Konica Minolta 4514-7706-02 User Manual

4514-7706-02
User Manual
Scanner Mode

Contents
Contents
1 Introduction
1.1 Welcome ........................................................................................1-1
Trademark Acknowledgements ..................................................1-1
1.2 Precautions....................................................................................1-2
1.2.1 General precautions ...................................................................1-2
1.2.2 User Instructions.........................................................................1-3
For the U.S.A. Users ..................................................................1-3
For Canada Users ......................................................................1-3
For European Users ...................................................................1-4
For Users of the Class B regulation’s countries .........................1-4
For Users except the Class B regulation’s countries..................1-4
Precautions for using network applications ................................1-5
Functions that cannot use network applications.........................1-5
1.3 Check for Enclosed Accessories ................................................1-7
2Overview
2.1 Scan to E-mail ...............................................................................2-1
2.2 Scan to Server (FTP).....................................................................2-2
2.3 Scan to PC (FTP)...........................................................................2-4
2.4 Scan to HDD ..................................................................................2-5
2.5 Internet Faxing ..............................................................................2-6
2.6 IP Address FAX (LAN-FAX)..........................................................2-7
2.7 Scan to PC (SMTP)........................................................................2-8
2.8 IP Scanner......................................................................................2-9
2.9 Document Forwording/Archive Distribution ............................2-10
2.10 Network Fax Transmission ........................................................2-11
2.11 Environments for Transmitting Scan Data ...............................2-12
Required environment ..............................................................2-12
Scanner Mode i

3 Preparation
3.1 LAN Connection ........................................................................... 3-1
Connecting the LAN cable ......................................................... 3-1
3.2 Network Settings .......................................................................... 3-3
3.2.1 List of Network Settings ............................................................. 3-3
Copier domain name and registering with a DNS server........... 3-6
3.2.2 Specifying Network Settings ...................................................... 3-7
Displaying the Network Settings screen .................................... 3-7
Basic Settings screen ................................................................ 3-9
DNS Settings screen................................................................ 3-10
Specifying the device name ..................................................... 3-11
SMTP Settings screen ............................................................. 3-12
POP3 Settings screen.............................................................. 3-13
Mail/Scan Setting (E-mail Mode) screen.................................. 3-14
Mail/Scan Setting (Scan Mode) screen.................................... 3-16
Scanner Settings screen.......................................................... 3-18
Registering an FTP site ........................................................... 3-20
Specifying a proxy.................................................................... 3-24
LDAP Setting screens.............................................................. 3-25
Frame Type Setting ................................................................. 3-26
Ping.......................................................................................... 3-26
3.2.3 Using PageScope Light ........................................................... 3-28
Accessing PageScope Light .................................................... 3-28
Operation ................................................................................. 3-29
Logging in Administrator mode ................................................ 3-30
Selecting the Display Language .............................................. 3-31
Penalty for Incorrect Attempts to Access Administrator
Mode ........................................................................................ 3-32
Allowing Administrator mode to be accessed again ................ 3-32
3.2.4 Using the Domain Name Buttons............................................. 3-33
Programming a domain name button....................................... 3-33
Using the domain name buttons .............................................. 3-35
3.2.5 Installing the Utilities ................................................................ 3-36
Utilities disk .............................................................................. 3-36
Installing IP Scanner (Windows Me, 98/95, XP, 2000 and
NT4.0) ...................................................................................... 3-36
Uninstalling (Windows Me, 98/95 and NT4.0).......................... 3-41
Uninstalling (Windows XP and 2000)....................................... 3-42
Contents
ii Scanner Mode

Contents
4 Performing a Scan to E-Mail Operation
4.1 Basic Transmission ......................................................................4-1
If the transmission could not be completed ................................4-3
4.2 Selecting a Recipient From the List on the One-Touch
Screen ............................................................................................4-5
4.3 Selecting a Recipient by Searching for It by Name ...................4-6
4.4 Selecting a Recipient Through an LDAP Search .......................4-8
When typing in directly ...............................................................4-8
When registering one-touch keys.............................................4-11
4.5 Typing In the Number of the One-Touch Key for the
Recipient......................................................................................4-15
4.6 Registering a Recipient ..............................................................4-16
Registering indexes..................................................................4-16
Registering one-touch keys ......................................................4-19
4.7 Changing/Deleting Recipients ...................................................4-22
4.8 Copying a One-Touch Key .........................................................4-23
4.9 Specifying the Scanning Options..............................................4-25
4.9.1 Quality & Reduction Screen .....................................................4-25
Quality tab ................................................................................4-25
Contrast tab..............................................................................4-25
Reduction/Area tab...................................................................4-26
4.9.2 FAX Menu Screen ....................................................................4-27
Network tab ..............................................................................4-27
4.10 Inserting Text Into a Transmission Document.........................4-29
5 Performing a Scan to Server (FTP) Operation
5.1 Basic Transmission ......................................................................5-1
5.2 Registering a Recipient ................................................................5-3
5.3 Changing/Deleting Recipients .....................................................5-7
5.4 Specifying the Scanning Options................................................5-8
5.4.1 Quality & Reduction Screen .......................................................5-8
Quality tab ..................................................................................5-8
Contrast tab................................................................................5-8
Reduction/Area tab.....................................................................5-9
5.4.2 FAX Menu Screen ....................................................................5-10
Network tab ..............................................................................5-10
5.5 URL Report ..................................................................................5-11
Scanner Mode iii

6 Performing a Scan to PC (FTP) Operation
6.1 Basic Transmission...................................................................... 6-1
6.2 Registering a Recipient................................................................ 6-3
6.3 Changing/Deleting Recipients..................................................... 6-6
6.4 Specifying the Scanning Options ............................................... 6-7
6.4.1 Quality/Reduction Screen .......................................................... 6-7
Quality tab.................................................................................. 6-7
Contrast tab ...............................................................................6-7
Reduction/Area tab ....................................................................6-8
6.4.2 FAX Menu Screen...................................................................... 6-9
7 Performing a Scan to HDD Operation
7.1 Basic Transmission...................................................................... 7-1
7.2 Registering a Recipient................................................................ 7-3
Creating a mail box (PageScope Light) ..................................... 7-3
7.3 Changing/Deleting Recipients..................................................... 7-7
7.4 Specifying the Scanning Options ............................................... 7-8
7.4.1 [Quality&Reduction Screen]....................................................... 7-8
Quality tab.................................................................................. 7-8
Contrast tab ...............................................................................7-8
Reduction/Area tab ....................................................................7-9
7.4.2 FAX Menu Screen.................................................................... 7-10
Network tab.............................................................................. 7-10
7.4.3 Specifying the File Storage Life ............................................... 7-11
7.5 Retrieving Scan Data.................................................................. 7-12
Retrieving Scan Data Using PageScope Light ........................ 7-12
Retrieving Scan Data by TWAIN.............................................. 7-13
Installing the TWAIN driver ...................................................... 7-13
Retrieving scan data ................................................................ 7-14
7.6 URL Report.................................................................................. 7-16
7.7 Penalty for Incorrect Attempts to Access a Mail Box ............. 7-17
Allowing a mail box to be accessed again ............................... 7-17
Contents
iv Scanner Mode

Contents
8 Performing an Internet Fax/IP Address FAX Operation
8.1 Basic Transmission ......................................................................8-1
8.2 Selecting a Fax Program ..............................................................8-4
8.3 Registering a Recipient ................................................................8-5
8.3.1 Registering as a One-Touch Key ...............................................8-5
For an Internet fax ......................................................................8-5
For an IP address fax .................................................................8-8
8.3.2 Registering as a Fax Program..................................................8-11
8.4 Changing/Deleting Recipients ...................................................8-15
8.5 Specifying the Scanning Options..............................................8-16
8.5.1 Quality&Reduction Screen .......................................................8-16
Quality tab ................................................................................8-16
Contrast tab..............................................................................8-16
Reduction/Area tab...................................................................8-17
8.5.2 FAX Menu Screen ....................................................................8-19
Functions that can be specified from the FAX Menu screen....8-19
Specifying FAX Menu settings..................................................8-22
Specifying the transmission source name................................8-23
Specifying whether the destination name is inserted ..............8-24
Specifying the setting for the “TX Report” parameter...............8-24
Specifying the 2in1 transmission setting ..................................8-25
Specifying double-sided transmission settings.........................8-26
Specifying the rotation transmission setting .............................8-27
Specifying the priority transmission setting ..............................8-27
Specifying the timer transmission setting .................................8-28
Specifying TX Marker (optional) ...............................................8-29
Specifying the Subject setting ..................................................8-29
Specifying the Reply setting .....................................................8-30
Specifying the file name setting................................................8-31
8.6 Transmitting to Multiple Recipients
(Broadcast Transmission)..........................................................8-32
Specifying using the one-touch keys........................................8-32
Specifying using 10-key Dialing screen....................................8-32
Specifying using a fax program ................................................8-33
Checking the results of the broadcast transmission.................8-34
8.7 Transmitting Using a Combination of One-Touch Keys and
Manual Input (Chain Dialing)......................................................8-35
Using the one-touch keys.........................................................8-35
By typing in the address ...........................................................8-36
8.8 Inserting Text Into a Transmission Document .........................8-37
Registering text.........................................................................8-39
Scanner Mode v

