Page 1

McAfee UnInstaller
User’s Guide
Version 6.0
Page 2

COPYRIGHT
Copyright © 1999 Network Associates, Inc. and its Affiliated Companies. All Rights Reserved.
No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
system, or translated into any language in any form or by any means without the written
permission of Network Associates, Inc.
TRADEMARK ATTRIBUTI ONS
* ActiveHelp, Bomb Shelter, Building a World of Trust, CipherLink, Clean-Up, Cloaking, CNX,
Compass 7, CyberCop, CyberMedia, Data Security Letter, Discover, Distributed Sniffer System, Dr
Solomon’s, Enterprise Secure Cast, First Aid, ForceField, Gauntlet, GMT, GroupShield, HelpDesk,
Hunter, ISDN Tel/Scope, LM 1, LA NGuru, Leadin g Help Desk Technolo gy, Magic Solu tions, Magi cSpy,
MagicTree, Magic University, MagicWin, MagicWord, McAfee, McAfee Associates, MoneyMagic, More
Power To You, Multimedia Cloaking, NetCrypto, NetOctopus, NetRoom, NetSca n, Net Shield, NetShiel d,
NetStalker, Net Tools, Network Associates, Network General, Network Uptime!, NetXRay, Nuts & Bolts,
PC Medic, PCNotary, PGP, PGP (Pretty Good Privacy), PocketScope, Pop-Up, PowerTelnet, Pretty
Good Privacy, PrimeSupport, RecoverKey, RecoverKey-International, ReportMagic, RingFence, Router
PM, Safe & Sound, SalesMagic, SecureCast, Service Level Manager, ServiceMagic, Site Meter, Sniffer,
SniffMaster, SniffNet, Stalker, Statistical Information Retrieval (SIR), SupportMagic, Switch PM,
TeleSniffer, TIS, TMach, TMeg, Tota l Network Security, Total Network Vis ibility, Total Service Desk,
Total Virus Defense, T-POD, Trusted Ma ch, Trusted Ma il, Uninstall er, Virex, Vi rex-PC, Virus Fo rum,
ViruScan, VirusScan, VShi eld, WebScan , Web Shield, W ebS niffer , WebSt alker W ebW all , and ZAC 2000
are registered trademarks of Network Associates and/or its affiliates in the US and/or other countries. All
other registered and unregistered trademarks in this document are the sole property of their respective
owners.
LICENSE AGREEMENT
NOTICE TO ALL USERS: CAREFULLY READ THE FOLLOWING LEGAL AGREEMENT
("AGREEMENT"), FOR THE LICENSE OF SPECIFIED SOFTWARE ("SOFTWARE") BY
NETWORK ASSOCIATES, INC. ("McAfee"). BY CLICKING THE ACCEPT BUTTON OR
INSTALLING THE SOFTWARE, YOU (EITHER AN INDIVIDUAL OR A SINGLE ENTITY)
CONSENT TO BE BOUND BY AND BECOME A PARTY TO THIS AGREEMENT. IF YOU DO
NOT AGREE TO ALL OF THE TERMS OF THIS AGREEMENT, CLICK THE BUTTON THAT
INDICATES THAT YOU DO NOT ACCEPT TH E TERMS OF THIS AGREEMENT AND DO
NOT INSTALL THE SOFTWARE. (IF APPLICABLE, YOU MAY RETURN THE PRODUCT
TO THE PLACE OF PURCHASE FOR A FULL REFUND.)
1. License Grant. Subject to the payment of the applicabl e license fees, and subject to the
terms and conditions of this Agreement, McAfee hereby grants to you a non-exclusive,
non-transferable right to use one copy of the specified version of the Software and the
accompanying documentation (t he "Documentation" ). You may insta ll one copy of th e
Software on one computer, workstation, personal digital assistant, pager, "smart phone"
or other electronic device for which the Software was designed (each, a "Client Device").
If the Software is licensed as a suite or bundle with more than one specified Software
product, this license applies to all such specified Software products, subject to any
restrictions or usage terms specified on the applicable price list or product packaging that
Issued June 2000 / McAfee UnInstaller v6.0
Page 3

(i.e., the required number of licenses would equal the number of distinct inputs to the
multiplexing or pooling software or hardware "front end"). If the number of Client
Devices or seats that can connect to the Software can exceed the number of licenses you
have obtained, then you must have a reasonable mechanism in place to ensure that your
use of the Software does not exceed the use limits specified for the licenses you have
obtained. This license authorizes you to make or download one copy of the
Documentation for each Client Device or seat that is licensed, provided that each such
copy contains all of the Documentation’s proprietary notices.
c. Volume Licenses. If the Software is licensed with volume license terms specified in the
applicable price list or product packaging for the Software, you may make, use and
install as many additional copies of the Software on the number of Client Devices as the
volume license authorizes. You must have a reasonable mechanism in place to ensure
that the number of Clien t Devices on which the S oftware has been insta lled does not
exceed the number of licenses you have obtained. This license authorizes you to make
or download one copy of the Documentation for ea ch additional copy authorized by the
volume license, provided that each such copy contains all of the Documentation’s
proprietary notices.
2. Term. This Agreement is effective for an unlimited duration unless and until earlier
terminated as set forth herein. This Agreement will terminate automatically if you fail to
comply with any of the limitations or other requirements described herein. Upon any
termination or expiration of this Agreement, you must destroy all copies of the Software
and the Documentation. You may terminate this Agreement at any point by destroying
all copies of the Software and the Documentation.
3. Updates. For the time period specified in the applicable price list or product packaging for
the Software you are entitled to download revisions or updates to the Software when and
as McAfee publishes them via its electronic bulletin board system, website or through
other online services. For a period of ninety (90) days from the date of the original
purchase of the Software, you are entitled to download one (1) revision or upgrade to the
Software when and as McAfee publishes it via its electronic bulletin board system, website
or through other online services. After the specified time period, you have no further
rights to receive any revisions or upgrades without purchase of a new license or annual
upgrade plan to the Software.
4. Ownership Rights. The Software is protected by United States copyright laws and
international treaty provisions. McAfee and its suppliers own and retain all right, title and
interest in and to the Software, including all copyrights, patents, trade secret rights,
trademarks and other intellectual property rights therein. Your possession, installation,
or use of the Software does not transfer to you any title to the intellectual property in the
Software, and you will not acquire any rights to the Software except as expressly set forth
in this Agreement. All copies of the Software and Documentation made hereunder must
contain the same proprietary notices that appear on and in the Software and
Documentation.
User’s Guide iii
Page 4

5. Restrictions. You may not rent, lease, loan or resell the Software. You may not permit
third parties to benefit from the use or functionality of the Software via a timesharing,
service bureau or other arrangement, except to the extent such use is specified in the
applicable list price or product packaging for the Software. You may not transfer any of
the rights granted to you under this Agreement. You may not reverse engineer,
decompile, or disassemble the Software, except to the extent the foregoing restriction is
expressly prohibited by applicable law. You may not modify, or create derivative works
based upon, the Software in whole or in part. You may not copy the Software or
Documentation except as expressly permitted in Section 1 above. You may not remove
any proprietary notices or labels on the Software. All rights not expressly set forth
hereunder are reserved by McAfee. McAfee reserves the right to periodically conduct
audits upon advance written notice to verify compliance with the terms of this
Agreement.
6. Warranty and Disclaimer
a. Limited Warranty. McAfee warrants that for sixty (60) days from the date of original
purchase the media (e.g., diskettes) on which the Software is contained will be free from
defects in materials and workmanship.
b. Customer Remedies. McAfee’s and its suppliers’ entire liability and your exclusive
remedy for any breach of the foregoing warranty shall be, at McA fee’s option, either (i)
return of the purchase price paid for the license, if any, or (ii) replacement of the
defective media in which the Software is contained. You must return the defective
media to McAfee at your expense with a copy of your receipt. Th is limited warra nty is
void if the defect has resulted from accident, abuse, or misapplication. Any replacement
media will be warranted for the remainder of the original warranty period. Outside the
United States, this remedy is not available to the extent McAfee is subject to restrictions
under United States export control laws and regulations.
c. Warranty Disclaimer. Except for the limited warranty set forth herein, THE
SOFTWARE IS PROVIDED "AS IS." TO THE MAXIMUM EXTENT PERMITTED BY
APPLICABLE LAW, MCAFEE DISCLAIMS ALL WARRANTIES, EITHER EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO IMPLIED WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, AND
NONINFRINGEMENT WITH RESPECT TO THE SOFTWARE AND THE
ACCOMPANYING DOCUMENTATION. YOU ASSUME RESPONSIBILITY FOR
SELECTING THE SOFTWARE TO ACHIEVE YOUR INTENDED RESULTS, AND FOR
THE INSTALLATION OF, USE OF, AND RESULTS OBTAINED FROM THE
SOFTWARE. WITHOUT LIMITING THE FOREGOING PROVISIONS, MCAFEE
MAKES NO WARRANTY THAT THE SOFTWARE WILL BE ERROR-FREE OR FREE
FROM INTERRUPTIONS OR OTHER FAILURES OR THAT THE SOFTWARE W ILL
MEET YOUR REQUIREMENTS. SOME STATES AND JURISDICTIONS DO NOT
ALLOW LIMITATIONS ON IMPLIED WARRANTIES, SO THE ABOVE LIMITATION
MAY NOT APPLY TO YOU. The foregoing provisions shall be enforceable to the
maximum extent permitted by applicable law.
iv McAfee UnInstaller
Page 5

7. Limitation of Liability. UNDER NO CIRCUMSTANCES AND UNDER NO LEGAL
THEORY, WHETHER IN TORT, CONTRACT, OR OTHERWISE, SHALL MCAFEE OR
ITS SUPPLIERS BE LIABLE TO YOU OR TO ANY OTHER PERSON FOR ANY
INDIRECT, SPECIAL, INCIDENTAL, OR CONSEQUENTIAL DAMAGES OF ANY
CHARACTER INCLUDING, WITHOUT LIMITATION, DAMAGES FOR LOSS OF
GOODWILL, WORK STOPPAGE, COMPUTER FAILURE OR MALFUNCTION, OR FOR
ANY AND ALL OTHER DAMAGES OR LOSSES. IN NO EVENT WILL MCAFEE BE
LIABLE FOR ANY DAMAGES IN EXCESS OF THE LIST PRICE MCAFEE CHARGES
FOR A LICENSE TO THE SOFTWARE, EVEN IF MCAFEE SHALL HAVE BEEN
ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. THIS LIMITATION OF
LIABILITY SHALL NOT APPLY TO LIABILITY FOR DEATH OR PERSONAL INJURY
TO THE EXTENT THAT APPLICABLE LAW PROHIBITS SUCH LIMITATION.
FURTHERMORE, SOME STATES AND JURISDICTIONS DO NOT ALLOW THE
EXCLUSION OR LIMITATION OF INCIDENTAL OR CONSEQUENTIAL DAMAGES,
SO THIS LIMITATION AND EXCLUSION MAY NOT APPLY TO YOU. The foregoing
provisions shall be enforceable to the maximum extent permitted by applicable law.
8. United States Government. The Software and accompanying Documentation are deemed
to be "commercial computer software" and "commercial computer software
documentation," respectively, pursuant to DFAR Section 227.7202 and FAR Section
12.212, as applicable. Any use, modification, reproduction, release, performance, display
or disclosure of the Software and accompanying Documentation by the United States
Government shall be governed solely by the terms of this Agreement and shall be
prohibited except to the extent expressly permitted by the terms of this Agreement.
9. Export Controls. Neither the Software nor the Documentation and underlying
information or technology may be downloaded or otherwise exported or re-exported (i)
into (or to a national or resident of ) Cuba, Iran, Iraq, Libya, North Korea, Sudan, Syria or
any other country to which the United States has embargoed goods; or (ii) to anyone on
the United States Treasury Department’s list of Specially Designated Nations or the
United States Commerce Department’s Table of Denial Orders. By downloading or using
the Software you are agreeing to the foregoing and you are certifying that you are not
located in, under the control of, or a national or resident of any such country or on any
such list.
IN ADDITION, YOU SHOULD BE AWARE OF THE FOLLOWING: EXPORT OF THE
SOFTWARE MAY BE SUBJECT TO COMPLIANCE WITH THE RULES AND
REGULATIONS PROMULGATED FROM TIME TO TIME BY THE BUREAU OF
EXPORT ADMINISTRATION, UNITED STATES DEPARTMENT OF COMMERCE,
WHICH RESTRICT THE EXPORT AND RE-EXPORT OF CERTAIN PRODUCTS AND
TECHNICAL DATA. IF THE EXPORT OF THE SOFTWARE IS CONTROLLED UNDER
SUCH RULES AND REGULATIONS, THEN THE SOFTWARE SHALL NOT BE
EXPORTED OR RE-EXPORTED, DIRECTLY OR INDIRECTLY, (A) WITHOUT ALL
EXPORT OR RE-EXPORT LICENSES AND UNITED STATES OR OTHER
GOVERNMENTAL APPROVALS REQUIRED BY ANY APPLICABLE LAWS, OR (B) IN
VIOLATION OF ANY APPLICABLE PROHIBITION AGAINST THE EXPORT OR
RE-EXPORT OF ANY PART OF THE SOFTWARE.
User’s Guide v
Page 6

