Page 1

Installation Guide
revision 5.0
McAfee® Network Security Platform
version 6.0
McAfee®
Network Protection
Industry-leading network security solutions
Page 2
COPYRIGHT
Copyright ® 2001 - 2010 McAfee, Inc. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into
any language in any form or by any means without the written permission of McAfee, Inc., or its suppliers or affiliate companies.
TRADEMARKS
ACTIVE FIREWALL, ACTIVE SECURITY, ACTIVESECURITY (AND IN KATAKANA), ACTIVESHIELD, CLEAN-UP, DESIGN (STYLIZED E), DESIGN (STYLIZED N),
ENTERCEPT, EPOLICY ORCHESTRATOR, FIRST AID, FOUNDSTONE, GROUPSHIELD, GROUPSHIELD (AND IN KATAKANA), INTRUSIVELY, INTRUSION PREVENTION
THROUGH INNOVATION, McAfee, McAfee (AND IN KATAKANA), McAfee AND DESIGN, McAfee.COM, McAfee VIRUSSCAN, NET TOOLS, NET TOOLS (AND IN KATAKANA),
NETSCAN, NETSHIELD, NUTS & BOLTS, OIL CHANGE, PRIMESUPPORT, SPAMKILLER, THREATSCAN, TOTAL VIRUS DEFENSE, VIREX, VIRUS FORUM, VIRUSCAN,
VIRUSSCAN, VIRUSSCAN (AND IN KATAKANA), WEBSCAN, WEBSHIELD, WEBSHIELD (AND IN KATAKANA) are registered trademarks or trademarks of McAfee, Inc. and/or
its affiliates in the US and/or other countries. The color red in connection with security is distinctive of McAfee brand products. All other registered and unregistered trademarks
herein are the sole property of their respective owners.
LICENSE AND PATENT INFORMATION
License Agreement
NOTICE TO ALL USERS: CAREFULLY READ THE APPROPRIATE LEGAL AGREEMENT CORRESPONDING TO THE LICENSE YOU PURCHASED, WHICH SETS FORTH
THE GENERAL TERMS AND CONDITIONS FOR THE USE OF THE LICENSED SOFTWARE. IF YOU DO NOT KNOW WHICH TYPE OF LICENSE YOU HAVE ACQUIRED,
PLEASE CONSULT THE SALES AND OTHER RELATED LICENSE GRANT OR PURCHASE ORDER DOCUMENTS THAT ACCOMPANIES YOUR SOFTWARE PACKAGING
OR THAT YOU HAVE RECEIVED SEPARATELY AS PART OF THE PURCHASE (AS A BOOKLET, A FILE ON THE PRODUCT CD, OR A FILE AVAILABLE ON THE WEB SITE
FROM WHICH YOU DOWNLOADED THE SOFTWARE PACKAGE). IF YOU DO NOT AGREE TO ALL OF THE TERMS SET FORTH IN THE AGREEMENT, DO NOT INSTALL
THE SOFTWARE. IF APPLICABLE, YOU MAY RETURN THE PRODUCT TO McAfee OR THE PLACE OF PURCHASE FOR A FULL REFUND.
License Attributions
This product includes or may include:
* Software developed by the OpenSSL Project for use in the OpenSSL Toolkit (http://www.openssl.org/). * Cryptographic software written by Eric A. Young and software written by
Tim J. Hudson. * Some software programs that are licensed (or sublicensed) to the user under the GNU General Public License (GPL) or other similar Free Software licenses
which, among other rights, permit the user to copy, modify and redistribute certain programs, or portions thereof, and have access to the source code. The GPL requires that for
any software covered under the GPL, which is distributed to someone in an executable binary format, that the source code also be made available to those users. For any such
software covered under the GPL, the source code is made available on this CD. If any Free Software licenses require that McAfee provide rights to use, copy or modify a software
program that are broader than the rights granted in this agreement, then such rights shall take precedence over the rights and restrictions herein. * Software originally written by
Henry Spencer, Copyright 1992, 1993, 1994, 1997 Henry Spencer. * Software originally written by Robert Nordier, Copyright (C) 1996-7 Robert Nordier. * Software written by
Douglas W. Sauder. * Software developed by the Apache Software Foundation (http://www.apache.org/). A copy of the license agreement for this software can be found at
www.apache.org/licenses/LICENSE-2.0.txt. * International Components for Unicode ("ICU") Copyright (C) 1995-2002 International Business Machines Corporation and others. *
Software developed by CrystalClear Software, Inc., Copyright (C) 2000 CrystalClear Software, Inc. * FEAD(R) Optimizer(R) technology, Copyright Netopsystems AG, Berlin,
Germany. * Outside In(R) Viewer Technology (C) 1992-2001 Stellent Chicago, Inc. and/or Outside In(R) HTML Export, (C) 2001 Stellent Chicago, Inc. * Software copyrighted by
Thai Open Source Software Center Ltd. and Clark Cooper, (C) 1998, 1999, 2000. * Software copyrighted by Expat maintainers. * Software copyrighted by The Regents of the
University of California, (C) 1996, 1989, 1998-2000. * Software copyrighted by Gunnar Ritter. * Software copyrighted by Sun Microsystems, Inc., 4150 Network Circle, Santa Clara,
California 95054, U.S.A., (C) 2003. * Software copyrighted by Gisle Aas. (C) 1995-2003. * Software copyrighted by Michael A. Chase, (C) 1999-2000. * Software copyrighted by
Neil Winton, (C) 1995-1996. * Software copyrighted by RSA Data Security, Inc., (C) 1990-1992. * Software copyrighted by Sean M. Burke, (C) 1999, 2000. * Software copyrighted
by Martijn Koster, (C) 1995. * Software copyrighted by Brad Appleton, (C) 1996-1999. * Software copyrighted by Michael G. Schwern, (C) 2001. * Software copyrighted by Graham
Barr, (C) 1998. * Software copyrighted by Larry Wall and Clark Cooper, (C) 1998-2000. * Software copyrighted by Frodo Looijaard, (C) 1997. * Software copyrighted by the Python
Software Foundation, Copyright (C) 2001, 2002, 2003. A copy of the license agreement for this software can be found at www.python.org. * Software copyrighted by Beman
Dawes, (C) 1994-1999, 2002. * Software written by Andrew Lumsdaine, Lie-Quan Lee, Jeremy G. Siek (C) 1997-2000 University of Notre Dame. * Software copyrighted by Simone
Bordet & Marco Cravero, (C) 2002. * Software copyrighted by Stephen Purcell, (C) 2001. * Software developed by the Indiana University Extreme! Lab
(http://www.extreme.indiana.edu/). * Software copyrighted by International Business Machines Corporation and others, (C) 1995-2003. * Software developed by the University of
California, Berkeley and its contributors. * Software developed by Ralf S. Engelschall <rse@engelschall.com> for use in the mod_ssl project (http:// www.modssl.org/). * Software
copyrighted by Kevlin Henney, (C) 2000-2002. * Software copyrighted by Peter Dimov and Multi Media Ltd. (C) 2001, 2002. * Software copyrighted by David Abrahams, (C) 2001,
2002. See http://www.boost.org/libs/bind/bind.html
Software copyrighted by Boost.org, (C) 1999-2002. * Software copyrighted by Nicolai M. Josuttis, (C) 1999. * Software copyrighted by Jeremy Siek, (C) 1999-2001. * Software
copyrighted by Daryle Walker, (C) 2001. * Software copyrighted by Chuck Allison and Jeremy Siek, (C) 2001, 2002. * Software copyrighted by Samuel Krempp, (C) 2001. See
http://www.boost.org for updates, documentation, and revision history. * Software copyrighted by Doug Gregor (gregod@cs.rpi.edu), (C) 2001, 2002. * Software copyrighted by
Cadenza New Zealand Ltd., (C) 2000. * Software copyrighted by Jens Maurer, (C) 2000, 2001. * Software copyrighted by Jaakko Järvi (jaakko.jarvi@cs.utu.fi), (C) 1999, 2000. *
Software copyrighted by Ronald Garcia, (C) 2002. * Software copyrighted by David Abrahams, Jeremy Siek, and Daryle Walker, (C) 1999-2001. * Software copyrighted by Stephen
Cleary (shammah@voyager.net
1999. * Software copyrighted by Dr. John Maddock, (C) 1998-2002. * Software copyrighted by Greg Colvin and Beman Dawes, (C) 1998, 1999. * Software copyrighted by Peter
Dimov, (C) 2001, 2002. * Software copyrighted by Jeremy Siek and John R. Bandela, (C) 2001. * Software copyrighted by Joerg Walter and Mathias Koch, (C) 2000-2002. *
Software copyrighted by Carnegie Mellon University (C) 1989, 1991, 1992. * Software copyrighted by Cambridge Broadband Ltd., (C) 2001-2003. * Software copyrighted by
Sparta, Inc., (C) 2003-2004. * Software copyrighted by Cisco, Inc and Information Network Center of Beijing University of Posts and Telecommunications, (C) 2004. * Software
copyrighted by Simon Josefsson, (C) 2003. * Software copyrighted by Thomas Jacob, (C) 2003-2004. * Software copyrighted by Advanced Software Engineering Limited, (C)
2004. * Software copyrighted by Todd C. Miller, (C) 1998. * Software copyrighted by The Regents of the University of California, (C) 1990, 1993, with code derived from software
contributed to Berkeley by Chris Torek.
), (C) 2000. * Software copyrighted by Housemarque Oy <http://www.housemarque.com>, (C) 2001. * Software copyrighted by Paul Moore, (C)
for documentation. * Software copyrighted by Steve Cleary, Beman Dawes, Howard Hinnant & John Maddock, (C) 2000. *
Issued NOVEMBER 2010 / Installation Guide
700-2252-00/ 5.0 - English
Page 3

Contents
Preface ........................................................................................................... v
Introducing McAfee Network Security Platform............................................................................. v
Conventions used in this book ...................................................................................................... v
Related Documentation.................................................................................................................vi
Contacting Technical Support ......................................................................................................vii
Chapter 1 About Network Security Platform.............................................. 1
Network Security Platform components ........................................................................................ 1
About McAfee Network Security Sensor ................................................................................1
Manager components ............................................................................................................4
McAfee Update Server...........................................................................................................6
Chapter 2 About Network Security Central Manager ................................ 8
Chapter 3 Preparing for the Manager installation...................................... 9
Pre-requisites ................................................................................................................................ 9
General settings .....................................................................................................................9
Other third-party applications ...............................................................................................10
Browser display settings (Windows) ....................................................................................10
Server requirements.............................................................................................................10
Manager installation with Local Service account privileges .................................................12
Client requirements ..............................................................................................................12
Java runtime engine requirements.......................................................................................12
Database requirements........................................................................................................13
Pre-installation recommendations............................................................................................... 13
Planning for installation ........................................................................................................13
Functional requirements.......................................................................................................14
Using anti-virus software with the Manager .........................................................................14
User interface responsiveness.............................................................................................15
Downloading the Manager/Central Manager executable ............................................................ 16
Chapter 4 Installing the Manager/Central Manager................................. 17
Installing the Manager ................................................................................................................. 17
Installing the Central Manager .................................................................................................... 28
Chapter 5 Starting the Manager/Central Manager ................................... 30
Accessing the Manager from a client machine............................................................................ 30
Java installation for client systems.............................................................................................. 31
Logging onto the Manager .......................................................................................................... 31
Logging onto the Central Manager.............................................................................................. 32
Authenticating Access to the Manager using CAC ..................................................................... 33
Shutting down the Manager/Central Manager services .............................................................. 35
Closing all client connections ...............................................................................................36
Shutting down using the Network Security Platform system tray icon .................................36
Shutting down using the Control Panel ................................................................................37
Chapter 6 Adding a Sensor........................................................................ 39
Before You Install Sensors.......................................................................................................... 39
Network topology considerations .........................................................................................39
Safety measures ..................................................................................................................39
Usage restrictions ................................................................................................................40
iii
Page 4

Unpacking the Sensor..........................................................................................................41
Cable Specifications.................................................................................................................... 41
Network Security Platform fail-closed dongle specification.................................................. 42
Console port pin-outs ...........................................................................................................42
Auxiliary port pin-outs...........................................................................................................42
Response port pin-outs ........................................................................................................43
Monitoring port pin-outs .......................................................................................................44
Configuring a Sensor................................................................................................................... 45
Configuration overview.........................................................................................................45
Establish a Sensor naming scheme.....................................................................................45
Communication between the Sensor and the Manager .......................................................46
Configuring the Sensor ........................................................................................................46
Adding a Sensor to the Manager .........................................................................................48
Verifying successful configuration........................................................................................49
Changing Sensor values ......................................................................................................50
Adding a secondary Manager IP..........................................................................................51
Removing a secondary Manager IP.....................................................................................51
Device Licenses .......................................................................................................................... 52
Importing a Device License..................................................................................................52
Manually assigning a device license ....................................................................................53
Chapter 7 Configuring the Update Server................................................ 55
Specifying the Update Server authentication .............................................................................. 55
Specifying a proxy server for Internet connectivity...................................................................... 56
Manually importing a software image or signature set................................................................ 57
Downloading software updates ................................................................................................... 57
Downloading signature set updates ............................................................................................ 60
Automating updates .................................................................................................................... 62
Automating signature set downloads from the Update Server.............................................62
Automatically deploy new signature sets to your devices....................................................63
Chapter 8 Uninstalling the Manager/Central Manager ............................ 65
Uninstalling using Add/Remove Programs.................................................................................. 65
Uninstalling via script................................................................................................................... 66
Index............................................................................................................. 68
iv
Page 5
Preface
This preface provides a brief introduction to the product, discusses the information in this
document, and explains how this document is organized. It also provides information such
as, the supporting documents for this guide and how to contact McAfee Technical Support.
Introducing McAfee Network Security Platform
McAfee® Network Security Platform [formerly McAfee® Intrushield®] delivers the most
comprehensive, accurate, and scalable Network Access Control (NAC), network Intrusion
Prevention System (IPS) and Network Threat Behavior Analysis (NTBA) for mission-critical
enterprise, carrier and service provider networks, while providing unmatched protection
against spyware; known, zero-day, and encrypted attacks.
McAfee
network traffic by analyzing NetFlow information flowing through the network in real time,
thus complementing the NAC and IPS capabilities in a scenario in which McAfee Network
Security Sensor, NAC Sensor, and NTBA Appliance are installed and managed through a
single Manager.
®
Network Threat Behavior Analysis Appliance provides the capability of monitoring
Conventions used in this book
This document uses the following typographical conventions:
Convention Example
Terms that identify fields, buttons,
tabs, options, selections, and
commands on the User Interface
(UI) are shown in
font.
Menu or action group selections
are indicated using a right angle
bracket.
Procedures are presented as a
series of numbered steps.
Names of keys on the keyboard
are denoted using UPPER CASE.
Text such as syntax, key words,
and values that you must type
exactly are denoted using
Courier New font.
Arial Narrow bold
Service field on the Properties tab specifies the
The
name of the requested service.
Select My Company > Admin Domain > Summary.
1. On the Configuration tab, click Backup.
Press ENTER.
Type: setup and then press ENTER.
v
Page 6

McAfee® Network Security Platform 6.0
Convention Example
Preface
Variable information that you must
type based on your specific
situation or environment is shown
in italics.
Parameters that you must supply
are shown enclosed in angle
brackets.
Information that you must read
before beginning a procedure or
that alerts you to negative
consequences of certain actions,
such as loss of data is denoted
using this notation.
Information that you must read to
prevent injury, accidents from
contact with electricity, or other
serious consequences is denoted
using this notation.
Notes that provide related, but
non-critical, information are
denoted using this notation.
Related Documentation
Type: Sensor-IP-address and then press
ENTER.
set Sensor ip <A.B.C.D>
Caution:
Warning:
Note:
The following documents and on-line help are companions to this guide. Refer to Quick
Tour for more information on these guides.
Quick Tour
Upgrade Guide
Getting Started Guide
IPS Deployment Guide
Manager Configuration Basics Guide
I-1200 Sensor Product Guide
I-1400 Sensor Product Guide
I-2700 Sensor Product Guide
I-3000 Sensor Product Guide
I-4000 Sensor Product Guide
I-4010 Sensor Product Guide
M-1250/M-1450 Sensor Product Guide
M-1250/M-1450 Quick Start Guide
M-2750 Sensor Product Guide
M-2750 Quick Start Guide
M-3050/M-4050 Sensor Product Guide
M-3050/M-4050 Quick Start Guide
M-6050 Sensor Product Guide
M-6050 Quick Start Guide
vi
Page 7

