Landmark Lighting D20R2 User Manual

D20R2-06/99
...a component of the PerformanceWorks for MVS and OS/390 solution suite
Features include the NaviGate
communications interface
System
Administrator’s
Guide
Version 2.0

The Monitor for MVS Version 2.0 – a component of the PerformanceWorks for MVS and OS/390
solution suite. Features include the NaviGate communications interface.
System Administrator’s Guide
This manual applies to The Monitor for MVS (TMON for MVS), a proprietary software product of
Landmark Systems Corporation. In North America, Landmark markets and supports TMON for MVS.
Internationally, TMON for MVS is marketed and supported by a network of software marketing firms.
The information contained herein is subject to change. Address comments to:
Landmark Systems Corporation
12700 Sunrise Valley Drive
Reston, Virginia 20191 -5804
1-800-775-LMRK (1-800-775-5675)
1-703-464-1300
Edition Date ........... June 1999
D20R2-06/99
Landmark Systems Corporation, the Landmark logo, NaviGate, NaviGraph, NaviPlex,
PerformanceWorks, Pinnacle, and The Monitor are registered trademarks of Landmark Systems
Corporation.
UNIX is a registered trademark in the United States and other countries licensed exclusively through
X/Open Company, Lt d. All other product and brand na mes mentioned are trademarks or regi stered
trademarks of their respective holders.
For definitive information with respect to CICS data areas (including control blocks), you should refer
to the appropriate IBM publication as identified in the CICS Library Guide (GC33-0356).
© 1988, 1999 by Landmark Systems Corporation
All rights reserved
This licensed work is confidential and proprietary and the property of Landmark Systems Corporation. Reproduction, disclosu r e, or use without the spec ific written authorization of L an d m ar k Sys tems Corporation is strictly prohibited.

Contents
Using this Guide . . . . . . . . . . . . . . . . . . . . . . . . . . . . . iii
Organization of this Guide . . . . . . . . . . . . . . . . . . . . . . . . iii
Notational Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . iii
Related Documentation . . . . . . . . . . . . . . . . . . . . . . . . . . iv
Comments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . vi
Chapter 1: Installation Verification Procedu re . . . . . . . . . . . . 1-1
IVP Checklist . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-1
IVP Steps . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-1
Chapter 2: Security Definitions . . . . . . . . . . . . . . . . . . . . 2-1
How Product Security Works . . . . . . . . . . . . . . . . . . . . . . 2-2
Tracing Security Pr oblems . . . . . . . . . . . . . . . . . . . . . . . . 2-4
Using External Security . . . . . . . . . . . . . . . . . . . . . . . . . 2-4
Using User Exit Security . . . . . . . . . . . . . . . . . . . . . . . . . 2-8
Using Internal Security . . . . . . . . . . . . . . . . . . . . . . . . . . 2-9
Security Definitions Menu . . . . . . . . . . . . . . . . . . . . . . . 2-14
User Profiles Directory . . . . . . . . . . . . . . . . . . . . . . . . . 2-16
User Definition . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-18
Secured Functions Directory . . . . . . . . . . . . . . . . . . . . . . 2-21
Function Code Table . . . . . . . . . . . . . . . . . . . . . . . . . . 2-24
Profiles/Resources Directory . . . . . . . . . . . . . . . . . . . . . 2-33
Detail Profile Definition . . . . . . . . . . . . . . . . . . . . . . . . 2-36
Function Access Level Table . . . . . . . . . . . . . . . . . . . . . . 2-41
Chapter 3: Landmark Product Communication . . . . . . . . . . . 3-1
Access Methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-1
Setting Up Landmark Pro duct Communi cation . . . . . . . . . . . 3-3
Using Explicit Pass-Through . . . . . . . . . . . . . . . . . . . . . 3-10
Using Implicit Pass-Through . . . . . . . . . . . . . . . . . . . . . 3-12
Using NaviGate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-13
Remote Sessions Dire ctor y . . . . . . . . . . . . . . . . . . . . . . . 3-18
Remote Session Definition . . . . . . . . . . . . . . . . . . . . . . . 3-21
Remote Sessions Logon . . . . . . . . . . . . . . . . . . . . . . . . 3-24
Chapter 4: Support and Maintenance . . . . . . . . . . . . . . . . 4-1
Customer Service Satisfaction Guarantee . . . . . . . . . . . . . . . 4-1
Year 2000 Compliance Warranty . . . . . . . . . . . . . . . . . . . . 4-2
Product Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-2
Product Maintenance . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-8
Configuration Changes and Disaster Recovery . . . . . . . . . . . 4-10
Appendix: TMON for MVS Sample Library . . . . . . . . . . . . . . A-1
Index
The Monitor for MVS 2.0 i
System Administrator’s Guide

Contents
ii

Using this Guide
The Monitor for MVS System Administrator’s Guide includes
information on the TMON for MVS installation verification
procedure as well as support and maintenance procedures. It also
includes information on security, the TMON for MVS Performance
Database, NaviGate , and t he distri b uted s am ple lib rary.
The audience for this guide includes both technicians and
managers in systems, programming, capacity planning, operations,
and security. A basic understa nding of MVS is assu m ed.
This section provides an overview of the guide, the conventions
used to document product use, and a list o f related do cumentat ion.
It also describes how t o su bmi t c om men ts to Landm ark.
Organization of this Guide
This guide is organized into the following chapters and appendix.
Chapter 1: Installation Verification Procedure
Provides a detailed TMON for MVS installation verification
procedure to help ensure all installation steps, documented in
PerformanceWorks for MVS and OS/390 Installation Guide, are
successfully completed.
Chapter 2: Security Definitions
Provides information on using Landmark’s security facilities to
secure TMON for MVS functions.
Chapter 3: Landmark Product Communication
Explains how to use Landmark product communication to define a
network betw een products and monitor address spaces any w here
in the network .
Chapter 4: Support and Maintenance
Describes the procedures, including standard maintenance, that
help Customer Services efficiently as sist you w ith TMON for MVS.
Please read this chapter before contacting Cu sto mer Servi ces or
your international representative.
Appendix: TMON for MVS Sample Library
Describes t he m em ber s o f the TMON for MV S sa mp l e li b rary.
Notational Conventions
The following notational conventions are used in this guide.
Notation Description
b A b with a slash through it indicates a blank.
... An ellipsis indicates that the previous parameter or
The Monitor for MVS 2.0 iii
System Administrator’s Guide
command can be repeat ed.

Related Documentation Using this Guide
Notation Description
’ = , ( ) + - * / These special characters punctuate commands and
{ } Braces surround required command parameters.
[ ] B rack et s surr ou nd co mm an d opt io ns .
| Vertical bars separate command options. Choose one
➥ An arrow id en t ifi es a cu r so r-s el ec t ab le fi e ld or li ne.
DD When used in a display form at, “DD” indicates the day in a
hh When us ed in a disp l ay fo rm at, “h h” in dic at e s hu nd red th s
HH When used in a display format, “HH” indicates the hour of
lower c ase Lower ca se char ac t er s in c om ma nd fo rm at sh ow
Mixed Ca se Mixed - case cha r ac te r s in co mm an d f or m at show
MM When used in a display form at, “MM” indicates minutes or
n When us ed in a di sp l ay form at , “n ” indi ca t es an int e ge r.
SS When used in a display form at, “SS” indicates the seconds
t When used in a di sp l ay form at , “t ” in dic at es te nt h s,
YY When used in a display form at, “YY” indicates the year.
underlined text Default values are underlined.
UPPER CA SE Upper case ch ar ac ter s i de nti f y co mm an ds or co nt rol
command options. The characters must be entered
exactl y as sh ow n.
option from the list.
A compa ss id en t ifi es a f ie ld t ha t h as a bu il t- in co nn ec ti on
to another Landmark MVS product in the same processor
compl ex . If th e ot her pr od uc t is act i ve and de f in ed to yo ur
syste m, cur so r- s elec t th e fie l d t o pa ss- th r ou gh to it .
date, from “01” through “31”.
of a second.
a day, from “00” through “23”.
info rm ati on yo u mu st su ppl y.
abbreviations for commands. Only the uppercase letters
must be entered.
month s. If used in a t im e f i eld, i t r ep res en ts th e m in ut e s
of the hour, from “01” through “59”. If used in a date field,
it repr es en t s the mo nt h i n t he year , f r om “0 1” th r ou gh “1 2”.
The number of n’s displayed represents the number of
digi ts in th e int e ge r.
of a time field, from “00” through “59”.
thousandths, or ten thousandths of a second.
statements. These characters must be entered exactly as
shown.
Related Documentation
To order additional copies of
TMON for MVS
documentation, see the order
form in The Monitor for
MVS Release Guide.
iv
The PerformanceWorks for MVS and OS/390 Online Documentation
Library CD-ROM provides all the TMON for MVS documenta tion
in BookManager READ and Adobe Acrobat Reader formats. It also
provides a copy of Adobe Acrobat Reader.
In addition to this guide, t he TMO N f or MVS docu menta tion
library includes:

