Page 1
Secure Microcontroller
User’s Guide
Rev 1/14
Maxim Integrated cannot assume responsibility for use of any circuitry other than circuitry entirely embodied in a Maxim Integrated product. No circuit patent licenses
are implied. Maxim Integrated reserves the right to change the circuitry and specifications without notice at any time.
Maxim Integrated 160 Rio Robles, San Jose, CA 95134 USA 1-408-601-1000
© 2014 Maxim Integrated Products, Inc. Maxim Integrated and the Maxim Integrated logo are trademarks of Maxim Integrated Products, Inc.
Page 2

Secure Microcontroller User’s Guide
TABLE OF CONTENTS
1. INTRODUCTION ................................................................................................................. 7
1.1 I
1.2 S
1.3 P
1.4 I
2. SELECTOR GUIDE .......................................................................................................... 12
3. SECURE MICROCONTROLLER ARCHITECTURE ........................................................ 13
3.1 B
3.2 CPU
4. PROGRAMMER’S GUIDE ................................................................................................ 18
4.1 S
4.2 DS5000
4.3 DS5000
4.4 DS5001/DS5002
4.5 DS5001/DS5002
4.6 DS5001/DS5002
4.7 L
4.8 S
4.9 I
4.10 A
4.11 P
5. MEMORY INTERCONNECT ............................................................................................ 51
6. LITHIUM/BATTERY BACKUP ......................................................................................... 58
6.1 D
7. POWER MANAGEMENT ................................................................................................. 62
7.1 I
7.2 S
7.3 V
7.4 P
7.5 T
7.6 P
8. SOFTWARE CONTROL ................................................................................................... 68
8.1 T
8.2 W
8.3 CRC
9. FIRMWARE SECURITY ................................................................................................... 74
9.1 S
9.2 RAM
9.3 E
9.4 E
9.5 E
9.6 E
9.7 D
9.8 O
9.9 S
9.10 M
MPORTANT NOTICE REGARDING DISCONTINUED DS2251T/DS2252T .............................................. 7
OFTWARE SECURITY ..................................................................................................................... 7
RODUCT DESCRIPTION .................................................................................................................. 9
NTRODUCTION TO THE DS5250 HIGH-SPEED SECURE MICROCONTROLLER ................................... 10
US ORGANIZATION ...................................................................................................................... 13
REGISTERS ........................................................................................................................... 13
ECURE MICROCONTROLLER MEMORY ORGANIZATION .................................................................. 18
4.1.1 Internal Registers ................................................................................................................................. 19
4.1.2 Program and Data Memory .................................................................................................................. 20
SERIES MEMORY ORGANIZATION ..................................................................................... 21
MEMORY MAP CONTROL .................................................................................................. 23
MEMORY ORGANIZATION ................................................................................... 24
MEMORY-MAPPED PERIPHERALS ....................................................................... 27
MEMORY MAP CONTROL .................................................................................... 28
OADING AND RELOADING PROGRAM MEMORY .............................................................................. 28
PECIAL FUNCTION REGISTERS ..................................................................................................... 33
NSTRUCTION SET ......................................................................................................................... 48
DDRESSING MODES ................................................................................................................. 48
ROGRAM STATUS FLAGS .......................................................................................................... 50
ATA RETENTION .......................................................................................................................... 58
DLE MODE .................................................................................................................................... 62
TOP MODE .................................................................................................................................. 64
OLTAGE MONITORING CIRCUITRY ................................................................................................ 64
OWER-FAIL INTERRUPT ............................................................................................................... 64
OTAL POWER FAILURE ................................................................................................................. 65
ARTIAL POWER FAILURES ............................................................................................................ 66
IMED ACCESS .............................................................................................................................. 68
ATCHDOG TIMER ........................................................................................................................ 70
MEMORY VERIFICATION ........................................................................................................ 71
8.3.1 Automatic CRC on Power-Up Feature ................................................................................................. 71
ECURITY LOCK ............................................................................................................................ 74
MEMORY .............................................................................................................................. 75
NCRYPTED MEMORY ................................................................................................................... 76
NCRYPTION ALGORITHM .............................................................................................................. 78
NCRYPTION KEY .......................................................................................................................... 78
NCRYPTION KEY SELECTION AND LOADING .................................................................................. 78
UMMY BUS ACCESS .................................................................................................................... 79
N-CHIP VECTOR RAM ................................................................................................................. 79
ELF-DESTRUCT INPUT ................................................................................................................. 80
ICROPROBE/DIE TOP COATING ................................................................................................ 81
2 of 187
Page 3

Secure Microcontroller User’s Guide
9.11 RANDOM NUMBER GENERATOR .................................................................................................. 81
9.12 S
9.13 A
ECURITY SUMMARY BY PART .................................................................................................... 81
PPLICATION: ADVANCED SECURITY TECHNIQUES ...................................................................... 82
10. RESET CONDITIONS ....................................................................................................... 85
10.1 R
10.1.1 Power-On Reset ................................................................................................................................... 87
10.1.2 No-VLI Power-On Reset ....................................................................................................................... 88
10.1.3 External Reset ...................................................................................................................................... 88
10.1.4 Watchdog Timer Reset ........................................................................................................................ 88
10.2 M
10.3 I
10.4 T
10.5 T
ESET SOURCES ....................................................................................................................... 85
EMORY MAP ............................................................................................................................ 89
NTERRUPTS .............................................................................................................................. 90
IMERS ...................................................................................................................................... 90
RANSIENT VOLTAGE PROTECTION ............................................................................................. 91
11. INTERRUPTS ................................................................................................................... 92
11.1 I
11.2 E
11.3 T
11.4 S
11.5 P
11.6 S
11.7 I
11.8 I
NTERRUPT SOURCES ................................................................................................................ 92
XTERNAL INTERRUPTS .............................................................................................................. 93
IMER INTERRUPTS .................................................................................................................... 93
ERIAL PORT INTERRUPTS ......................................................................................................... 93
OWER-FAIL WARNING INTERRUPT ............................................................................................ 94
IMULATED INTERRUPTS ............................................................................................................ 94
NTERRUPT PRIORITIES .............................................................................................................. 96
NTERRUPT ACKNOWLEDGE ........................................................................................................ 97
12. PARALLEL I/O ................................................................................................................. 99
12.1 O
12.2 I
12.3 R
12.4 R
12.5 RPC
12.6 RPC
12.7 DMA
UTPUT FUNCTIONS ................................................................................................................ 102
NPUT FUNCTION ...................................................................................................................... 103
EAD-MODIFY-WRITE INSTRUCTIONS ....................................................................................... 104
EPROGRAMMABLE PERIPHERAL CONTROLLER (RPC) ............................................................. 104
INTERRUPTS .................................................................................................................... 106
PROTOCOL ...................................................................................................................... 107
OPERATION ..................................................................................................................... 107
13. PROGRAMMABLE TIMERS .......................................................................................... 109
13.1 F
13.2 M
13.3 M
13.4 M
13.5 M
UNCTIONAL DESCRIPTION ....................................................................................................... 109
ODE 0 ................................................................................................................................... 111
ODE 1 ................................................................................................................................... 111
ODE 2 ................................................................................................................................... 112
ODE 3 ................................................................................................................................... 114
14. SERIAL I/O ..................................................................................................................... 115
14.1 F
14.2 B
14.3 S
14.4 A
UNCTION DESCRIPTION .......................................................................................................... 115
AUD RATE GENERATION ......................................................................................................... 118
YNCHRONOUS OPERATION (MODE 0) ...................................................................................... 119
SYNCHRONOUS OPERATION ................................................................................................... 120
15. CPU TIMING ................................................................................................................... 130
15.1 O
15.2 I
15.3 E
15.4 E
SCILLATOR ............................................................................................................................ 130
NSTRUCTION TIMING ............................................................................................................... 131
XPANDED PROGRAM MEMORY TIMING .................................................................................... 132
XPANDED DATA MEMORY TIMING ........................................................................................... 135
16. PROGRAM LOADING .................................................................................................... 137
16.1 I
16.2 I
16.3 I
16.4 E
16.5 S
NVOKING THE BOOTSTRAP LOADER ......................................................................................... 137
NVOKING THE BOOTSTRAP LOADER ON DS5000 SERIES DEVICES ............................................ 138
NVOKING THE BOOTSTRAP LOADER ON DS5001/DS5002 SERIES DEVICES .............................. 138
XITING THE LOADER ............................................................................................................... 139
ERIAL PROGRAM LOAD MODE ................................................................................................. 141
3 of 187
Page 4

Secure Microcontroller User’s Guide
16.6 AUTO-BAUD RATE DETECTION ................................................................................................. 142
16.7 B
16.8 C
16.9 C
16.10 C
16.11 E
16.12 I
16.13 P
16.14 P
16.15 P
16.16 RPC
OOTSTRAP LOADER INITIALIZATION ......................................................................................... 142
OMMAND LINE INTERFACE ...................................................................................................... 143
OMMAND LINE SYNTAX ........................................................................................................... 143
OMMAND SUMMARIES ............................................................................................................ 145
RROR MESSAGES .................................................................................................................. 148
NTEL HEX FILE FORMAT .......................................................................................................... 149
ARALLEL PROGRAM LOAD OPERATION .................................................................................... 150
ARALLEL PROGRAM LOAD MODE ............................................................................................ 152
ARALLEL PROGRAMMING CONCERNS ...................................................................................... 153
PROGRAM MODE OPERATION .......................................................................................... 153
17. REAL-TIME CLOCK (RTC) ............................................................................................ 155
17.1 DS5000T/DS2250T
17.2 I
17.3 R
17.4 S
MPORTANT DS5000T/DS2250T APPLICATION NOTE ............................................................... 156
EGISTERS .............................................................................................................................. 160
PECIAL BITS ........................................................................................................................... 160
17.5 DS2251T/DS2252T
17.6 M
EMORY MAP .......................................................................................................................... 163
17.7 DS2251T/DS2252T
RTC ........................................................................................................ 155
RTC ........................................................................................................ 162
RTC INTERRUPTS .................................................................................... 166
18. TROUBLESHOOTING .................................................................................................... 176
18.1 U
18.2 DS5000T/DS2250T
18.3 RAM
18.4 U
18.5 S
18.6 P
18.7 D
NEXPLAINED DEVICE RESETS ................................................................................................. 176
REPORTS THE INCORRECT TIME/DATE ...................................................... 176
LOSES DATA WHEN POWERED DOWN .............................................................................. 177
NABLE TO INVOKE STOP MODE ............................................................................................... 177
ERIAL PORT DOES NOT WORK ............................................................................................... 177
ROGRAM WILL NOT EXECUTE ................................................................................................. 177
O’S AND DON’TS .................................................................................................................... 179
19. INSTRUCTION SET DETAILS ....................................................................................... 181
4 of 187
Page 5

Secure Microcontroller User’s Guide
LIST OF FIGURES
Figure 3-1. Secure Microcontroller Architectural Block Diagram .............................................................. 15
Figure 4-1. Secure Microcontroller Memory Map ..................................................................................... 18
Figure 4-2. Scratchpad Register Map ....................................................................................................... 20
Figure 4-3. DS5000 Series Memory Map ................................................................................................. 23
Figure 4-4. Partitionable Memory Map for DS5001/DS5002 Series ......................................................... 26
Figure 4-5. Nonpartitionable Memory Map for DS5001/DS5002 Series ................................................... 27
Figure 4-6. Peripheral Enables in the Data Memory Map......................................................................... 28
Figure 4-7. Reloading Portions of a DS5000 Series Device ..................................................................... 31
Figure 4-8. Reloading a DS5001/DS5002 Series Device ......................................................................... 33
Figure 4-9. DS5000 SFR Map .................................................................................................................. 34
Figure 4-10. DS5001/DS5002 SFR Map .................................................................................................. 35
Figure 5-1. Memory Interconnect of the DS5000FP ................................................................................. 51
Figure 5-2. DS5000 Series Module Block Diagram .................................................................................. 52
Figure 5-3. Memory Interconnect of the Partitionable DS5001/DS5002 ................................................... 53
Figure 5-4. Memory Interconnect of the Nonpartitionable DS5001FP, DS5002FP .................................. 54
Figure 5-5. Memory Interconnect Using the 128kB SRAM ....................................................................... 55
Figure 5-6. DS2251T-128 Block Diagram ................................................................................................ 56
Figure 5-7. DS2252T-32 Block Diagram .................................................................................................. 57
Figure 6-1. Power-Supply Slew Rate ....................................................................................................... 59
Figure 7-1. Secure Microcontroller Power Cycling Timing........................................................................ 65
Figure 7-2. Secure Microcontroller Power Management .......................................................................... 67
Figure 8-1. Timed Access ......................................................................................................................... 69
Figure 8-2. CRC Code Example ............................................................................................................... 73
Figure 9-1. DS5000 Software Encryption Block Diagram ......................................................................... 76
Figure 9-2. DS5002 Software Encryption Block Diagram ......................................................................... 77
Figure 9-3. Dummy Bus Access Timing ................................................................................................... 80
Figure 10-1. Power-On Reset Timing ....................................................................................................... 87
Figure 11-1. Interrupt Request Sources ................................................................................................... 95
Figure 11-2. Interrupt Acknowledge Sequence ........................................................................................ 98
Figure 12-1. Port 0 Functional Circuitry .................................................................................................. 100
Figure 12-2. Port 1 Functional Circuitry .................................................................................................. 100
Figure 12-3. Port 2 Functional Circuitry .................................................................................................. 101
Figure 12-4. Port 3 Functional Circuitry .................................................................................................. 101
Figure 12-5. Parallel Port Output Buffers (Ports 1, 2, and 3) .................................................................. 103
Figure 12-6. Use of the RPC Mode ........................................................................................................ 105
Figure 13-1. Timer/Counter Mode 0 and 1 Operation ............................................................................ 112
Figure 13-2. Timer/Counter Mode 2 Operation ...................................................................................... 113
Figure 13-3. Timer 0 Mode 3 Operation ................................................................................................. 113
Figure 14-1. Mode 0 Block Diagram And Timing .................................................................................... 122
Figure 14-2. Serial Port Mode 1 Block Diagram ..................................................................................... 123
5 of 187
Page 6

Secure Microcontroller User’s Guide
Figure 14-3. Mode2 and 3 Block Diagram .............................................................................................. 124
Figure 15-1. Crystal Connection ............................................................................................................. 130
Figure 15-2. Clock Source Input ............................................................................................................. 131
Figure 15-3. Bytewide RAM Instruction Execution Timing...................................................................... 133
Figure 15-4. Expanded Program Memory Fetch .................................................................................... 134
Figure 15-5. Expanded Data Memory Read ........................................................................................... 134
Figure 15-6. Expanded Data Memory Write ........................................................................................... 135
Figure 16-1. Invoking and Exiting the Loader on the DS5001/DS5002 Series ....................................... 140
Figure 16-2. Serial Load Configuration ................................................................................................... 141
Figure 16-3. Parallel Program Load Configuration ................................................................................. 150
Figure 16-4. Parallel Program Load Cycles ............................................................................................ 151
Figure 17-1. DS5000T/DS2250T Functional Block Diagram .................................................................. 155
Figure 17-2. DS5000T/DS2250T RTC Pattern Comparison Register .................................................... 157
Figure 17-3. DS5000T/DS2250T RTC Register Entry Flowchart ........................................................... 158
Figure 17-4. DS5000T/DS2250T RTC Registers ................................................................................... 159
Figure 17-5. Time Register Examples .................................................................................................... 161
Figure 17-6. DS2251T/DS2252T RTC Block Diagram ........................................................................... 163
Figure 17-7. DS2251T/DS2252T RTC Memory Map.............................................................................. 164
LIST OF TABLES
Table 4-A. Instructions That Affect Program Status Flag ......................................................................... 50
Table 7-A. Pin States in Idle/Stop Modes ................................................................................................. 63
Table 8-A. Timed-Access-Protected Control Bits ..................................................................................... 69
Table 10-A. SFR Reset States ................................................................................................................. 86
Table 12-A. Use of the RPC Mode ......................................................................................................... 105
Table 14-A. Serial Port Operating Modes ............................................................................................... 116
Table 14-B. Timer 1 Baud Rate Generation ........................................................................................... 119
Table 14-C. Serial I/O Operating Modes ................................................................................................ 126
Table 16-A. Serial Loader Baud Rates For Different Crystal Frequencies ............................................. 142
Table 16-B. 8751-Compatible Program Load Cycles ............................................................................. 152
Table 17-A. Alarm Mask Bit Operation ................................................................................................... 166
6 of 187
Page 7

Secure Microcontroller User’s Guide
1. INTRODUCTION
The secure microcontroller family is a line of 8051-compatible devices that use nonvolatile (NV) RAM
rather than ROM for program storage. NV RAM allows the design of a “soft” microcontroller that
provides many unique features for embedded system designers. The enhanced security features employed
by the secure microcontroller family protect the user-application software against piracy and tampering.
These devices offer varying degrees of security, ranging from simple access prevention to a full
encryption of program and data memory of the device. Attempts to gain access to protected information
result in the self-destruction of all data. The secure microcontroller family is the heart of a wide range of
security-critical applications such as electronic banking, commercial transactions, and pay-TV access
control, or any application that requires the protection of proprietary software and algorithms.
The secure microcontroller family is divided between chips and modules. The chips are monolithic
microprocessors that connect to a standard SRAM and lithium battery. The modules combine the
microprocessor with the SRAM and lithium battery in a preassembled, pretested module. Depending on
the specific configuration, modules are available in either 40-pin encapsulated DIP or SIMM module
format.
In addition to NV RAM, Maxim microcontrollers offer a number of peripherals that simplify and reduce
the cost of embedded systems. Although the specific features of each chip or module vary, all devices
offer the following basic feature set:
100% code-compatible with 8051
Directly addresses 64kB program/64kB data memory
Nonvolatile memory control circuitry
10-year data retention in the absence of power
In-system reprogramming via serial port
128 bytes fast access scratchpad RAM
Two 16-bit general-purpose timer/counters
One UART
Five interrupts with two external
Dedicated memory bus, preserving four 8-bit ports for general purpose I/O
Power-fail reset
Early warning power-fail interrupt
Watchdog timer
1.1 Important Notice Regarding Discontinued DS2251T/DS2252T
The DS2251T and DS2252T have been discontinued and are no longer available. They remain in this
document for historical purposes only, and any references to them should be ignored.
1.2 Software Security
One of the most important features of the secure microcontroller family is firmware/memory security.
The devices were specifically designed to offer an unprecedented level of protection to the userapplication software, preventing unauthorized copying of firmware and denying access to critical data
values. The use of RAM rather than the traditional ROM or EPROM for program storage increases the
security, since tampering with the system results in the loss of the RAM contents. Additional features
such as real-time high-speed memory encryption, generation of dummy addresses on the bus, and internal
storage of vector RAM increases the security of a secure microcontroller/microprocessor-based system.
7 of 187
Page 8

Secure Microcontroller User’s Guide
The DS5002FP secure microprocessor chip offers the highest level of security, with permanently enabled
memory encryption, an 80-bit random encryption key, and a self-destruct input for tamper protection. The
DS5000FP soft microprocessor chip and DS5000(T) and DS2250(T) soft microcontroller modules offer
lesser, but still substantial, protection with optional data encryption and a 48-bit encryption key.
Separate Address/Data Bus
Soft microprocessor chips provide a nonmultiplexed address/data bus that interfaces to memory without
interfering with I/O ports. This bytewide bus connects directly to standard CMOS SRAM in 32kB x 8 or
128kB x 8 densities with no glue logic. Note that this is in addition to the standard 8051 port 0 and 2
multiplexed bus. In module form, the bytewide bus is already connected directly to on-board SRAM, so
the memory access becomes transparent and the I/O ports are free for application use. The extra memory
bus also allows for a time-of-day function; all soft microcontroller modules are available with built-in
real-time clocks (RTCs). Battery backup and decoding is automatically handled by the microprocessor.
Large Nonvolatile Memory
Soft microprocessor chips provide nonvolatile memory control for standard CMOS SRAM. Modules
combine the microprocessor chip with memory and lithium backup. This includes conditionally writeprotected chip enables and a power-supply output that switches between +5V and battery backup. The
chip enables are decoded automatically based on user-selectable memory sizes and partitioning.
Partitioning defines the portion of memory used for program and data segments. Areas that are designated
program are always write-protected and are treated as ROM. Data areas are write-protected only when
power is out of tolerance. A large nonvolatile memory is useful for data logging and as flexible program
storage. Memory is retained for over 10 years at room temperature in the absence of power by ultra-lowleakage lithium-backed circuits.
In-System Loading
The in-system programming capability lets the user update program code at any time. This program
loading is supervised by a built-in ROM-based bootstrap loader. The ROM loader becomes transparent
once program loading is complete. All devices allow program loading via the serial port. Data memory
can also be retrieved using this loader function. Selected versions provide other parallel loading protocols
as well. In-system loading allows a system to be configured during final system test. A user can load
custom software, diagnostic routines, or calibration constants. If something changes or new features arise,
the system can then be reprogrammed while in the field.
High-Reliability Operation
Secure microcontroller devices are designed for unsupervised operation in remote locations. Special
features prevent a system from running out of control during transient events. These include a reset when
power is out of tolerance; an early warning power-fail interrupt that allows software to save critical data;
and a watchdog to reset the micro if it gets lost. Also, nonvolatile memory allows software to save the
operating state so a task can be resumed when power returns to normal. The secure microcontroller
family consists of three chips and their associated modules. Differences stem from I/O, memory access,
and security features. The DS5000FP is used in DS2250T and DS5000(T) modules. A full selector guide
with all memory and speed permutations is provided in the next section.
8 of 187
Page 9

Secure Microcontroller User’s Guide
1.3 Product Description
All secure microcontroller products have the following standard 8051 family features:
8051-compatible instruction set
Four 8-bit pseudo-bidirectional I/O ports
Two 16-bit timer/counters
Five interrupts with two external
Addresses 64kB program and 64kB data memory
128 bytes scratchpad RAM
One UART
DS5000FP Soft Microprocessor Chip
The DS5000FP is the original soft microprocessor chip. It adds the following features to the 8051 set:
Nonmultiplexed bytewide address/data bus for memory access
Nonvolatile control for 8kB x 8 or 32kB x 8 SRAMs
Partitions one SRAM into program and data areas and write protects the program segment
Decodes memory for up to two 32kB x 8 SRAMs (#2 is data memory only)
Power-fail reset and interrupt
Precision watchdog timer
ROM-based serial bootstrap loader
Optional security features
− Memory encryption in real-time
− 48-bit user selected encryption key
− Security lock destroys memory if unlocked
− Vector RAM hides 48 bytes on-chip
− Dummy operations on the memory bus
DS5000(T) Soft Microcontroller Module
The DS5000 incorporates the DS5000FP chip in a 40-pin module with an 8051 footprint and pinout.
Familiar 40-pin DIP package
Built-in NV RAM of 32kB x 8
I/O ports not disturbed by on-board memory access
10-year data retention and clock operation in the absence of power
Partitions memory into program and data areas, write protects the program segment
Power-fail reset and interrupt
Precision watchdog timer
ROM-based serial bootstrap loader
Optional memory security
Optional built-in RTC (battery backed)
DS2250(T) Soft Microcontroller Module
The DS2250(T) incorporates the DS5000FP chip on a 40-pin SIMM module. It has the identical feature
set as the DS5000(T), but is in a different form-factor. This package change allows up to 64kB NV RAM
instead of 32kB. Note that as mentioned above, the second 32kB is restricted to data memory. Like the
DS5000(T), this module guarantees better than 10-year data retention at room temperature.
DS5001FP 128kB Soft Microprocessor Chip
9 of 187
Page 10

Secure Microcontroller User’s Guide
The DS5001FP provides the base feature set of the DS5000FP with the following extras. Note that the
DS5001FP has no memory encryption feature.
Accesses up to 128kB on the bytewide bus
Decodes memory for 32kB x 8 or 128kB x 8 SRAMs
Four additional decoded peripheral-chip enables
CRC hardware for checking memory validity
Optionally emulates an 8042-style slave interface
Bandgap reference for more accurate power monitor
DS2251T 128kB Soft Microcontroller Module (Discontinued)
The DS2251T is a SIMM based on the DS5001. It provides up to 128kB of on-board NV RAM and has
the bytewide bus available at the connector. This is used with the decoded peripheral enables for
memory-mapped peripherals such as a UART o r ADC. The parallel-access RTC has interrupt capability.
Like the older versions, the DS2251T provides 10-year data retention, even in the largest memory
configuration.
DS5002FP Secure Microprocessor Chip
The DS5002FP is a highly secure version of the DS5001FP. It provides the operating features of the
DS5001FP, with the following enhancements to the DS5000 security features.
Security is active at all times
Improved memory encryption using an 80-bit encryption key
Automatic random generation of encryption keys
Self-destruct input for tamper protection
Optional top-coating prevents microprobe (DS5002FPM)
DS2252T Secure Microcontroller Module (Discontinued)
The DS2252T incorporates the DS5002FP on a 40-pin SIMM. This includes from 32kB to 128kB of
secure memory with an RTC. The memory is highly secure from tampering and from competitors. Like
other products in the family, the D2252T has a data retention period of over 10 years at room
temperature.
1.4 Introduction to the DS5250 High-Speed Secure Microcontroller
The highest performance, most secure microcontroller available is the DS5250 high-speed secure
microcontroller. A member of the High-Speed Microcontroller family, the DS5250 device is a security
and performance enhanced version of the DS5002FP with the following features. More information about
it can be found on our website, www.maximintegrated.com/DS5250.
Security Features
• Designed to meet the physical security requirements of FIPS140 and Common Criteria certifications
• SRAM technology allows rapid “zeroization” of secure information as a tamper response
• Microprobe shield triggers tamper response if cryptographic boundary pentrated
• Environmental sensors trigger tamper response detect out-of-range conditions
• The equipment enclosure can be monitored by tamper response inputs for added protection
• External memory bus protected by single or triple-DES encryption
• Modulo Arithmetic Accelerator (MAA) for up to 4096-bit (e.g., PKI)
• DES and 112-bit key triple-DES engines available for secret key cryptography
10 of 187
Page 11

Secure Microcontroller User’s Guide
Random number generator
•
• Firmware bootstrap loader resides in a 16kB factory-programmed ROM
8051 Compatible with Expanded Addressing
• 4-clock/machine cycle architecture (25MHz/6.25 MIPS)
• Contiguous address space accesses up to 4MB program + 4MB data external memory
• Four 8-bit ports, one 6-bit port
Advanced Features
• CRC-16/32 generator
• Secure bootstrap loader resides in a 16kB factory-programmed ROM
• RTC with alarm interrupt and wake-up
• 5kB internal SRAM (1kB can be used as a stack for high-level language support)
• Dual data pointers with increment/decrement
• Programmable length MOVX instructions
• Power-fail/power-on reset circuits
• Watchdog timer
11 of 187
Page 12

Secure Microcontroller User’s Guide
Soft Microcontroller
Module
Soft Microcontroller
Module
Soft Microcontroller
Module
Soft Microcontroller
Module
Soft Microcontroller
Module
2. SELECTOR GUIDE
The following configurations are available. Speeds are rated maximums, but all members of the secure
microcontroller family are fully static and can be run as slow as desired.
CHIP DESCRIPTION
DS5000FP Soft Microprocessor Chip 16 DS5000FP-16
DS5001FP 128kB Microprocessor Chip 16 DS5001FP-16
DS5002FP Secure Microprocessor Chip 16 DS5002FP-16
MODULE DESCRIPTION
MEMORY
(kB)
MAX SPEED
(MHz)
SPEED
(MHz)
PART
RTC PACKAGE PART
DS5000
DS5000T
DS2250
DS2250
DS2250T
32 16 No 40 DIP DS5000-32-16
32 16 Yes 40 DIP DS5000T-32-16
32 16 No 40 SIMM DS2250-32-16
64 16 No 40 SIMM DS2250-64-16
64 16 Yes 40 SIMM DS2250T-64-16
12 of 187
Page 13

