Meru Networks AP100 professional installation

Meru Wireless Networking
Product
1.0 Beta Command-Line Interface Reference
July 2003
PRELIMINARY
Document Number: xxxxxx

Revision History
Revision Date
July 2003 0.1 1.0 Beta release.
Information in this document is provided in connection with Meru
property rights is granted by this document. Except as provided in Meru’s Terms and Conditions of Sale for such products, Meru assumes no liability
whatsoever, and Meru disclaims any express or implied warranty, relating to sale and/or use of Meru products including liability or warranties relating
to fitness for a particular purpose, merchantability, or infringement of any patent, copyright or other intellectual property right. Meru products are not
intended for use in medical, life saving, or life sustaining applications.
Meru may make changes to specifications and product descriptions at any time, without notice.
Designers must not rely on the absence or characteristics of any features or instructions marked “reserved” or “undefined.” Meru reserves these for
future definition and shall have no responsibility whatsoever for conflicts or incompatibilities arising from future changes to them.
The product may contain design defects or errors known as errata which may cause the product to deviate from published specifications. Current
characterized errata are available on request.
Meru Networks, Inc. might have patents or pending patent applications covering subject matter in this document. The furnishing of this document does
not give any license to these patents.
This document as well as the described in it are furnished under license and may only be used or copied in accordance with the terms of the license.
The information in this document is furnished for informational use only, is subject to change without notice, and should not be construed as a
commitment by Meru Networks, Inc.. Meru Networks, Inc. assumes no responsibility or liability for any errors or inaccuracies that may appear in this
document or any software that may be provided in association with this document. Except as permitted by such license, no part of this document may
be reproduced, stored in a retrieval system, or transmitted in any form or by any means without the express written consent of Meru Networks, Inc..
Contact your local Meru sales office or your distributor to obtain the latest specifications and before placing your product order.
Copies of documents which have an ordering number and are referenced in this document, or other Meru literature may be obtained by calling
or by visiting Meru’s website at http://www.merunetworks.com
Copyright © Meru Networks, Inc., 2003. All rights reserved.
*Other names and brands may be claimed as the property of others.
This product includes software developed by parties other than Meru. See the back page of this document for a list of copyrights and license
agreements.
Revision Description
®
products. No license, express or implied, by estoppel or otherwise, to any intellectual
PRELIMINARY

Contents
Chapter 1
Chapter 2
PRELIMINARY
About This Document. . . . . . . . . . . . . . . . . . vii
Audience . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . vii
In This Guide. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . vii
Other Sources of Information . . . . . . . . . . . . . . . . . . . . . . . viii
Typographic Conventions . . . . . . . . . . . . . . . . . . . . . . . . viii
Syntax Notation . . . . . . . . . . . . . . . . . . . . . . . . . . . ix
Contacting Meru . . . . . . . . . . . . . . . . . . . . . . . . . . . . ix
Web and Internet Sites . . . . . . . . . . . . . . . . . . . . . . . . ix
Customer Support Technicians . . . . . . . . . . . . . . . . . . . . . x
Key Concepts . . . . . . . . . . . . . . . . . . . . . . . 1
Network Layout . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1
Node Identification . . . . . . . . . . . . . . . . . . . . . . . . . . . .2
Serial Numbers and Node Numbers . . . . . . . . . . . . . . . . . . . 2
Using the Controller Console and the CLI . . . . . . . . . . . . . . . . . . 2
CLI Command Reference . . . . . . . . . . . . . . . . . 1
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2
Alarms Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
alarms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
asc: Subcontroller Commands . . . . . . . . . . . . . . . . . . . . . . . 5
asc all . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5
asc get . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5
asc ids . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
asc set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Revision 0.1, July 2003
Contents iii

