Kerio Tech Firewall6 User Manual

Kerio WinRoute Firewall 6
Administrator’s Guide
Kerio Technologies
Kerio Technologies. All Rights Reserved.
This guide provides detailed description on the Kerio WinRoute Firewall, version 6.5.1.
Improved version. All additional modifications and updates reserved.
For current product version, check http://www.kerio.com/kwfdwn.
Information regarding registered trademarks and trademarks are provided in appendix A.

Contents
1 Quick Checklist . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
2 Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
2.1 Kerio WinRoute Firewall . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
2.2 Conflicting software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
2.3 Installation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
2.4 WinRoute Components . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
2.5 WinRoute Engine Monitor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
2.6 Upgrade and Uninstallation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
2.7 Configuration Wizard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
3 WinRoute Administration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
3.1 Administration Window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
3.2 View Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
4 Product Registration and Licensing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
4.1 License types and number of users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
4.2 License information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
4.3 Registration of the product in the Administration Console . . . . . . . . . . . . . . . . 32
4.4 Product registration at the website . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
4.5 Subscription / Update Expiration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
4.6 User counter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
5 Network interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
6 Internet Connection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
6.1 Persistent connection with a single link . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
6.2 Connection with a single leased link — dial on demand . . . . . . . . . . . . . . . . . . . . 53
6.3 Connection Failover . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
6.4 Network Load Balancing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
7 Traffic Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
7.1 Network Rules Wizard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
7.2 How traffic rules work . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
7.3 Definition of Custom Traffic Rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
7.4 Basic Traffic Rule Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
7.5 Policy routing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
7.6 User accounts and groups in traffic rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 95
7.7 Partial Retirement of Protocol Inspector . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97
7.8 Use of Full cone NAT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 98
3

7.9 Media hairpinning . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
8 Configuration of network services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
8.1 DNS Forwarder . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
8.2 DHCP server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
8.3 Dynamic DNS for public IP address of the firewall . . . . . . . . . . . . . . . . . . . . . . . 118
8.4 Proxy server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
8.5 HTTP cache . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
9 Bandwidth Limiter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
9.1 How the bandwidth limiter works and how to use it . . . . . . . . . . . . . . . . . . . . . 130
9.2 Bandwidth Limiter configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
9.3 Detection of connections with large data volume transferred . . . . . . . . . . . . 135
10 User Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
10.1 Firewall User Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
11 Web Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
11.1 Web Interface Parameters Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
11.2 User logon and logout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 146
11.3 Status information and user statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
11.4 User preferences . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 150
11.5 Dial-up . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 153
12 HTTP and FTP filtering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 154
12.1 Conditions for HTTP and FTP filtering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
12.2 URL Rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
12.3 Global rules for Web elements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 162
12.4 Content Rating System (ISS OrangeWeb Filter) . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
12.5 Web content filtering by word occurrence . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
12.6 FTP Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
13 Antivirus control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
13.1 Conditions and limitations of antivirus scan . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
13.2 How to choose and setup antiviruses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 177
13.3 HTTP and FTP scanning . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
13.4 Email scanning . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 185
13.5 Scanning of files transferred via Clientless SSL-VPN . . . . . . . . . . . . . . . . . . . . . 187
14 Definitions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 189
14.1 IP Address Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 189
14.2 Time Intervals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 190
14.3 Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 192
14.4 URL Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 196
4

15 User Accounts and Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 199
15.1 Viewing and definitions of user accounts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 200
15.2 Local user accounts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 202
15.3 Local user database: external authentication and import of accounts . . . . . 211
15.4 Active Directory domains mapping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 214
15.5 User groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 219
16 Remote Administration and Update Checks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 223
16.1 Setting Remote Administration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 223
16.2 Update Checking . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 224
17 Advanced security features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
17.1 P2P Eliminator . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
17.2 Special Security Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230
18 Other settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 233
18.1 Routing table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 233
18.2 Universal Plug-and-Play (UPnP) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 236
18.3 Relay SMTP server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 238
19 Status Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 240
19.1 Active hosts and connected users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 240
19.2 Network connections overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 247
19.3 Alerts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 251
20 Basic statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 256
20.1 Volume of transferred data and quota usage . . . . . . . . . . . . . . . . . . . . . . . . . . . . 256
20.2 Interface statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 258
21 Kerio StaR — statistics and reporting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 262
21.1 Monitoring and storage of statistic data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 262
21.2 Settings for statistics and quota . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 264
21.3 Connection to StaR and viewing statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 267
21.4 Accounting period . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 270
21.5 Overall View . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 272
21.6 User statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 276
21.7 Users’ Activity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 277
21.8 Users by Traffic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 282
21.9 Top Visited Websites . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 283
21.10 Top Requested Web Categories . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 285
22 Logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 288
22.1 Log settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 288
22.2 Logs Context Menu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 291
22.3 Alert Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 295
5

22.4 Config Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 295
22.5 Connection Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 297
22.6 Debug Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 298
22.7 Dial Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 299
22.8 Error Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 301
22.9 Filter Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 303
22.10 Http log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 304
22.11 Security Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 306
22.12 Sslvpn Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 307
22.13 Warning Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 308
22.14 Web Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 309
23 Kerio VPN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 310
23.1 VPN Server Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 311
23.2 Configuration of VPN clients . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 316
23.3 Interconnection of two private networks via the Internet (VPN tunnel) . . . 317
23.4 Exchange of routing information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 322
23.5 Example of Kerio VPN configuration: company with a filial office . . . . . . . . . 323
23.6 Example of a more complex Kerio VPN configuration . . . . . . . . . . . . . . . . . . . . 337
24 Kerio Clientless SSL-VPN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 363
24.1 Configuration of WinRoute’s SSL-VPN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 363
24.2 Usage of the SSL-VPN interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 365
25 Specific settings and troubleshooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 371
25.1 Configuration Backup and Transfer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 371
25.2 Automatic user authentication using NTLM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 375
25.3 FTP on WinRoute’s proxy server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 378
25.4 Internet links dialed on demand . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 381
26 Technical support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 386
26.1 Essential Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 386
26.2 Tested in Beta version . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 387
26.3 Contacts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 387
A Legal Notices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 389
B Used open-source libraries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 390
Glossary of terms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 392
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 399
6
Chapter 1
Quick Checklist
In this chapter you can find a brief guide for a quick setup of “Kerio WinRoute Firewall” (called
briefly “WinRoute” in further text). After this setup the firewall should be immediately available
and able to share your Internet connection and protect your local network. For a detailed guide
refer to the separate WinRoute — Step-by-Step Configuration guide.
If you are not sure how to set any of the Kerio WinRoute Firewall functions or features, look up
the appropriate chapter in this manual. For information about your Internet connection (such
as your IP address, default gateway, DNS server, etc.) contact your ISP.
Note: In this guide, the expression firewall represents the host where WinRoute is (or will be)
installed.
1. The firewall must include at least two interfaces — one must be connected to the local
network (i.e. the Ethernet or Token Ring network adapters), another must be connected
to the Internet (i.e. USB ADSL modem, analog modem, ISDN adapter or network adapter).
TCP/IP parameters must be set properly at both/all interfaces.
Test functionality of the Internet connection and of traffic among hosts within the local
network before you run the WinRoute installation. This test will reduce possible problems
with debugging and error detections.
2. Run WinRoute installation. Specify a username and password for access to the administration from the configuration wizard (for details refer to chapters 2.3 and 2.7).
3. Set basic traffic rules using the Network Rules Wizard (see chapter 7.1).
4. Run the DHCP server and set required IP ranges including their parameters (subnet mask,
default gateway, DNS server address/domain name). For details, see chapter 8.2.
5. Check the DNS Forwarder’s configuration. Define the local DNS domain if you intend to
scan the hosts file and/or the DHCP server table. For details, see chapter 8.1.
6. Set user mapping from the Active Directory domain or create/import local user accounts
and groups. Set user access rights. For details see chapter 15.
7. Define IP groups (chapter 14.1), time ranges (chapter 14.2) and URL groups (chapter 14.4),
that will be used during rules definition (refer to chapter 14.2).
8. Create URL rules (chapter 12.2) and set the ISS OrangeWeb Filter module (chapter 12.4).
Set HTTP cache and automatic configuration of browsers (chapter 8.5). Define FTP rules
(chapter 12.6).
7