Secure Microcontroller User’s Guide
3. SECURE MICROCONTROLLER ARCHITECTURE
The secure microcontroller family is based on an 8051-compatible core with a memory interface and I/O
logic build around it. In general, most architecture features are identical to standard 8051s and apply to all
members of the secure microcontroller family. Differences between versions are mentioned. This section
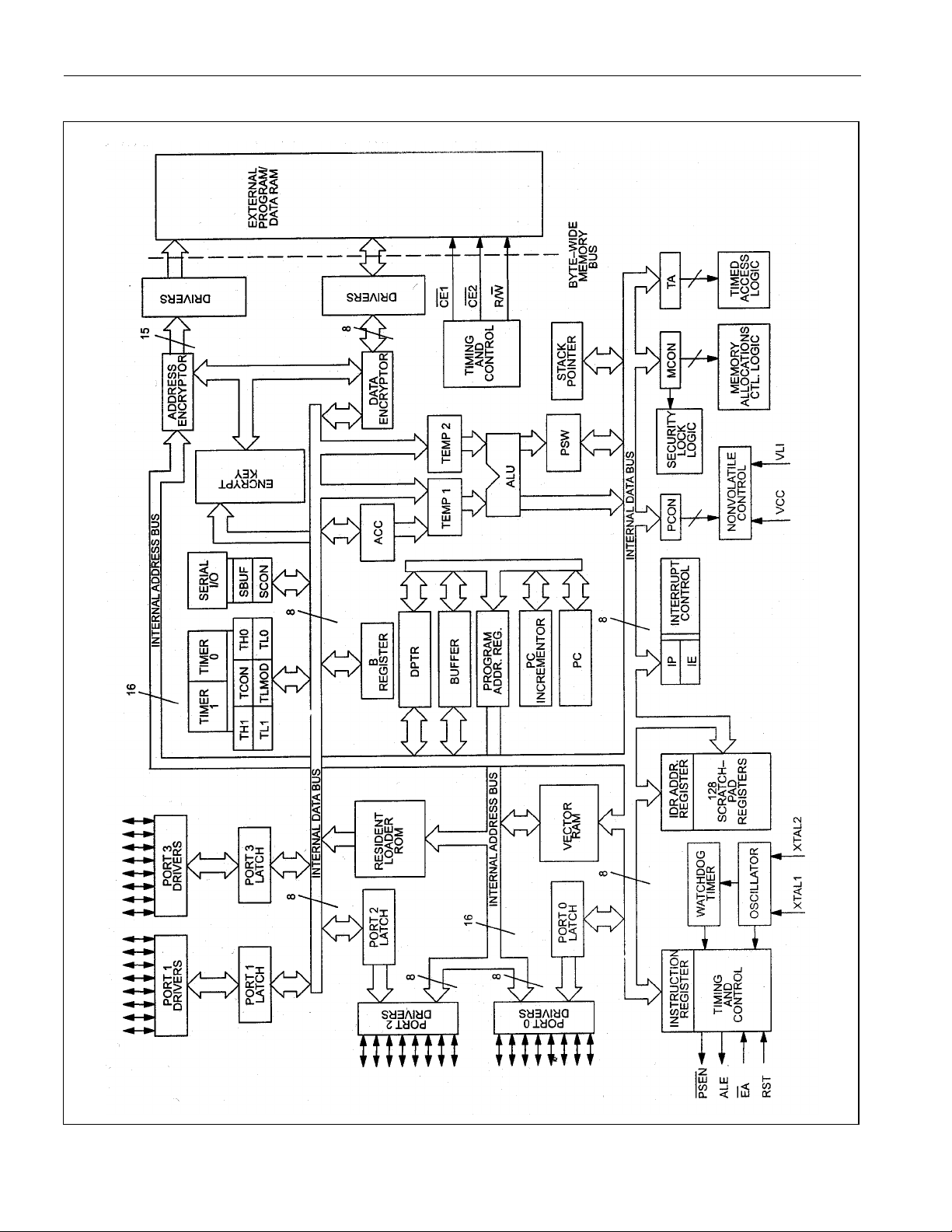
briefly documents the important features. Figure 3-1 shows a block diagram of the microcontroller core.
Users interested in a more thorough explanation of the 8051 architecture are referred to any of the
numerous texts on the subject.
3.1 Bus Organization
There are four major buses in the secure microprocessor: the internal data bus, the internal address bus,
the bytewide memory bus, and the expanded bus. All addresses and data that are transferred during
program execution are passed on the internal address and data buses. User program and data memory is
always accessed from either the bytewide program/data RAM or from external memory located on the
expanded bus. The bytewide memory bus allows access to program/data RAM in the same way as an
8051 family device would access internal ROM or EPROM memory. This bus can be used in place of the
expanded bus, freeing Port 2 and Port 0 pins for general I/O use.
3.2 CPU Registers
The CPU registers are mapped as special function registers (SFRs). They are identical in number and
function to those present within the 8051. These registers are described briefly:
Accumulator
The accumulator (A or ACC) is used as either a source and/or destination register in all arithmetic
instructions. It may also be used in most other types of instructions.
Stack Pointer
The stack pointer (SP) is an 8-bit register that marks the location of the last byte of data stored in the
stack. The stack itself can be located anywhere in the on-chip 128-byte scratchpad register area. The stack
pointer pre-increments during a stack push and post-decrements during a stack pop.
B Register
The major function of the B register is as a source and destination register during multiply and divide
instructions. It can also be used as a scratchpad register.
Program Status Word
The program status word (PSW) contains status flags that are set according to the results of a previously
executed instruction. In addition, the PSW contains register bank select bits.
Data Pointer
The data pointer (DPTR) is used to access data memory that can be mapped into bytewide data RAM or
onto external memory devices on the expanded bus. The DPTR is accessed by the user’s program as
either two 8-bit SFRs or as a 16-bit register with certain instructions.
13 of 187
Page 14

Secure Microcontroller User’s Guide
Scratchpad Registers
Scratchpad registers are 128 registers where data can be stored directly. They are addressed from 00H to
7FH and can be accessed by a MOV instruction. Included in the scratchpad area are four 8-byte banks of
working registers. These registers are not part of the data memory map.
Serial I/O
The on-chip serial I/O port is composed of a receive data buffer, a transmit data buffer, and a control
register. Both the receive data buffer and the transmit data buffer are accessed in a single location (SBUF)
in the SFR map. The control register (SCON) is accessed in a separate location. When the serial I/O
function is enabled, two external I/O pins (P3.0, P3.1) are reassigned in hardware to serve the transmit
and receive data functions.
Programmable Timers
Two 16-bit programmable timers are included that can perform various timing and counting functions.
Four registers (TH1, TL1, TH0, and TL0) access the upper and lower halves of each of the two
timer/counters. A single control register (TCON) is used to select the various operating modes of the two
timers. Two external I/O pins (P3.4, P3.5) can be programmed to serve as external counter inputs, one pin
for each of the two timer/counters.
14 of 187
Page 15
Secure Microcontroller User’s Guide
Figure 3-1. Secure Microcontroller Architectural Block Diagram
15 of 187
Page 16

Secure Microcontroller User’s Guide
Parallel I/O
Four SFRs provide access for the four parallel I/O port latches. These I/O ports are denoted as P0, P1, P2,
and P3. 32 bits of parallel I/O is available through these I/O ports. However, up to 16 bits are sacrificed
when the expanded bus mode is used to interface to external memory and up to 6 bits can be sacrificed if
any external interrupt inputs, timer counter inputs, or serial I/O functions are used. When using the
bytewide bus, ports are not affected.
Program/Data RAM Interface
Secure microcontrollers provide a nonmultiplexed bytewide bus that connects to external SRAM. They
also make this RAM nonvolatile, decode memory access for it, and write-protect portions designated as
program memory. The bytewide bus consists of up to 16 address lines (depending on the version), eight
data lines, read/write control, and decoded chip enables. When accessing the SRAM via its bytewide bus,
there is no activity on the ports. Thus if memory access is restricted to this bus, all ports are free for use
by the application. In module form, the microprocessor is already connected to SRAM via the bytewide
bus making program and data memory access appear internal. Secure microprocessors can also access
memory using the multiplexed expanded bus consisting of Port 0 and 2, WR (P3.6) and RD (P3.7) . This
is usually undesirable since it consumes port pins that can be used for other activity. If expanded bus
access is desired, up to 64kB ROM and 64kB RAM can be accessed in the same manner as a traditional
8051. Each version has different provisions for using the expanded bus, depending on memory map and
user’s configuration. These issues are discussed in the Programmer’s Guide in Section 4.
High-Reliability Circuitry
This feature ensures proper operation of the micro and maintains the contents of the program/data RAM
in the absence of V
using a self-contained lithium energy source. The logic provided includes the
CC
power-fail warning interrupt, automatic power-down and power-on reset. As a result, the program/data
RAM can be modified whenever necessary during execution of the user’s software but remains
unchanged when V
is absent. The circuitry also maintains the internal scratchpad RAM and certain
CC
SFRs during a power-down condition.
Software Encryption Logic
DS5000 and DS5002 series parts provide software security circuits that include the address encryptor,
data encryptor, and the encryption key word. When the device is operating in the encryption mode and
using the program/data RAM, the address encryptor is used to transform “logical” addresses on the
internal address bus into encrypted addresses that appear on the bytewide memory bus to the RAM.
Similarly, the data encryptor transforms data on the internal data bus into encrypted data during write
operations on the bytewide memory bus. When data is read back, the data encryptor restores it to its true
value. Although each encryptor uses its own algorithm for encrypting data, both depend on the encryption
key word stored on-chip.
Security Lock Logic
The security lock logic prevents a read or write to any program/data RAM location using the bootstrap
loader. In addition, it inhibits the device from fetching code in the expanded bus mode. By disabling
access to key internal resources, this feature precludes unauthorized disassembly of application software
contained in program/data RAM. In contrast with an EPROM security bit, clearing the security lock
wipes the entire RAM area.
16 of 187
Page 17

Secure Microcontroller User’s Guide
Vector RAM
The vector RAM is used to contain the reset and interrupt vector code when the soft microcontroller is
operating in the encryption mode. This feature is included to insure the security of the application
software. The operation of the vector RAM as well as the reason for its inclusion in the architecture are
discussed in Software Security in Section 1.1.
Timed-Access Logic
The timed-access logic protects against inadvertent changes to configuration and to the program RAM in
the event of a loss of software control. The protected configuration parameters include the partition
address bits in the MCON register as well as the enable watchdog-timer bit, stop mode bit, and power-on
reset bit in the PCON register.
Watchdog Timer
When the user’s software is being executed, the watchdog timer can be used to automatically restart the
processor in the event that software control is lost. It is also used to generate an oscillator start-up delay to
allow the clock frequency to stabilize. This occurs during reset cycles that follow a time in which the
oscillator has been stopped (stop mode reset and power-on reset).
Resident Loader ROM
The resident loader ROM contains firmware that controls the initial loading of the nonvolatile
program/data RAM. The firmware provides serial bootstrap load operation via the on-chip serial port. The
internal ROM is not accessible by the user and performs the loading function only when the device is
strapped for operation in the program mode. The ROM becomes transparent to the user once loading is
complete and has no affect on the memory map.
17 of 187
Page 18
Secure Microcontroller User’s Guide
SCRATCH PAD
SPECIAL
FFh
FFFFh--
0000
PROGRAM
64kB
DATA
INTERNAL REGISTERS
4. PROGRAMMER’S GUIDE
The secure microcontroller uses NV RAM technology for program and data memory. NV SRAM writeprotected memory segments are designated as program memory. The remaining RAM area is used as
nonvolatile data storage. One of the advantages of breaking a common RAM into two segments is that a
smaller number of memory chips is needed. For example, if a system requires 24kB of program memory
and 4kB of data memory, this all fits within one 32kB x 8 SRAM. The secure microcontroller can
subdivide this RAM into program and data segments, unconditionally write-protecting the program area.
The process of dividing the common memory space into ROM and RAM is called partitioning. The
original DS5000 series could partition one SRAM of up to 32kB. It could access a second RAM, but this
was restricted to data memory only. The DS5001/DS5002 series can partition two 32kB SRAMs, or even
one 128kB x 8 SRAM. Common elements of the programming model are detailed in the following
paragraphs, with individual differences highlighted.
4.1 Secure Microcontroller Memory Organization
Secure microcontrollers follow the standard 8051 convention of three memory areas. These include
internal registers, program memory, and data memory. These memory areas are not contiguous and are
accessed in different ways. The secure microcontroller duplicates all standard 8051 registers and adds
several new ones. They have a 64kB program and 64kB data space. However, secure microcontrollers
provide several ways to access these areas, and these features are what make the family unique.
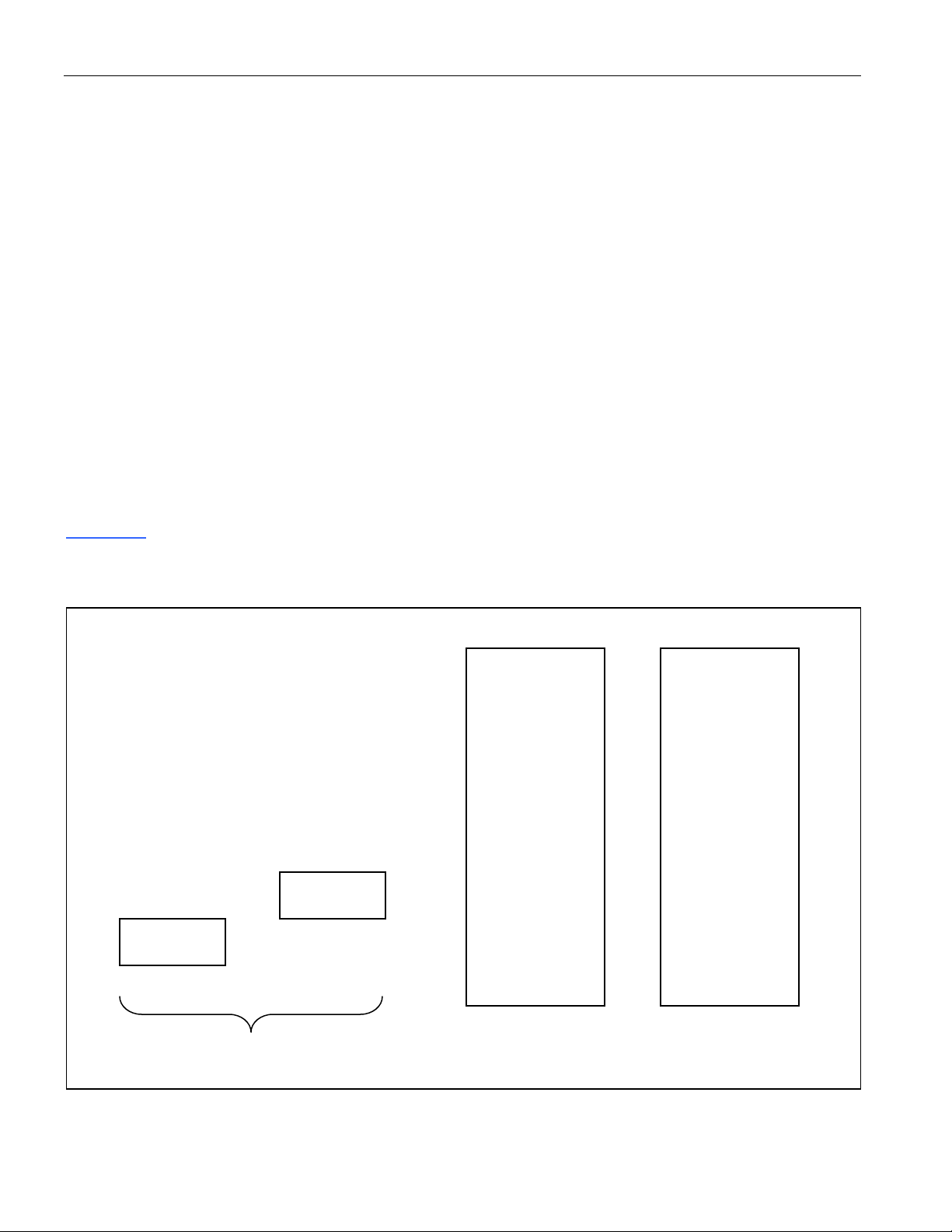
Figure 4-1 shows the memory map of secure microcontrollers in general terms. The specific details and
access to the memory areas are discussed below.
Figure 4-1. Secure Microcontroller Memory Map
7Fh
00
REGISTERS
FUNCTION
REGISTERS
MEMORY
MEMORY
18 of 187
Page 19
Secure Microcontroller User’s Guide
R1
R0
BANK STARTING ADDRESS (R0)
0
0
00h
0
1
08h
1
0
10h
1
1
18h
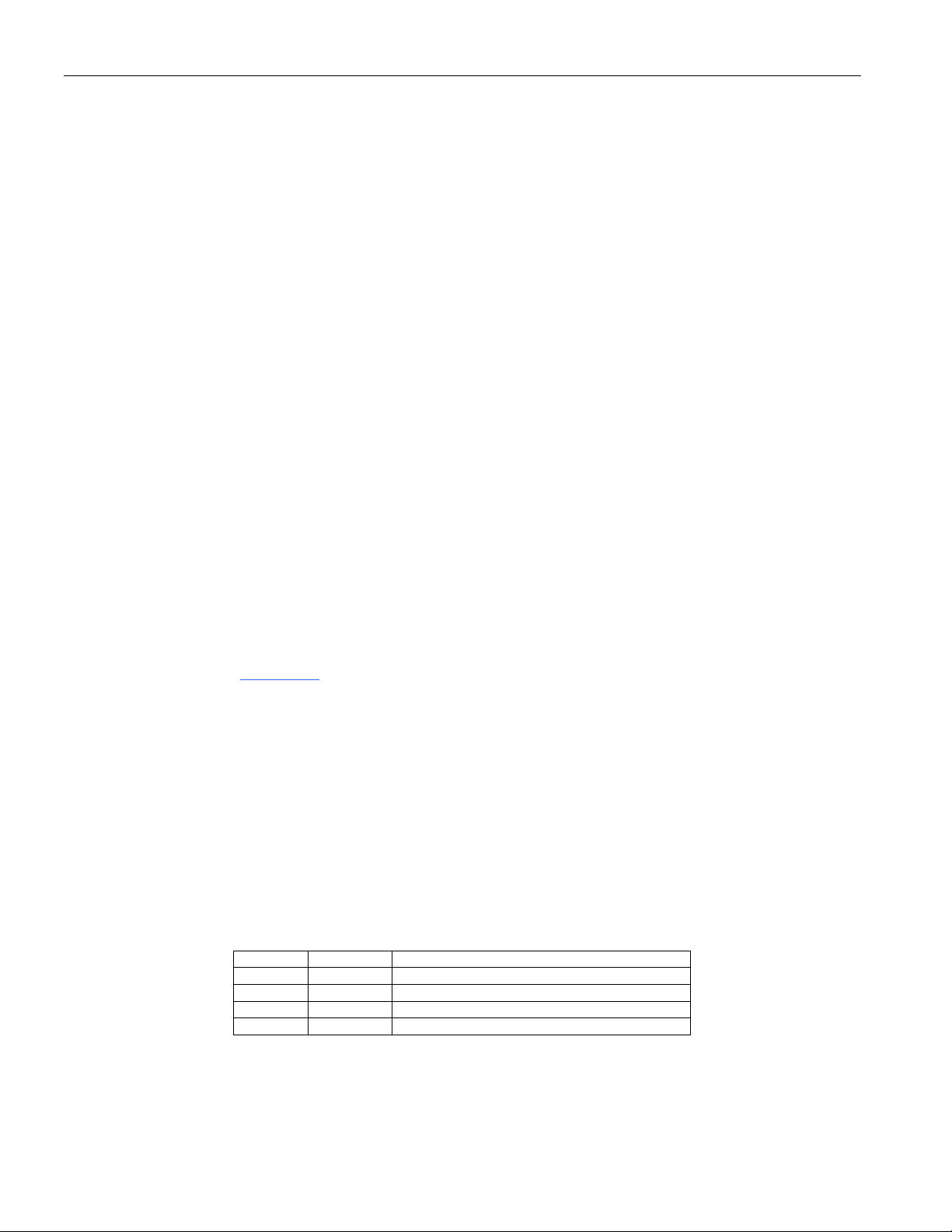
4.1.1 Internal Registers
The internal register space is divided into two parts. These are scratchpad registers and SFRs. There are
128 scratchpad registers, commonly referred to as on-chip RAM. The 128 bytes include four 8-byte banks
of working registers (R0–R7). The scratchpad registers are located at register addresses 00–7Fh. This area
is not located in the program or data memory area and is accessed by different instructions. The SFRs are
located between 80h and FFh. SFRs control the on-chip peripherals and memory configurations. Direct
addressing should be used to access the SFR locations. If register-indirect addressing is used,
indeterminate data is returned. Scratchpad registers are discussed immediately below, with SFR
descriptions following later in this section.
The scratchpad registers are general-purpose data storage RAM. They are commonl y used for temporary
storage of a small number of variables when high-speed access is needed. Off-chip RAM (MOVX) is
used when the quantity of data is larger than 128 bytes. The scratchpad registers are lithium backed and
are preserved in the absence of power.
The scratchpad area has two additional functions. First, 16 bytes of the scratchpad area are bit
addressable. That is, while each byte has an address of its own, these bits also have individual bit
addresses. Certain instructions operate on bits instead of bytes. Although the addresses appear the same,
the microprocessor can distinguish a bit address from a byte address by the instruction used. A large
number of individual software flags and conditions can be represented using 128 (16 x 8) individually
addressable bits.
A second use of the scratchpad area is for the programmer’s stack. Like the 8051, the secure
microcontroller uses a stack pointer (SP–81h) SFR to direct stack access into the internal registers. The
SP has a default value of 07h. This means that stack storage begins at location 08h. Each PUSH or CALL
instruction increments the SP. Note that while the SP is located in the SFR area, the stack itself is stored
in the scratchpad area. Figure 4-2
the use of C compilers becoming more frequent, the large memory model should be examined. This
compiler model places the stack in off-chip SRAM. Secure microcontroller-based systems usually have
an abundance of such SRAM compared to ROM based systems. While off-chip stack results in slower
execution time, the stack size becomes virtually unlimited.
The 8051 instruction set allows efficient (single cycle) access to variables when using the working
registers. These are a group of four 8-byte banks of scratchpad RAM. The active working registers are
referred to as R0–R7. They reside between location 00h and 1Fh, depending on which bank is currently
selected. Two bits in the SFR PSW, called R1 (PSW.4) and R0 (PSW.3), are used to determine which is
the active bank. Once selected, all instructions involving R0–R7 are directed to the selected group of 8
bytes. This scheme also allows for a fast context switch by simply changing banks. The following table
shows the operation of the register bank selection.
PSW.4-3; R1–R0
Register Bank Select Used to select an 8-byte bank of registers to be assigned as R0–R7.
shows the scratchpad register memory map. Programmer’s Note: With
19 of 187
Page 20
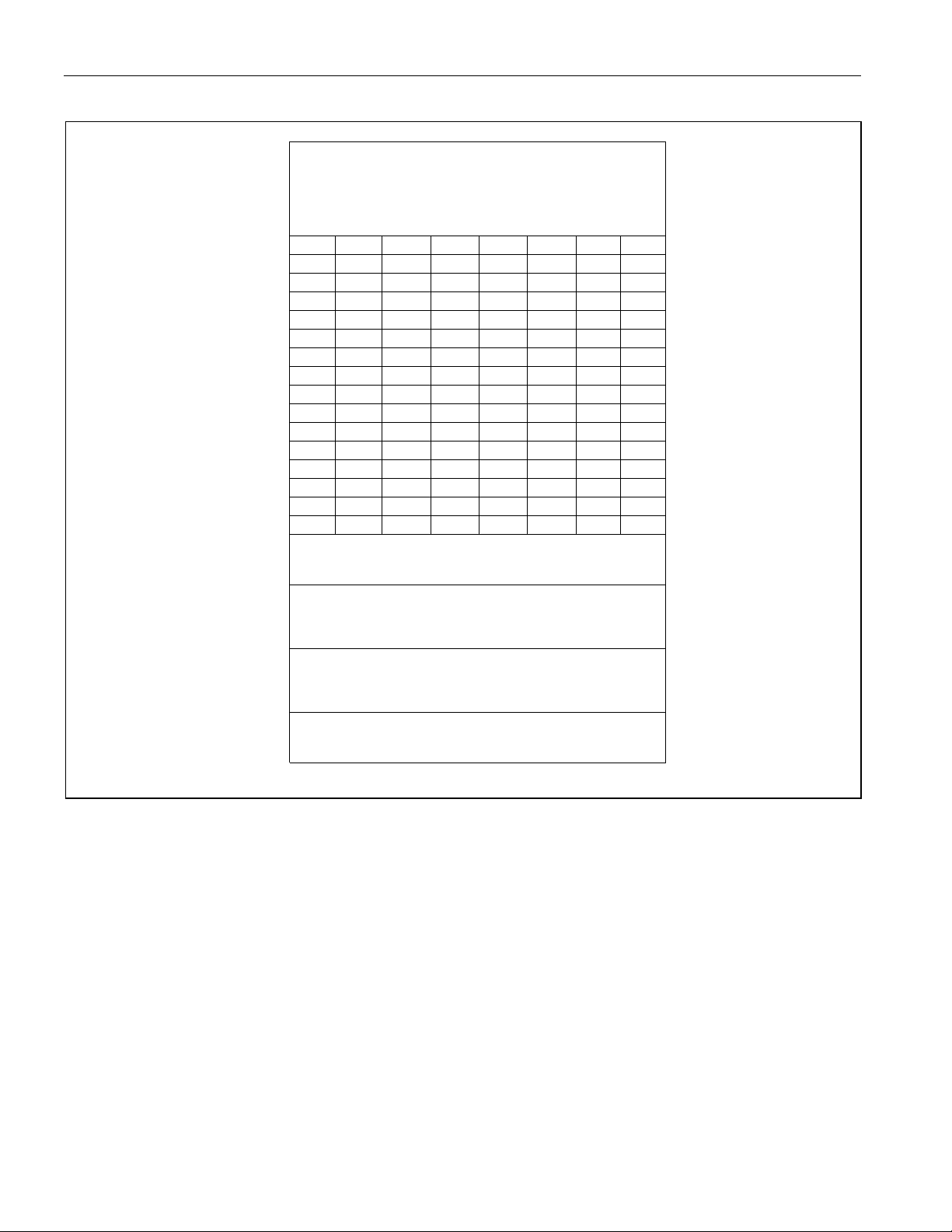
Figure 4-2. Scratchpad Register Map
7FH
2FH
7F
7E
7D
7C
7B
7A
79
78
2EH
77
76
75
74
73
72
71
70
2DH
6F
6E
6D
6C
6B
6A
69
68
2CH
67
66
65
64
63
62
61
60
2BH
5F
5E
5D
5C
5B
5A
59
58
2AH
57
56
55
54
53
52
51
50
29H
4F
4E
4D
4C
4B
4A
49
48
28H
47
46
45
44
43
42
41
40
27H
3F
3E
3D
3C
3B
3A
39
38
26H
37
36
35
34
33
32
31
30
25H
2F
2E
2D
2C
2B
2A
29
28
24H
27
26
25
24
23
22
21
20
23H
1F
1E
1D
1C
1B
1A
19
18
22H
17
16
15
14
13
12
11
10
21H
0F
0E
0D
0C
0B
0A
09
08
20H
07
06
05
04
03
02
01
00
1FH
18H
17H
10H
0FH
08H
07H
00H
MSB
LSB
≈
≈
Secure Microcontroller User’s Guide
BANK 3
BANK 2
BANK 1
BANK 0
4.1.2 Program and Data Memory
The secure microcontroller divides its main memory between program and data segments. Each map
consists of a 64kB area from 0000h–FFFFh. Program memory is inherently read-only, and data memory
is read/write. The CPU automatically routes program fetches to the program area and MOVX instructions
to the data memory area. All of these elements are in common with the standard 8051. Secure
microcontroller differences are in the memory interface, memory map control, and flexibility of the
memory resources.
Secure microcontrollers provide two separate buses for memory access. The first is a bytewide
address/data bus that is new to the 8051 architecture. This bus also provides a switched supply output that
makes standard SRAM into nonvolatile memory, decoded chip enables, and a R/W strobe. Furthermore,
the bytewide bus allows NV RAM memory to be divided between program and data segments. When
using a segment of the RAM as program memory, this area can be loaded using the bootstrap loader
function described later.
20 of 187
Page 21

Secure Microcontroller User’s Guide
CE1
CE1
CE2
CE2
CE1
CE2
CE2
CE1
CE2
CE1
The second bus is an expanded bus constituted by Ports 0 and 2. This is the standard 8051-compatible
memory bus that is available as an option, but is not needed in most cases. Program memory on the
expanded bus must be ROM/EPROM and data memory must be volatile SRAM. If NV RAM is needed
on the expanded bus, then it must be externally backed up and write protected. The secure microcontroller
makes no special provisions for NV RAM on the expanded bus. When discussing memory addressing of
secure microcontrollers, there are two important terms that are used frequently–partition and range. The
partition is the user-selectable address that divides the program segment from the data segment in a
common RAM area on the bytewide bus. The partition is a user-adjustable boundary that can be selected
during bootstrap loading or on the fly by the application software. The range is the total amount of
memory connected to the bytewide bus. This is set once during initial programming.
The DS5000 series devices can access up to 8kB and 64kB of NV RAM on the bytewide bus. Up to the
first 32kB are partitionable into program and data segments as described above. The DS5001/DS5002
series can access between 8kB and 128kBs on its bytewide bus with better partition control. The memory
map control resides in the MCON (address C6h) SFR on DS5000 devices. The DS5001 devices use the
MCON (address C6h) and RPCTL (address D8h) registers. Since the memory maps and control have
significant differences between these versions, they are described later in separate sections.
4.2 DS5000 Series Memory Organization
As mentioned above, the DS5000 series consists of the DS5000FP chip and the DS5000(T) and DS2250T
modules. The programming model discussed in this section applies to all of these parts. The DS5000FP
bytewide bus has 15 address lines, eight data lines, a R/W strobe, and two chip enables to access NV
RAM. In the case of a module, these are already connected and can be thought of as internal or embedded
memory. The DS5000 series can use either 8kB x 8 or 32kB x 8 SRAMs, selected using the range bit
(MCON.3) and has a value of 0 when 8kB SRAM is used and 1 when a 32kB SRAM is use d. Range is
selected during bootstrap loading and cannot be varied by the application software. The DS5000FP
accesses memory on its bytewide bus using two chip enables. The first,
RAM connected to
, whether 8kB or 32kB, can be divided between program and data segments. The
, is partitionable. That is, the
partition is user-selected and can be set during bootstrap loading and by software. Partitions are available
on 2kB boundaries in the DS5000, except for the last, which is 4kB. The partition is selected using the
MCON SFR described below.
same size as
. Access to
is restricted to data memory only. The RAM on
should be of the
is controlled by ECE2 bit (MCON.2) and is described below.
Figure 4-3 illustrates the functional memory map of a DS5000 series device. The partition, range, ECE2,
and the logical address combine to determine whether the DS5000 uses its bytewide bus or the expanded
bus. NV RAM access occurs when the logical address lies in one of the shaded regions. These are
program addresses below the partition address, data addresses above the partition and below the range
address, or data addresses between 0 and the range when ECE2 is set to a logic 1. Note that when using
ECE2 to force data access, the
DS5000 module or a DS2250 with less than 64kB RAM, no data memory exists under
has no affect on program memory, which continues from the
RAM is selected instead of the
RAM or the expanded bus normally.
RAM. This means that on a
. The ECE2
Note that the partition and range settings are not automatically linked, allowing a user to accidentally
select a partition that is larger than the range. When the range is 32kB, the partition address can be as high
as 32kB. When a range of 8kB is used, partition addresses below 8kB should be used. Any address that
does not map onto the bytewide bus is automatically routed to the expanded bus of Ports 0 and 2. For
module users, this means that any address not routed to internal memory goes to the ports.
21 of 187
Page 22

