Page 1

McAfee ePolicy Orchestrator 4.0.2
Product Guide
Page 2

COPYRIGHT
Copyright © 2008 McAfee, Inc. All Rights Reserved.
No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language in any form
or by any means without the written permission of McAfee, Inc., or its suppliers or affiliate companies.
TRADEMARK ATTRIBUTIONS
AVERT, EPO, EPOLICY ORCHESTRATOR, FLASHBOX, FOUNDSTONE, GROUPSHIELD, HERCULES, INTRUSHIELD, INTRUSION INTELLIGENCE,
LINUXSHIELD, MANAGED MAIL PROTECTION, MAX (MCAFEE SECURITYALLIANCE EXCHANGE), MCAFEE, MCAFEE.COM, NETSHIELD,
PORTALSHIELD, PREVENTSYS, PROTECTION-IN-DEPTH STRATEGY, PROTECTIONPILOT, SECURE MESSAGING SERVICE, SECURITYALLIANCE,
SITEADVISOR, THREATSCAN, TOTAL PROTECTION, VIREX, VIRUSSCAN, WEBSHIELD are registered trademarks or trademarks of McAfee, Inc.
and/or its affiliates in the US and/or other countries. McAfee Red in connection with security is distinctive of McAfee brand products. All other
registered and unregistered trademarks herein are the sole property of their respective owners.
LICENSE INFORMATION
License Agreement
NOTICE TO ALL USERS: CAREFULLY READ THE APPROPRIATE LEGAL AGREEMENT CORRESPONDING TO THE LICENSE YOU PURCHASED,
WHICH SETS FORTH THE GENERAL TERMS AND CONDITIONS FOR THE USE OF THE LICENSED SOFTWARE. IF YOU DO NOT KNOW WHICH
TYPE OF LICENSE YOU HAVE ACQUIRED, PLEASE CONSULT THE SALES AND OTHER RELATED LICENSE GRANT OR PURCHASE ORDER DOCUMENTS
THAT ACCOMPANIES YOUR SOFTWARE PACKAGING OR THAT YOU HAVE RECEIVED SEPARATELY AS PART OF THE PURCHASE (AS A BOOKLET,
A FILE ON THE PRODUCT CD, OR A FILE AVAILABLE ON THE WEB SITE FROM WHICH YOU DOWNLOADED THE SOFTWARE PACKAGE). IF YOU
DO NOT AGREE TO ALL OF THE TERMS SET FORTH IN THE AGREEMENT, DO NOT INSTALL THE SOFTWARE. IF APPLICABLE, YOU MAY RETURN
THE PRODUCT TO MCAFEE OR THE PLACE OF PURCHASE FOR A FULL REFUND.
License Attributions
Refer to the product Release Notes.
McAfee ePolicy Orchestrator 4.0.2 Product Guide2
Page 3

Contents
Introducing ePolicy Orchestrator 4.0.2. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
Configuring ePolicy Orchestrator Servers. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
ePolicy Orchestrator 4.0.2 components and what they do. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
The ePO server. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
The McAfee Agent. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
Using this guide. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
Audience. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Where to find McAfee enterprise product information. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
ePO user accounts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
Global administrators. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
How permission sets work. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
Contacts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
Server settings and the behaviors they control. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
Available server tasks and what they do. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
The Audit Log. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
The Event Log. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
Data exports from any table or chart. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
MyAVERT Security Threats . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Logging on and off from ePO servers. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Logging on to ePO servers. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Logging off of ePO servers. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Viewing the server version number . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Working with user accounts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Creating user accounts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Editing user accounts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Deleting user accounts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Working with permission sets. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Creating permission sets for user accounts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Duplicating permission sets. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Editing permission sets. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Deleting permission sets. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
3McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 4

Contents
Working with contacts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Creating contacts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Editing contacts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Deleting contacts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Working with server settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Specifying an email server. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Configuring the template and location for exported reports. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Determining which events are forwarded to the server. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Viewing and changing communication ports. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Working with the Server Task Log. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Viewing the Server Task Log. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Filtering the Server Task Log. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Purging the Server Task Log. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Working with the Audit Log. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Viewing the Audit Log. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Purging the Audit Log. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Purging the Audit Log on a schedule. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Working with the Event Log. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Viewing the Event Log. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Purging events. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Purging the Event Log on a schedule. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
Working with MyAvert Security Threats. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
Configuring MyAvert update frequency and proxy settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Viewing threat notifications. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Deleting threat notifications. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Exporting tables and charts to other formats. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Allowed Cron syntax when scheduling a server task. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Organizing Systems for Management. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
The System Tree. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
Considerations when planning your System Tree. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Administrator access. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Environmental borders and their impact on system organization. . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
Subnets and IP address ranges. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
Tags and systems with similar characteristics. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
Operating systems and software. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
Tags and how they work. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
Active Directory and NT domain synchronization. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
McAfee ePolicy Orchestrator 4.0.2 Product Guide4
Page 5

Contents
Active Directory synchronization. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
NT domain synchronization. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Criteria-based sorting. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
How settings affect sorting. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
IP address sorting criteria. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
Tag-based sorting criteria. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
Group order and sorting. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
Catch-all groups. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
How a system is first placed in the System Tree. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
Working with tags. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
Creating tags with the Tag Builder. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
Excluding systems from automatic tagging. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
Applying tags to selected systems. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
Applying criteria-based tags automatically to all matching. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
Creating and populating groups. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
Creating groups manually. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
Adding systems manually to an existing group. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Importing systems from a text file. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Sorting systems into criteria-based groups. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
Importing Active Directory containers. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
Importing NT domains to an existing group. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
Synchronizing the System Tree on a schedule. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61
Updating the synchronized group with an NT domain manually. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
Moving systems manually within the System Tree. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
Distributing Agents to Manage Systems. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
Agents and SuperAgents. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 65
Agent-server communication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
SuperAgents and broadcast wake-up calls. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
Agent activity logs. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
Agent policy settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
Security Keys. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
Agent-server secure communication keys. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
Master repository key pair. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
Other repository public keys. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
Methods of agent distribution. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
Creating custom agent installation packages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73
Distributing agents. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73
5McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 6

Contents
Deploying the agent with ePolicy Orchestrator. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
Installing the agent with login scripts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76
Installing the agent manually. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 77
Enabling the agent on unmanaged McAfee products. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
Including the agent on an image. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
Using other deployment products. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
Distributing the agent to WebShield appliances and Novell NetWare servers. . . . . . . . . . . . . . . . . . 79
Forcing the agent to call in to the server. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
Upgrading existing agents. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
Upgrading agents using login scripts or manual installation. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
Upgrading agents with ePolicy Orchestrator. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
Removing the agent. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
Running FRMINST.EXE from a command line. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
Removing agents when deleting systems from the System Tree. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
Removing agents when deleting groups from the System Tree. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
Removing agents from systems in query results. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
Maintaining the agent. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
Sending manual wake-up calls to systems. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
Sending manual wake-up calls to a group. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
Sending wake-up calls on a schedule. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
Viewing the agent activity log. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Viewing of the agent and product properties. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Running agent tasks from the managed system. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
Working with security keys. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
Agent command-line options. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 94
Agent installation command-line options. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 94
Creating Repositories. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
Repository types and what they do. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
Types of distributed repositories. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 98
Repository branches and their purposes. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
Repository list file and its uses. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
How repositories work together. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Ensuring access to the source site. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
Using Internet Explorer proxy settings for the master repository. . . . . . . . . . . . . . . . . . . . . . . . . . . 101
Configuring custom proxy settings for the master repository . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
Working with source and fallback sites. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
Switching source and fallback sites. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
McAfee ePolicy Orchestrator 4.0.2 Product Guide6
Page 7

Contents
Creating source sites. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104
Editing source and fallback sites. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
Deleting source or fallback sites. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
Using SuperAgents as distributed repositories. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
Creating SuperAgent repositories. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106
Selecting which packages are replicated to SuperAgent repositories. . . . . . . . . . . . . . . . . . . . . . . . 106
Deleting SuperAgent distributed repositories. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107
Creating and configuring FTP, HTTP, and UNC repositories. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107
Creating a folder location on an FTP, HTTP server or UNC share. . . . . . . . . . . . . . . . . . . . . . . . . . . 108
Adding the distributed repository to ePolicy Orchestrator. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
Enabling folder sharing for UNC and HTTP repositories. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
Editing distributed repositories . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110
Deleting distributed repositories. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110
Working with the repository list files. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110
Exporting the repository list SITELIST.XML file. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110
Exporting the repository list SITEMGR.XML file for backup or use by other servers. . . . . . . . . . . . 111
Importing distributed repositories from the SITEMGR.XML file. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
Importing source sites from the SITEMGR.XML file. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 112
Changing credentials on multiple distributed repositories. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 112
Managing Products with Policies and Client Tasks. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
Extensions and what they do. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
Policy management. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Policy application. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
Client tasks and what they do. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
Bringing products under management. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
Viewing policy information. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
Viewing groups and systems where a policy is assigned. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
Viewing the settings of a policy. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
Viewing policy ownership. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
Viewing assignments where policy enforcement is disabled. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
Viewing policies assigned to a group. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Viewing policies assigned to a specific system. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Viewing a group’s policy inheritance. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Viewing and resetting broken inheritance. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Working with the Policy Catalog. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
Creating a policy on the Policy Catalog page . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
Duplicating a policy on the Policy Catalog page. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122
7McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 8

Contents
Editing a policy’s settings from the Policy Catalog. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122
Renaming a policy from the Policy Catalog. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122
Deleting a policy from the Policy Catalog. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
Working with policies. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
Changing the owner of a policy. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
Sharing policies between ePO servers. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 124
Assigning a policy to a group of the System Tree. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
Assigning a policy to a managed system. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
Assigning a policy to multiple managed systems within a group. . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
Enforcing policies for a product on a group. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
Enforcing policies for a product on a system. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
Copying and pasting assignments. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127
Working with client tasks. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 128
Creating and scheduling client tasks. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
Editing client tasks. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
Deleting client tasks. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
Frequently asked questions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
Deploying Software and Updates. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
Deployment packages for products and updates. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
Product and update deployment. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
Deployment tasks. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
Update tasks. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
Global updating. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135
Pull tasks. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 136
Replication tasks. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
Repository selection. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
Server Task Log. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
Checking in packages manually. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
Using the Product Deployment task to deploy products to managed systems. . . . . . . . . . . . . . . . . . . . . . . . 139
Configuring the Deployment task for groups of managed systems. . . . . . . . . . . . . . . . . . . . . . . . . . 140
Configuring the Deployment task to install products on a managed system. . . . . . . . . . . . . . . . . . 140
Deploying update packages automatically with global updating. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
Deploying update packages with pull and replication tasks. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 142
Using pull tasks to update the master repository. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
Replicating packages from the master repository to distributed repositories. . . . . . . . . . . . . . . . . . 145
Configuring agent policies to use a distributed repository. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
Using local distributed repositories that are not managed. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
McAfee ePolicy Orchestrator 4.0.2 Product Guide8
Page 9

Contents
Checking in engine, DAT and EXTRA.DAT update packages manually. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 148
Updating managed systems regularly with a scheduled update task. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
Confirming that clients are using the latest DAT files. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
Evaluating new DATs and engines before distribution. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 150
Manually moving DAT and engine packages between branches. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 150
Deleting DAT or engine packages from the master repository. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151
Sending Notifications. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 152
Notifications and how it works. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 153
Throttling and aggregation. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 153
Notification rules and System Tree scenarios. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 153
Default rules. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
Planning. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
Determining how events are forwarded. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 156
Determining which events are forwarded immediately. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 156
Determining which events are forwarded. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
Setting up ePO Notifications. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
Giving users appropriate permissions to Notifications. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
Working with SNMP servers. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
Working with registered executables and external commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 160
Creating and editing Notification rules. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
Describing the rule. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
Setting filters for the rule. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164
Setting thresholds of the rule. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164
Configuring the notifications for the rule. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 165
Viewing the history of Notifications. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 166
Configuring the Notification Log. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 166
Viewing the details of Notification Log entries. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
Purging the Notifications Log. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
Product and component list. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 168
Frequently asked questions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 168
Querying the Database. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170
Queries. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170
Public and personal queries. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
Query permissions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
Query Builder. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
Multi-server roll-up querying. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
Preparing for roll-up querying. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
9McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 10

Contents
Registering ePO servers. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
Creating a Data Roll Up server task. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
Working with queries. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
Creating custom queries. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
Running an existing query. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
Running a query on a schedule. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
Making personal queries public. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178
Duplicating queries. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178
Sharing a query between ePO servers. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
Exporting query results to other formats. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
Default queries and what they display. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
MA: Agent Communication Summary query. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
MA: Agent Version Summary query. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
ePO: Compliance History query. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
ePO: Compliance Summary query. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
ePO: Malware Detection History query. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
ePO: Distributed Repository Status query. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
ePO: Failed User Actions in ePO Console query. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
ePO: Failed Logon Attempts query. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
ePO: Multi-Server Compliance History query. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
ePO: Systems per Top-Level Group query. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
ePO: Systems Tagged as Server query. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
ePO: Today’s Detections per Product query. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
Assessing Your Environment With Dashboards. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 184
Dashboards and how they work. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 184
Queries as dashboard monitors. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 184
Default dashboard monitors. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 184
Setting up dashboard access and behavior. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 185
Giving users permissions to dashboards. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 185
Configuring the refresh frequency of dashboards. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 185
Working with Dashboards. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 186
Creating dashboards. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 186
Making a dashboard active. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 186
Selecting all active dashboards. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
Making a dashboard public. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
Detecting Rogue Systems. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 189
What are rogue systems. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 189
McAfee ePolicy Orchestrator 4.0.2 Product Guide10
Page 11

Contents
How the Rogue System Sensor works. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 190
Passive listening to layer-2 traffic. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 190
Intelligent filtering of network traffic. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 190
Data gathering and communications to the server. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 191
Systems that host sensors. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 191
How detected systems are matched and merged. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 192
Rogue System Detection states. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 192
Overall system status. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 193
Rogue System Sensor status. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 194
Subnet status. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 195
Top 25 Subnets. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 195
Rogue Sensor Blacklist. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 195
Rogue System Detection policy settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 196
Considerations for policy settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 196
Rogue System Detection permission sets. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 197
Setting up Rogue System Detection. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 198
Configuring Rogue System Detection policy settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 198
Configuring server settings for Rogue System Detection. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 199
Editing compliance settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 199
Editing matching settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 199
Editing sensor settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 200
Setting up automatic responses to Rogue System Detection events. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
Working with detected systems. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 202
Adding systems to the Exceptions list. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 202
Adding systems to the Rogue Sensor Blacklist. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 202
Editing system comments. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 203
Exporting the Exceptions list. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 203
Importing systems to the Exceptions list. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 204
Merging detected systems. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 204
Removing systems from the Detected Systems list. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 204
Removing systems from the Exceptions list. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 205
Removing systems from the Rogue Sensor Blacklist. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 205
Viewing detected systems and their details. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 206
Working with sensors. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 206
Changing the sensor-to-server port number. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 206
Installing sensors. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 207
Editing sensor descriptions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 208
11McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 12

Contents
Removing sensors. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 209
Working with subnets. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 210
Adding subnets. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 210
Deleting subnets. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 210
Ignoring subnets. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 211
Including subnets. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 211
Renaming subnets. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 211
Viewing detected subnets and their details. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 212
Rogue System Detection command-line options. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 212
Default Rogue System Detection queries. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 213
Appendix: Maintaining ePolicy Orchestrator databases. . . . . . . . . . . . . . . . . . . . . . . . . . . . 214
Performing daily or weekly database maintenance. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 214
Performing weekly maintenance of MSDE databases. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 214
Performing regular maintenance of SQL Server databases. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 215
Backing up ePolicy Orchestrator databases regularly. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 216
Backing up a SQL database--see your SQL documentation. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 216
Backing up an MSDE database. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 216
Changing SQL Server information. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 217
Restoring ePolicy Orchestrator databases. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 217
Restoring a SQL database--see your SQL documentation. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 218
Restoring an MSDE database from a backup. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 218
McAfee ePolicy Orchestrator 4.0.2 Product Guide12
Page 13

Introducing ePolicy Orchestrator 4.0.2
ePolicy Orchestrator 4.0.2 provides a scalable platform for centralized policy management and
enforcement of your security products and the systems on which they reside. It also provides
comprehensive reporting and product deployment capabilities, all through a single point of
control.
Contents
ePolicy Orchestrator 4.0.2 components and what they do
Using this guide
Where to find McAfee enterprise product information
ePolicy Orchestrator 4.0.2 components and what
they do
The ePolicy Orchestrator software is comprised of these components:
• ePO server — The center of your managed environment. The server delivers security policy
and tasks, controls updates, and processes events for all managed systems.
• Master repository — The central location for all McAfee updates and signatures, residing on
the ePO server. Master repository retrieves user-specified updates and signatures from
McAfee or user-defined source sites.
• Distributed repositories — Placed strategically throughout your environment to provide access
for managed systems to receive signatures, product updates, and product installations with
minimal bandwidth impact. Depending on how your network is set up, you can set up
SuperAgent, HTTP, FTP, or UNC share distributed repositories.
• McAfee Agent — A vehicle of information and enforcement between the ePO server and
each managed system. The agent retrieves updates, ensures task implementation, enforces
policies and forwards events for each managed system.
The ePO server
The ePO server provides management, reporting, and enforcement capabilites and includes:
• A robust database that accrues information about product operation on the client systems
in your network.
• A querying system that lets you monitor the security status in your company, and quickly
act on gathered data.
• A software repository that stores the products and product updates (for example, DAT files)
that you deploy to your network.
13McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 14

Introducing ePolicy Orchestrator 4.0.2
Using this guide
The ePolicy Orchestrator server can segment the user population into discrete groups for
customized policy management. Each server can manage up to 250,000 systems.
The McAfee Agent
The agent is installed on the systems you intend to manage with ePolicy Orchestrator.
While running silently in the background, the agent:
• Gathers information and events from managed systems and sends them to the ePolicy
Orchestrator server.
• Installs products and updates on managed systems.
• Enforces policies and tasks on managed systems and sends events back to the ePO server.
You can deploy the agent from the console (to Windows systems) or copy the agent installation
package onto removable media or into a network share for manual or login script installation
on your systems. Agents must be installed manually on UNIX systems.
Using this guide
This guide provides information on configuring and using your product. For system requirements
and installation instructions, see the
This material is organized in the order that McAfee recommends to set up ePolicy Orchestrator
in a production environment for the first time, and is also accessible to anyone seeking specific
topics.
Setting up ePolicy Orchestrator for the first time?
This guide serves as a tool to help administrators set up their ePolicy Orchestrator environment
for the first time, and as a reference tool for more experienced users. Depending on your
environment, you may perform some of these tasks in a slightly different order.
McAfee recommends setting up ePolicy Orchestrator for the first time in this order:
1 Configure ePolicy Orchestrator servers — Set up user accounts and permissions, configure
settings, and get familiar with the user interface.
2 Organize systems for management — The System Tree allows you to organize and act on
all systems you manage with ePolicy Orchestrator. Before setting up other features, you
must create your System Tree.
3 Distribute agents — Each system you want to manage must have the McAfee Agent installed.
This section provides detailed information on distributing and maintaining agents in your
environment.
4 Create repositories — Before deploying any products, components, or updates to your
managed systems with ePolicy Orchestrator, you must configure and create update
repositories.
5 Manage product policies and tasks — Before deploying any products, components, or
updates to your managed systems with ePolicy Orchestrator, McAfee recommends
configuring the policy settings for these products and components. Although it is not
required to configure policy settings before deployment, by doing so you can ensure that
the products and components have the desired settings as soon as possible.
Installation Guide
.
McAfee ePolicy Orchestrator 4.0.2 Product Guide14
Page 15

Introducing ePolicy Orchestrator 4.0.2
Where to find McAfee enterprise product information
6 Deploy software and updates — Once your update repositories and policy settings are
created and configured, deploy the products, components, and updates to the desired
systems with ePolicy Orchestrator.
7 Configure advanced features — Once your managed environment is up and running, you
can configure and implement ePolicy Orchestrator’s advanced features, like Notifications,
queries and dashboards.
Audience
This information is intended primarily for network administrators who are responsible for their
company’s security program, and assumes the customer has installed and used ePolicy
Orchestrator in a lab environment.
Where to find McAfee enterprise product information
The McAfee documentation is designed to provide you with the information you need during
each phase of product implementation, from evaluating a new product to maintaining existing
ones. Depending on the product, additional documents might be available. After a product is
released additional information regarding the product is entered into the online Knowledgebase
available on McAfee ServicePortal.
Maintenance PhaseSetup PhaseInstallation PhaseEvaluation Phase
How can my company
benefit from this product?
Preparing for, installing
and deploying software
in a test environment.
• Detailed instructions for
common tasks.
Before, during, and after
installation.
Release NotesEvaluation Tutorial
•• Known issues in the
current release.
• Issues resolved since
the last release.
• Last-minute changes to
the product or its
documentation.
Installation Guide
• Preparing for, installing
and deploying software
in a production
environment.
with the product.
Product Guide
Help
• Setting up and
customizing the
software for your
environment.
Online Help
• Managing and deploying
products through ePolicy
Orchestrator.
• Detailed information
about options in the
product.
and
Online
Maintaining the software.Getting up-and-running
Online Help
• Maintaining the
software.
• Reference information.
• All information found in
the product guide.
Quick Reference Card
• Detailed instructions for
common and infrequent
important tasks.
Knowledgebase
(knowledge.mcafee.com)
• Release notes and
documentation.
• Supplemental product
information.
• Workarounds to
known issues.
Finding release notes and documentation for McAfee enterprise products
1 Go to knowledge.mcafee.com and select Product Documentation under Useful links.
2 Select <Product Name> | <Product Version> and select the required document from
the list of documents.
15McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 16

Configuring ePolicy Orchestrator Servers
The ePO server is the center of your managed environment, providing a single location from
which to administer system security throughout your network.
If your organization is very large or divided into multiple large sites, consider installing a separate
server at each site. This can reduce network traffic when managing agents, sending updates,
and replicating to distributed repositories within a local LAN. Network traffic has a larger impact
on your resources when this communication takes place across WAN, VPN, or other slower
network connections typically found between remote sites.
Are you configuring the ePO server for the first time?
When configuring the ePO server for the first time:
1 Review the conceptual information on user accounts, permission sets, server settings and
server tasks.
2 Decide on how to implement the flexibility of permission sets with user accounts.
3 Create user accounts and permission sets, and assign the permission sets as needed.
4 Set up your contacts list and email server settings.
Contents
ePO user accounts
How permission sets work
Contacts
Server settings and the behaviors they control
Available server tasks and what they do
The Audit Log
The Event Log
Data exports from any table or chart
MyAVERT Security Threats
Logging on and off from ePO servers
Viewing the server version number
Working with user accounts
Working with permission sets
Working with contacts
Working with server settings
Working with the Server Task Log
Working with the Audit Log
McAfee ePolicy Orchestrator 4.0.2 Product Guide16
Page 17

Configuring ePolicy Orchestrator Servers
ePO user accounts
Working with the Event Log
Working with MyAvert Security Threats
Exporting tables and charts to other formats
Allowed Cron syntax when scheduling a server task
ePO user accounts
User accounts provide a means for users to access and use the software. They are associated
with permission sets, which define what users are allowed to do with the software.
You must create user accounts and permission sets to accommodate the needs of each user
that logs on to the ePO server.
There are two types of users, global administrators and everyone else.
Global administrators
Global administrators have read and write permissions and rights to all operations. When you
install the server a global administrator account with the user name admin is created.
You can create additional global administrator accounts for people who require global
administrative rights.
Permissions exclusive to global administrators include:
• Create, edit, and delete source and fallback sites.
• Change server settings.
• Add and delete user accounts.
• Add, delete, and assign permission sets.
• Import events into ePolicy Orchestrator databases and limit events that are stored there.
How permission sets work
A permission set is a group of permissions that can be granted to any users by assigning it to
those users’ accounts. One or more permission sets can be assigned to any users who are not
global administrators (global administrators have all permissions to all products and features).
Permission sets only grant rights and access — no permission ever removes rights or access.
When multiple permission sets are applied to a user account, they aggregate. For example, if
one permission set does not provide any permissions to server tasks, but another permission
set applied to the same account grants all permissions to server tasks, that account has all
permissions to server tasks. Consider this as you plan your strategy for granting permissions
to the users in your environment.
When are permission sets assigned?
Global administrators can assign existing permission sets when creating or editing user accounts
and when creating or editing permission sets.
17McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 18