Chapter 1 Quick Checklist
9. Select an antivirus and define types of objects that will be scanned. If you choose the
integrated McAfee antivirus application, check automatic update settings and edit them if
necessary.
Note: External antivirus must be installed before it is set in WinRoute, otherwise it is not
available in the combo box.
10. Using one of the following methods set TCP/IP parameters for the network adapter of
individual LAN clients:
• Automatic configuration — activate the Obtain an IP address automatically option.
Do not set any other parameters.
• Manual configuration — define IP address, subnet mask, default gateway address,
DNS server address and local domain name.
Use one of the following methods to set the Web browser at each workstation:
• Automatic configuration — activate the Automatically detect settings option (Inter-
net Explorer) or specify URL for automatic configuration (other types of browsers).
For details, refer to chapter 8.5.
• Manual configuration — select type of connection via the local network or define
IP address and appropriate proxy server port (see chapter 8.4).
8

Chapter 2
Introduction
2.1 Kerio WinRoute Firewall
Kerio WinRoute Firewall 6.0 is a complex tool for connection of the local network to the Internet
and protection of this network from intrusions. It is developed for Windows systems (since
version 2000).
Basic Features
Transparent Internet Access
With Network Address Translation (NAT) technology, the local private network can be
connected to the Internet through a single public IP address (static or dynamic). Unlike proxy servers, with NAT technology all Internet services will be accessible from any
workstation and it will be possible to run most standard network applications, as if all
computers within the LAN had their own connection to the Internet.
Security
The integrated firewall protects all the local network including the workstation it is installed on, regardless of whether the NAT function (IP translation) is used or WinRoute is
used as a neutral router between two networks. Kerio WinRoute Firewall offers the same
standard of protection found in much more costly hardware solutions.
Relay Control tab
All the security settings within WinRoute are managed through so-called traffic policy
rules. These provide effective network protection from external attacks as well as easy
access to all the services running on servers within the protected local network (e.g. Web
Server, Mail server, FTP Server, etc.). Communication rules in the traffic policy can also
restrict local users in accessing certain services on the Internet.
Bandwidth Limiter
Typically, problems with Internet connection arise when a user attempts to download big
volume of data (installation archive, disk image, audio/video file, etc.) and thus the connection to the Internet and to other server services is slowed down for other users. The
WinRoute’s built-in Bandwidth Limiter module enables to reserve bandwidth for transfer
of big size data. The rest of the bandwidth will be constantly available for other services.
Protocol Maintenance (Protocol Inspectors)
You may come across applications that do not support the standard communication and
that may for instance use incompatible communication protocols, etc. To challenge this
problem, WinRoute includes so-called protocol inspectors, which identify the appropriate
application protocol and modify the firewall’s behavior dynamically, such as temporary
9

Chapter 2 Introduction
access to a specific port (it can temporarily open the port demanded by the server). FTP
in the active mode, Real Audio or PPTP are just a few examples.
Network Configuration
WinRoute has a built-in DHCP server, which sets TCP/IP parameters for each workstation
within your local network. Parameters for all workstations can be set centrally from a single point. This reduces the amount of time needed to set up the network and minimizes
the risk of making a mistake during this process.
DNS forwarder module enables easy DNS configuration and faster responses to DNS requests. It is a simple type of caching nameserver that relays requests to another DNS
server. Responses are stored in its cache. This significantly speeds up responses to frequent requests. Combined with the DHCP server and the system’s hosts file, the DNS
forwarder can be also used as a dynamic DNS server for the local domain.
Remote Administration
All settings are performed in the Kerio Administration Console, an independent administration console used to manage all Kerio’s server products. It can be run either on the
workstation with WinRoute or on another host within the local network or the Internet.
Communication between WinRoute and the administration console is encrypted and thus
protected from being tapped or misused.
Various Operating Systems Within The Local Network
WinRoute works with standard TCP/IP protocols. From the point of view of workstations
within the local network it acts as a standard router and no special client applications
are required. Therefore, any operating system with TCP/IP, such as Windows, Unix/Linux,
Mac OS etc., can be run within the LAN.
Additional Features
HTTP and FTP filtering
WinRoute can monitor all HTTP and FTP communication and block objects that do not
match given criteria. The settings can be global or defined specifically for each user.
Antivirus control
WinRoute can perform antivirus check of transmitted files. For this purpose, either the
built-in McAfee antivirus or an external antivirus program (e.g. NOD32, AVG, etc.) are
available. Antivirus check can be applied to HTTP, FTP, SMTP and POP3 protocols.
Transparent support for Active Directory
If WinRoute is employed in a network using the Active Directory domain, it is not necessary to create local accounts or import users from the domain as Active Directory directory accounts can be used in WinRoute. This option simplifies administration of user
accounts, especially for greater number of users.
10

2.2 Conflicting software
Email alerts
WinRoute can send email alerts informing users about various events. This function
makes firewall administration easier for the administrators since they need not connect
to WinRoute frequently to check it through. All sent alerts are saved in a special log file.
User quotas
A limit can be set for transmitted data per each user. This limit can be set for the amount
of downloaded or/and uploaded data per day/month. These limits are called quotas. If
any quota is exceeded, the connection to the Internet will be blocked for a corresponding
user. Email alert can be optionally sent to the user.
Blocking of P2P networks
WinRoute can detect and block so called Peer-to-Peer networks (networks used for sharing
of files, such as Kazaa, DirectConnect etc.).
Kerio StaR — statistics and reporting
Detailed statistics of the firewall interface (current speed of transmitted data, amount
of data transmitted in certain time periods) as well as of individual users (amount of
transmitted data, used services, visited websites and their categories, etc.) can be viewed
in WinRoute.
Basic statistics are available in the administration program while detailed statistics can
be found in the firewall’s web interface.
Kerio VPN — proprietary VPN server and client
WinRoute also provides a proprietary VPN solution which can be applied to the serverto-server and client-to-server modes. This VPN solution can perform NAT (even multiple)
at both ends. The Kerio VPN Client client software is included in the WinRoute package
that can be used for creation of client-to-server VPN types (connection of remote clients
to local networks).
Clientless SSL-VPN
The role of the VPN solution which requires a special application at the client side can be
supplied by remote access to a private network using a web browser. Clientless SSL-VPN
enables browsing through hosts and shared items in remote networks as well as files
downloads and saving. The traffic is secured by SSL (HTTPS).
2.2 Conflicting software
The WinRoute host can be used as a workstation, however it is not recommended as user
activity can affect the functionality of the operating system and WinRoute in a negative way.
WinRoute can be run with most of common applications. However, there are certain applications that should not be run at the same host as WinRoute for this could result in collisions.
Collision of low-level drivers
WinRoute Firewall may collide with applications that use low-level drivers with either
identical or similar technology.
11