Secure Microcontroller User’s Guide
When the partition is at 3000h and the range at 32kB, program memory below 3000h is acce ssed on the
bytewide bus. Program memory at or above 3000h is directed to the expanded bus or Ports 0 and 2. When
the partition is at 5800h and the range at 32K, data memory at 0000h is accessed on Ports 0 and 2. Data
memory at 6000h is located in NV RAM on the bytewide bus. When the partition is at 1000h and the
range at 8kB, all memory access above 1FFFh is on the expanded bus. The partition rules apply when the
range is below 8kB.
Important Application Note
The MCON register is an SFR unique to Maxim microcontrollers that contains nonvolatile memory
configuration information. This register should be set to the desired value before loading the device via
the bootstrap loader. Failure to correctly configure the MCON register can cause the device to operate
incorrectly, including symptoms that appear similar to a defective device. Because this register is
nonvolatile, incorrect memory settings will be preserved when power is removed. The DS5001FP,
DS5002FP, DS2251T, and DS2252T store additional memory configuration information in the RPCTL
register, which should also be set to the desired value before loading the user program via the bootstrap
loader.
Figure 4-3 illustrates the typical operation. There are two conditions that can modify this memory map.
The first is the EA pin. The second is the security lock. When the EA pin is grounded, the DS5000 forces
all memory access to the expanded bus. This causes the DS5000 to behave like an 8031, regardless of the
partition, range, or ECE2. The EA should be pulled to +5V for normal operation. The second modifier is
the security lock. When set, the security lock prevents the bootstrap loader from reading the contents of
the NV RAM. For security purposes, it also prohibits program memory access on the expanded bus.
Thus, all program fetches must be restricted to the bytewide bus when locked. The security lock overrides
the condition of the EA pin as well.
These memory map controls provide unprecedented flexibility to configure a system. However, it is
possible to select contradictory settings. The partitioning function allows a user to select the quantity of
program and data memory. It is possible to select all data and no program in NV RAM by choosing a
partition of 0000h. This is a valid selection, except when the security lock is set, as it simultaneously
configures and prohibits the use of program memory on the expanded bus. In this illegal event, special
circuits will automatically force the partition to a location of 7FFFh. This means all 32kB memory on the
bytewide bus is designated program memory. The second contradictory case is to select a range of 8kB,
and to choose a partition of greater than 8kB. This results in the range as the limiting factor. Addresses
above the range are automatically deflected to the expanded bus. No data memory is allocated in NV
RAM for this configuration.
22 of 187
Page 23
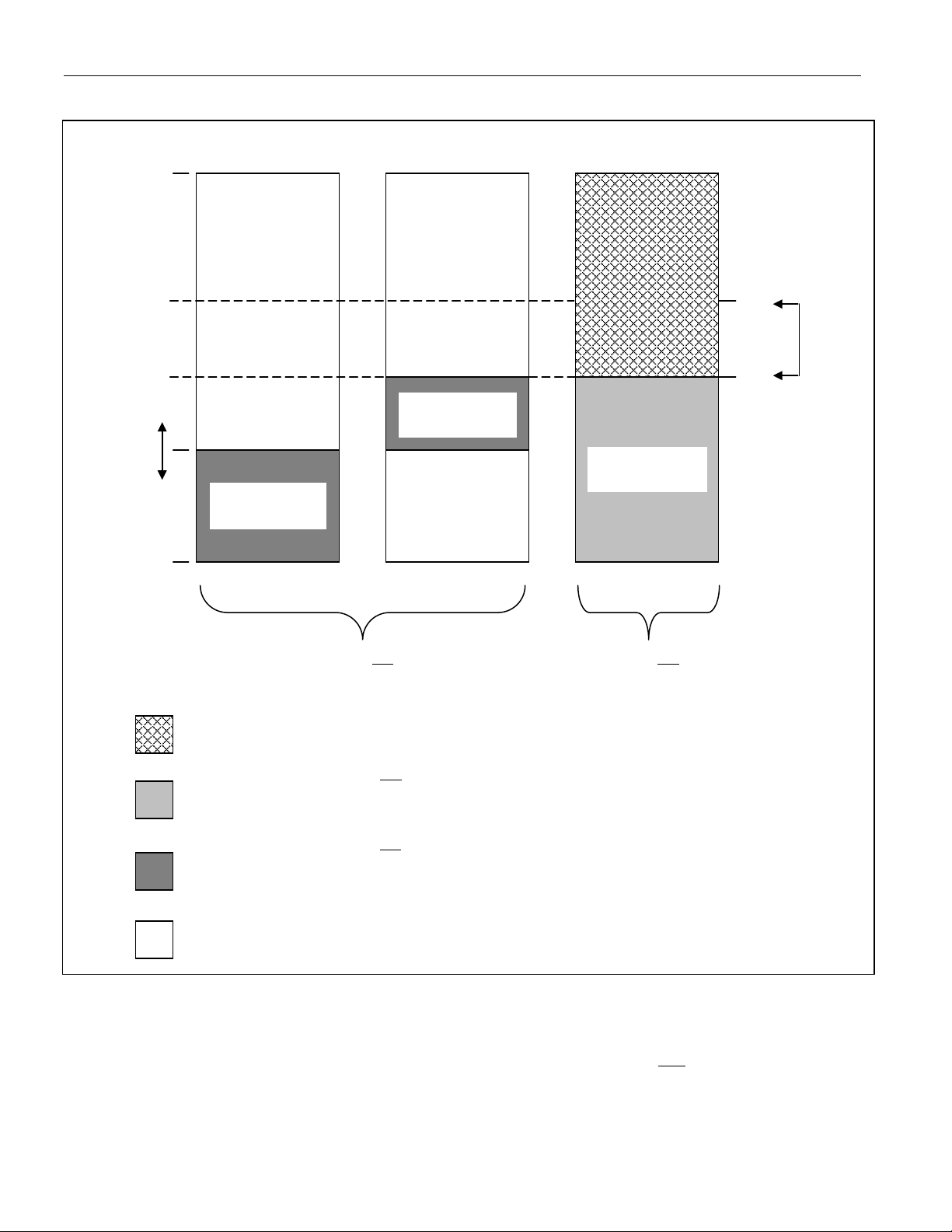
Figure 4-3. DS5000 Series Memory Map
CE2
32kB
RANGE
FFFFh
7FFFh
1FFFh
0000
PARTITION
ADDR.
ECE2=0
ECE2=1
BYTEWIDE
BYTEWIDE
BUS ACCESS
PROGRAM
DATA
DEVICE #1 SELECTED
WITH
CE1
BYTEWIDE
BUS ACCESS
DATA
DEVICE #2 SELECTED
WITH
CE2
64kB
= NO MEMORY ACCESS
CE2
CE1
4.3 DS5000 Memory Map Control
BUS ACCESS
MEMORY
= BYTEWIDE ACCESS WITH
(NV RAM)
= BYTEWIDE ACCESS WITH
(NV RAM)
= EXPANDED BUS ACCESS ON PORTS 0 AND 2
MEMORY
Secure Microcontroller User’s Guide
8kB
MEMORY
ADDR.
The partition and range can be selected using the bootstrap loader discussed in a later section. In addition,
the partition can be selected or modified by the application software and
controlled. However, in either case, the MCON SFR is used to choose these settings. The MCON register
is described fully in the SFR description section.
is normally software
23 of 187
Page 24
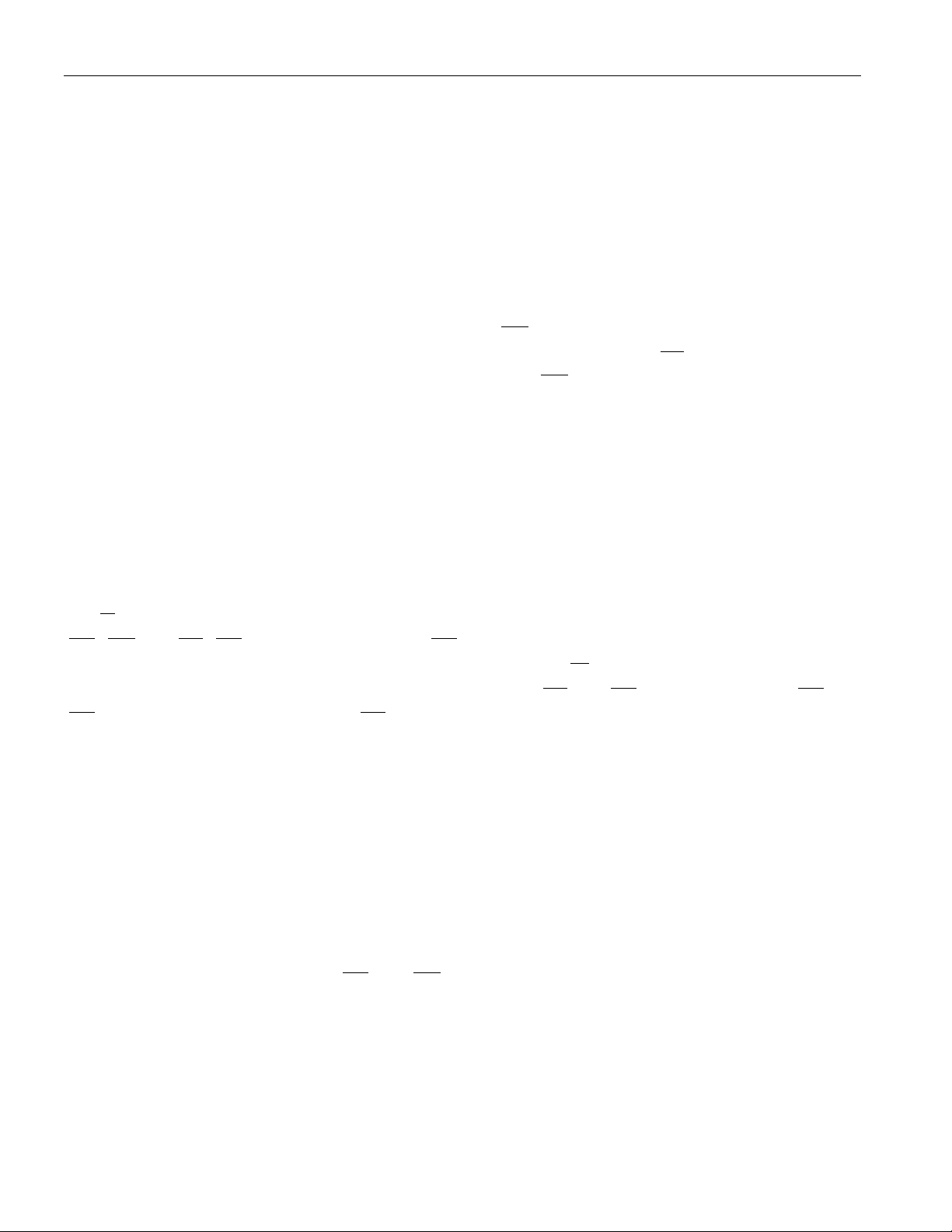
Secure Microcontroller User’s Guide
CE2
CE1
CE2
W
CE1
CE4
PE1-PE4
CE1
PE1
PE2
PE3
PE4
PE1
CE1
CE2
DS5000 SERIES MCON REGISTER
MCON.7–4 PA3–0
Partition Address Use to select the starting address of data memory in embedded RAM. Program
space lies below the partition address.
MCON.3 RA32/8
Range Address Sets the maximum usable address on the bytewide bus. RA32/8 = 0 sets range
address = 1FFFH (8kB); RA32/8 = 1 sets range address = 7FFFH (32kB)
MCON.2 ECE2
Enable Chip Enable 2 Used to enable or disable the
When ECE2 = 0, all MOVX instruction s activat e the
all MOVX instructions activate the
to 0 in the DS5000-8, DS5000-32, DS2250-8, and DS2250-32 modules.
MCON.1 PAA
Partition Address Access Used to protect the programming of the par titio n address s elect bit s. PA3–0 cannot
be written when PAA = 0. PAA can be written only via the timed-access register.
signal to additional RAM data memory space.
signal. When ECE2 = 1,
signal. Thi s bit should always be cleared
4.4 DS5001/DS5002 Memory Organization
Note that the DS5002FP is a high-security version of the DS5001FP, but has the same memory map and
I/O. The programming model discussed in this section applies to all of these parts and any reference to
the DS5001 applies to all of them. The DS5001 series bytewide bus has 16 address lines, eight data lines,
a R/
strobe, and a total of eight chip enables to access NV RAM and peripherals. Chip enables include
-
and
. The four chip enables (
-4) are for NV RAM access. How they are connected
depends on the memory mode and the selection of SRAMs. The PE signals are generally for memorymapped peripherals, but can be used for more RAM if desired.
are not. In the case of a module,
may be connected to a RTC. Memory map control resides in
and
are lithium-backed,
and
the MCON (C6h) and RPCTL (D8h) registers. The MCON register has selected differences from its
DS5000 counterpart. These are documented below. The RPCTL is not present in the DS5000. Also, not
all of the bits in this register pertain to memory map control. This section describes the relevant bits and
the SFR section below documents the entire register.
The DS5001/DS5002 series can use multiple 8kB x 8 or 32kB x 8 SRAMs or a single 128kB x 8 SRAM.
These parts can operate in either a partitionable (like DS5000) or nonpartitionable mode. The mode is
selected via the PM (MCON.1) bit of the MCON register. Note that the DS5001 MCON provides
different functions than the DS5000. In partitionable mode (PM = 0), the DS5001/DS5002 can use up to
64kB x 8 SRAM for program and data on its bytewide bus. It can partition this area into program and data
segments on 4kB boundaries. The 64kB memory space would consist of two 32kB x 8 SRAMs. Each is
accessed by a separate chip enable (
and
), but the microcontroller automatically decodes which
is needed.
While the DS5001/DS5002 can use between one 8kB x 8 SRAM and four 32kB x 8 SRAMs, it does not
automatically know which configuration is used. The user must identify the total RAM size using the
range bits RG1 and RG0. RG1 is located at MCON.3 and RG0 is located at RPCTL.0. These range bits
24 of 187
Page 25

Secure Microcontroller User’s Guide
RANGE
(kB)
CE1
CE2
1 1 64
0000–7FFFh
8000–FFFFh
1 0 32
0000–7FFFh
NA
0 1 16
0000–1FFFh
2000h–3FFFh
0 0 8
0000–1FFFh
NA
CE1
0 0 0 0 0000h
0 Program, Data = Range
0 0 0 1 1000h
4kB Program, Data = Range – 4kB
0 0 1 0 2000h
8kB Program, Data = Range – 8kB
0 0 1 1 3000h
12kB Program, Data = Range – 12kB
0 1 0 0 4000h
16kB Program, Data = Range – 16kB
0 1 0 1 5000h
20kB Program, Data = Range – 20kB
0 1 1 0 6000h
24kB Program, Data = Range – 24kB
0 1 1 1 7000h
28kB Program, Data = Range – 28kB
1 0 0 0 8000h
32kB Program, Data = Range – 32kB
1 0 0 1 9000h
36kB Program, 28kB Data
1 0 1 0 A000h
40kB Program, 24kB Data
1 0 1 1 B000h
44kB Program, 20kB Data
1 1 0 0 C000h
48kB Program, 16kB Data
1 1 0 1 D000h
52kB Program, 12kB Data
1 1 1 0 E000h
56kB Program, 8kB Data
1 1 1 1 FFFFh
64kB Program, 0kB Data
are selected during the bootstrap loading process and cannot be modified by the application software. The
table below shows the range values that can be selected when PM = 0 (partitionable).
RG1 RG0
ACCESS
ACCESS
The total RAM space is partitionable, regardless of which range is selected. This contrasts with the
DS5000 that allowed partitioning of
only (see the following partition table). PA3–0 are the four
MSBs of the MCON register (MCON.7-4). Note that the partition values do not scale depending on
range. That is, if a range of less than 64kB is selected, the partition settings above the range should not be
unused. The microcontroller automatically decodes which RAM to enable, and uses the partition to
decide if this is program memory or data memory.
Partition Table
PA3 PA2 PA1 PA0 PARTITION BYTEWIDE BUS MEMORY MAP
Figure 4-4 illustrates the functional memory map of a DS5001/DS5002 series device in partitionable
mode. Note that any access that does not correspond to a bytewide bus location is routed to the expanded
bus Ports 0 and 2.
25 of 187
Page 26
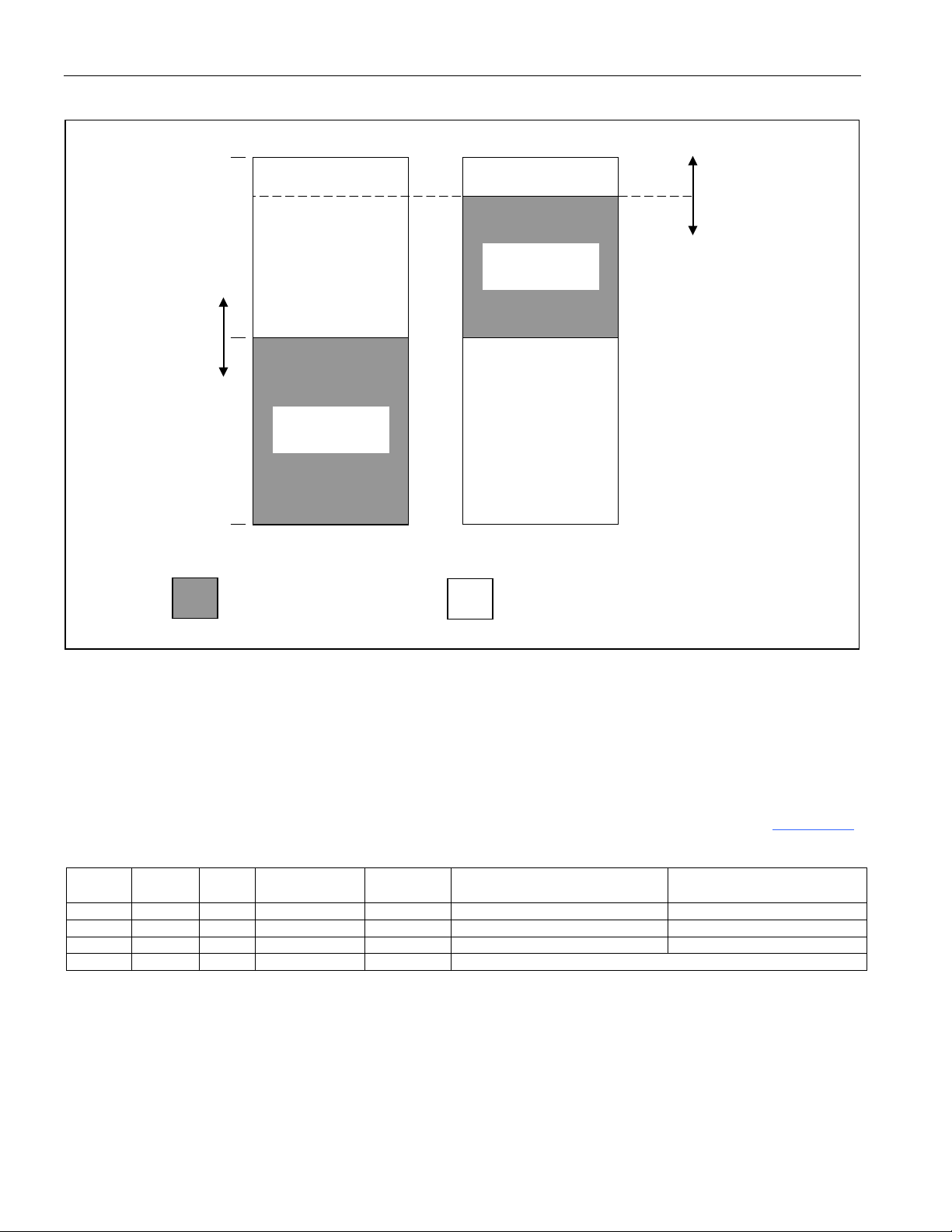
Secure Microcontroller User’s Guide
PROGRAM
(kB)
DATA
(kB)
1 0 0
32
64
1 at 32kB, CE1
2 at 32kB, CE3 and CE4
1 0 1
64
32
2 at 32kB, CE1 and CE2
1 at 32kB, CE3
1 1 0
64
64
2 at 32kB, CE1 and CE2
2 at 32kB, CE3 and CE4
0 1 1
64
64
1 at 128kB x 8, for both program and data
PES = 0
BYTEWIDE
BYTEWIDE
RANGE
64kB
PARTITION
ADDRESS
FFFFh
0000
PROGRAM
DATA
= BYTEWIDE ACCESS = EXPANDED BUS ACCESS ON PORT 0/2
Figure 4-4. Partitionable Memory Map for DS5001/DS5002 Series
BUS ACCESS
BUS ACCESS
MEMORY
MEMORY
(NV RAM)
The nonpartitionable mode allows the maximum amount of memory to be used on the bytewide bus. A
nonpartitionable mode would be used because the 8051 architecture is restricted to 64kB program and
64kB data (without bank switching). This means that if the maximum amount of either program or data
(or both) is needed, partitioning cannot be done. The DS5001/DS5002 series accommodates these
situations with four selections of nonpartitionable (PM = 1) memory control (see table below). These are
selected using the range bits when PM = 1. Also note the MSEL pin on DS5001/DS5002 series devices
that tells the processor whether multiple 32kB RAMs (MSEL = 1) or a 128kB RAM (MSEL = 0) is being
used. The four selections are as follows. The nonpartitionable memory map is shown in Figure 4-5
Bytewide bus segments begin at 0000h.
MSEL RG1 RG0
PROGRAM ACCESS DATA ACCESS
ADDRESS
.
Any address that does not fall into the bytewide bus are a is routed to the expanded bus of Ports 0 and 2.
This could only occur for the first two settings. Note that a single 128kB device is the least expensive in
terms of component cost and size. In this case, all memory addressable by the DS5001 is stored in a
nonvolatile 128kB x 8 SRAM. When the MSEL pin = 0, and RG0 = RG1 = PM = 1, the device
automatically converts CE1 to a chip enable, CE2 to A16, CE3 to A15, and CE4 is unused. The MSL bit,
accessible only via the bootstrap loader, selects whether the loader addresses the 64kB data or 64kB
program segment.
26 of 187
Page 27
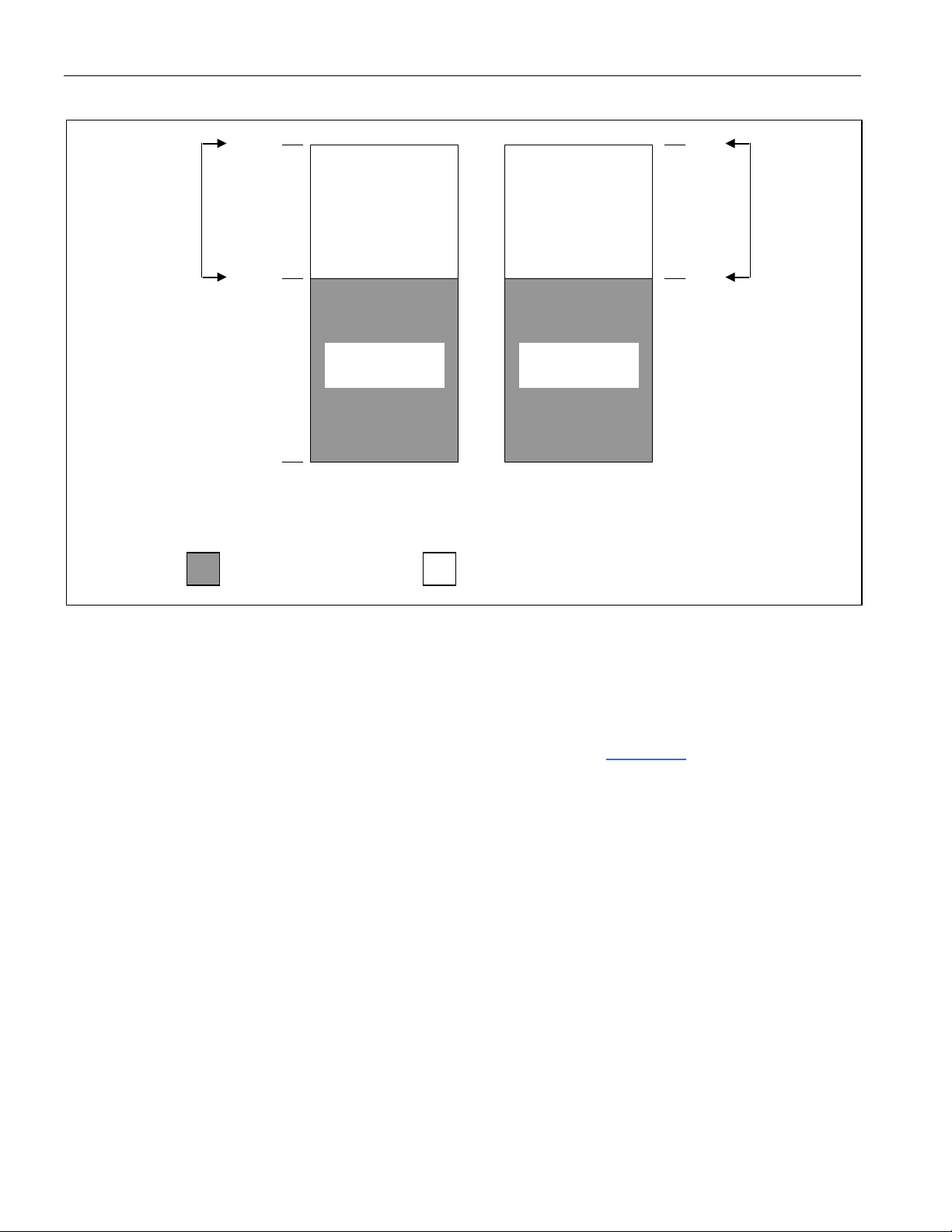
Secure Microcontroller User’s Guide
BYTEWIDE
BUS ACCESS
BYTEWIDE
BUS ACCESS
FFFFh
7FFFh
0000
64kB
32kB
PROGRAM
DATA
PROGRAM
DATA
RANGE
PES=0
= BYTEWIDE ACCESS
= EXPANDED BUS ACCESS ON PORTS 0 AND 2
Figure 4-5. Nonpartitionable Memory Map for DS5001/DS5002 Series
RANGE
(NV RAM)
MEMORY
MEMORY
4.5 DS5001/DS5002 Memory-Mapped Peripherals
The DS5001FP and DS5002FP provide four peripheral chip enables (PE4–PE1) designed to access
unencrypted peripherals on the bytewide bus. While PES = 1, all MOVX-based instructions present
unencrypted address and data on the bytewide bus. During these instructions the device asserts peripheral
chip-enable signals instead of the standard chip-enable signals based on the logical address. The
peripheral chip enables are decoded on 16kB boundaries, as shown in Figure 4-6
. The PES bit operates
the same way in both partitionable and nonpartitionable modes.
The peripheral enables interfaced to battery-backed and nonbattery-backed peripherals. The lowest two
peripheral enables, PE1 and PE2, are battery backed by the DS5001/DS5002. This means that when VCC
is removed, the device drives these chip enables to a logic high inactive state. These signals should be
interfaced to SRAM and other devices that are battery backed. The upper two peripheral enables, PE3 and
PE4, are not battery backed by the DS5001/DS5002. This means that when VCC is removed, the device
allows these signals to float to an undefined state. These signals should be interfaced to ADCs, UARTs,
and any other peripheral that is powered by VCC rather than V
CCO
.
A novel use of the PES signals is to double the available MOVX memory space. When set, the PES bit in
essence creates an overlay of 64kB, using the same MOVX addresses. By toggling the PES bit on and off,
the device can access up to 128kB of MOVX memory.
On occasion, a memory-mapped peripheral is needed that interfaces directly to an 8051 multiplexed bus.
When this occurs, MOVX instructions can be forced to use the expanded bus in any mode with the EXBS
bit (RPCTL.5). Setting this bit to logic 1 forces all MOVX instructions to the expanded bus. While EXBS
27 of 187
Page 28
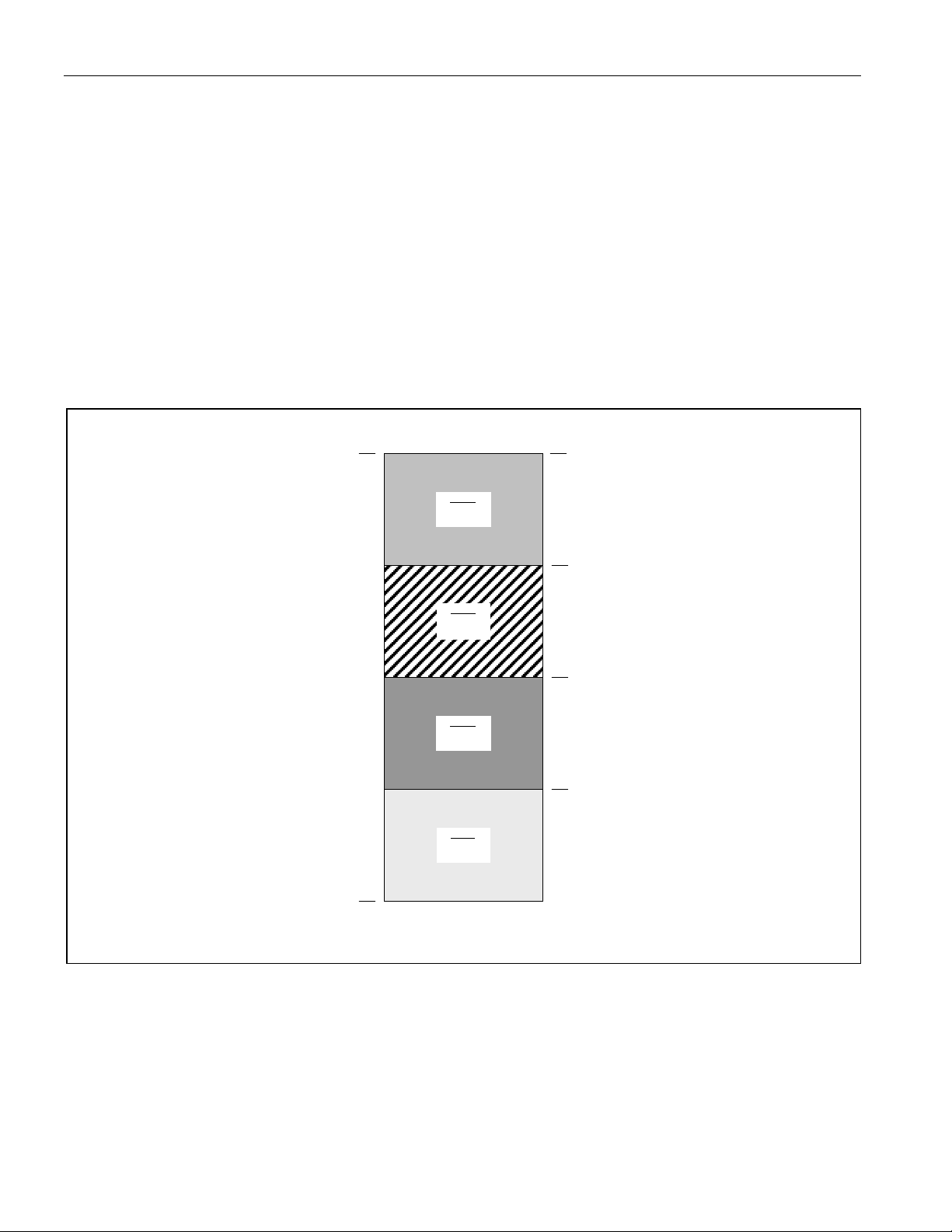
Secure Microcontroller User’s Guide
PE4
PE3
PE2 PE1
DATA
MEMORY
PES=1
FFFFh
BFFFh
7FFFh
3FFFh
64kB
0
= 1, the entire 64kB data memory map is accessed in this way. Clearing EXBS causes the microcontroller
to revert to its selected configuration. In most systems, the EXBS bit is not used.
4.6 DS5001/DS5002 Memory Map Control
Like the DS5000, the DS5001/DS5002 uses SFRs to control the memory map. The memory control
functions include the partition, range, partition mode (PM), expanded bus select (EXBS), peripheral
enable select (PES) and access enable (AE). The partition and range can be selected using the bootstrap
loader discussed in a later section. In addition, the partition can be selected or modified by the application
software by writing to the MCON register. PES is normally used by software and is also controlled by the
MCON register. The range is controlled by a combination of MCON and RPCTL bits. In addition, the
EXBS and AE are controlled using the RTPCL register. MCON and RPCTL are fully documented in the
SFR summary.
Figure 4-6. Peripheral Enables in the Data Memory Map
4.7 Loading and Reloading Program Memory
Soft microcontrollers are programmed through their integral bootstrap loader feature. This loader is also
used to configure the desired options for memory map control. The secure microcontroller uses its low
power lithium-backed circuits to ma intain critical settings in the absence of power. For this reason, it is
unnecessary to set the partition, range, etc. after every power-up or reset. Once set, they will remain
unless deliberately modified. Bootstrap loading is discussed in a later section. One of the major
28 of 187
Page 29

