Page 1

McAfee Advanced Threat Defense 4.6.0 Hardware
Setting up the Advanced Threat Defense
Appliance
Prepare the Advanced Threat Defense Appliance for installation and integration in the network.
Advanced Threat Defense Appliances
Depending on the model, the Advanced Threat Defense Appliance is a 1-U or 2-U rack dense chassis with Intel
Xeon® E5-2600 product family processor.
The Advanced Threat Defense Appliance runs on a pre-installed, hardened Linux kernel 3.6.0 and comes
preloaded with the Advanced Threat Defense software.
Guide
®
The Advanced Threat Defense Appliance is available in the following models:
• ATD-3000 — Standard model is a 1U chassis
• ATD-6000 — High-end model is a 2U chassis
• ATD-3100 — Standard model is a 1U chassis
• ATD-6100 — High-end model is a 1U chassis
The Advanced Threat Defense Appliances are purpose-built, scalable, and exible high-performance servers
designed to analyze suspicious les for malware.
1
Page 2

The following are the primary functions of the Advanced Threat Defense Appliance:
• Host the Advanced Threat Defense software that analyzes les for malware.
• Host the Advanced Threat Defense web interface.
• Host the virtual machines used for dynamic analysis of suspicious les.
For the performance values related to the appliances, contact Support.
Functions of a Advanced Threat Defense Appliance
The Advanced Threat Defense Appliances are purpose-built, scalable, and exible high-performance servers
designed to analyze suspicious les for malware.
The following are the primary functions of the Advanced Threat Defense Appliance:
• Host the Advanced Threat Defense software that analyzes les for malware.
• Host the Advanced Threat Defense web application.
• Host the virtual machines used for dynamic analysis of suspicious les.
For the performance values related to Advanced Threat Defense Appliances, contact McAfee support.
Before you install the Advanced Threat Defense Appliance
This section describes the tasks that you must complete before you begin to install a Advanced Threat Defense.
• Read all the provided documentation before installation.
• Make sure that you have selected a suitable location for installing the Advanced Threat Defense Appliance.
• Check that you have all the necessary equipment and components outlined in this document.
• Familiarize yourself with the McAfee Advanced Threat Defense Appliance network access card ports and
connectors as described in this document.
• Make sure you have the following information available when you congure the Advanced Threat Defense
Appliance:
• IPv4 address that you want to assign to the Appliance.
• Network mask.
• Default gateway address.
2
Page 3

Warnings and cautions
Read and follow these safety warnings when you install the Advanced Threat Defense Appliance. Failure to
observe these safety warnings could result in serious physical injury.
Advanced Threat Defense Appliance power on/o — the push-button on/o power switch on the front panel of
the Advanced Threat Defense Appliance does not turn o the AC power. To remove AC power from the Advanced
Threat Defense Appliance, you must unplug the AC power cord from either the power supply or wall outlet for
both the power supplies. If you press the push-button on/o power switch on the front panel of the Advanced
Threat Defense Appliance while the appliance is running, it reboots. If you want to power o the appliance, use
CLI command — shutdown, after the system halts press the power button until the appliance powers o.
The power supplies in your system might produce high voltages and energy hazards, which can cause bodily
harm. Only trained service technicians are authorized to remove the covers and access any of the components
inside the system.
Hazardous conditions — devices and cables: Hazardous electrical conditions might be present on power,
telephone, and communication cables. Turn o the Advanced Threat Defense Appliance and disconnect
telecommunications systems, networks, modems, and both the power cords attached to the Advanced Threat
Defense Appliance before opening it. Otherwise, personal injury or equipment damage can result.
Avoid injury — lifting the Advanced Threat Defense Appliance and attaching it to the rack is a two-person job.
This equipment is intended to be grounded. Ensure that the host is connected to earth ground during normal
use.
Do not remove the outer shell of the Advanced Threat Defense Appliance. Doing so invalidates your warranty.
Do not operate the system unless all cards, faceplates, front covers, and rear covers are in place. Blank faceplates
and cover panels prevent exposure to hazardous voltages and currents inside the chassis, contain
electromagnetic interference (EMI) that might disrupt other equipment and direct the ow of cooling air through
the chassis.
To avoid electric shock, do not connect safety extra-low voltage (SELV) circuits to telephone-network voltage (TNV)
circuits. LAN ports contain SELV circuits, and WAN ports contain TNV circuits. Some LAN and WAN ports both use
RJ-45 connectors. Use caution when connecting cables.
Usage restrictions
The following restrictions apply to the use and operation of Advanced Threat Defense Appliance:
• You should not remove the outer shell of the Advanced Threat Defense Appliance. Doing so invalidates your
warranty.
• The Advanced Threat Defense Appliance is not a general purpose server.
• McAfee prohibits the use of Advanced Threat Defense Appliance for anything other than operating the
Advanced Threat Defense solution.
• McAfee prohibits the
modication or installation of any hardware or software on the Advanced Threat
Defense Appliance that is not part of the normal operation of Advanced Threat Defense.
Unpack the shipment
1
Open the crate.
2
Remove the
3
Verify you have received all parts as listed in Check your shipment on page 4.
rst accessory box.
3
Page 4