Chapter 2 Introduction
• The Windows Firewall / Internet Connection Sharing system service. WinRoute can
automatically detect and disable this service on its host system.
• The Routing and Remote Access (RRAS) system service in the Windows Server
operating systems. This service also allows Internet connection sharing (NAT).
WinRoute can detect if there is NAT enabled in the RRAS service and it displays
a warning if it’s the case. Then, the server administrator has to to disable the
NAT in the RRAS service configuration.
If NAT is not enabled, no low-level collisions will occur and WinRoute may be
used along with RRAS.
• Network firewalls — i.e. Microsoft ISA Server, CheckPoint Firewall-1, WinProxy (by
Ositis), Sygate Office Network and Sygate Home Network, etc.
• Personal firewalls, such as Sunbelt Personal Firewall, Zone Alarm, Sygate Personal
Firewall, Norton Personal Firewall, etc.
• Software designed to create virtual private networks (VPN) — i.e. software applications developed by the following companies: CheckPoint, Cisco Systems, Nortel, etc. There are many such applications and their features vary from vendor to
vendor.
Under proper circumstances, use of the VPN solution included in WinRoute is
recommended (for details see chapter 23). Otherwise, we recommend you to test
a particular VPN server or VPN client with WinRoute trial version or to contact
our technical support (see chapter 26).
Note: VPN implementation included in Windows operating system (based on the
PPTP protocol) is supported by WinRoute.
Port collision
Applications that use the same ports as the firewall cannot be run at the WinRoute host
(or the configuration of the ports must be modified).
If all services are running, WinRoute uses the following ports:
• 53/UDP — DNS Forwarder
• 67/UDP — DHCP server
• 1900/UDP — SSDP Discovery service
• 2869/TCP — UPnP Host service
The SSDP Discovery and UPnP Host services are included in the UPnP support
(refer to chapter 18.2).
• 44333/TCP+UDP — traffic between Kerio Administration Console and WinRoute
Firewall Engine. This service cannot be stopped.
The following services use corresponding ports by default. Ports for these services can
be changed.
• 443/TCP — server of the SSL-VPN interface (see chapter 24)
• 3128/TCP — HTTP proxy server (see chapter 8.4)
• 4080/TCP — Web administration interface (refer to chapter 11)
• 4081/TCP — secured (SSL-encrypted) version of the Web administration interface
(see chapter 11)
12

2.3 Installation
• 4090/TCP+UDP — proprietary VPN server (for details refer to chapter 23)
Antivirus applications
Most of the modern desktop antivirus programs (antivirus applications designed to protect desktop workstations) scans also network traffic — typically HTTP, FTP and email
protocols. WinRoute also provides with this feature which may cause collisions. Therefore
it is recommended to install a server version of your antivirus program on the WinRoute
host. The server version of the antivirus can also be used to scan WinRoute’s network
traffic or as an additional check to the integrated antivirus McAfee (for details, see chapter 13).
If the antivirus program includes so called realtime file protection (automatic scan of
all read and written files), it is necessary to exclude directories cache (HTTP cache in
WinRoute — see chapter 8.5) and tmp (used for antivirus check). If WinRoute uses an
antivirus to check objects downloaded via HTTP or FTP protocols (see chapter 13.3), the
cache directory can be excluded with no risk — files in this directory have already been
checked by the antivirus.
The McAfee integrated antivirus plugin does not interact with antivirus application installed on the WinRoute host (provided that all the conditions described above are met).
2.3 Installation
System requirements
Requirements on minimal hardware parameters of the host where WinRoute will be installed:
• CPU 1 GHz
• 512 MB RAM
• 2 network interfaces
• 50 MB free disk space (for the installation)
• Disk space for statistics (see chapter 21) and logs (in accordance with traffic flow and
logging level — see chapter 22)
• For maximum protection of the installed product (particularly its configuration files),
it is recommended to use the NTFS file system.
The following browsers can be used to access the WinRoute (Kerio StaR — see chapter 21 and
Kerio SSL-VPN — see chapter 24) web services:
• Internet Explorer 6 and higher
• Firefox 1.5 and higher
• Safari
13

Chapter 2 Introduction
Installation packages
Kerio WinRoute Firewall is distributed in two editions: one is for 32-bit systems and the other
for 64-bit systems (see the product’s download page: http://www.kerio.com/kwfdwn).
The 32-bit edition (the “win32” installation package) supports the following operating systems:
• Windows 2000
• Windows XP (32 bit)
• Windows Server 2003 (32 bit)
• Windows Vista (32 bit)
• Windows Server 2008 (32 bit)
The 64-bit edition (the “win64” installation package) supports the following operating systems:
• Windows XP (64 bit)
• Windows Server 2003 (64 bit)
• Windows Vista (64 bit)
• Windows Server 2008 (64 bit)
Older versions of Windows operating systems are not supported.
Note:
1. WinRoute installation packages include the Kerio Administration Console. The separate
Kerio Administration Console installation package (file kerio-kwf-admin*.exe) is de-
signed for remote administration from another host. This package is identical both for
32-bit and 64-bit Windows systems. For details on WinRoute administration, see chapter
3.
2. For correct functionality of the Kerio StaR interface (see chapter 21), it is necessary that
the WinRoute host’s operating system supports all languages that would be used in the
Kerio StaR interface. Some languages (Chinese, Japonese, etc.) may require installation of
supportive files. For details, refer to documents regarding the corresponding operating
system.
Steps to be taken before the installation
Install WinRoute on a computer which is used as a gateway connecting the local network and
the Internet. This computer must include at least one interface connected to the local network
(Ethernet, WiFi, etc.) and at least one interface connected to the Internet. You can use either
a network adapter (Ethernet, WiFi, etc.) or a modem (analog, ISDN, etc.) as an Internet interface.
14