SOME COUNTRIES HAVE RESTRICTIONS ON THE USE OF ENCRYPTION WITHIN
THEIR BORDERS, OR THE IMPORT OR EXPORT OF ENCRYPTION EVEN IF FOR
ONLY TEMPORARY PERSONAL OR BUSINESS USE. YOU ACKNOWLEDGE THAT
THE IMPLEMENTATION AND ENFORCEMENT OF THESE LAWS IS NOT ALWAYS
CONSISTENT AS TO SPECIFIC COUNTRIES. ALTHOUGH THE FOLLOWING
COUNTRIES ARE NOT AN EXHAUSTIVE LIST THERE MAY EXIST RESTRICTIONS
ON THE EXPORTATION TO, OR IMPORTATION OF, ENCRYPTION BY: BELGIUM,
CHINA (INCLUDING HONG KONG), FRANCE, INDIA, INDONESIA, ISRAEL,
RUSSIA, SAUDI ARABIA, SINGAPORE, AND SOUTH KOREA. YOU
ACKNOWLEDGE IT IS YOUR ULTIMATE RESPONSIBILITY TO COMPLY WITH ANY
AND ALL GOVERNMENT EXPORT AND OTHER APPLICABLE LAWS AND THAT
MCAFEE HAS NO FURTHER RESPONSIBILITY AFTER THE INITIAL SALE TO YOU
WITHIN THE ORIGINAL COUNTRY OF SALE.
10.High Risk Activities. The Software is not fault-tolerant and is not designed or intended
for use in hazardous environments requiring fail-safe performance, including without
limitation, in the operation of nuclear facilities, aircraft navigation or communication
systems, air traffic control, weapons systems, direct life-support machines, or any other
application in which the failure of the Software could lead directly to death, personal
injury, or severe physical or property damage (collectively, "High Risk Activities").
McAfee expressly disclaims any express or implied warranty of fitness for High Risk
Activities.
11. Miscellaneous. This Agreement is governed by the laws of the United States and the State
of California, without reference to conflict of laws principles. The application of the
United Nations Convention of Contracts for the International Sale of Goods is expressly
excluded. This Agreement sets forth all rights for the user of the Software and is the entire
agreement between the parties. This Agreement supersedes any other communications
with respect to the Software and Documentation. This Agreement may not be modified
except by a written addendum issued by a duly authorized representative of McAfee. No
provision hereof shall be deemed waived unless such waiver shall be in writing and
signed by McAfee or a duly authorized representative of McAfee. If any provision of this
Agreement is held invalid, the remainder of this Agreement shall continue in full force
and effect. The parties confirm that it is their wish that this Agreement has been written
in the English language only.
12.McAfee Customer Contact. If you have any questions concerning these terms and
conditions, or if you would like to contact McAfee for any other reason, please call (408)
988-3832, fax (408) 970-9 727, or write: McAfee Software, 39 65 Freedom Circle, Santa Clara,
California 95054. http://www.mcafee.com.
Statements made to you in the course of this sale are subject to the Year 2000 Information
and Readiness Disclosure Act (Public Law 105-271). In the case of a dispute, this Act may
reduce your legal rights regarding the use of any statements regarding Year 2000
readiness, unless otherwise specified in your contract or tariff.
vi McAfee UnInstaller
Page 7

Table of Contents
Chapter 1. Welcome to UnInstaller . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1
When should I use UnInstaller? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1
About this manual . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2
Chapter 2. Installing UnInstaller . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3
What happens when I install UnInstaller? . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3
Why do I have to create the SmartLinks database? . . . . . . . . . . . . . . . . .4
What does the Interview do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .5
How do I put UnInstaller to work? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .5
What do the UnInstaller wizards do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . .6
What is PowerClean? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .8
How do I change UnInstaller defaults? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .8
What is McAfee Guardian? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .10
Chapter 3. Freeing Disk Space . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .13
How do I keep my computer free of unnecessary files? . . . . . . . . . . . . . . . . .13
How do I set up QuickClean to run automatically? . . . . . . . . . . . . . . . . .13
How do I schedule QuickClean to run at a specific time? . . . . . . . . . . .14
How do I free a specific amount of disk space on a drive? . . . . . . . . . . . . . .15
How do I change defaults for SpaceMaker? . . . . . . . . . . . . . . . . . . . . . .16
Chapter 4. Managing Applications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .17
How do I get rid of an application? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .18
How do I make a copy of an application to rebuild on another computer? .19
How do I rebuild a transported application on another computer? . . .20
How do I archive an application so I can use it again later? . . . . . . . . . . . . .21
How do I move an application from one location to another? . . . . . . . . . . . .22
How can I monitor installation? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .23
How do I set BackTrack Monitor to run in the background? . . . . . . . . .23
How do I monitor installation of a single application? . . . . . . . . . . . . . .24
How do I undo an application installation that I monitored? . . . . . . . . .25
User’s Guide vii
Page 8

Table of Contents
Chapter 5. Restoring Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .27
Restoring applications and files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .27
How do I restore an archived or backed-up application? . . . . . . . . . . . . . . . .27
How do I restore deleted files? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .29
How do I get rid of backup copies I no longer want? . . . . . . . . . . . . . . . . . . .30
How do I see what UnInstaller has done? . . . . . . . . . . . . . . . . . . . . . . . . . . . .30
Chapter 6. Using PowerClean . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .33
What can I do when I use the PowerClean feature? . . . . . . . . . . . . . . . . . . . .33
Why does the PowerClean feature open in read-only mode? . . . . . . . .34
How do I work with the PowerClean feature? . . . . . . . . . . . . . . . . . . . . . . . . .35
What are the default file groups? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .36
How can I create a custom group? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .37
What commands are on the PowerClean menus? . . . . . . . . . . . . . . . . .38
How do I use the tab panes? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .40
What do the color codes mean? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .40
How do I change the defaults for the PowerClean feature? . . . . . . . . . . . . . .41
How can I see what I have done using the PowerClean feature? . . . . . . . . .43
Appendix A. About Windows 98 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .45
Windows 98 Applications and Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .45
How does an application keep track of its configuration settings? . . . . . . .45
What is the Windows Registry? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .46
How are computer files named? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .46
What are file name extensions? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .47
What is an associated file? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .48
What are junk files? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .49
What are Internet cookies and how are they used? . . . . . . . . . . . . . . . .50
What are compressed files? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .51
What is an autoexpanding compressed file? . . . . . . . . . . . . . . . . . . . . .51
Appendix B. Product Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .53
How to Contact McAfee . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .53
Customer service . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .53
Technical support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .54
viii McAfee UnInstaller
Page 9

Table of Contents
McAfee training . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .55
User’s Guide ix
Page 10

Table of Contents
x McAfee UnInstaller
Page 11

1Welcome to UnInstaller
UnInstaller™ can be used for many more purposes than simply uninstalling
old applications.
For example, UnInstaller can clean up junk files that have built up on your
computer as you browsed the Internet, and it can do this cleanup
automatically on a schedule that you specify. UnInstaller can also move
applications from one hard disk to another— even to another computer—and
change all references to the application at the same time.
Consider the following questions for more suggestions.
When should I use Un Installer?
Think about how you use your computer to see how useful UnInstaller can be.
Do you….
• Have programs that you don’t use anymore, for example games that you
don’t play frequently?
Use the Archive wizard to create an archive of programs or games by
compressing them. Then when you want to play a game again, click the old
shortcut to the game and let UnInstaller restore it to its original location.
1
• Use the Internet?
When you surf the Internet, your computer can collect megabytes of
Internet junk files. Images, plug-ins, and other files you won’t need again
are downloaded to your computer. QuickClean can delete these files
quickly and reclaim disk space.
®
• Have a Zip
UnInstaller’s Archive and Transport wizards can compress entire
applications to a large removable disk. When you wa nt the applications
again, you restore them to the original computer or rebuild them on a
different computer without losing a ny setup information.
Perhaps more importantly, you ca n specify that UnInstaller backups
should be stored on a large removable disk to save space on your internal
hard drive.
• Have a new, second hard disk?
Use the Move wizard to relocate applications on the new disk and free
space on the old disk without losin g any setup information.
drive or other large-capacity removable disk drive?
User’s Guide 1
Page 12

Welcome to UnInstaller
• Have outdated applications that you will never use again?
If you have old applications that you no longer use, the Remove wizard
will remove all traces of them from your computer.
Of course, if you think you might use an appli c ation again in some
circumstances, you can use the Archive wizard to create a compressed
backup copy and keep shortcuts to the application on your computer so
that you can restore it easily.
About this manual
This manual contains general information about using UnInstaller. It does not
describe step-by-step use of the UnInstaller wizards.
More detailed procedural information and step-by-step information about the
wizards are contained in the online help. In any dialog box, click Help for
specific information about the dialog box. When using the PowerClean
feature, click PowerClean Help on the Help menu.
For information on new additions to UnInstaller, you can also open the
Readme.txt file located in the UnInstaller folder on your computer to view
additional information.
2 McAfee UnInstaller
Page 13

2Installing UnInstaller
The installation program on the UnInstaller CD lets you install the program
easily on your computer. Installation should start automatically when you put
the CD in the CD-ROM drive. The information in the following paragraphs
will help you install and start using UnInstaller.
What happens when I i nstall UnInstaller?
You can install and run UnInstaller if your computer is running Windows® 95
or later, or Windows NT 4.0 or later.
NOTE: To install UnInstaller on Windows NT, you must be logged in as
a user who has Administrator privileges.
To install UnI nstaller :
1. Insert the UnInstaller CD into your CD drive. The installation wizard should start automatically. If it does not, click the
drive letter of your CD drive in Windows Explorer, and double-click the
file named Setup.exe in the file list.
2
2. In the first installation wizard page, click Install UnInstaller.
3. Follow the instructions in the wizard pages to choose the drive and
folder where UnInstaller should be installed.
After each step, click Next.
4. Use the Interview wizard to specify some initial UnInstaller defaults, as
described in “What does the Interview do?,” on page 5.
As part of completing installation, UnInsta ller builds the SmartLinks
database for your computer while you provide information in a user
interview. When the interview is complete, the installation program
might still be building the SmartLinks database. Building the database
takes a few minutes. The larger your hard disk and the more data files it
contains, the longer it takes.
5. Click Finish in the final setup screen.
User’s Guide 3
Page 14