4
Remove the Advanced Threat Defense Appliance.
5
Place the Advanced Threat Defense Appliance as close to the installation site as possible.
6
Position the box with the text upright.
7
Open the top aps of the box.
8
Remove the accessory box within the Advanced Threat Defense Appliance box.
9
Remove the slide rail kit.
10
Pull out the packing material surrounding the Advanced Threat Defense Appliance.
11
Remove the Advanced Threat Defense Appliance from the anti-static bag.
12
Save the box and packing materials for later use in case you need to move or ship the Advanced Threat
Defense Appliance.
Check your shipment
Each product ships with all the items needed to install the appliance on a network.
To verify that you received all the necessary items, verify that you have received the following:
• Advanced Threat Defense Appliance
• Accessories itemized on the Content Sheet
• Set of tool-less slide rails
• Front bezel with key
McAfee Advanced Threat Defense Appliance front and back panels
Figure 1 ATD-3000 and ATD-6000 front panel
Label Description
1 System ID button with integrated indicator light
2 NMI button (recessed, tool required for use)
3 NIC 1 activity indicator light
4
• ATD-3000: NIC 3 activity indicator light
• ATD-6000: Not used
5 System cold reset button
6 System status indicator light
7 Power button with integrated indicator light
8 Hard drive activity indicator light
4
Page 5
Label Description
9
• ATD-3000: NIC 4 activity indicator light
• ATD-6000: Not used
10 NIC 2 activity indicator light
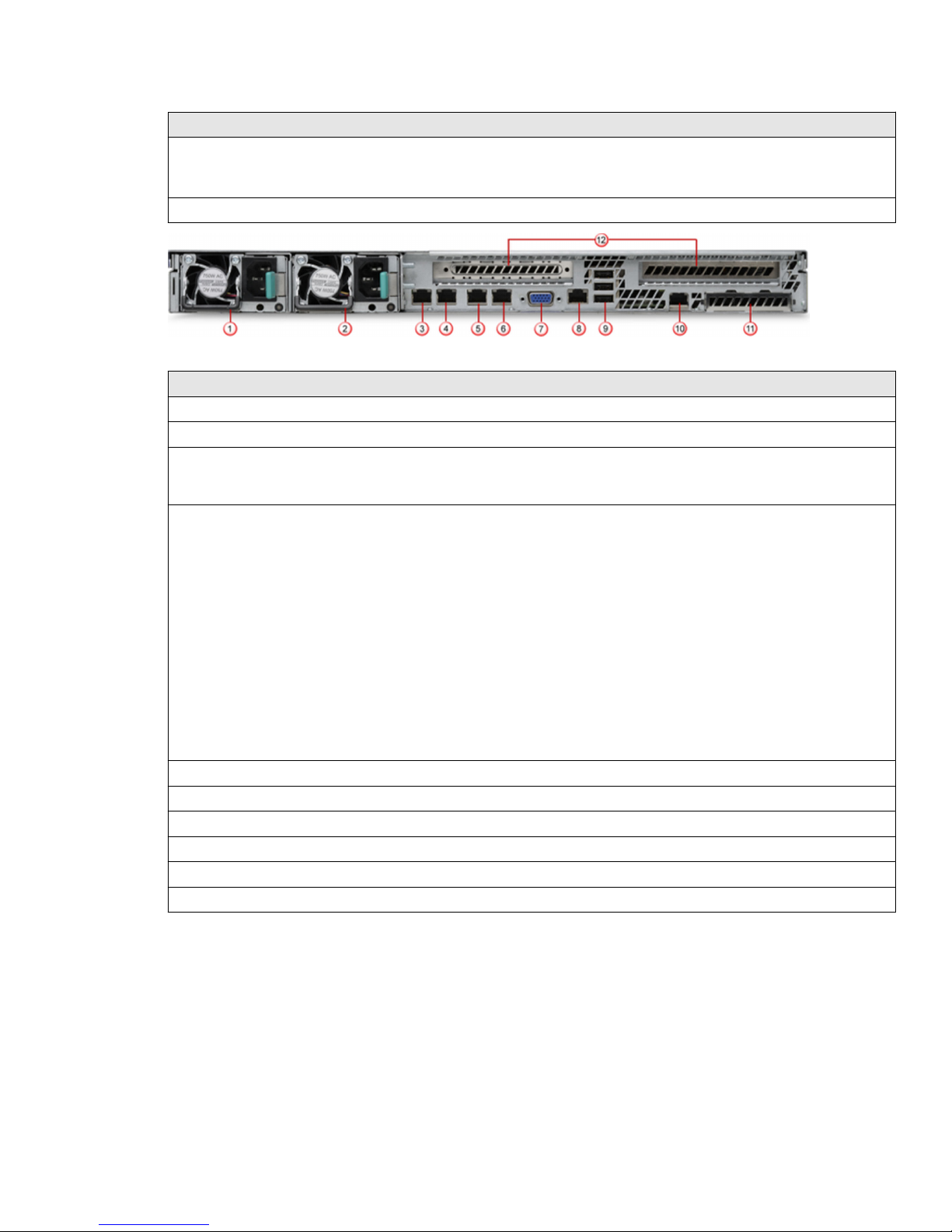
Figure 2 ATD-3000 Appliance back panel
Label Description
1 Power supply module 1
2 Power supply module 2
3 Management port (NIC 1). This is the eth-0 interface. The set appliance and set mgmtport
commands apply to this interface. For example, when you use the set appliance ip command, the
corresponding IP address is assigned to this interface.
4 NIC 2. This is the eth-1 interface. This interface is disabled by default.
• To enable or disable this interface, use the set intfport command. For example, set intfport
1 enable
• To assign the IP details to this interface use set intfport <eth 1, 2, or 3> ip <IPv4
address> <subnet mask>
For example, set intfport 1 ip 10.10.10.10 255.255.255.0