8.9 Checking Transmission Results............................................... 8-40
If an error e-mail message is received..................................... 8-41
Checking the operating functions............................................. 8-42
Checking Transmission Results............................................... 8-43
Checking Reception Results.................................................... 8-44
8.10 Receiving Documents (POP3 Reception)................................. 8-45
Receiving Internet faxes .......................................................... 8-45
Manually receiving faxes.......................................................... 8-45
Receiving an IP address fax .................................................... 8-46
8.11 Requesting/Returning the Activity Report ............................... 8-47
Conditions for sending a result notification .............................. 8-47
Full mode compatibility ............................................................ 8-47
8.12 Printing the Header Information in the Received Document.. 8-48
9 Performing a Scan to PC (SMTP) Operation
9.1 Basic Transmission...................................................................... 9-1
9.2 Registering a Recipient................................................................ 9-3
9.3 Changing/Deleting Recipients..................................................... 9-6
9.4 Specifying the Scanning Options ............................................... 9-6
9.4.1 Quality & Reduction Screen....................................................... 9-6
Quality tab.................................................................................. 9-6
Contrast tab ...............................................................................9-7
Reduction/Area tab ....................................................................9-7
9.4.2 FAX Menu Screen...................................................................... 9-9
Network tab................................................................................ 9-9
Contents
10 Using IP Scanner
10.1 IP Scanner ................................................................................... 10-1
Using a dial-up router............................................................... 10-2
Using a modem or terminal adapter......................................... 10-2
10.2 IP Scanner Window and Dialog Boxes ..................................... 10-3
Main window ............................................................................ 10-3
Main window (menu bar).......................................................... 10-5
Scanner Settings dialog box .................................................... 10-8
Sort Settings dialog box......................................................... 10-11
Divided Settings dialog box.................................................... 10-14
Notify Settings dialog box ...................................................... 10-17
ViewWindow .......................................................................... 10-20
vi Scanner Mode

Contents
10.3 Basic Transmission ..................................................................10-21
Programming the scanner button (from the computer)...........10-21
Scanning documents (from the copier)...................................10-24
Viewing the scanned image (from the computer)...................10-25
11 Distribution of Fax Documents
11.1 Specifying the Setting ................................................................11-1
F codes.....................................................................................11-1
11.2 Forwarding a Received Fax to IP Scanner................................11-3
11.3 Forwarding to IP Scanner...........................................................11-4
11.4 Sending a Fax to a Recipient .....................................................11-5
12 Network Fax Transmission
12.1 Network FAX Utility.....................................................................12-1
12.2 Operation .....................................................................................12-1
13 Specifying Management Settings
13.1 Specifying the Initial Screen ......................................................13-1
Specifying the setting ...............................................................13-4
13.2 Specifying the Initial Recipient Selection Screen....................13-5
Specifying the setting ...............................................................13-7
13.3 Viewing Counters (“Meter Count” Function)..........................13-10
“Meter Count” Function...........................................................13-10
Viewing counters ....................................................................13-11
13.4 Displaying the Administrator Management screen ...............13-12
Displaying the Administrator Management screen.................13-12
13.5 Specifying the Date and Time..................................................13-13
Setting the date and time........................................................13-13
Setting the time zone..............................................................13-14
Setting the Daylight Saving Time ...........................................13-16
13.6 Specifying the Language of the Reports and the
Transmission Source Name.....................................................13-17
Specifying the setting .............................................................13-17
13.7 Programming the Transmission Source Name......................13-18
Registering the transmission source name ............................13-18
13.8 Specifying Network Settings for Accounts ............................13-20
Specifying the setting .............................................................13-21
Scanner Mode vii

Contents
13.9 Specifying Transmission Settings.......................................... 13-22
13.9.1 Transmission Settings............................................................ 13-22
13.9.2 Specifying Transmission Settings .......................................... 13-23
Specify the default resolution................................................. 13-23
Specify the default contrast.................................................... 13-24
Specifying the default communication mode ......................... 13-24
Specifying the default transmission mode ............................. 13-25
Specifying the default method for attaching the transmission
source name .......................................................................... 13-26
Specifying the default transmission source name.................. 13-27
Specifying the default rotation transmission setting............... 13-28
Specifying double-sided transmission settings ...................... 13-29
13.10 Specifying that Received Documents Not Be Printed
(“Memory Lock” Function) ...................................................... 13-30
Specifying the time to stop printing........................................ 13-30
Specifying the password to restrict printing ........................... 13-32
Starting printing manually ..................................................... 13-33
13.11 Specifying the procedure for received documents
(“Doc. Manage.” function) ....................................................... 13-34
For documents classified with “Public Document” ................. 13-35
For documents classified with “F-Code” ................................ 13-37
For documents classified with “Port”...................................... 13-40
13.12 Specifying Report Output Settings......................................... 13-42
Report settings....................................................................... 13-42
Specifying the setting for the “TX Report” parameter ............ 13-42
Specifying the setting for the “Activity Report” parameter...... 13-43
13.13 Specifying Software Switch Settings
(Machine Functions)................................................................. 13-44
13.13.1 Specifying Software Switch Settings...................................... 13-45
Specifying functions with [Bit Selection]................................. 13-45
Specifying functions with [HEX Selection] ............................. 13-46
13.13.2 Specifying Settings Concerning the Confirmation Screen
13.13.3 Specifying Settings Concerning Whether or Not There Is a
For Broadcast Transmissions (Mode 014)............................. 13-48
Setting during production ....................................................... 13-48
Specifying the setting............................................................. 13-48
Connected Telephone or a Received Date Report and Their
Formats (Mode 016) .............................................................. 13-49
Setting during production ....................................................... 13-49
Specifying the setting............................................................. 13-49
viii Scanner Mode

Contents
13.13.4 Specifies Settings Concerning Internet Faxing (Mode 350) ...13-50
Setting during production........................................................13-50
Specifying the setting .............................................................13-50
13.13.5 Specifying Settings Concerning the SMTP Transmission
13.13.6 Specifying Settings Concerning the SMTP Reception
13.13.7 Specifying Settings Concerning the POP3 Reception
13.13.8 Specifying Settings Concerning the Default Address Input
13.13.9 Specifying Settings Concerning the Timeout for a
13.13.10 Specifying Settings Concerning the Transmission Interval
13.13.11 Specifies Settings Concerning Full Mode Functions
Timeout (Mode 356) ...............................................................13-51
Setting during production........................................................13-51
Specifying the setting .............................................................13-51
Timeout (Mode 357) ...............................................................13-52
Setting during production........................................................13-52
Specifying the setting .............................................................13-52
Timeout (Mode 358) ...............................................................13-53
Setting during production........................................................13-53
Specifying the setting .............................................................13-53
Screen and the From Information for Accounts (Mode 366) ..13-54
Setting during production........................................................13-54
Specifying the setting .............................................................13-54
DNS Inquiry (Mode 367).........................................................13-55
Setting during production........................................................13-55
Specifying the setting .............................................................13-55
for Divided E-Mail Messages (Mode 372) ..............................13-56
Setting during production........................................................13-56
Specifying the setting .............................................................13-56
With Internet Faxing (Mode 373)............................................13-57
Setting during production........................................................13-57
Specifying the setting .............................................................13-57
14 Reports and lists
14.1 Checking the Transmission Status (Activity Report (TX)) ......14-1
Outputting the Transmission Activity Report ............................14-1
14.2 Checking the Reception Status (Activity Report (RX))............14-4
Outputting the Reception Activity Report..................................14-4
14.3 Checking the Registered One-Touch Keys
(One-Touch Key List)..................................................................14-7
Outputting the one-touch key list..............................................14-7
Scanner Mode ix