Installing UnInstaller
By default, the Readme file appears in Notepad. If you do not want to
read the release notes in the Readme file, clear the check in the View
release notes? check box before you click Finish.
Why do I have to create the SmartLinks database?
The SmartLinks database stores information about the relationship between
files on your computer. It stores the names and locations of all files needed by
the operating system. For each application, th e Smar tLinks database stores
information about all of the files that the application needs to run correctly,
including icons, dynamically linked libraries (DLLs), and other executable
files, as well as operating system files that are used by the application. This
information makes the SmartLinks database a complete, cross-referenced
record of how executable and system files are used on your computer.
It is this information that makes using UnInstaller quick and safe. It ensures
that applications can be moved, archived, deleted, and transported safely and
completely, and it determines the files that can be safely deleted without
damaging an application or the operating system.
The SmartLinks database is created when you install UnInstaller. Because
building the database the first time can take several minutes, it is created in the
background as you provide some default information in an interview wizard.
When is the SmartLinks database updated?
After UnInstaller has created the SmartLinks database for your computer,
updating it takes much less time. Only records for files that have changed are
updated.
UnInstaller updates the SmartLinks database in the following circumstances:
• Each time you start UnInstaller, the old version of the da tabase is compared
with new information on your computer.
• After you restore files or applications from UnInstaller backup copies,
UnInstaller records changes that it has just made.
• After you delete or archive files or applications, UnInstaller records
changes.
• After you manually select a wizard from the main UnInstaller screen,
UnInstaller records changes that the wizard makes.
4 McAfee UnInstaller
Page 15

What does the Interview do?
As you install UnInstaller, you answer a few questions about how you use files
on your computer, and whether you want to schedule some UnInstaller
events.
To run the interview again, click Customization Interview on the Options
menu in the main UnInstaller screen.
The Settings dialog box pages also let you view or change all settings that you
specified in the interview. For information about using the Settings dialog box,
see “How do I change UnInstaller defaults?,” on page 8.
How do I put UnInstaller to wo rk?
UnInstaller uses safe and simple wizards to perform its major tasks. Whe n you
use an UnInstaller wizard to clean up your hard disk or manage applications,
at each step you see exactly what you are specifying, and you can go back to
previous screens and change options if you change your mind.
Even if you are an expert computer user, UnInstaller wizards can automate
tasks, such as removing junk files, that would otherwise be time-consuming or
error-prone.
Installing UnInstaller
User’s Guide 5
Page 16
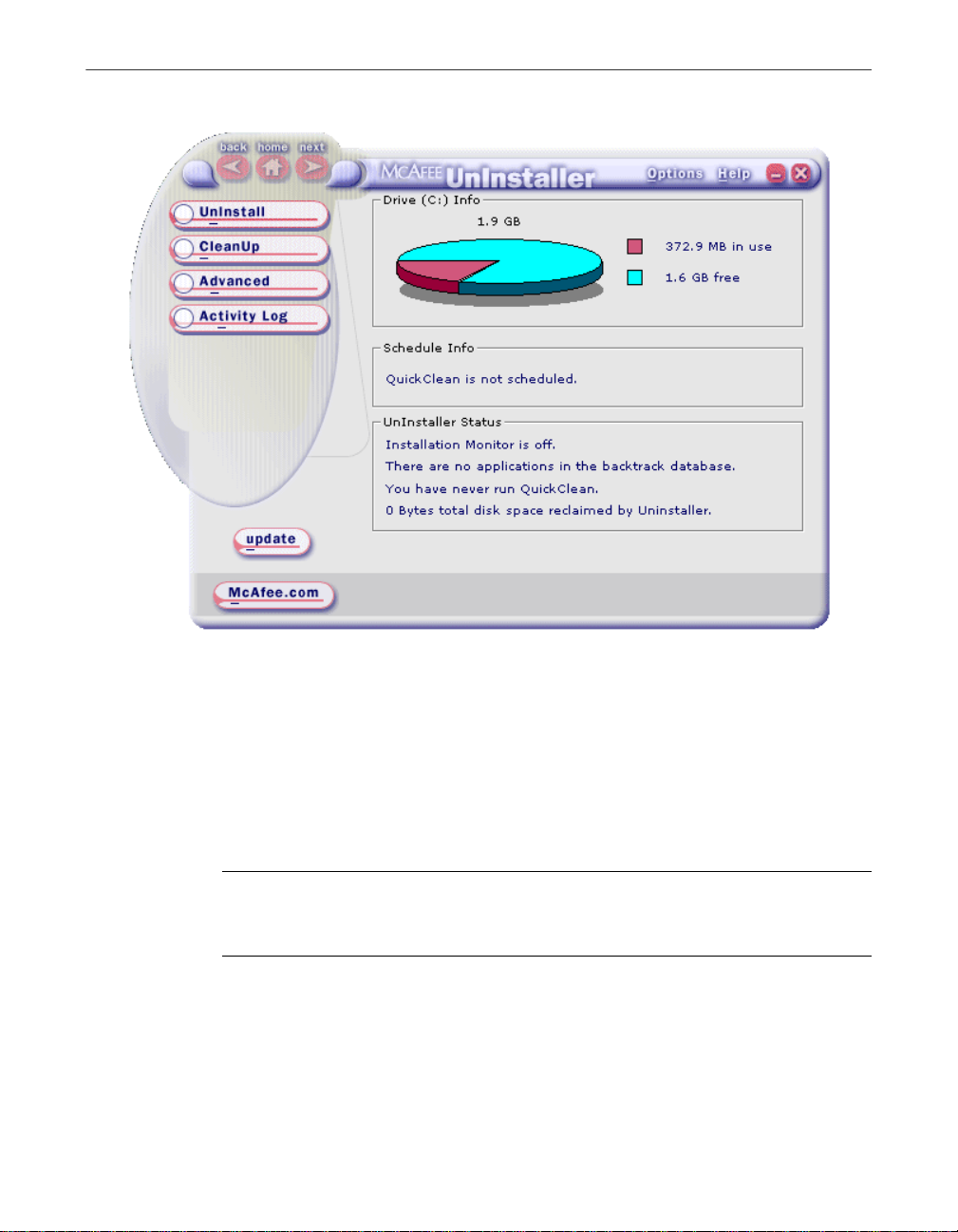
Installing UnInstaller
Figure 2-1. The UnInstaller Application window
To run an UnInstaller wizard, click its button in the main UnInstaller w indow.
What do the UnInstaller wizards do?
UnInstaller wizards simplify cleaning up disk space and managing
applications. The wizards are listed and described in Table 2-1.
NOTE: Wizards are designed to be easy to understand and to use. Each
wizard screen tells you what you need to know to enter information or
choose options. If you want to know more about a wizard, click Help.
6 McAfee UnInstaller
Page 17

Installing UnInstaller
By default, SpaceMaker and Remove wizards create backup copies of files
before they are deleted. Although you can turn off backup creation when you
run the wizard, it is a good idea to make backups. Later, when you are sure
that you do not want to undo any UnInstaller actions, you can delete the
backup copy.
Table 2-1. The UnInstaller wizards
This wizard... Does this...
QuickClean Deletes various kinds of junk files and unconnected items in
the Windows Registry. QuickClean can be scheduled to run
automatically at any interval you specify.
.
Remove Deletes any application you specify, and removes all related
shortcuts and Registry entries.
Archive Compresses an application into a backup file that you can
restore whenever you need it again. You can a lso in cl ude data
files that are associated with the application, if there are any.
.
Move Relocates an ap plication. Complete ly moves an applicatio n
from one drive or folder to another—even to another
computer—and adjusts shortcuts and Registry entries to refer
to the application in its new location.
.
Transport Packages an application so that you can rebuild it with the
same option settings on another computer. You can also select
and include data files that are associated with the application.
.
Restore Restores deleted applications or files if backup copies were
created.
You can restore an entire application, a few files from an
application, or a few miscel lan eous fi les, such as th ose d e leted
by Remove or SpaceMaker—but only if backup copies were
created before the files were deleted.
.
User’s Guide 7
Page 18

Installing UnInstaller
Table 2-1. The UnInstaller wizards (Continued)
This wizard... Does this...
BackTrack Monitors application installation.
SpaceMaker Deletes old files in specific categories until it has freed the
What is PowerClean?
PowerClean is not a wizard. It is a feature that lets you see files on your
computer, organized into categories, such as Internet Junk, Duplicate Files,
Archives, Multimedia Files, and so on. The feature also displays application
information that is stored in the Windows Registry.
If you are an experienced computer user, you can use Po werClean to manage
files manu ally . If yo u ar e in te re sted in trac ki ng s pe cif ic file s o r fi le s in spe cif ic
folders, you can even create custom files groups.
Lets you undo the installation of any application if it was
monitored by BackTrack.
.
amount of disk space you specify.
.
How do I change UnInstal ler defaults?
As you install UnInstaller, you have the chance to change some basic defaults
in the Interview. Later, after UnInstaller is installed, you can use the Settings
dialog box to review or change all default settings.
To see exactly what the default settings are, or to change them, click Settings
on the Options menu in the main UnInstaller screen. Then click the Settings
dialog box tabs for each wizard or option category.
The SpaceMaker, BackTrack, and QuickClean wizards and the PowerClean
feature all have Settings dialog box pages where you specify their default
behavior, including the age that files must be before they can be deleted.
8 McAfee UnInstaller
Page 19
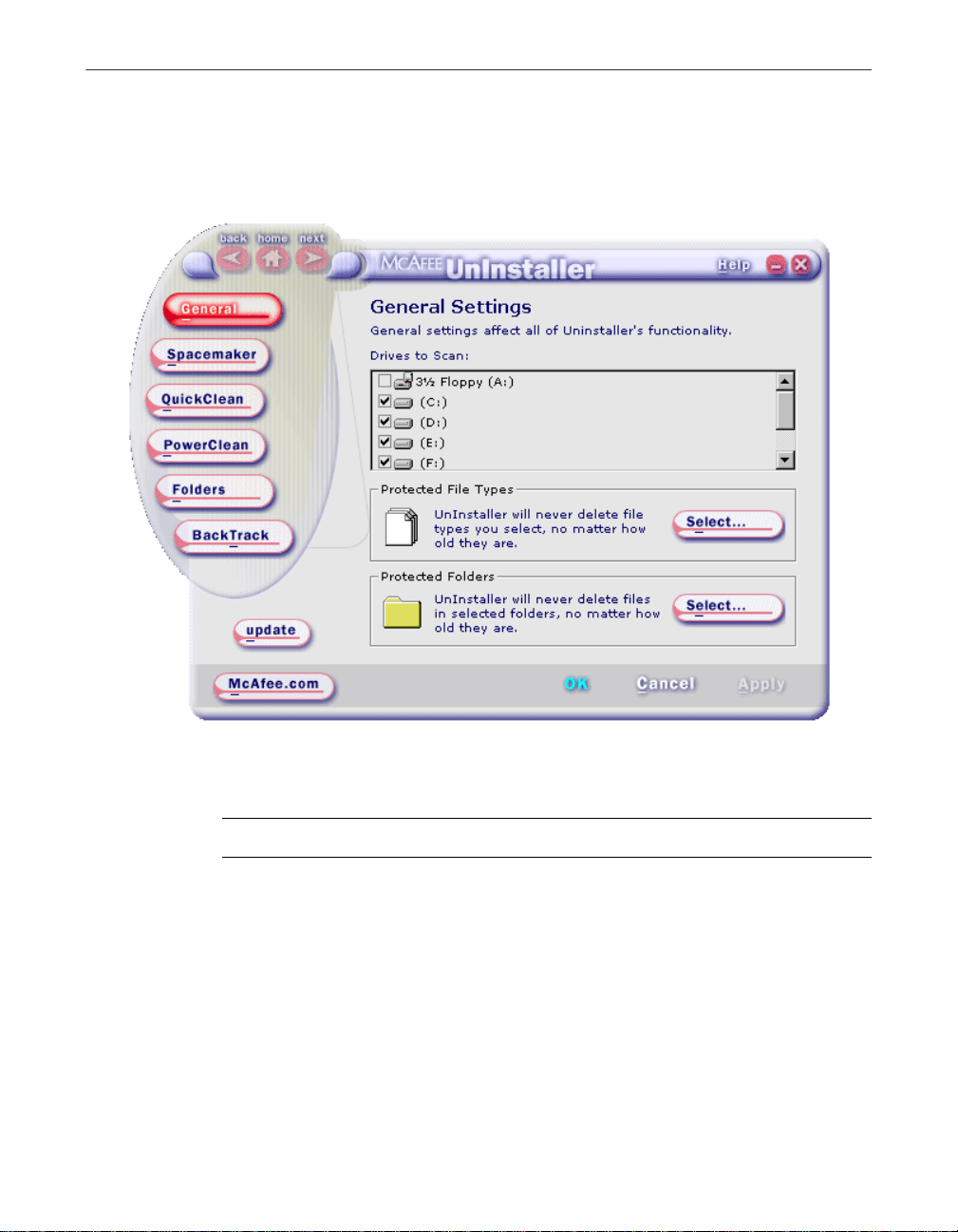
Installing UnInstaller
You can change most option settings temporarily when you run a wizard, and
you can open the Settings dialog box page for the wizard and make permanent
changes to the default.
Figure 2-2. The General page of the Settings dialog box
Table 2-1 on page 10 provides a brief description of each Settings dialog box
page and tells you where to find more information.
NOTE: For information about any Settings dialog box page, click Help.
User’s Guide 9
Page 20

