Page 1

User Guide
Page 2

Page 3

Contents
Introduction 3
McAfee SecurityCenter.......................................................................................................5
SecurityCenter features ............................................................................................ 6
Using SecurityCenter ................................................................................................ 7
Updating SecurityCenter........................................................................................ 13
Fixing or ignoring protection problems ................................................................17
Working with alerts ................................................................................................. 21
Viewing events......................................................................................................... 27
McAfee VirusScan ............................................................................................................. 29
VirusScan features................................................................................................... 30
Starting real-time virus protection......................................................................... 31
Starting additional protection................................................................................33
Setting up virus protection ..................................................................................... 37
Scanning your computer ........................................................................................ 53
Working with scan results....................................................................................... 57
McAfee Personal Firewall................................................................................................. 61
Personal Firewall features....................................................................................... 62
Starting Firewall ...................................................................................................... 65
Working with alerts ................................................................................................. 67
Managing informational alerts............................................................................... 69
Configuring Firewall protection............................................................................. 71
Managing programs and permissions ................................................................... 83
Managing system services ...................................................................................... 91
Managing computer connections.......................................................................... 97
Logging, monitoring, and analysis....................................................................... 105
Learning about Internet security .........................................................................115
McAfee QuickClean ........................................................................................................ 117
QuickClean features.............................................................................................. 118
Cleaning your computer....................................................................................... 119
Defragmenting your computer ............................................................................ 122
Scheduling a task................................................................................................... 123
McAfee Shredder............................................................................................................. 129
Shredder features .................................................................................................. 130
Shredding files, folders, and disks........................................................................ 131
McAfee Network Manager.............................................................................................. 133
Network Manager features ................................................................................... 134
Understanding Network Manager icons ............................................................. 135
Setting up a managed network............................................................................. 137
Managing the network remotely.......................................................................... 145
McAfee EasyNetwork...................................................................................................... 151
EasyNetwork features ........................................................................................... 152
Setting up EasyNetwork........................................................................................ 153
Sharing and sending files...................................................................................... 159
Sharing printers..................................................................................................... 165
i
Page 4

ii Contents
Reference......................................................................................................................... 168
Glossary 169
About McAfee 183
Copyright ............................................................................................................... 183
License ................................................................................................................... 184
Customer and Technical Support.................................................................................. 185
Using McAfee Virtual Technician ........................................................................ 186
Support and Downloads....................................................................................... 186
Index 196
Page 5

C HAPTER 1
Introduction
McAfee VirusScan Plus offers proactive PC security to prevent
malicious attacks, so you can protect what you value as well as
surf, search, and download files online with confidence. McAfee
SiteAdvisor’s Web safety ratings, help you avoid unsafe Web sites.
This service also provides security against multi-pronged attacks
by combining anti-virus, anti-spyware and firewall technologies.
McAfee’s security service continuously delivers the latest
software so your protection is never out-of-date. You can now
easily add and manage security for multiple PCs in your home.
Moreover, improved performance allows it to protect, without
disturbing you.
In this chapter
3
McAfee SecurityCenter ...............................................5
McAfee VirusScan .......................................................29
McAfee Personal Firewall ........................................... 61
McAfee QuickClean.....................................................117
McAfee Shredder.........................................................129
McAfee Network Manager..........................................133
McAfee EasyNetwork ..................................................151
Reference ..................................................................... 168
About McAfee ..............................................................183
Customer and Technical Support.............................. 185
Page 6

Page 7

C HAPTER 2
McAfee SecurityCenter
McAfee SecurityCenter allows you to monitor your computer's
security status, know instantly whether your computer's virus,
spyware, e-mail, and firewall protection services are up-to-date,
and act on potential security vulnerabilities. It provides the
navigational tools and controls you need to coordinate and
manage all areas of your computer's protection.
Before you begin configuring and managing your computer's
protection, review the SecurityCenter interface and make sure
that you understand the difference between protection status,
protection categories, and protection services. Then, update
SecurityCenter to ensure that you have the latest protection
available from McAfee.
After your initial configuration tasks are complete, you use
SecurityCenter to monitor your computer's protection status. If
SecurityCenter detects a protection problem, it alerts you so that
you can either fix or ignore the problem (depending on its
severity). You can also review SecurityCenter events, such as virus
scanning configuration changes, in an event log.
5
Note: SecurityCenter reports critical and non-critical protection
problems as soon as it detects them. If you need help diagnosing
your protection problems, you can run McAfee Virtual
Technician.
In this chapter
SecurityCenter features ..............................................6
Using SecurityCenter..................................................7
Updating SecurityCenter............................................13
Fixing or ignoring protection problems ....................17
Working with alerts .....................................................21
Viewing events............................................................. 27
Page 8

6 McAfee VirusScan Plus
SecurityCenter features
SecurityCenter provides the following features:
Simplified protection status
Easily review your computer's protection status, check for
updates, and fix potential protection problems.
Automated updates and upgrades
Automatically download and install updates for your registered
programs. When a new version of a registered McAfee program is
available, you get it at no charge while your subscription is valid,
ensuring that you always have up-to-date protection.
Real-time alerting
Security alerts notify you of emergency virus outbreaks and
security threats, and provide options to remove, neutralize, or
learn more about the threat.
Page 9

C HAPTER 3
Using SecurityCenter
Before you begin using SecurityCenter, review the components
and configuration areas you will use to manage your computer's
protection status. For more information about the terminology
used in this image, see
and
Understanding protection categories (page 9). Then, you can
review your McAfee account information and verifying the
validity of your subscription.
7
Understanding protection status (page 8)
In this chapter
Understanding protection status...............................8
Understanding protection categories........................9
Understanding protection services ...........................10
Managing your McAfee account ................................11
Page 10
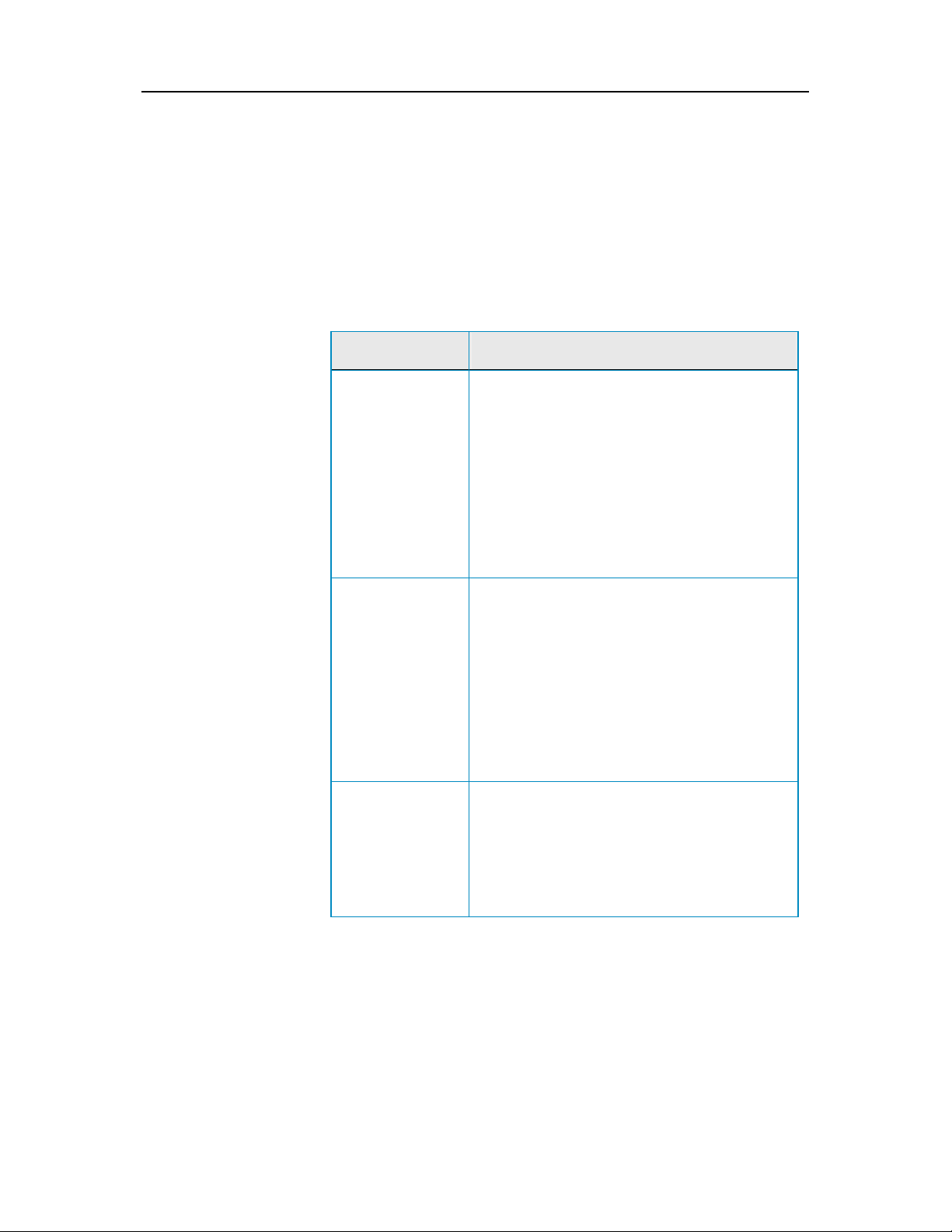
8 McAfee VirusScan Plus
Understanding protection status
Your computer's protection status is shown in the protection
status area on the SecurityCenter Home pane. It indicates
whether your computer is fully protected against the latest
security threats and can be influenced by things like external
security attacks, other security programs, and programs that
access the Internet.
Your computer's protection status can be red, yellow, or green.
Protection Status Description
Red Your computer is not protected. The protection
status area on the SecurityCenter Home pane is
red and states that you are not protected.
SecurityCenter reports at least one critical
security problem.
To achieve full protection, you must fix all
critical security problems in each protection
category (the problem category's status is set to
Action Required, also in red). For information
about how to fix protection problems, see
protection problems
(page 18).
Fixing
Yellow Your computer is partially protected. The
protection status area on the SecurityCenter
Home pane is yellow and states that you are not
protected. SecurityCenter reports at least one
non-critical security problem.
To achieve full protection, you must fix or ignore
the non-critical security problems associated
with each protection category. For information
about how to fix or ignore protection problems,
Fixing or ignoring protection problems
see
(page 17).
Green Your computer is fully protected. The protection
status area on the SecurityCenter Home pane is
green and states that you are protected.
SecurityCenter does not report any critical or
non-critical security problems.
Each protection category lists the services that
are protecting your computer.
Page 11
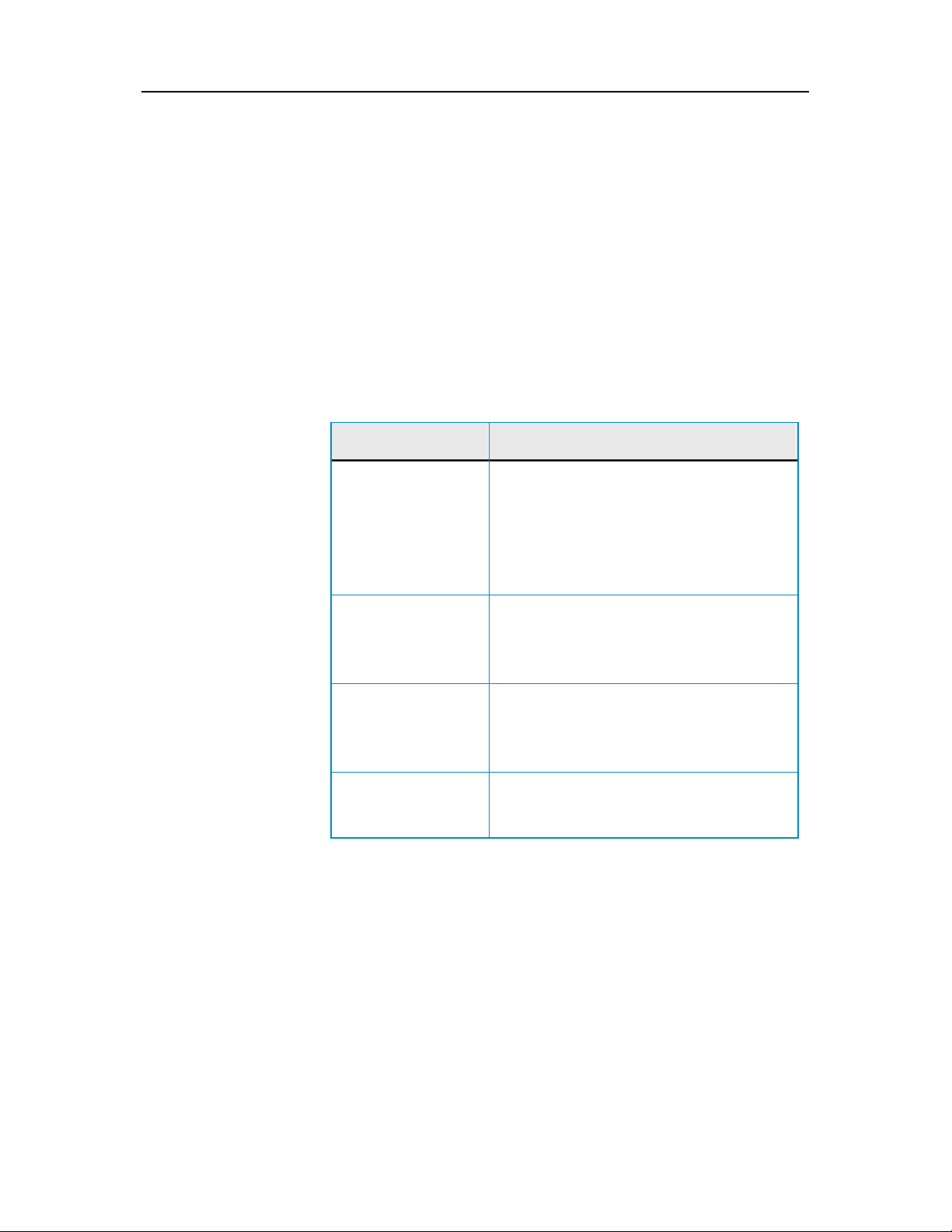
Chapter 3 Introduction 9
Understanding protection categories
SecurityCenter's protection services are divided into four
categories: Computer & Files, Internet & Network, E-mail & IM,
and Parental Controls. These categories help you to browse and
configure the security services protecting your computer.
You click a category name to configure its protection services and
view any security problems detected for those services. If your
computer's protection status is red or yellow, one or more
categories display an Action Required or Attention message,
indicating that SecurityCenter has detected a problem within the
category. For more information about protection status, see
Understanding protection status (page 8).
Protection Category Description
Computer & Files The Computer & Files category lets you
configure the following protection services:
Virus Protection
PUP Protection
System Monitors
Windows Protection
Internet & Network The Internet & Network category lets you
configure the following protection services:
Firewall Protection
Identity Protection
E-mail & IM The E-mail & IM category lets you configure
the following protection services:
E-mail Protection
Spam Protection
Parental Controls The Parental Controls category lets you
configure the following protection services:
Content Blocking
Page 12

