Page 1

N300 Smart Wi-Fi Router with Power
Ampliers, Managed Switch, and Mode
Selector
Command Reference Guide
Model Keenetic Lite (KN-1310)
OS Version 2.10
Edition 1.17 18.01.2018
help.keenetic.net
© Keenetic Limited, 2018
Page 2

Page 3
This guide contains Command-Line Interface (CLI) commands to maintain the Keenetic
Lite device. This guide provides a complete listing of all possible commands. The other
chapters provide examples of how to implement the most common of these commands,
general information on the interrelationships between the commands and the conceptual
background of how to use them.
1 Readership
This guide is for the networking or computer technician responsible for conguring and
maintaining the Keenetic Lite on-site. It is also intended for the operator who manages
the Keenetic Lite. This manual cover high-level technical support procedures available to
Root administrators and Keenetic Lite technical support personnel.
Preface
Preface
2 Organization
This manual covers the following topics:
Introduction to the CLI Describes how to use the Keenetic Lite Command-Line
Interface (CLI), its hierarchical structure, authorization
levels and its help features.
Command Reference Provides an alphabetical list of the available CLI commands
that you can use to congure the Keenetic Lite device.
3 Document Conventions
Command descriptions use the following conventions:
boldface font
italic font
[ optional ]
‹required›
Commands and keywords are in boldface.
Must be typed exactly as shown. Bold font
is used as a user input in examples.
Arguments for which you supply values are
in italics.
Elements in square brackets are optional.
Elements in angle brackets are required.
(x | y | z)
[x | y | z]
Keenetic Lite (KN-1310) — Command Reference Guide
Alternative keywords are grouped in round
brackets and separated by vertical bars.
Optional alternative keywords are grouped
in brackets and separated by vertical bars.
3
Page 4
Preface
Each command description is broken down into the following sub-sections:
Description of what the command does.Description
The general format of the command.Synopsis
Prex no
Change settings
Group entry
Interface type
Arguments
Example
The possibility of using no prex with
command.
The ability of command to change the
settings.
The possibility of multiple input.Multiple input
Name of the group that owns the command.
If there is no group, this section does not
displayed.
Type of interface, which can be managed by
the command. The section does not
displayed, if this context has no meaning for
the command.
Interfaces used in the system and the
relationships between them are shown in
the diagrams below.
List of arguments if they exists, and
explanations to them.
An illustration of how the command looks
when invoked. Because the interface is
straightforward, some of the examples are
obvious, but they are included for clarity.
Notes, cautionary statements, and safety warnings use these conventions.
Note: Means "reader take note". Notes contain helpful suggestions or
references to materials not contained in this manual.
Warning: Means "reader be careful". You are capable of doing something that
might result in equipment damage or loss of data.
4
Command Reference Guide — Keenetic Lite (KN-1310)
Page 5

Contents Overview
Contents Overview
Preface ............................................................................................................................................ 3
Product Overview .......................................................................................................................... 19
Introduction to the CLI .................................................................................................................. 21
Command Reference ..................................................................................................................... 27
Glossary ....................................................................................................................................... 291
Interface Hierarchy ...................................................................................................................... 299
HTTP API ...................................................................................................................................... 301
SNMP MIB ................................................................................................................................... 309
IPsec Encryption Levels ................................................................................................................ 315
Keenetic Lite (KN-1310) — Command Reference Guide
5
Page 6

Contents Overview
6
Command Reference Guide — Keenetic Lite (KN-1310)
Page 7

Table of Contents
Table of Contents
Preface .................................................................................................................................... 3
1 Readership ........................................................................................................................... 3
2 Organization ......................................................................................................................... 3
3 Document Conventions ........................................................................................................ 3
Table of Contents .................................................................................................................. 5
Chapter 1
Product Overview ................................................................................................................ 19
1.1 Hardware Conguration .................................................................................................. 19
Chapter 2
Introduction to the CLI ....................................................................................................... 21
2.1 Enter commands in the CLI .............................................................................................. 21
2.1.1 Entering a group ................................................................................................... 22
2.2 Getting Help and auto-completion ................................................................................... 22
2.3 Prex no .......................................................................................................................... 23
2.4 Multiple input ................................................................................................................... 24
2.5 Saving to startup settings ................................................................................................ 24
2.6 Delayed restart ................................................................................................................ 25
Chapter 3
Command Reference .......................................................................................................... 27
3.1 Core commands ............................................................................................................... 27
3.1.1 copy .................................................................................................................... 27
3.1.2 erase ................................................................................................................... 27
3.1.3 exit ...................................................................................................................... 28
3.1.4 ls ......................................................................................................................... 28
3.1.5 more ................................................................................................................... 29
3.2 access-list ...................................................................................................................... 30
3.2.1 access-list deny .................................................................................................. 30
3.2.2 access-list permit ............................................................................................... 33
3.3 cloud control client connect ........................................................................................ 35
3.4 cloud control client name ............................................................................................ 36
3.5 cloud control client session timeout ........................................................................... 37
3.6 components .................................................................................................................. 37
3.6.1 components commit .......................................................................................... 38
3.6.2 components install ............................................................................................ 38
3.6.3 components list ................................................................................................. 39
Keenetic Lite (KN-1310) — Command Reference Guide
7
Page 8

