lexma X548, XS548, XS796, X925, XS925 User Manual
...
Lexmark Multi-Function Pr inters Security Target
Lexmark X548, XS548, X748, X792, XS796,
X925, XS925, X950, X952, X954, XS955 and
6500e Scanner (with T650, T652, or T654
Printer) Multi-Function Printers
Security Target
Version 1.11
September 22, 2014
Lexmark International, Inc.
740 New Circle Road
Lexington, KY 40550

Lexmark Multi-Function Pr inters Security Target
2
Prepared By:
http://www.consulting-cc.com
Prepared For:
http://www.lexmark.com
DOCUMENT INTRODUCTION
Common Criteria Consulting LLC
15804 Laughlin Lane
Silver Spring, MD 20906
Lexmark International, Inc.
740 New Circle Road
Lexington, KY 40550
This document provides the basis for an evaluation of a specific Target of Evaluation (TOE), the
Lexmark X548, XS548, X748, X792, XS796, X925, XS925, X950, X952, X954, XS955 and
6500e Scanner (with T650, T652, or T654 Printer) Multi-Function Printers. This Security Target
(ST) defines a set of assumptions about the aspects of the environment, a list of threats that the
product intends to counter, a set of security objectives, a set of security requirements and the IT
security functions provided by the TOE which meet the set of requirements.
Various text from clauses 5, 7-9, and 12 reprinted with permission from IEEE, 445 Hoes Lane,
Piscataway, New Jersey 08855, from IEEE "2600.2™-2009 Standard for a Protection Profile in
Operational Environment B", Copyright © 2009 IEEE. All rights reserved.
REVISION HISTORY
Rev Description
1.0 January 13, 2011, initial release
1.1 January 19, 2011, addressed lab EORs
1.2 January 24, 2011, addressed lab EORs
1.3 May 4, 2011, enabled management via the touch panel and addressed FSP consistency
1.4 October 28, 2011, inserted CAVP certificate numbers, deleted references to Lexlink and
Netware
1.5 December 7, 2011, addressed TVOR comments, updated MFP versions
1.6 December 12, 2011, updated MFP version
1.7 December 14, 2011, updated MFP version for 6500e
1.8 February 23, 2012, Addressed FVOR comments
1.9 March 15, 2012, Code update to address a PJL vulnerability
1.10 July 17, 2012, Added the X748 as an additional MFP model
1.11 September 22, 2014, Assurance Continuity for new code version

Lexmark Multi-Function Pr inters Security Target
3
TABLE OF CONTENTS
1. SECURITY TARGET INTRODUCTION ................................................................. 9
1.1 Security Target Reference .......................................................................................... 9
1.2 TOE Reference ............................................................................................................ 9
1.3 Evaluation Assurance Level ....................................................................................... 9
1.4 Keywords ..................................................................................................................... 9
1.5 TOE Overview ............................................................................................................. 9
1.5.1 Usage and Major Security Features ........................................................................... 9
1.5.2 TOE type .................................................................................................................. 10
1.5.3 Required Non-TOE Hardware/Software/Firmware ................................................. 10
1.6 TOE Description ....................................................................................................... 10
1.6.1 Users ........................................................................................................................ 12
1.6.2 Objects (Assets) ....................................................................................................... 13
1.6.2.1 User Data .............................................................................................................. 13
1.6.2.2 TSF Data ............................................................................................................... 14
1.6.2.3 Functions ............................................................................................................... 14
1.6.3 Operations ................................................................................................................ 15
1.6.4 Channels ................................................................................................................... 15
1.7 Physical Boundary .................................................................................................... 15
1.8 Logical Boundary ...................................................................................................... 15
1.8.1 Audit Generation ...................................................................................................... 15
1.8.2 Identification and Authentication ............................................................................ 15
1.8.3 Access Control ......................................................................................................... 15
1.8.4 Management ............................................................................................................. 16
1.8.5 Operator Panel Lockout ........................................................................................... 16
1.8.6 Fax Separation ......................................................................................................... 16
1.8.7 Hard Disk Encryption .............................................................................................. 16
1.8.8 Disk Wiping ............................................................................................................. 16
1.8.9 Secure Communication ............................................................................................ 16
1.8.10 Self Test ................................................................................................................. 16
1.9 TOE Data ................................................................................................................... 16
1.9.1 TSF Data .................................................................................................................. 16
1.9.2 Authentication Data ................................................................................................. 19
1.9.3 Security Attributes ................................................................................................... 19
1.9.4 User Data ................................................................................................................. 20
1.10 Evaluated Configuration ........................................................................................ 20
1.11 Rationale for Non-Bypassability and Separation................................................. 22
2. CONFORMANCE CLAIMS ..................................................................................... 24
2.1 Common Criteria Conformance .............................................................................. 24
2.2 Protection Profile Conformance .............................................................................. 24
2.3 Security Requirement Package Conformance ....................................................... 24
3. SECURITY PROBLEM DEFINITION ................................................................... 25
3.1 Introduction ............................................................................................................... 25
3.2 Assumptions............................................................................................................... 25
3.3 Threats ....................................................................................................................... 25

Lexmark Multi-Function Pr inters Security Target
4
3.4 Organisational Security Policies .............................................................................. 26
4. SECURITY OBJECTIVES........................................................................................ 27
4.1 Security Objectives for the TOE ............................................................................. 27
4.2 Security Objectives for the Operational Environment .......................................... 27
5. EXTENDED COMPONENTS DEFINITION ......................................................... 29
5.1 Extended Security Functional Components ........................................................... 29
5.1.1 FPT_FDI_EXP Restricted forwarding of data to external interfaces ...................... 29
FPT_FDI_EXP.1 ............................................................................................................... 30
5.2 Extended Security Assurance Components ............................................................ 30
6. SECURITY REQUIREMENTS ................................................................................ 31
6.1 TOE Security Functional Requirements ................................................................ 31
6.1.1 Security Audit (FAU) .............................................................................................. 31
6.1.1.1 FAU_GEN.1 Audit Data Generation .................................................................... 31
6.1.1.2 FAU_GEN.2 User Identity Association ............................................................... 33
6.1.2 Cryptographic Support (FCS) .................................................................................. 33
6.1.2.1 FCS_CKM.1 Cryptographic Key Generation ....................................................... 33
6.1.2.2 FCS_CKM.4 Cryptographic Key Destruction ...................................................... 33
6.1.2.3 FCS_COP.1 Cryptographic Operation ................................................................. 33
6.1.3 User Data Protection (FDP) ..................................................................................... 34
6.1.3.1 FDP_ACC.1 Subset Access Control ..................................................................... 34
6.1.3.2 FDP_ACF.1 Security Attribute Based Access Control ........................................ 34
6.1.3.3 FDP_RIP.1 Subset Residual Information Protection ............................................ 37
6.1.4 Identification and Authentication (FIA) .................................................................. 37
6.1.4.1 FIA_AFL.1 Authentication Failure Handling....................................................... 37
6.1.4.2 FIA_ATD.1 User Attribute Definition ................................................................. 37