Configuring ePolicy Orchestrator Servers
Contacts
What happens when I install new products?
When a new product extension is installed it may add one or more groups of permissions to
the permission sets. For example, when you install a VirusScan Enterprise extension, a VirusScan
Enterprise section is added to each permission set. Initially, the newly added section is listed
in each permission set with no permissions yet granted. The global administrators can then
grant permissions to users through existing or new permission sets.
Default permission sets
ePolicy Orchestrator 4.0.2 ships with four default permission sets that provide permissions to
ePolicy Orchestrator functionality. These are:
• Executive Reviewer — Provides view permissions to dashboards, events, contacts, and can
view information that relates to the entire System Tree.
• Global Reviewer — Provides view access globally across functionality, products, and the
System Tree, except for extensions, multi-server roll-up data, registered servers, and software.
• Group Admin — Provides view and change permissions across ePolicy Orchestrator features.
Users that are assigned this permission set each need at least one more permission set that
grants access needed products and groups of the System Tree.
• Group Reviewer — Provides view permissions across ePolicy Orchestrator features. Users
that are assigned this permission set each need at least one more permission set that grants
access needed products and groups of the System Tree.
Contacts
Maintain a list of email addresses that ePolicy Orchestrator uses to send email messages to
specified users in response to events. Currently this list is used by Notifications, queries, and
export functionality.
Server settings and the behaviors they control
Various settings control how the ePolicy Orchestrator server behaves. You can change most
settings at anytime. However, you must reinstall the software to change the name of the server
or the port number the server uses for HTTP communication.
Types of ePO server settings are:
• Email server — Sepcifies the email server that is used when ePolicy Orchestrator sends email
messages.
• Event Filtering — Specifies which events are forwarded by the agent.
• Global Updating — Specifies whether and how global updating is enabled.
• MyAvert Security Threats — Specifies proxy settings and the update frequency for the
MyAvert Security Threats service.
• Ports — Specifies the ports used by the server when communicating with agents and the
database.
• Printing and exporting — Specifies how information is exported to other formats, and the
template for PDF exports.
McAfee ePolicy Orchestrator 4.0.2 Product Guide18
Page 19

Configuring ePolicy Orchestrator Servers
Available server tasks and what they do
• Repository Packages — Specifies whether any package can be checked in to any branch.
Only agents later then version 3.6 can retrieve packages other than updates from branches
other than Current.
• Security Keys — Specifies and manages the agent-server secure communication keys,
repository keys.
• System Tree Sorting — Specifies whether and how System Tree sorting is enabled in your
environment.
Available server tasks and what they do
The default set of server tasks is described here. For details on each of these, see the appropriate
section of this guide that covers that server task.
Improvements to server tasks
Server tasks are now more configurable, allowing you to chain multiple actions and subactions
within a single task, as well as more flexible scheduling.
Server task actions
• Event Migration — If you upgrade from a previous ePolicy Orchestrator installation, use this
task to migrate events from the old database to the new database, so that you can run
queries against your historical data. McAfee recommends scheduling this task to run at off
hours as soon as you can after upgrading.
• NT Domain/Active Directory Synchronization — Synchronizes select Windows NT domains
and Active Directory containers that are mapped to System Tree groups. This task can also
be performed manually.
• Purge Audit Log — Deletes entries from the Audit Log on user-configured age.
• Purge Event Log — Deletes events from the database based on user-configured criteria.
• Purge Notification Log — Deletes entries from the Notification Log by user-configured time.
• Purge Server Task Log — Deletes entries from the Server Task Log by user-configured age.
• Repository Pull — Retrieves packages from the source site, then places them in the master
repository.
• Repository Replication — Updates distributed repositories from the master repository.
• Roll Up Data: Managed Systems— Imports summary data from other registered ePO servers.
• Roll Up Data: Compliance History — Imports summary compliance data from other registered
ePO servers.
• Run Query — Runs a selected query and allows you to chain subactions related to the query
results. For example, you can email the results to someone in your organization, or deploy
agents to all systems in the query results.
• Run Tag Criteria — Evaluates all managed systems against a selected tag’s criteria, and
applies the tag to all matching systems.
19McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 20

Configuring ePolicy Orchestrator Servers
The Audit Log
The Audit Log
Use the Audit Log to maintain and access a record of all ePO user actions. The Audit Log entries
display in a sortable table. For added flexibility, you can also filter the log so that it only displays
failed actions, or only entries that are within a certain age.
The Audit Log displays seven columns:
• Action — The name of the action the ePO user attempted.
• Completion Time — The time the action finished.
• Details — More information about the action.
• Priority — Importance of the action.
• Start Time — The time the action was initiated.
• Success — Specifies whether the action was successfully completed.
• User Name — User name of the logged-on user account that was used to take the action.
Audit Log entries can be queried against. You can create queries with the Query Builder wizard
that target this data, or you can use the default queries that target this data. For example, the
Failed Logon Attempts query retrieves a table of all failed logon attempts.
The Event Log
Use the Event Log to quickly view and sort through events in the database. The Event Log can
be purged only by age.
You can choose which columns are displayed in the sortable table. You can choose from a
variety of event data to use as columns.
Depending on which products you are managing, you can also take certain actions on the
events. Actions are available on the buttons at the bottom of the page.
Common event format
All managed products now use a common event format. The fields of this format can be used
as columns in the Event Log. These include:
• Action Taken — The action that was taken by the product in response to the threat.
• Agent GUID — Unique identifier of the agent that forwarded the event.
• DAT Version — DAT version on the system which sent the event.
• Detecting Product Host Name — Name of the system hosting hosting the detecting product.
• Detecting Product ID — ID of the detecting product.
• Detecting Product IPv4 Address — IPv4 address of the system hosting the detecting product
(if applicable).
• Detecting Product IPv6 Address — IPv6 address of the system hosting the detecting product
(if applicable).
• Detecting Product MAC Address — MAC address of the system hosting the detecting product.
• Detecting Product Name — Name of the detecting managed product.
• Detecting Product Version — Version number of the detecting product.
McAfee ePolicy Orchestrator 4.0.2 Product Guide20
Page 21

Configuring ePolicy Orchestrator Servers
Data exports from any table or chart
• Engine Version — Version number of the detecting product’s engine (if applicable).
• Event Category — Category of the event. Possible categories depend on the product.
• Event Generated Time (UTC) — Time in Coordinated Universal Time that the event was
detected.
• Event ID — Unique identifier of the event.
• Event Received Time (UTC) — Time in Coordinated Universal Time that the event was
received by the ePO server.
• File Path
• Host Name — Name of the system which sent the event.
• IPv4 Address — IPv4 address of the system which sent the event.
• IPv6 Address — IPv6 address of the system which sent the event.
• MAC Address — MAC address of the system which sent the event.
• Network Protocol — The threat target protocol for network-homed threat classes.
• Port Number — The threat target port for network-homed threat classes.
• Process Name — The target process name (if applicable).
• Server ID
• Threat Name — Name of the threat.
• Threat Source Host Name — System name from which the threat originated.
• Threat Source IPv4 Address — IPv4 address of the system from which the threat originated.
• Threat Source IPv6 Address — IPv6 address of the system from which the threat originated.
• Threat Source MAC Address — MAC address of the system from which the threat originated.
• Threat Source URL — URL from which the threat originated.
• Threat Source User Name — User name from which the threat originated.
• Threat Type — Class of the threat.
• User Name — The threat source user name or email address.
Data exports from any table or chart
Data in any chart or table in ePolicy Orchestrator can be exported to four different formats.
Exported results are historical data and are not refreshed.
Unlike query results in the console, data in exported reports is not actionable.
Reports are available in several formats:
• CSV — Use this format to use the data in a spreadsheet application (for example, Microsoft
Excel).
• XML — Use this format to transform the data for other purposes.
• HTML — Use this report format to view the exported results as a web page.
• PDF — Use this report format when you need to print the results.
Exported data can be named and saved to any location, or emailed as attachments.
21McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 22

Configuring ePolicy Orchestrator Servers
MyAVERT Security Threats
MyAVERT Security Threats
The MyAvert Security Threats page informs you of the top ten medium-to-high-risk threats
for corporate users. You no longer need to manually search for this information from the press
(TV, radio, newspapers), informational web sites, mailing lists, or your peers. You are
automatically notified of these threats from McAfee Avert.
Protection status and risk assessment
You can easily determine whether the DAT and engine files in the Current branch of the master
repository provide protection against the top ten threats and, if not, the highest risk level of
any new threats.
Protection available
The DAT and engine files in the repository already provide protection against all threats that
are known to Avert. To determine whether each managed system is protected run a query
against DAT and engine file coveraget.
Protection pending on Mediium-to-Low Risk Threats
The updated DAT file for threats assessed by AVERT as medium risk is pending. However,
updated protection is available in a supplemental virus definition (EXTRA.DAT) file, which you
can manually download if you need protection before the next full DAT file is available, such
as in an outbreak scenario.
Protection Pending on High-Risk Threats
The updated DAT file for threats assessed by AVERT as high risk is pending. However, updated
protection is available in a supplemental virus definition (EXTRA.DAT) file, which you can
manually download if you need protection before the next full DAT file is available, such as in
an outbreak scenario.
Logging on and off from ePO servers
Use these tasks to log on to and off from ePO servers. Before using ePolicy Orchestrator, you
must be logged on to the ePO server with valid account credentials.
Tasks
Logging on to ePO servers
Logging off of ePO servers
Logging on to ePO servers
Use this task to log on to the ePO server. You must have valid credentials to do this. You can
log on to multiple ePO servers by opening a new browser session for each ePO server.
Task
1 Open an Internet browser and go to the URL of the server. The Log On to ePolicy
Orchestrator dialog box appears.
McAfee ePolicy Orchestrator 4.0.2 Product Guide22
Page 23

Configuring ePolicy Orchestrator Servers
Viewing the server version number
2 Type the User name and Password of a valid account.
NOTE: Passwords are case-sensitive.
3 Select the Language you want the software to display.
4 Click Log On.
Logging off of ePO servers
Use this task to log off of ePO servers. Log off from the ePO server whenever you finish using
the software.
Task
• To log off from the server, click Log Off at the top of any page, or close the browser.
Viewing the server version number
You can view the version number, edition, and license information of the ePolicy Orchestrator
server.
• To view the version number, edition, log on to the desired ePolicy Orchestrator server. This
information appears in the title bar.
• To view license information, go to the logon page.
• To view extension version information, go to Configuration | Extension.
Working with user accounts
Use these tasks to create and maintain user accounts.
Tasks
Creating user accounts
Editing user accounts
Deleting user accounts
Creating user accounts
Use this task to create a user account. You must be a global administrator to add, edit, or delete
user accounts.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Users.
2 Click New User. The New User page appears.
3 Type a user name.
23McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 24

Configuring ePolicy Orchestrator Servers
Working with permission sets
4 Select whether to enable or disable the logon status of this account. If this account is for
someone who is not yet a part of the organization you may want to disable it.
5 Select whether the new account uses ePO authentication or Windows authentication,
and provide the required credentials.
6 Optionally, provide the user’s full name, email address, phone number, and a description
in the Notes text box.
7 Choose to make the user a global administrator, or select the desired permission sets for
the user.
8 Click Save to save the current entries and return to the Users tab. The new user should
appear in the Users list.
Editing user accounts
Use this task to edit a user account. Global administrators can change passwords on any user
account. Other users can only change passwords on their own accounts.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Users.
2 Select the user you want to edit in the Users list, then click Edit.
3 Edit the account as needed.
4 Click Save.
Deleting user accounts
Use this task to delete a user account. You must be a global administrator to delete user
accounts.
NOTE: McAfee recommends disabling the Login status of an account instead of deleting it
until you are sure all valuable information associated with the account has been moved to other
users.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Users.
2 Select the user you want to delete in the Users list, then click Delete.
3 Click OK.
Working with permission sets
Use these tasks to create and maintain permission sets.
Tasks
Creating permission sets for user accounts
Duplicating permission sets
McAfee ePolicy Orchestrator 4.0.2 Product Guide24
Page 25
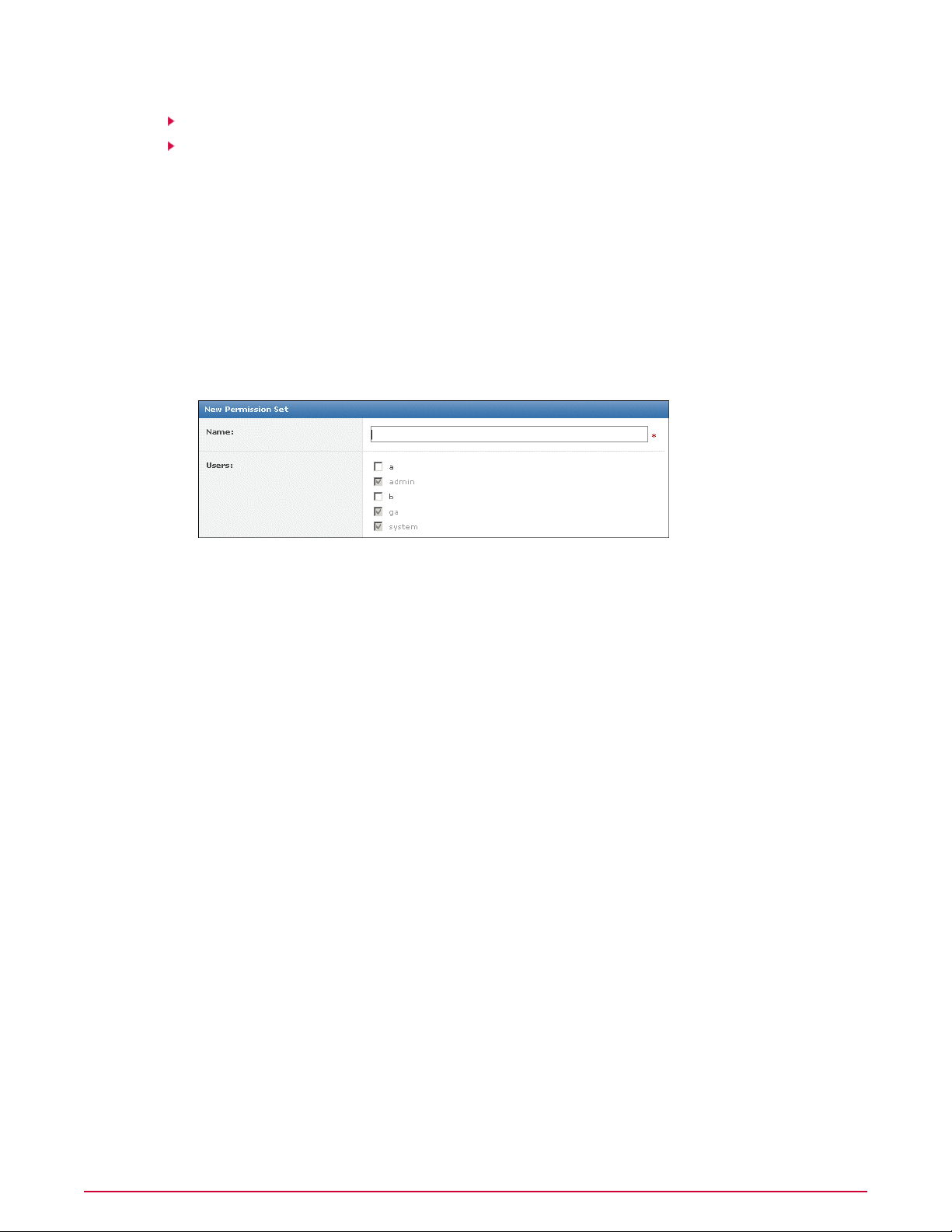
Configuring ePolicy Orchestrator Servers
Working with permission sets
Editing permission sets
Deleting permission sets
Creating permission sets for user accounts
Use this task to create a permission set.
Before you begin
You must be a global administrator to perform this task.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Permission Sets, then click New Permission Set.
Figure 1: New Permission Set page
2 Type a name for the permission set and select the users to which the set is assigned.
3 Click Save. The Permission Sets page appears.
4 Select the new permission set from the Permission Sets list. Its details appear to the
right.
5 Click Edit next to any section from which you want to grant permissions.
6 On the Edit Permission Set page that appears, select the appropriate options, then click
Save.
7 Repeat for all desired sections of the permission set.
Duplicating permission sets
Use this task to duplicate a permission set. Only global administrators can duplicate permission
sets.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Permission Sets, then select the permission set you want to edit
in the Permission Sets list. Its details appear to the right.
2 Click Duplicate, type a New name in the Action pane, then click OK.
3 Select the new duplicate in the Permission Sets list. Its details appear to the right.
4 Click edit next to any section with which you want to grant permissions.
5 On the Edit Permission Set page that appears, select the appropriate options, then click
Save.
6 Repeat for all sections of the permission set with which you want to grant permissions.
25McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 26

Configuring ePolicy Orchestrator Servers
Working with contacts
Editing permission sets
Use this task to edit a permission set. Only global administrators can edit permission sets.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Permission Sets, then select the permission set you want to edit
in the Permission Sets list. Its details appear to the right.
2 Click Edit next to any section from which you want to grant permissions.
3 On the Edit Permission Set page that appears, select the appropriate options, then click
Save.
4 Repeat for all desired sections of the permission set.
Deleting permission sets
Use this task to delete a permission set. Only global administrators can delete permission sets.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Permission Sets, then select the permission set you want to
delete in the Permission Sets list. Its details appear to the right.
2 Click Delete, then click OK in the Action pane. The permission set no longer appears in
the Permission Sets list.
Working with contacts
Use these tasks to create and maintain email address information of individuals that may receive
email messages from ePolicy Orchestrator.
Tasks
Creating contacts
Editing contacts
Deleting contacts
Creating contacts
Use this task to add email addresses to Contacts.
Task
For option definitions, click ? on the page displaying the options.
McAfee ePolicy Orchestrator 4.0.2 Product Guide26
Page 27
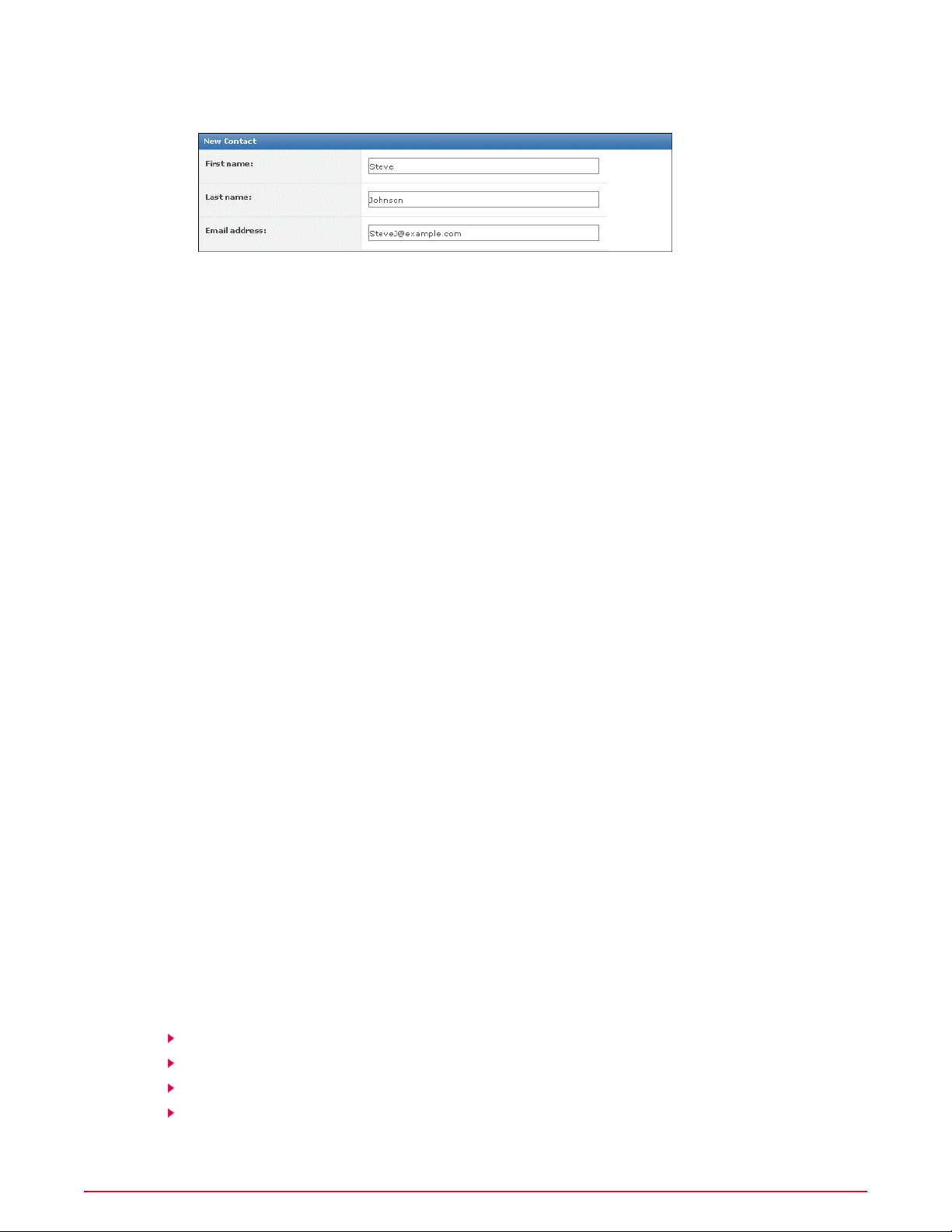
Configuring ePolicy Orchestrator Servers
Working with server settings
1 Go to Configuration | Contacts, then click New Contact.
Figure 2: New Contact page
2 Type a first name, last name, and email address for the contact.
3 Click Save. The new contact appears on the Contacts page.
Editing contacts
Use this task to edit information in an existing entry on the Contacts page.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Contacts, then select a contact.
2 Click Edit. The Edit Contact page appears.
3 Edit the information as desired.
4 Click Save.
Deleting contacts
Use this task to delete entries from the Contacts page.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Contacts, then select a contact.
2 Click Delete, then click OK in the Action pane. The contact no longer appears in the list.
Working with server settings
Use these tasks to configure and maintain server settings. Only the general server settings are
covered here. Feature-specific server settings are covered in the sections that cover those
features. For example, System Tree sorting server settings are covered in
for Management
Tasks
Specifying an email server
Configuring the template and location for exported reports
Determining which events are forwarded to the server
Viewing and changing communication ports
.
Organizing Systems
27McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 28