Using this Guide Related Documentation
• The Monitor for MVS Release Guide, which familiarizes TMON
for MV S users wi t h the features in the pro d uct.
• PerformanceWorks for MVS and OS/390 Installation Guide, which
includes everything you need to know to install
PerformanceWorks for MVS and OS/390. It describ es the
installation procedures designed to enable you to get
PerformanceWorks up and running as quickly and smoothly as
possible. I t a l so addresses a numbe r of the faciliti es and special
interfaces availa ble to y o u wi th the ins tall at ion of
PerformanceWorks.
• The Monitor for MVS Reference Manual, which provides an
overview of TMON for MVS as well as complete information
for online pro duct use.
• The Monitor for MVS Report Writer, which contains two
sections:
– Report Writer Reference Manual provides an overvi ew of
Report Writer capab i litie s a n d gener al usa ge guid eline s
that apply to all Landmark performance monito rs. R eport
Writer JCL and control statements also are provided in this
section.
– The Monitor for MVS Report Writer Supplement provides
product-specific information, such as data elements,
sample reports, and explanations of product databases and
record types.
The appendixes contain Report Writer messages and codes as well
as tips for using the Report Writer.
• The Monitor for MVS Messages and Codes, which includes error
messages and abnorma l term inati on c ode s for all TMO N fo r
MVS batch and online processing.
• Landmark File Services User’s Guide, which describes all LF S
components, functions , and co mm ands . It also inc ludes a
product appendix describing the LFS file stru cture and
SAMPLIB members supplied when you install TMON for MVS.
• Elect ro nic Customer S ervice System User ’s Guide , which describes
Landmark’s Electronic Cust omer S ervice sy ste m ( ECS ) that y ou
can use to access product maintenance 24 hours a day. It
describes hardware and software requirements, registration
procedures, and how to access ECS through the Inte rnet and
Telnet. It also tells you how to access information in a product
conference and download that information from ECS.
Instructions for uploading information to Landmark Customer
Services using a file transfer protocol also are provided.
The Monitor for MVS 2.0 v
System Administrator’s Guide

Comments Using this Guide
Comments
If you find an error or have any suggestions on how this
publication can better meet your needs, either send an e-mail to
Customer Servi ce s a t its@landmark.com or call them at
1-800-775-LMRK (5675). When reporting a documentation erro r,
include the name of the publication, chapter number, section name,
and a detailed description of t he error.
vi

Chapter 1: Installation Verification Procedure
After you have successfully installed TMON for MVS , as descri b ed
in PerformanceWorks for MVS and OS/390 Installat ion G uide, follow
the installation verification pro cedure (IVP) documented in this
chapter to ensure the base TMON for MVS product i s properly
installed and functioning in your enviro nment.
IVP Checklist
The following checklist indicates the TMON for MVS components
you will verify during the IVP. Call Customer Services or your
international representative if you have any problems.
1. Ve r i fy th e System Sel ection Me n u .
2. Veri fy the Activi ty Moni tor.
3. Verify the Exception Monitor.
4. Verify the Graphic Monitor.
5. Verify Collection Ana lys is.
6. Verify Sup ertrace .
7. Verify Uti lit ies.
IVP Steps
8. Verify the Delay Monitor.
9. Ve r i fy Re mote Sessi on s.
10. Veri fy the TMON fo r CI CS N aviG ate connection.
11. Verify the TMON for DB2 NaviGate connection.
This section includes step-by-step instructions to execute the IVP.
Complete the steps in the order they appear. These steps can be
run during one TMON for MVS sessio n.
1. Ve rify the Syst em Se lecti on Menu.
The System Selection Menu is the first screen displayed after you
log onto TMON for MVS and e nter yo ur user I D and p asswo rd.
a. Cursor-select a TMON for MV S syst em to disp lay the
Primary Menu.
b. To choose an opti o n from the Primary Menu , comp lete one of
the following steps.
The Monitor for MVS 2.0 1-1
System Administrator’s Guide

IVP Steps Chapter 1: Inst allation Verificati on Proc edure
◊ Enter the option number in the SELECTION field.
◊ Cursor-select the op tion number.
◊ Enter =n, where “n ” is the option n u mber.
2. Veri f y t h e Activity Mo n i tor.
a. Select Option 1, Acti vi ty Monitor, from the Primary Menu to
display the Activity Monitor Menu.
b. Select Option 1, System Activity, to display the System
Activity Monitor Menu.
c. S elect O pt ion 1, C PU Act ivity Displ ay, to display the CPU
Activity Display screen. It presents statistics describing the
mix of wo r k an d I / O activity cur rentl y e xe cu ti n g. The
execution status of the workload on the system and
perfor mance s tatistics fo r each pro c essor in the ph ysical
configuration are also displayed.
d. Press END or the PF3 k ey to return to th e Syste m Act iv it y
Monitor Menu.
e. Select Option 8, Expa nded Stora ge Activity, to display the
Expanded Stora g e Activity screen. Press ENTE R to displ ay
statistics. This screen sh ows how yo ur e xp and e d sto r ag e is
being used. It measures both allocati on a nd act ivit y to a nd
from ex panded s t or a ge.
f. Press END or the PF3 k ey twi ce to return to th e Acti vity
Monitor Menu.
g. S elect O pt ion 2, Workload Monitor, to display the Workload
Monitor Menu.
h. Select Opt ion 1, Workload Service Activity, to display the
Workload Serv i c e A ctivi ty s c reen . It provid es an over view
of resource consum ption and respon se t ime i nformation for
each workload defined to TMON for MVS.
i. P ress EN D or th e PF3 k ey twi ce to return to th e Acti vity
Monitor Menu.
j. Select Option 3, Job Execution Monitor, to display the Job
Execution Monitor screen. It displ ays syst emwide
statistics, the current status, and resource use of all jobs
shown.
k. Cursor-select a jo b n am e to di spla y the J ob D e tail Se lection
Menu.
l. P ress EN D or th e PF3 k ey twi ce to return to th e Acti vity
Monitor Menu.
m. Select Option 4, Virtual Storage Monitor, to display the
Virtual Storage Monitor Menu.
n. Select Option 4, Common Storage Monitor, to display the
Common Storage Monitor Menu.
1-2