2.3 Installation
We recommend you to check through the following items before you run WinRoute installation:
• Time of the operating system should be set correctly (for timely operating system and
antivirus upgrades, etc.)
• The latest service packs and any Microsoft recommended security updates should be
applied.
• TCP/IP parameters should be set for all available network adapters
• All network connections (both to the local network and to the Internet) should function
properly. You can use for example the ping command to detect time that is needed
for connections.
These checks and pre-installation tests may protect you from later problems and complications.
Note: Basic installation of all supported operating systems include all components required
for smooth functionality of WinRoute.
Installation and Basic Configuration Guide
Once the installation program is launched (i.e. by kerio-kwf-6.5.0-4400-win32.exe), it is
possible to select a language for the installation wizard. Language selection affects only the
installation, language of the user interface can then be set separately for individual WinRoute
components.
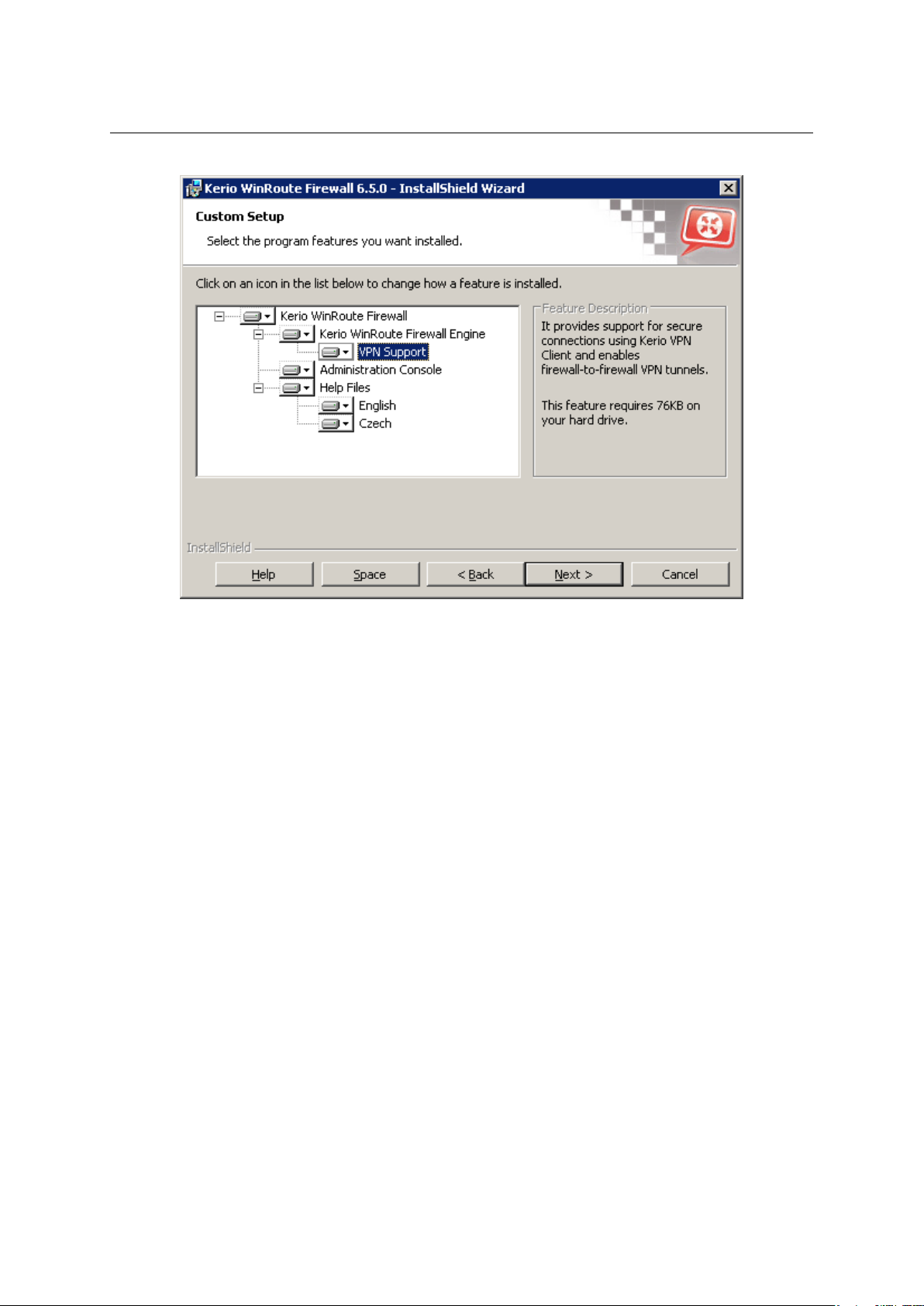
In the installation wizard, you can choose either Full or Custom installation. Cstom mode will
let you select optional componants of the program:
• Kerio WinRoute Firewall Engine — core of the application
• VPN Support — proprietary VPN solution developed by Kerio Technologies (Kerio VPN),
• Administration Console — the Kerio Administration Console application (universal con-
sole for all server applications of Kerio Technologies),
• Help files — this manual in the HTML Help format. For help files details, see Kerio
Administration Console — Help (available at http://www.kerio.com/kwf-manual).
Go to chapter 2.4 for a detailed description of all WinRoute components. For detailed description on the proprietary VPN solution, refer to chapter 23.
Having completed this step, you can start the installation process. All files will be copied to
the hard disk and all the necessary system settings will be performed. The initial Wizard will
be run automatically after your first login (see chapter 2.7).
Under usual circumstances, a reboot of the computer is not required after the installation (a
restart may be required if the installation program rewrites shared files which are currently in
15
Chapter 2 Introduction
Figure 2.1 Installation — customization by selecting optional components
use). This will install the WinRoute low-level driver into the system kernel. WinRoute Engine
will be automatically launched when the installation is complete. The engine runs as a service.
Note:
1. If you selected the Custom installation mode, the behavior of the installation program will
be as follows:
• all checked components will be installed or updated,
• all checked components will not be installed or will be removed
During an update, all components that are intended to remain must be ticked.
2. The installation program does not allow to install the Administration Console separately.
Installation of the Administration Console for the remote administration requires a separate installation package (file kerio-kwf-admin*.exe).
Protection of the installed product
To provide the firewall with the highest security possible, it is necessary to ensure that undesirable (unauthorized) persons has no access to the critical files of the application, especially
to configuration files. If the NTFS system is used, WinRoute refreshes settings related to access
rights to the directory (including all subdirectories) where the firewall is installed upon each
startup. Only members of the Administrators group and local system account (SYSTEM) are
assigned the full access (read/write rights), other users are not allowed access the directory.
16

