Page 1

Supplement for Common Criteria
Operational User Guidance and Preparative
Procedures
McAfee
McAfee
®
VirusScan
®
ePolicy Orchestrat or
®
Enterprise 8.8
®
4.5 Software
Page 2

COPYRIGHT
Copyright © 2011 McAfee, Inc. All Rights Reserved.
No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language in any form or by any
means without the written permission of McAfee, Inc., or its suppliers or affiliate companies.
TRADEMARK ATTRIBUTIONS
AVERT, EPO, EPOLICY ORCHESTRATOR, FOUNDSTONE, GROUPSHIELD, INTRUSHIEL D, LINU XSHIELD, MAX (MCAFEE SECURITYALLIANCE EXCHANGE),
MCAFEE, NETSHIELD, PORTALSHIELD, PREVENTSYS, SECURITYALLIANCE, SITEADVISOR, TOTAL PROTECTION, VIRUSSCAN, WEBSHIELD are registered
trademarks or trademarks of McAfee, Inc. and/or its affiliates in the US and/or other countries. McAfee Red in connection with security is distinctive of
McAfee brand products. All other registered and unregistered trademarks herein are the sole property of their respective owners.
LICENSE INFOR M A TION
License Agreement
NOTICE TO ALL USERS: CAREFULLY READ THE APPROPRIATE LEGAL AGREEMENT CORRESPONDING TO THE LICENSE YOU PURCHASED, WHICH SETS FORTH THE GENERAL TERMS
AND CONDITIONS FOR THE USE OF THE LICENSED SOFTWARE . I F YOU DO NOT KNOW WHICH T Y PE OF LI C E NSE YOU HAVE ACQUIR ED, PLEASE CONSULT THE SALES AND OTHER
RELATED LICENSE GRANT OR PURCHASE ORDER DOCU MENTS THAT ACCOMPANY YOUR SOFTWARE PACKAGING OR THAT Y OU HAVE RECEIVED SEPARATELY AS PART OF THE
PURCHASE (AS A BOOKLET, A FILE ON THE PRODUCT CD , OR A FILE AVAIL ABLE ON THE WEBSITE FROM WHICH YOU DOWNLOADED THE SOFTWAR E PAC K AGE). IF YOU DO NOT
AGREE TO ALL OF THE TERMS SET FORTH IN THE AGREEMENT, DO NOT INSTALL THE SOFTWARE. IF APPLICABLE, YOU MAY RETURN THE PRODUCT TO MCAFEE OR THE PLACE OF
PURCHASE FOR A FULL REFUND.
Prepared For:
Prepared By:
McAfee, Inc.
2821 Mission College Blvd.
Santa Clara, CA 95054
www.mcafee.com
Apex Assurance Group, LLC
530 Lytton Avenue, Ste. 200
Palo Alto, CA 94301
www.apexassurance.com
2 Operational User Guidanc e a nd Preparative Procedures Supplement for Comm on Criteria
Page 3

Contents
1 Introduction 5
About the Common Criteria ................................................................................................. 5
Assumptions ..................................................................................................................... 6
Authorized Administrators ............................................................................................ 6
Physical Access ........................................................................................................... 6
Acronyms ......................................................................................................................... 6
2 Installation Gui delines and Preparative Proced ur e s 7
Overview .......................................................................................................................... 7
Downloading the TOE ......................................................................................................... 7
Evaluated Configuration...................................................................................................... 8
Functionality Not Included in the Evaluatio n .................................................................... 9
Verify Software ................................................................................................................. 9
Updating System Software ......................................................................................... 10
Install Database Capacity Monitor Ex te nsio n ....................................................................... 10
Step 1: Adjust or Review Database space requirements ................................................. 11
Step 2: Create a Server Task to generate the Event ...................................................... 11
Step 3: Setting up the automatic response ................................................................... 12
3 Guidance for Administrators 15
Software Version Inspection .............................................................................................. 15
Required Password Length ................................................................................................ 15
Operational User Guidance and Preparative Procedures Su pp lem e nt for Common Criteria 3
Page 4

4 Operational User Guidanc e a nd Preparative Procedures Supplement for Comm on Criteria
Page 5

1 Introduction
This guide provides operational guidance and installation procedu r e s for the VirusSca n Enterprise 8.8
and ePolicy Orchestrator 4.5.