Chapter 1: Installation Verification Procedure IVP Steps
o. Select Option 5, Common Storage Summary, to display the
Common S torage Summ ary scree n . It sh ow s i n formation
about the allocation and use of c ommon storage areas.
p. Press END or the P F3 k ey three tim es to return to the Act iv ity
Monitor Menu.
q. Sele ct O ption 5, Pe rforma nce Param eters, to di splay the
Performance Parameters Menu.
r. Select O ption 2, Lo g ical Sw ap Co nsta nts, t o displ ay the
Logical Sw ap Co n sta n ts screen. It shows t h e thresholds
and measurements that SRM uses to control logical
swapping.
s. Press END or the P F3 k ey twi ce to return to th e Activi ty
Monitor Menu.
t. Select Opt ion 6, I/ O Monito r, to display the I/O Monitor
Menu.
u. Select Option 4, LC U Activi ty Moni tor, to display the LCU
Activity Monitor screen. It provides an overall view of I/O
activity on yo ur system by LC U.
v. Enter MAINMENU or = on the command lin e t o return to th e
Primary Menu.
3. Ve rify the Exce ption M onitor.
a. Select Option 2, Exception Monito r, from the Primary Menu
to display the Ex cepti o n Moni to r Menu .
b. Select Option 5, Threshold Recommendation Utility, to
display the Threshold Recommendati on Ut ility screen. You
can use this screen to analyze your site’s performance data
to determine suggested thresho ld valu es t hat c orrespond t o
the percentiles you specified for each exception severity
level.
c. Enter MAINMENU or = on the command line to return to the
Primary Menu.
4. Ve rify the G raphic Mo nitor.
a. Select Option 3, Graphic Monit or, from the Primary Menu to
display the Graphic Monitor screen. It provides a snapshot
of the acti vity on you r sy st em .
b. Cursor-select the CPU BUSY field to display the CPU Activi ty
Display screen.
c. Ent er MAINMENU or = on the command l i ne t o return to the
Primary Menu.
5. Verify Collection Analysis.
a. Select Option 4, Collection Analysis, from the Primary Menu
to di splay th e C ollec tion Analysis Graphi c Review s c reen.
It shows resource consumption and TSO first period
response time.
The Monitor for MVS 2.0 1-3
System Administrator’s Guide

IVP Steps Chapter 1: Inst allation Verificati on Proc edure
b. Cursor-select the CPU BUSY field to displa y the CPU Hi st ory
Activity Menu.
c. Ent er MAINMENU or = on the comm and l i ne t o return to the
Primary Menu.
6. Ve rify Supertrac e.
a. Select Option 5, Supertrace, from the Primary Menu to
display the Supertrace Menu.
b. S elect Option 4, System Memory Profile, to display the
System Memory Profile screen. It shows information on
storage usage by address spac e during t he las t in terv al.
c. Ent er MAINMENU or = on the comm and li n e t o return to th e
Primary Menu.
7. Verify Utilities.
a. Select Option 6, Utilities, from the Primary Menu to display
the Utilities Menu.
b. Select Optio n 1, S y ste ms S erv ic es, to display the Sy ste ms
Services Menu.
c. Select Option 1, APF Utility, to display the APF Utility screen.
It shows th e data set name and volume se rial n umb er o f
every currently authorized library in the APF list.
d. Enter MAINMENU or = on the command line t o return to th e
Primary Menu.
8. Verify the Delay Monitor.
a. Select Option 7, Delay Monitor, from the Primary Menu to
display the Delay Monitor Menu.
b. S elect O ption 1, Delay Analysis Summary, to display the
Delay Analysis Summary screen. It shows a breakdown of
delay activity by job.
c. Enter MAINMENU or = on the command line t o return to th e
Primary Menu.
9. Verify Remot e Sessi ons.
a. Select Option S, System Administration, from the Primary
Menu to display the System Administration Menu.
b. S elect O ption 1, Remot e Sessions, to di splay the Rem ote
Sessions Directory screen. It lists all Landmark products
defined in your network.
Review each entry. If no changes are required, skip Steps c and
d.
c. If the VTAM definition shipped in the TMON for MVS
.INSTLIB has been modified by your site , ent er the p refix
characters of VTAM SLU names in the SLU APPLID
PREFIX field. (The shipped TMON for MVS default is
1-4

Chapter 1: Installation Verification Procedure IVP Steps
“TMV”). Your site-specified SLU APPLID PREFIX remains
on th e screen.
d. If the applids defining other Landmark Perfor manceWorks
MVS products have been modified at you r site, selec t the
appropriate line, overtype the applid, and cursor-select
ADD. You will receive the following message.
LMRK00904I RECORD WAS SUCCESSFULLY ADDED
If any other message is received, refer to The Monitor for MVS
Messages and Codes to determine the reason for the message
and the corrective ac ti on.
Repeat Step d for each entry tha t requires modificatio n.
e. Enter =A.1 on the com ma nd l ine to dis pla y the R emote
Sessions Lo gon scree n. You can use this sc reen to a cce ss an
applid of another Landmark product.
f. Cursor-selec t any line that refl ec ts a stat us of “ACTI V E ”. You
should be transferred to the selected Landmark
PerformanceWorks MVS product.
g. Press the PF3 key or enter LOGOFF on the command line to
return to the TMON f or MVS Re mo te Ses si ons Lo g on
screen.
10. Verify the TMON for CI C S Nav i Gate connection.
a. Enter =1.3 on the comma nd line to di sp l ay the Jo b Exec ut ion
Monitor screen.
b. Tab twice to position the cursor at the DISPLAY field, and
enter C. The display of active tasks is reduced to show only
CICS tasks.
c. Cursor-select any CICS t ask to display the Job D e tail Sel ect ion
Menu.
d. Select Option 11, NaviGate to CICS/DB2 Mo nitor, to display
the TMON for CICS Primary Menu.
e. Select Option 4, MVS Cont entio n Monito r, to display the MVS
Contention Monitor Menu.
f. Select Option 1, Ac ti ve Job Summ ary, to display the TMON
for MVS Job Execution Monitor screen.
g. Press the PF3 key to display the TMON for CICS MVS
Contention Monitor Menu.
h. Select Option 2, Deta iled Analysis, to display the TMON for
MVS Job Delay Analysis screen.
i. Press the PF3 key to display the TMON for CICS MVS
Contention Monitor Menu.
j. Enter =7 on th e co mm an d li n e to di sp la y th e T MON f or CICS
File/DB Analysis Menu.
The Monitor for MVS 2.0 1-5
System Administrator’s Guide

IVP Steps Chapter 1: Inst allation Verificati on Proc edure
k. S elect O pt ion 1, Fi le/DB Activi ty, to display the TMON for
CICS File/DB Activity Selection Menu.
l. Tab to the SUMMARIZE BY field, overtype the “1” with a “2”
and press ENTER. The TMON for CICS File/DB Activity
screen is displayed.
m. Cursor-select a ny act iv e vol ume liste d i n the VO LSER
column to display the Device Deta il Selection Me nu. The
following message appears on th e screen.
TMVS18879I - I/O PROFILE SUCCESSFULLY STARTED
Press ENTER.
Wait approxi matel y two mi n utes be fore proceeding t o the next
step unless the follow ing message appe ars on th e scree n .
TMVS09701I I/O PROFILE COMPLETED. TYPE =5.1 TO ACCESS PROFILE MENU
n. Enter =5.1 on the com ma nd line to di spl ay the TMON for
MVS Profile Status/Selection screen.
o. Cursor-select the completed I/O profile to display the I/O
Profile screen.
p. Enter KEEP on the command line. The following message
appears on the screen.
TMVS14002I - TRACE DATA IS NOW KEPT
q. Enter MAINMENU or = on the command line to display the
TMON for MVS Primary Menu.
r. Enter LOGOFF on the command line and p ress ENT ER to
return to the TMON for CICS File/D B Acti vity Dis play
screen.
s. Enter LOGOFF on the command line and press ENT ER to
return to the TMON f or MVS Jo b Ex ecuti o n Mon i to r screen.
At this point, all connections t o TMON f or CICS sho uld have be en
terminated au tom atically with th e reverse-v ideo n a me of th e
“current” monitor (bottom center of border) removed.
11. Ve ri fy t h e T M ON fo r DB2 NaviGa te co n nection.
a. Enter =1.3 on the comma nd line to di sp l ay the Jo b Exec ut ion
Monitor screen.
b. Tab twice to position the cursor at the DISPLAY field, and
enter D. The display of ac ti ve t asks is reduce d to s how
only DB2 tasks.
c. Cursor-select any DB2 task to display the Job Detail Selection
Menu.
1-6
d. Select Option 11, NaviGate to CICS/DB2 Mo nitor, to display
the TMON for DB2 Primary Menu.