Table of Contents
3.6.4 components preset ............................................................................................ 40
3.6.5 components preview ......................................................................................... 40
3.6.6 components remove .......................................................................................... 41
3.6.7 components validity-period .............................................................................. 41
3.7 crypto ike key ............................................................................................................... 42
3.8 crypto ike nat-keepalive .............................................................................................. 43
3.9 crypto ike policy ........................................................................................................... 43
3.9.1 crypto ike policy lifetime ................................................................................... 44
3.9.2 crypto ike policy mode ...................................................................................... 45
3.9.3 crypto ike policy negotiation-mode .................................................................. 45
3.9.4 crypto ike policy proposal ................................................................................. 46
3.10 crypto ike proposal ..................................................................................................... 47
3.10.1 crypto ike proposal dh-group .......................................................................... 47
3.10.2 crypto ike proposal encryption ....................................................................... 48
3.10.3 crypto ike proposal integrity .......................................................................... 49
3.11 crypto ipsec transform-set ......................................................................................... 50
3.11.1 crypto ipsec transform-set cypher .................................................................. 50
3.11.2 crypto ipsec transform-set dh-group .............................................................. 51
3.11.3 crypto ipsec transform-set hmac .................................................................... 52
3.11.4 crypto ipsec transform-set lifetime ................................................................ 53
3.12 crypto ipsec prole ..................................................................................................... 53
3.12.1 crypto ipsec prole authentication-local ....................................................... 54
3.12.2 crypto ipsec prole authentication-remote ................................................... 54
3.12.3 crypto ipsec prole dpd-interval ..................................................................... 55
3.12.4 crypto ipsec prole identity-local ................................................................... 56
3.12.5 crypto ipsec prole match-identity-remote ................................................... 57
3.12.6 crypto ipsec prole mode ................................................................................ 57
3.12.7 crypto ipsec prole policy ............................................................................... 58
3.12.8 crypto ipsec prole preshared-key ................................................................. 59
3.12.9 crypto ipsec prole xauth ............................................................................... 59
3.12.10 crypto ipsec prole xauth-identity ............................................................... 60
3.12.11 crypto ipsec prole xauth-password ............................................................. 60
3.13 crypto map .................................................................................................................. 61
3.13.1 crypto map connect ......................................................................................... 62
3.13.2 crypto map enable ........................................................................................... 62
3.13.3 crypto map fallback-check-interval ................................................................ 63
3.13.4 crypto map force-encaps ................................................................................. 63
3.13.5 crypto map match-address ............................................................................. 64
3.13.6 crypto map nail-up ........................................................................................... 64
3.13.7 crypto map set-peer ........................................................................................ 65
3.13.8 crypto map set-peer-fallback .......................................................................... 66
3.13.9 crypto map set-prole ..................................................................................... 66
3.13.10 crypto map set-tcpmss .................................................................................. 67
8
Command Reference Guide — Keenetic Lite (KN-1310)
Page 9

