Page 1

Waspmote Encryption Libraries
Programming guide
Page 2

Index
Document version: v7.0 - 02/2017
© Libelium Comunicaciones Distribuidas S.L.
INDEX
1. Introduction ......................................................................................................................................... 3
2. Integrity ................................................................................................................................................ 6
2.1. Waspmote Libraries ....................................................................................................................................................................6
2.1.1. Waspmote Hash Files ................................................................................................................................................. 6
2.1.2. Constructor ....................................................................................................................................................................6
2.1.3. Pre-Dened Constants ...............................................................................................................................................6
2.2. Calculating Message Digest .....................................................................................................................................................7
2.2.1. Calculating MD5 hash .................................................................................................................................................7
2.2.2. Calculating SHA hash ................................................................................................................................................. 7
2.3. Printing Message ..........................................................................................................................................................................8
3. Authenticity ......................................................................................................................................... 9
3.1. Waspmote Libraries ................................................................................................................................................................. 10
3.1.1. Waspmote RSA Files .................................................................................................................................................10
3.1.2. Constructor ..................................................................................................................................................................10
3.1.3. Pre-Dened Constants .............................................................................................................................................10
3.2. Encrypting Message ................................................................................................................................................................. 10
4. Condentiality (privacy) ................................................................................................................... 11
4.1. Waspmote Libraries ................................................................................................................................................................. 13
4.1.1. Waspmote AES Files .................................................................................................................................................13
4.1.2. Constructor ..................................................................................................................................................................13
4.1.3. Pre-Dened Constants .............................................................................................................................................13
4.2. Calculating the encrypted message length ................................................................................................................... 13
4.3. AES Encryption .........................................................................................................................................................................13