iv
ats: Access Point Commands . . . . . . . . . . . . . . . . . . . . . . . . 8
ats all. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
ats get . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
ats ids . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
ats images. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
ats mappings . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
ats scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
ats set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
ats upgrade . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
auth: RADIUS Authentication Commands . . . . . . . . . . . . . . . . 12
auth all . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
auth del. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
auth get. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
auth new . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
auth set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
authstats get. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
Channel BSSID Commands . . . . . . . . . . . . . . . . . . . . . . . 15
channel all . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
channel get . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
channel ids . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
channel set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
connect or remote: Remote Connection Commands. . . . . . . . . . . . . 17
{connect | remote} . . . . . . . . . . . . . . . . . . . . . . . . . . 17
connect asc . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
connect ats . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
Console Commands . . . . . . . . . . . . . . . . . . . . . . . . . . 18
console get . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
console paging. . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
console set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
db: Configuration Backup Commands . . . . . . . . . . . . . . . . . . 20
db backup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
db delete . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
db list . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
db restore . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
Help Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
help . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
History Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
history . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
if...stats: Interface Statistics Commands . . . . . . . . . . . . . . . . . . 24
if80211stats all . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
if80211stats get . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
PRELIMINARY
if80211stats ids . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
ifstats. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
ifstats all . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
ifstats get . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
ifstats ids . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Contents
Revision 0.1, July 2003

if: Interface Commands . . . . . . . . . . . . . . . . . . . . . . . . . 29
{interface | ifc} . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
interface all . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
interface get. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
interface ids . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
interface set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
qoS or codec: Quality of Service Commands. . . . . . . . . . . . . . . . 32
qoscodec all . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
qoscodec del . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
qoscodec get . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
qoscodec ids . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
qoscodec new . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
qosrule or ruleQoS: Rule Commands . . . . . . . . . . . . . . . . . . . 36
qosrule all . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
qosrule del . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
qosrule get . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
qosrule ids . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
qosrule new. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
qosstats. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
qosvars . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
qosvars get . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
qosvars set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Quit Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
quit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
Reboot (or restart) Commands . . . . . . . . . . . . . . . . . . . . . . 43
{reboot | restart}. . . . . . . . . . . . . . . . . . . . . . . . . . . 43
reboot all . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
reboot asc. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
reboot ats . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
reboot wnc . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
security: RADIUS Security Commands . . . . . . . . . . . . . . . . . . 45
{security | sec} . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
security get . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
security set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
SNMP Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
snmp del . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
snmp get . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
snmp new . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
snmp set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
Station Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
station all . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
PRELIMINARY
station del . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
station get . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
station set. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
{stationstats | stastats} . . . . . . . . . . . . . . . . . . . . . . . . 51
stationstats all . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
Revision 0.1, July 2003
topo: Network Topology Commands . . . . . . . . . . . . . . . . . . . 53
Contents v

vi
{topoascats | ascats} . . . . . . . . . . . . . . . . . . . . . . . . . 53
topoascats all . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
topoats . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
topoats all. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
{topoatsats | atsats} . . . . . . . . . . . . . . . . . . . . . . . . . 54
topoatsats all . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
{topostaats | staats} . . . . . . . . . . . . . . . . . . . . . . . . . 55
topostaats all . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
topostation all . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
Watchdog Commands. . . . . . . . . . . . . . . . . . . . . . . . . . 57
{watchdog | wd}. . . . . . . . . . . . . . . . . . . . . . . . . . . 57
watchdog get . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
watchdog set . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
watchdog get . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
watchdog set . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
wirelessif or wif: Wireless Interface Commands . . . . . . . . . . . . . . 59
wirelessif all. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
wirelessif get . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
wirelessif ids . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61
wirelessif set . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61
wnc: Controller Commands . . . . . . . . . . . . . . . . . . . . . . . 63
wnc get . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
wnc set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
Glossary . . . . . . . . . . . . . . . . . . . . . . . . . 67
Alphabetic List of Terms and Abbreviations . . . . . . . . . . . . . . . . 67
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . .71
PRELIMINARY
Contents
Revision 0.1, July 2003