• You cannot assign the default gateway to this port. However, you can
congure a route on this
interface to route the trac to the desired gateway. To congure a route, use route add network
<IPv4 subnet> netmask <netmask> gateway <IPv4 address> intfport 1
For example, route add network 10.10.10.0 netmask 255.255.255.0 gateway
10.10.10.1 intfport 1. This command routes all
trac from the 10.10.10.0 command to
10.10.10.1 through NIC 2 (eth-1).
5 NIC 3. This is the eth-2 interface. The note described for NIC 2 applies to this interface as well.
6 NIC 4. This is the eth-3 interface. The note described for NIC 2 applies to this interface as well.
7 Video connector
8 RJ45 serial-A port
9 USB ports
10 RMM4 NIC port
5
Page 6
Label Description
11 I/O module ports/connectors (not used)
12 Add-in adapter slots from riser card 1 and riser card 2
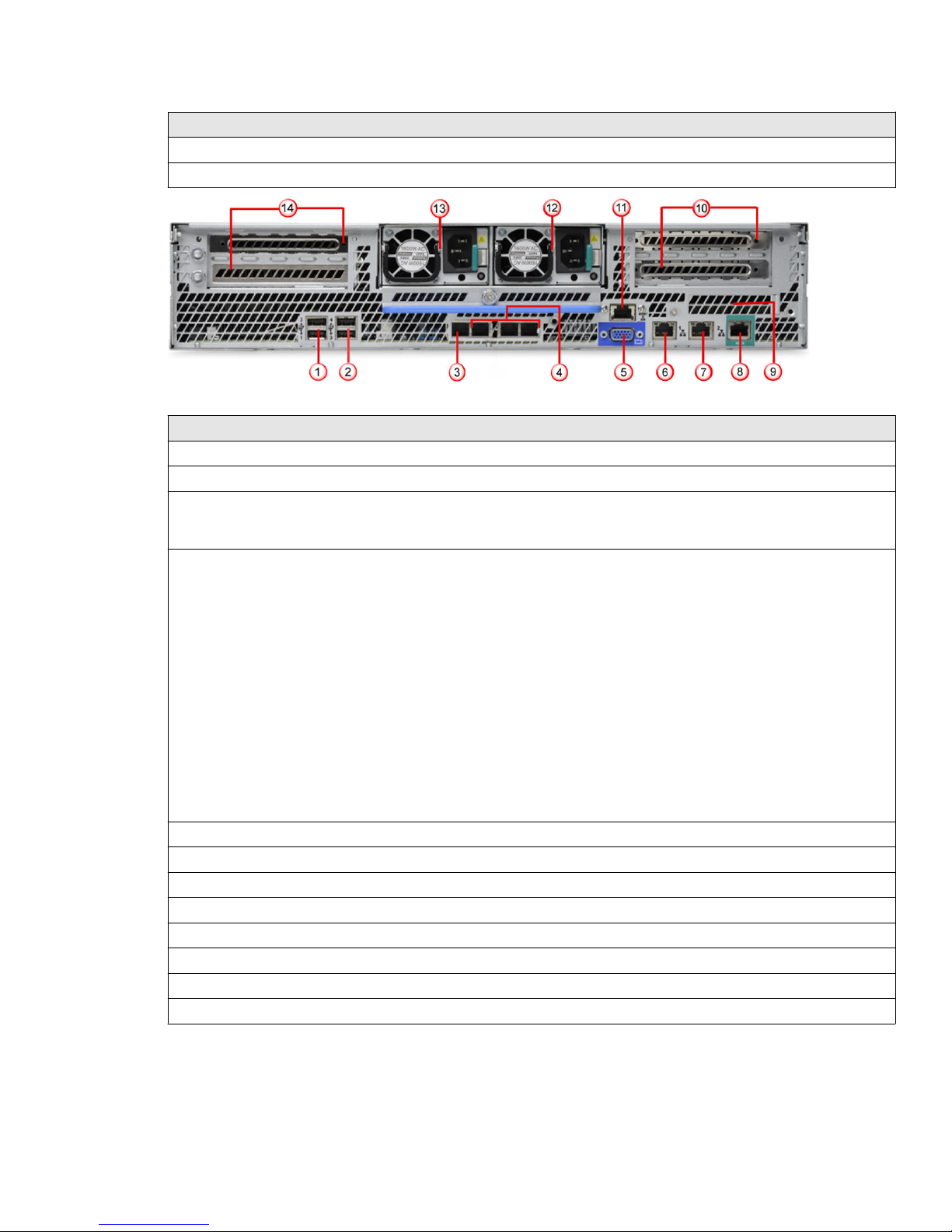
Figure 3 ATD-6000 Appliance back panel
Label Description
1 USB ports
2 USB ports
3 Management port. This is the eth-0 interface. The set appliance and set mgmtport commands
apply to this interface. For example, when you use the set appliance ip command, the
corresponding IP address is assigned to this interface.
4 Additional I/O module ports/connectors. These are the eth-1, eth-2, and eth-3 interfaces respectively.
These interfaces are disabled by default.
• To enable or disable an interface, use the set intfport command. For example, set intfport 1
enable to enable eth-1.
• To assign the IP details to an interface use set intfport <eth 1, 2, or 3> ip <IPv4
address> <subnet mask>
For example, set intfport 1 ip 10.10.10.10 255.255.255.0
• You cannot assign the default gateway to this port. However, you can
interface to route the trac to the desired gateway. To congure a route, use route add network
<IPv4 subnet> netmask <netmask> gateway <IPv4 address> intfport 1
For example, route add network 10.10.10.0 netmask 255.255.255.0 gateway
10.10.10.1 intfport 1. This command routes all
10.10.10.1 through eth-1.
5 Video connector
6 NIC 1 (currently not used)
7 NIC 2 (currently not used)
8 RJ45 serial-A port
9 I/O module ports/connectors (not used)
10 Add-in adapter slots from riser card
11 RMM4 NIC port
12 Power supply module 2
congure a route on this
trac from the 10.10.10.0 command to
6
Page 7