McAfee® Network Security Platform 6.0
M-8000 Sensor Product Guide
M-8000 Quick Start Guide
Gigabit Optical Fail-Open Bypass Kit Guide
Gigabit Copper Fail-Open Bypass Kit Guide
10 Gigabit Fail-Open Bypass Kit Guide
M-8000/M-6050/M-4050/M-3050 Slide Rail Assembly Procedure
M-2750 Slide Rail Assembly Procedure
M-series DC Power Supply Installation Procedure
Administrative Domain Configuration Guide
Manager Server Configuration Guide
CLI Guide
Device Configuration Guide
IPS Configuration Guide
NAC Configuration Guide
Integration Guide
System Status Monitoring Guide
Reports Guide
Custom Attack Definitions Guide
Central Manager Administrator's Guide
Best Practices Guide
Troubleshooting Guide
Special Topics Guide—In-line Sensor Deployment
Special Topics Guide—Sensor High Availability
Special Topics Guide—Virtualization
Special Topics Guide—Denial-of-Service
NTBA Appliance Administrator's Guide
NTBA Monitoring Guide
NTBA Appliance T-200 Quick Start Guide
NTBA Appliance T-500 Quick Start Guide
Preface
Contacting Technical Support
If you have any questions, contact McAfee for assistance:
Online
Contact McAfee Technical Support http://mysupport.mcafee.com.
Registered customers can obtain up-to-date documentation, technical bulletins, and quick
tips on McAfee's 24x7 comprehensive KnowledgeBase. In addition, customers can also
resolve technical issues with the online case submit, software downloads, and signature
updates.
Phone
Technical Support is available 7:00 A.M. to 5:00 P.M. PST Monday-Friday. Extended 24x7
Technical Support is available for customers with Gold or Platinum service contracts.
vii
Page 8

McAfee® Network Security Platform 6.0
Global phone contact numbers can be found at McAfee Contact Information
http://www.mcafee.com/us/about/cont
Note: McAfee requires that you provide your GRANT ID and the serial number of
your system when opening a ticket with Technical Support. You will be provided with
a user name and password for the online case submission.
Preface
act/index.html page.
viii
Page 9

C HAPTER 1
About Network Security Platform
McAfee® Network Security Platform [formerly McAfee® IntruShield®] is a combination of
network appliances and software built for the accurate detection and prevention of
intrusions, denial of service (DoS) attacks, distributed denial of service (DDoS) attacks,
and network misuse. Network Security Platform provides comprehensive network intrusion
detection and can block, or prevent, attacks in real time, making it truly an intrusion
prevention system (IPS).
Network Security Platform components
Network Security Platform consists of the following major components:
®
McAfee
McAfee® Network Security Manager (Manager), with its Web-based graphical user
interface
McAfee Update Server (on page 6
About McAfee Network Security Sensor
A McAfee® Network Security Sensor is a content-processing appliance built for accurate
detection and prevention of intrusions, misuse, and distributed denial of service (DDoS)
attacks. McAfee Network Security Sensor (Sensor) are specifically designed to handle
traffic at wire speed, inspect and detect intrusions with a high degree of accuracy, and
flexible enough to adapt to the security needs of any enterprise environment.
Network Security Sensor (Sensor) (on page 1)
)
When deployed at key network access points, a Sensor provides real-time traffic
monitoring to detect malicious activity and respond to the malicious activity as configured
by the administrator.
Sensors are configured and managed using McAfee Network Security Manager
(Manager). The process of configuring a Sensor and establishing communication with the
Manager is described in later chapters of this guide. The Manager server is described in
detail in the
Getting Started Guide.
Sensor functionality
The primary function of a device is to analyze traffic on selected network segments and to
respond when an attack is detected. The device examines the header and data portion of
every network packet, looking for patterns and behavior in the network traffic that indicate
malicious activity. The device examines packets according to user-configured policies, or
rule sets, which determine what attacks to watch for, and how to respond with
countermeasures if an attack is detected.
1
Page 10
McAfee® Network Security Platform 6.0
If an attack is detected, a Sensor responds according to its configured policy. Sensor can
perform many types of attack responses, including generating alerts and packet logs,
resetting TCP connections, “scrubbing” malicious packets, and even blocking attack
packets entirely before they reach the intended target.
Sensor platforms
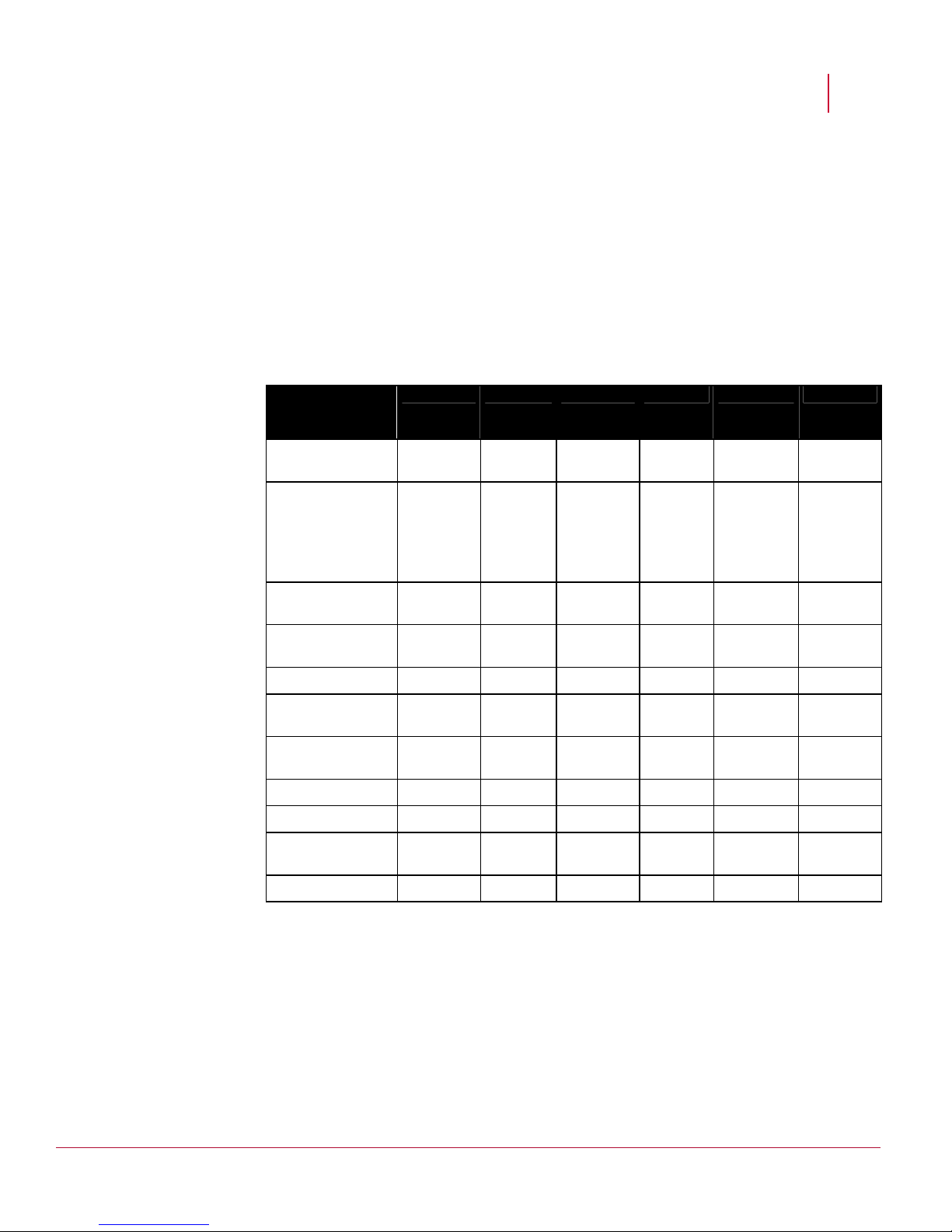
Network Security Platform offers several types of Sensor platforms providing different
bandwidth and deployment strategies.
I-series Sensors
I-4010 I-4000 I-3000 I-2700 I-1400 I-1200
About Network Security Platform
10/100 Base-T
Nil Nil Nil 6 4 2
Monitoring Port
10/100/1000
Gigabit Ethernet
Monitoring Port
RJ-45 Response
12
10/100/100
0 only with
Copper
SFP
4 12
10/100/100
0 only with
Copper
SFP
2 2 2 3 1 1
2 Nil Nil
Port
Ports Used for
Failover
6A and 6B 2A and 2B 6A and 6B 4A Response
port
Response
port
Internal Taps Nil Nil Nil Yes Yes Yes
Fail-open Control
6 2 6 Nil Nil Nil
Ports
10/100
1 1 1 1 1 1
Management port
Console Port 1 1 1 1 1 1
Auxiliary Port 1 1 1 1 1 1
Redundant power
Yes Yes Yes Yes Nil Nil
supply
Fail-closed dongles Nil Nil Nil 6 4 2
2
Page 11
McAfee® Network Security Platform 6.0
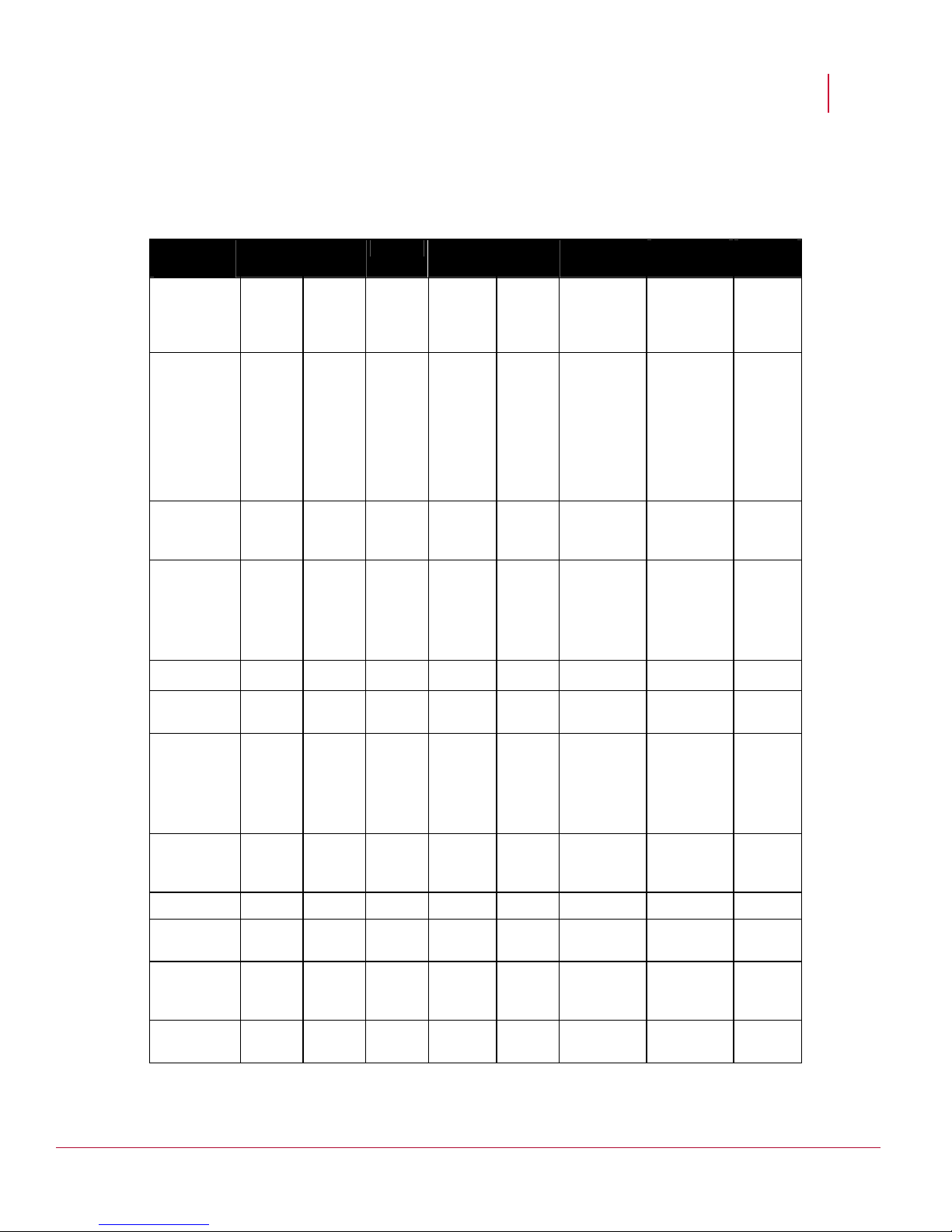
M-series and N-450 Sensors
M-8000 M-6050 M-4050 M-3050 M-2750 M-1450 M-1250 N-450
About Network Security Platform
10/100
Base-T
Monitoring
Nil Nil Nil Nil Nil 8 built-in
10/100/1000
RJ-45 ports
8 built-in
10/100/1000
RJ-45 ports
Nil
Port
Interface
Module
16 One
Gigabit
SFP
ports
8 SFP
ports
8 XFP
ports
4 XFP
ports
8 SFP
ports
4 XFP
ports
8 SFP
ports
20 SFP
ports
20 SFP
ports
12 Ten
Gigabit
XFP
ports
RJ-45
1 1 1 1 1 1 1 0
Response
Port
Ports Used
for failover
3A and
3B
4A
Note
that 4B
remains
unused.
2A 2A 10A
Note
that 10B
is
unused.
4A
Note that 4B
is unused.
4A
Note that 4B
is unused.
10A and
10B
Internal Taps Nil Nil Nil Nil Nil Yes Yes Nil
Fail-open
14 8 6 6 10 Nil Nil 10
Control Ports
Interconnect
ports
4 Ten
Gigabit
Nil Nil Nil Nil Nil Nil Nil
XFPs
2 RJ-45
ports
10/100/1000
1 1 1 1 1 1 1 1
Management
port
Console Port 2 1 1 1 1 1 1 1
Auxiliary
2 1 1 1 1 1 1 1
Port
Redundant
Yes Yes Yes Yes Yes Nil Nil Yes
power
supply
Fail-closed
Nil Nil Nil Nil Nil Nil Nil Nil
dongles
3
Page 12

McAfee® Network Security Platform 6.0
Each device is described in the corresponding Sensor Product Guide.
Manager components
The Manager is a term that represents the hardware and software resources that are used
to configure and manage the Network Security Platform. The Manager consists of the
following components:
About Network Security Platform
Either of the following hardware/OS server platform (on page 4
)
Microsoft Windows Server 2003 - SP2, Standard Edition, English or Japanese
Microsoft Windows Server 2008 - R2, Standard Edition, English or Japanese
the Manager software (on page 4
a back end database (on page 6
a connection to McAfee Update Server (on page 6)
)
) to persist data (MySQL version 5.1.47)
Manager server platform
The Manager server is a dedicated Windows Server 2003 SP2 / Windows 2008 R2 system
hosting the Manager software. You can remotely access the Network Security Platform
user interface from a Windows XP or Windows 7 system using an Internet Explorer 7.0 or
8.0.
Sensors use a built-in 10/100 Management port to communicate with the Manager server.
You can connect a segment from a Sensor Management port directly to the Manager
server; however, this means you can only receive information from one Sensor (typically,
your server has only one 10/100 network port). During the Sensor configuration, you will
establish communication between your Sensor(s) and your Manager server.
Manager software
The Manager software has a Web-based user interface for configuring and managing the
Network Security Platform. Network Security Platform users connect to the Manager
server from a Windows XP system using the Internet Explorer browser program. The
Network Security Platform user interface runs with Internet Explorer versions 7.0 and 8.0.
The Manager functions are configured and managed through a GUI application, the
Network Security Platform user interface, which includes complementary interfaces for
system status, system configuration, report generation, and fault management. All
interfaces are logically parts of the Manager program.
The Manager has five components:
Manager Home. The Manager Home page is the first screen displayed after the user logs
on to the system. The Manager Home page displays Operational Status-that is,
whether all components of the system are functioning properly, the number of
unacknowledged alerts in the system, and the configuration options available to the
current user. Options available within the Manager Home page are determined by the
current user's assigned role(s). The Manager Home page is refreshed every 5
seconds by default.
Operational Status. The Operational Status page displays the status of Manager,
database, and any deployed Sensors; including all system faults.
4
Page 13