This guide was written to provide the evidence requi r ed by the following assurance r equirements of
the Common Criteria (CC) Version 3.1, Part 3:
AGD_OPE.1
AGD_PRE.1
These assurance requirements call for documentation of installation procedures that provide assurance
that the TOE is installed and configured in the evaluated configuration.
This document serves as a supplement to the standard McAf ee doc umentation set including the
following:
McAfee VirusScan En terpr ise 8.8 Product Guide
McAfee VirusScan En terpr ise 8.8 Installation Guide
McAfee ePolicy O r c hestrator 4.5 Ins ta llation Guide
McAfee ePolicy O r c hestrator 4.5 Product Guide
These documents should be read prior t o c onfiguring the product in accordance with the Common
Criteria evaluated configuration. The documents listed above in conjunction with this s upplement
describe how to adm inister the TOE in a m an ner that meets the Common Criteria eva luated
configuration. Any changes to or deviations from the information provided in this document will re s ult
in noncomplianc e b e tween the product a nd the Common Criter ia e valuated configuration.
The audience f or this document includes administrators who are authorized to install and configu r e
TOE. Since administrators config ure the TOE and set policie s for use, there is n o s p ecific user guidanc e
documentation.
Contents
About the Common Criteria
Assumptions
Acronyms
About the Common Criteria
The Common Cr iter ia for Information T echnology Security Evaluation (or “Common Criteria”) provides
a methodology for evaluating security features of IT products. Product v e ndors pursue Comm on
Criteria evaluation to meet assurance needs of custome r s and to seek third-par ty validation of sec urity
function claims. The Target of Evaluation (TOE) en compasses the evaluate d security func tionality of a
product.
Operational User Guidanc e a nd Preparative Procedures Supplement for Comm on Criteria 5
Page 6

Introduction
Assumptions
The McAfee VirusScan En ter pr ise 8.8 and ePolicy Orchestra tor 4. 5 ( hereafter called “Target of
Evaluation” or the “TOE”) has achieved Common Criteria Evaluation Assurance Level 2 and augmented
by ALC_FLR.2 – Flaw Reporting P roc edures.
Please visit: http://www.commoncriteriaportal.org for more information on the Comm on Criteria.
Assumptions
The TOE and the TOE operating en vironment should be managed to satisfy the assumptions presented
in the following sec tions.
Authorized Administrators
Authorized administrators are non-hostile, are authenticated to the inter nal network, a nd follow all
administrator guidance. Human users (considered to be anyone who interacts with the T OE) who are
not authorized adm inistrators ca nnot access the administration feature s .
Physical Access
The TOE must be loca te d in a physically secure environment, a nd only an authorized administrator has
access to this environment. The evaluated configuration of the TOE can be compromised if an intruder
gains physical access to the product. Therefore only a uthorized administrators shall be allowed
physical access to the workstation(s) for power/reset controls.
Acronyms
The following table lists the acronyms used in this docu m ent:
Table 1 – Acronyms and Terms
Acronym Term
CC Common Criteria
EAL Evaluation Assurance Level
TOE Target of Evalu ation
TSF TOE Security F unction
6 Operational User Guidance and Prepa ra tiv e Procedures Supplement for Common Cr ite r ia
Page 7

2 Installation Guidelines and Preparative
Procedures
This section prov ides guidelines for in stalling McAfee VirusScan Enterpris e 8.8 and ePolicy Orchestrator
4.5 to meet the Common Criteria evaluated configuration . The following guidelines may augme nt the
details of or provide exceptions to the documents refer enced in the Purpos e s e c tion of this document.
Prior to installation, the administra tor should read an d be familiar with the details of all documentation
for VirusScan Enterprise 8.8 and ePolicy Orchestrator 4.5.
Contents
Overview
Downloading the TOE
Evaluated Configuration
Verify Software
Install Database Capacity Monitor Extension
Overview
Prior to installation, the administra tor should read an d be familiar with the details of all documentation
for McAfee VirusScan Enterprise 8.8 and ePolicy Orchestrator 4.5.
Downloading the TOE
The administrator s hould follow these steps to download the VirusScan TOE component:
1 Log in to the downloa d/upgrade site.
(https://secure.nai.com/us/forms/downloads/upgrades/login.asp) and enter the grant number
provided.