10 McAfee VirusScan Plus
Understanding protection services
Protection services are the core SecurityCenter components that
you configure to protect your computer. Protection services
directly correspond to McAfee programs. For example, when you
install VirusScan, the following protection services become
available: Virus Protection, PUP Protection, System Monitors,
and Windows Protection. For detailed information about these
particular protection services, see the VirusScan help.
By default, all protection services associated with a program are
enabled when you install the program; however you can disable a
protection service at any time. For example, if you install Privacy
Service, Content Blocking and Identity Protection are both
enabled. If you do not intend to use the Content Blocking
protection service, you can disable it entirely. You can also
temporarily disable a protection service while performing setup
or maintenance tasks.
Page 13

Chapter 3 Introduction 11
Managing your McAfee account
Manage your McAfee account from within SecurityCenter by
easily accessing and reviewing your account information and
verifying your current subscription status.
Note: If you installed your McAfee programs from a CD, you must
register them on the McAfee Web site to set up or update your
McAfee account. Only then are you entitled to regular, automatic
program updates.
Manage your McAfee account
You can easily access your McAfee account information (My
Account) from SecurityCenter.
1 Under Common Tasks, click My Account.
2 Log in to your McAfee account.
Verify your subscription
You verify your subscription to ensure that it has not yet expired.
Right-click the SecurityCenter icon
in the notification area
at the far right of your taskbar, and then click Verify
Subscription.
Page 14

Page 15

C HAPTER 4
Updating SecurityCenter
SecurityCenter ensures that your registered McAfee programs are
current by checking for and installing online updates every four
hours. Depending on the programs you have installed and
registered, online updates may include the latest virus definitions
and hacker, spam, spyware, or privacy protection upgrades. If
you want to check for updates within the default four hour
period, you can do so at any time. While SecurityCenter is
checking for updates, you can continue to perform other tasks.
Although it is not recommended, you can change the way
SecurityCenter checks for and installs updates. For example, you
can configure SecurityCenter to download but not install updates
or to notify you before downloading or installing updates. You
can also disable automatic updating.
Note: If you installed your McAfee programs from a CD, you
cannot receive regular, automatic updates for those programs
unless you register them on the McAfee Web site.
13
In this chapter
Check for updates .......................................................13
Configure automatic updates.....................................14
Disable automatic updates......................................... 14
Check for updates
By default, SecurityCenter automatically checks for updates every
four hours when your computer is connected to the Internet;
however, if you want to check for updates within the four hour
period, you can do so. If you have disabled automatic updates, it
is your responsibility to check for updates regularly.
On the SecurityCenter Home pane, click Update.
Tip: You can check for updates without launching SecurityCenter
by right-clicking the SecurityCenter icon in the notification
area at the far right of your taskbar, and then clicking Updates.
Page 16

14 McAfee VirusScan Plus
Configure automatic updates
By default, SecurityCenter automatically checks for and installs
updates every four hours when your computer is connected to
the Internet. If you want to change this default behavior, you can
configure SecurityCenter to automatically download updates and
then notify you when the updates are ready to be installed or to
notify you before downloading the updates.
Note: SecurityCenter notifies you when updates are ready to be
downloaded or installed using alerts. From the alerts, you can
either download or install the updates, or postpone the updates.
When you update your programs from an alert, you may be
prompted to verify your subscription before downloading and
installing. For more information, see Working with alerts (page
21).
1 Open the SecurityCenter Configuration pane.
How?
1. Under Common Tasks, click Home.
2. On the right pane, under SecurityCenter
Information, click Configure.
2 On the SecurityCenter Configuration pane, under Automatic
updates are disabled, click On, and then click Advanced.
3 Click one of the following buttons:
Install the updates automatically and notify me when
my services are updated (recommended)
Download the updates automatically and notify me
when they are ready to be installed
Notify me before downloading any updates
4 Click OK.
Disable automatic updates
If you disable automatic updates, it is your responsibility to check
for updates regularly; otherwise, your computer will not have the
latest security protection. For information about checking for
updates manually, see
1 Open the SecurityCenter Configuration pane.
How?
Check for updates (page 13).
Page 17

Chapter 4 Introduction 15
1. Under Common Tasks, click Home.
2. On the right pane, under SecurityCenter
Information, click Configure.
2 On the SecurityCenter Configuration pane, under Automatic
updates are enabled, click Off.
Tip: You enable automatic updates by clicking the On button or
by clearing Disable automatic updating and let me manually
check for updates on the Update Options pane.
Page 18

Page 19

C HAPTER 5
Fixing or ignoring protection problems
SecurityCenter reports critical and non-critical protection
problems as soon as it detects them. Critical protection problems
require immediate action and compromise your protection status
(changing the color to red). Non-critical protection problems do
not require immediate action and may or may not compromise
your protection status (depending on the type of problem). To
achieve a green protection status, you must fix all critical
problems and either fix or ignore all non-critical problems. If you
need help diagnosing your protection problems, you can run
McAfee Virtual Technician. For more information about McAfee
Virtual Technician, see the McAfee Virtual Technician help.
In this chapter
Fixing protection problems........................................ 18
Ignoring protection problems....................................19
17
Page 20

18 McAfee VirusScan Plus
Fixing protection problems
Most security problems can be fixed automatically; however,
some problems may require you to take action. For example, if
Firewall Protection is disabled, SecurityCenter can enable it
automatically; however, if Firewall Protection is not installed, you
must install it. The following table describes some other actions
that you might take when fixing protection problems manually:
Problem Action
A full scan of your computer has
not been performed in the last 30
days.
Scan your computer manually. For
more information, see the VirusScan
help.
Your detection signature files
(DATs) are out-of-date.
A program is not installed. Install the program from the McAfee
A program is missing
components.
A program is not registered, and
cannot receive full protection.
A program has expired. Check your account status on the
Update your protection manually.
For more information, see the
VirusScan help.
Web site or CD.
Reinstall the program from the
McAfee Web site or CD.
Register the program on the McAfee
Web site.
McAfee Web site.
Note: Often, a single protection problem affects more than one
protection category. In this case, fixing the problem in one
category clears it from all other protection categories.
Fix protection problems automatically
SecurityCenter can fix most protection problems automatically.
The configuration changes that SecurityCenter makes when
automatically fixing protection problems are not recorded in the
event log. For more information about events, see
Viewing events
(page 27).
1 Under Common Tasks, click Home.
2 On the SecurityCenter Home pane, in the protection status
area, click Fix.
Fix protection problems manually
If one or more protection problems persist after you try to fix
them automatically, you can fix the problems manually.
1 Under Common Tasks, click Home.
2 On the SecurityCenter Home pane, click the protection
category in which SecurityCenter reports the problem.
3 Click the link following the description of the problem.
Page 21

Chapter 5 Introduction 19
Ignoring protection problems
If SecurityCenter detects a non-critical problem, you can either
fix or ignore it. Other non-critical problems (for example, if
Anti-Spam or Privacy Service are not installed) are automatically
ignored. Ignored problems are not shown in the protection
category information area on the SecurityCenter Home pane,
unless your computer's protection status is green. If you ignore a
problem, but later decide that you want it to appear in the
protection category information area even when your computer's
protection status is not green, you can show the ignored problem.
Ignore a protection problem
If SecurityCenter detects a non-critical problem that you do not
intend to fix, you can ignore it. Ignoring it removes the problem
from the protection category information area in SecurityCenter.
1 Under Common Tasks, click Home.
2 On the SecurityCenter Home pane, click the protection
category in which the problem is reported.
3 Click the Ignore link beside the protection problem.
Show or hide ignored problems
Depending on its severity, you can show or hide an ignored
protection problem.
1 Open the Alert Options pane.
How?
1. Under Common Tasks, click Home.
2. On the right pane, under SecurityCenter
Information, click Configure.
3. Under Alerts, click Advanced.
2 On the SecurityCenter Configuration pane, click Ignored
Problems.
3 On the Ignored Problems pane, do the following:
To ignore a problem, select its check box.
To report a problem in the protection category
information area, clear its check box.
4 Click OK.
Tip: You can also ignore a problem by clicking the Ignore link
beside the reported problem in the protection category
information area.
Page 22

Page 23

C HAPTER 6
Working with alerts
Alerts are small pop-up dialog boxes that appear in the
bottom-right corner of your screen when certain SecurityCenter
events occur. An alert provides detailed information about an
event as well as recommendations and options for resolving
problems that may be associated with the event. Some alerts also
contain links to additional information about the event. These
links let you launch McAfee's global Web site or send information
to McAfee for troubleshooting.
There are three types of alerts: red, yellow, and green.
Alert Type Description
Red A red alert is a critical notification that requires a
21
response from you. Red alerts occur when
SecurityCenter cannot determine how to fix a
protection problem automatically.
Yellow A yellow alert is a non-critical notification that
usually requires a response from you.
Green A green alert is a non-critical notification that does
not require a response from you. Green alerts
provide basic information about an event.
Because alerts play such an important role in monitoring and
managing your protection status, you cannot disable them.
However, you can control whether certain types of informational
alerts appear and configure some other alert options (such as
whether SecurityCenter plays a sound with an alert or displays
the McAfee splash screen on startup).
In this chapter
Showing and hiding informational alerts..................22
Configuring alert options ...........................................24
Page 24