About This Document
This document describes the command-line interface (CLI) commands for the Meru
Wireless Networking Product.
It briefly explains some of the concepts that you need to know before using the
commands.
Audience
This guide is intended for network administrators who will install, configure, and
maintain a Meru wireless network. It assumes that you are familiar with the
following:
Wireless networking
Basic IP routing concepts
In This Guide
This guide includes the following chapters:
Chapter 1, “Key Concepts,” which provides useful information about Meru wire-
PRELIMINARY
less networking
Chapter 2, “CLI Command Reference,” which lists alphabetically all of the
commands in the Meru command-line interface
Revision 0.1, July 2003
“Glossary” which defines some terms used in this document
About This Document vii
Other Sources of Information
Other Sources of Information
This guide is part of the Meru wireless network documentation set, which also
includes:
Meru Wireless Networking Product Command-Line Interface Reference (CLI Reference),
which describes the Meru wireless network (software development kit),
including the <<>>, which consists of the <<>>
Meru Wireless Networking Product System Administrator’s Guide, which provides
<<>> using the Meru wireless network
Meru Wireless Networking Product Release Notes (Release Notes), which lists informa-
tion about the latest software release
Meru wireless network for the controller board Installation and Quick Start Guide
(Installation Guide), which describes how to install the Meru wireless network and
set up the networking environment
In addition, the Meru Web site provides valuable information on products, support,
and the company. See “Contacting Meru” on page ix.
Typographic Conventions
This document uses the following typographic conventions to help you locate and
identify information:
Italic text Used for new terms, emphasis, and book titles; also identifies arguments
in syntax descriptions.
Bold text Identifies keywords and punctuation in syntax descriptions.
Courier font Identifies file names, folder names, and text that either appears on the
screen or that you are required to type.
NOTE:
CAUTION:
Provides extra information, tips, and hints regarding the topic.
Identifies important information about actions that could result in damage
to or loss of data or could cause the application to behave in unexpected
ways.
WARNING!
Identifies critical information about actions that could result in
equipment failure or bodily injury.
PRELIMINARY
viii About This Document
Revision 0.1, July 2003
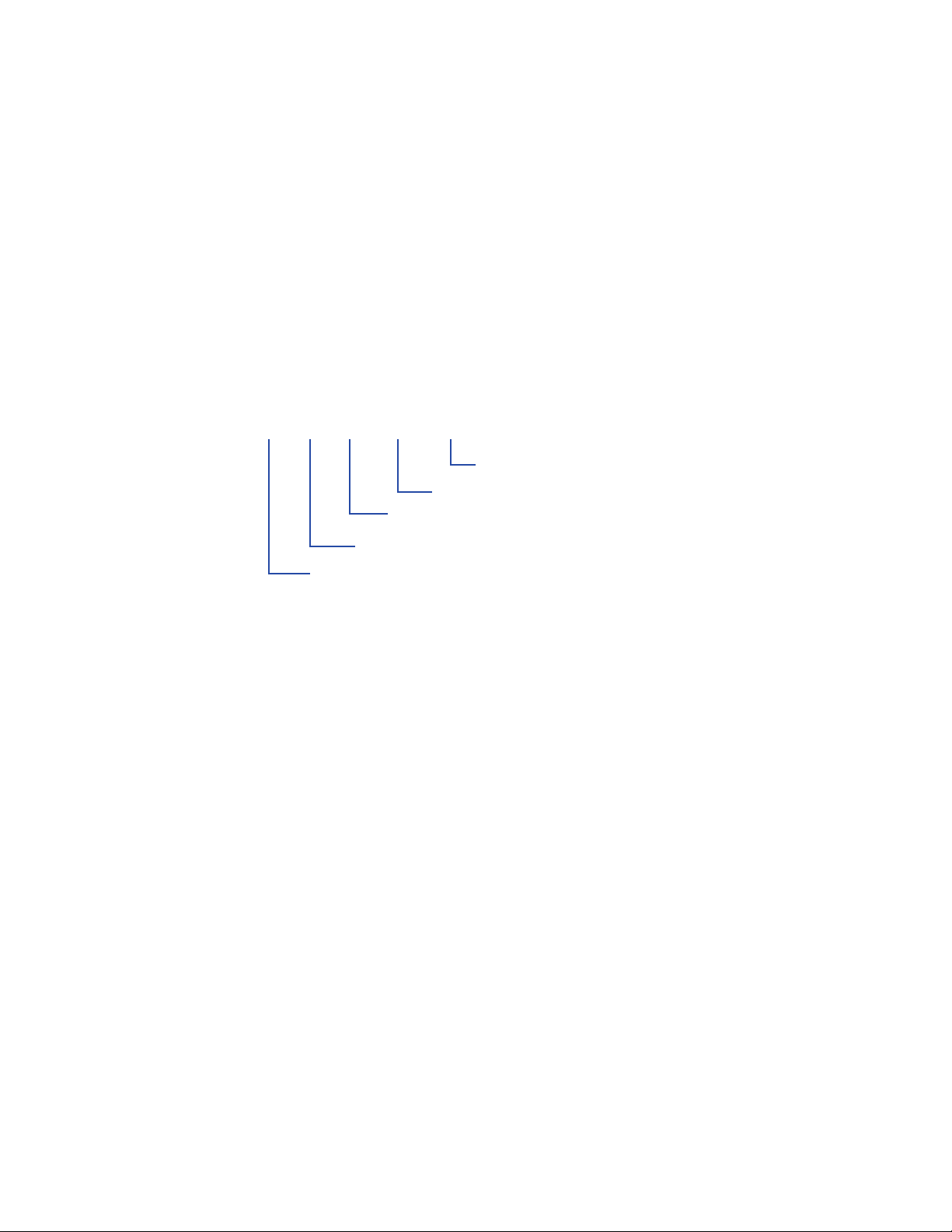
Contacting Meru
Syntax Notation
Courier font is used for code. In syntax descriptions, bold indicates required
keywords and a punctuation. In examples, bold highlights interesting parts. Italics
indicate values that are to be replaced, such as arguments or file names.
bold Required keywords and a punctuation.
italic Arguments.
[ ] Optional elements are enclosed by square brackets.
| Chocies among elements are separated by vertical bars.
{ } Required choice: Braces indicates that one of the enclosed elements must be
used.
… One or more of the preceding element is allowed.
The following figure shows a sample of syntax notation.
{ history | h}
Choose one of enclosed elements
[ number_lines ]
Arguments
Enclosed elements are optional
Separates choices
Keywords, required punctuation
Contacting Meru
You can reach Meru’s automated support services 24 hours a day, every day at no
charge. The services contain the most up-to-date information about Meru products.
You can access installation instructions, troubleshooting information, and general
product information.
Web and Internet Sites
PRELIMINARY
You can use the Internet to download software updates, troubleshooting tips, installation notes, and more.
For specific types of information and services, go to the following Web and Internet
sites:
Corporate: http://www.merunetworks.com
Wireless networking products: http://www.merunetworks.com/
FTP host: download.merunetworks.com
FTP directory: /support/network/
Revision 0.1, July 2003
About This Document ix