The My Products page appears show ing links for the products to which the customer is entitled.
For example, if th e g r a nt number includes entitlement to McA fee VirusScan Enter p r is e , there will
be an entry for the McAfee Active VirusScan.
2 Select McAfee Active VirusScan.
The list of related products a ppea r s .
3 Select VirusScan Enterprise v8.8.
The license agreement page a ppea r s .
Operational User Guidanc e a nd Preparative Procedures Supplement for Comm on Criteria 7
Page 8

Installation Guidelines and Preparative Procedures
Evaluated Configuration
4 Click I Agree.
The VirusScan Ente r p r ise download page appears.
5 On the Softwar e D ownloads tab, select VSE880LML.zip and VSE880_Client_Help.Zip.
6 Download each item.
7 On the Documentation tab, select English from the Language drop-down box.
8 Select any or all of the available VirusScan Enterprise documentation.
9 Download each item.
The administrator s hould follow these steps to download th e ePolicy Orchestrator TOE component:
1 Log in to the download/upgrade site
(https://secure.nai.com/us/forms/downloads/upgrades/login.asp
provided.
The My Products page appears.
2 Select McAfee Active VirusScan.
The list of related products a ppea r s .
) and enter the grant number
3 Select ePolicy Orchestrator v4.5.0.
The license agreement page a ppea r s .
4 Click I Agree, the ePolicy Orchestrator download p a g e a p pe a r s, containing a li st of links.
5 Click and download the ePolicy Orchestrator file (ePO450P3.Zip).
6 Click the Documentation tab.
7 Select English from the Language drop-down box, and click Go.
8 Select any or all of the available ePolicy O rchestrator documentation.
9 Download each item.
The administrator s hould follow these steps to download the Database Capacity Monitor TOE
component:
1 Log in to the McAfee Service Portal site (https://mysupport.mcafee.com/Eservice/Default.aspx
2 Select Download Software Updat es.
3 Click on Download E P olicy Orchestrator 4.5 Database C a pacity Monitor.
4 Follow the instructions in the Insta ll D a tabase Capacity Monitor Extension s ection of this
document.
).
Evaluated Configuration
The evaluated configuration in c ludes one or more instances of McAfee Agent and McAfee VirusScan
Enterprise and an instance of McAfee ePolicy Orchestrator. Note that for the evaluated configuration,
all user accounts defined in McAfee ePO must specify Windows authentica ltion (rather than McAfee
ePO authentication).
8 Operational User Guidance and Preparative Procedures Su pp lem e nt for Common Criteria
Page 9

Installation Guidelines and Preparative Procedures
Verify Software
The evaluated configur a tio n includes one or more instances of McAfee Agent and VirusScan Enterpr ise
and an instance of McAfee ePO. The following configuration should apply to the evaluated
configuration:
1 All user accounts defined in McAfee ePO must specify W indows authentication.
2 McAfee Agent should only be installed by using the McAfee ePO in ter face.
3 Remote viewing of T O E log files on the clients is disabled.
4 Only authoriz ed pr ocesses may initiate n e twork connections to remote port 25 (SMTP). The
Central Adminis tr a tor configures th e lis t of authorized processes.
5 The U.S. Government Protection P r ofile Anti-Virus Ap plic ations for Works tations in Basic
Robustness Environments requires the TOE to restrict s pecific management functionality to the
Central Adminis tr a tor role. At least on e e PO user must be defined as a Central Administra tor. For
this TOE, the Central Administrator role is defined as a n authorized admin istrator with Global
Administrator s ta tus.
6 Because the
Robustness Environments requires the TOE to restrict sp ec ific management f unctionality to the
Central Adminis tr a tor role, the following permissions may never be assigned:
a View audit log.
b View and purge audit log.
c View VSE settings.
d View and change VirusScan Enterprise settings.
U.S. Government P r otection Profile Anti-Virus Applications for Workstations in Basic
Functionality Not Included in the Evaluation
The following functionality is not in cluded in the evaluation:
The ability to protect against buf fer overflows
The ability to identify spyware
The Scriptscan feature that scans JavaScript and VBScript scripts
The ability to updat e the TOE (scan engine). Note that the ability to update the virus
signatures (DAT file) is included in the evaluation.