Secure Microcontroller User’s Guide
advantages of a secure microcontroller is the ability to change these settings, and even reload the entire
program memory while the device is installed in system. To completely re-program and re-configure a
device, the bootstrap loader must be invoked. However, the secure microcontroller is designed to allow a
partial reload of memory without invoking the bootstrap loader.
The major advantage of this technique is that it requires no hardware or external switches. Most of the
memory can be reprogrammed under application software control. It would commonly be used when the
target system connects to a PC through a serial port as part of an application, e.g., a data logger that must
dump memory periodically. While connected to the PC, it is extremely easy to reload portions of memory
using the “soft reload.”
Application software always has unrestricted read/write access to the NV RAM designated as data
memory. This is the memory that lies above the partition address and below the range address (the
nonpartitionable configuration of the DS5001/DS5002 is addressed separately). Data memory is read or
written using MOVX instructions. Only the area designated as program memory cannot be altered. The
key to doing a soft reload is to temporarily change the program memory RAM into data memory. Using
an SFR, the application software can authorize the secure microcontroller to temporarily redefine a
portion of the program memory area as data memory. Once this is done, the new code can be received
through a serial port (or other means) and written into data memory. When the process is complete and
the new memory is verified as correct, software converts the RAM back into write-protected program
memory for the duration. As with the memory map control, there are minor differences between the
DS5000 series and DS5001/DS5002 series devices in how this is accomplished.
Soft Reload of a DS5000 Series Device
When application software decides that it should reprogram a portion of memory, the software must
convert the target area into data memory. The DS5000 does this when software sets the PAA bit
(MCON.1) to a logic 1. PAA is the partition access-enable bit, which is protected from accidental
modification by the timed-access procedure. Timed access is discussed in a later section. When PAA = 1,
the microcontroller automatically moves the partition to 0800h and allows write access to the partition
control bits PA3–0 (MCON.7–4). At this time, the software can adjust the partition, but the new value is
not used until after PAA is cleared. The partition remains at 0800h as long as PAA = 1, regardless of the
partition control bits. This leaves a 2kB block of NV RAM (from 0000–0800h) assigned as program
memory. Apart from this, no other changes take place and software continues to operate normally.
Caution: Make certain that the code that controls the PAA resides in this first 2kB. When PAA = 1, all
addresses on the bytewide bus greater than 0800h are viewed as data memory and cannot be executed,
even if they were program memory originally. This gives the software read/write access to the remaining
6kB (range = 8kB) or 30kB (range = 32kB) of NV RAM on the bytewide bus.
At this time, software can begin reloading the target area of memory. There are two minor variations of
this procedure. First, a user’s loader routine that resides below 0800h (2kB) can reprogram the remainder
of memory as needed. This is done be receiving the new code through a serial port or other mechanism
and writing it to the RAM at the addresses where it will be executed. Since the RAM is data memory, the
write operation is done using MOVX instructions.
The second option is that the user’s code below 2kB can simply move the partition to a new value. This is
done by writing a new value for PA3–0 in MCON (MCON.7–4) while PAA is still set to 1, then clearing
PAA. The purpose of this would be that the loader routine mentioned in option 1 resides in memory
above 2kB, but below the target memory area. To gain access, the partition must be moved to a location
29 of 187
Page 30

Secure Microcontroller User’s Guide
that includes this loader routine. Once the partition is moved to this temporary location, the software
loader can reprogram new code as before.
When loading is complete, the partition must be either restored or set to a new value that is appropriate
for the new software. If the PA3–0 bits were not modified, the PAA bit can simply be cleared. This
restores the old partition. If the PAA3–0 were modified during loading or software has grown
significantly, a new partition is needed. The PA3–0 bits must be written while PAA is set to 1.
To summarize the soft reload, the procedure goes as follows:
1) Ensure that current program execution is in the range of 0000h to 0800h.
2) Set the PAA bit using a timed-access procedure.
3) Load new contents into program memory at addresses above 0800h using MOVX instructions.
4) Define a new partition address if necessary and write the appropriate bits into PA3–0 in the MCON
SFR.
5) Restore the current partition by clearing the PAA bit with a timed-access procedure.
6) Resume operation.
The following example illustrates the soft reload procedure. The original program requires a partition of
4000h (16kB). The new program is larger, requiring a partition of 6000h (24kB). The code that performs
these steps is shown below. This routine must be located below 0800h in program memory.
MOV TA, #0Aah ; TIMED ACCESS
MOV TA, #55h ; TIMED ACCESS 2
MOV MCON, #10001010b ; SET PAA BIT
.
. ; USER’S CODE TO LOAD RAM USING MOVX GOES HERE
.
MOV TA, #0Aah ; TIMED ACCESS
MOV TA, #55h ; TIMED ACCESS 2
MOV MCON, #11001000b ; LOAD NEW PARTITION AND CLEAR PAA BIT
30 of 187
Page 31

Secure Microcontroller User’s Guide
DATA
DATA
DATA
PROGRAM
SPACE
PROGRAM
SPACE
PROGRAM
BEFORE LOADING
DURING LOADING
AFTER LOADING
7FFFh
6000h
4000h
0800h
0000h
RANGE (32kB)
NEW PARTITION (24kB)
OLD PARTITION (16kB)
TEMP PARTITION (2kB)
0kB
= NV RAM PROGRAM MEMORY
Figure 4-7. Reloading Portions of a DS5000 Series Device
MEMORY
SPACE
MEMORY
SPACE
MEMORY
SPACE
MEMORY
MEMORY
SPACE
MEMORY
PAA = 0
PA3-0 = 1000b
PAA = 1
PA3-0 = XXXXb
PAA = 0
PA3-0 = 1100b
= NV RAM DATA MEMORY
Soft Reload of a DS5001/DS5002
However, a soft reload of a DS5001/DS5002 series device has minor variations from the DS5000 version.
First, there is no PAA bit in the DS5001/DS5002. If the DS5001/DS5002 is in a partitionable mode, the
user’s program must manipulate the partition control bits PA3–0, placing the partition to a value that
permits the target area to be loaded. Moving the partition to a new value should convert the target area to
data memory allowing read/write access. The user’s loader routine, then uses MOVX instructions to load
the new program contents into memory. This program can be received from a serial port or other
mechanism. When the loading procedure is complete, a new partition (or the old one) must be loaded.
Note that the loader routine must reside below the partition at all times.
In the DS5000 series, the PAA bit was protected by a timed-access procedure. In the DS5001/DS5002,
the PA3–0 bits are protected directly. The user’s program must use a timed-access procedure to alter
these bits. The microcontroller further protects the application by not permitting software to write a 0000b
into PA3–0. This would cause a program memory area of 0kB.
31 of 187
Page 32

Secure Microcontroller User’s Guide
If the device is in a nonpartitionable configuration, an extra step is required. To perform a soft reload of
the program in a nonpartitionable mode, the software must temporarily convert the microprocessor to a
partitionable mode using the access-enable bit (RPCTL.4). Setting the AE bit to a logic 1 converts the
DS5001/DS5002 into a partitionable mode for as long as it is set. This means that regardless of the
original setting, once AE = 1, the memory map is a 64kB partitionable mode. The partition is set to 1000h
(4kB) when AE = 1, so the loader routine must reside in this area. The user can then perform the soft
reload as previously discussed. When loading is complete, the software should clear the AE bit. Note that
AE requires software to use a timed-access procedure to alter it. This method allows a user to alter
program memory in a nonpartitionable mode. Data memory can be initialized by application software at
any time. Since full read/write access is available, no special provisions are needed.
Note: MOVX instructions using the data pointer as an operand must be used when executing a soft reload
(AE = 1) from any of the nonpartitionable memory modes. The use of MOVX instructions using R0 or
R1 as an operand does not write or read the correct address.
To summarize the soft reload for a DS5001/DS5002, the procedure goes as follows:
Partitionable Mode
1) Write a value to PA3–0 using a timed-access that gives access to the target area of memory.
2) Load new contents into program memory at addresses above the partition using MOVX instructions.
3) Define a new partition address if necessary and write the appropriate bits into PA3–0 in the MCON
SFR using a timed access.
4) Resume operation.
Nonpartitionable Mode
1) Set the AE bit to 1 using a timed-access procedure.
2) Load new contents into program memory at addresses above the partition (4kB) using MOVX
instructions.
3) Clear the AE bit using a timed-access procedure.
4) Resume operation.
The following illustrates an example where a soft reload is performed for a partitionable mode. The
original program requires a partition of 4000h (16kB). The new program is larger, requiring a partition of
A000h (40kB). A loader routine resides below address 1000h. The code that performs these steps is
shown below. Note that the timed-access procedure is performed, but is described in a later section.
MOV TA, #0Aah ; TIMED ACCESS
MOV TA, #55h ; TIMED ACCESS 2
MOV MCON, #00011000b ; SET PARTITION TO 1000h
.
. ; USER’S CODE TO LOAD RAM USING MOVX GOES HERE
.
MOV TA, #0Aah ; TIMED ACCESS
MOV TA, #55h ; TIMED ACCESS 2
MOV MCON, #10101000b ; LOAD NEW PARTITION OF A000h+
32 of 187
Page 33

Secure Microcontroller User’s Guide
DATA
DATA
DATA
PROGRAM
PROGRAM
PROGRAM
SPACE
BEFORE LOADING
DURING LOADING
AFTER LOADING
7FFFh
A000h
4000h
1000h
0000h
RANGE (32kB)
NEW PARTITION (24kB)
OLD PARTITION (16kB)
TEMP PARTITION (2kB)
0kB
= NO RAM PROGRAM MEMORY
= NV RAM DATA MEMORY
Figure 4-8. Reloading a DS5001/DS5002 Series Device
MEMORY
SPACE
MEMORY
SPACE
PA3-0 = 0100b
MEMORY
SPACE
MEMORY
SPACE
PA3-0 = 0001b
MEMORY
SPACE
MEMORY
PA3-0 = 1010b
4.8 Special Function Registers
The secure microcontroller uses SFRs to control most functions. In many cases, an SFR contains 8 bits,
each of which control a function or report status on a function. The SFRs reside in register locations
80–FFh. They can be accessed using MOV instructions with direct addressing. In addition, some of the
SFRs are bit addressable. This can be particularly useful when enabling a function without modifying
others in the register since an SFR can contain eight unrelated control and status functions.
With a few minor exceptions, the secure microcontroller provides identical SFRs to a standard 8051, plus
extra locations to control unique functions. Modifications to the standard 8051 SFR map are that the
PCON register GF1 (PCON.3) and GF0 (PCON.2) have been replaced by the enable power-fail interrupt
and the enable watchdog-timer bits, respectively. In addition, the secure microcontroller requires a timedaccess procedure before allowing software to modify the STOP bit (PCON.1). This prevents errant
software from creating a unrecoverable situation for the watchdog timer. The remaining SFRs are either
identical to the 8051 or new to the architecture.
There are some differences between the DS5000 series and the DS5001/DS5002 series SFRs. Figure 4-9
and Figure 4-10 show an overview of their respective SFR maps. Detailed descriptions follow.
Differences are denoted under the particular register. In some cases, the DS5001 and DS5002 have
registers that do not appear in the DS5000 (noted under the particular register).
33 of 187
Page 34

Figure 4-9. DS5000 SFR Map
Secure Microcontroller User’s Guide
34 of 187
Page 35

Figure 4-10. DS5001/DS5002 SFR Map
Secure Microcontroller User’s Guide
35 of 187
Page 36

Secure Microcontroller User’s Guide
D7
D6
D5
D4
D3
D2
D1
D0
SMOD
POR
PFW
WTR
EPFW
EWT
STOP
IDL
RW-0
RT-*
R-*
R-*
RW-0
RT-*
RT-0
RW-0
POR
Power Control Register
PCON, 087H
R = Unrestricted Read Access, W = Unrestricted Write Access, T = Timed-access Write Only, n = Value after Reset, * = Special: see description
PCON.7 SMOD
Double Baud Rate When set to 1, the baud rate is doubled when the serial port is being used in modes
1, 2, or 3.
PCON.6
Power-On Reset Indicates that the previous reset was initi ated du ring a power-on sequence. This bit
PCON.5 PFW
Power-Fail Warning Indicates that a potential power failure is in progress. Set to 1 whenever V
PCON.4 WTR
Watchdog Timer Reset Set to 1 following a watchdog timer timeout. If WTR is enabled, it indicates the
PCON.3 EPFW
Enable Power-Fail Interrupt Enables (EPFW = 1) or disables (EPFW = 0) the p ower-fail interrupt.
PCON.2 EWT
Enable Watchdog Timer Enables (EWT = 1) or disables (EWT = 0) the WTR. This bit is cleared to 0 on a
PCON.1 STOP
Stop Used to invoke the stop mode. When set to 1, program execution terminates
PCON.0 IDL
Idle Used to invoke the idle mode. When set to 1, program execution is halted and
is cleared to 0 when power-on reset occurs, and remains 0 until it is set to 1 by
software.
is
CC
below the V
threshold. Cleared to 0 immediately following a read operation of
PFW
the PCON register. Once set, it remains set until the read operation occurs,
regardless of activity on V
< V
. This bit is cleared to a 0 during a power-o n reset.
PFW
. After PFW is cleared by a read, it returns to 1 if VCC
CC
cause of the reset. Cleared to 0 immediately following a read of the PCON
register. This bit is set to 1 after a WTR and cleared to 0 on a power-on reset.
Remains unchanged during other types of resets.
power-on reset and remains unchanged during other types of reset.
no-V
LI
immediately and stop mode operation commences. Cleared to 0 when program
execution resumes following a hardware reset.
resumes when the idle bit is cleared to 0 following an interrupt or a hardware reset.
36 of 187
Page 37

Secure Microcontroller User’s Guide
D7
D6
D5
D4
D3
D2
D1
D0
TF1
TR1
TF0
TR0
IE1
IT1
IE0
IT0
RW-0
RW-0
RW-0
RW-0
RW-0
RW-0
RW-0
RW-0
INT1
INT1
INT1
INT0
INT0
Timer Control Register
TCON, 088H
R = Unrestricted Read Access, W = Unrestricted Write Access, T = Timed-access Write Only, n = Value after Reset, * = Special: see description
TCON.7 TF1
Timer 1 Over f low Flag Status bit set to 1 when timer 1 overflows from a previous count value of all 1s.
Cleared to 0 when CPU vectors to timer 1 interrupt service routine.
TCON.6 TR1
Timer 1 Run Control When set to 1 by soft ware, timer 1 operati on is enabled. Ti mer 1 is disabled when
cleared to 0.
TCON.5: TF0
Timer 0 Overflow Status bit set to 1 when timer 0 overflows from a previous count value of all 1s.
Cleared to 0 when CPU vectors to timer 0 interrupt service routine.
TCON.4: TR0
Timer 0 Run Control When set to 1 by software, timer 0 oper ation is enabled. Ti mer 0 is disabled wh en
cleared to 0.
TCON.3: IE1
Interrupt 1 Edge Detect Set to 1 to signal when a 1-to-0 transition (IT = 1) or a low level (IT = 0) has been
detected on the
if IT1 = 1.
TCON.2: IT1
Interrupt 1 Type Select When set to 1, 1-to-0 transitions on
from this pin. When cleared to 0,
TCON.1: IE0
Interrupt 0 Edge Detect Set to 1 to signal when a 1-to-0 transition (IT0 = 1) or a low level (IT0 = 0) has
been detected on the
processed only if IT0 = 1.
TCON.0: IT0
Interrupt 0 Type Select When set to 1, 1-to-0 transitions on
from this pin. When cleared to 0, INT0 is level activated.
pin. Cleared to 0 by hardware when interrupt processed only
are used to gen erate interrupt requests
is level activated.
pin. Cleared to a 0 by hardware when interrupt
are used to gen erate interrupt requests
37 of 187
Page 38

Timer Mode Register
D7
D6
D5
D4
D3
D2
D1
D0
GATE
M1
M0
GATE
M1
M0
RW-0
RW-0
RW-0
RW-0
RW-0
RW-0
RW-0
RW-0
INT
M1
M0
CONDITION
0
0
Mode 0: 8 bits with 5-bit prescale
0
1
Mode 1: 16 bits with no prescale
1
0
Mode 2: 8 bits with auto-reload
Mode 3: Timer 0 - Two 8-bit timers, Timer 1 Stopped
TMOD, 089H
Secure Microcontroller User’s Guide
C/T
R = Unrestricted Read Access, W = Unrestricted Write Access, T = Timed-access Write Only, n = Value after Reset, * = Special: see description
C/T
TMOD.7 (Timer 1);
TMOD.3 (Timer 0) GATE
Gate Control When set to 1 with TRn = 1, timer/counter’s input count pulses are only
delivered while a 1 is present on the
pin. When cleared to 0, count pulses
are always received by the timer/counter a long as TRn = 1.
TMOD.6 (Timer 1);
TMOD.2 (Timer 0) C/T
Counter/Timer Select When set to 1, the counter function is selected for the associat ed timer; when
cleared to 0, the timer function is selecte d.
TMOD.5-4 (Timer 1);
TMOD.1-0 (Timer 0) M1, M0
Mode Select These bits select the operating mode of the associated timer/counter as
follows:
1 1
38 of 187
Page 39

Secure Microcontroller User’s Guide
D7
D6
D5
D4
D3
D2
D1
D0
SM0
SM1
SM2
REN
TB8
RB8
TI
RI
RW-0
RW-0
RW-0
RW-0
RW-0
RW-0
RW-0
RW-0
0 0 0
SYNC 8 12 t
CLK
0 1 1
ASYNC
10
Timer 1 Overflow
1 0 2
ASYNC
11
64 t
CLK
or 32 t
CLK
1 1 3
ASYNC
11
Timer 1 Overflow
Serial Control Register
SCON, 098H
R = Unrestricted Read Access, W = Unrestricted Write Access, T = Timed-access Write Only, n = Value after Reset, * = Special: see description
SCON.7, SCON.6: SM0, SM1
“Mode Select”: Used to select the operational mode of the serial I/O port as follows:
SM0 SM1 MODE FUNCTION LENGTH (BITS) CL OCK PERIOD
SCON.5 SM2
Multiple MCU Comm Used to enable the multiple microcontr oller communications feature for modes 2
and 3. When SM2 = 1, RI IS activated only when serial words are received which
cause RB8 to be set to 1.
SCON.4 REN
Receive Enable When set to 1, the receive shift register is enabled. Disabled when cleared to 0.
SCON.3 TB8
Transmitted Bit 8 Can be set or cleared to define the state of the 9th data bit in modes 2 and 3 of a
serial data word.
SCON.2 RB8
Received Bit 8 Indicates the state of the 9th data bit received while in modes 2 or 3. If mode 1 is
selected with SM2 = 0, RB8 is the state o f the stop bit which was re ceived. RB8 is
not used in mode 0.
SCON.1 TI
Transmit Interrupt Status bit used to signal that a data word has been completely shifted out. In mode
0, it is set at the end of the 8th data bit. Set when the stop bit is transmitted in all
other modes.
SCON.0 RI
Receive Interrupt Status bit used to signal that a seri al data word has been received and load ed into
the receive buffer register. In mode 0, i t is set at t he e nd of the 8 th b it ti me. It is set
at the midbit time of the incoming stop bit in all other modes of a valid received
word according to the state of SM2.
39 of 187
Page 40

Secure Microcontroller User’s Guide
D7
D6
D5
D4
D3
D2
D1
D0
EA — —
ES
ET1
EX1
ET0
EX0
RW-0
RW-0
RW-0
RW-0
RW-0
RW-0
Interrupt Enable Register
IE, 0A8H
R = Unrestricted Read Access, W = Unrestricted Write Access, T = Timed-access Write Only, n = Value after Reset, * = Special: see description
IE.7 EA
Global Interrupt Enable When set to 1, each interrupt except for PFW may be individually enabled or
disabled by setting or clearing the associated IEx bit. When cleared to 0,
interrupts are globally disabled and no pending interrupt request will be
acknowledged except for PFW.
IE.4 ES
Enable Serial Interrupt When set to 1, an interrupt request from either the serial port’ s TI or RI flags
can be acknowledged. Serial I/O interrupts are disabled when cleared to 0.
IE.3 ET1
Enable Timer 1 Interrupt When set to 1, an interrupt request from Timer 1’s TF1 flag can be
acknowledged. Timer interrupts are disabled when cleared to 0.
IE.2 EX1
Enable External Interrupt 1 When set to 1, an interrupt request from the IE1 flag can be acknowledged.
Interrupts are disabled from this source when cl ear ed to 0.
IE.1 ET0
Enable Timer 0 Interrupt When set to 1, an interrupt request from timer 0’s TF0 flag can be
acknowledged. Interrupts are disabled from this source when cleared to 0.
IE.0 EX0
Enable External Interrupt 0 When set to 1, an interrupt from the IE0 flag can be acknowledged. Interrupts
are disabled from this source when clear ed to 0.
40 of 187
Page 41

Secure Microcontroller User’s Guide
D7
D6
D5
D4
D3
D2
D1
D0
RWT 1 1
PS
PT1
PX1
PT0
PX0
RT-1
R-1
R-1
RW-0
RW-0
RW-0
RW-0
RW-0
Interrupt Priority Register
IP, 0B8H
R = Unrestricted Read Access, W = Unrestricted Write Access, T = Timed-access Write Only, n = Value after Reset, * = Special: see description
IP.7 RWT
Reset Watchdog Timer When a 1 is written to this bit via the timed-access procedure the watchdo g timer
count will be reset and counting will begin again. Writing a 0 into this bit has no
effect. This bit will always read 1.
IP.4 PS
Serial Port Priority Programs serial port interrupts for high priority when set to 1. Low priority is
selected when cleared to 0.
IP.3 PT1
Timer 1 Priority Programs timer 1 interrupt for high priority when set to 1. Low priority is selected
when cleared to 0.
IP.2 PX1
External Interrupt 1 Priority Programs external interrupt 1 for high priority when set to 1. Low priority is
selected when cleared to 0.
IP.1 PT0
Timer 0 Priority Programs timer 0 interrupt for high priority when set to 1. Low priority is selected
when cleared to 0.
IP.0 PX0
External Interrupt 0 Priority Programs external interrupt 0 for high priority when set to 1. Low priority is
selected when cleared to 0.
41 of 187
Page 42

Secure Microcontroller User’s Guide
D7
D6
D5
D4
D3
D2
D1
D0
RNGE3
RNGE2
RNGE1
RNGE0
— — —
CRC
RB-*
RB-*
RB-*
RB-* RB-*
D7
D6
D5
D4
D3
D2
D1
D0
PA3
PA2
PA1
PA0
RA32/8
ECE2
PAA
SL
R*-*
R*-*
R*-*
R*-*
RB-*
RW-*
RT-0
R*-*
0 0 0 0 0000h (Invalid when SL = 1)
0 0 0
1
0800h
0 0 1
0
1000h
0 0 1
1
1800h
0 1 0
0
2000h
0 1 0
1
2800h
0 1 1
0
3000h
0 1 1
1
3800h
1 0 0
0
4000h
1 0 0
1
4800h
1 0 1
0
5000h
1 0 1
1
5800h
1 1 0
0
6000h
1 1 0
1
6800h
1 1 1
0
7000h*
1 1 1
1
8000h*
DS5001 CRC Register
CRC, 0C1H
R = Unrestricted Read Access, B = Modifiable only via Bootstrap Loader, n = Value after Reset, * = Special: see description
CRC.7-4 RNGE3-0 Determines the range over which a power-up CRC will be performed. Addresses
are specified on 4K boundaries. These bits are reset 0 on a no-V
reset and
LI
unchanged by all other resets.
CRC.0 CRC When set to 1, a CRC check will be performed on power-up or watchdog timeout.
CRC will be checked against stored values. An error will initiate Program Load
mode. These bits are reset 0 on a no-V
reset and unchanged by all other resets.
LI
DS5000 Memory Control Register
MCON, 0C6H
R = Unrestricted Read Access, W = Unrestricted Write Access, T = Timed-access Write Only, B = Modifiable only via Bootstrap Loader,
n = Value after Reset, * = Special: see description
MCON.7-4 PA3–0
Partition Address Selects the starting address of data memory on the bytewide bus. Program space
lies between address 0000h and the partition address. Writes to these bits are only
allowed when PAA = 1. Timed access is not requi red to write to PA3-0 o nce PAA
= 1.These bits are set to 1111b on a no-V
reset or when the security lock bit is
LI
cleared by hardware or the bootstrap loader. They are unchanged by all other
resets. These bits are also reset to 111 1b when software attempts to modify them
to 0000b when SL = 1 (illegal condition).
PA3 PA2 PA1 PA0 PARTITION ADDRESS
42 of 187
Page 43

