Konica Minolta 368, 308 User Manual

User’s Guide
Security Operations
2017. 2
Ver. 1.01

Contents
1 Security
1.1 Introduction ..................................................................................................................................... 1-2
Administrators.................................................................................................................................... 1-2
Compliance with the ISO15408 Standard ......................................................................................... 1-2
Operating Precautions ....................................................................................................................... 1-2
INSTALLATION CHECKLIST.............................................................................................................. 1-4
1.2 Security Functions .......................................................................................................................... 1-7
Check Count Clear Conditions .......................................................................................................... 1-7
1.3 Precautions for Operation Control................................................................................................ 1-9
1.4 Miscellaneous................................................................................................................................ 1-13
Roles of the Owner of the Machine ................................................................................................... 1-9
Roles and Requirements of the Administrator................................................................................... 1-9
Password Usage Requirements ........................................................................................................ 1-9
External authentication server control requirements ....................................................................... 1-10
Security function operation setting operating requirements............................................................ 1-10
Operation and control of the machine............................................................................................. 1-10
Machine Maintenance Control......................................................................................................... 1-12
Precautions for using the printer driver............................................................................................ 1-12
Password Rules ............................................................................................................................... 1-13
Precautions for Use of Various Types of Applications..................................................................... 1-14
Encrypting communications ............................................................................................................ 1-14
IPsec setting .................................................................................................................................... 1-14
Print functions.................................................................................................................................. 1-15
IPP printing ...................................................................................................................................... 1-15
Items of Data Cleared by Overwrite All Data Function .................................................................... 1-16
Fax functions.................................................................................................................................... 1-16
USB keyboard.................................................................................................................................. 1-16
Different types of boxes................................................................................................................... 1-17
Hardware and software used in the machine .................................................................................. 1-17
Firmware integrity verification function............................................................................................ 1-17
CS Remote Care function................................................................................................................ 1-18
Terminating a Session and Logging out .......................................................................................... 1-18
Authentication error during external server authentication.............................................................. 1-18
2 Administrator Operations
2.1 Accessing the Administrator Mode............................................................................................... 2-2
2.1.1 Accessing the Administrator Mode.................................................................................................... 2-2
2.1.2 Accessing the User Mode.................................................................................................................. 2-8
2.2 Enhancing the Security Function................................................................................................. 2-12
2.2.1 Items cleared by HDD Format ......................................................................................................... 2-14
2.2.2 Setting the Password Rules............................................................................................................. 2-15
2.2.3 Setting the Enhanced Security Mode .............................................................................................. 2-17
2.3 Protecting Machine from Illegal Firmware Update.................................................................... 2-20
Setting the FW Update (USB) Password ......................................................................................... 2-20
2.4 Preventing Unauthorized Access ................................................................................................ 2-23
Setting Prohibited Functions When Authentication Error ................................................................ 2-23
2.5 Canceling the Operation Prohibited State.................................................................................. 2-25
2.6 Setting the Authentication Method ............................................................................................. 2-27
2.6.1 Setting the Authentication Method .................................................................................................. 2-27
2.6.2 Setting the External Server .............................................................................................................. 2-30
2.7 ID & Print Setting Function........................................................................................................... 2-32
bizhub 368/308 Contents-1
Performing Release Setting ............................................................................................................. 2-25
Setting ID & Print.............................................................................................................................. 2-32

2.8 ID & Print Operation Setting Function......................................................................................... 2-34
Making ID & Print Operation Setting................................................................................................ 2-34
2.9 Auth. Operation Setting when print Documents are Stored Function ..................................... 2-35
Setting Auth. Operation Setting when print Documents are Stored Function................................. 2-35
2.10 System Auto Reset Function ....................................................................................................... 2-36
2.11 User Setting Function................................................................................................................... 2-38
2.12 Account Track Setting Function.................................................................................................. 2-44
2.13 User Box Function ........................................................................................................................ 2-49
2.13.1 Setting the User Box........................................................................................................................ 2-49
2.13.2 Changing the user/account attributes and box password .............................................................. 2-54
2.13.3 Setting Memory RX.......................................................................................................................... 2-59
2.14 Changing the Administrator Password....................................................................................... 2-62
2.15 Protecting Data in the HDD.......................................................................................................... 2-65
2.15.1 Setting the Encryption Key (encryption word) ................................................................................. 2-65
2.15.2 Changing the Encryption Key .......................................................................................................... 2-69
2.15.3 Setting the Overwrite HDD Data...................................................................................................... 2-71
2.16 Overwrite All Data Function ......................................................................................................... 2-73
2.17 Obtaining Job Log......................................................................................................................... 2-75
2.17.1 Obtaining and deleting a Job Log.................................................................................................... 2-75
2.17.2 Downloading the Job Log data........................................................................................................ 2-77
2.18 Setting time/date in machine....................................................................................................... 2-88
2.18.1 Setting time/date.............................................................................................................................. 2-88
2.18.2 Setting daylight saving time............................................................................................................. 2-91
2.19 SSL Setting Function .................................................................................................................... 2-93
2.19.1 Device Certificate Setting ................................................................................................................ 2-93
2.19.2 SSL Setting ...................................................................................................................................... 2-95
2.19.3 Removing a Certificate..................................................................................................................... 2-96
2.20 TCP/IP Setting Function....................................................................................................
2.20.1 Setting the IP Address ..................................................................................................................... 2-97
2.20.2 Registering the DNS Server............................................................................................................. 2-98
2.21 E-Mail Setting Function ................................................................................................................ 2-99
Setting the System Auto Reset function.......................................................................................... 2-36
Making user setting.......................................................................................................................... 2-39
Making account setting.................................................................................................................... 2-44
Changing the Administrator Password............................................................................................ 2-62
Setting the Overwrite All Data function............................................................................................ 2-73
Job Log data.................................................................................................................................... 2-79
........... 2-97
Setting the SMTP Server (E-Mail Server)......................................................................................... 2-99
3 User Operations
3.1 User Authentication Function ........................................................................................................ 3-2
3.1.1 Performing user authentication.......................................................................................................... 3-2
3.1.2 Accessing the ID & Print Document................................................................................................... 3-6
3.2 Change Password Function........................................................................................................... 3-7
Performing Change Password........................................................................................................... 3-7
3.3 Secure Print Function ................................................................................................................... 3-10
Accessing the Secure Print Document ............................................................................................ 3-10
3.4 User Box Function ........................................................................................................................ 3-13
3.4.1 Setting the User Box........................................................................................................................ 3-13
3.4.2 Changing the user/account attributes and box password .............................................................. 3-18
3.4.3 Accessing the User Box and User Box file ...................................................................................... 3-24
bizhub 368/308 Contents-2

4 Application Software
4.1 Data Administrator.......................................................................................................................... 4-2
4.1.1 Accessing from Data Administrator ................................................................................................... 4-2
4.1.2 Setting the user authentication method............................................................................................. 4-5
4.1.3 Changing the authentication mode.................................................................................................... 4-6
4.1.4 Making the user settings.................................................................................................................... 4-8
4.1.5 Making the account settings.............................................................................................................. 4-9
4.1.6 DNS Server Setting Function........................................................................................................... 4-10
4.1.7 E-Mail Setting Function.................................................................................................................... 4-11
bizhub 368/308 Contents-3

1
Security

1.1 Introduction
1 Security
1.1 Introduction
Thank you for purchasing our product.
This User's Guide contains the operating procedures and precautions to be used when using the security
functions offered by the bizhub 368/308 machine. To ensure the best possible performance and effective use
of the machine, read this manual thoroughly before using the security functions. The administrator of the machine should keep this manual for ready reference. The manual should be of great help in finding solutions to
operating problems and questions.
This User's Guide (version 1.01) covers the following.
Model name bizhub 368/bizhub 308
Version G00-09
Administrators
<Administrator of the machine>
There are two types of administrators; one who is implemented on the machine in advance, and the other
who is registered by the implemented administrator. The former is called the built-in administrator and the
latter is called a user administrator. Below, the administrator of the machine means the build-in administrator.
<User administrator>
The user administrator is a user who is given the authority to operate the machine as an administrator. The
administrator of the machine or the user administrator can register the user administrator. Be sure that "Precautions for Operation Control" applies to the user administrator. For details, see page 1-9.
The differences from the administrator of the machine are as follows:
- The same procedure as a user applies to the user administrator when he or she changes the password
or fails authentication.
- To change password, log on to the User Mode.
<Note>
Below, the administrator collectively means both the administrator of the machine and the user administrator.
1
Compliance with the ISO15408 Standard
When the Enhanced Security Mode on this machine is set to [ON], more enhanced security functions are
available.
This machine offers the security functions that comply with the ISO/IEC15408 (level: EAL2) and U.S. Government Approved Protection Profile - U.S. Government Protection Profile for Hardcopy Devices Version 1.0
(IEEE Std 2600.2
TM
-2009).
Operating Precautions
The machine gives an alarm message or an alarm sound (peep) when a wrong operation is performed or a
wrong entry is made during operation of the machine. (No "peep" alarm sound is issued if a specific sound
setting in Sound Setting of Accessibility Setting is set to [OFF].) If the alarm message or alarm sound is given,
perform the correct operation or make the correct entry according to the instructions given by the message
or other means.
The administrator must not leave the machine with each setting screen left displayed before, during, and after
access to each mode. If he or she has to leave the machine, make sure that he or she logs out and returns
the screen to the authentication screen.
The administrator must make sure that each individual general user logs out and returns the screen to the
authentication screen if he or she leaves the machine with each mode screen left displayed before, during,
and after access to each mode.
bizhub 368/308 1-2

