
IPES/IES-5408T Series
8 10/100TX + 4 1000T L2+ (w/8 PoE at/af) Industrial Managed
Switch w/ITU G.8032 Ring
User Manual
IP-67
IP-43
Apr. 2014

Recommendation for Shielded network cables
STP cables have additional shielding material that is used to reduce external interference. The
shield also reduces the emission at any point in the path of the cable. Our recommendation is
to deploy an STP network cable in demanding electrical environments. Examples of
demanding indoor environments are where the network cable is located in parallel with
electrical mains supply cables or where large inductive loads such as motors or contactors are
in close vicinity to the camera or its cable. It is also mandatory to use an STP cable where the
power device (like IP camera) is used outdoors or where the network cable is routed outdoors.

Important Notice
Lantech Communications Global, Inc. reserves the right to modify the
equipment, its specification or this manual without prior notice, in the interest
of improving performance, reliability, or servicing. At the time of publication
all data is correct for the operation of the equipment at the voltage and/or
temperature referred to. Performance data indicates typical values related to
the particular product.
No part of this documentation or information supplied may be divulged to any
third party without the express written consent of Lantech Communications
Global Inc. Products offered may contain software which is proprietary to
Lantech Communications Global Inc. The offer or supply of these products
and services does not include or infer any transfer of ownership.
Interference Issues
This Equipment has been tested and found to comply with the limits for a
Class A digital device, pursuant to Part 15 of the FCC rules. These limits are
designed to provide reasonable protection against harmful interference in a
commercial or industrial installation. This equipment generates, uses, and
can radiate radio frequency energy. It may cause harmful interference to
radio communications if the equipment is not installed and used in
accordance with the instructions.

FCC Warning
This Equipment has been tested and found to comply with the limits for a
Class-A digital device, pursuant to Part 15 of the FCC rules. These limits
are designed to provide reasonable protection against harmful interference
in a residential installation. This equipment generates, uses, and can
radiate radio frequency energy. It may cause harmful interference to radio
communications if the equipment is not installed and used in accordance
with the instructions. However, there is no guarantee that interference will
not occur in a particular installation. If this equipment does cause harmful
interference to radio or television reception, which can be determined by
turning the equipment off and on, the user is encouraged to try to correct
the interference by one or more of the following measures:
Reorient or relocate the receiving antenna.
Increase the separation between the equipment and receiver.
Connect the equipment into an outlet on a circuit different from that to
which the receiver is connected.
Consult the dealer or an experienced radio/TV technician for help.
CE Mark Warning
This is a Class-A product. In a domestic environment this product may
cause radio interference in which case the user may be required to take
adequate measures.

Content
Chapter 1 Introduction ............................................. 7
Specification ........................................................... 7
Chapter 2 Hardware Description ............................ 12
2.1 Physical Dimension ......................................12
2.2 Package Content: ........................................14
2.3 IP Protection ................................................15
2.4 LED Indicators .............................................18
Chapter 3 Hardware Installation ............................. 20
Chapter 4 Network Application ............................... 25
4.1 ITU G.8032 Scheme......................................25
4.2 Ring Coupling ...............................................25
4.3 Multiple Rings ...............................................26
4.4 Dual Homing .................................................27
4.5 Chain ............................................................27
Chapter 5 Console Management ........................... 29
5.1 Connecting to the Console Port....................29
5.2 Login in the Console Interface ......................29
Chapter 6 Web-Based Management ...................... 31
6.1 About Web-based Management ...................31
6.2 Preparing for Web Management ..................31
6.3 System Login ...............................................32
6.4 System .........................................................33
6.4.1 System Identification Configuration ...................... 33
6.4.2 System Information ............................................... 34

6.4.3 IP configuration ..................................................... 35
6.4.4 DHCP server ......................................................... 36
6.4.5 System Time ......................................................... 38
6.4.6 User Accounts – Access account management ... 41
6.4.7 SNMP Configuration ........................................... 42
6.4.8 Fault Relay Configuration ..................................... 43
6.4.9 Digital Input /Output .............................................. 44
6.4.10 Environmental Monitoring ................................... 46
6.5 Event & Log ................................................47
6.5.1 View Logs ............................................................. 47
6.5.2 Events ................................................................... 48
6.5.3 DDM event ............................................................ 49
6.5.4 Actions .................................................................. 50
6.5.5 Event Action Map ................................................. 53
6.6 Ports ................................................................55
6.6.1 Configuration ........................................................ 55
6.6.2 Status ................................................................. 56
6.6.3 Statistics ............................................................... 56
6.6.4 IEC Packet Statistics ............................................ 57
6.6.5 Mirroring ................................................................ 57
6.6.6 Rate Limiting ......................................................... 58
6.6.7 Loop Protection..................................................... 59
6.7 Power over Ethernet ......................................60
6.7.1 Configuration ........................................................ 60
6.7.2 Status .................................................................... 61
6.7.3 Detection ............................................................... 63
6.7.4 Scheduling ............................................................ 64
6.8 Topology ..........................................................65

6.9 QoS .................................................................68
6.9.1 QoS Policy ............................................................ 68
6.10 Security .........................................................70
6.10.1 MAC Address Tables .......................................... 70
6.10.2 Access Control List ............................................. 71
6.10.3 IEEE 802.1X Radius Server ............................... 72
6.10.4 IP Security .......................................................... 73
6.11 VLAN .............................................................74
6.11.1 802.1Q VLAN Config .......................................... 74
6.11.2 Status .................................................................. 76
6.12 MVR .............................................................. 76
6.12 LLDP .............................................................77
6.12.1 LLDP Configuration ............................................ 77
6.12.2 LLDP Neighbor ................................................... 78
6.12.3 LLDP Statistics ................................................... 80
6.13 CDP ...............................................................82
6.13.1 CDP Configuration Device Settings ................... 82
6.13.2 CDP Port Configuration ...................................... 83
6.13.3. CDP Status ........................................................ 83
6.14 IGMP Snooping .............................................85
6.14.1 IGMP Snooping Configuration ............................ 86
6.14.2 IGMP Snooping Status ....................................... 87
6.15 MSTP ............................................................89
6.15.1. MSTP Global Configuration ............................... 89
6.15.2 How to enable MSTP .......................................... 90
6.15.3 CIST Settings...................................................... 92
6.15.3.1 Bridge configuration .......................... 92

6.15.3.2 Port .................................................... 92
6.15.4. MSTP MSTI Settings ......................................... 93
6.15.5. MSTP Bridges Status ........................................ 94
6.15.6. Bridge status of all ports .................................... 95
6.16 Aggregation ................................................96
6.16.1. Aggregation Configuration ................................. 96
6.16.2 LACP Port Status ............................................... 97
6.17 PTP IEEE 1588 v2 ................................ .......98
6.18 G.8032 ERPS .............................................. 100
6.18.1. G.8032 Ethernet Ring Protection Configuration100
6.18.2 How to set ERPS G.8032 ................................. 103
6.19 Dual Homing .............................................. 106
6.20 Maintenance ................................................ 108
6.20.1 Save Configuration ........................................... 108
6.20.2 Config backup/restore ................................... 108
6.20.3 Restart device ................................................... 109
6.20.4 Firmware Upgrade ............................................ 110
6.20.5 Diagnostics ....................................................... 110
Appendix —SNMP OID ......................................... 113

7
Chapter 1 Introduction
Lantech IES-5408T & IPES-5408T (IP67/IP43) series is a high performance L2+
IP67/IP43 industrial Gigabit uplink switch with 8x10/100TX + 4 GigaT (w/8 PoE at/af
injectors-IPES model)by M12 connectors which provides L2 wire speed and advanced
security function for connecting PD network. It delivers ITU G.8032 ring recovery less
than 20ms, comprehensive QoS, , IGMPv1/v2/v3 & router port, QinQ*(double tag
VLAN) , MVR (multicast VLAN registration) , LACP link aggregation and advanced
security including ACL, TACAS+*, SSH/SSL, DHCP Option 82*which are important
features required in large network. It also supports Cisco Discovery Protocol (CDP) and
LLDP for Ciscoworks to detect the switch info to be shown on L2 map topology. The
user friendly UI, innovative auto topology drawing and topology demo makes IES-5408T
& IPES-5408T (IP67/IP43) series much easier to get hands-on. The complete CLI allows
professional engineer to configure by command line.
Specification
IES-5408T series
Hardware Specification
Standards
IEEE 802.3 10Base-T Ethernet
IEEE 802.3u 100Base-TX
IEEE 802.3ab 1000Base T
IEEE802.3x Flow Control and Back Pressure
IEEE802.3ad Port trunk with LACP
IEEE802.1d Spanning Tree
IEEE802.1w Rapid Spanning Tree
IEEE802.1s Multiple Spanning Tree
IEEE 802.3ad Link Aggregation Control Protocol (LACP)
IEEE 802.1AB Link Layer Discovery Protocol (LLDP)
IEEE 802.1X User Authentication (Radius)
IEEE802.1p Class of Service
IEEE802.1Q VLAN Tag
Switch Architecture
Back-plane (Switching Fabric): 9.6Gbps
Packet throughput ability (Full-Duplex): 23.8Mpps @64bytes
Transfer Rate
14,880pps for Ethernet port
148,800pps for Fast Ethernet port
1,488,000pps for Gigabit port
Mac Address
16K MAC address table
Jumbo frame
10KB for 10/100TX ports
Connector
10/100TX: 8 x M12 4-pole D-coded with auto MDI/MDI-X function
10/100/1000T: 4 x M12 8-pole A-coded with auto
MDI/MDI-X function
RS-232 connector: 1 x M12 5-pole A-coded
Power Input connector : 1 x M12 5-pole A-coded
Relay contact : 1 x M12 5-pole A-coded
Network Cable
10Base-T: 2-pair UTP/STP Cat. 3, 4, 5 cable
EIA/TIA-568 100-ohm (100m)
100Base-TX: 2-pair UTP/STP Cat. 5/ 5E cable
EIA/TIA-568 100-ohm (100m)
1000BaseT : 4-pair UTP/STP Cat. 5E/ 6 cable
EIA/TIA-568 100-ohm (100m)
8
Protocol
CSMA/CD
LED
Per unit: Power 1 (Green), Power 2 (Green), P-Fail (Red)
Ethernet port: Link/Activity (Green), Speed (Green); GigaT: Link/Activity (Green)
DI / DO
1 Digital Input (DI) :
Level 0: -30~2V / Level 1: 10~30V
Max. input current:8mA
1 Digital Output(DO): Open collector to 40 VDC, 200mA
Operating Humidity
5% ~ 95% (Non-condensing)
Operating Temperature
-40°C~75°C / -40°F~167°F
Storage Temperature
-40°C~85°C / -40°F~185°F
Redundant Power Supply
Standard model:
12~72VDC
-48VDC is available for single power input
Power Consumption
Max 10W
Case Dimension
IP67 model: Aluminum case
215mm(W)x201.4mm(H)x77.6mm(D)
IP43 model: Aluminum case
203mm(W)x188.4mm(H)x77.6mm(D)
Weight
1.3kgs(IP67). 1.1(IP43)
Installation
DIN Rail** and Wall Mount Design
EMI & EMS
FCC Class A,
CE EN61000-6-2, CE EN61000-6-4, CE EN61000-4-2, CE EN61000-4-3, CE EN61000-4-4, CE EN61000-4-5, CE EN61000-4-6,
CE N61000-4-8, EN61000-4-11
Stability Testing
IEC60068-2-32 (Free fall), IEC61373 (Shock),
IEC61373 (Vibration)
MTBF
n/a
Warranty
5 years
Software Specification
Management
SNMP v1 v2c, v3/ Web/Telnet/CLI
SNMP MIB
RFC 1215 Traps MIB,
RFC 1213 MIBII
RFC 1158 MIBII
RFC 1157 SNMP MIB,
RFC 1493 Bridge MIB,
RFC 1573 IF MIB
RFC 2674 VLAN MIB,
RFC 1643 EtherLike,
RFC 1757 RMON,
RFC 2674 Q-Bridge MIB
RFC 2790 Host Resource MIB
RSTP MIB*
LLDP MIB*
Private MIB
ITU G.8032
Support ITU G.8032 v2 for Ring protection in less than 20ms for self-heal recovery < 256 switches
Support various ring/chain topologies
Ring covers data & multicast* packets
Co-exist with RSTP on different ports
User friendly UI
Auto topology drawing
Topology demo
Auto configuration for G.8032 single ring
Port Trunk with LACP
LACP Port Trunk: 4 Trunk groups/Maximum 4 trunk members
Link aggregation to increase bandwidth
LLDP
Supports LLDP to allow switch to advise its identification and capability on the LAN
CDP
Cisco Discovery Protocol for topology mapping
VLAN
Port Based VLAN
IEEE 802.1Q Tag VLAN (256 entries)/ VLAN ID (Up to 4K, VLAN ID can be assigned from 1 to 4096.)
GVRP (256 Groups)*,GMRP*, QinQ*
IPv6/IPv4
Present
Spanning Tree
Supports IEEE802.1d Spanning Tree and IEEE802.1w Rapid Spanning Tree, IEEE802.1s Multiple Spanning Tree
Quality of Service
The quality of service determined by port, Tag and IPv4 Type of service, IPv4 Different Service
Class of Service
Support IEEE802.1p class of service, per port provides 8 priority queues
IP Security
Supports 10 IP addresses that have permission to access the switch management and to prevent unauthorized intruder.
Login Security
Supports IEEE802.1X Authentication/RADIUS
Port Mirror
Support 3 mirroring types: “RX, TX and Both packet”
Network Security
Support 10 IP addresses that have permission to access the switch management and to prevent unauthorized intruder.
802.1X access control for port based and MAC based authentication/MAC-IP-Port binding
Management access control with priority
256 Policy based Access Control List
SSL/ SSH for Management
TACACS+ for Authentication*
IGMP
Support IGMP snooping v1,v2,v3; Supports IGMP static route; 256 multicast groups; IGMP router port ; IGMP query
Multicast VLAN Registration
MVR enables multicast packets go through VLAN for VOD application
Bandwidth Control
Support ingress packet filter and egress packet limit.
The egress rate control supports all of packet type.