6.1.4.3 FIA_UAU.1 Timing of Authentication................................................................. 37
6.1.4.4 FIA_UAU.7 Protected Authentication Feedback ................................................. 38
6.1.4.5 FIA_UID.1 Timing of Identification .................................................................... 38
6.1.4.6 FIA_USB.1 User-Subject Binding ....................................................................... 38
6.1.5 Security Management (FMT) .................................................................................. 39
6.1.5.1 FMT_MOF.1 Management of Security Functions Behaviour .............................. 39
6.1.5.2 FMT_MSA.1 Management of Security Attributes ............................................... 39
6.1.5.3 FMT_MSA.3 Static Attribute Initialisation .......................................................... 39
6.1.5.4 FMT_MTD.1 Management of TSF Data .............................................................. 39
6.1.5.5 FMT_SMF.1 Specification of Management Functions ........................................ 41
6.1.5.6 FMT_SMR.1 Security Roles ................................................................................ 41
6.1.6 Protection of the TSF (FPT) .................................................................................... 43
6.1.6.1 FPT_FDI_EXP.1 Restricted forwarding of data to external interfaces ................ 43
6.1.6.2 FPT_STM.1 Reliable Time Stamps ...................................................................... 43
6.1.6.3 FPT_TST.1 TSF Testing ....................................................................................... 43
6.1.7 TOE Access (FTA) .................................................................................................. 43
6.1.7.1 FTA_SSL.3 TSF-Initiated Termination ................................................................ 43
6.1.8 Trusted Path/Channels (FTP) ................................................................................... 43
6.1.8.1 FTP_ITC.1 Inter-TSF Trusted Channel ................................................................ 43
6.2 TOE Security Assurance Requirements ................................................................. 43

Lexmark Multi-Function Pr inters Security Target
5
6.3 CC Component Hierarchies and Dependencies ..................................................... 44
7. TOE SUMMARY SPECIFICATION ....................................................................... 46
7.1 Security Functions .................................................................................................... 46
7.1.1 Audit Generation ...................................................................................................... 46
7.1.2 Identification and Authentication ............................................................................ 47
7.1.2.1 Backup Password .................................................................................................. 48
7.1.3 Access Control ......................................................................................................... 48
7.1.3.1 Internal Account Building Blocks ........................................................................ 52
7.1.3.2 LDAP+GSSAPI and PKI Auth Building Blocks .................................................. 52
7.1.3.3 Common Processing ............................................................................................. 52
7.1.3.4 Function Access Control ....................................................................................... 53
7.1.3.5 Postscript Access Control ..................................................................................... 54
7.1.4 Management ............................................................................................................. 55
7.1.4.1 Reports Menu ........................................................................................................ 55
7.1.4.2 Network/Ports Menu ............................................................................................. 55
7.1.4.3 Security Menu ....................................................................................................... 55
7.1.4.4 Settings Menu ....................................................................................................... 58
7.1.4.5 Security Reset Jumper ........................................................................................... 59
7.1.5 Operator Panel Lockout ........................................................................................... 60
7.1.6 Fax Separation ......................................................................................................... 60
7.1.7 Hard Disk Encryption .............................................................................................. 61
7.1.8 Disk Wiping ............................................................................................................. 61
7.1.9 Secure Communications .......................................................................................... 62
7.1.10 Self Test ................................................................................................................. 62
8. PROTECTION PROFILE CLAIMS ........................................................................ 63
8.1 TOE Type Consistency ............................................................................................. 63
8.2 Security Problem Definition Consistency ............................................................... 63
8.3 Security Objectives Consistency .............................................................................. 63
8.4 Security Functional Requirements Consistency .................................................... 63
8.5 Security Assurance Requirements Consistency ..................................................... 64
9. RATIONALE .............................................................................................................. 65
9.1 Rationale for IT Security Objectives....................................................................... 65
9.1.1 Rationale Showing Threats to Security Objectives ................................................. 65
9.1.2 Rationale Showing Policies to Security Objectives ................................................. 66
9.1.3 Rationale Showing Assumptions to Environment Security Objectives ................... 67
9.2 Security Requirements Rationale ............................................................................ 68
9.2.1 Rationale for Security Functional Requirements of the TOE Objectives ................ 68
9.2.2 Security Assurance Requirements Rationale ........................................................... 71
9.3 TOE Summary Specification Rationale .................................................................. 71

Lexmark Multi-Function Pr inters Security Target
6
LIST OF FIGURES
Figure 1 - TOE Model ................................................................................................... 12
LIST OF TABLES
Table 1 - Technical Characteristics of the MFP Models .............................................. 11
Table 2 - Technical Characteristics of the Integrated Printer Models .......................... 11
Table 3 - Notational prefix conventions ....................................................................... 12
Table 4 - Users ............................................................................................................. 13
Table 5 - User Data ...................................................................................................... 13
Table 6 - TSF Data ....................................................................................................... 14
Table 7 - Functions ....................................................................................................... 14
Table 8 - TSF Data ....................................................................................................... 16
Table 9 - Authentication Data ...................................................................................... 19
Table 10 - Security Attributes .................................................................................... 20
Table 11 - User Data .................................................................................................. 20
Table 12 - Source-Destination Combinations ............................................................ 22
Table 13 - Assumptions .............................................................................................. 25
Table 14 - Threats....................................................................................................... 25
Table 15 - Organizational Security Policies for the TOE .......................................... 26
Table 16 - Security Objectives for the TOE ............................................................... 27
Table 17 - Security Objectives of the Operational Environment ............................... 27
Table 18 - Audit data requirements ............................................................................ 31
Table 19 - Cryptographic Operations ......................................................................... 33
Table 20 - Common Access Control SFP Rules ........................................................ 35
Table 21 - Management of Security Functions Behaviour......................................... 39
Table 22 - TSF Data ................................................................................................... 40
Table 23 - FMT_SMR.1 Detail .................................................................................. 42
Table 24 - EAL2+ Assurance Requirements .............................................................. 44
Table 25 - TOE SFR Dependency Rationale ............................................................. 44
Table 26 - Access Control Items ................................................................................ 49
Table 27 - TOE Function Access Control SFP Rules ................................................ 53
Table 28 - Network/Ports Menu TSF Data ................................................................ 55

Lexmark Multi-Function Pr inters Security Target
7
Table 29 - Security Menu TSF Data .......................................................................... 55
Table 30 - General Settings Menu TSF Data ............................................................. 58