Installing UnInstaller
Table 2-1. Options in the Settings dialog box
Options on this page... Set this default behavior to determine...
General Which drives are tr ac ke d by t he SmartLinks database,
and which files and folders are excluded from all
wizard or PowerCle an lis ts.
Click Help in the General page of the Settings dialog
box for infor mation about these options.
SpaceMaker How old files must be before they can be deleted, and
which kinds of files can be deleted.
PowerClean Whether backups are created for deleted f iles, how ol d
files must be before they can be deleted, and other
delete protection options.
BackTrack Whether BackTrack’s I nsta llation Monito r runs as y ou
work, which kinds of installatio ns it monit ors, and
how long BackTrack archives are kept before they are
deleted.
QuickClean How old files must be before they can be deleted, and
what kinds of files can be deleted.
Folders The default backup, Archive, BackTrack, and
Transport compressed file locations.
Click Help in the Folders page of the Settings dialog
box for infor mation about these options.
What is McAfee G uardian?
You use McAfee Guardian to schedule the QuickClean wizard that keeps your
computer free of junk files and to set up Installation Monitor so that it either
does or does not run in the background as you work.
TIP: If the Guardian icon does not appear in the taskbar, start Guardian
Ð
by clicking McAfee Guardian from the UnInstaller menu in the
Windows Start menu Program s list.
10 McAfee UnInstaller
Page 21
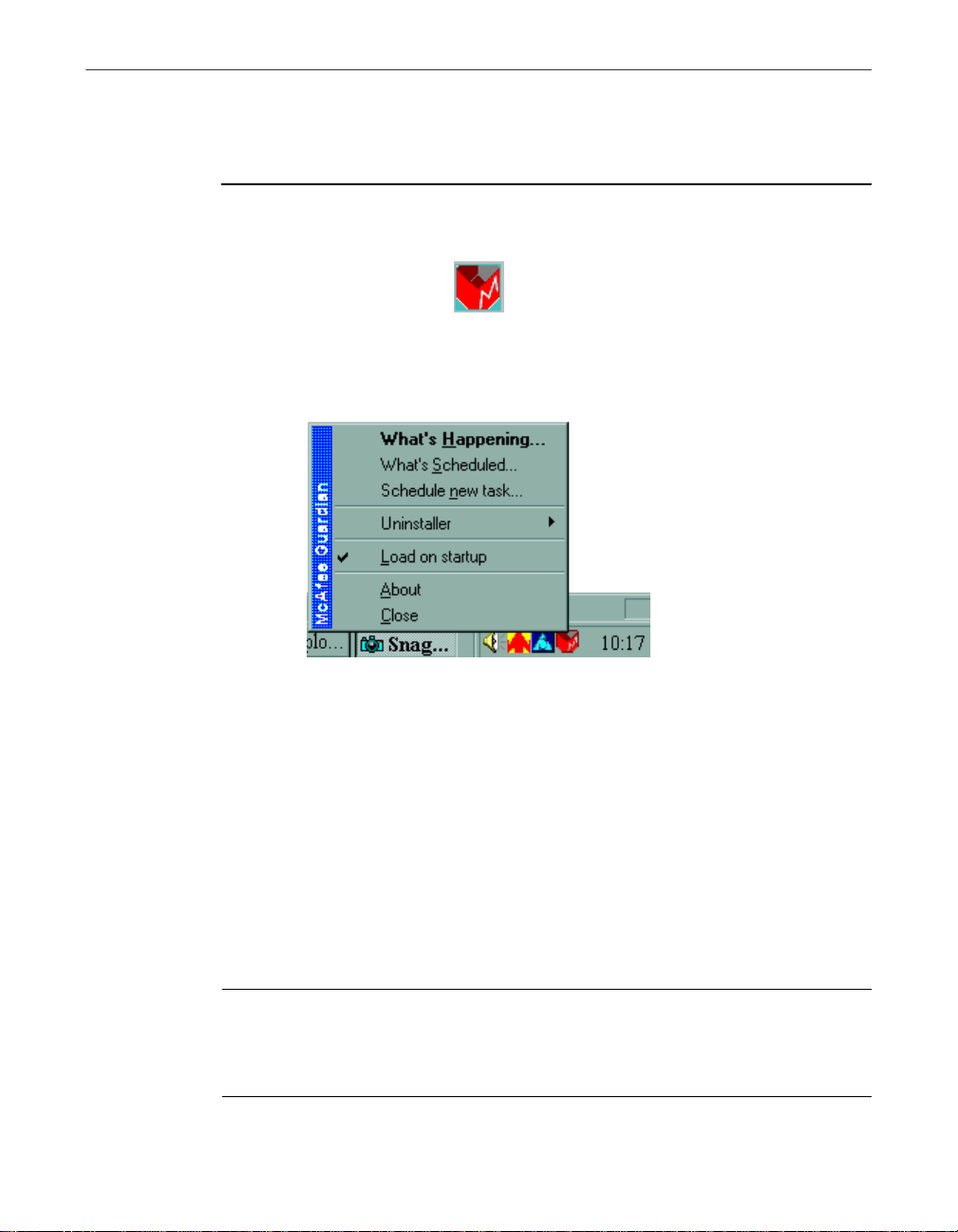
Installing UnInstaller
McAfee Guardian is the program that all McAfee Software applications use to
manage scheduled and as-you-work events.
To schedule an UnInst aller ev ent:
1. Right-click the Guardian icon in the clock area of the Windows taskbar,
and choose What’s Scheduled from the popup menu.
Figure 2-3. Scheduling events
The What’s Scheduled dialog box appears.
2. Select QuickClean or Installation Monitor from the list of scheduled
events in the Events window and click Schedule to open the Event
Schedule dialog box. The default scheduled events are:
• Qclean.exe
• Rebuild the Smartlinks Data base
• Run Installation Monito r in the Background
3. Choose the time or interval when you want the event to run, or choose
Never to turn off an as-you-work or scheduled event.
TIP: If you are running UnInstaller, you can schedule events selecting
Ð
Settings on the Options menu on the main UnInstaller screen and
choosing QuickClean. For more informa tion about scheduling, click
Help.
User’s Guide 11
Page 22

Installing UnInstaller
12 McAfee UnInstaller
Page 23

3Freeing Disk Space
3
Windows applications and the Internet can clutter your hard disk with large
unused files that take up disk space. Set up and schedule the automatic
QuickClean wizard to clean up these files at specified intervals, or use the
SpaceMaker wizard to clean up more kinds of files.
How do I keep my computer free o f unnecessary files?
Use the QuickClean wizard to perform any of the following actions to keep
your computer free of unused files and invalid shortcuts:
• Remove unused files in the cache folder of your Internet browser.
• Remove any temporary files in folders that are used by applications and
Windows.
• Clean up shortcuts, Registry entries, and remove references in operating
system files that are not connected to an y application.
• Empty the Recycle Bin.
When you click QuickClean in the UnInstaller window, the QuickClean
wizard appears. You select the kind of cleaner action you want it to perform
and then click Next to run the cleanup.
You can also schedule QuickClean to run automatically, as described in the
following section.
To remove more files of different kinds and free a specific amount of disk
space, use the SpaceMaker wizard, which is described in “How do I free a
specific amount of disk space on a drive?,” on page 15.
How do I set up QuickClean to run automatically?
You can run QuickClean whenever you need it, or you can set up QuickClean
to get rid of unnecessary files and junk on your computer at regular intervals
while you work.
User’s Guide 13
Page 24

Freeing Disk Space
To set up QuickC lean:
1. Click Settings on the Options menu in the main UnInstaller window and select the QuickCle an tab.
Figure 3-1. Setting QuickClean options
Make sure that the QuickClean options are set the way you want them.
The defaults in the QuickClean page of the Options dialog box specify
what kind of files and settings can be removed. You can also click
Schedule to specify the schedule for running QuickClean automatically.
2. Click QuickClean in the main UnInstaller window and run the wizard
manually once to see the default settings in action.
How do I schedule QuickClean to run at a specific time?
Events for McAfee applications are managed by the McAfee Guardian. Each
McAfee application adds to the list of events that the Gua rdian can run at a
scheduled time.
14 McAfee UnInstaller
Page 25

Freeing Disk Space
To change the QuickCl ean sched ule:
1. Right-click the red and white McAfee Guardian icon in the clock area of
the taskbar, and then select What’s Scheduled on the menu.
2. In the What’s Scheduled dialog box, select QuickClean and click
Schedule.
3. In the Event Schedule dialog box, choose the time interval for
QuickClean to run from the dropdown list box.
How do I free a specific amount of disk space on a drive?
If you need a specific amount of disk space on one of your drives, click
SpaceMaker in the UnInstaller screen and tell the SpaceMaker wizard how
much space you want, what kind of files it can delete, and whether you want
it to make compressed backup copies of the files. Then let it free space for you.
NOTE: By default, files are backed up before they are deleted. The
compressed backup uses less disk space than the deleted files, and gives
you a chance to recover deleted files later. Each time you run the
SpaceMaker wizard, you can turn off backups or specify a different
location for the backups.
Choose the SpaceMaker wizard to:
• Quickly create free space on one of your drives.
You can specify the drive and the amount of space you want to free. As
soon as SpaceMaker frees the specified amount of space, it stops deleting
files. If you choose to free as much space as possible, the wizard continues
to delete files until it can find no more files that are old enough to delete in
the categories you have chosen.
• Delete files from more categories than QuickClean.
SpaceMaker lets you delete files that some users might need, such as
bitmap and multimedia files, backup files that have the .BAK extension,
temporary files that Windows or Windows applications generate, screen
savers, online help files, and so on.
No file is deleted if it has been modified or accessed within the period
specified by the SpaceMaker page of the Settings dialog box. The default
period is 180 days.
User’s Guide 15
Page 26