1.1 Introduction
If an error message appears during operation of the machine, perform steps as instructed by the message.
For details of the error messages, refer to the User’s Guide furnished with the machine. If the error cannot be
remedied, contact your service representative.
Page rotation in the preview during scanning of the document in each of the copying, E-mail, and fax functions provided by the machine is reflected in the output. In the E-mail and fax functions, data can be deleted
by the page and the deletion is reflected in the output.
The Web Connection functions can be used only if the setting is made to accept "Cookie."
For any query, request, or opinion concerning the machine, please contact your dealer from which you purchased your machine or Service Representative.
Any notice concerning this machine will be given in writing by the dealer from which you purchased your machine or Service Representative.
1
bizhub 368/308 1-3
1.1 Introduction
INSTALLATION CHECKLIST
This Installation Checklist contains items that are to be check by the Service Engineer installing this machine.
The Service Engineer should check the following items, then explain each checked item to the administrator
of the machine.
To Service Engineer
Make sure that each of these items is properly carried out by checking the box on the right of each item.
1. Perform the following steps before installing this machine.
1
Check with the administrator of the machine to determine if the security functions of this
machine should be enhanced. If the functions should be enhanced, check the following.
If the security functions are not to be enhanced, quit the operation without checking the
following.
Before installing the machine, check with the administrator of the machine to determine if
the following is confirmed.
• Whether the Service Engineer has been informed that the unpacking procedure is to
be performed by the Service Engineer in the presence of the administrator.
• Whether the machine has been under the control of the administrator of the machine
with a check made to ensure that evidently the machine has not been unpacked or
used.
The Service Engineer should obtain the administrator's consent to the performance of this
item.
If the machine has been unpacked, check with the administrator that it was the administrator who unpacked the machine and nobody but the administrator has gain access to the
machine after the unpacking. Then, obtain the administrator's consent to the performance
of the installation procedure for the unpacked machine before attempting to start the procedure. If the administrator's consent cannot be obtained, call the dealer.
I swear that I would never disclose information as it relates to the settings of this machine
to anybody, or perform malicious or intentional act during setup and service procedures
for the machine.
When giving a copy of the User's Guide, explain the following to the administrator:
• A digital signature is assigned to the data certified by ISO15408. To ensure integrity of
the file, have the administrator of the machine confirm the digital signature using the
property of the provided data file in the user's PC environment.
Confirm the digital signature as follows.
Right click the provided exe file to display the property screen.
Select [Digital Signatures] - [Details] - [General], and check that Konica Minolta, Inc. is
displayed in the Name of signer field.
Select [View Certificate] - [General]. Then, check that the signing time is within the validated date of the certificate and that the certificate has been issued by a reliable certification authority.
Write down the serial number shown in [View Certificate] - [Details]. Access to the URL
for CRL Distribution Points and confirm that the serial number is not shown in
[Revocation List]. For confirmation, the Internet environment is required.
• Two versions are available, the HTML version and User's Guide Security Operations
(this User's Guide).
• In HTML version, option settings are described including functions those can be universally configured, but it does not mean that all of them are available.
• This User's Guide must first be read and the conditions described in this User's Guide
take precedence over the HTML version.
• If the security functions of the machine are to be enhanced, the machine and its surrounding environment should be set up and operated according to this User's Guide.
Refer to the Service Manual and perform the required installation and setup steps.
During the installation and setup procedure, make sure that no unnecessary parts are
mounted on the machine and have the administrator of the machine confirm that no unnecessary parts are mounted on the machine.
• Explain to the administrator making him/her check the cover of the Service Manual to
be referred that it is for bizhub 368/bizhub 308 (Version: G00-09).
Explain to the administrator that the following settings must be performed referring to
the manuals above.
• The Service Engineer must have the administrator confirm that the digital signature is
assigned to the firmware and the version of the firmware to be updated is the one that
is written on the Service Manual.
bizhub 368/308 1-4

1.1 Introduction
2. After this machine is installed, refer to the Service Manual and perform the following steps.
3. After this machine is installed, refer to this User’s Guide and perform the following steps.
1
Check that the model name and the Firmware version (card version) checked with the Service Manual agree with the value shown on the Firmware version display screen.
Check also that the MFP model name and the part numbers of the MFP board and the
eMMC board agree with those described in the Service Manual.
If there is a mismatch in the Firmware version number, explain to the administrator of the
machine that upgrading of the Firmware is necessary and perform upgrading of the Firmware.
Check that the Fax Kit has been mounted and set up properly, if fax functions are to be
used.
After the installation, conduct transmission and reception tests to make sure that the Fax
Kit has been mounted and set up properly.
Let the machine read the Custom Function Pattern Selection setting file to which an electronic signature is assigned.
Explain to the administrator that the Custom Function Pattern Selection setting file is dedicated to the machine in question.
Get the administrator of the machine to confirm that [ISO15408] is selected for [Send/Save]
of [Custom Function Pattern Selection] in the Administrator Settings and obtain his or her
consent not to change the setting.
Set CE Authentication to [ON] and set the CE Password.
Make the service settings necessary for the Enhanced Security Mode.
Check that the Administrator Password has been set by the administrator of the machine.
Select [Restrict] when the confirmation screen of machine usage information is displayed.
If [Allow] is mistakenly selected, make the following settings:
• Set the function counter (Transmission Meter Count and Device Information) to [Restrict].
• Set the TX Operation Log setting to [Do not Save].
For the setting procedure, see bizhub 558/458/368/308 User's Guide version 1.00 A9HJ9590BA-00.
Setting by the Service Engineer is required for the following:
• Debug Log Collection System function (software SW No. 155)
• Export Debug Log
Check that the Encryption Key has been set by the administrator of the machine.
Check that the Overwrite HDD Data has been set by the administrator of the machine.
Check that User Authentication has been set to [ON (MFP)], [External Server Authentication] (Active Directory only), or [Main + External Server] (Active Directory only) by the administrator of the machine.
Check that the date and time have been correctly set in the machine by the administrator
of the machine.
Check that the Job Log Settings (Audit Log) has been set to [Yes] by the administrator of
the machine.
Check that the certificate for SSL communications has been registered by the administrator of the machine.
In accordance with the security policies of the organization, register the certificate that is
issued by a reliable authentication authority.
Check that the ID & Print Settings has been set to [ON] by the administrator of the machine.
Check that the Memory RX Setting has been set to [Yes] by the administrator of the machine.
Check that IPsec has been set by the administrator of the machine for communications
between the machine and the external authentication server.
Check that IPsec has been set by the administrator of the machine for communications
between the machine and the DNS server.
Check that IPsec has been set by the administrator of the machine for communications
between the machine and the SMTP server.
Check that IPsec has been set by the administrator of the machine for communications
between the machine and a client PC.
bizhub 368/308 1-5

1.1 Introduction
After completing the checks, keep a copy of this list in the Service Representative and give the original of this
list to the administrator of the machine.
Please direct your any queries about using the machine to the Service Representative shown below.
1
Let the administrator of the machine set Enhanced Security Mode to [ON].
Check that the FW Update (USB) Password has been set by the administrator of the machine.
Check that the various functions to be disabled manually have been properly disabled by
the administrator of the machine.
The languages, in which the contents of the User’s Guide Security Operations have been
evaluated, are Japanese and English.
The following lists the manuals compatible with bizhub 368/bizhub 308 (Version: G00-09).
• bizhub 558/458/368/308 User’s Guide Ver. 1.00 A9HJ-9590BA-00
• bizhub 368/308 User’s Guide Security Operations 2017. 2 Ver. 1.01
Explain to the administrator of the machine that the settings for the security functions for
this machine have been specified.
Product Name Company Name User Division Name,
Contact
Customer (administrator of the
machine)
Service Representative
Person in charge
bizhub 368/308 1-6