Secure Microcontroller User’s Guide
*A 4kB increment (not 2kB) takes place between PA3–0 values 1110b and 1111b.
MCON.3 RA32/8
Range Address Set the maximum usable address on the bytewide bus.
RA32/8 = 0 sets range address = 1FFFH (8kB)
RA32/8 = 1 sets range address = 7FFFH (32kB)
Set to 1 during a no-V
reset and when the security lock bit is cleared by har dware
LI
or the bootstrap loader. Remains unchanged on all other types of resets.
MCON.2 ECE2
Enable Chip Enable 2 Used to enable or disable the CE2 signal for the bytewide bus data memory. When
ECE2 = 0, all MOVX instructions activate the CE1 signal. When ECE2 = 1, all
MOVX instructions activate the CE2 signal. This bit should always be cle ared t o 0
in the DS5000, DS5000-32, DS2250-8, and DS2250-32 versions.
MCON.1 PAA
Partition Address Access Used to protect the programming of the partition address select bits. PA3–0 cannot
be written when PAA = 0. PAA can be written only via the timed-access register.
MCON.0 SL
Security Lock Indicates that the security lock is set when SL = 1. Can only be modified by the
lock and unlock commands of the bootstrap loader. This bit cannot be modified by
the application software or by the bootstrap loader write command.
43 of 187
Page 44

Secure Microcontroller User’s Guide
D7
D6
D5
D4
D3
D2
D1
D0
PA3
PA2
PA1
PA0
RG1
PES
PM
SL
RT*-*
RT*-*
RT*-*
RT*-*
RB-*
RW-0
R*-*
R*-*
DS5001/DS5002 MCON Register
MCON, 0C6H
R = Unrestricted Read Access, W = Unrestricted Write Access, T = Timed-access Write Only, B = Modifiable only via Bootstrap Loader, n =
Value after Reset, * = Special: see description
MCON.7-4 PA3-0
Partition Address Bits When PM = 0, this address specifies the boundary between program and data
memory in a continuous space. These bi ts are timed-access protected. Cannot be
written by the application software if set to 0000b by the serial loader. If a 0000b
is written via the serial loader and t he security lock is set, the partition becomes
1111b. The same occurs if write access is available and application software writes
a 0000b. In addition, these bits are set t o 1111b if security lock is cleared. These
bits are set to 1111b on a no-V
unaffected by any other reset.
MCON.3 RG1
Range Bit 1 One of two bits that determine the range of program space. RG 0 is located in the
RPCTL register. This bit is set to 1 on a no-V
lock and is unaffected by any other reset. It can only be modified via the bootstrap
loader.
MCON.2 PES
Peripheral Enable Select When this bit is set, the data space is controlled by PE1–PE4. Peripherals are
memory mapped in 16kB blocks, and are accessed by encrypted MOVX
instructions on the bytewide bus.
MCON.1 PM
Partition Mode When PM = 0, a partitionable, continuous memory map is invoked. When PM = 1,
one of four fixed allocations is used. This bit is set to 1 on a no-V
unaffected by any other reset. It can only be modified via the bootstrap loader.
MCON.0 SL
Security Lock Indicates that the security lock i s set when SL = 1. Cleared to 0 o n a no-V
on reset. This bit can only be modified by the lock and unlock commands of the
bootstrap loader. This bit cannot be modified by the application software or by the
bootstrap loader write command.
reset or if the security lock is cleared. They are
LI
reset or a clearing of the security
LI
reset and is
LI
LI
power-
44 of 187
Page 45

Secure Microcontroller User’s Guide
D7
D6
D5
D4
D3
D2
D1
D0 C AC
F0
RS1
RS0
OV P
RW-0
RW-0
RW-0
RW-0
RW-0
RW-0
R-0
R1
R0
DATA REGISTER ADDRESS (R0)
0
0
00h
0
1
08h
1
0
10h
1
1
18h
Program Status Word Register
PSW, 0D0H
R = Unrestricted Read Access, W = Unrestricted Write Access, T = Timed-access Write Only, n = Value after Reset, * = Special: see description
PSW.7 C
Carry Set when the previous operation resulted in a carry (during addition) or a borrow
(during subtraction). Otherwise cleared.
PSW.6 AC
Auxiliary-Carry Set when the previous operation resulted in a carry (during addition) or a borrow
(during subtraction) from the low-order nibble. Otherwise cleared.
PSW.5 F0
User Flag 0 General-purpose flag bit that can be set or cleared as needed.
PSW.4-3 R1–R0
Register Bank Select Used to select an 8-byte bank of registers within the data register space to be
assigned as R0–R8 in subsequent instructions. The 8-byte bank starting address
selection is as follows:
PSW.2 OV
Overflow Set when a carry was generated into t he high-order bit, but not a carry out of the
high-order bit as a result of the previous operation, and v ice versa. OV is normally
used in 2’s complement arithmetic.
PSW.0 P
Parity Set if the modulo-2 sum of the eight bits of the accumulator is 1 (odd parity);
cleared on even parity.
45 of 187
Page 46

Secure Microcontroller User’s Guide
D7
D6
D5
D4
D3
D2
D1
D0
RNR
—
EXBS
AE
IBI
DMA
RPCON
RG0
R-0
RW-0
RT-0
R*W*-0
RW*-0
RW-0
RB-*
DS5001/DS5002 RPC Control Register
RPCTL, 0D8H
R = Unrestricted Read Access, W = Unrestricted Write Access, T = Timed-access Write Only, B = Modifiable only via Bootstrap Loader, n =
Value after Reset, * = Special: see description
RPCTL.7 RNR
When internal hardware sets this read-only bit to 1, a new random number is
available from the random number generator register of the DS5001/DS5002
(RNR;0CFh). This bit is cleared when the random number is read, and
approximately 160ms are required to generated th e next number. Because a reset
initiates the generation of a new random number, this bit will be set approximately
160µs after a reset.
RPCTL.5 EXBS
When this bit is set, all data memory (MOVX) accesses are ro uted t o the exp anded
bus (Ports 0 and 2). When cleared, MOVX accesses are touted to the bytewide
bus. This bit cannot be modified via the bootstrap loader.
RPCTL.4 AE
Access enable is used when a software reload is desired without using the
bootstrap loader. When set, the device is temporarily configured in a partitionable
configuration with the partition at 4kB. This occurs even if PM = 1. When cleared,
the prior memory configuration is resumed. This bit cannot be modified via the
bootstrap loader.
RPCTL.3 IBI
When this bit is set, the timer 1 interrupt is disabled and the interrupt vector (1Bh)
is converted to function as the RPC mode interrupt. This bit can be set only when
the RPCON bit is set. This bit is cleared on all resets an d when the RPCON bit is
cleared. This bit cannot be modified via the bootstrap loader.
RPCTL.2 DMA
This bit is set to enable DMA transfers when RPC mode is inv oked. It can o nly be
set when RPCON = 1. This bit is cleared on all resets and when the RPC is
cleared. This bit cannot be modified via the bootstrap loader.
RPCTL.1 RPCON
Enable the RPC 8042 I/O protocol. When set, port 0 becomes the data bus, and
port 2 becomes the control signals. This bit cannot be modified via the bootstrap
loader.
RPCTL.0 RG0
This is one of two range bits that deter min e th e size o f the p ro gram me mory spac e.
Its usage is shown above. It is cleared on a no-V
lock and unaffected by any other reset.
reset or clear ing of the security
LI
46 of 187
Page 47

Secure Microcontroller User’s Guide
D7
D6
D5
D4
D3
D2
D1
D0
ST7
ST6
ST5
ST4
IA0
F0
IBF
OBF * * * * * * * *
DS5001/DS5002 RPC Status Register
RPS, 0DAH
R = Unrestricted Read Access, W = Unrestricted Write Access, T = Timed-access Write Only, n = Value after Reset, * = Special: see description
RPS.7–4 General-purpose status bits that can be written by the microcontroller and can be
read by the external host. These bits are cleared wh en RPCON = 0. C an be read by
DS5001/DS5002 and host CPU when RPC mode is invoked. Can be written by the
DS5001/DS5002 when RPC mode is invoked.
RPS.3 IA0
Stores the value of the external system A0 for the last DBBIN wr ite when a valid
write occurs (as determined by the IBF flag). These bits are cleared when
RPCON = 0. Can be read by DS5001/DS5002 and host CPU when RPC mode is
invoked. Automatically written when a valid DBBIN Write occurs. Cannot be
written otherwise.
RPS.2 F0
General-purpose flag written by the DS5001/DS5002 and read by the external
host. These bits are cleared when RP CON = 0. Can be read by DS5001/DS5002
and host CPU when RPC mode is invoked. Can be written by the DS5001/DS5002
when RPC mode is invoked.
RPS.1 IBF
Input Buffer-Full Flag Input buffer-full flag is automatically set following a write by the external host as
part of the RPC communication. The bit is cleared when RPCON = 0 or following
a read of the DBBIN by the DS5001/DS5002. Can be read by DS5001/DS5002
and host CPU when RPC mode is invoked. This bit cannot be modified by
application software.
RPS.0 OBF
Output Buffer-Full Flag Output buffer-full Flag is automatically set following a write of the DBBOUT by
the DS5001/DS5002 as part of the RPC communication. The bit is cleared when
RPCON = 0 or following a read of the DBBOUT by the external host. This bit
cannot be modified by application software.
47 of 187
Page 48

Secure Microcontroller User’s Guide
4.9 Instruction Set
The secure microcontroller executes an instruction set that is object-code compatible with the industry
standard 8051 microcontroller. As a result, software tools written for the 8051 are compatible with the
secure microcontroller, including cross-assemblers, compilers, and debugging tools.
There are 42 instruction types recognized by the secure microcontroller. When the instruction uses both
source and destination operands, they are specified in the order of “destination, source.”
4.10 Ad dressing Modes
There are eight addressing modes. Five of these are used to address operands. The other three are used in
instructions that transfer execution of the program to another address (e.g., branch, jump, call). The
modes that address source operands include register addressing, direct addressing, register-indirect
addressing, immediate addressing, and register-indirect with displacement. The first three can also be
used to address a destination operand. Most instructions use operands that are located in the internal data
registers.
The addressing modes used for the control transfer instructions include relative addressing, page
addressing, and extended addressing. The operation of these addressing modes is summarized in the
following paragraphs. An example follows.
Register Addressing
Register addressing is used on operands contained in one of the eight registers (R7–R0) of the currently
selected working register bank. A register bank is selected via a 2-bit field in the PSW SFR. The working
registers can also be accessed through either direct addressing or register-indirect addressing. This is
because the working registers are mapped into the lower 32 bytes of internal data RAM, as previously
discussed.
ADD A, R4 ; Add Accumulator to Working register R4
Direct Addressing
Direct addressing is the only mode available for use on operands within the SFRs. Byte addressing can
also be used to access the 128 internal data registers.
MOV 072H, 074H ; Load direct reg. (072H) with direct reg. (074H)
Bit direct addressing is available on 128 bits located in the internal data registers in the byte addresses of
20H–2FH inclusive. Direct bit addressing is also available in SFRs located at addresses on 8-byte
boundaries starting at 80H (i.e., 80H, 88H, 90H, 98H, ...0F0H, 0F8H).
SETB 00H ; Set addressable bit 00H (D0 in Internal Data Reg. 20H)
Register-Indirect Addressing
Some instructions use register-indirect addressing for accessing operands in other internal data registers.
Use the contents of working register R1 or R0 as a pointer to other internal data registers.
ANL A, @R0 ; Logical AND of Accumulator with Internal Data
; register pointed to by contents of R0
48 of 187
Page 49

Secure Microcontroller User’s Guide
In addition, this addressing is used via the stack pointer register (SP) for manipulation of the stack. The
stack area is contained in the internal data register area. The PUSH and POP instructions are the only
ones that use SP for this addressing mode.
PUSH P0 ; Save the contents of the Port 0 SFR latch on the stack
The R0, R1, and the DPTR registers are used with register-indirect addressing for accessing data memory.
R1 or R0 in the selected working register bank can be used for accessing location within a 256-byte
block, pointed to by the current contents of the P2 SFR latch (address high byte).
MOVX A, @R1 ; Load the Accumulator with the contents of Data Memory
; addressed by the 8-bit contents of R1
The 16-bit DPTR register can be used to access any data memory location within the 64kB space.
MOVX @DPTR,A ; Load the Data Memory location pointed to by the
; contents of the DPTR with the Accumulator contents.
Immediate Addressing
Immediate addressing is used to access constants for use as operands that are contained in the current
instruction in program memory.
ORL A, #040H ; Logical OR of the Accumulator with the constant 040H
Register-Indirect with Displacement
Register-indirect with displacement addressing is used to access data in look-up tables in program
memory space. The location accessed is pointed to by the contents of either the DPTR or the PC registers,
which are used as a base register added together with the contents of the accumulator (A), which is used
as an index register.
MOVC A, @DPTR+A ; Load Accumulator with the contents of the
; Program Memory location pointed to by DPTR
; plus the value contained in the Accumulator
Relative Addressing
Relative addressing is used in the determination of a destination address for the conditional branch
instructions. Each of these instructions includes an 8-bit byte that contains a 2’s complement address
offset (-127 to +128), which is added to the PC to determine which destination address it is branched to
when the tested condition is found to be true. The PC points to the program memory location immediately
after the branch instruction when the offset is added. If the condition is found to be not true, then program
execution continues from the address of the following instruction.
JZ -20 ; Branch to the location (PC+2) -20 if the
; contents of the Accumulator = 0
Page Addressing
Page addressing is used by the control transfer instructions to specify a destination address within the 2kB
block in which the next contiguous instruction resides. The full 16-bit address is calculated by taking the
49 of 187
Page 50
Secure Microcontroller User’s Guide
FLAGS
FLAGS
C
OV
AC C OV
AC
ADD
± ± ±
CLR C
0
ADDC
± ± ±
CPL C
±
SUBB
± ± ±
ANL C, bit
±
MUL
0
ANL C,
bit
DIV
0 ±
ORL C, bit
±
ORL C,
bit
RRC
±
MOV C, bit
±
RLC
±
CJNE
±
SETB C
1
highest order 5 bits for the next contiguous instruction (PC + 2) and concatenating them with the lowest
order 11-bit field contained in the current instruction. The 11-bit field provides an efficient instruction
encoding of a destination address for these instructions.
ACALL 100H ; Call to the subroutine at address
; 0100H + current page address
If the instruction were located at 0830h, the destination address would be 800H + 100H or 900H.
Extended Addressing
Extended addressing is used in the control transfer instructions to specify a 16-bit destination address
within the entire 64kB addressable range of the secure microcontroller.
LJMP 0FF80H ; Jump to address 0FF80H
4.11 Program Status Flags
The PSW register contains the program status flags. Instructions that affect the states of the flags are
summarized in Table 4-A.
Table 4-A. Instructions That Affect Program Status Flag
INSTRUCTION
±
DA
0 = Cleared to 0
1 = Set to a 1
± = Modified according to the result of the operation.
±
INSTRUCTION
±
±
50 of 187
Page 51

Secure Microcontroller User’s Guide
WE
CE2
CE2
5. MEMORY INTERCONNECT
The secure microcontrollers are composed of microprocessors and modules. This section illustrates the
memory interconnect for the various chips and shows block diagrams of selected modules. The soft
microprocessor chips are 80-pin QFP packages that connect to a low-power CMOS SRAM. When using a
chip, the user must connect the bytewide bus to the RAM as shown in this section. In module form, the
bus is connected inside the package.
Preferred RAMs are those with the lowest possible data retention currents for the chosen memory
configuration. Note that data retention lifetime increases as RAM data retention current decreases and
battery size/capacity increases. The laws of physics decree that data retention currents can vary greatly
with temperature; be sure to select a device that meets the required data retention current over the
expected temperature range of the application. This is covered in detail in Section 6. In general, system
designers should carefully scrutinize the SRAM data sheet to ensure the memory device meets the
specifications.
In the case of the DS5000FP, the microprocessor can connect to either one or two SRAMs. They can be
8kB or 32kB, though the case of two 8kB RAMs could be prohibitively expensive. Figure 5-1 illustrates
the memory connection of a DS5000FP connected to one 32kB x 8. CE1 provides the chip select, and
R/W supplies the
signal. A second RAM could be added by simply using CE2 as the chip enable
with a common connection for the other signals.
In the case of DS5000-based modules including DS5000(T) and DS2250T, the SRAM is connected as
described above. Connections running between the microprocessor and RAM are not available at the pins.
The DS2250-64 has a second SRAM on
. The when present, the real-time clock is connected to
.
Figure 5-2 shows the module configuration with 32kB RAM and an RTC. This is identical for DS2250 or
DS5000 modules, which differ only in form factor.
Figure 5-1. Memory Interconnect of the DS5000FP
51 of 187
Page 52

Figure 5-2. DS5000 Series Module Block Diagram
WE
CE2
Secure Microcontroller User’s Guide
The DS5001FP/DS5002FP has several memory options. It can be connected to between one 8kB SRAM
and four 32kB SRAMs. It also supports one 128kB SRAM. In most cases the DS5001FP is used for its
greater memory access so it is not used with 8kB RAMs. In the partitionable mode (Section 4
), the device
can be connected to one or two SRAMs. Figure 5-3 illustrates the connection of two 32kB x 8 SRAMs.
Each RAM has its own chip enable, with a common
generated by the DS5001FP R/W signal. When
using the DS5001FP/DS5002FP with only one RAM, the second chip enable simply remains
unconnected. This solution provides 64kB of memory the user can partition into program and data
segments. The partition setting has no affect on the interconnect. Using the partition, the microcontroller
determines which memory blocks are program and write protects the appropriate addresses.
In the nonpartitionable case, the DS5001FP/DS5002FP can be connected to three or four 32kB x 8
SRAMs. Figure 5-4 shows the four RAM case. Each RAM has its own chip enable. To use three RAMs,
omit the unused chip enable (
or 4) as described in Section 4. This hardware configuration is similar
to the partitionable mode previously discussed. While this provides all 128kB of memory, it requires
more space and cost than the version shown in Figure 5-5. This uses the 128kB SRAM, which contains
all program and data memory. Note the MSEL signal is connected to ground to initiate this mode. The
user must still configure the PM bit and range during program loading.
52 of 187
Page 53

Secure Microcontroller User’s Guide
Figure 5-3. Memory Interconnect of the Partitionable DS5001/DS5002
53 of 187
Page 54

Secure Microcontroller User’s Guide
Figure 5-4. Memory Interconnect of the Nonpartitionable DS5001FP,
DS5002FP
54 of 187
Page 55

Secure Microcontroller User’s Guide
CE3
CE2
Figure 5-5. Memory Interconnect Using the 128kB SRAM
In the 128kB x 8 configuration, the microprocessor converts the
into A15 and
into A16.
Grounding the MSEL pin causes this configuration. The physical location of program memory is between
addresses 0000h to FFFFh. Data memory is located between 10000h and 1FFFFh. These physical
locations are transparent to the user. From a software perspective, both program and data are located
between 0000 and FFFFh. When the MSEL pin is grounded, the device cannot be partitioned. The MSL
bit accessed through the bootstrap loader is used to select access to the 64kB data or 64kB program
segment via the loader in the 128kB x 8 configuration.
The DS2251T 128kB micro stik uses a DS5001FP. The DS2252T secure micro stik is based on the
DS5002FP. The DS5002FP device provides additional memory security features. The modules are
available in 32kB, 64kB, and 128kB versions. Figure 5-6
is a block diagram of the DS2251T with 128kB
of NV RAM. This part can also be built with 32kB or 64kB. In this case, the 128kB RAM is replaced
with one or two 32kB RAMs. Figure 5-7 shows a DS2252T with 32kB of RAM. This part is also
available in 64kB or 128kB versions. The 64kB version uses two RAMs. The 128kB version uses the
single 128kB SRAM. This is entirely transparent to the user and is provided for completeness.
55 of 187
Page 56

Figure 5-6. DS2251T-128 Block Diagram
Secure Microcontroller User’s Guide
56 of 187
Page 57

Figure 5-7. DS2252T-32 Block Diagram
Secure Microcontroller User’s Guide
57 of 187
Page 58

Secure Microcontroller User’s Guide
6. LITHIUM/BATTERY BACKUP
Soft microcontroller devices are battery backed for data retention in the absence of VCC. The state of the
microcontroller in the soft microcontroller is also maintained, unlike a conventional processor system
using an external NV RAM. This section discusses the battery-backup feature, covering system design,
battery attach procedure, I/O pin restrictions, lifetime calculations, and battery/RAM size tradeoffs. Some
information is unnecessary to module users but it provides background information for proper handling
and system design. Each section highlights both chip and module considerations when there are
differences.
When properly used, secure microcontrollers provide better than 10 years of data retention in the absence
of power at room temperature. Elevated temperatures can cause increased normal data retention current to
be drawn by a RAM. Data retention current is only a concern when the device is in battery-backed mode
as no current is drawn from the battery while +5V is applied to the device. Therefore, data retention must
be viewed in the context of the power supply duty cycle. For example, if a system is rated for 10 years of
data retention, but will have power applied for 12 hours per day, the expected lifetime is greater than 20
years, or the lifetime of the battery, whichever is less.
6.1 Data Retention
The secure microcontroller family provides nonvolatile storage in ordinary SRAM. It accomplishes this
by battery backing the memory in the absence of power. When power (V
) begins to fail, the processor
CC
generates an internal power-fail reset condition as discussed in the next section. At this time, SRAM chip
enables are taken to a logic high inactive state. Also, I/O port pins also go to a logic high state. If power
continues to fall and crosses below the battery threshold, the microprocessor enters the data retention
state, and the microcontroller’s power-supply output to the SRAM (V
) is switched from VCC t o the
CCO
battery. Battery-backed chip enables are maintained at a logic high state, but nonbacked chip enables and
I/O port pins follow V
down. Maintaining chip enables at an inactive level and lowering the power
CC
supply to approximately +3V causes the NV RAM to enter a data retention state. Thus the combination
retains data for a long period as the circuits draw a very small current from the battery. Maxim soft/secure
microcontroller modules easily exceed 10 years of data retention, and solutions can be designed using
discrete Maxim soft/secure microcontroller chips, SRAMs and batteries to achieve a much greater
lifetime as required by the user’s application.
Battery-Backed Circuits
The secure microcontroller is completely battery-backed, meaning that both internal configuration and
data are preserved when power is removed. In order to achieve this ultra-low power state, special logic in
the microprocessor places all internal nodes in a predictable (low power) state. This occurs during system
power-down while VCC is falling below the reset voltage threshold but is still above the battery voltage
(VLI). To allow time for the internal battery control circuitry to switch from VCC to battery power, the
power supply must allow at least 40 µs (130 µs for DS5001/DS5002) between the V
CCMIN
and VLI.
Failure to meet this condition may result in an incomplete transition to battery-backed mode, resulting in
a substantial increase in microprocessor backup current (in excess of the data sheet specification) and/or
program/data corruption. Fortunately, a modest amount of system capacitance is enough to prevent fast
slewing. The actual value will depend on the total system loading. This slew rate must be met for either a
chip or module solution. Figure 6-1 illustrates the power supply conditions that should be met.
58 of 187
Page 59

Secure Microcontroller User’s Guide
40µs, 130µs
VCC
V
VLI
LITHIUM
Figure 6-1. Power-Supply Slew Rate
CCMIN
CURRENT
Each time VCC is restored, the battery-backed functions remain in their previous state. The exception is
when the device performs a no-VLI r eset. This special reset event is a one-time, user-initiated action that
forces selected SFR bits to special states. The no-VLI reset is documented in Section 10, Reset Conditions.
A module user [DS5000(T), DS2250(T), DS2252(T)] never experiences a no-VLI r eset because it occurs
only once as a part of the factory assembly process.
Battery-Attach Procedure
This section applies to microprocessor chips only, not modules. When a microprocessor is received from
the factory, all nonvolatile functions are absent since there is no backup source connected to the chip. As
mentioned above, the microprocessor must place circuits in a low-power state to prepare for battery
backup. If a battery were attached to an uninitialized chip, the backup current would be unpredictable. For
this reason, the following battery-attach procedure must be followed.
1) Apply VCC to the microprocessor.
2) Attach the battery to the V
input.
LI
3) Configure and program the device as normal. (Optional at this time.)
4) Power-down the microprocessor (remove V
) using the guidelines discussed above while leaving the
CC
battery attached.
It is imperative that the battery-attach procedure be followed correctly. Connecting the battery without
performing the battery-attach procedure can result in a high-drain on the battery until VCC is first applied,
significantly reducing battery life. Note that the battery-attach procedure does not automatically initiate a
no-VLI reset, and battery-backed bits are undefined until initialized by the bootstrap loader, user-software,
or a no-VLI reset. Following a battery-attach procedure, the first command sent to the bootstrap loader
must be the Unlock command to initialize the state of the security lock bit.
Important Application Note
Maxim recommends a direct connection between the battery and the VLI pin of the microprocessor. The
inclusion of diodes or resistors in series with the VLI pin of the microprocessor is not necessary and may
result in a loss of memory integrity under certain circumstances.
In most applications it is not necessary to add decoupling capacitors to the V
memory devices will be attached to the pin. If decoupling capacitors are required, the must have a high
line if a small number of
CCO
59 of 187
Page 60

Secure Microcontroller User’s Guide
CE
a year)
in days
of(number *day)a
in hours
of(number
* amps) incurrent
retention(Data
hours amp incapacity Battery
120 x 10
-3
= 120 x 10-3
(75 + 500 + 400) x 10-9 x 24 x 365) = 8.54 x 10-3
= 14 years
ESR rating over the intended operating temperature range to ensure against leakage that may shorten
battery life.
Battery Lifetime
The calculations of data retention lifetime are helpful for chip or module users. They can serve as design
and system reliability guidelines. All microcontroller modules are rated for better than 10 years of data
retention in the absence of VCC at +25°C. Following these guidelines, similar performance can be
achieved using chips. It is also not difficult to achieve better than 10 years depending on the user’s actual
environment and design goals.
The system lifetime can be determined from three parameters: data retention current, battery capacity, and
battery self-discharge. Lithium cells have extremely good self-discharge performance, and manufacturer’s
data and Maxim charact erization has determined that the self-discharge of a coin cell lithium battery is
less than 0.5% per year at +25°C. Consequently, even after 15 years of shelf life, the lithium cell would
have 90% of its capacity remaining. Therefore when using a lithium coin cell, the self-discharge
mechanism is not a consideration for rating equipment life.
Data retention current is a combination of RAM, microprocessor, RTC, and other battery-backed circuits,
if any. In a Maxim module, these are screened for combination with the appropriate battery. When
designing with discrete soft/secure microprocessors, the user must balance the size/cost of a larger lithium
cell with the data retention current/cost of SRAMs.
When designing a chip-based system and selecting the appropriate SRAM, the most important
specification is data retention current. This is not the same as standby current. Data retention current
should be specified with
possibly for other temperatures. The lifetime calculations are illustrated below. The formula for data
retention life in years is as follows:
= VIH and VCC = 3V. This specification is usually available at +25°C, and
As an example, a microprocessor rated for 75nA, SRAM for 500nA, RTC for 400nA for a total of 950nA
of current consumption in battery-backed mode. A Panasonic CR1632 lithium cell is selected, which has
a capacity of 120mAh.
Thus, a system with less than 1µA of data retention current and a CR1632 lithium cell achieves well over
10 years of data retention in the absence of VCC. Referring to the recommended RAM chart in the
previous section, the user finds a variety of RAMs that allow this at room temperature. It makes no
difference if the system operates at +70°C, as long as data retention is at +25°C. If storage is at elevated
temperature, than the data retention current should be derated accordingly. If the manufacturer does not
specify data retention current over temperature, a conservative number is a 70% increase per +10°C.
Thus, if a RAM in data retention mode draws 1µA at +25°C, it draws approximately 1.7µA at +35°C. A
second example illustrates the case of elevated temperature storage.
In this example, the system is constructed using a DS5001FP chip with a Sony CXK581000P-LL 128kB
x 8kB SRAM. The system is stored at +40°C. The data retention current of this RAM is 2.4µA at +40°C.
The DS5001FP data retention current actually drops as temperature increases, so the maximum of 75nA
60 of 187
Page 61