14.4 Checking the Details of Registered Fax Programs
(Fax Program List)...................................................................... 14-9
Outputting a fax program list.................................................... 14-9
14.5 Checking Account Information (Account List)...................... 14-11
Outputting an account list ...................................................... 14-11
14.6 Checking Secured Information for Each Account
(Account List (Security)).......................................................... 14-13
Outputting an account list (security)....................................... 14-13
14.7 Checking the Settings For Each Function (Settings List) .... 14-15
Outputting the settings list...................................................... 14-15
14.8 Checking the Forwarding Settings (Forwarding List)........... 14-17
Outputting the forwarding list ................................................. 14-17
15 Troubleshooting
15.1 When Certain Displays Appear ................................................. 15-1
15.1.1 Icons ........................................................................................15-1
POP reception.......................................................................... 15-1
POP3 reception error............................................................... 15-1
15.1.2 Administrator login ................................................................... 15-2
While registering the network................................................... 15-2
15.2 Transmission Results Error Codes .......................................... 15-3
Scan to Server (FTP) transmissions ........................................ 15-3
Scan to PC (FTP) transmissions.............................................. 15-4
Scan to HDD transmissions..................................................... 15-4
URL notification (with Scan to Server (FTP) and Scan to
HDD transmissions)................................................................. 15-4
Internet fax transmissions/Scan to E-mail transmissions......... 15-5
Internet fax receptions ............................................................. 15-6
Scan to PC (SMTP) transmissions .......................................... 15-7
IP Scanner ............................................................................... 15-8
Network FAX (Gateway TX)..................................................... 15-8
15.3 Troubleshooting ......................................................................... 15-9
Internet fax transmissions/Scan to E-mail transmissions......... 15-9
IP address faxing ................................................................... 15-10
Internet fax receptions ........................................................... 15-10
Distribution of Fax Documents............................................... 15-12
Scan to PC (SMTP) transmissions ........................................ 15-12
IP Scanner ............................................................................. 15-13
Network FAX (Gateway TX)................................................... 15-17
PageScope Light.................................................................... 15-18
Others .................................................................................... 15-19
Contents
x Scanner Mode

Introduction
1 Introduction
1.1 Welcome
This manual provides descriptions on the use of network application
functions used with the Internet or on an intranet.
For precautions concerning the use and safety of the main device, refer to
the User Manual provided with the device.
Store the User Manual and utilities disk in a safe place.
Trademark Acknowledgements
Windows®, Windows NT®, Microsoft® and its logo are registered
trademarks of Microsoft Corporation in the United States and other
countries.
IBM and PC/AT are registered trademarks of International Business
Machines Corporation in the United States and other countries.
Ethernet is a registered trademark of Xerox Corporation.
Netscape Navigator is a trademark of Netscape Communications
Corporation.
Adobe® and Acrobat® are trademarks of Adobe Systems Incorporated.
Network FAX is a registered trademark of Comuse Co., Ltd.
KONICA MINOLTA and KONICA MINOLTA logo are trademarks or
registered trademarks of KONICA MINOLTA HOLDINGS, INC.
PageScope is a trademark or a registered trademark of KONICA
MINOLTA BUSINESS TECHNOLOGIES, INC.
1
All other company names and product names mentioned in this manual
are trademarks or registered trademarks of their respective companies.
This product uses the Software Development Kit developed by Peerless
Systems Corporation.
Copyright© 2001 Peerless Systems Corporation. All rights reserved.
This product uses the NEST Office SDK developed by Novell, Inc.
Copyright© 1999 Novell, Inc. NEST is a trademark of Novell, Inc. in the
United States and other countries.
Scanner Mode 1-1

1
1.2 Precautions
1.2.1 General precautions
1. The reproduction of the content of this manual, either partially or in full,
is prohibited without prior permission.
2. The content of this manual is subject to change without notice.
3. Unauthorized duplication or modification is strictly prohibited.
4. This manual was created with careful attention to content; however, if
inaccuracies, errors or omissions are noticed, please contact your
sales or service representative.
5. Some network application functions may not be supported, depending
on the operating environment or other software.
The actual performance of network application functions is determined
by various factors, such as the system configuration, customer data
and operator controls.
Since the operating environment of network application functions
differs depending on the customer, the configuration of specific
products and the suitability of the application software should be
determined specifically for the customer.
6. We assume no responsibility for consequences arising from use,
regardless of items 4 and 5 mentioned above.
7. The software provided with the device, the software included on the
CD-ROM and information such as the design of and materials related
to this manual are the sole property of NEC Corporation, NEC Access
Technica and their licensors.
NEC Corporation, NEC Access Technica and their licensors own all
patents, copyrights and titles to this manual, from the design,
production and duplication to the use and marketing rights. However,
these limitations do not apply if written permission to transfer the
above-mentioned rights to another company is received.
8. The touch panel screens and computer windows and dialog boxes
shown in this manual may differ slightly from the actual products.
Introduction
1-2 Scanner Mode

Introduction
1.2.2 User Instructions
For the U.S.A. Users
FCC Part 15-Radio Frequency Devices
This device complies with Part 15 of the FCC Rules. Operation is subject to the following two
conditions: (1) This device may not cause harmful interference, and (2) this device must
accept any interference received, including interference that may cause undesired operation.
NOTE
This equipment has been tested and found to comply with the limits for a Class A digital
device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide
reasonable protection against harmful interference when the equipment is operated in a
commercial environment. This equipment generates, uses, and radiate radio frequency
energy and if not installed and used in accordance with the instruction manual, may cause
harmful interference to radio communications.
Operation of this equipment in a residential area is likely to cause harmful interference in
which case the user will be required to correct the interference at his own expense.
WARNING
The design and production of this unit conform to FCC Regulations, and any changes or
modifications must be registered with the FCC and are subject to FCC control. Any changes
made by purchaser or user without first contacting the manufacturer will be subject to penalty
under FCC regulations.
FCC-F02
This device must be used with shielded interface cables. The use of non-shielded cables is
likely to result in interference with radio communications and is prohibited under FCC rules.
1
For Canada Users
Interference-Causing Equipment Standard (ICES-003 Issue 3)
This Class A digital apparatus complied with Canadian ICES-003
Cet appareil numérique de la classe A est conforme à la norme NMB-003 du Canada.
IC-F03
Scanner Mode 1-3
1
Introduction
For European Users
CE Marking (Declaration of Conformity)
This product complies with the following EU directives:
89/336/EEC, 73/23/EEC and 93/68/EEC directives.
This declaration is valid for the area of the European Union.
This device must be used with shielded interface cables. The use of non-shielded cables is
likely to result in interference with radio communications and is prohibited under EU
directives.
For Users of the Class B regulation’s countries
This device must be used with shielded interface cables. The use of non-shielded cables is
likely to result in interference with radio communications and is prohibited under CISPR 22
rules and local rules.
For Users except the Class B regulation’s countries
WARNING
This is a Class A product. In a domestic environment this product may cause radio
interference in which case the user may be required to take adequate measures.
This device must be used with shielded interface cables. The use of non-shielded cables is
likely to result in interference with radio communications and is prohibited under CISPR 22
rules and local rules.
1-4 Scanner Mode

Introduction
Precautions for using network applications
G Internet faxes and Scan to E-mail transmissions are sent and received
G If transmission from the mail server to the recipient is not possible for
G For some reason, the e-mail describing the error may not be received.
G Since the privacy of transmissions through the Internet or an intranet
G Telephones on a LAN cannot be used.
G It may take some time for a transmission to be sent due to Internet/
G Depending on the mail servers, it may not be possible to send
1
with the help of a mail server; they are not sent directly to the recipient
or received directly from the sender. In addition, as soon as
transmission with the server is finished correctly, the transmission is
considered complete.
some reason, an e-mail describing the error will be received from the
server.
If confirmation of the transmission is required, call the recipient after
transmission to confirm reception.
is limited, we recommend sending important documents directly to the
recipient through a common telephone line.
intranet traffic.
documents with a large number of pages or a large amount of image
data.
Functions that cannot use network applications
The following functions can be used with normal fax transmissions using
a common telephone line, but cannot be used with network applications.
G Batch transmission
G Polling transmission
G Real-Time transmission
G Password transmission
G Remote copying
G Confidential box
G Bulletin board registration
G On-hook
G Remote retrieval of bulletin board
✎
Note
Password transmission and remote copying can be specified in the
operation, but they will not function.
Scanner Mode 1-5