McAfee® Network Security Platform 6.0
Configure. The Configure page provides all system configuration options, and facilitates
the configuration of your devices - Sensors and NTBA Appliances, failover pairs of
Sensors, administrative domains, users, roles, Network Access Control (NAC), attack
policies and responses, user-created signatures, and system reports. Access to
various activities, such as user management, system configuration, or policy
management is based on the current user's role(s) and privileges.
Threat Analyzer. The Threat Analyzer page displays the hosts detected on your network
as well as the detected security events that violate your configured security policies.
The Threat Analyzer provides powerful drill-down capabilities to enable you to see all
of the details on a particular alert, including its type, source and destination
addresses, and packet logs where applicable.
Reports. You can generate reports for the security events detected by the system and
reports on system configuration. Reports can be generated manually or automatically,
saved for later viewing, and/or e-mailed to specific individuals.
Other key features of Manager include:
About Network Security Platform
The
Incident Generator: The Incident Generator enables creation of attack incident
conditions, which, when met, provide real-time correlative analysis of attacks. Once
incidents are generated, view them using the Incident Viewer, which is within the Threat
Analyzer.
For more information on Manager components, see
Manager Server Configuration Guide.
Integration with other McAfee products: You can integrate Network Security Platform
with other McAfee products to provide you with a comprehensive network security
solution.
McAfee ePolicy Orchestrator: McAfee ePolicy Orchestrator (ePO) is a scalable
platform for centralized policy management and enforcement of your system
security products such as, anti-virus, desktop firewall, and anti-spyware
applications. You can integrate McAfee Network Security Platform with ePO 4.0.
The integration enables you to query the ePO server from the Manager for viewing
details of a network host.
McAfee Host Intrusion Prevention: McAfee Host Intrusion Prevention (HIP) is a host-
based intrusion prevention system that prevents external and internal attacks on the
hosts in the network, thus protecting services and applications running on them.
Network Security Platform integrates with McAfee Host Intrusion Prevention version
7.0.
McAfee Network Access Control: Using Network Security Sensors, you can enforce
network access control (NAC) based on system health, user identity, or both. For
system-health-based NAC, the Sensors depend on McAfee Network Access
Control (McAfee NAC) for posture assessment. You need to configure ePO
configuration details at the admin domain level and then install the trust between a
Sensor and the ePO Server on which McAfee NAC is installed. This enables the
Sensor to communicate with McAfee NAC to get host details and also to notify
McAfee NAC about hosts sending unwanted traffic on the network.
McAfee Vulnerability Manager: Vulnerability assessment is an automated process of
pro-actively identifying vulnerabilities of computing systems in a network to
determine security threats in the network. Network Security Platform integrates with
McAfee Vulnerability Manager to enable import of the Vulnerability Manager scan
data into the Manager, to provide automated updating of IPS-event data relevancy.
You can also initiate a Vulnerability Manager on-demand scan of a single or group
of IP addresses directly from the Threat Analyzer console. This provides a simple
way for security administrators to access near real-time updates of host vulnerability
details, and improved focus on critical events.
5
Page 14

McAfee® Network Security Platform 6.0
McAfee Artemis: Network Security Platform integrates with McAfee Artemis
technology, which is an Internet-based service that provides active malware
detection in an Internet cloud. Network Security Sensors use McAfee Artemis to
provide real-time malware detection and protection for users during file downloads
from the Internet. Network Security Platform also provides users the option to
upload Custom Fingerprints that can be used for malware detection.
McAfee Global Threat Intelligence: McAfee Global Threat Intelligence (GTI) is a global
threat correlation engine and intelligence base of global messaging and
communication behavior; including reputation, volume, trends, email, web traffic
and malware. By having McAfee Global Threat Intelligence integration, you can
report, filter, and sort hosts involved in attacks based on their network reputation
and the country of the attack origin.
For more information on all the above mentioned integration options, see
Integration Guide.
Integration with third-party products: Network Security Platform enables the use of
multiple third-party products for analyzing faults, alerts, and generated packet logs.
Fault/Alert forwarding and viewing: You have the option to forward all fault
management events and actions, as well as IPS alerts to a third-party application.
This enables you to integrate with third-party products that provide trouble ticketing,
messaging, or any other response tools you may wish to incorporate. Fault and/or
alert forwarding can be sent to the following ways:
- Syslog Server: forward IPS alerts and system faults
- SNMP Server (NMS): forward IPS alerts and system faults
- Java API: forward IPS alerts
- Crystal Reports: view alert data from database via email, pager, or script
Packet log viewing: view logged packets/flows using third-party software, such as
Ethereal.
About Network Security Platform
Manager database
The Manager server operates with an RDBMS (relational database management system)
for storing persistent configuration information and event data. The compatible database is
MySQL (current version 5.1.47).
The Manager server for Windows (only) includes a MySQL database that can be installed
(embedded) on the target Windows server during Manager software installation.
Your MySQL database can be tuned on-demand or by a set schedule via Manager user
interface configuration. Tuning promotes optimum performance by defragmenting split
tables, re-sorting and updating indexes, computing query optimizer statistics, and checking
and repairing tables.
To graphically administrate and view your MySQL database, you can download the
MySQL administrator from the MySQL Web site http://dev.mysql.com/downloads/gui-tools.
McAfee Update Server
For your Network Security Platform to properly detect and protect against malicious
activity, the Manager and Sensors must be frequently updated with the latest signatures
and software patches available. Thus, the Network Security Platform team constantly
researches and develops performance-enhancing software and attack-detecting
6
Page 15

McAfee® Network Security Platform 6.0
signatures that combat the latest in hacking, misuse, and denials of service (DoS). When a
severe-impact attack happens that cannot be detected with the current signatures, a new
signature update is developed and released. Since new vulnerabilities are discovered
regularly, signature updates are released frequently.
New signatures and patches are made available to customers via McAfee
Security Update Server (Update Server). The Update Server is a McAfee owned and
operated file server that houses updated signature and software files for Managers and
Sensors in customer installations. The Update Server securely provides fully automated,
real-time signature updates without requiring any manual intervention.
Note: Communication between the Manager and the Update Server is SSL-
secured.
Configuring software and attack signature updates
You configure interaction with the Update Server using the Manager Configure > Update Server
page. You can pull updates from the Update Server on demand or you can schedule
update downloads. With scheduled downloads, the Manager polls the Update Server (over
the Internet) at the desired frequency. If an update has been posted, that update is
registered as “Available” in the Manager interface for on-demand downloaded. Once
downloaded to the Manager, you can immediately download (via an encrypted connection)
the update to deployed Sensors or deploy the update based on a Sensor update schedule
you define. Acceptance of a download is at the discretion of the administrator.
About Network Security Platform
®
Network
You have a total of five update options:
Automatic update to Manager, manual update from Manager to Sensors. This option enables
Manager server to receive updates automatically, but allows the administrator to
selectively apply the updates to the Sensors.
Manual update to Manager, automatic update from Manager to Sensors. This option enables the
administrator to select updates manually, but once the update is selected, it is applied
to the Sensors automatically, without reboot.
Fully manual update. This option allows the security administrator to determine which
signature update to apply per update, and when to push the update out to the
Sensor(s). You may wish to manually update the system when you make some
configuration change, such as updating a policy or response.
Fully automatic update. This option enables every update to pass directly from the Update
Server to the Manager, and from the Manager to the Sensor(s) without any
intervention by the security administrator. Note that fully automatic updating still
happens according to scheduled intervals.
Real-time update. This option is similar to fully automatic updating. However, rather than
wait for a scheduled interval, the update is pushed directly from Update Server to
Manager to Sensor. No device needs to be rebooted; the Sensor does not stop
monitoring traffic during the update, and the update is active as soon as it is applied to
the Sensor.
7
Page 16

C HAPTER 2
About Network Security Central Manager
McAfee® Network Security Platform [formerly McAfee® IntruShield®] provides a centralized,
“manager of managers” capability, named McAfee
McAfee Network Security Central Manager (Central Manager) allows users to create a
management hierarchy that centralizes policy creation, management, and distribution
across multiple McAfee® Network Security Managers. For example, a policy can be
created in the Central Manager and synchronized across all McAfee Network Security
Managers (Managers) added to that Central Manager. This avoids manual customization
of policy at every Manager.
The Central Manager provides you with a single sign-on mechanism to manage the
authentication of global users across all Managers. McAfee® Network Security Sensor
configuration and threat analysis tasks are performed at the Manager level.
®
Network Security Central Manager.
8
Page 17
C HAPTER 3
Preparing for the Manager installation
software requirements and pre-installation tasks you should perform prior to installing the
software.
This section describes the McAfee® Network Security Manager (Manager) hardware and
Unless explicitly stated, the information in this chapter applies to both the McAfee
®
Network Security Central Manager and Manager though the sections refer to Manager.
Pre-requisites
The following sections list the Manager installation and functionality requirements for your
operating system, database, and browser.
Caution: We strongly recommend that you also check the corresponding Release
Notes. If you are installing the Manager as part of an upgrade to the latest version of
Network Security Platform, refer to
General settings
McAfee recommends you use a dedicated server, hardened for security, and placed
on its own subnet. This server should not be used for programs like instant messaging
or other non-secure Internet functions.
You must have
the Manager software, as well as the installation of an embedded MySQL database
for Windows Managers during Manager installation.
It is essential that you synchronize the time on the Manager server with the current
time. To keep time from drifting, use a timeserver. If the time is changed on the
Manager server, the Manager will lose connectivity with all McAfee
Sensors (Sensors) and the McAfee
Update Server] because SSL is time sensitive.
If Manager Disaster Recovery (MDR) is configured, ensure that the time difference
between the Primary and Secondary Managers is less than 60 seconds. (If the spread
between the two exceeds more than two minutes, communication with the Sensors
will be lost.
Administrator/root privileges on your Windows server to properly install
Network Security Platform 6.0 Upgrade Guide.
®
®
Network Security Update Server [formerly IPS
Network Security
Tip: For more information about setting up a time server on Windows Server 2003
SP2, see the following Microsoft KnowledgeBase article:
http://support.microsoft.com/kb/816042
Note: Once you have set your server time and installed the Manager, do not change
the time on the Manager server for any reason. Changing the time may result in
errors that could lead to loss of data.
http://support.microsoft.com/kb/816042//.
9
Page 18
McAfee® Network Security Platform 6.0
Other third-party applications
Install a packet log viewing program to be used in conjunction with the Threat Analyzer
interface. Your packet log viewer, also known as a protocol analyzer, must support library
packet capture (libpcap) format. This viewing program must be installed on each client you
intend to use to remotely log onto the Manager to view packet logs.
Wireshark (formerly known as Ethereal) is recommended for packet log viewing. WireShark is a
network protocol analyzer for Windows servers that enables you to examine the data
captured by your Sensors. For information on downloading and using Ethereal, go to
www.wireshark.com
Browser display settings (Windows)
The Manager is viewed via a client browser. Only Windows XP SP2 and Windows 7
clients are supported using Internet Explorer 7.0 or 8.0.
Set your display to 32-bit or higher by selecting
Setting
, and configuring the “Colors” field to True Color (32bit).
McAfee recommends setting your monitor’s “Screen Area” to
1024 x 768 pixels. This can be done by changing the display settings at:
Start > Settings > Control Panel > Display > Settings.
When working with the Manager using Internet Explorer, your browser should check
for newer versions of stored pages. By default, Internet Explorer is set to automatically
check for newer stored page versions. To check this function, open your IE browser
and go to
Internet files,” and under “Check for newer versions of stored pages:” select any of the
four choices except for Never. Selecting Never will cache Manager interface pages that
require frequent updating, and not refreshing these pages may lead to system errors.
Preparing for the Manager installation
. http://www.wireshark.org
Start > Settings > Control Panel > Display >
Tools > Internet Options > General, click the Settings button under “Temporary
Server requirements
The following are the system requirements for a Manager server running with a MySQL
database.
Component Minimum Recommended
OS
Memory
Any one of the following:
Windows Server 2003 Standard Edition,
SP2 (32 or 64 bit), English OS
Windows Server 2008 R2 Standard
Edition, (64 bit), English OS
Windows Server 2003 R2 (Standard
Edition), Japanese OS (32 or 64 bit)
Windows Server 2008 R2 (Standard
Edition), Japanese OS (64 bit)
Note: For 64-bit, only X64 architecture is
supported.
2GB or higher for 32-bit
4GB or higher for 64-bit
Windows Server 2008
R2 Standard Edition,
English or Japanese OS,
(64 bit)
4GB
10
Page 19
McAfee® Network Security Platform 6.0
Component Minimum Recommended
CPU
Disk space
Network
Monitor
Hosting the Manager on a VMware platform
The following are the system requirements for hosting Manager server on a VMware
platform.
Component Minimum Recommended
Preparing for the Manager installation
Server model processor such as Intel Xeon Same
40GB 80GB disk with 8MB
memory cache
100Mbps card 10/100/1000Mbps card
32-bit color, 1024 x 768 display setting 1280 x 1024
OS
Any one of the following:
Windows Server 2003 Standard Edition,
Same as the minimum
requirement
SP2 (32 or 64 bit), English OS
Windows Server 2008 R2 Standard Edition,
(64 bit), English OS
Windows Server 2003 R2 (Standard
Edition), Japanese OS (32 or 64 bit)
Windows Server 2008 R2 (Standard
Edition), Japanese OS (64 bit)
Note: For 64-bit, only X64 architecture is
supported.
Memory
Virtual CPUs
Disk Space
2GB 2GB or higher
2 2 or more
40GB 80GB
The following are the system requirements for hosting Manager server on a VMware
platform such as Dell Powered Edge 1950.
Component Minimum
Virtualization software VMWare ESX Server Version 3.5.0 Update 3 Build
123630
Virtual Infrastructure
Client
CPU Intel Xeon ® CPU ES 5335 @ 2.00GHz; Physical
Memory Physical Memory: 16GB
Internal Disks 364.25 GB
Version 2.5.0 Build 19826
Processors – 2; Logical Processors – 8; Processor
Speed – 2.00GHz.
11
Page 20
McAfee® Network Security Platform 6.0
Manager installation with Local Service account privileges
The Manager installs the following services as a Local Service:
McAfee Network Security Manager
McAfee Network Security Manager Database
McAfee Network Security Manager User Interface (Apache)
Preparing for the Manager installation
Note: McAfee Network Security Manager Watchdog runs as a
Local System to
facilitate restart of the Manager in case of abrupt shutdown.
The Local Service account has fewer privileges on accessing directories and resources than
the
Local System. By default, the Manager installation directory and database directory are
granted full permission to the
Local Service account during installation or upgrade of
Manager.
Set the permissions to a
Local Service as needed in the following scenarios:
Backup directory location: If the backup directory was different from the Network
Security Manager installed directory before upgrade to the current release, full
permission on these directories for a
Local Service should be granted.
Notification script execution: If a user uses a script that accesses directories or
resources located in directories other than in Network Security Manager installed
directories for notifications like alerts, faults etc.,full permission on these directories for
a
Local Service should be granted.
Database configuration: If a user has a MySQL database configured for using a
directory for temporary files other than the one provided during installation, then those
directories should be given full permissions for a Local Service.
Client requirements
The following are the system requirements for client systems connecting to the Manager
application.
Component Minimum
OS Any one of the following:
Memory 1GB. Recommended is 2GB.
Browser Internet Explorer (IE) 7.0 or 8.0 (only 32 bit IE is supported)
Monitor 32-bit color, 1024x768 display
Java runtime engine requirements
When you first log onto the Manager, a version of JRE is automatically installed on the
client machine (if it is not already installed). This version of the JRE software is required for
operation of various components within Manager including the Threat Analyzer and the
Custom Attack Editor.
Windows XP (Standard Edition) SP2
Windows 7
12
Page 21

