Page 1

NS7x00 Quick Start Guide
Revision D
McAfee Network Security Platform
This quick start guide explains how to quickly set up and activate your McAfee® Network Security Platform NS7100,
NS7200, and NS7300 Sensors in in-line mode. These models have a throughput of 1.5 Gbps, 3 Gpbs, and 5 Gbps
respectively.
All product documentation referenced in this quick start guide is found on the McAfee ServicePortal.
The NS7100/NS7200/NS7300 Sensor model
Figure 1 Sensor front panel
Console port (1)
1
RJ-11 port (1) for fail-open control of two built-in SFP+ ports in slot G0. The RJ-11 port supports 1 Gbps (SFP)
2
copper or
SFP+ 1/10 Gigabit Ethernet ports (2)
3
Two slots for I/O modules (Any combination of the interface modules can be used.)
4
• SFP/SFP+ 1/10 GigE Monitoring ports (8)
• RJ-45 10/100/1000 Mbps with internal fail-open Ethernet Monitoring ports (6)
• 10/1 GigE SM 8.5 micron with internal fail-open Monitoring ports (4)
• 10/1 GigE MM 50 micron with internal fail-open Monitoring ports (4)
• 10/1 GigE MM 62.5 micron with internal fail-open Monitoring ports (4)
RJ-45 10/100/1000 Mbps Ethernet Monitoring ports (8)
5
ber and 10 Gbps (SFP+) (SR and LR).
The RJ-11 port controls only the SFP+ 1/10 port pair in passive fail-open mode.
1
Page 2

The supported transceiver modules are SFP+ (M2M and SM), SFP Fiber (MM and SM) and SFP Copper.
Figure 2 Sensor rear panel
Auxiliary port (1)
1
USB ports (2)
2
Power supply inlet (2)
3
The NS7x00 Sensors are shipped with one power supply unit. Second power supply (optional) is
supported to enable redundancy.
RJ-45 10/100/1000 Response port (R1) (1)
4
RJ-45 10/100/1000 Management port (Mgmt) (1)
5
1 Verify the contents in the box
The following accessories are shipped in the NS7x00 Sensor crate:
• Sensor
• Power cords (McAfee provides standard and international power cables.)
• Set of rack mounting rails
• Printed Quick Start Guide
2 Verify the hardware and software requirements
Make sure to meet the following hardware requirements. For more information, see the McAfee Network
Security Platform Installation Guide.
The following are the system requirements for a Manager server.
2
Page 3