9
Ingress filter packet type combination rules are Broadcast/Multicast/Flooded Unicast packet, Broadcast/Multicast packet, Broadcast
packet only and all types of packet.
The packet filter rate can be set an accurate value through the pull-down menu for the ingress packet filter and the egress packet
limit.
PTP v2 & RTC
Support hardware-based IEEE1588 PTPv2 in 1μs with 4 x GigaT ports
Built-in RTC(Real Time Clock) to keep track of time
Flow Control
Supports Flow Control for Full-duplex and Back Pressure for Half-duplex
Environmental Monitoring
System status for input voltage, current and ambient temperature to be shown in GUI and sent alerting if any abnormal status
System Log
Supports System log record and remote system log server
SMTP/Text SMS
Supports SMTP Server and 6 e-mail accounts for receiving event alert; can send SMS text alert via mobile
Relay Alarm
Provides one relay output for port breakdown, power fail and alarm.
Alarm Relay current carry ability: 1A @ DC24V
Protection
Miss-wiring avoidance
Repowered auto ring restore(Node failure protection)
Loop protection
SNMP Trap
Up to 3 trap stations; trap types including:
Device cold start
Authorization failure
Port link up/link down
Abnormal environmental monitoring
DHCP
Provide DHCP Client/ DHCP Server/ relay Option 82*
DNS
Provide DNS client feature and support Primary and Secondary DNS server.
SNTP
Supports SNTP to synchronize system clock in Internet
Firmware Update
Supports TFTP firmware update, TFTP backup / InstaConfig** firmware upgrade / backup for multiple switches
Configuration
upload and download
Supports text configuration file for system quick installation
IfAlias
Each port allows an alphabetic string of 128-byte assigned as its own unique name via the SNMP or CLI interface
*Future release
**Optional
IPES-5408T-8 series
Hardware Specification
Standards
IEEE 802.3 10Base-T Ethernet
IEEE 802.3u 100Base-TX
IEEE 802.3ab 1000Base T
IEEE802.3x Flow Control and Back Pressure
IEEE802.3ad Port trunk with LACP
IEEE802.1d Spanning Tree
IEEE802.1w Rapid Spanning Tree
IEEE802.1s Multiple Spanning Tree
IEEE 802.3ad Link Aggregation Control Protocol (LACP)
IEEE 802.1AB Link Layer Discovery Protocol (LLDP)
IEEE 802.1X User Authentication (Radius)
IEEE802.1p Class of Service
IEEE802.1Q VLAN Tag
IEEE802.3at/af Power over Ethernet
Switch Architecture
Back-plane (Switching Fabric): 9.6Gbps
Packet throughput ability (Full-Duplex): 23.8Mpps @64bytes
Transfer Rate
14,880pps for Ethernet port
148,800pps for Fast Ethernet port
1,488,000pps for Gigabit Fiber Ethernet port
Mac Address
16K MAC address table
Jumbo frame
10KB for 10/100TX ports
Connector
10/100TX: 8 x M12 4-pole D-coded with auto MDI/MDI-X function
10/100/1000T: 4 x M12 8-pole A-coded with auto
MDI/MDI-X function
RS-232 connector: 1 x M12 5-pole A-coded
Power Input connector : 1 x M23 5-pole A-coded
Relay contact : 1 x M12 5-pole A-coded
Network Cable
10Base-T: 2-pair UTP/STP Cat. 3, 4, 5 cable
EIA/TIA-568 100-ohm (100m)
100Base-TX: 2-pair UTP/STP Cat. 5/ 5E cable
EIA/TIA-568 100-ohm (100m)
1000BaseT : 4-pair UTP/STP Cat 5E/ 6 cable
EIA/TIA-568 100-ohm (100m)
Protocol
CSMA/CD
PoE pin assignment
RJ-45 port # 1~#8 support IEEE 802.3at End-point, Alternative A mode. Per port provides 30W (802.3at) at 53~56VDC ; 15W
(802.3af) at 48V~56VDC.
Positive (VCC+): RJ-45 pin 1,2.
Negative (VCC-): RJ-45 pin 3,6.
LED
Per unit: Power 1 (Green), Power 2 (Green), P-Fail (Red)
Ethernet port: Link/Activity (Green), Speed (Green); GigaT: Link/Activity (Green)

10
DI / DO
1 Digital Input (DI) :
Level 0: -30~2V / Level 1: 10~30V
Max. input current:8mA
1 Digital Output(DO): Open collector to 40 VDC, 200mA
Operating Humidity
5% ~ 95% (Non-condensing)
Operating Temperature
-40°C~75°C / -40°F~167°F
Storage Temperature
-40°C~85°C / -40°F~185°F
Redundant Power Supply
12~56VDC for Ethernet Data
48~56VDC for PoE feeding
12~56VDC for PoE feeding on 12V model
-48VDC is available for single power input
72VDC for Data (10W); PoE (100W)
Power Consumption
10W
PoE Power Budget
240W for 802.3at 54V input
120W for 802.3af 48V input
90W for 12V input
120W for 24V input
100W for 72V Input
Case Dimension
IP67 model: Aluminum case
285mm(W)x201.4mm(H)x84.4mm(D)
IP43 model: Aluminum case
273mm(W)x188.4mm(H)x84.4mm(D)
Weight
1.3kgs(IP67), 1.1kgs(IP43)
Installation
DIN Rail** and Wall Mount Design
EMI & EMS
FCC Class A,
CE EN61000-6-2, CE EN61000-6-4, CE EN61000-4-2, CE EN61000-4-3, CE EN61000-4-4, CE EN61000-4-5, CE EN61000-4-6,
CE N61000-4-8, EN61000-4-11
Stability Testing
IEC60068-2-32 (Free fall), IEC61373 (Shock),
IEC61373 (Vibration)
Certifications
NFF*, E-mark*, EN50155
Warranty
5 years
Software Specification
Management
SNMP v1 v2c, v3/ Web/Telnet/CLI
SNMP MIB
RFC 1215 Traps MIB,
RFC 1213 MIBII
RFC 1158 MIBII
RFC 1157 SNMP MIB,
RFC 1493 Bridge MIB,
RFC 1573 IF MIB
RFC 2674 VLAN MIB,
RFC 1643 EtherLike,
RFC 1757 RMON,
RFC 2674 Q-Bridge MIB
RFC 2790 Host Resource MIB
RSTP MIB*
LLDP MIB*
Private MIB
ITU G.8032
Support ITU G.8032 v2 for Ring protection in less than 20ms for self-heal recovery < 256 switches
Support various ring/chain topologies
Ring covers data & multicast* packets and can co-exist with RSTP
User friendly UI
Auto topology drawing
Topology demo
Auto configuration for G.8032 (Auto mode) single ring
Port Trunk with LACP
LACP Port Trunk: 4 Trunk groups/Maximum 4 trunk members
Link aggregation to increase bandwidth
LLDP
Supports LLDP to allow switch to advise its identification and capability on the LAN
CDP
Cisco Discovery Protocol for topology mapping
PoE Management/ per Port PoE
status
PoE Detection to check if PD is hang up then restart the PD
PoE Scheduling to On/OFF PD upon routine time table
Per port PoE status incl. voltage, current, watts
VLAN
Port Based VLAN
IEEE 802.1Q Tag VLAN (256 entries)/ VLAN ID (Up to 4K, VLAN ID can be assigned from 1 to 4096.)
GVRP (256 Groups)*,GMRP*, QinQ*
IPv6/IPv4
Present
Spanning Tree
Supports IEEE802.1d Spanning Tree and IEEE802.1w Rapid Spanning Tree, IEEE802.1s Multiple Spanning Tree
Quality of Service
The quality of service determined by port, Tag and IPv4 Type of service, IPv4 Different Service
Class of Service
Support IEEE802.1p class of service, per port provides 8 priority queues
IP Security
Supports 10 IP addresses that have permission to access the switch management and to prevent unauthorized intruder.
Login Security
Supports IEEE802.1X Authentication/RADIUS
Port Mirror
Support 3 mirroring types: “RX, TX and Both packet”
Network Security
Support 10 IP addresses that have permission to access the switch management and to prevent unauthorized intruder.
802.1X access control for port based and MAC based authentication/MAC-IP-Port binding
Management access control with priority
256 Policy based Access Control List
SSL/ SSH for Management