Contacting Meru
Customer Support Technicians
United States and Canada: (7:00 - 17:00 M-F Pacific Time)
PRELIMINARY
x About This Document
Revision 0.1, July 2003

Chapter 1
Key Concepts
Network Layout
Corporate network
PRELIMINARY
Revision 0.1, month 2003
Controller (WNC)
Access Point (ATS )
Subcontroller (ASC)
Ethernet Switch
Access Point
Access Point
Access Point
Access Point
Key Concepts 1

Node Identification
Node Identification
A node is a piece of equipment in a Meru wireless network. Each node is uniquely
identified by two pieces of information:
The node type: One of WNC (a controller), ASC (a subcontroller; contained
within the controller), or ATS (an access point).
The node number: An integer; unique within the node type.
Many commands require only a node number because the command is specific to a
node type. Other commands require both the node type and the node number.
For example, if a network contains one controller (which always contains a subcontroller) and three access points, they are identified as follows:
Description Node Type Node Number
Controller WNC 1
Subcontroller ASC 1
First installed access point ATS 1
Second installed access point ATS 2
Third installed access point ATS 3
If the first access point is removed from the network and a new one is installed, the
new one becomes ATS 4, not ATS 1.
Serial Numbers and Node Numbers
When you connect an access point to your Meru wireless network, the controller
automatically reads its serial number and assigns it a permanent node number. This
node number acts as an alias for the serial number, so if an access point is unplugged
and placed elsewhere in the network, the controller recognizes the access point as the
same node number.
When you configure an access point, the configuration in the controller belongs to the
node number, so the configuration can follow the access point.
Using the Controller Console and the CLI
You can connect to the controller using one of three methods:
SSH
Telnet
PRELIMINARY
Serial port
Your connection serves as the console for the controller. Logging in to the controller
places you into the Meru command-line interface (CLI), which is similar to a
command shell. The prompt for the CLI is
2 Key Concepts
Revision 0.1, month 2003