McAfee® Network Security Platform 6.0
Database requirements
The Manager requires communication with MySQL database for the archiving and retrieval
of data.
The Manager installation set includes a MySQL database for installation (that is,
embedded on the target Manager server). You must use one of the supported OS listed
under Server requirements (on page 10
supplied version of MySQL (currently 5.1.47). The MySQL database
Manager.
Note: If you have a MySQL database previously installed on the target server,
uninstall the previous version and install the Network Security Platform version.
Pre-installation recommendations
These McAfee® Network Security Platform [formerly McAfee® IntruShield®] pre-installation
recommendations are a compilation of the information gathered from individual interviews
with some of the most seasoned McAfee Network Security Platform System Engineers at
McAfee.
Preparing for the Manager installation
) and must use the Network Security Platform-
must be dedicated to the
Planning for installation
Before installation, ensure that you complete the following tasks:
®
The server, on which McAfee
should be configured and ready to be placed online.
You must have administrator privileges for McAfee Network Security Manager
(Manager) server.
This server should be dedicated, hardened for security, and placed on its own subnet.
This server should not be used for programs like instant messaging or other nonsecure Internet functions.
Make sure your hardware requirements meet the requirements. See Server
requirements (on page 10
Ensure the proper static IP address has been assigned to the Manager server. For the
Manager server, McAfee strongly recommends assigning a static IP against using
DHCP for IP assignment.
If applicable, configure name resolution for the Manager.
Ensure that all parties have agreed to the solution design, including the location and
mode of all McAfee
®
Network Security Sensor, the use of sub-interfaces or interface
groups, and if and how the Manager will be connected to the production network.
Get the required license file and grant number. Note that you do not require a license
file for using Manager/Central Manager version 6.0.7.5 or above.
Accumulate the required number of wires and (supported) GBICs, SFPs, or XFPs.
Ensure these are approved hardware from McAfee or a supported vendor. Ensure
that the required number of Network Security Platform dongles, which ship with the
McAfee Network Security Sensors (Sensors), are available.
Crossover cables will be required for 10/100 or 10/100/1000 monitoring ports if they
are directly connected to a firewall, router, or end node. Otherwise, standard patch
cables are required for the Fast Ethernet ports.
Network Security Manager software will be installed,
).
13
Page 22
McAfee® Network Security Platform 6.0
If applicable, identify the ports to be mirrored, and someone who has the knowledge
and rights to mirror them.
Allocate the proper static IP addresses for the Sensor. For the Sensors, you cannot
assign IPs using DHCP.
Identify hosts that may cause false positives, for example, HTTP cache servers, DNS
servers, mail relays, SNMP managers, and vulnerability scanners.
Functional requirements
Following are the functional requirements to be taken care of:
Install Wireshark (formerly known as Ethereal http://www.wireshark.com
http://www.wireshark.org) on the client PCs. Ethereal is a n
for Unix and Windows servers, used to analyze the packet logs created by Sensors.
Ensure the correct version of JRE is installed on the client system, as described in the
Release Notes. This can save a lot of time during deployment.
Determine a way in which the Manager maintains the correct time. To keep time from
drifting, for example, point the Manager server to an NTP timeserver. (If the time is
changed on the Manager server, the Manager will lose connectivity with all Sensors
and the McAfee
If Manager Disaster Recovery (MDR) is configured, ensure that the time difference
between the Primary and Secondary Managers is less than 60 seconds. (If the spread
between the two exceeds more than two minutes, communication with the Sensors
will be lost.)
If you are upgrading from a previous version, we recommend that you follow the
instructions in the respective version’s release notes or, if applicable, the
Guide
.
Preparing for the Manager installation
etwork protocol analyzer
®
Network Security Update Server because SSL is time sensitive.)
Upgrade
Using anti-virus software with the Manager
If you plan to install anti-virus software such as McAfee VirusScan on the Manager, be
sure the MySQL directory and its sub-directories are excluded from the anti-virus scanning
processes. For example selecting ...\Manager\MySQL and its subdirectories will exclude the
entire MySQL installation directory from the anti-virus scanning processes. Otherwise,
Network Security Platform packet captures may result in the deletion of essential MySQL
files.
Also exclude the Network Security Platform installation directory and its sub-directories
because temporary files are created there that might conflict with the anti-virus scanner.
Note: If you install McAfee VirusScan 8.5.0i on the Manager after the installation of
the Manager software, the MySQL scanning exceptions will be created
automatically, but the Network Security Platform exceptions will not.
McAfee VirusScan and SMTP notification
From 8.0i, VirusScan includes an option (enabled by default) to block all outbound
connections over TCP port 25. This helps reduce the risk of a compromised host
propagating a worm over SMTP using a homemade mail client.
14
Page 23

McAfee® Network Security Platform 6.0
VirusScan avoids blocking outbound SMTP connections from legitimate mail clients, such
as Outlook and Eudora, by including the processes used by these products in an exclusion
list. In other words, VirusScan ships with a list of processes it will allow to create outbound
TCP port 25 connections; all other processes are denied that access.
The Manager takes advantage of the JavaMail API to send SMTP notifications. If you
enable SMTP notification and also run VirusScan 8.0i or above, you must therefore add
java.exe to the list of excluded processes. If you do not explicitly create the exclusion
within VirusScan, you will see a Mailer Unreachable error in the Manager Operational Status
to each time the Manager attempts to connect to its configured mail server.
To add the exclusion, follow these steps:
Preparing for the Manager installation
1 Launch the
2 Right-click the task called
VirusScan Console.
Access Protection and choose Properties from the right-click
menu.
3 Highlight the rule called
4 Click
Edit.
5 Append java.exe to the list of
6 Click
OK to save the changes.
Prevent mass mailing worms from sending mail.
Processes to Exclude.
User interface responsiveness
The responsiveness of the user interface, the Threat Analyzer in particular, has a lasting
effect on your overall product satisfaction.
In this section we suggest some easy but essential steps, to ensure that Network Security
Platform responsiveness is optimal:
During Manager software installation, use the recommended values for memory and
connection allocation.
You will experience better performance in your configuration and data forensic tasks
by connecting to the Manager from a browser on a client machine. Performance may
be slow if you connect to the Manager using a browser on the server machine itself.
Perform monthly or semi-monthly database purging and tuning. The greater the
quantity of alert records stored in the database, the longer it will take the user
interface to parse through those records for display in the Threat Analyzer. The
default Network Security Platform settings err on the side of caution and leave alerts
(and their packet logs) in the database until the user explicitly decides to remove
them. However, most users can safely remove alerts after 30 days.
Caution: It is imperative that you tune the MySQL database after each purge
operation. Otherwise, the purge process will fragment the database, which can
lead to significant performance degradation.
Defragment the disks on the Manager on a routine basis, with the exception of the
MySQL directory. The more often you run your defragmenter, the quicker the process
will be. Consider defragmenting the disks at least once a month.
Warning: Do NOT attempt to defragment the MySQL directory using an O/S
defrag utility. To defragment MySQL tables, use a MySQL-specific utility,
myisamchk available in the <mysqlinstallation>\bin directory.
Limit the quantity of alerts to view when launching the Threat Analyzer. This will
reduce the total quantity of records the user interface must parse and therefore
potentially result in a faster initial response on startup.
15
Page 24

McAfee® Network Security Platform 6.0
When scheduling certain Manager actions (backups, file maintenance, archivals,
database tuning), set a time for each that is unique and is a minimum of an hour
after/before other scheduled actions. Do not run scheduled actions concurrently.
Downloading the Manager/Central Manager executable
You need to download the version of the Manager or Central Manager that you want to
install. You need to download it from the McAfee Update Server.
1 Keep the following information handy before you begin the installation process. You
must have received the following from McAfee via email.
Grant Number and Password – If you have not received your credentials, contact
McAfee Technical Support [http://mysupport.mcafee.com/]
2 Close all open applications.
3 Go to McAfee Update Server [https://menshen.intruvert.com/] and log on, using the
Grant Number and Password.
4 Go to
5 Download the zip and extract the setup file.
Manager Software Updates > <required version number> folder and select the required
Manager software version.
Preparing for the Manager installation
16
Page 25

C HAPTER 4
Installing the Manager/Central Manager
This section contains installation instructions for the McAfee® Network Security Manager
(Manager) software on your Windows server, including the installation of a MySQL
database. Unless explicitly stated, the information in this chapter applies to both the
McAfee
Manager.
Caution: Close all open programs, including email, the
window, and instant messaging to avoid port conflicts. A port conflict may cause the
Manager program to incur a BIND error on startup, hence failing initialization.
Close any open browsers and restart your server after installation is complete. Open
browsers may be caching old class files and cause conflicts.
IIS (Internet Information Server) and PWS (Personal Web Server) must be disabled or
uninstalled from the target server.
The following are the high-level steps for installing and starting the Manager:
1 Prepare your target server for Manager software installation. See Preparing for
2 Install the Manager software. See Installing the Manager (on page 17).
3 Start the Manager program. During initial client login from the Manager server or a
®
Network Security Central Manager and Manager though the sections refer to
Administrative Tools > Services
installation (on page 9).
client machine, Java runtime engine software (provided) must be installed for proper
program functionality. See Starting the Manager software (on page 30
).
Installing the Manager
The steps presented are for installation of theManager/ Central Manager software. The
installation procedure prompts you to submit program and icon locations, including the
location and access information of your database. Please read each step carefully before
proceeding to the next.
Note 1: Ensure that the Pre-requisites (on page 9
server has been prepared before commencing installation.
Note 2: You can exit the setup program by clicking Cancel in the setup wizard. Upon
cancellation, all temporary setup files are removed, restoring your server to its same
state prior to installation.
Note 3: After you complete a step, click
installation process.
Note 4: Unless specified during installation, Network Security Manager is installed
by default.
) have been met and your target
Next; click Previous to go one step back in the
17
Page 26

McAfee® Network Security Platform 6.0
Note 5: The Installation Wizard creates the default folders based on the Manager
Type you are installing. For example, for a first-time installation of Network Security
Manager, the default location is C:\Program Files\McAfee\Network Security
Manager\App. For Network Security Central Manager, it is C:\Program
Files\McAfee\Network Security Central Manager\App. Similarly, the Wizard creates
default folders for the MySQL database as well. For the sake of explanation, this
section mentions only the folder paths for Network Security Manager unless it is
necessary to mention the path for Network Security Central Manager.
Note 6: This note is relevant if you are installing the Central Manager or the
Manager on a 64-bit OS. Before you begin to install, make sure the Windows
Regional and Language Options are configured accordingly. For example, if you are
installing it on Windows Server 2003 R2 (Standard Edition), Japanese 64 bit OS,
ensure that the Windows Regional and Language Options are configured for
Japanese. If not, the Installation Wizard will treat the server as a 32-bit machine.
Note 7: When you upgrade to or install Manager 6.0.7.x or above, it is automatically
integrated with McAfee Global Threat Intelligence to send your alert, general setup,
and feature usage data to McAfee for optimized protection. If you do not wish to
send these data, then disable the integration with Global Threat Intelligence.
However, note that to be able to query TrustedSource for information on the source
or target host of an attack, you need to send at least your alert data summary to
McAfee. For details, see the
Integration Guide.
Installing the Manager/Central Manager
1 Log onto your Windows server as Administrator and close all open programs.
2 Run the Manager executable file that you downloaded from the McAfee Update
Server. The Installation Wizard starts with an introduction screen.
For information on downloading the executable, see Downloading the
Manager/Central Manager executable (on page 16
).
Figure 1: Manager Installation Wizard - Welcome screen
18
Page 27

McAfee® Network Security Platform 6.0
3 Confirm your acknowledgement of the License Agreement by selecting “I accept the
terms of the License Agreement.” You will not be able to continue the installation if
you do not select this option.
Figure 2: Manager Installation Wizard - License Agreement
Installing the Manager/Central Manager
4 Select the Manager type to choose installation of either Network Security Manager or Network
Security Central Manager
.
For an upgrade, Network Security Manager or Network Security Central Manager is
displayed accordingly which you cannot change.
Figure 3: Select Manager type
Note: The Network Security Central Manager once installed cannot be
converted to Network Security Manager and vice versa.
19
Page 28

McAfee® Network Security Platform 6.0
5 Choose a folder where you want to install the Manager software.
For a first-time installation, the default location is C:\Program Files\McAfee\Network
Security Manager\App. For an upgrade, it is the same location as that of the earlier
version.
Restore Default Folder: resets the installation folder to the default location.
Choose: Browse to a different location.
Caution: Installing the Manager software on a network-mapped drive may
result in improper installation.
The Manager software cannot be installed to a directory path containing special
characters such as a comma (,), equal sign (=), or pound sign (#).
Installing the Manager/Central Manager
Figure 4: Manager Installation Wizard - Choose Install Folder
6 Choose a location for the Manager shortcut icon:
On the Start Menu
On the Desktop
On the Quick Launch Bar
Create Icons for All Users
You can include or remove multiple options by using the the relevant check boxes.
Create Icons for All Users is applicable only for creating product icons for
Note:
Start Menu and Desktop.
20
Page 29

McAfee® Network Security Platform 6.0
Figure 5: Manager Installation Wizard - Choose Shortcut Folder
7 Set the following:
Database Type is displayed as MySQL.
You must use only the MySQL bundled with the Manager installation file. rovide
the database connection information as follows:
Database Name: Type a name for your database. It is recommended you keep the
default entry of “
Database User: Type a user name for database-Manager communication; this
account name is used by the Manager. This account enables communication
between the database and the Manager. When typing a user name, observe the
following rules:
- The MySQL database user name can be a combination of alphabets [both
uppercase (A-Z) and lowercase (a-z)], numbers [0-9] and/or, special characters
like "~ ` ! @ # $ % - * _ + [ ] : ; , ( ) ? { }".
- The first character must be a letter.
- Do not use null or empty characters.
- Do not use more than 16 characters.
Database Password: Type a password for the database-Manager communication
account. This password relates to the
- The MySQL database password can be a combination of alphabets [both
uppercase (A-Z) and lowercase (a-z)], numbers [0-9] and/or, special characters
like "~ ` ! @ # $ % - * _ + [ ] : ; , ( ) ? { }".
- Do not use null or empty characters.
Important: This password is
the root password is added/entered in Step 9.
MySQL Installation Directory: Type or browse to the absolute location of your selected
Manager database. For a first-time installation, the default location is: C:\program
files\McAfee\Network Security Manager\MySQL. For upgrades, the default location
is the previous installation directory. You can type or browse to a location different
from the default. However, the database must be on the same server as the
Manager.
Installing the Manager/Central Manager
lf” intact.
Database User account.
not the root password for database management;
21
Page 30

McAfee® Network Security Platform 6.0
Figure 6: Manager Installation Wizard - Customize Installation
8 Click Next.
Note: If you are creating a new database, Network Security Platform will ask
you, through a pop-up window, to confirm that you really want to create a new
database. Click
Continue to continue with the installation.
Installing the Manager/Central Manager
Figure 7: New MySQL Installation
9 Type the root password for your database. If this is the initial installation, type a root
password and then type it again to confirm. The
root access configuration privileges for your MySQL database.
- Use a combination of alphabets [both uppercase (A-Z) and lowercase (a-z)],
numbers [0-9] and/or, special characters like "~ ` ! @ # $ % - * _ + [ ] : ; , ( ) ? { }".
- Do not use null or empty characters.
Tip: For security reasons, you can set a
MySQL Root Password that is different
from the Database Password in Step 7.
22
MySQL Root Password is required for
Page 31

McAfee® Network Security Platform 6.0
Figure 7: My SQL Root Password
10 Click Next.
Installing the Manager/Central Manager
Figure 8: Manager Installation Wizard - specify RAM usage
Note: Make sure the OS version displayed in the Customize Installation page of
the Wizard is correct. If your server is 64-bit and if the OS Version displays as
32-bit then you may not have set the Windows Regional and Language Options
to match the language of the OS. For example, if it is a Japanese OS, then you
must have configured the Regional and Language Options for Japanese. You
can access the Regional and Language Options dialog from the Windows
Control Panel. If the OS version is incorrect, then you must abort the Manager
installation, change the Regional and Language Options accordingly, and then
begin the installation again.
23
Page 32

