Konica Minolta bizhub PRO 1051, TWAIN driver, 1051 User Manual

User’s Guide
4037-9571-05
TWAIN driver

Contents
1 Introduction
1.1 System requirements ........................................................................1-1
2 Installing the TWAIN Driver
2.1 Installation procedure .......................................................................2-1
To install the software ....................................................................2-1
2.2 Uninstalling ........................................................................................2-1
3 Importing Images
3.1 To import images ..............................................................................3-1
Import procedure ............................................................................3-1
3.2 Scanning Using the PUSH Scan Function ......................................3-4
To scan using the PUSH Scan function .........................................3-4
3.3 Scanning Using the Prescan Function ............................................3-6
To scan using the Prescan function ...............................................3-6
3.4 With user authentication ..................................................................3-8
To perform the user authentication operation ................................3-8
3.5 With account track .......................................................................... 3-10
To perform the account track operation .......................................3-10
3.6 Settings in the Main Window .........................................................3-11
3.7 Parameters on the Settings tab .....................................................3-12
3.8 Parameters on the Image tab ........................................................3-14
3.9 Parameters on the Area tab ...........................................................3-15
4 Selecting the Scanning Device
To select a device ........................................................................... 4-1
5 Registering a New Scanning Device
To register a device ........................................................................5-1
5.1 Checking Authentication Information .............................................5-4
TWAIN driver i

About this Product
With the TWAIN driver, a multifunctional product (MFP) can be used as a network scanner. The scan data can be imported into an image-processing application on the computer, where the data can be processed or edited.
Trademarks and registered trademarks
Trademark acknowledgements
®
Microsoft
Microsoft Corporation in the United States and/or other countries.
and Windows® are either registered trademarks or trademarks of
RSA® is a registered trademark or trademark of RSA Security Inc. RSA
BSAFE
United States and/or other countries.
All other company and product names are either trademarks or registered
trademarks of their respective companies.
Dialog boxes
The dialog boxes shown in this manual are those that appear in Windows XP.
®
is a registered trademark or trademark of RSA Security Inc. in the
License information
This product includes RSA BSAFE Cryptographic software
from RSA Security Inc.
2
Note
The dialog boxes that appear in this document may differ from those that
appear on your computer, depending on the installed devices and specified settings.
2
Note
Unauthorized reproduction, translation or duplication of this document,
whether in its entirety or in part, is strictly prohibited.
The content of this document is subject to change without notice.
Copyright © 2005 KONICA MINOLTA BUSINESS TECHNOLOGIES, INC. All
rights reserved.
TWAIN driver ii

LICENSE ISSUES
The OpenSSL toolkit stays under a dual license, i.e. both the conditions of
the OpenSSL License and the original SSLeay license apply to the toolkit.
See below for the actual license texts. Actually both licenses are BSD-style
Open Source licenses. In case of any license issues related to OpenSSL
please contact openssl-core@openssl.org.
OpenSSL License
Copyright © 1998-2001 The OpenSSL Project. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must
display the following acknowledgment:
"This product includes software developed by the OpenSSL Project for
use in the OpenSSL Toolkit. (http://www.openssl.org/)"
4. The names "OpenSSL Toolkit" and "OpenSSL Project" must not be used
to endorse or promote products derived from this software without prior
written permission. For written permission, please contact opensslcore@openssl.org.
5. Products derived from this software may not be called "OpenSSL" nor
may "OpenSSL" appear in their names without prior written permission
of the OpenSSL Project.
6. Redistributions of any form whatsoever must retain the following acknowledgment:
"This product includes software developed by the OpenSSL Project for
use in the OpenSSL Toolkit (http://www.openssl.org/)"
THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT "AS IS" AND
ANY EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT
SHALL THE OpenSSL PROJECT OR ITS CONTRIBUTORS BE LIABLE FOR
ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON
ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY,
OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY
TWAIN driver iii

WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
This product includes cryptographic software written by Eric Young
(eay@cryptsoft.com). This product includes software written by Tim Hudson
(tjh@cryptsoft.com).
Original SSLeay License
Copyright © 1995-1998 Eric Young (eay@cryptsoft.com) All rights reserved.
This package is an SSL implementation written by Eric Young (eay@cryptsoft.com).
The implementation was written so as to conform with Netscapes SSL.
This library is free for commercial and non-commercial use as long as the following conditions are aheared to. The following conditions apply to all code
found in this distribution, be it the RC4, RSA, lhash, DES, etc., code; not just
the SSL code. The SSL documentation included with this distribution is covered by the same copyright terms except that the holder is Tim Hudson
(tjh@cryptsoft.com).
Copyright remains Eric Young’s, and as such any Copyright notices in the
code are not to be removed.
If this package is used in a product, Eric Young should be given attribution
as the author of the parts of the library used.
This can be in the form of a textual message at program startup or in documentation (online or textual) provided with the package.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the copyright notice, this list
of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must
display the following acknowledgement:
"This product includes cryptographic software written by Eric Young
(eay@cryptsoft.com)"
The word ‘cryptographic’ can be left out if the rouines from the library being used are not cryptographic related.
4. If you include any Windows specific code (or a derivative thereof) from
the apps directory (application code) you must include an acknowledgement:
"This product includes software written by Tim Hudson (tjh@cryptsoft.com)"
TWAIN driver iv

THIS SOFTWARE IS PROVIDED BY ERIC YOUNG "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
(INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE
GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH
DAMAGE.
The licence and distribution terms for any publically available version or derivative of this code cannot be changed. i.e. this code cannot simply be copied and put under another distribution licence [including the GNU Public
Licence].
TWAIN driver v

Introduction
1 Introduction
1.1 System requirements
In order to use this software, a TWAIN-compatible image-processing application must first be installed on the computer.
- Operating system
Windows NT Workstation 4.0 (SP6a or later)
Windows NT Server 4.0 (SP6a or later)
Windows 2000 Professional (SP4 or later)
Windows XP Home Edition (SP3 or later)
Windows XP Professional (SP3 or later)
Windows Vista Home Basic (SP1 or later)*
Windows Vista Home Premium (SP1 or later)*
Windows Vista Business (SP1 or later)*
Windows Vista Enterprise (SP1 or later)*
Windows Vista Ultimate (SP1 or later)*
* 32-bit (x86) editions of Windows Vista are supported.
- Computer
According to the environment recommended for the operating system
- Memory
According to the environment recommended for the operating system
- Network
Computer with TCP/IP protocol settings correctly specified
- Hard disk
20 MB or more of available space
1
TWAIN driver 1-1