11
TACACS+ for Authentication*
IGMP
Support IGMP snooping v1,v2,v3; Supports IGMP static route; 256 multicast groups; IGMP router port ; IGMP query
Multicast VLAN Registration
MVR enables multicast packets go through VLAN for VOD application
Bandwidth Control
Support ingress packet filter and egress packet limit.
The egress rate control supports all of packet type.
Ingress filter packet type combination rules are Broadcast/Multicast/Flooded Unicast packet, Broadcast/Multicast packet, Broadcast
packet only and all types of packet.
The packet filter rate can be set an accurate value through the pull-down menu for the ingress packet filter and the egress packet
limit.
PTP v2 & RTC
Support hardware-based IEEE1588 PTPv2 in 1μs with 4 x GigaT ports
Built-in RTC(Real Time Clock) to keep track of time
Flow Control
Supports Flow Control for Full-duplex and Back Pressure for Half-duplex
Environmental Monitoring
System status for input voltage, current and ambient temperature to be shown in GUI and sent alerting if any abnormal status
System Log
Supports System log record and remote system log server
SMTP/Text SMS
Supports SMTP Server and 6 e-mail accounts for receiving event alert; can send SMS text alert via mobile
Relay Alarm
Provides one relay output for port breakdown, power fail and alarm.
Alarm Relay current carry ability: 1A @ DC24V
Protection
Miss-wiring avoidance
Repowered auto ring restore (node failure protection)
Loop protection
SNMP Trap
Up to 3 trap stations; trap types including:
Device cold start
Authorization failure
Port link up/link down
PoE port event
Abnormal environmental monitoring
DHCP
Provide DHCP Client/ DHCP Server/ relay Option 82*
DNS
Provide DNS client feature and support Primary and Secondary DNS server.
SNTP
Supports SNTP to synchronize system clock in Internet
Firmware Upgrade
Firmware upgrade via TFTP or Lantech InstaConfig**
Configuration
upload and download
Supports text configuration file for system quick installation
IfAlias
Each port allows an alphabetic string of 128-byte assigned as its own unique name via the SNMP or CLI interface
*Future release
**Optional
12
Chapter 2 Hardware Description
In this paragraph, it will describe the Industrial switch’s hardware spec, port, cabling
information, and wiring installation.
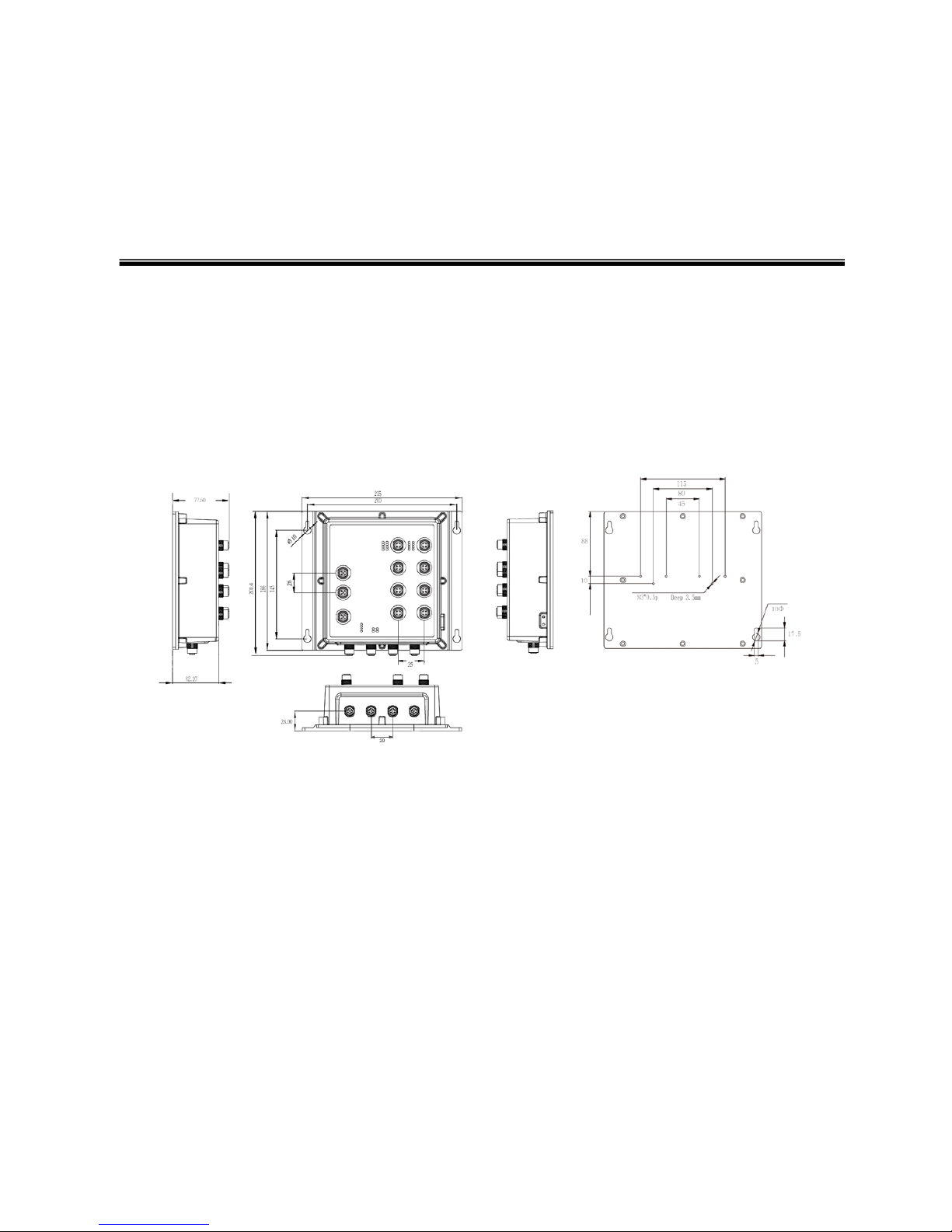
2.1 Physical Dimension
Aluminum case. IP-67,
285 (W) x 201.4 (D) x 84.4 (H) mm
13
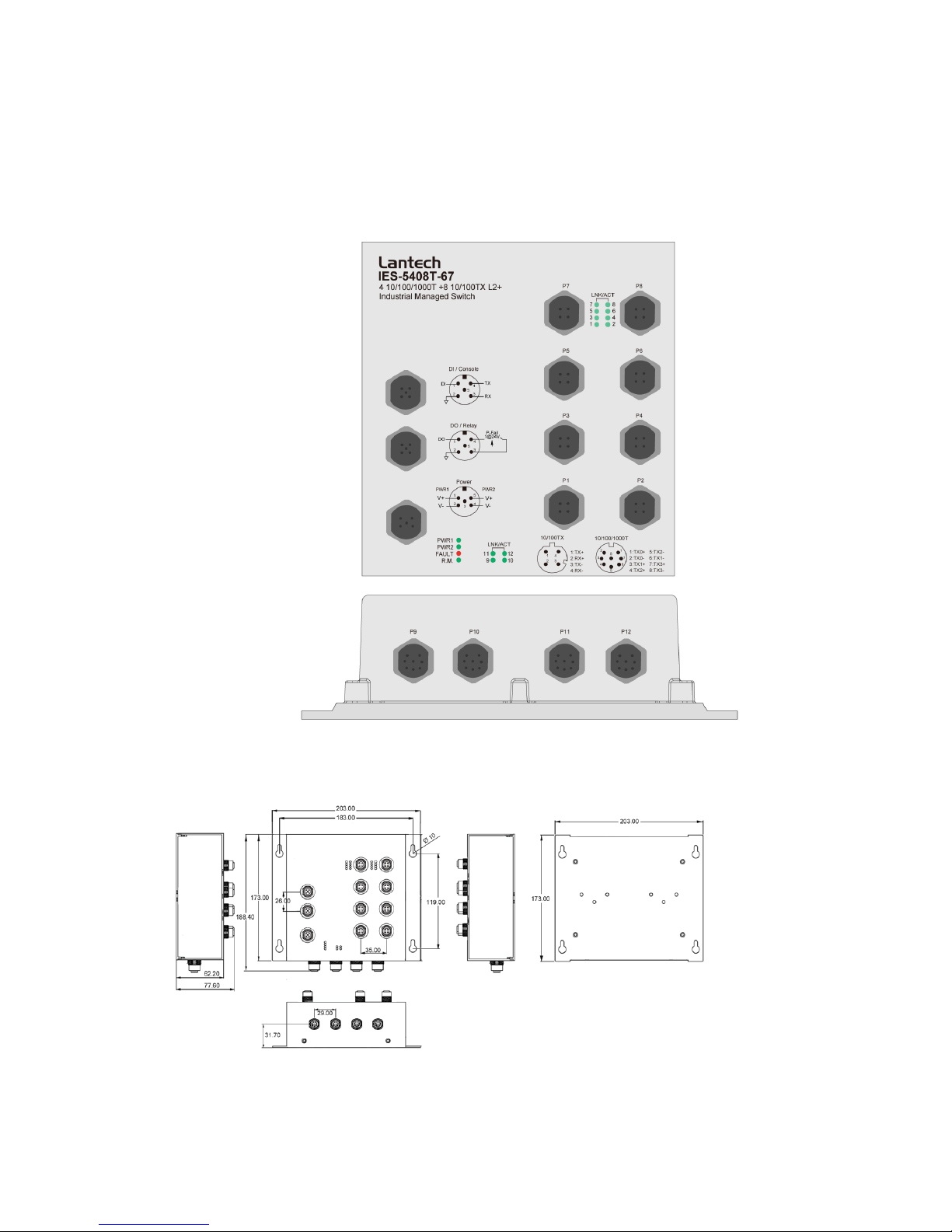
Port description of IP-67 series switch
Aluminum case. IP-43,
273 (W) x 188.4(D) x 84.4 (H) mm
**The port description of IP-43 model is the same as of IP-67 one.

14
2.2 Package Content:
Manual CD Product Console cable
15
2.3 IP Protection
The IP Code, Ingress Protection Rating, sometimes also interpreted as International
Protection Rating, classifies and rates the degree of protection provided against the
intrusion (including body parts such as hands and fingers), dust, accidental contact, and
water in mechanical casings and with electrical enclosures. It is published by the
International Electrotechnical Commission (IEC)
Solid particle protection
The first digit indicates the level of protection that the enclosure provides against access
to hazardous parts (e.g., electrical conductors, moving parts) and the ingress of solid
foreign objects.
Level
Object size
protected against
Effective against
0
—
No protection against contact and ingress of objects
1
>50 mm
Any large surface of the body, such as the back of a
hand, but no protection against deliberate contact
with a body part
2
>12.5 mm
Fingers or similar objects
3
>2.5 mm
Tools, thick wires, etc.
4
>1 mm
Most wires, screws, etc.
5
Dust protected
Ingress of dust is not entirely prevented, but it must
not enter in sufficient quantity to interfere with the
satisfactory operation of the equipment; complete
protection against contact
6
Dust tight
No ingress of dust; complete protection against
contact
16
Liquid ingress protection
The second digit indicates the level of protection that the enclosure provides against
harmful ingress of water.
Level
Protected
against
Testing for
Details
0
Not
protected
—
—
1
Dripping
water
Dripping water (vertically
falling drops) shall have no
harmful effect.
Test duration: 10 minutes
Water equivalent to 1 mm
rainfall per minute
2
Dripping
water when
tilted up to
15°
Vertically dripping water
shall have no harmful effect
when the enclosure is tilted
at an angle up to 15° from
its normal position.
Test duration: 10 minutes
Water equivalent to 3 mm
rainfall per minute
3
Spraying
water
Water falling as a spray at
any angle up to 60° from
the vertical shall have no
harmful effect.
Test duration: 5 minutes
Water volume: 0.7 litres per
minute
Pressure: 80–100 kPa
4
Splashing
of water
Water splashing against
the enclosure from any
direction shall have no
harmful effect.
Test duration: 5 minutes
Water volume: 10 litres per
minute
Pressure: 80–100 kPa
5
Water jets
Water projected by a
nozzle (6.3 mm) against
enclosure from any
direction shall have no
harmful effects.
Test duration: at least
15 minutes
Water volume: 12.5 litres per
minute
Pressure: 30 kPa at distance
of 3 m

17
6
Powerful
water jets
Water projected in powerful
jets (12.5 mm nozzle)
against the enclosure from
any direction shall have no
harmful effects.
Test duration: at least
3 minutes
Water volume: 100 litres per
minute
Pressure: 100 kPa at
distance of 3 m
7
Immersion
up to 1 m
Ingress of water in harmful
quantity shall not be
possible when the
enclosure is immersed in
water under defined
conditions of pressure and
time (up to 1 m of
submersion).
Test duration: 30 minutes
Immersion at depth of at
least 1 m measured at
bottom of device, and at least
15 cm measured at top of
device
8
Immersion
beyond 1 m
The equipment is suitable
for continuous immersion in
water under conditions
which shall be specified by
the manufacturer.
Normally, this will mean
that the equipment is
hermetically sealed.
However, with certain types
of equipment, it can mean
that water can enter but
only in such a manner that
it produces no harmful
effects.
Test duration: continuous
immersion in water
Depth specified by
manufacturer
9
Powerful
high
temperature
water jets
Protected against closerange high pressure, high
temperature spray downs.
—
18
2.4 LED Indicators
The diagnostic LEDs that provide real-time information of system and optional status are
located on the front panel of the industrial switch. The following table provides the
description of the LED status and their meanings for the switch.
LED
Color
Status
Meaning
R.M
Green
On
The switch unit is owner switch of ITU-Ring
Off
The switch is not owner switch
PWR1
Green
On
Power 1 is active
Off
Power 1 is inactive
PWR2
Green
On
Power 2 is active
Off
Power 2 is inactive
FAULT
Red
On
Power or port failure
Off
No failure
P1 ~ P16
Link/Ack
On
A network device is detected.
Blinking
The port is transmitting or receiving packets
from the TX device.
Off
No device attached
PoE(1~8)(IP
ES)
On
The port is operating in PoE mode.(IPES)
Off
The port is not operating in PoE
mode.(IPES)
P17 ~ P20
Link/Ack
On
A network device is detected.
Blinking
The port is transmitting or receiving packets
from the TX device.
19
Off
No device attached.

20
Chapter 3 Hardware Installation
3.1Hardware installation
3.1.1Unpack switch and check the accessory with packing content list
3.1.2 Mount the switch on desired position. For the best ventilation, it is
suggested to mount the switch on metallic surface.
3.1.3 Connect the M23/M12 connector of power input. The PoE power
supply for IPES-5408T series is connected via a 5-pole M23 female
connector while IES-5408T is with a 5-pole M12 female connector.
Voltage of Power Input
For IPES-5408T series, the voltage of power input should use
48VDC to feed power IEEE 802.3af standardized devices or
54VDC for IEEE 802.3at standardized ones.
For IPES-5408T-12V series, the power input voltage can be from
9.2V to 56VDC to feed power on both the 802.3af and 802.3at
standardized devices.
With IPES-5408T-72V series, the power input voltage can be from
72V to feed power on both 802.3af/at standardized devices. IES5408T series can accept power input ranging from
9.2V~72V(12V~72V) to be powered.
Please make sure that the external power supply unit you use to
provide the PoE voltage meet the following criteria:
The output voltage of power supply must exceed 48VDC for 802.3af
and 53VDC for 802.3at operation(with IPES-5408T-72V, only 72VDC
can power both the 802.3af and 802.3at PD.)
The power consumption can satisfy the total power request from all
PD devices required.
21
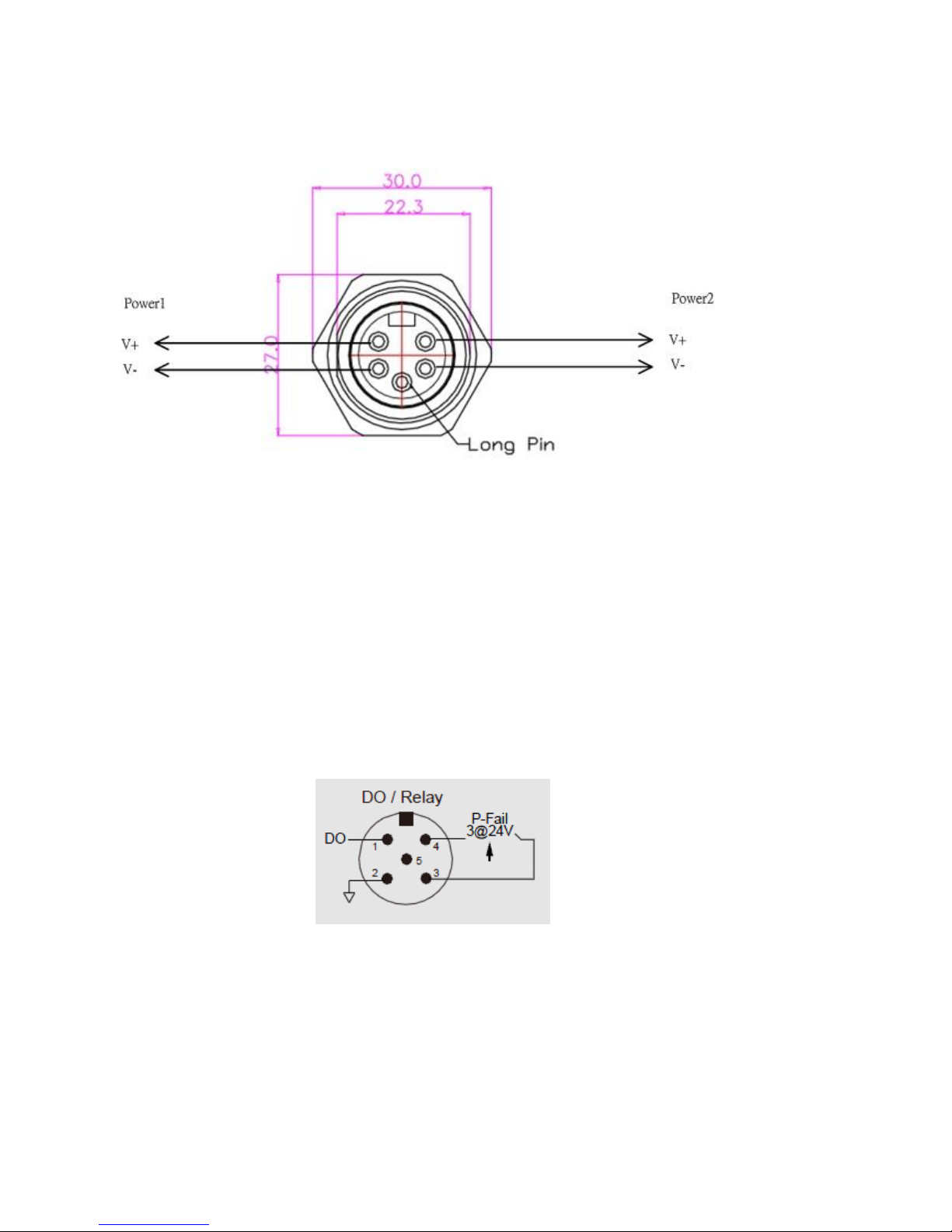
Pin assignment of Power input
Redundant Power Input
The power input can be supported redundantly. The supply voltage is
electrically isolated from the housing.
Note: With single power supply of the mains voltage, the device will
report a power failure. You can disable this power fail event via web
browser.
Pin assignment of alarm relay
A break in contact is reported via the relay contact :
The failure of at least one of the two supply voltages.
The break link status of at least one switch port.

