be set
to ‘1’.
If the QEISIDL bit is cleared, the timer will function
normally, as if the CPU Idle mode had not been
entered.
13.8 Quadrature Encoder Interface Interrupts
The quadrature encoder interface has the ability to
generate an interrupt on occurrence of the following
events:
• Interrupt on 16-bit up/down position counter
rollover/underflow
• Detection of qualified index pulse, or if CNTERR
bit is set
• Timer period match event (overflow/underflow)
• Gate accumulation event
The QEI interrupt flag bit, QEIIF, is asserted upon
occurrence of any of the above events. The QEIIF bit
must be cleared in software. QEIIF is located in the
IFS2 status register.
Enabling an interrupt is accomplished via the respective enable bit, QEIIE. The QEIIE bit is located in the
IEC2 Control register.
DS70118G-page 78 © 2006 Microchip Technology Inc.
Page 81

© 2006 Microchip Technology Inc. DS70118G -page 79
TABLE 13-1: QEI REGISTER MAP
SFR
Name
QEICON 0122 CNTERR
DFLTCON 0124
POSCNT 0126 Position Counter<15:0>
MAXCNT 0128 Maximun Count<15:0>
Legend: u = uninitialized bit
Note: Refer to “dsPIC30F Family Reference Manual” (DS70046) for descriptions of register bit fields.
Addr. Bit 15 Bit 14 Bit 13 Bit 12 Bit 11 Bit 10 Bit 9 Bit 8 Bit 7 Bit 6 Bit 5 Bit 4 Bit 3 Bit 2 Bit 1 Bit 0 Reset State
— QEISIDL INDX UPDN QEIM2 QEIM1 QEIM0 SWPAB — TQGATE TQCKPS1 TQCKPS0 POSRES TQCS UPDN_SRC
— — — — — IMV1 IMV0 CEID QEOUT QECK2 QECK1 QECK0 — — — —
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
1111 1111 1111 1111
dsPIC30F2010
Page 82

dsPIC30F2010
NOTES:
DS70118G-page 80 © 2006 Microchip Technology Inc.
Page 83

dsPIC30F2010
14.0 MOTOR CONTROL PWM MODULE
Note: This data sheet summarizes features of this g roup
of dsPIC30F devices and is not intended to be a complete
reference source. For more information on the CPU,
peripherals, register descriptions and general device
functionality, refer to the “dsPIC30F Family Reference
Manual” (DS70046).
This module simplifies the task of generating multiple,
synchronized Pulse Width Modulated (PWM) outputs.
In particular, the following power and motion control
applications are supported by the PWM module:
• Three Phase AC Induction Motor
• Switched Reluctance (SR) Motor
• Brushless DC (BLDC) Motor
• Uninterruptible Power Supply (UPS)
The PWM module has the following features:
• 6 PWM I/O pins with 3 duty cycle generators
• Up to 16-bit resolution
• ‘On-the-Fly’ PWM frequency changes
• Edge and Center-Aligned Output modes
• Single Pulse Generation mode
• Interrupt support for asymmetrical updates in
Center-Aligned mode
• Output override control for Electrically
Commutative Motor (ECM) operation
• ‘Special Event’ comparator for scheduling other
peripheral events
pins to optionally drive each of the PWM
•FLTA
output pins to a defined state
This module contains 3 duty cycle generators, numbered 1 through 3. The modul e has 6 PW M output p ins,
numbered PWM1H/PWM 1L throu gh PWM 3H/PWM3 L.
The six I/O pins are grouped into high/low numbered
pairs, denoted by the suffix H or L, respectively. For
complementary loads, the low PWM pins are always
the complement of the corresponding high I/O pin.
A simplified block diagram of the Motor Control PWM
modules is shown in Figure 14-1.
The PWM module allows several modes of operation
which are beneficial for specific power control
applications.
© 2006 Microchip Technology Inc. DS70118G-page 81
Page 84

dsPIC30F2010
FIGURE 14 -1: PWM BLOCK DI AGR AM
PWMCON1
PWM Enable and Mode SFRs
PWMCON2
DTCON1 Dead-Time Control SFR
16-bit Data Bus
FLTACON
OVDCON
PTMR
Comparator
PTPER
PTPER Buffer
FLTA Pin Control SFR
PWM Manual
Control SFR
PWM Generator #3
PDC3 Buffer
PDC3
Comparator
PWM Generator
#2
PWM Generator
#1
Channel 3 Dead-Time
Generator and
Override Logic
Channel 2 Dead-Time
Generator and
Override Logic
Channel 1 Dead-Time
Generator and
Override Logic
Output
Driver
Block
PWM3H
PWM3L
PWM2H
PWM2L
PWM1H
PWM1L
FLTA
PTCON
Comparator
SEVTCMP
SEVTDIR
PTDIR
Special Event
Postscaler
Special Event Trigger
PWM Time Base
Note: Details of PWM Generator #1 and #2 not shown for clarity.
DS70118G-page 82 © 2006 Microchip Technology Inc.
Page 85