Using the Controller Console and the CLI
wnc>
Use the console command to adjust the appearance of the console display.
The CLI keeps a history of the commands typed during your current session. Use the
history command to list these commands . For example:
wnc> history
1 help
2 console set columns=80 rows=60
3 history
Each history line is displayed with a number. You can redisplay any previous
command for editing by typing an exclamation point (!) followed by the line number.
For example:
wnc> !2
wnc> console set columns=80 rows=60
The cursor remains at the end of the redisplayed line so that you can edit the
command. The CLI supports the following keystrokes to position the cursor for
editing:
Keyboard key
Home Position cursor at the beginning of the command line.
End Position cursor at the end of the command line.
Right arrow ( ---> ) Move the cursor to the right.
Left arrow (<---) Move the cursor to the left.
Backspace, Delete, Del Remove the characterto the left of the cursor position.
Up arrow, down arrow Scroll through the command history and allow editing on
whichever line the cursor is positioned. This command
becomes your current command.
ESC Clears the command line.
For example:
wnc> history
1 help
2 console set columns=80 rows=60
3 history
4 console set columns=80 rows=20
PRELIMINARY
Pressing the up arrow redisplays the preceding commands one at a time, in reverse
order, on the command line. For example, if you scroll through the commands to the
first command executed and then press return, it executes that command line, so your
next command history is:
Revision 0.1, month 2003
Key Concepts 3

Using the Controller Console and the CLI
1 help
2 console set columns=80 rows=60
3 history
4 console set columns=80 rows=20
5 help
PRELIMINARY
4 Key Concepts
Revision 0.1, month 2003

Chapter 2
CLI Command Reference
This chapter describes the syntax and operation of all CLI commands.
Commands are organized alphabetically within categories. The categories are
“Alarms Commands” on page 3
“asc: Subcontroller Commands” on page 5
“ats: Access Point Commands” on page 8
“auth: RADIUS Authentication Commands” on page 12
“Channel BSSID Commands” on page 15
“connect or remote: Remote Connection Commands” on page 17
“Console Commands” on page 18
PRELIMINARY
Revision 0.1, July 2003
“db: Configuration Backup Commands” on page 20
“Help Commands” on page 22
“History Commands” on page 23
“if...stats: Interface Statistics Commands” on page 24
“if: Interface Commands” on page 29
“qoS or codec: Quality of Service Commands” on page 32
“qosrule or ruleQoS: Rule Commands” on page 36
“Quit Commands” on page 42
“Reboot (or restart) Commands” on page 43
“security: RADIUS Security Commands” on page 45
CLI Command Reference 1

Overview
Overview
“SNMP Commands” on page 47
“Station Commands” on page 50
“topo: Network Topology Commands” on page 53
“Watchdog Commands” on page 57
“wirelessif or wif: Wireless Interface Commands” on page 59
“wnc: Controller Commands” on page 63
The CLI recognizes three classes of user. The ability to use commands in this chapter
depends on the user’s class. Users can be:
User Class Description
guest Can use only those commands that display information.
admin Can use most commands, including all the commands that guest can use.
support Can use all commands.
PRELIMINARY
2 CLI Command Reference
Revision 0.1, July 2003
Alarms Commands
These commands provide information about alarm or error status in the Meru wireless network.
alarms
Displays the controller’s alarm log.
Syntax alarms
Alarms Commands
Description Displays the controller’s alarm log file, showing the date and time of each event along
with the originating node and the severity of the alarm. The log lists all alarms for all
nodes in the Meru wireless network that have occurred since the controller’s most
recent reboot.
If there have been no alarms, the command displays
No entries.
Otherwise, the command lists the following information for each alarm:
Information Description
Time Date and time of the alarm in UTC (MM/DD hh:mm:ss), where:
MM = Month number (01 - 12).
DD = Day number.
hh = Hour (00 - 23).
mm = Minute.
ss = Second.
Node Consists of two parts:
PRELIMINARY
Node Type, one of ATS (an access point), ASC (a subcontroller), or WNC
(a controller)
Revision 0.1, July 2003
Node number within that type: An integer
CLI Command Reference 3
Alarms Commands
Information Description
Type Alarm type. One of the following:
LINK UP
LINK DOWN
ASC DOWN
ATS DOWN
WATCHDOG FAILURE
Severity The severity of the alarm, either CRITICAL or CLEAR (alarm state has
been cleared
Example To view the alarm log:
wnc> alarms
This produces output similar to the following:
Time (UTC) Node Type Severity
-------------- -------- ------------------------- ------------07/17 17:25:55 ATS 0001 LINK UP CLEAR
PRELIMINARY
4 CLI Command Reference
Revision 0.1, July 2003