Label Description
13 Power supply module 1
14 Add-in adapter slots from riser card
Figure 4 ATD-3100 and ATD-6100 front panel
Table 1 The following table will be updated as soon as the front panel image arrives.
Label Description
A System ID button with integrated indicator light
B NMI button (recessed, tool required for use)
C NIC 1 activity indicator light
D System status indicator light
E Power button with integrated indicator light
F Hard drive activity indicator light
G System cold reset button
H NIC 2 activity indicator light
Figure 5 ATD-3100 and ATD-6100 Appliance back panel
7
Page 8

Label Interface port
A Power connector A
B Power connector B
C Ethernet interface 2 (intf2)
D Ethernet interface 3 (intf3)
E VGA connector
F Serial console interface
G USB 3.0 ports
H BMC port (RMM)
I Ethernet interface 0 (ATD Management Interface)
J Ethernet interface 1 (intf1)
If an item is missing or damaged, contact your supplier.
Hardware specications
Before you set up the Advanced Threat Defense Appliance, review the hardware specications.
Specication ATD-3100 ATD-6100 ATD-3000 ATD-6000
Packaging
Dimension
Chassis Intel R1208WTTGSR
Chassis
Dimension
Weight 22.7 Kg (50 lbs) 22.7 Kg (50 lbs) 15 Kg (33 lbs) 22.7 Kg (50 lbs.)
Form Factor 1U rack mountable;
Motherboard S2600WTT S2600WTT S2600GZ4 S4600LH2
CPU 2 x E5-2609v4, 1.7GHz,
Storage
Length = 38", Width =
24", Height = 7"
(Wildcat Pass)
Length = 28", Width =
17.3", Height = 1.7"
ts 19-inch rack
20M cache, 8 Cores
• Disk space HDD: 4 x
1.2TB, SAS, 12GB/s,
10K RPM, 2.5",
Raid-5
Length = 38", Width =
24", Height = 7"
Intel R1208WTTGSR
(Wildcat Pass)
Length = 28", Width =
17.3", Height = 1.7"
1U rack mountable;
ts 19-inch rack
2 x E5-2695v4, 2.1GHz,
45M cache, 18 Cores
• Disk space HDD: 6 x
1.2TB, SAS, 12GB/s,
10K RPM, 2.5",
Raid-5
Length = 38", Width
= 24", Height = 7"
R1304GZ4GC R2304LH2HKC
Length = 29", Width
= 17.25", Height =
1.7"
1U rack mountable;
ts 19-inch rack
2 x E5-2658,
2.10GHz, 20M
Cache, 8 Cores
• Disk space HDD:
2 x 4TB
• SSD: 2 x 400 GB
Length = 36", Width =
24", Height = 7"
Length = 29", Width =
17.25", Height =
3.43"
2U rack mountable;
ts 19-inch rack
4 x E5-4640,
2.40GHz, 20M Cache,
8 Cores
• Disk space HDD: 4
x 4TB
• SSD: 2 x 800 GB
• SSD: 2 x Intel
Enterprise grade
400GB, 2.5", Raid-0
Memory 16 x 16 GB DDR4
2400MHz ECC
Remote
Management
8
RMM4LITE2 RMM4LITE2 RMM4R RMM4
• SSD: 2 x Intel
Enterprise grade 800
GB, 2.5", Raid-0
16 x 32 GB DDR4
2400MHz ECC
192 GB 256 GB
Page 9