Table of Contents
3.13.11 crypto map set-transform ............................................................................. 68
3.13.12 crypto map virtual-ip dns-server ................................................................... 68
3.13.13 crypto map virtual-ip enable ......................................................................... 69
3.13.14 crypto map virtual-ip nat .............................................................................. 69
3.13.15 crypto map virtual-ip range .......................................................................... 70
3.14 dns-proxy .................................................................................................................... 71
3.14.1 dns-proxy bantime ........................................................................................... 71
3.14.2 dns-proxy max-ttl ............................................................................................ 72
3.14.3 dns-proxy proceed ........................................................................................... 72
3.14.4 dns-proxy threshold ........................................................................................ 73
3.15 dyndns prole ............................................................................................................. 74
3.15.1 dyndns prole domain .................................................................................... 74
3.15.2 dyndns prole password ................................................................................. 75
3.15.3 dyndns prole send-address ........................................................................... 75
3.15.4 dyndns prole type .......................................................................................... 76
3.15.5 dyndns prole update-interval ....................................................................... 77
3.15.6 dyndns prole url ............................................................................................ 77
3.15.7 dyndns prole username ................................................................................ 78
3.16 interface ...................................................................................................................... 78
3.16.1 interface authentication chap ........................................................................ 79
3.16.2 interface authentication eap-md5 .................................................................. 79
3.16.3 interface authentication eap-ttls .................................................................... 80
3.16.4 interface authentication identity ................................................................... 80
3.16.5 interface authentication mschap ................................................................... 81
3.16.6 interface authentication mschap-v2 .............................................................. 82
3.16.7 interface authentication pap .......................................................................... 82
3.16.8 interface authentication password ................................................................ 83
3.16.9 interface authentication shared ..................................................................... 83
3.16.10 interface authentication wpa-psk ................................................................ 84
3.16.11 interface bandwidth-limit ............................................................................. 84
3.16.12 interface ccp ................................................................................................... 85
3.16.13 interface channel ........................................................................................... 86
3.16.14 interface channel auto-rescan ...................................................................... 86
3.16.15 interface channel width ................................................................................ 87
3.16.16 interface compatibility .................................................................................. 88
3.16.17 interface connect ........................................................................................... 88
3.16.18 interface country-code .................................................................................. 89
3.16.19 interface debug .............................................................................................. 90
3.16.20 interface description ..................................................................................... 90
3.16.21 interface down ............................................................................................... 91
3.16.22 interface duplex ............................................................................................. 91
3.16.23 interface dyndns prole ................................................................................ 92
3.16.24 interface dyndns update ............................................................................... 92
Keenetic Lite (KN-1310) — Command Reference Guide
9
Page 10

Table of Contents
3.16.25 interface encryption disable ......................................................................... 93
3.16.26 interface encryption enable .......................................................................... 93
3.16.27 interface encryption key ............................................................................... 94
3.16.28 interface encryption mppe ............................................................................ 95
3.16.29 interface encryption wpa .............................................................................. 95
3.16.30 interface encryption wpa2 ............................................................................ 96
3.16.31 interface owcontrol ..................................................................................... 96
3.16.32 interface hide-ssid ......................................................................................... 97
3.16.33 interface igmp downstream .......................................................................... 98
3.16.34 interface igmp fork ........................................................................................ 98
3.16.35 interface igmp upstream ............................................................................... 99
3.16.36 interface include ............................................................................................ 99
3.16.37 interface inherit ........................................................................................... 100
3.16.38 interface ip access-group ............................................................................ 101
3.16.39 interface ip address ..................................................................................... 101
3.16.40 interface ip address dhcp ............................................................................ 103
3.16.41 interface ip adjust-ttl ................................................................................... 103
3.16.42 interface ip adjust-ttl send .......................................................................... 104
3.16.43 interface ip alias .......................................................................................... 105
3.16.44 interface ip dhcp client class-id ................................................................... 105
3.16.45 interface ip dhcp client debug ..................................................................... 106
3.16.46 interface ip dhcp client displace ................................................................. 107
3.16.47 interface ip dhcp client dns-routes ............................................................. 107
3.16.48 interface ip dhcp client fallback .................................................................. 108
3.16.49 interface ip dhcp client hostname .............................................................. 108
3.16.50 interface ip dhcp client name-servers ........................................................ 109
3.16.51 interface ip dhcp client release ................................................................... 110
3.16.52 interface ip dhcp client renew ..................................................................... 110
3.16.53 interface ip dhcp client routes .................................................................... 111
3.16.54 interface ip global ........................................................................................ 111
3.16.55 interface ip mru ........................................................................................... 112
3.16.56 interface ip mtu ........................................................................................... 112
3.16.57 interface ip remote ...................................................................................... 113
3.16.58 interface ip tcp adjust-mss .......................................................................... 114
3.16.59 interface ipcp default-route ........................................................................ 114
3.16.60 interface ipcp dns-routes ............................................................................. 115
3.16.61 interface ipcp name-servers ........................................................................ 115
3.16.62 interface ipcp vj ........................................................................................... 116
3.16.63 interface ipsec encryption-level .................................................................. 117
3.16.64 interface ipsec ignore .................................................................................. 118
3.16.65 interface ipsec ikev2 .................................................................................... 118
3.16.66 interface ipsec preshared-key ..................................................................... 119
3.16.67 interface ipv6 address ................................................................................. 119
10
Command Reference Guide — Keenetic Lite (KN-1310)
Page 11