1.2 Security Functions
1.2 Security Functions
Setting the Enhanced Security Mode to [ON] will validate the security function of this machine. For details of
the settings of different security functions to be changed by turning [ON] the Enhanced Security Mode, see
page 2-12.
The following the major security functions when the Enhanced Security Mode is set to [ON].
Function Description
Identification and authentication function
User limiting function Specific functions to be used by each user/account may be limited. For de-
HDD encryption function By setting the Encryption Key, the data stored in the HDD is encrypted, there-
Auditing function Information including operations performed on the machine and a job history
Residual information deleting function
Network communication
protecting function
1
Access control is then provided through password authentication for any access to the Administrator Mode, User Authentication mode, User Box, a User
Box data file, and a Secure Print document. Access is thereby granted only
to the authenticated user. A password that can be set must meet the Password Rules. The machine does not accept setting of an easily decipherable
password. For details of the Password Rules, see page 1-13.
If a wrong password is entered, during password authentication, a predetermined number of times (once to three times.) or more set by the administrator, the machine determines that it is unauthorized access through Prohibited
Functions When Authentication Error, prohibiting any further entry of the
password. By prohibiting the password entry operation, the machine prevents unauthorized use or removal of data. The administrator is responsible
for resetting the prohibition of the password entry operation. For details, see
page 2-25.
tails, see page 2-38.
by protecting the data in the HDD. For details, see page 2-65.
can be stored in the HDD. Setting the Job Log (Audit Log) allows an illegal
act or inadequate operation performed on the machine to be traced. The obtained Job Log can be downloaded and viewed from the Web Connection.
For details, see page 2-75.
When the machine is to be discarded or use of a leased machine is terminated at the end of the leasing contract, setting of the Overwrite HDD Data function while the machine was in use allows residual unnecessary data to be
deleted, because the machine overwrites a specific overwrite value over the
unnecessary data. This prevents data leakage. (Passwords, addresses, and
other data set while the machine was in use should, however, be deleted
manually.) For details, see page 2-71.
To delete data including the passwords, addresses, and other data all at
once, the Overwrite All Data function overwrites and erases all data stored in
all spaces of the HDD. The function also resets all passwords saved in the
flash memory and eMMC to factory settings, preventing data from leaking.
For details, see page 2-73. For details of items to be cleared by Overwrite All
Data function, see page 1-16.
Communication data transmitted to or from the machine and client PC can
be encrypted using the IPsec, which prevents information leakage through
sniffing over the network. For details, see page 1-14.
Check Count Clear Conditions
In the Enhanced Security Mode, the number of wrong entries at the time of authentication is checked. The
following is the conditions for clearing or resetting the number.
<Administrator Authentication>
- Authentication of Administrator of the machine is successful.
<User Authentication Mode>
- Authentication of User Administrator is successful.
- User Authentication mode is successful.
- Release of Prohibited Functions When Authentication Error is executed.
<Account Track Mode>
- Account Track mode is successful.
- Release of Prohibited Functions When Authentication Error is executed.
bizhub 368/308 1-7

1.2 Security Functions
<Secure Print>
- Authentication of Secure Print is successful.
- Release of Prohibited Functions When Authentication Error is executed.
<Box>
- Authentication of User Box is successful.
- Authentication for execution of change of User Box Name and User Box Password is successful.
- Release of Prohibited Functions When Authentication Error is executed.
1
bizhub 368/308 1-8

1.3 Precautions for Operation Control
1.3 Precautions for Operation Control
This machine and the data handled by this machine should be used in an office environment that meets the
following conditions. The machine must be controlled for its operation under the following conditions to protect the data that should be protected.
Roles of the Owner of the Machine
The owner (an individual or an organization) of the machine should take full responsibility for controlling the
machine, thereby ensuring that no improper operations are performed.
- The owner of the machine should have the administrator recognize the organizational security policy
and procedure, educate him or her to comply with the guidance and documents prepared by the manufacturer, and allow time for him or her to acquire required ability. The owner of the machine should
also operate and manage the machine so that the administrator can configure and operate the machine
appropriately according to the policy and procedure.
- The owner of the machine should have users of the machine recognize the organizational security policy
and procedure, educate them to follow the policy and procedure, and operate and manage the machine
so that the users acquire the required ability.
- The owner of the machine should vest the user with authority to use the machine according to the organizational security policy and procedure.
- The owner of the machine should operate and manage the machine so that the administrator checks
the Job Log (Audit Log) data at appropriate timing to thereby determine whether a security compromise
or a faulty condition has occurred during an operating period.
- If the Job Log (Audit Log) data is to be exported to another product, the owner of the machine should
ensure that only the administrator performs the task. The owner of the machine should also operate and
manage the machine so that the Job Log (Audit Log) data is not illegally accessed, deleted, or altered.
1
Roles and Requirements of the Administrator
The administrator should take full responsibility for controlling the machine, thereby ensuring that no improper operations are performed.
- A person who is capable of taking full responsibility for controlling the machine should be appointed as
the administrator to make sure that no improper operations are performed.
- When using an external authentication server, an SMTP server (mail server), or a DNS server, each server should be appropriately managed by the administrator and should be periodically checked to confirm
that settings have not been changed without permission.
Password Usage Requirements
The administrator must control the Administrator Password, Encryption Key, FW Update (USB) Password,
and User Box Password appropriately so that they may not be leaked. These passwords should not be ones
that can be easily guessed. The user, on the other hand, should control the Secure Print Password and User
Password appropriately so that they may not be leaked. Again, these passwords should not be ones that can
be easily guessed.
<To Achieve Effective Security>
- Make absolutely sure that only the administrator of the machine knows the Administrator Password.
- Make absolutely sure that only the administrator knows the Encryption Key, FW Update (USB) Pass-
word, and User Box Password.
- Make sure that the administrator of the machine changes the Administrator Password regularly.
- The administrator must change the Encryption Key, FW Update (USB) Password, and User Box Pass-
word at regular intervals.
- The administrator of the machine should make sure that any number that can easily be guessed from
birthdays, employee identification numbers, and the like is not set for the Administrator Password.
- The administrator should make sure that any number that can easily be guessed from birthdays, employee identification numbers, and the like is not set for the Account Password, Encryption Key, FW
Update (USB) Password, and User Box Password.
- If a User Password has been changed, the administrator should have the corresponding user change
the password as soon as possible.
- If the Administrator Password has been changed by the Service Engineer, the administrator of the machine should change the Administrator Password as soon as possible.
bizhub 368/308 1-9