Specication ATD-3100 ATD-6100 ATD-3000 ATD-6000
Power Supply 750 W redundant 750 W redundant 2x 750W, AC
redundant, hot
swappable
Network
Interfaces
(Copper)
Dual Integrated 10
GB/1 GB/100 MB and
Dual 10 GB/1 GB/100
MB Module
Dual Integrated 10
GB/1 GB/100 MB and
Dual 10 GB/1 GB/100
MB Module
Dual Integrated 10
GB/1 GB/100 MB
and Dual 10 GB/1
GB/100 MB Module
2x 1600W, AC
redundant, hot
swappable
Dual Integrated 10
GB/1 GB/100 MB and
Dual 10 GB/1 GB/100
MB Module
Default ports used in Advanced Threat Defense communication
The Advanced Threat Defense Appliance uses many ports for network communications.
Client Server Default
port
Any (desktop) Advanced Threat Defense TCP 443
(HTTPS)
Any (desktop) Advanced Threat Defense TCP 6080
(HTTPS)
Any (FTP
client)
Any (SFTP
client)
Sensor Advanced Threat Defense TCP 8505 No Communication channel
Manager Advanced Threat Defense TCP 443
Advanced
Threat
Defense
Advanced
Threat
Defense
Advanced
Threat
Defense
Any (SSH
client)
Advanced Threat Defense TCP 21 (FTP) No Access the FTP servers on
Advanced Threat Defense TCP 22
(SFTP)
(HTTPS)
McAfee ePO TCP 8443 Yes Host information queries.
tunnel.web.trustedsource.org
List.smartfilter.com
Advanced Threat Defense TCP 2222
TCP 443
(HTTPS)
TCP 80
(HTTP)
(SSH)
Congurable Description
No Access the Advanced
Threat Defense web
interface.
No For VM activation process
and X-mode.
Advanced Threat Defense.
No Access the SFTP servers
on Advanced Threat
Defense.
between a Sensor and
Advanced Threat Defense.
No Communication between
the Manager and
Advanced Threat Defense
through the RESTful APIs.
No File Reputation queries.
No URL updates.
No CLI access.
9
Page 10