4.4. Printing Message .......................................................................................................................................................................14
5. Secure Communication Scheme ....................................................................................................... 15
6. Key Management on Meshlium ........................................................................................................ 16
6.1. Link layer key Management (only XBee) ..........................................................................................................................16
6.2. Application Layer Key Management (AES libraries) .....................................................................................................18
7. Code examples and extended information .................................................................................... 20
8. API changelog .................................................................................................................................... 22
9. Certications ...................................................................................................................................... 23
-2- v7.0
Page 3
Introduction
1. Introduction
This guide explains the Encryption library features and functions. There are no great variations in this library for our new product
lines Waspmote v15 and Plug & Sense! v15, released on October 2016.
Anyway, if you are using previous versions of our products, please use the corresponding guides, available on our Development
website.
You can get more information about the generation change on the document “New generation of Libelium product lines”.
The new Encryption Libraries are designed to add to the Waspmote sensor platform the capabilities necessary to protect the
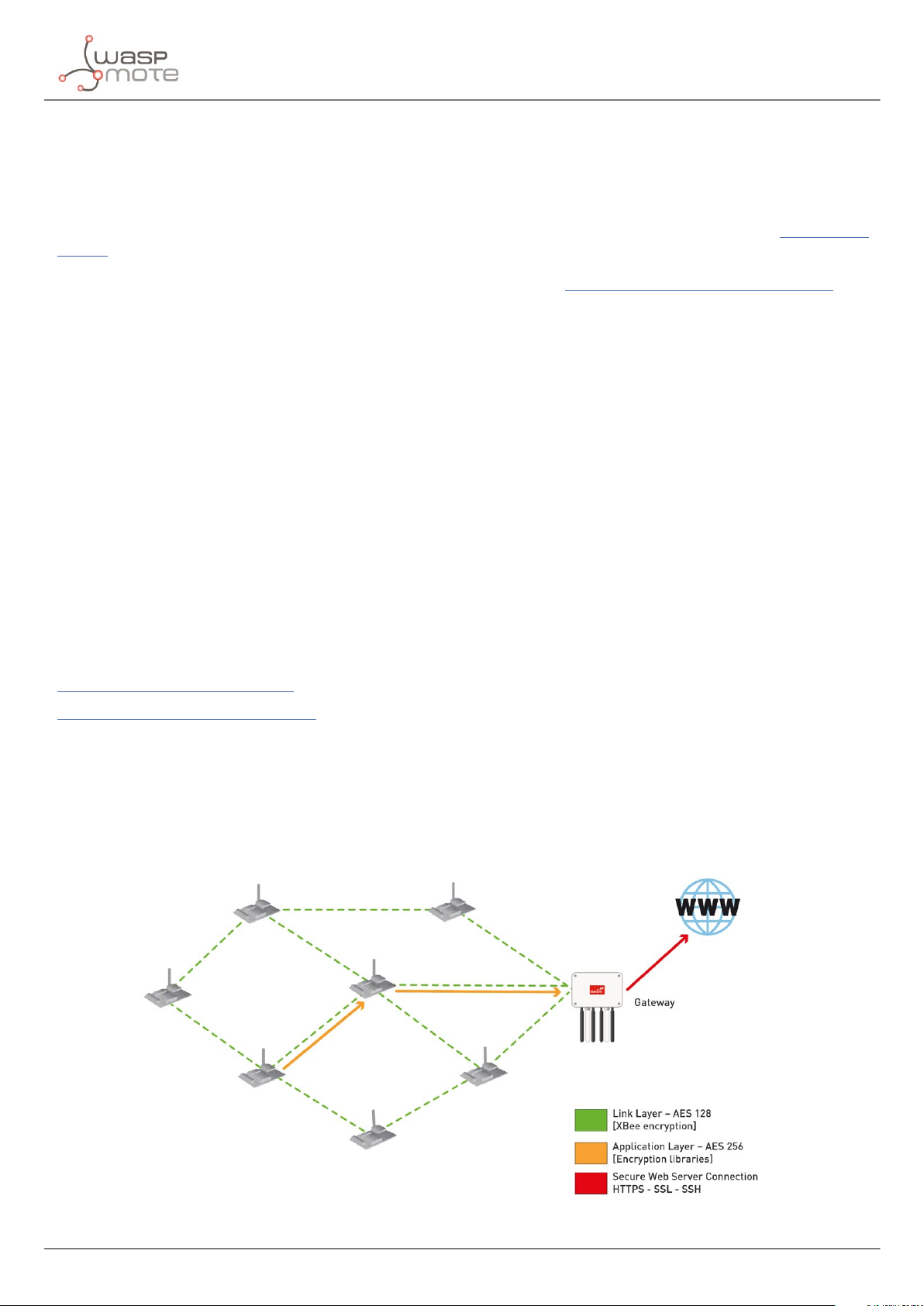
information gathered by the sensors. To do so three cryptography layers are dened:
• Link Layer: In the rst one all the nodes of the network share a common preshared key which is used to encrypt the
information using AES 128. This process is carried out by specic hardware integrated in the same 802.15.4/ZigBee radio,
allowing the maximum eciency of the sensor nodes energy consumption. This rst security layer ensures no third party
devices will be able to even connect to the network (access control).
• Application Layer: In the second security layer each node uses a point to point encryption scheme with Meshlium -the
Gateway of the network-. This way, even the intermediate nodes of the network (the ones which forward the information
to the destination) will not be able to see the sensor data transmitted. Messages are sent using AES, (implemented by the
software library) ensuring complete condentiality and privacy while maintaining the minimum resources of the node in
term of computing cycles and energy consumption.
• Secure Web Server Connection: The third security technique is carried out in Meshlium -the Gateway- where HTTPS and
SSH connections are used to send the information to the Cloud server located on the Internet.
A fourth optional encryption layer allows each node to encrypt the information using the Public key of the Cloud server. Thus,
the information will be kept condentially all the way from the sensor device to the web or data base server on the Internet.
Note: The Encryption Libraries are part of the Waspmote API and have been designed to work solely on top of the Waspmote and
Waspmote Plug & Sense sensor platforms. More info at:
http://www.libelium.com/waspmote
http://www.libelium.com/plug_&_sense
- Transmission of sensor data:
Information is encrypted in the application layer via software with AES using the key shared exclusively between the origin and
the destination. Then the packet is encrypted again in the link layer via hardware with AES 128 so that only trusted packets be
forwarded, ensuring access control and improving the usage of resources of the network.
Figure : Communication diagram
-3- v7.0
Page 4
Introduction
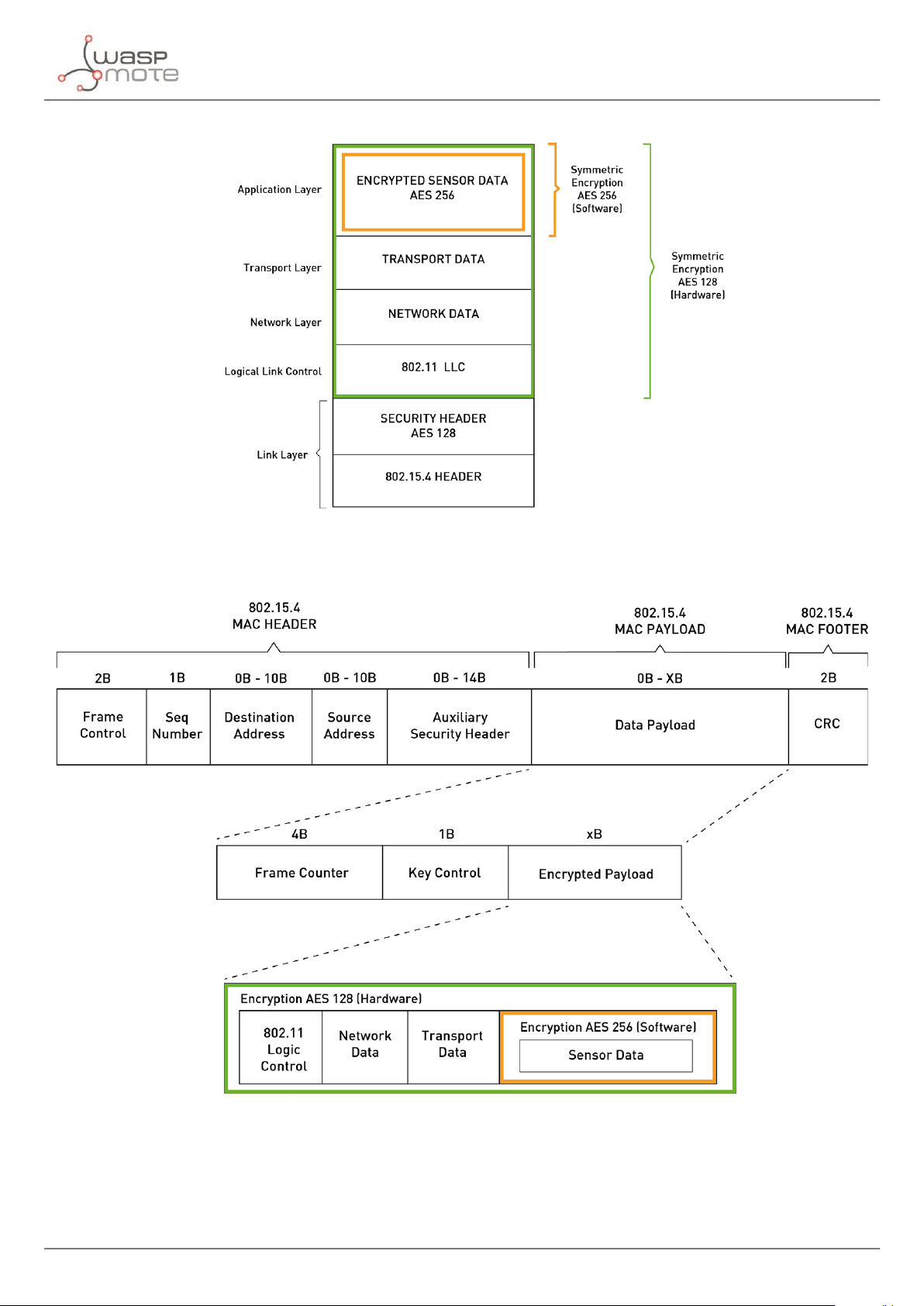
Figure : Waspmote frame on OSI stack for communication (via 802.15.4)
Figure : Waspmote frame structure for communication (via 802.15.4)
-4- v7.0
Page 5