dsPIC30F2010
14.1 PWM Time Base
The PWM time base is provided by a 15-bit timer with
a prescaler and post scaler . The time ba se is acce ssible
via the PTMR SF R. PTMR<15> is a read -only status
bit, PTDIR, that indic ates th e prese nt count dir ect ion of
the PWM time base. If PTDIR is cleared, PTMR is
counting upwards. If PTDIR is set, PTMR is counting
downwards. The PWM time base is configured via the
PTCON SFR. The time base is enabled/disabled by
setting/clearing the PTEN bit in the PTCON SFR.
PTMR is not cleared when the PTEN bit is cleared in
software.
The PTPER SFR sets the counting period for PTMR.
The user must write a 15-bit value to PTPER<14:0>.
When the value in PTMR<14:0> matches the value in
PTPER<14:0>, the time ba se will ei ther Reset to ‘0’, or
reverse the count direction on the next occurring clock
cycle. The action taken depends on the Operating
mode of the time base.
Note: If the period register is set to 0x0000, the
timer will stop counting, and the interrupt
and the special event trigger will not be
generated, even if the special event value
is also 0x0000. The module will not update
the period register if it is already at
0x0000; therefore, the user must disable
the module in order to update the period
register.
The PWM time base can b e configured for four dif ferent
modes of operation:
• Free Running mode
• Single Shot mode
• Continuous Up/Down Count mode
• Continuous Up/Down Count mode with interrupts
for double updates
These four modes are selected by the PTMOD<1:0>
bits in the PT CON SFR. The Up/Down Coun ting modes
support center-aligned PWM generation. The Single
Shot mode allows the PWM module to support pulse
control of certain Electronically Commutative Motors
(ECMs).
The interrupt sig nal s ge nera ted by the PWM time bas e
depend on the mode sele ction bit s (PTMO D<1:0>) and
the postscaler bit s (P T OP S<3:0>) in the PT CON SFR.
14.1.1 FREE RUNNING MODE
In the Free Running mode, the PWM time base counts
upwards until the value in the Time Base Period register (PTPER) is matched. The PT MR register is reset on
the following input clock edge and the time base will
continue to count upwards as long as the PTEN bit
remains set.
When the PWM time base is in the Free Runnin g mode
(PTMOD<1:0> = 00), an interrupt event is generat ed
each time a match wi th the P TPER register o ccurs an d
the PTMR register is Reset to zero. The postscaler
selection bi ts m ay b e us ed i n th i s mode of th e t im er t o
reduce the frequency of the interrupt events.
14.1.2 SINGLE-SHOT MODE
In the Single-Shot Counti ng m ode, t he PWM tim e base
begins counting upwards when the PTEN bit is set.
When the value in the PTMR register matches the
PTPER register, the PTMR register will be reset on the
following input clock edge and the PTEN bit will be
cleared by the hardware to halt the time base.
When the PWM time base is in the Single-Shot mode
(PTMOD<1:0> = 01), an interrupt event is generat ed
when a match with the PTPER register occurs, the
PTMR register is reset to zero on the following input
clock edge, and the P TEN bit is cleared. The postscaler
selection bits have no effect in this mode of the timer.
14.1.3 CONTINUOUS UP/DOWN COUNTING MODES
In the Continuous Up/Down Counting modes, the PWM
time base count s upwards until the va lue in the P TPER
register is matched. The timer will begin counting
downwards on the following input clock edge. The
PTDIR bit in the PTCON SFR is read-only and indicates the counting direction The PTDIR bit is set when
the timer counts downwards.
In the Up/Down Counting mode (PTMOD<1:0> = 10),
an interrupt event is generated each time the value of
the PTMR register becomes zero and the PWM time
base begins to count upwards. The postscaler selection bits may be used in this m ode of the timer t o reduce
the frequency of the interrupt events.
© 2006 Microchip Technology Inc. DS70118G-page 83
Page 86

dsPIC30F2010
14.1.4 DOUBLE UPDATE MODE
In the Double Up date mode (PTMOD<1:0> = 11), an
interrupt event is ge nerated eac h time the P TMR re gister is equal to ze ro, as well as each time a period match
occurs. The p ostscal er se lectio n bits ha ve no effect in
this mode of the timer.
The Double Update mode provid es two addition al functions to the user. First, the control loop bandwidth is
doubled because the PWM duty cycles can be
updated, tw ice p er peri od. Seco nd, asym metr ical cen ter-aligned PWM waveforms can be generated, which
are useful for minimizing output waveform distortion in
certain motor control applications.
Note: Programming a value of 0x0001 in the
period register could generate a continuous interrupt pulse, and hence, must be
avoided.
14.1.5 PWM TIME BASE PRESCALER
The input clock to PTMR (FOSC/4), has prescaler
options of 1:1, 1:4 , 1:16 or 1:64, s elected by c ontrol bit s
PTCKPS<1:0> in the PTCON SFR. The prescaler
counter is cleared when any of the following occurs:
• a write to the PTMR register
• a write to the PTCON register
• any device Reset
The PTMR register is not cleared when PTCON is
written.
14.1.6 PWM TIME BASE POSTSCALER
The match output of PTMR can optionally be postscaled through a 4-bit postscaler (which gives a 1:1 to
1:16 scaling).
The postscaler counter is cleared when any of the
following occurs:
• a write to the PTMR register
• a write to the PTCON register
• any device Reset
The PTMR register is not cleared when PTCON is written.
14.2 PWM Period
PTPER is a 15-bit register and is used to set the counting period for the PWM time base. PTPER is a doublebuffered register. The PTPER buffer contents are
loaded into the PTPER register at the following
instances:
• Free Running and Single Shot modes:
PTMR register is reset to zero after a match with
the PTPER register.
• Up/Down Counting modes
register is zero.
The value held in the PTPER buffer is automatically
loaded into the PTPER register when the PWM time
base is disabled (PTEN = 0).
The PWM period can be determined using
Equation 14-1:
: When the PTMR
EQUATION 14-1: PWM PERIOD
T
TPWM =
(PTMR Prescale Value)
If the PWM time base is configured for one of the Up/
Down Count modes, the PWM period is found using
Equation 14-2.
CY • (PTPER + 1)
EQUATION 14-2: PWM PERIOD (UP/DOWN
COUNT MODE)
T
TPWM =
The maximum resolution (in bits) for a given device
oscillator and PW M frequency ca n be determined using
Equation 14-3:
CY • 2 • (PTPER + 0.75)
(PTMR Prescale Value)
EQUATION 14-3: PWM RESOLUTION
Resolution =
log (2)
log (2 • TPWM / TCY)
When the
DS70118G-page 84 © 2006 Microchip Technology Inc.
Page 87