22
3.1.4 Fitting the device, grounding
Install the system in a dry and clean area to protect the switch to
get exposed with dirt.
Plug the connector to the power supply plug then turn on the power
supply.
Ground
The chassis is grounded via a separate ground nut (M3).
Use toothed locking washers for a good electrical connection.
Ground screw of IPES-5408T switch
3.1.5 Connect the M12 connector with RJ-45 data cable, ports are not
used shall be caped that comes with the package to insulate the
surrounding.
23
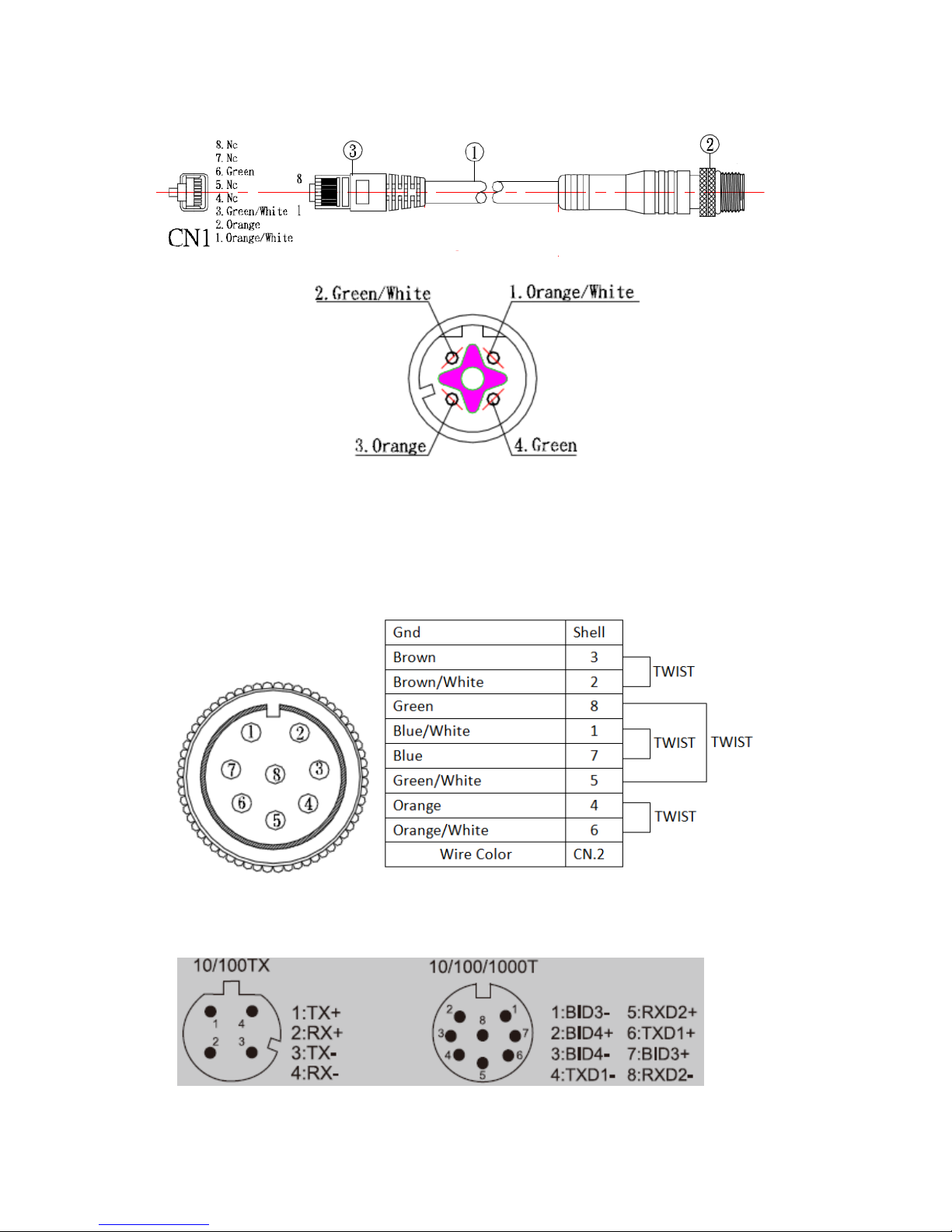
Pin assignment of M12 10/100Tx network connector
Pin assignment of M12 10/100/100T network connector