Secure Microcontroller User’s Guide
180 x 10-3 = 180 x 10-3
= 8.3 years
is conservative. This gives a total data retention current of 2475nA. In this system, a Rayovac BR2325
with a capacity of 180mAh is used.
(2400 + 75) x 10-9 x 24 x 365) = 21.68 x 10-3
Note that these ratings are for continuous data retention so VCC is assumed absent for the entire period.
The lifetime will increase based on the ratio of time when VCC is applied vs. data retention time.
Using Lithium Cells
In the vast majority of soft/secure microcontroller applications, lithium cells are the preferred battery.
Their voltage varies only slightly over its useful life; a CR chemistry begins life at +3.3V and drops to
+2.9V near the end of life. Although some users choose to incorporate battery clips so that lithium cells
can be replaced, this is not recommended since such clips are susceptible to shock and vibration and
could result in a corruption of program or data memory. Therefore, soldered battery tabs are
recommended. If a user elects to use a battery clip with a capacitor (to support momentary disconnect),
the leakage of the capacitor should be considered in the lifetime calculations.
Freshness Seal
The secure microcontroller family is designed to maximize the lifetime of the backup battery. These
devices incorporate a solid-state freshness seal that electrically isolates the battery from any loading when
systems do not require data retention, such as a completely assembled but unprogrammed system stored
in inventory. Since data retention is not required, there is no need to draw any current from the battery.
Thus even in the absence of power, the SRAM and RTC leakage currents are not drawn from the battery
while the freshness seal is applied.
This feature is available to module users of the DS5000 series [DS5000(T), DS2250T] and all users of the
DS5001/2 series [DS5001FP, DS5002FP, DS2251T, DS2252T]. All secure microcontroller are shipped
with the freshness seal applied. In the case of a DS5001/DS5002 series device, the freshness seal can be
reapplied via the bootstrap loader at any time. To invoke the freshness seal on a DS5001, DS5002 series
device, the “N” command should be issued to the bootstrap loader.
To clear the freshness seal, simply apply VCC. On a DS5000 series device, the user cannot restore the
freshness seal. Therefore, if freshness seal is desired for storage, the part should not be powered up when
received or installed.
Important Application Note
The pins on a secure microcontroller chip or module are generally as resilient as other CMOS circuits.
They have no unusual susceptibility to electrostatic discharge (ESD) or other electrical transients.
However, no pin on a soft microcontroller chip or module should ever be taken to a voltage below
ground. Negative voltages on any pin can activate internal parasitic diodes that draw current directly from
the battery. If a device pin is connected to the “outside world” where it can be handled or come in contact
with electrical noise, protection should be added to prevent the device pin from going below -0.3V. It is
also common for power supplies to give a small undershoot on power up, which should be prevented.
Application Note 93: Design Guidelines for Microcontrollers Incorporating NV RAM di scusses how to
protect devices against these conditions.
61 of 187
Page 62

Secure Microcontroller User’s Guide
7. POWER MANAGEMENT
All secure microcontrollers are implemented using CMOS circuitry for low power consumption. Two
software-initiated modes are available for further power saving at times when processing is not required
and VCC is at normal operating voltage. These are the idle and stop modes. The additional third mode is
the data retention or zero-power state, which is made possible by the on-chip circuitry. The control and
status bits that apply to these operating modes are contained in the PCON register and are summarized in
Control/Status Bits for Power Control. In addition, Table 7-A summarizes the state of external pins in
each of these modes.
7.1 Idle Mode
Idle mode suspends activity of the CPU but allows the timer/counters, I/O pins, and serial port to continue
their operation. This greatly reduces the number of switching nodes and thereby dramatically reduces the
total power consumption of the device. Idle mode is useful for applications in which lower power
consumption is desired with fast response to external interrupts but no other processing.
Software invokes idle mode by setting the IDL bit (PCON.0) to a logic 1. The instruction that sets this bit
is the last instruction executed before idle mode operation begins. Once in idle mode, the microprocessor
preserves the entire CPU status including the stack pointer, program counter, program status word,
accumulator, and RAM. There are two ways to terminate the idle mode. The first is from an interrupt that
has been previously enabled prior to entering idle mode. This will clear the IDL bit and cause the CPU to
enter the interrupt service routine as normal. When the RETI instruction is executed, the next instruction
that is executed is the one that immediately follows the instruction that set the IDL bit.
The second method of terminating the idle mode is by a reset. At this time the IDL bit is cleared and the
CPU is placed in the reset state. Since the clock oscillator continues to run in the idle mode, an oscillator
startup delay (referred to as t
following the reset. Two machine cycles are required to complete the reset operation (24 oscillator
periods). It should be noted that the watchdog timer continues to run during idle and that a reset from the
on-chip watchdog timer terminates idle mode.
in the AC Electrical Specifications in the data sheet) is not generated
POR
62 of 187
Page 63

Secure Microcontroller User’s Guide
POR
PROGRAM
MEMORY
Idle
Bytewide
1 1 Port Data
Port Data
Port Data
Port Data
Idle
Expanded
1 1 High-Z
Port Data
Address
Port Data
Stop
Bytewide
1 0 Port Data
Port Data
Port Data
Port Data
Stop
Expanded
1 0 High-Z
Port Data
Port Data
Port Data
Control/Status Bits for Power Control
PCON.6
Power-On Reset Indicates that the previous reset was initiated during a power-on sequence.
Initialization: Cleared to 0 by a power-on reset. Remains at 0 until set to a 1 by software.
Read Access: Can be read normally at any time.
Write Access: Can be written only by using the timed-access register
.
PCON.5 PFW
Power-Fail Warning Indicates that a potential power-failure is in progress. Set to 1 when V
voltage is
CC
below the V PFW threshold. Cleared to a 0 immediately following a read of the
PCON register. Once set, it remains set unti l read regardless of V
CC
.
Initialization: Cleared to a 0 during a power-on reset.
Read Access: Can be read normally at any time.
Write Access: Cannot be written.
PCON.3 EPFW
Enable Power-Fail Interrupt Used to enable or disable the po wer-fail interrupt. When EPFW is set to 1, it is
enabled; it is disabled when EPFW is cleared to a 0.
Initialization: Cleared to a 0 on any type of reset.
Read Access: Can be read normally anytime.
Write Access: Can be written normally anytime.
PCON.1: STOP
Stop Used to invoke the Stop mode. When set to a 1, program execution will terminate
immediately and Stop mode operation will commence. Cleared to a 0 when
program execution resumes following a hardware reset.
Initialization: Clear to a 0 on any type of reset.
Read Access: Can be read anytime.
Write Access: Can be written only by using the timed-access register.
PCON.0: IDL
Idle Used to invoke to idle mode. When set at 1, program execution is halted and
resumes when the idle bit is cleared to 0, following an interrupt or a hardware
reset.
Initialization: Cleared to 0 on any type of reset or interrupt.
Read Access: Can be read normally anytime.
Write Access: Can be written normally anytime.
Table 7-A. Pin States in Idle/Stop Modes
MODE
ALE PSEN P0 P1 P2 P3
63 of 187
Page 64

Secure Microcontroller User’s Guide
7.2 Stop Mode
Stop mode is initiated by setting the STOP bit (PCON.1). The operation of the oscillator is halted in stop
mode so that no internal clocking signals are produced for either the CPU or the I/O circuitry. An external
reset via the RST pin is the only means of exiting this mode without powering down (VCC taken below
V
) and then backing up to produce a power-on reset. The STOP bit can only be set by using the
CCMIN
timed-access software procedure described in Section 8. Since the oscillator is disabled in this mode, the
watchdog timer also ceases operation. When the external reset signal is issued to terminate the Stop
mode, a 21,504-clock delay is generated to allow the clock oscillator to start up and its frequency to
stabilize as is done for a power-on reset as described in Section 10. The original contents of those SFRs
that are initialized by a reset are lost.
7.3 Voltage Monitoring Circuitry
The on-chip voltage monitoring circuitry automatically places the microprocessor in its data retention
state when V
CC
< V
. It ensures that the proper internal control signals are generated and that power
CCMIN
from the battery is applied at the proper times so that the program/data RAM, data in the scratchpad
registers, and certain SFRs remain unchanged when VCC is cycled on and off. In addition, an interrupt is
available for signaling the processor of an impending power-fail condition so that the operational state of
the processor can be saved just prior to entering the data retention.
The voltage-monitoring circuitry recognizes three voltage thresholds below nominal operating voltage.
These thresholds are identified as V
(power-fail warning voltage), V
PFW
(minimum operating
CCMIN
voltage), and VLI (lithium supply) voltage. These thresholds are used to initiate required actions within
the microprocessor during situations when VCC power is cycled on and off. The timing diagram shown in
Figure 7-1
illustrates key internal activities during power cycling.
7.4 Power-Fail Interrupt
When VCC > V
operating voltage and drop to a level below the V
, program execution proceeds as normal. If VCC should decay from its nominal
CCMIN
threshold, the PFW status flag (PCON.5) is set. In
PFW
addition, a power-fail warning interrupt is generated if it has been enabled via the EPFW control bit
(PCON.3). The purpose of these indicators is to warn the processor of a potential power failure.
The V
The V
thres hold is above the specified minimum value for VCC (V
PFW
threshold is selected so that with a reasonable power-supply slew rate, ample time is allowed
PFW
) for full processor operation.
CCMIN
for the application software to save all critical information which would otherwise be lost in the absence
of VCC. Such information can include the states of the accumulator, stack pointer, data pointer, and other
SFRs that are initialized with a reset when VCC voltage is applied once again. Saved data can be placed
into scratchpad RAM or bytewide NV RAM. Through the use of the power-fail warning interrupt, an
orderly shutdown of the system can be performed prior to the time that processor operation is halted in
the event that VCC voltage is removed entirely.
The PFW flag is set to a logic 1 whenever VCC < V
PFW bit from software, or a power-on reset. If VCC is still below the V
. It is cleared in one of two ways: a read of the
PFW
threshold when the bit is
PFW
cleared, the PFW bit is immediately set once again. An interrupt is generated any time both the EPFW bit
and the PFW flag are set.
64 of 187
Page 65

Secure Microcontroller User’s Guide
Figure 7-1. Secure Microcontroller Power Cycling Timing
7.5 Total Power Failure
If VCC voltage should fall below the V
placing the CPU in a reset condition and then stopping the internal clock oscillator circuit, as illustrated in
Figure 7-1. At this time the interface to the program/data RAM is disabled by pulling the CE line high.
This action guarantees an orderly shutdown for the lithium-backed RAM.
The microprocessor is automatically placed in the data retention state if VCC voltage drops below VLI; the
control circuitry accomplishes this by switching the internal power-supply line (V
lithium power source. At this time, data is retained and no power is drawn from VCC.
When power is once again applied to the system, the VCC voltage eventually crosses the VLI threshold.
When this action is detected, the microprocessor automatically switches its internal supply line from the
lithium source back to the VCC pin. When VCC voltage eventually goes above the V
threshold, processor operation halts. This is done by first
CCMIN
) from pin to the
CCI
threshold, the
CCMIN
65 of 187
Page 66
Secure Microcontroller User’s Guide
clock oscillator is allowed to start up and an internal power-on reset cycle is executed. Part of the cycle
involves a considerable delay that is generated to allow the clock oscillator frequency to stabilize.
Activity on the RST pin is ignored until this sequence is completed. The time required for this cycle is
shown as t
in Figure 7-1 and is specified in the AC Electrical Specifications of the data sheet. A
POR
detailed description of the power-on reset cycle operation is given in Section 10.
Typically, the time taken for the power-on reset cycle is longer to complete than it takes for VCC to rise
above the V
program begins as illustrated in Figure 7-1. If the pow e r -on reset cycle completes before VCC>V
is set again as a result of VCC<V
threshold. In this case the internal PFW flag will be reset before execution of the user’s
PFW
PFW
during user software execution. A power-fail inte rrupt occurs at this
PFW
, PFW
time if the EPFW bit is enabled. A user should monitor the POR bit to know the power-supply status. See
to Figure 7-2 for details.
7.6 Partial Power Failures
Two cases of partial power failure can occur in which VCC voltage does not go through a completed
power-fail cycle, as previously described. The first case is that in which VCC drops below the V
threshold and then returns to its nominal level without going below the VLI threshold. The second case is
that in which VCC drops below the V
below the V
threshold. Both of these cases are very possible in a system application and could be
CCMIN
threshold and then returns to its nominal level without going
PFW
caused by a “brownout” condition prom the power supply.
The first case is indistinguishable by the software from the complete power-fail cycle that was previously
described. When VCC drops below V
drops below V
. The only operational difference is that if VCC never drops below the VLI threshold,
CCMIN
the PFW flag is set and the clock oscillator stops when VCC
PFW,
the internal power-supply line is never switched over to the lithium cell. When VCC rises back above the
V
threshold, the power-on reset cycle is executed as before. As a result, no special processing is
CCMIN
required in software to accommodate this case.
In the case that VCC dips without going below VLI, the PFW flag is set and a power-fail warning interrupt
still occurs when VCC drops below the V
threshold. The PFW flag remains set until it is cleared by
PFW
either a reset of the flag by the software or by a power-on cycle. If it is cleared while VCC is still below
the V
threshold, then it remains cleared until the next time V
threshold, it is immediately set again. If it is cleared after VCC has risen back above the V
PFW
goes below V
CC
PFW
.
As long as the PFW = 1, an interrupt occurs if EPFW is set. If the software executes a service routine in
response to a PFW interrupt and exits the service routine with the PFW flag still set, the processor is
immediately interrupted again. In a typical application, however, the power-fail interrupt service routine
would test the PFW flag in a conditional loop to determine if VCC has risen back above V
PFW
then return control to the main program in response to the event. See Figure 7-2 for details.
CCMIN
PFW
an d would
66 of 187
Page 67

Secure Microcontroller User’s Guide
Figure 7-2. Secure Microcontroller Power Management
67 of 187
Page 68

Secure Microcontroller User’s Guide
8. SOFTWARE CONTROL
Several features have been incorporated into the secure microcontroller to help ensure the orderly
execution of the application software in the face of harsh electrical environments. Any microcontroller
that is operating in a particularly noisy environment is susceptible to loss of software control. Electrical
transients such as a glitch on the clock or a noise spike on an I/O pin can cause the loss of key variables in
internal registers and/or execution of code out of its logical sequence. Such transients can send the
microcontroller into an indefinite period of seemingly random software execution.
Timed access, watchdog timer, and CRC hardware features have been built in to help provide control and
recovery under difficult operating conditions. The operation of these features is described below.
8.1 Timed Access
The timed-access feature is one of two levels of protection for critical SFR bits. For critical bits that
might need to be modified during normal operation, the timed-access procedure protects against an
inadvertent write operation. These bits may only be modified through the execution of a specific multiple
instruction software sequence that involves the timed-access register (TA; C7h). This restriction prevents
a potentially catastrophic change in the configuration by an inadvertent write during times when software
control has been lost.
In order to modify the protected bits listed in Table 8-A, a pattern of two bytes must first be written to the
timed-access register. The first write should be a value of 0AAh and the second should be a value of 55h.
After this sequence is performed, the protected bits may be modified. Upon receiving a 0AAh in the
Timed-access register, two timers are initiated. The first timer allows two instruction cycles to write a
55h. This means a one- or two-cycle instruction can be used. If 55h is not written within two cycles,
timed access is reset. The second timer requires that the protected bit be modified within four instruction
cycles. Since this timer started prior to writing 55h, the remaining time depends on which type of
instruction was used to write 55h. If a one-cycle instruction was used to write 55h, then three cycles
remain to modify protected bits. In the same way, if a two-cycle instruction was used to write 55h, then
two cycles remain. This is depicted in
In the rare case that back-to-back timed accesses are performed, the user must be aware that the 4-cycle
timed-access window must close before another timed access can begin. This is only an issue if a 1-cycle
instruction is performed after the MOV TA, #55h instruction, leaving one cycle remaining in the 4-cycle
count. The user can eliminate this problem by either using a 2-cycle instruction after the MOV TA, #55h
instruction, or by inserting another instruction between the two timed-access procedures. Violating this
rule results in a failure of the second timed-access procedure, leaving the bit(s) unmodified.
Figure 8-1 and demonstrated in the accompanying code.
68 of 187
Page 69

Secure Microcontroller User’s Guide
NAME
MICRO
LOCATION
DESCRIPTION
EWT
All Secure Micros
PCON.2
Enables the Watchdog Timer Reset function
RWT
All Secure Micros
IP.7
Resets the Watchdog Timer count
STOP
All Secure Micros
PCON.1
Stop Mode Enable
POR
All Secure Micros
PCON.6
Power-on Reset
PAA
DS5000 series
MCON.1
Partition Address Access bit (protects PA3–0)
PA3–0
DS5001, DS5002 series
MCON.7–4
Partition Address Bits
AE
DS5001, DS5002 series
RPCTL.4
Access Enable
4 CYCLES
2 CYCLES
WRITE
WRITE
WINDOW FOR
TIMED ACCESS CLOSES
Figure 8-1. Timed Access
AAh
55h
This code allows the reset of the watchdog timer:
MOV 0C7H,#0AAh ; 1st TA Value
MOV 0C7H,#055h ; 2nd TA Value 2 Cycles
SETB IP.7 ; Reset Watchdog Timer 1 Cycle
The watchdog timer bit may have been set using ORL IP, #80H, which takes 2 cycles.
This code allows the reset of the watchdog timer using a different approach:
MOV A, #55h ; Setup Acc for fast write
MOV 0C7H, #0AAh ; 1st TA Value
MOV 0C7H, A ; 2nd TA Value 1 Cycle
MOV A, IP ; Get Current IP 1 Cycle
ORL A, #80H ; Prepare for fast write 1 Cycle
MOV IP, A ; Reset Watchdog Timer 1 Cycle
Note that a new value for IP could have been retrieved from any direct register instead of
the current IP.
Table 8-A lists the bits that are write-access protected by the timed-access function.
Table 8-A. Timed-Access-Protected Control Bits
The timed-access feature is especially useful in protecting the watchdog timer control bits during the
interval before the timeout of the watchdog timer. The EWT bit is protected to prevent errant software
from disabling the watchdog timer, and the protection of the RWT bit prevents an accidental restart of the
watchdog timeout. Thus software must really intend to reset the timeout in order to do so.
69 of 187
Page 70

Secure Microcontroller User’s Guide
POR informs the software of the power supply condition. Specifically, it means the power has previously
dropped below the V
level and returned to normal. In many systems, this is a unique condition that
CC MIN
requires interaction with external hardware. Protecting this bit with a timed-access procedure prevents the
microcontroller from accidentally performing a power-on reset procedure.
On a DS5000 series device, the PAA bit allows software to alter the partition. If this is done accidentally,
the resulting configuration could be unrecoverable without human intervention. This could mean
selecting a partition that is outside of the user’s plan and that causes the system to fail. In a like manner,
the PA3–0 bits on a DS5001 series device are protected through timed access. As the DS5001 does not
have a PAA bit, the partition control bits are directly protected. The motivation for protecting the AE bit
is similar. This bit invokes a partitionable configuration where one had not been selected during bootstrap
loading. While there are several valid reasons to select AE, accidentally selecting this condition might be
unrecoverable without manual intervention.
Timed-access logic protects against a single inadvertent write modifying a critical control bit. It does not
protect against inadvertently entering a section of code that contains the correct sequence to modify a
protected bit. However, the statistical protection does greatly improve the system’s resilience to a crash.
8.2 Watchdog Timer
The on-chip watchdog timer provides a method of restoring proper operation during transients that cause
the loss of software control. The watchdog timer incorporates a free-running counter that starts counting
as soon as the clock oscillator begins operation following a power-on reset. When the watchdog timer is
enabled, it eventually reaches a timeout condition after 122,800 machine cycles, unless the application
software resets it. If a 12MHz crystal is used as the time-base element, this gives a timeout period of
122.88ms. An internal reset to the CPU is generated if the timeout condition is reached. Software that
uses the watchdog timer must periodically reset the watchdog to 0h critical points in the program. If
controlled execution is lost so that these check points are not encountered within the timeout period, the
watchdog timer provides an automatic reset. The SFR bits that control the watchdog include the enable
watchdog timer bit (EWT; PCON.2), the reset watchdog timer bit (RWT; IP.7), and the watchdog timerreset status flag (WTR; PCON.4).
If the watchdog timer is desired, the first step is to reset the timer count. This is necessary since the timer
is free running and can be about to time out. Set the RWT bit to a logic 1 using a timed-access procedure.
This restarts the timer with the full interval. Then enable the watchdog timer-reset function by setting the
EWT bit to a logic 1, again with a timed-access procedure. Note that the EWT bit only controls whether
the reset is issued, not whether the timer runs. The watchdog timer must now be reset prior to 122,800
machine cycles or it will reset the CPU. If the watchdog timer is not used, clear the EWT bit to a logic 0
using a timed-access procedure. Since the EWT bit is nonvolatile, this ensures the watchdog-reset
function remains disabled.
If operation without the watchdog timer is desired, the EWT bit should be cleared following any type of
reset by using the timed-access register. This ensures the watchdog timer never causes an undesired reset
during execution of the application software.
During subsequent program execution, the watchdog timer can be reset by a timed-access write operation
that sets the RWT bit to 1. This causes the watchdog timer to begin counting machine cycles again from
an initial count of 0. The RWT bit is automatically cleared immediately after the watchdog timer is reset.
The following code fragments illustrates the reset of the watchdog timer:
70 of 187
Page 71

Secure Microcontroller User’s Guide
DS5000FP
Not Supported
Not Supported
DS5001FP
Yes
Yes
DS5002FP
Not Supported
Yes
MOV 0C7H, #0AAh ; 1st TA Value
MOV 0C7H, #055h ; 2nd TA Value
SETB IP.7 ; Reset Watchdog Timer
If the timeout period expires without the timer being reset by the software, the Watchdog Timer will reset
the CPU, set the WTR status flag (regardless of whether the reset is enabled), and start counting again.
The WTR flag allows the application software to distinguish this type of reset from other reset so that
special processing can be performed to accommodate this case. The WTR bit is cleared only by a read of
the PCON register. Therefore, this register should be read during initialization following a reset in order
to properly interpret the source of the reset. The Watchdog Timer is also reset by any other type of reset
and will begin its count as soon as the reset condition is released.
The Watchdog Timer Reset Bit (WTR) is held in a logic 1 state for 8192 clock cycles following the timeout of the watchdog 122,880 cycle counter. During this time, the bit may be read but attempts to clear the
bit will fail. This condition will not be noticed if the Enable Watchdog Timer bit (EWT) is set, because
the 8192 cycle count will be reset during the device reset triggered by the watchdog time-out. The bit may
then be cleared, if desired, during application’s power-on reset routine.
Some applications may use the watchdog timer but not set the EWT bit, preferring instead to poll the
WTR bit in software to detect a watchdog time-out. In this case, one approach is for the application
software to continually read the EWT bit as long as it is set. When the 8192 clock cycle period is
complete, the last read of the EWT bit will successfully clear the bit and exit the routine. Alternatively,
software can poll the WTR bit until it is set, then reset the watchdog via the RWT bit to clear the 8192
cycle count. The next read of the PCON register will clear WTR bit as expected.
8.3 CRC Memory Verification
When using nonvolatile memory, there is always the potential for a catastrophic event to alter the
memory contents. These events include lightning, massive ESD, severe mistreatment, etc. No nonvolatile
technology is immune to these events. To compensate, the DS5001/DS5002 series contain circuitry that
enables the microcontroller to perform a CRC function, as summarized below. The DS5002FP does not
support the automatic CRC on power-up feature because the sequential memory access of a CRC could
make it easier for a outsider to gain information about the system.
PART AUTOMATIC CRC ON POWER-UP HARDWARE SUPPORT FOR SOFTWARE CRC
8.3.1 Automatic CRC on Power -Up Feature
If the CRC option is selected through the Bootstrap Loader, then on power up or after a Watchdog Timer
reset, the microcontroller will automatically perform a CRC-16 on the memory. The range over which it
is performed is selected by the user, and the result is compared to a pre-stored value. If the CRC-16 is in
error, the DS5001 series microcontroller will enter the Bootstrap Loader and wait. From the perspective
of the system, the appears held in a reset condition.
71 of 187
Page 72

Secure Microcontroller User’s Guide
RNGE3
RNGE2
RNGE1
RNGE0
—
—
MDM
CRC
This function is supported in the CRC register, accessible via the Bootstrap Loader. Setting the CRC bit
(LSB) enables the power-up CRC function. The upper nibble of the CRC register (values 0h–Fh) defines
the address space in 4kB blocks over which the CRC calculation is performed. For example, if the nibble
is set to 0001b, the CRC range is from 0000 to 0FFFh. Once the LSB of the CRC register is set, the
loader “I” command will cause the CRC of the specified block to be computed. The result is
automatically stored in the last two bytes of the specified block. These bytes should not be used by the
application. This computation will be correct provided that the CRC range is less than or equal to the
partition if PM = 0. If PM = 1, using 32kB RAMs, the CRC range must be less than or equal to the
program range.
If CRC is enabled, the DS5001FP will automatically invoke the Bootstrap Loader on either power-up or a
Watchdog timeout and the CRC check will be performed. If an error is detected, the Bootstrap Loader
will wait for reloading. If there is no error, the application will begin at address 0000h following a reset.
Automatic checking of the CRC can be disabled by writing a 0 to the CRC register LSB. As mentioned
above, this is done using the “W” command in loader mode. The CRC hardware uses registers 0C3h and
0C2h for most and least significant byte intermediate storage.
DS5001 CRC REGISTER (Address 0C1h)
CRC.7-4 RANGE 3–0
Determines the range over which a power-up CRC will be performed. Addresses
are specified on 4kB boundaries.
Initialization: Reset to 0 on a no-V
Read Access: Can be read at any time.
Write Access: Cannot be written by application software. Can be written by bootstrap loader.
CRC.1 MDM
When set to 1, the bootstrap loader attempts to use a modem (UART) on PE4 if
CRC is incorrect. This feature is no longer useful following the obsoletion of the
corresponding modem devices.
Initialization: Reset to 0 on a no-V
Read Access: Can be read at any time.
Write Access: Cannot be written by application software. Can be written by bootstrap loader.
CRC.0 CRC
When set to 1, a CRC check is performed on power-up or watchdog timeout. CRC
is checked against stored values. An err or initiates program load mode. This bit is
not present in the DS5002, as the device does not support the power-on CRC
function.
Initialization: Reset to 0 on a no-V
Read Access: Can be read at any time.
Write Access: Cannot be written by application software. Can be written by bootstrap loader.
reset.
LI
reset.
LI
reset.
LI
As mentioned, the CRC-16 hardware is available to the application software. Although a CRC could be
computed completely in software, the process is much faster if the DS5001/DS5002 CRC-16 hardware is
used. This feature can perform a CRC-16 on 64kB of memory in approximately 500ms. In addition, the
CRC-16 is a superior method of checking the file validity compared to a checksum.
72 of 187
Page 73

Secure Microcontroller User’s Guide
This routine tests the CRC-16 circuit in the DS5001/DS5002FP
crcmsb
equ
0C3h
crclsb
equ
0C2h
org
00h
; after reset, CRC regs = 0000
begin:
mov
p2, crcmsb
;p2 = 00 read crcmsb register
mov
p3, crclsb
;p3 = 00 read crclsb register
mov
crclsb, #075h
;check crc register operation
;data in = 75 result = E7C1
mov
crclsb, #08Ah
;data in = 8A result = 37A7
mov
crclsb, #00Bh
;data in = 0B result = 7D37
mov
crclsb, #075h
;data in = 75 result = 31FD
mov
crclsb, #0C7h
;data in = C7 result = 13B1
mov
crclsb, #0AAh
;data in = AA result = 0B53
mov
crclsb, #075h
;data in = 75 result = DA8A
mov
crclsb, #0C7h
;data in = C7 result = 351A
mov
crclsb, #055h
;data in = 55 result = F474
mov
crclsb, #043h
;data in = 43 result = D6B5
nop
;delay after last write and before first read
;let CRC finish
mov
p0, crcmsb
;p0 = D6 read CRCMSB register
mov
p1, crclsb
;p1 = B5 read CRCLSB register
mov
crclsb ,crclsb
;clear CRC, data in = B5 result = 00D6
nop
;need delay
mov
crclsb ,crclsb
;cleared, data in = D6 result = 0000
nop
mov
p2, crcmsb
;p1 = 00 read crcmsb register
mov
p3, crclsb
;p1 = 00 read crclsb register
end_loop:
sjmp
$
end
The CRC-16 logic is accessed via the CRCMSB and CRCLSB SFRs mentioned above. The software
must sequentially write the memory values into the CRC LSB at location 0C2h. After a delay of one
instruction cycle, the 16-bit result will be available at 0C3h and 0C2h. When using the CRC-16 hardware
as part of an application, the CRC should first be cleared by writing the LSB back twice with a delay in
between for computation. This process makes the CRC-16 result equal to 0000h. The code example
shown in Figure 8-2 displays the CRC-16 result on ports 0 and 1.
Figure 8-2. CRC Code Example
73 of 187
Page 74

Secure Microcontroller User’s Guide
Security Lock
Yes
Yes
Yes
RAM memory
Yes
Yes
Yes
Encrypted memory
None
Yes, user must enable
Yes
Encryption Key
None
48 bits
80 bits (64 bits rev Bx)
Encryption Key Selection
None
User selected
True random number
Encryption Keys loaded
N/A
When user selects
Automatic, any new load/dump
Dummy bus access
None
Yes, when encrypted
Yes
On-chip Vector RAM
None
Yes, when encrypted
Yes
Self-Destruct Input
None
None
Yes
Die Top Coating
None
None
Optional (only on DS5002FPM)
Random Number Generator
Yes
None
Yes
9. FIRMWARE SECURITY
One of the outstanding features of the secure microcontroller is its firmware security. The family far
surpasses the standard offering of ROM-based microcontrollers in keeping system attackers or
competitors from viewing the contents of memory. In a standard EPROM-based microcontroller, a
knowledgeable attacker can disable the EPROM security bit and have access to the entire memory
contents. The secure microcontroller’s improved security makes it a natural choice for systems with high
security requirements such as financial transaction terminals. However, the firmware security can also be
employed to keep competitors from copying proprietary algorithms. Allowing access to these algorithms
can create an instant competitor. This section describes the security features and their application. Also
included are guidelines to using microcontroller security within the framework of total system security.
As with memory map control, there are variations between the different secure microcontroller versions.
The original DS5000 has a high level of firmware security and the DS5002 has added several distinct
improvements. Note that the DS5001 has only minimal security and should only be applied when other
physical security is used or when security is not needed.
Security Overview
The usefulness of the security features are evident in an application dispenses services on a pay per
service basis. Electronically bypassing the security would allow the dispensing of the service for free,
resulting in lost revenue to the system owner. Another common application is the transmission of secret
information. The user’s algorithm and key data could be observed in an unsecured system, resulting in a
break in the secure transmission. The secure microcontroller family protects the contents of memory from
being viewed. This is done with a combination of circuit techniques and physical security. The
combination is a formidable defense. Regardless of the application, the secure microcontroller protects
the contents of memory from tampering and observation. This preserves secret information, access to
services, critical algorithms etc. The security features of the secure microcontroller include physical
security against probe, memory security through cryptographic scrambling, and memory bus security
preventing analysis of the CPU’s operation. The table below provides a brief summary of the versions
and their security features. A detailed description of each feature follows. In the description, elements that
are unique to a particular secure microcontroller version have that version underlined.
FEATURE DS5001 DS5000 DS5002
9.1 Security Lock
The easiest way to dump (view) the memory contents of a secure microcontroller is using the bootstrap
loader. On request, the loader will transfer the contents of memory to a host PC. The security lock
prevents this. The lock is the minimal security feature, available even in the DS5001FP. Once set, the
security lock prevents the loader from accessing memory. In fact, no loader commands (except Unlock)
will work while the lock is set. The security lock is similar in function to an EPROM security bit on a
74 of 187
Page 75