2.3 Installation
Warning
If the FAT32 file system is used, it is not possible to protect WinRoute in the way suggested
above. For this reason, it is recommended to install WinRoute only on computers which use
the NTFS file system.
Conflicting Applications and System Services
The WinRoute installation program detects applications and system services that might conflict with the WinRoute Firewall Engine.
1. Windows Firewall’s system components
1
and Internet Connection Sharing.
These components provide the same low-level functions as WinRoute. If they are running concurrently with WinRoute, the network communication would not be functioning
correctly and WinRoute might be unstable. Both components are run by the Windows Fire-
wall / Internet Connection Sharing system service.2.
Warning
To provide proper functionality of WinRoute, it is necessary that the Internet Connection
Firewall / Internet Connection Sharing detection is stopped and forbidden!
2. Universal Plug and Play Device Host and SSDP Discovery Service
The services support UPnP (Universal Plug and Play) in the Windows XP, Windows
Server 2003, Windows Vista and Windows Server 2008 operating systems. However, these
services collide with the UPnP support in WinRoute (refer to chapter 18.2).
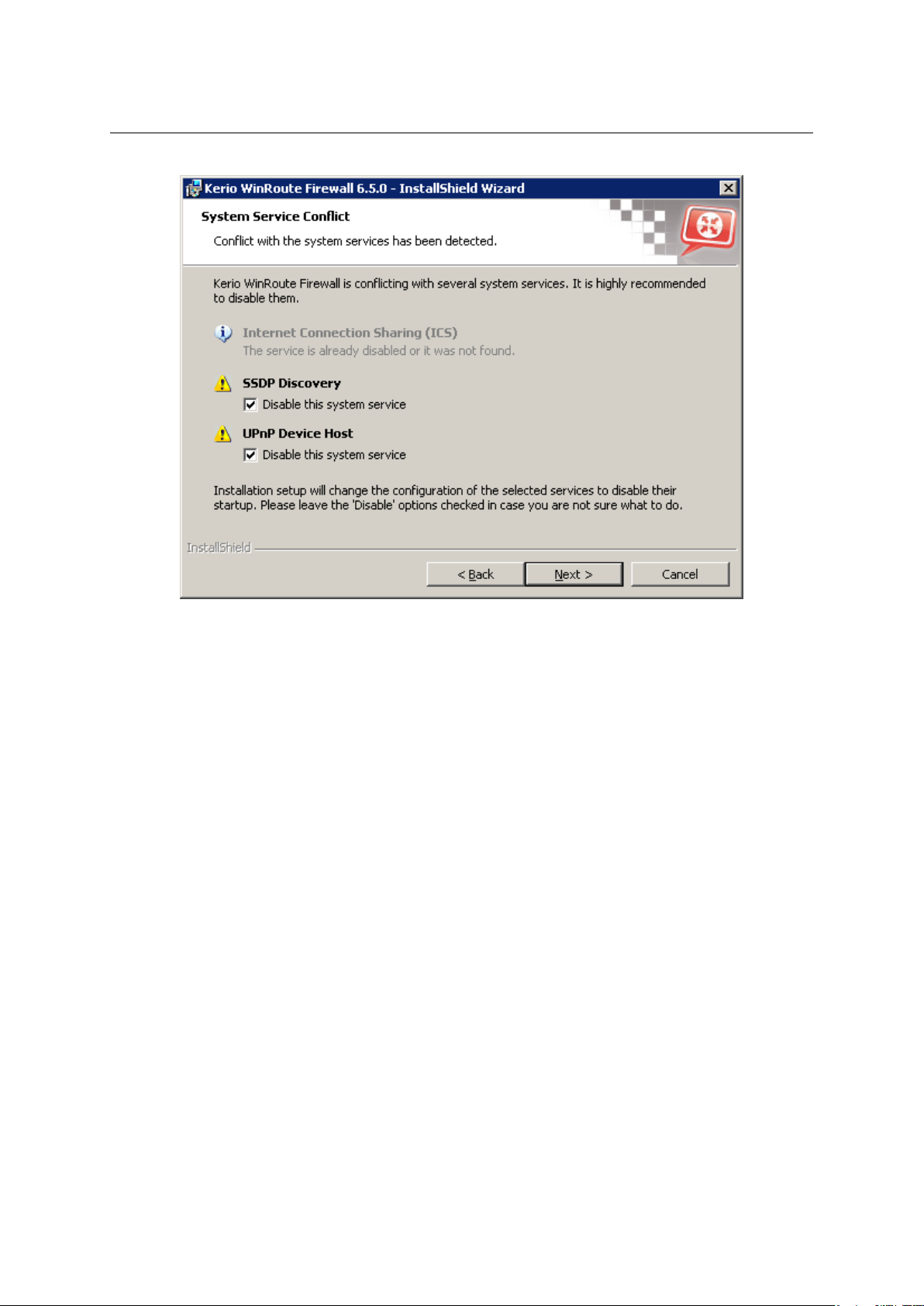
The WinRoute installation includes a dialog where it is possible to disable colliding system
services.
By default, the WinRoute installation disables all the colliding services listed. Under usual
circumstances, it is not necessary to change these settings. Generally, the following rules are
applied:
• The Windows Firewall / Internet Connection Sharing (ICS) service should be disabled.
Otherwise, WinRoute will not work correctly. The option is a certain kind of warning
which informs users that the service is running and that it should be disabled.
• To enable support for the UPnP protocol in WinRoute (see chapter 18.2), it is neces-
sary to disable also services Universal Plug and Play Device Host and SSDP Discovery
Service.
• If you do not plan to use support for UPnP in WinRoute, it is not necessary to disable
the Universal Plug and Play Device Host and SSDP Discovery Serviceservices.
1
In Windows XP Service Pack 1 and older versions, the integrated firewall is called Internet Connection Firewall
2
In the older Windows versions listed above, the service is called Internet Connection Firewall / Internet Connection
Sharing.
17
Chapter 2 Introduction
Figure 2.2 Disabling colliding system services during installation
Note:
1. Upon each startup, WinRoute detects automatically whether the Windows Firewall / Internet Connection Sharing is running. If it is, WinRoute stops it and makes a record in the
warning log. This helps assure that the service will be enabled/started immediately after
the WinRoute installation.
2. On Windows XP Service Pack 2, Windows Server 2003, Windows Vista and Windows
Server 2008, WinRoute registers in the Security Center automatically. This implies that
the Security Center always indicates firewall status correctly and it does not display warnings informing that the system is not protected.
2.4 WinRoute Components
Kerio WinRoute consists of the three following components:
WinRoute Firewall Engine
is the core of the program that provides all services and functions. It is running as
a service in the operating system (the service is called Kerio WinRoute Firewall and it is
run automatically within the system account by default).
WinRoute Engine Monitor
Allows viewing and modification of the Engine’s status (stopped/running) and setting of
start-up preferences (i.e. whether Engine and/or Monitor should be run automatically at
18

2.5 WinRoute Engine Monitor
system start-up). It also provides easy access to the Administration Console. For details,
refer to chapter 2.5.
Note: WinRoute Firewall Engine is independent on the WinRoute Engine Monitor. The
Engine can be running even if there is no icon in the system tray.
Kerio Administration Console
It is a versatile console for local or remote administration of Kerio Technologies server
products. For successful connection to an application you need a plug-in with an
appropriate interface. Kerio Administration Console is installed hand-in-hand with
the appropriate module during the installation of Kerio WinRoute. Detailed guidance
for Kerio Administration Console is provided in Kerio Administration Console — Help
(
http://www.kerio.com/kwf-manual).
2.5 WinRoute Engine Monitor
WinRoute Engine Monitor is a standalone utility used to control and monitor the WinRoute
Firewall Engine status. The icon of this component is displayed on the toolbar.
Figure 2.3 WinRoute Engine Monitor icon in the Notification Area
If WinRoute Engine is stopped, a white crossed red spot appears on the icon. Under different
circumstances, it can take up to a few seconds to start or stop the WinRoute Engine application.
Meanwhile, the icon gets grey and is inactive — does not respond to mouse clicking.
On Windows, left double-clicking on this icon runs the Kerio Administration Console (described
later). Use the right mouse button to open the following menu:
Figure 2.4 WinRoute Engine Monitor menu
19