24
3.1.6 Check the status of LED, make sure the switch was in working
status.
Note:
The protection class IP67/IP43 is only achieved when bolted together.
The other components attaching to the system have to meet with the
IP67/IP43 protection class in order to reach the whole system IP 67/IP43
protection.
Empty ports must be sealed with the protective caps supplied.
25
Chapter 4 Network Application
4.1 ITU G.8032 Scheme
LANTECH G.8032 protocol is following ITU (International Telecommunication Unit)
G.8032 v2 draft. The benefits of G.8032 are:
1. <50ms recovery time when failover
2. G.8032 has defined the protocol scheme, parameters, functions, test measures to be
unified that the users can evaluate the possible network infrastructure without literally
testing each brand in large scale.
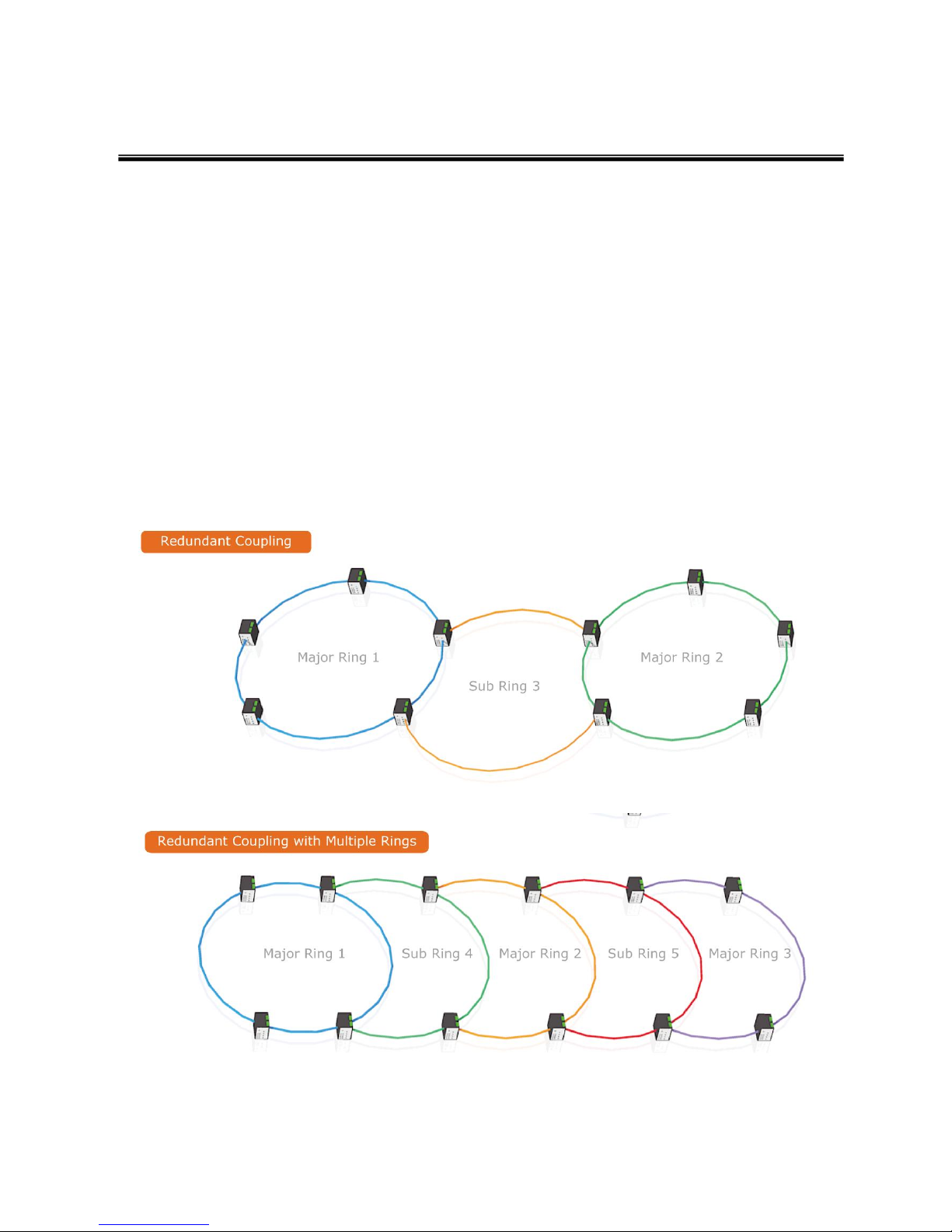
4.2 Ring Coupling
26
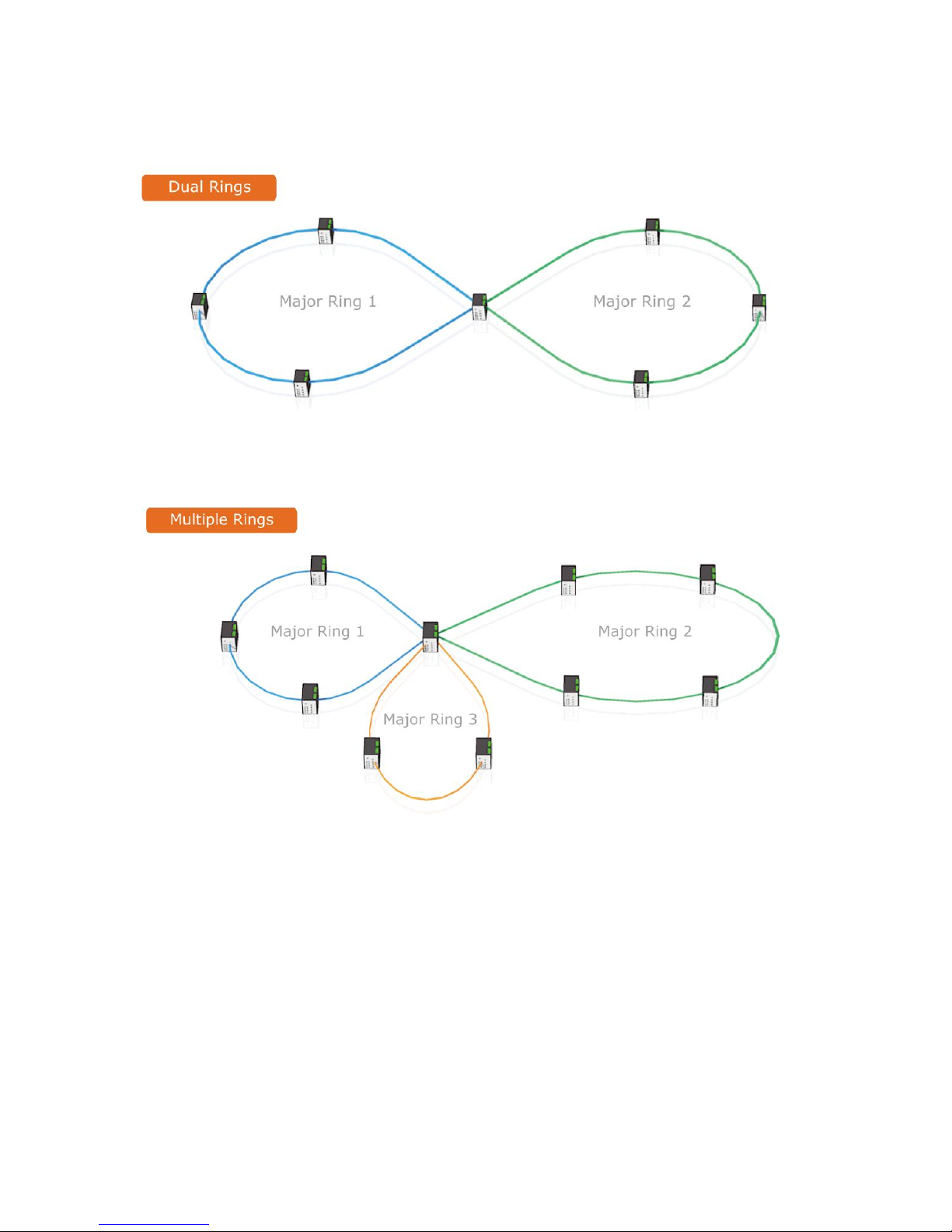
4.3 Multiple Rings
27
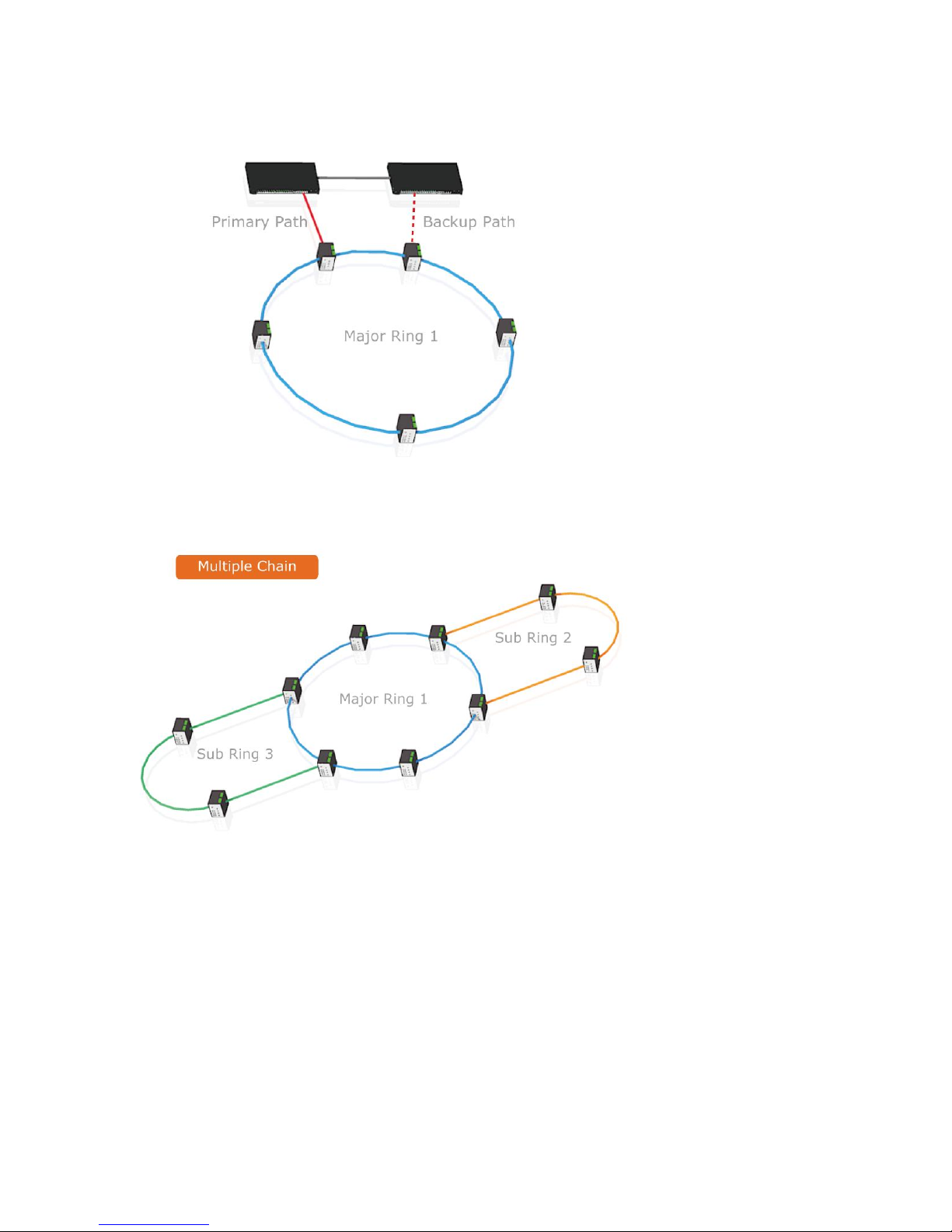
4.4 Dual Homing
4.5 Chain
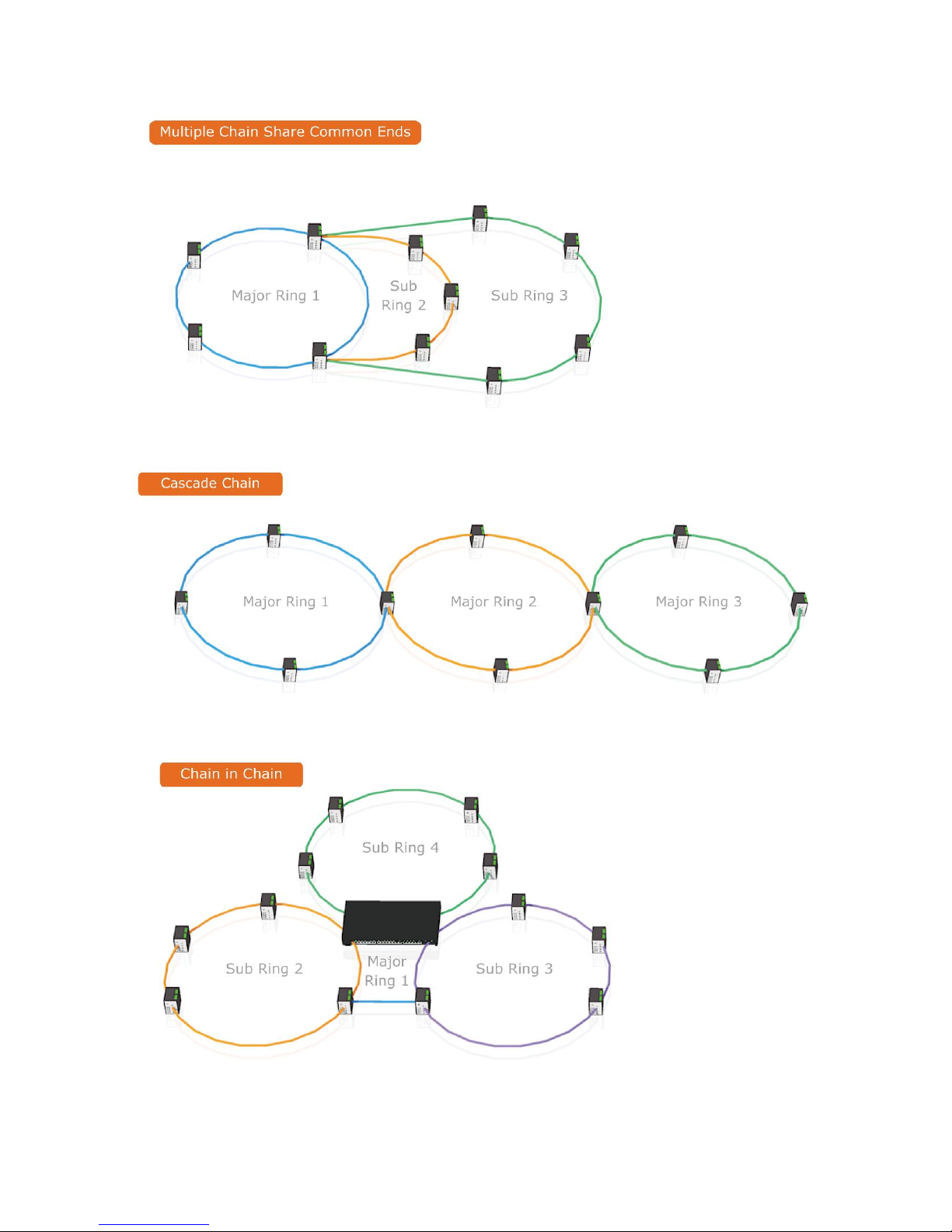
28

29
Chapter 5 Console Management
5.1 Connecting to the Console Port
The supplied cable which one end is M12 5-pole connector and the other end is RS-232
connector. Attach the end of RS-232 connector to PC or terminal and the other end of
M12 connector to the console port of the switch. The connected terminal or PC must
support the terminal emulation program.
5.2 Login in the Console Interface
When the connection between Switch and PC is ready, turn on the PC and run a
terminal emulation program or Hyper Terminal and configure its communication
parameters to match the following default characteristics of the console port:
Baud Rate:115200 bps
Data Bits: 8
Parity: none
Stop Bit: 1
Flow control: None

30
The settings of communication parameters
Having finished the parameter settings, click ‘OK’. When the blank screen shows up,
press Enter key to have the login prompt appears. Key in ‘admin’ (default value) for both
User name and Password (use Enter key to switch), then press Enter and the Main
Menu of console management appears. Please see below figure for login screen.
Console login interface

31
Chapter 6 Web-Based Management
This section introduces the configuration and functions of the Web-Based
management.
6.1 About Web-based Management
There is an embedded HTML web site residing in flash memory on CPU board of the
switch, which offers advanced management features and allows users to manage the
switch from anywhere on the network through a standard browser such as Microsoft
Internet Explorer.
The Web-Based Management supports Internet Explorer 6.0 or later version. And, it
is applied for Java Applets for reducing network bandwidth consumption, enhance
access speed and present an easy viewing screen.
6.2 Preparing for Web Management
Before using the web management, install the industrial switch on the network and
make sure that any one of the PCs on the network can connect with the industrial
switch through the web browser. The industrial switch default value of IP, subnet
mask, username and password are listed as below:
IP Address: 192.168.16.1
Subnet Mask: 255.255.255.0
Default Gateway: 192.168.16.254
User Name: admin
Password: admin

32
6.3 System Login
1. Launch the Internet Exploreron the PC(the switch also support Mozila and
Chrome browser).
2. Key in “http:// “+” the IP address of the switch”, and then Press “Enter”.
3. The login screen will appear right after
4. Key in the user name and password. The default user name and password are
the same as ‘admin’.
5. Press Enter or click the OK button, and then the home screen of the Web-based
management appears.
6. The switch also support SSL security login, if you need SSL to protect your
access account of switch, please key in “https//” + “ the IP address of switch “,
and press “Enter”
Login screen

33
6.4 System
6.4.1
System Identification Configuration
Name:
An administratively assigned name for this managed switch. By convention, this is
the node's fully-qualified domain name. A domain name is a text string drawn from
the alphabet (A-Z), digits (0-9), minus sign (-). No space characters are permitted as
part of a name. The first or last character must not be a minus sign. The allowed
string length is 0 to 255.
Description:
Display the description of switch. The allowed string length is 0 to 255.
Location:
The physical location of this node(e.g., telephone closet, 3rd floor). The allowed
string length is 0 to 255, and the allowed content is the ASCII characters from 32 to
126.
Contact:
The textual identification of the contact person for this managed node, together with
information on how to contact this person. The allowed string length is 0 to 255, and
the allowed content is the ASCII characters from 32 to 126.
.

34
6.4.2 System Information
User can find the system name, description, location and contact personnel to
identify the switch. The version table below is a read-only field to show the basic
information of the switch.

35
6.4.3 IP configuration
The switch is a network device which needs to be assigned an IP address for being
identified on the network. Users can select a methodof assigning IP address to the
switch.
DHCP Client: Enable or disable the DHCP client function. When DHCP client
function is enabled, the switch will obtain an IP address from the network DHCP
server automatically. The default IP address will be replaced by the assigned IP
address from the DHCP server. After the user clicks Apply, a popup dialog
shows up to inform the user that when the DHCP client is enabled, the current IP
will lose and user should find the new IP obtained from the DHCP server.
IP Address: Assign a static IP address to the switch from the subnet address
range that the network is using. If DHCP client function is enabled, this switch is
configured as a DHCP client. The network DHCP server will assign the IP
address to the switch and the switch displays it in this column. The default IP is
192.168.1.88 or the user can choose an IP address manually when DHCP Client
is disabled.
Subnet Mask: Assign the subnet mask of the IP address. If DHCP client
function is disabled, the user has to assign the subnet mask in this column field.
Gateway: Assign the network gateway for the switch. If DHCP client function is
disabled, the user has to assign the gateway in this column field. The default
gateway is 192.168.1.254.
DNS Server IP: Assign the primary DNS IP address.
And then, click
Apply
.