Minimum required Recommended
Operating
system
Any of the following Microsoft operating systems:
• Windows Server 2008 R2 Standard or Enterprise Edition, SP1
(Full Installation), English operating system
• Windows Server 2008 R2 Standard or Enterprise Edition, SP1
(Full Installation), Japanese operating system
• Windows Server 2012 Standard Edition (Server with a GUI)
English operating system
• Windows Server 2012 Standard Edition (Server with a GUI)
Japanese operating system
• Windows Server 2012 R2 Standard Edition (Server with a GUI)
English operating system
• Windows Server 2012 R2 Standard Edition (Server with a GUI)
Japanese operating system
• Windows Server 2012 R2 Datacenter Edition (Server with a
GUI) English operating system
• Windows Server 2012 R2 Datacenter Edition (Server with a
GUI) Japanese operating system
Only X64 architecture is supported.
Same as the minimum
required.
Memory 8 GB 8 GB or more
CPU Server model processor such as Intel Xeon Same
Disk space 100 GB 300 GB or more
Network 100 Mbps card 1000 Mbps card
Monitor 32-bit color, 1440 x 900 display setting 1440 x 900 (or higher)
The following are the system requirements for client systems connecting to the Manager application.
Minimum Recommended
Operating
system
• Windows 7 English or Japanese
• Windows 8 English or Japanese
• Windows 8.1 English or Japanese
The display language of the Manager client must be
same as that of the Manager server operating
system.
RAM 2 GB 4 GB
3
Page 4
Minimum Recommended
CPU 1.5 GHz processor 1.5 GHz or faster
Browser
• Microsoft Internet Explorer 9, 10, or 11
• Mozilla Firefox