Table 31 - Fax Settings Menu TSF Data .................................................................... 58
Table 32 - Email Settings Menu TSF Data ................................................................ 59
Table 33 - Print Settings/Setup Settings Menu TSF Data .......................................... 59
Table 34 - Threats, Policies and Assumptions to Security Objectives Mapping ....... 65
Table 35 - Threats to Security Objectives Rationale .................................................. 66
Table 36 - Policies to Security Objectives Rationale ................................................. 67
Table 37 - Assumptions to Security Objectives Rationale ......................................... 67
Table 38 - SFRs to Security Objectives Mapping ...................................................... 68
Table 39 - Security Objectives to SFR Rationale....................................................... 69
Table 40 - SFRs to TOE Security Functions Mapping .............................................. 71
Table 41 - SFR to SF Rationale.................................................................................. 72
ACRONYMS LIST
AES ................................................................................. Advanced Encryption Standard
AIO ..................................................................................................................... All In One
BSD .................................................................................. Berkeley Software Distribution
CAC ................................................................................................ Common Access Card
CAVP .................................................... Cryptographic Algorithm Validation Program
CC ........................................................................................................... Common Criteria
CM ......................................................................................... Configuration Management
EAL .......................................................................................Evaluation Assurance Level
ESP ................................................................................. Encapsulating Security Payload
FTP ................................................................................................. File Transfer Protocol
GSSAPI ............................... Generic Security Services Application Program Interface
HTTP .................................................................................. HyperText Transfer Protocol
I&A ................................................................................. Identification & Authentication
IPSec ......................................................................................... Internet Protocol Security
IPv4......................................................................................... Internet Protocol version 4
IPv6......................................................................................... Internet Protocol version 6
ISO .......................................................................... International Standards Orgaization
IT ................................................................................................. Information Technology
KDC ............................................................................................. Key Distribution Center
LAN ................................................................................................... Local Area Network
LDAP .................................................................. Lightweight Directory A ccess Proto col
MB ....................................................................................................................... MegaByte
MFD ................................................................................................ Multi-Finction Device

Lexmark Multi-Function Pr inters Security Target
8
MFP ............................................................................................... Multi-Function Printer
NTP............................................................................................... Network Time Protocol
OSP ................................................................................... Organizational Security Policy
PIV ..................................................................................... Personal Identity Verification
PJL .................................................................................................. Printer Job Language
PKI ........................................................................................... Public Key Infrastructure
PP ............................................................................................................ Protection Profile
RFC .............................................................................................. Request For Comments
SASL............................................................. Simple Authentication and Security Layer
SFP ............................................................................................. Security Function Policy
SFR .............................................................................. Security Functional Requirement
SMTP .............................................................................Simple Mail Transport Protocol
ST ................................................................................................................Security Target
TFTP ................................................................................. Trivial File Transfer Protocol
TOE ................................................................................................... Target of Evaluation
TSF ............................................................................................... TOE Security Function
UI .................................................................................................................. User Interface
URL ........................................................................................ Uniform Resource Locator
USB .................................................................................................... Universal Serial Bus

Lexmark Multi-Function Pr inters Security Target
9
1. Security Target Introduction
This Security Target (ST) describes the objectives, requirements and rationale for the Lexmark
X548, XS548, X748, X792, XS796, X925, XS925, X950, X952, X954, XS955 and 6500e
Scanner (with T650, T652, or T654 Printer) Multi-Function Printers. The language used in this
Security Target is consistent with the Common Criteria for Information Technology Security
Evaluation, Version 3.1 and all international interpretations through March 17, 2011. As such,
the spelling of terms is presented using the internationally accepted English.
1.1 Security Target Reference
Lexmark X548, XS548, X748, X792, XS796, X925, XS925, X950, X952, X954, XS955 and
6500e Scanner (with T650, T652, or T654 Printer) Multi-Function Printers Security Target,
version 1.11, September 22, 2014.
1.2 TOE Reference
Lexmark X548 (LHS40.VK.P440), XS548 (LHS40.VK.P440), X748 (LHS40.NY.P440), X792
(LHS40.MR.P440), XS796 (LHS40.MR.P440), X925 (LHS40.HK.P440), XS925
(LHS40.HK.P440), X950 (LHS40.TQ.P440), X952 (LHS40.TQ.P440), X954
(LHS40.TQ.P440), XS955 (LHS40.TQ.P440) and 6500e Scanner (LHS40.JR.P440) (with T650
(LHS40.JR.P440), T652 (LHS40.JR.P440), or T654 (LHS40.JR.P440) Printer) Multi-Function
Printers
1.3 Evaluation Assurance Level
Assurance claims conform to EAL2 (Evaluation Assurance Level 2) augmented with
ALC_FLR.2 from the Common Criteria for Information Technology Security Evaluation,
Version 3.1.
1.4 Keywords
Hardcopy, Paper, Document, Printer, Scanner, Copier, Facsimile, Fax, Document Server,
Document Storage and Retrieval, Nonvolatile storage, Residual data, Temporary data, Disk
overwrite, Network interface, Shared communications medium, Multifunction Device,
Multifunction Product, All-In-One, MFD, MFP
1.5 TOE Overview
1.5.1 Usage and Major Security Features
The MFPs are multi-functional printer systems with scanning, fax, and networked capabilities. Their
capabilities extend to walk-up scanning and copying, scanning to fax, scanning to email, and
servicing print jobs through the network. The MFPs feature an integrated touch-sensitive operator
panel.
The major security features of the TOE are:
1. All Users are identified and authenticated as well as authorized before being granted
permission to perform any restricted TOE functions.
2. Administrators authorize Users to use the functions of the TOE.
3. User Document Data are protected from unauthorized disclosure or alteration.
4. User Function Data are protected from unauthorized alteration.

Lexmark Multi-Function Pr inters Security Target
10
5. TSF Data, of which unauthorized disclosure threatens operational security, are protected
from unauthorized disclosure.
6. TSF Data, of which unauthorized alteration threatens operational security, are protected
from unauthorized alteration.
7. Document processing and security-relevant system events are recorded, and such records
are protected from disclosure or alteration by anyone except for authorized personnel.
1.5.2 TOE type
Miscellaneous (Multifunction Hard Copy Device)
1.5.3 Required Non-TOE Hardware/Software/Firmware
The TOE is a complete MFP, including the firmware and hardware. To be fully operational, any
combination of the following items may be connected to the TOE:
1. A LAN for network connectivity. The TOE supports IPv4 and IPv6.
2. A telephone line for fax capability.
3. IT systems that submit print jobs to the MFP via the network using standard print
protocols.
4. IT systems that send and/or receive faxes via the telephone line.
5. An IT system acting as the remote syslog recipient of audit event records sent from the
TOE.
6. LDAP server to support Identification and Authentication (I&A). This component is
optional depending on the type(s) of I&A mechanisms used.
7. Card reader and cards to support PKI authentication using Common Access Card (CAC)
or Personal Identity Verification (PIV) cards. This component is optional depending on
the type(s) of I&A mechanisms used. The supported card readers are:
a. Omnikey 5121 SmartCard Reader,
b. Omnikey 5321 SmartCard Reader,
c. Omnikey 5125 SmartCard Reader,
d. Omnikey 3121 SmartCard Reader,
e. Any other Omnikey SmartCard Readers that share the same USB Vendor IDs
and Product IDs with the above readers (example Omnikey 3021),
f. SCM SCR 331.