asc: Subcontroller Commands
asc: Subcontroller Commands
These commands manage aspects of subcontrollers.
asc all
Displays configuration information for all subcontrollers recognized by the
controller. See asc get for details.
Syntax asc all
asc get
Displays configuration information for one or more subcontrollers.
Syntax asc get node_id [...]
Argument Description
node_id One or more node numbers identifying subcontrollers that are associated with
this controller. Information is displayed for all the listed subcontrollers.
NOTE:
Description Displays the following configuration information for each of the specified subcon-
trollers:
Field Description
PRELIMINARY
Node ID The unique numeric ID of the subcontroller.
Serial Number Serial number of the subcontroller.
Description A text description of this subcontroller.
To list information for all subcontrollers, use asc all.
Revision 0.1, July 2003
CLI Command Reference 5

asc: Subcontroller Commands
Field Description
Uptime The uptime of the subcontroller, in hours, minutes, and seconds
Location A text description of the location of this subcontroller.
Contact Person or organization responsible for this subcontroller.
(hh:mm:ss).
Operational
State
Availability Status
Alarm State The severity of the current alarm on the subcontroller. If more than one
Virtual MAC
Address
Software Version
The operational state of the subcontroller:
ENABLED: The subcontroller is operating correctly.
DISABLED: The subcontrollers is found by the controller but it is not
operating correctly.
The availability of the subcontroller:
OFFLINE: The controller cannot find the subcontroller.
ONLINE: The controller can find the subcontroller.
alarm is current, the highest severity is displayed. In order of increasing
severity, the states are
NO ALARM: The subcontroller is not in an alarm state.
MINOR
MAJOR
CRITICAL.
The virtual MAC address of the wireless network to which this subcontroller belongs. This value is set with the wnc set command.
The version of the software running on the subcontroller.
asc ids
Displays the node numbers for all known subcontrollers.
Syntax asc ids
Description Displays a list of node numbers of type ASC that are associated with this controller.
6 CLI Command Reference
PRELIMINARY
Numbers are displayed one on each output line.
Revision 0.1, July 2003

Example
asc set
Sets one or more of the configuration values for the specified subcontroller.
Syntax asc set node_id
[ desc=<val> ]
[ location=<val> ]
[ contact=<val> ]
[ {wncdns=<val> | dns=<val>} ]
Argument Description
node_id The unique numeric ID of the subcontroller.
asc: Subcontroller Commands
desc A text description for this subcontroller
location A text description of the location of this subcontroller.
contact Text name for the person or organization responsible for this subcontrol-
ler.
Description You must specify at least one configuration value.
PRELIMINARY
Revision 0.1, July 2003
CLI Command Reference 7

ats: Access Point Commands
ats: Access Point Commands
These commands manage aspects of access points.
ats all
Displays configuration information for all access point recognized by the controller.
See ats get for details.
Syntax ats all
ats get
Displays configuration information for one or more access points.
Syntax ats get node_id [...]
Argument Description
node_id One or more node numbers identifying access points that are associated with
this controller. Information is displayed for all the listed access point.
NOTE:
Description Displays the following configuration information for each of the specified access
points:
Field Description
To list information for all access points, use ats all.
PRELIMINARY
Node ID The unique numeric ID of the access point.
Serial Number Serial number of the access point.
Description A text description for this access point.
8 CLI Command Reference
Revision 0.1, July 2003