Secure Microcontroller User’s Guide
single-chip microcontroller, in that it prevents a programmer from reading the memory. In addition, the
security lock prevents the microcontroller from executing code on the expanded bus of Ports 0 and 2.
Thus an attacker cannot add a memory and use MOVC instructions to would force the microcontroller to
read out the contents of protected memory. However, the secure microcontroller security lock does
provide one important difference from EPROM security bits. When the security lock is cleared, it
destroys the RAM contents. If a knowledgeable user were to physically erase the security bit in an
EPROM-based microcontroller, the memory contents would remain to be read. The security lock consists
of a multiple bit latch distributed throughout the microprocessor with circuits that collapse the lock in the
event of tampering. Clearing the lock starts an irreversible destructive process that acts differently for
each device as described below.
In a DS5001 clearing the lock causes the loader to manually write over the first 32KB of NV RAM with
zeros. Thus the contents of memory would be erased. This is obviously a low level of security but deters
casual inspection. In a DS5000 or DS5002, clearing the lock causes an instantaneous erasure of the
Encryption Key and Vector RAM. This action is unpreventable once the lock is cleared and happens
independent of VCC or operating frequency. Once the erasure has occurred, a DS5000 assumes a
nonsecure state. In a DS5002, the Loader proceeds to load a new Encryption Key once the erasure has
occurred. In both, the Bootstrap Loader will then proceed to overwrite the first 32KB of RAM if power is
available and the crystal is still present. Thus the instantaneous erasure of the Encryption Key effectively
renders the contents of memory useless since it can no longer be properly deciphered.
The Security Lock is set via the Bootstrap Loader using the “Z” command. Once issued, the Loader will
continue to communicate with a user but will not perform other commands. The Loader will respond with
an error message in the event that further commands are issued. While the Lock is set, the Loader has no
access to the Byte–wide bus memory. The Security Lock can be cleared using the “U” command. Issuing
this command to a locked part results in the destructive process described above. No confirmation is
requested. The status of the Security Lock can be read by application software at MCON.0. This bit is
only a status flag and cannot be affected by user software.
Important Application Note
The memory contents of a secure microcontroller are not secure unless both the security lock bit is set
AND the memory encryption feature is activated via the bootstrap loader. (The memory encryption
feature is activated automatically in the DS5002FP) Failure to set the lock bit may result in incomplete
protection of the memory contents.
9.2 RAM Memory
NV RAM provides a useful way to store program and data. The contents can be retained for a long
period, but can be changed when desired. This attribute is important when considering security. No matter
what probing techniques are used on a ROM, the contents remain unaffected. With resources and
patience, a determined attacker will obtain the contents of a ROM based product. NV RAM can be
destroyed on demand. The user’s physical security must simply remove the power (VCC and V
microprocessor chip to eliminate the memory contents. Thus NV RAM provides flexibility as well as
security. Enough physical security can be combined with even a DS5001 to provide a very secure system.
The DS5002 even provides a direct facility to destroy memory discussed below.
75 of 187
) from a
BAT
Page 76

Secure Microcontroller User’s Guide
9.3 Encrypted Memory
The heart of secure microcontroller security is the memory encryption function. Since the NV RAM is
visible, the memory contents and memory bus are encrypted. That is, in real-time, the addresses and data
moving between the RAM and the microcontroller are scrambled by on-chip encryption circuits. Thus, an
attacker that observes the RAM contents or memory bus sees unintelligible addresses and data.
Figure 9-1 shows the conceptual diagram of the memory encryptor for a DS5000 series device. Figure 9-2
shows the encryptor for a DS5002.
Figure 9-1. DS5000 Software Encryption Block Diagram
In a DS5000, the encryption feature is optional. A DS5000 can be locked irrespective of its encryption
and encrypted irrespective of the lock. Neither makes much sense by itself. The encryption process is
enabled by loading an Encryption Key for the first time. Prior to loading a Key, the DS5000 remains in a
nonencrypted state. Once encrypted, the memory interface will remain so until a part is locked, then
unlocked. The process of clearing the Security Lock deactivates the encryption circuits. Note that an
Encryption Key of zero is still a valid Key. The DS5002FP is a superior security device, as it has
encryption enabled at all times and generates its own security keys.
Encryption logic consists of an address encryptor and a data encryptor using separate but related
algorithms. These encryptors are high-speed, bidirectional, and repeatable circuits that are transparent to
the application software. Addresses and data that are scrambled prior to writing to RAM will be correctly
unscrambled when reading. Each encryptor operates with its own algorithm but both are dependent on the
Encryption Key. Encryptors operate while programs are being loaded so that the memory contents are
stored in its scrambled form. When program memory is fetched, the process is reversed. Thus the actual
program or data is only present in its “true” form while inside the microcontroller.
76 of 187
Page 77

Secure Microcontroller User’s Guide
Figure 9-2. DS5002 Software Encryption Block Diagram
The address encryptor translates each “logical” address, i.e., the normal sequence of addresses that are
generated in the logical flow of a program, into an encrypted address (or physical address) at which the
byte is actually stored in RAM. Each time a logical address is generated either during program loading or
during execution, the address encryptor circuits use the Encryption Key value and the address itself to
form the physical address that will be presented to the RAM on the Bytewide bus. The encryption
algorithm is such that there is one and only one physical address for every possible logical address. The
address encryptor operates over the entire memory range.
The Data Encryptor operates in a similar manner to the address encryptor. As each byte including op
code, operand, or data is received during Bootstrap Loading, its value is scrambled prior to storing it in
RAM. The value that is actually written in RAM is an encrypted representation. All values that are
subsequently stored in RAM during execution also are encrypted. As each byte is read back to the CPU
during execution, the internal Data Encryptor restores it to its original value. This encryptor uses the
Encryption Key and the data value itself, but also the logical address. Thus the same data with the same
Key will have different physical values at different address locations. The data encryption algorithm is
repeatable and reversible so that with the same key, data and address, the same encrypted value will be
obtained. Note however that there are many possible encrypted data values for each possible true value
due to the algorithms dependency on Key and address.
Using the combination of address and data encryption, the normal flow of program code is unintelligible
in the NV RAM. What had been a sequential flow of addresses is now apparently random. The values
stored in each memory location appear to have no relation to the original data. Another factor that makes
analysis more difficult is that all 256 possible values in each memory are valid possibilities. Thus an
encrypted value is not only scrambled, but it becomes another potentially valid byte.
77 of 187
Page 78

Secure Microcontroller User’s Guide
Different memory areas are encrypted in the DS5000 and DS5002. For a DS5000, all memory accessed
under CE1 can be encrypted. CE2 is not encrypted. This allows access to peripherals such as a Real-time
Clock to be performed using CE2. For the DS5002, encryption is performed on all bytes stored under
CE1– CE4. The memory or peripherals accessed by PE1–PE4 on a DS5002 are not encrypted.
9.4 Encryption Algorithm
The secure microcontroller family uses a proprietary encryption algorithm. The DS5000FP and
DS5002FP use different encryption algorithms, with the DS5002FP being the most secure, with a longer
encryption key than the DS5000FP and an encryption algorithm that is more nonlinear. In addition, the
DS5002FP memory encryptor uses elements of the DES (Data Encryption Standard), although not the
entire algorithm. The encryption algorithm is supported by the fact that both address and data are
encrypted, the algorithm and key are both secret, the most critical data can be stored on chip in vector
RAM (discussed below), and the bus activity is scrambled using dummy access (discussed below). For
this reason, a security analysis of the DS5002FP is much more complicated than a simple mathematical
treatment of the encryption algorithm.
9.5 Encryption Key
The DS5000FP uses a 40-bit Encryption Key that is stored on-chip. As mentioned above, the Key is the
basis of the encryption algorithm. Tampering with or unlocking the microcontroller will cause the Key to
be instantaneously destroyed. If the memory contents are encrypted, they become useless without this
Key. A user selects the 40-bit Key and loads it via the bootstrap loader. Selecting this Key enables the
encryption feature. The DS5002FP uses an 80-bit Key. It is similarly stored on-chip in tamper resistant
circuits. Using a wider Key gives the encryption more complexity and more permutations that must be
analyzed by an attacker. Apart from the Key width and encryptor complexity, the principal differences
between the DS5000FP and DS5002FP are discussed below under Key selection and loading.
9.6 Encryption Key Selection and Loading
One of the significant differences between DS5000FP and DS5002FP lies in encryption key management.
In the case of a DS5000FP, the user must select a 40-bit key during program loading. This Key must be
selected prior to loading the microcontroller, as the memory will be encrypted as it is loaded. The Key
selection process must be protected since an attacker that learns the Key can reproduce the user’s code.
This would be done by loading the correct Key in an unlocked DS5000FP, attaching the encrypted
memory chip, and dumping the code using the Bootstrap Loader.
The DS5002FP provides an improved Key management system. The microcontroller chooses its own
80-bit Encryption Key from a number that is internally generated and secret. The Keys come from a true
hardware random number generator. There is no method to discover the Key value, and no attacker can
force the DS5002 to a particular Key. In addition, no one can “forget” to enable the encryptor, since it is
always enabled. An additional advantage of the secret Key is that an attacker cannot “characterize” the
encryptor by repeatedly loading known Keys and observing the result.
As mentioned above, encryption is always enabled on the DS5002FP. Each time the Bootstrap Loader is
invoked, a new random number is prepared. If a Fill, Load, Dump, Verify, or CRC command is
requested, the Loader selects the random number as a new Encryption Key prior to accessing the
memory. Execution of a Load or Fill command results in the data being loaded in an encrypted form
determined by the value of the newly-generated Key. Any subsequent Dump, Verify, or CRC within the
same Bootstrap session will cause the contents of the encrypted RAM to be read out and properly
78 of 187
Page 79

Secure Microcontroller User’s Guide
decrypted by the micro. Once a new Key is loaded, it will allow all commands to work properly within
the same Bootstrap session since memory access is done using the correct Key. Exiting and re-entering
the Bootstrap Loader, then doing a Dump will not work since this action would first result in Loading a
new Encryption Key. The microcontroller would no longer be able to decrypt the RAM contents. This
extra precaution is used regardless of the Security Lock. It prevents an attacker from retrieving memory
through the Bootstrap Loader even if the programmer forgets to lock the DS5002FP. Once the Security
Lock is set, all Bootstrap Loader access to the memory is prohibited.
9.7 Dummy Bus Access
The secure microcontroller disguises its memory contents through encryption. Additional steps are also
used to prevent analysis of the bus activity by 8051-savy hackers. Both the DS5000FP and DS5002FP
insert dummy MOVX read operations when possible. In the 8051 architecture, there are typically two
identical memory accesses per instruction cycle, but most operations so nothing with the second program
fetch. In the secure microcontroller, a pseudo-random address is generated for the dummy cycle and this
random memory address is actually fetched, but the dummy data is discarded. The real and dummy
accesses are interleaved according to a pseudo-random process so that the execution always appears the
same. During these pseudo-random cycles, the RAM is to all appearance read. Thus by repeatedly
switching between real and dummy access, it is impossible to distinguish a dummy cycle from a real one,
and a large percentage of the memory fetches will be garbage that has no meaning. The dummy accesses
are always performed on a DS5002FP, but are only used on a DS5000FP when encryption is enabled.
9.8 On-Chip Vector RAM
A 48-byte RAM area is incorporated inside the DS5000FP and DS5002FP. This area maps to the first 48
locations of program memory to store reset and interrupt vectors. Any other data stored in the first 48
locations will be contained in this Vector RAM. The principal reason for the Vector RAM is that the reset
and interrupt vectors are known logical addresses in the 8051 family. Thus an attacker could force a reset
or interrupt and discover the encrypted address generated by the secure microcontroller. By storing these
Vectors in on-chip RAM, it is impossible to observe such relationships. Although it is very unlikely that
an application program could be deciphered by observing the vector addresses, the Vector RAM
eliminated this possibility. Note that the dummy accesses discussed above also occur while the Vector
area is being accessed.
The Vector RAM is automatically loaded with the reset and interrupt vectors during Bootstrap Loading.
This feature is transparent to operation and no action is required to use it. However, considering the
Vector area feature can improve overall system security. As mentioned above, the Vector RAM is
instantaneously destroyed in the event of an unlock (also by a self-destruct on DS5002FP). Since it is
hidden and subject to destruction, the 48 bytes are the most secure memory in a system. Thus the most
critical constants can also be stored there. This is an ideal location for storing DES keys for applications
involving data encryption such as electronic funds transfer.
The Vector RAM is always used on a DS5002FP. The data stored between logical location 00h and 30h
will be loaded into and executed for the Vector RAM. This data will not be duplicated in NV RAM
accessed by the Bytewide bus. The operation of DS5000FP Vector RAM is the same, but only when the
encryption feature is enabled. When a DS5000FP has not had an Encryption Key loaded, the Vector
RAM is left unused.
79 of 187
Page 80

Figure 9-3. Dummy Bus Access Timing
Secure Microcontroller User’s Guide
9.9 Self-Destruct Input
The self-destruct input (SDI) is an active-high input pin designed to be used with external tamperdetection circuitry. The SDI feature operates in both powered (VCC > 4.5V) and battery-backed (VCC <
4.5V) modes. To guard against accidental activation, the pin is debounced, with accept and rejection
criteria as shown in the DC electrical characteristics (refer to data sheet). Once activated, the SDI pin
instantaneously clears the security lock, initiating the sequence of events described in the Security Lock
section. In addition, the microprocessor erases its external memory by:
1) Removing power from the V
2) Removing power from all bytewide bus control signals (CEx, R/W, etc.)
3) Grounding address and data lines to remove excess charge that could help retain data.
CCO
pin
80 of 187
Page 81

Secure Microcontroller User’s Guide
Once activated, the SDI event duration is determined by the state of VCC and the SDI pin. Once both VCC
> 4.5V and SDI = 0 are met, SDI remains active for an additional 1792 machine cycles before exiting the
SDI state.
9.10 Microprobe/Die Top Coating
The DS5002FPM is provided with a special top-layer coating that is designed to prevent a microprobe
attack. The coating is implemented with a second layer of metal on the microcontroller die. This metal
will result in a short circuit of critical functions if probing is attempted. The probing action destroys the
data that is secret. Also, security circuits and Vector RAM derive their power from this screen. Therefore
they will be de-powered if the top coating is removed, also destroying the secret data. In this event, any
critical data stored on-chip will be destroyed and off-chip data is rendered useless.
9.11 Random Number Generator
The DS5002FP incorporates a random number generator used by the bootstrap loader to generate
encryption keys. The application software can also use it to improve overall system security.
For example, to foil an attacker developing a histogram of code execution, the random number generator
could be used to decide how long to spend on particular activities. The output of the DS5002FP random
number generator should be hashed to get uniform random numbers. Using random numbers that have
been run through a linear feedback shift register (LFSR), such as CRC-16, will pass the suite of tests
defined in section 4.11.1 of the Federal Information Processing Standards Publication 140-1 (FIPS PUB
140-1), Security Requirements for Cryptographic Modules.
The random number is created 8 bits at a time. They are obtained by the application code at SFR location
0CFh. The random number takes 160µs to develop. Reading a byte from register 0CFh starts the
generation of another random number. After the random number is read, another is available
approximately 160µs later. The RNR bit (RPCTL.7; 0D8h) is set to logic 1 each time a new number is
available. If the random number is read prior to RNR being set, the value is 00.
9.12 Security Summary by Part
The preceding information outlined each of the security features. Their inclusion in various parts is shown
in the table at the beginning of this section. For completeness, the following is a summary description of
security features for each part in the secure microcontroller family.
DS5000FP/DS5000(T)/DS2250(T)
The DS5000 is the second generation of a microcontroller with security. The first is an earlier version of
DS5000 circa 1988, now obsolete. The DS5000 incorporates a combination of real-time memory
encryption and Security Lock. The memory encryption is optional however. To invoke the encryption, the
user must select a 48-bit encryption key using the bootstrap loader. A user then loads the memory that is
automatically encrypted using this key. After the memory is loaded and verified, the DS5000 can be
locked. Locking the micro prevents an attacker from using the bootstrap loader to decrypt and dump the
memory contents. Unlocking the DS5000 destroys the encryption key and vector RAM. Vector RAM is
48 bytes of secret storage on-chip. It is used to hold reset and interrupt vectors as well as any application
values than must be hidden. In addition to encrypting the memory, the DS5000 generates dummy bus
cycles to obscure the actual program flow. Dummy cycles appear to be actual memory fetches but are not
actually used inside the microcontroller. Also fundamental to the security of a DS5000 is its basis on
RAM. This allows all security features to be changed frequently. The strategy is that an attacker must
81 of 187
Page 82

Secure Microcontroller User’s Guide
spend a long time breaking into the DS5000, but the user can simply change system security at any time.
Thus any stolen information has a very limited lifetime.
DS5001FP/DS2251T
The DS5001 is a newer product than the DS5000, but has less security. It is useful in systems that need a
large memory, but that provide sufficient physical security for all needs. The DS5001 incorporates a
security lock. This is used to prevent the bootstrap loader from dumping memory. Once locked, the
bootstrap loader cannot access the memory. Unlocking the DS5001 causes the bootstrap loader to write
over the NV RAM. The RAM nature of the DS5001 product allows a user to vary security frequently and
to manually destroy it if necessary.
DS5002FP/DS2252(T)
The DS5002 adopts the memory and I/O improvements of the DS5001 and improves on the security of
the DS5000. It is a high security version of the DS5001. This device is intended for maximum security
and has numerous improvements to the DS5000. The security is always enabled on a DS5002. Thus an
attacker cannot characterize the security and the user cannot forget to enable the security. The DS5002
follows a similar scheme of memory encryption and Security Lock. The DS5002 encryptor is a superior
algorithm using an 80-bit encryption key. In addition, the Key is managed by the DS5002. Using the
Bootstrap Loader, each part generates a random number for its 80-bit Key prior to loading memory.
Leaving and reentering the Bootstrap loader causes the DS5002 to select a new number as a potential
Key. Any subsequent memory access with the Loader causes the new Key to be installed. Like the
DS5000, the DS5002 also uses dummy bus access and Vector RAM to further hide memory bus activity.
The Security Lock of a DS5002 is similar in nature to the DS5000. Once locked, the DS5002 Bootstrap
Loader does not have access to memory. Unlocking the DS5002 destroys the Encryption Key and Vector
RAM. The NV RAM accessed by the Bytewide bus is also manually erased under Bootstrap Loader
control. The DS5002 provides an external method to clear the Security Lock using its Self-Destruct Input
(SDI). This causes the erasure of the Key and Vector RAM and also removes power from the NV RAM.
The DS5002FPM provides an internal metal microprobe shield to prevent microprobing of the die.
9.13 Ap pl ication: Advanced Security Techniques
The secure microcontroller family has been used for numerous applications requiring security. Different
levels of security are required depending on the sensitivity of the application and the value of the
protected information. As mentioned above, the goal of the microcontroller security is to make stealing
the protected information more difficult than the information is worth. This task actually has two pieces.
First, the secure microcontroller makes attack difficult. This is combined with the user’s physical security
to make information retrieval difficult. The second part is to make the protected information less
valuable. To this end, the NV RAM nature allows a user to frequently alter the firmware based security
aspects of the system. Thus if the critical information changes before the security can be broken, the
information that is actually retrieved will be worthless. To assess the security of a system, the total
implementation must be examined. The DS5000FP or DS5002FP provide a high level of security, but the
user’s firmware can accidentally defeat some features. A sampling of implementation issues that will
make the DS5000FP or DS5002FP more difficult to crack is discussed in the following paragraphs. There
are also suggestions on making a system more secure using external circuits.
Avoid Clear Text
The encryption algorithms used by DS5000FP or DS5002FP are generally adequate to prevent analysis
when combined with well-developed code. However, the encryption is defeated to some extent if the user
82 of 187
Page 83

Secure Microcontroller User’s Guide
stores text that appears on a display in encrypted form. This gives the pirate a starting point to look for the
clear text in encrypted storage and analyze the encryption algorithm. The “data answer” is already known.
If clear text is required, then preferably store it in nonencrypted memory. If this is impractical, then
disperse it so that it is hard to find. Avoid at all costs reading the clear text from memory then
immediately displaying it. This is a sure means to identify the encrypted values of the text for the
attacker.
Avoid CRC or Checksum
Running a checksum on power up provides the pirate with a sequential listing of the addresses in
encrypted form. Therefore the attacker has a great advantage in deciphering the Address Encryptor.
Preferably avoid a checksum. If one is needed, then check the minimum amount of memory and perform
the check in nonsequential fashion.
Avoid Long Straight Runs of Code
A common coding practice is to run numerous sequential operations. This is common knowledge and
should be avoided. The pirate can use this in the same way as a checksum process. It provides a
sequential listing of encrypted addresses and assists with analysis of the address encryption. This problem
can be avoided by using occasional jump commands in the software.. These can be jumps for no reason
other than to space out straight runs of code. However, using jumps also provides several other techniques
to make bus analysis more difficult. As an example, the code can jump into Vector RAM. While in this
area, dummy access will occur on the bus.
Use Random Values
The Random Number Generator of the DS5002FP can be used to make a pirate’s task more difficult.
When time is available, the software should perform random actions at random time intervals. As an
example, the Random Number Generator can be used to select a timer interrupt value. Thus the
microprocessor will be interrupted at random intervals making characterization very difficult. Software
can elect to out of Vector RAM for a random period of time. Also as discussed above, the microprocessor
generates dummy RAM reads when possible. However, it cannot generate dummy writes. However the
user’s code can. Random numbers can be written to address that are known to be unused. If this is done
while the microprocessor is visibly performing a meaningful task, it will make analysis very difficult.
Vector RAM
As mentioned above, the Vector RAM can be used for many things beside vectors. This is the most
secure storage in the system. It resides on-chip behind tamper protection. Thus it is useful for storing the
most sensitive data. Thus even an attacker could break the encryption, this information would still be
secret. For EFT or similar applications, this is a good location for the storage of DES keys. Since DES is
a public algorithm, the real protection is keeping the DES key secret. As this is only 8 bytes, it fits well
within the Vector RAM.
Change Code
Perhaps most importantly, the user should reprogram portions of the secure microcontroller that deal with
security. For example, if the microprocessor is performing DES, the user can change DES keys. Any
security system can be broken with enough time and resources. By altering the security features, this
threat can be minimized.
83 of 187
Page 84

Secure Microcontroller User’s Guide
External Circuits
A variety of external circuits can support secure operation. For example, the DS2401 is a unique 48-bit
silicon serial number. If it is installed with the microprocessor, it can be read when the system is first
powered up, then stored inside the secure microcontroller. This serializes the system. If the software ever
finds a different serial number (or missing number) from the stored one, it can refuse to work. This would
mean that the microprocessor had been moved.
Tamper Protection
Using a variety of tamper sensors in conjunction with the DS5002 makes the system very difficult to
crack. These circuits vary from simple switches to light, temperature, pressure, or oxygen sensors. When
the physical security is violated, the SDI pin is activated and the memory contents are destroyed.
84 of 187
Page 85

Secure Microcontroller User’s Guide
10. RESET CONDITIONS
10.1 Reset Sources
The secure microcontroller family provides proper reset operation with a minimum of external circuitry.
In fact, for many applications, external reset circuitry is not required. The possible sources of reset are:
a) Power-on (operating voltage applied to VCC)
b) No-VLI power-on
c) External RST pin
d) Watchdog timeout
Certain actions are taken in all cases where a reset has been issued. Whenever any type of reset is
executed, the ALE and PSEN quasi-bidirectional pins are configured as inputs. In addition, an internal
reset line (IRST) is active continuously until the condition that is causing the reset has been removed.
SFRs are initialized during reset as shown in Table 10-A. Reset Status Bits contains a summary of the bits
that indicate the source of the most recent reset.
Reset Status Bits
PCON.6 POR
Power-On Reset Indicates that the previous reset was initiated during a power-on.
Initialization: Cleared to 0 whenever a power-on reset occurs; remains unchanged on
other types of resets. Must be set to 1 by softwar e.
Read Access: Can be read normally anytime.
Write Access: Can be written only by using the timed-acce ss r egister.
PCON.4 WTR
Watchdog Timer Reset Set to 1 when a timeout condition of the watchdog timer occurs. Cleared
to 0 immediately following a read operation.
Initialization: Set to 1 on a watchdog timeout reset. Remains unchanged on any other
type of reset.
Read Access: Read normally anytime.
Write Access: Not writable.
PCON.2 EWT
Enable Watchdog Timer The watchdog timer is enabled if EWT = 1 and is disabled if EWT = 0.
This is not technically a status bit but can indicate a no-V
Initialization: Cleared to 0 on a no-V
types of reset.
Read Access: May be read normally anytime.
Write Access: Writeable only by using the timed-access register.
power-on reset. Remains unchanged during other
LI
reset condition.
LI
85 of 187
Page 86

Table 10-A. SFR Reset States
REGISTER
LOCATION
RESET CONDITION
RESET TYPE
PC
N/A
000h
All
ACC
E0h
00h
All B F0h
00h
All
PSW
D0h
00h
All
SP
81h
07h
All
DPTR
83h, 82h
0000h
All
P0–P3
80h, 90h, A0h, B0h
FFh
All
IP
B8h
0XX00000b
All
IE
A8h
0XX00000b
All
TMOD
89h
00h
All
TCON
88h
00h
All
TH0
8Ch
00h
All
TL0
8Ah
00h
All
TH1
8Dh
00h
All
TL1
8Bh
00h
All
SCON
98h
00h
All
SBUF
99h
XXXXXXXXb
All
0UUU0U00b
0U010U00b
External reset
Watchdog timer
UUUUUU0Ub
UUUUUU0Ub
External reset
Watchdog timer
UUUUU0UUb
UUUUU0UUb
External reset
Watchdog timer
UUh UUh UUh UUh UUh
UUh UUh UUh UUh UUh
External reset
Watchdog timer
0X00000Ub
0X00000Ub
External reset
Watchdog timer
Status (DS5001/2)
DAh
00h
All
RNR (DS5001/2)
CFh
XXh
All
UUUUXXUUb
UUUUXXUUb
External reset
Watchdog timer
CRC High (DS5001/2)
C3h
00h
All
CRC Low (DS5001/2)
C2h
00h
All
Secure Microcontroller User’s Guide
PCON 87h
MCON (DS5000) C6h
MCON (DS5001/2) C6h
Encryption Key (DS5000) N/A
RPCTL (DS5001/2) D8h
CRC (DS5001) C1h
00000U00b
00000000b
UUUUUU0Ub
11111000b
UUUUU0UUb
11111000b
UUh UUh UUh UUh UUh
Disabled
0X00000Ub
0X000000b
UUUUXXUUb
0000XX00b
Power-on reset
No-V
reset
LI
Power-on reset
No-V
reset
LI
Power-on reset
No-V
reset
LI
Power-on reset
No-V
reset
LI
Power-on reset
No-V
reset
LI
Power-on reset
No-V
reset
LI
X indicates a bit that is indeterminate on a reset. U indicates a bit that is unchanged from its previous state on a reset.
86 of 187
Page 87

Secure Microcontroller User’s Guide
10.1.1 Power-On Reset
The secure microcontroller family provides an internal power-on reset capability that requires no external
components. When voltage is applied to the VCC pin from a power-off condition, the device automatically
performs an internal reset sequence to prepare the processor for execution of the application software.
The traditional capacitor reset circuit should not be used. Figure 10-1 illustrates the timing associated
with the power-on reset cycle.
Figure 10-1. Power-On Reset Timing
This cycle begins with power-on reset delay time. This is generated by the internal control circuitry to
allow the internal clock oscillator to start up from its halted state that is in effect when VCC is below
V
shown as t
. The period t
CCMIN
is a mechanical startup time that is dependent on the individual crystal. The delay
CSU
in the figure is generated by internal circuitry that counts a total of 21,504 (1.792ms at
POR
12MHz) clock oscillator periods before it allows the internal reset line to be released. The purpose of this
delay is to allow time for the clock frequency to stabilize.
The power-on reset delay is not the total amount of time that must pass before execution can begin in the
application from the initial application of VCC v oltage. First the power supply slew rate is required for
VCC to rise from 0V to the V
threshold shown in Figure 10-1. Next, operation with a crystal is partly
CCMIN
mechanical and some time is required to get the mass of the crystal into vibrational motion. The user
should consult the crystal vendor for a start-up time specification.
When a power-on reset cycle is in progress, the external RST pin has no effect on internal operation.
Once control of the processor is transferred to the user’s program, a hardware reset may be issued
externally via the RST pin.
A power-on reset causes special initialization to be performed on the SFR as shown in Table 10-A.
87 of 187
Page 88