1.6 TOE Description
The TOE provides the following functions related to MFPs:
1. Printing – producing a hardcopy document from its electronic form
2. Scanning – producing an electronic document from its hardcopy form
3. Copying – duplicating a hardcopy document
Lexmark Multi-Function Pr inters Security Target
11
X548
IBM 750CL PowerPC
Color
25
XS548
IBM 750CL PowerPC
Color
25
X748
Freescale 7448 PowerPC
Color
35
X792
Freescale 7448 PowerPC
Color
50
XS796
Freescale 7448 PowerPC
Color
50
X925
Freescale 7448 PowerPC
Color
30
XS925
Freescale 7448 PowerPC
Color
30
X950
IBM 750CL PowerPC
Color
40
X952
IBM 750CL PowerPC
Color
45
X954
IBM 750CL PowerPC
Color
50
XS955
IBM 750CL PowerPC
Color
50
6500e
IBM 750CL PowerPC
Mono
See Table 2 -
T650
500 MHz ARM
45
T652
500 MHz ARM
50
T654
600 MHz ARM
55
4. Faxing – scanning documents in hardcopy form and transmitting them in electronic form
over telephone lines, and receiving documents in electronic form over telephone lines and
printing them in hardcopy form
The Lexmark 6500e Scanner is integrated with a T65x monochrome printer to provide a
complete MFP. The scanner unit provides the touch panel, original document handler, fax
interface, and network interface. The printer unit provides the print engine and its only external
connection is to the scanner unit. The TOE includes the hardware and firmware in both the
scanner and printer units. All of the other models included in the evaluation (X548, XS548,
X748, X792, XS796, X925, XS925, X950, X952, X954, and XS955) are complete MFPs in a
single unit.
All of the MFPs included in this evaluation provide the same security functionality. Their
differences are in the speed of printing and support for color operations. The following tables
summarize the technical characteristics of the models.
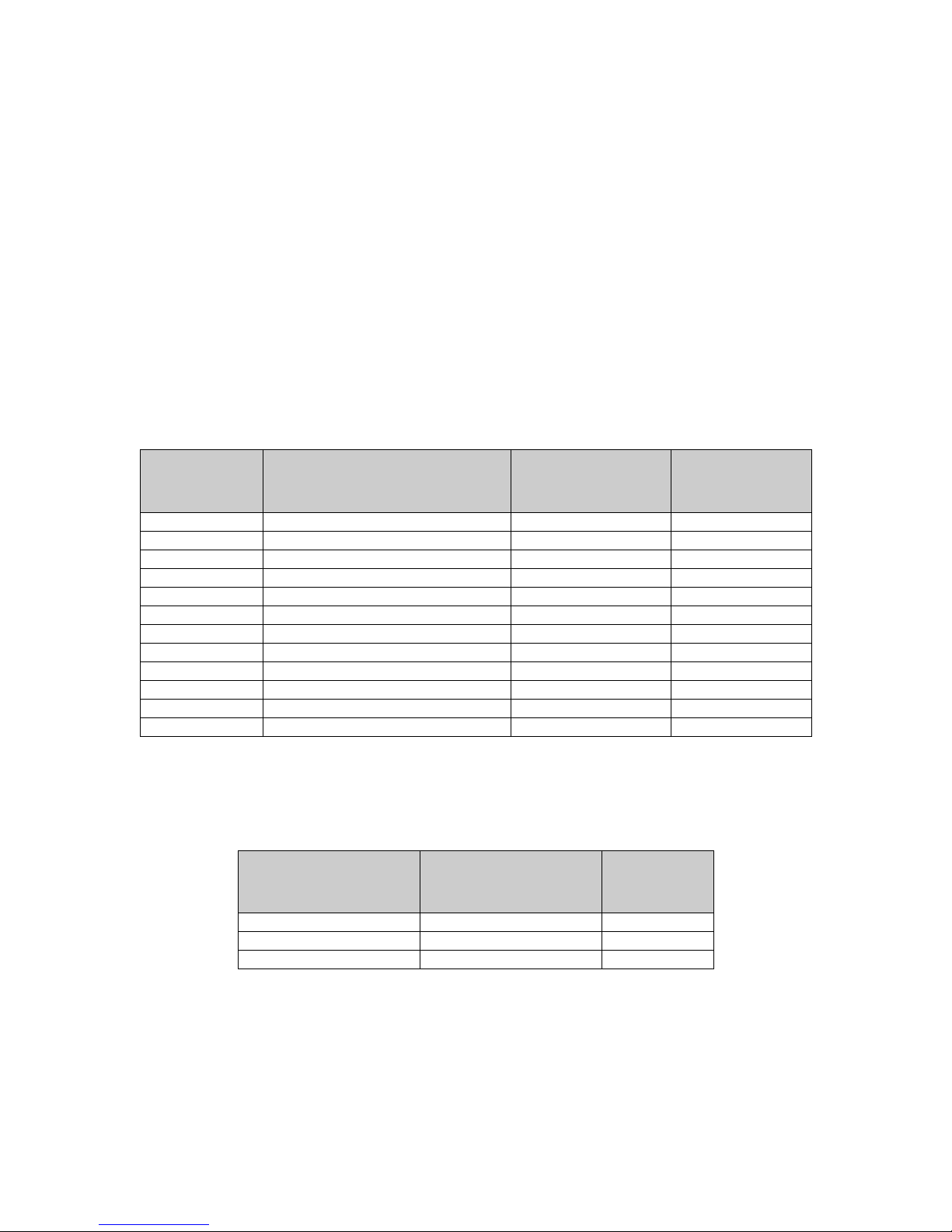
Table 1 - Technical Characteristics of the MFP Models
Model Processor Color/Mono Pages Per
Minute
The speed of printing for the 6500e Scanner solution is dependent on the printer model that the
scanner is integrated with. The following table provides this information.
Table 2 - Technical Characteristics of the Integrated Printer Models
Model Processor Pages Per
Minute
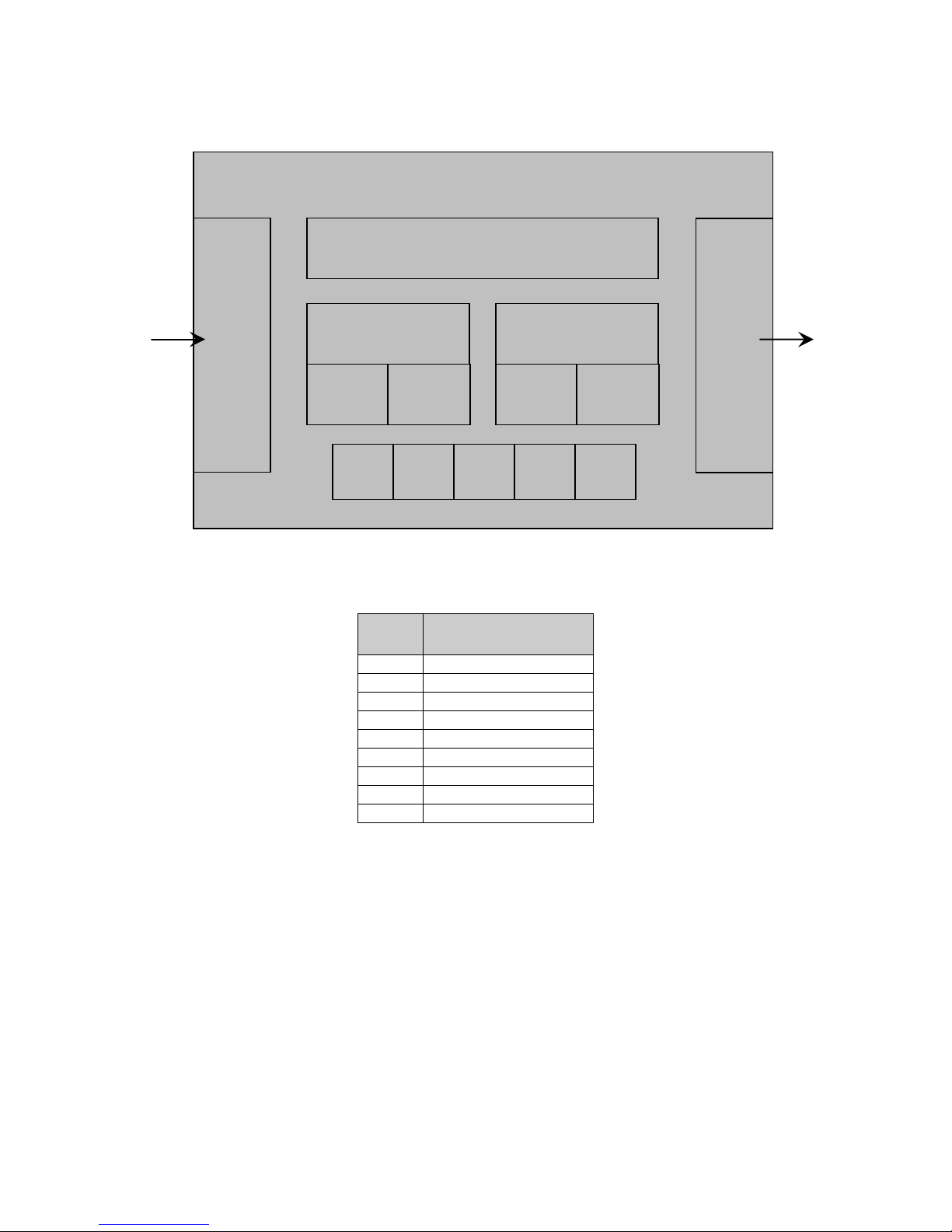
The Target of Evaluation (TOE) is described using the standard Common Criteria terminology of
Users, Objects, Operations, and Interfaces. Two additional terms are introduced: Channel
describes both data interfaces and hardcopy document input/output mechanisms, and TOE
Owner is a person or organizational entity responsible for protecting TOE assets and establishing
related security policies. In this document, the terms User and Subject are used interchangeably.