Chapter 1: Installation Verification Procedure IVP Steps
e. Select Option 4, Ac tive J ob Summary, to display the TMON
for MVS Job Execution Monitor screen.
f. Press the PF3 key to display the TMON for MVS Primary
Menu.
g. Press the PF3 key to display the TMON for DB2 Primary
Menu.
h. Press the PF3 key to display the TMON for MVS Job
Execution Monitor screen.
At this point, all connections to TMON for DB2 should have been
terminated au tom atically with th e reverse-v ideo n a me of th e
“current” monitor (bottom center of border) removed.
i. Ent er LOGOFF on the command line to log off of TMON for
MVS.
The Monitor for MVS 2.0 1-7
System Administrator’s Guide

Chapter 1: Inst allation Verificati on Proc edure
1-8

Chapter 2: Security Definitions
You can secure access t o you r La n dma rk Performan c eWorks MVS
product and its individual f unc tions u sin g three different methods:
External Security, User Exit Security, and Internal Security. You
also can choose not to secure product functions at all . Use the
Security Definitions Menu to select the pa rti cular ty pe o f securi ty
you want.
External Security controls pro duct usage through IBM’s system
authorization facility (SAF), which transfers control to security
products such as RACF, CA-ACF2, and CA-TOP SECRET.
User Exit Security lets you create your own security sy ste m t hrough
user exits.
Internal Security controls product usage through screens described
in this chap ter. Please note that whi l e Inte rn al S ecuri ty p rovide s
complete protection of all secured functions, it does not produce an
audit trail. If your site requires an audit trail, use External Security
to protect acc ess to secured functions.
Landmark PerformanceWorks MVS products check sec urity in the
following two areas.
• User logon security controls the ability to log onto the product.
Resolving accidental access
problems caused by security
• Function security protects variou s p rodu ct f unctions. Only
specific fu n ctions of La nd ma rk Perfor manc eWorks MVS
products are secured, as defined on the Secured Functions
Directory screen. A complete list of secured functions is
provided later in this chapter.
Landmark PerformanceWorks MVS product s sup port ce rta in
combinations of Inte rnal, Exte rnal, User Exi t, a nd no secu rity for
user logon and function sec urity. For example, you might use
External Security to control user logon a cce ss a nd I nterna l Secu rity
to control access to functions. T h e foll ow ing ta b le i denti f ies the
valid security combinations.
User Logon Security
Type
External Yes Yes Yes Yes
User Exit Yes No Yes Yes
Internal Yes No Yes Yes
None No No No Yes
Key: Yes = a valid combination No = an invalid combination
Internal External User Exit None
If, while defining your system security, you find you cannot access
your system beca us e of the se cu rit y you ha ve est abl ish ed, you
must re s tore the pri m ary control reco rd (t he C reco rd) in the
control file. Use the sample JCL provided in the appropriate
member of your product sample library to do the restore. The
Funct ion S ec ur i ty Ty pe
The Monitor for MVS 2.0 2-1
System Administrator’s Guide
How Product Security Works Chapter 2: Security Definitions
following table identifies the sample library member you should
use for each Landmark PerformanceWorks MVS product.
Member S ampl e Lib ra ry
TCECRS TMON for CICS/ESA
TMON8CRS TMON for CICS/MVS
TDBCRS TMON for DB2
TDCCRS TMON for DBCTL
TMQCRS TMON for MQSeries
TMVRSTOR TMON for MVS
How Pr oduct Security Works
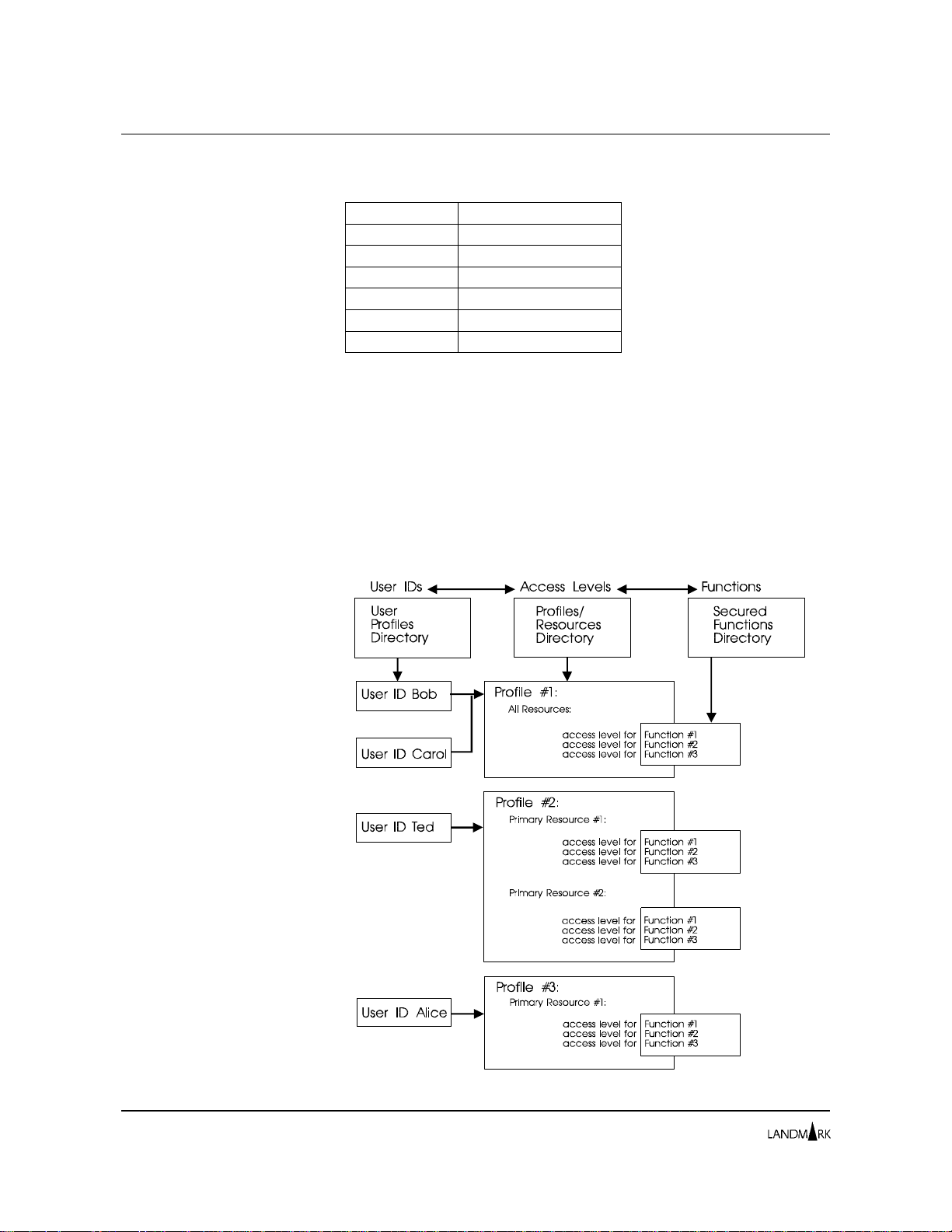
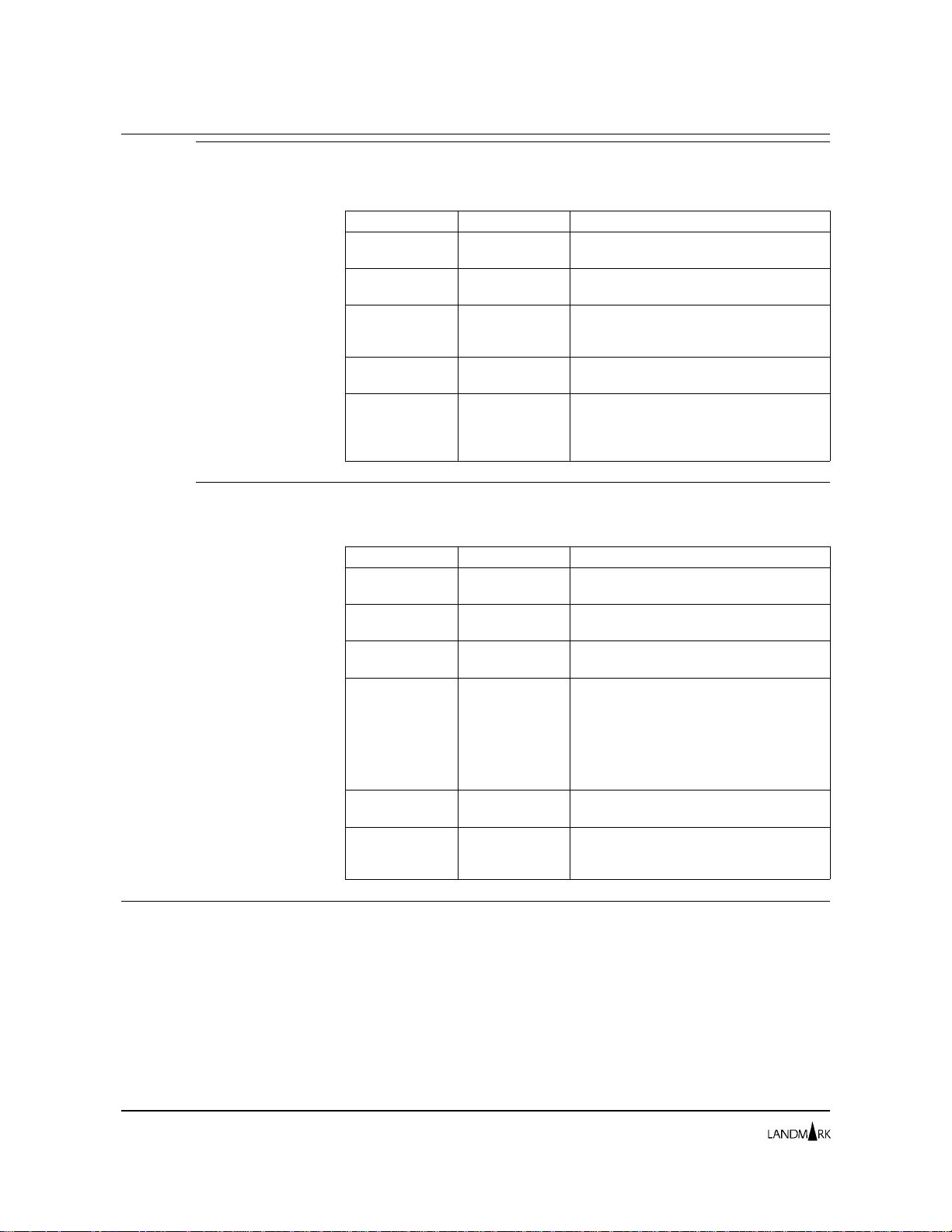
This section describes how product se cu rity c ompon ent s intera ct.
Figure 2-1 depicts the interaction of th e s ecurity components.
Users are authorized to use product functions through access levels
specified in profiles. Profiles e xp l ic it ly assign an a cce ss
(authorization) level for each secured function and supply values
for any required primary resources.
2-2
Figure 2 -1. S ec ur i ty c om p onents