Introduction
Common security issues which are solved include:
- Access control: by using AES 128 in the link layer we ensure that only nodes with the shared key can access to the routing
capabilities of the sensor network. If a strange node sends a message to the network the message will be discharged in the rst
hop so no extra communication resources will be used. The AES 128 algorithm is implemented in the same radio using specic
hardware, for this reason the information will be automatically discarded and not even sent to the microcontroller. This provides
an extra layer of security as the main control unit of the node will not be interrupted from performing basic tasks or event not
awaken from the sleep mode (what ensures optimum energy usage).
- Authentication: the library implements also RSA with asymmetric key scheme. Each node has a pair of Public/Private keys
(1024b) which uses to sign the messages in order to ensure the authenticity of origin and destination.
- Data Condentiality (Privacy): by doubling encryption of the messages we ensure that rst that only the nodes which form
part of the network can see the general routing packets (AES 128 in the link layer) and after that we establish an encryption
tunnel by direct P2P encryption between origin and destination (using AES).
- Data Integrity: the new library uses hash algorithms such as MD5 and SHA to create the checksum of the message and to
ensure that the nal information received correspond with the original sent.
- Non-repudiation: by signing the messages with RSA keys we have also the legal proof that the information sent really was
sent by a specic sensor node and not by other. Important in the future when all the sensitive sensor information has to be
legally approved.
Each node may store thousands of dierent Public Keys of the nodes of the network in its SD card. So we can establish a real P2P
encryption among any sensor and the Gateway and even between any sensor and any web or data base server directly.
The new Libraries are specically designed to be used in the Waspmote hardware sensor platform and are distributed along
with the Waspmote IDE which is distributed under an open source license.
Note: The Encryption Libraries are part of the Waspmote API and have been designed to work solely on top of the Waspmote and
Waspmote Plug & Sense sensor platforms. More info at:
http://www.libelium.com/waspmote
http://www.libelium.com/plug_&_sense
-5- v7.0
Page 6