Table of Contents
3.16.68 interface ipv6 force-default ......................................................................... 120
3.16.69 interface ipv6 name-servers ........................................................................ 120
3.16.70 interface ipv6 prex ..................................................................................... 121
3.16.71 interface ipv6cp ........................................................................................... 122
3.16.72 interface lcp acfc .......................................................................................... 122
3.16.73 interface lcp echo ......................................................................................... 123
3.16.74 interface lcp pfc ........................................................................................... 124
3.16.75 interface mac access-list address ................................................................ 124
3.16.76 interface mac access-list type ..................................................................... 125
3.16.77 interface mac address ................................................................................. 126
3.16.78 interface mac address factory ..................................................................... 126
3.16.79 interface mac clone ..................................................................................... 127
3.16.80 interface peer ............................................................................................... 127
3.16.81 interface ping-check prole ........................................................................ 128
3.16.82 interface power ............................................................................................ 129
3.16.83 interface pppoe service ............................................................................... 129
3.16.84 interface preamble-short ............................................................................ 130
3.16.85 interface rekey-interval ............................................................................... 130
3.16.86 interface rename ......................................................................................... 131
3.16.87 interface rf e2p set ....................................................................................... 131
3.16.88 interface security-level ................................................................................ 132
3.16.89 interface speed ............................................................................................ 133
3.16.90 interface speed nonegotiate ....................................................................... 134
3.16.91 interface ssid ................................................................................................ 134
3.16.92 interface switchport access ......................................................................... 135
3.16.93 interface switchport friend ......................................................................... 136
3.16.94 interface switchport mode .......................................................................... 137
3.16.95 interface switchport trunk .......................................................................... 138
3.16.96 interface trafc-shape ................................................................................. 138
3.16.97 interface tsp ................................................................................................. 139
3.16.98 interface tunnel destination ....................................................................... 141
3.16.99 interface tunnel eoip id ............................................................................... 142
3.16.100 interface tunnel source ............................................................................. 143
3.16.101 interface tx-burst ....................................................................................... 144
3.16.102 interface tx-queue ..................................................................................... 144
3.16.103 interface up ................................................................................................ 145
3.16.104 interface usb power-cycle .......................................................................... 145
3.16.105 interface wmm ........................................................................................... 146
3.16.106 interface wps .............................................................................................. 146
3.16.107 interface wps auto-self-pin ........................................................................ 147
3.16.108 interface wps button ................................................................................. 147
3.16.109 interface wps peer ..................................................................................... 148
3.16.110 interface wps self-pin ................................................................................ 148
Keenetic Lite (KN-1310) — Command Reference Guide
11
Page 12

Table of Contents
3.17 ip arp ......................................................................................................................... 149
3.18 ip dhcp class .............................................................................................................. 150
3.18.1 ip dhcp class option ....................................................................................... 150
3.19 ip dhcp host ............................................................................................................... 151
3.20 ip dhcp pool ............................................................................................................... 152
3.20.1 ip dhcp pool bind ............................................................................................ 153
3.20.2 ip dhcp pool class ........................................................................................... 153
3.20.3 ip dhcp pool debug ......................................................................................... 155
3.20.4 ip dhcp pool default-router ........................................................................... 155
3.20.5 ip dhcp pool dns-server ................................................................................. 156
3.20.6 ip dhcp pool domain ...................................................................................... 156
3.20.7 ip dhcp pool enable ........................................................................................ 157
3.20.8 ip dhcp pool lease .......................................................................................... 157
3.20.9 ip dhcp pool range ......................................................................................... 158
3.20.10 ip dhcp pool update-dns .............................................................................. 159
3.20.11 ip dhcp pool wpad ........................................................................................ 159
3.21 ip dhcp relay lan ....................................................................................................... 160
3.22 ip dhcp relay server .................................................................................................. 160
3.23 ip dhcp relay wan ...................................................................................................... 161
3.24 ip host ........................................................................................................................ 162
3.25 ip hotspot .................................................................................................................. 162
3.25.1 ip hotspot auto-scan interface ...................................................................... 163
3.25.2 ip hotspot auto-scan interval ........................................................................ 163
3.25.3 ip hotspot auto-scan passive ......................................................................... 164
3.25.4 ip hotspot auto-scan timeout ........................................................................ 165
3.25.5 ip hotspot default-policy ............................................................................... 165
3.25.6 ip hotspot host ............................................................................................... 166
3.25.7 ip hotspot policy ............................................................................................ 167
3.25.8 ip hotspot wake ............................................................................................. 168
3.26 ip http lockout-policy ............................................................................................... 168
3.27 ip http port ................................................................................................................ 169
3.28 ip http proxy ............................................................................................................. 170
3.28.1 ip http proxy allow ......................................................................................... 170
3.28.2 ip http proxy domain ..................................................................................... 171
3.28.3 ip http proxy domain ndns ............................................................................ 172
3.28.4 ip http proxy upstream .................................................................................. 172
3.29 ip http security-level ................................................................................................. 173
3.30 ip http ssl enable ...................................................................................................... 173
3.31 ip name-server .......................................................................................................... 174
3.32 ip nat ......................................................................................................................... 175
3.33 ip nat vpn .................................................................................................................. 176
3.34 ip route ...................................................................................................................... 176
3.35 ip search-domain ...................................................................................................... 178
12
Command Reference Guide — Keenetic Lite (KN-1310)
Page 13