Chapter 2: Security Definitions How Product Security Works
When a user tries to use a secured function, a security
authorization call is made to verify that the user has the necessary
security clearance. The following information is used in the
security check:
• Use r ID
• Password (for a sign-on attempt only)
• Function ID
• Acc ess, or aut horization, le vel (NON E, READ, UPDT, CNTL, or
ALTR) of the user ID for the function. Acce ss levels are
described in “Detail Profile Definition,” later in this chapter.
Some Landmark product functi ons require a primary reso urce or
both a p r i mary and a s econdary resource. These funct io n s are
generically referred to as resou rce functions. Functions that do no t
requir e re s ources are ca lled system functions.
• TMO N f or CI CS p rimary reso urces are job n ames; s eco nd ary
resources are not use d.
• TMON for DB2 pri m ary resou rces a re D B2 su b sy ste m n a mes;
secondary resources are DB2 plan names.
• TMON f or DB CT L primary resources are DBCT L subsystem
names; secondary resources are not used. (The primary
resource needed to a cce ss a DBC TL subsyste m i s the DBC T L
subsystem name; thereafter, it is the object name.)
• TMO N f or MQ Series pri mary resources are queue manager and
object names; secondary resources are not used. (The primary
resourc e n e ed ed to ac c ess a queue man ager is t h e queue
manager name; thereafter, it is t he objec t name.)
• TMON for MVS primary resources are job names or volume
serial numbers; s eco n dary reso urces are not us ed.
Primary and secondary resources qualify the security authorization
check. For functions specifying a primary resource, a security
check is made for the function with the specific primary resource.
(For TMON for DB2, if a secondary resource is specified, the
security check is m ade for th e fun ction with both the pri ma ry and
secondary resources.) Th e us er is restricted to using th e function
only for the resource(s) specified.
TMON for CICS example Supp os e y ou w an t t o restrict the job names displayed on th e Job
Selection List screen for a given user. In the following example,
only j ob s with jo b n a mes startin g with “DE V ” a n d “TE S T ” are
displayed on the Job Selecti on List screen for user I D SAMPLE.
User ID: SAMPLE
Password: Not needed for this se curity c heck
Function ID: JOBLIST
The Monitor for MVS 2.0 2-3
System Administrator’s Guide

Tracing Security Problems Chapter 2: Security Definitions
Access level: READ
Primary resource: DEV* and TEST*
Secondary resource: None
Tracing Security Problems
Regardless of whi ch ty p e o f secu ri ty you choose to imple men t
(External, Internal, or User Exit), you may need to trace security
processing and resolve a security problem. Landmark provides a
trace facility for Landma rk security p rocessing. To start the
security trace during product initialization, add the
TRACE=SECURITY parameter to the appropriate data set spec ifi ed
in your startup JCL, which is identified by the following ddnames:
• TMO NPRMS (for T MON for C ICS/ESA and TMON for
CICS/MVS)
• TMDBP R MS (for TMON for DB2)
• TDBCPRMS (for TMON for DBCTL)
• TMQ SPR MS ( for TMON for MQS eries)
• TMV S PRMS (for TMON for MVS)
Adding this parame ter a ctivates a security tra ce for I nte rn al
Security for the product. Ea ch ti m e a sec urity che ck i s ma de, t he
check is traced. Read about the da ta set in yo ur product
installation completion instructions in PerformanceWorks for MVS
and OS/390 Installat ion G u ide.
To activate the tra ce fa cility w hen th e p roduct is already ex ecuti ng ,
enter $TRACEON on the command li ne. To deactivate the trac e
facility once you have started it, enter $TRACEOFF on the
command line.
Using External Security
External Security links to an d u ses sec urity de fini tions specified by
external se cu rit y p rodu cts that use I BM’ s system autho riz ation
facility (SAF), such as RACF, CA-ACF2, and CA-TOP SECRET.
This discussion of Ext ernal Sec urity provides genera l inst ructions
for defining RACF security for yo ur Landmark PerformanceWorks
MVS product. CA-ACF2 inst ructio ns a re given in m emb er
ACF2DOC in the Strategic Services samp le library. CA-TOP
SECRET instructions are given in member TSDOC in the Strategic
Services sample library. If you do not have RACF, CA-ACF2, or
CA-TOP SECRET installed, you must set up corresponding
definitions using the security product you do have installed.
If you use External Securi ty to cont rol user lo gon a cce ss, y ou ca n
use any of the security types (internal, external , user exit, or none)
to control access to product funct ions. I f, howe ver, you choose to
2-4