McAfee® Network Security Platform 6.0
11 Enter a value to set Actual Maximum RAM Usage. The RAM size indicated here
determines the recommended amount of program memory (virtual memory) to
allocate for server processes required by Network Security Platform.
Since Jboss memory uses hard-disk-based memory (program memory), the total
amount of both can exceed the Manager server’s RAM memory size.
Both 32-bit and 64-bit versions of Windows Server 2003 (SP2) English are supported.
For Japanese, Windows Server 2003 R2 (Standard Edition), (both 32 bit and 64 bit if
the Central Manager/Manager version is 5.1.11.x or above; for all other 5.1, only 32
bit)
Note:
For 32-bit, the Recommended Maximum RAM Usage is 1170 MB and the Actual
Maximum RAM Usage
For 64-bit, the
2 or 1170 MB - whichever is greater. The
between 512 MB up to the
12 Set the following (applicable only Network Security Manager):
Number of Sensors: Select the numbers of McAfee
(Sensors) to be managed by this installation of the Manager.
Actual Maximum DB connections: Enter the maximum number of simultaneous
connections database connections allowed from the Manager. The default is 40.
The recommended number indicated above is based on the Number of Sensors.
Installing the Manager/Central Manager
can be between 512 and 1170 MB.
Recommended Maximum RAM Usage is Physical Server Memory divided by
Actual Maximum RAM Usage can be
Physical Server Memory size.
®
Network Security Sensors
Figure 9: Selecting the number of sensors
13 If the Manager server has multiple IP addresses, you can specify a dedicated IPv4
and IPv6 address that it should use to communicate with the Sensors.
To specify an IP, select
address from the corresponding list.
Some key points to note:
In the Wizard, the option to specify a dedicated interface is displayed only if the
Manager has more than one IP. When configuring the sensors, you need to
configure the same IP that you specify here as the Manager server IP.
Use a Dedicated Interface? and then select the IPv4 and IPv6
24
Page 33

McAfee® Network Security Platform 6.0
Network Security Platform assumes that all the IP addresses are bound to the
same host name. McAfee recommends that you use a separate system for the
Manager to avoid using multiple host names.
If the Manager has an IPv6 address then you can add Sensors with IPv6
addresses to it.
If an IP address is not displayed in the drop-down list or if a deleted IP address is
displayed, then cancel the installation, restart the server, and re-install the Manager.
Post-installation, if you want to change the dedicated IP that you already
specified, you need to re-install the Manager.
Do not specify a dedicated interface if you plan to use one Manager server for
Sensors deployed in different networks that are not reachable to one another.
Assume that you have a Sensor deployed in the 10.0.10.x network and another
Sensor in 172.16.10.x network and that you wish to manage both these Sensors
using one Manager server. Assume that the Manager server is connected to both
these networks with IP addresses of 10.0.10.10 and 172.16.10.10. Now if you
specify 10.0.10.10 as the dedicated interface during installation, then it will use this
IP address even to communicate with the Sensor in 172.16.10.x, which will fail. So,
for such cases do not specify a dedicated interface. An alternative solution could be
deploying the Manager in a DMZ such that it can communicate with both the
Sensors using the DMZ IP address.
Consider that you want to use one Manager server to manage two Sensors
deployed in two different networks that are reachable to one another. Assume that
the Manager server has two IP addresses - one for each network. In this case, it is
recommended that you configure both the Manager IPs in both the Sensors (using
the set manager secondary ip command) regardless of whether you specify a
dedicated interface or not.
If you plan to configure Manager Disaster Recovery (MDR), then the dedicated IP
address that you choose now must be specified as the peer Manager IP address
during MDR configuration. For example, if this is the secondary Manager, then the
dedicated interface that you choose now must be specified as the peer manager IP
address when configuring MDR on the primary.
Installing the Manager/Central Manager
Figure 10: Selecting the dedicated interface
25
Page 34

McAfee® Network Security Platform 6.0
14 Review the “Pre-Installation Summary” section for accurate folder locations and disk
space requirements. This page lists the following information:
Product Name: shows product as Manager.
Install Folder: the folder you specified in Step 5.
Shortcut Folder: the folder you specified in Step 6.
Manager type: type of Manager being installed.
Database: the type of database being used by Network Security Platform, which is
MySQL.
Database Installation location: the location on your hard drive where the database is to
be located, which you specified in Step 7.
Dedicated Interface: the IPv4 and IPv6 addresses that you specified for Manager-to-
Sensor communication are displayed.
Installing the Manager/Central Manager
Figure 11: Pre-installation Summary
15 Click Install. The Manager software and the MySQL database are installed to your
target server. If upgrading, database information is synchronized during this process.
26
Page 35

McAfee® Network Security Platform 6.0
Figure 12: Installing the Manager
Important: Post-installation, you can check the initdb.log (from the installation
folder) for any installation errors. In case of errors, contact McAfee Support with
initdb.log.
16 A congratulatory message appears upon successful installation.
The Manager Installation Wizard displays the following fields.
a.
For ManagerInstallation, the following fields are displayed:
default Username
default
Check box to Launch the Web-based user interface on exit?
(by default, the check box is enabled).
URL for access web-based user interface.
Password
Installing the Manager/Central Manager
Figure 13: Completing the installation
27
Page 36

McAfee® Network Security Platform 6.0
For Manager Upgradation b.
Check box to
(by default, the check box is enabled).
Figure 14: Upgrade Complete page
URL to access web-based user interface
Launch the Web-based user interface on exit?
Installing the Manager/Central Manager
17 Click Done.
18 Use the shortcut icon that you created to begin using the Manager.
The Manager program opens by default in https mode for secure communication.
19 Type a valid Login ID (default: admin) and Password (default: admin123) for Network
Security Manager and Login ID (default: nscmadmin) and Password (default:
admin123) for Network Security Central Manager.
Upon initial client login, you are required to install Java applications. See Java
installation for client systems (on page 31
20 You can use the Manager Initialization Wizard to complete the basic configuration
steps.
Installing the Central Manager
The installation of the Central Manager is similar to that of Manager. Follow the steps
provided in Installing the Manager (on page 17
During installation, you need to select the Manager type as Network Security Central Manager. By
default,
Network Security Manager is selected.
).
).
28
Page 37

McAfee® Network Security Platform 6.0
Figure 15: Select Manager type
Note: Sensor communication Interface is not present during Central Manager installation.
There can be only one active installation on a Windows machine. Every Central Manager
and Manager installation has its own MySQL database. No centralized database exists in
an Central Manager setup.
Installing the Manager/Central Manager
Note: Central Manager has to be of equal or higher version than the corresponding
Managers.
29
Page 38

C HAPTER 5
Starting the Manager/Central Manager
Network Security Platform, this translates to a Super User role at the root admin domain.
Your actual view of the interface may differ, depending on the role you have been
assigned within Network Security Platform. For example, certain tasks may be unavailable
to you if your role denies you access. If you find you are unable to access a screen or
perform a particular task, consult your Network Security Platform Super User.
Important: For testing purposes, you can access the Manager from the server. For
working with the Manager/Central Manager, McAfee recommends that you access
the server from a client machine. Running the Manager/Central Manager interface
client session on the server can result in slower performance due to program
dependencies, such as Java, which may consume a lot of memory.
To view the Manager/Central Manager interface, do the following:
1 Make sure the following services are running on the Manager server:
McAfee Network Security Manager
McAfee Network Security Manager Database
McAfee Network Security Manager User Interface
McAfee Network Security Manager Watchdog
This section assumes you have permissions granting you access to the software. In
See Manager installation with Local Service account privileges (on page 12
).
If you have installed the Central Manager, then make sure the following services are
running on the Central Manager server:
McAfee Network Security Central Manager
McAfee Network Security Central Manager Database
McAfee Network Security Central Manager User Interface
McAfee Network Security Central Manager Watchdog
2 Open the Manager using the shortcut icon that you created during installation.
The interface opens in an Internet Explorer window in HTTPS mode for secure
communication.
3 To log onto the Manager, see Logging onto Network Security Manager (on page 31
).
Accessing the Manager from a client machine
To access Manager from a client machine:
1 Start your browser (Internet Explorer 7.0 or 8.0) and then type the URL of the
Manager server: https://<hostname or host-IP>
2 To log on to the Manager, see Logging onto Network Security Manager (on page 31).
30
Page 39

McAfee® Network Security Platform 6.0
Java installation for client systems
The Manager software requires Java runtime engine software for some of its components.
When you first log onto the Manager from a client system, you are prompted to download
and install the appropriate version of the JRE software.
You must download and install these programs for proper functioning of the Manager
program.
Logging onto the Manager
Once you have successfully started the Manager service and connected to the server via
an Internet Explorer browser, the
Login page appears.
Starting the Manager/Central Manager
Figure 16: Login Screen
To log onto the Manager:
1 Do one of the following:
For initial login after a new installation:
For Login ID, type admin.
For
Tip: McAfee
password as one of your first operations within Manager.
If you are not the Network Security Platform system administrator/Super User:
Type the
Type the valid
2 Click
When you upgrade to or install Manager 6.0.7.x or above, it is automatically integrated
with McAfee Global Threat Intelligence to send your alert, general setup, and feature
usage data to McAfee for optimized protection. If you do not wish to send these data,
then disable the integration with Global Threat Intelligence. However, note that to be
able to query TrustedSource for information on the source or target host of an attack,
you need to send at least your alert data summary to McAfee. For details, see the
Integration Guide.
Password, type admin123.
strongly recommends that you change the default username and
Login ID supplied to you by your administrator.
Password for the specified Login ID.
Log In or press Enter.
31
Page 40

McAfee® Network Security Platform 6.0
3 The Manager Home page appears as shown in the Network Security Manager Home
page.
During initial login (per client), Network Security Platform prompts you to install the
following:
Security certificate granting the Manager program write access to your client.
Click
Always.
Java runtime engine: You must install this plug-in to view objects in the Manager
Home page and other areas of the Manager program, such as the Threat Analyzer.
You can opt to display your company's logo and accompanying text on the Manager Login
page.For details, see Adding a Log-on Banner,
Logging onto the Central Manager
To log onto the Central Manager:
1 Do one of the following:
For initial logon after a new installation:
For Login ID, type nscmadmin.
For Password, type admin123.
Starting the Manager/Central Manager
Manager Server Configuration Guide.
Figure 17: The Central Manager Login Page
Note1: For upgrades from 5.1 to 6.0, the login ID is the same as it was in 5.1.
Tip: McAfee strongly recommends that you change the default username and
password as one of your first operations within the system.
If you are not McAfee Network Security Platform System administrator/Super User:
Type the
Type the valid
2 Click
Log In or press Enter. The Central Manager Home page appears as shown in
Accessing Central Manager Home page
During initial logon (per client), Network Security Platform prompts you to install the
following:
Security certificate granting the Central Manager program write access to your
client. Click Always.
Login ID supplied to you by your administrator.
Password for the specified Login ID.
32
Page 41

McAfee® Network Security Platform 6.0
Java Runtime Engine: You must install this plug-in to view objects in the Central
Manager Home page and other areas of the Central Manager program, such as the
Custom Attack Editor.
You can opt to display your company's logo and accompanying text on the Central
Manager Login page. For details, see Adding a Logon Banner,
Guide
.
Authenticating Access to the Manager using CAC
Common Access Card (CAC) is a smart card that is used for general identification as well
as authentication of user access to secure networks. CAC holds a unique digital certificate
and user information such as photograph, personal identification number (PIN) and
signature to identify each user. Network Security Platform provides an option of
authentication of users who tried to log onto the Manager based on their smart card
verification.
When a smart card reader is connected to your Manager client, and a user swipes a smart
card, the card reader authenticates if the digital certificate and the user information are
trusted and valid. If the user information is trusted, the client browser retrieves the
certificate from CAC, with the help of the CAC software and sends it to the Manager. The
Manager receives the certificate, verifies if the certificate issued is from a trusted
Certificate Authority (CA). If the certificate is from a trusted CA, a secure session is
established and the user is permitted to log on.
Starting the Manager/Central Manager
Manager Server Configuration
At a high level, authenticating user access to the Manager through CAC can be brought
about by a 4-step process:
Verify the CAC certificate format
Set up user accounts
Enable CAC authentication
Log on to the Manager using CAC
Verifying the CAC certificate format
.pem is the universal standard to read digital certificate files. If your CA certificate is using
other formats such as .cer, you need to convert those to .pem format. To convert a .cer
certificate to .pem format:
1 Open the command prompt, locate the
OpenSSL/bin folder, and execute the following
command:
openssl x509 -in <XXX.cer> -inform DER -out <YYY.pem> -outform
PEM
All the PEM-encoded certificate can be combined into one master CA file, and the
SSLCACertificateFile must contain a list of Root CA’s and intermediary CA’s that are
trusted by the Manager.
Setting up CAC users in the Manager
1 Connect the smart card reader to your Manager client through a USB port.
The smart card reader can be connected to a Manager server, if the server doubles
up as a Manager client.
a Refer the card reader manufacturer's recommendations for the necessary device
drivers to be installed.
33
Page 42

McAfee® Network Security Platform 6.0
b Install the ActivIdentify and ActivClient CAC software on the Manager client.
These software are provided to you along with the card reader device and help
validate the digital certificate and user information stored in the card.
Note: McAfee currently supports integration with smart card reader model
SCR3310 from TxSystems.
2 Insert a card into the card reader.
3 Open the CAC Client software > Smart Card Info > User Name.
The user name is a combination of alphanumeric characters and a few special
characters like "." or spaces. For example, "BROWN.JOHN.MR .0123456789"
4 Log onto the Manager and create a user with the exact same name that is,
"BROWN.JOHN.MR .0123456789".
5 Close the current browser session of the Manager.
Enabling CAC authentication
The CAC authentication feature is disabled by default. It is mandatory to setup the CAC
user accounts, before enabling it.
To enable CAC, do the following:
Note: CAC Authentication can be enabled only through the MySQL command line.
Starting the Manager/Central Manager
1 Log onto the MySQL command line and enter:
update iv_emsproperties set value='TRUE' where
name='iv.access.control.authentication.requireClientCertificate
BasedAuthentication'
2 Perform the following tasks:
Change the corresponding Apache files to enable Client-Authentication:
a.
Apache/conf/iv_ssl.conf –
Uncomment the following lines:
b.
#RewriteRule ^(.*)$ - [E=RedirectPort=444]
#Listen 0.0.0.0:444
c.
SSLCACertificateFile attribute to point to the file containing the trusted CA
Set
Certificates.
In
Apache/conf/iv_ssl_mapping.conf , uncomment the following line:
d.
#RewriteRule ^(.*)$ - [E=RedirectPort=444]
3 Close all client connections.
4 Stop the McAfee Network Security Manager service.
5 Stop the McAfee Network Security Manager User Interface service.
6 Restart both the McAfee Network Security Manager service and the McAfee Network
Security Manager User Interface service.
For details on how to close client connections, stop/ restart the Manager services etc., see
Manager Installation Guide.
Logging onto the Manager using CAC authentication
1 Insert a card into the card reader.
2 Start a fresh browser session for the Manager.
34
Page 43