• Google Chrome (App mode in Windows 8 is not
supported.)
• Internet Explorer 11
• Mozilla Firefox 20.0 or
later
• Google Chrome 24.0 or
later
If you are using Google Chrome, add the Manager
certicate to the trusted certicate list.
Install the following software:
• Sensor image
• Manager image
• Signature set
3 Install the slide rails and rack-mount the Sensor
McAfee recommends rack-mounting your Sensor. For maintenance purposes, you must have access to the
front and rear of the Sensor.
Before you mount the Sensor on the rack, make sure that the power is o. Remove the power cable
and all network interface cables from the Sensor.
Due to the weight of the appliance, McAfee recommends that two people place the chassis into the
rail cabinet.
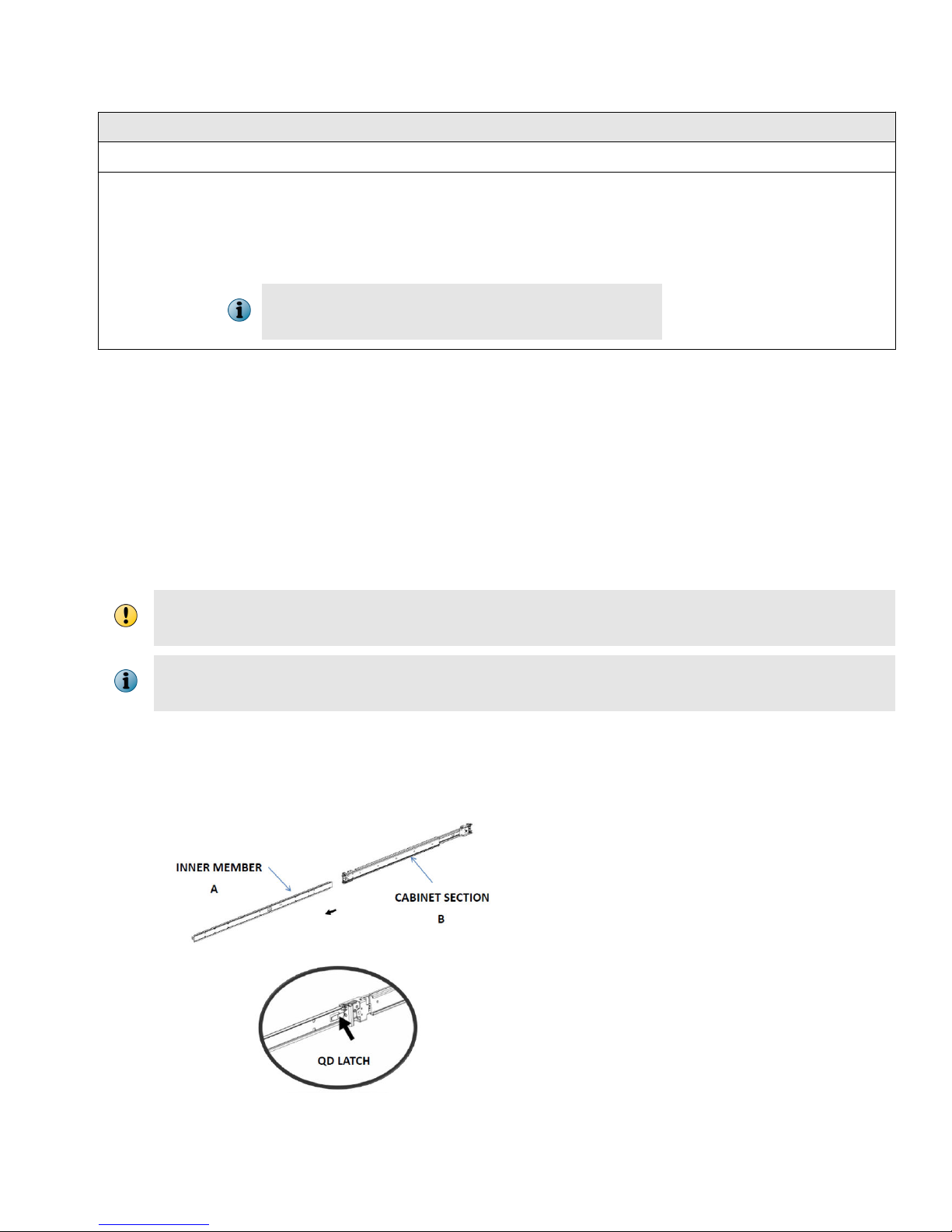
Disassemble the inner slide rail members from the cabinet sections.
a
Pull the inner member out until it comes to a lock position.
a
Depress the QD latch to fully disconnect the inner members.
b
4
Page 5
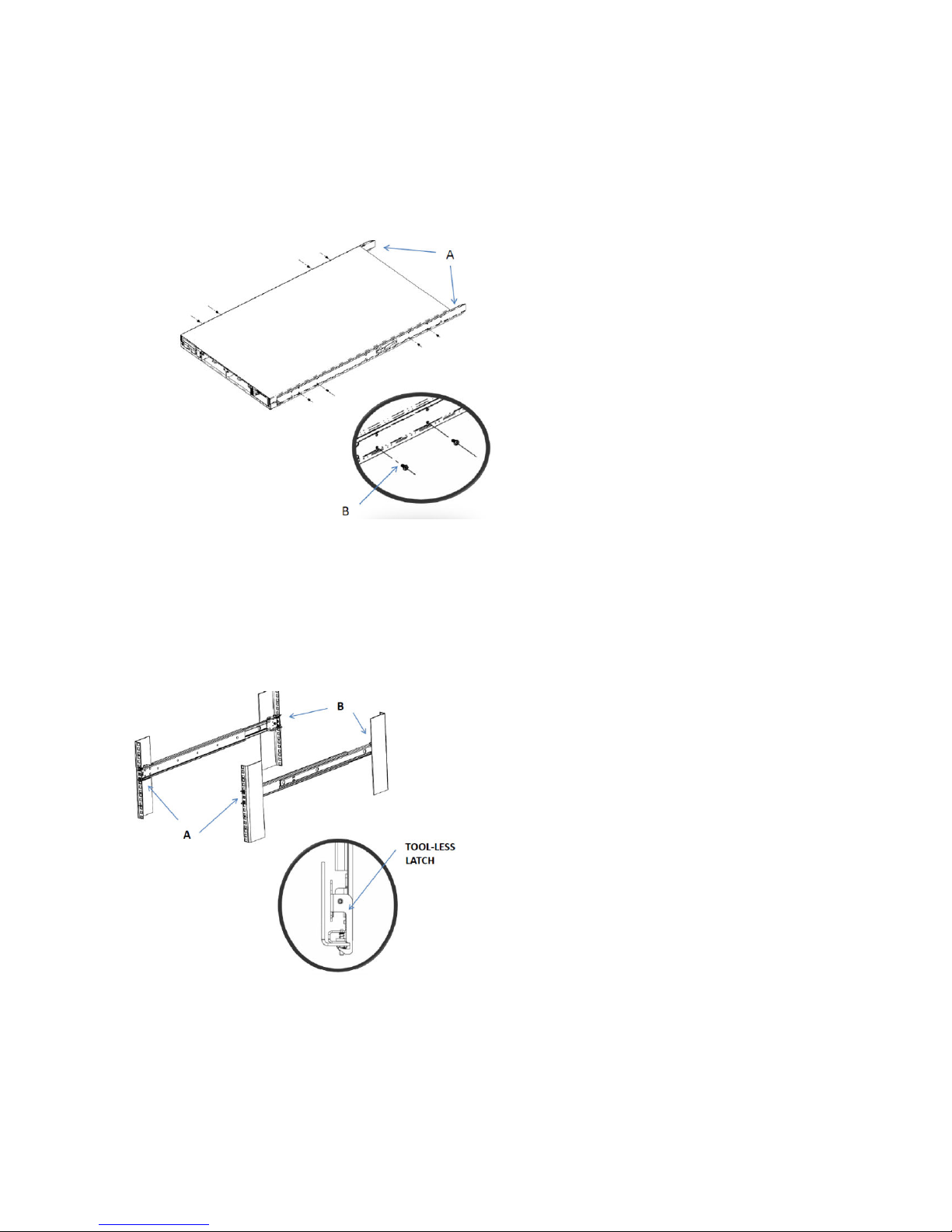
Mount the inner members to the chassis unit.
b
Place each inner member on both sides of the chassis unit. Position the bottom mounting holes of
a
the inner member with matching mounting holes on chassis unit.
Use screws to secure inner members in place. Apply to both sides of chassis unit.
b
Mount the slide cabinet sections to the rack.
c
Install the front end of each slide cabinet section to the rack using the slide tool-less features. The
a
tool-less latch rotates when the bracket is pressed up against the rack rails.
Align, adjust, and attach the rear brackets to the rack rail.
b
5
Page 6