Lexmark Multi-Function Pr inters Security Target
12
U.
User
D.
Data
F.
Function
T.
Threat
P.
Policy
A.
Assumption
O.
Objective
OE.
Environmental objective
+
Security Attribute
TSF
User
User
TSF
TSF
Fax
Copy
Scan
Print
Shared
Functions
Figure 1 - TOE Model
Input
Channel
User Data
Document
Data
Functions
Common MF P F unctions
Function
Functions
Functions
Protected
Data
Functions
TSF Data
Confidential
Medium
The following prefixes are used to indicate different entity types:
Table 3 - Notational prefix conventions
Prefix Type of entity
Output
Channel
Data
1.6.1 Users
Users are entities that are external to the TOE and which interact with the TOE. There may be
two types of Users: Normal and Administrator.
Lexmark Multi-Function Pr inters Security Target
13
U.USER
Any authorized User.
U.NORMAL
A User who is authorized to perform User Document Data processing
terms identified above are used.
U.ADMINISTRATOR
A User who has been specifically granted the authority to manage some
used.
D.DOC
User Document Data consists of the information contained in a user’s document. This
5. User data in received faxes
Table 4 - Users
Designation Definition
functions o f the TOE.
In the remainder of this document, the term “Normal User” is used
interchangeably with U.NORMAL.
The TOE provides user-level permissions to access specific document
processing f unc ti o ns ( e.g. print, copy). When i t is necessa ry to distinguish
the specific permission, that in formation is supplied. Otherwise the generic
portion or all of the TOE and whose actio ns may affect the TOE securit y
policy (TSP).
In the remainder of this document, the terms “Administrator” and
“Authorized Administrator” are used interchangeably with
U.ADMINISTRATOR.
The TOE provides user -level permissions to access specific management
functions. When it is necessary to distinguish the specific permission, t hat
information is supplied. Otherwise the generic terms identified above are
1.6.2 Objects (Assets)
Objects are passive entities in the TOE, that contain or receive information, and upon which
Subjects perform Operations. Objects are equivalent to TOE Assets. There are three categories of
Objects: User Data, TSF Data, and Functions.
1.6.2.1 User Data
User Data are data created by and for Users and do not affect the operation of the TOE Security
Functionality (TSF). This type of data is composed of two types of objects: User Document
Data, and User Function Data.
Table 5 - User Data
Designation Definition
includes the original document itself in either hardcopy or electronic form, image data,
or residually-stored data created by the hardcopy device while processing an original
document and printed hardcopy output.
For this TOE, D.DOC includes:
1. User data contained in jobs submitted from the network for printing
2. Scanned data to be printed (copying)
3. Scanned data to be faxed
4. Scanned data to be emailed

Lexmark Multi-Function Pr inters Security Target
14
D.FUNC
User Function Data are the information about a user’s document or job to be processed
5. Job information for user data in received faxes
D.PROT
TSF Protected Data are assets for which alteration by a User who is neither an
security of the TOE, but for which disclosure is acceptable.
D.CONF
TSF Confidential Data are assets for which either disclosure or alteration by a User
operational security of the TOE.
F.PRT
Printing: a function in which electr onic document input is converted to physical
document output
F.SCN
Scanning: a function in which p hysical document input is converted to ele c tr onic
document output
F.CPY
Copying: a function in which physical document input is dup lic a te d to physical
document output
F.FAX
Faxing: a function in which physical document input is converted to a te le phone-based
document facsimile (fax) reception is converted to physical document output
F.SMI
Shared-medium interface: a function that transmits or receives User Data or TSF Data
wired o r wirele ss ne t wor k media and most radio-frequency wireless media
Designation Definition
by the TOE.
For this TOE, D.FUNC includes:
1. Job information for network print jobs
2. Job information for scanned data to be printed (copying)
3. Job information for scanned data to be faxed
4. Job information for scanned data to be emailed
1.6.2.2 TSF Data
TSF Data are data created by and for the TOE and that might affect the operation of the TOE.
This type of data is composed of two types of objects: TSF Protected Data and TSF Confidential
Data.
Table 6 - TSF Data
Designation Definition
Administrator nor the owner of the data would have an effect on the operational
who is neither an Administrator nor the owner o f the data would have an effect on the
1.6.2.3 Functions
Functions perform processing, storage, and transmission of data that may be present in the TOE.
These functions are described in the following table.
Table 7 - Functions
Designation Definition
document facsimile (fax) transmission, and a function in which a telephone-based
over a communications medium which is or can be shared by other users, such as

Lexmark Multi-Function Pr inters Security Target
15
1.6.3 Operations
Operations are a specific type of action performed by a Subject on an Object. Five types of
operations are addressed: those that result in disclosure of information (Read), those that result in
alteration of information (Create, Modify, Delete), and those that invoke a function (Execute).
1.6.4 Channels
Channels are the mechanisms through which data can be transferred into and out of the TOE.
Private Medium Interface: mechanism for exchanging information that use (1) wired electronic
methods over a communications medium which, in conventional practice, is not accessed by
multiple simultaneous Users; or, (2) Operator Panel and displays that are part of the TOE. It is an
input-output channel. The touch panel and phone line are private medium interfaces.