Configuring ePolicy Orchestrator Servers
Working with server settings
Specifying an email server
Use this task to specify an email server that ePolicy Orchestrator usea to send email messages.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Server Settings, then click Email Server in the Settings list.
2 Click Edit. The Edit Email Server page appears.
3 Type the SMTP server name and SMTP server port.
4 Select whether to authenticate to the email server, and provide credentials if Authenticate
is selected.
5 Type the email address of the return address on messages sent from ePolicy Orchestrator.
6 Click Save, then select Email Server.
7 In the content area next to Test email, type a valid email address for receiving email
messages, then click Test to validate the settings.
Configuring the template and location for exported reports
Use this task to define the appearance and storage location for tables and dashboards you
export as documents. You can configure:
• Headers and footers, including a custom logo, name, page numbering, etc.
• Page size and orientation for printing.
• Directory where exported tables and dashboards are stored.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Server Settings, then select Printing and Exporting in the
Settings list.
2 Click Edit. The Edit Printing and Exporting page appears.
3 Next to Headers and footers for exported documents:
a Click Edit Logo to provide a custom image or text to use as the header.
b Select the desired metadata from the drop-down lists that you want displayed in the
header and footer.
c Select a Page size.
d Select a Page orientation.
4 Type a new location or except the default location to save exported documents.
5 Click Save.
Determining which events are forwarded to the server
Use this task to determine which events are forwarded to the server. This selection impacts the
bandwidth used in your environment, as well as the results of event-based queries.
McAfee ePolicy Orchestrator 4.0.2 Product Guide28
Page 29
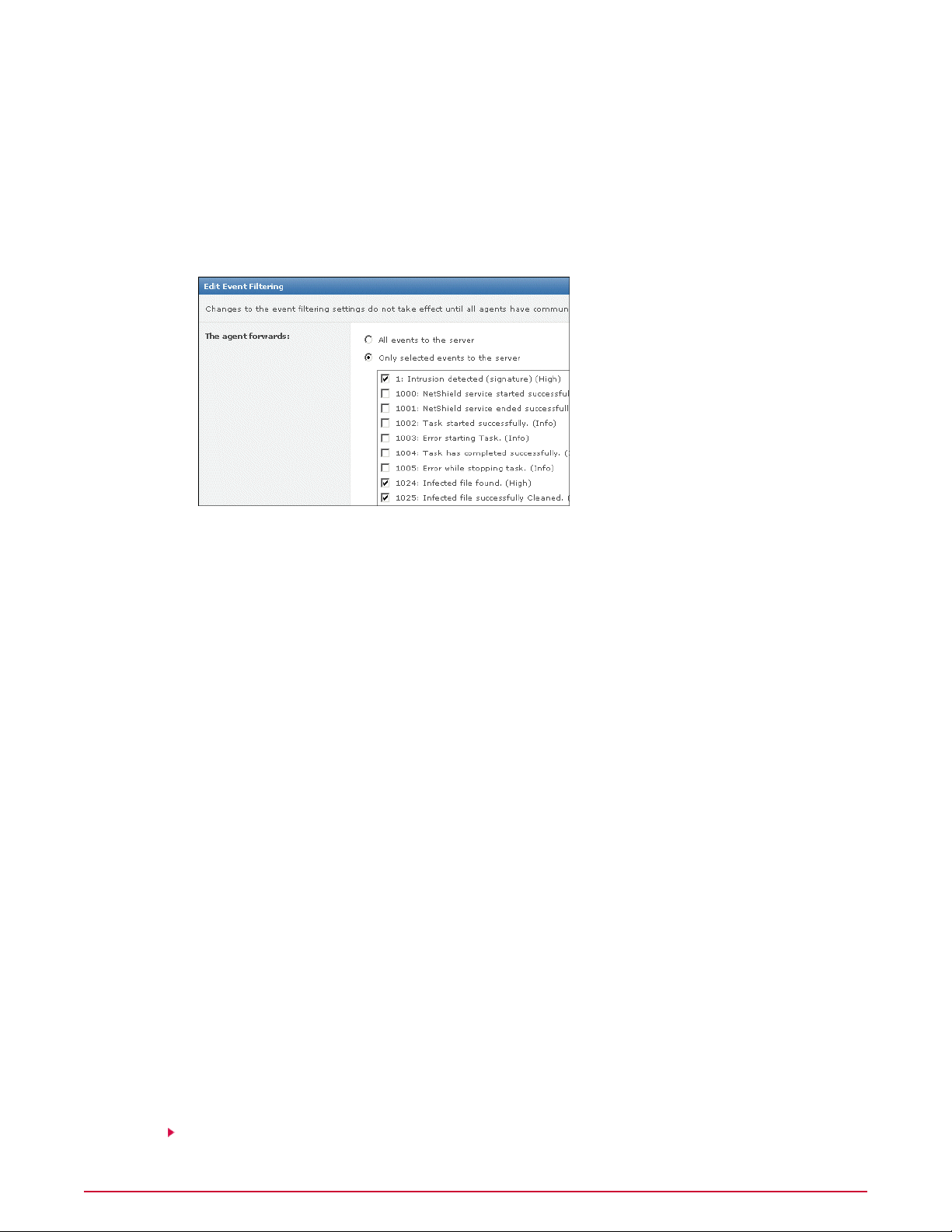
Configuring ePolicy Orchestrator Servers
Working with the Server Task Log
Before you begin
You must be a global administrator to perform this task.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Server Settings, select Event Filtering, then click Edit at the
bottom of the page. The Edit Event Filtering page appears.
Figure 3: Edit Event Filtering page
2 Select the events you want the agent to forward to the server, then click Save.
Changes to these settings take effect after all agents have communicated with the ePO server.
Viewing and changing communication ports
Use this task to view the ports ePolicy Orchestrator uses for communication with distributed
components. These ports were originally configured during installation. After installation you
can only change the two ports used for agent communication. If you need to change other
ports, you must reinstall the server and reconfigure the ports in the installation wizard.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Server Settings, select Ports, then click Edit at the bottom of
the page. The Edit Ports page appears.
2 Change the agent-server communication or agent broadcast communication ports as
necessary, then click Save.
NOTE: The agent-server communication port is used for agent-server communication; the
agent broadcast port is used for SuperAgent wake-up calls.
Working with the Server Task Log
Use these tasks to view and maintain the Server Task Log.
Tasks
Viewing the Server Task Log
29McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 30
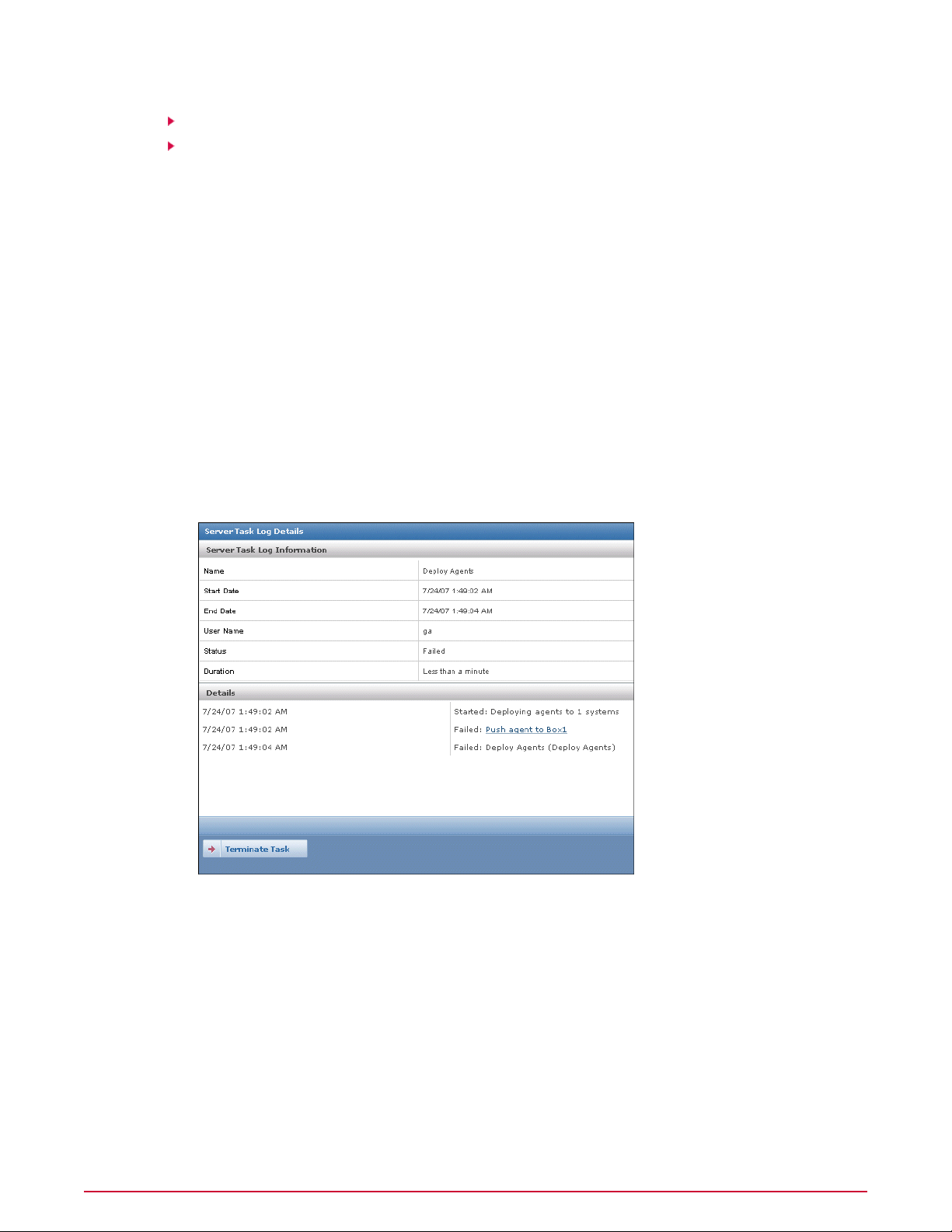
Configuring ePolicy Orchestrator Servers
Working with the Server Task Log
Filtering the Server Task Log
Purging the Server Task Log
Viewing the Server Task Log
Use this task to review the status of server tasks and long-running actions.
The status of each server task appears in the Status column:
• Completed — Task completed successfully.
• Failed — Task was started but did not complete successfully.
• In progress — Task has started but not finished.
• Waiting — This message appears when the task is waiting for another task to finish.
• Terminated — Task was terminated before it finished.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Reporting | Server Task Log.
2 Click any entry in the log to view its details.
Figure 4: Server Task Log Details page
Filtering the Server Task Log
As the Server Task Log grows, you can filter it to show only the most recent activity. You can
filter the log to show only entries from the last day, last seven days, last 30 days, or by Failed
or In Progress task statuses.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Reporting | Server Task Log.
McAfee ePolicy Orchestrator 4.0.2 Product Guide30
Page 31

Configuring ePolicy Orchestrator Servers
Working with the Audit Log
2 Select the desired filter from the Filter drop-down list.
Purging the Server Task Log
As the Server Task Log grows, you can purge items older than a user-configurable number of
days, weeks, months, or years.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Reporting | Server Task Log, then click Purge.
2 In the Action panel, type a number of days, weeks, months, or years. All items of this age
and older are deleted.
3 Click OK.
Working with the Audit Log
Use these tasks to view and purge the Audit Log. The Audit Log records actions taken by ePO
users.
Tasks
Viewing the Audit Log
Purging the Audit Log
Purging the Audit Log on a schedule
Viewing the Audit Log
Use this task to view a history of administrator actions. Available data depends on how often
and by what age the Audit Log is purged.
Before you begin
You must have appropriate permissions to perform this task.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Reporting | Audit Log. The details of administrator actions are displayed in a
table.
Figure 5: Audit Log page
31McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 32

Configuring ePolicy Orchestrator Servers
Working with the Audit Log
2 Click any of the column titles to sort the table by that column (alphabetically).
3 From the Filter drop-down list, select an option to narrow the amount of visible data. You
can remove all but the failed actions, or only show actions that occurred within a selected
amount of time.
4 Click any entry to view its details.
Figure 6: Audit Log Entry Details page
Purging the Audit Log
Use this task to purge the Audit Log. You can only purge Audit Log records by age. when you
purge the Audit Log, the records are deleted permanently.
Before you begin
You must have appropriate permissions to perform this task.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Reporting | Audit Log.
2 Click Purge.
3 In the Action panel, next to Purge records older than, type a number and select a time
unit.
4 Click OK.
All records older than the specified time frame are purged.
Purging the Audit Log on a schedule
Use this task to purge the Audit Log with a scheduled server task.
Before you begin
You must have appropriate permissions to perform this task.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Automation | Server Tasks, then click New Task. The Description page of the
Server Task Builder wizard appears.
2 Name and describe the task, then click Next. The Actions page appears.
McAfee ePolicy Orchestrator 4.0.2 Product Guide32
Page 33

Configuring ePolicy Orchestrator Servers
Working with the Event Log
3 Select Purge Audit Log from the drop-down list.
4 Select whether to purge by age or from a queries results. If you purge by query, you must
pick a query that results in a table of Audit Log entries.
5 Click Next. The Schedule page appears.
6 Schedule the task as needed, then click Next. The Summary page appears.
7 Review the task’s details, then click Save.
Working with the Event Log
Use these tasks to view and puge the Event Log
Tasks
Viewing the Event Log
Purging events
Purging the Event Log on a schedule
Viewing the Event Log
Use this task to view the Event Log.
Before you begin
You must have appropriate permissions to perform this task.
Task
1 Go to Reporting | Event Log.
2 Click any of the column titles to sort the events. You can also select Choose Columns
from the Options drop-down list to select different table columns that meet your needs.
3 Select events in the table, then click Show Related Systems to see the details of the
systems that sent the selected events.
Purging events
Use this task to purge event records from the database. Purging event records deletes them
permanently.
Before you begin
You must have appropriate permissions to perform this task.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Reporting | Event Log.
2 Click Purge.
3 In the Actions panel, next to Purge records older than, type a number and select a
time unit.
33McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 34
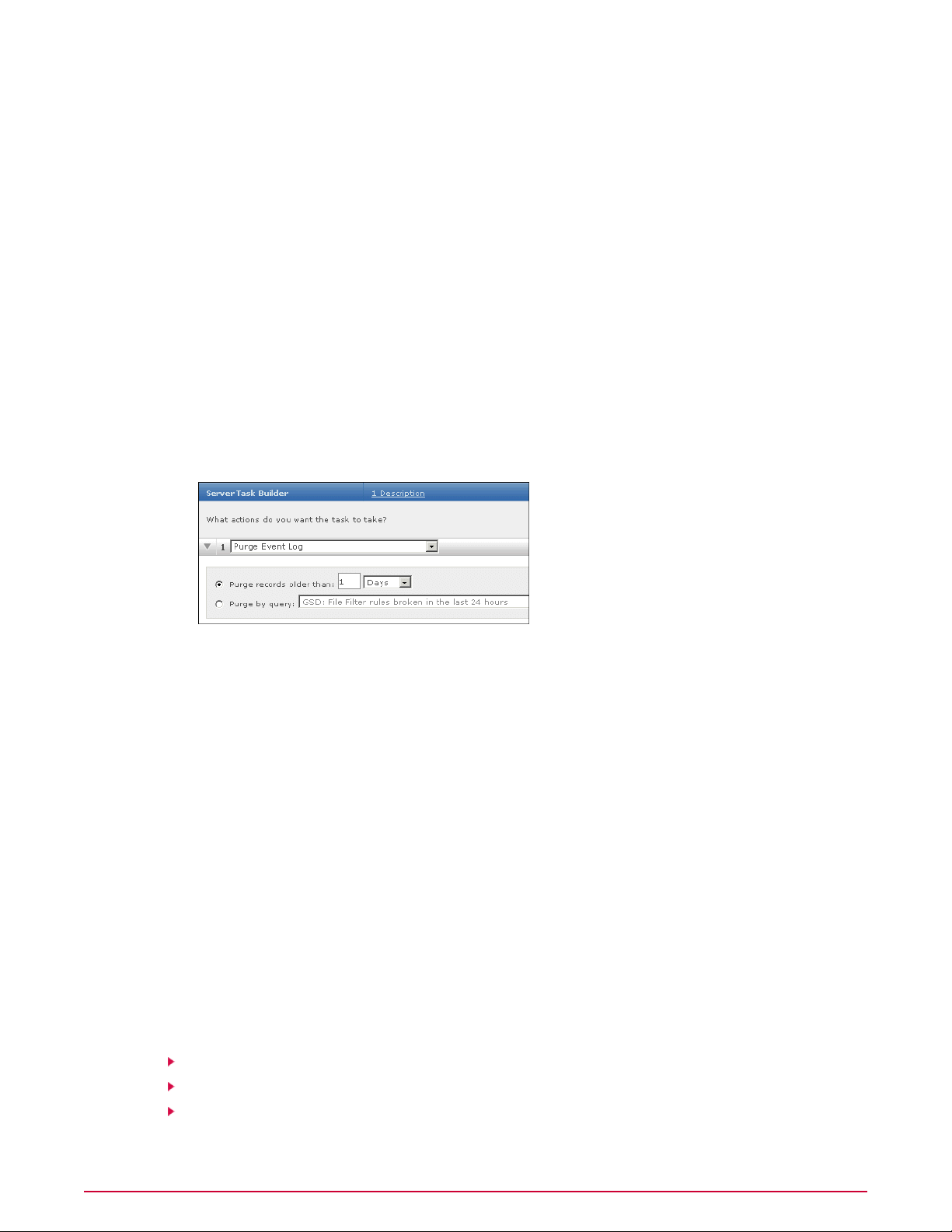
Configuring ePolicy Orchestrator Servers
Working with MyAvert Security Threats
4 Click OK.
Records older than the specified age are deleted permanently.
Purging the Event Log on a schedule
Use this task to purge the Event Log with a scheduled server task.
Before you begin
You must have appropriate permissions to perform this task.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Automation | Server Tasks, then click New Task. The Description page of the
Server Task Builder wizard appears.
2 Name and describe the task, then click Next. The Actions page appears.
3 Select Purge Event Log from the drop-down list.
Figure 7: Purge Event Log server task action
4 Select whether to purge by age or from a queries results. If you purge by query, you must
pick a query that results in a table of events.
5 Click Next. The Schedule page appears.
6 Schedule the task as needed, then click Next. The Summary page appears.
7 Review the task’s details, then click Save.
Working with MyAvert Security Threats
Use these task to mark threat notifications as read or unread or delete them. Data is sorted by
the date the threat was discovered. In addition, you can click the threat name to go to view
information from the McAfee Avert website about each threat.
NOTE: Each user views a MyAvert page that is unique to their account. When one user deletes,
or marks threat notifications as read or unread, these actions are not represented in the table
when another user account logs on.
Tasks
Configuring MyAvert update frequency and proxy settings
Viewing threat notifications
Deleting threat notifications
McAfee ePolicy Orchestrator 4.0.2 Product Guide34
Page 35
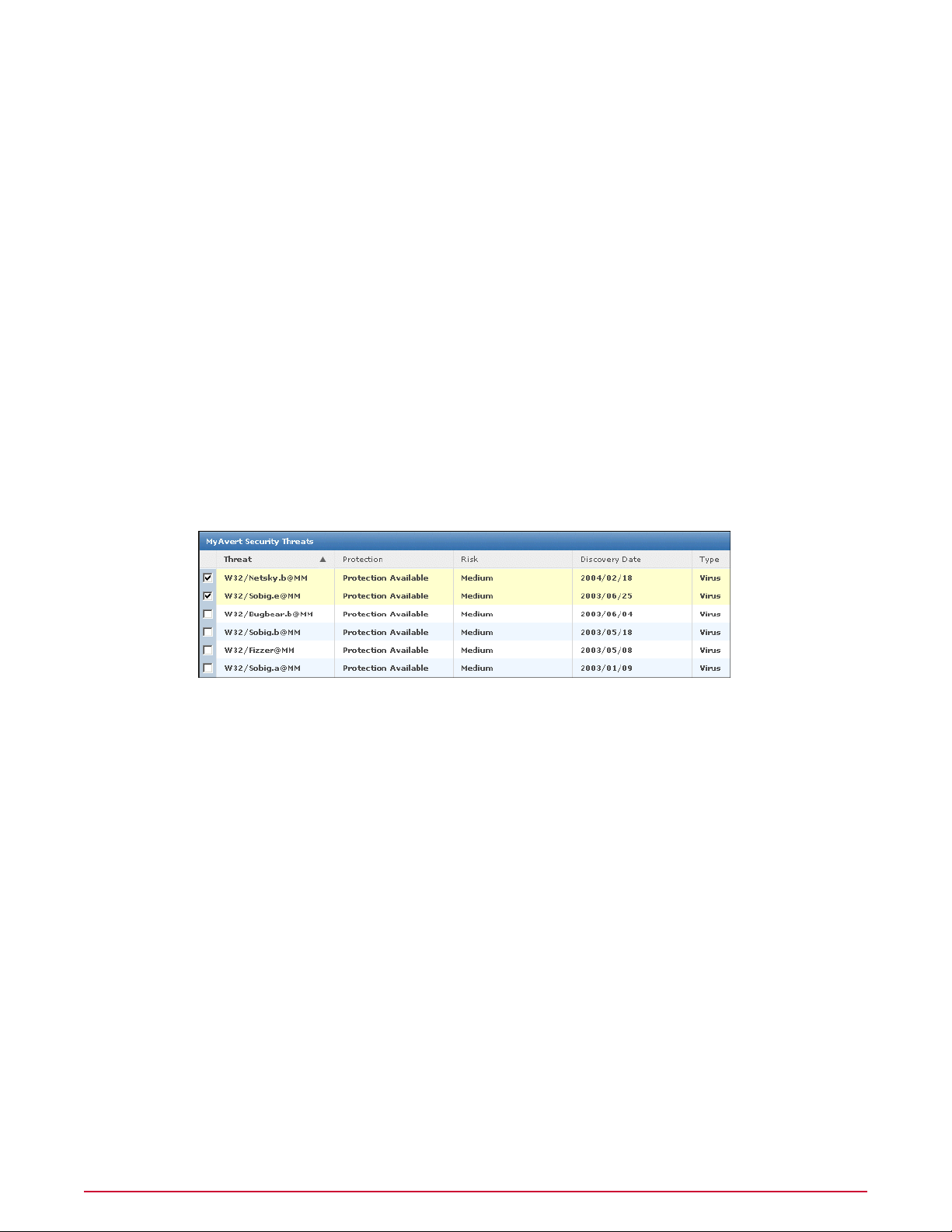
Configuring ePolicy Orchestrator Servers
Working with MyAvert Security Threats
Configuring MyAvert update frequency and proxy settings
Use this task to configure proxy settings adn the update frequency for MyAvert Security Threats.
Task
1 Go to Configuration | Server Settings, select MyAvert Security Threats, then click
Edit.
2 Choose how often you want the MyAvert threat notifications updated.
3 Then choose whether to use a proxy to access this service. If you select to use a proxy,
provide the required details to use your proxy.
Viewing threat notifications
Use this task to view notification threats and mark threats as read or unread. You can filter
threats by their importance, or whether they’ve been marked read, or unread.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Reporting | MyAvert.
Figure 8: MyAvert Security Threats page
2 If you want to narrow the viewable notifications, select an option from the Filter drop-down
list.
3 If you want to mark notifications as read or unread, select the desired threats, then click
Mark Read or Mark Unread, as needed. You may need to select Read or Unread from
the Filter drop-down list to view the notifications you want to mark.
Deleting threat notifications
Use this task to delete threat notifications from the MyAvert page. You cannot delete any
threat notifications for which protection is still pending.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Reporting | MyAvert.
2 Select threat notifications for which protection is available, then click Delete.
35McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 36
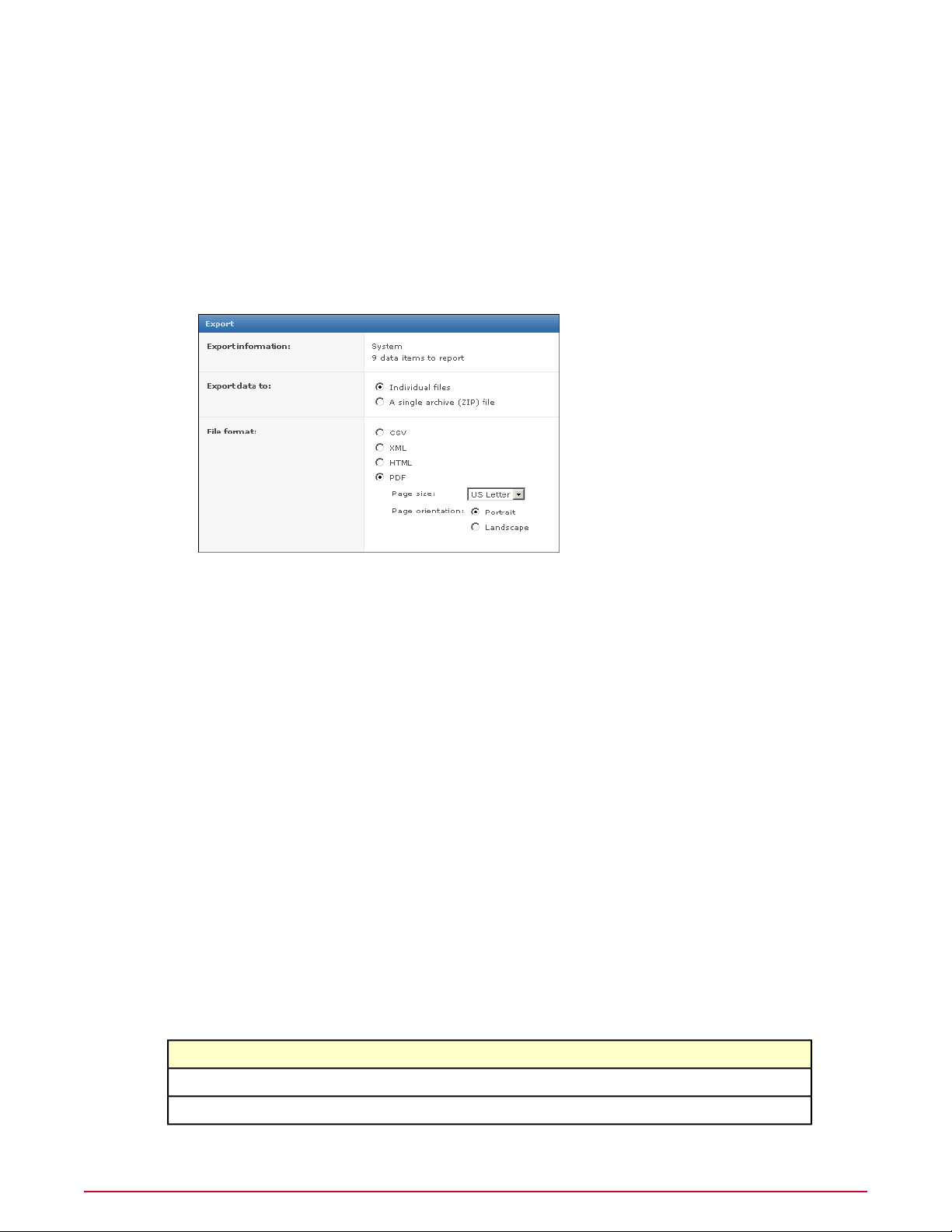
Configuring ePolicy Orchestrator Servers
Exporting tables and charts to other formats
Exporting tables and charts to other formats
Use this task to export data for other purposes. You can export to HTML and PDF finals for
viewing formats, or to CSV or XML files for using and transforming the data in other applications.
Task
For option definitions, click ? on the page displaying the options.
1 From the page displaying the data (tables or charts), select Export Table or Export Data
from the Options menu. The Export page appears.
Figure 9: Export page
2 Select whether the data files are exported individually or in a single archive (ZIP) file.
3 Select the format of the exported file. If exporting to a PDF file, select the page size and
orientation.
4 Select whether the files are emailed as attachments to selected recipients, or whether they
are saved to a location on the server to which a link is provided. You can open or save the
file to another location by right-clicking it.
NOTE: When typing multiple email addresses for recipients, you must separate entries with
a comma or semi-colon.
5 Click Export.
The files are created and either emailed as attachments to the recipients, or you are taken to
a page where you can access the files from links.
Allowed Cron syntax when scheduling a server task
Cron syntax is made up of 6 or 7 fields, separated by a space. Accepted Cron syntax, by field
in descending order, is detailed below in the table. Most Cron syntax is acceptable, however
there are a few cases that are not supported. For example, you cannot specify both the Day of
Week and Day of Month values.
Allowed Special CharactersAllowed ValuesField Name
, - * /0 - 59Seconds
, - * /0 - 59Minutes
McAfee ePolicy Orchestrator 4.0.2 Product Guide36
Page 37