1.3 Precautions for Operation Control
- The administrator should have users ensure that the passwords set for the User Authentication, Secure
Print, and the box that can be used by the user are known only by the user concerned.
- The administrator should have users change the passwords set for the User Authentication at regular
intervals.
- The administrator of the machine should have the user administrator log on to the User Mode and
change his or her password in [Utility] - [User Settings] - [Change Password] if he or she changes the
password.
- The administrator should make sure that any user does not set any number that can easily be guessed
from birthdays, employee identification numbers, and the like for the passwords set for the User Authentication and Secure Print.
- The administrator should disclose the Account Password to the user in accordance with the operating
environment of the machine and the security policies of the organization on his or her own responsibility.
External authentication server control requirements
The administrator and the server administrator are required to apply patches to, or perform account control
for, this machine and the external authentication server connected to the office LAN in which the machine is
installed to ensure operation control that achieves appropriate access control.
This machine can be used only after the user who uses this machine has been registered in the external authentication server. The server administrator should also check registered users at regular intervals to thereby
ensure that any unnecessary users are left registered.
1
Security function operation setting operating requirements
The administrator should observe the following operating conditions.
- The administrator should make sure that the machine is operated with the settings described in the installation checklist made properly in advance.
- The administrator should make sure of correct operation control so that the machine is used with the
Enhanced Security Mode set to [ON].
- The administrator should make sure of correct operation control so that the appropriate FW Update
(USB) Password is used with [FW Update (USB) Permission Setting] set to [Password Priority].
- When the Enhanced Security Mode is turned [OFF], the administrator is to make various settings according to the installation checklist and then set the Enhanced Security Mode to [ON] again. For details
of settings made by the service engineer, contact your service representative.
- When the machine is to be discarded or use of a leased machine is terminated at the end of the leasing
contract, the administrator should use the Overwrite HDD Data function and the Overwrite All Data
function to thereby prevent data to be protected from leaking.
Operation and control of the machine
The administrator should perform the following operation control.
- The administrator should log off from the Administrator Mode whenever the operation in the Administrator Mode is completed. The administrator of the machine should also make sure that each individual
user logs off from the User Authentication mode after the operation in the User Authentication mode is
completed, including operation of the Secure Print document, User Box, and User Box file.
- During user registration and box registration, the administrator should make sure that the correct settings are made for the correct users, including functional restrictions and box attributes.
- The administrator should set the Encryption Key and FW Update (USB) Password according to the environment, in which this machine is used.
- The administrator should appropriately control the device certificate (SSL certificate) registered in the
machine.
- The administrator should ensure that no illegal connection or access is attempted when the machine is
to be connected to an external interface.
- The administrator should appropriately control the file of Job Log (Audit Log) data downloaded to, for
example, a PC and ensure that none other than the administrator of the machine handle it.
- The administrator should check the Job Log (Audit Log) data at appropriate timing, thereby determining
whether a security compromise or a faulty condition has occurred during an operating period.
- When generating or deleting Job Log (Audit Log) and Job Log (Audit Log) data, the administrator should
check conditions of using this machine by the user.
bizhub 368/308 1-10
1.3 Precautions for Operation Control
- The administrator should make sure that each individual user updates the OS of the user's terminal and
applications installed in it to eliminate any vulnerabilities.
- The administrator should set the account track and make sure that the machine is operated through
operative association with the account track.
- The administrator should delete cache following the procedure specified for each browser when seeing
previews on a web browser because the contents can be cached on PCs and make sure that users
perform the same procedure.
- The administrator must not select a modem method when setting CS Remote Care.
- The administrator should make sure that a USB device is not illegally connected to the machine.
The administrator disables the following functions and operates and manages the machine under a condition
in which those functions are disabled.
Function Name Setting Procedure
IP Address Fax Function * Using [Administrator Settings] - [Network Settings] - [Network Fax Set-
Internet Fax Function * Using [Administrator Settings] - [Network Settings] - [Network Fax Set-
Relay User Box Using [Administrator Settings] - [Fax Settings] - [Function Settings] -
File Re-TX Box Using [Administrator Settings] - [Fax Settings] - [Function Settings], set
PC-Fax Permission Using [Administrator Settings] - [Fax Settings] - [Function Settings], set
ID & Print Delete after Print
Setting
User Box Settings Using [Administrator Settings] - [System Settings] - [User Box Settings],
Report Settings Using [Administrator Settings] - [Fax Settings], set all report output set-
Bulletin Board User Box • Do not create [Bulletin Board User Box] using [Utility] - [One-
Delete Other User Jobs Using [Administrator Settings] - [System Settings] - [Restrict User Ac-
RAW Port Number Using [Administrator Settings] - [Network Settings] - [TCP/IP Settings] -
FTP TX Settings Using [Administrator Settings] - [Network Settings] - [FTP Settings], set
SMB Settings • Using [Administrator Settings] - [Network Settings] - [SMB Settings],
E-Mail RX (POP) Using [Administrator Settings] - [Network Settings] - [E-Mail Settings], set
SNMP Settings Using [Administrator Settings] - [Network Settings], set [SNMP Settings]
TCP Socket Settings • Using [Administrator Settings] - [Network Settings] - [Forward] - [TCP
1
tings] - [Network Fax Function Settings], set [IP Address Fax Function] to
[OFF].
tings] - [Network Fax Function Settings], set [Internet Fax Function] to
[OFF].
[Function ON/OFF Setting], set [Relay RX] to [OFF].
[Incomplete TX Hold] to [No].
[PC-Fax Permission Setting] to [Restrict].
Using [Administrator Settings] - [System Settings] - [User Box Settings],
set [ID & Print Delete after Print Setting] to [Always Delete].
set [Allow/Restrict User Box] to [Prohibit].
tings of [Report Settings] to [OFF].
Touch/User Box Registration] - [Create User Box].
• Do not create [Bulletin Board User Box] using [Administrator Settings]
- [One-Touch/User Box Registration] - [Create User Box].
cess] - [Restrict Access to Job Settings], set [Delete Other User Jobs] to
[Restrict].
[RAW Port Number], set [Port 1 to Port 6] to [OFF].
[FTP TX Settings] to [OFF].
set [Client Settings] to [OFF].
• Using [Administrator Settings] - [Network Settings] - [SMB Settings],
set [SMB Server Settings] to [OFF].
• Using [Administrator Settings] - [Network Settings] - [SMB Settings],
set [WINS/NetBIOS Settings] to [OFF].
• Using [Administrator Settings] - [Network Settings] - [SMB Settings],
set [Direct Hosting Setting] to [OFF].
[E-Mail RX (POP)] to [OFF].
to [OFF].
Socket Settings], set [TCP Socket] to [OFF].
• Using [Administrator Settings] - [Network Settings] - [Forward] - [TCP
Socket Settings], set [TCP Socket (ASCII Mode)] to [OFF].
bizhub 368/308 1-11
1.3 Precautions for Operation Control
Function Name Setting Procedure
SSL/TLS Version Setting Start the Web Connection and, using [Security] - [PKI Settings] - [SSL
WebDAV Settings • Using [Administrator Settings] - [Network Settings] - [WebDAV Set-
DPWS Settings (Printer Settings/Scanner Settings)
LPD Setting Using [Administrator Settings] - [Network Settings] - [Detail Settings], set
Remote Access Setting Using [Administrator Settings] - [Network Settings], set [Remote Access
LLMNR Setting Using [Administrator Settings] - [Network Settings] - [TCP/IP Settings],
AirPrint Using [Administrator Settings] - [Authorization function Setting] - [Install
Bonjour Setting Using [Administrator Settings] - [Network Settings], set [Bonjour Setting]
Mopria Setting Using [Administrator Settings] - [Network Settings] - [Mopria Setting], set
Send Domain Limit Settings Using [Administrator Settings] - [Network Settings], set [Send Domain
LLTD Setting Using [Administrator Settings] - [Network Settings] - [Detail Settings] -
Personal Data Security Settings
1
Setting] of the administrator mode, cancel the selection of [SSLv3] of
[SSL/TLS Version Setting].
tings], set [WebDAV Client Settings] to [OFF].
• Using [Administrator Settings] - [Network Settings] - [WebDAV Settings], set [WebDAV Server Settings] to [OFF].
• Using [Administrator Settings] - [Network Settings] - [DPWS Settings],
set [Printer Settings] to [OFF].
• Using [Administrator Settings] - [Network Settings] - [DPWS Settings],
set [Scanner Settings] to [OFF].
[LPD Setting] to [Disable].
Setting] to [OFF].
set [LLMNR Setting] to [Disable].
License] - [Function Code], prohibit entering the AirPrint-enabling code
and enabling AirPrint.
to [OFF].
[Terminal Request Response Setting] to [OFF] and do not to set it to [ON].
Limit Settings] to [Do Not Limit] and do not to set it to [Limit].
[Device Setting], set [LLTD Setting] to [Disable] and do not to set it to [Enable].
Using [Administrator Settings] - [Security Settings] - [Security Details], set
[Job History] and [Current Job] under [Personal Data Security Settings] to
[Yes].
*: It will not be displayed in case of service mode where the setting is not configured (the function is set to
OFF when it is not displayed).
Machine Maintenance Control
The administrator should perform the following maintenance control activities.
- Provide adequate control over the machine to ensure that only the Service Engineer is able to perform
physical service operations on the machine.
- Provide adequate control over the machine to ensure that any physical service operations performed
on the machine by the Service Engineer are overseen by the administrator.
- Some options require that Enhanced Security Mode be turned [OFF] before they can be used on the
machine. If you are not sure whether a particular option to be additionally purchased is fully operational
with the Enhanced Security Mode turned [ON], contact your Service Representative.
- Install the machine at a safe site that can be monitored and operate and manage the machine while
ensuring that the machine is protected from unauthorized physical access.
Precautions for using the printer driver
The following precautions should be used when the printer driver is to be used in this machine:
- When a document is to be transmitted from the PC to the machine, user registration is necessary in
advance.
- With the external server authentication, a user is registered in this machine when he or she has been
successful in identification authentication on the control panel.
- Any document that has been transmitted by a user who is yet to be registered is discarded.
bizhub 368/308 1-12
1.4 Miscellaneous
1.4 Miscellaneous
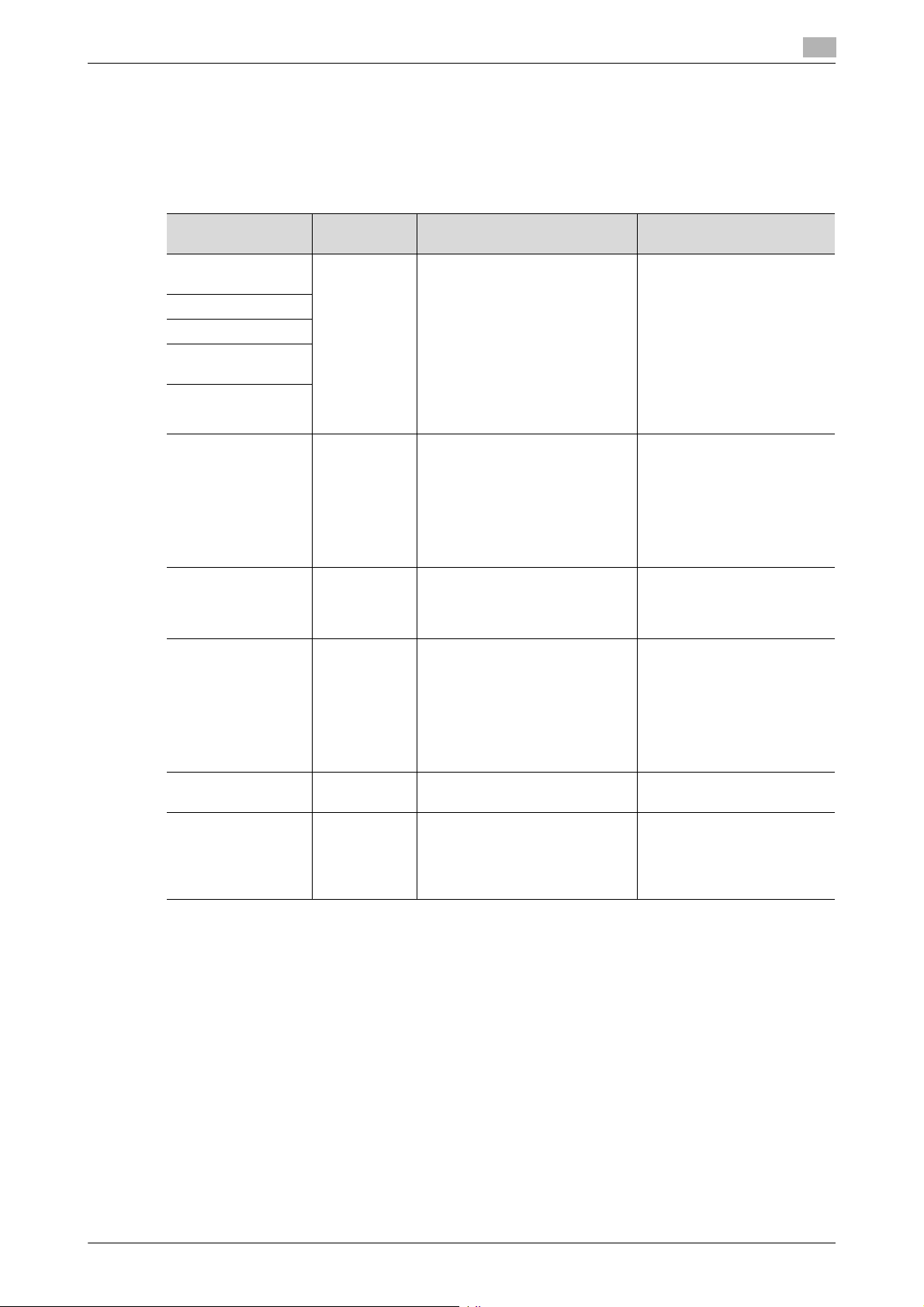
Password Rules
Study the following table for details of the number and types of characters that can be used for each password. For details of the settings of the Password Rules, see page 2-15.
1
Types of
passwords
Administrator
Password
User Password
Account Password
Public User Box
Password
Annotation User
Box Password
Secure Print
Password
Confidential RX
password
FW Update (USB)
Password
Memory RX User
Box Password
Encrypted PDF
Password
*
: The minimum number of characters set in [Set Minimum Password Length] must be set for the password.
The default value is 12.
Precautions for Use of Umlaut
- Setting or entering an umlaut from the control panel may be disabled depending on the setting made
in this machine, but not on the client PC side including Web Connection. If an umlaut is set in a password on the PC side, therefore, the umlaut cannot be entered from the control panel, which means that
this particular password is not usable.
Number of
characters
8 to 64
characters
8 to 64
characters
8 characters • Numeric characters: 0 to 9
0 to 20
characters
1 to 8
characters
- - • The password rules are
Types of characters Conditions for set-
• Numeric characters: 0 to 9
*
• Alpha characters: upper and
lower case letters
• Symbols: !, #, $, %, &, ', (, ),
*, ,, -, ., /, :, ;, <, =, >, ?, @, [,
\, ], ^, _, `, {, |, }, ~, +
• Special characters (98 characters)
Selectable from among a total of
191 characters
• Numeric characters: 0 to 9
*
• Alpha characters: upper and
lower case letters
• Symbols: !, #, $, %, &, ', (, ),
*, ,, -, ., /, :, ;, <, =, >, ?, @, [,
\, ], ^, _, `, {, |, }, ~, +, SPACE
Selectable from among a total of
94 characters
• Symbols: *, #
• Numeric characters: 0 to 9
• Alpha characters: upper and
lower case letters
• Symbols: !, #, $, %, &, ', (, ),
*, ,, -, ., /, :, ;, <, =, >, ?, @, [,
\, ], ^, _, `, {, |, }, ~, +, SPACE
Selectable from among a total of
94 characters
• Numeric characters: 0 to 9 • The password rules are
ting/changes
• A password only consisting of identical characters cannot be registered
or changed.
• The current password
must be entered before a
change can be made in
the setting.
• A new password to be
set should not be the
same as the current one.
• A password only consisting of identical characters cannot be
registered.
• A password only consisting of identical characters cannot be registered
or changed.
• A new password needs
to be re-entered.
not applicable.
not applicable.
• Password that is set
when PDF document is
created.
bizhub 368/308 1-13