1
Introduction
The following functions can be used with network applications.
G Image quality specification
G Density specification
G Non-reduction mode
G Scan area specification
G 2in1
G 2-sided transmission
G TX marker stamp (optional)
G TSI
G Destination insert
G Forward the received facsimile ducuments (Document Management)
G Priority transmission
G Timer transmission
G Rotation transmission
1-6 Scanner Mode
Introduction
1.3 Check for Enclosed Accessories
Check that all of the following are included.
If anything is missing or damaged, contact your service representative.
Network Scan Kit (SU-2)
G TWAIN driver CD-ROM containing electronic manuals
This CD-ROM contains the TWAIN driver, the Scanner Mode User
Manual and the PageScope Light User Manual.
Internet Fax & Network Scan Kit (SU-3)
G TWAIN driver CD-ROM containing electronic manuals
This CD-ROM contains the TWAIN driver, the Scanner Mode User
Manual and the PageScope Light User Manual.
G Utility Disk (CD-ROM)
The Utility Disk contains the utilities (e.g., IP Scanner and Network
FAX), the IP Scanner User Manual and the Network FAX User
Manual.
✎
Tip
In order to use the Network Scan Kit or the Internet FAX & Network
Scan Kit, the Printer Controller (Pi3505e or Pi3505e/PS) and the
Network Interface Card must be installed.
1
✎
Note
The LAN cable (cable for Fast Ethernet 100BASE-TX) is not included.
CAUTION
Only use the CD-ROM in a player that is CD-ROM-compatible.
➜ If a player not compatible with the CD-ROM format is used, your ears
or speakers may be damaged by the loud noise produced.
Scanner Mode 1-7