Integrity
2. Integrity
The data integrity security ensures the correctness or accuracy of data. The data is protected against unauthorized modication,
deletion, creation, and replication and provides an indication of these unauthorized. Integrity implies that the data is an exact
copy of some original version.
Data integrity is provided by hash functions like Message Digest Algorithm (MD5) or Secure Hash Algorithm (SHA). The following
methods are provided by the Encryption libraries:
• MD5 algorithm takes as input a message of arbitrary length and produces as output a 128-bit “ngerprint” or “message
digest” of the input message. MD5 is currently a standard, Internet Engineering Task Force (IETF) Request for Comments
(RFC) 1321. In comparison, MD5 is not quite as fast as the MD4 algorithm, but oers much more assurance of data security.
• SHA is considered to be the successor to MD5. The Federal Information Processing Standard (FIPS 180-2) species four
secure hash algorithms: SHA-1, SHA-256, SHA-384, and SHA-512. All algorithms are iterative, one-way hash functions
that can process a message with a maximum length of 264 bits to 2
sentation called a message digest. The input message is processed in 512-bit to 1024-bit blocks. The four algorithms
dier most signicantly in the number of bits for the message digest length. Each SHA algorithm processes a message
in two stages: preprocessing and hash computation. Preprocessing involves padding a message, parsing the padded
message into 512-bit or 1024-bit blocks, and setting initialization values to be used in the hash computation. The hash
computation generates a message schedule from the padded message and uses that schedule, along with functions,
constants, and word operations to iteratively generate a series of hash values. The nal hash value generated by the hash
computation is used to determine the message digest.
128
bits to produce a 160 to 512-bit condensed repre-
2.1. Waspmote Libraries
2.1.1. Waspmote Hash Files
WaspHash.h is the header le of the class, and WaspHash.cpp is the class where the functions and variables are implemented.
It is mandatory to include the Hash library when using it. The following line must be introduced at the beginning of the code:
#include <WaspHash.h>
2.1.2. Constructor
To start using Waspmote Hash library, an object from class ‘WaspHash’ must be created. This object, called ‘HASH’, is created
inside the Waspmote Hash library and it is public to all libraries. It is used through the guide to show how the Waspmote Hash
library works.
When creating this constructor, no variables are initialized by default.
2.1.3. Pre-Dened Constants
There are some constants dened in ‘WaspHash.h’ related with the dierent encryption and padding modes that can be used
to encrypt and decrypt messages.
-6- v7.0
Page 7
Integrity
2.2. Calculating Message Digest
This section will describe how calculate a message digest depends on the selected algorithm. The dierent algorithms provide
dierent messages digest size.
For example, the Message Digest (MD5) hash is a mathematical algorithm which produces a unique 128 bit number (a hash)
created from the data input. If even one bit of data changes, the hash value will change.
2.2.1. Calculating MD5 hash
Previously, a variable to store the message digest must be declared. This variable must be correctly dimensioned to contain the
calculated hash message.
{
uint8_t hash_message[16];
}
The features that must be met in order to calculate the MD5 algorithm are:
Algorithms
MD5 128 128 512 2⁶⁴− 1 32
The next code shows how to calculate the message digest with HASH.md5(). The inputs expected are: the pointer to the buer
where the output is stored, the input message pointer and the length of the input message.
{
char message[] = “Libelium”;
HASH.md5(hash_message_md5, (uint8_t*)message, strlen(message)*8);
}
Output size
(bits)
Internal state
size (bits)
Block size
(bits)
Max message
size (bits)
Word size
(bits)
2.2.2. Calculating SHA hash
The features that must be met in order to calculate the SHA algorithm are:
Algorithms
SHA-1 160 160 512 2⁶⁴− 1 32 80
SHA-224 224 256 512 2⁶⁴− 1 32 64
SHA-256 256 256 512 2⁶⁴− 1 32 64
SHA-384 384 512 512 2¹²⁸− 1 64 80
SHA-512 512 512 1024 2¹²⁸− 1 64 80
Output size
(bits)
Internal state
size (bits)
Block size
(bits)
Max message
size (bits)
Word size
(bits)
Rounds
Previously, a variable to store the message digest must be declared. This variable must be correctly dimensioned to contain the
calculated hash message.
If SHA-1 is used, the variable that stores the hash message is dened:
{
uint8_t hash_message[20];
}
If SHA-384 is used, the variable that stores the hash message is dened:
{
uint8_t hash_message[48];
}
-7- v7.0
Page 8

Integrity
Next code shows how to calculate the message digest with HASH.sha(). The inputs expected are: the SHA algorithm, the
pointer to the buer where the output is stored, the input message pointer and the length of the input message.
{
char message[] = “Libelium”;
HASH.sha(SHA1, hash_message, (uint8_t*)message, strlen(message)*8);
}
{
char message[] = “Libelium”;
HASH.sha(SHA384, hash_message, (uint8_t*)message, strlen(message)*8);
}
2.3. Printing Message
Using the hash function HASH.printMessageDigest() the message digest is written via USB port.
{
// Write message digest by USB port
HASH.printMessageDigest(“SHA-1:”, hash_message, 20);
HASH.printMessageDigest(“MD5:”, hash_message, 16);
}
Example of use may be found in:
http://www.libelium.com/development/waspmote/examples/hash-01-md5
http://www.libelium.com/development/waspmote/examples/hash-02-sha1
-8- v7.0
Page 9