Freeing Disk Space
How do I change defaults for SpaceMaker?
The preset SpaceMaker defaults are shown in Figure 3-2.
Figure 3-2. Setting SpaceMaker options
To view or change SpaceMaker defaults, click Settings from the Options
menu, and click the SpaceMaker tab in the Settings dialog box.
Each time you run SpaceMaker you can change most defaults temporarily.
The one default that you cannot change when the wizard is running is the age
that files must be before they can be deleted.
16 McAfee UnInstaller
Page 27

4Managing Applications
The UnInstaller wizards that manage applications are simple and extremely
safe. They will not damage your computer or destroy data by removing
important operating system files or files required by any application except
the one you are removing, archiving, or moving.
To use an UnInstaller wizard you must have enough free disk space on your
computer for the wizard to work in and enough space to store any backup
copies of files or applications that the wizard may make. Even though a
backup is compressed to its smallest pos sible size, it will take up some space
on your hard drive.
When you click one of the application management wizard buttons—Remove,
Archive, Move, or Transport—the wizard opens and guides you through three
or four quick steps to perform the action.
NOTE: By default, applications are backed up before they are deleted.
The compressed backup uses less disk space than the deleted application
files, and gives you a chance to recover the application or some of its files
later. Each time you run the Remove wizard, you can turn off backups or
specify a different location where the backups are stored.
4
In the first screen of the Remove, Archive, Move, and Transport wizards, you
choose an application by expan d ing the list of applications with shortcuts o n
your desktop, or in the Windows Start menu, as shown in Figure 4-1.
User’s Guide 17
Page 28

Managing Applications
Ð TIP: If any associated files are open when you move, tra nsport, remove,
or archive an application, UnInstaller asks you to reboot your computer
so that it can run Application Cleanup to close and back up those files
gracefully.
Figure 4-1. Choosing an application to remove
If the application does not appear in these list s, click Browse to find
application programs, which have the extension .EXE, and choose the one you
want.
How do I get rid of an ap plication?
The Remove wizard gets rid of all traces of the application, including shortcuts
and Registry entries. If the application has associated data f iles, you can
remove those at the same time if you want to. If UnInstaller detects that an
application has an uninstall program of its own, you will be given the choice
to use the application’s uninstall program or the UnInstaller Remove wizard.
To start the Remove wizard, click Remove in the UnInstaller window.
18 McAfee UnInstaller
Page 29

Managing Applications
Choose the Remove wizard to completely remove:
• An application that you no longer use.
As you buy new programs, old programs become obsolete or no longer
useful. The Remove wizard keeps your computer up-to-date by deleting all
old applications and cleaning up the Registry and operating system
settings associated with them.
• A demo application that you downloaded and decided not to purchase.
Demo applications usually cannot be used after a specified date, but they
still remain on your disk, taking up space. Use the Remove wizard to clean
them up.
• An application that you want to reinstall because it is behaving incorrectly.
Sometimes reinstalling a program from scratch fixes minor problems. The
Remove wizard can uninstall the program and remove all references to it
in the Registry and operating system files so that you can perform a clean
reinstallation.
WARNING: Make sure that you let the Remove wizard create a backup
+
copy of the application before it is removed. Then you can restore it if you
change your mind in a few minutes or a few days later. When you are
sure that you do not need the backup, delete it to free disk space, as
described in“How do I get rid of backup copies I no longer want?,” on
page 30
How do I make a copy of an appl ication to rebuild on another computer?
Use the Transport wizard to package an entire application and its
configuration settings so that you can rebuild the application with exactly the
same option settings on a different computer. To start the Transport wizard,
click Transport in the UnInstaller window.
You can also include associated data files in the Transport package. For
example, if you are transporting your spreadsheet program from your work
computer to your laptop computer, you can include the spreadsheets that you
have created.
To recreate the application, run the package file from the new computer, as
described in the next section, “How do I rebuild a transported application on
another computer?”
User’s Guide 19
Page 30

Managing Applications
+ WARNING: Make sure that the application license permits you to run a
copy of the application on more than one computer. Some application
licences now permit you to use a single copy of the application on more
than one computer as long as only one computer is in use at a time.
Choose the Transport wizard to:
• Create a copy of an application on a different computer.
The Transport wizard creates a compressed file that contains an entire
application, including its option and Registry setting information. You can
use this file to rebuild an application with the same settings on your office
and laptop computers.
• Move an application to a new computer.
Avoid time-consuming application setup when you buy a new computer.
Use the Transport wizard to reinstall your old applications with the same
option settings.
How do I rebuild a transported application on another computer?
An application that you package w ith the Transport wizard can be rebuilt on
another computer that can access the disk or the network where you stored the
Transport package file, and that is running Windows 95 or later. Simply
double-click the name of the Transport package file in a Windows Explorer file
list, and follow instructions that appear on the screen.
You do not need to have UnInstaller installed on the machine where you
reinstall the transported application. You do need to make sure that the
application license agreement permits you to use the application on more than
one computer.
A package file created by the Transport wizard contains:
• The applica t io n itself.
• Registry entries that store application default settings, and other
information needed to set up the application exactly as it was on the
original computer.
• The part of the Transport wizard that rebuilds the application.
• Any data files, spreadsheets, document files, and so forth, that you have
chosen to include.
20 McAfee UnInstaller
Page 31

Managing Applications
To rebuild a transported application on a new computer:
1. If you created the Transport package on a removable disk, insert the disk
that contains the package file.
If you created the Transport package on a network drive, make sure that
the computer where you want to build the transported application is
connected to the networ k drive.
2. In the Windows Explorer, click the letter of the drive that contains the Transport package file.
3. Double-click the name of the packa ge file in the Explorer file list. The Transport wizard opens.
4. Follow the wiz ard instructions to build the application on the new computer.
How do I archive an application so I can use it again later?
Use the Archive wizard to create a compressed backup copy, called an archive ,
of an application and remove it from your computer until you need it again.
To start the Archive wizard, click Archive in the UnInstaller window.
To free the most hard-disk space, store the archive on a removable disk, such
as a Zip
compressed files reduce the amount of space the application takes up.
After the Archive wizard creates the compressed archive file, it removes the
application from the folder where it was installed, but leaves the shortcuts to
the application in place. When you click a sho r tcut to the application in the
Windows Start menu Programs list, or on your Windows desktop, taskbar, or
elsewhere, a message box appears, explaining that UnInstaller has archived
the application and asking if you would like to restore it.
Choose the Archive wizard if you:
• Want to store useful applications that you rarely use.
®
disk. But even if you store the archive on your hard drive, its
NOTE: You can also use the Restore wizard to restore archived
applications.
User’s Guide 21
Page 32

Managing Applications
If you have old games or specialized programs, archive them to free disk
space, but keep the shortcuts and other entry points available from your
desktop.UnInstaller keeps track of applications that you have archived.
Their shortcuts and Start menu Programs list entries remain in place. If you
click a shortcut or Programs list entry for an archived application, you can
choose whether to restore the application.
• Think you might need an application again.
If you are not sure that you want to get rid of an application entirely,
instead of using the Remove wizard and creating a backup file, use the
Archive wizard and retain information.
• Want to free space on your computer by removing an application
temporarily.
If you need disk space to perform a task that requires a large amount of
temporary space, for example, you can archive applications to free the
space. Then you can quickly restore the applications when you no longer
need their disk space.
How do I move an application from one location to another?
Use the Move wizard to copy an application to a ne w location , either on your
local computer or to another computer, and remove the application from its
old location. To start the Move wizard, click Move in the UnInstaller window.
After the application is moved, the wizard changes all shortcuts and Registry
entries to refer to it in its new location.
Choose the Move wizard to move an application:
• From a crowded hard disk to a new, second hard disk with more space.
If you have installed a second hard disk, relocate some applications from
your primary hard disk to create more space there.
• From your local computer to a drive on another computer.
If you have more than one computer at your disposal, you can manage how
you use the available disk space by moving applications between hard
drives.
• From one folder to another.
22 McAfee UnInstaller
Page 33

You can reorganize application folders on your computer by combining
applications in subfolders of a single folder. For example, if you have
several Adobe applications, you might move them into individual
subfolders in a main Adobe folder.
Moving an application does not change its position in the Windows Start
menu Programs list.
How can I monitor installation?
The UnInstaller BackTrack wizard can restore your system to the state it was
in before you installed a monitored application.
You can use the UnInstaller Installation Monitor to watch applications as they
install making a record of every file that was added, deleted, or changed
during installation. Then, you can use the BackTrack wizard to completely
remove the monitored application from your computer and return all settings
to their previous values before the application was installed. You can set up
Installation Monitor in one of two ways:
• Set up BackTrack Monitor to run in the background continuously, waiting
for you to run an installation file with a specific name or from a specific
folder, or to install an application from a self-expanding compressed file
with the .EXE extension.
Managing Applications
• Start BackTrack Monitor just before you install an application, and specify
the program that runs the application installation, as d escribed in “How do
I monitor installation of a single applicatio n?,” on page 25.
How do I set BackTrack Monitor to run in the background?
To keep BackTrack M onitor act ive whi le yo u work on yo ur co mputer:
1. Click Settings on the Options menu in the main UnInstaller screen.
User’s Guide 23
Page 34

Managing Applications
2. Click the BackTrack button, and specify what you want to monitor.
Figure 4-2. Setting BackTrack Monitor options
To run Installation Monitor automatically in the background while you
work, you must select either or both of the options on the BackTrack
page. When BackTrack Monitor detects an installation program, it
displays a message box where you can choose whether to monitor the
installation.
TIP: Many installation programs start automatically as soon as you insert
Ð
a CD disc into your CD drive. To make sure that installations fro m CDs
are monitored, open the Settings dialog box and set BackTrack to monitor
setup files before you insert the CD disc into the drive.
How do I monitor installation of a single application?
If you’d prefer to run BackTrack Monitor only when you are actually installing
applications, follow these steps:
24 McAfee UnInstaller
Page 35

Managing Applications
1. In the Windows taskbar, right-click the Guardian icon, point to
UnInstaller, and click Launch Installation Monitor. (By default, the icon
is located in the lower-right corner of your screen near the clock.)
2. In the dialog box that appears, click Browse to find and select the
installation program that y ou want to monitor.
Installation programs are usually named Setup.exe, CDsetup.exe, and so
on.
3. Click Monitor to start installing the application.
Before installation actually starts, BackTrac k Monitor saves Registry
settings and other information on your computer so that its original state
can be restored later if you choose to remove the application from your
computer.
How do I undo an application installation that I monitored?
Use the UnInstaller BackTrack wizard to undo the installation of an
application that was tracked by BackTrac k Monitor.
WARNING: You cannot use the BackTrack wizard to undo the
+
installation of an application that BackTrack Monitor did not monitor. In this
situation, use the Remove wizard.
To undo an applic atio n ins tallati on:
1. Click BackT rack in the main UnInstaller screen to start the BackTrack
wizard.
2. In the first BackTrack wizard screen, click Next.
3. Select the BackTrack archive from the list and click Next again.
The BackTrack wizard processes the archive to determine what it needs
to undo. At this point if you’re interested, you can click Details to see
what BackTrack will do to individual files, and when you’re fi nished
reviewing this information, click OK to return to the BackTrack wizard
screen.
WARNING: Do not change the sele ction of any of the files. Let
+
BackTrack use its judgment to decide which files you still need and
which files should be removed or replaced.
4. Click Next.
User’s Guide 25
Page 36

Managing Applications
5. Click Close to return to the main UnInstaller screen.
The BackTrack wizard removes the application and returns Registry
settings to the values that were in effect before the application was
installed. The wizard displays a message telling you when it successfully
completes the job.
26 McAfee UnInstaller
Page 37