22 McAfee VirusScan Plus
Showing and hiding informational alerts
Informational alerts notify you when events occur that do not
pose threats to your computer's security. For example, if you
have set up Firewall Protection, an informational alert appears by
default whenever a program on your computer is granted access
to the Internet. If you do not want a specific type of informational
alert to appear, you can hide it. If you do not want any
informational alerts to appear, you can hide them all. You can
also hide all informational alerts when you play a game in
full-screen mode on your computer. When you finish playing the
game and exit full-screen mode, SecurityCenter starts displaying
informational alerts again.
If you mistakenly hide an informational alert, you can show it
again at any time. By default, SecurityCenter shows all
informational alerts.
Show or hide informational alerts
You can configure SecurityCenter to show some informational
alerts and hide others, or to hide all informational alerts.
1 Open the Alert Options pane.
How?
1. Under Common Tasks, click Home.
2. On the right pane, under SecurityCenter
Information, click Configure.
3. Under Alerts, click Advanced.
2 On the SecurityCenter Configuration pane, click
Informational Alerts.
3 On the Informational Alerts pane, do the following:
To show an informational alert, clear its check box.
To hide an informational alert, select its check box.
To hide all informational alerts, select the Do not show
informational alerts check box.
4 Click OK.
Tip: You can also hide an informational alert by selecting the Do
not show this alert again check box in the alert itself. If you do
so, you can show the informational alert again by clearing the
appropriate check box on the Informational Alerts pane.
Page 25

Chapter 6 Introduction 23
Show or hide informational alerts when gaming
You can hide informational alerts when you are playing a game in
full-screen mode on your computer. When you finish the game
and exit full-screen mode, SecurityCenter starts displaying
informational alerts again.
1 Open the Alert Options pane.
How?
1. Under Common Tasks, click Home.
2. On the right pane, under SecurityCenter
Information, click Configure.
3. Under Alerts, click Advanced.
2 On the Alert Options pane, select or clear the Show
informational alerts when gaming mode is detected
check box.
3 Click OK.
Page 26

24 McAfee VirusScan Plus
Configuring alert options
The appearance and frequency of alerts is configured by
SecurityCenter; however, you can adjust some basic alert options.
For example, you can play a sound with alerts or hide the splash
screen alert from displaying when Windows starts. You can also
hide alerts that notify you about virus outbreaks and other
security threats in the online community.
Play a sound with alerts
If you want to receive an audible indication that an alert has
occurred, you can configure SecurityCenter to play a sound with
each alert.
1 Open the Alert Options pane.
How?
1. Under Common Tasks, click Home.
2. On the right pane, under SecurityCenter
Information, click Configure.
3. Under Alerts, click Advanced.
2 On the Alert Options pane, under Sound, select the Play a
sound when an alert occurs check box.
Hide the splash screen at startup
By default, the McAfee splash screen appears briefly when
Windows starts, notifying you that SecurityCenter is protecting
your computer. However, you can hide the splash screen if you
do not want it to appear.
1 Open the Alert Options pane.
How?
1. Under Common Tasks, click Home.
2. On the right pane, under SecurityCenter
Information, click Configure.
3. Under Alerts, click Advanced.
2 On the Alert Options pane, under Splash Screen, clear the
Show the McAfee splash screen when Windows starts
check box.
Tip: You can show the splash screen again at any time by
selecting the Show the McAfee splash screen when Windows
starts check box.
Page 27

Chapter 6 Introduction 25
Hide virus outbreak alerts
You can hide alerts that notify you about virus outbreaks and
other security threats in the online community.
1 Open the Alert Options pane.
How?
1. Under Common Tasks, click Home.
2. On the right pane, under SecurityCenter
Information, click Configure.
3. Under Alerts, click Advanced.
2 On the Alert Options pane, clear the Alert me when a virus
or security threat occurs check box.
Tip: You can show virus outbreak alerts at any time by selecting
the Alert me when a virus or security threat occurs check box.
Page 28

Page 29

C HAPTER 7
Viewing events
27
An event is an action or configuration change that occurs within a
protection category and its related protection services. Different
protection services record different types of events. For example,
SecurityCenter records an event if a protection service is enabled
or disabled; Virus Protection records an event each time a virus is
detected and removed; and Firewall Protection records an event
each time an Internet connection attempt is blocked. For more
information about protection categories, see
protection categories
(page 9).
Understanding
You can view events when troubleshooting configuration issues
and reviewing operations performed by other users. Many
parents use the event log to monitor their children's behavior on
the Internet. You view recent events if you want to examine only
the last 30 events that occurred. You view all events if you want to
examine a comprehensive list of all events that occurred. When
you view all events, SecurityCenter launches the event log, which
sorts events according to the protection category in which they
occurred.
In this chapter
View recent events ......................................................27
View all events .............................................................27
View recent events
You view recent events if you want to examine only the last 30
events that occurred.
Under Common Tasks, click View Recent Events.
View all events
You view all events if you want to examine a comprehensive list
of all events that occurred.
1 Under Common Tasks, click View Recent Events.
2 On the Recent Events pane, click View Log.
3 On the event log's left pane, click the type of events you want
to view.
Page 30

Page 31

C HAPTER 8
McAfee VirusScan
VirusScan's advanced detection and protection services defend
you and your computer from the latest security threats, including
viruses, Trojans, tracking cookies, spyware, adware, and other
potentially unwanted programs. Protection extends beyond the
files and folders on your desktop, targeting threats from different
points of entry—including e-mail, instant messages, and the
Web.
With VirusScan, your computer's protection is immediate and
constant (no tedious administration required). While you work,
play, browse the Web, or check your e-mail, it runs in the
background, monitoring, scanning, and detecting potential harm
in real time. Comprehensive scans run on schedule, periodically
checking your computer using a more sophisticated set of
options. VirusScan offers you the flexibility to customize this
behavior if you want to; but if you don't, your computer remains
protected.
29
With normal computer use, viruses, worms, and other potential
threats may infiltrate your computer. If this occurs, VirusScan
notifies you about the threat, but usually handles it for you,
cleaning or quarantining infected items before any damage
occurs. Although rare, further action may sometimes be required.
In these cases, VirusScan lets you decide what to do (rescan the
next time you start your computer, keep the detected item, or
remove the detected item).
Note: SecurityCenter reports critical and non-critical protection
problems as soon as it detects them. If you need help diagnosing
your protection problems, you can run McAfee Virtual
Technician.
In this chapter
VirusScan features....................................................... 30
Starting real-time virus protection ............................31
Starting additional protection....................................33
Setting up virus protection.........................................37
Scanning your computer ............................................53
Working with scan results...........................................57
Page 32

30 McAfee VirusScan Plus
VirusScan features
VirusScan provides the following features.
Comprehensive virus protection
VirusScan's advanced detection and protection services defend
you and your computer from the latest security threats, including
viruses, Trojans, tracking cookies, spyware, adware, and other
potentially unwanted programs. Protection extends beyond the
files and folders and on your desktop, targeting threats from
different points of entry—including e-mail, instant messages, and
the Web. No tedious administration required.
Resource-aware scanning options
If you experience slow scan speeds, then you can disable the
option to use minimal computer resources, but keep in mind that
highter priority will be given to virus protection than to other
tasks. VirusScan offers you the flexibility to customize real-time
and manual scanning options if you want to; but if you don't,
your computer remains protected.
Automatic repairs
If VirusScan detects a security threat while running a real-time or
manual scan, it tries to handle the threat automatically according
to the threat type. This way, most threats can be detected and
neutralized without your interaction. Although rare, VirusScan
may not be able to neutralize a threat on its own. In these cases,
VirusScan lets you decide what to do (rescan the next time you
start your computer, keep the detected item, or remove the
detected item).
Pausing tasks in full-screen mode
When enjoying things like watching movies, playing games on
your computer, or any activity that occupies your entire
computer screen, VirusScan pauses a number of tasks, such as
manual scans.
Page 33

Chapter 8 Introduction 31
Starting real-time virus protection
VirusScan provides two types of virus protection: real-time and
manual. Real-time virus protection constantly monitors your
computer for virus activity, scanning files each time you or your
computer access them. Manual virus protection lets you scan
files on demand. To make sure that your computer stays
protected against the latest security threats, leave real-time virus
protection on and set up a schedule for regular, more
comprehensive, manual scans. By default, VirusScan performs a
scheduled scan once a week. For more information about
real-time and manual scanning, see
(page 53).
Although rare, there may be times when you want to temporarily
stop real-time scanning (for example, to change some scanning
options or troubleshoot a performance issue). When real-time
virus protection is disabled, your computer is not protected and
your SecurityCenter protection status is red. For more
information about protection status, see "Understanding
protection status" in the SecurityCenter help.
Scanning your computer
Start real-time virus protection
By default, real-time virus protection is turned on and protecting
your computer against viruses, Trojans, and other security
threats. If you turn off real-time virus protection, you must turn it
on again to stay protected.
1 Open the Computer & Files Configuration pane.
How?
1. On the left pane, click Advanced Menu.
2. Click Configure.
3. On the Configure pane, click Computer & Files.
2 Under Virus protection, click On.
Stop real-time virus protection
You can turn off real-time virus protection temporarily, and then
specify when it resumes. You can automatically resume
protection after 15, 30, 45, or 60 minutes, when your computer
restarts, or never.
1 Open the Computer & Files Configuration pane.
How?
Page 34

32 McAfee VirusScan Plus
1. On the left pane, click Advanced Menu.
2. Click Configure.
3. On the Configure pane, click Computer & Files.
2 Under Virus protection, click Off.
3 In the dialog box, select when to resume real-time scanning.
4 Click OK.
Page 35

C HAPTER 9
Starting additional protection
In addition to real-time virus protection, VirusScan provides
advanced protection against scripts, spyware, and potentially
harmful e-mail and instant message attachments. By default,
script scanning, spyware, e-mail, and instant messaging
protection are turned on and protecting your computer.
Script scanning protection
Script scanning protection detects potentially harmful scripts
and prevents them from running on your computer. It monitors
your computer for suspect script activity, such as a script that
creates, copies, or deletes files, or opens your Windows registry,
and alerts you before any damage occurs.
Spyware protection
33
Spyware protection detects spyware, adware, and other
potentially unwanted programs. Spyware is software that can be
secretly installed on your computer to monitor your behavior,
collect personal information, and even interfere with your control
of the computer by installing additional software or redirecting
browser activity.
E-mail protection
E-mail protection detects suspect activity in the e-mail and
attachments you send.
Instant messaging protection
Instant messaging protection detects potential security threats
from instant message attachments that you receive. It also
prevents instant messaging programs from sharing personal
information.
In this chapter
Start script scanning protection.................................34
Start spyware protection.............................................34
Start e-mail protection................................................34
Start instant messaging protection............................35
Page 36

34 McAfee VirusScan Plus
Start script scanning protection
Turn on script scanning protection to detect potentially harmful
scripts and prevent them from running on your computer. Script
scanning protection alerts you when a script tries to create, copy,
or delete files on your computer, or make changes to your
Windows registry.
1 Open the Computer & Files Configuration pane.
How?
1. On the left pane, click Advanced Menu.
2. Click Configure.
3. On the Configure pane, click Computer & Files.
2 Under Script scanning protection, click On.
Note: Although you can turn off script scanning protection at any
time, doing so leaves your computer vulnerable to harmful
scripts.
Start spyware protection
Turn on spyware protection to detect and remove spyware,
adware, and other potentially unwanted programs that gather
and transmit information without your knowledge or permission.
1 Open the Computer & Files Configuration pane.
How?
1. On the left pane, click Advanced Menu.
2. Click Configure.
3. On the Configure pane, click Computer & Files.
2 Under Script scanning protection, click On.
Note: Although you can turn off spyware protection at any time,
doing so leaves your computer vulnerable to potentially
unwanted programs.
Start e-mail protection
Turn on e-mail protection to detect worms as well as potential
threats in inbound (POP3) e-mail messages and attachments.
1 Open the E-mail & IM Configuration pane.
How?
Page 37