Mount the chassis unit into the mounted cabinet sections.
d
Guide the chassis unit into the pre-installed cabinet sections. Allow the pre-installed inner members
a
to slide into the outer members until they lock in place.
Depress the QD latch on both sides and continue to push the chassis unit in until fully closed.
b
Secure the chassis unit through the rack rails.
e
With the chassis unit in a fully closed position, secure using two truss head screws.
a
Drive the screws through the inner member ange and through the rack rails. The screws thread
b
directly to the cabinet slide members. Tighten the screws.
4 Install the interface modules
You can purchase the following interface modules and insert them into the relevant slots on your NS7x00
Sensor.
• 8-port SFP/SFP+ 1/10 Gigabit interface module
• 6-port RJ-45 10/100/1000 Mbps with internal fail-open interface module
• 4-port 10/1 GigE SM 8.5 micron with internal fail-open interface module
6
Page 7

• 4-port 10/1 GigE MM 50 micron with internal fail-open interface module
• 4-port 10/1 GigE MM 62.5 micron with internal fail-open interface module
Remove the module from its protective packaging.
a
Hold the module using your thumb and forenger and insert it into the modular bay.
b
Drive in the screws xed on the sides of the module to attach it to the Sensor.
c
5 Connect the Management and Console ports
On the rear panel of the NS7x00 Sensors, plug a Category 5e Ethernet cable in the Management port
a
(labeled Mgmt).
Plug the other end of the cable into the network device connected to your Manager server.
b
7
Page 8

On the front panel of the NS7x00 Sensors, plug the DB9 Console cables into the Console port (labeled
c
Console).
Connect the other end of the Console port cable directly to a COM port of the PC or terminal server you
d
are using to congure the Sensor (for example, a PC running correctly congured Windows
Hyperterminal software). You must directly connect to the console for initial conguration, you cannot
congure the Sensor remotely.
Terminal servers are provided for console access.
The required settings for Hyperterminal are:
• Baud rate: 115200 • Stop Bits: 1
• Number of Bits: 8 • Control Flow: None
• Parity: None
Plug one end of the power cable into the power inlet and plug the other end into a power source. The
e
Sensor ships with standard US power and international cables.
The NS-series Sensor does not have a power switch. You can directly plug the power cable into
a power source.
8
Page 9