1
Introduction
1-8 Scanner Mode
Overview
2Overview
Paper documents can easily be converted to electronic data and used, for
example, with electronic filing. Scanned image data (scan data) can be
sent to other computers through a network as either a TIFF file or a PDF
file.
The scanned image can be sent using any of the following methods.
Choose the appropriate method according on the network environment
and purpose.
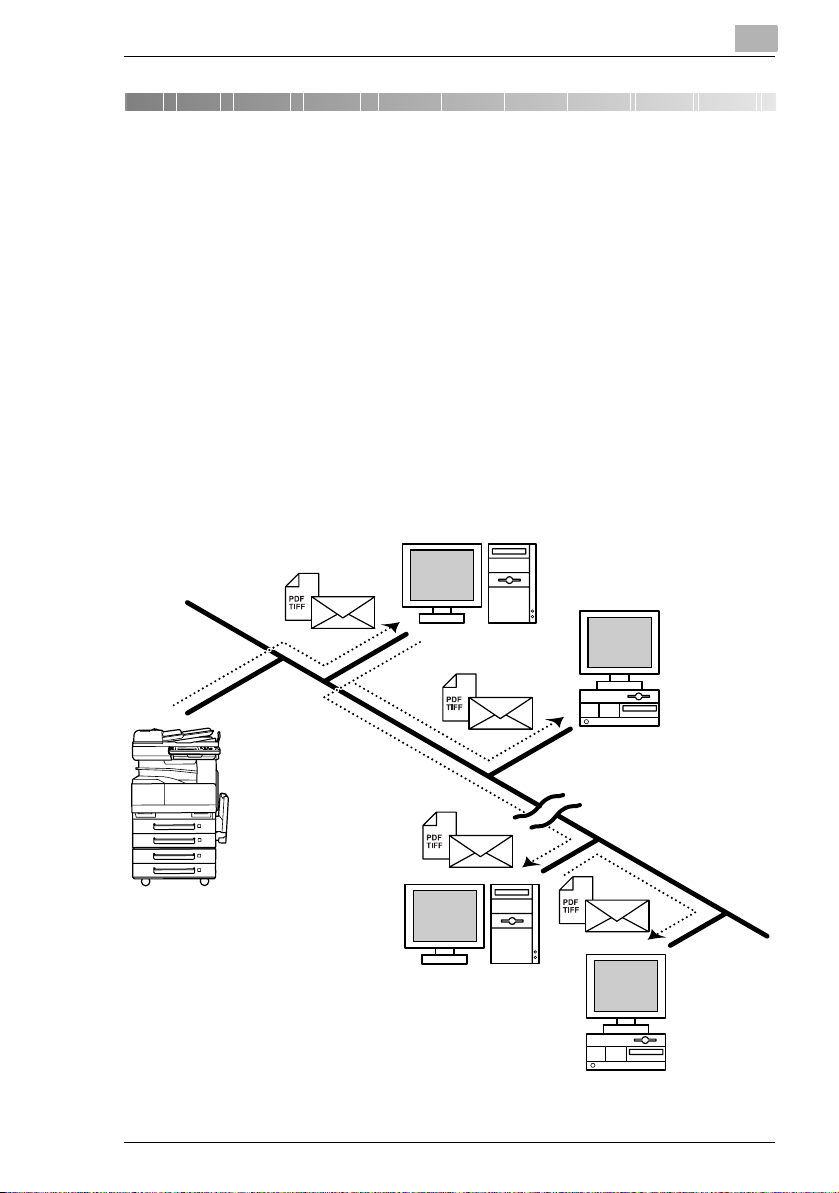
2.1 Scan to E-mail
G Scan data is attached to an e-mail message as a TIFF or PDF file, then
sent to a computer through an intranet or the Internet.
G A network environment that includes a mail server is required.
2
Mail server
Client computer
Intranet
Internet
Mail server
Client computer
Scanner Mode 2-1
2
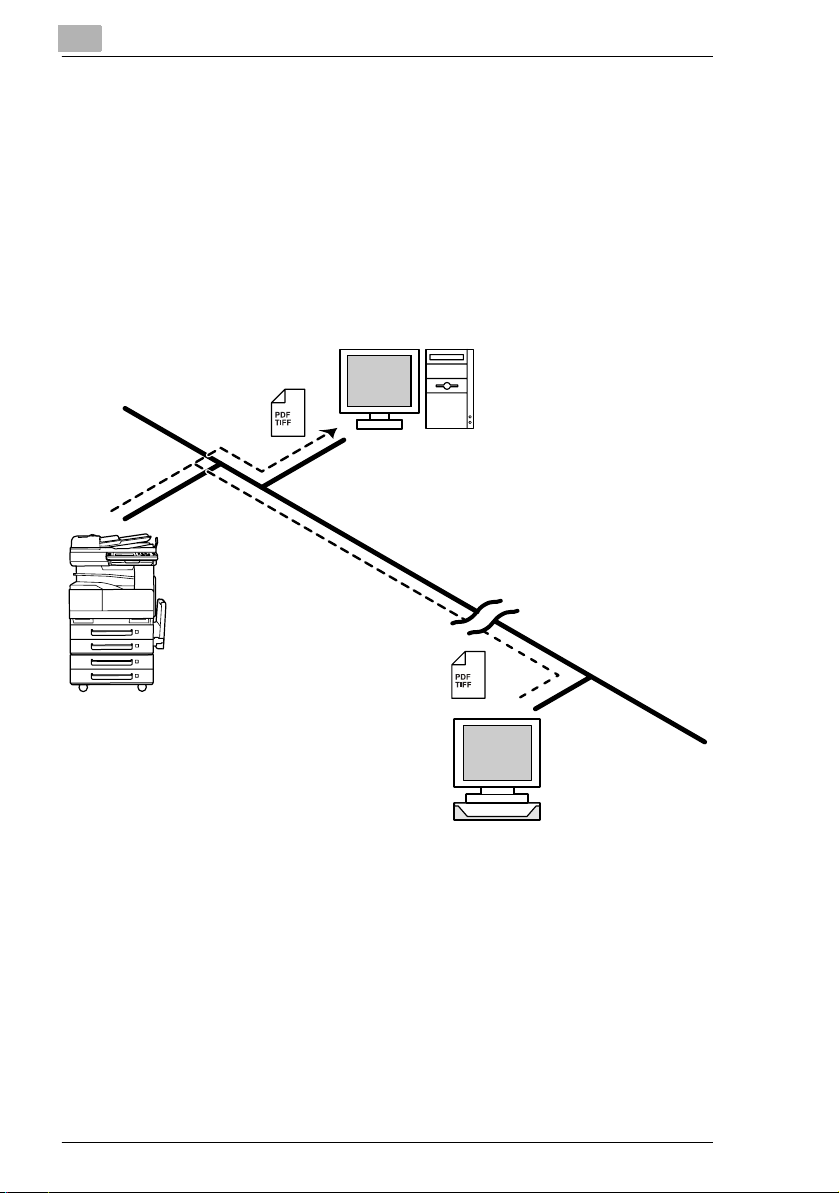
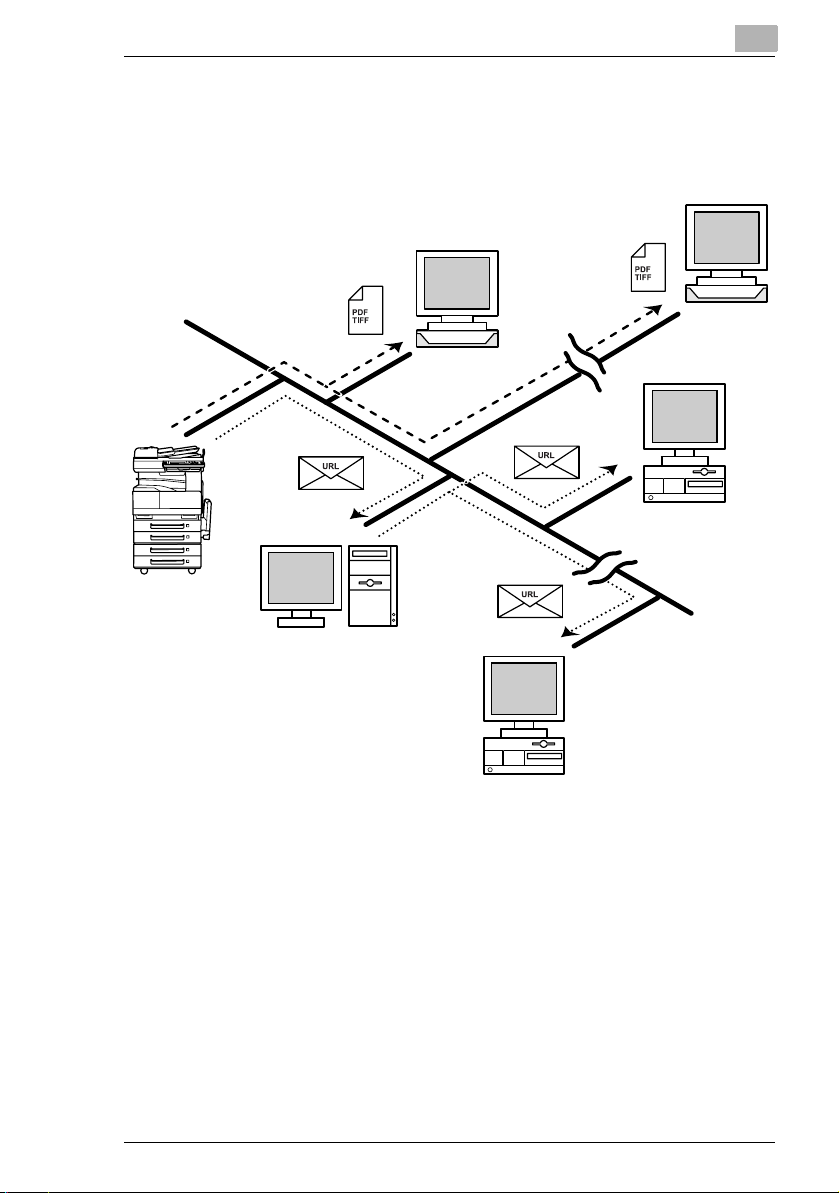
2.2 Scan to Server (FTP)
G Scan data can be uploaded as TIFF or PDF files to a specified
directory on an FTP server.
G A network environment that includes an FTP server is required.
G An FTP server on the Internet can be accessed through a proxy
server.
G A maximum of five FTP server can be registered, and a maximum of
five directories can be set up on each FTP server.
Overview
FTP server
Intranet
Internet
FTP server
2-2 Scanner Mode
Overview
2
G With the “URL Report” function, a notification of the URL where the
scan data is saved can be sent by e-mail. (If the “URL Report” function
is used, a mail server is required.)
FTP server
FTP server
Internet
Client computer
Intranet
Internet
Mail server
Client computer
Scanner Mode 2-3
2
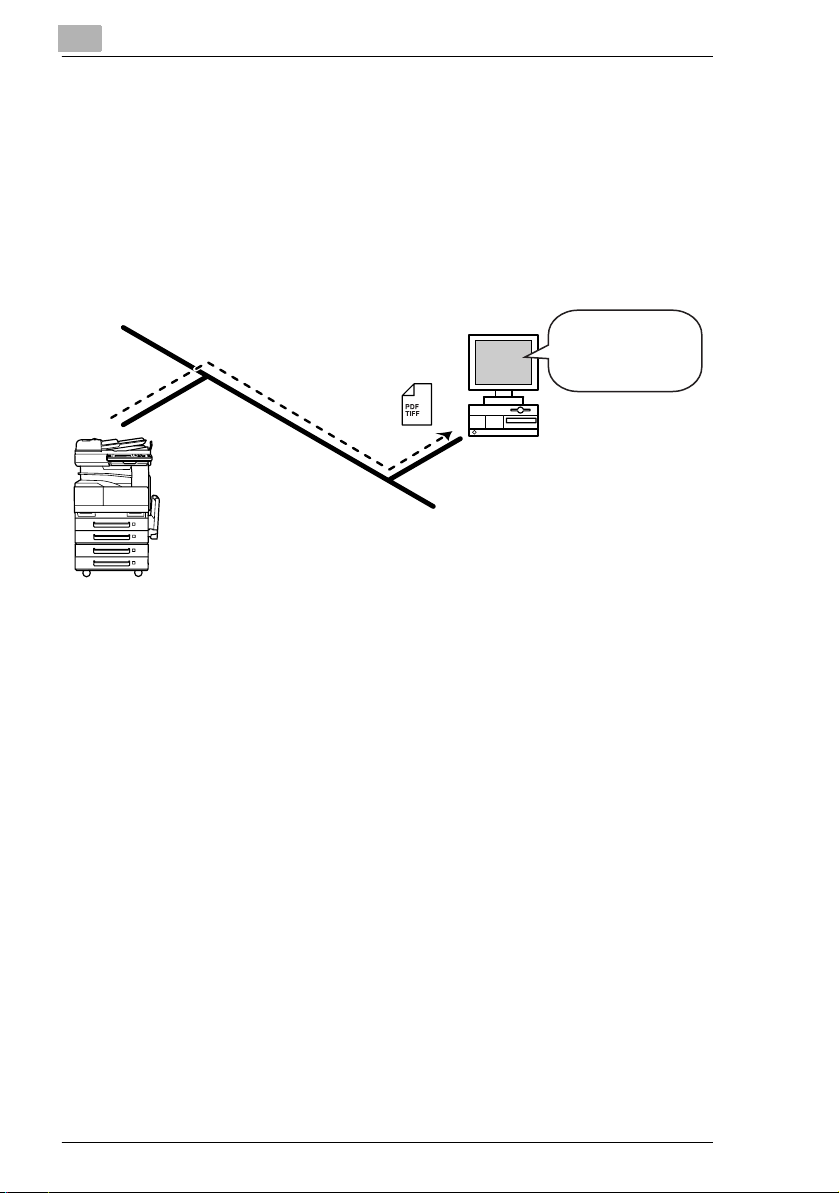
2.3 Scan to PC (FTP)
G Scan data can be sent as TIFF or PDF files to client computers using
FTP.
G The FTP server application must be running on the client computers.
G The forwarding destination on the client computer is the root folder
specified with the FTP server application. This setting cannot be
specified from the copier’s control panel or from PageScope Light.
Overview
FTP server
application
Intranet
Client computer
2-4 Scanner Mode