The optional Aler t Manager product
Verify Software
The administrator s hould follow one of the following points to ensure the proper version of software is
installed:
The administrator c an view McAfee ePO versioning information on the title bar/tab header
when logged into ePolicy O r chestrator:
Operational User Guidanc e a nd Preparative Procedures Supplement for Comm on Criteria 9
Page 10
Installation Guidelines and Preparative Procedures
Install Database Capacity Monitor Extension
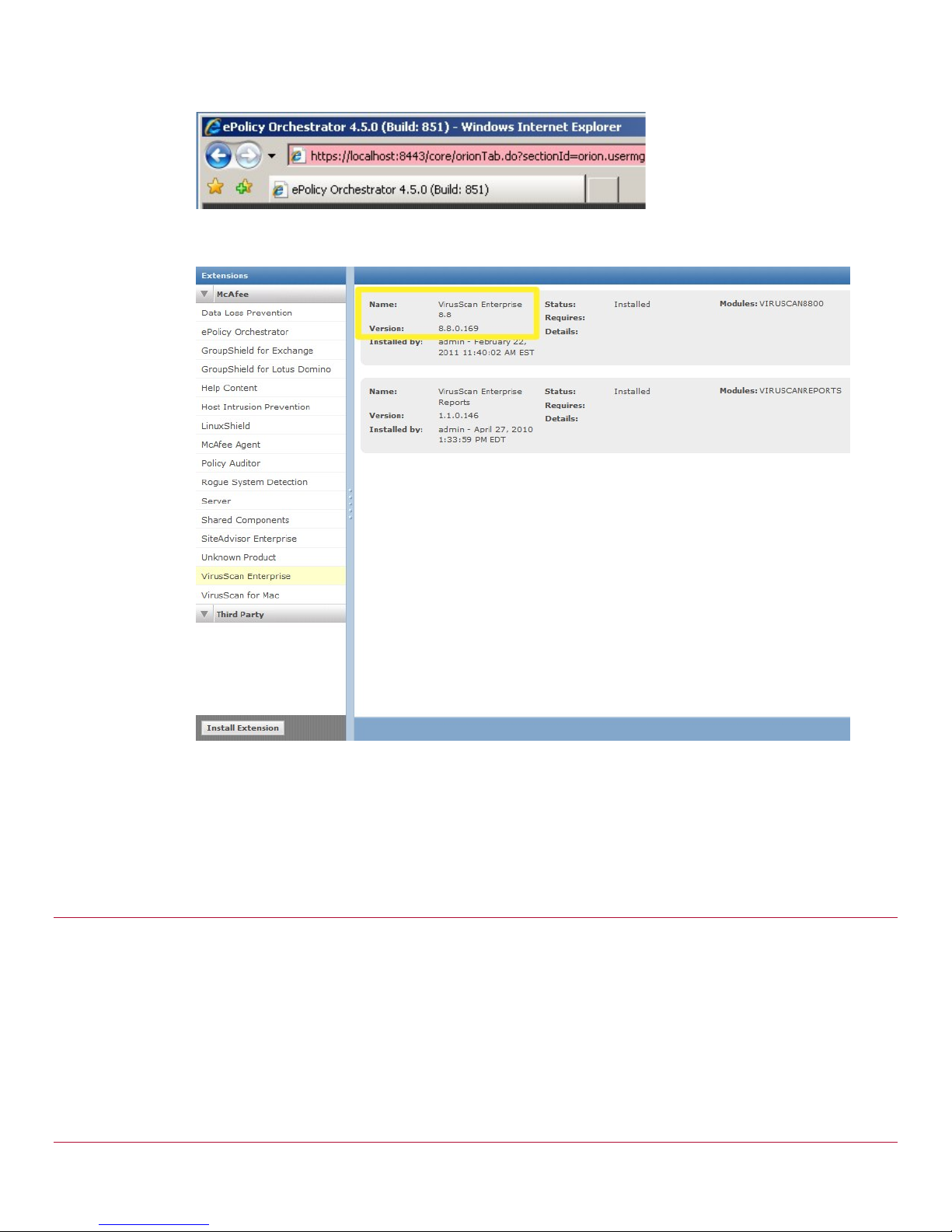
The administrator c an view VirusScan Enterprise versioning information via Menu / Software /
Extensions / VirusScan Enterprise when logged into ePolic y Orchestrator
Updating System Software
If the TOE is not ru nning the evaluated version of softwar e, the administrator should contact McAfee
to obtain the appropriate license/ gr ant for the evaluated s oftware version.