Table of Contents
3.36 ip static ...................................................................................................................... 178
3.37 ip telnet ..................................................................................................................... 180
3.37.1 ip telnet lockout-policy .................................................................................. 180
3.37.2 ip telnet port .................................................................................................. 181
3.37.3 ip telnet security-level ................................................................................... 181
3.37.4 ip telnet session max-count .......................................................................... 182
3.37.5 ip telnet session timeout ............................................................................... 183
3.38 ip trafc-shape host ................................................................................................. 183
3.39 ipv6 rewall .............................................................................................................. 184
3.40 ipv6 local-prex ........................................................................................................ 184
3.41 ipv6 name-server ...................................................................................................... 185
3.42 ipv6 route .................................................................................................................. 186
3.43 ipv6 subnet ................................................................................................................ 186
3.43.1 ipv6 subnet bind ............................................................................................ 187
3.43.2 ipv6 subnet mode .......................................................................................... 188
3.43.3 ipv6 subnet number ....................................................................................... 188
3.43.4 ipv6 subnet stateless-dhcp ............................................................................ 189
3.44 isolate-private ........................................................................................................... 189
3.45 known host ............................................................................................................... 190
3.46 ndns ........................................................................................................................... 190
3.46.1 ndns book-name ............................................................................................ 190
3.46.2 ndns check-name ........................................................................................... 193
3.46.3 ndns drop-name ............................................................................................. 194
3.46.4 ndns get-booked ............................................................................................ 195
3.46.5 ndns get-update ............................................................................................. 196
3.47 ntce shaping ............................................................................................................. 198
3.48 ntp ............................................................................................................................. 198
3.49 ntp server .................................................................................................................. 199
3.50 ntp sync-period ......................................................................................................... 199
3.51 opkg chroot ............................................................................................................... 200
3.52 opkg disk ................................................................................................................... 200
3.53 opkg dns-override ..................................................................................................... 201
3.54 opkg initrc ................................................................................................................. 202
3.55 opkg timezone .......................................................................................................... 202
3.56 ping-check prole ..................................................................................................... 203
3.56.1 ping-check prole host .................................................................................. 204
3.56.2 ping-check prole max-fails .......................................................................... 204
3.56.3 ping-check prole min-success ..................................................................... 205
3.56.4 ping-check prole mode ................................................................................ 206
3.56.5 ping-check prole port .................................................................................. 206
3.56.6 ping-check prole power-cycle ..................................................................... 207
3.56.7 ping-check prole restart-interface ............................................................. 207
3.56.8 ping-check prole timeout ............................................................................ 208
Keenetic Lite (KN-1310) — Command Reference Guide
13
Page 14

Table of Contents
3.56.9 ping-check prole update-interval ............................................................... 208
3.57 ppe ............................................................................................................................. 209
3.58 pppoe pass ................................................................................................................ 209
3.59 schedule .................................................................................................................... 210
3.59.1 schedule action .............................................................................................. 211
3.59.2 schedule description ...................................................................................... 211
3.60 service cloud-control ................................................................................................ 212
3.61 service dhcp .............................................................................................................. 212
3.62 service dhcp-relay ..................................................................................................... 213
3.63 service dns-proxy ...................................................................................................... 213
3.64 service http ............................................................................................................... 214
3.65 service igmp-proxy ................................................................................................... 214
3.66 service ipsec .............................................................................................................. 215
3.67 service ntce ............................................................................................................... 215
3.68 service ntp-client ...................................................................................................... 216
3.69 service snmp ............................................................................................................. 216
3.70 service telnet ............................................................................................................ 217
3.71 service udpxy ............................................................................................................ 217
3.72 service upnp .............................................................................................................. 218
3.73 service vpn-server ..................................................................................................... 218
3.74 show .......................................................................................................................... 219
3.74.1 show associations .......................................................................................... 219
3.74.2 show clock date ............................................................................................. 220
3.74.3 show clock timezone-list ............................................................................... 221
3.74.4 show crypto ike key ....................................................................................... 222
3.74.5 show crypto map ........................................................................................... 222
3.74.6 show dot1x ..................................................................................................... 224
3.74.7 show drivers ................................................................................................... 225
3.74.8 show interface ............................................................................................... 226
3.74.9 show interface bridge .................................................................................... 227
3.74.10 show interface channels .............................................................................. 228
3.74.11 show interface country-codes ..................................................................... 229
3.74.12 show interface mac ...................................................................................... 230
3.74.13 show interface rf e2p ................................................................................... 232
3.74.14 show interface stat ...................................................................................... 233
3.74.15 show interface wps pin ................................................................................ 233
3.74.16 show interface wps status ........................................................................... 234
3.74.17 show ip arp ................................................................................................... 235
3.74.18 show ip dhcp bindings ................................................................................. 236
3.74.19 show ip dhcp pool ........................................................................................ 236
3.74.20 show ip hotspot ............................................................................................ 237
3.74.21 show ip name-server .................................................................................... 239
3.74.22 show ip nat ................................................................................................... 239
14
Command Reference Guide — Keenetic Lite (KN-1310)
Page 15