Configuring ePolicy Orchestrator Servers
Allowed Cron syntax when scheduling a server task
Allowed Special CharactersAllowed ValuesField Name
, - * /0 - 23Hours
, - * ? / L W C1 - 31Day of Month
, - * /1 - 12, or JAN - DECMonth
, - * ? / L C #1 -7, or SUN - SATDay of Week
, - * /Empty, or 1970 - 2099Year (optional)
Notes on allowed special characters
• Commas (,) are allowed to specify additional values. For example, “5,10,30” or
“MON,WED,FRI”.
• Asterisks (*) are used for "every.” For example, “*” in the minutes field is "every minute".
• Question marks (?) are allowed to specify no specific value in the Day of Week or Day of
Month fields.
NOTE: The question mark must be used in one of these fields, but cannot be used in both.
• Forward slashes (/) identify increments. For example, “5/15” in the minutes field means the
task runs at minutes 5, 20, 35 and 50.
• The letter "L" means "last" in the Day of Week or Day of Month fields. For example, "0 15
10 ? * 6L" means the last Friday of every month at 10:15 am.
• The letter "W" means "weekday". So, if you created a Day of Month as "15W", this means
the weekday closest to the 15th of the month. Also, you can specify "LW", which would
mean the last weekday of the month.
• The pound character "#" identifies the "Nth" day of the month. For example, using "6#3"
in the Day of Week field is the third Friday of every month, "2#1" is the first Monday, and
"4#5" is the fifth Wednesday.
NOTE: If the month does not have fifth Wednesday, the task does not run.
37McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 38

Organizing Systems for Management
ePolicy Orchestrator 4.0.2 provides some new features and improvements to existing features
to organize and manage your systems.
• The Directory has been replaced by the System Tree — The System Tree allows for easy
management of policies and tasks, and organization of systems and groups.
• Tags — This new feature allows you to create labels that can be applied to systems manually
or automatically, based on criteria assigned to the tag. You can sort systems into groups
based on tags (like IP address sorting), or use tags for criteria in queries.
• NT Domain and Active Directory synchronization — This feature now allows for:
• True synchronization of the Active Directory structure.
• Control of potential duplicate system entries in the System Tree.
• Control of systems in the System Tree when they are deleted from the the domain or
container.
• Sorting systems into groups automatically — You can now use tags as sorting criteria in
addition to the previous functionalities of IP address sorting. Each type of sorting criteria
can be used alone or in combination.
The System Tree contains all of the systems managed by ePolicy Orchestrator; it is the the
primary interface for managing policies and tasks on these systems. You can organize systems
into logical groups (for example, functional department or geographic location) and sort them
by IP address or tags. You can manage policies (product configuration settings) and schedule
tasks (for example, updating virus definition files) for systems at any level of the System Tree.
Before configuring the software to deploy or manage the security software in your environment,
you must plan how to best organize systems for management and select the methods to bring
in and keep systems in the System Tree.
TIP: Many factors can influence how you should create and organize your System Tree. McAfee
recommends taking time to review this entire guide before you begin creating your System
Tree.
Are you setting up the System Tree for the first time?
When setting up the System Tree for the first time:
1 Reviewing the conceptual topics in this section to so you can use it with other features to
organize your systems efficently.
2 Evaluate the methods of populating it with your systems, and keeping it up-to-date. For
example, through Active Directory synchronization, or criteria-based sorting.
3 Create and populate the System Tree.
McAfee ePolicy Orchestrator 4.0.2 Product Guide38
Page 39

Organizing Systems for Management
The System Tree
Contents
The System Tree
Considerations when planning your System Tree
Tags and how they work
Active Directory and NT domain synchronization
Criteria-based sorting
How a system is first placed in the System Tree
Working with tags
Creating and populating groups
Moving systems manually within the System Tree
The System Tree
The System Tree organizes managed systems in units for monitoring, assigning policies,
scheduling tasks, and taking actions.
Groups
The System Tree is a hierarchical structure that allows you to group your systems within units
called
groups
Groups have these characteristics:
• Groups can be created by global administrators or users with the appropriate permissions.
• A group can include both systems and other groups.
• Groups are administered by a global administrator or a user with appropriate permissions.
Grouping systems with similar properties or requirements into these units allows you to manage
policies for systems in one place, rather than setting policies for each system individually.
As part of the planning process, consider the best way to organize systems into groups prior
to building the System Tree.
Lost&Found group
The System Tree root (My Organization) includes a Lost&Found group. Depending on the
methods for creating and maintaining the System Tree, the server uses different characteristics
to determine where to place systems. The Lost&Found group stores systems whose locations
could not be determined.
The Lost&Found group has the following characteristics:
• It can't be deleted.
• It can't be renamed.
• Its sorting criteria can't be changed (although you can provide sorting criteria for the
subgroups you create within it.)
• It always appears last in the list and is not alphabetized among its peers.
• All users with view permissions to the System Tree can see systems in Lost&Found.
.
39McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 40

Organizing Systems for Management
Considerations when planning your System Tree
• When a system is sorted into Lost&Found, it is placed in a subgroup named for the system’s
domain. If no such group exists, one is created.
NOTE: If you delete systems from the System Tree, you also need to remove their agents.
Otherwise, these systems continue to appear in the Lost&Found group because the agent
continues to communicate to the server.
Inheritance
Inheritance is an important property that simplifies policyand task administration. Because of
inheritance, child groups in the System Tree hierarchy inherit policies set at their parent groups.
For example:
• Policies set at the My Organization level of the System Tree are inherited by groups below
it.
• Group policies are inherited by subgroups or individual systems within that group.
Inheritance is enabled by default for all groups and individual systems that you add to the
System Tree. This allows you to set policies and schedule client tasks in fewer places.
However, inheritance can be broken by applying a new policy at any location of the System
Tree (provided a user has appropriate permissions) to allow for customization. You can lock
policy assignments to preserve inheritance.
Considerations when planning your System Tree
An efficient and well-organized System Tree can simplify maintenance. Many administrative,
network, and political realities of each environment can affect how your System Tree is
structured. Plan the organization of the System Tree before you build and populate it. Especially
for a large network, you want to build the System Tree only once.
Because every network is different and requires different policies — and possibly different
management — McAfee recommends planning your System Tree before implementing the
software.
Regardless of the methods you choose to create and populate the System Tree, consider your
environment while planning the System Tree.
Administrator access
When planning your System Tree organization, consider the access requirements of those who
must manage the systems.
For example, you may have very decentralized network administration in your organization,
where different administrators have responsibilities over different parts of the network. For
security reasons, you may not have a global administrator account that can access every part
of your network. In this scenario, you may not be able to set policies and deploy agents using
a single global administrator account. Instead, you may need to organize the System Tree into
groups based on these divisions and create accounts and permission sets.
Questions to consider include:
• Who is responsible for managing which systems?
• Who requires access to view information about the systems?
• Who should not have access to the systems and the information about them?
McAfee ePolicy Orchestrator 4.0.2 Product Guide40
Page 41

Organizing Systems for Management
Considerations when planning your System Tree
These questions impact both the System Tree organization, and the permission sets you create
and apply to user accounts.
Environmental borders and their impact on system organization
How you organize the systems for management depends on the borders that exist in your
network. These borders influence the organization of the System Tree differently than the
organization of your network topology.
McAfee recommends evaluating these borders in your network and organization, and whether
they must be considered when defining the organization of your System Tree.
Topological borders
Your network is already defined by NT domains or Active Directory containers. The better
organized your network environment, the easier it is to create and maintain the System Tree
with the synchronization features.
Geographic borders
Managing security is a constant balance between protection and performance. Organize your
System Tree to make the best use of limited network bandwidth. Consider how the server
connects to all parts of your network, especially remote locations that are often connected by
slower WAN or VPN connections, instead of faster LAN connections. You may want to configure
updating and agent-server communication policies differently for remote sites to minimize
network traffic over slower connections.
Grouping systems first by geography provides several advantages for configuring policies:
• You can configure update policies for the group so that all systems update from one or more
distributed software repositories located nearby.
• You can schedule client tasks to run at times better suited to the site’s location.
Political borders
Many large networks are divided by individuals or groups responsible for managing different
portions of the network. Sometimes these borders do not coincide with topological or geographic
borders. Who accesses and manages the segments of the System Tree affects how you structure
it.
Functional borders
Some networks are divided by the roles of those using the network; for example, Sales and
Engineering. Even if the network is not divided by functional borders, you may need to organize
segments of the System Tree by functionality if different groups require different policies.
A business group may run specific software that requires special security policies. For example,
arranging your email exchange servers into a group and setting specific exclusions for VirusScan
Enterprise on-access scanning.
Subnets and IP address ranges
In many cases, organizational units of a network use specific subnets or IP ranges, so you can
create a group for a geographic location and set IP filters for it. Also, if your network isn’t spread
out geographically, you can use network location, such as IP address, as the primary grouping
criterion.
41McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 42

Organizing Systems for Management
Tags and how they work
If possible, consider using sorting criteria based on IP address information to automate System
Tree creation and maintenance. Set IP subnet masks or IP address range criteria for applicable
groups within the System Tree. These filters automatically populate locations with the appropriate
systems.
Tags and systems with similar characteristics
You can use tags for automated sorting into groups. Tags identify systems with similar
characteristics. If you can organize your groups by characteristics, you can create and assign
tags based on that criteria, then use these tags as group sorting criteria to ensure systems are
automatically placed within the appropriate groups.
If possible, consider using tag-based sorting criteria to automatically populate groups with the
appropriate systems.
Operating systems and software
Consider grouping systems with similar operating systems to manage operating system-specific
products and policies more easily. If you have some older systems running Windows 95 or
Windows 98. You can create a group for such legacy systems together to deploy and manage
security products on these systems separately. Additionally, by giving these systems a
corresponding tag, you can automatically sort them into a group.
Tags and how they work
Tags are a new feature of ePolicy Orchestrator 4.0.2. Tags are like labels that you can apply
to one or more systems, automatically (based on criteria) or manually. Once tags are applied,
you can use them organize systems in the System Tree or run queries that result in an actionable
list of systems. Therefore, with tags as organizational criteria, you can apply policies, assign
tasks, and take a number of actions on systems with the same tags.
Traits of tags
With tags, you can:
• Apply one or more tags to one or more systems.
• Apply tags manually.
• Apply tags automatically, based on user-defined criteria, when the agent communicates with
the server.
• Exclude systems from tag application.
• Run queries to group systems with certain tags, then take direct action on the resulting list
of systems.
• Base System Tree sorting criteria on tags to group systems into desired System Tree groups
automatically.
Who can use tags
Users with appropriate permissions can:
• Create and edit tags and tag criteria.
McAfee ePolicy Orchestrator 4.0.2 Product Guide42
Page 43

Organizing Systems for Management
Active Directory and NT domain synchronization
• Apply and remove existing tags to systems in the groups to which they have access.
• Exclude systems from receiving specific tags.
• Use queries to view and take actions on systems with certain tags.
• Use scheduled queries with chained tag actions to maintain tags on specific systems within
the parts of the System Tree they have access.
• Configure sorting criteria based on tags to ensure systems stay in the appropriate groups
of the System Tree.
Types of tags
There are two types of tags:
• Tags without criteria. These tags can be applied only to selected systems in the System Tree
(manually) and systems listed in the results of a query.
• Criteria-based tags. These tags are applied to all non-excluded systems at each agent-server
communication. Such tags use criteria based on any properties sent by agent. They can also
be applied to non-excluded systems on demand.
Active Directory and NT domain synchronization
ePolicy Orchestrator 4.0.2 offers improved integration with both Active Directory and NT domains
as a source for systems, and even (in the case of Active Directory) as a source for the structure
of the System Tree.
Active Directory synchronization
If your network runs Active Directory, you can use Active Directory synchronization to create,
populate, and maintain part or all of the System Tree with Active Directory synchronization
settings. Once defined, the System Tree is updated with any new systems (and subcontainers)
in your Active Directory.
Active Directory integration is enhanced with the release of ePolicy Orchestrator 4.0.2. In
addition to previous functionality, you can now:
• Synchronize with your Active Directory structure, by importing systems and the Active
Directory subcontainers (as System Tree groups) and keeping them up-to-date with Active
Directory. At each synchronization, both systems and the structure are updated in the System
Tree to reflect the systems and structure of Active Directory.
• Import systems as a flat list from the Active Directory container (and its subcontainers) into
the synchronized group.
• Control what to do with potential duplicate systems.
• Use the system description, which is imported from Active Directory with the systems.
In previous versions of ePolicy Orchestrator, there were the two tasks: Active Directory Import
and Active Directory Discovery. Now, use this process to integrate the System Tree with your
Active Directory systems structure:
1 Configure the synchronization settings on each group that is a mapping point in the System
Tree. At the same location, you can configure whether to:
2 Deploy agents to discovered systems.•
43McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 44

Organizing Systems for Management
Active Directory and NT domain synchronization
• Delete systems from the System Tree when they are deleted from Active Directory.
• Allow or disallow duplicate entries of systems that already exist elsewhere in the System
Tree.
3 Use the Synchronize Now action to import Active Directory systems (and possibly structure)
into the System Tree according to the synchronization settings.
4 Use an NT Domain/Active Directory Synchronization server task to regularly synchronize
the systems (and possibly the Active Directory structure) with the System Tree according
to the synchronization settings.
Types of Active Directory synchronization
There are two types of Active Directory synchronization (systems only and systems and
structure). Which one you use depends on the level of integration you want with Active Directory.
With each type, you control the synchronization by selecting whether to:
• Deploy agents automatically to systems new to ePolicy Orchestrator. You may not want to
set this on the initial synchronization if you are importing a large number of systems and
have limited bandwidth. The agent installation package is about 3.62 MB in size. However,
you may want to deploy agents automatically to any new systems that are discovered in
Active Directory during subsequent synchronizations.
• Delete systems from ePolicy Orchestrator (and remove their agents) when they are deleted
from Active Directory.
• Prevent adding systems to the group if they exist elsewhere in the System Tree. this ensures
no duplicate systems if you manually move or sort the system to another location.
• Exclude certain Active Directory containers from the synchronization. These containers and
their systems are ignored during synchronization.
Systems and structure
When using this synchronization type, changes in the Active Directory structure are carried over
into your System Tree structure at the next synchronization. When systems or containers are
added, moved, or removed in Active Directory, they are added, moved, or removed in the
corresponding locations of the System Tree.
When to use this synchronization type
Use this to ensure the System Tree (or parts of it) look exactly like your Active Directory structure.
If the organization of Active Directory meets your security management needs and you want
the System Tree to continue to look like the mapped Active Directory structure, use this
synchronization type with subsequent synchronizations.
Systems only
Use this synchronization type to import systems from an Active Directory container, including
those in non-excluded subcontainers, as a flat list to a mapped System Tree group. You can
then move these to the desired locations in the System Tree by assigning sorting criteria to
groups.
If you choose this synchronization type, be sure to select not to add systems again if they exist
elsewhere in the System Tree. This prevents duplicate entries for systems in the System Tree.
McAfee ePolicy Orchestrator 4.0.2 Product Guide44
Page 45

Organizing Systems for Management
Criteria-based sorting
When to use this synchronization type
Use this synchronization type when you use Active Directory as a regular source of systems for
ePolicy Orchestrator, but the organizational needs for security management do not coincide
with the organization of containers and systems in Active Directory.
NT domain synchronization
Use your NT domains as a source for populating your System Tree. When you synchronize a
group to an NT domain, all systems from the domain are put in the group as a flat list. You can
manage those systems in the single group, or you can create subgroups for more granular
organizational needs. Use a method, like automatic sorting to populate these subgroups
automatically.
If you move systems to other groups or subgroups of the System Tree, be sure to select to not
add the systems when they already exist elsewhere in the System Tree.
Unlike Active Directory synchronization, only the system names are synchronized with NT domain
synchronization — the system description is not synchronized.
Criteria-based sorting
As in past releases of ePolicy Orchestrator, you can use IP address information to automatically
sort managed systems into specific groups. You can also create sorting criteria based on tags,
which are like labels assigned to systems. You can use either type of criteria or both to ensure
systems are where you want them in the System Tree.
Systems only need to match one criterion of a group's sorting criteria to be placed in the group.
After creating groups and setting your sorting criteria, take a Test Sort action to confirm the
criteria and sorting order achieve the desired results.
Once you have added sorting criteria to your groups, you can run the Sort Now action. The
action moves selected systems to the appropriate group automatically. Systems that do not
match the sorting criteria of any group are moved to Lost&Found.
New systems that call into the server for the first time are added automatically to the correct
group. However, if you define sorting criteria after the initial agent-server communication, you
must run the Sort Now action on those systems to move them immediately to the appropriate
group, or wait until the next agent-server communication.
Sorting status of systems
On any system or collection of systems, you can enable or disable System Tree sorting. If you
disable System Tree sorting on a system, it is excluded from sorting actions.
System Tree sorting settings on the ePO server
For sorting to take place, sorting must be enabled on the server and on the systems. By default,
sorting at each agent-server communication is enabled.
Test sorting systems
Use this feature to view where systems would be placed during a sort action. The Test Sort
page displays the systems and the paths to the location where they would be sorted. Although
this page does not display the sorting status of systems, if you select systems on the page
45McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 46

Organizing Systems for Management
Criteria-based sorting
(even ones with sorting disabled) clicking Move Systems places those systems in the location
identified.
How settings affect sorting
You can choose three server settings that determine whether and when systems are sorted.
Also, you can choose whether any system can be sorted by enabling or disabling System Tree
sorting on selected systems in the System Tree.
Server settings
The server has three settings:
• Disable System Tree sorting — If criteria-based sorting does not meet your security
management needs and you want to use other System Tree features (like Active Directory
synchronization) to organize your systems, select this setting to prevent other ePO users
from mistakenly configuring sorting criteria on groups and moving systems to undesirable
locations.
• Sort systems on each agent-server communication — Systems are sorted again at
each agent-server communication. When you change sorting criteria on groups, systems
move to the new group at their next agent-server communication.
• Sort systems once — Systems are sorted at the next agent-server communication and
marked to never be sorted again at agent-server communication as long as this setting is
selected. However, selecting such a system and clicking Sort Now does sort the system.
System settings
You can disable or enable System Tree sorting on any system. If System Tree sorting is disabled
on a system, that system will not be sorted regardless of how the sorting action is taken. If
System Tree sorting is enabled on a system, that system is sorted always for the manual Sort
Now action, and may be sorted at agent-server communication, depending on the System Tree
sorting server settings.
IP address sorting criteria
In many networks, subnets and IP address information reflect organizational distinctions, such
as geographical location or job function. If IP address organization coincides with your needs,
consider using this information to create and maintain parts or all of your System Tree structure
by setting IP address sorting criteria for such groups. This functionality has changed in this
version of ePolicy Orchestrator, which now allows for setting of IP sorting criteria randomly
through the tree — you no longer need to ensure that the child group’s IP address sorting
criteria is a subset of the parent’s (as long as the parent has no assigned criteria). Once
configured, you can sort systems at agent-server communication, or only when a sort action is
manually initiated.
Please know that IP address sorting criteria should not overlap between different groups. Each
IP range or subnet mask in a group’s sorting criteria should cover a unique set of IP addresses.
If criteria does overlap, which group those systems end up in depends on the order of the
subgroups on the Groups tab.
McAfee ePolicy Orchestrator 4.0.2 Product Guide46
Page 47

Organizing Systems for Management
How a system is first placed in the System Tree
Tag-based sorting criteria
In addition to using IP address information to sort systems into the appropriate group, you can
define sorting criteria based on the tags assigned to systems.
Tag-based criteria can be used with IP address-based criteria for sorting.
Group order and sorting
To provide additional flexibility with System Tree management, you can configure the order of
a group’s subgroups, and therefore the order by which they are considered for a system’s
placement during sorting. When multiple subgroups have matching criteria, changing this order
can change where a system ends up in the System Tree.
Additionally, if you are using catch-all groups, they must be the last subgroup in the list.
Catch-all groups
Catch-all groups are groups whose sorting criteria is set to All others on the Sorting Criteria
page of the group. Only subgroups at the last position of the sort order can be catch-all groups.
These groups receive all systems that sorted into the parent group, but did not sort into any
of the catch-all’s peers.
How a system is first placed in the System Tree
When the agent communicates with the server for the first time, the server uses an algorithm
to place the system in the System Tree. When it cannot find any location for a system, it puts
the system in the Lost&Found group.
At the first agent-server communication
On each agent-server communication, the server attempts to locate the system in the System
Tree by agent GUID (only systems whose agents have already called into the server for the
first time have an agent GUID in the database). If a matching system is found, it is left in it’s
existing location.
If a matching system is not found, the server uses an algorithm to sort the systems into the
appropriate groups. Systems can be sorted into any criteria-based group in the System Tree,
no matter how deep it is in the structure, as long as each parent group in the path does not
have non-matching criteria. Parent groups of a criteria-based subgroup must either have no
criteria or matching criteria.
Remember, the order subgroups are placed the Group tab, determines the order subgroups
are considered by the server when it searches for a group with matching criteria.
1 The server searches for a system without an agent GUID (its agent has never called in
before) with a matching name in a group with the same name as the domain. If found,
the system is placed in that group. This can happen after the first Active Directory or NT
domain synchronization, or when you have manually added systems to the System Tree.
2 If a matching system is still not found, the server searches for a group of the same name
as the domain from which the system originates. If such a group is not found, one is created
under the Lost&Found group, and the system placed there.
3 Properties are updated for the system.
47McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 48

Organizing Systems for Management
Working with tags
4 The server applies all criteria-based tags to the system if the server is configured to run
sorting criteria at each agent-server communication.
5 What happens next depends on whether System Tree sorting is enabled on both the server
and the system.
• If System Tree sorting is disabled on either the server or the system, the system is left
where it is.
• If System Tree sorting is enabled on the server and system, the system is moved based
on the sorting criteria in the System Tree groups.
NOTE: Systems that are added by Active Directory or NT Domain synchronization have
System Tree sorting disabled by default. Therefore, they are not sorted on the first
agent-server communication
6 The server considers the sorting criteria of all top-level groups according to the sorting
order on the My Organization group’s Group tab. The system is placed in the first group
with matching criteria or a catch-all group it considers.
a Once sorted into a group, each of its subgroups are considered for matching criteria
according to their sorting order on the Group tab.
b This continues until there is no subgroup with matching criteria for the system, and is
placed in the last group found with matching criteria.
7 If such a top-level group is not found, then the subgroups of top-level groups (without
sorting criteria) are considered according to their sorting.
8 If such a second-level criteria-based group is not found, then the criteria-based third-level
groups of the second-level unrestricted groups considered.
NOTE: Subgroups of groups with unmatching criteria are not considered, a group must
have matching criteria or have no criteria in order for its subgroups to be considered for a
system.
9 This continues down through the System Tree until a system is sorted into a group.
NOTE: If the server System Tree sorting setting is configured to sort only on the first
agent-server communication, a flag is set on the system and it can never be sorted again
at agent-server communication unless the server setting is changed to enable sorting on
every agent-server communication.
10 If the server cannot sort the system into any group, it is placed in the Lost&Found group
within a subgroup named after its domain.
Working with tags
Use these tasks to create and apply tags to systems.
Tasks
Creating tags with the Tag Builder
Excluding systems from automatic tagging
Applying tags to selected systems
Applying criteria-based tags automatically to all matching
McAfee ePolicy Orchestrator 4.0.2 Product Guide48
Page 49

Organizing Systems for Management
Working with tags
Creating tags with the Tag Builder
Use this task to create a tag with the Tag Builder wizard. Tags can use criteria that’s evaluated
against every system:
• Automatically at agent-server communication.
• When the Run Tag Criteria action is taken.
• Manually on selected systems, regardless of criteria, with the Apply Tag action.
Tags without criteria can only be applied manually to selected systems.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree | Tag Catalog, then click New Tag. The Description
page of the Tag Builder wizard appears.
2 Type a name and meaningful description, then click Next. The Criteria page appears.
3 Select and configure the desired criteria, then click Next. The Evaluation page appears.
NOTE: To apply the tag automatically, you must configure criteria for the tag.
4 Select whether systems are evaluated against the tag’s criteria only when the Run Tag
Criteria action is taken, or also at each agent-server communication, then click Next. The
Preview page appears.
NOTE: These options are unavailable if criteria was not configured. When systems are
evaluated against a tag’s criteria, the tag is applied to systems that match the criteria and
have not been excluded from the tag.
5 Verify the information on this page, then click Save.
NOTE: If the tag has criteria, this page displays the number of systems that will receive
this tag when evaluated against its criteria.
The tag is added to the list of tags on the Tag Catalog page.
Excluding systems from automatic tagging
Use this task to exclude systems from having specifc tags applied. Alternatively, you can use a
query to collect systems, then exclude the desired tags from those systems from the query
results.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree, then select the group that contains the systems.
2 Select the desired systems, then click Exclude Tag at the bottom of the page.
NOTE: If you don’t see this button, click More Actions.
3 In the Action panel, select the desired tag to exclude from the selected systems from the
drop-down list, then click OK.
4 Verify the systems have been excluded from the tag:
a Go to Systems | Tag Catalog, then select the desired tag in the list of tags.
49McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 50