Client Server Default
port
Advanced
Threat
Defense (DAT
updates)
wpm.webwasher.com
wpm1‑2.webwasher.com
wpm1‑3.webwasher.com
TCP 443
(HTTPS)
wpm1‑4.webwasher.com
wpm‑usa.webwasher.com
wpm‑usa1.webwasher.com
wpm‑usa2.webwasher.com
wpm‑asia.webwasher.com
tau.mcafee.com
tau1‑2.mcafee.com
tau1‑3.mcafee.com
tau1‑4.mcafee.com
tau‑usa.mcafee.com
tau‑usa1.mcafee.com
tau‑usa2.mcafee.com
tau‑manual.mcafee.com
tau‑ldv1.securelabs
.webwasher.com
tau‑ldv2.securelabs
.webwasher.com
tau‑ldv3.securelabs
.webwasher.com
tau‑europe.mcafee.com
tau‑dnv1.securelabs
.webwasher.com
tau‑dnv2.securelabs
.webwasher.com
tau‑dnv3.securelabs
.webwasher.com
tau‑asia.mcafee.com
rpns.mcafee.com
mwg‑update.mcafee.com
Congurable Description
No Updates for McAfee
Gateway Anti-Malware
Engine and McAfee
Anti-Malware Engine.
Advanced
atdupdate.mcafee.com
Threat
Defense
(Software
updates)
10
TCP 443
(HTTPS)
No Updates for the Advanced
Threat Defense software.
The update includes new
detection and application
package.
Page 11

Set up the hardware
Install and integrate the hardware in your network.
Install or remove rack handles
• To install a rack handle, align it with the two holes on the side of the Advanced Threat Defense Appliance
and attach the rack handle to the Appliance with two screws as shown.
Figure 6 Installing the rack handle
• To remove a rack handle, remove the two screws holding the rack handle in place, and remove the rack
handle from the server system as shown.
Figure 7 Removing the rack handle
11
Page 12

Rack mount the appliance
To install the Advanced Threat Defense Appliance on the four-post 19-inch rack, use the rack-mounting kit. You
can use the kit with most industry-standard rack cabinets.
Task
For each mounting rail, use the following steps.
1
At the front of the rack, position the right or left mounting rail on the corresponding side so that the
a
mounting bracket aligns with the rack holes.
Always load the rack from the bottom up. If you are installing multiple appliances, start with the lowest
available position.
Figure 8 Slide rail installation
At the back of the rack, pull the back mounting-bracket (extending the mounting rail) so that it aligns with
b
the rack holes.
On each side of the rack, ensure that the mounting rails are the same level.
Figure 9 Install rail to rack
Clip the rail to the rack and secure it with the tie wraps.
c
12
Page 13

Slide both rails so they are fully extended.
2
Figure 10 Full extend slide
With help from another person, lift the Advanced Threat Defense Appliance and install the chassis to the rail
3
on both the sides.
Drop in the rear spool rst, then the middle, then the front.
Figure 11 Install the Appliance to rail
At least two people are required to lift and attach the Advanced Threat Defense Appliance to the rack.
If required, attach the lockable bezel to protect the front panel.
Lift the release tab and push the Advanced Threat Defense Appliance into the rack.
4
Figure 12 Lift release tab and push Appliance into rack
To remove the Advanced Threat Defense Appliance from the rack, lift the release tab next to the chassis
front spool, then lift it out of the rails.
13
Page 14