Chapter 9 Introduction 35
1. On the left pane, click Advanced Menu.
2. Click Configure.
3. On the Configure pane, click E-mail & IM.
2 Under E-mail protection, click On.
Note: Although you can turn off e-mail protection at any time,
doing so leaves your computer vulnerable to e-mail threats.
Start instant messaging protection
Turn on instant messaging protection to detect security threats
that can be included in inbound instant message attachments.
1 Open the E-mail & IM Configuration pane.
How?
1. On the left pane, click Advanced Menu.
2. Click Configure.
3. On the Configure pane, click E-mail & IM.
2 Under Instant Messaging protection, click On.
Note: Although you can turn off instant messaging protection at
any time, doing so leaves your computer vulnerable to harmful
instant message attachments.
Page 38

Page 39

C HAPTER 10
Setting up virus protection
VirusScan provides two types of virus protection: real-time and
manual. Real-time virus protection scans files each time you or
your computer access them. Manual virus protection lets you
scan files on demand. You can set different options for each type
of protection. For example, because real-time protection
continuously monitors your computer, you might select a certain
set of basic scanning options, reserving a more comprehensive
set of scanning options for manual, on-demand protection.
In this chapter
Setting real-time scan options ...................................38
Setting manual scan options ......................................40
Using SystemGuards options .....................................44
Using trusted lists........................................................ 50
37
Page 40

38 McAfee VirusScan Plus
Setting real-time scan options
When you start real-time virus protection, VirusScan uses a
default set of options to scan files; however, you can change the
default options to suit your needs.
To change real-time scanning options, you must make decisions
about what VirusScan checks for during a scan, as well as the
locations and file types it scans. For example, you can determine
whether VirusScan checks for unknown viruses or cookies that
Web sites can use to track your behavior, and whether it scans
network drives that are mapped to your computer or just local
drives. You can also determine what types of files are scanned (all
files, or just program files and documents, since that is where
most viruses are detected).
When changing real-time scanning options, you must also
determine whether it's important for your computer to have
buffer overflow protection. A buffer is a portion of memory used
to temporarily hold computer information. Buffer overflows can
occur when the amount of information suspect programs or
processes store in a buffer exceeds the buffer's capacity. When
this occurs, your computer becomes more vulnerable to security
attacks.
Set real-time scan options
You set real-time scan options to customize what VirusScan looks
for during a real-time scan, as well as the locations and file types
it scans. Options include scanning for unknown viruses and
tracking cookies as well as providing buffer overflow protection.
You can also configure real-time scanning to check network
drives that are mapped to your computer.
1 Open the Real-Time Scanning pane.
How?
1. Under Common Tasks, click Home.
2. On the SecurityCenter Home pane, click Computer &
Files.
3. In the Computer & Files information area, click
Configure.
4. On the Computer & Files Configuration pane, ensure
that virus protection is enabled, and then click
Advanced.
2 Specify your real-time scanning options, and then click OK.
To... Do this...
Detect unknown viruses and
new variants of known
viruses
Select the
viruses using heuristics
box.
Scan for unknown
check
Page 41

Chapter 10 Introduction 39
To... Do this...
Detect cookies
Select the
tracking cookies
Scan and remove
check box.
Detect viruses and other
potential threats on drives
that are connected to your
network
Protect your computer from
buffer overflows
Specify which types of files
to scan
Select the
check box.
Select the
overflow protection
Click either
(recommended)
Scan network drives
Enable buffer
check box.
All files
or Program
files and documents only
.
Page 42

40 McAfee VirusScan Plus
Setting manual scan options
Manual virus protection lets you scan files on demand. When you
start a manual scan, VirusScan checks your computer for viruses
and other potentially harmful items using a more comprehensive
set of scanning options. To change manual scanning options, you
must make decisions about what VirusScan checks for during a
scan. For example, you can determine whether VirusScan looks
for unknown viruses, potentially unwanted programs, such as
spyware or adware, stealth programs, such as rootkits which can
grant unauthorized access to your computer, and cookies that
Web sites can use to track your behavior. You must also make
decisions about the types of files that are checked. For example,
you can determine whether VirusScan checks all files or just
program files and documents (since that is where most viruses
are detected). You can also determine whether archive files (for
example, .zip files) are included in the scan.
By default, VirusScan checks all the drives and folders on your
computer each time it runs a manual scan; however, you can
change the default locations to suit your needs. For example, you
can scan only critical system files, items on your desktop, or
items in your Program Files folder. Unless you want to be
responsible for initiating each manual scan yourself, you can set
up a regular schedule for scans. Scheduled scans always check
your entire computer using the default scan options. By default,
VirusScan performs a scheduled scan once a week.
If you find that you are experiencing slow scan speeds, consider
disabling the option to use minimal computer resources, but
keep in mind that higher priority will be given to virus protection
than to other tasks.
Note: When enjoying things like watching movies, playing games
on your computer, or any activity that occupies your entire
computer screen, VirusScan pauses a number of tasks, including
automatic updates and manual scans.
Set manual scan options
You set manual scan options to customize what VirusScan looks
for during a manual scan as well as the locations and file types it
scans. Options include scanning for unknown viruses, file
archives, spyware and potentially unwanted programs, tracking
cookies, rootkits, and stealth programs.
1 Open the Manual Scan pane.
How?
Page 43

Chapter 10 Introduction 41
1. Under Common Tasks, click Home.
2. On the SecurityCenter Home pane, click Computer &
Files.
3. In the Computer & Files information area, click
Configure.
4. On the Computer & Files Configuration pane, ensure
that virus protection is enabled, and click Advanced.
5. Click Manual Scan in the Virus Protection pane.
2 Specify your manual scanning options, and then click OK.
To... Do this...
Detect unknown viruses and
new variants of known
viruses
Select the
viruses using heuristics
box.
Scan for unknown
check
Detect and remove viruses in
.zip and other archive files
Detect spyware, adware, and
other potentially unwanted
programs
Detect cookies
Detect rootkits and stealth
programs that can alter and
exploit existing Windows
system files
Use less processor power for
scans while giving higher
priority to other tasks (such
as Web browsing or opening
documents)
Specify which types of files
to scan
Set manual scan location
Select the
archive files
Select the
Scan .zip and other
check box.
Scan for spyware and
potentially unwanted
programs
Select the
tracking cookies
Select the
other stealth programs
box.
Select the
computer resources
Click either
(recommended)
check box.
Scan and remove
check box.
Scan for rootkits and
check
Scan using minimal
check box.
All files
or Program
files and documents only
.
You set the manual scan location to determine where VirusScan
looks for viruses and other harmful items during a manual scan.
You can scan all files, folders, and drives on your computer or you
can restrict scanning to specific folders and drives.
1 Open the Manual Scan pane.
How?
Page 44

42 McAfee VirusScan Plus
1. Under Common Tasks, click Home.
2. On the SecurityCenter Home pane, click Computer &
Files.
3. In the Computer & Files information area, click
Configure.
4. On the Computer & Files Configuration pane, ensure
that virus protection is enabled, and click Advanced.
5. Click Manual Scan in the Virus Protection pane.
2 Click Default Location to Scan.
3 Specify your manual scanning location, and then click OK.
To... Do this...
Scan all the files and
folders on your computer
Select the
Computer check box.
(My)
Scan specific files, folders,
and drives on your
computer
Scan critical system files
Clear the
Computer check box,
and select one or more
folders or drives.
Clear the
(My)
(My)
Computer check box,
and then select the
Critical System Files
check box.
Schedule a scan
Schedule scans to thoroughly check your computer for viruses
and other threats any day and time of the week. Scheduled scans
always check your entire computer using the default scan
options. By default, VirusScan performs a scheduled scan once a
week. If you find that you are experiencing slow scan speeds,
consider disabling the option to use minimal computer
resources, but keep in mind that higher priority will be given to
virus protection than to other tasks.
1 Open the Scheduled Scan pane.
How?
Page 45

Chapter 10 Introduction 43
1. Under Common Tasks, click Home.
2. On the SecurityCenter Home pane, click Computer &
Files.
3. In the Computer & Files information area, click
Configure.
4. On the Computer & Files Configuration pane, ensure
that virus protection is enabled, and click Advanced.
5. Click Scheduled Scan in the Virus Protection pane.
2 Select Enable scheduled scanning.
3 To reduce the amount of processor power normally used for
scanning, select Scan using minimal computer resources.
4 Select one or more days.
5 Specify a start time.
6 Click OK.
Tip: You can restore the default schedule by clicking Reset.
Page 46

44 McAfee VirusScan Plus
Using SystemGuards options
SystemGuards monitor, log, report, and manage potentially
unauthorized changes made to the Windows registry or critical
system files on your computer. Unauthorized registry and file
changes can harm your computer, compromise its security, and
damage valuable system files.
Registry and files changes are common and occur regularly on
your computer. Because many are harmless, SystemGuards'
default settings are configured to provide reliable, intelligent, and
real-world protection against unauthorized changes that pose
significant potential for harm. For example, when SystemGuards
detect changes that are uncommon and present a potentially
significant threat, the activity is immediately reported and
logged. Changes that are more common, but still pose some
potential for damage, are logged only. However, monitoring for
standard and low-risk changes is, by default, disabled.
SystemGuards technology can be configured to extend its
protection to any environment you like.
There are three types of SystemGuards: Program SystemGuards,
Windows SystemGuards, and Browser SystemGuards.
Program SystemGuards
Program SystemGuards detect potentially unauthorized changes
to your computer's registry and other critical files that are
essential to Windows. These important registry items and files
include ActiveX installations, startup items, Windows shell
execute hooks, and shell service object delay loads. By
monitoring these, Program SystemGuards technology stops
suspect ActiveX programs (downloaded from the Internet) in
addition to spyware and potentially unwanted programs that can
automatically launch when Windows starts.
Windows SystemGuards
Windows SystemGuards also detect potentially unauthorized
changes to your computer's registry and other critical files that
are essential to Windows. These important registry items and files
include context menu handlers, appInit DLLs, and the Windows
hosts file. By monitoring these, Windows SystemGuards
technology helps prevent your computer from sending and
receiving unauthorized or personal information over the
Internet. It also helps stop suspect programs that can bring
unwanted changes to the appearance and behavior of the
programs that are important to you and your family.
Browser SystemGuards
Page 47

Chapter 10 Introduction 45
Like Program and Windows SystemGuards, Browser
SystemGuards detect potentially unauthorized changes to your
computer's registry and other critical files that are essential to
Windows. Browser SystemGuards, however, monitor changes to
important registry items and files like Internet Explorer add-ons,
Internet Explorer URLs, and Internet Explorer security zones. By
monitoring these, Browser SystemGuards technology helps
prevent unauthorized browser activity such as redirection to
suspect Web sites, changes to browser settings and options
without your knowledge, and unwanted trusting of suspect Web
sites.
Enable SystemGuards protection
Enable SystemGuards protection to detect and alert you to
potentially unauthorized Windows registry and file changes on
your computer. Unauthorized registry and file changes can harm
your computer, compromise its security, and damage valuable
system files.
1 Open the Computer & Files Configuration pane.
How?
1. On the left pane, click Advanced Menu.
2. Click Configure.
3. On the Configure pane, click Computer & Files.
2 Under SystemGuard protection, click On.
Note: You can disable SystemGuard protection, by clicking Off.
Configure SystemGuards options
Use the SystemGuards pane to configure protection, logging, and
alerting options against unauthorized registry and file changes
associated with Windows files, programs, and Internet Explorer.
Unauthorized registry and file changes can harm your computer,
compromise its security, and damage valuable system files.
1 Open the SystemGuards pane.
1. Under Common Tasks, click Home.
2. On the SecurityCenter Home pane, click Computer &
Files.
3. In the Computer & Files information area, click
Configure.
4. On the Computer & Files Configuration pane, ensure
that SystemGuard protection is enabled, and click
Advanced.
2 Select a SystemGuard type from the list.
Program SystemGuards
Windows SystemGuards
Page 48