1.4 Miscellaneous
Precautions for Use of Various Types of Applications
Comply with the following requirements when using the Web Connection or an application of various other
types
The administrator should make sure that the user observes the following requirements.
- The password control function of each application stores the password that has been entered in the PC
being used. Disable the password management function of each application and perform an operation
without storing a password.
Use a web browser or an application of various other types that shows "*" or "-" for the password entered.
- Once the password has been entered, do not leave your PC idle without logging on.
- Set the web browser so that cache files are not saved.
- Do not access any other site once you have logged onto the machine with the Web Connection. Ac-
cessing any other site or a link included in e-mail, in particular, can lead to execution of an unintended
type of operation. Whenever access to any other site is necessary, be sure first to log off from the machine through the Web Connection.
- Using the same password a number of times increases the risk of spoofing.
- If a web browser such as Internet Explorer is used on the client PC side, "TLS v1.0" or more should be
used for the SSL setting.
- Optional applications not described in this User’s Guide are not covered by certification of ISO15408.
Encrypting communications
1
This machine guarantees encrypted communication via IPsec.
IPsec setting
This machine offers a choice of two authentication methods of [Pre-Shared Key] and [Digital Signature] for
authenticating the remote machine with which to communicate.
When [Pre-Shared Key] is to be used, control the pre-shared key appropriately to ensure that it is not leaked
to any third party other than the remote machine with which to communicate. For the shared key, set a value
that consists of a combination of eight or more alphanumeric characters and that cannot be easily guessed.
Do not set a value that can be easily guessed from your birthday, employee identification number, and the
like.
[Digital Signature] has a higher security strength than [Pre-Shared Key].
The ISO15408 evaluation for the machine is performed on the basis of the [Pre-Shared Key].
Do not use DES or 3DES in the encryption algorithm of [IKE Settings]. Use AES. [Main Mode] and [Aggressive
Mode] are available in [Negotiation Mode]. The default setting is [Main Mode]. The administrator should operate the machine with the [Main Mode] setting.
Leaking the pre shared key for IPsec set on the MFP increases the risk of spoofing of the MFP, etc. Therefore,
set machine-specific pre shared keys and manage them safely.
An illegal DNS response (e.g., a response exceeding 2048 bytes) made by the DNS server may cause the
TOE to perform an unexpected operation. The administrator should control such that the DNS server does
not make such a response. It should also be noted that setting of multiple DNS servers increases the risk.
Note that unencrypted communication can be established if the IPsec setting is not made over the whole address range (0 to 255 for IPv4) and an IP address outside the range is assigned to a client PC.
Select an ESP Encryption Algorithm from AES-GCM, AES-CBC, and AES-CTR for IPsec SA Settings. Furthermore, when AES-CBC or AES-CTR is selected, select an ESP Authentication Algorithm from SHA-1,
SHA-2, and AES-XCBC.
NOTICE
The administrator of the machine should make sure that SSL encryption communication is not performed with
the SSL set in SSL v3.
Do not use an SSL certificate that is electronically signed by MD5, as an increased risk results of data to be
protected being tampered with or leaked.
To eliminate the risk of the data to be protected being tampered with or leaked, refer to the recommended
ciphers list disclosed by, for example, NIST and CRYPTREC and use the appropriate cryptographic technique.
bizhub 368/308 1-14