Overview
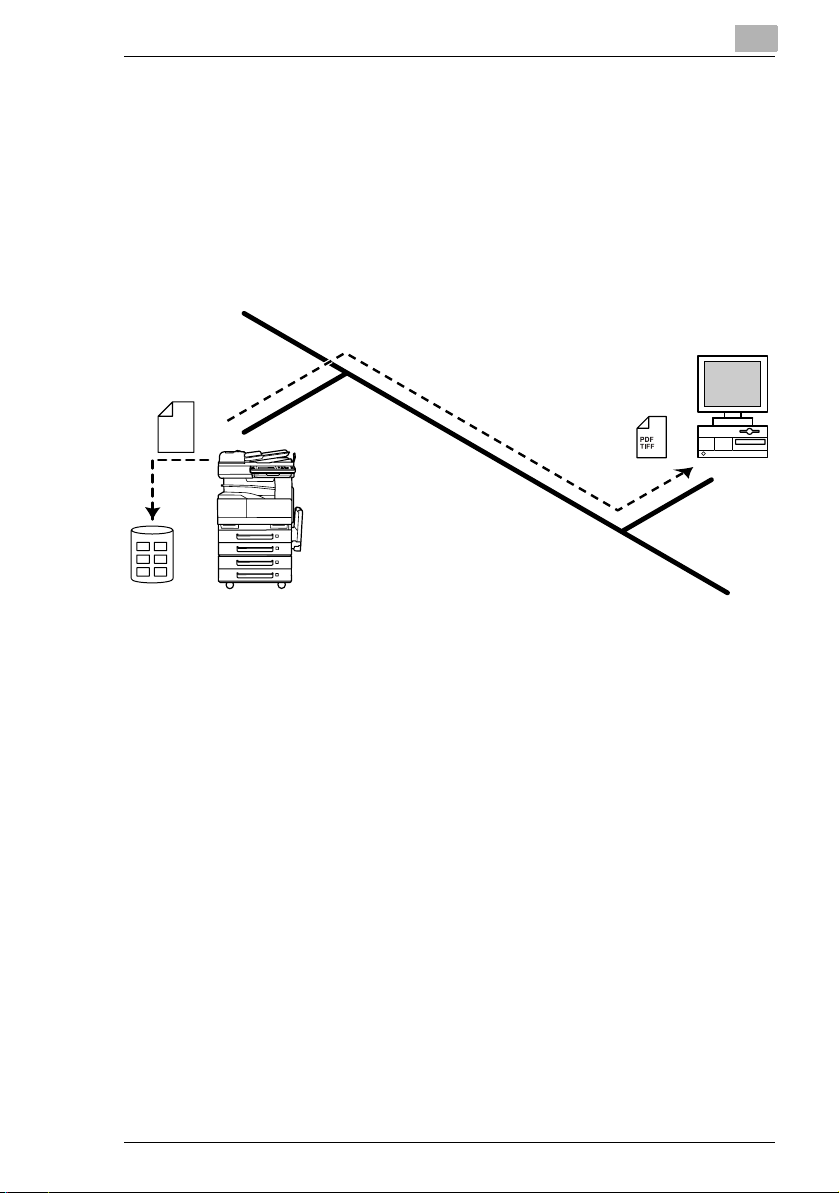
2.4 Scan to HDD
G Scan data is saved on the copier’s hard disk as TIFF or PDF files.
The saved files can be retrieved with PageScope Light or TWAIN
driver.
G With the “URL Report” function, a notification of the URL where the
scan data is saved can be sent by e-mail.
(If the “URL Report” function is used, a mail server is required.)
Scan
data
HDD
Intranet
Client
computer
2
Scanner Mode 2-5
2
2.5 Internet Faxing
G As opposed to a normal fax, which transmits through telephone lines,
Internet fax sends and receives fax images through the Internet.
Internet fax uses the Internet electronic mail (e-mail) setup to send and
receive fax images. Image data scanned at an Internet fax terminal is
attached to an e-mail message as a TIFF-F file, then sent to the
recipient’s Internet fax terminal. The file attached to the received email message is printed by the Internet fax terminal on the receiving
end.
In addition, since e-mail is used, the fax can be sent to an individual email address, not just an Internet fax terminal. In this case, the fax
image arrives at the receiving end as an attachment to an e-mail
message received with the usual mail client software.
Overview
Mail server
Client computer
Internet fax
terminal
Intranet
Internet
Mail server
Client computer
2-6 Scanner Mode
Overview
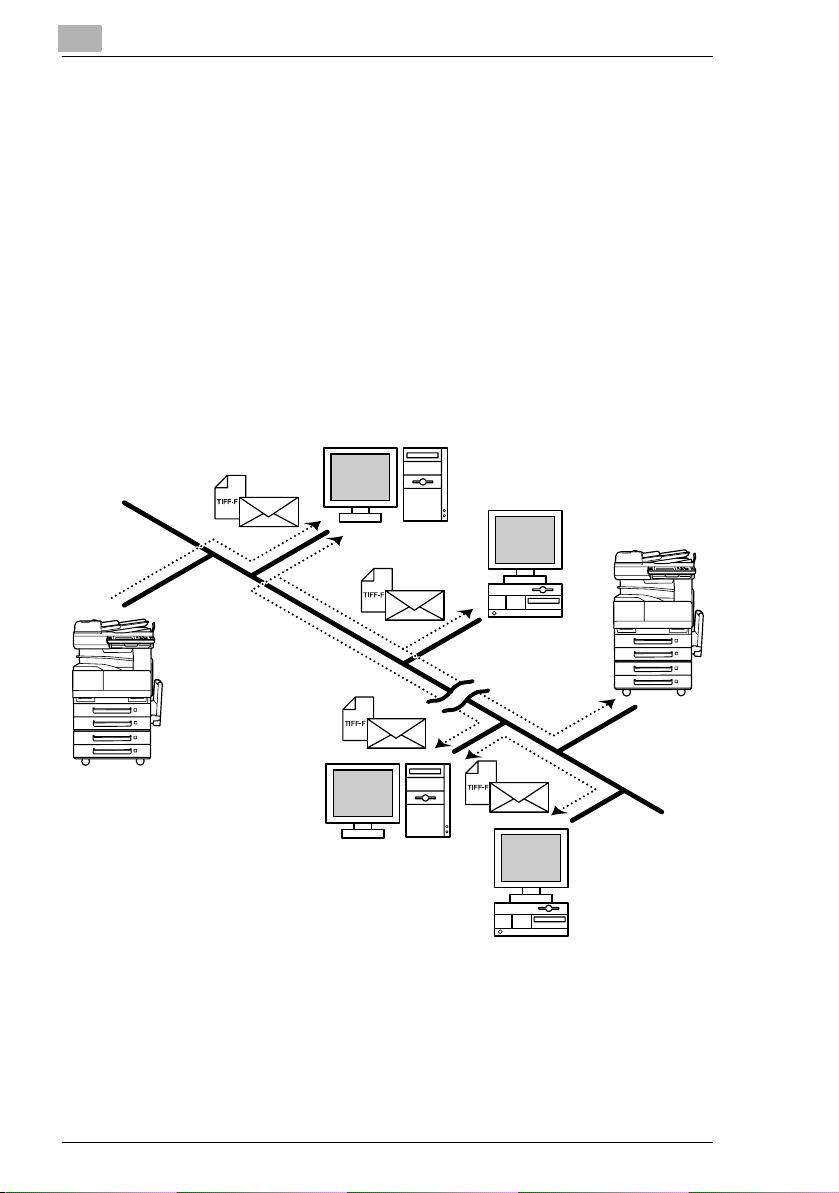
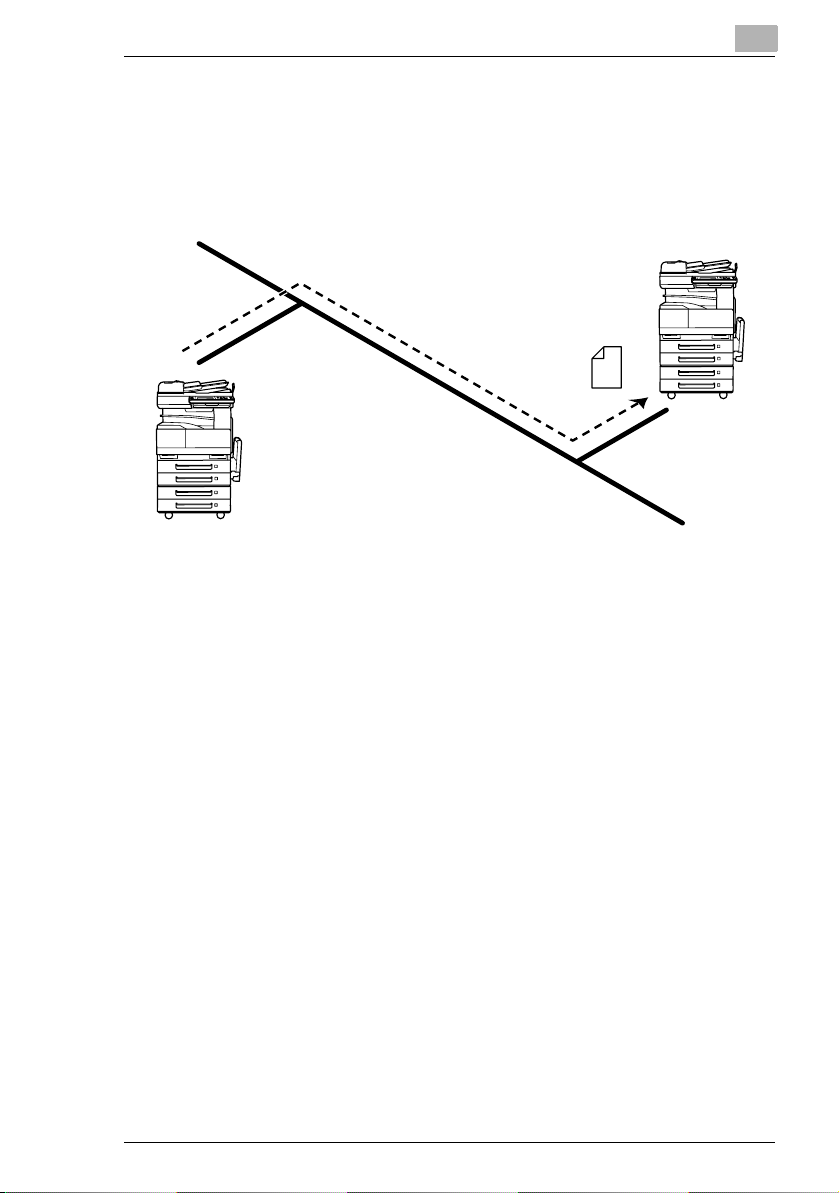
2.6 IP Address FAX (LAN-FAX)
G Scan data is sent to a copier of the same type (Internet fax) through
the Intranet, without passing through a mail server.
Intranet
1 Program a one-touch key with the IP address or the host name of the
recipient.
2
Internet fax terminal
(Same type of unit
as copier)
2 Use the one-touch key to specify the recipient, and then specify the
settings for sending the data (IP address fax transmission).
3 The recipient receives the fax image (IP address fax reception).
Scanner Mode 2-7
2
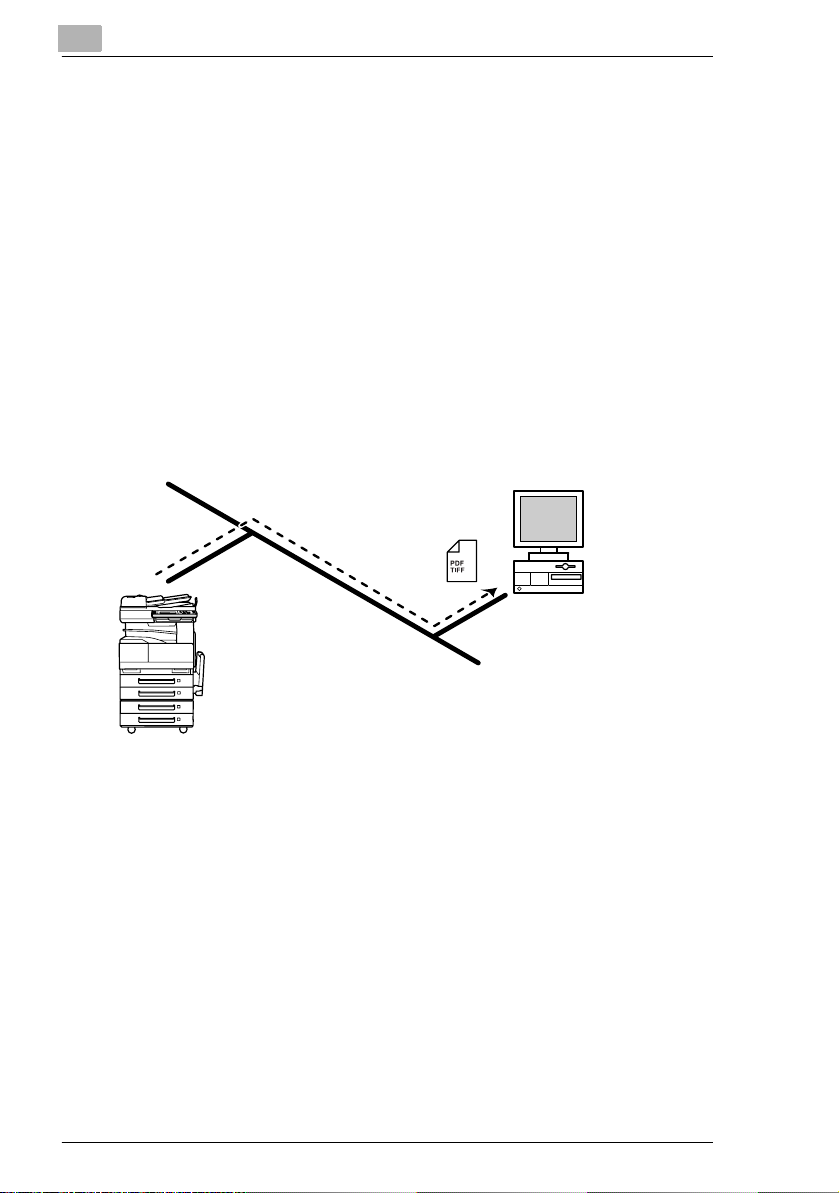
2.7 Scan to PC (SMTP)
G Scan data can be sent as TIFF or PDF files to client computers using