Shared-medium Interface: mechanism for exchanging information that use wired network
electronic methods over a communications medium which, in conventional practice, is or can be
simultaneously accessed by multiple Users. It is an input-output channel. The standard network
interface is a shared-medium interface.
Original Document Handler: mechanism for transferring User Document Data in hardcopy
form into the TOE. It is an input channel. The scanner is an original document handler.
Hardcopy Output Handler: mechanism for transferring User Document Data out of the TOE in
hardcopy form. It is an output channel. The printer is a hardcopy output handler.
1.7 Physical Boundary
This section provides context for the TOE evaluation by describing the physical boundary of the
TOE. The physical boundary of the TOE consists of all of the MFP hardware and firmware.
In the case of a scanner integrated with a printer, the TOE consists of all of the scanner hardware and
firmware, all of the printer hardware and firmware, as well as the cable interconnecting the two units.
The Scanner is connected to an external network (for user access) on its primary network interface,
and the scanner’s secondary network interface is connected to the printer.
1.8 Logical Boundary
The TOE supports the security functions documented in the following sections.
1.8.1 Audit Generation
The TOE generates audit event records for security-relevant events and transmits them to a
remote IT system using the syslog protocol.
1.8.2 Identification and Authentication
The TOE supports I&A with a per-user selection of internal accounts (processed by the TOE) or
integration with an external LDAP server (in the operational environment). PKI authentication
may also be specified for users of the touch panel. A Backup Password mechanism may also be
enabled.
1.8.3 Access Control
Access controls configured for functions (e.g. fax usage) and menu access are enforced by the
TOE.
Lexmark Multi-Function Pr inters Security Target
16
Access Control
Access control authorizations specify the restrictions on
accessible), or restricted by a specified security template.
X
Account Status
Login status information is asso c ia te d with all accounts
status.
X
Analog Fax - Cancel
Faxes
Specifies whether pending faxes can be canceled by users.
X
1.8.4 Management
Through web browser sessions, authorized administrators may configure access controls and
perform other TOE management functions.
1.8.5 Operator Panel Lockout
Authorized users may lock and unlock the touch panel. When the touch panel is locked, print
jobs are still accepted but they are queued on the disk drive until the touch panel is unlocked.
1.8.6 Fax Separation
The TOE ensures that only fax traffic is sent or received via the attached phone line. Incoming
traffic is processed as fax data only; no management access or other data access is permitted. In
the evaluated configuration, the only source for outgoing faxes is the scanner.
1.8.7 Hard Disk Encryption
All use data submitted to the TOE and stored on the hard disk is encrypted to protect its
confidentiality in the event the hard drive was to be removed from the TOE.
1.8.8 Disk Wiping
In the evaluated configuration, the TOE automatically overwrites disk blocks used to store user
data as soon as the data is no longer required. The mechanism used to perform the overwrite
complies with NIST SP800-88 (dated September 2006), and the DSS "Clearing and Sanitization
Matrix" (C&SM) available at http://www.sdisac.com/clearing_and_sanitization_matrix.doc
(dated 5 March 2001).
1.8.9 Secure Communication
The TOE protects the confidentiality and integrity of all information exchanged over the attached
network by using IPSec with ESP for all network communication.
1.8.10 Self Test
During initial start-up, the TOE performs self tests on its hardware components and the integrity
of the building blocks and security templates.
1.9 TOE Data
1.9.1 TSF Data
Table 8 - TSF Data
Item Description D.CONF D.PROT
Authorizations
menus or functions. Items may be configured for no
security (accessible to everyone), disabled (not
used to authenticate against a building block. For each
building block and account, the TOE tracks the number of
login failures, time of the earliest login failure, and lock
Lexmark Multi-Function Pr inters Security Target
17
Analog Fax - Driver to
fax
Specifies whether driver fax jobs are treated as PS jobs
and printed or sent as faxes.
X
Analog Fax - Enable
Fax Receive
Specifies whether incoming faxes may be received.
X
Analog Fax - Fax
Forwarding
Specifies whether fax forwarding of incomi ng faxes to a
destination ot her than the printer is enabled.
X
Analog Fax - Holding
Faxes
Defines conditions for holding incoming faxes.
X
Date and Time
Controls whether the time is tracked internally or from a
the parameters for communicat io n wit h the se rve r .
X
Disk Encryption
Specifies whether or not files stored on disk are
operation.
X
Disk Wiping Automatic Method
Specifies the method used for automatic disk wiping.
X
Disk Wiping - Wiping
Mode
Controls the mode used for disk wiping.
X
E-mail images sent
Specifies whether ima ges forwarded via SMTP are sent as
URL.
X
Enable Audit
Determines if the device records events in the secure audit
log and (if enabled) in the remote syslog.
X
Enable Fax Scans
Specifies whether users can create faxes with the device’s
scanner.
X
Enable FTP/TFTP
Enables FTP/TFTP server on the TOE.
X
Enable HTTP Server
Enables HTTP(S) server on the TOE.
X
Enable Remote Syslog
Determines if the device transmits logged events to a
remote server.
X
Fax Mode
Specifies whether the fax function is operat ing in Analog
a fax server via SMTP).
X
Fax Server - Enable
Analog Receive
This parameter controls whether incoming faxes are
supported when operating in fax server mode
X
Fax Storage Location
Specifies the storage location for faxes. This parameter
accessible to administrators d uring operation.
X
Held Print Job
Expiration Timer
Specifies the amount of time a received print job is saved
for a user to release before it is automatically deleted.
X
Internal Account
The building blocks specify Internal Accounts as the
specify memberships.
X
Internal Account
The set of Internal Account Groups may be used to
authorizations for access controls using Internal Accounts.
X
IPSec Settings
The configuration parameters for IPSec that require IPSec
IPv6) with certificate validation.
X
Internal Accounts
Credentials
Specifies whether Internal Accounts use username and
X
Item Description D.CONF D.PROT
Parameters
as
remote NTP server. If an NTP server is used, it specifies
encrypted. This parameter must be set to “Enable” during
installation and is not accessible to administrators during
an attachment or FTP’d to a file syste m and sent as a
mode or as a Fax Server (outgoing faxes are forwarded to
must be set to “Disk” during installatio n and is not
Building Blocks
Groups
Required User
mechanism to be used for I&A or authorizations and
configure group membership for Internal Accounts and
with ESP for all networ k communication (IPv4 and/or
password or just username for the I&A process.
Lexmark Multi-Function Pr inters Security Target
18
Job Waiting
Specifies whether a print job may be placed in the Held
be processed immediately
X
LDAP Certificate
Specifies what verification (if any) should be done on the
proceeds normally.
X
LDAP+GSSAPI –
Specifies whether the default certificate or a specific
LDAP server.
X
LDAP+GSSAPI –
MFP Credentials
Specifies the Username and password to be used when
performing LDAP queries.
X
LDAP+GSSAPI
The building blocks specify LDAP+GSSAPI as the
required object names).
X
LES Applications
Specifies whether enhanced service Java applications may
administrators during operation.
X
Login Restrictions
Determines how many failed authe ntications are allowed
user is logged off automatically.