5Restoring Information
Restoring applications and files
Removed applications and files that have been backed up by UnInstaller can
be restored by the Restore wizard. The Restore wizard also restores archived
applications.
The Restore wizard does restore:
• Archived applicat ions.
• Removed applications that the Remove wizard backed up.
• Files that were removed by the SpaceMaker or Remove wizards, or that
you deleted using the PowerClean feature, if backup copies were made.
The Restore wizard does not restore:
• Move wizard actions.
• Installation of an application that was tracked by Installation Monitor.
• Transported applications.
5
• Files and Registry settings removed by QuickClean.
How do I restore an archived or backed-u p application?
The Restore wizard can completely restore any application if you have
archived it or let the Remove wizard make a backup copy of the application
before you removed it. The backup copy or the archive must still be available.
To restore an appl ication :
1. Click Restore in the UnInstaller main window.
2. On the Restore wizard screen, click the arrow by the dropdown list and
select the backup or archive folder (Figure 5-1).
• If you do not see the archive you are looking for, you might have
stored it in a different folder. Click Browse to find archives or
backups in other folders. When you select a folder, the archives or
backups that it contains appear in the Restore wizard list.
User’s Guide 27
Page 38

Restoring Information
• The information in the Restore wizard list includes the name of the
backup or archive file, such as “Archive of Glaxian,” the name of the
wizard that created the backup, and the date the backup was
created.
Figure 5-1. Selecting an application to restore
3. Select an archive or backup f r om the Restore wizard list and click Next.
4. On the second wizard screen, the names of all files that will be restored
5. In the second wizard screen, you can select files to restore, and click Next.
6. In the third Restore wizard screen you can choose:
28 McAfee UnInstaller
are displayed.
WARNING: Do not deselect any files if you are restoring an entire
+
application. If you deselect files, critical application files may not be
restored and the application may not run correctly, or at all.
• How to replace files in restoration folders. You can choose to:
Only replace older files with newer files.
Page 39

Always replace existing files.
Never replace existing files.
The default is “Only replace older files with newer files”.
• Whether to confirm restoring each file.
If you choose to confirm files as they are restored, you must click
OK for each file in a message box. To restore remaining files without
confirming them, you can click Yes to All at any time.
7. Click Restore to begin restoring the application.
When the wizard restores the application, it displays a message that the
job is completed. You can click Report to view details of restoration
activity.
How do I restore delet ed files?
The Restore wizard can also restore individual files that the SpaceMaker
wizard has deleted, or that you have deleted using the PowerClean feature, if
UnInstaller made backup copies of the files.
Restoring Information
To restore individ ual fi les:
1. Click Restore in the main UnInstaller window.
2. On the Restore wizard screen, click the arrow by the dropdown list and
select the backup or archive folder (Figure 5-1).
To see a list of the files contained in the backup or archive, click Next.
3. Select the files you want to restore from the list that appears in the next
wizard screen; then click Next.
4. In next wizard screen, you can choose:
• How to replace files in restoration folders. You can choose to:
Only replace older files with newer files.
Always replace existing files.
Never replace existing files.
The default is “Only replace older files with newer files”.
• Whether to confirm replacing each file.
User’s Guide 29
Page 40

Restoring Information
If you choose to confirm files as they are replaced, you must click
OK for each file in a message box. To restore remaining files without
confirming them, you can click Yes to All at any time.
5. Click Restore to begin restoring the files.
When the wizard restores the file, it displays a message that the job is
completed. You can click Report to view details of restoration activity.
How do I get rid of backup copies I no longer want?
UnInstaller backs up deleted files and applications so that you can restore
them if you change your mind later.
Backup files, which are compressed files containing copies of all deleted files,
are stored on your computer in a location you can specify in the General page
of the Settings dialog box or in other locations that you can specify when you
run one of the UnInstaller wizards.
But note that although backup copies are compressed, eventually they will
take up a lot of disk space. When you are sure that you will no longer want or
need a backup of a deleted application or group of files, delete the backup file.
To delete a backup fil e:
1. Select the backup file in the first Restore wizard page list.
2. Click Report and select the Report Log tab to see a list of files contained
in the backup. Click Close to return to the first Restore wizard page.
3. If you are sure that you will not need any of these files, click Delete. You are prompted to confirm deleting the file.
How do I see what UnInstaller has done?
The Reports dialog box displays numeric and graphic information about
actions performed in the PowerClean feature and by UnInstaller wizards.
When you first open the Reports dialog box, you see summary information
from the Master Log in all pages. To see information about a specific action,
click Open. Then choose the action from the list that appears, and click OK.
The information that appears depends on whether you are viewing Master
Log totals, or have chosen a specific action report.
30 McAfee UnInstaller
Page 41

Restoring Information
Action report logs display a complete list of files that were deleted or modified
by each individual action. These reports can be useful in tracking down old
versions of files that were deleted but backed up, or were archived.
Figure 5-2. The Report Summary
• Report Summary tab
This page shows numeric data about the total number of files affected, the
total size of files moved, compressed, or deleted, the disk-space savings,
and so on. The pie chart on the right shows the percent of disk space
regained by the selected action if you are viewing a specific action report,
or by all UnInstaller actions, if you are viewing Master Log information.
• Report Log tab
This page lists all changes made by the individual wizards or in the
PowerClean feature if you are viewing a specific action report.
If you are viewing Master Log information, you see a list of available action
reports. Click Open to chose an action report to view.
• Disk Analysis and File Analysis tabs
User’s Guide 31
Page 42

Restoring Information
If you only want to see what UnIns taller has done, you can review the list of
actions displayed in the Reports window. However, if you want to keep a
record of UnInstaller actions for later reference, you can print the report
information or save it as a file.
The Disk Analysis page displays the percent of total disk space regained by
deleting, moving, or archiving files in each file category. The File Analysis
displays the total number of files in each category.
32 McAfee UnInstaller
Page 43

6Using PowerClean
6
If you are an experienced computer user, you can use the PowerClean feature
for custom file and Registry manag e ment.
Using the PowerClean feature you can view, move, copy, delete, and archive
files from the UnInstaller default categories, which are usefully organized into
groups of duplicate files, non-critical files, disconnected shortcuts, and so on.
In addition, you can create custom file groups of your own to make it easier to
manage specific kinds of files in specific locations.
NOTE: To protect you against deleting files unintentionally, and remind
you that you use PowerClean at your own risk, the PowerClean feature
opens in read-only mode. To turn off read-only mode, clear the check
next to Read-only mode in the PowerClean page of the Settings dialog
box.
What can I do when I u se the PowerClean feature?
The PowerClean feature provides manual file man ag e ment and Registry
management for experienced computer users.
Use the PowerClean feature to perform these file-management tasks:
• Delete, archive, move, rename, or copy selected files or defined groups of
files.
You can perform the same actions on individual files or groups of files that
the UnInstaller wizards perform on entire applications.
• Find out what application uses a selected file.
Right-click File Links from the popup menu to see what application uses a
selected file. If the selected file is an executable file, such as a .DLL or .EXE
file, the File Links dialog box displays a list of the files that are used by the
executable file itself.
• Create custom file groups that contain only files that you specify.
Set up custom file groups to archive or delete files from specified folders on
your computer. For information about creating custom file groups, see
“How can I create a custom group?,” on page 37.
• Add programs and files to the Start menu.
User’s Guide 33
Page 44

Using PowerClean
When you install applications or executable files, you can often choose not
to add them to the Programs list. These application f iles appear in the
Disconnected Executables file group list.
To add an executable file to the Windows Programs list, select the file name
in the PowerClean list. Then click Connect to Start menu on the Tools
menu and specify where you want to add the file in the Programs list.
Why does the PowerClean feature open in read-only mode?
When you click PowerClean in the UnInstaller main window, the PowerClean
feature opens in read-only mode.
You see a message box explaining that you cannot delete an y files. This feature
protects you from deleting files or making other changes unintentionally.
Even in read-only mode, however, you can use the PowerClean feature to:
• Explore the file links and Registry entries on your computer.
This is a good way to learn how yo ur computer works and what files it
uses.
You can select a file, and then choose File Links from the popup menu to
see what application uses the selected file.
• Create a custom file group.
Although you cannot delete, move, copy, or archive any files in read-only
mode, you can still define a custom file group to manage specific files
quickly. Creating custom file groups is described on pa ge 36.
When you want to use PowerClean to manage files, clear the check next to
Read-only mode on the PowerClean page of the Settings dialog box. Open the
Settings dialog box by clicking Settings from the Options menu.
34 McAfee UnInstaller
Page 45

Using PowerClean
How do I work with th e PowerClean feature?
The PowerClean feature opens in a dialog box that works like the Windows
Explorer. Like the Explorer window, it has a menu bar, a status bar, and a
toolbar that you can customize. Each pane also has a shortcut menu that pops
up when you right-click an item in the Cleanup Types or file list pane. The file
list shortcut menu is shown in Figure 6-1.
Figure 6-1. The PowerClean shortcut menu
The left pane displays an expandable list of default file groups. Click the + next
to the group name to expand the group list. For information about the default
groups, see “What are the default file groups?,” on page 36. For information
about creating a new file group, see “How can I create a custom group?,” on
page 37.
The right pane displays the names of files in the selected default group. Files
are color-coded to indicate how important they are to your computer and its
applications. For information about the color codes, see “What do the color
codes mean?,” on page 41.
User’s Guide 35
Page 46

Using PowerClean
What are the default file groups?
In PowerClean, files on your computer are grouped into category lists that
make it easy to ma nage fi les of cert ain type s on all dr ives and folders. You can
add your own file groups, as described in “How can I create a custom group?,”
on page 37.
When you start using PowerClean, the major file groups appear in the tree list
in the dialog box. Click the plus sign (+) next to a file group to display
subgroups and files.
NOTE: For more information about the default groups, click Help. Then
click the What files are in the default file gro ups? topic in the What do
you want to know about PowerClean? section.
The major file groups are described briefly in the following table. A
description of the selected group or subgroup appears in the Advice tab pane.
Note that some files appear in more than one group. For example, the
Non-Critical Files group contains an Archive subgroup which contains the
same files as the Internet Stuff group Archive subgroup
Table 6-1. The PowerClean default file groups
Category Description
Non-Critical Files Files that can be deleted without causing your
computer to crash or fail to operate correctly.
Note, however, that this group includes several
subgroups that contain files such as backup files with
the .BAK extension, and archive files, including all files
with the .ZIP extension, as well as bitmap files (.BMP)
and other image and multimedia files.
Internet Stuff Files downloaded from the Internet with an archive
extension, such as .A RC, .CA B, a nd .ZIP, a s we ll as fil e s
that your Internet browser caches for future use,
including .GIF and .JPG files.
The Internet Documents category includes all .HTM
and .HTML files found on your computer. If you are
developing Web-based information, these files should
not be removed without careful examination.
36 McAfee UnInstaller
Page 47

Using PowerClean
Table 6-1. The PowerClean default file groups (Continued)
Category Description
Duplicates Duplicated files on your computer. By default,
duplicate files must have the same file name, size, and
date.
To define duplicate files simply as files that have the
same file name, or the same file name and date, change
the option setting in the Advanced page of the Options
dialog box.
Disconnected Items Two kinds of files are included in this group:
Files that are assoc iat e d wit h ap plic a tions that are no
longer on your computer.
Programs that are not on the Start menu Programs list
or on the Windows desktop.
Files that are asso c iated with programs you have
removed can safely be deleted. Progr ams that are not on
the Start menu list, however, might be valid programs
that you decided not to include on the Programs list, or
executable files that are used only by other applications.
Windows Shell Items All items on the Start menu Programs list or the
Windows desktop.
Windows Registry Important Registry entries for applications.
Registered File Types Files in each file-type categor y that is associated with an
application.
Custom File Groups This group contains file groups that you name and
define. For information about creating your own file
groups, see the following section.
How can I create a custom group?
Custom file groups make it easy for you to manage collections of files that you
define. After you create a custom file group, you can easily change its
definition to find a different set of files, or to find files in a different location.
To create a custom fil e grou p:
1. Click Create Custom Group on the Tools menu. The Custom Group
dialog box appears.
2. Enter a name for the new group.
User’s Guide 37
Page 48