SMTP.
G From the client computer, the enclosed IP Scanner application must
be used to first specify the folder where data is saved. In addition, the
IP Scanner application can be set to save the data in a folder that was
created using the name of the one-touch key.
G In order to receive the data at a client computer and save it as an
image file, the enclosed utilities IP Scanner and Image Receiver are
required.
G If there is a DHCP server on the network, this function may not operate
correctly since IP addresses are automatically distributed to each
computer. In this case, specify a fixed IP address for the computer or
use IP Scanner.
Intranet
Overview
Client computer
1 Program a one-touch key with the IP address of the computer
receiving the data.
2 Using the same procedure for sending e-mail messages, specify that
the data is to be sent to a computer.
3 The sent scan data is received by the recipient computer.
4 The IP Scanner application converts the data to a TIFF or PDF file,
then saves the file in the specified folder.
2-8 Scanner Mode
Overview
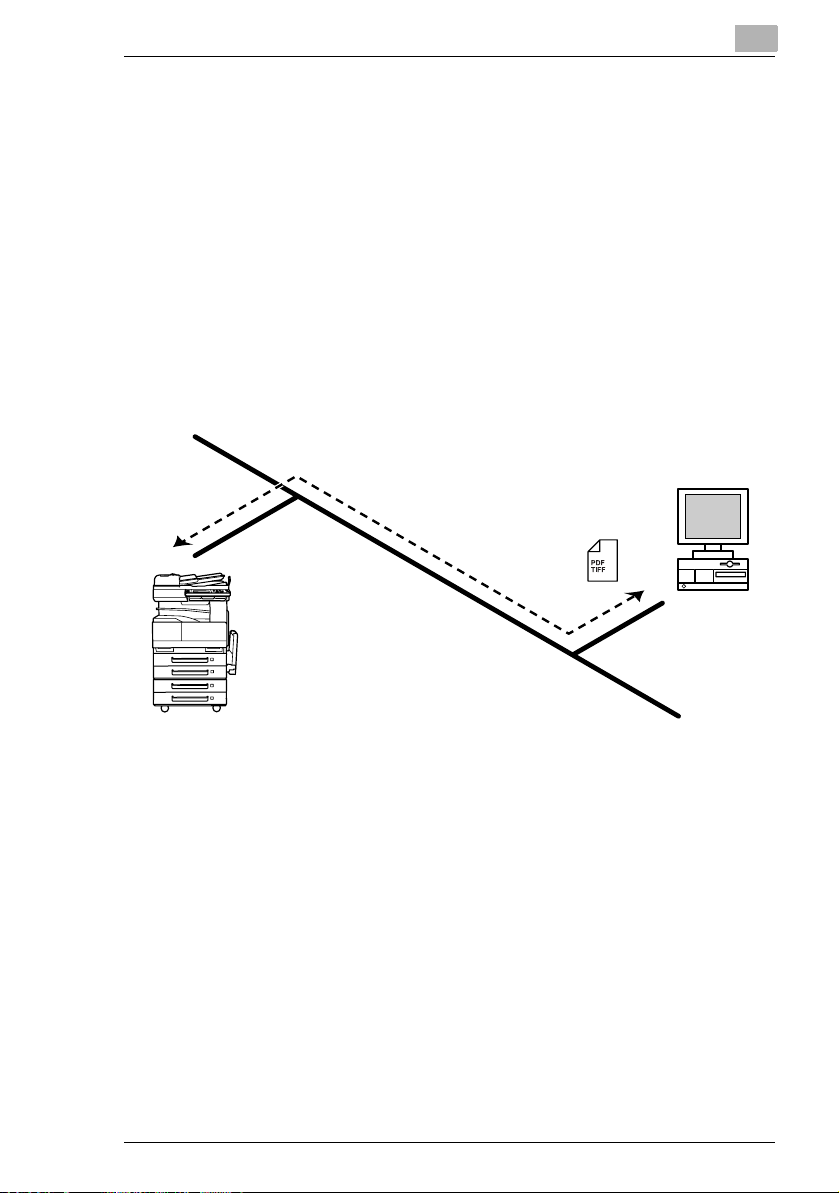
2.8 IP Scanner
G Scan data is sent to a client computer, where it is saved in a folder that
is created using the name of the scanner button.
G After programming a button (Scan data destination and scan settings)
from the client computer when scanning, a paper document can easily
be saved as an electronic file with just the touch of a button in the
copier’s touch panel.
In order to receive the data at a client computer and save it as an
image file, the enclosed utilities IP Scanner and Image Receiver are
required.
G This function can be used in a network without a LAN if a crossover
cable is used to connect the copier to a client computer. (Network
settings are required.)
2
Client computer
1 From the computer, program a button (recipient of the scan data).
2 Touch the programmed button to send the scan image.
3 The sent scan image is received by the recipient computer.
4 The IP Scanner application converts the data to a TIFF or PDF file,