X
Network Port
Defines the parameters required for the TOE to
communicate via the standard network port
X
PKI Auth Buil ding
The building block specifies PKI as the mechanism to be
Templates.
X
Remote Sysl og
Parameters
Defines the communica tion to the r emote syslog system
X
Item Description D.CONF D.PROT
Jobs queue if the required resources (e.g. paper type) are
not currently availabl e, enabling subsequent print jobs to
Verification
Certificate
Building Blocks
certificate sent by an LDAP server. Demand specifies
that the server certificate is requested; if no certificate is
provided or if a bad certificate is pr ovided, the session is
terminated immediately. Try indicates the server
certificate is requested; if no ce rtificate is provided, the
session proceeds normally. If a bad certificate is provided,
the session is terminated imme diately. Allow indicates
the server certificate is requested; if no certificate is
provided, the session proceeds normally. If a bad
certificate is provided, it will b e ignore d and the session
certificate is required when communicating with an
mechanism to be used for I&A or authorizations and
specify parameters for retrieving information from an
LDAP server (e.g. group names to check, search base,
be executed on the TOE. This parameter must be set to
“Enable” during installation a nd is not a ccessible to
within the “Failure time frame” value before the offending
User Name is prevented from accessing any function
protected with the same building blo ck for the dur ation of
the “Lockout time” value. The “Panel Login Timeout”
determines how long the operator panel can remain idle
on the Home screen before the user is logged off
automatically. The “Remote Login Timeout” determines
how l ong web browser sessions can remain idle before the
Block
used for I&A or authorizations and specifies parameters
for validating the certificate from the card and retrieving
information from Active Directo ry. This building block is
configured during installation. I t c a n’t be viewed or
modified operationally but can be configured in Security
Lexmark Multi-Function Pr inters Security Target
19
Security Reset
Specifies the behavior of the TOE when a position change
control to its factory default sec urity level.
X
Security Templates
Security Templates are used to configure access controls
associated function or menu.
X
Simple Kerberos Setup
Defines the KDC Address, KDC Port, and Re alm for
mechanism.
X
SMTP Setup Settings
Define the SMTP server to be used to send email from the
TOE
X
SMTP Setup Settings User-Initiated E-mail
Specifies what credentials (if any) are used to authenticate
with an external SMTP server.
X
Touch Panel Menu
Display - FTP
Specifies whether or not the FTP icon should be displayed
on the touch panel menu.
X
Touch Panel Menu
shortcuts
Specifies whether or not the FTP shortcuts icon should be
X
Touch Panel Menu
Display - USB Drive
Specifies whether or not the USB Drive icon should be
displayed on the touch p anel menu.
X
USB Buffer
Disables all activity via the USB device ports.
X
Use Backup Password
Enables access to the Security Menu via the Backup
Password
X
Backup Password
The Backup Password mechanism allows an administrator to access the
configured for it.
Internal Account
Internal Accounts are used in conjunction with the Internal Account
for each defined account are used with Internal Account authentication.
Item Description D.CONF D.PROT
Jumper
of the Security Rest Jumper is detected. No Effect
indicates the jumper should be ignored. “No Security”
preserves all of the building blocks and templates that a
user has defined, but resets each access control to its
factory default security level. “Reset to Defaults” deletes
all building blocks and templates and resets each access
for restricted functions and menus. Each security
template specifies 2 building blocks – one for
authentication and one for authorization. The 2 building
blocks may be the same. The security template also
specifies a set of groups that are authorized to access the
communication with the KDC. K DC communication is
required if the TOE is using the LDAP+GSSAPI
Display - FTP
displayed on the touch p anel menu.
1.9.2 Authentication Data
All the items described in the following table are D.CONF.
Table 9 - Authentication Data
Item Description
Security Menu via a web browser session, regardless of the access controls
Usernames and Passwords
authentication and authorization mechanism. The username and pas sword
1.9.3 Security Attributes
All the items described in the following table are D.CONF.
Lexmark Multi-Function Pr inters Security Target
20
Group Memberships
The set of group memberships associated with the current session as the
result of successful I&A.
Username
The username specified during a successful I&A interaction.
Copy Job
Data input to the TOE via the scanner and destined for the printer.
Held Faxes
Data received via the fax interface and held until released by an authorized
administrator.
Held Jobs
Data received via the network interface that is destined for the printer and
held until released at the touch panel by the submitter.
Incoming Fax Job
Data received via the fax interface and destined for the printer.
Network Print Job
Data received via the network interface and destined for the printer. All
network print jobs are held until released.
Scanned Job to be
Emailed
Data input to the TOE via the scanner and destined for the SMTP server
specified by an authorized administrator.
Scanned Job to be Faxed
Data input to the TOE via the scanner and queued for transmission as a fax
via the phone line.
Table 10 - Security Attributes
Item Description
1.9.4 User Data
All the items described in the following table have both a D.DOC and D.FUNC component.
Table 11 - User Data
Item Description
1.10 Evaluated Configuration
The following configuration options apply to the evaluated configuration of the TOE:
1. The TOE includes the single Ethernet interface that is part of the standard configuration
of every MFP model. No optional network interfaces are installed.
2. No optional parallel or serial interfaces are installed. These are for legacy connections to
specific IT systems only.
3. All USB ports on the MFPs that perform document processing functions are disabled. In
the operational environments in which the Common Criteria evaluated configuration is of
interest, the users typically require that all USB ports are disabled. If PKI authentication
is used, the card reader is physically connected to a specific USB port during TOE
installation; in the evaluated configuration this USB port is limited in functionality to
acting as the interface to the card reader.
4. Operational management functions are performed via browser sessions to the embedded
web server or via the management menus available through the touch panel.
5. Disk encryption is enabled.
6. Access controls are configured for all TSF data so that only authorized administrators are
permitted to manage those parameters.

Lexmark Multi-Function Pr inters Security Target
21
7. All network communication is required to use IPSec with ESP to protect the
confidentiality and integrity of the information exchanged, including management
sessions that exchange D.CONF and D.PROT. Certificates presented by remote IT
systems are validated.
8. Support for AppleTalk is disabled since it does not provide confidentiality and integrity
protection.
9. I&A may use Internal Accounts and/or LDAP+GSSAPI on a per-user basis. The Backup
Password mechanism may be enabled at the discretion of the administrators. PKI
authentication is used for touch panel users. No other I&A mechanisms are included in
the evaluation because they provide significantly lower strength than the supported
mechanisms.
10. LDAP+GSSAPI and PKI authentication require integration with an external LDAP
server such as Active Directory. This communication uses default certificates; the LDAP
server must provide a valid certificate to the TOE. Binds to LDAP servers for
LDAP+GSSAPI use device credentials (not anonymous bind) so that the information
retrieved from Active Directory can be restricted to a specific MFP. Binds to LDAP
servers for PKI authentication use user credentials from the card (not anonymous bind) so
that the information retrieved from Active Directory can be restricted to a specific user.
11. Internal Accounts require User ID and password (rather than just User ID).
12. Audit event records are transmitted to a remote IT system as they are generated using the
syslog protocol.
13. Disk wiping functionality is configured for automatic mode with a multi-pass method.
This approach is the more secure form of disk wiping and is compliant with NIST SP80088 and the DSS "Clearing and Sanitization Matrix" (C&SM).