dsPIC30F2010
14.3 Edge-Aligned PWM
Edge-aligned PWM signals are produced by the module
when the PWM time base is in the Free Running or Single Shot mode. For edge-aligned PWM outputs, the output has a period specified by the value in PTPER and a
duty cycle specified by the appropriate duty cycle register (see Figure 14-2). The PWM output is driven active
at the beginning of the period (PTMR = 0) and is driven
inactive when the value in the duty cycle register
matches PTMR.
If the value in a particular duty cycle register is zero,
then the output on the corresponding PWM pin will be
inactive for the en tire PWM p erio d. In add iti on, the output on the PWM pin will be active for the entire PWM
period if the value in the duty cycle register is greater
than the value held in the PTPER register.
FIGURE 14-2: EDGE-ALIGNED PWM
New Duty Cycle Latched
PTPER
PTMR
Value
14.4 Center-Aligned PWM
Center-aligned PWM s ignals are produc ed by the mo dule when the PWM time base is configured in an Up/
Down Counting mode (see Figure 14-3).
The PWM compare output is driven to the active state
when the value of the duty cycle register matches the
value of PTMR and the PWM time base is counting
downwards (PTDIR = 1). The PWM compar e o utp ut is
driven to the inacti ve st ate w hen th e PWM ti me bas e is
counting upwards (PTDIR = 0) and the value in the
PTMR register matches the duty cycle value.
If the value in a particular duty cycle register is zero,
then the output on the corresponding PWM pin will be
inactive for the entire PWM period. In additi on, the output on the PWM pin will be active for the entire PWM
period if the value in the duty cycle register is equal to
the value held in the PTPER register.
FIGURE 14-3: CENTER-ALIGNED PWM
Period/2
PTPER
Duty
Cycle
PTMR
Value
0
0
Duty Cycle
Period
Period
14.5 PWM Duty Cycle Comparison Units
There are four 16-bit Special Function Registers
(PDC1, PDC2, PDC3 and PDC4) used to specify duty
cycle values for the PWM module.
The value in each duty cycle register determines the
amount of time that the PWM output is in the active
state. The duty cycle registers are 16 bits wide. The
LSb of a duty cycle register determines whether the
PWM edge occurs in the beginning. Thus, the PWM
resolution is effectively doubled.
© 2006 Microchip Technology Inc. DS70118G-page 85
Page 88

dsPIC30F2010
14.5.1 DUTY CYCLE REGISTER BUFFERS
The four PWM duty cycle regi sters are doub le-buf fered
to allow glitchless updates of the PWM outputs. For
each duty cycle, there is a duty cycle register that is
accessible by the user and a s econd duty cyc le register
that holds the actual comp are value used in the pre sent
PWM period.
For edge-aligned PWM output, a new duty cycle value
will be updated whene ver a match with the PTPER re gister occurs and PTMR is reset. The contents of the
duty cycle buffers are automatically loaded into the
duty cycle registers when the PWM time base is disabled (PTEN = 0) and the UDIS bit is cleared in
PWMCON2.
When the PWM time base is in the Up/Down Counting
mode, new duty cycle values are updated when the
value of the PTMR register is zero and the PWM time
base begins to count upwa rds. The co ntents o f the dut y
cycle buffers are automatically loaded into the duty
cycle registers when the PWM time base is disabled
(PTEN = 0).
When the PWM time base is in the Up/Down Counting
mode with do uble update s, new duty c ycle va lues are
updated when the value of the PTMR register is zero,
and when the value of the PTMR register matches the
value in the PTPER register. The contents of the duty
cycle buffers are automatically loaded into the duty
cycle registers when the PWM time base is disabled
(PTEN = 0).
14.6 Complementary PWM Operation
In the Complementary mode of operation, each pair of
PWM outputs is obtained by a complementary PWM
signal. A dead time may be optionally inserted during
device swi tchin g, whe n bot h out puts are inac tive for a
short period (Refer to Section 14.7 “Dead-Time Gen-
erators”).
In Complementary mode, the duty cycle comparison
units are assigned to the PWM outputs as follows:
• PDC1 register controls PWM1H/PWM1L outputs
• PDC2 register controls PWM2H/PWM2L outputs
• PDC3 register controls PWM3H/PWM3L outputs
The Complementary mode is sele cted for each PWM
I/O pin pair by clearing the appropriate PMODx bit in the
PWMCON1 SFR. The PWM I/O pins are set to
Complementary mode by default upon a device Reset.
14.7 Dead-Time Generators
Dead-time generation may be provided when any of
the PWM I/O pin pairs are operating in the Complementary Output mode. The PWM outputs use PushPull drive circuits. Due to the inab ili ty of the powe r output devices to switch in stantaneously, some amount of
time must be pro vided between th e turn off ev ent of one
PWM output in a complementary pair and the turn on
event of the other transistor.
14.7.1 DEAD-TIME GENERATORS
Each complementary output pair for the PWM module
has a 6-bit down counter that is used to produce the
dead-time insertion. As shown in Figure 14-4, the
dead-time unit has a rising and falling edge detector
connected to the duty cycle comparison output.
14.7.2 DEAD-TIME RANGES
The amount of dead time provided by the dead-time
unit is selected by specifying the input clock prescaler
value and a 6-bit unsigned value.
Four input clock prescaler selections have been provided to allow a suit able rang e of dead t imes, based on
the device operating frequency. The dead-time clock
prescaler value is selected usi ng the DTAPS<1:0> and
DTBPS<1:0> control bits in the DTCON1 SFR. One of
four clock prescaler options (T
is selected for the dead-time value.
After the prescaler value is selected, the dead time is
adjusted by loading a 6-bit unsigned value into the
DTCON1 SFR.
The dead-time unit pres caler is cleared on the f ollowing
events:
• On a load of the down timer due to a duty cycle
comparison edge event.
• On a write to the DTCON1 register.
• On any device Reset.
Note: The user should not modify the DTCON1
values while th e PWM modu le is opera ting
(PTEN = 1). Unexpected results may
occur.
CY , 2TCY, 4TCY or 8TCY)
DS70118G-page 86 © 2006 Microchip Technology Inc.
Page 89