Using PowerClean
3. Specify the files that the group should include. You can enter complete
file names, or file names that contain wildcard characters, such as * and ?.
To enter more than one file name, separate the names with semicolons (;).
For example, to find graphics files with specific extensions, you might
enter
*.bmp;*.tif;*.jpg
or to find spreadsheet files for January and February, you might enter
jan*.xls;feb*.xls
4. Enter the top level of the path to search for files.
For example, you might enter:
C:\My Documents
Click Browse to select a path instead of typing a path name.
• To search subfolders of the paths you enter, select the Search
Subfolders check box.
5. Click OK to save the new group.
To change the definition of a custom file group:
1. Select the file group in the Cleanup Types list.
2. Click Edit File Group from the Tools menu. The Custom Group dialog
box appears.
3. Change the information in the dialog box. You can change any
information that appears, including the nam e of the custo m group.
4. Click OK to save the changes.
What commands are on the PowerClean menus?
All of the shortcut menu commands shown in Figure 6-1 on page 35, and
other, less often used commands, are available from the menus in the menu
bar.
38 McAfee UnInstaller
Page 49

Using PowerClean
The menu bar categories and the commands that they contain are listed in
Table 6-2 .
Table 6-2. PowerClean menu commands
This menu... Contains these commands...
File All of the file management commands
on the popup menu as well as Print List,
View Report, and Exit.
Edit Select all, Invert Selection, and Undo.
Tools Archive, Connect to Start Menu, Find
Target, Refresh SmartLinks Database,
Refresh Internet Folders, Create Custom
Group, Edit Custom Group, Delete
Custom Group
View List, Details, Arrange Icons
Options Settings, Customize Toolbar, Toolbar,
Cleanup Tabs, Status Bar, Save
Preferences on Exit, Save Preferences
Now
NOTE: For more information about the menu commands, click Help and
click What do the PowerClean menu commands do? in the What do you
want to know about PowerClean? section.
User’s Guide 39
Page 50

Using PowerClean
How do I use the tab panes?
The tab panes below the group and file lists display information, either about
the selected file or about the actions that you have performed during this
PowerClean session.
Table 6-3. Information in the PowerClean tab panes
Click this
tab...
Advice Information about the selected default group of files,
Report The list of files you have backed up and deleted in the
Viewer The contents of the selected file, if your computer has a
To see...
including suggestions about what you should or should
not do.
If you select a custom group that you created yourself,
the defining characteristics of the group are displayed,
such as
Search for *.xls
Search in C:\MyFiles
Search subfolders: TRUE
current PowerClean session.
For a full list of Event Logs, click V iew Report on the
File menu.
viewer that can display files of this type. You can view
most graphics and icon files, word processing and
spreadsheet files, and other common file types.
You can also view technical information about
executable files.
To remove the tab panes from the PowerClean dialog box window, clear the
check next to Cleanup Tabs on the Options menu.
What do the color codes mean?
The colored icon next to each file name in the PowerClean d ialog box indicates
the how important the file is to the operating system or to an installed
application.
40 McAfee UnInstaller
Page 51

Using PowerClean
In some cases, the color code is determined by your default settings. For
example, if you specify that files of a specific type in a specific location should
never be deleted, those files are marked with a red circle.
Table 6-4. Descriptions of PowerClean color codes
Code Description
Red circle with a
diagonal line across it
Red circle Critical files used by applications, and files th at ar e
Yellow square Important files.
Green triangle Files that are not important to the operating system
Files marked with this code are necessary for your
computer to run correctly.
You cannot delete these files from the PowerClean
dialog box.
not old enough to be deleted.
The original default is set to prevent you from
deleting these files. We strongly recommend that
you keep this default setting. Files used by
applications should never be deleted.
To change the age files must reach before they can
be deleted, change the accessed and/or modified
age specified in the Settings dialog box.
These files might be used by applications on your
computer. They might also be linked to
applications on a removable disk that is not
currently available.
Read information in the Advice tab before you
delete these files and ma ke su re that deleting them
will not cause operating system or application
problems.
or applications.
They might be very important to you, however.
Make sure that you know what they are used for
before you delete them, and create backups in case
you need them again.
How do I change the defaults for the PowerClean feature?
If you have started the PowerClean feature and are working in the
PowerClean dialog box, click Settings on the Options menu. The Settings
dialog box opens with the PowerClean page open.
User’s Guide 41
Page 52

Using PowerClean
If you have started UnInstaller, but are not are not working with the
PowerClean feature, click Options in the main UnInstaller window, then click
Settings in the menu that appears. When the Settings dialog box opens, click
the PowerClean tab.
Figure 6-2. Setting PowerClean options
The original default settings are shown in Figure 6-2. These settings:
• Turn on read-only mode.
• Specify that files must be 180 days old to be deleted.
• Create backups of all deleted files.
• Prevent you from deleting files marked by a red circle as well as files
• Set the strictest criteria for duplicate files.
You can also specify the folder where you intentionally download files from
the Internet, if you have such a folder on your computer. If you are using one
of the most common Internet browsers, such as AOL, Internet Explorer, or
Netscape Navigator, UnInstaller automatically finds the folder where the
browser caches files that it downloads as you open a page on the Internet.
42 McAfee UnInstaller
marked by a red circle with a diagonal line across it.
Page 53

If you are using an unusual browser, click Cache Folders... to specify the folder
where cached files are stored.
NOTE: For more information about the setting PowerClean opti ons,
click Help and click How do I set options? in the What do you want to
know about PowerClean? section.
How can I see what I have don e using th e PowerClean feature?
The Report tab contains information only about actions that you’ve taken
during the current PowerClean session.
For detailed information about all actions you have performed using the
PowerClean feature, including use of the Undo command, click View Report
on the File menu.
The Reports dialog box appears. Choose events to view as described in “ How
do I see what UnInstaller has done?,” on page 31.
Using PowerClean
User’s Guide 43
Page 54

Using PowerClean
44 McAfee UnInstaller
Page 55

AAbout Windows 98
Windows 98 Applications and Files
This appendix provides background information for computer users who a re
curious about how Windows 98 applications keep track of information, and
how computer files are named and used.
You don’t need to know the information in this appendix to use UnInstaller
wizards, but if you are an inexperienced computer user, read ing this appendix
might give you the information you need to use the advanced features of the
UnInstaller PowerClean feature.
How does an application keep track of its configuration settings?
In Windows 3.1 and earlier, applications usually stored option setting s in text
files called .INI files.
Primarily for backward compatibility and other historical reasons, some
applications still store information in .INI files. You can see the list of all .INI
files on your computer if you open the Windows folder in the Windows
Explorer, and click the Type column header in the file list pane. Then look for
files with the .INI file name extension.
A
NOTE: If you do not see file name extensions, see “How can I see
extensions in the Windows Explorer file list?,” on page 47 to find out how
to set up the Explorer to display extensions. If you do not know what file
name extensions are, see “What are file name extensions?,” on page 47.
One advantage of storing options in .INI text files is that it is easy for anyone
to open the file in Notepad or another text editor, and view or change the
settings. But this advantage can be a disadvantage if users make changes
incorrectly. Furthermore, the .INI files have size and other constraints, lack a
standard for organization and change, and are often left behind when you use
the Windows Add/Remove Programs to get rid of an application.
For these reasons and others, in Windows 98 and Windows NT 4.0 and later,
Windows and applications store option settin gs in the Windows system
Registry.
User’s Guide 45
Page 56

About Windows 98
What is the Windows Registry?
The Registry is a database that stores system and applica tion configuration
information. The database file format protects system and application
information from uninformed tampering, and ensures that information is
stored according to specific and well-defined standards so that it can be
accessed reliably by applications.
Registry data is stored in a file called System.dat. It can be viewed or edited by
the Registry editor, which is called Regedit.exe. The Registry editor is not
meant for casual use. You can seriously damage your computer system if you
edit the Registry. To examine important Registry entries safely, use the
UnInstaller PowerClean feature.
Some applications, especially older applications, do not remove all of their
entries from the Registry when you use Windows Add/Remove Programs to
get rid of an them.
UnInstaller cleans up the Registry and gets rid of unconnected .INI files either
when you use the Remove wizard to uninstall an application, or when you run
the QuickClean wizard to get rid of junk files and unconnected Registry
entries.
How are computer files named?
All of the files on your computer have names that the operating system uses to
keep track of them.
In DOS and Windows 3.1 and earlier, all file names have to meet the
eight-dot-three file-name convention. This convention specifies that the first
part of the file name can have as many as eight characters. These characters are
followed by a dot, or period. Then the seco nd part of the file nam e, which can
have as many as three characters, follows the dot. For example, a file might be
called Mydoc.txt, but it could not be called Mydocument.txtfile.
In Windows 98 and Windows NT, files can have much longer names, names
that describe them better so that you can see immediately what the file
contains or does. You can name a file Gas Mileage.xls, or Acme Computer
Let.doc.
Occasionally, however, you might have an application that does not use the
long file names. Then you will see a truncated version of the long file name,
such as Gasmil~1.xls. If you ha ve many such applications, you might still
prefer to use the eight-dot-three convention for file names.
46 McAfee UnInstaller
Page 57

About Windows 98
What are file name extensions?
The last three characters of a file name, the characters that follow the dot, are
called the file name extension, or extension.
Extensions can have more than three characters, but th ey usually have three or
fewer characters because most current applications have historically used
three characters to identify different kinds of files.
The extension is used by Windows to identify the application that opens or
runs the file by default, as described in “What is an associated file?”
How can I see extensions in the Windows Explorer file list?
By default, you do not see the file name extension in the Windows Explorer file
list.
To turn on displa y of ext ension s in old er versi ons of Windows:
1. In the Windows Explorer window, click any folder name.
2. In the View menu at the top of the Explorer window, click Options.
3. Clear the check next to Hide MS-DOS file extensions fo r file types t hat
are registered.
4. Click Apply.
5. Click Like Current Folder to make all folders display file names with
extensions.
6. Close the dialog box by clicking Cancel or OK.
If you have installed I nternet Ex plorer 4.0 in Win dows, f ollow these steps:
1. In the Windows Explorer window, click any folder name.
2. In the View menu at the top of the Explorer window, click Folder
Options, then click the View tab in the dialog box that appears.
3. In the Advanced Settings list in the View page, clear the check next to
Hide file extensions for known file types to make the folder display
files names with their extensions.
4. Click Apply.
5. Click Like Current Folder to make all folders display file names with
extensions.
User’s Guide 47
Page 58

About Windows 98
6. Close the dialog box by clicking Cancel or OK.
What is an associated file?
An associated file is a file whose extension is registered as belonging to a
specific application. These files are opened or run automatically by that
application when you double-click the file name in the Windows Explorer file
list.
For example, a file with the extension .TXT will open in Notepad, even if the
contents of the file is not readable by a text editor. The file name extension is
the only way Windows can tell wha t application should open a file.
If you double-click a file name that has an extension that is not registered for
any application, a dialog box appears asking what application you want to use
to open the file.
You can choose an application from the list in the dialog box or click Other to
find an application that you think might be able to read the file. To register the
extension permanently to the application you choose, make sure that the
Always use this program to open this file option is checked.
An application can have more than one associated extension. For example,
Microsoft Word has associated several extensions, including .DOC, . DOT,
.WBK, and .RTF.
What are some common associated extensions?
In addition to .TXT, which is associated with Notepad, there are many other
extensions associated with applications. To see a list of these applications and
associated files, click the Registered Files group in the UnInstaller
PowerClean dialog box. Using the PowerClean feature is described in “How
do I work with the PowerClean feature?,” on page 35.
48 McAfee UnInstaller
Page 59