Authenticity
3. Authenticity
Authenticity is the assurance that a message, transaction, or other exchange of information is from the source it claims to be
from. Authenticity involves proof of identity.
For ensuring message authenticity, RSA algorithm is used. The RSA cryptosystem is the most widely-used public key cryptography
algorithm in the world. It can be used to encrypt a message without the need to exchange a secret key separately. Its security is
based on the diculty of factoring large integers.
The RSA algorithm can be used for both public key encryption and digital signatures:
• Public-key encryption: Party A can send an encrypted message to party B without any prior exchange of secret keys. A
just uses B’s public key to encrypt the message and B decrypts it using the private key, which is only known by the receiver.
• Digital signatures: RSA can also be used to sign a message, so A can sign a message using their private key and B can verify
it using A’s public key.
Key generation
• 1. Choose two dierent prime numbers p and q. For security purposes, the integers p and q should be chosen at random,
and should be of similar bit-length.
• 2. Compute n = p·q. The resulting n is used as the modulus for both public and private keys. Its length, usually expressed in
bits, is the key length.
• 3. Compute φ(n) = (p-1)(q-1).
• 4. Choose a public exponent ’e’ such that 1 < e < φ(n), which is coprime to φ(n). The number e is released as the public key
exponent.
• 5. Compute a private exponent ’d’ that satises the congruence ed ≡ 1 (mod φ(n)). The number d is kept as the private key
exponent.
• 6. The public key consists of the modulus n and the public exponent e. The private key consists of the modulus n and
the private exponent d, which must be kept secret. p, q, and φ(n) must also be kept secret because they can be used to
calculate d.
The best size for a modulus depends on one’s security needs. The larger the modulus, the greater the security, but also the slower
the RSA algorithm operations. One should choose a modulus length upon consideration, rst, of the value of the protected data
and how long it needs to be protected, and, second, of how powerful one’s potential threats might be. Typical bit lengths are
1024, 2048, 3072, 4096, etc.
This is the process of transforming a plaintext message into ciphertext, or vice-versa. The RSA function, for message ‘m’ and key
‘k’ is evaluated as follows:
F(m,k) = mk mod n
There are obviously two cases:
• RSA Encryption scheme: Encrypting with the public key, and then decrypting with the private key
- Encryption rule: F (m,e) = me mod n = c
- Decryption rule: F (c,d) = cd mod n = m
- Where ‘m’ is the message, ‘e’ is the public exponent, ‘d’ is the private exponent and ‘c’ is the ciphertext.
-9- v7.0
Page 10

Authenticity
• RSA Signature scheme: Encrypting with the private key, and then decrypting with the public key.
- Encryption rule: F (m,d) = md mod n = s
- Decrypti on rule: F (s,e) = se mod n = m
- Where ‘m’ is the message, ‘e’ is the public exponent, ‘d’ is the private exponent and ‘c’ is the ciphertext.
RSA is slower than certain other symmetric cryptosystems. RSA is, in fact, commonly used to securely transmit the keys for
another less secure, but faster algorithm.
3.1. Waspmote Libraries
3.1.1. Waspmote RSA Files
WaspRSA.h is the header le of the class, and WaspRSA.cpp is the class where the functions and variables are implemented.
It is mandatory to include the RSA library when using it. The following line must be introduced at the beginning of the code:
#include <WaspRSA.h>
3.1.2. Constructor
To start using Waspmote RSA library, an object from class ‘WaspRSA’ must be created. This object, called ‘RSA’, is created inside
the Waspmote RSA library and it is public to all libraries. It is used through the guide to show how the Waspmote RSA library
works.
When creating this constructor, no variables are initialized by default.
3.1.3. Pre-Dened Constants
There are some constants dened in ‘WaspRSA .h’ related with the dierent encryption and padding modes that can be used to
encrypt messages.
3.2. Encrypting Message
The function RSA.encrypt() encrypts an original message to an encrypted message using the public exponent ‘e’ and the
modulus ‘n’. Receiver can decrypt the message using the private key.
{
RSA.encrypt( original_message,
public_exponent,
modulus,
encrypted_message,
sizeof(encrypted_message));
}
Note: The maximum input size message must be smaller than the modulus.
Example of use:
http://www.libelium.com/development/waspmote/examples/rsa-01-encryption
-10- v7.0
Page 11