FIGURE 14-4: DEAD-TIME TIMING DIAGRAM
Duty Cycle Generator
PWMxH
PWMxL
dsPIC30F2010
14.8 Independent PWM Output
An independent PWM Output mode is required for driving certain types of loads. A particular PWM output pair
is in the Independent Output mode when the corresponding PMOD bit in the PWMCON1 register is set.
No dead-time control is im plemented between adjacent
PWM I/O pins when the module is operating in the
Independent mode a nd b oth I/O pin s a re al low e d to b e
active simultaneously.
In the Independent mode, each duty cycle gen erator is
connected to both of the PWM I/O pins in an output
pair. By using the associated duty cycle register and
the appropriate bits in the OVDCON register, the user
may select the following signal output options for each
PWM I/O pin operating in the Independent mode:
• I/O pin outputs PWM signal
• I/O pin i nactive
• I/O pin active
14.9 Single Pulse PWM Operation
The PWM module p roduces single pul se outputs whe n
the PTCON co ntrol bits PTMOD <1:0> = 10. On ly edgealigned outputs may be produced in the Single Pulse
mode. In Single Pulse mode, the PWM I/O pin(s) are
driven to the active state when the PTEN bit is set.
When a match wi th a duty cycle registe r occurs, the
PWM I/O pin is driven to the inactive state. When a
match with the PTPER register occurs, the PTMR register is cleared, all active PWM I/O pins are driven to
the inactive state, the PTEN bit is cleared, and an
interrupt is generated.
14.10 PWM Output Override
The PWM output override bits allow the user to manually drive t he PWM I/O pins to sp ecified logic stat es,
independent of the duty cycle comparison units.
All control bits associated with the PWM output override function are contained in the OVDCON register.
The upper half of the OVDCON register contains six
bits, POVDxH<3:1 > and POVDxL<3 :1>, that de termine
which PWM I/O pins will be overridden. The lower half
of the OVDCON register contains six bits,
POUTxH<3:1> and POUTxL<3:1>, that determine the
state of the PWM I/O pins when a particular output is
overridden via the POVD bits.
14.10.1 COMPLEMENTARY OUTPUT MODE
When a PWMxL pin is driven active via the OVDCON
register, the output signal is forced to be the complement of the corresponding PWMxH pin in the pair.
Dead-time insertion is still performed when PWM
channels are overridden manu all y.
14.10.2 OVERRIDE SYNCHRONIZATION
If the OSYNC bit in the PWMCON2 register is set, all
output overrides performed via the OVDCON register
are synchronized to the PWM tim e b ase. Sy nc hron ou s
output overrides occur at the following times:
• Edge-Aligned mode, when PTMR is zero.
• Center-Aligned modes, when PTMR is zero and
when the value of PTMR matches PTPER.
© 2006 Microchip Technology Inc. DS70118G-page 87
Page 90

dsPIC30F2010
14.1 1 PWM Output and Polarity Control
There are three device Configuration bits associated
with the PWM module that provide PWM output pin
control:
• HPOL Configuration bit
• LPOL Configuration bit
• PWMPIN Configuration bit
These three bits in the FPORBOR Configu rati on re gi s-
ter (see Sec tio n 21 ) wor k in conj unc tio n wit h th e thr ee
PWM enable bits (PWMEN<3:1>) located in the
PWMCON1 SFR. The Configuration bits and PWM
enable bits ensure that the PWM pin s are in the c orrect
states after a device Reset occurs. The PWMPIN configuration fuse allows the PWM module outputs to be
optionally en ab l ed on a de vi ce R e set . If P WMP I N = 0,
the PWM outputs will be driven to their inactive states
at Reset. If PWMPIN = 1 (default), the PWM outputs
will be tri-stated. The HPOL bit specifie s the polarity for
the PWMxH outpu ts, whereas the LPOL bi t specifies
the polarity for the PWMxL outputs.
14.11.1 OUTPUT PIN CONTROL
The PEN<3:1>H and PEN<3:1>L control bits in the
PWMCON1 SFR enable each high PWM output pin
and each low PWM output pin, respectively. If a particular PWM output pin not enabled, it is treated as a
general purpose I/O pin.
14.12 PWM FLTA Pins
There is one FLT A pin (FL T A ) associated with the PWM
module. When asserted, this pin can optionally drive
each of the PWM I/O pins to a defined state.
14.12.1 FAULT PIN ENABLE BITS
The FLTACON SFR has 4 control bits that determine
whether a particular pair of PWM I/O pins is to be controlled by the FLTA
I/O pin pair f or FLTA
should be set in the FLTACON register.
If all enable bits are cleared in the FLTACON register,
then the FL TA
ule and the pin may be used as a general purpose
interrupt or I/O pin.
Note: The FLTA pin logic can operate indepen-
input pin. To enable a specific PWM
overrides, the corresponding bit
input pin has no ef fect on the PWM mo d-
dent of the PWM logic. If all the enable bits
in the FLT ACON register are cleared, then
the FLTA
purpose interrupt pin(s). Each FLTA
has an interrupt vector, interrupt flag bit
and interrupt priority bi ts associa ted with it.
pin(s) could be used as general
pin
cleared, the PWM I/O pin is dri ven to the inact ive s tat e.
If the bit is set, the PWM I/O pin will be driven to the
active state. The active and inactive states are referenced to the polarity defined for each PWM I/O pin
(HPOL and LPOL polarity control bits).
14.12.3 FAULT INPUT MODES
The FLTA input pin has two modes of operation:
• Latched Mode: When the FLTA
the PWM outputs will go to the states defined in
the FLTACON register. The PWM outputs will
remain in this state until the FLTA
high and the corresponding interrupt flag has
been cleared in software. When both of these
actions have occurred, the PWM outputs will
return to normal operation at the beginning of the
next PWM cycle or half-cycle boundary. If the
interrupt flag is cleared before the FLTA
ends, the PWM module will wait until the FLTA
is no longer asserted to r estore the o utputs.
• Cycle-by-Cycle Mode: When the FLTA
is driven low, the PWM outputs remain in the
defined FLTA
held low. After the FLTA
PWM outputs return to normal operation at the
beginning of the following PWM cycle or
half-cycle boundary.
The Operating mode for the FLTA
using the FLTAM control bit in the FLTACON Special
Function Register.
The FLTA
states for as lo ng as the FLTA pin is
pin is driven high, the
pin can be controlled manually in software.
pin is driven low,
pin is driven
condition
pin
input pin
input pin is selected
14.13 PWM Update Lockout
For a complex PWM applicatio n, the user ma y nee d to
write up to four duty cycl e regi sters an d the time base
period register, PTPER, at a given time. In some applications, it is im portant that all buf fer regis ters be written
before the new duty c ycle and perio d values are loaded
for use by the module.
The PWM update lockout feature is enabled by setting
the UDIS control bit in the PWM C ON 2 SFR. Th e U DIS
bit affects all duty cycle buffer registers and the PWM
time base period buffer, PTPER. No duty cycle
changes or period va lue ch ang es wi ll h av e effect while
UDIS = 1.
14.12.2 FAULT STATES
The FLTACON special function register has 8 bits that
determine the state of each PWM I/O pin when it is
overridden by a FLTA
DS70118G-page 88 © 2006 Microchip Technology Inc.
input. When these bits are
Page 91