Chapter 2 Introduction
Start-up Preferences
With these options WinRoute Engine and/or WinRoute Engine Monitor applications can be
set to be launched automatically when the operating system is started. Both options are
enabled by default.
Administration
Runs Kerio Administration Console (equal to double-clicking on the WinRoute Engine Monitor icon).
Internet Usage Statistics
Opens Internet Usage Statistics in the default browser. For details, see chapter 21.
Start / Stop WinRoute Firewall
Switches between the Start and Stop modes. The text displays the current mode status.
Exit Engine Monitor
An option to exit WinRoute Engine Monitor. It does not affect status of the WinRoute
Engine application (this will be announced by a report).
Note:
1. If a limited version of WinRoute is used (e.g. a trial version), a notification is displayed
7 days before its expiration. This information is displayed until the expiration.
2. WinRoute Engine Monitor is available in English only.
2.6 Upgrade and Uninstallation
Upgrade
In this chapter you can find a description of WinRoute upgrade within the versions 5.x and 6.x
(i.e. upgrade from the 5.1.10 version to the 6.3.0 version or from 6.3.0 to 6.3.1). Direct
upgrade from 4.x versions or earlier to the 6.x version is not supported.
Simply run the installation of a new version to upgrade WinRoute (i.e. to get a new release
from the Kerio Web pages — http://www.kerio.com/).
All windows of the Kerio Administration Console must be closed before the (un)installation is
started. All of the three WinRoute components will be stopped and closed automatically.
The installation program detects the directory with the former version and updates it by replacing appropriate files with the new ones automatically. License, all logs and user defined
settings are kept safely.
20
2.6 Upgrade and Uninstallation
Uninstallation
To uninstall WinRoute, stop all three WinRoute components. The Add/Remove Programs
option in the Control Panel launches the uninstallation process. All files under the WinRoute
directory can be optionally deleted.
(the typical path is C:\Program Files\Kerio\WinRoute Firewall)
— configuration files, SSL certificates, license key, logs, etc.
Figure 2.5 Uninstallation — asking user whether files created in WinRoute should be deleted
Keeping these files may be helpful for copying of the configuration to another host or if it is
not sure whether the SSL certificates were issued by a trustworthy certification authority.
During uninstallation, the WinRoute installation program automatically refreshes the original
status of the Windows Firewall / Internet Connection Sharing, Universal Plug and Play Device
Host) and SSDP Discovery Service system services.
Update Checker
WinRoute enables automatic checks for new versions of the product at the Kerio Technologies
website. Whenever a new version is detected, its download and installation will be offered
automatically.
For details, refer to chapter
16.2.
21
Chapter 2 Introduction
2.7 Configuration Wizard
Using this Wizard you can define all basic WinRoute parameters. It is started automatically by
the installation program.
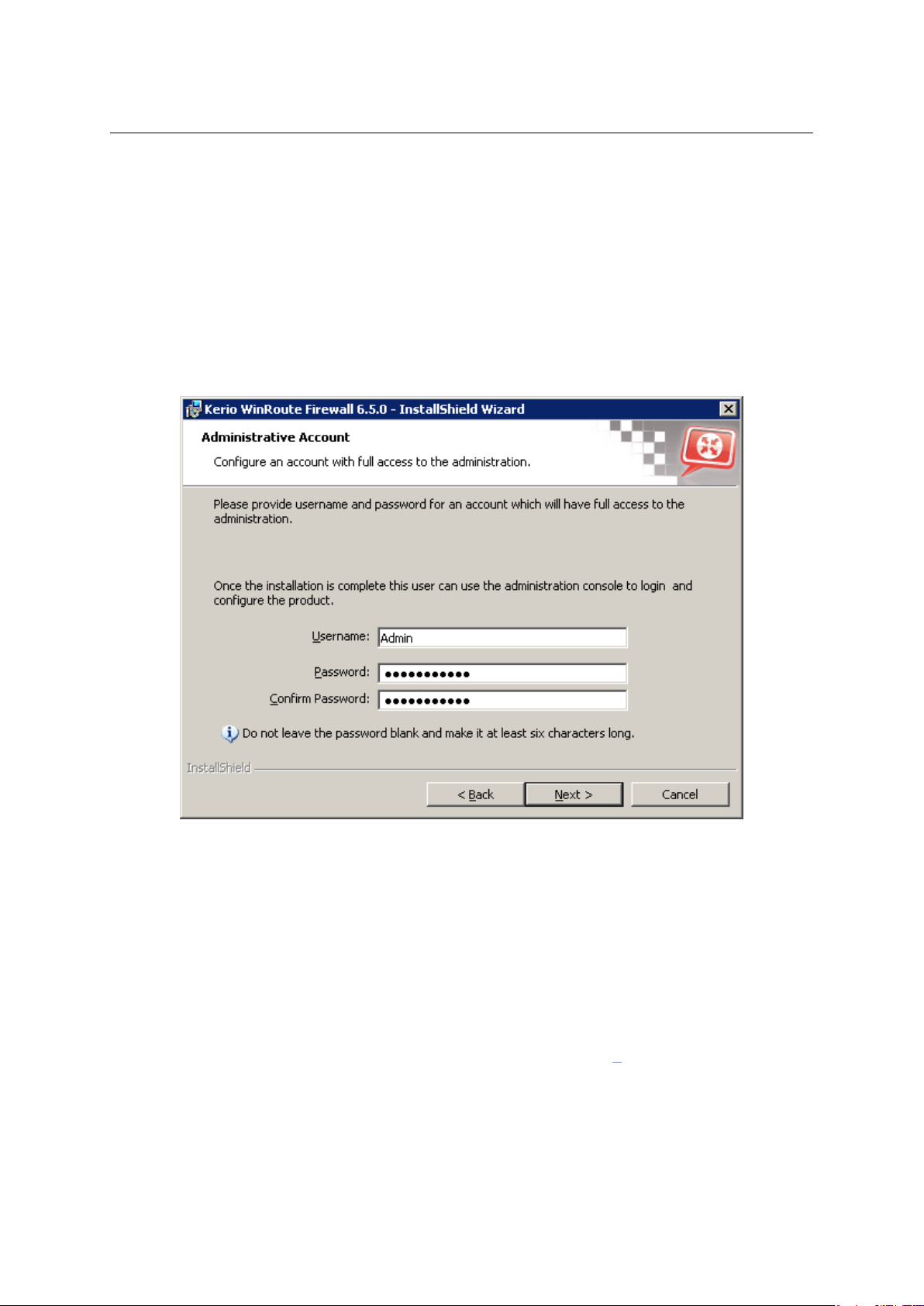
Setting of administration username and password
Definition of the administration password is essential for the security of the firewall. Do not
use the standard (blank) password, otherwise unauthorized users may be able to access the
WinRoute configuration.
Figure 2.6 Initial configuration — Setting of administration username and password
Password and its confirmation must be entered in the dialog for account settings. Name Admin
can be changed in the Username edit box.
Note: If the installation is running as an upgrade, this step is skipped since the administrator
account already exists.
Remote Access
Immediately after the first WinRoute Firewall Engine startup all network traffic will be blocked
(desirable traffic must be permitted by traffic rules — see chapter 7). If WinRoute is installed
remotely (i.e. using terminal access), communication with the remote client will be also interrupted immediately (WinRoute must be configured locally).
Within Step 2 of the configuration wizard specify the IP address of the host from which the
firewall will be controlled remotely (i.e. using terminal services) to enable remote installation
22
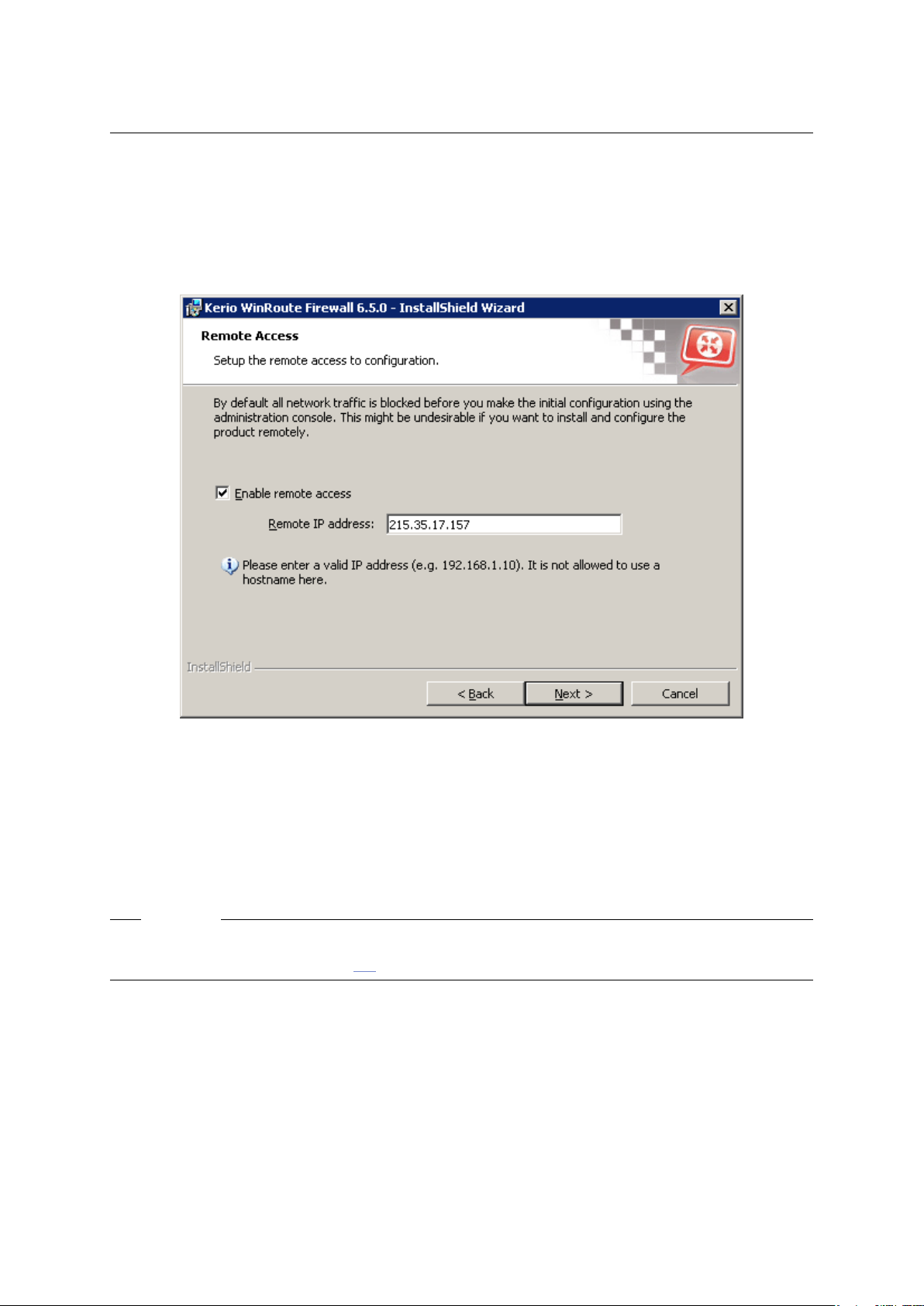
2.7 Configuration Wizard
and administration. Thus WinRoute will enable all traffic between the firewall and the remote
host.
Note: Skip this step if you install WinRoute locally. Allowing full access from a point might
endanger security.
Figure 2.7 Initial configuration — Allowing remote administration
Enable remote access
This option enables full access to the WinRoute computer from a selected IP address
Remote IP address
IP address of the computer from where you will be connecting (e.g. terminal services
client). This field must contain an IP address. A domain name is not allowed.
Warning
The remote access rule is disabled automatically when WinRoute is configured using the network policy wizard (see chapter 7.1).
23