Organizing Systems for Management
Working with tags
b Next to Systems with tag in the details pane, click the link for the number of systems
excluded from automatic tagging. The Systems Excluded from the Tag page appears.
c Verify the desired systems are in the list.
Applying tags to selected systems
Use this task to apply a tag manually to selected systems in the System Tree.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree, then select the group that contains the desired system.
2 Select the desired systems, then click Apply Tag at the bottom of the page.
NOTE: If you don’t see this button, click More Actions.
3 In the Action panel, select the desired tag from the drop-down list to apply to the selected
systems, then click OK.
4 Verify the tags have been applied:
a Go to Systems | Tag Catalog, then select the desired tag in the list of tags.
b Next to Systems with tag in the details pane, click the link for the number of systems
tagged manually. The Systems with Tag Applied Manually page appears.
c Verify the desired systems are in the list.
Applying criteria-based tags automatically to all matching
Use these tasks to apply criteria-based tags automatically to all systems that match its criteria.
Tasks
Applying criteria-based tags to all matching systems
Applying criteria-based tags on a schedule
Applying criteria-based tags to all matching systems
Use this task to apply a criteria-based tag to all systems that match the criteria, except for those
that have been excluded from the tag.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | Tag Catalog, then select the desired tag from the Tags list.
2 Click Run Tag Criteria.
3 In the Action panel, select whether to reset manually tagged and excluded systems.
NOTE: This removes the tag from systems that don’t match the criteria and applies the
tag to systems which match criteria but were excluded from receiving the tag.
4 Click OK.
5 Verify the systems have the tag applied:
McAfee ePolicy Orchestrator 4.0.2 Product Guide50
Page 51
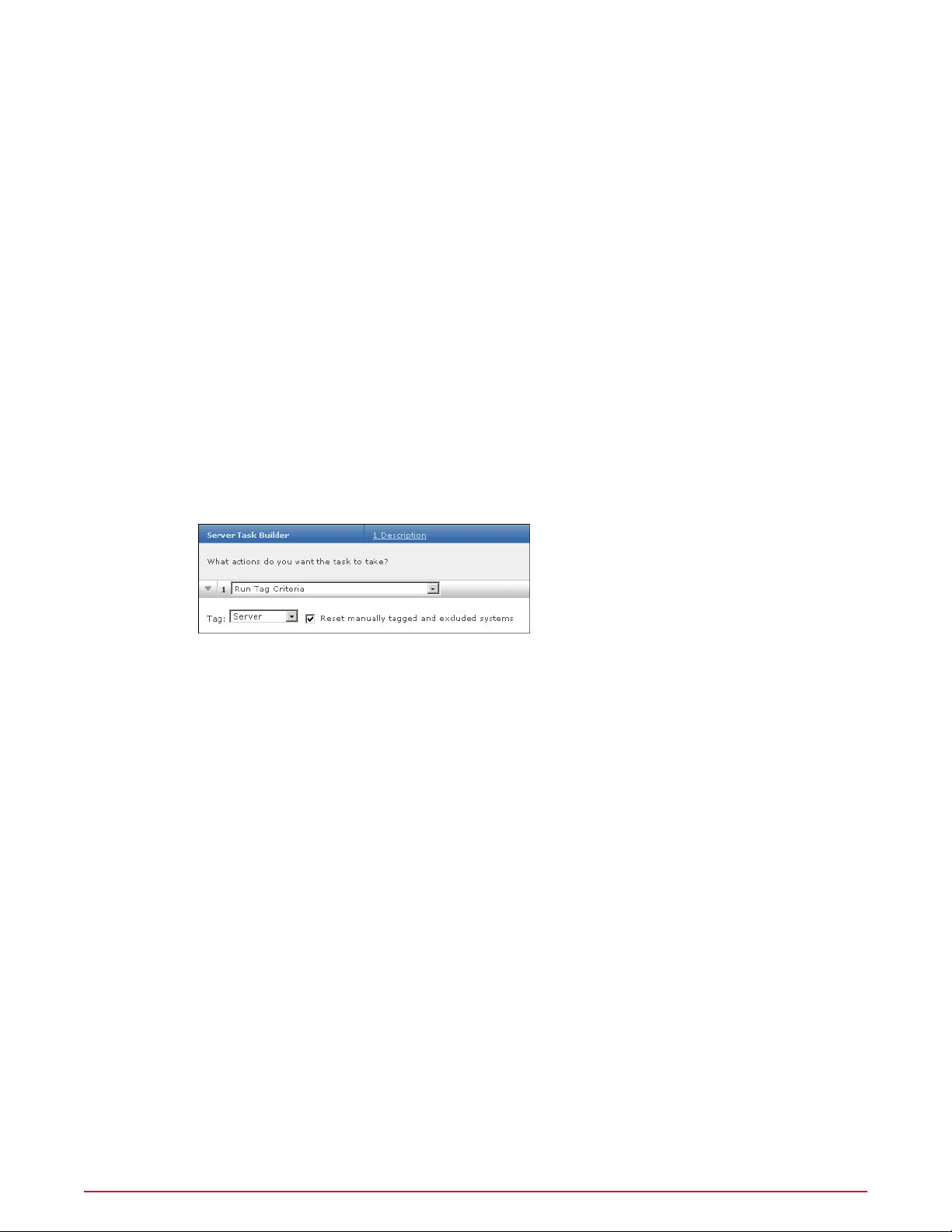
Organizing Systems for Management
Creating and populating groups
Go to Systems | Tag Catalog, then select the desired tag in the list of tags.a
b Next to Systems with tag in the details pane, click the link for the number of systems
with tag applied by criteria. The Systems with Tag Applied by Criteria page appears.
c Verify the desired systems are in the list.
The tag is applied to all systems that match its criteria.
Applying criteria-based tags on a schedule
Use this task to schedule a regular task that applies a tag to all systems that match its criteria.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Automation | Server Tasks, then click New Task. The Server Task Builder
page appears.
2 Name and describe the task and select whether the task is enabled once it is created, then
click Next. The Actions page appears.
3 Select Run Tag Criteria from the drop-down list, then select the desired tag from the
Tag drop-down list.
Figure 10: Run Tag Criteria server task action
4 Select whether to reset manually tagged and excluded systems.
NOTE: This removes the tag on systems that don’t match the criteria and applies the tag
to systems that match criteria but were excluded from receiving the tag.
5 Click Next. The Schedule page appears.
6 Schedule the task as desired, then click Next. The Summary page appears.
7 Review the task settings, then click Save.
The server task is added to the list on the Server Tasks page. If you selected to enable the
task in the Server Task Builder wizard, it runs at the next scheduled time.
Creating and populating groups
Use these tasks to create and populate groups. You can populate groups with systems, either
by typing NetBIOS names for individual systems or by importing systems directly from your
network.
There is no single way to organize a System Tree, and because every network is different, your
System Tree organization can be as unique as your network layout. Although you won’t use
each method offered, you can use more than one.
For example, if you use Active Directory in your network, consider importing your Active Directory
containers rather than your NT domains. If your Active Directory or NT domain organization
51McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 52

Organizing Systems for Management
Creating and populating groups
does not make sense for security management, you can create your System Tree in a text file
and import it into your System Tree. If you have a smaller network, you can create your System
Tree by hand and import each system manually.
Best practices
While you won’t use all of the System Tree creation methods, you also probably won’t use just
one. In many cases, the combination of methods you choose balances ease of creation with
the need for additional structure to make policy management efficient.
For example, you might create the System Tree in two phases. First, you can create 90% of
the System Tree structure by importing whole NT domains or Active Directory containers into
groups. Then, you can manually create subgroups to classify systems together that may have
similar anti-virus or security policy requirements. In this scenario, you could use tags, and
tag-based sorting criteria on these subgroups to ensure they end up in the desired groups
automatically.
If you want all or part of your System Tree to mirror the Active Directory structure, you can
import and regularly synchronize the System Tree to Active Directory.
If one NT domain is very large or spans several geographic areas, you can create subgroups
and point the systems in each to a separate distributed repository for efficient updating. Or,
you can create smaller functional groupings, such as for different operating system types or
business functions, to manage unique policies. In this scenario, you could also use tags and
tag-based sorting criteria to ensure the systems stay in the group.
If your organization’s IP address information coincides with your security management needs,
consider assigning IP address sorting criteria to these groups before agent distribution, to ensure
that when agents check into the server for the first time, the systems are automatically placed
in the correct location. If you are implementing tags in your environment, you can also use tags
as sorting criteria for groups, or even a combination of IP address and tag sorting criteria.
Although you can create a detailed System Tree with many levels of groups. McAfee recommends
that you create only as much structure as is useful. In large networks, it is not uncommon to
have hundreds or thousands of systems in the same container. Assigning policies in fewer places
is easier than having to maintain an elaborate System Tree.
Although you can add all systems into one group in the System Tree, such a flat list makes
setting different policies for different systems very difficult, especially for large networks.
Tasks
Creating groups manually
Adding systems manually to an existing group
Importing systems from a text file
Sorting systems into criteria-based groups
Importing Active Directory containers
Importing NT domains to an existing group
Synchronizing the System Tree on a schedule
Updating the synchronized group with an NT domain manually
Creating groups manually
Use this task to create groups manually. You can populate these groups with systems by typing
NetBIOS names for individual systems or by importing systems directly from your network.
McAfee ePolicy Orchestrator 4.0.2 Product Guide52
Page 53
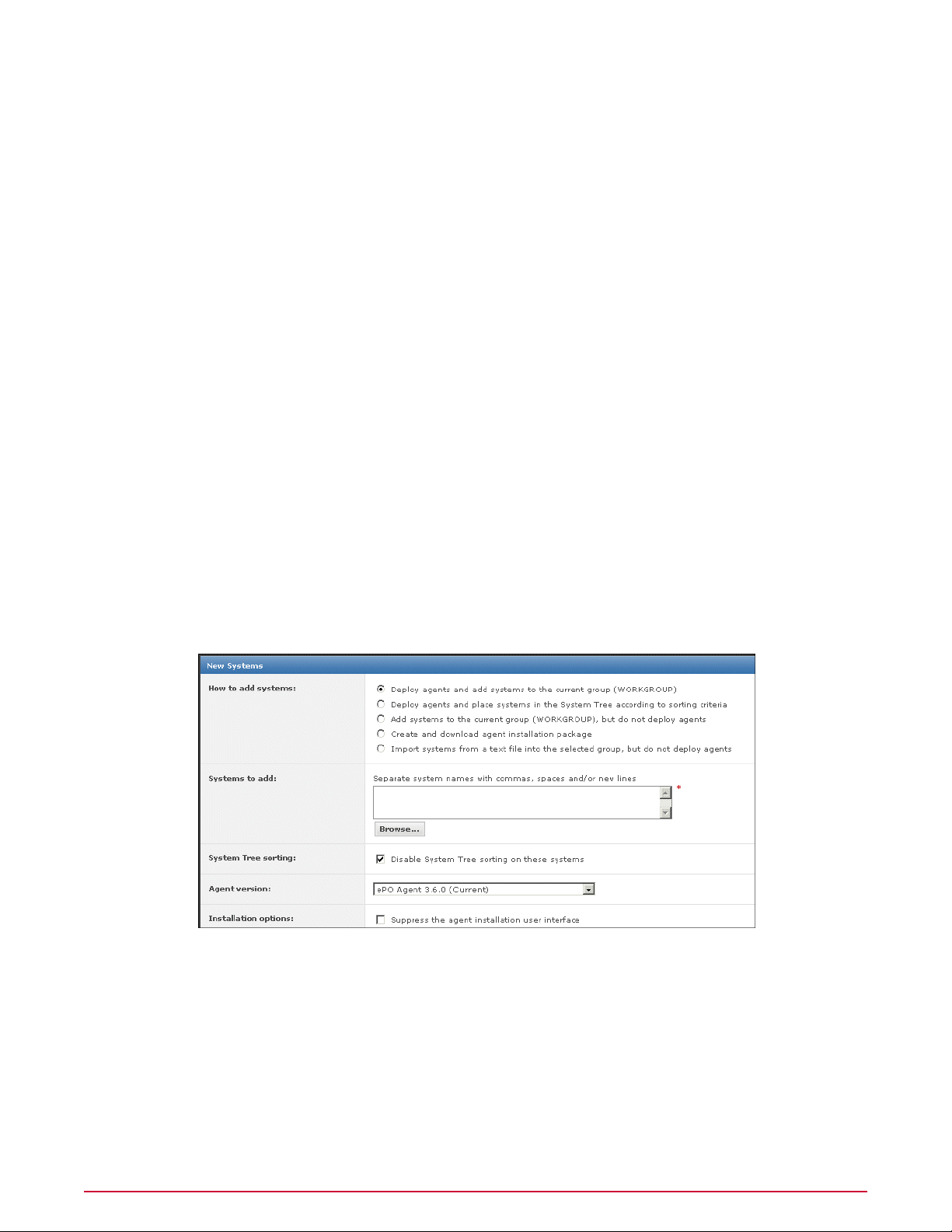
Organizing Systems for Management
Creating and populating groups
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree | Group, then select the desired group in the System
Tree, under which to create another group.
2 Click New Subgroup at the bottom of the page. The New Subgroup dialog box appears.
3 Type the desired name then click OK. The new group appears in the System Tree.
4 Repeat as necessary until you are ready to populate the groups with the desired systems.
Add systems to the System Tree and ensure they get to the desired groups by:
• Typing system names manually.
• Importing them from NT domains or Active Directory containers. You can regularly
synchronize a domain or a container to a group for ease of maintenance.
• Setting up IP address-based or tag-based sorting criteria on the groups. When agents
check in from systems with matching IP address information or matching tags, they are
automatically placed in the appropriate group.
Adding systems manually to an existing group
Use this task to import systems from your Network Neighborhood to groups. You can also import
a network domain or Active Directory container.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree, then click New Systems. The New Systems page
appears.
Figure 11: New Systems page
2 Select whether to deploy the agent to the new systems, and whether the systems are
added to the selected group or to a group according to sorting criteria.
3 Next to Systems to add, type the NetBIOS name for each system in the text box, separated
by commas, spaces, or line breaks. Alternatively, click Browse to select the systems.
4 If you selected Deploy agents and add systems to the current group, you can enable
automatic System Tree sorting. Do this to apply the sorting criteria to these systems.
5 If you selected to deploy agents to the new systems:
53McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 54

Organizing Systems for Management
Creating and populating groups
Select the agent version to deploy.a
b Select whether to suppress the agent installation user interface on the system. Select
this if you do not want the end-user to see the installation interface.
c Configure the agent installation path or accept the default.
d Type valid credentials to install the agent.
6 Click OK.
Importing systems from a text file
Use these tasks to create a text file of systems and groups to import into the System Tree.
Tasks
Creating a text file of groups and systems
Importing systems and groups from a text file
Creating a text file of groups and systems
Use this task to create a text file of the NetBIOS names for your network systems that you want
to import into a group. You can import a flat list of systems, or organize the systems into groups,
then add the specified systems to them. You can create the text file by hand. In large networks,
use other network administration tools to generate a text file list of systems on your network.
Define the groups and their systems by typing the group and system names in a text file. Then
import that information into ePolicy Orchestrator. You must have network utilities, such as the
NETDOM.EXE utility available with the Microsoft Windows Resource Kit, to generate complete
text files containing complete lists of the systems on your network. Once you have the text file,
edit it manually to create groups of systems, and import the entire structure into the System
Tree.
Regardless of how you generate the text file, you must use the correct syntax before importing
it.
Task
For option definitions, click ? on the page displaying the options.
1 List each system separately on its own line. To organize systems into groups, type the
group name followed by a backslash (\), then list the systems belonging to that group
beneath it, each on a separate line.
GroupA\system1
GroupA\system2
GroupA\system3
GroupA\system4
2 Verify the names of groups and systems, and the syntax of the text file, then save the text
file to a temporary folder on your server.
Importing systems and groups from a text file
Use this task to import systems or groups of systems into the System Tree from a text file you
have created and saved.
McAfee ePolicy Orchestrator 4.0.2 Product Guide54
Page 55

Organizing Systems for Management
Creating and populating groups
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree, then click New Systems. The New Systems page
appears.
2 Select Import systems from a text file into the selected group, but do not deploy
agents.
3 Click Browse, then select the text file.
4 Select what to do with systems that already exist elsewhere in the System tree.
5 Click OK.
The systems are imported to the selected group in the System Tree. If your text file organized
the systems into groups, the server creates the groups and imports the systems.
Sorting systems into criteria-based groups
Use these tasks to configure and implement sorting to group systems. For systems to sort into
groups, sorting must be enabled on the server and the desired systems, and sorting criteria
and the sorting order of groups must be configured.
Tasks
Adding sorting criteria to groups
Enabling System Tree sorting on the server
Enabling and disabling System Tree Sorting on Systems
Sorting systems manually
Adding sorting criteria to groups
Use this task to configure sorting criteria for a group. Sorting criteria can be based on IP address
information or tags.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree | Group, then select the group in the System Tree.
2 Next to Sorting criteria click Edit. The Sorting Criteria page for the selected group
appears.
3 Select Systems that match any of the criteria below, then the criteria selections
appear.
NOTE: Although you can configure multiple sorting criteria for the group, a system only
has to match a single criterion to be placed in this group.
4 Configure the criterion. Options include:
• Tags — Add specific tags to ensure systems with such tags that come into the parent
group are sorted into this group.
• IP addresses — Use this text box to define an IP address range or subnet mask as
sorting criteria. Any system whose address falls within it is sorted into this group.
5 Repeat as necessary until sorting criteria areconfigured for the group, then click Save.
55McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 56

Organizing Systems for Management
Creating and populating groups
Enabling System Tree sorting on the server
Use this task to enable System Tree sorting on the server. System Tree sorting must be enabled
on the server and the desired systems for systems to be sorted.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Server Settings, select System Tree Sorting in the Setting
Categories list, then click Edit.
2 Select whether to sort systems only on the first agent-server communication or on each
agent-server communication.
If you selected to sort only on the first agent-server communication, all enabled systems are
sorted on their next agent-server communication and are never sorted again for as long as this
option is selected. However, these systems can be sorted again manually by taking the Sort
Now action, or by changing this setting to sort on each agent-server communication.
If you selected to sort on each agent-server communication, all enabled systems are sorted at
each agent-server communication as long as this option is selected.
Enabling and disabling System Tree Sorting on Systems
Use this task to enable or disable System Tree sorting on systems. The sorting status of a
system determines whether it can be sorted into a criteria-based group. Alternatively, you can
change the sorting status on systems in any table of systems (such as query results), and also
automatically on the results of a scheduled query.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree | Systems, then select the desired systems.
2 Click Change Sorting Status, then select whether to enable or disable System Tree
sorting on selected systems.
NOTE: You may need to click More Actions to access the Change Sorting Status
option. To view the sorting status of systems, add the column to the Systems page.
Figure 12: Change Sorting Status options
Depending on the server setting for System Tree sorting, these systems are sorted on the next
agent-server communication. Otherwise, they can only be sorted with the Sort Now action.
Sorting systems manually
Use this task to sort selected systems into groups with criteria-based sorting enabled.
McAfee ePolicy Orchestrator 4.0.2 Product Guide56
Page 57

Organizing Systems for Management
Creating and populating groups
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree | Systems, then select the group that contains the
desired systems.
2 Select the systems, then click Sort Now. You may have to click More Actions to access
this option. The Sort Now dialog box appears.
NOTE: If you want to preview the results of the sort before sorting, click Test Sort instead.
(However, if you move systems from within the Test Sort page, all selected systems are
sorted, even if they have System Tree sorting disabled.)
3 Click OK to sort the systems.
Importing Active Directory containers
Use this task to import systems from your network’s Active Directory containers directly into
your System Tree by mapping Active Directory source containers to the groups of the System
Tree. Unlike previous versions, you can now:
• Synchronize the System Tree structure to the Active Directory structure so that when
containers are added or removed in Active Directory, the corresponding group in the System
Tree is added or removed also.
• Delete systems from the System Tree when they are deleted from Active Directory.
• Prevent duplicate entries of systems in the System Tree when they already exist in other
groups.
Before you begin
You must have appropriate permissions to perform this task.
Best practices
Implementation of this feature depends on whether you are creating the System Tree for the
first time or if you upgrading from a previous version with an existing System Tree structure
with which you are not using Active Directory integration.
If you have been using a previous version of ePolicy Orchestrator and already have a
fully-populated System Tree, you can still take advantages of Active Directory integration by
mapping your System Tree groups to Active Directory containers. You can use this feature to
create mapping points between Active Directory containers and System Tree groups to import
any new systems found in Active Directory to the appropriate location of the System Tree.
Task
For option definitions, click ? on the page displaying the options.
57McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 58

Organizing Systems for Management
Creating and populating groups
1 Go to Systems | System Tree | Group, then select the desired group in the System
Tree. This should be the group to which you want to map an Active Directory container.
NOTE: You cannot synchronize the My Organization or Lost&Found groups of the
System Tree.
Figure 13: Synchronization Settings page
2 Next to Synchronization type click Edit. The Synchronization Settings page for the
selected group appears.
3 Next to Synchronization type select Active Directory. The Active Directory
synchronization options appear.
4 Select the type of Active Directory synchronization you want to occur between this group
and the desired Active Directory container (and its subcontainers):
• Systems and container structure — Select this option if you want this group to truly
reflect the Active Directory structure. When synchronized, the System Tree structure
under this group is modified to reflect that of the Active Directory container it's mapped
to. When containers are added or removed in Active Directory, they are added or
removed in the System Tree. When systems are added, moved, or removed from Active
Directory, they are added, moved, or removed from the System Tree.
• Systems only — Select this option if you only want the systems from the Active
Directory container (and non-excluded subcontainers) to populate this group, and this
group only. No subgroups are created like when mirroring Active Directory.
5 Select whether a duplicate entry for the system will be created for a system that already
exists in another group of the System Tree.
TIP: McAfee does not recommend selecting this option, especially if you are only using the
Active Directory synchronization as a starting point for security management and use other
System Tree management functionalities (for example, tag sorting) for further organizational
granularity below the mapping point.
6 In Active Directory domain, type the fully-qualified domain name of your Active Directory
domain.
7 In Active Directory credentials, type the Active Directory user credentials that ePolicy
Orchestrator uses to retrieve the Active Directory information.
8 Next to Container, click Browse and select a source container in the Select Active
Directory Container dialog box, then click OK.
9 To exclude specific subcontainers, click Add next to Exclusions and select a subcontainer
to exclude, then click OK.
McAfee ePolicy Orchestrator 4.0.2 Product Guide58
Page 59

Organizing Systems for Management
Creating and populating groups
10 Select whether to deploy agents automatically to new systems. If you do, be sure to
configure the deployment settings.
TIP: McAfee recommends that you do not deploy the agent during the initial import if the
container is large. Deploying the 3.62 MB agent package to many systems at once may
cause network traffic issues. Instead, import the container, then deploy the agent to groups
of systems at a time, rather than all at once. Consider revisiting this page and selecting
this option after the initial agent deployment, so that the agent is installed automatically
on new systems added to Active Directory.
11 Select whether to delete systems from the System Tree when they are deleted from the
Active Directory domain.
12 To synchronize the group with Active Directory immediately, click Synchronize Now.
Clicking Synchronize Now saves any changes to the synchronization settings before
synchronizing the group. If you have an Active Directory synchronization notification rule
enabled, an event is generated for each system added or removed (these events appear
in the Notfifications Log, and are queryable). If you deployed agents to added systems,
the deployment is initiated to each added system. When the synchronization completes,the
Last Synchronization time is updated, displaying the time and date when the
synchronization finished, not when any agent deployments completed.
NOTE: Alternatively, you can schedule an NT Domain/Active Directory Synchronization
server task for the first synchronization. This is useful if you are deploying agents to new
systems on the first synchronization, when bandwidth is a larger concern.
13 When the synchronization completes, view the results with the System Tree.
Once the systems are imported, distribute agents to them if you did not select to do so
automatically. Also, consider setting up a recurring NT Domain/Active Directory Synchronization
server task to keep your System Tree up to date with any new systems or organizational changes
in your Active Directory containers.
Importing NT domains to an existing group
Use this task to import systems from an NT domain to a group you created manually.
You can populate groups automatically by synchronizing entire NT domains with specified
groups. This is an easy way to add all the systems in your network to the System Tree at once
as a flat list with no system description.
If the domain is very large, you can create subgroups to assist with policy management or
System Tree organization. To do this, first import the domain into a group of your System Tree,
then manually create logical subgroups.
TIP: To manage the same policies across several domains, import each of the domains into a
subgroup under the same group, on which you can set policies that inherit into each of the
subgroups.
When using this method:
• Set up IP address or tag sorting criteria on subgroups to automatically sort the imported
systems.
• Schedule a recurring NT Domain/Active Directory Synchronization server task for easy
maintenance.
59McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 60

Organizing Systems for Management
Creating and populating groups
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree | Group, then select or create a group in the System
Tree.
2 Next to Synchronization type, click Edit. The Synchronization Settings page for the
selected group appears.
Figure 14: Synchronization Settings page
3 Next to Synchronization type, select NT Domain. The domain synchronization settings
appear.
4 Next to Systems that exist elsewhere in the System Tree, select what to do with
systems that would be added during synchronization already exist in another group of the
System Tree.
NOTE: McAfee does not recommend selecting Add systems to the synchronized group
and leave them in their current System Tree location, especially if you are only using
the NT domain synchronization as a starting point for security management and use other
System Tree management functionalities (for example, tag sorting) for further organizational
granularity below the mapping point.
5 Next to Domain, click Browse and select the NT domain to map to this group, then click
OK. Alternatively, you can type the name of the domain directly in the text box.
NOTE: When typing the domain name, do not use the fully-qualified domain name.
6 Select whether to deploy agents automatically to new systems. If you do so, be sure to
configure the deployment settings.
TIP: McAfee recommends that you do not deploy the agent during the initial import if the
domain is large. Deploying the 3.62 MB agent package to many systems at once may cause
network traffic issues. Instead, import the domain, then deploy the agent to smaller groups
of systems at a time, rather than all at once. However, once you've finished deploying
agents, consider revisiting this page and selecting this option after the initial agent
deployment, so that the agent is installed automatically on any new systems that are added
to the group (or its subgroups) by domain synchronization.
7 Select whether to delete systems from the System Tree when they are deleted from the
NT domain.
McAfee ePolicy Orchestrator 4.0.2 Product Guide60
Page 61