Install Database Capacity Monitor Extension
The purpose of th e feature is to enable the use of automatic responses to alert t he administrator of
the exhaustion of storage spa c e being used by the SQL database. To fac ilitate events, a new project
has been created that allows the user to configure alert settings. This project is being released by w a y
of an extension and can be insta lled by th e end user.
To install the Databa se Capacity Mon itor Extension, foll ow the instructions below:
1 Download the Databa se Capacity Mon itor Extension (DBCapMon.zip) from McAfee Service Portal.
2 As a Global Admin, select Software / Extensions from the main menu.
10 Operational User Guidan c e a nd Preparative Procedures Supplement for Comm on Criteria
Page 11
Installation Guidelines and Preparative Procedures
Install Database Capacity Monitor Ex te nsio n
3 Select Install Extension.
4 Follow the prompts to install the down loa ded extension.
5 Once installed, v e r ify that the version matches below:
Creating and generating responses for Database is a three-part sequence. These steps requ ire
adjusting or reviewing database limi ts, setting up a serv er task and finally c r e a ting an Automatic
Response.
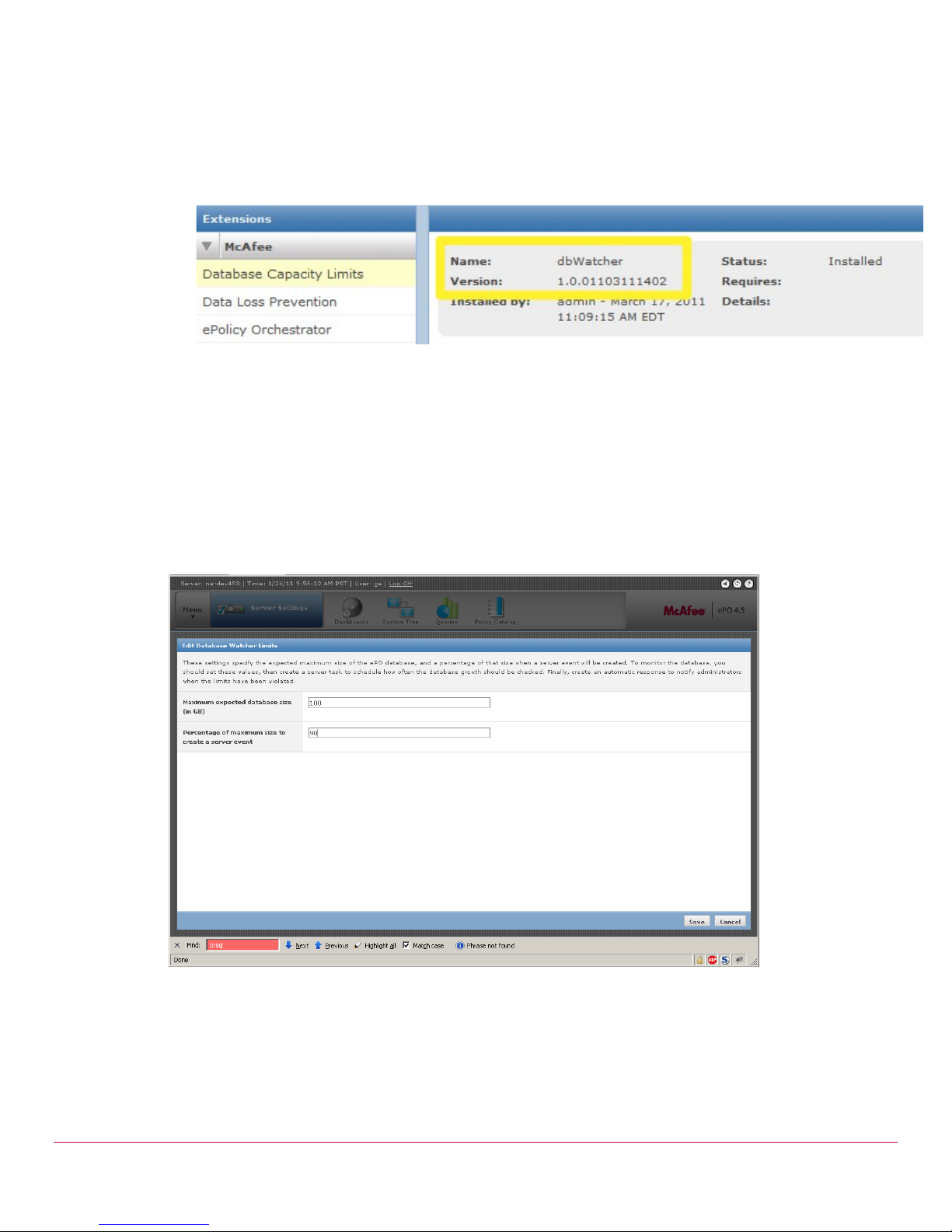
Step 1: Adjust or Review Database space requirements
The user can create a query for systems with less than, for example, 10GB free of system drive space.