Installing the TWAIN Driver
2 Installing the TWAIN Driver
2.1 Installation procedure
Follow the procedure described below to install the TWAIN driver.
The enclosed User Software CD-ROM is required to install the software.
To install the software
1 Turn the computer on and start Windows.
2 Insert the User Software CD-ROM into the computer’s CD-ROM drive.
– The CD menu is displayed.
2
3 Select "TWAIN Driver" from "Scanner Install" and follow the instruc-
tions on the screen.
Installation begins and the necessary files are copied to the computer.
When all of the necessary files have been copied to the computer, the
Installation Completed dialog box appears.
4 Click [Finish].
The installation of the TWAIN driver is complete.
2.2 Uninstalling
The TWAIN driver can be uninstalled using either of the following two methods.
- Using "Add or Remove Programs" ("Add/Remove Programs" with Windows 2000)
- Using Setup.exe again
2
Note
Before uninstalling, quit the TWAIN driver.
TWAIN driver 2-1
Importing Images
3 Importing Images
3.1 To import images
Images can be imported from the image-processing application compatible
with the TWAIN driver. Here, an example is given using Adobe Photoshop.
2
Note
If the multifunctional product is not set to allow scanner transmissions, it
will not be possible to scan an image with the TWAIN driver.
Import procedure
1 Start up the application to be used for processing the image.
3
2 From the [File] menu, point to [Import], and then select the TWAIN driv-
er.
– Depending on the program, the command "Select Device" may be
available.
If this is the case, click "Select Device" and select the TWAIN driver.
Then, carry out the import operation.
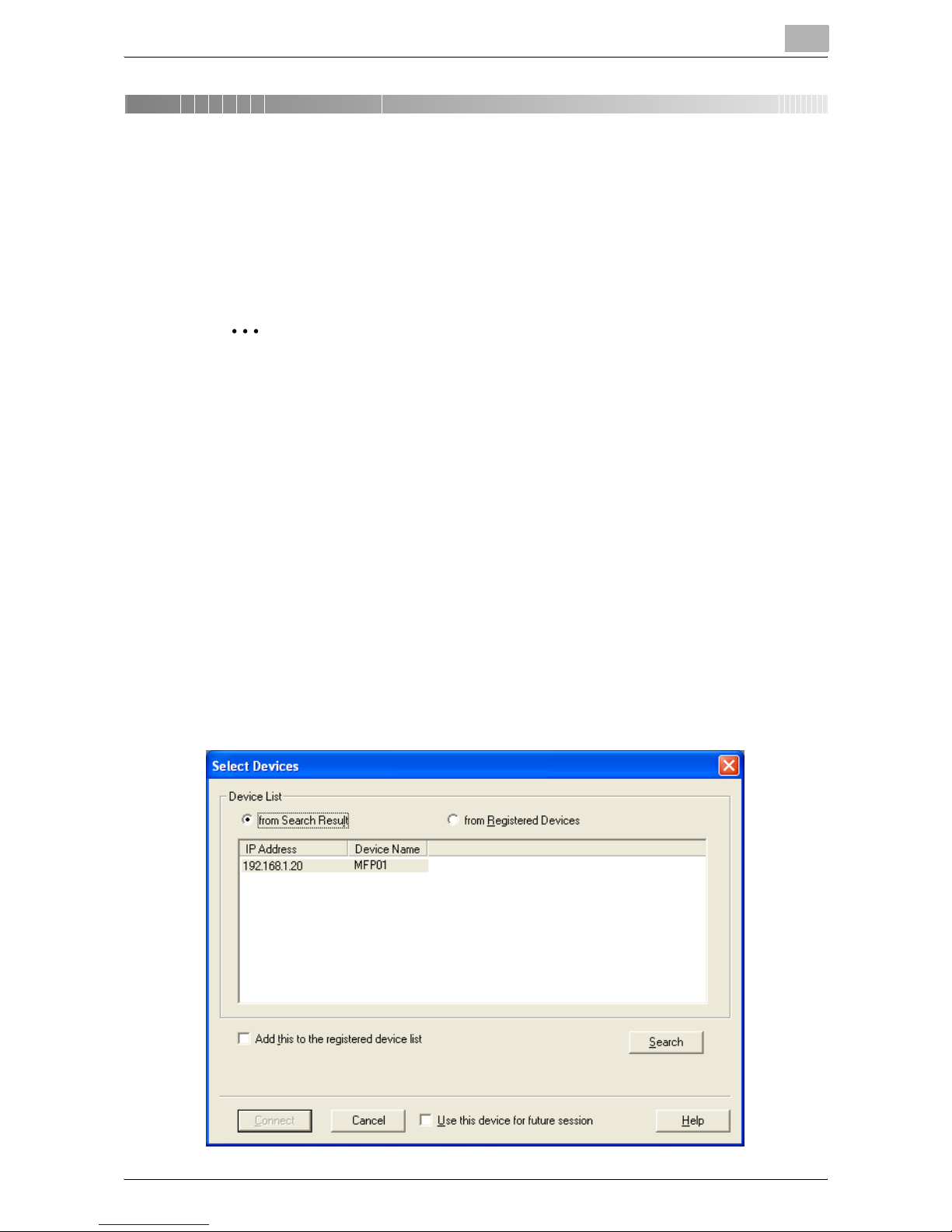
The Select Devices dialog box appears.
3 Select the device to be connected, and click [Connect].
TWAIN driver 3-1
Importing Images
– If user authentication or account track settings have been specified
– If the multifunctional product is set so that scanner transmissions
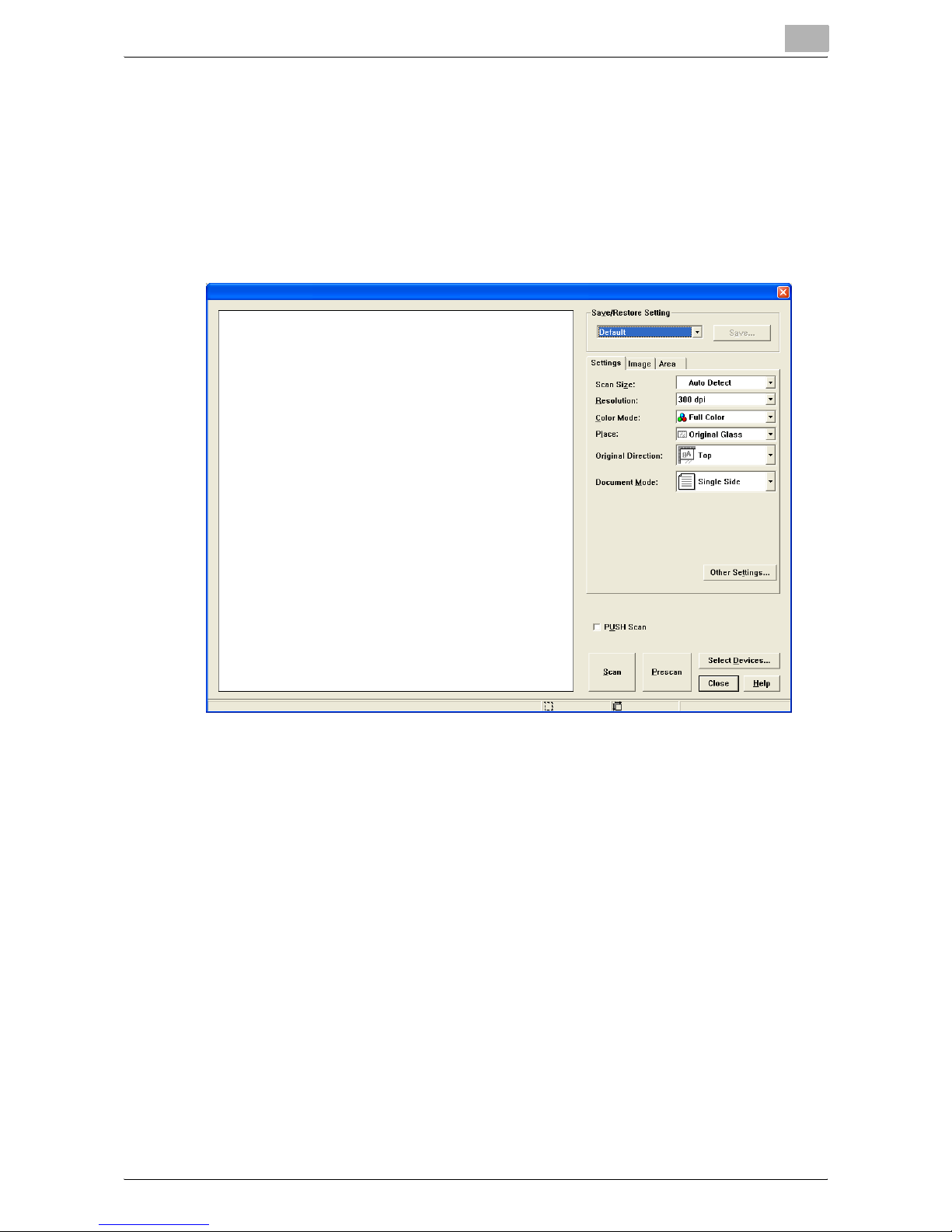
The main window appears.
3
from the device, the corresponding authentication dialog box appears. For details, refer to "With user authentication" on page 3-8
and "With account track" on page 3-10.
cannot be performed by the user that is logged on, it will not be
possible to scan an image.
4 Specify the scan settings.
– For detailed descriptions of the main window, refer to "Settings in
the Main Window" on page 3-11.
5 Load the document into the ADF or position it on the original glass.
TWAIN driver 3-2
 Loading...
Loading...