Page 1

Internet Guard Dog
User’s Guide
Version 3.0
Page 2

COPYRIGHT
Copyright © 2000 Network Associates, Inc. and its Affiliated Companies. All Rights Reserved. No part
of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
into any language in any form or by any means without the written permission of Network Associates,
Inc.
TRADEMARK ATTRIBUTIONS
* ActiveHelp, Bomb Shelter, Building a World of Trust, CipherLink, Clean-Up, Cloaking, CNX,
Compass 7, CyberCop, CyberMedia, Data Security Letter, Discover, Distributed Sniffer System, Dr
Solomon’s, Enterprise Secure Cast, First Aid, ForceField, Gauntlet, GMT, GroupShield, HelpDesk,
Hunter, ISDN Tel/Scope, LM 1, L ANGuru, Leading Help Desk Technology, Magic Solutions, MagicSpy,
MagicTree,Magic University, MagicWin, MagicWord,McAfee, McAfeeAssociates, MoneyMagic, More
Power To You,M ultimedia Cloaking,NetCrypto, NetOctopus, N etRoom, NetScan,Net Shield, NetShield,
NetStalker, Net Tools, Network Associates, Network General, Network Uptime!, NetXRay, Nuts & Bolts,
PC Medic, PCNotary, PGP, PGP (Pretty Good Privacy), PocketScope, Pop-Up, PowerTelnet, Pretty
Good Privacy, PrimeSupport,RecoverKey, RecoverKey-International, ReportMagic,RingFence, Router
PM, Safe & Sound, SalesMagic, SecureCast, Service Level Manager, ServiceMagic, Site Meter, Sniffer,
SniffMaster, SniffNet, Stalker, Statistical Information Retrieval (SIR), SupportMagic, Switch PM,
TeleSniffer, TIS, TMach, TMeg, Total Network Security, Total Network Visibility, Total Service Desk,
Total Virus Defense, T-POD, Trusted Mach, Trusted Mail, Uninstaller, Virex, Virex-PC, Virus Forum,
ViruScan, VirusScan, VShield, WebScan, WebShield, WebSniffer, WebStalker WebWall, and ZAC 2000
are registered trademarks of Network Associates and/or its affiliates in the USand/or other countries. All
other registered and unregistered trademarks in this document are the sole property of their respective
owners.
LICENSE AGREEMENT
NOTICE TO ALL USERS: CAREFULLY READ THE FOLLOWING LEGAL AGREEMENT
("AGREEMENT"), FOR THE LICENSE OF SPECIFIED SOFTWARE ("SOFTWARE") BY
NETWORK ASSOCIATES, INC. ("McAfee"). BY CLICKING THE ACCEPT BUTTON OR
INSTALLING THE SOFTWARE, YOU (EITHER AN INDIVIDUAL OR A SINGLE ENTITY)
CONSENT TO BE BOUND BY AND BECOME A PARTY TO THIS AGREEMENT. IF YOU DO
NOT AGREE TO ALL OF THE TERMS OF THIS AGREEMENT, CLICK THE BUTTON THAT
INDICATES THAT YOU DO NOT ACCEPT THE TERMS OF THIS AGREEMENT AND DO NOT
INSTALL THE SOFTWARE. (IF APPLICABLE, YOU MAY RETURN THE PRODUCT TO THE
PLACE OF PURCHASE FOR A FULL REFUND.)
1. License Grant. Subject to the payment of the applicable license fees, and subject to the terms and
conditions of this Agreement, McAfee hereby grants to you a non-exclusive,non-transferable right
to use one copy of the specified version of the Software and the accompanying documentation (the
"Documentation"). You may install one copy of the Software on one computer, workstation,
personal digital ass istant, pager, "smart phone" or other electronic d evice for which the Software
was designed (each, a "Client Device"). If the Software is licensed as a suite or bundle with more
than one specified Software product, this license applies to all such specified Software products,
subject to any restrictions or usage terms specified on the applicable price list or product packaging
that apply to any of such Software products individually.
Issued February 2000/ Internet Guard Dog v3.0
Page 3

(i.e., the required number of licenses would equal the number of distinct inputs to the
multiplexing or pooling software or hardware "front end"). If the number of Client Devices or
seats that can connect to the Software can exceed the number of licenses youhave obtained,then
you must have a reasonable mechanism in place to ensure that your use of the Software does not
exceed theuse limits specified for the licenses you have obtained. This license authorizesyou to
make or downloadone copyof the Documentation for eachClient Device or seat that is licensed,
provided that each such copy contains all of the Documentation's proprietary notices.
c. Volume Licenses. If the Software is licensed with volume license terms specified in the
applicable price list or product packaging for the Software, you may make, use and install as
many additional copies of the Software on the number of Client Devices as the volume license
authorizes. You must have a reasonable mechanism in p lace to ensure that the number of Client
Devices on which the S oftware has been installed does not exceed the number of licenses you
have obtained. This license authorizesyou to make or download one copy of theDocumentation
for each additional copy authorizedby thevolume license,provided that each such copy contains
all of the Documentation's proprietary notices.
2. Term. This Agreement is effective for an unlimited duration unless and until earlier terminated as
set forth herein. This Agreement will terminate automatically if you fail to comply with any of the
limitations or other requirements described herein. Upon any termination or expiration of this
Agreement, you must destroy all copies of the Software and the Documentation. You may
terminate this Agreement at any point by destroying all copies of the Software and the
Documentation.
3. Updates. For the time period specified in the applicable price list or product packaging for the
Software you are entitled to download revisions or updates to the Software when and as McAfee
publishes them via its electronic bulletin board system, website or through other online services.
For a period of ninety (90) days from the date of the original purchase of the Software, you are
entitled to download one (1) revision or upgrade to the Software when and as McAfee publishes it
via its electronic bulletin board system, website or through other online services. After the
specified time period, you have no further rights to receive any revisions or upgrades without
purchase of a new license or annual upgrade plan to the Software.
4. Ownership Rights. The Software is protected by United States copyright laws and international
treaty provisions. McAfee and its suppliers own and retain all right, title and interest in and to the
Software, including all copyrights, patents, trade secret rights, trademarks and other intellectual
property rights therein. Your possession, installation, or use of the Software does not transfer to
you any title to the intellectual property in the Software, and you will not acquire any rights to the
Software except as expressly set forth in this Agreement. All copies of the Software and
Documentation made hereundermust contain the same proprietarynotices thatappear onand in the
Software and Documentation.
User’sGuide iii
Page 4

5. Restrictions. Youmay not rent, lease, loan or resell the Software. You maynot permitthird parties
to benefit from the use or functionality of the Software via a timesharing, service bureau or other
arrangement, except to the extent such use is specified in the applicable list price or product
packaging for the Software. You may not transfer any of the rights granted to you under this
Agreement. You may not reverse engineer, decompile, or disassemble the Software, except to the
extent the foregoing restriction is expressly prohibited by applicable law. You may not modify, or
create derivative works based upon, the Software in whole or in part. You may not copy the
Software or Documentation exceptas expressly permitted inSection 1above. You may not remove
any proprietary notices or labels on the Software. All rights not expressly set forth hereunder are
reserved by McAfee. McAfee reserves the right to periodically conduct audits upon advance
written notice to verify compliance with the terms of this Agreement.
6. Warranty and Disclaimer
a. Limited Warranty. McAfee warrants that for sixty (60) days fromthe date of originalpurchase
the media (e.g., diskettes) on which the Software is contained will be free from defects in
materials and workmanship.
b. Customer Remedies. McAfee's and its suppliers' entire liability and your exclusive remedy for
any breach of the foregoing warranty shall be, at McAfee's option, either (i) return of the
purchase price paid forthe license, if any, or (ii) replacementof thedefective media in which the
Software is contained. You must return the defective media to McAfee at your expense with a
copy of your receipt. This limited warranty is void if the defect has resulted from accident,
abuse, or misapplication. Any replacement media will be warranted for the remainder of the
original warranty period. Outside the United States, this remedy is not available to the extent
McAfee is subject to restrictions under United States export control laws and regulations.
c. Warranty Disclaimer. Except for the limited warranty set forth herein, THE SOFTWARE IS
PROVIDED "AS IS." TO THE MAXIMUM EXTENT PERMITTED BY APPLICABLE
LAW, MCAFEE DISCLAIMS ALL WARRANTIES, EITHER EXPRESS OR IMPLIED,
INCLUDING BUT NOT LIMITED TO IMPLIED WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, AND
NONINFRINGEMENT WITH RESPECT TO THE SOFTWARE AND THE
ACCOMPANYING DOCUMENTATION. YOU ASSUME RESPONSIBILITY FOR
SELECTING THE SOFTWARE TO ACHIEVE YOUR INTENDED RESULTS, AND FOR
THE INSTALLATION OF, USE OF,AND RESULTSOBTAINED FROMTHE SOFTWARE.
WITHOUT LIMITING THE FOREGOING PROVISIONS, MCAFEE MAKES NO
WARRANTY THAT THE SOFTWARE WILL BE ERROR-FREE OR FREE FROM
INTERRUPTIONS OR OTHER FAILURES OR THAT THE SOFTWARE WILL MEET
YOUR REQUIREMENTS. S OME STATES AND JURISDICTIONS DO NOT ALLOW
LIMITATIONS ON IMPLIED WARRANTIES, SO THE ABOVE LIMITATION MAY NOT
APPLY TO YOU. The foregoing provisions shall be enforceable to the maximum extent
permitted by applicable law.
iv Internet Guard Dog
Page 5

7. Limitation of Liability.UNDER NO CIRCUMSTANCES AND UNDER NO LEGAL THEORY,
WHETHER IN TORT, CONTRACT, OR OTHERWISE, SHALL MCAFEE OR ITS SUPPLIERS
BE LIABLE TO YOU OR TO ANY OTHER PERSON FOR ANY INDIRECT, SPECIAL,
INCIDENTAL, OR CONSEQUENTIAL DAMAGES OF ANY CHARACTER INCLUDING,
WITHOUT LIMITATION, DAMAGES FOR LOSS OF GOODWILL, WORK STOPPAGE,
COMPUTER FAILURE OR MALFUNCTION, OR FOR ANY AND ALL OTHER DAMAGES
OR LOSSES. IN NO EVENT WILL MCAFEE BE LIABLEFOR ANY DAMAGES IN EXCESS
OF THE LIST PRICE MCAFEE CHARGES FOR A LICENSE TO THE SOFTWARE, EVEN IF
MCAFEE SHALL HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
THIS LIMITATION OF LIABILITY SHALL NOT APPLY TO LIABILITY FOR DEATH OR
PERSONAL INJURY TO THE EXTENT THAT APPLICABLE LAW PROHIBITS SUCH
LIMITATION. FURTHERMORE, SOME STATES AND JURISDICTIONS DO NOT ALLOW
THE EXCLUSION OR LIMITATION OF INCIDENTAL OR CONSEQUENTIAL DAMAGES,
SO THIS LIMITATION AND EXCLUSION MAY NOT APPLY TO YOU. The foregoing
provisions shall be enforceable to the maximum extent permitted by applicable law.
8. United States Government. The Software and accompanying Documentation are deemed to be
"commercial computer software" and "commercial computer software documentation,"
respectively, pursuant to DFAR Section 227.7202 and FAR Section 12.212, as applicable. Any
use, modification, reproduction, release, performance, display or disclosure of the Software and
accompanying Documentation by the United States Government shall be governed solely by the
terms of this Agreement and shall be p roh ibited except to the extent expressly permitted by the
terms of this Agreement.
9. Export Controls. Neither the Software nor the Documentation and underlying information or
technology may be downloaded or otherwise exported or re-exported (i) into (or to a national or
resident of ) Cuba, Iran, Iraq, Libya, North Korea, Sudan, Syria or any other country to which the
United States has embargoed goods; or (ii) to anyone on the United States Treasury Department's
list of Specially Designated Nations or the United States Commerce Department's Table of Denial
Orders. By downloading or using the Software you are agreeing to the foregoing and you are
certifying that you are not located in, under the control of, or a national or resident of any such
country or on any such list.
IN ADDITION, YOU SHOULD BE AWARE OF THE FOLLOWING: EXPORT OF THE
SOFTWARE MAY BE SUBJECT TO COMPLIANCE WITH THE RULES AND
REGULATIONS PROMULGATED FROM TIME TO TIME BY THE BUREAU OF EXPORT
ADMINISTRATION, UNITED STATES DEPARTMENT OF COMMERCE, WHICH
RESTRICT THE EXPORT AND RE-EXPORT OF CERTAIN PRODUCTS AND TECHNICAL
DATA. IF THE EXPORT OF THE SOFTWARE IS CONTROLLED UNDER SUCH RULES
AND REGULATIONS, THEN THE SOFTWARE SHALL NOT BE EXPORTED OR
RE-EXPORTED, DIRECTLY OR INDIRECTLY, (A) WITHOUT ALL EXPORT OR
RE-EXPORT LICENSES AND UNITED STATES OR OTHER GOVERNMENTAL
APPROVALS REQUIRED BY ANY APPLICABLE LAWS, OR (B) IN VIOLATION OF ANY
APPLICABLE PROHIBITION AGAINST THE EXPORT OR RE-EXPORT OF ANY PART OF
THE SOFTWARE.
User’sGuide v
Page 6

SOME COUNTRIES HAVE RESTRICTIONS ON THE USE OF ENCRYPTION WITHIN
THEIR BORDERS, OR THE IMPORT OR EXPORT OF ENCRYPTION EVEN IF FOR ONLY
TEMPORARY PERSONAL O R BUSINESS USE. YOU ACKN OWLEDGE THAT THE
IMPLEMENTATION AND ENFORCEMENT OF THESE LAWS IS NOT ALWAYS
CONSISTENT AS TO SPECIFIC COUNTRIES. ALTHOUGH THE FOLLOWING
COUNTRIES ARE NOT AN EXHAUSTIVE LIST THERE MAY EXIST RESTRICTIONS ON
THE EXPORTATION TO, OR IMPORTATION OF, ENCRYPTION BY: BELGIUM, CHINA
(INCLUDING HONG KONG), FRANCE, INDIA, INDONESIA, ISRAEL, RUS SIA, SAUDI
ARABIA, SINGAPORE, AND SOUTH KOREA. YOU ACKNOWLEDGE IT IS YOUR
ULTIMATE RESPONSIBILITY TO COMPLY WITH ANY AND ALL GOVERNMENT
EXPORT AND OTHER APPLICABLE LAWS AND THAT MCAFEE HAS NO FURTHER
RESPONSIBILITY AFTER THE INITIAL SALE TO YOU WITHIN THE ORIGINAL
COUNTRY OF SALE.
10.High Risk Activities. The Software is not fault-tolerant and is not designed or intended for use in
hazardous environments requiring fail-safe performance, including without limitation, in the
operation of nuclear facilities, aircraft navigation or communication systems, air traffic control,
weapons systems, direct life-support machines, or any other application in which the failure of the
Software could lead directly to death, personal injury, o r severe physical or property damage
(collectively, "High Risk Activities"). McAfee expressly disclaims any express or implied
warranty of fitness for High Risk Activities.
11.Miscellaneous. This Agreement is governed by the laws of the United States and the State of
California, without reference to conflict of laws principles. The application of the United Nations
Conventionof Contracts for the InternationalSale of Goods is expressly excluded. ThisAgreement
sets forth all rights for the user of the Software and is the entireagreement betweenthe parties. This
Agreement supersedes any other communicationswith respectto theSoftware and Documentation.
This Agreement may not be modified except by a written addendum issued by a duly authorized
representative of McAfee. No provision hereof shall be deemed waived unless such waiver shall
be in writing and signed by McAfee or a duly authorized representative of McAfee. If any
provision of this Agreement is held invalid, the remainder of this Agreement shall continue in full
force and effect. The parties confirm that it is their wish that this Agreement has been written in
the English language only.
12.McAfee Customer Contact. If you have any questions concerning these terms and conditions, or
if you would like to contact McAfee for any other reason, please call (408) 988-3832, fax (408)
970-9727, or write: McAfee Software, 3965 Freedom Circle, Santa Clara, California 95054.
http://www.mcafee.com.
Statements made to you in the course of this sale are subject to the Year 2000 Information and
Readiness Disclosure Act(Public Law105-271). In the case ofa dispute, this Act may reduce your
legal rights regarding the use of any statements regarding Year 2000 readiness, unless otherwise
specified in your contract or tariff.
vi Internet Guard Dog
Page 7