36
6.4.4 DHCP server
DHCP is the abbreviation of Dynamic Host Configuration Protocol that is a protocol
for assigning dynamic IP addresses to devices on a network. With dynamic
addressing, a device can have a different IP address every time it connects to the
network. In some systems, the device's IP address can even change while it is still
connected. DHCP also supports a mix of static and dynamic IP addresses. Dynamic
addressing simplifies network administration because the software keeps track of IP
addresses rather than requiring an administrator to manage the task. This means that
a new computer can be added to a network without the hassle of manually assigning
it a unique IP address.
The system provides the DHCP server function. Having enabled the DHCP server
function, the switch system will be configured as a DHCP server.
DHCP Server: Enable or Disable the DHCP Server function. Enable—the switch
will be the DHCP server on your local network.
IP Range(up): Type in an IP address. Low IP address is the beginning of the
dynamic IP range. For example, dynamic IP is in the range between
192.168.1.100 ~ 192.168.1.200. In contrast, 192.168.1.100 is the Low IP

37
address.
IP Range(down): Type in an IP address. High IP address is the end of the
dynamic IP range. For example, dynamic IP is in the range between
192.168.1.100 ~ 192.168.1.200. In contrast, 192.168.1.200 is the High IP
address.
Subnet Mask: Type in the subnet mask of the IP configuration.
Gateway: Type in the IP address of the gateway in your network.
DNS: Type in the Domain Name Server IP Address in your network.
Lease Time: It is the time period that system will reset the dynamic IP
assignment to ensure the dynamic IP will not been occupied for a long time or
the server doesn’t know that the dynamic IP is idle.
And then, click
Apply
.

38
6.4.4.1 DHCP status
You can check the status of used DHCP IP in here.
6.4.5 System Time
SNTP (Simple Network Time Protocol) is a simplified version of NTP which is an
Internet protocol used to synchronize the clocks of computers to a specified time
reference. Because time usually just advances, the time on different node stations
will be different. With the communicating programs running on those devices, it would
cause time to jump forward and back, a non-desirable effect. Therefore, the switch
provides comprehensive mechanisms to access national time and frequency
dissemination services, organize the time-synchronization subnet and the local clock
in each participating subnet peer.
Daylight saving time (DST) is the convention of advancing clocks so that afternoons
have more daylight and mornings have less. Typically clocks are adjusted forward
one hour near the start of spring and are adjusted backward in autumn.
Time zone: Universal Time Coordinated. Set the switch location time zone. The
following table lists the different location time zone for your reference.
Local Time Zone
Conversion from UTC
Time at 12:00 UTC
November Time Zone
- 1 hour
11am

39
Oscar Time Zone
-2 hours
10 am
ADT - Atlantic Daylight
-3 hours
9 am
AST - Atlantic Standard
EDT - Eastern Daylight
-4 hours
8 am
EST - Eastern Standard
CDT - Central Daylight
-5 hours
7 am
CST - Central Standard
MDT - Mountain Daylight
-6 hours
6 am
MST - Mountain
Standard
PDT - Pacific Daylight
-7 hours
5 am
PST - Pacific Standard
ADT - Alaskan Daylight
-8 hours
4 am
ALA - Alaskan Standard
-9 hours
3 am
HAW - Hawaiian
Standard
-10 hours
2 am
Nome, Alaska
-11 hours
1 am
CET - Central European
FWT - French Winter
MET - Middle European
MEWT - Middle
European Winter
SWT - Swedish Winter
+1 hour
1 pm
EET - Eastern
European, USSR Zone 1
+2 hours
2 pm
BT - Baghdad, USSR
Zone 2
+3 hours
3 pm
ZP4 - USSR Zone 3
+4 hours
4 pm

40
ZP5 - USSR Zone 4
+5 hours
5 pm
ZP6 - USSR Zone 5
+6 hours
6 pm
WAST - West Australian
Standard
+7 hours
7 pm
CCT - China Coast,
USSR Zone 7
+8 hours
8 pm
JST - Japan Standard,
USSR Zone 8
+9 hours
9 pm
EAST - East Australian
Standard GST
Guam Standard, USSR
Zone 9
+10 hours
10 pm
IDLE - International Date
Line
NZST - New Zealand
Standard
NZT - New Zealand
+12 hours
Midnight
SNTP Client setting
Time zone
This filed is to select the Timezone which this switch is located
Manual
Synchronize the time with the desktop which connect with switch.
SNTP :
This is to enable/disable the SNTP service, enable the SNTP client is to use the
service from SNTP server, the system time will follow the SNTP server, disable
is to use local time without any SNTP server information, note that the network
should be enabled to have system receive time information from SNTP server if
it is enabled

41
NTP Sever :
Set the SNTP server IP address. You can assign a local network time server’s IP
address or an internet time server’s IP address.
Click
Apply
to have the configuration take effect.
6.4.6 User Accounts – Access account management
There are 2 default accounts in switch – admin with read-write permission and user
with read only permission, you can add new account and set its permission here.

42
6.4.7 SNMP Configuration
Simple Network Management Protocol (SNMP) is the protocol developed to manage
nodes (servers, workstations, routers, switches and hubs etc.) on an IP network.
SNMP enables network administrators to manage network performance, find and
solve network problems, and plan for network growth. Network management systems
learn of problems by receiving traps or change notices from network devices
implementing SNMP.
Agent Version: V1/V2c/V3, not selectable.
Response Locale: select the format code of SNMP message.
Here you can define the new community string set and remove the unwanted
community string.
Community String: Fill the name string.
Privilege:Read only. Enables requests accompanied by this community
string to display MIB-object information.
Read/write. Enables requests accompanied by this community
string to display MIB-object information and to set MIB objects.
Click.
Apply

43
A trap manager is a management station that receives the SNMP trap messages
generated by the switch. If no trap manager is defined, no traps will be issued. To
define a management station as a trap manager, assign an IP address, enterthe
SNMP community strings, and select the SNMP trap version.
IP Address: Enter the IP address of the trap manager.
Community: Enter the community string for the trap station.
Version: Select the SNMP trap version type—v1 or v2c.
Click
Add
.
To remove the community string, select the community string listed in the current
manager’s field and click
Remove
.
6.4.8 Fault Relay Configuration
The Fault Relay Alarm function provides the Power Failure and Port Link
Down/Broken detection. With both power input 1 and power input 2 installed and the
check boxes of power 1/power 2 ticked, the FAULT LED indicator will then be
possible to light up when any one of the power failures occurs. As for the Port Link
Down/Broken detection, the FAULT LED indicator will light up when the port failure
occurs; certainly the check box beside the port must be ticked first. Please refer to
the segment of ‘Wiring the Fault Alarm Contact’ for the failure detection.
Power Failure : Tick the check box to enable the function of lighting up the
FAULT LED on the panel when power fails.
Port Link Down/Broken : Tick the check box to enable the function of lighting
up FAULT LED on the panel when Ports’ states are link down or broken.

44
Note: The interface of Port Link Down/Boken will be changed with different switch
model automatically.
6.4.9 Digital Input /Output
The IPES/IES Industrial Switch contains two digital outputs and two digital inputs.
Outputs are open-collector transistor switches that may be controlled by the host
computer. They provide control signals, which can be applied to heaters, pumps, and
other electrical equipment. The digital inputs may be read by the host computer and
used to sense the state of a remote digital signal.
Digital Input Setting
When DI0/DI1function is enabled; first Digital Input (DI0) and second Digital
Input (DI1) will then be available respectively.
Digital Input: Choose the transition type to trigger DI0/DI1.
LowHigh: Having focused this radio button, DI0/DI1 will only report the
status when the external device’s voltage changes from low to high.

45
HighLow: Having focused this radio button, DI0/DI1 will only report the
status when the external device’s voltage changes from high to low.
Both: Having focused this radio button, DI0/DI1 will report both the status
when the external device’s voltage changes from high to low or low to high.
Event description: Please fill in the description for the event.
Digital Output Setting
When DO0/DO1function is enabled; first Digital Output (DO0) and second Digital
Output (DO1) will then be available respectively.
Condition: Tick the check boxes to decide whether or not to send the events via
digital output with the event about port fail or power fail or both.
Action: Choose the transition type of DO0/DO1.
LowHigh: When switch receive the event about port fail or power fail,
DO0/DO1 will switch the output voltage from low to high.
HighLow: When switch receive the event about port fail or power fail,
DO0/DO1 will switch the output voltage from high to low.

46
6.4.10 Environmental Monitoring
You can monitor the Voltage 、Current、Consumption、Temp、and
PoE Consumption(for the PoE series switch) in this function.

47
6.5 Event & Log
6.5.1 View Logs
This will show you the log in local interface, you can press or F5 to
refresh the web page and get the newest event log.

48
6.5.2 Events
6.5.2.1 Environmental Monitoring Event
You can set the trigger range of each event here, for example, if you set the
blue bar in the range from 20V to 50V, when the voltage of power input is over 50VDC
or lower than the 20VDC, it will trigger the event system.
Note: This function only available with the –M model supporting the optional
sensor of Environmental Monitoring Module.

49
6.5.3 DDM event
The switch supports DMI where can read all the parameters info from DDM SFP
when plugged into SFP slots, the shown information is as above including SFP
temperature, input voltage, TX bias, TX dBm and RX dBM.
You can set the trigger range of each event here, for example, when you set the
blue bar in the range from -45∘C to 90∘C, if the working Temp. of SFP module is over
90∘C or lower than the -45∘C, it will trigger the event system.
Note: This function will be displayed when DDM SFP is inserted.

50
6.5.4 Actions
6.5.4.1 Local Log Action
Save to Local: Save log to local file
6.5.4.2 Remote Syslog Action
Log to Remote Syslog Server: Save log to Syslog Server

51
6.5.4.3 Email Action
Email Alert: Sent log via Email
6.5.4.4 SMS Action
SMS Alert: Sent log via SMS service.
(The must connect with internet and define the SMS server before using this function)

52
(Currently the SMS service is offered by LANTECH in Taiwan.)
6.5.4.5 SNMP Trap Action
SNMP Trap Action: The setting page of this function will be redirect to SNMP
TRAP.
6.5.3.6 DOut Action
DOUT Action: The setting page of this function will be redirect to Digital
Input/Output.

53
6.5.5 Event Action Map
6.5.5.1Event Actions:
A. Choose the event which you want to active
B. You will find the event which you select will be display as below, then choose
forwarding method to define how to forward this event to manager side.

54
C. You can set the forwarding method of port break event in here.

55
6.6 Ports
6.6.1 Configuration
In Port control you can configurethe settings of each port to control the connection
parameters, and the status of each port is listed beneath.
Port No.: The port number which you want to be configured.
Type: Current port state.
Description: Port description.
Enables: enable/disable the switch port.
Flow Control: Whether or not the receiving node sends feedback to the sending
node is determined by this item. When enabled, once thedevice exceeds the
input data rate of another device, the receiving device will send a PAUSE frame
which halts the transmission of the sender for a specified period of time. When
disabled, the receiving device will drop the packet if too much to process.
Speed:Itcan be set as auto or set speed and negotiated way manually.
Click
Apply
to have the configuration take effect.

56
6.6.2 Status
It will show you the status of port configuration setting.
6.6.3 Statistics
The following chart provides the current statistic information which displays the realtime packet transfer status for each port. The user might use the information to plan
and implement the network, or check and find the problem when the collision or
heavy traffic occurs.
Port: The port number.
Type: Displays the current speed of connection to the port.
Link: The status of linking—‘Up’ or ‘Down’.
State: It’s set by Port Control. When the state is disabled, the port will not
transmit or receive any packet.
Tx Good Packet: The counts of transmitting good packets via this port.
Tx Bad Packet: The counts of transmitting bad packets (including undersize
[less than 64 octets], oversize, CRC Align errors, fragments and jabbers packets)
via this port.
Rx Good Packet: The counts of receiving good packets via this port.

57
Rx Bad Packet: The counts of receiving good packets (including undersize [less
than 64 octets], oversize, CRC error, fragments and jabbers) via this port.
Tx Abort Packet: The aborted packet while transmitting.
Packet Collision: The counts of collision packet.
Packet Dropped: The counts of dropped packet.
Rx Bcast Packet: The counts of broadcast packet received.
Rx Mcast Packet: The counts of multicast packet received.
Tx Mcast Packet: The counts of multicast packet transmitted
Click
Clear
button to clean all counts.
6.6.4 IEC Packet Statistics
This function will count the industrial control packet(Like Goose、Modbus、
PTP…etc) with switch.
6.6.5 Mirroring
The Port mirroring is a method for monitor traffic in switched networks. Traffic through
ports can be monitored by one specific port, which means traffic goes in or out
monitored (source) ports will be duplicated into mirror (destination) port.
Destination :You can set which switch port will be responsible for collecting the
data which was duplicated from the source port.