The user can cr eate a server task to mail th e r e s ults of this query to a designated recip ient. From the
server configu r ation, select the “ D a ta b a se watcher limits” c ategory. Clicking edit will that use to
specify the maximum ex pected databa se and the percentage at which a server event will be triggered.
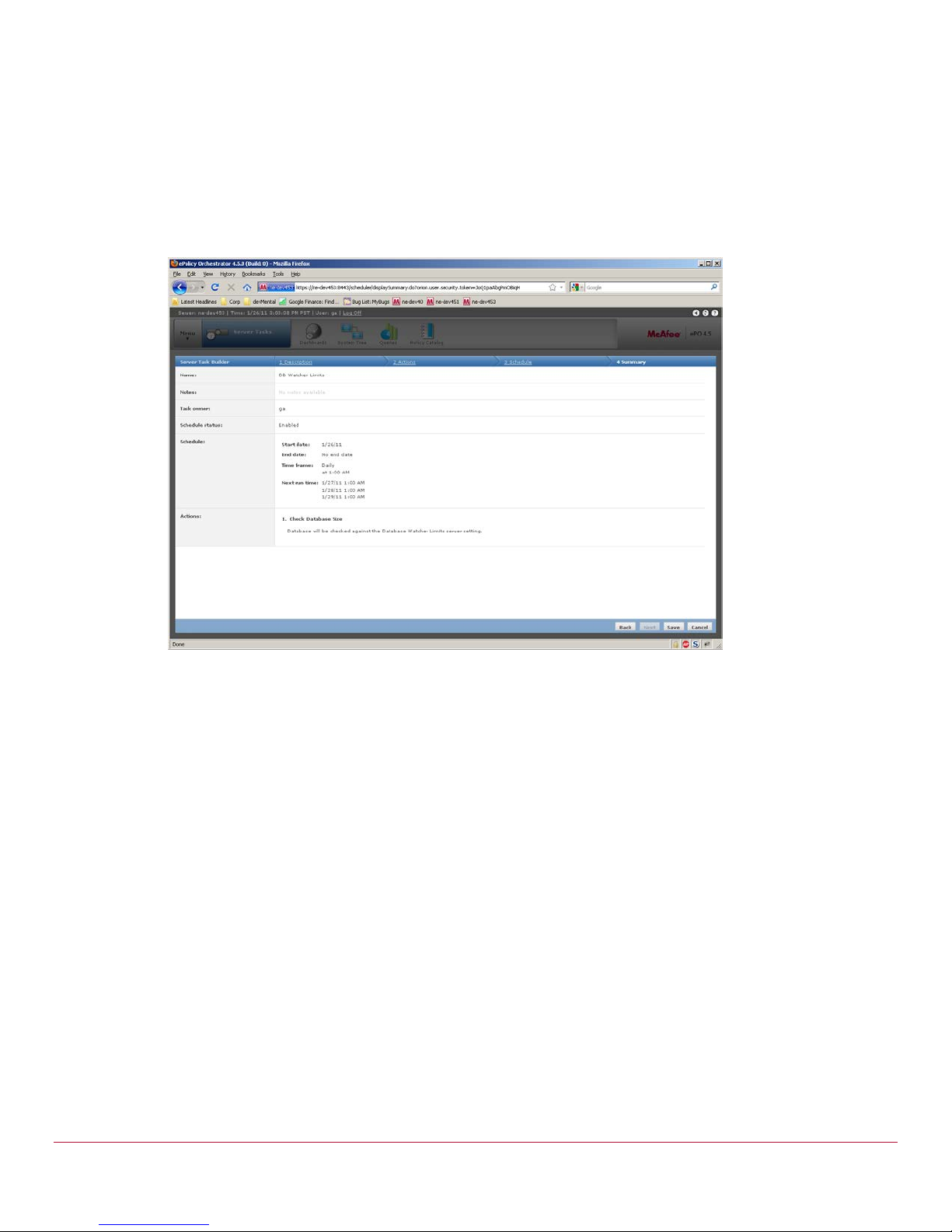
Step 2: Create a Server Task to generate the Event
To use the limits specified a user must create a server task to run the “Check Database Size” action
and set a schedu le a t which the limits will be que ried.