Chapter 2: Security Definitions Using External Security
use External Securi ty fo r access to product func ti ons, y o u al so m u st
use External Security fo r log on acce ss.
If you want to use External S ecurity for l ogon an d In ternal or Use r
Exit Security for functions, you can bypass the RACF, CA-TOP
SECRET, and CA- AC F 2 i n struction s we supply. Read “Exte rn al
Security Simplified Sign-On,” later in this section.
Considerations when
switching to External Security
If you switch from I nte rn al Secu ri ty fo r product f u n ction s to
External Security without defining anythi ng to your exte rnal
security product, you will not b e able to a cce ss yo ur system. I f this
ha ppens, you m ust re store th e pr i mary co ntro l rec o rd (t he C
record) in the c ont rol f ile. Use the sam p le JCL given in the
appropriate member of yo ur product sa mpl e lib rary to do the
restore. Refer to the table provided earlier in this chapt er for the
member you should use for your Landmark PerformanceWorks MVS
product.
RACF Security To define RACF security for your product’s user logon and
functions, complete the following steps. Refer to your RACF
documentation for complete information on RACF processing.
1. Add $LMRKTMR to the RACF class desc riptor table .
Add the resource class, $LMRKTMR, to the RACF cla ss descrip tor
table (CDT). Then reassemble the table (see member
$RACFCDT in the Strategic Servi ce s samp le library ).
2. Add $LMRKTMR to the RACF router table.
Add two entries for the $LMRKTMR resource class to t h e RACF
router table, as shown in member $RACFRTB in the Strategic
Services sample library. Then reassemble the table.
To reduce the amount of ti me the product spends reading the
RACF data set, we recomme nd y ou p lace th e route r tabl e
entries dire ctly in the RACLIST.
3. Activate $LMRKTMR in RACF.
Enter the following RAC F c om man d to a ctivate the $LMRKTMR
resource class in RA CF.
SETROPTS CLASSACT($LMRKTMR)
4. Define your product user IDs to RACF.
If you have not already done so, define your product user IDs to
RACF.
Note When RACF passw ords are changed, they immedi atel y affect
product security.
5. Define a RACF general resource for pro duct logon.
Use the following model to define a RACF general resource for
user logon acce ss:
The Monitor for MVS 2.0 2-5
System Administrator’s Guide

Using External Security Chapter 2: Security Definitions
applid.SIGNON UACC(NONE)
where “applid” is the product application ID defined during
installation a n d “S IGNON” is the func tion n a me that controls
user access and log o n to the product. Review the fun cti o n code
table, later in this chapter, for more information about product
functions. The default user access level should be NONE (no
access to the product) , as sh ow n i n the UAC C p ara me ter in th e
model. Logon acce ss to the product is then co n trolled throu gh
RACF access lists.
6. Define a RACF general resource for e ach product functi on.
To control acces s to th e produ ct functions, use the fo llo wi n g model
to define a RACF general resource for each product function:
applid.function[.res1[.res2]] UACC(NONE)
where “applid” is the product application ID defined during
installation, “function” is th e functi on name, “res1” is the
primary resource specification (if any) for this security
definition, “res2” is the secondary resource specification (if
any) for this security definition, and the UACC parameter
specifies the access level for the function. You can specify
asterisks (*) as pattern matching characters for “res1” and
“res2.” The default user access level should be NONE (no
access to product fun ctions), as shown in th e UACC p a ram eter
in the model.
With Internal
Security for
Functions
You can find descriptions of all product functions, their applicable
resources, and their valid access levels in the function code and
the function ac ces s level tabl es, late r in t h is chap ter.
You can find $RACFGDF, a supplied CLIST program, in the
Strategic Services sa mpl e library. The CLIST creates a sample
set of RACF general resource definitions for product functions
and resources.
Once general resources are defined for all product functions, access
to them is controlled through RACF access lists.
7. Activate External Security for user l ogon ac ces s and acce ss t o
functions.
Enter X in both the USER LOGON and FACILITIES fields of the
Security Definitions Menu.
If you are using RACF t o secu re user logon acces s , you can use
Internal Securi ty or Use r Exi t S ecuri ty to control access to product
functions. If you choose to do this, ski p Step s 6 and 7 a nd p erform
the following steps instead. You also can use the External Security
simplified sign-on f eature desc ribed late r in t h is sec tion.
8. Define Internal Security profiles for your site.
Use the supplied profiles or create your own. Read “Using Internal
Security,” later i n thi s chapt er, for further information.
2-6
Chapter 2: Security Definitions Using External Security
9. Identify the profile that should be used by each pr oduct us er ID.
You can use two me th o d s to ide nti fy the p rofi le th a t sh ould be
used for each user ID.
a. For each product user ID defined to RACF, specify the
following RACF installation data in RACF:
LMRK(profile)
where “profile” is the name of an Internal Security profile.
b. Define each RAC F-defined user ID t o Inte rnal Security using
the Internal Security screens provided with your Landm ark
PerformanceWorks MVS product. Read “Using Internal
Security,” later in this chapter, for more information.
If you do not identify a profile for a user ID, your Landmark
PerformanceWorks MVS product uses the $DEFAULT profile,
which is distributed with eac h product.
10. Ac tivate External Security for user logon access and Internal
Security for access to functions.
Enter X in the USER LOGON f ield and a n I in the FACILITIES field
of the Security Def initions Menu. The following ta ble indica te s
how to access this menu from within each Landma rk
PerformanceWorks MVS product.
External Se cur it y
Simplified Sign-On
Implementation Perform these procedures only after you have consulted with the
Product To Gain Access to Menu:
=10.1 .7
TMON for CICS/ESA Enter
TMON for CICS/ESA screen.
TMON for CICS/MVS Enter
TMON for CICS/MVS screen.
TMON f or DB 2 Enter
TMON for DB2 screen.
TMON f or DB CT L Ent er
TMON f or DB CT L sc r ee n.
TMON for MQSeries Enter
TMON for MQSeries screen.
TMON f or MV S E nt er
TMON for MVS screen.
on the co mm and l i ne of any
=10.1 .9
on the co mm and l i ne of any
=8.1
on the c om ma nd line of an y
=9.1
on the c om ma nd line of an y
=8.1
on the c om ma nd line of an y
=S.2
on the c om ma nd line of an y
If you want to use External S ecurity for u ser logon ac ces s to your
Landmark PerformanceWorks MVS product, but use eithe r I nterna l
Security or User Exit Sec urity to co ntrol user access to product
functions, yo u c an u se the Ex terna l Secu rit y simp lif ied si g n-o n
feature. This feature lets you skip most of the RACF, CA-ACF2,
and CA-TOP SECRET instructions for set ti ng up ex terna l us er
logon security.
data center security personnel at your site. Complet e the fol lowing
steps to implement the External Security simplified sign-on feature.
The Monitor for MVS 2.0 2-7
System Administrator’s Guide

Using User Exit Security Chapter 2: Security Definitions
1. Ensu re th at IBM’s system author ization f ac i lity (SA F) is active .
SAF always is active if you are using RACF, but you may need to
perform a manua l s tep to ac ti vat e S AF wi th other software
packages. For example, to activate SAF in CA-ACF2, the SAF
bit needs to be turn e d on in the CA-ACF2 global system
options.
2. Define product user IDs to your external se curit y product.
If you have not already done so, define product user IDs to your
security product. Ref er to th e se curit y product documentation
for complete instructions.
3. Verify the logon access level of the $DEFAULT profile.
If you want to restrict a cce ss to a La ndmark product t o ce rta in user
IDs, ensure that the Landmark-supplied $ DEFAULT profile has
an access setting of NONE for the SIGNO N funct ion. Read
about product secured functions (incl uding the SIGN ON
function) in t he f unc ti on co de t ab le, l at er in th i s cha p ter. When
a user logs on, the system checks the user ’s profile to see if
SIGNON access is defined. If it is, the logon attem pt is
successful. If no profile can be found for the user, the Internal
Security $DEFAULT profile is used.
4. Activate the External Security simplified sign-on feature for
user logon access.
Enter S at the USER LOGON prompt on the Sec urity Defini tions
Menu. Note that you ca n not e nte r S at the FACILITIES prompt.
The External Security simplified sign-on feature is valid only
for control of user logon.
Once you have activated the simplified sign-on feature, all users
already defined to your external security pack age with va lid user
IDs and passw ords ca n log on to th e product. I f yo u want to allow
only a subset of these users to log on, you can control user logon
further using profiles and the SIGNON funct ion (as de scrib ed in
Step 3).
Using User Exit Security
You can create your own security system through user exits.
Member $USRXIT of the Strat egic Servi ces sa mpl e library cont ains
a sample se cu rit y user exit and sa mp l e J CL with w h ic h to a sse mble
and link the exit.
To implement User Exit Security, follow these steps:
1. Create the user exit.
Landmark PerformanceWorks MVS products point register 1 to
storage containing the information mapped in member
$USRPRMS of the Strategic Services sample library. Your user
exit should pass a return code in register 15. If the return code
is zero (0), access to the function i s grante d. If the return code
is a nonzero number, access to the function is denied.
2-8