6 Connect the monitoring ports
This procedure describes how to connect cables to a Sensor that runs in in-line mode.
Plug the cable appropriate for use with your transceiver module into one of the monitoring ports labeled
a
x (for example, 1).
Plug the cable appropriate for use with your transceiver module into one of the monitoring ports labeled
b
y (for example, 2).
Connect the other end of each cable to the network devices that you want to monitor. For example, if you
c
plan to monitor trac between a switch and a router, connect the cable connected to 1 to the router and
the one connected to 2 to the switch.
7 Install the Manager software
For detailed instructions, see the McAfee Network Security Platform Installation Guide.
You must have administrator rights on the target Windows Server to install the Manager software.
A MySQL database is included with the Manager and is installed (embedded) automatically on your
target Windows Server during this process.
The following steps briey explain the Manager installation:
Prepare the system according to the requirements outlined in McAfee Network Security Platform Installation
a
Guide and the McAfee Network Security Platform Release Notes.
Close all open applications.
b
Go to the McAfee Update Server (https://menshen1.intruvert.com/) and log on, using the grant number
c
and password.
d Go to the Manager Software Updates folder and select the latest Manager software version available.
Download the .zip
e
f Double-click Manager _<version>_setup.exe and follow the on-screen prompts.
le to the target Windows Server and extract the setup le.
8 Start the Manager
Click Start | Programs | McAfee | Network Security Manager | Network Security Manager.
9
Page 10

9 Add the Sensor to the Manager
The Manager displays the Logon page.
Log on to the Manager using the default user name (admin) and password (admin123).
a
b Click Devices.
c To add a Sensor in the Manager, click Global | Add and Remove Devices, then click New.
You do not require a license le to enable IPS on NS-series Sensors.
The Add New Device page is displayed. We recommend using the Add Device wizard to add a device.
Enter the following mandatory information in the appropriate elds.
d
1) Device Name — The Sensor name must begin with a letter. The maximum length of the name is 25
characters.
2) Device Type — Species the type of device to be added. Select IPS Sensor.
10
Page 11

3) Shared Secret — The shared secret must be a minimum of 8 characters and maximum of 25
characters in length. The key cannot start with an exclamation mark nor can have any spaces. The
parameters that you can use to dene the key are:
• 26 alphabets: Uppercase and lowercase
(A, B, C,...Z and a,b,c,...z)
• 32 symbols: ~ ` ! @ # $ % ^ & * ( ) _ + ‑ =
[ ] { } \ | ; : " ' , . <? /
• 10 digits: 0 1 2 3 4 5 6 7 8 9
The Sensor name and shared secret key that you enter in the Manager must be identical
to the shared secret that you will later enter during physical installation or initialization of
the Sensor (using CLI) in Step 10 - Congure Sensor information. If not, the Sensor will not be
able to register itself with the Manager.
4) Updating Mode — Select Online or Offline.
Selecting Offline enables Oine Sensor update. Online is the default mode.
e Click Save. The added Sensor is displayed on the Add and Remove Devices page.
10 Congure Sensor information
Congure the Sensor with the network information, a name, and the shared secret key that the Sensor uses to
establish secure communication with the Manager. Use the name and key values you set in Step 9 - Add the
Sensor to the Manager.
The rst time you congure a Sensor, you must have physical access to the Sensor.
At any time during conguration, you can type a question mark (?) to get help on the Sensor CLI commands.
For a list of all commands, type commands.
Log on to the Sensor using the terminal connected to the Console port.
a
At the prompt, log on using the default Sensor user name (admin) and password (admin123).
b
11
Page 12