Secure Microcontroller User’s Guide
The distinguishing action taken during a power-on reset is that the POR bit is cleared in order to indicate
that a power-on reset has just occurred. All other control bits that are initialized according to the type of
reset are left unchanged from their previous condition.
10.1.2 No-VLI Power-On Reset
During a power-on reset cycle, at the end of the power-on reset-delay time, internal circuitry measures the
voltage on the VLI pin of the microprocessor. If VLI <~0.8V, a no-VLI power-on reset is initiated and SFR
are initialized during the rest as shown in Table 10-A. These include:
1) The POR bit (PCON.6) is cleared to indicate that a power-on reset has just occurred.
2) The watchdog timer is disabled by writing a 0 into the EWT bit (PCON.2).
3) The partition address bits (PA3-0) are set to all 1s. In addition, the range function is set to select a
32kB address space for the RAM.
4) On a DS5000, the encryption key and software encryption operation are disabled.
5) Finally, the security lock bit is cleared to 0.
10.1.3 External Reset
For applications that require an external reset capability, a reset pin (RST) is provided with a Schmitt
trigger input. This input can be used to force a reset condition any time when the micro is executing the
application program or when it is in either the idle or stop modes. Reset is initiated by holding the RST
pin active (high) for a minimum time of two machine cycles (24 clock oscillator periods). If the reset was
initiated from stop mode, the rising edge results in an internally generated power-on reset time (t
POR
),
which is required for the oscillator to start and for the clock frequency to stabilize.
All the control bits that are initialized according to the type of reset within the SFRs are left unchanged
from their previous condition following an external reset. Note: An RC circuit should not be used on the
reset pin to generate a power-on reset.
10.1.4 Watchdog Timer Reset
The on-chip watchdog timer is provided as a method of restoring proper software operation in the event
that software control is lost. The watchdog timer is enabled via the EWT bit (PCON.2). This bit can only
be written by using the timed-access function.
Once the watchdog timer is initialized, an internal reset is issued if the software fails to reset the timer via
the RWT bit (IP.7) at least once before it reaches its timeout condition. The timeout period is equal to
122,880 machine cycles. If a 12MHz crystal is used as the time-base element, this gives a timeout period
of 122.88ms. To reset the watchdog timer in the application software, the RWT bit must be written with a
1 using the timed-access procedure. The watchdog timer is also reset following any other type of reset.
When a watchdog timer reset occurs, special initialization is performed on the SFRs, as shown in
Table 10-A
. The distinguishing action taken during this type of reset is that the WTR status flag is set to
indicate that a watchdog timer reset has just occurred.
Application: Reset Routine Example
Like the 8051, Maxim microcontrollers will begin execution at address 0000h. This is the Reset Vector,
followed by other vector locations used for interrupts. These are discussed in the section covering
interrupt operation. Since there are only three memory locations dedicated to the Reset Vector, the user
will typically insert a jump statement to a more convenient memory address. This will be the reset
88 of 187
Page 89

Secure Microcontroller User’s Guide
MEMORY
INTERRUPTS
TIMERS/SERIAL
PROTECTION
Partition
Power-fail
Timer setup
Watchdog Timer
Current Memory Map
External
Timer for baud-rates
POR
Data Pointer
Serial Port
Serial Port
Timer
routine. It can lie any where in the 64kB of program memory addressed by the device. A common choice
is location 0030h. Thus at location 0000h, the user would use the instruction SJMP 30h. This instruction
requires two bytes, so it easily fits in the available space. At the location of the reset routine, the user
places instructions that initialize the microprocessor and any external hardware specific to the application.
This note describes the operations that are typically done and shows some example code. The following
functions are typically initialized in a user’s reset routine:
10.2 Me mory Map
The most critical and most overlooked initialization is that of the memory map. Several of these functions
are nonvolatile and are not cleared during a reset. Those that are cleared could leave the microprocessor
in an undesirable state. Therefore, the user should either verify the correctness of the memory map or
simply set it properly following each reset. An example of how the memory map could be incorrect on
reset is as follows.
The user typically sets the Partition, Range, etc., during Bootstrap Loading. In the course of operating
however, the user may temporarily move the Partition to alter a lookup table. If while the Partition is
moved, a reset should occur, the Partition will remain in the temporary position unless corrected.
In developing the reset routine, the user should carefully note the reset state of each critical bit. For
example, when using the ECE2 on a DS5000FP, note that it is not altered on reset. On a DS5001FP, the
PES bit is cleared on a reset. Thus a DS5000T that is accessing the Real-time Clock when a reset occurs
will still be pointing the CE2 space after reset. The DS2251T user that is accessing the RTC when a reset
occurs will start in the normal memory configuration.
A code example that initializes the memory map is as follows. It assumes that the DS5000FP user
requires a Partition of 5800h. A DS5001FP using the same code would use a Partition of B000h.
MCON EQU 0C6h
Org 00h
SJMP Start
Org 30h
Start :
MOV TA, #0Aah ;Timed
MOV TA, #55h ; Access
ORL MCON, #02h ;Set PAA - DS5000 ONLY
MOV MCON, #0B8h ;Set Partition to 5800 on DS5000, B000h on DS5001
MOV TA, #0Aah ;Timed - DS5000 ONLY
MOV TA, #55h ; Access - DS5000 ONLY
ANL MCON, #0FDh ;Clear PAA - DS5000 ONLY
Another common memory requirement is the initialization of the Data Pointer. When using NV RAM to
store data, this pointer must be moved to the Partition address (in a partitionable configuration). Thus if
89 of 187
Page 90

Secure Microcontroller User’s Guide
the Partition is set to 5800h, the DPTR should be set to 5800h to start. Once data has been saved in NV
RAM, the DPTR should be saved in a known, nonvolatile location so that is can be restored on a reset.
10.3 Interrupts
All interrupts are disabled after a reset so the user must enable individual interrupts as needed, as well as
the global interrupt. Any interrupt needing a higher priority must be selected as such. The following code
example shows the enabling of individual interrupts. A user would combine the appropriate bits as needed
by the application. In this application example, the serial port is given a high priority interrupt.
ORG 00h
SJMP Start
Org 30h
Start :
ORL PCON, #08h ;Enable Power–fail Warning by setting EPFW
SETB PS ;Set Serial Port Interrupt to High Priority
SETB ES ;Enable Serial Port Interrupt
SETB ET1 ;Enable Timer 1 Interrupt
SETB EX1 ;Enable External Interrupt 1
SETB ET0 ;Enable Timer 0 Interrupt
SETB EX0 ;Enable External Interrupt 0
SETB EA ; Globally enable interrupts
10.4 Timers
The microprocessor disables timer activity (excluding the Watchdog) and serial port communication on a
reset. Therefore, each timer (and serial port, if used) must be reinitialized as part of the reset routine. This
is covered in detail in the User’s Guide section on Timers and Serial I/O respectively. Shown here is an
example of Timer and Serial Port setup. In this example, Timer 0 is set up to generate a 10ms interrupt.
Timer 1 is setup to generate 9600 baud for the serial port. The serial port is set up for asynchronous
communication with a PC (mode 1). A crystal frequency of 11.0592MHz is assumed.
ORG 00h
SJMP Start
Org 30h
Start :
SETB PS ;Set Serial Port Interrupt to High Priority
SETB ES ;Enable Serial Port Interrupt
SETB ET0 ;Enable Timer 0 Interrupt
MOV TMO, #00100001b ;Select Timer 1 mode 2 – 8 bit auto–reload,
; Timer 0 mode 1 – 16 bit manual reload
MOV TH1, #0FDh ;Setup 9600 baud
MOV TL1, #00h ; ” ”
MOV TH0, #0DBh ;Select a 10 ms count. 9216 counts = 10 ms
MOV TL0, #0FFh ; 9216d counts = 2400h counts (FFFFh–2400h =
; DBFFh)
; Timer 0 ISR must reload DBFFh manually
MOV SCON, #01010011b ;Select Serial Port mode 1,
; TXD and RXD interrupts active
MOV TCON, #01010000b ;Enable the operation of both Timers
SETB EA ;Globally enable interrupts
90 of 187
Page 91

Secure Microcontroller User’s Guide
10.5 Transient Voltage Protection
The microprocessor provides protection from transients through a built in power-fail/power-on reset and
Watchdog Timer. Each of these functions should be initialized by the user as part of the reset routine. The
following code demonstrates the set up for a user that will support the Watchdog function.
TA EQU 0C7h
ORG 00h
SJMP Start
Org 30h
Start :
MOV TA, #0Aah ;Timed
MOV TA, #55h ; Access
ORL IP, #80h ;Set RWT to restart the Watchdog Timer
MOV TA, #0Aah ;Timed
MOV TA, #55h ; Access
ORL PCON, #44h ;Set POR (PCON.6) bit for power-on reset detect
; and enable Watchdog Timer by setting EWT
(PCON.2)
91 of 187
Page 92

Secure Microcontroller User’s Guide
INTERRUPT SOURCE
VECTOR ADDRESS
FLAG
FLAG LOCATION
External Interrupt 0
0003h
IE0
TCON.1
Timer Interrupt 0
000Bh
TF0
TCON.5
External Interrupt 1
0013h
IE1
TCON.3
Timer Interrupt 1
001Bh
TF1
TCON.7
Serial I/O
0023h
RI & TI
SCON.0, SCON.1
Power-fail Warning
002Bh
PFW
PCON.5
INTERRUPT SOURCE
ENABLE BIT
LOCATION
External Interrupt 0
EX0
IE.0
Timer Interrupt 0
ET0
IE.1
External Interrupt 1
EX1
IE.2
Timer Interrupt 1
ET1
IE.3
Serial Port Interrupt
ES
IE.4
Power-fail Interrupt
EPFW
PCON.3
11. INTERRUPTS
The secure microcontroller family follows the standard 8051 convention for interrupts (with one extra)
and is fully compatible. An interrupt stops the normal flow of processing and allows software to react to
an event with special processing. This event can be external, time-related, or the result of serial
communication. However, the interrupt will not be performed until the completion of the current
instruction. This is discussed in more detail below. For each interrupt, there is an interrupt vector location.
When an interrupt occurs, the CPU performs a call to the corresponding vector address. Since the vector
addresses are only 8 bytes apart, these ISRs typically use a jump to another more location in program
memory where the interrupt service routine (ISR) is stored. An ISR performs special processing
associated with the event that caused the interrupt. When the ISR is complete, the user returns control to
the main program using an RETI instruction. This is the last instruction in an ISR and it performs two
functions. First, it returns control to the main program preempted by the interrupt. Second, the RETI
clears the interrupt condition, allowing the CPU to respond to other interrupts.
There are six interrupt vector locations in a secure microcontroller. Each interrupt generally has an
enable-control bit, a status flag bit, and a priority bit. Except for the new Power-fail Interrupt, the enablecontrol bits are located in the IE register and the priority bits are located in the IP register. The flags are
located in various SFRs. In the case of the Serial Interrupt, there are two sources with the same vector, but
a separate flag indicates the source of the event. Each ISR vector has a unique physical address. For
example, the External interrupt 0 vector is location 0003h, but the Timer 0 vector is 000Bh. Also note, the
flags correspond to the event, not the interrupt. These flags will be activated even if a particular interrupt
is not enabled so that software can poll the event. The flags (except serial port) are cleared when the CPU
calls to the interrupt vector.
11.1 Int errupt Sources
As shown above, there are two external interrupts, two timer interrupts, two serial communication
interrupts, and a power-fail interrupt. To use an interrupt (except PFW), the software must globally enable
the interrupt function by setting the EA bit (IE.7). EA is cleared to logic 0 by all resets. Next, each
individual interrupt must be enabled by using the other bits of the interrupt enable (IE) SFR. Each source
has a corresponding bit that must be set to logic 1. These are listed below.
92 of 187
Page 93

Secure Microcontroller User’s Guide
11.2 External Interrupts
The two external interrupts are INT0 and INT1. They correspond to P3.2 and P3.3 respectively. These
pins become interrupts when the respective interrupt is enabled. Otherwise, they are simply port pins. No
other special action is required. Each pin is sampled once per machine cycle when the interrupts are
enabled. Setting the EX0 bit to logic 1 enables INT0. Setting the EX1 bit to logic 1 enables INT1. These
bits are located at IE.0 and IE.2, respectively. The external interrupts each have a status flag that indicates
that the condition has occurred. The flags are IE0 at TCON.1 and IE1 at TCON.3. These flags are set to
logic 1 when the interrupt condition occurs. They are cleared when the CPU calls to the appropriate
interrupt vector.
The external interrupts can be programmed to respond to falling-edge or low-level activation. IT0
(TCON.0) and IT1 (TCON.2) control the edge/level nature of INT0 and INT1, respectively. When ITn is
logic 0, the associated interrupt is low-level activated. This causes the IEn flag to be set for as long as the
INTn pin remains logic 0. The interrupt (if enabled) will remain active during this period. Note that the
level interrupt is not latched. Thus the pin must be held in a low state until the ISR can be activated. If the
INTn pin i s brought to logic high prior to beginning the ISR, there will be no interrupt. If INTn is left at
logic low after the RETI instruction of the ISR, another interrupt will be activated after one instruction is
executed.
Setting the INTn bit to logic 1 causes the external interrupt to be edge activated. This causes the device to
detect a falling edge on the INTn pin. This edge condition is latched until the interrupt is serviced. Th us
in edge mode, the INTn pin can go from logic 1 to logic 0, then back to logic 1 and the interrupt will still
be active. After the falling-edge has been detected, the INTn pin is subsequently ignored until after the
ISR is complete. The edge detector is actually a “pseudoedge” detector. Since the pin is actually sampled,
the condition must be a logic high for at least one machine cycle and logic low for at least one machine
cycle in order to guarantee recognition of the falling edge. The IEn flag is automatically cleared when the
interrupt is serviced.
11.3 Time r Interrupts
The secure microcontroller, like the 8051, has two internal timers. These timers can each generate an
interrupt when the value in the timer registers overflows. When the Timer 0 overflows, the TF0 flag is set
to al logic 1. Likewise for the TF1 flag with respect to Timer 1. TF0 is located at TCON.5 and TF1 is
located at TCON.7. These flags indicate the overflow condition. If the corresponding timer interrupt is
desired, then ET0 at IE.1 and ET1 at IE.3 must be set to logic 1, respectively. When set, the timer
overflow will cause an interrupt to the appropriate vector location. If the interrupt is active, the CPU
automatically clears the flag.
11.4 Serial Port Interrupts
The on-chip serial port generates an interrupt when either a word is received or a word is transmitted. The
interrupt is effectively a logical OR of the two conditions. Each condition has its own flag. The flags
operate regardless of whether the interrupt has been enabled. RI is located at SCON.0 and represents a
serial word received. TI is located at SCON.1 and represents a serial word transmitted. Each flag is set to
logic 1 to indicate an active state. Since there are two flags for one interrupt, these flags are used by the
ISR to determine the cause of the interrupt. The flags must be cleared by software to clear the interrupt
condition. Setting the ES bit at IE.4 to logic 1 activates the serial interrupt.
93 of 187
Page 94

Secure Microcontroller User’s Guide
11.5 Power-Fail Warning Interrupt
The secure microcontroller family adds a new interrupt, the early warning power-fail interrupt (PFW), to
the standard 8051 collection. During a power-down or brown out, as VCC is falling, the secure
microcontroller can generate an early warning power-fail interrupt. This allows the software to save
critical data prior to entering a reset condition. Since the NV RAM is not affected by a reset, this data is
effectively saved. Software can use the PFW to save the current routine, current data, shut off external
functions, or simply to enter a known region of memory for the power-down. It is used in conjunction
with the power monitor and nonvolatile memory.
Setting the EPFW bit at PCON.3 to logic 1 enables PFW. The PFW flag is located at PCON.5. Whenever
VCC drops below the V
by software. If the voltage is still below the V
regardless of whether the interrupt is enabled. The V
voltage threshold, the PFW flag is set to logic 1. This flag is cleared when read
PFW
, the flag will again be set immediately. This occurs
PFW
voltage is different for each member of the
PFW
secure microcontroller family. Check the electrical specifications for details. Note that the EA globalenable bit does not control the PFW interrupt. It can only be enabled or disabled using the EPFW bit.
11.6 Simulated Interrupts
Except for PFW, any interrupt can be forced by setting the corresponding flag to logic 1 in software. This
causes the code to jump to the appropriate interrupt vector. Clearing the appropriate flag manually will
clear a pending interrupt. Note that the PFW flag cannot be written by software.
94 of 187
Page 95

Figure 11-1. Interrupt Request Sources
Secure Microcontroller User’s Guide
95 of 187
Page 96

Secure Microcontroller User’s Guide
Interrupt Enable Control Bits
All bits are read/write at any time and are cleared to 0 following any hardware reset.
IE.7 EA
Enable All Interrupts When set to 1, each interrupt except for PFW may be individually enabled or
disabled by setting or clearing the associated IE.x bit. When cleared to 0,
interrupts are globally disabled and no pending interrupt request will be
acknowledged except for PFW.
IE.4 ES
Enable Serial Interrupt When set to 1, an interrupt request from eith er the serial port’s TI or RI flags
can be acknowledged. Serial I/O interrupts are disabled when cleared to 0.
IE.3 ET1
Enable Timer 1 Interrupt When set to 1, an interrupt request from Timer 1’s TF1 flag can be
acknowledged. Interrupts are disabled from this source when cleared to 0.
IE.2 EX1
Enable External Interrupt 1 When set to 1, an interrupt from the IE1 flag can be acknowledged. Interrupts
are disabled from this source when clear ed to 0.
IE.1 ET0
Enable Timer 0 Interrupt When set to 1, an interrupt request from Timer 0’s TF0 flag can be
acknowledged. Interrupts are disabled from this source when cleared to 0.
IE.0 EX0
Enable External Interrupt 0 When set to 1, an interrupt request from the IE0 flag can be acknowledged.
Interrupts are disabled from this source when cl ear ed to 0.
11.7 Interrupt Priorities
The secure microcontroller provides a three priority interrupt scheme. Multiple priority levels allow
higher priority sources to interrupt lower priority ISRs. The Power-fail Warning Interrupt automatically
has the highest priority if enabled. The user can program the remaining interrupts to either high or low
priority. The priority scheme works as follows. The ISR for a low priority source can be interrupted by a
high priority source. A low priority ISR cannot be interrupted by another low priory source. Neither can a
high priority ISR be interrupted by a another high priority source. The PFW source will interrupt any ISR
if activated.
In the case of simultaneous interrupt requests, the microcontroller has a natural scheme to arbitrate. First,
if high and low priority interrupt requests are received simultaneously, then the high priority source will
be serviced. If two or more requests from equal priority sources are received, the following natural
priority scheme will be used to arbitrate.
96 of 187
Page 97

Secure Microcontroller User’s Guide
PRIORITY
FLAG
INTERRUPT SOURCE
1
PFW
Power-Fail Warning
2
IE0
External Interrupt 0
3
TF0
Timer 0 Interrupt
4
IE1
External Interrupt 1
5
TF1
Timer 1 Interrupt
6
RI+TI
Serial I/O Interrupt
Each interrupt priority is determined by an individual bit as in the following table. Setting the appropriate
bit to a logic 1 will cause that interrupt to be high priority.
Interrupt Priority Control Bits
All bits are read/write at any time and are cleared to 0 following any hardware reset.
IP.4 PS
Serial Port Priority Programs Serial Port interrupts for high priority when set to 1. Low priority is
selected when cleared to 0.
IP.3 PT1
Timer 1 Priority Programs Timer 1 interrupt for high priority when set to 1. Low priority is selected
when cleared to 0.
IP.2 PX1
External Interrupt 1 Priority Programs External Interrupt 1 for high priority when set to 1. Low priority is
selected when cleared to 0.
IP.1 PT0
Timer 0 Priority Program Timer 0 interrupt for high priority when set to 1. Low priority is selected
when cleared to 0.
IP.0 PX0
External Interrupt 0 Priority Programs External Interrupt 0 for high priority when set to 1. Low priority is
selected when cleared to 0.
11.8 Int errupt Acknowledge
The various interrupt flags are sampled an latched once every machine cycle, specifically during clock
phase S5P2 (see CPU timing section) regardless of other interrupt related activity. Likewise, the latched
states of the flags are polled once every machine cycle for the sampling that took place during the
previous machine cycle.
A complete interrupt acknowledge sequence consists of a total of four machine cycles, labeled as IA1,
IA2, IA3, and IA4 in Figure 11-2. The various interrupt flags are sampled and latched once every
machine cycle, specifically during clock phase S5P2. This is shown in the diagram as IA1. If one or more
pending interrupt registers are latched, then during the following machine cycle (IA2) priority is resolved
between one or more active interrupt requests.
Also during IA2, the hardware checks the state of the machine to insure that the following criteria are met
before servicing the pending interrupt:
97 of 187
Page 98

Secure Microcontroller User’s Guide
a) The current cycle is not part of an instruction within an interrupt service routine of an interrupt of
equal or higher priority.
b) The current cycle is not the final machine cycle of an instruction that accesses the IP or IE registers.
If the above criteria are met during IA2, then a long call will be executed during IA3 and IA4 to the
vector location of the pending interrupt of highest priority and the interrupt acknowledge sequence will be
complete. If the criteria during IA2 are not met, then the interrupt acknowledge sequence is aborted and
the interrupt request latches will be polled on the next machine cycle (which would have been IA3).
Figure 11-2. Interrupt Acknowledge Sequence
The first criteria for the continuation of an interrupt acknowledge cycle maintains the priority relationship
between interrupts and their priority level assignment. As a result, pending interrupt sources cannot be
acknowledged during the execution of service routines of interrupts that are of equal or higher priority.
Interrupt acknowledges are not allowed during an RETI instruction or during instructions which access IP
or IE in order to insure that at least one more instruction will be executed before an interrupt is serviced.
The interrupt request flags are sampled and latched during every machine cycle regardless of the other
interrupt activity on the device. Each time an attempt acknowledge takes place during IA2, it is based on
the latched value of the flags during the previous machine cycle. If the interrupt acknowledge does not
take place for one of the reasons cited above, the request flag will become subsequently inactive and the
interrupt will have been lost and will not be serviced.
When an interrupt request is acknowledged, a long call is executed to the interrupt vector location and the
2-byte return address is pushed onto the stack. In addition, an internal flag is set which indicates the
interrupt source that is being serviced. Execution then proceeds from the interrupt vector location. At the
conclusion of the interrupt service routine, an RETI instruction should be performed to return control to
the main program. The RETI performs the same action as a RET, but performs the additional operation of
clearing the interrupt-in-service flag to inform the hardware that a service routine is no longer in progress.
Therefore, an RETI should always be used to terminate an interrupt service routine.
Higher priority interrupts, which are enabled, can interrupt lower priority interrupts. According to this
rule, a higher priority interrupt could become pending just prior to machine cycle IA3 during an interrupt
acknowledge of a lower priority interrupt. This would cause the hardware to vector to the higher priority
service routine during the two machine cycles just after the long call to the lower priority interrupt so that
no instruction within the lower priority interrupt service routine would have been executed.
98 of 187
Page 99

Secure Microcontroller User’s Guide
PIN
NAME
FUNCTION
P3.7
RD
Expanded Data Memory Read Strobe
P3.6
WR
Expanded Data Memory Write Strobe
P3.5
T1
Timer/Counter 1 Input
P3.4
T0
Timer/Counter 0 Input
P3.3
INT1
External Interrupt 1 Input
P3.2
INT0
External Interrupt 0 Input
P3.1
TXD
Serial Port Transmit Data
P3.0
RXD
Serial Port Receive Data
12. PARALLEL I/O
The secure microcontroller provides four 8-bit bidirectional ports for general-purpose I/O functions. Each
port pin is bit and byte addressable using four SFRs that control the respective port latch. Each bit has an
associated latch (accessed via SFR), input buffer circuit, and output driver circuit. Ports 0, 2, and 3 also
have alternate functions that can be used in place of general I/O. All of the SFR latches for the parallel
port pins are written with 1’s during a hardware reset. Figure 12-1 through Figure 12-4 illustrates
functional circuit diagrams for bits within each of the four I/O ports. Port 1 has no alternate function; it is
always available for parallel I/O functions.
Ports 0 and 2 can serve as a multiplexed Expanded Memory bus for applications needing memory
mapped I/O. In the DS5001/2FP the Ports 0 and 2 can also serve as a slave RPC interface to a host
microprocessor. Port 3 pins each have individual, optional functions described below. Enabling the
optional function by writing a 1 to the associated latch bit in the Port 3 SFR automatically converts the
I/O pin into its alternate function. For example, enabling the serial port automatically converts P3.0 and
P3.1 into the RXD and TXD function. Alternate functions pins and general I/O pins can be enabled
independent of each other. Enabling selected pins to perform their alternate function leaves the other as
bit addressable I/O pins.
In many cases it may be desirable to use a combination of pure I/O and alternate function pins on port 3.
For example, a user may decide to use the serial port and INTO pins, leaving 5 pins available for use as
general purpose I/O (assuming P3.6 and P3.7 are not being used to access external memory). SETB and
CLR commands can be used to access the general I/O pins without any effect on the pins being used in
their alternate function. If the MOV command is used to write to port 3, however, software must always
write a logic 1 to the pins that are being used in their alternate function. Failure to do so will disturb their
function, resulting in serial port data corruption or disabling of the alternate function in the case of other
pins.
99 of 187
Page 100
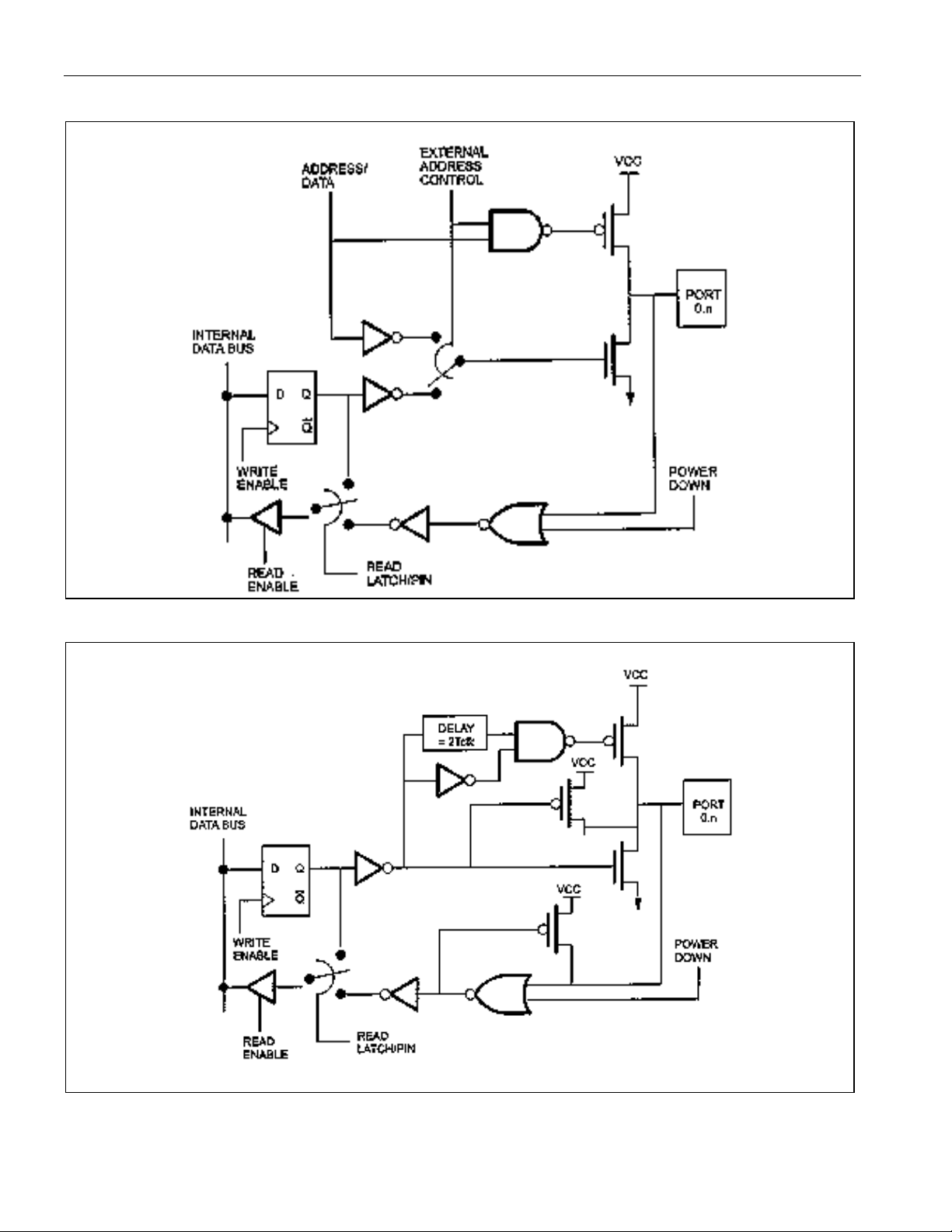
Figure 12-1. Port 0 Functional Circuitry
Secure Microcontroller User’s Guide
Figure 12-2. Port 1 Functional Circuitry
100 of 187
 Loading...
Loading...