McAfee® Network Security Platform 6.0
You are prompted to choose a CA certificate.
3 Select the certificate.
You are prompted to enter the PIN.
4 Enter the PIN.
A maximum of 3 attempts is allowed while entering PIN, following which, the user will
be locked out.
If the user name, certificate, and PIN match, you are directly given access to the
Manager Home Page.
Troubleshooting Tips
If the card is not inserted in the card reader, the Manager will not be accessible in this
setup.
When authenticating users through CAC, you do not have to enter your Manager user
name and password while logging on.
If you are locked out after entering invalid PIN, you can use the ActivClient CAC software
to get a new PIN.
If you are unable to view the Manager Login page after CAC authentication has been
enabled, it means that the CAC certificate was NOT signed by a trusted CA listed in
the
SSLCACertificateFile. To remedy the problem, import the relevant CA into the
SSLCACertificateFile trusted CA list.
You have imported the relevant CA into the SSLCACertificateFile trusted CA list, and
yet you are unable to view the Manager Login page, then check whether a firewall is
blocking your access to destination port 444 on the Manager server.
If you are able to view the Manager Login page but are unable to log onto the
Manager, it means that the user name on the CAC card does not match the user
name in the Manager database. To remedy the problem, verify that the user name
on the CAC card exactly matches the Manager user name.
Starting the Manager/Central Manager
Shutting down the Manager/Central Manager services
A proper shutdown of the Manager/Central Manager prevents data corruption by allowing
data transfer and other processes to gracefully end prior to machine shutdown.
Shutting down the Manager
A proper shutdown of the Manager services requires the following steps be performed:
1 Close all client connections. See Closing all client connections to the Manager (on
page 36
2 Stop the McAfee Network Security Manager service.
3 Stop the McAfee Network Security Manager User Interface service.
4 Stop the McAfee Network Security Manager Watchdog service.
5 Stop the McAfee Network Security Manager MySQL service.
Shutting down the Central Manager
A proper shutdown of the Central Manager services requires the following steps be
performed:
).
35
Page 44

McAfee® Network Security Platform 6.0
1 Close all client connections.
2 Stop the McAfee Network Security Central Manager service.
3 Stop the McAfee Network Security Central Manager User Interface service.
4 Stop the McAfee Network Security Central Manager Watchdog service.
5 Stop the McAfee Network Security Central Manager MySQL service.
Note: In a crash situation, the Manager/Central Manager will attempt to forcibly shut
down all its services.
Closing all client connections
The following procedure details the recommended steps for determining which users are
currently logged on to the Manager/Central Manager server. All client-session
configuration and data review should be gracefully closed prior to server shutdown.
1 Log onto the Manager/Central Manager server via a browser session.
2 Click Configure to open the Configuration page.
3 In the Resource Tree, click the Manager node. The Manager Information page opens.
4 Check the
determine which users are logged in.
5 Ask the users to close all Manager windows such as Threat Analyzer and Manager
Home page and log out of all open browser sessions.
Current Application Users section of the Manager Information table to
Starting the Manager/Central Manager
Shutting down using the Network Security Platform system
tray icon
1 Right-click the Manager/Central Manager icon in your System Tray. The icon displays
as an "M" enclosed within a shield.
Figure 18: Network Security Manager in the System Tray
2 Select Stop Network Security Manager Service or Stop Central Manager Service.
Figure 18: Stop Central Manger - Right-click Menu
36
Page 45

McAfee® Network Security Platform 6.0
Once this service is completely stopped, continue to the next step.
3 Go to
4 Open
5 Open
Start > Settings > Control Panel.
Administrative Tools.
Services.
6 Find and select
Manager Database
7 Click the
next step.
McAfee Network Security Manager Database or McAfee Network Security Central
Starting the Manager/Central Manager
in the services list under the “Name” column.
Stop Service button. Once this service is completely stopped, continue to the
Figure 19: Stopping the MySQL Service
8 You can now safely shut down/reboot your server.
Shutting down using the Control Panel
1 Go to Start > Settings > Control Panel.
2 Open
3 Open Services.
4 Select
5 Click the
Administrative Tools.
Network Security Manager Service or Network Security Central Manager Service in the
services list under the “Name” column.
Stop Service button. Once this service is completely stopped, continue to the
next step.
37
Page 46

McAfee® Network Security Platform 6.0
Figure 20: My SQL Services
6 Find and select McAfee Network Security Manager Database or McAfee Network Security Central
Manager Database
7 Click the
next step.
Starting the Manager/Central Manager
in the services list under the “Name” column.
Stop Service button. Once this service is completely stopped, continue to the
Figure 21: Stopping the MySQL Service
8 You can now safely shut down/reboot your server.
38
Page 47

C HAPTER 6
Adding a Sensor
After installing the Manager software and a successful logon session, the next step is to
add one or more Sensors to the Manager. For more information on configuring a Sensor,
see the CLI Guide and Device Configuration Guide.
Before You Install Sensors
This section describes best practices for deployment of McAfee® Network Security
Sensors (Sensors) on your network and is generic to all Sensor appliance models.
Topics include system requirements, site planning, safety considerations for handling the
Sensor, and usage restrictions that apply to all Sensor models.
Sensor specifications, such as physical dimensions, power requirements, and so on are
described in each Sensor model’s Product Guide.
Network topology considerations
Deployment of McAfee® Network Security Platform [formerly McAfee® IntruShield®]
requires basic knowledge of your network to help determine the level of configuration and
amount of installed Sensors and McAfee® Network Security Managers (Managers)
required to protect your system.
The Sensor is purpose-built for the monitoring of traffic across one or more network
segments. For more information on McAfee Network Security Platform, see the Getting
Started Guide
.
Safety measures
Please read the following warnings before you install the product. Failure to observe these
safety warnings could result in serious physical injury.
Warning: Read the installation instructions before you connect the system to its
power source.
Warning: To remove all power from the I-4000 Sensor, unplug all power cords,
including the redundant power cord.
Warning: Only trained and qualified personnel should be allowed to install, replace,
or service this equipment.
Warning: The Network Security Platform 4000 Sensor has no ON/OFF switch. Plug
the Sensor into a power supply ONLY after you have completed rack installation.
39
Page 48

McAfee® Network Security Platform 6.0
Warning: Before working on equipment that is connected to power lines, remove
jewelry (including rings, necklaces, and watches). Metal objects will heat up when
connected to power and ground and can cause serious burns or weld the metal
object to the terminals.
Warning: This equipment is intended to be grounded. Ensure that the host is
connected to earth ground during normal use.
Warning: Do not remove the outer shell of the Sensor. Doing so will invalidate your
warranty.
Warning: Do not operate the system unless all cards, faceplates, front covers, and
rear covers are in place. Blank faceplates and cover panels prevent exposure to
hazardous voltages and currents inside the chassis, contain electromagnetic
interference (EMI) that might disrupt other equipment, and direct the flow of cooling
air through the chassis.
Warning: To avoid electric shock, do not connect safety extra-low voltage (SELV)
circuits to telephone-network voltage (TNV) circuits. LAN ports contain SELV
circuits, and WAN ports contain TNV circuits. Some LAN and WAN ports both use
RJ-45 connectors. Use caution when connecting cables.
Warning: This equipment has been tested and found to comply with the limits for a
Class A digital device, pursuant to Part 15 of the FCC Rules. These limits are
designed to provide reasonable protection against harmful interference when the
equipment is operated in a commercial environment. This equipment generates,
uses, and can radiate radio frequency energy and, if not installed and used in
accordance with the instruction manual, may cause harmful interference to radio
communications. Operation of this equipment in a residential area is likely to cause
harmful interference in which case the user will be required to correct the
interference at his own expense.
Adding a Sensor
Working with fiber-optic ports
Fiber-optic ports (for example, FDDI, OC-3, OC-12, OC-48, ATM, GBIC, and
100BaseFX) are considered Class 1 laser or Class 1 LED ports.
These products have been tested and found to comply with Class 1 limits of IEC
60825-1, IEC 60825-2, EN 60825-1, EN 60825-2, and 21CFR1040.
Warning: To avoid exposure to radiation, do not stare into the aperture of a fiber-
optic port. Invisible radiation might be emitted from the aperture of the port when no
fiber cable is connected.
Usage restrictions
The following restrictions apply to the use and operation of a Sensor:
You may not remove the outer shell of the Sensor. Doing so will invalidate your
warranty.
The Sensor appliance is not a general purpose workstation.
40
Page 49

McAfee® Network Security Platform 6.0
McAfee prohibits the use of the Sensor appliance for anything other than operating
the Network Security Platform.
McAfee prohibits the modification or installation of any hardware or software in the
Sensor appliance that is not part of the normal operation of the Network Security
Platform.
Unpacking the Sensor
To unpack the Sensor:
1 Place the Sensor box as close to the installation site as possible.
2 Position the box with the text upright.
3 Open the top flaps of the box.
4 Remove the accessory box.
5 Verify you have received all parts. These parts are listed on the packing list and in
Contents of the Sensor box (on page 41
6 Pull out the packing material surrounding the Sensor.
7 Remove the Sensor from the anti-static bag.
8 Save the box and packing materials for later use in case you need to move or ship the
Sensor.
Adding a Sensor
), below.
Contents of the Sensor box
The following accessories are shipped in the Sensor box:
One Sensor
One power cord. McAfee provides a standard, 2m NEMA 5-15p (US) power cable (3
wire). International customers must procure a country-appropriate power cable with
specific v/a ratings.
One set of rack mounting ears.
Fail-closed dongles (two for the I-1200, four for the I-1400, six for I-2700).
One printed Quick Start guide.
Release notes.
Cable Specifications
This section lists the specifications for all cables to use with McAfee® Network Security
Sensors (Sensors).
41
Page 50

McAfee® Network Security Platform 6.0
Network Security Platform fail-closed dongle specification
Adding a Sensor
The I-1200 and I-1400 Sensors require the dongle specified in Figure McAfee
Security Platform
Fail-Closed Dongle Specification for all monitoring modes requiring a fail-closed
connection. Configurations requiring the dongle are described in the Sensor
®
Network
Product Guide
chapter on cabling the Sensor.
Figure 22: Fail-Closed Dongle Specification
Console port pin-outs
McAfee supplies a console cable. The specifications for this cable are as follows:
The Console port is pinned as a DCE so that it can be connected to a PC's COM1 port
with a straight-through cable.
Pin # Signal Direction on Sensor
1 DCD Output
2 RXD Output
3 TXD Input
4 DTR Input
5 GND not applicable
6 DSR Output
7 RTS Input
8 CTS Output
9 No Connection Not applicable
Auxiliary port pin-outs
The Auxiliary (Aux) port is pinned as a DTE so that it can be connected to a modem with a
straight-through cable.
Pin # Signal Direction on Sensor
42
Page 51

McAfee® Network Security Platform 6.0
Pin # Signal Direction on Sensor
1 DCD Input
2 RXD Input
3 TXD Output
4 DTR Output
5 GND n/a
6 DSR Input
7 RTS Output
8 CTS Input
9 RI Input
Management port pin-outs
The Management (Mgmt) port uses a Cat 5/Cat 5e cable.
Pin # Signal Direction on Sensor
Adding a Sensor
1 TxD+ Output
2 TxD- Output
3 RxD+ Input
4
These pins are terminated to ground through a 75 ohm
resistor & capacitor.
5
6 RxD- Input
7
These pins are terminated to ground through a 75 ohm
resistor & capacitor.
8
Note: Category 5 Enhanced (Cat 5e) cable is required for transmission speeds up to
1 Gigabit per second (Gigabit Ethernet). For Ethernet networks running at 10 or 100
Mbps, Category 5 (Cat 5) OR Cat 5e cable can be used.
Throughout this guide, cabling specifications will be mentioned as Cat 5/Cat 5e.
Response port pin-outs
The Response ports use Cat 5/Cat 5e cables.
Pin # Signal Direction on Sensor
1 TxD+ Output
2 TxD- Output
3 RxD+ Input
43
Page 52

McAfee® Network Security Platform 6.0
Pin # Signal Direction on Sensor
4
5
6 RxD- Input
7
8
Monitoring port pin-outs
The following ports are relevant go Monitoring port pin-outs.
These pins are terminated to ground through a 75 ohm
resistor & capacitor.
These pins are terminated to ground through a 75 ohm
resistor & capacitor.
Adding a Sensor
Gigabit Ethernet (GE) ports (on page 44
Fast Ethernet (FE) 10/100/1000 ports (on page 44)
)
Gigabit Ethernet (GE) ports
GBIC monitoring ports use cables appropriate for the type of GBIC you choose to use.
This includes cabling for failover between the GBIC ports on two failover Sensors.
Fast Ethernet (FE) 10/100/1000 ports
10/100/1000 monitoring ports use Cat 5/Cat 5e cables. The Sensor's normal mode of
operation, using pins 1&2 and 3&6, is to fail-open—that is, data will continue to pass
through the Sensor allowing continued data flow. In this mode, pins 4&5 are terminated to
ground via 75 ohm and a capacitor.
44
Page 53

McAfee® Network Security Platform 6.0
Pin # Signal Direction on Sensor
1 TxD+ FO (See text above.)
2 TxD- FO
3 RxD+ Input
4 TxD+ FC Reserved for use in the fail-closed
5 TxD- FC
6 RxD- Input
7
8
Configuring a Sensor
This section describes how to configure a McAfee® Network Security Sensor (Sensor).
This information is generic to all Sensor appliance models.
Adding a Sensor
dongle.
These pins are terminated to ground
through a 75 ohm resistor & capacitor.
Note: The information presented in this chapter was developed based on devices in
a specific lab environment. All Sensors used in this document started with a cleared
(default) configuration. If you are working in a live network, please ensure that you
understand the potential impact of any command before using it. For more
information on the available Sensor CLI commands, see the CLI Guide.
Configuration overview
At a high level, the process of configuring the Sensor involves the following steps. Detailed
instructions follow in subsequent sections of this chapter.
1 (Pre-installation) Establish a Sensor naming scheme (on page 45
2 Install and bring up the Sensor. (This information is described in detail in the Product
Guide for each Sensor model.)
3 Add the Sensor to Manager (on page 48
) using the McAfee® Network Security
Manager (Manager) Configuration page.
4 Configuring the Sensor (on page 46
5 Configuring the Sensor (on page 46
) with a unique name and shared key value.
)’s network information (for example, IP address
and netmask, Sensor name, and so on).
6 Verify that the Sensor is on the network. (See Configuring the Sensor (on page 46
7 Verify connectivity between the Manager and the Sensor. (See Verifying successful
configuration (on page 49))
) for your Sensors.
))
Establish a Sensor naming scheme
Once you have configured a Sensor with a name, you will be unable to change the name
without reconfiguring the Sensor. McAfee recommends that you establish an easily
45
Page 54

McAfee® Network Security Platform 6.0
recognizable naming scheme prior to deployment that indicates your Sensors’ locations or
purposes, and which ensures unique names. The Manager will not recognize two Sensors
with identical names.
Sensors are represented by name in several areas of McAfee® Network Security Platform
and its alert data: the Manager Configuration page, alert and configuration reports, and the
Threat Analyzer. Thus, it is a good idea to make your Sensor naming scheme clear
enough to interpret by anyone who might need to work with the system or its data.
For example, if you were deploying Sensors at a university, you might name your Sensors
according to their location on the campus:
Sensor1_StudentUnion, Sensor1_Library
Note: Sensor name is case-insensitive. Do not use case to distinguish between
Sensors; for example, do not use both Sensor1 and Sensor1.
Communication between the Sensor and the Manager
The Sensor initiates all communication with the Manager server until secure
communication is established between the two devices. Later, configuration information is
pushed from Manager to Sensor. The Manager does not poll the network to discover the
Sensor.
Sensor1_WeanHall, Sensor2_WeanHall,
Adding a Sensor
, and so on.
Note: All communication between the Manager and Sensor is secure. Refer to
"KnowledgeBase KB55587" for details.
Configuring the Sensor
At any time during configuration, you can type ? to get help on the Sensor CLI commands.
To see a list of all commands, type commands. These commands are described in the CLI
.
Guide
Note: The first time you configure a Sensor, you must have physical access to the
Sensor.
If you are moving a Sensor to a new environment and wish to wipe the Sensor back to its
factory default settings, start by typing factorydefaults from the CLI. See the
for specific details on the usage of factorydefaults command.
1 Open a hyperterminal session to configure the Sensor. (For instructions on connecting
to the Console port, see the section Cabling the Console Port, in the Product Guide
for your Sensor model.)
2 At the login prompt, log on to the Sensor using the default username admin and
password admin123.
Note 1:
McAfee strongly recommends that you change the default password later for
security purposes as described in Step 9.
Note 2: By default, the user is prompted for configuration set up, immediately
after login. Else, the user can choose to start the setup later from command
prompt using the setup command. For more information, see the
CLI Guide.
CLI Guide
46
Page 55