46 McAfee VirusScan Plus
Browser SystemGuards
3 Under I want to, do one of the following:
To detect, log, and report unauthorized registry and file
changes associated with Program, Windows, and Browsers
SystemGuards, click Show alerts.
To detect and log unauthorized registry and file changes
associated with Program, Windows, and Browsers
Systemguards, click Only log changes.
To disable detection of unauthorized registry and file
changes associated with Program, Windows, and Browser
Systemguards, click Disable the SystemGuard.
Note: For more information about SystemGuards types, see
About SystemGuards types (page 46).
About SystemGuards types
SystemGuards detect potentially unauthorized changes to your
computer's registry and other critical files that are essential to
Windows. There are three types of SystemGuards: Program
SystemGuards, Windows SystemGuards, and Browser
SystemGuards
Program SystemGuards
Program SystemGuards technology stops suspect ActiveX
programs (downloaded from the Internet) in addition to spyware
and potentially unwanted programs that can automatically
launch when Windows starts.
SystemGuard Detects...
ActiveX
Installations
Startup Items Spyware, adware, and other potentially
Windows Shell
Execute Hooks
Shell Service
Object Delay
Load
Unauthorized registry changes to ActiveX
installations that can harm your computer,
compromise its security, and damage
valuable system files.
unwanted programs that can install file
changes to startup items, allowing suspect
programs to run when you start your
computer.
Spyware, adware, and other potentially
unwanted programs that can install
Windows shell execute hooks to prevent
security programs from running properly.
Spyware, adware, and other potentially
unwanted programs that can make registry
changes to the shell service object delay load,
allowing harmful files to run when you start
your computer.
Windows SystemGuards
Page 49

Chapter 10 Introduction 47
Windows SystemGuards technology helps prevent your computer
from sending and receiving unauthorized or personal
information over the Internet. It also helps stop suspect programs
that can bring unwanted changes to the appearance and
behavior of the programs that are important to you and your
family.
SystemGuard Detects...
Context Menu
Handlers
AppInit DLLs Unauthorized registry changes to Windows
Unauthorized registry changes to Windows
context menu handlers that can affect the
appearance and behavior of Windows menus.
Context menus allow you to perform actions on
your computer, such as right-clicking files.
appInit DLLs that can allow potentially harmful
files to run when you start your computer.
Windows Hosts
File
Winlogon Shell Spyware, adware, and other potentially
Winlogon User
Init
Windows
Protocols
Winsock
Layered Service
Providers
Windows Shell
Open
Commands
Spyware, adware, and potentially unwanted
programs that can make unauthorized changes
in your Windows hosts file, allowing your
browser to be redirected to suspect Web sites
and to block software updates.
unwanted programs that can make registry
changes to the Winlogon shell, allowing other
programs to replace Windows Explorer.
Spyware, adware, and other potentially
unwanted programs that can make registry
changes to Winlogon user init, allowing suspect
programs to run when you log on to Windows.
Spyware, adware, and other potentially
unwanted programs that can make registry
changes to Windows protocols, affecting how
your computer sends and receives information
on the Internet.
Spyware, adware, and other potentially
unwanted programs that can install registry
changes to Winsock Layered Service Providers
(LSPs) to intercept and change information you
send and receive on the Internet.
Unauthorized changes to Windows shell open
commands that can allow worms and other
harmful programs to run on your computer.
Shared Task
Scheduler
Spyware, adware, and other potentially
unwanted programs that can make registry and
file changes to the shared task scheduler,
allowing potentially harmful files to run when
you start your computer.
Page 50

48 McAfee VirusScan Plus
SystemGuard Detects...
Windows
Messenger
Service
Spyware, adware, and other potentially
unwanted programs that can make registry
changes to the Windows messenger service,
allowing unsolicited ads and remotely run
programs on your computer.
Windows
Win.ini File
Browser SystemGuards
Spyware, adware, and other potentially
unwanted programs that can make changes to
the Win.ini file, allowing suspect programs to
run when you start your computer.
Browser SystemGuards technology helps prevent unauthorized
browser activity such as redirection to suspect Web sites, changes
to browser settings and options without your knowledge, and
unwanted trusting of suspect Web sites.
SystemGuard Detects...
Browser Helper
Objects
Internet Explorer
Bars
Internet Explorer
Add-ons
Spyware, adware, and other potentially
unwanted programs that can use browser
helper objects to track Web browsing and
show unsolicited ads.
Unauthorized registry changes to Internet
Explorer Bar programs, such as Search and
Favorites, that can affect the appearance and
behavior of Internet Explorer.
Spyware, adware, and other potentially
unwanted programs that can install Internet
Explorer add-ons to track Web browsing and
show unsolicited ads.
Internet Explorer
ShellBrowser
Internet Explorer
WebBrowser
Internet Explorer
URL Search Hooks
Internet Explorer
URLs
Unauthorized registry changes to the
Internet Explorer shell browser that can
affect the appearance and behavior of your
Web browser.
Unauthorized registry changes to the
Internet Explorer Web browser that can
affect the appearance and behavior of your
browser.
Spyware, adware, and other potentially
unwanted programs that can make registry
changes to Internet Explorer URL search
hooks, allowing your browser to be
redirected to suspect Web sites when
searching the Web.
Spyware, adware, and other potentially
unwanted programs that can make registry
changes to Internet Explorer URLs, affecting
browser settings.
Page 51

Chapter 10 Introduction 49
SystemGuard Detects...
Internet Explorer
Restrictions
Spyware, adware, and other potentially
unwanted programs that can make registry
changes to Internet Explorer restrictions,
affecting browser settings and options.
Internet Explorer
Security Zones
Internet Explorer
Trusted Sites
Internet Explorer
Policy
Spyware, adware, and other potentially
unwanted programs that can make registry
changes to Internet Explorer security zones,
allowing potentially harmful files to run
when you start your computer.
Spyware, adware, and other potentially
unwanted programs that can make registry
changes to Internet Explorer trusted sites,
allowing your browser to trust suspect Web
sites.
Spyware, adware, and other potentially
unwanted programs that can make registry
changes to Internet Explorer policies,
affecting the appearance and behavior of
your browser.
Page 52

50 McAfee VirusScan Plus
Using trusted lists
If VirusScan detects a file or registry change (SystemGuard),
program, or buffer overflow, it prompts you to trust or remove it.
If you trust the item and indicate that you do not want to receive
future notification about its activity, the item is added to a trusted
list and VirusScan no longer detects it or notifies you about its
activity. If an item has been added to a trusted list, but you decide
you want to block its activity, you can do so. Blocking prevents
the item from running or making any changes to your computer
without notifying you each time an attempt is made. You can also
remove an item from a trusted list. Removing allows VirusScan to
detect the item's activity again.
Manage trusted lists
Use the Trusted Lists pane to trust or block items that have been
previously detected and trusted. You can also remove an item
from a trusted list so that VirusScan detects it again.
1 Open the Trusted Lists pane.
1. Under Common Tasks, click Home.
2. On the SecurityCenter Home pane, click Computer &
Files.
3. In the Computer & Files information area, click
Configure.
4. On the Computer & Files Configuration pane, ensure
that virus protection is enabled, and click Advanced.
5. Click Trusted Lists in the Virus Protection pane.
2 Select one of the following trusted list types:
Program SystemGuards
Windows SystemGuards
Browser SystemGuards
Trusted Programs
Trusted Buffer Overflows
3 Under I want to, do one of the following:
To allow the detected item to make changes to the
Windows registry or critical system files on your computer
without notifying you, click Trust.
To block the detected item from making changes to the
Windows registry or critical system files on your computer
without notifying you, click Block.
To remove the detected item from the trusted lists, click
Remove.
Page 53

Chapter 10 Introduction 51
4 Click OK.
Note: For more information about trusted list types, see About
trusted lists types (page 51).
About trusted lists types
SystemGuards on the Trusted Lists pane represent previously
unauthorized registry and file changes that VirusScan has
detected but that you have chosen to allow from an alert of from
the Scan results pane. There are five types of trusted list types
that you can manage on the Trusted Lists pane: Program
SystemGuards, Windows SystemGuards, Browser SystemGuards,
Trusted Programs, and Trusted Buffer Overflows.
Option Description
Program
SystemGuards
Program SystemGuards on the Trusted Lists
pane represent previously unauthorized registry
and file changes that VirusScan has detected, but
that you have chosen to allow from an alert or
from the Scan Results pane.
Program SystemGuards detect unauthorized
registry and file changes associated with ActiveX
installations, startup items, Windows shell
execute hooks, and shell service object delay
load activity. These types of unauthorized
registry and file changes can harm your
computer, compromise its security, and damage
valuable system files.
Windows
SystemGuards
Windows SystemGuards on the Trusted Lists
pane represent previously unauthorized registry
and file changes that VirusScan has detected, but
that you have chosen to allow from an alert or
from the Scan Results pane.
Windows SystemGuards detect unauthorized
registry and file changes associated with context
menu handlers, appInit DLLs, the Windows
hosts file, the Winlogon shell, Winsock Layered
Service Providers (LSPs), and so on. These types
of unauthorized registry and file changes can
affect how your computer sends and receives
information over the Internet, change the
appearance and behavior of programs, and allow
suspect programs to run on your computer.
Page 54

52 McAfee VirusScan Plus
Option Description
Browser
SystemGuards
Browser SystemGuards on the Trusted Lists pane
represent previously unauthorized registry and
file changes that VirusScan has detected, but
that you have chosen to allow from an alert or
from the Scan Results pane.
Browser SystemGuards detect unauthorized
registry changes and other unwanted behavior
associated with Browser helper objects, Internet
Explorer add-ons, Internet Explorer URLs,
Internet Explorer security zones, and so on.
These types of unauthorized registry changes
can result in unwanted browser activity such as
redirection to suspect Web sites, changes to
browser settings and options, and trusting of
suspect Web sites.
Trusted
Programs
Trusted Buffer
Overflows
Trusted programs are potentially unwanted
programs that VirusScan has previously
detected, but which you have chosen to trust
from an alert or from the Scan Results pane.
Trusted buffer overflows represent previously
unwanted activity that VirusScan has detected,
but which you have chosen to to trust from an
alert or from the Scan Results pane.
Buffer overflows can harm your computer and
damage files. Buffer overflows occur when the
amount of information suspect programs or
processes store in a buffer exceeds the buffer's
capacity.
Page 55

C HAPTER 11
Scanning your computer
When you start SecurityCenter for the first time, VirusScan's
real-time virus protection starts protecting your computer from
potentially harmful viruses, Trojans, and other security threats.
Unless you disable real-time virus protection, VirusScan
constantly monitors your computer for virus activity, scanning
files each time you or your computer access them, using the
real-time scanning options that you set. To make sure that your
computer stays protected against the latest security threats, leave
real-time virus protection on and set up a schedule for regular,
more comprehensive manual scans. For more information about
setting real-time and manual scan options, see
protection
VirusScan provides a more detailed set of scanning options for
manual virus protection, allowing you to periodically run more
extensive scans. You can run manual scans from SecurityCenter,
targeting specific locations according to a set schedule. However,
you can also run manual scans directly in Windows Explorer
while you work. Scanning in SecurityCenter offers the advantage
of changing scanning options on-the-fly. However, scanning
from Windows Explorer offers a convenient approach to
computer security.
(page 37).
53
Setting up virus
Whether you run a manual scan from SecurityCenter or Windows
Explorer, you can view the scan results when it finishes. You view
the results of a scan to determine whether VirusScan has
detected, repaired, or quarantined viruses, trojans, spyware,
adware, cookies, and other potentially unwanted programs. The
results of a scan can be displayed in different ways. For example,
you can view a basic summary of scan results or detailed
information, such as the infection status and type. You can also
view general scan and detection statistics.
In this chapter
Scan your computer....................................................54
View scan results .........................................................54
Page 56

54 McAfee VirusScan Plus
Scan your computer
You can run a manual scan from either the Advanced or Basic
menu in SecurityCenter. If you run a scan from the Advanced
menu, you can confirm your manual scan options before
scanning. If you run a scan from the Basic menu, VirusScan starts
scanning immediately, using the existing scanning options. You
can also run a scan in Windows Explorer using the existing
scanning options.
Do one of the following:
Scan in SecurityCenter
To... Do this...
Scan using existing
settings
Scan on the Basic menu.
Click
Scan using changed
settings
Scan on the Advanced menu, select
Click
the locations to scan, select scan options,
and then cliick
Scan Now.
Scan in Windows Explorer
1. Open Windows Explorer.
2. Right-click a file, folder, or drive, and then click Scan.
Note: The scan results appear in the Scan completed alert.
Results include the number of items scanned, detected, repaired,
quarantined, and removed. Click View scan details to learn
more about the scan results or work with infected items.
View scan results
When a manual scan finishes, you view the results to determine
what the scan found and to analyze the current protection status
of your computer. Scan results tell you whether VirusScan
detected, repaired, or quarantined viruses, trojans, spyware,
adware, cookies, and other potentially unwanted programs.
On the Basic or Advanced menu, click Scan and then do one
of the following:
To... Do this...
View scan results in the
alert
View more information
about scan results
View a quick summary
of the scan results
View scan results in the Scan completed
alert.
Click
completed alert.
Point to the
the notification area on your taskbar.
View scan details in the Scan
Scan completed icon in
Page 57