Organizing Systems for Management
Creating and populating groups
8 To synchronize the group with the domain immediately, click Synchronize Now, then
wait while the systems in the domain are added to the group.
NOTE: Clicking Synchronize Now saves changes to the synchronization settings before
synchronizing the group. If you have an NT domain synchronization notification rule enabled,
an event is generated for each system added or removed. (These events appear in the
Notifications Log, and are queryable). If you selected to deploy agents to added systems,
the deployment is initiated to each added system. When the synchronization completes,
the Last Synchronization time is updated. The time and date are when the synchronization
finished, not when any agent deployments completed.
9 If you want to synchronize the group with the domain manually, click Compare and
Update. The Manually Compare and Update page appears.
NOTE: Clicking Compare and Update saves any changes to the synchronization settings.
a If you are going to remove any systems from the group with this page, select whether
to remove their agents when the system is removed.
b Select the systems to add to and remove from the group as necessary, then click Update
Group to add the selected systems. The Synchronize Setting page appears.
10 Click Save, then view the results in the System Tree if you clicked Synchronize Now or
Update Group.
Once the systems are added to the System Tree, distribute agents to them if you did not select
to deploy agents as part of the synchronization. Also, consider setting up a recurring NT
Domain/Active Directory Synchronization server task to keep this group up-to-date with new
systems in the NT domain.
Synchronizing the System Tree on a schedule
Use this task to schedule a server task that updates the System Tree with changes in the mapped
domain or Active Directory container. Depending on a group’s synchronization settings, this
task:
• Adds new systems on the network to the specified group.
• Adds new corresponding groups when new Active Directory containers are created.
• Deletes corresponding groups when Active Directory containers are removed.
• Deploys agents to new systems.
• Removes systems that are no longer in the domain or container.
• Applies policies and tasks of the site or group to new systems.
• Prevents or allows duplicate entries of systems that still exist in the System Tree that you’ve
moved to other locations.
NOTE: The agent cannot be deployed to all operating systems in this manner. You might need
to distribute the agent manually to some systems.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Automation | Server Tasks, then click New Task at the bottom of the page. The
Description page of the Server Task Builder appears.
61McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 62

Organizing Systems for Management
Moving systems manually within the System Tree
2 Name the task and choose whether it is enabled once it is created, then click Next. The
Actions page appears.
3 From the drop-down list, select NT Domain/Active Directory Synchronization.
4 Select whether to synchronize all groups or selected groups. If you are synchronizing only
some synchronized groups, click Select Synchronized Groups and select specific ones.
5 Click Next. The Schedule page appears.
6 Schedule the task, then click Next. The Summary page appears.
7 Review the task details, then click Save.
NOTE: In addition to the task running at the scheduled time, you can run this task
immediately by clicking Run next to the task on the Server Tasks tab.
Updating the synchronized group with an NT domain manually
Use this task to update a synchronized group with its mapped NT domain, including:
• Add systems currently in the domain.
• Remove systems from your System Tree that are no longer in the domain.
• Remove agents from all systems that no longer belong to the specified domain.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree | Group, then select the group that is mapped to the NT
domain.
2 Next to Synchronization type, click Edit. The Synchronization Settings page appears.
3 Near the bottom of the page, click Compare and Update. The Manually Compare and
Update page appears.
4 If you are removing systems from the group, select whether to remove the agents from
systems that are removed.
5 Click Add All or Add to import systems from the network domain to the selected group.
Click Remove All or Remove to delete systems from the selected group.
6 Click Update Group when finished.
Moving systems manually within the System Tree
Use this task to move systems from one group to another in the System Tree. You can move
systems from any page that displays a table of systems, including the results of a query.
Even if you have a perfectly organized System Tree that mirrors your network hierarchy, and
use automated tasks and tools to regularly synchronize your System Tree, you may need to
move systems manually between groups. For example, you may need to periodically move
systems from the Lost&Found group.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree | Systems, then browse to and select the systems.
McAfee ePolicy Orchestrator 4.0.2 Product Guide62
Page 63

Organizing Systems for Management
Moving systems manually within the System Tree
2 Click Move Systems. The Select New Group page appears.
NOTE: You may need to click More Actions to access this action.
3 Select whether to enable or disable System Tree sorting on the selected systems when
they are moved.
4 Select the group in which to place the systems, then click OK.
63McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 64

Distributing Agents to Manage Systems
Managing your network systems effectively is dependent on each system running an active,
up-to-date agent.
There are several methods to distribute the agent. The ones you use depend on:
• The realities of your environment.
• Whether you are upgrading agents or distributing them for the first time.
Are you distributing agents for the first time?
When deploying agents throughout your environment for the first time:
1 Review the information in this chapter to understand the agent, its policies and tasks, and
the methods to distribute it.
2 Configure agent policy settings for the System Tree groups to which you are distributing
agents.
3 Distribute agents with the chosen methods to the desired locations.
Contents
Agents and SuperAgents
Agent-server communication
Agent activity logs
Agent policy settings
Security Keys
Methods of agent distribution
Creating custom agent installation packages
Distributing agents
Forcing the agent to call in to the server
Upgrading existing agents
Removing the agent
Maintaining the agent
Agent command-line options
Agent installation command-line options
McAfee ePolicy Orchestrator 4.0.2 Product Guide64
Page 65

Distributing Agents to Manage Systems
Agents and SuperAgents
Agents and SuperAgents
The agent is the distributed component of ePolicy Orchestrator that must be installed on each
system in your network that you want to manage. A SuperAgent is an agent that is enabled to
broadcast wake-up calls by network broadcast segment. SuperAgents can also be used as a
repository from which to distribute products and updates.
The agent collects and sends information among the ePO server, update repositories, managed
systems, and products. Systems cannot be managed by ePolicy Orchestrator without an installed
agent.
Agent installation folder
The location of the agent installation folder differs on managed systems and the server by
default.
On the server system, the agent is installed in this location:
<SYSTEM_DRIVE>\PROGRAM FILES\MCAFEE\COMMON FRAMEWORK
On the managed system, if the agent was installed as part of another product installation or
pushed from the console to the system, it is installed by default in this location:
<SYSTEM_DRIVE>\PROGRAM FILES\MCAFEE\COMMON FRAMEWORK
On the managed system, if you are upgrading the agent from version 2.5.1, the new agent is
also installed after the existing agent is uninstalled, by default in this location:
<SYSTEM_DRIVE>\PROGRAM FILES\NETWORK ASSOCIATES\COMMON FRAMEWORK
CAUTION: Once the agent has been installed, you cannot change its installation directory without
first removing it.
Agent language packages
Agent installation packages, both default and custom, install in English. These are in the master
repository by default for clean installations.
Each agent language package includes only those files needed to display the user interface in
that language. Agent language packages can be replicated to distributed repositories.
After the initial agent-server communication, the agent retrieves the new package that
corresponds to the in-use locale and applies it. In this way, the agents retrieve only language
packages for the locales being used on each managed system.
NOTE: The interface continues to appear in the current language until the new language package
has been applied.
Multiple language packages can be stored on managed systems to allow users to switch
languages by changing the locale. If a locale is selected for which a language package is not
available locally, the interface appears in English.
Agent language packages are available for these languages:
• Italian• Brazilian Portuguese
• Chinese (Simplified) • Japanese
• Korean• Chinese (Traditional)
• English • Polish
• Spanish• Dutch
• French (Standard) • Swedish
• German (Standard)
65McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 66
Distributing Agents to Manage Systems
Agent-server communication
The agent installation package
The FRAMEPKG.EXE file is created when you install the server. It is a customized installation
package for agents that report to your server. The package contains the server name, its IP
address, ASCI port number, and other information that allows the agent to communicate with
the server.
By default, the agent installation package is installed in this location:
C:\PROGRAM FILES\MCAFEE\EPO\DB\SOFTWARE\CURRENT\ ePOAGENT3000\INSTALL\0409\FRAMEPKG.EXE
This is the installation package that the server uses to deploy agents.
The default agent installation package contains no embedded user credentials. When executed
on the system, the installation uses the account of the currently logged-on user.
Agent-server communication
During agent-server communication, the agent and server exchange information using SPIPE,
a proprietary network protocol used by ePolicy Orchestrator for secure network transmissions.
At each communication, the agent collects its current system properties, as well as any events,
and sends them to the server. The server sends any new or changed policies, tasks, and
repository list to the agent. The agent then enforces the new policies locally on the managed
system.
Agent-server communication can be initiated in three ways:
• Agent-to-server communication interval (ASCI)
• Agent-initiated communication after agent startup
• Agent wake-up calls
• Communication initiated manually from the managed system
Agent-to-server-communication interval
The agent-to-server-communication interval (ASCI) is set on the General tab of the McAfee
Agent policy pages. This setting determines how often the agent calls into the server for data
exchange and updated instructions. By default, the ASCI is set to 60 minutes; the agent checks
into the server once every hour.
When deciding whether to modify this policy setting, you must consider your organization’s
threat response requirements, available bandwidth, and the hardware hosting the server. Be
aware that ASCI communication can generate significant network traffic, especially in a large
network. In such a case, you probably have agents in remote sites connecting over slower
network connections. For these agents, you may want to set a less frequent ASCI. The following
table lists general ASCI recommendations for common network connection speeds.
General recommended ASCI settings
Recommended ASCINetwork Size
60 minutesGigabit LAN
60 minutes100mb LAN
360 minutesWAN
360 minutesDial-up or RAS
180 minutes10mb LAN
McAfee ePolicy Orchestrator 4.0.2 Product Guide66
Page 67

Distributing Agents to Manage Systems
Agent-server communication
Recommended ASCINetwork Size
150 minutesWireless LAN
NOTE: For complete information on balancing bandwidth, server hardware, and ASCI
determination, see the
ePolicy Orchestrator 4.0.2 Hardware Sizing and Bandwidth Usage Guide
Agent-initiated after agent startup
After the installation, and after the agent service is stopped and restarted, the agent calls into
the server at a randomized interval within ten minutes. Subsequent communications occur with
the ASCI set in the agent policy (60 minutes by default).
You can force the agent to communicate to the server immediately after the installation by
running the CMDAGENT.EXE with the /P command-line option.
Wake-up calls
Wake-up calls prompt the agents to call in to the server. Wake-up calls can be sent manually
or scheduled as a client task. These are useful when you have made policy changes or checked
in updates that you want to apply to the managed systems sooner than the next ASCI.
Wake-up calls can also configured on query results which are scheduled in the Server Task
Builder wizard.
.
SuperAgents and broadcast wake-up calls
If you plan to use agent wake-up calls to initiate agent-server communication, consider converting
an agent on each network broadcast segment into a SuperAgent. SuperAgents distribute the
bandwidth impact of the agent wake-up call, minimizing network traffic.
Instead of sending agent wake-up calls from the server to every agent, the server sends the
SuperAgent wake-up call to SuperAgents in the selected System Tree segment. When
SuperAgents receive this wake-up call they send broadcast wake-up calls to all the agents in
their network broadcast segments. This reduces network traffic. This is beneficial in large
67McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 68
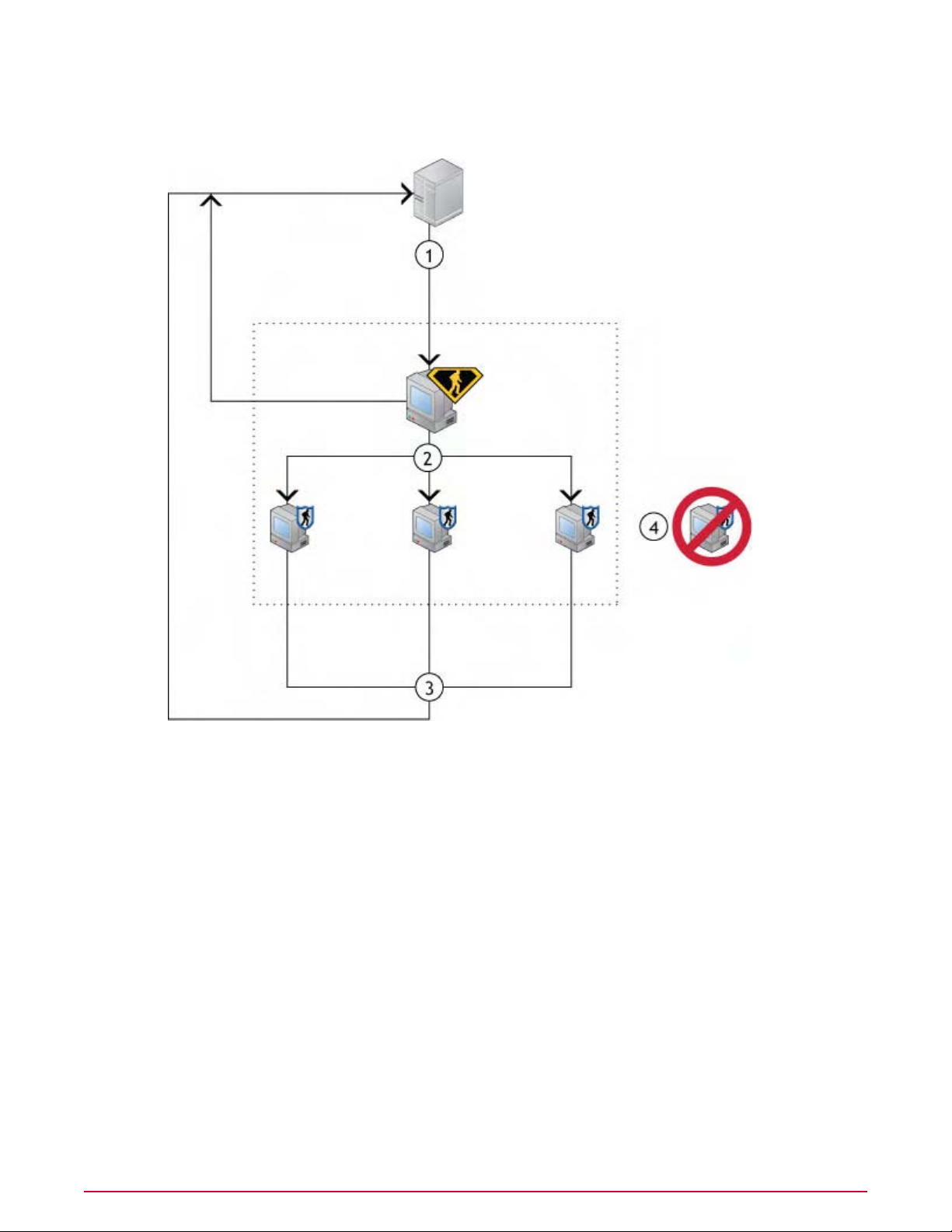
Distributing Agents to Manage Systems
Agent-server communication
networks where ePolicy Orchestrator may manage agents in remote sites over lower-speed
WAN or VPN connections.
Figure 15: SuperAgent and Broadcast Wake-Up Calls
1 Server sends a wake-up call to all SuperAgents.
2 SuperAgents send a broadcast wake-up call to all agents in the same broadcast segment.
3 All agents (regular agents and SuperAgents) exchange data with the server.
4 Any agents without an operating SuperAgent on its broadcast segment are not prompted
to communicate with the server.
Best practices
To deploy sufficient numbers of SuperAgents to the appropriate locations, first determine the
broadcast segments in your environment and select a system (preferably a server) in each to
host a SuperAgent. Be aware that agents in broadcast segments without SuperAgents do not
receive the broadcast wake-up call, and therefore, do not call in to the server.
Similar to the regular agent wake-up call, the SuperAgent wake-up call uses the SPIPE protocol.
Ensure the agent wake-up communication port (8081 by default) and the agent broadcast
communication port (8082 by default) are not blocked.
McAfee ePolicy Orchestrator 4.0.2 Product Guide68
Page 69

Distributing Agents to Manage Systems
Agent activity logs
Agent activity logs
The agent log files are useful for determining agent status or troubleshooting. Two log files
record agent activity, both are located in the agent installation folders on the managed system.
Agent activity log
The agent activity log is an XML file named agent_<system>.xml where <system> is the
NetBIOS name of the system on which the agent is installed. This log file records agent activity
related to thingssuch as policy enforcement, agent-server communication, and event forwarding.
You can define a size limit of this log file.
On the Logging tab of the McAfee Agent policy pages, you can configure the level of agent
activity that is recorded.
Detailed agent activity log
The detailed agent activity log is named agent_<system>.log file where <system> is the
NetBIOS name of the system on which the agent is installed. In addition to the information
stored in the agent activity log, the detailed activity log contains troubleshooting messages.
This file has a 1MB size limit. When this log file reaches 1MB, a backup copy is made
(agent_<system>_backup.log).
Agent policy settings
Agent policy settings determine agent performance and behavior in your environment, including:
• How often the agent calls in to the server.
• How often the agent enforces policies on the managed system.
• How often the agent delivers event files to the server.
• Where the agent goes for product and update packages.
Before distributing a large number of agents throughout your network, consider carefully how
you want the agent to behave in the segments of your environment. Although you can configure
agent policy after agents are distributed, McAfee recommends setting agent policy prior to the
distribution to prevent unnecessary resource impact.
For complete descriptions of options on the agent policy pages, click ? on the page displaying
the options. However, some of the most important policy settings are discussed here.
Priority event forwarding
The agent and security software on the managed system generate software events constantly
during normal operation. These can range from information events about regular operation,
such as when the agent enforces policies locally, to critical events, such as when a virus is
detected and not cleaned. These events are sent to the server at each agent-server
communication and stored in the database. A typical deployment of ePolicy Orchestrator in a
large network can generate thousands of these events an hour. Most likely, you won’t want to
see each of these.
Typically, you may want to know about higher severity events immediately. You can configure
the agent to forward events that are equal to or greater than a specified severity immediately
(specific event severities are determined by the product generating the events). If you plan to
69McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 70

Distributing Agents to Manage Systems
Agent policy settings
use Notifications, enabling immediate uploading of higher severity events is necessary for those
features to function as intended.
You can enable immediate uploading of events on the Events tab of the McAfee Agent policy
pages.
Full and minimal properties
The agent sends information from the managed system to the server at each agent-server
communication, allowing you to view the properties of individual systems from ePolicy
Orchestrator.
The agent sends the complete set of properties during the initial communication. After that,
the agent sends only properties that have changed since the last communication.
However, the agent sends the complete set again if:
• Policy is set to send full properties, and enforced on the managed systems.
• Properties versions on the agent and the ePO server differ by more than two.
The properties listed depend on whether you selected to send full or minimal properties on the
General tab of the McAfee Agent policy pages.
Full properties
If you specify to collect the full set of properties, the agent collects:
• System properties:
• System hardware information.
• Installed software information.
• Processor speed.
• Operating system.
• Time zone.
• Most recent date and time that properties were updated.
• Product properties:
• Installation path.
• Detection definition (DAT) file version number.
• Product version number.
• Specific policy settings configured for each product.
Minimal properties
If you specify to collect only minimal properties, the agent collects only these product properties:
• Installation path.
• Detection definition (DAT) file version number.
• Product version number.
• Specific policy settings configured for each product.
McAfee ePolicy Orchestrator 4.0.2 Product Guide70
Page 71

Distributing Agents to Manage Systems
Security Keys
Agent policy and distributed repositories
By default, the agent can update from any repository in its repository list (SITELIST.XML) file.
The agent can use a network ICMP ping command or the repository’s subnet address to
determine the distributed repository with the fastest response time out of the top five repositories
in the list. Usually, this is the distributed repository that is closest to the system on the network.
For example, a managed system in a remote site far from the ePO server probably selects a
local distributed repository. By contrast, an agent in the same LAN as the server probably
updates directly from the master repository.
If you require tighter control over which distributed repositories the agents use, you can enable
or disable specific distributed repositories on the Repositories tab of the McAfee Agent policy
pages. Allowing agents to update from any distributed repository ensures they get the update
from some location. Using a network ICMP ping, the agent should update from the closest
distributed repository from the top five in the repository list.The agent selects a repository each
time the agent service (McAfee Framework Service) starts or when the repository list
changes.
Proxy settings
To access the McAfee update sites, the agent must be able to access the Internet. Use the
agent policy settings to configure proxy server settings for the managed systems.The Proxy
tab of the McAfee Agent policy pages includes settings to:
• Use Internet Explorer proxy settings.
• Configure custom proxy settings.
• Disable any proxy use.
The default setting is Use Internet Explorer Proxy Settings, allowing an agent to use the
current proxy server location and credential information currently configured in the Internet
Explorer browser installed on that system.However, you may need to use ePolicy Orchestrator
to configure custom proxy server settings for systems in your network. For example, maybe
they use a different browser and don’t have Internet Explorer installed.
Security Keys
ePolicy Orchestrator and the agents use keys to secure agent-server communication and to
sign and validate unsigned packages.
Agents update changes to keys on the next Update client task for the agent.
Agent-server secure communication keys
Agent-server secure communication (ASSC) keys are used by the agents to communicate
securely with the server. You can make any ASSC key pair the master, which is the one currently
assigned to agents deployed. Exisiting agents using other keys in the list change to the new
master after the next update. Be sure to wait until all agents have updated to the new master
before deleting older keys.
Agents previous to version 3.6 use a legacy key. If you are upgrading from a previous version
of ePolicy Orchestrator, the legacy key may be the master key by default.
71McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 72

Distributing Agents to Manage Systems
Methods of agent distribution
Master repository key pair
The master repository private key signs all unsigned content in the master repository. These
keys are in anticipation of the McAfee Agent 4.0.
Agents version 4.0 or later use the public key to verify the repository content originating from
the master repository on this ePO server. If the content is unsigned, or signed with an unknown
repository private key, the downloaded content is considered invalid and deleted.
This key pair is unique to each server installation. However, by exporting and importing keys,
you can use the same key pair in a multi-server environment.
These keys are a new feature and only agents 4.0 or later are compliant with the new protocols.
Other repository public keys
These are the public keys that agents use to verify content from other master repositories in
your environment or McAfee source sites. Each agent reporting to this server uses the keys in
this list to verify content that originates from other ePO servers in your organization, or from
McAfee owned sources.
If an agent downloads content that originated from a source for which the agent does not have
the appropriate public key, the agent discards the content.
These keys are a new feature and only agents 4.0 or later are able to use the new protocols.
Methods of agent distribution
Due to the variety of scenarios and requirements of different environments, there are several
methods you can use to distribute the agent to the systems you want to manage. Before using
any of these methods, you should consider each.
The following table details the advantages and disadvantages of the different methods to
distribute the agent.
Table 1: Advantages and disadvantages of agent distribution methods
creating Directory
Deploying agents from
ePolicy Orchestrator
Using login scripts
Automatic; no other steps are required.Deploying agents while
This is an efficient method for distributing
the agent.
This is an efficient method for an
environment where systems log on to the
network frequently. You do the work
once, and the agent is deployed
automatically.
DisadvantagesAdvantagesMethod
If you are creating sites by importing large NT
domains or Active Directory containers, too
much network traffic may be generated for your
resources.
You must embed user credentials with
administrator rights to the desired systems.
Also, you must ensure that systems running
Microsoft XP Service Pack 2, have the
FRAMEPKG.EXE file added to the firewall
exceptions list.
Systems that don’t log on to the network
frequently, may not be running the most
up-to-date agent.
Installing manually
McAfee ePolicy Orchestrator 4.0.2 Product Guide72
This is an efficient method if you are not
using ePolicy Orchestrator to deploy the
agent, or if you have many Windows 95
and Windows 98 systems and do not want
to enable file and print sharing on them.
This is not a time-efficient method if you have
many systems.
Page 73

Distributing Agents to Manage Systems
Creating custom agent installation packages
DisadvantagesAdvantagesMethod
Including the agent on an
image
unmanaged McAfee
products the agent to the current release. You cannot
Prevents the bandwidth impact that other
forms of distribution can cause. Reduces
the overhead by integrating the task into
another.
Saves significant bandwidth and time.Enabling the agent on
If you do not use images consistently, this
method would not be efficient to ensure
coverage.
The disabled agent may be out-of-date and
require you run the deployment task to upgrade
change the agent installation folder without
removing and reinstalling the agent. Agents
that you enable may be located in a different
folder than agents that you deploy in your
network by some other method.
Creating custom agent installation packages
Use this task to create a custom agent installation package.
If you use a distribution method other than ePolicy Orchestrator deployment capabilities (such
as login scripts or third-party deployment software), you must create a custom agent installation
package (FRAMEPKG.EXE) with embedded administrator credentials if users do not have local
administrator permissions. The user account credentials you embed are used to install the
agent.
NOTE: For Microsoft Windows XP Service Pack 2 and later operating systems do not allow
embedded administrator credentials until the package file name has been added to the exception
list of the Windows firewall.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree, then click New Systems. The New Systems page
appears.
2 Next to How to add systems, select Create and download agent installation
package.
3 Type the desired Credentials for agent installation, then click OK.
4 When prompted, select the location for downloading and saving the installation package.
5 Distribute the custom installation package file as needed.
Distributing agents
Use any of these tasks to distribute agents across your environment. The methods you choose
depend on the requirements in your environment.
Tasks
Deploying the agent with ePolicy Orchestrator
Installing the agent with login scripts
Installing the agent manually
Enabling the agent on unmanaged McAfee products
73McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 74