Condentiality (privacy)
4. Condentiality (privacy)
Condentiality refers to ensure that information is not accessed by unauthorized people. Information is intelligible only to its
rightful recipients. Although third parties may be able to read (a copy of) the message sent, they must not be able to make sense
of it. Condentiality is assurance of data privacy. Sending frames with condentiality can be achieved through symmetric key
encryption. AES algorithm has been implemented for this purpose.
Advanced Encryption Standard (AES) is a symmetric key encryption algorithm that supports key lengths of 128, 192, and 256
bits. AES encrypts a block of bytes at the same time, unlike stream ciphers that encode each single item individually. This feature
allows the algorithm to be very fast. It has the advantage of occupying very little memory and consequently makes it very
suitable for low memory capacity devices.
AES is able to encrypt and decrypt a block of data using an AES key. The key and the block of data have a xed length. The
length of the block of data is always 128-bit (16 bytes), while the key size can be:
• 128-bit key size (16 bytes)
• 192-bit key size (24 bytes)
• 256-bit key size (32 bytes)
As AES is classied as a block cipher algorithm, there are dierent modes of operation. A mode of operation describes how
to repeatedly apply a cipher’s single-block operation to securely transform amounts of data larger than a block. This library
implements two modes of operation:
• ECB mode: The simplest of the encryption modes is the electronic codebook (ECB) mode. The message is divided into
blocks of 16 bytes and each block is encrypted separately. Notice that this mode is the only one supported by Meshlium.
Figure : CBC mode encryption
-11- v7.0
Page 12

Condentiality (privacy)
• CBC mode: Each 16-byte block of plaintext is XORed with the previous ciphertext block before being encrypted. This
way, each ciphertext block depends on all plaintext blocks processed up to that point. To make each message unique, an
initialization vector must be used in the rst block. This initialization vector size is 16 bytes, so is the same size as the data
block size. Notice that this mode is not supported by Meshlium.
Figure : ECB mode encryption
A block cipher works on xed size blocks, but messages come in a variety of lengths. So some modes of operation require that
the nal block be padded before encryption. Several padding schemes exist, but this library provide two padding schemes:
• ZEROS: this method adds 0s until the last block size is completed. Notice that this mode is the only one supported by
Meshlium.
• PKCS5: this method adds the input at the trailing end with k - (l mod k) octets all having value k - (l mod k), where l is the
length of the input. Notice that this mode is not supported by Meshlium.
AES Algorithm Key Size Data Block Size
AES-128 128 bits 16 bytes
AES-192 192 bits 16 bytes
AES-256 256 bits 16 bytes
-12- v7.0
Page 13

Condentiality (privacy)
4.1. Waspmote Libraries
4.1.1. Waspmote AES Files
WaspAES.h is the header le of the class, and WaspAES.cpp is the class where the functions and variables are implemented.
It is mandatory to include the AES library when using it. The following line must be introduced at the beginning of the code:
#include <WaspAES.h>
4.1.2. Constructor
To start using Waspmote AES library, an object from class ‘WaspAES’ must be created. This object, called ‘AES’, is created inside
the Waspmote AES library and it is public to all libraries. It is used through the guide to show how the Waspmote AES library
works.
When creating this constructor, no variables are initialized by default.
4.1.3. Pre-Dened Constants
There are some constants dened in ‘WaspAES.h’ related with the dierent encryption and padding modes that can be used to
encrypt messages.
4.2. Calculating the encrypted message length
Before using an encryption function, the length of the encrypted message is needed in order to create the proper memory
buers. As the data block size is 16 bytes, the nal length is multiple of 16.
The next code shows how to calculate the length of the ciphertext in bytes. The function AES.sizeOfBlocks() returns the
total length of the 16-byte data blocks that will be included within the message.
{
char plaintext[] = ”Original Text”;
uint16_t length;
length = AES.sizeOfBlocks(plaintext);
}
4.3. AES Encryption
The next code shows how to encrypt a message from a plaintext with the function AES.encrypt().
When calling this function, the mode of operation must be specied between: ECB or CBC. In the case that the mode of operation
is CBC, the initialization vector must be dened as a 16-byte array of bytes.
Finally, the padding mode must be specied between two possibilities: PKCS5 or ZEROS
Example of use:
{
// AES 128 encryption: ECB mode, PKCS5 padding
AES.encrypt( 128,
password,
message,
encrypted_message,
ECB,
PKCS5);
-13- v7.0
Page 14