McAfee® Network Security Platform 6.0
3 Set the name of the Sensor. At the prompt, type:
set sensor name <WORD>
The Sensor name is a case-sensitive alphanumeric character string up to 25
characters. The string can include hyphens, underscores, and periods, and must
begin with a letter.
Example: set Sensor name Engineering_Sensor1
4 Set the IP address and subnet mask of the Sensor. At the prompt, type:
set sensor ip <A.B.C.D> <E.F.G.H>
Specify a 32-bit address written as four eight-bit numbers separated by periods as in
<A.B.C.D>, where A,B,C or D is an eight-bit number between 0-255. <E.F.G.H>
represents the subnet mask.
Example: set sensor ip 192.34.2.8 255.255.255.0
Or
Specify an IPv6 address as given below:
set sensor ipv6 <A:B:C:D:E:F:G:H/I>
where <A:B:C:D:E:F:G:H> is a 64-bit address written as octet (eight groups) of
four hexadecimal numbers, separated by colons. Each group (A,B,C,D etc)
represents a group of hexadecimal numbers between 0000-FFFF. This is followed by
a prefix length I with value between 0 and 128.
Example: set sensor ipv6
2001:0db8:8a2e:0000:0000:0000:0000:0111/64
If one or more four-digit group(s) is 0000, the zeros may be omitted and replaced with
two colons (::)
Example: set sensor ipv6 2001:0db8:8a2e::0111/64
Note: Setting the IP address for the first time—that is, during the initial
configuration of the Sensor—does not require a Sensor reboot. Subsequent
changes to the IP address will, however, require that you reboot the Sensor for
the change to take effect. If a reboot is necessary, the CLI will prompt you to do
so. For information on rebooting, see Conditions requiring a Sensor reboot,
Troubleshooting Guide.
5 If the Sensor is not on the same network as the Manager, set the address of the
default gateway. Note that you should be able to ping the gateway (that is, gateway
should be reachable). At the prompt, type:
set sensor gateway <A.B.C.D>
Use the same convention as the one for Sensor IP address.
Example: set sensor gateway 192.34.2.8
Or
Specify an IPv6 address of the gateway for the Manager server as given below:
set sensor gateway-ipv6 <A:B:C:D:E:F:G:H>
where <A:B:C:D:E:F:G:H> is a 128-bit address written as octet (eight groups) of
four hexadecimal numbers, separated by colons. Each group ( A,B,C,D etc ) is a
group of hexadecimal numbers between 0000-FFFF.
Example: set sensor gateway-ipv6
2001:0db8:8a2e:0000:0000:0000:0000:0111
If one or more four-digit group(s) is 0000, the zeros may be omitted and replaced with
two colons (::)
Example: set sensor gateway-ipv6 2001:0db8:8a2e::0111
6 Set the IPv4 or IPv6 address of the Manager server. At the prompt, type:
set manager ip <A.B.C.D>
Adding a Sensor
47
Page 56

McAfee® Network Security Platform 6.0
Use the same convention as the one for Sensor IP address.
Example: set manager ip 192.34.3.2
Or
Type an IPv6 address of the Manager server, as given below:
set manager ip <A:B:C:D:E:F:G:H>
where <A:B:C:D:E:F:G:H> is a 128-bit address written as octet (eight groups) of
four hexadecimal numbers, separated by colons. Each group ( A,B,C,D etc ) is a
group of hexadecimal numbers between 0000-FFFF.
Example: set manager ip 2001:0db8:8a2e:0000:0000:0000:0000:0111
If one or more four-digit group(s) is 0000, the zeros may be omitted and replaced with
two colons (::)
Example: set manager ip 2001:0db8:8a2e::0111
7 Ping the Manager from the Sensor to determine if your configuration settings to this
point have successfully established the Sensor on the network. At the prompt, type:
ping <manager IP address>
The success message "
If not, type show to verify your configuration information and check to ensure that all
information is correct. If you run into any difficulties, see
8 Set the
shared key value for the Sensor. This value is used to establish a trust
relationship between the Sensor and the Manager.
At the prompt, type:
set sensor sharedsecretkey
The Sensor then prompts you to enter a shared secret key value. Type the shared
secret key value at the prompt. The Sensor then prompts you to verify the value. Type
the value again.
Note: The shared secret key value must be between 8 and 25 characters of
ASCII text. The shared secret key value is case-sensitive. Example:
IPSkey123
host <ip address> is alive " appears.
Troubleshooting Guide.
Adding a Sensor
9 (Optional, but recommended) Change the Sensor password. At the prompt, type:
passwd
The Sensor prompts you to enter the new password and prompts you for the old
password.
A password must be between 8 and 25 characters, is case-sensitive, and can consist
of any alphanumeric character or symbol.
Note: McAfee strongly recommends that you choose a password with a
combination of characters that is easy for you to remember but difficult for
someone else to guess.
10 To exit the session, type exit.
Adding a Sensor to the Manager
Once a Sensor is configured with a name and shared key value, you can add the Sensor
in the Manager
Adding a physically installed and network-connected Sensor to the Manager activates
communication between them.
Configuration page.
48
Page 57

McAfee® Network Security Platform 6.0
Note: The process of installing and connecting a Sensor is described in the Product
Guide for each Sensor model.
The following steps describe how to add a Sensor to the Manager:
1 Start the Manager software.
2 Log on to the Manager (the default username is admin; the default password is
admin123).
3 Click
Configure tab from the Manager Home page.
4 Click on the
5 Click
Figure 23: Add a new sensor
New. The Add New Device form appears.
Device List node and select Device List > Devices.
Adding a Sensor
6 Type the same Device Name you entered on the Sensor.
Caution: The exact same Sensor Name and Shared Secret must also be
entered into the CLI of the Sensor during physical installation. If not, the
Manager will not recognize a Sensor trying to communicate with the Manager.
7 Ensure the selected Sensor type is “ IPS or NAC Sensor”
8 Enter the Shared Secret.
9 Confirm the
10 Select an
11 (Optional) Type the
12 Click
Shared Secret.
Updating Mode as Online or Offline. Online is the default mode.
Contact Information and Location.
Save to begin the Manager-Sensor handshake process, or click Cancel to end the
installation before handshake.
Verifying successful configuration
There are three ways to check that the Sensor is configured and available:
On the
On the
On the
Sensor, type status. (For more information on the status command, see the
CLI Guide.)
Manager, check the Sensor’s Operational Status. (On the Manager Home page, see
Operational Status or click Operational Status tab. If the cell is green, the Sensor is active. If
it is yellow, click on the cell to see details on the Sensor. For more information on this
process, see
Sensor from the
Port Settings
Manager Server Configuration Guide.)
Manager, go to the Configuration page, and select the node representing the
Resource Tree, and then select Device List > Sensor_Name > Physical Device >
. Look at the color of the button(s) representing the ports on the Sensor,
and check the color legend on the screen to see the status of the Sensor’s ports. (For
more information on this process, see
Manager Server Configuration Guide.)
49
Page 58

McAfee® Network Security Platform 6.0
Note: If you have difficulty in troubleshooting the above, see Troubleshooting Guide.
Also, see CLI Guide for a description of all available CLI commands.
Changing Sensor values
Changing certain values on the Sensor, like the Sensor’s name or Sensor IP address,
require you to “break trust” between the Sensor and the Manager before you make the
change, and then re-establish the communication with the Manager. Essentially, the
Manager knows the Sensor by a specific set of information; if you want to change any of it,
you must re-establish the communication with the Manager.
Changing any of these values requires you to “break trust” with the Manager:
Sensor name
Note: Changing a Sensor’s name requires you to delete it from the Manager
and re-add it, or in other words, re-configure the Sensor from the beginning. For
instructions, see Add the Sensor to Manager (on page 48
the Sensor (on page 46
Sensor shared secret
Manager IP
Sensor IP and subnet mask
Adding a Sensor
) and then Configuring
).
Changing Sensor IP or Manager IP
1 On the Sensor, type deinstall.
This breaks the trust relationship with the Manager.
2 Type the command and the new value.
For example, type set manager IP 192.168.3.2
3 Type the
interface.)
Example: set sensor sharedsecretkey
The Sensor then prompts you to enter a shared secret key value. Type the shared
secret key value at the prompt. The Sensor then prompts you to verify the value. Type
the value again.
Note: The shared secret key value must be between 8 and 25 characters of
ASCII text. The shared secret key value is case-sensitive. Example:
IPSkey123
4 If you changed the Sensor IP address, then you must reboot the Sensor.
Type reboot
You must confirm that you want to reboot the Sensor.
Sensor shared secret. (This value must match the value set for the Sensor in the Manager
50
Page 59

McAfee® Network Security Platform 6.0
Changing Sensor’s shared secret key
1 In the Manager Configuration page , select Device List >Device List >Devices .
2 Select a Sensor.
3 Click
4 Type a new
5 Click
6 On the Sensor, type deinstall.
7 This breaks the trust relationship with the Manager.
8 Type
9 Type exit.
Edit.
Save.
the new Sensor shared secret. (This value must match the value set for the Sensor in the
Manager interface.)
Example: set sensor sharedsecretkey
The Sensor then prompts you to enter a shared secret key value. Type the shared
secret key value at the prompt. The Sensor then prompts you to verify the value. Type
the value again.
Note: The shared secret key value must be between 8 and 25 characters of
ASCII text. The shared secret key value is case-sensitive. Example:
IPSkey123
Shared Secret.
Adding a Sensor
Adding a secondary Manager IP
Note that this command is used to add an IP address for a second NIC in one Manager
server; this is not a command to use to set up a Manager Disaster Recovery peer—or
Secondary—Manager.
To add a secondary Manager IP,
On the Sensor, type set manager secondary ip <A.B.C.D.>
Specify a 32-bit address written as four eight-bit numbers separated by periods,
where A,B,C or D represents an eight-bit number between 0-255.
Example: set manager secondary ip 192.168.3.19
Or
Type set manager secondary ip <A:B:C:D:E:F:G:H>
where <A:B:C:D:E:F:G:H> is a 128-bit address written as octet (eight groups) of
four hexadecimal numbers, separated by colons. Each group ( A,B,C,D etc ) is a
group of hexadecimal numbers between 0000-FFFF.
Example: set manager secondary ip
2001:0db8:8a2e:0000:0000:0000:0000:0111
If one or more four-digit group(s) is 0000, the zeros may be omitted and replaced with
two colons (::).
Example: set manager secondary ip 2001:0db8:8a2e::0111
Removing a secondary Manager IP
To remove a secondary Manager IP , type deletemgrsecintf
51
Page 60

McAfee® Network Security Platform 6.0
Device Licenses
No license file is required for enabling IPS on I-series and M-series Sensors; no license is
required for enabling NAC on N-450 Sensors. In other words, when you add a Sensor to
the Manager, upon discovery, the native functionality supported on the Sensor model is
automatically enabled.
You require an add-on license to enable NAC on M-series Sensors. You can import/assign
the license using the
Importing a Device License
After adding a physical device (Sensor or NTBA Appliance) to the Manager, you need to
associate a license with the device. For this, you can import a license to the Manager, and
then the Manager automatically binds the license to the device. You can also manually
assign a license to the device.
The Manager mode functionalities (IPS, NAC and NAC with IPS) are dependent on the
type of device license imported to the Manager.
Device List > Add-On Licenses page.
Adding a Sensor
Importing a Device License
1 Retrieve the file from e-mail.
To enable the NAC mode on M-series Sensors, you need an Add-on license. Contact
McAfee support (with your device serial numbers) to obtain the Add-on license file.
Note: The IPS mode is enabled by default in the Manager.
2 Go to Device List > Device List > Add-On Licenses page.
The Device Licenses page is displayed.
Figure 24: Device License Import
3 To import a Device license, click Import to view the Import License File dialog.
Figure 25: Import Sensor License File Dialog
52
Page 61

McAfee® Network Security Platform 6.0
Adding a Sensor
4 Click
5 If the license has a serial number, the Manager automatically binds the license with
Browse to browse and select the appropriate license for the device file (.jar
format) received from McAfee. Click
After a successful import, these licenses are stored in “<Network Security Manager
install directory>\App\LICENSES\SensorLicense”.
the matching device model added to the Manager.
Import to import the license file.
Error raised if incorrect license file is selected for import
The following error is raised if an incorrect license file is selected for import.
Error Description/Cause
Action failed <File Name> could not be processed by the Manager.
Change in License due to purchase of additional functionality
If you upgrade from a temporary license or if you opt to upgrade your device to use
additional functionality for example, from IPS to IPS and NAC, you need to change the
device license by importing a new device license that can overwrite the existing one. This
can be done through the Manager during a Manager session. You do not have to log out
of an open Manager session to install the new license.
Manually assigning a device license
Manual assignment of a device license is applicable to add-on license files alone. Add-on
licenses have a unique license key. Once imported in the Manager, the license file can be
manually assigned to the matching M-series Sensor model.
Add-on licenses are applicable only to activating the NAC feature on M-series Sensors
along with IPS.
You can also revoke the manual binding of add-on licenses.
To manually assign an add-on license:
1 In the
Device Licenses page, select Manual Assignment.
Figure 26: Manual assignment of Sensor license
53
Page 62

McAfee® Network Security Platform 6.0
2 Select a license from the drop down.
Devices matching the selected Sensor license model are displayed.
3 Select the required device, and click
The license is assigned to the selected device, and displayed in the
page.
Figure 27: Device License Import
4 Here, you can unbind the manual assignment of device license.
For this, select the device from
Assign.
Adding a Sensor
Device Licenses
Current License Assignments and click Revoke.
Note: Only device licenses that are manually assigned can be revoked.
54
Page 63

C HAPTER 7
Configuring the Update Server
After installing the Manager software, one of the first tasks you will perform is setting the
schedule for receiving updates from the McAfee
Server). These updates include signature files for your Sensors and software for your
Manager and/or Sensors.
Before you can perform on-demand and scheduled downloading actions, you must
authenticate your credentials with the Update Server. You are not required to enter an IP
address or hostname for contacting the Update Server; contact information is hardcoded
into Manager. You need only supply your credentials using the
provides your credentials by email.
You can only perform one download/upload at a time from any Network Security Platform
component, including the Update Server.
Specifying the Update Server authentication
The Authentication action authenticates communication between your Manager or Central
Manager and the Update Server. This connection establishes all future communication for
downloading new signature sets and Sensor or NTBA Appliance software files from the
Update Server onto the Manager. Once you enter your credentials (ID and password given
to you by McAfee), the Manager attempts to contact the Update Server via hardcoded
communication settings.
®
Network Security Update Server (Update
Credentials action. McAfee
Note: You are not required to enter an IP address or hostname to reach the Update
Server. You only need to submit your credentials, the Manager then attempts the
connection with the hardcoded settings. You cannot change these settings.
To establish the Manager or Central Manager communication with the Update Server, do
the following:
1 Select
Manager (or Central Manager) > Update Server > Authentication.
Figure 28: Update Server Credentials Page
2 Enter the Grant Number and Password.
3 Click
4 Click
Save.
Delete to delete the credentials.
Note: If no congratulatory note is returned, re-enter your credentials. If you feel
you have entered the values correctly, check the User Activity Audit Log (for more
information, see Generating a User Activities Audit,
Administrative Domain
55
Page 64

McAfee® Network Security Platform 6.0
Configuration Guide) action to confirm success or failure. If the Password is
incorrect, or if you did not receive the same via e-mail from McAfee, plea
contact McAfee Customer Support.
Once communication is successful, you can use the Software, Signature Sets, Automation,
Manual Imports,
Specifying a proxy server for Internet connectivity
If you employ a proxy server for Internet connectivity, you can configure the Manager or
ur devices to connect to that server for proxy service. This is necessary if you want to
yo
download updates directly to Manager from the Update Server or if you wish to download
host reputation and country of origin information during integration with TrustedSource.
The Manager supports application-level HTTP/HTTPS proxies, such as Squid, iPlanet,
Microsoft Proxy Server, and Microsoft ISA.
Note 1: To use Microsoft ISA, you must configure this proxy server with basic
authentication. Network Security Platform does not support Microsoft ISA durin
NTLM (Microsoft LAN Manager) authentication.
Note 2: SOCKS, a network-level proxy, is not currently supported by Network
Security Platform.
and Proxy Server actions.
Configuring the Update Server
se
g
To specify your proxy server, do the following:
1 Select Manager > Misc > Proxy Server or Device List > Misc > Proxy Server. The Proxy Server
page displays.
Figure 29: Proxy Server Settings
2 Type the Proxy Server Name or IP Address. This can be either IPv4 or IPv6 address.
3 T
ype the Proxy Port of your proxy server.
4 Type
5 Provide the appropriate URL.
6 Click
When the Manager or the device mak
indicating that the proxy server settings are valid.
User Name and Password.
You may test to ensure that the connection works by
entering a Test URL and clicking Test Connection.
Save to save your settings.
es a successful connection, it displays a message
56
Page 65