Distributing Agents to Manage Systems
Distributing agents
Including the agent on an image
Using other deployment products
Distributing the agent to WebShield appliances and Novell NetWare servers
Deploying the agent with ePolicy Orchestrator
Use this task to deploy agents to your systems with ePolicy Orchestrator. This method uses
Windows NT push technology.
This method is recommended if large segments of your System Tree are already populated.
For example, if you created System Tree segments by importing domains or Active Directory
containers and you chose not to deploy during the import.
Before you begin
To use this method, several requirements must be met, including:
• Systems must already be added to the System Tree.
NOTE: If you have not yet created the System Tree, you can deploy the agent installation
package to systems at the same time that you are adding groups, and systems to the System
Tree. However, McAfee does not recommend this procedure if you are creating your System
Tree by importing large NT domains or Active Directory containers. This can generate too
much network traffic.
• Specify domain administrator credentials. Domain administrator rights are required on a
system to access the default Admin$ shared folder. The ePO server service requires access
to this shared folder in order to install agents and other software.
• Verify the ePO server can communicate with the desired systems.
Before beginning a large agent deployment, use ping commands to verify that the server
can communicate with a few systems in each segment of your network.
If the targeted systems respond to the ping, then ePolicy Orchestrator can reach the
segments.
NOTE: The ability to successfully use ping commands from the ePO server to the managed
systems is not required for the agent to communicate with the server after the agent is
installed. This is only a useful test for determining if you can deploy agents from the server.
• Verify that the Admin$ share folders on the desired systems are accessible from the server.
This test also validates your administrator credentials, because you cannot access remote
Admin$ shares without administrator rights.
To access Admin$ shares on desired systems from the ePO server, select Start | Run, then
type the path to the client Admin$ share by specifying either the system name or IP address.
If the systems are properly connected over the network, your credentials have sufficient
rights, and if the Admin$ shared folder is present, you should see a Windows Explorer
dialog box.
• Ensure file and print sharing is enabled. This is disabled by default on Windows 95, Windows
98, and Windows ME systems. In addition, if you have systems in your network running
these operating systems, make sure they can be managed by ePolicy Orchestrator. By
default, these systems do not allow ePO administration. To enable these systems for ePO
administration, download VCREDIST.EXE and DCOM 1.3 updates from the Microsoft web
site and install them on each client as required.
McAfee ePolicy Orchestrator 4.0.2 Product Guide74
Page 75

Distributing Agents to Manage Systems
Distributing agents
• Ensure network access is enabled on Windows XP Home systems. Deploy the agent from
ePolicy Orchestrator or install a custom agent installation package on systems running
Windows XP Home, you must enable network access.
To enable network access on systems running Windows XP Home, go to Start | Control
Panel | Performance and Maintenance | Administrative Tools | Local Security
Policy | Security Settings | Local Policies | Security Options | Network access:
Sharing and security model for local accounts, then select Classic - local users
authenticate as themselves.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree, then select the groups or system to which you want to
deploy the agent.
2 Click Deploy Agents. The Deploy McAfee Agent page appears.
Figure 16: Deploy McAfee Agent page
3 Select the desired Agent version from the drop-down list.
4 If you are deploying agents to a group, select whether to include systems from its
subgroups.
5 Select whether to:
• Install only on systems that do not already have an agent managed by this
ePO server
• Suppress the agent installation user interface
• Force installation over existing version
This option is not available if Install only on systems that do not already have
an agent managed by this ePO server is selected.
NOTE: Force installation may be necessary if you experience issues with a new agent and
need to re-install the earlier version. This option is recommended for downgrading agents
only.
6 Accept the default Installation path or select from the drop-down list.
7 Specify Credentials for agent installation that have rights to the systems.
8 Click OK to send the agent installation package to the selected systems.
75McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 76

Distributing Agents to Manage Systems
Distributing agents
Installing the agent with login scripts
Use this task to set up and use network login scripts to install the agent on systems logging on
to the network.
Using network login scripts is a reliable method to make sure that every system logging on to
your network is running an agent. You can create a login script to call a batch file that checks
if the agent is installed on systems attempting to log onto the network. If no agent is present,
the batch file can install the agent before allowing the system to log on. Within ten minutes of
being installed, the agent calls in to the server for updated policies, and the system is added
to the System Tree.
This is a desirable method to use when:
• Sorting filters or NT domain names are assigned to the segments of your System Tree.
• You already have a managed environment and want to ensure that new systems logging
on to the network become managed as a result.
• You already have a managed environment and want to ensure systems are running a current
version of the agent.
Best practices
McAfee recommends you first create segments of your System Tree that use either network
domain names or sorting filters that add the expected systems to the desired groups. If you
don’t, all systems are added to the Lost&Found group and you must move them later manually.
The details of the login script depends on your needs. Consult your operating system
documentation for writing login scripts. This task uses a basic example.
Task
For option definitions, click ? on the page displaying the options.
1 Copy the FRAMEPKG.EXE agent installation package on your server to a shared folder on
a network server to which all systems have permissions.
Systems logging on to the network are directed to this folder to run the agent installation
package and install the agent when they log on.
By default, the agent installation package is in this location:
C:\PROGRAM FILES\MCAFEE\EPO\DB\SOFTWARE\CURRENT\ ePOAGENT3000\INSTALL\0409\FRAMEPKG.EXE
2 Create a custom agent installation package with embedded administrator user credentials.
These credentials are required to install the agent on the system.
3 Create a batch file that contains the lines you want to execute on systems when they log
onto the network. The contents of this batch file may differ depending on your needs, but
its purpose is to:
• Check whether the agent has been installed in the expected location.
• Run FRAMEPKG.EXE if it is not present.
McAfee ePolicy Orchestrator 4.0.2 Product Guide76
Page 77

Distributing Agents to Manage Systems
Distributing agents
Below is a sample batch file that checks whether the agent is installed and, if it is not, runs
the FRAMEPKG.EXE to install the agent.
IF EXIST “C:\Windows\System32\ePOAgent\NAIMAS32.EXE”
\\<COMPUTER>\<FOLDER>\UPDATE$\FRAMEPKG.EXE /FORCEINSTALL /INSTALL=AGENT
IF EXIST “C:\ePOAgent\FRAMEWORKSERVICE.EXE” GOTO END_BATCH
\\MyServer\Agent\UPDATE$\FRAMEPKG.EXE /FORCEINSTALL /INSTALL=AGENT
:END_BATCH
NOTE: The installation folders for your distribution may be different than in this example,
depending on where you have specified to install the agent.
This example checks:
• The default installation location of the older agent version 2.5.1 and, if present, upgrades
it to the agent version 3.5.
• The default installation folder for the agent version 3.5 and, if not present, installs the
new agent.
4 Save the EPO.BAT batch file to the NETLOGON$ folder of your primary domain controller
(PDC) server. The batch file runs from the PDC every time a system logs on to the network.
5 Add a line to your login script that calls the batch file on your PDC server. This line would
look similar to this example:
CALL \\PDC\NETLOGON$\EPO.BAT
Each system runs the script and installs the agent when it logs on to the network.
Installing the agent manually
Use this task to run the installer locally on a system.
This is a desirable method to install agents for the following circumstances:
• Your organization requires that software is installed on systems manually.
• You intend to use ePolicy Orchestrator for policy management only.
• You have systems running Windows 95, Windows 98, or Windows ME and do not want to
enable file and print sharing on them.
• You assigned sorting filters or NT domain names when creating the segments of your System
Tree.
You can install the agent on the system, or distribute the FRAMEPKG.EXE installer for users to
run the installation program themselves.
After the agent is installed, it calls into the server and adds the new system to the System Tree.
Task
For option definitions, click ? on the page displaying the options.
1 Distribute the agent installation package to the desired system.
If you want end-users (who have local administrator rights) to install the agent on their
own systems, distribute the agent installation package file to them. You can attach it to an
email message, copy it to media, or save it to a shared network folder.
2 Double-click FRAMEPKG.EXE and wait a few moments while the agent is installed. Within
ten minutes, the agent calls in to the ePO server for the first time.
3 As needed, bypass the ten-minute interval by forcing the agent to call in with the
CMDAGENT/p command line.
77McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 78

Distributing Agents to Manage Systems
Distributing agents
Enabling the agent on unmanaged McAfee products
Use this task to enable agents on existing McAfee products in your environment.
Before purchasing ePolicy Orchestrator, you may have already been using McAfee Enterprise
products in your network. Some of the more recent McAfee products that use the AutoUpdate
updater, such as VirusScan Enterprise, install with the agent in a disabled state. To start
managing these products with ePolicy Orchestrator, you can enable the agent that is already
on the system.
Enabling the agent on each system instead of deploying the 3.63MB agent installation package
saves significant network bandwidth.
NOTE: You cannot change the agent installation folder without removing and reinstalling the
agent. Agents that you enable may be in a different folder than agents that you deploy in your
network by another method.
Assigning sorting filters or NT domain names to the desired System Tree segments saves
valuable time.
You must copy the SITELIST.XML repository list file from the ePO server to the desired systems.
The repository list contains network address information the agent requires to call in to the
server after being installed.
Task
For option definitions, click ? on the page displaying the options.
1 Export the repository list (SITELIST.XML) from the Master Repository page to a temporary
folder on the system, such as C:\TEMP.
2 Run this command on the desired system:
FRMINST.EXE /INSTALL=AGENT /SITEINFO=C:\TEMP\SITELIST.XML
/SITEINFO is the location of the SITELIST.XML file that you exported.
Reference the SITELIST.XML file in the temporary folder. By default, the FRMINST.EXE file
is installed in this location:
C:\PROGRAM FILES\MCAFEE\COMMON FRAMEWORK
NOTE: Existing McAfee products were most likely installed with an older version of the
agent. These agents are
ePO server. Enable and run a deployment task configured to upgrade the enabled agent
on the managed system.
not
automatically upgraded to the latest version that is on the
Including the agent on an image
Use this information to install the agent using an image. The first time the user logs on to a
system built using a common image that includes the agent, the system is assigned a unique
ID called a
global unique identifier
(GUID).
CAUTION: Before creating an image for this purpose, remove the agent GUID registry value
from the agent registry key. A GUID is regenerated on the first ASCI with the ePO server.
This is a desirable method to use when:
• Your organization uses standard installation images for new systems.
• You have access to some systems in your environment only when they are brought in for
repair.
McAfee ePolicy Orchestrator 4.0.2 Product Guide78
Page 79

Distributing Agents to Manage Systems
Forcing the agent to call in to the server
For instructions, see the documentation for your preferred image-creation product.
Using other deployment products
You may already use other network deployment products to deploy software. You can use many
of these tools, such as Microsoft Systems Management Server (SMS), IBM Tivoli, or Novell
ZENworks, to deploy agents. Configure your deployment tool of choice to distribute the
FRAMEPKG.EXE agent installation package located on your ePO server.
For instructions, see the documentation of the desired deployment tool.
Distributing the agent to WebShield appliances and Novell NetWare servers
You cannot use ePolicy Orchestrator to deploy agents to WebShield®appliances or Novell
NetWare servers. Instead, use a login script or manual installation.
These systems require different agents, which can be downloaded from the McAfee web site.
These agent installation packages are not installed on the ePO server by default.
See your product documentation for details.
Forcing the agent to call in to the server
Use this task to force the new agent to call into the ePO server immediately. You can do this
from any system on which an agent has just been installed. This is useful after installing the
agent manually.
Task
For option definitions, click ? on the page displaying the options.
1 From the system where you just installed the agent, open a DOS command window by
selecting Start | Run, type command, and press Enter.
2 In the command window, navigate to the agent installation folder containing the
CMDAGENT.EXE file.
3 Type this command.
CMDAGENT /p
4 Press Enter. The agent calls into the server immediately.
When the agent calls in to the server for the first time, the system is added to the System Tree
as a managed system. If you configured criteria-based sorting for the System Tree, the system
is added to the location appropriate for its IP address or tags. Otherwise, the system is added
to the Lost&Found group. Once the system is added to the System Tree, you can manage its
policies through ePollicy Orchestrator.
Upgrading existing agents
Use these tasks to upgrade existing agents in your environment.
79McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 80

Distributing Agents to Manage Systems
Upgrading existing agents
If you have been using an older version of ePolicy Orchestrator and have previous agent versions
in your environment, you can upgrade those agents once you’ve installed your ePO server. The
procedure for upgrading the agent depends on which previous agent version is running on your
managed systems.
NOTE: Some previous agent versions are not fully functional in ePolicy Orchestrator 4.0.2. For
full agent functionality, upgrade to agent version 3.6 Patch 1 or later.
Tasks
Upgrading agents using login scripts or manual installation
Upgrading agents with ePolicy Orchestrator
Upgrading agents using login scripts or manual installation
If you don’t use ePolicy Orchestrator to deploy agents or products to managed systems, you
can use your preferred agent distribution method to upgrade existing agents. Upgrading agents
without using ePolicy Orchestrator, such as upgrading manually or using network login scripts,
is the same as installing agents for the first time. You must distribute the FRAMEPKG.EXE
installation file and launch it on the system using your preferred method.
Upgrading agents with ePolicy Orchestrator
Use this task to upgrade existing agents with the Product Deployment client task. This method
provides more control over where and when the upgrade occurs. This is the same deployment
task that can be used to deploy products such as VirusScan Enterprise to systems that are
already running agents.
Best practices information
You can use the deployment task to upgrade agents. McAfee releases newer versions of the
agent periodically. You can deploy and manage these newer versions of the agent with ePolicy
Orchestrator. When available, you can download the agent installation package from the McAfee
update site and check it into the master repository. Then use the deployment task to upgrade
the agents.
CAUTION: Upgrading the agent using the deployment task is not the same as updating an
existing agent using the Update client task. Upgrading the agent is for installing a new version
of the agent over an older one, such as installing the agent version 3.6 over the version 3.0.
The update task is used to update an existing version of the agent with additional updates,
such as DAT files and patches, or updating the agent version 3.0.1 to version 3.0.2.
Task
For option definitions, click ? on the page containing the options.
1 Ensure that the desired agent installation package is checked into the master software
repository.
2 Go to Systems | System Tree | Client Tasks, then select a portion of the System Tree
for which you want to upgrade the agent.
3 Click New Task. The Description page of the Client Task Builder wizard appears.
4 Name the task, select Product Deployment (McAfee Agent) from the drop-down lists,
then click Next. The Configuration page appears.
McAfee ePolicy Orchestrator 4.0.2 Product Guide80
Page 81

Distributing Agents to Manage Systems
Removing the agent
5 Select the agent version from the drop-down list.
6 Select Install from the Action drop-down list.
7 Add any command-line options.
8 Select whether to run the task at each policy enforcement interval.
9 Select whether to run an update task after successful deployments, then click Next.
10 Schedule the task as needed, then click Next. The Summary page appears.
11 Verify the task’s details, then click Save.
The task is added to the list of client tasks everywhere it’s assigned in the System Tree.
Removing the agent
Use these tasks to remove agents from systems.
NOTE: You cannot remove the agent using the Product Deployment task, which is used to
remove products such as VirusScan Enterprise.
Tasks
Running FRMINST.EXE from a command line
Removing agents when deleting systems from the System Tree
Removing agents when deleting groups from the System Tree
Removing agents from systems in query results
Running FRMINST.EXE from a command line
Use this task to remove the agent from a command line.
Task
• Run the agent installation (FRMINST.EXE) program with the /REMOVE=AGENT command-line
option. By default this file is located at:
C:\PROGRAM FILES\MCAFEE\COMMON FRAMEWORK
Removing agents when deleting systems from the System Tree
Use this task to remove agents from systems that you are deleting from the System Tree.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree | Systems, then select the group under System Tree
that contains the systems you want to delete.
2 Select the systems from the list, then click Delete at the bottom of the page (you may
need to first click More Actions).
3 In the Action panel, select Remove agent, then click OK.
The selected systems are deleted from the System Tree and their agents are removed at their
next agent-server communication.
81McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 82

Distributing Agents to Manage Systems
Maintaining the agent
Removing agents when deleting groups from the System Tree
Use this task to remove agents from all systems in a group, which you are deleting from the
System Tree.
CAUTION: When you delete a group, all child groups and systems are also deleted. If you select
the Remove agents from all systems checkbox when deleting systems, ePolicy Orchestrator
removes the agents from all child systems.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree | Groups, then select the desired group under System
Tree.
2 Click Delete Group at the bottom of the page (you may need to first click More Actions).
The Delete Group dialog box appears.
3 Select Remove agent from all systems, then click OK.
The selected systems are deleted from the System Tree and their agents are removed at their
next agent-server communication.
Removing agents from systems in query results
Use this task to remove agents from systems listed in the results of queries (for example, the
Agent Versions Summary query).
Task
For option definitions, click ? on the page displaying the options.
1 Run the desired query.
2 Select systems from the query results, then click Delete at the bottom of the page.
3 In the Action panel, click Yes when prompted whether to remove the agent.
The agent is uninstalled after the next agent-server communication.
Maintaining the agent
Use these tasks to ensure agents in your environment are up-to-date and functioning as
expected. You may need to perform these tasks on a regular basis.
Tasks
Sending manual wake-up calls to systems
Sending manual wake-up calls to a group
Sending wake-up calls on a schedule
Viewing the agent activity log
Viewing of the agent and product properties
Running agent tasks from the managed system
Working with security keys
McAfee ePolicy Orchestrator 4.0.2 Product Guide82
Page 83
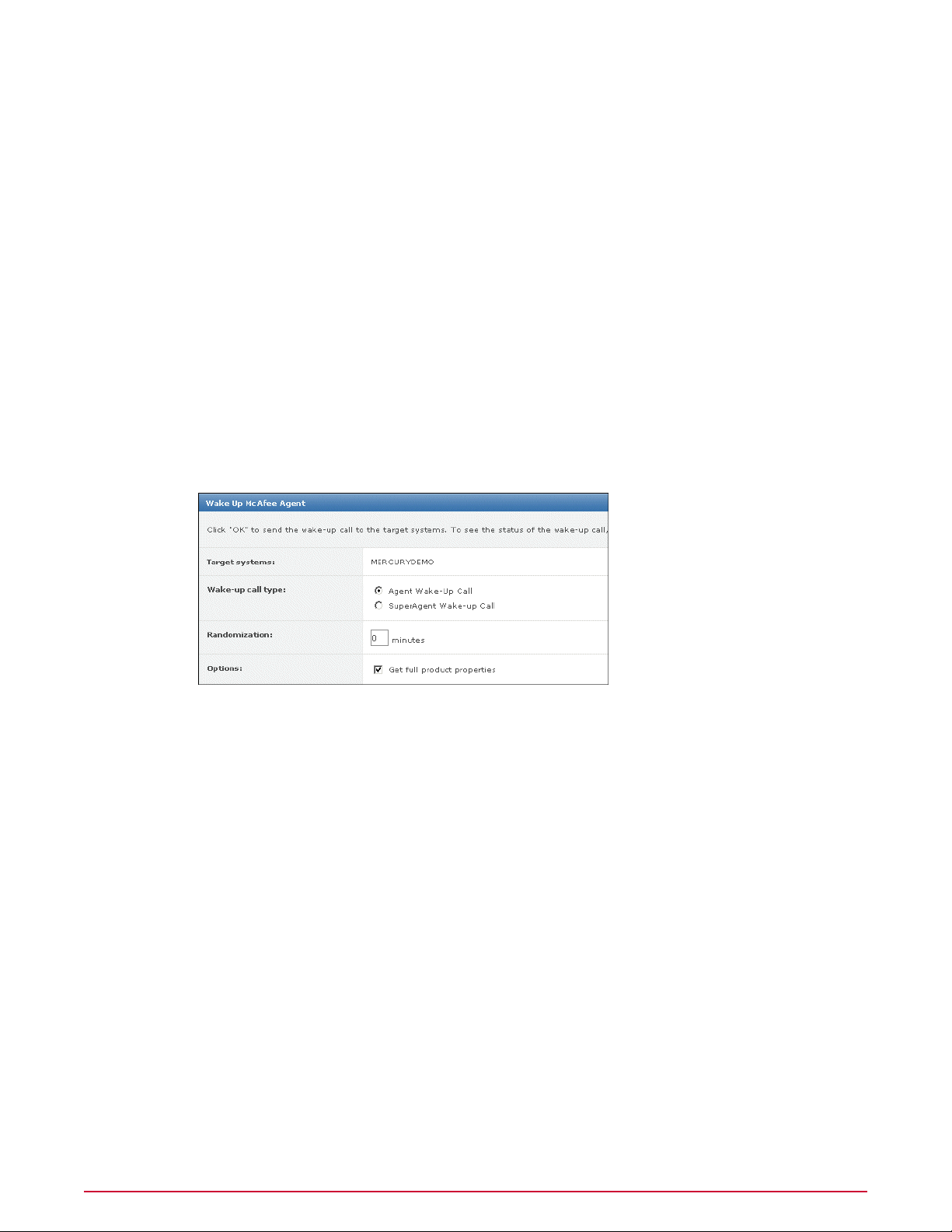
Distributing Agents to Manage Systems
Maintaining the agent
Sending manual wake-up calls to systems
Use this task to manually send an agent or SuperAgent wake-up call to systems in the System
Tree. This is useful when you make policy changes and you want agents to call in for an update.
Before you begin
Before sending the agent wake-up call to systems, make sure that wake-up support for the
systems’ groups is enabled and applied on the General tab of the McAfee Agent policy pages
(enabled by default).
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree | Systems, then select the group that contains the
systems.
2 Select the systems from the list, then click Wake Up Agents. The Wake Up McAfee
Agent page appears.
NOTE: You may need to click More Actions to expose this action.
Figure 17: Wake Up McAfee Agent page
3 Verify the systems appear next to Target systems.
4 Select whether to send an Agent Wake-Up Call or SuperAgent Wake-Up call next to
Wake-up call type.
5 Accept the default or type a different Randomization (0 - 60 minutes). Consider carefully
the number of systems that are receiving the wake-up call with how much bandwidth is
available. If you type 0, agents respond immediately.
6 During regular communication, the agent sends only properties that have changed since
the last agent-server communication. This task is set by default to Get full product
properties. To send the complete properties as a result of this wake-up call, ensure this
is option selected.
7 Click OK to send the agent or SuperAgent wake-up call.
Sending manual wake-up calls to a group
Use this task to manually send an agent or SuperAgent wake-up call to a System Tree group.
This is useful when you have made policy changes and you want agents to call in for an update.
83McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 84

Distributing Agents to Manage Systems
Maintaining the agent
Before you begin
Before sending the agent wake-up call to such a group, make sure that wake-up support for
the group is enabled and applied on the General tab of the McAfee Agent policy pages
(enabled by default).
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree | Groups, then select the group under System Tree.
2 Click Wake Up Agents. The Wake Up McAfeeAgent page appears.
NOTE: You may need to click More Actions to expose this action.
3 Verify the group appears next to Target group.
4 Select whether to send the agent wake-up call to All systems in this group or to All
systems in this group and subgroups.
5 Select whether to send an Agent wake-up call or SuperAgent wake-up call next to
Type.
6 Accept the default or type a different Randomization (0 - 60 minutes). If you type 0,
agents respond immediately.
7 During regular communication, the agent sends only properties that have changed since
the last agent-server communication. This task is set by default to Get full product
properties. To send the complete properties as a result of this wake-up call, ensure this
is option selected.
8 Click OK to send the agent or SuperAgent wake-up call.
Sending wake-up calls on a schedule
Use this task to create a scheduled agent wake-up call.
NOTE: SuperAgent wake-up calls cannot be scheduled.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree | Client Tasks, then select the group or systems to send
the wake-up call.
2 Click New Task. The Description page of the Client Task Builder wizard appears.
3 Name the task, select and Agent Wake-up Call (McAfee Agent) from the drop-down
list, then click Next. The Configuration page appears.
4 Select whether the agents that receive the wake-up call send full or minimal properties,
then click Next.
5 Schedule the task as needed, then click Next. The Summary page appears.
6 Verify the task’s details, then click Save.
When complete, the scheduled task appears in the list of available tasks on the Client Tasks
tab of the selected System Tree group. If the task is enabled, it runs at the next scheduled time
on systems that have received the task. To ensure all desired systems have the task information,
send a manual wake-up call to them.
McAfee ePolicy Orchestrator 4.0.2 Product Guide84
Page 85

Distributing Agents to Manage Systems
Maintaining the agent
Viewing the agent activity log
Use these tasks to view the agent activity log. The agent activity log records an agent’s activity.
The amount of detail depends on the policy settings you selected on the Logging tab of the
McAfee Agent policy pages.
These log files can be viewed from the managed system or from the console.
Tasks
Viewing the agent activity log from the managed system
Viewing the agent activity log from the ePO server
Viewing the agent activity log from the managed system
Use this task to view the agent activity log from the system on which the agent is installed.
Task
For option definitions, click ? on the page that displays the options.
1 Right-click the agent icon in the system tray.
NOTE: The agent icon is available in the system tray only if the Show McAfee system
tray icon (Windows only) option is selected on the General tab of the McAfee Agent
policy pages. If it is not visible, select this option and apply it. When you finish viewing the
log file content, you can hide the icon again by deselecting the option and applying the
change.
2 Select Status Monitor from the menu. The status monitor appears, the agent activity log
is displayed.
3 Close the status monitor when finished.
Viewing the agent activity log from the ePO server
Use this task to view agent activity log of a system from the server.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree | Systems, then select the system.
2 Click View Agent Log.
3 To view the backup copy of the FrameSvc.exe or NaPrdMgr.exe detailed log, click previous.
NOTE: Although remote viewing of log files is enabled by default, you can disable remote
viewing of the log files. If you can’t view the log remotely, verify that the Enable remote
access to log option is selected on the Logging tab of the McAfee Agent policy pages.
Viewing of the agent and product properties
Use this task to verify that the properties match the policy changes you have made. This is
useful for troubleshooting. The properties available depend on whether you configured the
agent to send full or minimal properties on the McAfee Agent policy pages.
85McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 86