Table of Contents
Chapter1. WelcometoInternetGuardDog™......................1
UsingInternetGuardDog ..........................................1
HowInternetGuardDogworks..................................2
UserSetup ..................................................2
VirusScan ...................................................2
Activity Logs . . . . ............................................2
SecurityCheck ...............................................3
InternetGuardDogandyouronlineconnection....................3
InternetGuardDogfeatures ....................................3
What’snewinInternetGuardDog ...................................5
Otherfeaturesandenhancements ...............................6
About Internet Guard Dog documentation . . . . . . . . . . . . . . ...............6
How this book is organized . . . . . ...............................7
UsingInternetGuardDoghelp .................................7
Chapter2. InstallingInternetGuardDog™ .......................11
Systemrequirements .............................................11
Installing Internet Guard Dog . . . . . . . . ..............................12
Troubleshooting installation problems ..............................12
Step1:Cleanupyourharddrive ...............................13
Step 2: Remove temporary files . . ..............................13
Step3:Closeothersoftware...................................14
Installing McAfee VirusScan from the Internet Guard Dog CD . . . . . . . . . . .14
Chapter 3. Quick Tour of Internet Guard Dog™ . . . . . . . . . . . . . . . . . . . 15
UsingtheInternetGuardDogInterview ..............................15
What information does Internet Guard Dog ask me to enter? . . . . . . . .16
HowInternetGuardDogAdministratorworks ....................17
HowpasswordprotectionworksinGuardDog ...................18
UsingtheInternetGuardDogHomescreen ..........................18
HowUserSetupworks .......................................20
HowInternetFilteringworks ..................................21
User’s Guide vii
Page 8

Table of Contents
HowPrivacyandSecurityoptionswork .........................22
Options ....................................................23
UsingMcAfeeVirusScan......................................23
Viewing Activity Logs . . . . . . . . . . ..............................23
UpdatingInternetGuardDogandVirusScan .....................24
PerformingaSecurityCheck ..................................25
WhatInternetGuardDogdoeswhileyourPCisrunning................26
UsingtheInternetGuardDogshortcutmenu ....................26
Responding to Internet Guard Dog alert messages . ..............27
Using Browser Buddy to retrieve or store your Web site passwords .27
Usingfileencryption .........................................29
Chapter4. PrivacyFeatures ...................................31
WhatCookieBlockerdoes ........................................31
Responding to a Cookie Blocker alert message . . . . ..............32
Why should I change my Cookie Blocker settings? . ..............33
WhatIdentityProtectordoes ......................................33
Responding to an Identity Protector alert message . ..............34
Why should I change my Identity Protector settings? . . . . . . . . . . . . .35
WhatWebTrailCleanerdoes ......................................36
Responding to the Web Trail Cleaner alert message ..............36
Why should I change my Web Trail Cleaner settings? . . . . . . . . . . . . .37
WhatSearchFilterdoes ..........................................37
Chapter5. SecurityFeatures ..................................39
WhatGatekeeperdoes ...........................................39
Responding to Gatekeeper alert messages . . . . . . . . ..............39
Why should I change my Gatekeeper settings? . . . . . ..............42
WhatFileGuardiandoes ..........................................43
Responding to File Guardian alert messages . . . . . . ..............43
Why should I change my File Guardian settings? . . . ..............46
WhatPasswordManagerdoes .....................................47
Chapter6. McAfeeVirusScan..................................49
WhatisMcAfeeVirusScan?........................................49
StartingVirusScan ...........................................49
viii Internet Guard Dog
Page 9

Table of Contents
VirusScanCentralwindow ....................................50
VirusScanClassicwindow ....................................50
ConfiguringVirusScan .......................................51
AppendixA. InternetSecurityandPrivacy .......................55
NetworksandtheInternet .........................................55
TCP/IPisthesubsystem ......................................55
Whypackets?...............................................56
TheInternetandtheWeb…whatisthedifference? ................56
PrivacyandsecurityontheWeb ...............................57
WhydoesInternetprivacymattertome? ........................57
PrivacyontheWeb...............................................58
Whoissnooping? ...........................................58
Snoopingandsniffing ........................................58
Webserversandfirewalls .....................................58
WhatcanIdotokeepmystuffsafe?............................59
HowcanItellifaWebsiteissecure? ...........................59
Howdoesencryptionwork? ...................................60
SecurityontheWeb ..............................................61
Nastyapplets ...............................................62
CanIpreventprogramsfromaccessingtheInternet?..............62
Computer viruses and the Web . . . . . . . ..............................62
Arevirusesreallythatdangerous? .............................63
Typesofviruses.............................................63
HowcanmyPCbecomeinfectedwithavirus? ...................64
Frequently asked quest ions about Internet privacy . . . . . . ..............64
SourcesforInternetprivacyandsecurityinformation ..................66
Finding out about Internet hoaxes ..............................66
More information about computer viruses . . . . . . . . . ..............66
More information about secur ity . ..............................67
More information about priva cy . . ..............................67
Appendix B. Product Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .69
HowtoContactMcAfee ...........................................69
Customerservice ............................................69
User’s Guide ix
Page 10

Table of Contents
Technical support ...........................................70
McAfeetraining .............................................71
x Internet Guard Dog
Page 11

1Welcome to Internet Guard Dog
Using Internet Guard Dog
In the last fewyearsthe Internet has changedfrom acommunications network
that government entities and universities used almost exclusively, to an
information treasure house that people of all ages and occupations can now
access. With an Internet account, youcan send electronic mail (e-mail) around
the world in seconds, do research without leaving home, meet new friends in
an onlinechat room, or shop without getting out of your bathrobe. However,
with all these conveniences come a certain element of risk. When you use the
Internet, information istransmitted fromyourcomputer toother computers in
the Internet—information you may not want other people to have. And those
computers can also send files to your computer that may contain viruses.
While most of these files are harmless, some can invade your privacy or even
damage the data on your computer’s hard drive.
Figure 1-1. Internet Guard Dog Home screen
™
1
McAfee’s Internet Guard Dog addresses any of these potential risks with its
comprehensive features designed to protect your privacy and security when
surfing the Internet.
User’s Guide 1
Page 12

Welcome to Internet Guard Dog™
With its new features, you can now also act as an Administrator and apply
customized protection settings not only for yourself, but for other users of
your computer and easily monitor potential risk they may encounter while
browsing the Internet.
How Internet Guard Dog works
Internet Guard Dog works via the following main features displayed in the
Home screen:
User Setup
As the Administrator, this feature allows you to setup protection settings for
other users of your computer. Y ou can add, edit and delete a user’s
profile—then setup individual privacy, security and Internet filtering options
that Internet Guard Dogwill apply w henever any of these users are browsing
the Web through your computer.
See the following for more information:
• “Customize User Setup Settings” on page 33.
• Chapter 4, “Privacy Features.”
• Chapter 5, “Security Features.”
VirusScan
Internet Guard Dog now uses the McAfee VirusScan to address virus-related
problems you may encounter through the Internet. This feature allows you to
set how to perform a virus scan operation on your computer; what to do if a
virus isfound; and how it should alert you once thevirus is detected. You can
also direct VirusScan to keep a recordof actions performedon yourcomputer.
With these mainfeatures of InternetGuard Dog, youarein controlat all times.
You decide what security and privacy features to use. If your concerns or
computing habits change, it is easy to change Internet Guard Dog protection
settings to meet your needs and those of others who use your computer
frequently. See “What is McAfee VirusScan?” on page 49.
Activity Logs
On the Internet Guard Dog Home screen, Activity Logs allow you to view a
list of all the interactions that you and other profiled users of your computer
had with Internet Guard Dog, including the date and time of the action. You
can print, save or clear this list. See “Viewing Activity Logs” on page 23.
2 Internet Guard Dog
Page 13

Welcome to Internet Guard Dog™
Security Check
You can run a complete check of your computer for any privacy or security
problems via this feature. After Internet Guard Dog performs the check, it
displays any problem found, provides additional information about the
problem, and guides you through on how to solve the problem. See
“Performing a Security Check” on page 25.
Internet Guard Dog and your online connection
To use all Internet Guard Dog features, you must have an Internet connection
through a local network or a modem. Some networks have an Internet
connection that you can use by connecting to the network-either directly or
through dial-up networking. If you don’t connect through a network, your
computer must have a modem installed.
You can establish anInternet connectionthrough anInternet Service Provider
(ISP) such as Earthlink. An ISP acts as a middleman between you and the
Internet. Your computer connects (using your modem) to the ISP’s equipment,
which in turn connects to the Internet. You may also be connected to the
Internet through an online service such as America Online or Compuserve.
In addition, you must also have a browser. A browser is software, such as
Netscape Navigator or Microsoft Internet Explorer (it must be a version
designed for Windows 95 or Windows 98), that allows you to view text and
graphics and download files from Web sites.
Internet Guard Dog features
This section brieflydescribes other featuresof Internet GuardDog that protect
you from the most common Internet threats. If you want more background
information on Internet privacy, security, and virus issues, see “Internet
Security and Privacy” on page 55.
NOTE: Only the designated Admi nistrator or Self-Administrator can
have access to these features which allow them to customize protection
settings for themselves and in the case of the Administrator, protection
forotherprofiledusersofthesamecomputer.
User’s Guide 3
Page 14

Welcome to Internet Guard Dog™
Protection from privacy threats
• Identity Protector monitors your Internet connection and warns you
before private information is sent to an unsecure Internet site. It stops
programs and other people that use your computer (like your kids) from
sendingyour name and credit cardnumbers overthe Internetwithout your
approval.
• Cookie Blocker prevents Web sites from storing cookies on your hard
drive. Third-party Web sites use cookies to track your Web browsing
habits. You can choose your level of interaction with Cookie Blocker. (For
more information, see “What are cookies and how are they used?” on
page 65.)
• Web Trail Cleaner cleans yourWeb browsing trailssuch as cachedfiles; list
ofURLs (Uniform ResourceLocator,also known as Webaddress)visited; and
history files—when you close your browser. This feature prevents other
users of your computer to track your online movements by viewing the
files and URL addresses l eft over from your Internet browsing.
• Search Filterprevents search information that you request at one Web site
from being passed along to the next site you visit. Without Search Filter,
your browser can transfer your search request information from one Web
site to another without your knowledge.
Protection from security threats
• Gatekeeper allows you to control the programs that have access to your
Internet connection. Programs on your PC can be programmed to access to
the Internet without your consent.
• File Guardian protects files that contain your sensitive data from being
opened, renamed, copied, moved, or deleted. Programs, such as ActiveX
and Java programs, can scan your PC for personal information or delete
files without your permission.
File Guardian also limits access to protected files either to programs you
specify or through file encryption. It can limitthe programs that can access
your tax, on-line banking, or personal accounting data files.
• Password Manager stores your Web site login names and passwords for
protected Web sitesin one securelocation. When you are visitinga site that
requires this information, drag it from Browser Buddy to the form
displayed in your browser. No more storing your login names and
passwords in an unsecure location, such as post-it notes on your monitor
or in a text file on your Windows desktop.
4 Internet Guard Dog
Page 15

Protection from virus threats
Using the McAfee VirusScan, the following features are available:
• Scan to start the default virus scan task immediately, or config ure a virus
scan task that suits your needs.
• Scheduler to launch the McAfee VirusScan Scheduler. This utility enables
you to configure and run unattended virus scan operations.
• Virus info to display virus information via the McAfee Web site.
What’s new in Internet Guard Dog
Internet Guard Dog version 3.0 includes these new features.
• Inclusion of McAfee VirusScan
McAfee VirusScan is now included in Internet Guard Dog. Select from
availableoptions to customized how you want itto protectyour computer.
• Multi-user Logon and user settings
Internet Guard Dog now allows multiple users to have different
protections settings. The main user can also act as an Administrator
customizing settings for other users of the same computer.
Welcome to Internet Guard Dog™
• Internet Filtering options
After an Administrator has added profiles of other users of the computer,
Internet Filtering optionscan be usedbased ondefault URL sites,word list,
rating systems, and Internet access time. Administrator can also enter
additional lists or sites if desired.
• Activity Logs
An Administrator can view a list of activity, maintenance and violation
logs at the single click of a button. This list contains information such as
duration of computer use or any protection setting violation that a profiled
user may have committed (e.g., attem pting to pass credit card number).
Administrator also has the option to clean, print or save this list.
• Improved online Help interface
The online Help is now displayed via a tri-pane Explorer View Help
window. While viewing a topic within the Help file, the user can now also
view the table of contents as well as access the index and full-text search
options simultaneously while the topic is displayed on the right-hand side
of the window.
User’s Guide 5
Page 16

Welcome to Internet Guard Dog™
Other features and enhancements
• Internet Guard Dog password
Protects the information and settings in Internet Guard Dog from being
viewed or changed. It also prevents other users of your computer from
sending out information that you specify as private.
• File Guardian enhancement
Protects individual files even when encrypted.
• Improved cookie management
Indicates whethercookies are direct or indirect and the domain where it is
coming from.
• Personal identity protection
“Mark” personal identity information and sensitive files (such as financial
records and credit card numbers) so they’ll never be sent over the Internet
without your OK.
• Encrypt sensitive files
Add an extra layer of protection by encoding files to prevent them from
being read—until you decode them.
• Browser Buddy enhancement
Store and manage your Web site passwords in one convenient, secure
location. User can now reset numbers.
• Single Update button
At the single click of a button, user can update both Internet Guard Dog
and McAfee VirusScanvia the Web.
About Internet Guard Dog documentation
This manual provides the basicinformation youneed to install, set up,and use
Internet Guard Dog. More detailed information on Internet Guard Dog is
provided by the Help files which you can access while working within the
different windows.
6 Internet Guard Dog
Page 17