Chapter 3
WinRoute Administration
All Kerio products including WinRoute are administered through the Kerio Administration
Console application(an application used for administration of all Kerio Technologies’ server
products; thereinafter Administration Console). Using this program you can access WinRoute
Firewall Engine either locally (from the WinRoute host) or remotely (from another host). Traffic
between Administration Console and WinRoute Firewall Engine is encrypted. This protects you
from tapping and misuse.
The Administration Console is installed along with WinRoute (see chapters 2.3 and 2.4). The
separate installation package Administration Console for WinRoute is available for remote administration from another host.
Detailed guidelines for the Administration Console are provided under Kerio Administration
Console — Help (to view these guidelines, use option Help → Contents in the main Administration Console window, or you can download it from http://www.kerio.com/kwf-manual).
The following chapters of this guide provide descriptions on individual sections of the
WinRoute administration dialog window which is opened upon a successful login to the
WinRoute Firewall Engine.
Note:
1. Administration Console for WinRoute is available in English, Spanish, Czech, Slovak and
Russian.
2. Upon the first login to WinRoute after a successful installation, the traffic rules wizard is
run so that the initial WinRoute configuration can be performed. For a detailed description
on this wizard, please refer to chapter 7.17.1.
3.1 Administration Window
The WinRoute administration dialog window (“administration window”) will be opened upon
a successful login to the WinRoute Firewall Engine through the Administration Console. This
window is divided into two parts:
• The left column contains the tree view of sections. The individual sections of the
tree can be expanded and collapsed for easier navigation. Administration Console
remembers the current tree settings and uses them upon the next login.
• In the right part of the window, the contents of the section selected in the left column
is displayed (or a list of sections in the selected group).
24
3.1 Administration Window
Figure 3.1 The main window of Administration Console for WinRoute
Administration Window — Main menu
The main menu provides the following options:
File
• Reconnect — reconnection to the WinRoute Firewall Engine after a connection
drop-out (caused for example by a restart of the Engine or by a network error).
• New connection — opens the main window of the Administration Console. Use
a bookmark or the login dialog to connect to a server.
This option can be useful when the console will be used for administration of
multiple server applications (e.g. WinRoute at multiple servers). For details, refer
to the Help section in the Administration Console manual.
Note: The New Connection option opens the same dialog as running the Administration Console from the Start menu.
• Quit — this option terminates the session (users are logged out of the server and
the administration window is closed). The same effect can be obtained by clicking
the little cross in the upper right corner of the window or pressing Alt+F4 or
Ctrl+Q.
Edit
Options under Edit are related to product registration and licensing. The options available
in the menu depend on the registration status (for example, if the product is registered
as a trial version, it is possible to use options of registration of a purchased license or
a change of registration data).
25