Distributing Agents to Manage Systems
Maintaining the agent
Task
For option definitions, click ? on the page displaying the options.
1 Go to Systems | System Tree | Systems, then select the system.
2 Click the system in the list. Properties for the system, installed products, and the agent
appear.
Running agent tasks from the managed system
Use these tasks to perform selected tasks from the system where the agent is installed.
If you can access the managed system where the agent is installed, you can view and manage
some features of the agent.
NOTE: The agent interface is available on the managed system only if you selected Show
McAfee system tray icon on the General tab of the McAfee Agent policy pages.
Tasks
Running an update manually
Sending full properties to the ePO server
Sending events to the ePO server immediately
Updating policies
Enforcing policies
Viewing agent settings
Viewing agent and product version numbers
Running an update manually
Use this task to run an update from the managed system.
Task
1 Right-click the McAfee tray icon.
2 Select McAfee Agent | Update Now. The agent performs an update from repository
determined in the agent policy.
Product updates include:
• Patch releases.
• Legacy product plug-in (.DLL) files.
• Service pack releases.
• SuperDAT (SDAT*.EXE) packages.
• Supplemental detection definition (EXTRA.DAT) files.
• Detection definition (DAT) files.
Sending full properties to the ePO server
Use this task to send full properties to the server from the managed system.
McAfee ePolicy Orchestrator 4.0.2 Product Guide86
Page 87

Distributing Agents to Manage Systems
Maintaining the agent
Task
1 Right-click the McAfee tray icon at the managed system, then select McAfee Agent |
Status Monitor. The Agent Status Monitor appears.
2 Click Collect and Send Props.
Sending events to the ePO server immediately
Use this task to send events to the server immediately from the managed system.
Task
1 Right-click the McAfee tray icon at the managed system, then select McAfee Agent |
Status Monitor. The Agent Status Monitor appears.
2 Click Send Events.
Updating policies
Use this task to prompt the agent from the managed system to call in to the server to update
policy settings.
Task
1 Right-click the McAfee tray icon on the desired system, then select McAfee Agent |
Status Monitor. The Agent Status Monitor appears.
2 Click Check New Policies.
Enforcing policies
Use this task to prompt an agent to enforce all configured policies on the managed system.
Task
1 Right-click the McAfee tray icon on the desired system, and select McAfee Agent | Status
Monitor. The Agent Status Monitor appears.
2 Click Enforce Policies.
Viewing agent settings
Use this task to view the agent settings from the managed system.
Task
1 Right-click the McAfee tray icon at the managed system.
2 Select McAfee Agent | Settings.
Agent settings include:
• Agent ID (GUID).
• System name.
• User name of the logged-on user.
• Policy enforcement interval.
• ASCI.
87McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 88

Distributing Agents to Manage Systems
Maintaining the agent
Viewing agent and product version numbers
Use this procedure to look up the agent and product version numbers from the managed system.
This is useful for troubleshooting when installing new agent versions or confirming that the
installed agent is the same version as the one displayed in the agent properties on the server.
Task
1 Right-click the McAfee tray icon.
2 Select McAfee Agent | About.
Working with security keys
Use these tasks to work with and manage security keys.
Tasks
Using ASSC keys in multi-server environments
Generating and using new ASSC keys
Exporting ASSC keys to allow agents to access multiple ePO servers
Viewing systems that use an ASSC key pair
Making an ASSC key pair the master
Deleting ASSC keys
Using master repository keys in multi-server environments
Backing up and restoring security keys
Using ASSC keys in multi-server environments
Use either of these tasks to ensure that all agents can communicate with any required server
in the environment.
Previous versions of ePolicy Orchestrator allowed agents to easily roam among multiple ePO
servers within an organization. Importing ASSC keys into other ePO servers allows agents
version 3.6 or later that are managed by source ePO server to successfully communicate with
these other ePO servers.
Two strategies ensure agents can communicate with multiple servers. Use a common master
ASSC key pair for all ePO servers, or use a different master ASSC key pair for each ePO server
and make each server aware of the other servers’ keys.
Tasks
Using the same ASSC key pair for all servers and agents
Using a different ASSC key pair per ePO server
Using the same ASSC key pair for all servers and agents
Use this task to ensure that all ePO servers and agents use the same ASSC key pair.
Task
For option definitions, click ? on the page displaying the options.
McAfee ePolicy Orchestrator 4.0.2 Product Guide88
Page 89

Distributing Agents to Manage Systems
Maintaining the agent
1 Export the desired ASSC keys from the desired ePO server.
2 Import the ASSC keys to all other servers.
3 Make the imported key the master on all servers.
4 Run an agent update task so that all agents begin using the keys immediately.
5 When all agents are using the new keys, delete any unused keys.
6 Back up all keys.
Using a different ASSC key pair per ePO server
Use this task to ensure all agents can communicate with any required server in an environment
where each ePO server is required to have a unique ASSC key pair.
You can ensure that agents can communicate with multiple servers by importing the necessary
key pairs into all servers with which the agents may communicate.
Task
For option definitions, click ? on the page displaying the options.
1 Export the master ASSC key pair from each ePO server in your environment.
2 Import each of these key pairs into every server.
Generating and using new ASSC keys
Use this task to generate new agent-server secure communication (ASSC) keys. Do this if you
discover a key has been compromised. McAfee recommends creating and using new ASSC keys
routinely, for example every three months.
Task
For option definitions, click ? on the page displaying them.
1 Go to Configuration | Server Settings, then select Security Keys in the Setting
Categories list.
2 Click Edit in the details pane. The Edit Security Keys page appears.
3 Click New Key next to the Agent-server secure communication keys list
4 When you want agents to use the new key, select the key in the list, then click Make
Master.
Agents version 3.6 or later begin using the new key at the first agent-server communication
after their next update task completes.
5 Delete the old key only after all agents have stopped using it.
To the right of every key in the list is the number of agents currently using it.
6 Back up all keys.
Exporting ASSC keys to allow agents to access multiple ePO servers
Use this task to export ASSC keys for use by other ePO servers in your environment.
Task
For option definitions, click ? on the page displaying the options.
89McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 90

Distributing Agents to Manage Systems
Maintaining the agent
1 Go to Configuration | Server Settings, then select Security Keys in the Setting
Categories list.
2 In the details pane, click Edit.
3 In the Agent-server secure communication keys list, select the desired key, then click
Export. The Export Agent-Server Communication Keys dialog box appears.
4 Click OK. The File Download dialog box appears.
5 Click Save, then browse to a location to save the ZIP file.
6 Change the name of the file as needed, then click Save.
Viewing systems that use an ASSC key pair
Use this task to view the systems whose agents use a specific ASSC key pair in the Agent-server
secure communication keys list. You may want to view the systems still using the previous
key pair after making a different key pair the master. Do not delete a key pair until you know
that no agents are still using it.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Server Settings, select Security Keys from the Setting
Categories list, then click Edit.
2 In the Agent-server secure communication keys list, select the desired key, then click
View Agents.
The Systems Using ASSC Key Pair page appears. This page displays a standard table listing
all of the systems whose agents are using the selected keys. Click any system in the list to view
its details, or select the checkboxes next to desired systems and take any of the actions available
below the table.
Making an ASSC key pair the master
Use this task to make another key pair listed in the Agent-server secure communication
keys list the master. Do this after importing or generating a new key pair.
Make the Legacy key pair the master only if you don’t have any agents 3.6 or later in your
environment. Later versions cannot use the legacy key pair.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Server Settings, select Security Keys from the Setting
Categories list, then click Edit.
2 Select the desired key from the Agent-server secure communication keys list, then
click Make Master.
3 As needed, create an update task for the agents to run immediately, so that agents update
after the next agent-server communication.
NOTE: Before deleting the previous master key pair from the list, wait until all agents begin
using the new master key pair. Agents begin using the new key pair after the next update
task for the agent completes. At any time, you can see which agents are using any of the
ASSC key pairs in the list.
McAfee ePolicy Orchestrator 4.0.2 Product Guide90
Page 91

Distributing Agents to Manage Systems
Maintaining the agent
4 Back up all keys.
Deleting ASSC keys
Use this task to delete unused ASSC keys in the Agent-server secure communication keys
list.
CAUTION: Do not delete any keys that are currently in use by any agents, or those agents are
not able to communicate with the server.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Server Settings, select Security Keys from the Setting
Categories list, then click Edit.
2 Select the desired key in the Agent-server secure communication keys list, then click
Delete. The Delete Key dialog box appears.
3 Click OK to delete the key pair from this server.
Using master repository keys in multi-server environments
Use these tasks to ensure agents version 3.6 or later can use content originating from any ePO
server in your environment.
The server signs all unsigned content that is checked in to the repository with the master
repository private key. Agents use the master repository public key to validate content retrieved
from repositories in your organization or McAfee source sites.
The master repository key pair is unique for each installation. If you use multiple servers, each
uses a different key. If your agents may download content that originates from different master
repositories, you must ensure that agents (version 4.0 or later) recognize the content as valid.
You can ensure this in two ways:
• Use the same master repository key pair for all servers and agents.
• Ensure agents are configured to recognize any repository public key used in your environment.
Tasks
Using one master repository key pair for all servers
Ensuring agents can use content from other ePO servers
Using one master repository key pair for all servers
Use this task to ensure all ePO servers and agents use the same master repository key pair in
a multi-server environment.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Server Settings on the server whose SC key pair you want to
use for all servers in your environment, select Security Keys in the Setting Categories
list, then click Edit.
91McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 92

Distributing Agents to Manage Systems
Maintaining the agent
2 Next to Local master repository key pair, click Export Key Pair. The Export Master
Repository Key Pair dialog box appears.
3 Click OK. The File Download dialog box appears.
4 Click Save. The Save As dialog box appears.
5 Browse to the location to which to save the ZIP file containing the SC key files. This should
be a location accessible by the other servers, then click Save.
6 Go to Configuration | Server Settings on other servers in your environment, select
Security Keys in the Setting Categories list, then click Edit.
7 Click Import next to Import and back up keys. The Import Keys wizard appears.
8 Browse to the ZIP file containing the exported master repository key files, then click Next.
9 Verify these are the keys you want to import, then click Save.
The imported master repository key pair replaces the existing master repository key pair. Agents
begin using the master repository key pair at the next agent update task.
Ensuring agents can use content from other ePO servers
Use this task to ensure agents can use content originating from other ePO servers in a
multi-server environment when each server uses a different master repository key.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Server Settings on each server in your environment, select
Security Keys in the Setting Categories list, then click Edit.
2 Next to Local master repository key pair, click Export Public Key. The Export Master
Repository Public Key dialog box appears.
3 Click OK. The File Download dialog box appears.
4 Click Save. The Save As dialog box appears.
5 Browse to a location to which to save the ZIP file containing the key files. This should be
a location that is accessible to the other servers, then click Save.
6 After exporting the public key from each server, go to Configuration | Server Settings
on each server, select Security Keys in the Setting Categories list, then click Edit.
7 Click Import, next to Import and back up keys. The Import Keys dialog box appears.
8 Browse to the location containing the exported ZIP files, select one, then click Next.
9 Verify this is the desired master repository public key, then click Save.
10 Repeat until all master repository public keys used in your environment have been imported
into each server.
After the next agent update task completes, agents recognize content signed by master repository
private keys across your environment.
McAfee ePolicy Orchestrator 4.0.2 Product Guide92
Page 93

Distributing Agents to Manage Systems
Maintaining the agent
Backing up and restoring security keys
Use these tasks to back up and restore the security keys. McAfee recommends periodically
backing up all of the security keys and storing them in a secure network location so that they
can be restored easily in the unexpected event any are lost from the ePO server.
NOTE: McAfee recommends backing up all keys before making any changes to the key
management settings.
Tasks
Backing up all security keys
Restoring security keys from a backup file
Backing up all security keys
Use this task to back up all security keys currently managed on this ePO server.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Server Settings, select Security Keys from the Setting
Categories list, then click Edit. The Edit Security Keys page appears.
2 Click Back Up All near the bottom of the page. The File Download dialog box appears.
3 Click Save. The Save As dialog box appears.
4 Browse to a secure network location to store the ZIP file, then click Save.
Restoring security keys from a backup file
Use this task to restore all security keys from a backup file.
Before you begin
You must have already created a backup ZIP file of all of your keys.
CAUTION: When you restore security keys, all existing keys are removed and replaced by the
keys in the backup ZIP file. Ensure the needed keys are in the backup file.
Task
For option definitions, click ? on the page displaying the options.
1 Go to Configuration | Server Settings, select Security Keys from the Setting
Categories list, then click Edit. The Edit Security Keys page appears.
2 Click Restore All at the bottom of the page. The Restore Security Keys wizard appears.
3 Browse to and select the backup ZIP file, then click Next.
4 Verify the keys in this file are the ones you want to overwrite your existing keys, then click
Restore.
93McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 94

Distributing Agents to Manage Systems
Agent command-line options
Agent command-line options
Use the Command Agent (CMDAGENT.EXE) tool to perform selected agent tasks from the
managed system. CMDAGENT.EXE is installed on the managed system at the time of agent
installation. Perform this task locally on managed systems using this program or the McAfee
tray icon.
The CMDAGENT.EXE file is located in the agent installation folder. By default, this location is:
C:\PROGRAM FILES\MCAFEE\COMMON FRAMEWORK
Option definitions
DescriptionOption
/C
Checks for new policies. The agent contacts the ePO server for new or updated policies, then enforces
them immediately upon receipt.
Prompt the agent to enforce policies locally./E
Send properties and events to the ePO server./P
Displays the agent monitor./S
Agent installation command-line options
Depending on whether the agent is already installed, use command-line options when you run
the agent installation package (FRAMEPKG.EXE) or the agent framework installation
(FRMINST.EXE) program.
You can employ these command-line options when using the deployment task to upgrade to a
new version of the agent.
This table describes all of the agent installation command-line options. These options are
case-sensitive, but their values are.
FRAMEPKG.EXE and FRMINST.EXE command-line options
DescriptionCommand
/DATADIR
Specifies the folder on the system to store agent data files. The default location is:
<Documents and Settings>\All Users\Application Data\McAfee\Common
Framework.If the operating system not have a Documents and Settings folder,
the default location is the Data folder within the agent installation folder.
Sample: FRAMEPKG /INSTALL=AGENT /DATADIR=<AGENT DATA PATH>
not
/DOMAIN/USERNAME/PASSWORD
/FORCEINSTALL
McAfee ePolicy Orchestrator 4.0.2 Product Guide94
Specifies an NT domain, and account credentials used to install the agent. The
account must have rights to create and start services on the desired system. If left
unspecified, the credentials of the currently logged-on account are used. If you
want to use an account that is local to the desired system, use the system’s name
as the domain.
Sample: FRAMEPKG /INSTALL=AGENT /DOMAIN=Domain1
/USERNAME=jdoe /PASSWORD=password
Specifies that the existing agent is uninstalled, then the new agent is installed. Use
this option only to change the installation directory or to downgrade the agent.
When using this option, McAfee recommends specifying a different directory for
the new installation (/INSTDIR).
Page 95

Distributing Agents to Manage Systems
Agent installation command-line options
DescriptionCommand
Sample: FRAMEPKG /INSTALL=AGENT /FORCEINSTALL
/INSTDIR=c:newagentdirectory
/INSTALL=AGENT
/INSTALL=UPDATER
/INSTDIR
/REMOVE=AGENT
/SILENT or /S
/SITEINFO
/USELANGUAGE
Installs and enables the agent.
Sample: FRAMEPKG /INSTALL=AGENT
Enables the AutoUpdate 7.0 component if it has already been installed, and does
NOT change whether the agent is enabled. This command-line option upgrades
the agent.
Sample: FRAMEPKG /NSTALL=UPDATER
Specifies the installation folder on the desired system. You can use Windows system
variables, such as <SYSTEM_DRIVE>. If not specified, the default location
is:<DRIVE>:\program files\mcafee\common framework
Sample: FRAMEPKG /INSTALL=AGENT /INSTDIR=C:\ePOAgent
Disables the agent, and removes it if not in use.
Sample: FRMINST /REMOVE=AGENT
Installs the agent in silent mode, hiding the installation interface from the end-user.
Sample: FRAMEPKG /INSTALL=AGENT /SILENT
Specifies the folder path to a specific repository list (SITELIST.XML) file.
Sample: FRAMEPKG /INSTALL=AGENT /SITEINFO=C:\MYSITELIST.XML
Specifies the language version of the agent that you want to install. If you select
a locale other than the 12 languages with locale IDs, the software appears in
English. If you install multiple language versions, the locale selected in operating
system determines the language version that displays.
Sample: FRAMEPKG /INSTALL=AGENT /USELANGUAGE 0404
95McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 96

Creating Repositories
Security software is only as effective as the latest installed updates. For example, if your DAT
files are out-of-date, even the best anti-virus software cannot detect new threats. It is critical
that you develop a robust updating strategy to keep your security software as current as possible.
ePolicy Orchestrator software’s repository architecture offers flexibility to ensure deploying and
updating software is as easy and automated as your environment allows. Once your repository
infrastructure is in place, create update tasks that determine how, where, and when your
software is updated.
Are you creating repositories for the first time?
When creating and setting up repositories for the first time:
1 Understand the purpose of each type of repository, repository branch, and site.
2 Decide which types of repositories to use and their locations.
3 Create and populate your repositories.
Contents
Repository types and what they do
How repositories work together
Ensuring access to the source site
Working with source and fallback sites
Using SuperAgents as distributed repositories
Creating and configuring FTP, HTTP, and UNC repositories
Working with the repository list files
Changing credentials on multiple distributed repositories
Repository types and what they do
To deliver products and updates throughout your network, ePolicy Orchestrator offers several
types of repositories that create a robust update infrastructure when used together. These
provide the flexibility to develop an updating strategy to ensure your systems stay up-to-date.
Master repository
The master repository maintains the latest versions of security software and updates for your
environment. This repository is the source for the rest of your environment. There is one master
repository for each ePolicy Orchestrator server.
McAfee ePolicy Orchestrator 4.0.2 Product Guide96
Page 97

Creating Repositories
Repository types and what they do
The master repository is configured when installed. However, you must ensure that proxy server
settings are configured correctly. By default, ePolicy Orchestrator uses Microsoft Internet Explorer
proxy settings.
Distributed repositories
Distributed repositories host copies of your master repository’s contents. Consider using
distributed repositories and placing them throughout your network strategically to ensure
managed systems are updated while network traffic is minimized, especially across slow
connections.
As you update your master repository, ePolicy Orchestrator replicates the contents to the
distributed repositories.
Replication can occur:
• Automatically when specified package types are checked in to the master repository with
global updating.
• On a recurring schedule with Replication tasks.
• Manually, by running a Replicate Now task.
A large organization can have multiple locations with limited bandwidth connections between
them. Distributed repositories help reduce updating traffic across low-bandwidth connections.
If you create a distributed repository in the remote location and configure the systems within
the remote location to update from this distributed repository, the updates are copied across
the slow connection only once — to the distributed repository — instead of once to each system
in the remote location.
If global updating is enabled, distributed repositories update managed systems automatically,
as soon as selected updates and packages are checked into the master repository. You do not
need to spend additional time creating and configuring repositories or the update tasks.
Source site
The source site provides all updates for your master repository. The default source site is the
McAfeeHttp update site, but you can change the source site or create multiple source sites if
you require. McAfee recommends using the McAfeeHttp or McAfeeFtp update sites as your
source site.
NOTE: Source sites are not required. You can download updates manually and check them in
to your master repository. However, using a source site automates this process.
McAfee posts software updates to these sites regularly. For example, DAT files are posted daily.
Update your master repository with updates as they are available.
Use pull tasks to copy source site contents to the master repository.
The McAfee update sites provide detection definition (DAT) and scanning engine file updates,
as well as some language packs. You must check in all other packages and updates to the
master repository manually.
Fallback site
The fallback site is a source site that’s been enabled as the fallback, from which managed
systems can retrieve updates when their usual repositories are inaccessible. For example, when
network outages or virus outbreaks occur, accessing the established location may be difficult.
Therefore, managed systems can remain up-to-date in such situations. The default fallback site
is the McAfee HTTP (McAfeeHttp) update site. You can enable only one fallback site.
97McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 98

Creating Repositories
Repository types and what they do
If managed systems use a proxy server to access the Internet, you must configure agent policy
settings for those systems to use proxy servers when accessing this fallback site.
Types of distributed repositories
ePolicy Orchestrator supports four types of distributed repositories. Consider your environment
and needs when determining which type of distributed repository to use. You are not limited
to using one type, and may need several, depending on your network.
SuperAgent repositories
Use systems hosting SuperAgents as distributed repositories. SuperAgent repositories have
several advantages over other types of distributed repositories:
• Folder locations are created automatically on the host system before adding the repository
to the repository list.
• File sharing is enabled automatically on the SuperAgent repository folder.
• SuperAgent repositories don’t require additional replication or updating credentials — its
account permissions are created when the agent is converted to a SuperAgent.
TIP: Although SuperAgent broadcast wake-up call functionality requires a SuperAgent in
each broadcast segment, this is not a requirement for SuperAgent repository functionality.
Managed systems only need to “see” the system hosting the repository.
• SuperAgents and global updating use a proprietary network protocol, SPIPE.
TIP: McAfee recommends combining SuperAgent repositories and global updating to ensure
your managed environment is up-to-date.
FTP repositories
If you are unable to use SuperAgent repositories, use an existing FTP server to host a distributed
repository. Use your existing FTP server software such as Microsoft Internet Information Services
(IIS) to create a new folder and site location for the distributed repository. See your web server
documentation for details.
HTTP repositories
If you are unable to use SuperAgent repositories, use an existing HTTP server to host a
distributed repository. Use your existing HTTP server software such as Microsoft Internet
Information Services (IIS) to create a new folder and site location for the distributed repository.
See your web server documentation for details.
UNC share repositories
If you are unable to use SuperAgent repositories, create a UNC shared folder to host a distributed
repository on an existing server. Be sure to enable sharing across the network for the folder so
that the ePolicy Orchestrator server can copy files to it and agents can access it for updates.
Unmanaged repositories
If you are unable to use managed distributed repositories, ePolicy Orchestrator administrators
can create and maintain distributed repositories that are not managed by ePolicy Orchestrator.
If a distributed repository is not managed, a local administrator must keep it up-to-date manually.
McAfee ePolicy Orchestrator 4.0.2 Product Guide98
Page 99

Creating Repositories
Repository types and what they do
Once the distributed repository is created, use ePolicy Orchestrator to configure managed
systems of a specific System Tree group to update from it.
TIP: McAfee recommends that you manage all distributed repositories through ePolicy
Orchestrator. This and using global updating, or scheduled replication tasks frequently, ensures
your managed environment is up-to-date. Use unmanaged distributed repositories only if your
network or organizational policy do not allow managed distributed repositories.
Repository branches and their purposes
ePolicy Orchestrator provides three repository branches, allowing you to maintain three versions
of all packages in your master and distributed repositories. The repository branches are Current,
Previous, and Evaluation. By default, ePolicy Orchestrator uses only the Current branch. You
can specify branches when adding packages to your master repository. You can also specify
branches when running or scheduling update and deployment tasks to distribute different
versions to different parts of your network.
Update tasks can retrieve updates from any branch of the repository, but deployment tasks use
the Current branch only.
To use the Evaluation and Previous branches for packages other than updates, you must select
this in the Repository Packages server settings. Agent versions 3.6 and earlier can only retrieve
update packages from the Evaluation and Previous branches.
Current branch
The Current branch is the main repository branch for the latest packages and updates. Product
deployment packages can be added only to the Current branch, unless support for the other
branches has been enabled.
Evaluation branch
You may want to test new DAT and engine updates with a small number of network segments
or systems before deploying them to your entire organization. Specify the Evaluation branch
when checking in new DATs and engines to the master repository, then deploy them to a small
number of test systems. After monitoring the test systems for several hours, you can add the
new DATs to your Current branch and deploy them to your entire organization.
Previous branch
Use the Previous branch to save and store the prior DAT and engine files before adding the
new ones to the Current branch. In the event that you experience an issue with new DAT or
engine files in your environment, you have a copy of previous versions that you can re-deploy
to your systems if necessary. ePolicy Orchestrator saves only the most immediate previous
version of each file type.
You can populate the Previous branch by selecting Move existing packages to Previous
branch when you add new files to your master repository. The option is available when you
pull updates from a source site and when you manually check in packages to the Current branch.
Repository list file and its uses
The repository list (SITELIST.XML) file contains the names of all the repositories you are
managing. The repository list includes the location and encrypted network credentials that
managed systems use to select the repository and retrieve updates. The server sends the
repository list to the agent during agent-server communication.
99McAfee ePolicy Orchestrator 4.0.2 Product Guide
Page 100

Creating Repositories
How repositories work together
If needed, you can export the repository list to external files (SITELIST.XML or SITEMGR.XML).
Use an exported SITELIST.XML file to:
• Import to an agent at installation.
• Import the repository list from a previous installation of ePolicy Orchestrator or from another
McAfee product.
Use an exported SITEMGR.XML file to:
• Back up and restore your distriubted repositories and source sites if you need to reinstall
the server.
• Import the distributed repositories and source sites from a previous installation of ePolicy
Orchestrator.
How repositories work together
The repositories work together in your environment to deliver updates and software to managed
systems. You may or may not need distributed repositories.
Figure 18: Sites and Repositories Delivering Packages to Systems
1 The master repository regularly pulls DAT and engine update files from the source site.
2 The master repository replicates the packages to distributed repositories in the network.
3 The managed systems in the network retrieve updates from a close repository. If managed
systems can’t access the distributed repositories or the master repository, they retrieve
updates from the fallback site.
McAfee ePolicy Orchestrator 4.0.2 Product Guide100
 Loading...
Loading...