Table of Contents
3.74.23 show ip route ............................................................................................... 240
3.74.24 show ipsec .................................................................................................... 241
3.74.25 show ipv6 addresses .................................................................................... 242
3.74.26 show ipv6 prexes ....................................................................................... 243
3.74.27 show ipv6 routes .......................................................................................... 244
3.74.28 show last-change ......................................................................................... 244
3.74.29 show log ....................................................................................................... 245
3.74.30 show ndns .................................................................................................... 246
3.74.31 show netlter ............................................................................................... 246
3.74.32 show ntce hosts ........................................................................................... 247
3.74.33 show ntp status ............................................................................................ 247
3.74.34 show ping-check .......................................................................................... 248
3.74.35 show running-cong .................................................................................... 249
3.74.36 show self-test ............................................................................................... 252
3.74.37 show site-survey .......................................................................................... 252
3.74.38 show system ................................................................................................. 253
3.74.39 show tags ..................................................................................................... 253
3.74.40 show upnp redirect ...................................................................................... 254
3.74.41 show version ................................................................................................ 255
3.74.42 show vpn-server ........................................................................................... 256
3.75 snmp community ...................................................................................................... 256
3.76 snmp contact ............................................................................................................ 257
3.77 snmp location ........................................................................................................... 257
3.78 system ....................................................................................................................... 258
3.78.1 system button ................................................................................................ 258
3.78.2 system clock date .......................................................................................... 259
3.78.3 system clock timezone .................................................................................. 260
3.78.4 system conguration factory-reset .............................................................. 260
3.78.5 system conguration save ............................................................................ 261
3.78.6 system debug ................................................................................................. 261
3.78.7 system domainname ..................................................................................... 262
3.78.8 system hostname ........................................................................................... 262
3.78.9 system led shutdown ..................................................................................... 263
3.78.10 system log clear ........................................................................................... 264
3.78.11 system log reduction ................................................................................... 264
3.78.12 system log server ......................................................................................... 264
3.78.13 system log suppress ..................................................................................... 265
3.78.14 system mode ................................................................................................ 266
3.78.15 system reboot .............................................................................................. 266
3.78.16 system set .................................................................................................... 267
3.79 tools ........................................................................................................................... 268
3.79.1 tools arping .................................................................................................... 268
3.79.2 tools ping ........................................................................................................ 269
Keenetic Lite (KN-1310) — Command Reference Guide
15
Page 16