Chapter 11 Introduction 55
To... Do this...
View scan and
detection statistics
Double-click the
in the notification area on your taskbar.
Scan completed icon
View details about
detected items,
infection status, and
type.
Double-click the
in the notification area on your taskbar,
and then click
Scan Progress: Manual Scan pane.
Scan completed icon
View Results on the
Page 58

Page 59

C HAPTER 12
Working with scan results
If VirusScan detects a security threat while running a real-time or
manual scan, it tries to handle the threat automatically according
to the threat type. For example, If VirusScan detects a virus,
Trojan, or tracking cookie on your computer, it tries to clean the
infected file. If it cannot clean the file, VirusScan quarantines it.
With some security threats, VirusScan may not be able to clean or
quarantine a file successfully. In this case, VirusScan prompts you
to handle the threat. You can take different actions depending on
the threat type. For example, if a virus is detected in a file, but
VirusScan cannot successfully clean or quarantine the file, it
denies further access to it. If tracking cookies are detected, but
VirusScan cannot successfully clean or quarantine the cookies,
you can decide whether to remove or trust the them. If
potentially unwanted programs are detected, VirusScan does not
take any automatic action; instead, it lets you decide whether to
quarantine or trust the program.
57
When VirusScan quarantines items, it encrypts and then isolates
them in a folder to prevent the files, programs, or cookies from
harming your computer. You can restore or remove the
quarantined items. In most cases, you can delete a quarantined
cookie without impacting your system; however, if VirusScan has
quarantined a program that you recognize and use, consider
restoring it.
In this chapter
Work with viruses and Trojans...................................57
Work with potentially unwanted programs ..............58
Work with quarantined files....................................... 58
Work with quarantined programs and cookies.........59
Work with viruses and Trojans
If VirusScan detects a virus or Trojan in a file on your computer
during a real-time scan or manual scan, it tries to clean the file. If
it cannot clean the file, VirusScan tries to quarantine it. If this too
fails, access to the file is denied (in real-time scans only).
1 Open the Scan Results pane.
How?
Page 60

58 McAfee VirusScan Plus
1. Double-click the Scan completed icon in the
notification area at the far right of your taskbar.
2. On the Scan Progress: Manual Scan pane, click View
Results.
2 In the scan results list, click Viruses and Trojans.
Note: To work with the files that VirusScan has quarantined, see
Work with quarantined files (page 58).
Work with potentially unwanted programs
If VirusScan detects a potentially unwanted program on your
computer during a real-time or manual scan, you can either
remove or trust the program. Removing the potentially unwanted
program does not actually delete it from your system. Instead,
removing quarantines the program to prevent it from causing
damage to your computer or files.
1 Open the Scan Results pane.
How?
1. Double-click the Scan completed icon in the
notification area at the far right of your taskbar.
2. On the Scan Progress: Manual Scan pane, click View
Results.
2 In the scan results list, click Potentially Unwanted
Programs.
3 Select a potentially unwanted program.
4 Under I want to, click either Remove or Trust.
5 Confirm your selected option.
Work with quarantined files
When VirusScan quarantines infected files, it encrypts and then
moves them to a folder to prevent the files from harming your
computer. You can then restore or remove the quarantined files.
1 Open the Quarantined Files pane.
How?
1. On the left pane, click Advanced Menu.
2. Click Restore.
3. Click Files.
2 Select a quarantined file.
3 Do one of the following:
To repair the infected file and return it to its original
location on your computer, click Restore.
Page 61

Chapter 12 Introduction 59
To remove the infected file from your computer, click
Remove.
4 Click Yes to confirm your selected option.
Tip: You can restore or remove multiple files at the same time.
Work with quarantined programs and cookies
When VirusScan quarantines potentially unwanted programs or
tracking cookies, it encrypts and then moves them to a protected
folder to prevent the programs or cookies from harming your
computer. You can then restore or remove the quarantined
items. In most cases, you can delete a quarantined without
impacting your system.
1 Open the Quarantined Programs and Tracking Cookies pane.
How?
1. On the left pane, click Advanced Menu.
2. Click Restore.
3. Click Programs and Cookies.
2 Select a quarantined program or cookie.
3 Do one of the following:
To repair the infected file and return it to its original
location on your computer, click Restore.
To remove the infected file from your computer, click
Remove.
4 Click Yes to confirm the operation.
Tip: You can restore or remove multiple programs and cookies at
the same time.
Page 62

Page 63

C HAPTER 13
McAfee Personal Firewall
Personal Firewall offers advanced protection for your computer
and your personal data. Personal Firewall establishes a barrier
between your computer and the Internet, silently monitoring
Internet traffic for suspicious activities.
Note: SecurityCenter reports critical and non-critical protection
problems as soon as it detects them. If you need help diagnosing
your protection problems, you can run McAfee Virtual
Technician.
In this chapter
Personal Firewall features ..........................................62
Starting Firewall ..........................................................65
Working with alerts .....................................................67
Managing informational alerts...................................69
Configuring Firewall protection.................................71
Managing programs and permissions....................... 83
Managing system services.......................................... 91
Managing computer connections..............................97
Logging, monitoring, and analysis.............................105
Learning about Internet security ...............................115
61
Page 64

62 McAfee VirusScan Plus
Personal Firewall features
Personal Firewall provides the following features.
Standard and custom protection levels
Guard against intrusion and suspicious activity using Firewall's
default or customizable protection settings.
Real-time recommendations
Receive recommendations, dynamically, to help you determine
whether programs should be granted Internet access or network
traffic should be trusted.
Intelligent access management for programs
Manage Internet access for programs, through alerts and Event
Logs, and configure access permissions for specific programs.
Gaming protection
Prevent alerts regarding intrusion attempts and suspicious
activities from distracting you during full-screen gameplay.
Computer startup protection
As soon as Windows® starts, Firewall protects your computer
from intrusion attempts, unwanted programs and network traffic.
System service port control
Manage open and closed system service ports required by some
programs.
Manage computer connections
Allow and block remote connections between other computers
and your computer.
HackerWatch information integration
Track global hacking and intrusion patterns through
HackerWatch's Web site, which also provides current security
information about programs on your computer, as well as global
security events and Internet port statistics.
Lockdown Firewall
Instantly block all inbound and outbound traffic between your
computer and the Internet.
Restore Firewall
Instantly restore Firewall's original protection settings.
Advanced Trojan detection
Detect and block potentially malicious applications, such as
Trojans, from relaying your personal data to the Internet.
Page 65

Chapter 13 Introduction 63
Event logging
Track recent inbound, outbound, and intrusion events.
Monitor Internet traffic
Review worldwide maps showing the source of hostile attacks
and traffic. In addition, locate detailed owner information and
geographical data for originating IP addresses. Also, analyze
inbound and outbound traffic, monitor program bandwidth and
program activity.
Intrusion prevention
Protect your privacy from possible Internet threats. Using
heuristic-like functionality, McAfee provides a tertiary layer of
protection by blocking items that display symptoms of attacks or
characteristics of hacking attempts.
Sophisticated traffic analysis
Review both inbound and outbound Internet traffic and program
connections, including those that are actively listening for open
connections. This allows you to see and act upon programs that can be
vulnerable to intrusion.
Page 66

Page 67

C HAPTER 14
Starting Firewall
65
As soon as you install Firewall, your computer is protected from
intrusion and unwanted network traffic. In addition, you are
ready to handle alerts and manage inbound and outbound
Internet access for known and unknown programs. Smart
Recommendations and Trusting security level (with the option
selected to allow programs outbound-only Internet access) are
automatically enabled.
Although you can disable Firewall from the Internet & Network
Configuration pane, your computer will no longer be protected
from intrusion and unwanted network traffic, and you will be
unable to effectively manage inbound and outbound Internet
connections. If you must disable firewall protection, do so
temporarily and only when necessary. You can also enable
Firewall from the Internet & Network Configuration panel.
Firewall automatically disables Windows® Firewall and sets itself
as your default firewall.
Note: To configure Firewall, open the Internet & Network
Configuration pane.
In this chapter
Start firewall protection..............................................65
Stop firewall protection ..............................................66
Start firewall protection
You can enable Firewall to protect your computer from intrusion
and unwanted network traffic, as well as manage inbound and
outbound Internet connections.
1 On the McAfee SecurityCenter pane, click Internet &
Network, and then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is disabled, click On.
Page 68

66 McAfee VirusScan Plus
Stop firewall protection
You can disable Firewall if you do not want to protect your
computer from intrusion and unwanted network traffic. When
Firewall is disabled, you cannot manage inbound or outbound
Internet connections.
1 On the McAfee SecurityCenter pane, click Internet &
Network, and then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Off.
Page 69

C HAPTER 15
Working with alerts
Firewall employs an array of alerts to help you manage your
security. These alerts can be grouped into three basic types:
Red alert
Yellow alert
Green alert
Alerts can also contain information to help you decide how to
handle alerts or get information about programs running on your
computer.
In this chapter
About alerts.................................................................. 68
67
Page 70

68 McAfee VirusScan Plus
About alerts
Firewall has three basic alert types. As well, some alerts include
information to help you learn or get information about programs
running on your computer.
Red alert
A red alert appears when Firewall detects, then blocks, a Trojan
on your computer, and recommends that you scan for additional
threats. A Trojan appears to be a legitimate program, but can
disrupt, damage, and provide unauthorized access to your
computer. This alert occurs in every security level, except Open.
Yellow alert
The most common type of alert is a yellow alert, which informs
you about a program activity or network event detected by
Firewall. When this occurs, the alert describes the program
activity or network event, and then provides you with one or
more options that require your response. For example, the New
Network Detected alert appears when a computer with Firewall
installed is connected to a new network. You can choose to trust
or not trust the network. If the network is trusted, Firewall allows
traffic from any other computer on the network and is added to
Trusted IP Addresses. If Smart Recommendations is enabled,
programs are added to the Program Permissions pane.
Green alert
In most cases, a green alert provides basic information about an
event and does not require a response. Green alerts are disabled
by default, and usually occur when Standard, Trusting, Tight, and
Stealth security levels are set.
User Assistance
Many Firewall alerts contain additional information to help you
manage your computer's security, which includes the following:
Learn more about this program: Launch McAfee's
global security Web site to get information about a
program that Firewall has detected on your computer.
Tell McAfee about this program: Send information to
McAfee about an unknown file that Firewall has detected
on your computer.
McAfee recommends: Advice about handling alerts. For
example, an alert can recommend that you allow access
for a program.
Page 71

C HAPTER 16
Managing informational alerts
Firewall allows you to display or hide informational alerts when it
detects intrusion attempts or suspicious activity during certain
events, for example, during full-screen gameplay.
In this chapter
Display alerts while gaming........................................69
Hide informational alerts ...........................................69
Display alerts while gaming
You can allow Firewall informational alerts to be displayed when
it detects intrusion attempts or suspicious activity during
full-screen gameplay.
69
1 On the McAfee SecurityCenter pane, click Advanced Menu.
2 Click Configure.
3 On the SecurityCenter Configuration pane, under Alerts,
click Advanced.
4 On the Alert Options pane, select Show informational alerts
when gaming mode is detected.
5 Click OK.
Hide informational alerts
You can prevent Firewall informational alerts from being
displayed when it detects intrusion attempts or suspicious
activity.
1 On the McAfee SecurityCenter pane, click Advanced Menu.
2 Click Configure.
3 On the SecurityCenter Configuration pane, under Alerts,
click Advanced.
4 On the SecurityCenter Configuration pane, click
Informational Alerts.
5 On the Informational Alerts pane, do one of the following:
Select Do not show informational alerts to hide all
informational alerts.
Clear an alert to hide.
6 Click OK.
Page 72