Condentiality (privacy)
// AES 128 encryption: CBC mode, ZEROS padding
uint8_t IV[16] =
{0x00,0x01,0x02,0x03,0x04,0x05,0x06,0x07,0x08,0x09,0x0A,0x0B,0x0C,0x0D,0x0E,0x0F};
AES.encrypt( 128,
password,
message,
encrypted_message,
CBC,
ZEROS,
IV);
}
The input message length can be any value. However, the output message length will be a multiple of 16 bytes.
The AES password is padded with zeros in the case it does not reach the proper length selected by the AES encryption function.
4.4. Printing Message
Some functions have been created to write encrypted message to the USB port.
{
// Writes the encrypted message to the USB port on Matrix format
AES.printMatrix(encrypted_message, length);
}
Example of use may be found in:
http://www.libelium.com/development/waspmote/examples/aes-01-aes128-ecb-pkcs/
http://www.libelium.com/development/waspmote/examples/aes-02-aes192-ecb-pkcs/
http://www.libelium.com/development/waspmote/examples/aes-03-aes256-ecb-pkcs/
http://www.libelium.com/development/waspmote/examples/aes-04-aes128-cbc-zeros/
http://www.libelium.com/development/waspmote/examples/aes-05-aes256-cbc-zeros/
http://www.libelium.com/development/waspmote/examples/aes-06-aes256-cbc-zeros/
-14- v7.0
Page 15

Secure Communication Scheme
5. Secure Communication Scheme
It is possible to communicate from Waspmote to Meshlium directly using secure communication schemes.
In the case that XBee modules are used to communicate, the user has the chance to enable the AES-128 link layer encryption
that these modules provide. On the other hand, application layer encryption can be used thanks to the AES encryption libraries.
This second option is available for any kind of communication module provided by Waspmote (XBees, LoRa, 3G, GPRS, WiFi,
Bluetooth, BLE, Industrial Protocols, etc). The API libraries permit to use AES encryption with dierent key sizes: 128, 192 or 256
bits.
The following diagram shows how the communication scheme works:
Figure : Communication scheme
The user has three dierent possibilities: AES-128, AES-192 and AES-256. Regarding the cipher block mode, only ECB is supported
to communicate to Meshlium. Besides, zeros padding is the only choice permitted.
The process of how to encrypt a previously created frame is as follows:
1. Create a new Frame (ASCII or BINARY)
2. Generate an encrypted frame from the original one
3. Send the encrypted frame
For more information about how to create encrypted frames go to: Data Frame guide
Once the encrypted frame is received by Meshlium, the sensorParser decrypts the frame and stores the sensor elds inside the
database automatically.
Example of sending encrypted frames to Meshlium via XBee-802.15.4:
http://www.libelium.com/development/waspmote/examples/aes-07-encryption-128-cbc-zeros/
-15- v7.0
Page 16

Key Management on Meshlium
6. Key Management on Meshlium
Meshlium is a gateway which can contain 4 dierent radio interfaces: WiFi AP, 4G/3G/GPRS, Bluetooth and RF communications.
RF communications may be implemented by several RF modules. Meshlium can also integrate a GPS module for mobile and
vehicular applications. These features along with an aluminium IP65 enclosure allows Meshlium to be placed anywhere outdoor..
Figure : Meshlium
More info: http://www.libelium.com/meshlium
6.1. Link layer key Management (only XBee)
Waspmote settings
Encryption in this layer is provided through the AES 128b algorithm. Specically through the type AES-CTR. Only XBee modules
support encryption in the link layer. Encryption is done inside the XBees, in a transparent way for the user. The XBees take care
of everything: the sender XBee gets the not-encrypted data to send, cyphers it and transmits the secret message. On the other
hand, the receiver XBee receives the message, de-cyphers it and delivers not-encrypted data. In order to enable encryption in
this layer and set the proper private AES key, Waspmote API provides the following functions to be applied in Waspmote codes
(i.e. XBee-802.15.4):
{
xbee802.encryptionMode(1);
xbee802.setLinkKey(key);
}
-16- v7.0
Page 17

Key Management on Meshlium
Meshlium settings
In Meshlium’s Manager System, inside Sensor Network section, users can set the encryption mode to the Meshlium’s XBee
module receiver for the link layer.
Depending on the kind of XBee model the parameters to be congured may vary.
Complete list:
• PAN ID: Personal Arena Network ID
• Channel: frequency channel used
• Network Address (4 hex digits): 16-bit address (only for 802.15.4)
• Node ID: maximum 20 characters
• Power level: [0..4] (by default 4)
• Encrypted mode: true/false (by default false)
• Encryption Key: 16 characters
• MAC: 64b hardware address. It is a read only value divided in two parts:
- MAC high: 32-bit (hex eld)
- MAC low: 32-bit (hex eld)
The parameters to enable AES-128 to link layer are: “Encrypted mode” and “Encrypted key”.
Figure : XBee Plugin
-17- v7.0
Page 18

Key Management on Meshlium
6.2. Application Layer Key Management (AES libraries)
Meshlium is capable to properly receive encrypted data from Waspmote. The coding process is made in the application layer, so
it’s Waspmote and Meshlium processors (and not the XBee module) which encrypt and decrypt the messages.
The user have to set a key for the encryption in Waspmote and Meshlium.
In the Manager System, inside section Tools, go to encryption section:
Figure : Key Management
For each Waspmote a new specic AES key must be specied. Thus, Waspmotes keys are added to a encryption Key le. In this
interface, the user must specify both node ID and Waspmote AES secret key (128, 192 or 256 bits) for each Waspmote. On the
other hand, in Waspmote codes the node ID is specied when frame.setID() function is called.
After dening the above elds it is necessary to press the button “Save Waspmote”. A new entry is generated in the list.
To delete Waspmotes from the list, select the Waspmote to be deleted and press “Delete Waspmote”. After this step, the encrypted
Waspmote frames received can not be decrypted anymore.
-18- v7.0
Page 19