How this book is organized
This User’s Guide is designed to get you using Internet Guard Dog quickly.
Read chapters 1 and 2 to get Internet Guard Dog installed and running. You
only need to read Chapters 3, 4, 5, and 6 if you want further information on
customizing Internet GuardDog orusing specific features. Read Chapter7 for
furtherinformation on McAfeeVirusScan. Ifyou are new tothe Internetorjust
want to find out more about Internet privacy and security issues, read
Appendix A.
To find out Read
Welcome to Internet Guard Dog™
Table 1-1.
What this version of Internet Guard Dog does
and how to find information about Internet
Guard Dog.
System requirements and how to install
Internet Guard Dog.
HowtousethemainfeaturesofInternet
Guard Dog.
What the Cookie Blocker, Identity Protector,
Web Trail Cleaner, and Search Filter features
are and how to work with them.
What the Gatekeeper, File Guardian, and
Password Manager features are and how to
work with them.
What the VirusScan features are and how to
work with them.
What privacy, security, and virus issues exist
on the Internet.
How to contact McAfee Software sales,
customer service and support departments.
Chapter 1, “Welcome to
Internet Guard Dog™.”
Chapter 2, “Installing Internet
Guard Dog™.”
Chapter 3, “Quick Tour of
Internet Guard Dog™.”
Chapter 4, “Privacy Features.”
Chapter 5, “Security Features.”
Chapter 6, “McAfee
VirusScan.”
Appendix A, “Internet Security
and Privacy”
Appendix B, “Product Support”
Using Internet Guard Dog help
To launch InternetGuard Dog help
1. In the Internet Guard Dog Home screen, click Help; then select Help
Topics. The Help system is displayed via a tri-pane Explorer View
window.
User’s Guide 7
Page 18

Welcome to Internet Guard Dog™
2. You can search for a help topic via the Contents, Index or Find tabs.
•Contentstab
•Indextab
NOTE: To go to the next page of help, click the next >>browse button
(if activated). To return to the previous page, click the previous <<
browse button (if activated) or click the Back button.
•Findtab.
1. Double-click a book icon to display its table of contents of related topics.
2. Locate the topic you want; thenpoint and double-clickto open the Help topic.
1. In the text box, type the first few letters of the word or phrase you are looking for.
2. Locate what you are looking for; then double-click the topic or click the Display button.
Clicking the Find tab enables you to launch a full text search. When
you search for topics via the Find tab for the first tim e, a Find Setup
Wizard is displayed. Follow the instructions on screen to setup the
full text search option. After setup is complete:
1. In the text box, type the first few letters of the word or phrase
you are looking for. You can also select matching words to
narrow your search.
2. Once you have located what you are looking for in the display topic box, click the topic.
To display help for a screen
1. In the Internet Guard Dog Home screen, click Help.
2. Click Help for this screen to display a help topic that explains what you
can do in or what you may need to know about the current Internet
Guard Dog screen.
8 Internet Guard Dog
Page 19

Welcome to Internet Guard Dog™
To get help for settings in a dialog box
• Whenever you see the button in the upper-right corner of a dialog
box, click the button, then click on the setting for which you want
information.
User’s Guide 9
Page 20

Welcome to Internet Guard Dog™
10 Internet Guard Dog
Page 21

2Installing Internet Guard Dog
Most installation problems are a caused by having programs running while
you try to install new software. Even if the installation appears normal, you
won’tbe ableto runthe newprogram. To avoid installationproblems, close all
open programs before you install Internet Guard Dog, including programs
that run in the background, such as screen savers or virus checkers.
System requirements
To use Internet Guard Dog you need:
• IBM PC or compatible computer running Windows 95 or Windows 98.
• 16 megabytes (MB) minimum of RAM.
• 20MBfreeharddiskspacetoinstallInternetGuardDogandMcAfee
VirusScan. Additionaldisk space isrequired to installany optionalInternet
software that may be included on the compact disc (CD) version.
• 256-color video display or better. Internet Guard Dog looks and operates
best in a resolution of 800x600 pixels (or greater) and a color palette of
32,000colormode(15 bit) or higher. 256-color palette is supported, but may
cause some color changes (caused by ‘palette swapping’) when switching
between applications.
™
2
• Microsoft mouse or compatible pointing device.
• Access to the Internet, either a dial-up a ccount with an Internet Service
Provider (ISP) or a constant connection through a network.
• Windows 95 or Windows 98 Web browser (also called a 32-bit browser).
SomeHelp features—McAfeeSoftware on theWeb, Internet Guard Dogon
the Web, FAQs, and Report a problem—require you to connect to the
McAfee Software Web site with a Web browser (software that allows you
to vi ew documents and download files from the World WideWeb). To use
all the online support features, the browser must be Microsoft
Explorer, Netscape Navigator
Windows 95 or Windows 98.
NOTE: America Online users need AOL’s 32-bit Winsock to use
Internet Guard Dog. To upgrade from a 16-bit Winsock, contact
America Online.
™
,orAmericaOnlinev3.0(orlater)for
®
Internet
User’s Guide 11
Page 22

Installing Internet Guard Dog™
Installing Internet Guard Dog
After closing all open programs, you are ready to install Internet Guard Dog
on your PC. Installation should go smoothly, however, if you do have
difficulties, see “Troubleshooting installation problems” on page 12.
To installInternet Guard Dog
1. Close all open programs.
2. Insert the Internet Guard Dog CD in the CD-ROM drive.
3. In the InternetGuard Dog Setup screen, click Install Internet GuardDog.
NOTE: If the setup screen doesn’t start automatically when you
close your CD-ROM drive, click Start on the Windows taskbar, click
Run, then typed:\setup. IfD is not the driveletter ofyour CD-ROM
drive, substitute the correct drive letter.
4. After installationis completed, InternetGuard Dog’s Interviewfeatureis
launched. Follow through the screen instructions and provide
information as needed.
NOTE: Only the Administrator can access this Interview feature of
Internet Guard Dog. For more information, see “Using the Internet
Guard Dog Interview” on page 15.
Troubleshooting installation problems
A failed installation can cause software problems that are difficult to track
down. The major causes of installation failure are:
• Hard drive errors
• Temporary files that conflict with the installation
• Attempting to install while other software is running
Follow the procedure outlined below to minimize the affect that these
common conditions may have on your installation.
12 Internet Guard Dog
Page 23

Step 1: Clean up your hard drive
Run the Windows 95 hard drive utilities, ScanDisk and Disk Defragmenter to
identify and fix any errors on your hard drive:
1. ClickStart on the Windows taskbar, pointto Programs,then Accessories,
then System Tools, and click ScanDisk.
2. In the ScanDisk window, select Standard and Automatically fix errors.
NOTE: These are the default settings.
3. Click Advanced. In the Advanced Settings dialog box, make sure the
following settings are selected:
• Only if errors found
•Replacelog
• Delete
•Free
4. Ignore the other options, and click OK. Click Start. ScanDisk begins
scanningyour drive forerrors. Depending onthesize of yourhard drive,
ScanDisk may take several minutes to complete its job.
Installing Internet Guard Dog™
5. When ScanDisk is finished, close ScanDisk.
6. ClickStart on the Windows taskbar, pointto Programs,then Accessories,
then System Tools, and click Disk Defragmenter.
7. Click OK to start Disk Defragmenter. Depending on the speed of your
computer and the size of your drive, this may take several minutes to
complete.
8. Close Disk Defragmenter when it has finished defragmenting your disk.
Step 2: Remove temporary files
Delete the contents of the Windows Temp folder:
1. Double-click the My Computer icon on your desktop. The My Computer
window opens. Double-click the C: drive. You are now viewing the
contents of your hard drive.
2. Double-click the Windows folder.
3. In the Windows folder, double-click the Temp folder.
User’s Guide 13
Page 24

Installing Internet Guard Dog™
4. In themenu, click Edit,thenclick Select All.All of the itemsin your Temp
folder are highlighted.
5. Press the Delete key on your keyboard to delete the files. If Windows
asks about deleting files, click Yes.
6. In the Windows taskbar, click Start, then click Shut Down.
7. Click Restart the computer, then click Yes in the Shut Down Windows
dialog box to restart your PC.
Step 3: Close other software
Disable all software running in the background:
1. Hold down the Ctrl and Alt keys on your keyboard, and then press the
Delete key once. The Close Program dialog box appears.
2. Click End Task for every item on the list except Explorer.
3. Repeat steps 2 and 3 until you’ve closed everything except Explorer.
4. When you see only Explorer in the Close Program dialog box, click Cancel.
You are now ready to install your new software.
Installing McAfee VirusScan from the Internet Guard Dog CD
The Internet Guard Dog CD contains a copy of McAfee VirusScan.
To install McAfee VirusScan
1. Insert the Internet Guard Dog CD in the CD-ROM drive.
2. In the Internet Guard Dog Setup screen, click Install McAfee VirusScan.
3. Follow the instructions on your screen.
14 Internet Guard Dog
Page 25

3Quick Tour of Internet Guard Dog
Internet Guard Dog is a simple program to use. In fact, this one chapter covers
themain things youneedto know aboutusingInternet Guard Dog. Youbegin
with answering a few questions via the Interview so that Internet Guard Dog
can effectively use its feature to protect you from Internet threats.
™
Using the Internet Guard DogInterview
Although Internet Guard Dog is set up to use security and privacy settings
that are appropriate for most users, some features require your input. The
Interview provides an easy means of customizing your Internet Guard Dog
settings.
Eachinterview screen eithertells you abouta Internet Guard Dogfeature, asks
you to enter information, or asks you how you want Internet Guard Dog to
respond to certain situations. (Figure 3-1.)
3
Figure 3-1. Internet Guard Dog Interview screen.
On each interview screen you can click Back to return to a previous screen or
click Next to move to the next screen. In the final interview screen, you click
Finish to save the settings you selected and close the Interview.
User’s Guide 15
Page 26

Quick Tour of Internet Guard Dog™
What information does Internet Guard Dog ask me to enter?
The Internet Guard Dog interview asks you to enter the personal andfinancial
information that you want to protect. All the information you enter into
Internet Guard Dog is stored in encrypted form on your hard disk— it is never
sent to McAfee Software.
You may want to gather your personal information before you start the
interview. During the interview, Internet Guard Dog allows you to enter:
• A password that you can use to protect your Internet Guard Dog
information.
• Personal and financial information that you want to protect from being
sent out over the Internet without your knowledge:
•Name
• Address
• Social Security number
• Telephone number
• E-mail address
• Other financial numbers such as bank account, brokerage account,
credit card, phone card, and so on.
• Any Web site login names and passwords that you want to store in
Password Manager.
• Information about other users of your computer. If you are the
Administrator, you can create user profiles and set protection settings that
Internet Guard will use whenever the user is browsing the Internet via
your computer. See “How Internet Guard Dog Administrator works” on
page 17.
For optimal protection by Identity Protector, include all dashes (such as Social
Security number, bank account numbers, brokerage accounts, and ATM
cards). For example, if you enter 123-45-6789 as your social security number,
Guard Dog will recognize the number with or without the dashes. If you enter
123456789, Guard Dog won’t alert you if the number is sent out with dashes
(123-45-6789). Credit cards do not need dashes because you type the numbers
into separate boxes.
16 Internet Guard Dog
Page 27

Quick Tour of Internet Guard Dog™
NOTE: You can fine-tune the configuration of Internet Guard
Dog’s privacy and security features in the Protection Settings. Click
Options on the Internet Guard Dog Home screen, then click
Protection Settings.
How Internet Guard Dog Administrator works
Since Internet GuardDog nowoffers multi-userlogon capabilities,this feature
allows one userto act as the administratorof personal information, protection
and security settings entered via the Internet Guard Dog features. This is
particularly useful if for example, you would want to filter, block or monitor
certaintypes of informationthat you donot want your children toaccesswhen
browsing the Internet.
Creating an Internet Guard Dog Administrator account can only be done in
the Interview feature of Internet Guard Dog. And only the designated
Administrator can access and change information and protection settings of
the computer.
After this setup is complete, the Administrator can add other users and set the
levels of security and protection for each user profile.
See the Internet Guard Dog online Help to view step-by-step instructions on
how to set an Administrator account.
Self-Administrator
The Internet Guard Dog Administrator may designate another user as a
Self-Administrator.Thisfeaturemaybeusedifforexample,theuserisan
adult and is deemed responsible enough to customize his privacy and
protection settings on his own.
This user can access Internet Guard Dog features and change his settings, not
anyone else’s.
See the Internet Guard Dog online Help to view step-by-step instructions on
how to designate a user as a Self-Administrator.
NOTE: In adding user profiles, the Administrator can designate a
user as a Self-Administrator.
User’s Guide 17
Page 28

Quick Tour of Internet Guard Dog™
How password protection works in Guard Dog
Whenever you start Windows, Internet Guard Dog prompts you to enter the
password you set during the Interview. When you enter an incorrect
password, it displays the hint that you provided when you created your
password.
Without the passwordyou can stillopen the GuardDogHome screen,but you
won’t be able to change your CheckUp Settings or Protections Settings. Also,
Internet Guard Dog won’t let you use the Password Manager information in
Browser Buddy or send out information protected by Identity Protector.
WARNING: Do not forget your password. If you do, you’re only option
is to reinstall Internet Guard Dog and start all over. You will lose your
previous Internet Guard Dog settings, Password Manager information
and won’t be able to use any of your encrypted files.
Using the Internet Guard Dog Home screen
After the interview ends, Internet Guard Dog displays its Home screen
(Figure 3-2).
18 Internet Guard Dog
Figure 3-2. Internet Guard Dog Home screen.
Page 29

Quick Tour of Internet Guard Dog™
Table 3-1. Actions you can perform in the Home screen
To do this Click this
Add, edit or delete user profile; set Internet
filtering and other options.
Perform or schedule a virus scan. VirusScan. This launches the
Perform a security check to find any privacy or
security problem on your computer.
Display user activity logs Activity Logs
Display the McAfee Software Home screen in
your Web browser.
Display the McAfee Software Support page in
your Web browser.
Access the McAfee Web site. McAfee.com
Display the Support FAQ page in your Web
browser.
Initiate update of Internet Guard Dog and
McAfee VirusScan components installed on
your computer.
Create an e-mail message addressed to
McAfee Software Technical Support site.
Launch the Internet Guard Dog Help file. Help, then select either Help
User Setup
McAfee VirusScan
Security Check
Help, then select McAfee
Software on the Web
Help, then select Internet
Guard Dog on the Web
Help, then Frequently Asked
Questions
Update. This launches the
McAfee Software Update
Finder
Help, then Report a problem
Topics or Help for this screen
Display Internet Guard Dog product version
number.
Close the Internet Guard Dog Home screen.
(This doesn’t affect the monitoring portion of
Internet Guard Dog, which continues to run.)
Help, then About
Closebuttoninthe
upper-right corner of
the Internet Guard Dog
window.
NOTE: If your dial-up Internet account is not set up to dial
automatically, connect to the Internet before you use any of the
Web-based Help commands.
User’s Guide 19
Page 30