Table of Contents
3.79.3 tools ping6 ...................................................................................................... 270
3.79.4 tools pppoe-discovery .................................................................................... 271
3.79.5 tools traceroute .............................................................................................. 272
3.80 udpxy ......................................................................................................................... 274
3.80.1 udpxy buffer-size ........................................................................................... 274
3.80.2 udpxy buffer-timeout .................................................................................... 275
3.80.3 udpxy interface .............................................................................................. 275
3.80.4 udpxy port ...................................................................................................... 276
3.80.5 udpxy renew-interval .................................................................................... 277
3.80.6 udpxy timeout ................................................................................................ 277
3.81 upnp forward ............................................................................................................ 278
3.82 upnp lan .................................................................................................................... 278
3.83 upnp redirect ............................................................................................................ 279
3.84 user ............................................................................................................................ 280
3.84.1 user password ................................................................................................ 281
3.84.2 user tag .......................................................................................................... 281
3.85 vpn-server ................................................................................................................. 282
3.85.1 vpn-server interface ...................................................................................... 283
3.85.2 vpn-server lcp echo ........................................................................................ 283
3.85.3 vpn-server mppe ............................................................................................ 284
3.85.4 vpn-server mppe-optional ............................................................................. 285
3.85.5 vpn-server mru .............................................................................................. 285
3.85.6 vpn-server mtu ............................................................................................... 286
3.85.7 vpn-server multi-login ................................................................................... 286
3.85.8 vpn-server pool-range ................................................................................... 287
3.85.9 vpn-server static-ip ........................................................................................ 287
3.86 yandexdns ................................................................................................................. 288
3.86.1 yandexdns assign ........................................................................................... 288
3.86.2 yandexdns check-availability ........................................................................ 289
3.86.3 yandexdns enable .......................................................................................... 289
Glossary .............................................................................................................................. 291
Appendix A
Interface Hierarchy ........................................................................................................... 299
Appendix B
HTTP API ............................................................................................................................. 301
B.1 REST Core Interface ....................................................................................................... 301
B.1.1 Resource Location ............................................................................................... 301
B.1.2 Methods .............................................................................................................. 301
B.1.3 Data Format ........................................................................................................ 302
B.2 XML Core Interface ........................................................................................................ 305
B.2.1 Command Request .............................................................................................. 306
B.2.2 Conguration Request ........................................................................................ 307
16
Command Reference Guide — Keenetic Lite (KN-1310)
Page 17

Table of Contents
B.2.3 Request Packet .................................................................................................... 307
Appendix C
SNMP MIB ........................................................................................................................... 309
C.1 SNMPv2-MIB ................................................................................................................ 309
C.2 IF-MIB ............................................................................................................................ 309
C.3 IP-MIB ............................................................................................................................ 311
C.4 UDP-MIB ........................................................................................................................ 312
C.5 HOST-RESOURCES-MIB .................................................................................................. 312
C.6 UCD-SNMP-MIB ............................................................................................................. 312
Appendix D
IPsec Encryption Levels .................................................................................................... 315
D.1 weak .............................................................................................................................. 315
D.2 normal ........................................................................................................................... 316
D.3 normal-3des .................................................................................................................. 316
D.4 strong ............................................................................................................................ 317
D.5 weak-pfs ........................................................................................................................ 317
D.6 normal-pfs ..................................................................................................................... 319
D.7 normal-3des-pfs ............................................................................................................ 319
Keenetic Lite (KN-1310) — Command Reference Guide
17
Page 18

Table of Contents
18
Command Reference Guide — Keenetic Lite (KN-1310)
Page 19
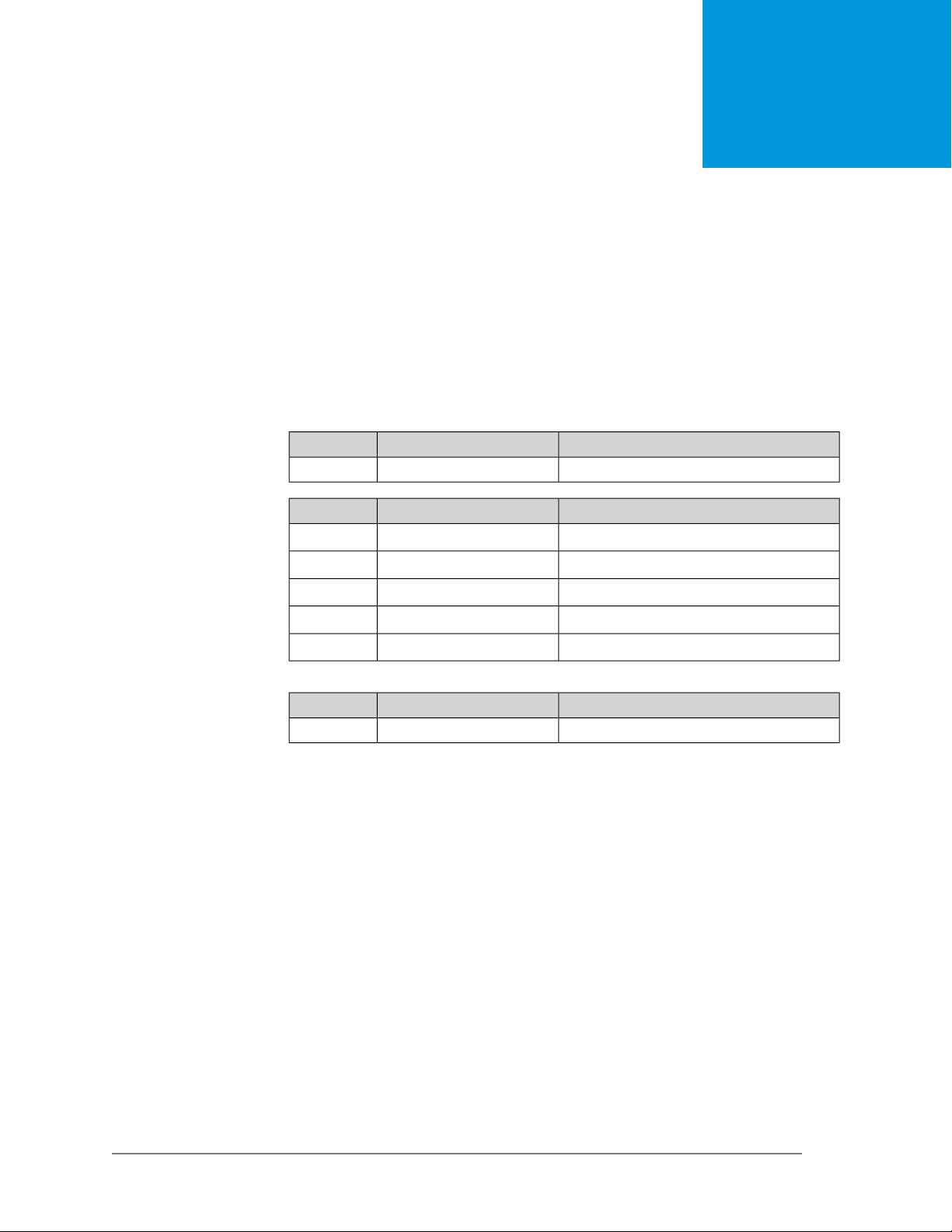
Product Overview
1.1 Hardware Conguration
CPU MT7628NN MIPS® 24KEc 575 MHz
RAM Winbond W9751G6KB-25 64Mb DDR2
Flash Winbond W25Q128JVFQ 16Mb SPI
1
Ethernet
Wi-Fi
NotesChipsetPorts
Integrated5
NotesSpeedLabel
WAN port100 Mbps0
100 Mbps1
100 Mbps2
100 Mbps3
100 Mbps4
NotesChipsetBand
802.11bgn 2x2MediaTek MT76032.4 GHz
Keenetic Lite (KN-1310) — Command Reference Guide19Command Reference Guide — Keenetic Lite (KN-1310)
Page 20