McAfee® Network Security Platform 6.0
Manually importing a software image or signature set
The Manual Import action enables manual loading of the latest Sensor and NTBA Appliance
software and signature files to the Manager (or Central Manager) from another
workstation. This method is particularly useful if the Manager server is in a lab or secure
environment and you do not want to compromise that environment by an Internet
connection. This is crucial for administrators who do not want to connect their Manager to
the Update Server via the Internet.
McAfee provides an alternate FTP server that contains the latest updates. You can
download the update you need from the FTP location to a client machine. Once the image
file is downloaded to the alternate machine, you configure Manager to pull the file from the
client to the Manager server using the
To import software/signature files to your Manager (or Central Manager); do the following:
Import action.
Configuring the Update Server
1 Select
Figure 30: Import Signature Set From File
2 Click Browse to locate the Sensor or NTBA Appliance software or Signature set file, or
3 Click
Note: The Sensor needs to be rebooted after manual import. For more information
on rebooting the Sensor, see Device Configuration Guide. The guide also has
information alert and packet log interruptions.
Manager (or Central Manager) > Update Server > Manual Import.
type the file’s absolute path name on your network.
Import.
Downloading software updates
You can download available Sensor software (including NTBA Appliance) updates ondemand from the Update Server. If more than one version is available, select the most
recent version (that with the highest version number).
Automation enables the Manager to check the Update Server for software updates on a
periodic basis. For more information on Automation configuration, see Automating updates
(on page 62).
To download available software updates to the Manager, do the following:
1 Select
Server.
Manager > Update Server > Software. There are two tables on this screen:
Software available for download: current software versions available on the Update
57
Page 66

McAfee® Network Security Platform 6.0
Software on the Manager: the software versions that have been downloaded to the
Manager.
Figure 31: Sensor Software Details Page
2 Select the required software update from the “Software Available for Download” column of
Software table.
the
Note: Click a version listed in the “
details of the software update.
3 Click Download to download the software updates.
Configuring the Update Server
Software Available for Download” column to view
Note: The following options are available for Sensor:
Update all Sensors under the Sensors node; for more information, see Updating the
Configuration of all Sensors,
Device Configuration Guide.
Update a single Sensor; for more information, see Updating the software on a
Sensor, Device Configuration Guide.
Using a TFTP server to update Sensor software
Instead of downloading the Sensor software onto the Manager from the Update Server,
you can download it onto a TFTP server, and then to the Sensors using Sensor CLI
commands. You can use the TFTP-server method if you are unable to update the Sensors
through the Manager. To know the difference between the two methods, see the
Guide
.
To download a software image directly to the Sensor via a TFTP server, you must first
download the software image to your TFTP server.
Note: See your TFTP server documentation for specific instructions on how to
download the image to your TFTP server.
1 Download the software image from the Update Server to your TFTP server. This file is
compressed in a .jar file.
2 Rename the .jar file to .zip file.
3 Unzip the file using Winzip.
4 Extract the files to your TFTP boot folder [/tftpboot].
5 Once the image is on your TFTP server, upload the image from the TFTP server to
the Sensor.
From your
Sensor Console, perform the following steps:
Upgrade
58
Page 67

McAfee® Network Security Platform 6.0
a Log on to the Sensor. The default username is admin and default password
admin123. McAfee strongly recommends you change the default password, in
case you haven't done so already.
b Specify the IPv4 or IPv6 address of the TFTP server to identify it to the Sensor.
At the prompt, type:
set tftpserver ip <A.B.C.D>
Example: set tftpserver ip 192.34.2.8
where <A.B.C.D> represents an IPv4 address.
Or
Specify an IPv6 address as given below:
set tftpserver ip <A:B:C:D:E:F:G:H>
where <A:B:C:D:E:F:G:H> represents a 128-bit address written as octet
(eight groups) of four hexadecimal numbers, separated by colons. Each group
(A,B,C,D etc) represents a group of hexadecimal numbers between 0000-FFFF.
Example:
set tftpserver ip 2001:0db8:8a2e:0000:0000:0000:0000:0111
If one or more four-digit group(s) is 0000, the zeros may be omitted and replaced
with two colons (::)
Example: set tftpserver ip 2001:0db8:8a2e::0111
c Load the image file on the Sensor. At the prompt, type:
loadimage <filename>
Example: loadimage sensorsw_2700_xxxx
d A message appears when the image is loaded. To use the new software image,
you must reboot the Sensor. At the prompt, type:
reboot
You must confirm that you want to reboot.
Once the reboot process is complete, the Sensor deletes the old signature set.
Because the signature set is incompatible with the current Manager version, the
Sensor's System Health Status on the CLI is displayed as "uninitialiazed."
Configuring the Update Server
Figure 32: System Health Status: uninitialized
59
Page 68

McAfee® Network Security Platform 6.0
Then, the Sensor contacts the Manager for the latest signature set. After the signature
set is downloaded to the Sensor, its System Health Status is displayed as "good."
Figure 33: System Health Status: good
Configuring the Update Server
6 Verify the Sensor's System Health Status is “good”; check the Sensor status from CLI
by typing the status command.
You can also check whether the Sensor is updated with the latest software version as
well as latest signature set by going to
7 Use the Threat Analyzer to verify the performance of the Sensors.
This is to make sure the upgrade was successful. For information on how to check
Sensor performance from the Threat Analyzer, see Viewing Sensor performance
statistics,
System Status Monitoring Guide.
Downloading signature set updates
The Signature Sets action enables you to download available attack signature updates ondemand from the Update Server to the Manager server. You can then push the signature
download onto your Sensors or NTBA Appliance.
Note that
Manager) in the path
Tip: Because incremental emergency signature sets can be downloaded along with
regular signature sets, you no longer need to use custom attack definitions feature
to import late-breaking attacks.
The Signature Sets action not only allows you to import regular signature sets, but also
incremental emergency signature sets that include attack signatures not yet available in
regular signature sets. Incremental emergency signature sets are meant to address latebreaking attacks that may need to be addressed immediately. Emergency signature sets
are non-cumulative and can only add new signatures, so they do not contain a full set of
signatures. To ensure that you have a complete set of signatures, Network Security
Signature Sets feature is available in Network Security Central Manager (Central
/ My Company / Central Manager > Update Server > Signature Sets.
Device List > Sensor_Name > Summary.
60
Page 69

McAfee® Network Security Platform 6.0
Platform checks to see if a required regular signature set is missing and downloads it prior
to downloading the related emergency signature set.
Configuring the Update Server
Note: You must use the
Signature Sets or Automation action in order for Network
Security Platform to download a required regular signature set automatically, prior to
downloading an emergency signature set. You will receive an error if you try to
import an emergency signature set via the
Import action.
When a signature file, or version, is downloaded, the version is listed in the Signature Sets
action configuration table as the
Active Manager Signature Set. Signatures files are not applied
to the Manager, rather, the current version is the version that is pushed to the Sensor(s) or
NTBA Appliance when you are ready to update your Sensor’s or NTBA Appliance's
signature set.
Setting a schedule enables the Manager to check the Update Server for signature updates
on a periodic basis, download the available updates, and push these updates to your
Sensors or NTBA Appliances without your intervention. For more information on Scheduler
configuration, see Automating updates (on page 62).
To download the latest signatures to the Manager, do the following:
1 Select Manager > Update Server > Signature Sets.
Figure 34: Download Signatures Configuration
2 View the Active Manager Signature Set: Version n. This is the version that is currently
available for your Sensors or NTBA Appliances to download. This signature set is kept
in a queue for download to your Sensors or NTBA Appliances. You can only have one
version in the queue for download.
3 Select the signature update you want from
Signature Sets Available For Download. You can
click a version number to view update details.
Note 1: If you have downloaded the latest version, a default message reads,
“No new signature sets available. The Manager has the most recent signature
set.”
Note 2: Click view all to display all the signature updates available on the Update
Server. These are signatures you have already downloaded or upgraded to a
new version.
4 Click Download.
A status window opens to verify signature download progress. The
Download button
only appears when there is a new version to download.
Note: When the download is complete, you can update the Sensor signature set by
performing one of the following actions:
For more information on downloading signature sets to all Sensors, see Updating the
Configuration of all Sensors,
Device Configuration Guide
61
Page 70

McAfee® Network Security Platform 6.0
For more information on downloading signature sets to a single Sensor, see
Updating the software on a Sensor, Device Configuration Guide
Automating updates
McAfee is constantly researching security issues and developing new signatures to
provide the best protection available. New signatures are being constantly developed, and
existing ones modified, to respond to the most current attacks. Software updates
continually improve Sensor and NTBA Appliance performance. These enhancements are
made available on a regular basis via the Update Server.
Update availability is not confined to a set day and time; rather, updates are provided
when they are developed, enabling you to have the latest improvements as soon as they
are ready. The Automation feature enables you to configure the frequency by which the
Manager (or Central Manager) checks the Update Server for updates. At your automated
time, the Manager polls the Update Server; if an update is available that is newer than the
current signature set for the Sensor and NTBA Appliance software versions on your
Manager, that update is downloaded to the Manager. You can check what has been
downloaded at the
Note: The Automation feature is available in the Network Security Central Manager
(Central Manager) in the path / My Company / Central Manager > Update Server > Automation.
Software and Signature Sets option.
Configuring the Update Server
After downloading a signature set update, you can configure your Manager to push the
update to all of your Sensors or NTBA Appliances either immediately or by automation.
Since signature sets can be updated to Sensors and NTBA Appliances in real time without
shutdown, this scheduling feature enables you to propagate the latest signature set across
your Sensors and NTBA Appliances quickly.
The Automation action combines two actions for update scheduling:
Automating signature set downloads from the Update Server (on page 62): Configure
a schedule by which Manager polls the Update Server for available signature set
updates.
Automatically deploy new signature sets to your devices (on page 63): Enable either
automatic or scheduled downloading of the most recently downloaded signature set to
your Sensors.
Note: You must perform each action separately.
Automating signature set downloads from the Update Server
In the Update Server Automation, you schedule the Manager to poll the Update Server for
signature downloads on a periodic basis. Once your polling schedule is set, you can use
the Signatures action to check what signature updates have been downloaded to your
Manager and thus available for download to your Sensors and NTBA Appliances.
Note: If your Manager does not have a connection to the Internet, then you do not
need to set the automation. Rather, you would use your Network Security Platform
Support account to download the latest updates from the Update Server. For more
information, see Updating your Signatures and Software, Network Security Platform
Quick Tour
.
62
Page 71

McAfee® Network Security Platform 6.0
To configure an Update Server signature set downloads, do the following:
Configuring the Update Server
1 Select
Manager > Update Server > Automation.
Figure 35: Signature Set Download Scheduler
2 Select Yes to enable automation. No is selected by default.
Note: Select No and click Apply at any time to disable the polling automation.
3 Select the Schedule frequency by which you want the Manager to poll the Update
Server. The polling choices are:
Frequently: Several times a day during a specified time period
Daily: once a day
Weekly: once a week
4 Fill in the
selected
5 Click Save when done.
Once enabled, the Manager will download signature sets from the Update Server
against your set automation.
Start Time:, End Time:, and Recur every fields to your desired interval. Your
Automatic Downloading frequency choice affects these fields.
Automatically deploy new signature sets to your devices
From the Update Server Automation, you can automate signature file updating for all of
your Sensors and NTBA Appliances. This means you can have all of your Sensors and
NTBA Appliances updated:
1) As soon as signature updates are downloaded to the Manager from the Update Server
(real-time)
2) By a set schedule, or
3) By both a real-time setting and a scheduled time in an effort to reinforce immediate
updating with a scheduled check to make sure the latest update is loaded to your Sensors.
Note1: Setting both options enables the system to check update availability for
cases where the real-time updating may have missed an update.
Note2: If you are going to use automated updating, McAfee recommends a
scheduled time rather than real time for signature updating in case of slower
performance experienced during signature file download. You can schedule a time
when you know your network sees a lesser amount of traffic.
To deploy new signature sets to your Sensors automatically, do the following:
63
Page 72

McAfee® Network Security Platform 6.0
1 Select Manager > Update Server > Automation.
Figure 36: Sensor Update Scheduler
2 In the Automatic Deployment, click Yes at Deploy in Real-time to have the Manager push
signature sets update to all Sensors and NTBA Appliances immediately after it is
downloaded to the Manager.
time after enabling it, return to this page, select
AND/OR
Yes at Deploy at Scheduled Interval to apply a schedule for downloading signature
Click
updates from the Manager to the Sensors.
Scheduled Interval
Save
.
3 Select the
downloaded signature set. The polling choices are:
Frequently: Several times a day during a specified period at interval indicated in the
Recur every
Daily: once a day
Weekly: once a week
4 Fill in the
Your selected
5 Click Save to save your changes.
Configuring the Update Server
No is the default. To turn off the Deploy in Real-time at any
No, and click Save.
No is the default. To turn off the Deploy at
at any time after enabling it, return to this page, select No, and click
Schedule: frequency by which you want the Manager to check for a newly
option.
Start Time, End Time, and Recur every fields to desired interval specifications.
Automation frequency choice affects these fields.
64
Page 73

C HAPTER 8
Uninstalling the Manager/Central Manager
You uninstall McAfee® Network Security Manager (Manager) and McAfee® Network
Security Central Manager (Central Manager) using the standard Windows Add/Remove
Programs feature.
Uninstalling using Add/Remove Programs
You must have Administrator privileges on your Windows server to uninstall Network
Security Manager or Network Security Central Manager. Follow the steps given below for
uninstalling Central Manager and Manager.
► To uninstall the Manager software:
Note: McAfee recommends you stop the Manager service and applicable Java
services before starting an uninstall. If not, you will have to manually delete files
from the Network Security Platform program folder.
1 Go to Start > Settings > Control Panel > Add/Remove Programs and select Network Security
Platform.
Figure 37: Uninstalling the Manager
2 Click Uninstall to start the uninstallation process.
3 After uninstallation, the message "All items were successfully uninstalled" message is
displayed.
65
Page 74

McAfee® Network Security Platform 6.0
Figure 38: Uninstall Complete
Note: Uninstallation of the Network Security Platform database (MySQL) is not
part of this uninstallation.
Uninstalling the Manager/Central Manager
Figure 39: Uninstall Complete
Uninstalling via script
You can also uninstall the Network Security Manager/Network Security Central Manager
by executing a script from the Network Security Platform program folder.
66
Page 75

McAfee® Network Security Platform 6.0
► To uninstall via script:
1 Navigate to the directory containing the uninstallation script. The default path is:
<Network Security Platform installation directory>\UninstallerData
2 Run Uninstall ems.exe.
Uninstalling the Manager/Central Manager
67
Page 76

Index
A
about the Update Server .......................................... 6
adding the Sensor to NSM ..................................... 50
Authenticated Proxy server .................................... 58
S
safety warnings ...................................................... 40
Sensor licenses...................................................... 53
Sensor naming scheme ......................................... 47
Sensor responsibilities............................................. 1
signature updates .................................................. 66
T
technical support.................................................... viii
C
CA 32
CAC........................................................................ 32
CAC software ......................................................... 32
conventions .............................................................. v
D
dedicated interface................................................. 11
F
fail-closed dongle specification ..............................43
H
hosting ISM on VMware ........................................... 4
I
import command ....................................................53
M
McAfee Network Security Central Manager ............. 1
Central Manger services ...................................31
U
Update Server.......................................................... 1
Update Server ..................................................... 7
usage restrictions................................................... 42
V
VMware platform...................................................... 4
N
Network Security Platform
system components ............................................3
Network Security Platform license file.................... 53
Network Security Platform Update Server
See Update Server............................................. 6
 Loading...
Loading...