Quick Tour of Internet Guard Dog™
How User Setup works
The Internet Guard Dog Administrator can add, edit and delete profiles of
other users who browse the Internet through the same computer. After
profiling users, the Administrator can customize their individual protection
settings, including Internet filtering options and can even monitor their
browsing habits.
User Profile
To customize protection settings for another user, click User Setup from the
Internet Guard Dog Home page, the User Setup screen is displayed. You can
add, edit or delete a user’s profile from this screen. Click any of the buttons
available and follow through the instructions displayed on screen.
Figure 3-3. User Setup screen
See the Internet Guard Dog online Help to view step-by-step instructions on
how to add, edit or delete a user’s profile.
20 Internet Guard Dog
Page 31

How Internet Filtering works
As a new feature of Internet Guard Dog, you can further customize the
protection settings of a profiled user via the Internet Filtering options.
Fromthe User Setupscreen, selecta user; click EditUser Options; then click
the Internet Filtering button.
Content Filter
After launching Internet Filtering, the Content Filter screen i s displayed. This
screen allows you to quickly enable or disable Internet Guard Dog filters.
• Allow Internet Access. Select this option if y ou want the user to access to
the Internet at all tim es.
• Filter Web Access. Select this option if you want to limit the user’s access
to the Internet.
• Use Search Cleaner. Select this option if you want Internet Guard Dog to
automatically filter certain contents (e.g., words and phrases).
• Enable Ad Blocker. Select this option if you want Internet Gu ard Dog to
block certain ads that you do not want the user to view.
Quick Tour of Internet Guard Dog™
• Allow Chat. Select this option if you want to allow the user to go into
online chat rooms.
• Filter Chat. Selectthis option ifyou wantto allow the usertogo into online
chat rooms but filter certain contents (e.g., words and phrases).
Internet filtering
You can also set specific Internet filteri ng options. Click the Internet Filtering
button and select via the following drop-down menuoptions:
• Content Ratings. This option allows you to control what kind of Web
contents the user is allowed to view.
• URL List. This option allows you to control what Web sites the user is
allowed or not allowed to view.
• Word List. This option allows you to filter Web sites and chat messages
using words and phrases.
• Access Times.Thisoptionallowsyoutocontrolthetimesthatauseris
allowed access to the Internet.
See the Internet Guard Dog online Help to view step-by-step instructions on
how to set any of these Internet filtering options.
User’s Guide 21
Page 32

Quick Tour of Internet Guard Dog™
Figure 3-4. Internet Filtering screen (URL List)
How Privacy and Security options work
Internet Guard Dog allows you todetermine levels of privacy and security
using a series of configurable options called Protection Settings. A part of
Internet Guard Dog is always on duty in the background to protect your
computer’s data and your privacy based on the choices you make. Internet
Guard Dog displays settings on a series of Protection Settings pages
containing check boxes, list boxes, buttons, and other controls that you can
use to enter settings.
Privacy features Security features
Identity Protector Gatekeeper
Cookie Blocker File Guardian
Web Trail Cleaner Password Manager
Search Protector
For more information, see Chapter 4, “Privacy Features” and Chapter 5 ,
“Security Features.”
22 Internet Guard Dog
Page 33

Internet Guard Doghas a database of URLsites, extensive word list aswell
as a new rating system to use in protecting users fromInternet privacy and
security threats.The Administrator can also set thetime andday that auser
can have access to the Internet.
See the Internet Guard Dog online Help for more information and
step-by-step instructions on how to set its Internet filtering options.
Options
The Options button in the User Setup screen allows you to access and
change settings of specific Internet Guard Dog features such as changing
passwords and alert message sound effects.
See the Internet Guard Dog online Help for more information and
step-by-step instructions on how to change settingsvia this feature.
Using McAfee VirusScan
Internet Guard Dog now uses the McAfee VirusScan to address virus-related
problems you may encounter through the Internet. This feature allows you to
set how to perform a virus scan operation on your computer; what to do if a
virus isfound; and how it should alert you once thevirus is detected. You can
also direct VirusScan to keep a recordof actions performedon yourcomputer.
Quick Tour of Internet Guard Dog™
For more information, see Chapter 6, “McAfee VirusScan.”
Viewing Activity Logs
Internet Guard Dog now provides alist ofactivities that an Administrator can
view via theActivity Logsfeature. This listis generated basedon his preferred
security and privacy settings for himself and for other profiled users he
created. Anything from dates and time that a user logged on, to PC
maintenance, and violation (e.g., a user attempting to pass a credit card
number) can be viewed at the single click of a button.
TheAdministratorcanprint,saveorclearthislistwhichcontainanyofthe
following:
• Violation
Displays any activity of a profiled user that violates any of the preset
protection settings that the Administrator has indicated (e.g., attempting
to pass a credit card number).
User’s Guide 23
Page 34

Quick Tour of Internet Guard Dog™
• Maintenance
Displays list of actions that Internet Guard Dog performed including the
specific feature used to complete the task.
• Activity
Displays identity of profiled user who browsed the Internet using the
computer. It also displays the day, date and time that the user logon and
off on the computer.
NOTE: For step-by-step instructions on working with any of the
report logs, see Internet Guard Dog online Help.
Updating Internet Guard Dog and VirusScan
Internet Guard Dog can keep up with new viruses and Internet threats when
you update its program files and virus patterns over the Internet.
NOTE: If you purchased Internet Guard Dog on CD, you should run
Update even if you’ve just installed Internet Guard Dog. In the time
between when the CD was created and when you installed it, new virus
patterns are likely to be available.
To update the Internet Guard Dog program or virus patternfiles
McAfee Software programs now include a central location for launching the
product’s components. For Internet Guard Dog, you can also initiate their
updates from the Homescreen. Click the Update buttonin the Home screen.
InternetGuard Dog’s update applet willlaunch and searchesfor anyavailable
update. If an update is available, information is displayed.
24 Internet Guard Dog
Page 35

Performing a Security Check
After completing the interview, you’ll want to find out how your PC may be
at risk. Security Check examines your PC for privacy and security problems
and then guides you through fixing any problem it finds. If you are using the
settings suggested by Internet Guard Dog in the interview, you only need to
run Security Check right after installation and then every month or so. If you
reduce the levelof protection, youshould run Security Check morefrequently.
You can also change the Security Check settings to customize how you want
this feature to work on your computer.
To perform a Security Check
1. Click Security Check on the Internet Guard Dog Home screen. After security check is complete, Internet Guard Dog displays a report
describing any problems it discovered. (Figure 3-5 on page 25)
Figure 3-5. The Guard Dog Report screen
Quick Tour of Internet Guard Dog™
2. To view a problem that Internet Guard Dog has identified, highlight the item and click Fix.
3. Read the Internet Guard Dog recommendation and then click the
appropriatebutton. If you w ant more information, click Help, then click
Help for this screen.
A check mark appears next to each problem that you fix.
User’s Guide 25
Page 36

Quick Tour of Internet Guard Dog™
4. Repeat steps 2 and 3 for each problem that you want to fix.
5. When you have finished, click the Back or the Home button to return to
the Internet Guard Dog Home screen.
What Internet Guard Dog does while your PC is running
While you use your PC, Internet Guard Dog is on the lookout for potential
privacy and security problems and takes action when it finds a problem.
(Internet Guard Dog uses the information stored in Protection Settings to
determine what to monitor and how to react.) You can tell when Internet
GuardDogisworkingbecauseitsiconappearsintheWindowstaskbaras
shown in Figure 3-6.
Figure 3-6. The Internet Guard Dog icon in the taskbar.
Right-click to display the
InternetGuard Dog shortcut
menu
NOTE:If you see an InternetGuard Dog alertmessage, see “Responding
to Internet Guard Dog alert messages” later in this chapter.
Using the Internet Guard Dog shortcut menu
Evenwhen you aren’t runningthemain Internet Guard Dogprogram, youstill
have quick access to several features using the shortcut menu. Right-click the
Internet Guard Dog icon on the Windows taskbar to display this menu. You
canthendoanyofthefollowing:
• Start the Internet Guard Dog main program.
• Display Browser Buddy, which lets you retrieve your Internet passwords
and displays statistics on how many cookies have beenallowed orblocked,
and how often it has cleared search information.
• Display Windows help for Internet Guard Dog.
• Encrypt and decrypt files that File Guardian protects.
• Close the part of Internet Guard Dog that monitors your PC while
Windows runs.
26 Internet Guard Dog
Page 37
Quick Tour of Internet Guard Dog™
Responding to Internet Guard Dog alert messages
Internet Guard Dog works as you work to protect your privacy and security.
When Internet Guard Dog detects a potential problem, it either handles the
problem automatically or warns you with an alert message based on your
Internet Guard Dog settings.
Each alert message tells you what potential problem triggered the message
and Internet Guard Dog’s recommendation on how to respond. If you want
more information about theproblem, clickthe Question Mark button and then
click anywhere inside the alert message.
If you find over time that you are being alerted to potential security risks too
often, you can adjust the alert message settings in Protection Settings. Cookie
Blocker andGatekeeper require a period of adjustment before Internet Guard
Dog has learnedt o address your concerns withthe least amountof disruption.
TIP: If you decide you no longer want to see an alert message, use the
question mark (?) button in the alert message to find out what setting to
change. All of the settings that control the alert messages are located
under Protection Settings in the Options menu.
Using Browser Buddy to retrieve or store your Web site passwords
You can depend on Internet Guard Dog to help you easily navigate through
the intricacies of the Web. For example, when you connect to Web sites that
require a name and pass word, you can use Browser Buddy to:
• Drag your username or password f rom Password Manager and drop it on
the login form for the Web site.
• Add new password information for a Web site.
Browser Buddy can also tell you how many cookies have been allowed or
rejected by Cookie Blocker and how many times a search information you
initiated from one Web site, has been blocked by Search Protector from b eing
passed to another Web site.
TIP: Browser Buddy always remains displayed on top of any programs
open on your screen. If Browser Buddy is located in an awkward
position, you can close it and reopen it as needed.
User’s Guide 27
Page 38

Quick Tour of Internet Guard Dog™
To open Browser Buddy
1. Right-click the Internet Guard Dog icon on the Windows taskbar, then
click Browser Buddy. The dialog box is displayed.
To add a new username and password
Figure 3-7. Browser Buddy
1. In Browser Buddy, select Add New Entry from the Password Manager
2. In the Web site text box, enter the Web site address; in theUsername text
3. In the Password text box, type the password that confirms your identity.
4. Click OK.
To retrieve your username and password
1. In Browser Buddy, select the site name if it doesn’t appear automatically
2. Drag your username or password from the Password Manager box to
28 Internet Guard Dog
drop-down list. The Enter password to save dialog box is displayed.
box, type the name by which you identify yourself to this Web site, this
may correspond toUser Name, Member ID, MemberName, Login ID, or
Login Name, and so on.
(In Password Manager, Internet Guard Dog displays one asterisk for
each character in your password.)
in the Current Web Site list.
appropriate field in your Web site’s login form.
Page 39

The text appears in the field. (If the site that you are logging into displays
your password text as a series of asterisks (*), Internet Guard Dog will
display one asterisk for each character in your password.)
3. Continue logging in as usual to the Web site.
Using file encryption
File encryption translates a file into a “secret” code that makes the file
unreadable. You must decode or decrypt thefilebeforeyoucanuseit.Thefile
encryption in Internet Guard Dog is designed so that you caneasily encryptor
decrypt all of the files that you designate for encryption in File Guardian.
NOTE: Before you can encrypt a file, you must add it to the Guarded
Files list in File Guardian. For step-by-step instructions on adding a file
to the Guarded Files list, see Internet Guard Dog Help.
To encrypt or decrypt files
• Right-click the Internet Guard Dog icon on the Windows taskbar, then
click Encrypt File Guardian files or Decrypt File Guardian files.
Quick Tour of Internet Guard Dog™
User’s Guide 29
Page 40

Quick Tour of Internet Guard Dog™
30 Internet Guard Dog
Page 41

4Privacy Features
Internet Guard Dog’s Privacy features protect browsing and personal
informationthat you don’t want anybodyto accessas a resultof your surfing
through the Internet.
What Cookie Blocker does
Cookies are smallfiles that your Web browserstores onyour PC at the request
of a Web server. Each time you view a Web page from the Web server, your
browser sends the cookie back to the server. These cookies can act like a tag,
which lets the Web server track what pages you view and how often you
return to them. Some Web sites, such as Microsoft Expedia
store your password and preferences so that you can automatically log on to
the site. For a more detailed description of cookies, see “What are cookies and
how are they used?” on page 65.
Internet Guard Dog’s Cookie Blocker offers three options for controlling the
use of cookies on your computer. Internet Guard Dog can:
• Reject all cookies.
• Accept all cookies.
™
,usecookiesto
4
• Display an alert message each time a cookie is sent to your browser. The
alert displays the name of the entity trying to set the cookie, and provides
you the option either to acceptthe cookie or not.
When setting up Cookie Blocker in Protection Settings, you can select one
optionfor direct sitesand another forindirectsites.Direct sites are those that
you deliberately access. For example: typing the URL address in the
location bar of your Web browser; clicking a link in a Web page; or
selecting from your list of bookmarks or favorite sites. Indirect sites are
those that you access because the site you are connecting to directly
displays content from another site as part of its own content. For example,
if you went directly to Cool_site.com, it could display an ad from
Ads-r-us.com (the indirect site) in a separate frame in the Cool_site page.
If during the Interview, you accepted Internet Guard Dog’s
recommendation on how to respond to cookies, Cookie blocker will:
• Automatically allow cookies to be accepted from direct sites.
• Display an alert message when an indirect sites tries to set a cookie.
User’s Guide 31
Page 42

Privacy Features
Responding to a Cookie Blocker alert message
If during the Interview, you set Internet Guard Dog to prompt you for action
then it will display the Cookie Blocker alert message the first time a site tries
to set a cookie.
You can respond to the alert message in the following ways:
Table 4-1.
If you choose Internet Guard Dog
Accept always Accepts the cookie and adds the site to the
Allowed list. The next time you go to that site,all
cookies from that site are allowed automatically.
Never accept Rejects the cookie and adds the site to the
Rejected list. The next time you go to that site, all
cookies from that site are refused
automatically.(In some cases, the cookie may be
written to your local hard disk, but your privacy
is protected because thecookie is never sentback
to the requestingpage.)
Each time you visit a site that appears in either the Allowed or Rejected list,
Internet Guard Dogadds thenumber of cookiesaccepted or rejectedto the list.
You can see the totals for a Web site in the Browser Buddy.
If you change your mind about a site, you can remove it from the Allowed or
Rejected list in the Cookie Blocker settings. The next time that you visit that
site it will be as if you are visiting it for the first time. If you want to remove
cookies for a site from which you’ve previously accepted cookies, run a
Security Check and remove the cookies for that site.
32 Internet Guard Dog
TIP: You can run Security Check so that it only looks for cookies. On the
Internet Guard Dog Home screen: click the Options menu; select
CheckUp Settings; then clear all optio ns except Cookie Check. After you
are finished with the CheckUp, don’t forget to change back your settings.
Page 43