1.4 Miscellaneous
Use the following browsers to ensure safety. Use of any of the following browsers achieves communication
that ensures confidentiality of the image data transmitted and received.
Microsoft Internet Explorer
- 9/10/11
Mozilla Firefox
- 20 or later
Microsoft Internet Explorer 11 is used for the ISO15408 evaluation for this machine.
Print functions
Only the following procedures are guaranteed for the print functions performed from the client PC.
- Use IPPS printing for the print functions performed using the printer driver.
- Use direct printing from the Web Connection for the print functions not performed via the printer driver.
IPP printing
IPP (Internet Printing Protocol) is a function that allows printing via the Internet by using the HTTP (HyperText
Transfer Protocol) of the TCP/IP Protocol. IPPS (IPP over SSL/TLS) is the type of IPP that performs the SSL
encryption communication.
<Installing printer driver>
To perform IPPS printing, the printer driver must be installed. Start the printer addition wizard of the Windows
Vista/7/8/8.1/Server 2008/Server 2008 R2/Server 2012/Server 2012 R2 and type [DNS Host Name] and
[Default DNS Domain Name] of this machine in the following format in the "URL" field.
https://[DNS host name].[default DNS domain name]/ipp
For [DNS host name] and [default DNS domain name], specify the names set with the DNS server.
1
<Registering the certificate in Windows Vista or later>
Windows Vista or later, which offers enhanced security functions, gives a certificate error message if the SSL
certificate is one that is not issued by a certification body. In such cases, it becomes necessary to register
the certificate of this machine as that issued by a reliable party for the computer account.
First, register Host Name and IP address of this machine in the DNS server in advance. Then, in TCP/IP Settings of Web Connection, set the DNS Host Name and DNS Default Domain Name registered with the DNS
server.
It should also be noted that, for the certificate to be imported, a certificate for SSL encryption communication
should be registered in Web Connection and exported in advance as the certificate including the public key.
1 From "Continue to this website," call the Web Connection window to the screen.
2 Click "Certificate Error" to display the certificate. Then, click "Install Certificate" to install the certificate.
3 Display the physical stores. Then, deploy the certificate, which has earlier been exported, in "Local
Computer" of "Trusted Root Certification Authorities" to thereby import the certificate.
bizhub 368/308 1-15

1.4 Miscellaneous
Items of Data Cleared by Overwrite All Data Function
The Overwrite All Data function clears the following items of data.
Items of Data Cleared Description
Password Rules Sets [Disable] and disables [Set Minimum Password Length]
User registration data Deletes all user-related data that has been registered
Account track registration data Deletes all account track-related data that has been registered
Box registration data/file Deletes all User Box-related information and files saved in User Box
Secure Print ID/Password/
document
ID & Print document Deletes all ID & Print documents saved in ID & Print User Box
Image files • Image files other than Secure Print documents, ID & Print docu-
Destination recipient data files Deletes all destination recipient data including e-mail addresses and
Encryption Key Clears the currently set Encryption Key
Administrator Password Clears the currently set password, resetting it to the factory setting
FW Update (USB) Password Clears the currently set FW Update (USB) Password
Device certificate
(SSL certificate)
SSL encryption strength Deletes the SSL certificate to thereby clear the SSL encryption
SSL-compliant protocol Makes the protocol not complying with SSL
Network Setting Clears the currently set network settings (DNS Server setting, IP Ad-
Daylight Saving Time Set to [No]
Time Adjustment Setting (NTP) Set to [OFF]
Time/date data Varies corrected data, if the time-of-day data is corrected due to, for
1
Deletes all Secure Print document-related information and files saved
ments, and User Box files
• Data files left in the HDD data space, used as image files and not
deleted through the general deletion operation
• Temporary data files generated during print image file processing
telephone numbers
(1234567812345678)
Deletes the currently set Device certificate (SSL certificate)
strength
dress setting, and SMTP Server setting), resetting it to the factory setting
example, the daylight saving time
Fax functions
An optional Fax Kit is required for using fax functions. Contact your Service Representative.
USB keyboard
The USB keyboard is not used for the ISO15408 evaluation for this machine.
Do not use a USB keyboard.
bizhub 368/308 1-16

1.4 Miscellaneous
Different types of boxes
A box may be a user box or a system box. The user can store documents in the User Box. Also, the user can
print a file from the User Box or send a file to another user. The System Box is used by the system to temporarily store files when the user uses the facsimile or print function together with the file storage function of
the box.
The User Box (*) cannot be used under the operation and control of this machine.
Type Description
Public User Box * This is the public box in which all users can store documents and use
Personal User Box * This is a personal box. Only users who have logged in to the system
Group User Box * This is a group box. Only users belonging to the same department (or
Secure Print Box When you print a document from the PC or when you select the Se-
Memory RX Box When a facsimile is received by the Memory RX function, it is stored
ID & Print Box When you print a document from the PC, the files transferred with the
Annotation User Box When a stored file is printed out or sent to another user, its date, time
Password Encrypted PDF Box When a password protected PDF file is printed out or stored in the
1
them. Note that a password is set for the box and the set password
needs to be entered before access can be gained to the box.
can store and use documents in the Personal User Box.
group) can store and use documents in the Group User Box.
cure Print function using the printer driver, this data file is stored in the
Secure Print User Box.
in the Memory RX User Box.
ID & Print function are stored in the ID & Print User Box.
and any annotations are added to this box automatically.
User Box, the file is stored in the Password Encrypted PDF User Box.
Hardware and software used in the machine
The following lists the software, hardware, and their versions used for the ISO15408 evaluation for this machine and they are the same as those listed on the security target.
The ISO15408 evaluation assumes that the HDD is mounted in the machine. Any configuration not including
the HDD is not guaranteed by the ISO15408 evaluation.
The user should appropriately manage the hardware and software used with the machine on his or her own
responsibility.
Hardware/software Version, etc.
FAX Kit FK-514
Printer Driver PCL: Ver. 6.1.2.0
PS: Ver. 6.1.2.0
XPS: Ver. 6.1.2.0
Data Administrator with Device Set-Up and Utilities
Data Administrator Ver. 4.1.38000
External authentication server Active directory mounted on Windows Server 2008 R2 Standard Ser-
DNS server Windows Server 2008 R2 Standard Service Pack1
Ver. 1.0.09000
vice Pack 1
Firmware integrity verification function
When the main power switch is turned ON with the Enhanced Security Mode set to [ON], the machine
checks the encryption key and the hash value to thereby determine that its firmware is fully operational.
If a fault occurs in the firmware, a malfunction screen appears when the machine is started, warning that a
fault has occurred. To reset the fault condition, turn [OFF] the Enhanced Security Mode and restart the machine, or update the firmware. For more details, consult your Service Representative.
bizhub 368/308 1-17
1.4 Miscellaneous
CS Remote Care function
CS Remote Care is a system that manages the machine through transmission and reception of various types
of data for managing the machine between the machine and the CS Remote Care center computer via a telephone/fax line, a network, or E-mail. Functions are disabled to access the LAN from the telephone line and
to directly transfer received fax.
When the Enhanced Security Mode is set to [ON], the following functions are no longer usable: instructing to
rewrite the firmware, sending and receiving account counter information, rewriting settings of the machine,
and the Counter Remote Control function.
Terminating a Session and Logging out
The machine allows the operator to automatically log out from or terminate a session, if it is unable to detect
an operation on the control panel or a communication packet on the network. Additionally, if a user changes
the user password on the control panel while the same user accessing the machine via Web Connection,
the session of Web Connection is terminated.
The following shows the setting range and the default setting of each function. Set the time according to the
environment in which the machine is used.
The administrator should explain to the user that the following settings are made. The administrator should
also explain to the user immediately as soon as the setting has been changed.
Function name/software, etc Description
System Auto Reset Setting range
Auto Logout
(Web Connection)
Data Administrator Default setting: [60] minutes (No change can be made in the setting)
1
• [1] to [9] minutes, Default setting: [1] minute
Setting procedure
• [Utility] - [Administrator Settings] - [System Settings] - [Reset Settings] - [System Auto Reset]
Setting range
• [Admin. Mode Logout Time]: [1] to [60] minutes
Default setting: [10] minutes
• [User Mode Logout Time]: [1] to [60] minutes
Default setting: [60] minutes
Setting procedure
• Start the Web Connection and, in the Administrator Mode, select
[Security] - [Auto Logout].
The time setting represents consideration for the time-consuming
task, such as downloading the registered information. Be careful
about leaving your seat, because the time setting is rather long.
Authentication error during external server authentication
If a user is unable to log in successfully during user authentication using the external server authentication,
possible causes include the status of connection to the external server, the condition of the external server
(the server is down), and the status of user registration with the external server such as the number of users
to be controlled by the machine reaching its limit and the user password quality on the external server.
The administrator should check these points and make the appropriate settings.
bizhub 368/308 1-18