About Windows 98
An application always has the .EXE extension. Table A-1 lists the extensions of
files you might download from the Internet.
Table A-1. Extensions of files commonly downloaded from the Internet
This extension... Indicates this kind of file...
ARC, .ARJ, .CAB,
.GZ, .LZH, .TAR,
.TAZ, .TGZ, .Z, .ZIP,
and .ZOO
.HTM or .HTML Internet files. They will be
.MPG, .AVI, .FLC,
and .MOV
.JPG and .GIF Graphics files that are usually
What are junk files?
Junk files are files that you did not create on purpose, but that accumulate on
your computer as you use applications, and, particularly, as you browse the
Internet.
Applications often create temporary files as you work, either to store
intermediate versions of files that you are creating, or to keep track of status
changes. If the application exits unexpectedly, it cannot remove these files in
the usual way, although they are not used the next time you start the
application. The files stay on your disk and take up disk space.
Compressed archive files
created by different
compression programs.
opened by your default
browser.
Multimedia files. They can be
opened by a multimed ia p lay e r.
opened by your Internet
browser.
If all temporary files were stored in the same folder with the document files,
you might be able to find them and delete them yourself, but these files are
often stored in the Windows temporary folder, or in application-specific
temporary folders.
TIP: To make sure that you have deleted all unusable temporary files,
Ð
schedule UnInstaller’s QuickClean wizard to run regularly, as described
in “How do I s chedule Q uickCl ean to r un at a spe cific t ime?,” o n page 15.
User’s Guide 49
Page 60

About Windows 98
The more serious source of junk files is the Internet. When you open a page on
an Internet site, all of the files that are used by that page are downloaded to
your computer and stored in the Internet browser’s cache folder. The browser
stores these files in case you return to the same page, so that it can display the
graphics and text immediately instead of downloading them again.
Nevertheless, unless you return often to an Internet page that uses these files,
the cached files are not very useful, and they can take up a lot of disk space.
Graphics files in particular take up a lot of disk space. After you have been
browsing the Internet for a while, you might have several megabytes of disk
space used just by cached files.
These files can be deleted without damaging your system, or even making
your Internet connection run more slowly.
Schedule UnInstaller’s QuickClean wizard to get rid of these junk files
regularly, as described in “How do I schedule QuickClean to run at a specific
time?,” on page 15.
What are Internet cookies and how are they used?
A cookie is a small file that contains information. The information in the cookie
varies, depending on its purpose. One thing a cookie does not contain is a
program that can be executed on your computer.
For example, when you use an Internet site to buy computer equipment, you
may add items to a “shopping basket.” Information about the items you add
to the shopping basket is stored in a cookie on your computer because the
Internet browser cannot retain information that you entered in one Internet
page when you switch to another Internet page. The cookie saves information
about your purchases and allows the site to create a final order form for you.
Another example is the cookie that an electronic version of a newspaper stores
on your computer to keep an encrypted copy of your user n ame and password
so that you do not need to enter this informa tion each time you con nect to the
site.
The newspaper probably also uses the cookie information to record each time
you connect to the site, what pages you use, and whether you click an y of the
advertiser’s banners. Reputable sites provide privacy information to tell you
how the information that is gathered is used.
These examples of cookies are clearly useful to you, at least in some way.
However, other sites might download cookies just to collect information about
your Internet use. These cookies are clearly not useful to you at all.
50 McAfee UnInstaller
Page 61

To block cookies selectively, so that only cookies you want use Guard Dog. To
delete old cookies, open UnInstaller’s PowerClean feature and click Cookies
in the Internet Files group.
What are compressed files?
Compressed files are files that have been recoded to remove extra space and
use less disk space than the expanded, usable version of the file. You cannot
use a compressed file until you expand it to its origin al f ormat.
Files that contain text can often be compressed to less than half of their
uncompressed size.
You can also create a compressed file archive by compressing more than one
individual file into a single compressed file container. UnInstaller uses this
method of storing backup copies of files deleted by SpaceMaker and using the
PowerClean feature.
You use the same program to expand a compressed file as you used to
compress the file. There are many file compression programs available. One of
the best known compression programs for Windows is WinZip
program that is available from the Internet.
About Windows 98
®
, a shareware
What is an autoexpanding compressed file?
An autoexpanding compressed file immediately expands all of the files that it
contains when you double-click the file name. The extension of an
autoexpanding compressed file is .EXE, just like the extension of an
application. These files are also called self-extracting compressed files.
When you cre ate a com pressed f ile arch ive, you can make it an autoex panding
file. The file compression program adds executable code to the compressed
archive file, and this code is run to expand all of the files contained in the
archive.
The disadvantage of using an autoexpanding compressed file is that you
cannot select the files to be expanded, or the folders to which they are
expanded. The advantage of an autoexpanding compressed file is that you do
not need to have the file compression program on the computer where the files
are expanded.
Application installation programs that you download from the Internet are
usually autoexpanding comp ressed files.
User’s Guide 51
Page 62

About Windows 98
52 McAfee UnInstaller
Page 63

BProduct Support
BEFORE YOU CONTACT McAfee Software for technical support, locate
yourself near the computer with McAfee UnInstaller installed and verify the
information listed below:
• Have you sent in your product registration card?
• Version of McAfee UnInstaller
• Customer number if registered
• Model name of hard disk (internal or external)
• Version of system software
• Amount of memory (RAM)
• Extra cards, boards or monitors
• Name and version of conflicting software
• EXACT error message as on screen
• What steps were performed prior to receiving error message?
B
• A complete description of problem
How to Contact McAfee
Customer service
To order products or obtain product information, contact the McAfee
Customer Care department at (408) 988-3832 or write to the following address:
McAfee Software
3965 Freedom Circle
Santa Clara, CA 95054
U.S.A.
You can also order products online at http://store.mcafee.com
User’s Guide 53
Page 64

Product Support
If you need further assistance or have specific questions about our products,
send your questions via email to the appropriate address below:
• For general questions about ordering software: mcafeestore@beyond.com
• For help in downloading software: mcafeedownloadhelp@beyond.com
• For a status on an existing order: mcafeeorderstatus@beyond.com
To inquire about a promotion: mcafeepromotions@beyond.com
Technical support
Support via the web
McAfee is famous for its dedication to customer satisfaction. We have
continued this tradition by making our site on the World Wide Web
(http://www.mcafee.com) a valuable resource for answers to technical
support issues.
We encourage you to make this your first stop for answers to frequently asked
questions, for updates to McAfee software, an d for access to McAfee news an d
virus information.
Take advantage of the McAfee Product KnowledgeCenter—your free online
product support center - 24 hours a day, 7 days a week
(http://support.mcafee.com/tech_supp/pkc.asp).
Support forums and telephone contact
If you do not find what you need or do not have web access, try one of our
automated services.
Table B-1.
World Wide Web www.mcafee.com
CompuServe GO MCAFEE
America Online keyword MCAFEE
Microsoft Network mcafee
54 McAfee UnInstaller
Page 65

If the automated services do not have the answers you need, please contact
McAfee at the following numbers Monday through Friday between 9:00 AM
and 6:00 PM Pacific time for 30-day free support, and 24 hours a day - 7 days
a week for Per Minute or Per Incident support.
30-Day Free Telephone Support 972-855-7044
Per Minute Telephone Support 1-900-225-5624
Per Incident Telephone Support ($35) 1-800-950-1165
McAfee training
For information about scheduling on-site training for any McAfee product,
call (800) 338-8754.
Disclaimer: Time and telephone numbers are subject to change without prior
notice.
Product Support
Table B-1.
User’s Guide 55
Page 66

Product Support
56 McAfee UnInstaller
Page 67

Index
A
applications
archiving
monitoring installation of
moving to new location
rebuildi ng transporte d
removing
transporting
Archive wizard
described
restoring archived applications
when to use
autoexpanding compressed files, described
21
23
22
21
18
19
21
27
21
B
BackTrack
how to use
setting defaults for
See also Installation Monitor.
backup and archive files
specifying default location for
23 to 25
10
10
custom file gr o u p s, in PowerClean feat ure
dialog box
36
D
database, SmartLinks described 4
defaults
how set
list of Settings dialog box page s
See also Settings dialog box.
deleted files, restoring
disk space
freeing
51
DOS file names, described
8 to 10
29
13
46
E
extensions
associating files with applications
displaying in Windows Explorer file list
47
file name defined
of files from Internet
47
49
10
48
C
color codes, in PowerClean feature dialog box
40
compressed files
autoexpanding, described
described
cookies
defined
deleting old
how used by Internet
51
50
51
51
50
F
features
listed and described
1
User’s Guide 57
Page 68

Index
file groups, in PowerClean feature dialog box
36 to 37
45
files
associated, defined
48
autoexpanding compressed files
described
compressed, described
cookies, deleting
deleting manually
deleting unused by using wizards
51
51
51
33
13
displaying extensions in Explorer file list
47
extensions described
junk files described
naming conventions for
removing junk files
removing to free disk space
47
49
46
13
16
G
Guardian
how to start
scheduling QuickClean
Guardiant
scheduling an event with
11
15
11
M
McAfee Guardian. SeeGuardian.
monitored installation, undoing
25
Move wizard
described
when to use
22
22
O
options, setting. See Settings dialog box.
P
PowerClean feature dialog box
cache folders, when to specify
color codes, interpreting
custom file gr o u p
changing definition
creating
36
file groups described
original default settings listed
read-only mode, turning off
setting defaults for
tab panes, using
40
40
38
36 to 37
34
10
43
42
I
.INI files, how used 45
installation
of UnInstaller
requirements
Installation Monitor
monitoring a specific installation
running while you work
See also BackTrack.
Internet
cookies, how used
extensions of files downloaded
junk files downloaded
3
3
50
50
49
24
Q
QuickClean wizard
how to use
scheduling
setting defaults for
13
14
14
R
read-only mode, turning off for PowerClean
feature dialog box
rebuilding transported applications
Registry, described
remove Installation Monitored application
Remove wizard
described
when to use
34
20
46
25
18
19
User’s Guide 58
Page 69

Index
Reports dialog box
described
tab pages described
viewing event details
30
31
30
Restore wizard
described
restoring archived applications
restoring deleted files
27
27
29
restoring
deleted application
deleted files
29
transported applications
27
20
undoing a monitored application
installation
25
S
scheduling
events run by Guardian
QuickClean to run automatically
self-extracting compressed files, described
Settings dialog box
BackTrack (Installation Monitor) options
24
BackTrack options
Folders page
10
General page described
PowerClean options
QuickClean options
setting defaults in
SpaceMaker options
SmartLinks database
described
when updated
4
4
SpaceMaker wizard
setting options for
when to use
15
11
14
10
10
10, 42
10, 14
10
10, 16
10, 16
T
tab panes, in PowerClean feature dialog box 40
Transport wizard
described
19
rebuilding transported applications
when to use
20
U
undo
installation of application if monitored
25
W
Windows Registry, described 46
wizards
21 to 22
7
22
13 to 15
18 to 19
27 to 30
15 to 16
19 to 21
51
Archive
listed and described
Move
QuickClean
Remove
Restore
SpaceMaker
Transport
20
User’s Guide 59
Page 70

Index
User’s Guide 60
 Loading...
Loading...