Privacy Features
Why should I change my Cookie Blocker settings?
If you want a good level of privacy protection without having to see any
Cookie Blocker alertmessages, use therecommended settings—always accept
cookies from sites that you visit directly and decide on a case-by-case basis
whether to accept cookies coming from sites that you haven’t visited directly.
You may also change your settings under specific circumstances (see Table
5-2).
Table 4-2.
If you Use this option
Want the least number of
cookies set and highest
assurance of privacy.
Always want to know when
cookies are sent.
Are not concerned at allabout
cookies.
Reject for both Direct Sites and Indirect Sites.
If a site requires you to accept a cookie, you can
change this setting temporarily to Prompt.
Prompt for both Direct Sites and Indirect Sites.
Be prepared to respond to a large number of
alert messages.
After you respond to the Cookie Blocker alert
message, you won’t see additional alert
messages for that site.
Either turn off Cookie Blocker or change the
Indirect Sites setting to Accept.
You should choose the second method if you
want to keep a total of the cookies added to
your PC, which you can view in the Browser
Buddy.
What Identity Protector does
It is easy to forget that when you sendinformation over the Internet, it doesn’t
go directly from your computer to the computer that is storing the Web page
information. Instead, the information can pass through many computers
before it reaches its final destination.
Identity Protector can keep your software from sending any personal
information over the Internet to an unsecure site. Although you don’t have to
worry about a sitewhen itusing asecure connection, there are many Web sites
that use a secure connection only when dealing with credit card transactions.
(For more information, see “Privacy on the Web” on page 58.)
User’s Guide 33
Page 44

Privacy Features
If more than one person is using your computer, make sure that you create an
Internet Guard Dog password. If the person using your computer doesn’t
enter the Internet Guard Dog password, it automatically replaces any
protected personal information sent to an unsecure site with the text, “xxxx.”
For example, if your child tries to order the latest CD without entering your
Internet Guard Dog password, it replacesyour credit card number with “xxxx
xxxx xxxx xxxx.”
Identity Protector offers three optional responses whenever an application
tries to send out information over the Internet to an unsecure site:
• Let the information go out.
• Block the information from going out.
• Display an alert message when any application tries to send the
information over the Internet to an unsecure site. This is the response that
Internet Guard Dog sets up when you add information to protect in the
Internet Guard Dog Interview.
Responding to an Identity Protector alert message
During the Interview, Internet Guard Dog asked you to enter your personal
and financial information that you want to protect. Internet Guard Dog
displays the Identity Protector alert message the first time an application tries
to send out this information to an unsecure site.
You can respond to the alert message in the following ways:
If you choose Internet Guard Dog
This time only Allows the information to go out just this time.
Not this time Prevents the information from going out this
34 Internet Guard Dog
Table 4-3.
time.
Page 45

Privacy Features
Why should I change my Identity Protector settings?
You may want to change your settings under the following circumstances:
Table 4-4.
If you Use this option
Are the only person using
your PC and you don’t
want to be alerted every
time.
Have more than one
person using your PC.
Youwanttobewarned
any time this information
is being sent out.
Enter all of the information that you want to
prevent from going out and select Allow Always.
Create an Internet Guard Dog password. If the
Internet Guard Dog password is not entered after
you st art Windows, an unauthorized user of your
PC can’t view or send out your personal
information.
Enter all of the information that you may want to
prevent from going out andselect AllowAlways or
Ask Before Blocking. For information that you
always want to prevent from going out, select
Block Always.
Create an Internet Guard Dog password. If the
Internet Guard Dog password is not entered after
you start Windows, any information entered in
Identity Protector will be blocked from being sent
out.
Enter all of the information that you may want to
prevent from going out and select Ask Before
Blocking.
NOTE:When InternetGuard Dogasks foryour passwordand youenter
it, the password stays in effect until you restart Windows. If you’ve
entered your password and want to block others from sending out your
personal information, restart Windows before letting anyone else use
your PC.
User’s Guide 35
Page 46

Privacy Features
What Web Trail Cleaner does
As you surf the Internet, your browser stores information that makes your
browsing experience more satisfying. It uses the information as follows:
Table 4-5.
Your browser uses To
Cached files Speed up the display of Web page elements such
as graphics.
URLs visited Display a list of sites that you’ve visited using
Web addresses.
History Display a list of sites that you’ve visited using
Web site names.
The files left on your PC can be viewed by others and depending on your
browser’s settings, can take up many megabytes of disk space.
If you accepted Internet Guard Dog’s recommendation during the interview,
Internet Guard Dog displays the Web Trail Cleaner alert message when you
close your browser.
Responding to the Web Trail Cleaner alert message
You can respond to the alert message in the following ways.
Table 4-6.
If you choose Internet Guard Dog
Clean Deletes all of the cached files, history and URL
information associated with the selected Web
site (Domain).
Select a site for cleaning by selecting the check
box next to the site name.
Don’t clean Closes the Alert message and continues closing
your browser.
By default,Internet Guard Dog selects the sites that are not bookmarked (that
is, part of your list of favorite sites) because it is less likely that you’ll returnto
these sites. If you don’t return to a site, the cached files for the site are never
used again—they just sit and take up disk space until they are ultimately
deleted by your browser.
If you later want to delete the files that you’ve left behind, run the Internet
Guard Dog Security Check.
36 Internet Guard Dog
Page 47

Privacy Features
Why should I change my Web Trail Cleaner settings?
You may want to change your settings under the following circumstances:
Table 4-7.
If you Use this option
Want to see exactly what files
are being deleted.
Want to remove all traces of
your browsing.
Want to remove files only for
Web sites that you haven’t
bookmarked or added to your
list of favorites.
What Search Filter does
When you perform a search in your Web browser, the search information is
displayed in the address box of your Web browser. When you go to another
site, the browser retains the search information and the next site you visit can
extract it without your knowledge. Search Filter blocks this information from
being passed along to the next site.
If you have Search Filter selected in the Security Settings of Internet Guard
Dog, it automatically removes search information before you go to another
Web site. Internet Guard Dog does not display an alert message for this
feature, but you can see the number o f times Search Filter blocks this
information in the Browser Buddy.
Prompt to Clean Up after closing Web browser.
Automatically Clean Up after closing Web
browser. (Clear the check box for “Keep
bookmarked items.”)
Automatically Clean Up after closing Web
browser.
Keep bookmarked items.
User’s Guide 37
Page 48

Privacy Features
38 Internet Guard Dog
Page 49

5Security Features
Internet Guard Dog’s security features safeguard your Internet connection
and protect the files on your PC from prying eyes and destructive programs.
What Gatekeeper does
Gatekeeper lets you control what programs on your PC can have access to
your Internet connection. Gatekeeper can also warn you about any of these
potentially harmful actions:
• Your browser is directed to a harmful site—one that has been known to
contain virus-infected files (e.g., Trojan horses, prank or destructive
ActiveX controls, or other security concerns).
• A program silently uses your modem to connect to another computer.
• A program starts up another program.
• A program sends out over the Internet a number that follows a common
credit card number pattern.
Responding to Gatekeeper alert messages
5
Internet Guard Dog can d isplay five different Gatekeeper-related alert
messages. If you are usingthe defaultsettings suggestedby theInterview, you
will see the messages related to Internet access, harmful sites, programs
starting another program, and programs sending out credit card-like
numbers.
Internet access alert message
Each time you start a program that attempts to use your Internet connection,
Internet Guard Dog checksto see if that program is in the list of programs
allowed to access the Internet. If the program is not in the list, Internet Guard
Dog displays an alert message to tell you that the program is trying to connect
to the Internet and asks you how to deal with the program.
Because Internet Guard Dog displays an alert the first time you start an
Internet program, you may want to start each of the Internet-connected
programs you use regularly in order to get those alerts out of the way at one
time.
User’s Guide 39
Page 50

Security Features
You can respond to the Internet access alert message in the following ways:
Table 5-1.
If you choose Internet Guard Dog
This time only Allows the program to access the Internet this time
only and warns you the next time it tries to access the
Internet.
Allow always Allows the program to access the Internet at any time.
In Protection Settings for Gatekeeper, the program is
added to thelist of programsallowed to automatically
access the Internet. If you decide later that you do not
want this program to use your Internet connection,
select its name and click Remove.
Not this time Prevents the program from accessing the Internet.
This choice stays in effect until the next time you
restart Windows or for Internet Explorer 4 users, until
you close your browser.Use this option if you want
Internet Guard Dog to warn you the next time the
program tries to access the Internet.
Harmful site alert message
Before you can connect to a harmful site, Internet Guard Dog will display an
alert message, “Your browser is visiting Sitename,aWebsitethatmayharm
your PC or data.”
You must immediately close your browser to end your browser’s connection
tothissite.Thefasteryoucloseyourbrowser,thelesstimethesitehasto
transfer harmful data to your PC.
If you want to view the Web site anyway, click Continue.
Program starts up another program message
When another program starts to run another program, Internet Guard Dog
checks to see if you’ve authorized this action. If you haven’t allowed the
program to always open the other program, Internet Guard Dog displays an
alert message.
40 Internet Guard Dog
Page 51

You can respond to the alert message in the following ways:
Table 5-2.
If you choose Internet Guard Dog does this
Allow always Allows the program to start the other program.
Not this time Prevents the program from starting the other
program just this time.
This time only Allows the program to start the other program
just this time.
Any credit card number goes out message
When a program sends a number resembling a credit card number over the
Internet, an alert message is displayed.
You can respond to the alert message in the following ways:
Table 5-3.
If you choose Internet Guard Dog
Security Features
Not this time Prevents the program from sending the number
this time.
This time only Allows the program to send the number just this
time.
User’s Guide 41
Page 52

Security Features
Why should I change my Gatekeeper settings?
The Gatekeeper settings suggested by the Interview will display the fewest
number of alert messages. If you are using an older browser version or just
want a higher level of security, you may want to change your settings under
the following circumstances:
Table 5-4.
If you Use this option
• Want to be warned when the site that you are
going to has been known to cause damage,
e.g. containsvirus-infected files,Trojan horse,
prank or destructiveActiveX controls, or other
security concerns. (To keep Internet Guard
Dog’s list ofharmful sitescurrent and effective,
use Update monthly.)
• Want to be warned when a program is using
your modem to dial out.
• Want to be warned when a program starts up
another program.
Many newer programs will warn you before
doing this, but older programs may not do so.
For example, Internet Explorer 4 uses “helper
programs” to display documents.
• Want to be warned before any number that
resembles a credit card number is sent out
over the Internet.
To protect specific numbers, see “What
Identity Protector does” on page 33.
• Want to see a list of what programs you have
allowed to automatically access the Internet.
(A program is added to the list when you click
Accept Always in the Internet access alert
message.)
If you change your mind, you can remove a
program from the list. You will be warned the
next time that program tries to access the
Internet.
Going to harmful sites.
My modem dials silently.
Program tries to launch
another program.
Any credit card number
goes out.
These programs are always
allowedaccesstothe
Internet
42 Internet Guard Dog
Page 53

What File Guardian does
File Guardian can protect files that contain your sensitive data from being
opened, renamed, copied, moved, or deleted. For added protection, you can
even encrypt files protected by File Guardian. Internet Guard Dog can also
alert you if a program attempts one of the following potentially harmful
activities:
• A program attempts to reformat your hard drive.
• An ActiveX control attempts to delete files on your hard drive.
• An ActiveX control attempts to scan files on your hard drive.
• A program attempts to access your system password files.
When Internet Guard Dog displays an alert message, you can decide if the
program shouldbe allowed to continue the operation or not.
Responding to File Guardian alert messages
Internet Guard Dog can d isplay five different File Guardian-related alert
messages. If you are using the default setting suggested by the Interview, you
will only see: guarded file; ActiveX scan; ActiveX delete; and drive format
messages.
Security Features
Guarded file alert message
Using File Guardian, you can set which files to guard on your hard drive and
what programs can be used to open the files. If an unauthorized application
attempts to access a guarded file, Internet Guard Dog displays an alert
message that tells you what application is trying to open which file.
You canthen decide whether you want to give the program in question access
to the file. If you did not run the unauthorized program yourself, you should
immediately investigate the program to determine its source.
If you choose Internet Guard Dog
Allow always Permits the program to open the file and adds
Not t his time Stops the program from opening the file and
Table 5-5.
theprogramtothelistofprogramsthatare
authorized to access the file without further
warnings.
warns you the next time the program tries to
open the file.
User’s Guide 43
Page 54

Security Features
ActiveX scan alert message
There are legitimate reasons for allowing an ActiveX control to read through,
or scan, all of your files. For example, you can go to one site on the Web that
uses an ActiveX control to look for viruses on your PC. However, if a site
begins to scan your files without warning you, Internet Guard Dog gives you
a chance to think about how much you trust the site.
When Internet Guard Dog detects an ActiveX control scanning the files on
your PC, it displays an alert message that tells you what ActiveX controls is
scanning your hard drive.
You can respond to the alert message in the following ways:
If you choose Internet Guard Dog
Not this time Stops the ActiveX control from running this
This time only Permits the ActiveX control to scan your drive
Table 5-6.
time.
If you change your mind, reloadthe page inyour
browser and click This time only the next time
Internet Guard Dog displays its ActiveX scan
message.
just this time.
ActiveX delete alert message
There are legitimate reasons forallowing anActiveX control to deletefiles. For
example, if a control installs special software on your PC to let you interact
with its Web site, the control may need t o delete files that it created for
temporary use. However, if a site doesn’t warn you and begins to delete files,
Internet Guard Dog gives you a chance to see what file is being deleted and
think about how much you trust the site.
When Internet Guard Dog detects an ActiveX control deleting files on your
PC, it displays an alert message that tells you the name of the control.
44 Internet Guard Dog
Page 55

You can respond to the alert message in the following ways:
If you choose Internet Guard Dog
Not this time Stops the ActiveX control from running this
This time only Permits the ActiveX control to delete files just
Drive format alert message
When a format command is started, Internet Guard Dog doesn’t know
whether you told your PC to form at a Zip disk or whether a rogue ActiveX
control has started to format your hard disk. You know that this activity is
legitimate when you start the formatting command or if you know that a
program you are using needs to format a hard disk (or a Zip or Jaz disk).
Security Features
Table 5-7.
time.
If you change your mind, reloadthe page inyour
browser and click Allow this time the next time
Internet Guard Dog displays its ActiveX delete
message.
this time.
When Internet Guard Dog detects a format command, it displays an alert
message that tells you which program started the format command.
If you don’t know why your disk is being formatted, note the name of the
program inthe alert message andthen turnoff yourcomputer using its power
switch. If the program has the letters OCX as part of its name, it is an ActiveX
control.Do not restartyour browser untilyou have runan Internet GuardDog
CheckUp and removed the suspicious ActiveX control from your PC.
Continue if you want the program to format your disk.
Click
User’s Guide 45
Page 56