dsPIC30F2010
14.14 PWM Special Event Trigger
The PWM module has a special event trigger that
allows A/D conversi ons to be synchronize d to the PWM
time base. The A/D sa mp ling an d conv ersio n time may
be programmed to occur at any point within the PWM
period. The special even t trigger allows the user to mi nimize the delay betwee n the time when A/D con version
results are acquired, and the time when the duty cycle
value is updated.
The PWM special event trigger has an SFR named
SEVTCMP, and five control bits to control it s opera tion.
The PTMR value for which a special event trigger
should occur is loaded into the SEVTCMP register.
When the PWM time base is in an Up/Down Counting
mode, an addi tional con trol bit is r equired t o speci fy the
counting phase for the special event trigger. The count
phase is selected using the SEVTDIR control bit in the
SEVTCMP SFR. If the SEVTDIR bit is cleared, the special event trigger will occur on the upward counting
cycle of the PWM time base. If the SEVTDIR bit is set,
the special event trigger will occur on the downward
count cycle of the PWM time base. The SEVTDIR
control bit has no effect unless the PWM time base is
configured for an Up/Down Counting mode.
14.14.1 SPECIAL EVENT TRIGGER POSTSCALER
The PWM special event trigger has a postscaler that
allows a 1:1 to 1:16 postscale ratio. The postscaler is
configured by writing the SEVOPS<3:0> control bits in
the PWMCON2 SFR.
The special event output postscaler is cleared on the
following events:
• Any write to the SEVTCMP register
• Any device Re set
14.15 PWM Operation During CPU Sleep Mode
The FLTA A and FLTA B input pins have the ability to
wake the CPU from Sleep mode. The PWM module
generates an interrupt if either of the FLTA pins is
driven low while in Sleep.
14.16 PWM Operation During CPU Idle Mode
The PTCON SFR contains a PTSIDL control bit. This
bit determines if the PWM module will continue to
operate or stop when the device enters Idle mode. If
PTSIDL = 0, the module will continue to operate. If
PTSI DL = 1, the module will stop operation as long as
the CPU remains in Idle mode.
© 2006 Microchip Technology Inc. DS70118G-page 89
Page 92

DS70118G-page 90 © 2006 Microchip Technology Inc.
TABLE 14-1: PWM REGISTER MAP
SFR Name
PTCON 01C0 PTEN
PTMR 01C2 PTDIR PWM Timer Count Val ue
PTPER 01C4
SEVTCMP 01C6 SEVTDIR PWM Special Event Compare Register
PWMCON1 01C8
PWMCON2 01CA
DTCON1 01CC DTBPS<1:0> DTB<5:0> DTAPS<1:0> Dead Time A Value
FLTACON 01D0
OVDCON 01D4
PDC1 01D6 PWM Duty Cycle #1 Register
PDC2 01D8 PWM Duty Cycle #2 Register
PDC3 01DA PWM Duty Cycle #3 Register
Addr. Bit 15 Bit 14 Bit 13 Bit 12 Bit 11 Bit 10 Bit 9 Bit 8 Bit 7 Bit 6 Bit 5 Bit 4 Bit 3 Bit 2 Bit 1 Bit 0 Reset State
—PTSIDL — — — — — PTOPS<3:0> PTCKPS<1:0> PTMOD<1:0>
— PWM Time Base Period Register
— — — — — PTMOD3 PTMOD2 PTMOD1 — PEN3H PEN2H PEN1H — PEN3L PEN2L PEN1L
— — — — SEVOPS<3:0> — — — — — — OSYNC UDIS
— — FAOV3H FAOV3L FAOV2H FAOV2L FAOV1H FAOV1L FLTAM — — — — FAEN3 FAEN2 FAEN1
— — POVD3H POVD3L POVD2H POVD2L POVD1H POVD1L — — POUT3H POUT3L POUT2H POUT2L POUT1H POUT1L
0000 0000 0000 0000
0000 0000 0000 0000
0011 1111 1111 1111
0000 0000 0000 0000
0000 0000 0111 0111
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0011 1111 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
dsPIC30F2010
Legend: u = uninitialized bit
Note: Refer to “dsPIC30F Family Reference Manual” (DS70046) for descriptions of register bit fields.
Page 93