1 New Server Task:
Operational User Guidance and Preparative Procedures Supplement for C om m on Criteria 11
Page 12
Installation Guidelines and Preparative Procedures
Install Database Capacity Monitor Ex te nsio n
a Provide name and Enable the tas k.
b Select the “Check Database Size” action.
c Provide schedule settings.
d Review and save the server task.
This server task creates entries in the EPOServerEvents table u s ing the event id of ‘16081’ and
contains information pertaining to the audit log entry a nd server informa tion. The presence of the
event id in this table r ep resents the limits have been met base d on the criteria set in the configuration
screen. This p r oc e s s does not generate the ale rts and commun ic ation; this will be v ia a n automatic
response.
Step 3: Setting up the automatic response
1 Select the ePO Notification group, a nd specify “server” fr om the event type.
12 Operational User Guidan c e a nd Preparative Procedures Supplement for Comm on Criteria
Page 13

Installation Guidelines and Preparative Procedures
Install Database Capacity Monitor Ex te nsio n
2 Add the Event ID as a filter and specify ‘16081’ as the value:
On the Aggregation ta b of the Automatic Resp onse builder screen, it should be noted that
throttling shou ld b e used in order to not ov er load an overload s ystem.
From the Actions screen the user can specify the appropriate response; in this case a server issue
is being created and assigned to the globa l administrator.
Operational User Guidanc e a nd Preparative Procedures Supplement for Comm on Criteria 13
Page 14

Installation Guidelines and Preparative Procedures
Install Database Capacity Monitor Ex te nsio n
3 Review settings and save th e a utomatic response settings.
14 Operational User Guidance and Preparative Procedu r es Supplement for Common Criteria
Page 15
3 Guidance for Administrators
The Common Criteria evalua ted c onfiguration is designed to be as flex ible as possible in a deployment
scenario. As s uch, the ongoing guidan ce for administra tor s is largely covered in the McAfee VirusS c an
Enterprise 8.8 software Product Gu id e. Administrators should read and configu r e th e s oftware
according to the guidelines in ava ila b le documentation and according to their site-specific security
policies. Following those guidelines a nd those mentioned below will ensure that the TOE is
administered in a mann er th at complies with the Common Criteria evaluation.
Contents
Software Version Inspection
Required Password Length
Software Version Inspection
The administrator s hould periodically verify that the evaluated version of software is run ning.
Required Password Length
When adding other administrator accou nts to the TOE, the a dministrator should choose strong
passwords by adhering to the following r ules:
Use long passwords (8 characters or longer).
Do not use somethin g found in a dictionar y (in any language or j a rgon).
Do not use a name (including that of a spouse, parent, child, pet, fantasy character, famous
person, and location) or any varia tion of the account name or administrator identity.
Do not use accessible information (such as phone numbers, license plates, or social security
numbers).
Do not use a birthday or a simple number pa ttern.
Use a mixture of upper and lower case lette r s , as well as digits or punctuation. When choosing
a new password, make sure it is un rela ted to any previous password.
Note that the administrator should also follow these r ules when maintain ing his/her own passw ord.
Operational User Guidanc e a nd Preparative Procedures Supplement for Comm on Criteria 15
 Loading...
Loading...