58
Mirrpr From:You can set which switch port will be duplicated then send to the
destination port.
Note1 : All the duplicated data of the source port can be separated with RX and
TX, if you want to collect multi-source ports at the same time, you can assign the
Tx of one destination port to be responsible for collecting all the Tx data of
source ports and assign another RX of destination port to be responsible for
collecting all the Rx data of source ports.
And then, click
Apply
button.
6.6.6 Rate Limiting
You can set up every port’s bandwidth rate and frame limitation type.
All the ports support port egress/Ingress rate control. For example, assume port
1 is 10Mbps, users can set it’s effective egress rate is 1Mbps, ingress rate is
500Kbps. The switch performs the ingress rate by packet counter to meet the
specified rate
Click
Apply
to apply the settings

59
6.6.7 Loop Protection
The loop Protection is used to detect the presence of traffic. When switch receives
packet’s (looping detection frame) MAC address the same as oneself from port, show
Loop Protection happens. The port will be locked when it received the looping
Protection frames.
Enable Loop Protection:
Control whether loop protections is enabled (as a whole). .
Interval:
The interval between each loop protection PDU sent on each port. valid values are 1 to 10
seconds.
Shutdown :
The period (in seconds) for which a port will be kept disabled in the event of a loop is detected
(and the port action shuts down the port). Valid values are 0 to 604800 seconds (7 days). A
value of zero will keep a port disabled (until next device restart).

60
6.7 Power over Ethernet (only available for IPES series)
This segment shows the PoE(Power over Ethernet) function complying with IEEE
802.3af/at standards
6.7.1 Configuration
Maximum Power Available:
This function will limit the total power consumption and cannot exceed 250W.
Port No.
The number of each PoE port
Enable
Enable/disable the PoE function of each PoE port
Priority
Set the priority of power supply, if the total power consumption of all PoE ports
was over the value of maximum power available, the switch will offer the power
to the high priority PoE port and stop to supply power to the low priority PoE port.

61
Power Limit
Set the Maximum power of each PoE port
6.7.2 Status
Power Consumption:
Total power consumption of all PoE ports
Main Voltage:
The input voltage for PoE power source
Main Current
The input current for PoE power source
----------------------------------------------------------------------------------------------------------------
Port No.
The number of each PoE port.
Link
The connection status of each PoE port.

62
State
The PoE state of the end device.(Unknown means the end device is none-PD
device)
Temperature
Temperature of PoE chipset
Current
Output current of each PoE port
Voltage
Output Voltage of each PoE port
Power
Power consumption of each PoE port
Detection Class
The PoE class of each PD device where connects with switch.
Note:
802.3af send 15.4W; receive 12.95W ~48VDC
802.3at send 30.0W; receive 25.50W ~54VDC

63
6.7.3 Detection
The PoE detection function is to detect whether the connected PD is still alive by
pinging the IP address. Should the PD is not responding, the switch can be set for
consequence action such as rebooting PD etc. Note: The PD must have IP address.
No.
The number of PoE port
Enabled
Enable the PoE port with PoE detection function.
IP address
The IP address of the connected PD.

64
Interval
How frequent the switch will ping the IP address of PD.
Retry Time
How many times of ping failure the switch will define the PD as dead or failure.
Failure Log
Failure times of the PD detection.
Failure Action
When the switch can not detect the PD, there are several failure action to be set
as followings:
Nothing: No action
Power Down: shutdown the power of the PoE port
Power On: keep the power on with the PoE port
Restart Forever: Restart the power of the PoE port always.
Restart Once: only restart the PoE power one time.
Reboot time
To set the reboot time of PD in order for the switch to check PD connection after
PD is completely boot up.
6.7.4 Scheduling
The Poe scheduling is to feed or shut down PoE power over a routine schedule in the
following table.

65
6.8 Topology
This function can help user to build the network topology drawing automatically for
the switches that are in closed looped and show the detail information of each switch
node by clicking the icon. The topology view drawing can show the backup path
with the dot line for overall picture, please remember to enable LLDP function before
you use this function.
Topology Status

66
Text View:
Display each switch in your network by text.
The Topology was build with the information from LLDP where can let you see the
information from other switches.
Nodes:
show the information of each switch like MAC address and IP address.
Links:
show the information of each connection .
Rings:
show the information from ITU-Ring function
Graphic View:
Display each switch connection in the network by graphic.
You can see the topology diagram which is assorted by the LLDP information.
Physical :
display the physical connection of network .
Ring :
Beside the physical connection, also show the information about ITU-Ring

67
Demo:
Demo display each topology in different connection.

68
6.9 QoS
Quality of Service (QoS) is the ability to provide different priority to different
applications, users or data flows, or to guarantee a certain level of performance to a
data flow. QoS guarantees are important if the network capacity is insufficient,
especially for real-time streaming multimedia applications such as voice over IP or
Video Teleconferencing, since these often require fixed bit rate and are delay
sensitive, and in networks where the capacity is a limited resource, for example in
cellular data communication. In the absence of network congestion, QoS
mechanisms are not required.
6.9.1 QoS Policy
Using the weight fair queue scheme
tThe switch will follow 8:4:2:1 rate to process priority queue from High to lowest
queue. For example, while the system processing,1 frame of the lowest queue, 2
frames of the low queue, 4 frames of the middle queue, and 8 frames of the high
queue will be processed at the same time in accordance with the 8,4,2,1 policy rule.

69
Priority Type
There are 3 priority type selections available—CoS, TOS-only, TOS first, . Disable
means no priority type is selected.
CoS
Set up the COS priority level. With the drop-down selection item of Priority
Type above being selected as COS only/COS first, this control item will
then be available to set the queuing policy for each port.
ToS-only
ToS priority: the system provides 0~63 ToS priority level. Each level has 8
type of priority - 0~7. The default value is "1" priority for each level. When
the IP packet is received, the system will check the ToS level value in the IP
packet has received. For example: user set the ToS level 25 is 7. The port 1
is following the ToS priority policy only. When the packet received by port 1,
the system will check the ToS value of the received IP packet. If the ToS
value of received IP packet is 25(priority = 7), and then the packet priority
will have highest priority.
ToS-First
When the packet tag with both the CoS and ToS , the switch will check the
ToS tag at first, then check the CoS tag.
Click
Apply
to have the configuration take effect.

70
6.10 Security
6.10.1 MAC Address Tables
Use the MAC address table to ensure the port security.
Static MAC Address
You can add a static MAC address; it remains in the switch's address table,
regardless of whether the device is physically connected to the switch. This saves the
switch from having to re-learn a device's MAC address when the disconnected or
powered-off device is active on the network again. You can add / modify / delete a
static MAC address. MAC Address: Enter the MAC address of the port that should
permanently forward traffic, regardless of the device network activity. VLAN ID :
Entering the VLAN ID. Port No : pull down the selection menu to select the port
number.
MAC Filtering
By filtering MAC address, the switch can easily filter pre-configure MAC address and
reduce the un-safety. You can add and delete filtering MAC address. MAC Address:
Enter the MAC address that you want to filter.
All MAC Addresses
you can view the port that connected device's MAC address and related device's
MAC address.

71
6.10.2 Access Control List
The switch access control list (ACL) is probably the most commonly used object in
the OSI layer 2 and 3. It is used for access filtering. The ACLs are divided into MAC
and IP filtering.
6.10.2.1 ACL with Layer2 (MAC)
No:
The number of ACL record.
Port:
assign the port which you want to enable the ACL function.
Direction:
Let the switch check the destination address or source address of packet.
Address: assign the MAC address which you want to deny.
Mask: set the mask to filter the MAC range.
6.10.2.2 ACL with Layer3 (IP)
No:
The number of ACL record.
Port:
assign the port which you want to enable the ACL function.
Direction:
let the switch check the destination address or source address of packet.
Address:
assign the IP address which you want to deny.
Mask:
set the mask to filter the IP range.

72
6.10.3 IEEE 802.1X Radius Server
802.1X is an IEEE authentication specification which prevents the client from
accessing a wireless access point or wired switch until it provides authority, like the
user name and password that are verified by an authentication server (such as
RADIUS server).
After enabling the IEEE 802.1X function, you can configure the parameters of this
function.
Server IP
Assign the RADIUS Server IP address.
Server Port
Set the UDP destination port for authentication requests to the specified RADIUS
Server.
Shared Key
Set an encryption key for using during authentication sessions with the specified
RADIUS server. This key must match the encryption key used on the RADIUS Server.
NAS Identifier
Set the identifier for the RADIUS client.
Enable on Ports
Enable or disable 802.1x protocol.

73
6.10.4 IP Security
IP security function allows user to assign 20 specific IP addresses that have
permission to access the switch through the web browser for the securing switch
management.
Enable IP Security
When this option is in Enable mode, the Enable Web Server and Enable Telnet
Server and Enable SSH Server check boxes will then be available.
Enable Web Server
When this check box is checked, the IP addresses among IP permit list will be
allowed to access via web service.
Enable Telnet Server
When this check box is checked, the IP addresses among IP permit list will be
allowed to access via telnet service.
Enable SSH Server
When this check box is checked, the IP addresses among IP permit list will be
allowed to access via ssh service.
IP permit list
Assign up to 20 specific IP address. Only these 10 IP address can access and
manage the switch through the Web browser

74
6.11 VLAN
A Virtual LAN (VLAN) is a logical network grouping that limits the broadcast domain,
which would allow you to isolate network traffic, so only the members of the same
VLAN will receive traffic from the ones of the same VLAN. Basically, creating a VLAN
on a switch is logically equivalent of reconnecting a group of network devices to
another Layer 2 switch. However, all the network devices are still plugged into the
same switch physically.
6.11.1 802.1Q VLAN Config
Management VLAN ID:
This will set which VLAN group can access the switch, the default “0” means all
VLAN group, this limitation will not support port based VLAN.
Link Type:
There are 3 types of link type.
1. Access Link: A segment which provides the link path for one or more stations to
the VLAN-aware device. An Access Port (untagged port), connected to the access

75
link, has an untagged VID (also called PVID). After an untagged frame gets into the
access port, the switch will insert a four-byte tag in the frame. The contents of the
last 12-bit of the tag is untagged VID. When this frame is sent out through any of
the access port of the same PVID, the switch will remove the tag from the frame to
recover it to what it was. Those ports of the same untagged VID are regarded as
the same VLAN group members.
Note: Because the access port doesn’t have an understanding of tagged
frame, the column field of Tagged VID is not available.
2. Trunk Link: A segment which provides the link path for one or more VLANaware devices (switches). A Trunk Port, connected to the trunk link, has an
understanding of tagged frame, which is used for the communication among
VLANs across switches. Which frames of the specified VIDs will be forwarded
depends on the values filled in the Tagged VID column field. Please insert a
comma between two VIDs.
Note:
A trunk port doesn’t insert tag into an untagged frame, and therefore the untagged
VID column field is not available.
It’s not necessary to type ‘1’ in the tagged VID. The trunk port will forward
the frames of VLAN 1.
The trunk port has to be connected to a trunk/hybrid port of the other switch.
Both the tagged VID of the two ports have to be the same.
3. Hybrid Link: A segment which consists of Access and Trunk links. The hybrid
port has both the features of access and trunk ports. A hybrid port has a PVID
belonging to a particular VLAN, and it also forwards the specified tagged-frames
for the purpose of VLAN communication across switches.
PVID
This column field is available when Link Type is set as Access Link and Hybrid Link.
Assign a number in the range between 1 and 4094.
Tagged VID:
This column field is available when Link Type is set as Trunk Link and Hybrid Link.

76
Assign a number in the range between 1 and 4094.
6.11.2 Status
You can see the status of each VLAN group in here.
6.12 MVR
The MVR feature enables multicast traffic forwarding on the Multicast VLAN. In a
multicast television application, a PC or a television with a set-top box can receive
the multicast stream. Multiple set-top boxes or PCs can be connected to one
subscriber port, which is a switch port configured as an MVR receiver port. When a
subscriber selects a channel, the set-top box or PC sends an IGMP join message to
Switch A in order to join the appropriate multicast. Uplink ports that send and receive
multicast data to and from the multicast VLAN are called MVR source ports.
VLAN ID
Specify the Multicast VLAN ID.
Multicast Addresses
Multicast Addresses of the group displayed.
Port Members
Ports under this group.