dsPIC30F2010
15.0 SPI MODULE
Note: This data sheet summarizes features of this g roup
of dsPIC30F devices and is not intended to be a complete
reference source. For more information on the CPU,
peripherals, register descriptions and general device
functionality, refer to the “dsPIC30F Family Reference
Manual” (DS70046).
The Serial Peripheral Interface (SPI) module is a synchronous serial inte rface. It is us eful for commun icating
with other peripheral devices such as EEPROMs, shift
registers, display drivers and A/D converters or other
microcontrollers. It is compatible with Motorola's SPI
and SIOP interfaces.
15.1 Operating Function Description
Each SPI module consists of a 16-bit shift register,
SPIxSR (where x = 1 or 2), used for shifting data in
and out, and a buffer register, SPIxBUF. A control register, SPIxCON, configures the module. Additionally, a
status register, SPIxSTAT, indicates various status
conditions.
The serial interface consists of 4 pins: SDIx (serial
data input), SDOx (serial data output), SCKx (shift
clock input or output) and SSx
select).
In Master mode operation, SCK is a clock output, but
in Slave mode, it is a clock input.
A series of eight (8) or sixteen (16) clock pulses shifts
out bits from the SPIxSR to SDOx pin and simultaneously shifts in data from SDIx pin. An interrupt is
generated when the transfer is complete and the corresponding interrupt flag bit (SPI1IF or SPI2IF) is set.
This interrupt can be disabled through an interrupt
enable bit (SPI1IE or SPI2IE).
The receive operation is double-buffered. When a
complete byte is received, it is transferred from
SPIxSR to SPIxBUF.
If the receive buffer is full when new data is being
transferred from SPIxSR to SPIxBUF, the module will
set the SPIROV bit, indicating an overflow condition.
The transfer of the data from SPIxSR to SPIxBUF will
not be completed and the new data will be lost. The
module will not respond to SCL transitions while
SPIROV is ‘1’, effectively disabling the module until
SPIxBUF is read by user software.
Transmit writes are also double-buffered. The user
writes to SPIxB UF. When the master or slave t ransfer
is completed, the contents of the shift register
(SPIxSR) is moved to the receive buffer. If any transmit data has been written to the buffer register, the
contents of the transmit buffer are moved to SPIxSR.
The received data is thus placed in SPIxBUF and the
transmit data in SPIxSR is ready for the next transfer.
(active-low slave
In Master mode, the clock is generated by prescaling
the system clock. Data is transmitted as soon as a
value is written to SPIxBUF. The interrupt is generated
at the middle of the transfer of the last bit.
In Slave mode, data is transmitted and received as
external clock pulses appear on SCK. Again, the interrupt is generated when the last bit is latched. If SSx
control is enabled, then transmission and reception
are enabled only when SSx
will be disabled in SSx
The clock provided to the module is (F
clock is then prescaled by the primary (PPRE<1:0>)
and the secondary (SPRE<2:0>) prescale factors. The
CKE bit determines whether transmit occurs on transition from active clock state to Idle clock state, or vice
versa. The CKP bit selects the Idle state (high or low)
for the clock.
= low. The SDOx output
mode with SSx high.
OSC/4). This
15.1.1 WORD AND BYTE
COMMUNICATION
A control bit, MODE16 (SPIxCON<10>), allows the
module to communicate in either 16-bit or 8-bit mode.
16-bit operation is identical to 8-bit operation, except
that the number of bits transmitted is 16 instead of 8.
The user software must disable the module prior to
changing the MODE16 bit. The SPI module is reset
when the MODE16 bit is changed by the user.
A basic difference betw een 8-bit and 16-bit op eration is
that the data is transmitted out of bit 7 of the SPIxSR for
8-bit operation, and data is transmitted out of bit 15 of
the SPIxSR for 16-bit operation . In both m odes, dat a is
shifted into bit 0 of the SPIxSR.
15.1.2 SDOx DISABLE
A control bit, DISSDO, is provided to the SPIxCON register to allow the SDOx output to be disabled. This will
allow the SPI module to be connected in an input only
configuration. SDO can also be used for general
purpose I/ O.
15.2 Framed SPI Support
The module supports a basic framed SPI protocol in
Master or Slave mode. The contro l bit FRMEN enab les
framed SPI support and causes the SSx pi n to perform
the frame synchronization pulse (FSYNC) function.
The control bit SPIFSD determines whether the SSx
pin is an input or an output (i.e., whether the module
receives or generates the frame synchronization
pulse). The frame pulse is an active-high pulse for a
single SPI clock cycle. When frame synchronization is
enabled, the data transmission starts only on the
subsequent transmit edge of the SPI clock.
Note: Both the transmit buffer (SPIxTXB) and
the receive buffer (SPIxRXB) are mapped
to the same register address, SPIxBUF.
© 2006 Microchip Technology Inc. DS70118G-page 91
Page 94

dsPIC30F2010
FIGURE 15-1: SPI BLOCK DIAGRAM
Read Write
Internal
Data Bus
Shift
clock
Clock
Control
SPIxBUF
Transmit
SDIx
SDOx
SSx
SCKx
Note: x = 1 or 2.
SPIxBUF
Receive
SPIxSR
bit 0
SS & FSYNC
Control
FIGURE 15-2: SPI MASTER/SLAVE CONNECTION
SPI Master
SDOx
Edge
Select
Secondary
Prescaler
1:1-1:8
Enable Master Clock
SDIy
SPI Slave
Primary
Prescaler
1:1, 1:4,
1:16, 1:64
CY
F
Serial Input Buffer
(SPIxBUF)
Shift Register
(SPIxSR)
MSb
PROCESSOR 1
Note: x = 1 or 2, y = 1 or 2.
LSb
SDIx
SCKx
Serial Clock
SDOy
SCKy
Serial Input Buffer
(SPIyBUF)
Shift Register
(SPIySR)
MSb
PROCESSOR 2
LSb
DS70118G-page 92 © 2006 Microchip Technology Inc.
Page 95

dsPIC30F2010
15.3 Slave Select Synchronization
The SSx pin allows a Synchronous Slave mode. The
SPI must be configured in SPI Slave mode, with SSx
pin control enabled (SSEN = 1). When the SSx pin is
low, transmission and reception are enabled, and the
SDOx pin is driven. When SSx pin goes high, the SDOx
pin is no longer driven. Also, the SPI module is resynchronized, and all counters/control circuitry are
reset. Therefore, when the SSx
again, transmission/reception will begin at the MSb,
even if SSx had been de-asserted in the middle of a
transmit/receive.
pin is asserted low
15.4 SPI Operation During CPU Sleep Mode
During Sleep mode, the SPI module is shut down. If
the CPU enters Sleep mode while an SPI transaction
is in progress, then the transmission and reception is
aborted.
The transmitter and receiver will stop in Sleep mode.
However, register contents are not affected by
entering or exiting Sleep mode.
15.5 SPI Operation During CPU Idle Mode
When the device enters Idle mode, all clock sources
remain functional. The SPISIDL bit (SPIxSTAT<13>)
selects if the SPI module will stop or continue on Idle.
If SPISIDL = 0, the module will continue to operate
when the CPU enters Idle mode. If SPISIDL = 1, the
module will stop when the CPU enters Idle mode.
© 2006 Microchip Technology Inc. DS70118G-page 93
Page 96