14. User data sent by the MFP in email messages is sent as an attachment (not as a web link).
15. No Java applications are loaded into the MFP by Administrators. These applications are
referred to as LES applications in end user documentation. The following LES
applications are installed by Lexmark before the TOE is shipped: “PKI Authentication”,
“PKI Held Jobs”, and “CAC Smartcard Authentication Token”.
16. No option card for downloadable emulators is installed in the TOE.
17. All fax jobs are stored on disk (rather than NAND) to ensure their contents are wiped
upon completion of each job. Incoming faxes are always held until released by an
authorized administrator.
18. Some form of credentials (device or user) is required to authenticate to the SMTP server.
19. Fax forwarding is disabled to limit the destinations for incoming faxes to the local printer
only.
20. NPAP, PJL and Postscript have the ability to modify system settings. The capabilities
specific to modifying system settings via these protocols are disabled.
21. All administrators must be authorized for all of the document processing functions (print,
copy, scan, fax).
Lexmark Multi-Function Pr inters Security Target
22
Printer
May Be Disabled Or
Restricted
May Be Disabled Or
Restricted
May Be Disabled Or
Restricted
Outgoing Fax
Disabled
May Be Disabled Or
Restricted
Disabled
Email (via the Network
Interface)
n/a
May Be Disabled Or
Restricted
Disabled
FTP (via the Network
Interface)
n/a
Disabled
Disabled
22. All network print jobs are held until released via the touch panel. Every network print
job must include a PJL SET USERNAME statement to identify the userid of the owner of
the print job. Held print jobs may only be released by an authenticated user with the
same userid as specified in the print job.
23. All incoming fax jobs are held until released via the touch panel. Held print jobs may
only be released by an authenticated user with the U.ADMINISTRATOR role.
24. Administrators are directed (through operational guidance) to specify passwords adhering
to the following composition rules for Internal Accounts and the Backup Password:
• A minimum of 8 characters
• At least one lower case letter, one upper case letter, and one non-alphabetic
character
• No dictionary words or permutations of the user name
25. All unnecessary network ports are disabled.
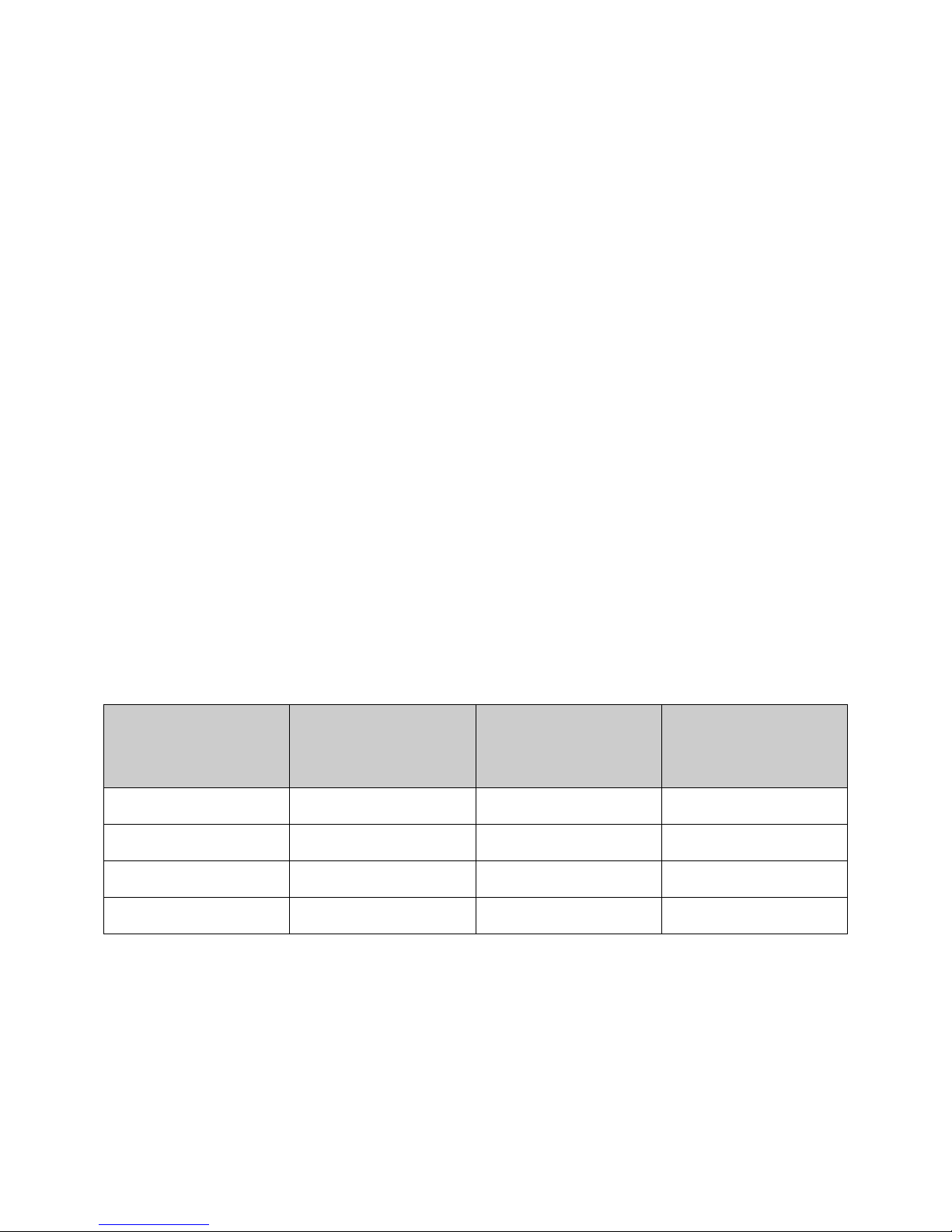
The following table defines the combinations of possible input sources and destinations that are
included in the evaluated configuration. In the table, the following meanings are used:
Destination
• “May Be Disabled Or Restricted” indicates that the functionality is included in
the evaluation but may be disabled or restricted to an authorized set of users at the
discretion of an administrator
• “Disabled” indicates the functionality exists within the TOE but is always
disabled by an administrator for the evaluated configuration
• “n/a” indicates the functionality does not exist in the TOE
Table 12 - Source-Destination Combinations
Source
Print Protocols (via
Scanner Incoming Fax
the Network
Interface)
1.11 Rationale for Non-Bypassability and Separation
The TOE is a stand-alone system that includes all hardware and software required for operation.
The TOE is not a general-purpose platform; rather it is a specialized platform with strictly
controlled functionality made available to the users. By limiting the functionality, the TSF is
protected from corruption or compromise. The TOE interfaces are separated into 2 categories –
security enforcing and security supporting. Security enforcing interfaces invoke the TSF and

Lexmark Multi-Function Pr inters Security Target
23
ensure that all enforcement functions complete successfully before allowing the user invoked
action to proceed. Security supporting interfaces ensure that the TSF cannot be interfered with
via those interfaces (i.e., they are isolated from the TSF). Multiple simultaneous users are
supported, and the TOE enforces separate domains for each process/user to ensure the
appropriate attributes and privileges are associated with each process/user.
 Loading...
Loading...