2
Administrator Operations

2.1 Accessing the Administrator Mode
2 Administrator Operations
2.1 Accessing the Administrator Mode
In Administrator Mode, the settings for the machine system and network can be registered or changed.
This machine implements authentication of the user of the Administrator Mode function through the Administrator Password or User Password that verifies the identity as the administrator of the person who accesses
the function. During the authentication procedure, the Administrator Password entered for the authentication
purpose appears as "*" or "-" on the display.
When the Enhanced Security Mode is set to [ON], the number of times in which authentication fails is counted.
NOTICE
Make sure that none of the general users of the machine will know the Administrator Password.
If the Administrator Password is forgotten, it must be set again by the Service Engineer. Contact your Service
Representative.
The user who is given the administrative right by the administrator can access the Administrator Mode when
logging on as the user administrator.
2
2.1.1 Accessing the Administrator Mode
The machine does not accept access to the Administrator Mode under any of the following conditions. Wait
for some while before attempting to gain access to the Administrator Mode again.
- The Administrator Mode has been logged on to through access made from the PC.
- A remote operation is being performed from an application on the PC.
- There is a job being executed by the machine.
- There is a reserved job (timer TX, fax redial waiting, etc.) in the machine.
- Immediately after the main power switch has been turned ON.
- A malfunction code is displayed on the machine.
<From the Control Panel as the Administrator of the Machine>
0 If another administrator has already logged on to the Administrator Mode using Web Connection, the
machine displays a message saying that other administrator has logged on and rejects access as the
administrator. Wait until the message disappears before attempting to access the Administrator Mode
once again.
0 When accessing the Administrator Mode from the control panel, if [Export to the device] operation is
being executed using the Data Administrator, the machine displays a message that tells not to turn
off the power because of the remote operation being performed and rejects any operation on the control panel. Wait until the message disappears before attempting to access the Administrator Mode once
again.
0 Do not leave the machine with the setting screen of Administrator Mode left shown on the display. If it
is absolutely necessary to leave the machine, be sure first to log off from the Administrator Mode.
bizhub 368/308 2-2

2.1 Accessing the Administrator Mode
1 Touch [Utility].
2 Touch [Administrator Settings].
3 Enter the Administrator Password from the keyboard.
2
% Touch [C] to clear all characters.
% Touch [Delete] to delete the last character entered.
% Touch [Shift] to show the upper case/symbol screen.
% Touch [Cancel] to go back to the previous screen.
4 Touch [OK].
% If a wrong Administrator Password is entered, a message that tells that the Administrator Password
does not match appears. Enter the correct Administrator Password.
% If the Enhanced Security Mode is set to [ON], entry of a wrong password is counted as unauthorized
access. If a wrong Administrator Password is entered a predetermined number of times (once to
three times) or more set by the administrator, a message appears saying that the machine accepts
no more Administrator Passwords because of unauthorized access for any subsequent entry of the
Administrator Password. The machine is then set into an access lock state.
To cancel the access lock state, settings must be made by the Service Engineer; or, turn off, and
then turn on, the main power switch of the machine. If the main power switch is turned off and
on, the access lock state is canceled after the lapse of time set for [Release Time Settings]. When
the main power switch is turned off, then on again, wait at least 10 seconds to turn it on after turning it off. If there is no wait period between turning the main power switch off, then on again, the
machine may not function properly.
5 Press the Reset key to log off from the Administrator Mode.
bizhub 368/308 2-3
2.1 Accessing the Administrator Mode
<From the Control Panel as the User Administrator>
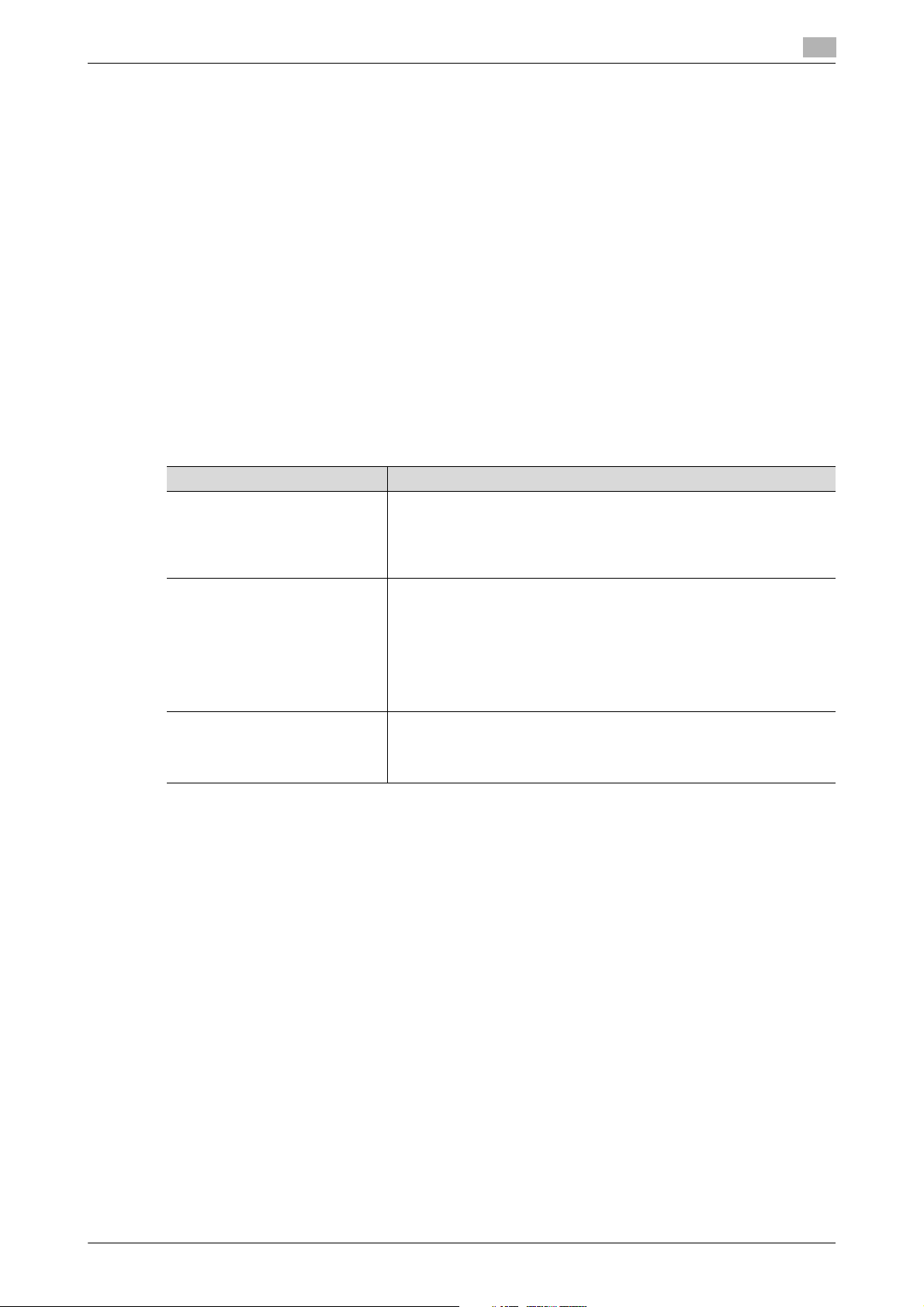
1 Touch [Operation Rights] to select [Administrator].
2 Enter the user name and the password, then touch [OK].
3 Touch [Login] or press the Access key to log in to this machine.
2
4 Touch Menu - [Utility] - [Administrator Settings].
5 The Administrator Mode is displayed. Perform a desired operation.
6 Press the Reset key to log off from the Administrator Mode.
bizhub 368/308 2-4