Chapter 2: Security Definitions Using Internal Security
2. Specify the program name of your user exit i n the USER EXIT
startup parameter.
This parameter can be included in a data set or member that is
identified by the:
– TMONPRMS DD sta teme nt i n TMON for CICS/ESA and
TMON for CICS/MVS sta rtu p JCL
– TMDBPRMS DD statement in TMON for DB2 startup JCL
– TD BCPRMS DD statement in TMO N f or DBCTL
– TMQSPRMS DD statement in TMO N for MQS eries startu p
JCL
– TMVSPRMS DD statement in TMON for MVS s tartup J CL.
TMON for DB2 example //TMDBPRMS DD *
USEREXIT=name
If you specify a USEREXIT program name that the product cannot
find when it starts up, an S806 abend occ urs.
3. Stop and restart the product.
Shut down and restart t he produc t.
4. Activate Us er Exit S ecurity.
Depending on whether you are using User Exit Security to control
user logon access or access to f u n cti ons, enter U in either the
USER LOGON field or the FACILITIES field, or both. Check
the user logon/function security type table at the beginning of
this chapter to be sure you are using valid combinations of
security types f or the se two fie lds . If no u se r ex it program h as
been specified in the USEREXIT startup parameter, an error
occurs indicating you have selected an invalid security
combination.
Using Internal Security
You can use the Internal Security system supplied with your
Landmark PerformanceWorks MVS product to s ecure user logon
access and acc ess to p roduct functions. If you use In te rnal Se cu rity
to secure logon access, y ou ca n not use Exte rnal S ecuri ty to secure
product functions. If you use In ternal Se curit y to secure access to
functions, y o u m ust secure logon access. You can use any of the
methods describ ed in th i s cha p ter t o se cure log on a cce ss.
Internal Security is defined through the sc reens describ ed in the
rest of this chapter.
Do you require audit trails? While Internal Security provides compl ete protec tion of all secured
functions, it do es n ot produce a n audi t tra il. If you r si te requires
an audit trail, use Exte rnal Secu rity to p rotect access to secured
functions.
The Monitor for MVS 2.0 2-9
System Administrator’s Guide
Using Internal Security Chapter 2: Security Definitions
Supplied User IDs and
Profiles
Change the supplied
passwords.
Internal Security is distribute d with a predefined maste r user ID
and password for each Landmark PerformanceWorks MVS product.
The follo wi ng table lists the master user I D and password provided
for each product.
Product User ID Password
TMON for CI CS /ES A TMONC ICS TMONCI CS
TMON for CI CS /MV S TMONCI CS TMONCI CS
TMON for DB 2 T MO ND B2 TMOND B2
TMON for DB CT L TMO ND BC T MO ND BC
TMON for MQSeries TMONMQ TMONMQ
TMON for MV S TMONMVS TMONMVS
If you specify that user logon security should use Internal Security
(by setting the USER LOGON f ield on t h e Security Def init ions
Menu to I), the master user ID can access product Internal Security
screens.
Internal Security for each p roduct also is distri buted with a
predefined s et of g eneric auth orization profiles an d user ID s . E ach
of the profiles begins with the dollar sign character ($) and ca n be
used as a template for definition of site-specific pro files.
If you choose to use Internal Security, once you have installed the
Landmark PerformanceWorks MVS product, change the passw ord
for the master user ID and these other pro duct-supplied user IDs.
When pass words are changed, they immedi ately affect prod u ct
security.
2-10
TMON for CICS The following table lists the supplied user IDs and profiles for
TMON for CICS/ESA and TMON for CICS/MV S .
User ID Profile ID Description
APPROG $DEFAULT User ID and default profile ID for an
AUTOSTRT $AUTOSTR User ID and default profile ID for an
SYSADMN $SYSADMN User ID and default profile ID for a
SYSPROG $SYSPROG User ID and default profile ID for a
applications programmer.
automatically started terminal. Read
“Chapter 13: Cross System Monitor
Administration” in
Refere nc e Ma nu al
Perf orma nc e M on it o r au tom at i c s tar ts .
Do not mod i fy th is us er I D an d p ro fil e
ID. If you do, Performance Monitor
automatic starting will not work.
system administrator.
systems programmer.
The Monitor for CICS
for a de scr ip t io n of
Chapter 2: Security Definitions Using Internal Security
User ID Profile ID Description
TMONCICS $MASTER Master user ID and default profile ID.
This profile grants user ID TMONCICS
the ability to do everything in TMON for
CICS/ESA. Do not change or delete
this user ID and profile. This ensures
that you al wa ys can up da t e yo ur
Internal Security definitions.
TMON for DB2 The following table lists the supplied user IDs and profiles for
TMON for DB2.
User ID Profile ID Description
APPPROG $DEFAULT User ID and default profile ID for an
AUTOSTRT $AUTOSTR User ID and default profile ID for an
DBADM $DBADM User ID and default profile ID for a
SYSADM $SYSADM User ID and default profile ID for the
SYSPROG $SYSPROG User ID and default profile ID for a DB2
TMONDB2 $MASTER Master user ID and default profile ID.
applications programmer.
automatically started terminal. Do not
modify this user and profile ID. If you
do, autostart capabilities are disabled.
database administrator.
TMON for DB2 system administrator.
systems programmer.
This profile grants user ID TMONDB2
the ability to do everything in TMON for
DB2. Th is en su r es that yo u al w ays ca n
update your Internal Security definitions.
TMON for DBCTL The following table lists the supplied user IDs and profiles for
TMON for DBCTL.
User ID Profile ID Description
APPPROG $DEFAULT User ID and default profile ID for an
AUTOSTRT $AUTOSTR User ID and default profile ID for an
DBADM $DBADM User ID and default profile ID for a
SYSADM $SYSADM User ID and default profile ID for the
SYSPROG $SYSPROG User ID and default profile ID for a
TMONDBC $MASTER Master user ID and default profile ID.
The Monitor for MVS 2.0 2-11
System Administrator’s Guide
applications programmer.
automatically started terminal. Do not
modify this user and profile ID. If you
do, autostart capabilities are disabled.
database administrator.
TMON for DBCTL system administrator.
DBCTL systems programmer.
This profile grants user ID TMONDBC
the ability to do everything in TMON for
DBCTL . Th is en su r es that yo u al way s
can update your Internal Security
definitions.
Using Internal Security Chapter 2: Security Definitions
TMON for
MQSeries
The following table lists the supplied user IDs and profiles for
TMON for MQSeries.
User ID Profile ID Description
APPPROG $DEFAULT User ID and default profile ID for an
applications programmer.
MQADM $MQADMIN User ID and default profile ID for an
MQSeries administrator.
SYSADM $SYSADM User ID and default profile ID for the
TMON for MQSeries system
administrator.
SYSPROG $SYSPROG User ID and default profile ID for an
MQSeries systems programmer.
TMONMQ $MASTER Master user ID and default profile ID.
This profile grants user ID TMONMQ the
ability to do everything in TMON for
MQSeries.
TMON for MVS The following table lists the supplied user IDs and profiles for
TMON for MVS.
User ID Profile ID Description
$DEFAULT $DEFAULT User ID and default profile ID for an
$SYSADMN $SYSADMN User ID and default profile ID for a
$SYSPROG $SYSPROG User ID and default profile ID for a
$UPERMAN $UPERMAN Master user ID and default profile ID.
$SECURITY $SECURITY User ID and default profile ID for the
$DBADMIN $DBADMIN User ID and default profile ID for the
applications programmer.
system administrator.
systems programmer.
This profile grants user ID $UPERMAN
the ability to do everything in TMON for
MVS. Th is en su r es that yo u al w ays ca n
update your Internal Security definitions,
do not change or delete this user and
profile ID (except the user ID password).
security administrator.
TMON for MVS control file data
administrator.
Implementing Internal
Security
2-12
To activate Inte rnal S ecuri ty at you r si te, fol low th e se steps:
1. Define Internal Security profiles for your site.
Use the supplied profiles or create your own. Read
“Profiles/Resources Directory” and “Detail Profile Definition,”
later in this chapter, for further information on adding,
updating, and deleting profiles.