Optional, but recommended. Change the Sensor password. At the prompt, type: passwd.The Sensor
c
prompts you to enter the new password and prompts you for the old password.
A password must contain between 8–25 characters, is case sensitive, and can consist of any
alphanumeric character or symbol.
Set the name of the Sensor:
d
You can enter the setup command at the prompt. This automatically prompts you to provide
the information shown in items d through g and item j. Alternatively, you can use the set
command. If you use the set command, manually enter the complete command syntax as
shown in items d through g and item j.
At the prompt, type: set sensor name <word>.
Example: set sensor name HR_sensor1
The Sensor name is a case-sensitive character string up to 25 characters. The string can include
hyphens, underscores, and periods, and must begin with a letter.
If the Sensor is not on the same network as the Manager, set the address of the default Gateway. At the
e
prompt, type: set sensor gateway <A.B.C.D>
Example: set sensor gateway 192.168.3.68
Set the IP address of the Manager server. At the prompt, type: set manager ip <A.B.C.D>.
f
Example: set manager ip 192.168.2.8
Set the IP address and subnet mask of the Sensor. At the prompt, type: set sensor ip <A.B.C.D>
g
<E.F.G.H>.
Example: set sensor ip 192.168.2.12 255.255.255.0
Specify an IP address using four octets separated by periods: X.X.X.X, where X is a number
between 0 and 255, followed by a subnet mask in the same format.
If prompted, reboot the Sensor. Type: reboot
h
The Sensor can take up to ve minutes to complete its reboot.
Ping the Manager from the Sensor to determine if your
i
conguration settings to this point have
successfully established the Sensor on the network. At the prompt, type:
ping <manager IP address>.
If the ping is successful, continue with the following steps. If not, type show to verify your conguration
settings and check that the information is correct.
Set the shared secret key value for the Sensor. At the prompt, type:
j
12
Page 13

set sensor sharedsecretkey
The Sensor then prompts you to enter and then conrm the shared secret key value.
This value is used to establish a trust relationship between the Sensor and the Manager. The
secret key value can be between 8 and 25 characters of any ASCII text. The shared key value is
case-sensitive. Make sure that the value matches the shared secret key value you provided in
the Manager interface in Step 9 - Add the Sensor to the Manager.
To verify the conguration information, type show. Check that all information is correct.
k
To exit the session, type exit.
l
11 Verify successful installation
In the Sensor CLI, type: status. The status report is displayed.
a
The Sensor parameter System Initialized must be yes, and for Manager communication Trust
Established must be yes.
b From the Manager Dashboard, view the Manager status in the System Health monitor.
13
Page 14

The Manager status displays as Up and Sensor status is Active.
c From the Manager, click Devices | <Device_Name> | Setup | Physical Ports to open the Physical Ports page.
<Device_Name> indicates the name of the Sensor you added.
d A policy named Default Inline IPS is active upon Sensor addition. To view this policy, select Intrusion
Prevention | Policy | IPS Policies. Select Default Inline IPS from the list and click View / Edit.
The Default Inline IPS policy contains attacks already congured with a "blocking" Sensor
response action. If any attack in the policy is triggered, the Sensor automatically blocks the
attack. To tune this or any other McAfee-provided policies, you can clone the policy and then
customize it as described in the McAfee Network Security Platform IPS Administration Guide.
e Click Devices | <Device_Name> | Setup | Physical Ports.
Select the port on the Sensor that you cabled to view port settings. Make sure that your port settings
f
match the cabling, for example, if port 1 is cabled for the in-line mode, then the Operating Mode in the port
setting must be in-line mode.
For more information on port settings, see Conguring the monitoring and response ports of a
Sensor, McAfee Network Security Platform IPS Administration Guide.
14
Page 15

12 You're up and running!
Your Sensor is actively monitoring connected segments and communicating with the Manager for
administration and management operations.
For detailed usage instructions, see the McAfee Network Security Platform IPS Administration Guide, or click
a
the Detailed Help buttons in the upper-right corner of each window in the Manager.
b Start the Analysis | Threat Analyzer to view alert statistics as attacks are detected. A summary of alerts is
displayed in the Unacknowledged Alert Summary area of the Manager Dashboard page.
Having problems? See the McAfee Network Security Platform Troubleshooting Guide for troubleshooting
c
information.
Most deployment problems stem from
d
conguration mismatches between the Sensor and the network
devices to which it is connected. Check the duplex and auto-negotiation settings on both devices to
ensure that they are synchronized.
To contact technical support, go to https://support.mcafee.com.
15
Page 16

Copyright © 2017 McAfee, LLC
McAfee and the McAfee logo are trademarks or registered trademarks of McAfee, LLC or its subsidiaries in the US and other countries. Other
marks and brands may be claimed as the property of others.
16 700-4423D00
 Loading...
Loading...