Turn on the Advanced Threat Defense Appliance
The Advanced Threat Defense Appliance has redundant power supplies pre-installed.
The Advanced Threat Defense Appliance ships with two AC power cords
Task
Plug one end of the AC power cord into the rst power supply module in the back panel, then plug the other
1
end into the power source.
Plug one end of the other AC power cord into the second power supply module in the back panel, then plug
2
the other end into the power source.
Advanced Threat Defense powers up without pressing the on/o button on the front panel.
To turn o the Advanced Threat Defense Appliance AC power, you must unplug both AC power cords from
the back panel or power source.
The on/o button on the front panel does not turn on/o the AC power.
To restart the Advanced Threat Defense Appliance, you must press the on/o power switch on the front
panel while the appliance is turned on.
To turn o the Advanced Threat Defense Appliance, use the shutdown CLI command, then press the on/o
power switch.
specic to your country or region.
Handling the front bezel
You can remove the front bezel if required, and then re-install it. However, before you install the bezel, you must
install the rack handles.
Task
Remove the front bezel.
1
Unlock the bezel if it is locked.
a
Remove the left end of front bezel from rack handle.
b
Rotate the front bezel anticlockwise to release the latches on the right end from the rack handle.
c
14
Page 15

Install the front bezel.
2
Lock the right end of the front bezel to the rack handle
a
Rotate the front bezel clockwise until the left end clicks into place
b
Lock the bezel if needed.
c
Enable RMM
Enable Intel RMM on your Advanced Threat Defense Appliance.
Task
Restart the Advanced Threat Defense Appliance.
1
2 During the reboot process, press F2.
3 On the BIOS Setup Utility page, select the Server Management tab.
4 Select BMC LAN Configuration.
5 Locate Intel (R) RMM4 LAN configuration and
a Highlight IP Source, press Enter, then select Static.
b Highlight IP Address, then enter the IP address.
c Highlight Subnet Mask, then enter the subnet mask address.
d Highlight Gateway IP, then enter the gateway IP address.
6 Locate User configuration and
a Highlight User status, press Enter, then select Enabled.
b Highlight User password, press Enter, then enter the root account password.
c Press Enter,
7 Press F10, then press Enter.
Log on to the RMM interface.
8
conrm the password, then press Enter again.
congure the settings.
congure the settings.
15
Page 16

Connect the management port
When you connect your network device to the Advanced Threat Defense Appliance, you can
appliance IP address and other parameters for integration in your network.
Task
1
On the rear panel, plug the Category 5e or 6 Ethernet cable in the Ethernet port 1
The Ethernet port 1 is the ATD Management port.
Plug the other end of the cable into the network device.
2
congure the
.
Congure the Advanced Threat Defense Appliance network information
Manage the Advanced Threat Defense Appliance from a remote computer or terminal server.
Task
On the Advanced Threat Defense Appliance back panel, plug the console cable (RJ45 to DB9 serial) into the
1
console port (RJ45 serial-A port).
Locate the computer or port of the terminal server you are using to
2
Appliance, then connect the other end of the cable into the COM port.
From your Microsoft Windows-based computer, run the HyperTerminal using the following settings.
3
• Baud rate — 9600
• Number of Bits — 8
• Parity — None
• Stop Bits — 1
• Control Flow — None
To log on to the Advanced Threat Defense Appliance, use the following credentials.
4
• User name — cliadmin
• Password — atdadmin
To access all the built-in command syntax instructions, enter help or ?. For a list of all commands, enter
list.
Open the command prompt and
5
Enter the Advanced Threat Defense Appliance name.
a
For example, set appliance name matd_appliance_1.
Best Practice: Use an alphanumeric character string up to 25 characters. The string must begin with a
letter and can include hyphens, underscores, and periods, but not spaces.
congure the Advanced Threat Defense Appliance.
congure the Advanced Threat Defense
Enter the Advanced Threat Defense Appliance management port IP address and subnet mask.
b
For example, set appliance ip 10.34.2.8 255.255.255.0.
Do not assign this class C network IP address: 192.168.55.0/24.
Enter the default gateway IP address.
c
For example, set appliance gateway 12.34.2.1.
16
Page 17