Security Features
Why should I change my File Guardian settings?
You may want to change your settings under the following circumstances:
Table 5-8.
If you Use this option
• Want to be warned when an ActiveX control
looks through the files on your PC.
This may happen legitimately if the control
needs to find a file to use. If you are
concerned, check with the site that sent you
the control.
• Want to be warned when an ActiveX control
deletes a files.
This may happen legitimately if the control is
deleting older or temporary files that it uses. If
you are concerned,check with the site that
sent you the control.
• Want to be warned when any program tries to
format any of your drives.
An alert message appears whenever you
format a floppy disk, other removable media,
or hard disk. You may want to turn this option
off temporarily if you are going to format a lot
of disks and don’t want to see any messages.
• Want to be warned when any program
accesses your Windows password files (i.e.,
any file with the .pwl extension locatedin the
Windows directory).
Windows functions that are
password-protected use these password files.
• Want to prevent any program from opening a
file or files. For further protection, you can
have Internet Guard Dog include the file when
you encrypt files.
You can protect individual files, files in a
specific folder, files of the same type, files on
thesamedrive.
ActiveX scans my drive
ActiveX deletes files from
my drive
My drive is being formatted
Password files are accessed
Guarded files
46 Internet Guard Dog
NOTE: For step-by-step instructions on adding, editing, or removing
files in the Guarded Fi les list, allowing a program to access a guarded
file, or encrypting or decrypting files, see Internet Guard Dog Help.
Page 57
What Password Manager does
Password Manager lets you store your various Web site login names and
passwords in one secure location. When you are visiting a Web site that
requires this information, you can drag it from the Browser Buddy to the form
displayed in your browser.
In Protection Settings, you can:
• View your list of stored login names and passwords.
• Add a record.
• Edit a record.
• Remove a record.
You can also add a record in the Browser Buddy. For more information, see
“Using Browser Buddy to retrieve or store your Web site passwords,” in
Chapter 3.
To add a password record
Security Features
1. In the Internet Guard Dog Home screen, click the Options menu, then
select Protection Settings.
2. Click Password Manager. (If the check box next to Password Manager is
not selected, you won’t be able to add, edit, or remove records.)
3. Click Add.
4. Type the information that you want to store in the record.
5. Click OK.
To edit a password record
1. In the Password Manager list, do one of the following:
• Double-click the record you want to edit.
• Click the record you want to edit, then click
2. Change the information that you want to store in the record.
3. Click OK.
Edit.
User’s Guide 47
Page 58

Security Features
To remove a password record
• In the Password Manager list, click a record to select it, then click
Remove.
48 Internet Guard Dog
Page 59

6McAfee VirusScan
What is McAfee VirusScan?
The VirusScan name applies both to the entire set of desktop anti-virus
program components describedin this chapter, andto a particular component
of that set: SCAN32.EXE, or the VirusScan “on-demand” scanner. “On
demand” means that you as a user control when VirusScan starts and ends a
scan operation, which targets it examines, what it does when it finds a virus,
or any other aspect of the program’s operation. Other VirusScan components,
by contrast, operate automatically or according to a schedule you set.
VirusScan originally consisted solely of an on-demand scanner—features
since integrated into theprogram nowprovide a cluster of anti-virus functions
that give you maximum protection against virus infections and attacks from
malicious software.
The VirusScan on-demand component operates in two modes: the VirusScan
“Classic” interface gets you up and running quickly, with a minimum of
configuration options, but with the full power of the VirusScan anti-virus
scanning engine; the VirusScan Advanced mode adds flexibility to the
program’s configuration options,including the ability to run more than one
scan operation concurrently.
6
Starting VirusScan
VirusScan comes with a single, default scan operation pre-configured and
ready to run. You can start this scan operation to look for vi ruses on your C:
drive immediately, or you can configure andrun your own scan operations to
suit your needs. VirusScanAdvanced alsocomes witha singlepre-configured
scan operation, which scans all of your local hard disks.
To start VirusScan, either
•ClickVirusScan from the Internet Guard Dog Home screen; or
•ClickStart in the Windows taskbar, point to Programs,thentoMcAfee
VirusScan.Next,chooseMcAfee VirusScan Central from the list that
appears.
If you want to use the VirusScan Classic window, either
• Afterlaunching VirusScan from theInternet Gu ard DogHome screen,click
Classic VirusScan;or
•ClickStart in the Windows taskbar, then choose Run from the menu that
appears. Type SCAN32.EXE in the Run dialog box, then click OK.
User’s Guide 49
Page 60
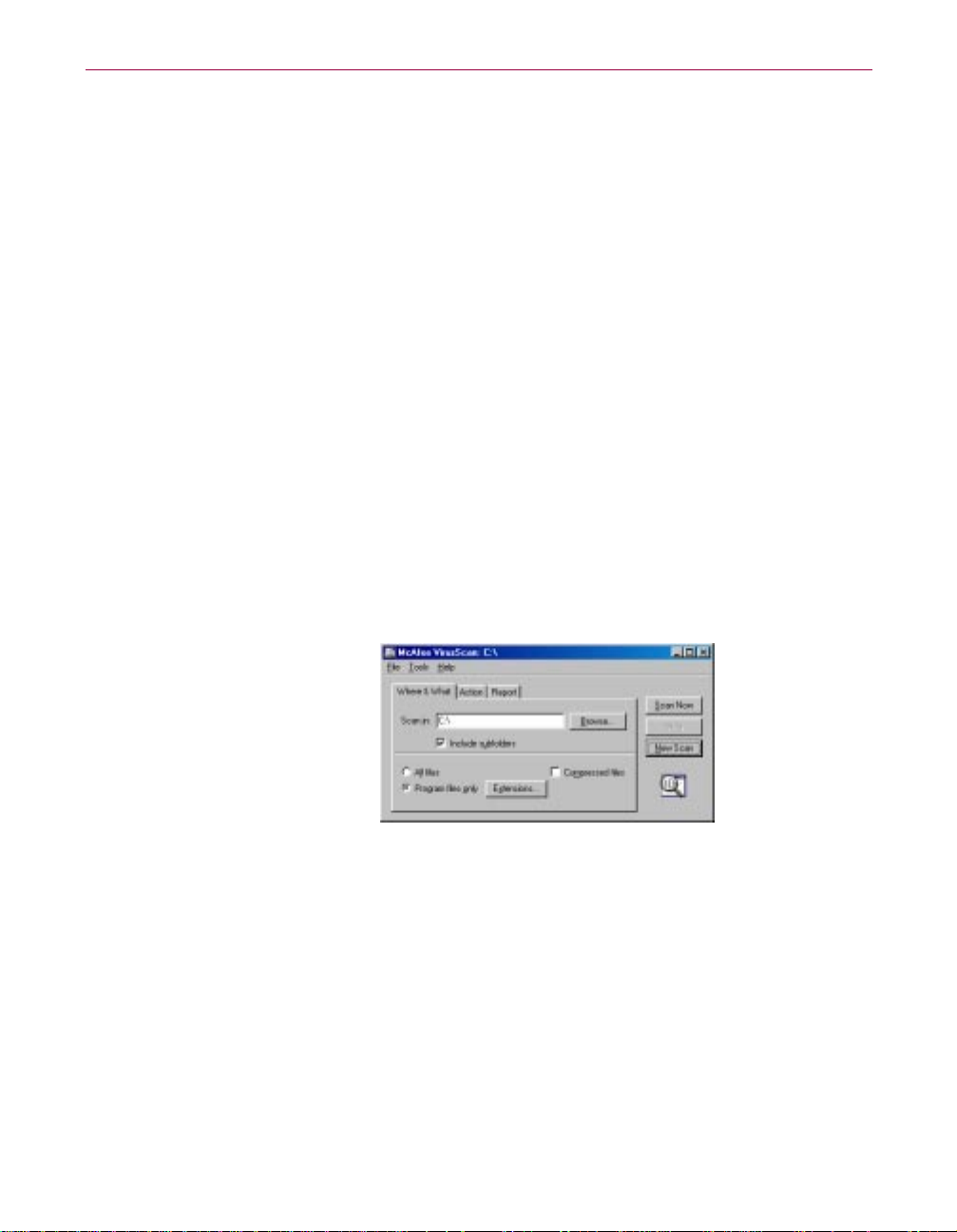
McAfee VirusScan
Any of these methods will launch VirusScan.
VirusScan Central window
After launching VirusScan from the Internet Guard Dog Home screen, the
VirusScan Central window is displayed. The following main features are
available to use:
•ClickScan to start the default scan task immediately, or configure a scan
task that suits your needs (see Configuring VirusScan).
•ClickScheduler to launch the McAfee VirusScan Scheduler. This utility
enables you to configure and run unattended scan operations.
•ClickQuarantine to display a list of quarantined files. The Quarantine
feature allows you to isolate an infected file in order to avoid spreading a
virus.
•ClickUpdate to check for updated versions of VirusScan and DAT files.
VirusScan Classic window
After launching VirusScan Classic window, you can click Scan Now at the
right of the window to start the default scan task immediately, or configure a
scan task that suits your needs by clicking the tabs at the top of the window
and choosing options in each property page.
The menus at the top of the VirusScan window allow you to change some
aspects of the program’s operation. You can:
• Save or restore default settings.
• Save new settings.
• Open the VirusScan activity log.
50 Internet Guard Dog
Figure 6-8. VirusScan Classic window
Page 61

Figure 6-9. VirusScan Activity Log
• Quit VirusScan.
• Change VirusScan modes.
• Activate password protection.
• Start VirusScan Scheduler.
• Open the online help file.
•
McAfee VirusScan
NOTE:
informationand step-by-stepinstructionson howto use any of
the features of the Classic window.
Configuring VirusScan
To perform a scan operation, VirusScan needs to know what you want it to
scan, what you want it to do ifit finds a virus, and how it should let you know
when it has. You can also tell VirusScan to keep a record of its actions.A series
of property pages controls the options for each task.
Options for each task
• Choosing Where & What options
VirusScan initially assumes that you want to scan your C: drive and all of
its subfolders, and to restrict the files it scans only to those susceptible to
virus infection
To modify these options, follow these guidelines:
See the McAfee VirusScan online Help for more
User’s Guide 51
Page 62

McAfee VirusScan
• Choose a volume or folder on your system or on yournetwork that
you want VirusScan to examine for viruses.
Click to expand the listing for an item shown in the dialog box.
Click to collapse an item. You can select hard disks, folders or
files as scan targets, whether they reside on your system oron other
computers on your network. You cannot select My Computer,
Network Neighborhood, or multiple volumes as scan targets from
VirusScan Classic—to choose these items as scan targets, you must
switch to VirusScan Advanced.
• Specify thetypes offiles you wantVirusScanto examine. Bydefault,
VirusScan looks for viruses in files with the extensions .EXE,.COM,
.DO?, .XL?, .MD?, .VXD, .SYS, .BIN, .RTF, .OBD, and .DLL. Files
with .DO?, .XL?, .RTF, .MD?, and .OBD extensions are Microsoft
Office files, all of which can harbor macro virus infections. The ?
character is a wildcard that enables VirusScan to scan both
document and template files.
• Choosing Action options
When VirusScan detects a virus, it can respond either by asking you what
it should do with the infected file, or by automatically taking anaction that
you determi ne ahead of time. You can specify which response options you
want VirusScan to give you when it finds a virus, or which actions you
want it to take on its own. These response options include:
52 Internet Guard Dog
• Prompt User for Action. Choose this response if you expect to be at
your computer when VirusScan scans your disk—VirusScan will
displayan alert message when it finds a virus and offer you the full
range of its available response options.
• Move infected files automatically. Choose this response to have
VirusScan moveinfected files to a quarantinedirectory as soon as it
finds them. By default, VirusScan moves these files to a folder
named INFECTED that it creates at the root level of the drive on
which it found the virus. For example, if VirusScan found an
infected file in T:\MY DOCUMENTS and you specified INFECTED
as the quarantine directory, VirusScan would copy the file to
T:\INFECTED.
You can enter a different name in the text box provided, or click
Browse to locate a suitable folder on your hard disk.
• Clean infected files automatically. Choose this response to tell
VirusScan to remove the virus code from the infected file assoon as
it finds it. If VirusScan cannot remove the virus, it will note the
incident in its log file.
Page 63

McAfee VirusScan
• Delete infected files automatically. Use this option to have
VirusScan delete every infected file it finds immediately. Be sure to
enable its reporting feature so that you have a record of which files
VirusScan deleted. You will need to restore deleted files from
backup copies. If VirusScan cannot delete an infected file, it will
note the incident in its log file.
• Continue scanning. Use this option only if you plan to leave your
computer unattended while VirusScan checks for viruses. If you
also activate the VirusScan reporting feature, the program will
record the names of any viruses it finds and the names of infected
files so that you can delete them at your next opportunity.
• Choosing Report options
By default, VirusScan beeps to alert you when it finds a virus. You can use
theReportpagetoenableordisablethisalert,ortoaddanalertmessageto
the Virus Found dialog box that appears when VirusScan finds an infected
file. This alertmessage cancontain any information, from asimple warning
to instructions abouthow to report the incidentto a networkadministrator.
This same page determines the size and location of VirusScan’s log file. By
default, the program lists its current settings and summarizes all of the
actions it takes during its scanning operations in a log file called
VSCLOG.TXT. You can have VirusScan write its log to this file, or you can
use any text editor to create a text file for VirusScan to use. You can then
open and print the log file for later review from within VirusScan or from
your text editor.
• Choosing Alert and Log options
You can select the types of alert methods you want VirusScan to use when
it finds a virus.
• Display a custom message. Select the Display message checkbox,
then enter the message you want to appear in the text box provided.
You can enter a message up to 225 characters in length.
NOTE:
To have VirusScan display your message, you must
have selected Prompt user for action as your response in the
Action option.
• Beep. Select the Sound alert checkbox.
User’s Guide 53
Page 64

McAfee VirusScan
You can also select the Log to file option. By default, VirusScan writes log
information to the file VSCLOG.TXT in the VirusScan program directory.
You can enter a different name and path in the text box provided, or click
Browse to locate a suitable file elsewhere on your hard disk or on your
network.
54 Internet Guard Dog
Page 65

AInternet Security and Privacy
This chapter provides some background information that will help you
understand Internet security and privacy threats, and discusses strategies for
using Guard Dog to protect yourself and your computer.
Networks and the Internet
A computer network links individual computers together so they can share
data and resources. To network, computers need some means of
connection—either a modem or a Network Interface Card (NIC—some
computers have NICs already built-in). The modem or NIC is responsible for
sending and receiving data through the network. Netw orks are sometimes
called local area networks (LAN) because they link the computers at a single
locale, such as an office or building. In a small office, computers can be linked
directly by connecting them together with cable. This very simple network is
called a peer-to-peer network, wherein all of the computers are equal to one
another. Windows has peer-to-peer networking capabilities built into the
operatingsystem. The increasedtraffic inlarger networksrequires theservices
of a special computer, called a server. Servers help larger networks operate by
figuring out how to route messages to the appropriate recipient.
A
The Internet is avast computer network, connecting computers together from
around world and allowing them to work together and share information.
When you connect to the Internet, your computer becomes a part of a
worldwide network of computers.
TCP/IP is the subsystem
The Internet is based on a system called Transmission Control
Protocol/InternetProtocol (TCP/IP).TCP allows computersto share data by
first breaking it down into little segments called packets. In addition to data,
each packet contains the address o f the machine sending the packet, and the
address of the intended recipient. The TCP part of the system is what is
responsible for addressing the data and breaking into packets. IP, the second
part of the system, is responsible for routing packets from the sending
computer to the recipient computer.Special computers called routers read the
address on each packet, and figure out how to route them to the appropriate
destination.
User’s Guide 55
Page 66