DS70118G-page 94 © 2006 Microchip Technology Inc.
TABLE 15-1: SPI1 REGISTER MAP
SFR
Name
SPI1STAT 0220 SPIEN
SPI1CON 0222
SPI1BUF 0224 Transmit and Receive Buffer
Addr. Bit 15 Bit 14 Bit 13 Bit 12 Bit 11 Bit 10 Bit 9 Bit 8 Bit 7 Bit 6 Bit 5 Bit 4 Bit 3 Bit 2 Bit 1 Bit 0 Reset State
— SPISIDL — — — — — — SPIROV — — — — SPITBF SPIRBF
— FRMEN SPIFSD — DISSDO MODE16 SMP CKE SSEN CKP MSTEN SPRE2 SPRE1 SPRE0 PPRE1 PPRE0
0000 0000 0000 0000
0000 0000 0000 0000
0000 0000 0000 0000
dsPIC30F2010
Legend: u = uninitialized bit
Note: Refer to “dsPIC30F Family Reference Manual” (DS70046) for descriptions of register bit fields.
Page 97

dsPIC30F2010
16.0 I2C MODULE
Note: This data sheet summarizes features of this g roup
of dsPIC30F devices and is not intended to be a complete
reference source. For more information on the CPU,
peripherals, register descriptions and general device
functionality, refer to the “dsPIC30F Family Reference
Manual” (DS70046).
The Inter-Integrated Circuit (I2C) module provides
complete hardware support for both Slave and MultiMaster modes of the I2C serial communication
standard, with a 16-bit interface.
This module offers the following key features:
2
C interface supporting both Master and Slave
•I
operation.
2
•I
C Slave mode supports 7 and 10-bit address.
•I2C Master mode supports 7 and 10-bit address.
2
C port allows bidirectional transfers between
•I
master and slaves.
• Serial clock synchronization for I
used as a handshake mechanism to s uspen d and
resume serial transfer (SCLREL control).
2
C supports Multi-Master operation; detects bus
•I
collision and will arbitrate accordingly.
FIGURE 16-1: PROGRAMMER’S MODEL
2
C port can be
16.1 Operating Function Description
The hardware fully im plements all the maste r and slave
functions of the I
specifications, as well as 7 and 10-bit addressing.
Thus, the I
a master on an I
16.1.1 VARIOUS I2C MODES
The following types of I2C operation are supported:
2
C Slave operation with 7-bit address
•I
2
•I
C Slave operation with 10-bit address
•I2C Master operation with 7 or 10-bit address
See the I
2
16.1.2 PIN CONFIGURATION IN I2C MODE
I2C has a 2-pin inter fac e: pin SCL is clock and pin SD A
is data.
2
C Standard and Fast mode
2
C module can operate either as a slave or
2
C bus.
C programmer’s model in Figure 16-1.
bit 7
bit 7
bit 8
bit 15
bit 15
bit 9
2
16.1.3 I
C REGISTERS
I2CCON and I2CSTAT are con trol and sta tus re gisters ,
respectively. The I2CCON register is rea dable and writable. The lower 6 bits of I2CSTAT are read-only. The
remaining bits of the I2CSTAT are read/write.
I2CRSR is the shift register used for shifting data,
whereas I2CRCV is the buffer register to which data
bytes are written, or from which data bytes are read.
I2CRCV is the receive buffer, as shown in Figure 16-1.
I2CTRN is the transmit register to which bytes are written during a transmit operation, as shown in Figure 16 -2.
I2CRCV (8 bits)
bit 0
I2CTRN (8 bits)
bit 0
I2CBRG (9 bits)
bit 0
I2CCON (16 bits)
bit 0
I2CSTAT (16 bits)
bit 0
I2CADD (10 bits)
bit 0
The I2CADD register hol ds the s lave a ddress . A st atus
bit, ADD10, indicates 10-bit Address mode. The
I2CBRG acts as the Baud Rate Generator (BRG)
reload value.
In receive operations, I2CRSR and I2CRCV together
form a double-buffered receiver. When I2CRSR
receives a complete byte, it is transferred to I2CRCV
and an interrupt pulse is generated. During
transmission, the I2CTRN is not double-buffered.
Note: Following a Restart condition in 10-bit
mode, the user only needs to match the
first 7-bit address.
© 2006 Microchip Technology Inc. DS70118G-page 95
Page 98

dsPIC30F2010
FIGURE 16-2: I2C BLOCK DI AGR AM
Internal
Data Bus
SCL
SDA
Shift
Clock
Stop bit Generate
I2CRCV
I2CRSR
Match Detect
I2CADD
Start and
Stop bit Detect
Start, Restart,
Collision
Detect
LSB
Addr_Match
Control Logic
Read
Write
Read
Write
I2CSTAT
Read
Write
Shift
Clock
Acknowledge
Generation
Clock
Stretching
I2CTRN
Reload
Control
BRG Down
Counter
LSB
FCY
I2CBRG
I2CCON
Read
Write
Read
Write
Read
DS70118G-page 96 © 2006 Microchip Technology Inc.
Page 99