ats: Access Point Commands
Field Description
Uptime The uptime of the access point, in hours, minutes, and seconds
(hh:mm:ss).
Location Text description of the location of this access point.
Contact Person or organization responsible for this access point.
Operational State The operational state of the access point:
ENABLED: The access point is operating correctly.
DISABLED: The access point is known by the controller but it is not
operating correctly.
Availability Status The availability of the access point:
OFFLINE: The controller cannot find the access point.
ONLINE: The controller can find the access point.
Alarm State The severity of the current alarm on the access point. If more than one
alarm is current, the highest severity is displayed. In order of increasing severity, the states are NO ALARM, MINOR, MAJOR, or CRITICAL.
ats ids
PRELIMINARY
Bound to ASC The subcontroller node ID to which the access point is bound.
Security Mode The security mode that the access point is in; either OPEN or 802.1x.
Privacy Bit The privacy state that the access point is in; one of ON, OFF, or AUTO.
Boot Script The script to run when the access point boots.
Virtual MAC Address The virtual MAC address of the access point.
Boot Image Version The version of the ROM boot image on the access point.
Runtime Image Version
FPGA Version The version of the FPGA chip on the access point.
Displays the node numbers for all known access points.
The version of the runtime image on the access point.
Syntax ats ids
Revision 0.1, July 2003
CLI Command Reference 9

ats: Access Point Commands
Description Displays a list of node numbers of type ATS that are associated with this controller.
Numbers are displayed one on each output line.
ats images
Lists access point upgrade image versions that have been copied to the controller.
ats mappings
Displays access point comm node and nms node ID mappings.
ats scripts
Lists available access point boot scripts.
See wnc set for information on how to assign a default script for all access points.
See ats set for how to assign a script to a specific access point.
ats set
Sets one or more of the configuration values for the specified access point.
Syntax ats set <node_id>
[ desc=text_desc ]
PRELIMINARY
[ location=text_loc ]
[ contact=text_contact ]
[ bootscript=script_name ]
10 CLI Command Reference
Revision 0.1, July 2003

Argument Description
desc Text description for this access point.
location Text description of the location of this access point.
contact Person or organization responsible for this access point.
bootscript The name of the script to run when the access point boots. Use ats
ats upgrade
Installs upgraded software onto the ATS.
ats: Access Point Commands
scripts to display the names of valid scripts. See wnc set for additional
information.
Syntax ats upgrade {<node-id> | all}
<version>
[noreboot | <delay>]
To upgrade the software on an ATS, enter its node id and the version that was previously downloaded onto the WNC. Available images may be listed using the 'ats
images' command. After the upgrade the ATS will reboot immediately when the
upgrade is complete, unless the 'noreboot' option or a delay (in seconds) is given as
the last argument.
PRELIMINARY
Revision 0.1, July 2003
CLI Command Reference 11
auth: RADIUS Authentication Commands
auth: RADIUS Authentication
Commands
These commands allow a user to manage RADIUS authentication information
(authentication secret and RADIUS IP address).
auth all
Displays configuration information for all RADIUS authentications. See auth get for
details.
Syntax auth all
auth del
Deletes the authentications specified by the authentication IDs.
Syntax auth del <auth_id> [...]
auth get
Displays configuration information for one or more authentications.
Syntax auth get <auth_id> [...]
PRELIMINARY
12 CLI Command Reference
Revision 0.1, July 2003
auth: RADIUS Authentication Commands
Argument Description
auth_id One or more numbers identifying authentications that are associated with this
controller. Information is displayed for all the listed items.
NOTE:
Description Displays the following fields for each of the authentications requested:
Field Description
Authentication ID A unique alphanumeric ID of the RADIUS server information.
RADIUS Server Secret The string to hold the RADIUS secret key.
RADIUS Server IP
Address
To list information for all subcontrollers, use auth all.
IP address of the RADIUS server in nnn.nnn.nnn.nnn format.
auth new
Create a new authentication.
Syntax auth new <auth_id>
[
[ {radiusip=<val> | ip=<val>} ]
{radiussecret=<val> | secret=<val>} ]
PRELIMINARY
auth set
Revision 0.1, July 2003
Argument Description
{radiussecret=<val> |
secret=<val>}
{radiusip=<val> | ip=<val>} IP address of the RADIUS server in nnn.nnn.nnn.nnn format.
Sets one or more of the configuration values for the specified authentication.
The string to hold the RADIUS secret key.
CLI Command Reference 13
 Loading...
Loading...