Chapter 2: Security Definitions Using Internal Security
2. Define your product users to Internal Sec urity.
Use the supplied user IDs or add your own. Read “User Profiles
Directory” and “User Definition,” later in this chapter, for
further information on adding, updating, and deleti ng user IDs.
3. Activate I nternal Se c urity.
Depending on whether you are using Internal Security for user
logon acc ess or access to func t io n s, e n ter I in eithe r the USER
LOGON or the FACILITIES fields (or both) of the Secu rit y
Definitions Menu. Check the user logon/function security type
table at the be ginni ng of th is ch a pt er to b e sure you are using
valid combinati ons o f securi ty ty p es for t h ese tw o fiel ds.
All the parameters o n the I nte rn al S ecuri ty scree ns are st ored in
records in the product control file. To update the control file once
you have modified the parameters on a screen, you must
cursor-select the ADD, UPDATE, or DELETE field. Cursor-select
the ADD field to add a record to the control file, the UPDATE field
to update a record, and the DELETE field to delete a record. If you
do not cursor-select one of these fields, no modifications are made to
the control file. Read the description of each screen to fully
determine how and when to use the ADD, UPDATE, and DELETE
fields.
The Monitor for MVS 2.0 2-13
System Administrator’s Guide
Security Definitions Menu Chapter 2: Security Definitions
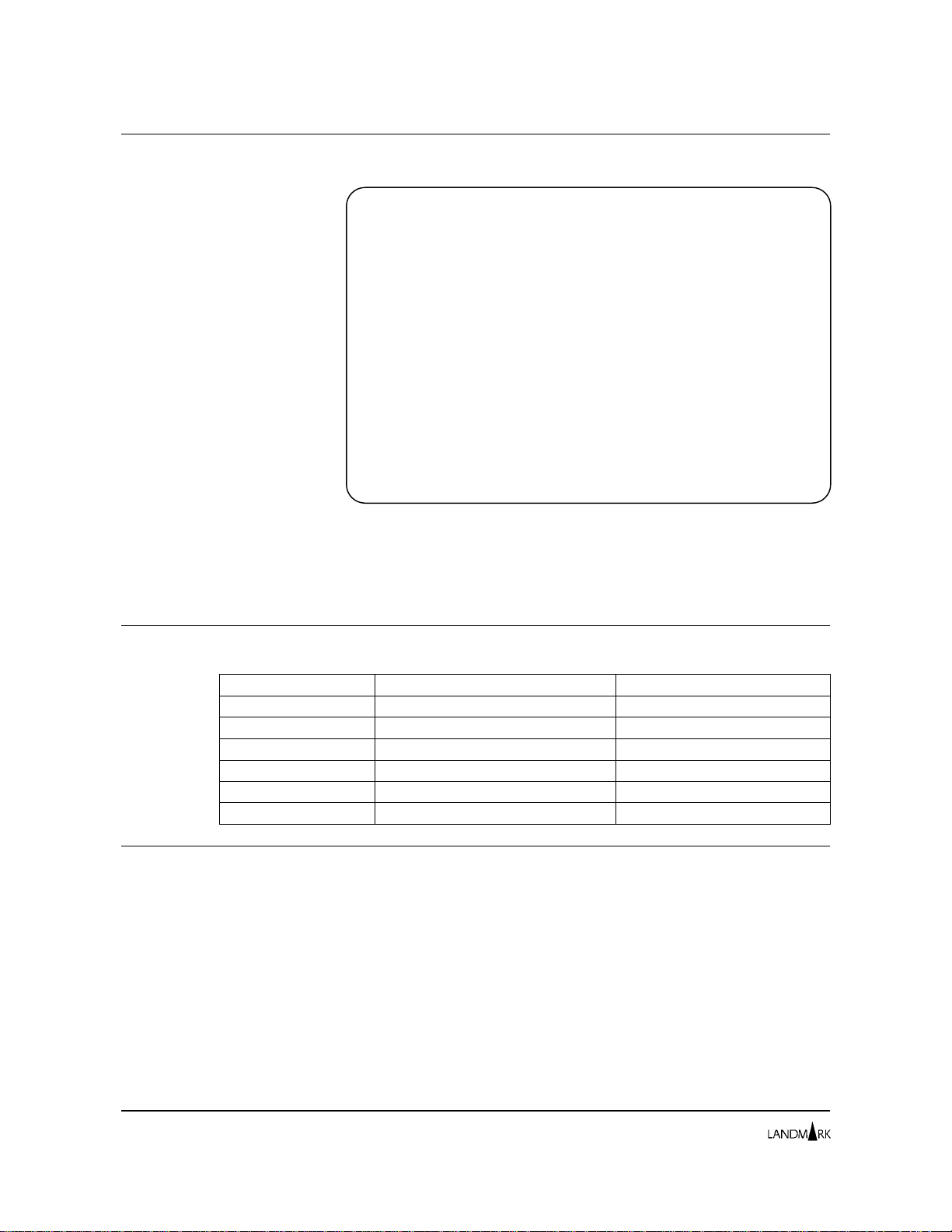
Security Definitions Menu
JOBNAME: THE MONITOR FOR MVS DATE:
SYSID : VERSION: 2.0 TIME:
SECURITY DEFINITIONS MENU
CYCLE MMSS SELECTION
MAXIMUM USERS: 127 CURRENT USERS: 012
1 USER PROFILES DIRECTORY
2 SECURED FUNCTIONS DIRECTORY
3 PROFILES/RESOURCES DIRECTORY
SECURITY METHOD ACTIVE: (I,X,S,U,N)
USER LOGON: N
FACILITIES: N
HELP INFORMATION = PF1 PF KEY ASSIGNMENTS = PA1
The Security Def initi o ns Menu l et s you sp ec ify th e t ype of security
you want to use for logon access to your Landmark
PerformanceWorks MVS product. You also can select product
Internal Security serv ic es from this s creen.
Accessing this Screen To access this screen, complete one of the following paths.
Produc t Action Displays
=10.1.7
TMON for CICS/ESA On the command line, enter
TMON for CICS/MVS On the command line, enter
TMON fo r D B2 On the co mm and l in e, en t er
TMON fo r D BC TL O n t he co mm an d l in e, en t er
TMON for MQSeries On the command line, enter
TMON fo r M VS On the co mm an d l ine, en t er
. S ecur i ty De fi n iti on s M en u
=10.1.9
. S ecur i ty De fi n iti on s M en u
=8.1
. S ec uri ty Defi n it ion s M en u
=M.1
. Secur i ty De fi n iti on s M en u
=8.1
. S ec uri ty Defi n it ion s M en u
=S.2
. S ecur i ty Defi n it ion s M en u
Options 1 USER PROFILES DIRECTORY
Displays all authorized user IDs for your product and their profile
assignments. Use this option to add, chan ge, or delete user
definition s. These include user I D p as swo rds a nd p rofi le se tti n g s.
2 SECURED FUNCTIONS DIRECTORY
Displays the functions that are secured in your product.
3 PROFILES/RESOURCES DIRECTORY
Displays all currently defined Internal Se curit y profiles and thei r
qualifying resources for your product. Use this option to add,
change, or delete profile definiti ons a nd the ir associated resources.
2-14
 Loading...
Loading...