77
6.12 LLDP
Link Layer Discovery Protocol (LLDP) is defined in the IEEE802.1AB, it is an
emerging standard which provides a solution for the configuration issues caused by
expanding LANs. LLDP specifically defines a standard method for Ethernetnetwork
devices such as switches, routers and wireless LAN access points to advertise
information about themselves to other nodes on the network and store the
information they discover. LLDPruns on all 802 media. The protocol runs over the
data-link layer only, allowing two systems running different network layer protocols to
learn about each other.
6.12.1 LLDP Configuration
Enabled
Enabled The switch will send out LLDP information, and will analyze LLDP
information received from neighbours.
Tx Interval

78
The switch periodically transmits LLDP frames to its neighbours for having the
network discovery information up-to-date. The interval between each LLDP frame is
determined by the Tx Interval value. Valid values are restricted to 5 - 32768 seconds.
The LLDP port settings relate to the currently selected stack unit, as reflected by the
page header.
Port No
The switch port number of the logical LLDP port.
Port Id
Enter characters to be id name for the logical LLDP port.
Mode
Select LLDP mode.
Rx only The switch will not send out LLDP information, but LLDP information from
neighbor units is analyzed.
Tx only The switch will drop LLDP information received from neighbors, but will send
out LLDP information.
Disabled The switch will not send out LLDP information, and will drop LLDP
information received from neighbors.
Both The switch will send out LLDP information, and will analyze LLDP information
received from neighbors.
6.12.2 LLDP Neighbor
This page provides a status overview for all LLDP neighbors. The displayed table
contains a row for each port on which an LLDP neighbor is detected. The columns
hold the following information:
Local Port

79
The port on which the LLDP frame was received.
Chassis ID
The Chassis ID is the identification of the neighbor's LLDP frames.
Remote Port ID
The Remote Port ID is the identification of the neighbor port.
Port Description
Port Description is the port description advertised by the neighbor unit.
System Name
System Name is the name advertised by the neighbour unit.
System Capabilities
System Capabilities describes the neighbour unit's capabilities. The possible
capabilities are:
1. Other
2. Repeater
3. Bridge
4. WLAN Access Point
5. Router
6. Telephone
7. DOCSIS cable device
8. Station only
9. Reserved
When a capability is enabled, the capability is followed by (+). If the capability is
disabled, the capability is followed by (-).
Management Address
Management Address is the neighbor unit's address that is used for higher layer
entities to assist discovery by the network management. This could for instance hold

80
the neighbor's IP address.
6.12.3 LLDP Statistics
This page provides an overview of all LLDP traffic.
Two types of counters are shown. Total are counters that refer to the whole stack,
switch, while Port refer to per port counters for the currently selected switch.
6.12.3.1 Total
Neighbours Aged Out
Shows the number of entries deleted due to Time-To-Live expiring.
Neighbours Added
Shows the number of new entries added since switch reboot.
Neighbours Deleted
Shows the number of new entries deleted since switch reboot.
Frames Discarded
If an LLDP frame is received on a port, and the switch's internal table has run full, the
LLDP frame is counted and discarded. This situation is known as "Too Many
Neighbours" in the LLDP standard. LLDP frames require a new entry in the table
when the Chassis ID or Remote Port ID is not already contained within the table.
Entries are removed from the table when a given port's link is down, an LLDP
shutdown frame is received, or when the entry ages out.
Frames Received In Error
The number of received LLDP frames containing some kind of error.
Frames In
The number of LLDP frames received on the port.
Frames Out

81
The number of LLDP frames transmitted on the port.
TLVs Discarded
Each LLDP frame can contain multiple pieces of information, known as TLVs (TLV is
short for "Type Length Value"). If a TLV is malformed, it is counted and discarded.
TLVs Unrecognized
The number of well-formed TLVs, but with an unknown type value.
Ports
The displayed table contains a row for each port. The columns hold the following
information:
Port
The port on which LLDP frames are received or transmitted.
Neighbors Aged Out
Shows the number of entries deleted due to Time-To-Live expiring.
Neighbors Added
Shows the number of new entries added since switch reboot.
Neighbors Deleted
Shows the number of new entries deleted since switch reboot.
Frames Discarded
If an LLDP frame is received on a port, and the switch's internal table has run full, the
LLDP frame is counted and discarded. This situation is known as "Too Many
Neighbors" in the LLDP standard. LLDP frames require a new entry in the table when
the Chassis ID or Remote Port ID is not already contained within the table. Entries
are removed from the table when a given port's link is down, an LLDP shutdown
frame is received, or when the entry ages out.
Frames Received In Error
The number of received LLDP frames containing some kind of error.
Frames In
The number of LLDP frames received on the port.
Frames Out
The number of LLDP frames transmitted on the port.
TLVs Discarded
Each LLDP frame can contain multiple pieces of information, known as TLVs (TLV is
short for "Type Length Value"). If a TLV is malformed, it is counted and discarded.

82
TLVs Unrecognized
The number of well-formed TLVs, but with an unknown type value.
6.13 CDP
The Cisco Discovery Protocol (CDP) is a proprietary data link layer protocol
developed by Cisco. It is used to share information about other directly connected
Cisco equipment, such as the OS version and IP address
6.13.1 CDP Configuration Device Settings
CDP Enabled
Enabled the switch will send out CDP information, and will analyze CDP information
received from neighbors.
Tx Interval(secs)
The switch periodically transmits CDP frames to its neighbours for having the
network discovery information up-to-date. The interval between each CDP frame is
determined by the Tx Interval value. Valid values are restricted to 5 - 32768 seconds.
Tx Holdtime(secs)
Each CDP frame contains information about how long the information in the CDP

83
frame shall be considered valid. The holdtime between each CDP frame is
determined by the Tx Holdtime value. Valid values are restricted to 5 - 32768
seconds.
6.13.2 CDP Port Configuration
Port
The switch port number of the logical CDP port.
Enabled
The switch will send out CDP information, and will analyze CDP information received
from neighbors.
6.13.3. CDP Status
Statistics
Total Packets Output
The number of CDP frames transmitted on the switch.
Total Packets Input
The number of CDP frames received on the switch.
Neighbors
The displayed table contains a row for each port on which an CDP neighbour is

84
detected. The columns hold the following information:
Local Port
The port on which the CDP frame was received.
Version
Version is the CDP version advertised by the neighbor unit.
Ageout TTL
Ageout TTL is the ageout Time-To-Live advertised by the neighbor unit.
Device ID
The Device ID is the identification of the neighbor's CDP frames.
Platform
Platform is the description advertised by the neighbor unit.
Software Version
Software Version is the software version advertised by the neighbor unit.
Addresses
Addresses is the neighbour unit's address that is used for higher layer entities to
assist discovery by the network management. This could for instance hold the
neighbor's IP address.

85
6.14 IGMP Snooping
The switch support IP multicast, you can enable IGMP protocol on web
management’s switch setting configuration page, then the IGMP snooping
information displays. IP multicast addresses range are from 224.0.0.0 through
239.255.255.255.

86
6.14.1 IGMP Snooping Configuration
6.14.1.1 Global Configuration
Enable Query: enable or disable the IGMP query function. The IGMP query
information will be displayed in IGMP status section.
Enable Snooping: enable or disable the IGMP protocol.
Flood Well-known Multicasr traffic:let the switch know how to process the
Multicast data stream which was unregistered with IGMP Query.
6.14.1.2 Port Related Configuration
Port
The switch port number of the logical port.
Router Port
Specify which ports act as router ports. A router port is a port on the Ethernet switch
that leads towards the Layer 3 multicast device or IGMP querior.
If an aggregation member port is selected as a router port, the whole aggregation
will act as a router port.
Fast Leave
Enable the fast leave on the port.

87
6.14.2 IGMP Snooping Status
6.14.2.1 Statistics
VLAN ID
The VLAN ID of the entry.
Status Querior
Shows the Querior status is "ACTIVE" or "IDLE".
"DISABLE" denotes the specific interface is administratively disabled.
Queries Transmitted
The number of Transmitted Queries.
Queries Received
The number of Received Queries.
V1 Reports Received
The number of Received V1 Reports.
V2 Reports Received
The number of Received V2 Reports.

88
V3 Reports Received
The number of Received V3 Reports.
V2 Leaves Received
The number of Received V2 Leaves.
IGMP Groups
Entries in the IGMP Group Table are shown on this page.
VLAN ID
VLAN ID of the group.
Multicast Addresses
Group address of the group displayed.
Port Members
Ports under this group.
Membership Interval
The group hold aging out TTL

89
6.15 MSTP
The section describes that how to configure the Spanning Tree Bridge and STP
System settings. It allows you to configure STP System settings are used by all STP
Bridge instance in the Switch.
6.15.1. MSTP Global Configuration
Mode
Show the STP protocol version setting. Valid values are STP, RSTP and MSTP.
Name
The name identifying the VLAN to MSTI mapping. Bridges must share the name and
revision (see below), as well as the VLAN-to-MSTI mapping configuration in order to
share spanning trees for MSTI's (Intra-region). The name is at most 32 characters.
Revision
The revision of the MSTI configuration named above. This must be an integer
between 0 and 65535.
Forward Delay

90
The delay used by STP Bridges to transit Root and Designated Ports to Forwarding
(used in STP compatible mode). Valid values are in the range 4 to 30 seconds.
Max Age
The maximum age of the information transmitted by the Bridge when it is the Root
Bridge. Valid values are in the range 6 to 40 seconds, and MaxAge must be <=
(FwdDelay-1)*2.
Maximum Hop Count
This defines the initial value of remaining Hops for MSTI information generated at the
boundary of an MSTI region. It defines how many bridges a root bridge can distribute
its BPDU information to. Valid values are in the range 6 to 40 hops.
6.15.2 How to enable MSTP
6.15.2.1 Enter MSTP CIST Settings , press icon to enable MSTP
PS: (The default was disable with all ports)
6.15.2.2 Check the status of STP, all ports should display “Yes”

91
6.15.2.3 Remember to press “Apply”
6.15.2.4 Save setting

92
6.15.3 CIST Settings
6.15.3.1 Bridge configuration
VLANs Mapped
The list of VLANs mapped to the MSTI. The VLANs must be separated with
comma and/or space. A VLAN can only be mapped to one MSTI. An unused
MSTI should just be left empty. (I.e. not having any VLANs mapped to it.)
Unmapped VLANs are mapped to the CIST. (The default bridge instance).
Bridge Priority
Control the bridge priority. Lower numeric values have better priority. The bridge
priority plus the MSTI instance number, concatenated with the 6-byte MAC
address of the switch forms a Bridge Identifier.
6.15.3.2 Port
Port No
The switch port number of the logical STP port.
Enabled STP
Control whether STP is enabled on this switch port.
Path Cost
Controls the path cost incurred by the port. The Auto setting will set the path cost
as appropriate by the physical link speed, using the 802.1D recommended values.
Using the Specific setting, a user-defined value can be entered. The path cost is
used when establishing the active topology of the network. Lower path cost ports
are chosen as forwarding ports in favour of higher path cost ports. Valid values
are in the range 1 to 200000000.
Priority
Control the port priority. This can be used to control priority of ports having
identical port cost. (See above).

93
edge_mode
Control whether the oper Edge flag should start as being set or cleared. (The
initial oper Edge state when a port is initialized). Control whether the bridge
should enable automatic edge detection on the bridge port. This allows oper Edge
to be derived from whether BPDU's are received on the port or not.
p2p_mode
Description: Controls whether the port connects to a point-to-point LAN rather
than a shared medium. This can be automatically determined, or forced either
true or false. Transition to the forwarding state is faster for point-to-point LANs
than for shared media.
6.15.4. MSTP MSTI Settings
Instance No
VLANs
The list of VLANs mapped to the MSTI. The VLANs must be separated with
comma and/or space. A VLAN can only be mapped to one MSTI. An unused
MSTI should just be left empty. (I.e. not having any VLANs mapped to it.)
Unmapped VLANs are mapped to the CIST. (The default bridge instance).
Priority
Control the bridge priority. Lower numeric values have better priority. The bridge
priority plus the MSTI instance number, concatenated with the 6-byte MAC
address of the switch forms a Bridge Identifier.

94
6.15.5. MSTP Bridges Status
Instance
The Bridge Instance. ex: CIST, MSTI1, ...
Bridge ID
The Bridge ID of this Bridge instance.
Root ID
The Bridge ID of the currently elected root bridge.
Root Port
The switch port currently assigned the root port role.
Root Cost
Root Path Cost. For the Root Bridge it is zero. For all other Bridges, it is the sum of
the Port Path Costs on the least cost path to the Root Bridge.
Topology State
The current state of the Topology Change Flag of this Bridge instance.
Topology Change Last
The time since last Topology Change occurred.

95
6.15.6. Bridge status of all ports
Port
The switch port number of the logical STP port.
Role
The current STP port role of the port. The port role can be one of the following values:
AlternatePort BackupPort RootPort DesignatedPort Disabled.
State
The current STP port state of the port. The port state can be one of the following
values: Discarding Learning Forwarding.

96
6.16 Aggregation
Port trunking is the combination of several ports or network cables to expand the
connection speed beyond the limits of any one single port or network cable. Link
Aggregation Control Protocol (LACP),which is a protocol running on layer 2, provides
a standardized means in accordance with IEEE 802.3ad to bundle several physical
ports together to form a single logical channel. All the ports within the logical channel
or so-called logical aggregator work at the same connection speed and LACP
operation requires full-duplex mode.
6.16.1. Aggregation Configuration
Trunking Group :
There are 6 trunk groups to be selected.
Enable LACP Dynamic Trunking:
Enable LACP with the dedicated trunking group.
Port member: This column field allows the user to choose the total number of
active port up to four. With LACP, e.g. you assign four ports to be the members
of a trunk group whose work ports column field is set as two; the exceed ports
are standby/redundant ports and can be aggregated if working ports fail.

97
6.16.2 LACP Port Status
You can check the setting of Port aggregation in Status.
Group ID
Number of trunking group
TYPE
' Static for static aggregation and Dynamic for LACP.
System ID
The ID of each Trunking group
Trunk Members
Each switch port is listed for each group ID. Select a radio button to include a
port in an aggregation, or clear the radio button to remove the port from the
aggregation. By default, no ports belong to any aggregation group. Only full duplex
ports can join an aggregation and ports must be in the same speed in each group.

98
6.17 PTP IEEE 1588 v2
The Precision Time Protocol (PTP) is a protocol used to synchromize clocks
throughout a network where achieves clock accuracy in the 1us range, making it
suitable for measurement and control systems. IEEE 1588 v2 is designed for local
systems requiring accuracies beyond those attainable using NTP. It is also designed
for applications that cannot bear the cost of a GPS receiver at each node, or for
which GPS signals are inaccessible.
Enable on:
Select which port you want to enable PTP function.
Domain:
Set the PTP domain
Priority1:
 Loading...
Loading...