Chapter 3 WinRoute Administration
• Copy license number to clipboard — copies the license number (the ID licence
item) to the clipboard. This may be helpful e.g. when ordering an upgrade or
subscription, where the number of the base license is required, or when sending
an issue to the Kerio Technologies technical support.
• Register trial version — registration of the product’s trial version.
• Register product — registration of a product with a purchased license number.
• Install license — use this option to import your license key file (for details, see
chapter 4.4).
Help menu
• Show Server’s Identity — this option provides information about the firewall
which the Administration Console is currently connected to (name or IP address
of the server, port and SSL-certificate fingerprint). This information can be used
for authentication of the firewall when connecting to the administration from
another host (see Kerio Administration Console — Help).
• Administrator’s guide — this option displays the administrator’s guide in HTML
Help format. For details about help files, see Kerio Administration Console — Help
manual.
• About — this page provides information about current version of the application
(WinRoute’s administration module in this case), a link to our company’s website,
etc.
Status bar
The status bar at the bottom of the administration window displays the following information
(from left to right):
Figure 3.2 Administration Console status bar
• The section of the administration window currently selected in the left column. This
information facilitates navigation in the administration window when any part of the
section tree is not visible (e.g. when a lower screen resolution is selected).
• Name or IP address of the server and port of the server application (WinRoute uses
port 44333).
• Name of the user logged in as administrator.
• Current state of the Administration Console: Ready (waiting for user’s response), Load-
ing (retrieving data from the server) or Saving (saving changes to the server).
26
3.2 View Settings
Detection of WinRoute Firewall Engine connection drop-out
Administration Console is able to detect the connection failure automatically. The failure is
usually detected upon an attempt to read/write the data from/to the server (i.e. when the Ap-
ply button is pressed or when a user switches to a different section of Administration Console).
In such case, a connection failure dialog box appears where the connection can be restored.
Figure 3.3 Detection of WinRoute Firewall Engine connection drop-out
After you remove the cause of the connection failure, the connection can be restored. Admin-
istration Console provides the following options:
• Apply & Reconnect — connection to the server will be recovered and all changes done
in the current section of the Administration Console before the disconnection will be
saved,
• Reconnect — connection to the server will be recovered without saving any changes
performed in the particular section of the console before the disconnection.
If the reconnection attempt fails, only the error message is shown. You can then try to reconnect using the File → Restore connection option from the main menu, or close the window and
restore the connection using the standard procedure.
3.2 View Settings
Many sections of the Administration Console are in table form where each line represents
one record (e.g. detailed information about user, information about interface, etc.) and the
columns consist of individual entries for these records (e.g. name of server, MAC address, IP
address, etc.).
WinRoute administrators can define — according to their liking — the way how the information
in individual sections will be displayed. When you right-click each of the above sections, a popup menu with Modify columns option is displayed. This entry opens a dialog window where
users can select which columns will be displayed/hidden.
27
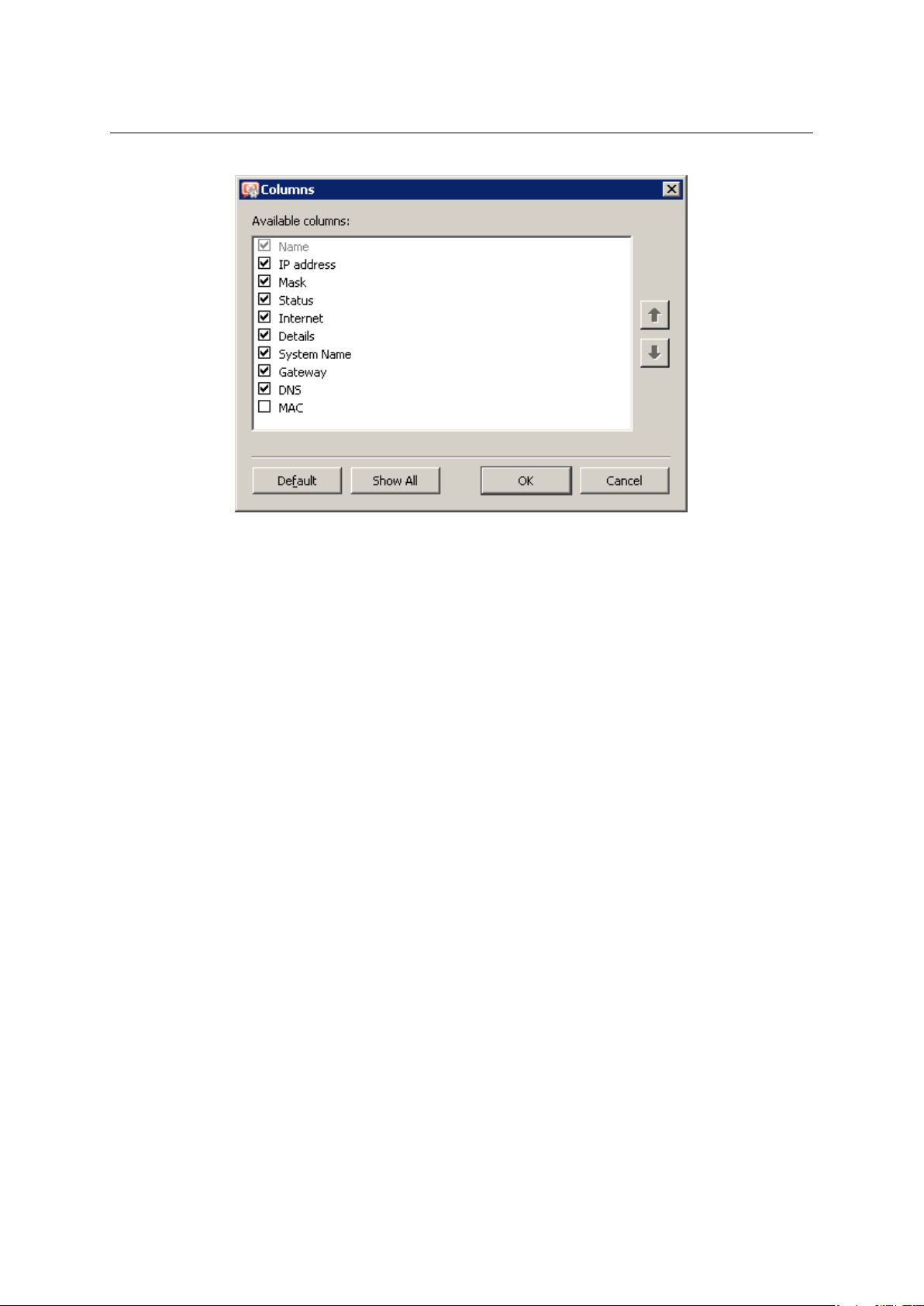
Chapter 3 WinRoute Administration
Figure 3.4 Column customization in Interfaces
This dialog offers a list of all columns available for a corresponding view. Use checking boxes
on the left to enable/disable displaying of a corresponding column. You can also click the
Show all button to display all columns. Clicking on the Default button will restore default
settings (for better reference, only columns providing the most important information are
displayed by default).
The arrow buttons move the selected column up and down within the list. This allows the
administrator to define the order the columns will be displayed.
The order of the columns can also be adjusted in the window view. Left-click on the column
name, hold down the mouse button and move the column to the desired location.
Note: Move the dividing lines between the column headers to modify the width of the individual columns.
28

Chapter 4
Product Registration and Licensing
When purchased, Kerio WinRoute Firewall must be registered, Upon registration of the product,
so called license key is generated.(the license.key file — see chapter 25.1). If the key is not
imported, WinRoute will behave as a full-featured trial version and its license will be limited
by the expiration timeout.
This means that the trial version differs from the full WinRoute version only in the aspect
whether the license has been registered or not. This gives each customer an opportunity
to test and try the product in the particular environment during the 30-day period. Then,
once the product is purchased, the customer can simply register the installed version by the
purchased license number (see chapter
the trial version and reinstall the product.
Once the 30-day trial period expires, WinRoute cuts the speed of all network traffic of the
computer where it is installed to 4 KB/s. Also, the routing is blocked (which implies that the
WinRoute’s host cannot be used as a gateway for the Internet). Upon registration with a valid
license number (received as a response to purchase of the product), WinRoute is available with
full functionality.
4.3). This means that it is not necessary to uninstall
Note: If your license key gets lost for any reason (e.g. after the harddisk breakdown or by an
accidental removal, etc.), you can simply use the basic product’s purchase number to recover
the license. If even this number gets lost, contact the sales department of Kerio Technologies.
4.1 License types and number of users
License types (optional components)
WinRoute can optionally include the following components: McAfee antivirus (refer to chapter 13) or/and the ISS OrangeWeb Filter module for web pages rating (see chapter 12.4). These
components are licensed individually.
License keys consist of the following information:
WinRoute license
Basic WinRoute license. Its validity is defined by the two following factors:
• update right expiration date — specifies the date by which WinRoute can be up-
dated for free. When this date expires, WinRoute keeps functioning, however, it
cannot be updated. The time for updates can be extended by purchasing a subscription.
• product expiration date — specifies the date by which WinRoute stops functioning
and blocks all TCP/IP traffic at the host where it is installed. If this happens, a new
valid license key must be imported or WinRoute must be uninstalled.
29

Chapter 4 Product Registration and Licensing
McAfee license
This license is defined by the two following dates:
• update right expiration date (independent of WinRoute) — when this date expires,
the antivirus keeps functioning, however, neither its virus database nor the antivirus can be updated yet.
Warning
Owing to persistent incidence of new virus infections we recommend you to use
always the most recent antivirus versions.
• plug-in expiration date— specifies the date by which the antivirus stops functioning and cannot be used anymore.
ISS OrangeWeb Filter license
ISS OrangeWeb Filter module is provided as a service. License is defined only by an
expiration date which specifies when this module will be blocked.
Note: Refer to Kerio Technologies website (http://www.kerio.com/) to get up-to-date infor-
mation about individual licenses, subscription extensions, etc.
Deciding on a number of users (licenses)
WinRoute’s license key includes information about maximal number of users allowed to use
the product. In accordance with the licensing policy, number of users is number of hosts
protected by WinRoute, i.e. sum of the following items:
• All hosts in the local network (workstations and servers),
• all possible VPN clients connecting from the Internet to the local network.
The host where WinRoute is installed in not included in the total number of users.
Warning
If the maximal number of licensed users is exceeded, WinRoute may block traffic of some
hosts!
4.2 License information
The license information can be displayed by selecting Kerio WinRoute Firewall (the first item in
the tree in the left part of the Administration Console dialog window — this section is displayed
automatically whenever the WinRoute administration is entered).
Product
name of the product (WinRoute)
30
 Loading...
Loading...