2.1 Accessing the Administrator Mode
<From the Web Connection as the Administrator of the machine>
0 If you have already logged on to the Admin Mode from the control panel or using Web Connection, the
machine displays a message that tells that another administrator has previously logged on and rejects
any attempt to log on to the Admin Mode using the Web Connection. Click [OK] and wait for some
while before attempting to access the Admin Mode once again.
0 If [Export to the device] operation is being executed using the Data Administrator, the machine dis-
plays a message that tells you cannot log on to the mode because of the remote operation being performed and rejects any attempts to the Admin Mode via the Web Connection. Click [OK] and wait for
some while before attempting to access the Admin Mode once again.
0 Do not leave the machine with the Admin Mode setting screen left shown on the display. If it is abso-
lutely necessary to leave the machine, be sure first to log off from the Admin Mode.
0 If you have logged on to the Admin Mode using the Web Connection and if you close the web browser
without clicking [Logout], the control panel remains locked for 160 sec.
0 Different initial screens appear after you have logged on to the Admin Mode depending on the Custom-
ize setting. The descriptions herein given are concerned with the display screen set in [Meter Counter]
of Maintenance.
1 Start the Web browser.
2 Enter the IP address of the machine in the address bar.
3 Press the [Enter] key to start Web Connection.
2
4 Click the Administrator radio button and [Login].
5 Select the "Administrator (Admin Mode)" in the Administrator, and enter the Administrator Password in
the "Password" box.
bizhub 368/308 2-5

2.1 Accessing the Administrator Mode
% If "Administrator (Admin Mode)" is selected, the settings for the machine system and network can
be registered or changed.
% When accessing the Admin Mode using the Web Connection, enter the same Administrator Pass-
word as that for the machine.
6 Click [OK].
% If a wrong Administrator Password is entered, a message that tells that the authentication has failed
appears. Enter the correct Administrator Password.
% If the Enhanced Security Mode is set to [ON], entry of a wrong password is counted as unauthorized
access. If a wrong Administrator Password is entered a predetermined number of times (once to
three times) or more set by the administrator, a message appears saying that the machine accepts
no more Administrator Passwords because of unauthorized access for any subsequent entry of the
Administrator Password. The machine is then set into an access lock state.
To cancel the access lock state, settings must be made by the Service Engineer; or, turn off, and
then turn on, the main power switch of the machine. If the main power switch is turned off and
on, the access lock state is canceled after the lapse of time set for [Release Time Settings]. When
the main power switch is turned off, then on again, wait at least 10 seconds to turn it on after turning it off. If there is no wait period between turning the main power switch off, then on again, the
machine may not function properly.
7 Click [Logout].
8 Click [OK].
This allows you to log off from the Admin Mode.
2
bizhub 368/308 2-6
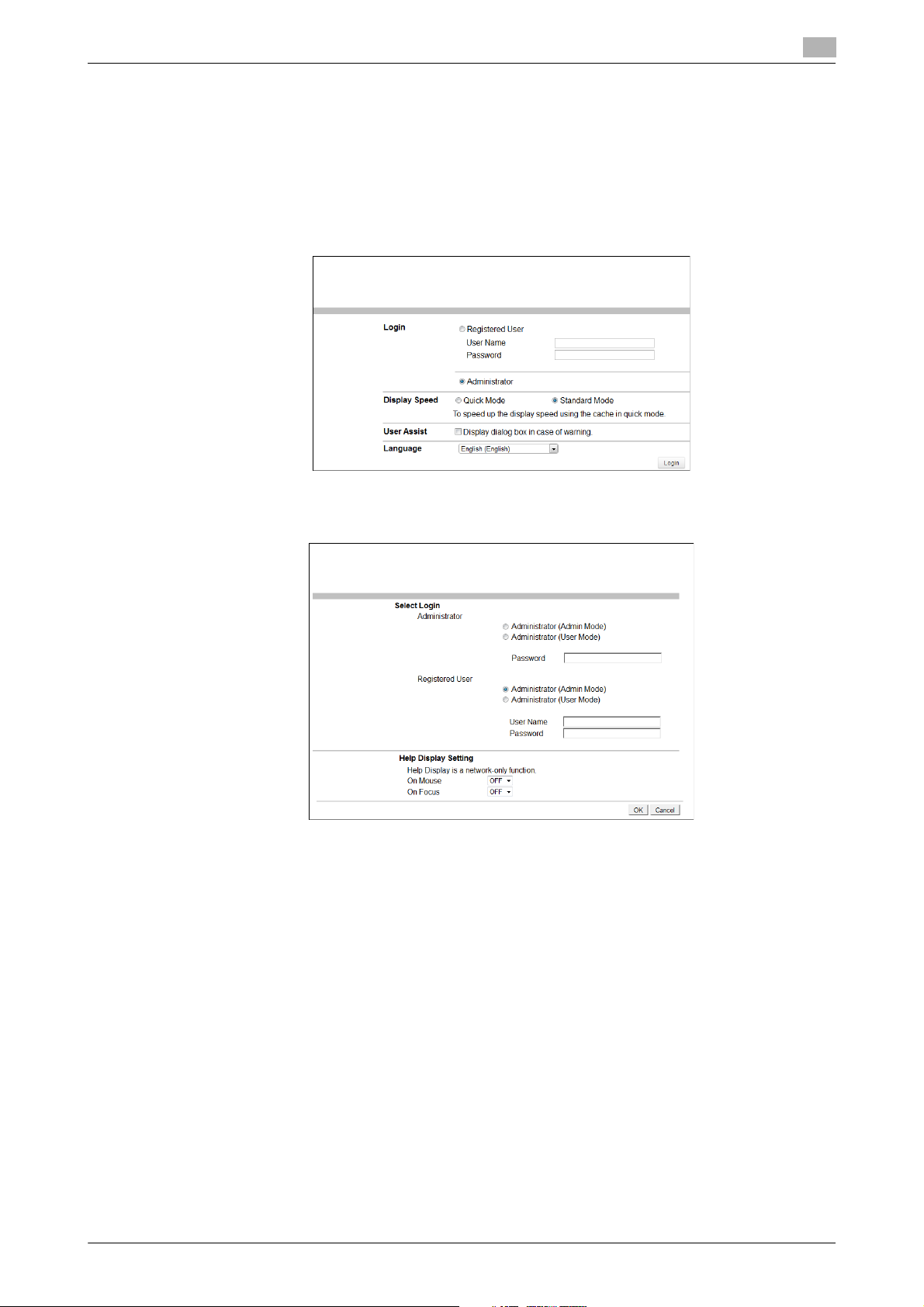
2.1 Accessing the Administrator Mode
<From the Web Connection as the User Administrator>
1 Start the Web browser.
2 Enter the IP address of the machine in the address bar.
3 Press the [Enter] key to start Web Connection.
4 Click the Administrator radio button and [Login].
5 Select "Administrator (Admin Mode)" in the Registered User and enter the user name in the "User
Name" box and the user password in the "Password" box.
2
% If "Administrator (Admin Mode)" is selected, the settings for the machine system and network can
be registered or changed.
% When accessing the Admin Mode using the Web Connection, enter the same User Password as
that for the machine.
6 Click [OK].
% If a user administrator enters a wrong User Password, a message that tells that the authentication
has failed appears. Enter the correct User Password.
% If the Enhanced Security Mode is set to [ON], the entry of a wrong User Password is counted as
unauthorized access. If a wrong User Password is entered a predetermined number of times (once
to three times) or more set by the administrator, a message appears saying that the machine accepts no more User Passwords because of unauthorized access for any subsequent entry of the
User Password. The machine is then set into an access lock state. To cancel the access lock state,
the administrator must perform the Release Setting. Contact the administrator.
7 Click [Logout].
8 Click [OK].
This allows you to log off from the User Administrator Mode.
bizhub 368/308 2-7

2.1 Accessing the Administrator Mode
Tips
2.1.2 Accessing the User Mode
You can log on to the User Mode as an administrator. In the User Mode, you can check or delete a job, which
is disabled in Administrator Mode.
The authority relating to box settings is the same as that of Administrator Mode.
<From the Control Panel>
0 The administrator must first make User Authentication settings before he or she can access User Mode.
For details of the User Authentication, see page 2-27.
0 Do not leave the machine with the User Mode setting screen left shown on the display. If it is absolutely
necessary to leave the machine, be sure first to log off from the User Mode.
1 Touch the keyboard icon in the [User Name] field.
2
2 Enter "admin" in [User Name]. Enter the password set for this machine in [Password].
% Touch [C] to clear all characters.
% Touch [Delete] to delete the last character entered.
% Touch [Shift] to show the upper case/symbol screen.
% Touch [Cancel] to go back to the previous screen.
3 Touch [OK].
bizhub 368/308 2-8
 Loading...
Loading...