Page 73

C HAPTER 17
Configuring Firewall protection
Firewall offers a number of methods to manage your security and
to tailor the way you want to respond to security events and
alerts.
After you install Firewall for the first time, your computer's
protection security level is set to Trusting and your programs are
allowed outbound-only Internet access. However, Firewall
provides other levels, ranging from highly restrictive to highly
permissive.
Firewall also offers you the opportunity to receive
recommendations on alerts and Internet access for programs.
In this chapter
Managing Firewall security levels ..............................72
Configuring Smart Recommendations for alerts......76
Optimizing Firewall security ......................................78
Locking and restoring Firewall...................................81
71
Page 74

72 McAfee VirusScan Plus
Managing Firewall security levels
Firewall's security levels control the degree to which you want to
manage and respond to alerts. These alerts appear when it
detects unwanted network traffic and inbound and outbound
Internet connections. By default, Firewall's security level is set to
Trusting, with outbound-only access.
When Trusting security level is set and Smart Recommendations
is enabled, yellow alerts provide the option to either allow or
block access for unknown programs that require inbound access.
When known programs are detected, green informational alerts
appear, and access is automatically allowed. Allowing access lets
a program create outbound connections and listen for
unsolicited incoming connections.
Generally, the more restrictive a security level (Stealth and Tight),
the greater the number of options and alerts that are displayed
and which, in turn, must be handled by you.
The following table describes Firewall's six security levels,
starting from the most restrictive to the least:
Level Description
Lockdown Blocks all inbound and outbound network connections,
including access to Web sites, e-mail, and security updates.
This security level has the same result as removing your
connection to the Internet. You can use this setting to
block ports you set to open on the System Services pane.
Stealth Blocks all inbound Internet connections, except open
ports, hiding your computer's presence on the Internet.
The firewall alerts you when new programs attempt
outbound Internet connections or receive inbound
connection requests. Blocked and added programs appear
on the Program Permissions pane.
Tight Alerts you when new programs attempt outbound Internet
connections or receive inbound connection requests.
Blocked and added programs appear on the Program
Permissions pane. When the security level is set to Tight, a
program only requests the type of access it requires at that
time, for example outbound-only access, which you can
either allow or block. Later, if the program requires both an
inbound and an outbound connection, you can allow full
access for the program from the Program Permissions
pane.
Standard Monitors inbound and outbound connections and alerts
you when new programs attempt Internet access. Blocked
and added programs appear on the Program Permissions
pane.
Page 75

Chapter 17 Introduction 73
Level Description
Trusting Allows programs to have either inbound and outbound
(full) or outbound-only Internet access. The default
security level is Trusting with the option selected to allow
programs outbound-only access.
If a program is allowed full access, then Firewall
automatically trusts it and adds it to the list of allowed
programs on the Program Permissions pane.
If a program is allowed outbound-only access, then
Firewall automatically trusts it when making an outbound
Internet connection only. An inbound connection is not
automatically trusted.
Open Allows all inbound and outbound Internet connections.
Firewall also allows you to immediately reset your security level
to Trusting (and allow outbound-only access) from the Restore
Firewall Protection Defaults pane.
Set security level to Lockdown
You can set Firewall's security level to Lockdown to block all
inbound and outbound network connections.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Security Level pane, move the slider so that
Lockdown displays as the current level.
4 Click OK.
Set security level to Stealth
You can set the Firewall security level to Stealth to block all
inbound network connections, except open ports, to hide your
computer's presence on the Internet.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Security Level pane, move the slider so that Stealth
displays as the current level.
4 Click OK.
Note: In Stealth mode, Firewall alerts you when new programs
request outbound Internet connection or receive inbound
connection requests.
Page 76

74 McAfee VirusScan Plus
Set security level to Tight
You can set the Firewall security level to Tight to receive alerts
when new programs attempt outbound Internet connections or
receive inbound connection requests.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Security Level pane, move the slider so that Tight
displays as the current level.
4 Click OK.
Note: In Tight mode, a program only requests the type of access it
requires at that time, for example, outbound-only access, which
you can allow or block. If the program later requires both an
inbound and an outbound connection, you can allow full access
for the program from the Program Permissions pane.
Set security level to Standard
You can set the security level to Standard to monitor inbound
and outbound connections and alert you when new programs
attempt Internet access.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Security Level pane, move the slider so that Standard
displays as the current level.
4 Click OK.
Set security level to Trusting
You can set Firewall's security level to Trusting to allow either full
access or outbound-only network access.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Security Level pane, move the slider so that Trusting
displays as the current level.
4 Do one of the following:
To allow full inbound and outbound network access,
select Allow Full Access.
To allow outbound-only network access, select Allow
Outbound-Only Access.
Page 77

Chapter 17 Introduction 75
5 Click OK.
Note: The Allow Outbound-Only Access is the default option.
Set security level to Open
You can set Firewall's security level to Open to allow all inbound
and outbound network connections.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Security Level pane, move the slider so that Open
displays as the current level.
4 Click OK.
Page 78

76 McAfee VirusScan Plus
Configuring Smart Recommendations for alerts
You can configure Firewall to include, exclude, or display
recommendations in alerts when any programs attempt Internet
access. Enabling Smart Recommendations helps you decide how
to handle alerts.
When Smart Recommendations is enabled (and the security level
is set to Trusting with outbound-only access enabled), Firewall
automatically allows or blocks known programs, and displays in
the alert a recommendation when it detects potentially
dangerous programs.
When Smart Recommendations is disabled, Firewall neither
allows or blocks Internet access, nor recommends an action plan
in the alert.
When Smart Recommendations is set to Display Only, an alert
prompts you to allow or block access, but recommends an action
plan in the alert.
Enable Smart Recommendations
You can enable Smart Recommendations for Firewall to
automatically allow or block programs, and alert you about
unrecognized and potentially dangerous programs.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Security Level pane, under Smart
Recommendations, select Enable Smart
Recommendations.
4 Click OK.
Page 79

Chapter 17 Introduction 77
Disable Smart Recommendations
You can disable Smart Recommendations for Firewall to allow or
block programs, and alert you about unrecognized and
potentially dangerous programs. However, the alerts exclude any
recommendations about handling access for programs. If
Firewall detects a new program that is suspicious or is known to
be a possible threat, it automatically blocks the program from
accessing the Internet.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Security Level pane, under Smart
Recommendations, select Disable Smart
Recommendations.
4 Click OK.
Display Smart Recommendations only
You can display Smart Recommendations for the alerts to provide
action plan recommendations only so that you decide whether to
allow or block unrecognized and potentially dangerous
programs.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Security Level pane, under Smart
Recommendations, select Display Only.
4 Click OK.
Page 80

78 McAfee VirusScan Plus
Optimizing Firewall security
There are many ways the security of your computer can be
compromised. For example, some programs can attempt to
connect to the Internet before Windows® starts. In addition,
sophisticated computer users can trace (or ping) your computer
to determine whether it is connected to a network. Firewall
allows you to defend against both types of intrusion by allowing
you to enable startup protection and to block ping requests. The
first setting blocks programs from accessing the Internet as
Windows starts up and the second blocks ping requests that help
other users detect your computer on a network.
Standard installation settings include automatic detection for the
most common intrusion attempts, such as Denial of Service
attacks or exploits. Using the standard installation settings
ensures that you are protected against these attacks and scans;
however, you can disable automatic detection for one or more
attacks or scans on the Intrusion Detection pane.
Protect your computer during startup
You can protect your computer as Windows starts up to block
new programs that did not have, and now need, Internet access
during startup. Firewall displays relevant alerts for programs that
had requested Internet access, which you can allow or block. To
use this option, your security level must not be set to Open or
Lockdown.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Security Level pane, under Security Settings, select
Enable startup protection.
4 Click OK.
Note: Blocked connections and intrusions are not logged while
startup protection is enabled.
Page 81

Chapter 17 Introduction 79
Configure ping request settings
You can allow or prevent detection of your computer on the
network by other computer users.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Security Level pane, under Security Settings, do one
of the following:
Select Allow ICMP ping requests to allow detection of
your computer on the network using ping requests.
Clear Allow ICMP ping requests to prevent detection of
your computer on the network using ping requests.
4 Click OK.
Configure intrusion detection
You can detect intrusion attempts to protect your computer from
attacks and unauthorized scans. The standard Firewall setting
includes automatic detection for the most common intrusion
attempts, such as Denial of Service attacks or exploits; however,
you can disable automatic detection for one or more attacks or
scans.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Firewall pane, click Intrusion Detection.
4 Under Detect Intrusion Attempts, do one of the following:
Select a name to automatically detect the attack or scan.
Clear a name to disable automatic detection of the attack
or scan.
5 Click OK.
Configure Firewall Protection Status settings
You can configure Firewall to ignore that specific problems on
your computer are not reported to the SecurityCenter.
1 On the McAfee SecurityCenter pane, under SecurityCenter
Information, click Configure.
2 On the SecurityCenter Configuration pane, under Protection
Status, click Advanced.
3 On the Ignored Problems pane, select one or more of the
following options:
Firewall protection is disabled.
Page 82

80 McAfee VirusScan Plus
Firewall is set to Open security level.
Firewall service is not running.
Firewall Protection is not installed on your computer.
Your Windows Firewall is disabled.
Outbound firewall is not installed on your computer.
4 Click OK.
Page 83

Chapter 17 Introduction 81
Locking and restoring Firewall
Lockdown instantly blocks all inbound and outbound network
traffic to help you isolate and troubleshoot a problem on your
computer.
Lock Firewall instantly
You can lock Firewall to instantly block all network traffic
between your computer and the Internet.
1 On the McAfee SecurityCenter pane, under Common Tasks,
click Lockdown Firewall.
2 On the Lockdown Firewall pane, click Lockdown.
3 Click Yes to confirm.
Tip: You can also lock Firewall by right-clicking the
SecurityCenter icon in the notification area at the far right of
your taskbar, then click Quick Links, and then click Lockdown
Firewall.
Unlock Firewall instantly
You can unlock Firewall to instantly allow all network traffic
between your computer and the Internet.
1 On the McAfee SecurityCenter pane, under Common Tasks,
click Lockdown Firewall.
2 On the Lockdown Enabled pane, click Unlock.
3 Click Yes to confirm.
Page 84

82 McAfee VirusScan Plus
Restore Firewall settings
You can quickly restore Firewall to its original protection settings.
This restore resets your security level to Trusting and allows
outbound-only network access, enables Smart
Recommendations, restores the list of default programs and their
permissions in the Program Permissions pane, removes trusted
and banned IP addresses, and restores system services, event log
settings, and intrusion detection.
1 On the McAfee SecurityCenter pane, click Restore Firewall
Defaults.
2 On the Restore Firewall Protection Defaults pane, click
Restore Defaults.
3 Click Yes to confirm.
Tip: You can also restore Firewall's default settings by
right-clicking the SecurityCenter icon in the notification area
at the far right of your taskbar, then click Quick Links, and then
click Restore Firewall Defaults.
Page 85

C HAPTER 18
Managing programs and permissions
Firewall allows you to manage and create access permissions for
existing and new programs that require inbound and outbound
Internet access. Firewall lets you control full or outbound-only
access for programs. You can also block access for programs.
In this chapter
Allowing Internet access for programs...................... 84
Allowing outbound-only access for programs.......... 86
Blocking Internet access for programs ......................87
Removing access permissions for programs.............89
Learning about programs...........................................90
83
Page 86

84 McAfee VirusScan Plus
Allowing Internet access for programs
Some programs, like Internet browsers, need to access the
Internet to function properly.
Firewall allows you use the Program Permissions page to:
Allow access for programs
Allow outbound-only access for programs
Block access for programs
You can also allow a program to have full and outbound-only
Internet access from the Outbound Events and Recent Events log.
Allow full access for a program
You can allow an existing blocked program on your computer to
have full inbound and outbound Internet access.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Firewall pane, click Program Permissions.
4 Under Program Permissions, select a program with
Blocked or Outbound-Only Access.
5 Under Action, click Allow Access.
6 Click OK.
Allow full access for a new program
You can allow a new program on your computer to have full
inbound and outbound Internet access.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Firewall pane, click Program Permissions.
4 Under Program Permissions, click Add Allowed Program.
5 In the Add Program dialog box, browse for and select the
program that you want to add, then click Open.
Note: You can change the permissions of a newly added program
as you would an existing program by selecting the program, and
then clicking Allow Outbound-Only Access or Block Access
under Action.
Page 87