Restart the Advanced Threat Defense Appliance.
d
Enter the management port speed and duplex settings using one of the following commands:
e
• set mgmtport auto — Sets the management port in auto mode for speed and duplex.
• set mgmtport speed (10|100) duplex (full|half) — Sets the speed to 10 or 100 Mbps at
full or half duplex.
To change the Advanced Threat Defense Appliance password, enter passwd.
f
Passwords are case sensitive, must not include spaces, and must contain the following:
• Between 8 and 25 characters
• At least one uppercase letter
• At least one lowercase letter
• At least one digit
• At least one alphanumeric character or symbol
Best Practice: Enter a password with a combination of characters that is easy for you to remember, but
dicult for someone else to guess.
Verify the conguration.
g
• To view the conguration details, enter show.
• To check the network connectivity, enter ping <IP address>.
The success message host <ip address> is alive appears. If the host is not reachable, failed
to talk to <ip address> appears.
Copyright © 2018 McAfee, LLC
McAfee and the McAfee logo are trademarks or registered trademarks of McAfee, LLC or its subsidiaries in the US and other countries. Other
marks and brands may be claimed as the property of others.
0-00
17
Page 18

A
Appendix
These additional information can be used to learn more about your appliance.
Grantley Platform
The McAfee Advance Threat Defense appliances are built on the Grantley platform. Equipped with the CPUs
from the Xenon® E5-2600 v3 and Xenon® E5-2600 v4 product families, DDR4 memory, and 10 GB Ethernet
modules, your appliances are fast and ecient. For more information about the Grantley platform, visit:
http://www.intel.com/content/www/us/en/embedded/products/grantley-refresh/overview.html
https://software.intel.com/en-us/articles/intel-xeon-processor-e5-2600-v3-product-family-technical-overview
Boradwell-EP
The CPUs from the Xenon® E5-2600 v3 and Xenon® E5-2600 v4 product families on the McAfee Advance Threat
Defense appliances are manufactured in Intel's 14 Nm process technology. The ATD-3100 with two Xenon
E5-2609v4 CPUs have eight cores and threads with 20 MB of Intel's Smart Cache. The ATD-6100 with two Xenon
E5-2695v4 has 18 cores and 36 threads with 45 MB of Intel's Smart Cache. The ATD-3000 and ATD-6000 with two
E5-2658 and four E5-4640 respectively has eight cores and 16 threads with 20 MB of Intel's Smart Cache. For
more information about the Broadwell-EP, visit ark.intel.com.
Chassis
The ATD-3100 and ATD-6100 appliances are built on Intel's Wildcat Pass 1U rack system. The ATD-3000 is built
on Intel's Grizzly Pass 1U and ATD-6000 is built on Intel's Lizard Head Pass 2U rack system. For more
information about Wildcat Pass, Grizzly Pass, and Lizard Head Pass, visit ark.intel.com.
Storage
The McAfee Advance Threat Defense appliances use both HDDs and SSDs for storage. The HDDs are set in 3+1
RAID 5 conguration and the SSDs are set in 1+1 RAID 0 conguration.
18
Page 19

Remote management module (RMM)
The ATD-3100 and ATD-6100 appliances are equipped with Intel's RMM4LITE2 modules. The ATD-3000 and
ATD-6000 are equipped with Intel's RMM4R and RMM4 modules. The RMM4 modules have the following
features which allow administrators to:
• Redirect KVM from RMM4 NIC or the baseboard NIC used for management trac.
• Redirect media, that is, to mount a CD-ROM, Floppy disk, or a USB storage device to a server.
• Remotely troubleshoot system through all system level event logs, sensors reading, power statistics, and
debug messages that are readily available in RMM UI console.
For more information about Intel's RMM, visit:
http://www.intel.com/content/www/us/en/server-management/intel-remote-management-module.html
19
Page 20

Copyright © 2018 McAfee, LLC
McAfee and the McAfee logo are trademarks or registered trademarks of McAfee, LLC or its subsidiaries in the US and other countries. Other
marks and brands may be claimed as the property of others.
20
0-00
 Loading...
Loading...