then saves the file in the specified folder.
Scanner Mode 2-9
2
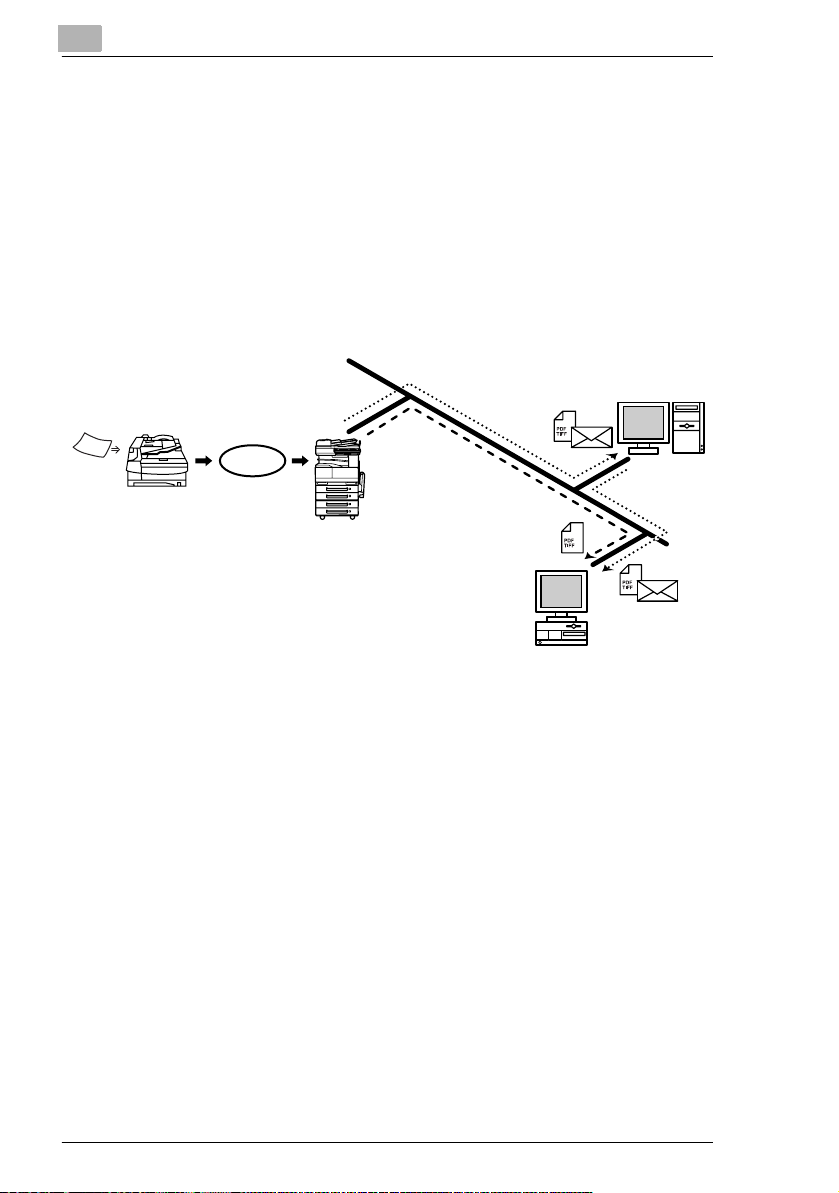
2.9 Document Forwording/Archive Distribution
G Image data received from a fax machine on a common telephone line
can be sent directly to a computer or attached to an e-mail message.
In order to transmit the fax document by e-mail, a network environment
that includes a mail server is required.
G The fax document can be be received at your own computer.
G Received fax documents can be classified as “F-Code”, “Port” or
“Public Document”, and the distribution destinations for each type of
document can be specified.
Overview
Facsimile
terminal
Facsimile
communication
Telephone
line
Client computer
Mail server
1 From the copier, select a Doc. Manage setting to classify the fax
image.
2 The fax image is sent to the computer specified as the recipient.
3 The fax image is received by the recipient computer as an image file.
2-10 Scanner Mode
Overview
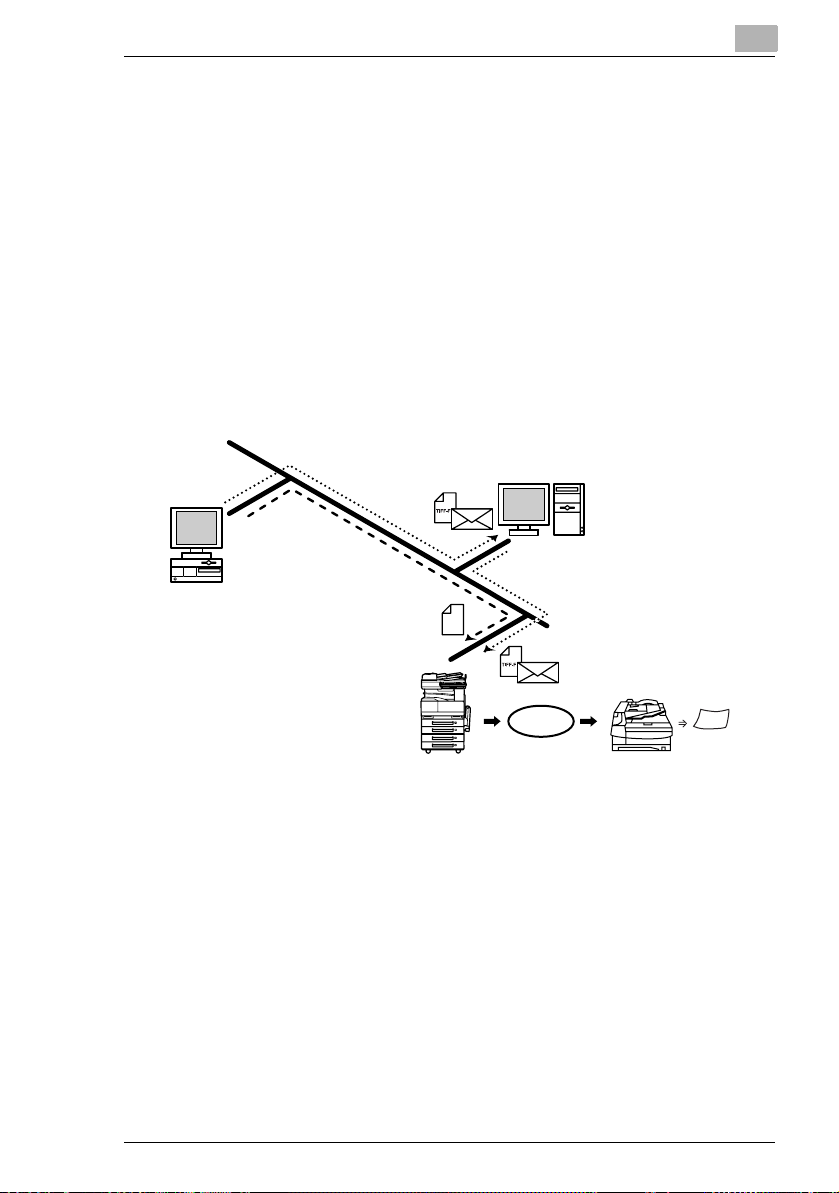
2.10 Network Fax Transmission
G To use Network Fax transmission, “Network FAX” is required, one of
the attached utilities. Be sure to confirm the network environment, then
perform the network setting and the setup of Network FAX.
G A document created in an application, such as word-processing
software, can be faxed by specifying the telephone (fax) number of the
recipient, without first printing the document.
In addition, the result of the fax transmission can be checked from the
computer.
G An e-mail address or a telephone (fax) number can be specified for the
recipient.
G In order to perform direct faxing operations using a mail server, the
DNS settings must be specified.
Client computer
2
Mail server
Telephone
line
Facsimile
communication
Facsimile terminal
1 Specify the fax number of the destination (specify the recipient after
specifying printing from the application).
2 The image data is transmitted from the client computer or mail server.
3 The data received by the computer is sent to the specified fax number.
Scanner Mode 2-11
 Loading...
Loading...