Chapter 18 Introduction 85
Allow full access from the Recent Events log
You can allow an existing blocked program that appears in the
Recent Events log to have full inbound and outbound Internet
access.
1 On the McAfee SecurityCenter pane, click Advanced Menu.
2 Click Reports & Logs.
3 Under Recent Events, select the event description, and then
click Allow Access.
4 In the Program Permissions dialog, click Yes to confirm.
Related topics
View outbound events (page 107)
Allow full access from the Outbound Events log
You can allow an existing blocked program that appears in the
Outbound Events log to have full inbound and outbound Internet
access.
1 On the McAfee SecurityCenter pane, click Advanced Menu.
2 Click Reports & Logs.
3 Under Recent Events, click View Log.
4 Click Internet & Network, and then click Outbound Events.
5 Select a program, and under I want to, click Allow Access.
6 In the Program Permissions dialog, click Yes to confirm.
Page 88

86 McAfee VirusScan Plus
Allowing outbound-only access for programs
Some programs on your computer require outbound Internet
access. Firewall lets you configure program permissions to allow
outbound-only Internet access.
Allow outbound-only access for a program
You can allow a program to have outbound-only Internet access.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Firewall pane, click Program Permissions.
4 Under Program Permissions, select a program with
Blocked or Full Access.
5 Under Action, click Allow Outbound-Only Access.
6 Click OK.
Allow outbound-only access from the Recent Events log
You can allow an existing blocked program that appears in the
Recent Events log to have outbound-only Internet access.
1 On the McAfee SecurityCenter pane, click Advanced Menu.
2 Click Reports & Logs.
3 Under Recent Events, select the event description, and then
click Allow Outbound-Only Access.
4 In the Program Permissions dialog, click Yes to confirm.
Allow outbound-only access from the Outbound Events log
You can allow an existing blocked program that appears in the
Outbound Events log to have outbound-only Internet access.
1 On the McAfee SecurityCenter pane, click Advanced Menu.
2 Click Reports & Logs.
3 Under Recent Events, click View Log.
4 Click Internet & Network, and then click Outbound Events.
5 Select a program, and under I want to, click Allow
Outbound-Only Access.
6 In the Program Permissions dialog, click Yes to confirm.
Page 89

Chapter 18 Introduction 87
Blocking Internet access for programs
Firewall allows you to block programs from accessing the
Internet. Ensure that blocking a program will not interrupt with
your network connection or another program that requires
access to the Internet to function properly.
Block access for a program
You can block a program from having inbound and outbound
Internet access.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Firewall pane, click Program Permissions.
4 Under Program Permissions, select a program with Full
Access or Outbound-Only Access.
5 Under Action, click Block Access.
6 Click OK.
Block access for a new program
You can block a new program from having inbound and
outbound Internet access.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Firewall pane, click Program Permissions.
4 Under Program Permissions, click Add Blocked Program.
5 On the Add Program dialog, browse for an select the program
that you want to add, and then click Open.
Note: You can change the permissions of a newly added program
by selecting the program and then clicking Allow
Outbound-Only Access or Allow Access under Action.
Page 90

88 McAfee VirusScan Plus
Block access from the Recent Events log
You can block a program that appears in the Recent Events log
from having inbound and outbound Internet access.
1 On the McAfee SecurityCenter pane, click Advanced Menu.
2 Click Reports & Logs.
3 Under Recent Events, select the event description, and then
click Block Access.
4 In the Program Permissions dialog, click Yes to confirm.
Page 91

Chapter 18 Introduction 89
Removing access permissions for programs
Before removing a program permission, ensure that its absence
does not affect your computer's functionality or your network
connection.
Remove a program permission
You can remove a program from having any inbound or
outbound Internet access.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Firewall pane, click Program Permissions.
4 Under Program Permissions, select a program.
5 Under Action, click Remove Program Permission.
6 Click OK.
Note: Firewall prevents you from modifying some programs by
dimming and disabling certain actions.
Page 92

90 McAfee VirusScan Plus
Learning about programs
If you are unsure which program permission to apply, you can get
information about the program on McAfee's HackerWatch Web
site.
Get program information
You can get program information from McAfee's HackerWatch
Web site to decide whether to allow or block inbound and
outbound Internet access.
Note: Ensure that you are connected to the Internet so that your
browser launches McAfee's HackerWatch Web site, which
provides up-to-date information about programs, Internet access
requirements, and security threats.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Firewall pane, click Program Permissions.
4 Under Program Permissions, select a program.
5 Under Action, click Learn More.
Get program information from the Outbound Events log
From the Outbound Events log, you can get program information
from McAfee's HackerWatch Web site to decide which programs
to allow or block inbound and outbound Internet access.
Note: Ensure that you are connected to the Internet so that your
browser launches McAfee's HackerWatch Web site, which
provides up-to-date information about programs, Internet access
requirements, and security threats.
1 On the McAfee SecurityCenter pane, click Advanced Menu.
2 Click Reports & Logs.
3 Under Recent Events, select an event, and then click View
Log.
4 Click Internet & Network, and then click Outbound Events.
5 Select an IP address, and then click Learn more.
Page 93

C HAPTER 19
Managing system services
To work properly, certain programs (including Web servers and
file-sharing server programs) must accept unsolicited
connections from other computers through designated system
service ports. Typically, Firewall closes these system service ports
because they represent the most likely source of insecurities in
your system. To accept connections from remote computers,
however, the system service ports must be open.
In this chapter
Configuring system service ports...............................92
91
Page 94

92 McAfee VirusScan Plus
Configuring system service ports
System service ports can be configured to allow or block remote
network access to a service on your computer.
The list below shows the common system services and their
associated ports:
File Transfer Protocol (FTP) Ports 20-21
Mail Server (IMAP) Port 143
Mail Server (POP3) Port 110
Mail Server (SMTP) Port 25
Microsoft Directory Server (MSFT DS) Port 445
Microsoft SQL Server (MSFT SQL) Port 1433
Network Time Protocol Port 123
Remote Desktop / Remote Assistance / Terminal Server (RDP)
Port 3389
Remote Procedure Calls (RPC) Port 135
Secure Web Server (HTTPS) Port 443
Universal Plug and Play (UPNP) Port 5000
Web Server (HTTP) Port 80
Windows File Sharing (NETBIOS) Ports 137-139
System service ports can also be configured to allow a computer
to share its Internet connection with other computers connected
to it through the same network. This connection, known as
Internet Connection Sharing (ICS), allows the computer that is
sharing the connection to act as a gateway to the Internet for the
other networked computer.
Note: If your computer has an application that accepts either
Web or FTP server connections, the computer sharing the
connection may need to open the associated system service port
and allow forwarding of incoming connections for those ports.
Page 95

Chapter 19 Introduction 93
Allow access to an existing system service port
You can open an existing port to allow remote access to a
network service on your computer.
Note: An open system service port can make your computer
vulnerable to Internet security threats; therefore, only open a port
if necessary.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Firewall pane, click System Services.
4 Under Open System Service Port, select a system service to
open its port.
5 Click OK.
Block access to an existing system service port
You can close an existing port to block remote network access to
a service on your computer.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Firewall pane, click System Services.
4 Under Open System Service Port, clear a system service to
close its port.
5 Click OK.
Configure a new system service port
You can configure a new network service port on your computer
that you can open or close to allow or block remote access on
your computer.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Firewall pane, click System Services.
4 Click Add.
5 In the System Services pane, under Ports and System
Services, enter the following:
Program name
Inbound TCP/IP ports
Page 96

94 McAfee VirusScan Plus
Outbound TCP/IP ports
Inbound UDP ports
Outbound UDP ports
6 If you want to send this port's activity information to another
networked Windows computer that shares your Internet
connection, select Forward network activity on this port to
network users who use Internet Connection Sharing.
7 Optionally describe the new configuration.
8 Click OK.
Note: If your computer has a program that accepts either Web or
FTP server connections, the computer sharing the connection
may need to open the associated system service port and allow
forwarding of incoming connections for those ports. If you are
using Internet Connection Sharing (ICS), you also need to add a
trusted computer connection on the Trusted IP Addresses list.
For more information, see Add a trusted computer connection.
Modify a system service port
You can modify inbound and outbound network access
information about an existing system service port.
Note: If port information is entered incorrectly, the system
service fails.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Firewall pane, click System Services.
4 Select a system service, and then click Edit.
5 In the System Services pane, under Ports and System
Services, enter the following:
Program name
Inbound TCP/IP ports
Outbound TCP/IP ports
Inbound UDP ports
Outbound UDP ports
6 If you want to send this port's activity information to another
networked Windows computer that shares your Internet
connection, select Forward network activity on this port to
network users who use Internet Connection Sharing.
7 Optionally describe the modified configuration.
8 Click OK.
Page 97

Chapter 19 Introduction 95
Remove a system service port
You can remove an existing system service port from your
computer. After removal, remote computers can no longer access
the network service on your computer.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Firewall pane, click System Services.
4 Select a system service, and then click Remove.
5 At the prompt, click Yes to confirm.
Page 98

Page 99

C HAPTER 20
Managing computer connections
You can configure Firewall to manage specific remote
connections to your computer by creating rules, based on
Internet Protocol addresses (IPs), that are associated with remote
computers. Computers that are associated with trusted IP
addresses can be trusted to connect to your computer and those
IPs that are unknown, suspicious, or distrusted, can be banned
from connecting to your computer.
When allowing a connection, ensure that the computer that you
trust is safe. If a computer that you trust is infected through a
worm or other mechanism, your computer can be vulnerable to
infection. In addition, McAfee recommends that the computer(s)
you trust are protected by a firewall and an up-to-date antivirus
program also. Firewall does not log traffic or generate event alerts
from IP addresses in the Trusted IP Addresses list.
Computers that are associated with unknown, suspicious, or
distrusted IP addresses can be banned from connecting to your
computer.
97
Since Firewall blocks all unwanted traffic, it is normally not
necessary to ban an IP address. You should ban an IP address
only when you are certain an Internet connection poses a specific
threat. Ensure that you do not block important IP addresses, such
as your DNS or DHCP server, or other ISP-related servers.
Depending on your security settings, Firewall can alert you when
it detects an event from a banned computer.
In this chapter
Trusting computer connections ................................98
Banning computer connections ................................101
Page 100

98 McAfee VirusScan Plus
Trusting computer connections
You can add, edit, and remove trusted IP addresses on the
Trusted and Banned IPs pane, under Trusted IP Addresses.
The Trusted IP Addresses list on the Trusted and Banned IPs
pane allows all traffic from a specific computer to reach your
computer. Firewall does not log traffic or generate event alerts
from IP addresses that appear in the Trusted IP Addresses list.
Firewall trusts any checked IP addresses on the list, and always
allows traffic from a trusted IP through the firewall on any port.
Activity between the computer associated with a trusted IP
address and your computer is not filtered or analyzed by Firewall.
By default, Trusted IP Addresses lists the first private network that
Firewall finds.
When allowing a connection, ensure that the computer that you
trust is safe. If a computer that you trust is infected through a
worm or other mechanism, your computer can be vulnerable to
infection. In addition, McAfee recommends that the computer(s)
you trust are protected by a firewall and an up-to-date antivirus
program also.
Add a trusted computer connection
You can add a trusted computer connection and its associated IP
address.
1 On the McAfee SecurityCenter pane, click Internet &
Network, then click Configure.
2 On the Internet & Network Configuration pane, under
Firewall protection is enabled, click Advanced.
3 On the Firewall pane, click Trusted and Banned IPs.
4 On the Trusted and Banned IPs pane, select Trusted IP
Addresses, and then click Add.
5 Under Add Trusted IP Address Rule, do one of the
following:
Select Single IP Address, and then enter the IP address.
Select IP Address Range, and then enter the starting and
ending IP addresses in the From IP Address and To IP
Address boxes.
 Loading...
Loading...