Internet Security and Privacy
Why packets?
Whygo through all this trouble,breaking data down into packets? Theanswer
lies in the origins of TCP/IP. Like the Internet itself, it is a product of the Cold
War. The United States Department of Defense originally developed the
Internet. It was designed to ensure secure communications, even with
multiple communications network failures anticipated in the event of a
nuclearwar.TCP/IPsolvestheproblemofnetworkfailurebyassumingthat
a certain amount ofnoise alwaysexists in the network— noise referring either
to random data errors or more serious system crashes. If you have ever tried
to speak in a noisy room, you know the necessity of repeating yourself—and
that is exactly what TCP/IP is designed to do. Breaking the data down into
packets allows the Internet to seek alternate routes if one route is inaccessible.
If a packet cannot get through or arrives damaged, the receiving computer
simply requests it again until it arrives successfully.
When you send an e-mail message, for example, it is broken into several
packets. Depending on how noisy the network is, each packet may need to be
routed over a separate route in order to find its way to its destination.
Furthermore, networkproblems may cause some of the packets to be delayed
so they arrive out of order. To compensate, TCP examines each packet as it
arrives to verify that it's OK. Once all the packets are received, TCP puts them
back in their original order. Of course, all of this happens quickly and
automatically, so you will never see the process at work.
The Internet and the Web…what is the difference?
Before the Web, the Internet was mostly command-line driven and
character-based— you had to type in the exact Internet address of the place
youwanted to goa t acommand line. In 1989,Tim Berners-Leeof theEuropean
Particle Physics Laboratoryproposed anew way toshare information over the
Internet. The essential feature in Berner-Lee’s vision of the Web is that it links
documents together. When you click a link on a Web page, you are
automatically connected to another Web site. This linking function, combined
with the increasing graphics abilities of home computers, transformed the
Internet into a graphically rich place, complete with video, sound, and
pictures. Through the linking of information together in a
graphically-appealing package, the Web made the Internet more attractive to
the typical consumer.
The Internet is a network of linked computers that uses TCP/IP as its
underlying messaging system. The World Wide Web (WWW, or just “Web”
for short) is hosted by the Internet, and is an ever-expanding collection of
documents employing a special coding scheme named Hypertext Markup
Language (HTML).
56 Internet Guard Dog
Page 67

NOTE: HTML is a set of commands designed to be interpreted by Web
browsers. An HTML document consists of content (prose, graphics,
video, etc.) and a series of commands that tell a Web browser how to
display the content.
Privacy and security on the Web
Before the advent of the Web, Internet security usually posed a problem only
forsystem administrators trying tokeep meddlesomehackersaway from their
systems. When the Web arrived, the popularity of the Internet skyrocketed.
Almost overnight, people began doing all sorts of potentially sensitive
activitiesover theInternet, including: banking and stock transactions;sending
personal data toWeb sites;performing Web searches;and orderingbooks and
clothes. While the Web is responsible for making the Internet more accessible,
it also opens new possibilities for data theft, invasions of privacy, and fraud.
Why does Internet privacy matter to me?
Step back and consider the range of sensitive transactionswe makeevery day.
As an example,considera simple ATMtransaction:We assume thatfollowing
conditions prevail whenever we use our ATM cards:
Internet Security and Privacy
• Privacy: Only you and the intended recipient can access the transaction
information. ThePIN youuse to access your bankaccount providesa fairly
high level ofprivacy—as long as you don’tshare your PIN with others,and
don’t leave your card lying around, your checking account balance is safe
from prying eyes.
• Integrity: Nothing can intervene and change the information during the
transaction. When we take twenty dollars out of our checking account, we
have a reasonable expectation that the ATM will not add an extra zero.
• Trust: You can trust that the recipient is who they claim to be; the recipient
cantrustthatyouarewhoyouclaimtobe.
Organizations likebanks and insurancecompanies arelegally obliged toabide
by federal statutes that govern the sanctity of your transaction information.
The problem with Internet is that it has not yet evolved into well-established
institutional mechanisms that guarantee the sanctity of your information.
User’s Guide 57
Page 68

Internet Security and Privacy
Privacy on the Web
Who is snooping?
Hackers are a breed of human being that thrive on gaining illegal access to
computersin order toaccess, steal, and sometimescorrupt data. Manyhackers
are quitebenign—breaking into asecure system is a challenge and a thrill. But
some computer hackers think that if they don’t care for someone or some
organization, it is OK to break in to their computers and wreak havoc. Other
hackers think that the on-line theft of money and resources i s legitimate, as
long as it goes to support more hacking.
Snooping and sniffing
Since its inception, the Internet has been (and largely remains) an open
network. Opennessmeans that information on the Internet travels without
any special security: Anyone who can monitor network traffic can intercept it.
This sort of monitoring is called “sniffing,” and is easy to perform using
“sniffers.” Sniffers are programs (or hardware devices) designed to monitor
data traveling over a network. Originally, sniffers were designed to help
network administrators track down networking problems. Unfortunately, the
same tool can also be used to steal information. Sniffers are insidious and
difficult to detect.
Sniffing often begins when a hacker breaches the security of a local Internet
Security Provider (ISP). A hacker does not need physical access to the ISP’s
premises—sometimes a telephone line is sufficient (although it is also possible
to sniff with physical access to network cables). Once a hacker compromises
an ISP’s system, the network traffic that travels through the ISP is no longer
secure.
Web servers and firewalls
Secure transactions are only one p art of the problem. When an ISP’s Web
server receives information, the ISP m ust be able to keep the information safe.
Hackers liketo attack the security of Web serversbecause Web server security
is still in its infancy. As a consequence, Web administrators assume that aWeb
server is open to attack, and try to keep them decoupled from other,
mission-critical computers. Some Web applications must, however, interact
with corporate databases, an open door to a clever hacker. One form of
security technology called a “firewall” can close the door, but firewalls are
often maintained poorly,and even in the best environment, cannotsafeguard
certain services.
58 Internet Guard Dog
Page 69

What can I do to keep my stuff safe?
With sniffer in place, a hacker can intercept credit card numbers and other
private information by capturing data transmissions, and then using
pattern-matching algorithms to filter out the valuable information.
Intercepted credit card info can be sold to criminals, intent on committing
fraud.
To avoid this problem, Web browsers incorporate encryption technologythat
cloaks information and makes it difficult to get at. Encryption is the basic
technique that the Web uses to guarantee information security.
The current encryption standard is called “Secure Sockets Layer” (SSL),
supported both by Microsoft and Netscape, and incorporated in their
browsers. An icon in the browser changes to indicate that SSL is active. When
you make a transaction with SSL active, you can be fairly comfortable that the
transaction is safe.
When you visit an SSL-secured site, the latest versions of Netscape
Communicatorand Microsoft InternetExplorer useavisual cue to tellyouthat
the site is secure. For more information, see Howcan I tell ifa Web site issecure?
NOTE: Guard Dog’s CheckUp lets you know if y our Web browser is
up-to-date. The latest browser versions usually offer an enhanceddegree
of security.
Internet Security and Privacy
How can I tell if a Web site is secure?
Today, many sites use SSL to set up secure commerce on the Web. In addition
to Web server security, the most common Internet browsersprovide feedback
about the security level of the site to which you are currently connected. For
example,NetscapeCommunicatordisplaysa lock iconin the lowerleft corner
of the browser window. If the lock icon is broken, the site is not secure. If the
lock sym bol is notbroken, thesite issecure. In addition, if the lock symbol has
a gold background, the site is using strong, 128-bit encryption.
Recent versions of Microsoft Internet Explorer and America Online browsers
also display security information. For more information about how your
browser indicates the security level of sites, refer to your browsers on-line
help, or the printed documentation.
User’s Guide 59
Page 70

Internet Security and Privacy
If SSL is so great, what is the problem?
SSL is affected by a couple of problems. One problem is that not everyone has
anSSL-enabledserver or browser.Some Webadministratorsdon’twant to use
SSL because they have to pay for it, and it can also slow down server
transactions. A more onerous problem that affects SSL is the way it is
implemented. It turns out that some developers made incorrect assumptions
aboutSSL,whichmeanssomeolderbrowserversionsarelesssecure.The
good news is that Microsoft and Netscape now coordinate their security
efforts, which means a more s ecure, universal standard for Web security.
What about authentication?
Authentication is a method of assuring that both parties to an Internet
transaction are who they claim to be. For example,if you get account balance
information from your bank, you want to be sure that you are contacting the
bank, and notsome unauthorized entity. Inaddition, thebank wants tobe sure
that they are providing the information to you, and not just to a person who
happens to know your bank account number.
Authentication usually entails entering a user ID and a password. To
circumvent intercepted passwords and IDs, authentication employs
encryption to scramble this information before transmitting it.
NOTE: Certificates are Microsoft technologies designed to guarantee a
person’s identity and Web site security. Personal certificates verify that
you are who you claim to be. Web site certificates verify that a Web site
is secure andwhat it claims to be(so Web sites can’t falsifytheir identity).
When you open a Web site that hasa certificate, Internet Explorer checks
if the certificate is correct. If the certificate is not OK, Internet Explorer
warns you. Certificatesare great,in theory. Theproblem is thatthey only
establish a security standard—Web sites are free to choose to use
certificates, or not.
How does encryption work?
The only way to keep a secret is if you do not tell anyone, and if you do not jot
it down. If you need to share the secret, you can hide it within another
message, and let the intended recipient know how to find it. Computer
encryption hides messages by making the original data unintelligible. The
intent is to garble the data so that it can not be read. Inthis case, the data it self
is useless if access by an unintended recipient.
60 Internet Guard Dog
Page 71

Internet Security and Privacy
The simplest encryption systems use letter shifting, in which a message is
encrypted by shifting every letter n letters later in the alphabet. For example,
say A is changed to B, and B to C, etc. As long as the recipient knows how you
shifted the letters, they can easily decrypt the message by reversing the
process. Of course, a brute force approach to breaking this sort of encryption
would simply try all possible 26-letter combinations until the final message
was retrieved—not a very strong m ethod of encryption.
Computer encryption uses a much more difficult technique of hiding the
message. Rather than a simple letter-shifting scheme, the original message is
transformed by a mathematical algorithm. The algorithm uses a secret “key”
to scramble the message, and the key is necessary to unscramble it. The key is
similar to a house key: The more teeth a key has, the more difficult it is to pick
the lock. Similarly, “strong” encryption uses keys with many “teeth”—in this
case, bits of data.
Thereare two commonly usedlevelsof encryption. The internationalstandard
is 40-bit encryption, but some sites in the United States use a higher level of
128-bit encryption. The number of bits indicates the length of the key used to
encrypt data. The longer the key, the stronger and more secure the encryption.
On the Web, your browser works with secure Web sites to establish and
manage the encryption that secures information. If your browser security
options include the Secure Sockets Layer (SSL), which ensures
data-transmission privacy, you should turn on this option to facilitate secure
data transmission.
NOTE: Guard Dog’s CheckUp automatically checks your browser’s
security level, and lets you know if you need to change it.
Security on the Web
One of themost exciting Webdevelopments is theevolution of downloadable,
executable programs. Java and ActiveX are tw o tools that help developers
create programs that can “live” inside Web pages, and use your Web browser
to automatically run over the Internet. Java allows Web pages to host small
programs called “applets.” When Java-enabled browsers access a Web page
containing Java, they automatically download and run the applets they find
on the page. This is an intriguing development, since it makes it possible to
download and run programs over the Web. Complete, Web-driven programs
written entirely in Java are on the horizon. ActiveX is a similar technology,
developed by Microsoft.
User’s Guide 61
Page 72

Internet Security and Privacy
Javacontains an internal securitysystem that addresses securityrisks. ActiveX
uses a differentmodel, based on certificate authentication.Certificates contain
information about who developed the ActiveX code. The idea here is that if
you know who developed the code, it is safe to run it. Both security schemes
offer a level of safety, but no one can yet promise that executable content is
entirely safe.
Nasty applets
One possible security threat is a malign Java or Active X program that attacks
your computer over the Web. A nasty applet might, for example, thwart Java
security by circumventing its security model, and des troy data on your hard
disk, or grab sensitive information from your hard drive. The latest browsers
have done a good job of fixing these issues. As long as you are using the latest
version of your browser, you are protected. To date, there have been no
legitimate reports of hostile Java or ActiveX harming anyone. However, there
is no guarantee that an attack will not happen in the future.
Can I prevent programs from accessing the Internet?
You can use Guard Dog to specify the applications that are allowed to access
the Internet from your computer. Obviously, your default Internet browser is
one of these applications.
If the Guard Dog Gatekeeperis runningin the background while youwork on
the Internet, each time an application tries to access the Internet a dialog box
appears to ask if you want to allow this access once only, always, or never.
Computer viruses and the Web
A computer virus is a small computer program that automatically replicates
itself and spreads from one computer t o another. Viruses may infect
programs, your hard drive, and even some document files that employ
macros. Viruses do not infect data files, but they can create problems that
prevent you from accessing your data. Viruses are not accidents—they are
always created by computer programmers.
PC viruses are similar to biological viruses in that they:
• Are spread from host to host—the “host,” in this instance, is your PC.
• Are very good at reproducing themselves.
• Can wreak havoc on an infected host system.
62 Internet Guard Dog
Page 73