dsPIC30F2010
16.2 I2C Module Addresses
The I2CADD register contains the Slave mode
addresses. The register is a 10-bit register.
If the A10M bit (I2CCON<10>) is ‘0’, the address is
interpreted by the mo dul e as a 7 -bit address. When an
address is received, i t is c omp ared to the 7 LSbs of the
I2CADD register.
If the A10M bit is ‘1’, the address is assumed to be a
10-bit address. When an address is received, it will be
compared with the binary value ‘1 1 1 1 0 A9 A8’
(where A9, A8 are two Most Significant bits of
I2CADD). If that value matches, the next address will
be compared with the Least Significant 8 bits of
I2CADD, as specifie d in the 10-bi t addressi ng proto col.
TABLE 16-1: 7-BIT I2C™ SLAVE
ADDRESSES SUPPORTED BY
dsPIC30F
0x00 General call address o r Start byte
0x01-0x03 Reserved
0x04-0x07 Hs mode Master codes
0x08-0x77 Valid 7-bit addresses
0x78-0x7B Valid 10-bit addresses
(lower 7 bits)
0x7C-0x7F Reserved
16.3 I2C 7-bit Slave Mode Operation
Once enabled (I2CEN = 1), the slave module will wait
for a St art bit to occur (i.e., the I
lowing the detection of a Start bit, 8 bi ts are shifted in to
I2CRSR and the address is compared against
I2CADD. In 7-bit mode (A10M = 0), bits I2CADD<6:0>
are compared against I2CRSR<7:1> and I2CRSR<0>
is the R_W bit. All incoming bits are sampled on the
rising edge of SCL.
If an address match occurs, an acknowledgement will
be sent, and the slave event interrupt flag (SI2CIF) is
set on the falling edge of the ninth (ACK
address match does not affect the contents of the
I2CRCV buffer or the RBF bit.
16.3.1 SLAVE TRANSMISSION
If the R_W bit received is a ‘1’, then the serial port will
go into Tra nsmi t mode. It will s end AC K
and then hold SCL to ‘
ing to I2CTRN. SCL is releas ed by settin g the SCLREL
bit, and 8 bits of data are shifted out. Data bits are
shifted out on the fa lling edge of SCL, s uch that SDA i s
valid during SCL high (see timing diagram). The interrupt pulse is sent on the falling edge of the ninth clock
pulse, regardless of the status of the ACK
from the master.
0
2
C module is ‘Idle’). Fo l-
) bit. The
on the ninth bit
’ until the CPU re sponds by wr it-
received
16.3.2 SLAVE RECEPTION
If the R_W bit received is a ‘0’ during an address
match, then Receive mode is initiated. Incoming bits
are sampled on the risi ng ed ge of SCL. After 8 bi t s are
received, if I2CRCV is not full or I2COV is not set,
I2CRSR is transferred to I2CRCV. ACK
ninth clock.
If the RBF flag is set, indicating that I2CRCV is still
holding data from a pre vious operati on (RBF = 1), the n
is not sent; however, the interrupt pulse is gener-
ACK
ated. In the case of an overflow, the contents of the
I2CRSR are not loaded into the I2CRCV.
Note: The I2CRCV will be loaded if the I2COV
bit = 1 and the RBF flag = 0. In this case,
a read of the I2CRCV was performed, but
the user did not clear the state of the
I2COV bit before the next receive
occurred. The acknowledgement is not
sent (ACK
updated.
= 1) and the I2CRCV is
is sent on the
16.4 I2C 10-bit Slave Mode Operation
In 10-bit mode, the basic receive and transmit operations are the same as in the 7-bit mode. However, the
criteria for address match is more complex.
2
C specification dictates that a slave must be
The I
addressed for a write operation, with two address byte s
following a Start bit.
The A10M bit is a control bit that signifies that the
address in I2CADD is a 10-bit address rather than a
7-bit address. The address detection protocol for the
first byte of a message address is identical for 7-bit
and 10-bit messages, but the bits being compared are
different.
I2CADD holds the entire 10-bit address. Upon receiving an address following a Start bit, I2CRSR <7:3> is
compared against a literal ‘11110’ (the default 10-bit
address) and I2CRSR<2:1> are compared against
I2CADD<9:8>. If a match occurs and if R_W = 0, the
interrupt pulse is sent. The ADD1 0 bit will be cleare d to
indicate a partial address match. If a match fails or
R_W = 1, the ADD10 bit is cleared and the module
returns to the Idle state.
The low byte of the address is then received and compared with I2CADD<7:0>. If an address match occurs,
the interrupt pulse is generated and the ADD10 bit is
set, indicating a complete 10-bit address match. If an
address match did not occur, the ADD10 bit is cleared
and the module returns to the Idle state.
© 2006 Microchip Technology Inc. DS70118G-page 97
Page 100

dsPIC30F2010
16.4.1 10-BIT MODE SLAVE TRANSMISSION
Once a slave is addressed in this fashion, with the full
10-bit address (we will refer to this state as
"PRIOR_ADDR_MATCH"), the master can begin
sending data bytes for a slave reception operation.
16.4.2 10-BIT MODE SLAVE RECEPTION
Once addressed, the ma ster ca n genera te a Rep eated
Start, reset the high byte of the address and set the
R_W bit without generating a Stop bit, thus initiating a
slave transmit operation.
16.5 Automatic Clock Stretch
In the Slave modes, the modu le can synchroniz e buffer
reads and write to the master device by clock
stretching.
16.5.1 TRANSMIT CLOCK STRETCHING
Both 10-bit and 7-bit Transmit modes implement clock
stretching by asserting the SCLREL bit after the falling
edge of the ninth clock if the TBF b it is clea red, ind icating the buffer is empty.
In Slave Transmit modes, clock stretching is always
performed, irrespective of the STREN bit.
Clock synchronization takes place following the ninth
clock of the transmit sequence. If the device samples
an ACK
TBF bit is still clear, then the SCLREL bit is automatically cleared. The SCLREL being cleared to ‘0’ will
assert the S CL line low. The user ’s ISR must set the
SCLREL bit before transmission is allowed to continue. By holding the SC L l ine lo w, the user has time to
service th e ISR and load the conte nts of the I2C TRN
before the master device can initiate another transmit
sequence.
on the falling edg e of the ninth clock , and if the
Note 1: If the user loads the contents of I2CTRN,
setting the TBF bit before the fallin g edge
of the ninth clock , th e SCLR EL bit w il l not
be cleared and clock stretching will not
occur.
2: The SCLREL bi t can be set in sof tware,
regardless of the state of the TBF bit.
16.5.3 CLOCK STRETCHING DURING 7-BIT ADDRESSING (STREN = 1)
When the STREN bit is set in Slave Receive mode,
the SCL line is held low when the buffer register is full.
The method for stretching the SCL output is the same
for both 7 and 10-bit Addressing modes.
Clock stretching takes place following the ninth clock of
the receive sequence. On the falling edge of the ninth
clock at the end of the ACK
set, the SCLREL bit is automatically cleared, forcing the
SCL output to be held low. The user’s ISR must set the
SCLREL bit before reception is allowed to continue. By
holding the SCL line low, the user has time to service
the ISR and read the contents of the I2CRCV before the
master device can initiate another receive sequence.
This will prevent buffer overruns from occurring.
Note 1: If the user reads the contents of the
I2CRCV, clearing the RBF bit before the
falling edge of the ninth clock, the
SCLREL bit will not be cleared and clock
stretching will not occur.
2: The SCLREL bit can be set in software,
regardless of the sta te of the RBF bit. The
user should be careful to clear the RBF bit
in the ISR before the next receive
sequence in order to prevent an overflow
condition.
sequence, if the RBF bit is
16.5.4 CLOCK STRETCHING DURING 10-BIT ADDRESSING (STREN = 1)
Clock stretching takes place automatically during the
addressing sequence. Because this module has a
register for the entire address, it is not necessary for
the protocol to wait for the address to be updated.
After the address phase is complete, clock stretching
will occur on each data receive or transmit sequence
as was described earlier.
16.5.2 RECEIVE CLOCK STRETCHING
The STREN bit in the I2CCON register can be used to
enable clock stretching in Slave Receive mode. When
the STREN bit is set, the SCL pin will be held low at
the end of each data receive sequence.
DS70118G-page 98 © 2006 Microchip Technology Inc.
 Loading...
Loading...