Key Management on Meshlium
The AES secret key is necessary to recognize the frames sent each Waspmote to Meshlium.
Figure : Waspmote to Meshlium with AES 256
When an encrypted frame arrives to Meshlium, the sensorParser will consult the encryptionKey le for the AES secret key, and
use the AES algorithm to decrypt the message.
-19- v7.0
Page 20

Code examples and extended information
7. Code examples and extended information
In the Waspmote Development section you can nd complete examples:
http://www.libelium.com/development/waspmote/examples
Example:
/*
* ------Waspmote AES_01 Encryption 128 ECB PKCS ------- *
* This example shows how to encrypt plain text using:
* - AES algorithm
* - 128-bit key size
* - PKCS Padding
* - ECB Cipher Mode
*
* Copyright (C) 2015 Libelium Comunicaciones Distribuidas S.L.
* http://www.libelium.com
*
* This program is free software: you can redistribute it and/or modify
* it under the terms of the GNU General Public License as published by
* the Free Software Foundation, either version 2 of the License, or
* (at your option) any later version.
*
* This program is distributed in the hope that it will be useful,
* but WITHOUT ANY WARRANTY; without even the implied warranty of
* MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
* GNU General Public License for more details.
*
* You should have received a copy of the GNU General Public License
* along with this program. If not, see <http://www.gnu.org/licenses/>.
*
* Version: 0.4
* Design: David Gascón
* Implementation: Alvaro Gonzalez, Yuri Carmona
*/
#include “WaspAES.h”
// Dene a 16-Byte (AES-128) private key to encrypt message
char password[] = “libeliumlibelium”;
// original message on which the algorithm will be applied
char message[] = “This_is_a_message”;
// Variable for encrypted message’s length
uint16_t encrypted_length;
// Declaration of variable encrypted message
uint8_t encrypted_message[300];
void setup()
{
// init USB port
USB.ON();
USB.println(F(“AES_01 example:”));
USB.println(F(“- 128-bit Key Size”));
USB.println(F(“- ECB Cipher Mode”));
USB.println(F(“- PKCS5 padding”));
USB.println();
USB.print(F(“\nOriginal message:”));
-20- v7.0
Page 21

Code examples and extended information
USB.println(message);
USB.print(F(“Original length:”));
USB.println((int)strlen(message));
USB.println();
}
void loop()
{
////////////////////////////////////////////////////////////////
// 1. Encrypt message
////////////////////////////////////////////////////////////////
USB.println(F(“1. Encrypt message”));
// 1.1. Calculate length in Bytes of the encrypted message
encrypted_length = AES.sizeOfBlocks(message);
// 1.2. Calculate encrypted message with ECB cipher mode and PKCS5 padding.
AES.encrypt( AES_128
, password
, message
, encrypted_message
, ECB
, PKCS5);
// 1.3. Printing encrypted message
USB.print(F(“AES Encrypted message:”));
AES.printMessage( encrypted_message, encrypted_length);
// 1.4. Printing encrypted message’s length
USB.print(F(“AES Encrypted length:”));
USB.println( (int)encrypted_length);
USB.println();
delay(5000);
USB.println(F(“***********************”));
}
-21- v7.0
Page 22

8. API changelog
Keep track of the software changes on this link:
www.libelium.com/development/waspmote/documentation/changelog/#Encryption
API changelog
-22- v7.0
Page 23

Certications
9. Certications
Libelium oers 2 types of IoT sensor platforms, Waspmote OEM and Plug & Sense!:
• Waspmote OEM is intended to be used for research purposes or as part of a major product so it needs nal certication on
the client side. More info at: www.libelium.com/products/waspmote
• Plug & Sense! is the line ready to be used out-of-the-box. It includes market certications. See below the specic list of
regulations passed. More info at: www.libelium.com/products/plug-sense
Besides, Meshlium, our multiprotocol router for the IoT, is also certied with the certications below. Get more info at:
www.libelium.com/products/meshlium
List of certications for Plug & Sense! and Meshlium:
• CE (Europe)
• FCC (US)
• IC (Canada)
• ANATEL (Brazil)
• RCM (Australia)
• PTCRB (cellular certication for the US)
• AT&T (cellular certication for the US)
Figure : Certications of the Plug & Sense! product line
You can nd all the certication documents at:
www.libelium.com/certications
-23- v7.0
 Loading...
Loading...