Biological viruses have proven to be tenacious— modern medicine’s success
in fighting viral infection has, so far, been rather l imited. Fortunately, PC
viruses differ from biological viruses in that they are easier to combat, once
they are identified.
Are viruses really that dangerous?
Bear in mind that your chances of contracting a PC virus are slim, and even
more so,your chancesof contracting a trulyvicious virus. The scariest viruses
are malicious programs that intentionally corrupt or delete the data on your
PC. More benign viruses might simply display a message on your monitor or
make a strange sound, and then disappear. But even the most benign virus
occupies some disk space, andmany remain in memory, whichcan causeyour
PC to crash or behave erratically.
Types of viruses
There are three main types of viruses:
• File or program viruses: A program virus attaches itself to a specific
program on your PC. Since many PC’s share certain files in common (for
example, the DOS program command.com, or the command “dir”),which
make these files tempting targets for virus programmers. Program viruses
are dormant until you run the associated program.
Internet Security and Privacy
• Boot viruses (or Master Boot Record viruses): The boot sector of a disk is
aphysicallocationon thedisk that containsinformationaboutthe disk and
the files it contains. All disks and drives have a boot sector, even if they
aren’t “bootable.” A boot virus infects the boot sector of floppy disks and
hard drives, and are activated when you access or boot from an afflicted
disk.
• Macro viruses: Macro viruses are contained in document files, such as
Microsoft Word or Excel files. These files can contain macros that can
automate your work—but macros canalso be written to dodamage to your
PC. Macro viruses are activated when you open an infected document file.
A final word should be said about hoax “viruses,” whichare not viruses in the
strictest sense of the term. A hoax virus replicates a hoax, spread by
misinformed (if well intentioned) e-mail claiming that if you download a
certain file, or ifyou receive an e-mailwith a certain subjectline, you willinfect
your PC with a virus. E-mail messages are always safe; they are simple text
files, and cannot contain viruses. Attachments to e-mail messages (an
attachment is a file that a message sender attaches to a message—it is
downloaded to your PC when you retrieve the message) can contain viruses.
(If E-mail file access is turned on in Virus Sentry, Guard Dog automatically
scans e-mail attachments before you open them.)
User’s Guide 63
Page 74
Internet Security and Privacy
How can my PC become infected with a virus?
An important thing to keep in mind is that viruses are spread only when you
run an infected application (or open an infected document file, in the case of
macro viruses). A viruscannot travel overyour telephone line andinfect your
PC on its own. You must first download or copy an infected application and
then run the application in order to infect your PC with a virus.
The only way to entirely avoid virus infection is to do nothing—don’t use the
Internet; never download a file; never accept a diskette from someone else;
never share Word or Excel files. Of course, this draconian “Robinson Crusoe”
cure is unrealistic in today’s computing environment, where sharing data is
the norm and accessing the Internet is an everyday occurrence.
NOTE:Internt Guard Dog offers comeswith McAfee VirusScan whichis
easy to use. It automatically scans your PC for signs of virus infection,
and investigates suspect files before they have a chanceof infecting your
PC.
Viruses are spreadwhen infected diskettes are sharedbetween PCs, andwhen
you download and run infectedfiles from on-line services, bulletin boards, or
the Internet. Another potential (but remote) route for virus transmission is
when you access Web pages that use Microsoft ActiveX technology or Sun’s
Java. Web pages that use ActiveX, for example, can automatically download
programs to your PC, and these programs might be infected with a virus.
Although there isno known casew here ActiveXand Java havespread viruses,
there is still a possibility— remote as it may be—for your PC to encounter a
virusinthisway.
A virus might be hidden in the next file you download, or on a diskette you
borrow —even diskettes purchased at a store. Downloaded shareware is also
a source of infection.
NOTE: Although Java and ActiveX are not, strictly speaking, viruses
(i.e., it can’t spread and replicate), they can still harm your PC. Guard
Dog’s default settings allow it to monitorall Javaand ActiveX activity on
your PC, and warn you before something potentially dangerous occurs.
Frequently asked questions about Internet privacy
What information do Web sites collect about me?
Web sites collect information about you in two major ways.
64 Internet Guard Dog
Page 75

Internet Security and Privacy
• First, youcan provide the informationyourself whenyou registersoftware
or respond to Internet questionnaires.
• Second, when you ask to be allowed access to the electronic version of a
newspaper, or use a “shopping cart” to buy products on the Web, a cookie,
described in “What are cookiesand howare t hey used?” on page 65,might
be written to your computer where it stores information,such asyour user
ID and password for the newspaper or the articles you bought with their
quantity and price.
What information do companies get when I register products online?
Companies get only the information that you enter in the registration form
when you registerelectronically.They donot getany information about your
computer system, your use of your computer, or other stored information
unless you provide it as part of the registration.
This information is used for the company’s marketing research and to send
you information about new releases, other products, and so on. The
information mightbe sold toother companies,just asmailing listsof magazine
subscribers or mail order companies can be sold to others.
Some companies allow you to specify that you do not want to receive mailings
or to have your name and address sold to other companies. If the company
does not provide this option, you can enter false information to prevent
mailings, either postal or electronic, from reaching you.
What are cookies and how are they used?
A cookie is a small file that contains data. The data in the cookie varies,
depending on its purpose. Upon the request of a Web site, your Web browser
stores cookies on your computer. Usually, cookies just contain information
that enhances your Web experience. For example, when you use an Internet
site to buy computer equipment, you may add items to a “shopping basket.”
Information about the items you add to the shopping basket is stored in a
cookie on your computer because the Internet browser cannot retain
information that youentered inone Internet page when youswitch toanother
Internet page. The cookie saves informationabout your purchasesand allows
the site to create a final order form for you.
Another example is the cookie that a Web store keeps on your computer,
holding your user name and password so that you do not need to enter this
informationeachtimeyouconnecttothesite.
User’s Guide 65
Page 76

Internet Security and Privacy
Some stores may use the cookie information to record each time you connect
to the site, what pages you use, and whether you click any of advertiser
banners. Reputable sites provide privacy information to tell you how the
information that is gathered is used.
The above examples of cookies are clearly useful to you, at least in some way.
However, other sitesmight download cookies justto collectinformation about
your Internet use. These cookies are clearly not useful to you at all.
You can use the Guard Dog Cookie Blocker to control which cookies can be
downloaded to your computer. For more information, see “What Cookie
Blocker does” on page 31.
Sources for Internet privacy and security information
Finding out about Internet hoaxes
The United States Department of Energy—Computer Incident Advisory Capability
Lists and describes hoaxes, viruses, and miscellaneous security information.
http://ciac.llnl.gov/
More information about computer viruses
International Computer Security Association Anti-Virus Lab
http://www.ncsa.com/virus/
Describes viruses, virus alerts, as well as hoaxes.
Yahoo!'s virus page
Yahoo!'s virus page contains links to anti-virus software companies, Usenet
virus newsgroups, and links to specific virus information.
Usenet virus FAQ
Contains a nicely organized compendium of information about viruses
collected from Usenet virus newsgroups.
http://www.cis.ohio-state.edu/hypertext/faq/bngusenet/comp/virus/top.
html
66 Internet Guard Dog
Page 77

More information about security
Two good starting places for information about Web security is the on-line
help for Netscape Communicator and Microsoft Internet Explorer.
National Institute of Health’s Computer Security Information site
Good links to many security information sites.
http://www.alw.nih.gov/Security/security.html
Microsoft’s Security site
White papers and descriptions of M icrosoft’s security efforts
http://www.microsoft.com/security/
More information about privacy
Electronic Freedom Foundation
http://www.eff.org/pub/Privacy/
Internet Security and Privacy
Internet Privacy Coalition
http://www.privacy.org/ipc/
User’s Guide 67
Page 78

Internet Security and Privacy
68 Internet Guard Dog
Page 79

BProduct Support
BEFORE YOU CONTACT McAfee Software for technical support, locate
yourself near the computer with McAfee Guard Dog installed and verify the
information listed below:
• Have you sent in your product registration card?
• Version of Internet Guard Dog
• Customer number if registered
• Model name of hard disk (internal or external)
• Version of system software
•Amountofmemory(RAM)
• Extra cards, boards or monitors
• Name and version of conflicting software
• EXACT error message as on screen
• What steps were performed prior to receiving error message?
B
• A complete description of problem
How to Contact McAfee
Customer service
To order products or obtain product information, contact the McAfee
Customer Service department at (972) 308-9960 or write to the following
address:
McAfee Software
3965 Freedom Circle
Santa Clara, CA 95054
U.S.A.
You can also order products online at http://store.mcafee.com
User’s Guide 69
Page 80

Product Support
If you need further assistance or have specific questions about our products,
send your questions via email to t he appropriate address below:
• For general questions about ordering software: mcafeestore@beyond.com
• For help in downloading software: mcafeedownloadhelp@beyond.com
• For a status on an existing order: mcafeeorderstatus@beyond.com
To inquire about a promotion: mcafeepromotions@beyond.com
Technical support
Support via the web
McAfee is famous for its dedication to customer satisfaction. We have
continued this tradition by making our site on the World Wide Web
(http://www.mcafee.com) a valuable resource for answers to technical
support issues.
We encourageyou to make this your first stop for answers to frequently asked
questions,forupdates to McAfeesoftware, andfor accessto McAfeenews and
virus information.
Take advantage of the McAfee Product KnowledgeCenter—your free online
product support center - 24 hours a day, 7 days a week
(http://support.mcafee.com/tech_supp/pkc.asp).
Support forums and telephone contact
If you do not find what you need or do not have web access, try one of our
automated services.
Table B-1.
World Wide Web www.mcafee.com
CompuServe GO MCAFEE
America Online keyword MCAFEE
Microsoft Network mcafee
70 Internet Guard Dog
Page 81

If the automated services do not have the answers you need, please contact
McAfee at the following numbers Monday through Friday between 9:00 AM
and 6:00 PM Pacific time for 30-day free support, and 24 hours a day - 7 days
a week for Per Minute or Per Incident support.
30-Day Free Telephone Support 972-308-9960
Per Minute Telephone Support 1-900-225-5624
Per Incident Telephone Support ($35) 1-800-950-1165
McAfee training
For information about scheduling on-site training for any McAfee product,
call (800) 338-8754.
Disclaimer:Timeandtelephonenumbersaresubjecttochangewithoutprior
notice.
Product Support
Table B-1.
User’s Guide 71
Page 82

Product Support
72 Internet Guard Dog
Page 83

Index
A
action options, choosing
in VirusScan Classic 52
ActiveX controls 39
deleting files 43
protection against damage by 43
scanning hard drives43
viruses and 64
alert messages 27
audible, sounding 53
Cookie Blocker 32
File Guardian 43
ActiveX alert message 44
ActiveX delete alert message 44
drive format alert message 45
guarded file alert message 43
Gatekeeper 39
any credit card number goes out 41
harmful site 40
Internet access 39
program starts up another program 40
help for 27
Identity Protector 34
Web Trail Cleaner 36
audible alert messages, sounding 53
B
bookmarks 36
boot sector viruses 63
Browser Buddy
adding a new password record 28
dragging passwords from 28
opening 28
Password Manager and 27
Search Protector and37
browser history 36
C
cached files 36 CheckUp
using 25
configuration
of VirusScan Classic 51
Cookie Blocker
alert message 32
Browser Buddy and27
described 31
settings 33
cookies
Browser Buddy 27 defined 65
credit cards
protecting with Gatekeeper 39
protecting with Identity Protector 33
D
decrypting files
using shortcut menu 26
defaults
scan targets 52
detection
options
adding scan targets 52 direct sites 31 diskettes
boot sector viruses 63
disks
choosing as scan targets52
, 33
User’s Guide 73
Page 84

Index
E
attachments and viruses 63
messages and viruses 63
encrypting files 29
File Guardian and 43
using shortcut menu 26
extensions, use of to identify scan targets 52
F
file encryption 29 File Guardian
ActiveX alert message 44
ActiveX delete alert message 44
alert message 43
described 43
drive format alert message 45
encrypting and decrypting files 29
guarded file alert message 43
settings 46
file name extensions
use of to identify vulnerable files 52
files
choosing as scan targets52
encrypting and decrypting 29
protectingfrom ActiveX controls 43
protecting with File Guardian 43
VSCLOG.TXT, as VirusScan log 53
folders
choosing as scan targets52
G
Gatekeeper
alert messages 39
any credit card number goes out alert
message 41
described 39
harmful site alert message 40
Internet access alert message 39
programstarts up another programalert
message 40
settings 42
Getting S tarted manual
described 7
Guard Dog
See also alert messages; Protection
Settings
alert messages
CheckUp 25
help, described 7
Home screen 18
installing 12
, 23
Log 2
manual, described 7
new features 5
password 18
shortcut menu 26
system requirements 11
taskbar icon 26
updating24
guarding files 29
H
hard drives, protecting 43 Help
opening from VirusScan Classic and
VirusScan Advanced 51
help
alert messages and 27
using 7
74 Internet Guard Dog
Page 85

Index
history files 36 hoax viruses63 Home screen
items on 19
using 18
I
icon for Guard Dog 26 Identity Protector
alert message34
described 33
settings 35 indirect sites 31 infected files
moving 52
use of quarantine folder to isolate 52 Internet connection, protecting 39 Internet Filtering Options 21 Internet Guard Dog Administrator 17 Internet privacy and security
Guard Dog solutions 3
Interview 15
, 33
J
Java and viruses 64
L
Log 2, 23 log file
creating with text editor 53
VSCLOG.TXT as 53
login names 47
M
macro viruses 63
managing Web passwords 27
Master Boot Record viruses 63
menu, shortcut 26
messages See alert messages
modem 39
multiple users and passwords 34
O
OCX 45 online help
opening from VirusScan Classic and
VirusScan Advanced 51
options
VirusScan Classic
Action 52
Report 53
Where & What 51
P
Password Manager
adding a new record using Browser
Buddy 28
adding record to 47
deleting record 48
described 47
editing record 47
User’s Guide 75
Page 86

Index
passwords
activating and deactivating 35
adding record to Password Manager 47
adding with Browser Buddy 28
Browser Buddy and 27
deleting Password Manager record 48
dragging from Browser Buddy 28
editing Password Manager record47
forgotten 18
protecting Web site 47
protecting Windows 43
storing in Password Manager 47
using for Guard Dog 18
personal information, protecting 33
Privacy Features 31
privacy threats 4
program extensions, designating as scan
targets 52 program viruses 63 programs, protecting 39 protecting
credit cards 39
files from ActiveX controls 43
files with encryption 29
hard drives 43
Internet connection 39
programs 39
Windows password file 43
Protection Settings
Cookie Blocker 33
File Guardian 46
Gatekeeper 42
Identity Protector 35
Password Manager47
Search Protector 37
Web Trail Cleaner 37
Q
quarantine folder, use of to isolate infected
files 52
question mark button 27
R
report file
VSCLOG.TXT as 53
report options, choosing
in VirusScan Classic 53
report See Log
response options
setting
for VirusScan Classic 52
S
scan task
action options, configuring 52
logging options, configuring
in VirusScan Classic 53
report options, configuring
for VirusScan Classic 53
targets for
adding 52
Where & What options, configuring 51
search information 37
Search Protector
Browser Buddy and 37
described 37
settings 37 secure connection 33 security threats 4 Self-Administrator 17 settings
Cookie Blocker 33
File Guardian 46
Gatekeeper 42
Identity Protector 35
Search Protector 37
Web TrailCleaner 37
76 Internet Guard Dog
Page 87

Index
shareware and viruses 64 shortcut menu 26 Start menu
using to start VirusScan Classic 49
T
targets for scanning
adding 52
task
action options, configuring 52
adding scan targets to 52
logging options, configuring
in VirusScan Classic 53
report options, configuring
for VirusScan Classic 53
Where & What options, configuring 51 taskbar icon 26 text
editor, use of to create log file 53 turning on/off
Guard Dog monitoring 26
U
unsecure site 34 Update button, using 24 updating Guard Dog and virus patterns
using Update 24 URLs 36 username
adding with Browser Buddy 28
dragging from Browser Buddy 28
V
viruses
ActiveX and 64
e-mail attachments and 63
e-mail messages and 63
file and program 63
hoax 63
how dangerous? 63
how spread 62
Java and 64
macro 63
threats 5
types of 63
updating list of 24
who creates them 62
VirusScan
Action options
configuring in VirusScan Classic 52
property pages
Action 52
Where & What 51
what it does 49
VirusScan Classic
Action options, choosing 52
Report options, choosing 53
starting 49
Where & What options, choosing51
VSCLOG.TXT, as VirusScan report file 53
W
warnings See alert messages Web password management 27 Web sites
harmful 39
storing login names and passwords 47
Web Trail Cleaner
alert message 36
described 36
settings 37
Where & What options
choosing in VirusScan Classic 51
User’s Guide 77
Page 88

Index
Windows
protecting password file 43
taskbar 26
using help 7
Windows Start menu, using to startVirusScan
Classic. 49
78 Internet Guard Dog
 Loading...
Loading...