Chapter 1 Product Overview
20
Page 21

2
Introduction to the CLI
This chapter describes how to use the Keenetic Lite Command-Line Interface (CLI), its
hierarchical structure, authorization levels and its help features.
The primary tool for managing the Keenetic Lite router is the command line interface (CLI).
System settings can be dened as a sequence of commands, which can be executed to
bring the device to the specied condition.
Keenetic Lite has three types of settings:
Current settings running cong is a set of commands describing the current
status of the system. Current settings are stored in RAM and
reect every change of the system settings. However, the
content of RAM is lost when the device is turned off. To
restore the settings after reboot, they must be saved in
non-volatile memory.
Startup conguration startup cong is a sequence of commands, which is stored in
a specic partition of the non-volatile memory. It is used to
initialize the system immediately after startup.
Default settings default cong contains factory default settings of Keenetic
Lite. RESET button is used to reset startup conguration to
the factory default.
Files startup-config and running-config can be edited manually, without participation
of the command line. It should be remembered that the lines with ! in the beginning are
ignored by the parser and the arguments which contain spaces must be enclosed in double
quotes (for example, ssid "Free Wi-Fi"). Quotes themselves are ignored by the parser.
Responsibility for the accuracy of the changes rests with their author.
2.1 Enter commands in the CLI
Command line interpreter in Keenetic Lite is designed for beginners as well as experts.
All command names and options are clear and easy to remember.
Commands are divided into groups and arranged in a hierarchy. Thus, to do a setting, the
operator needs to enter a sequence of nested command group names (node commands),
and then enter the nal command with parameters.
For example, IP-address of the FastEthernet0/Vlan2 network interface is set using the
address command, which is located in the interface → ip group:
(config)>interface FastEthernet0/Vlan2 ip address 192.168.15.43/24
Network address saved.
Keenetic Lite (KN-1310) — Command Reference Guide
21
Page 22

Chapter 2 Introduction to the CLI
2.1.1 Entering a group
Some of the node commands (containing a group of child commands) can be “entered”
to allow direct executing of the child commands without typing the node name as prex.
In this case the prompt is changed to indicate the entered group.
The exit command or [Ctrl]+[D] key combination can be used to exit a group.
For example, after entering the interface group the command line prompt is changed to
(config-if):
(config)>interface FastEthernet0/Vlan2
(config-if)>ip address 192.168.15.43/24
Network address saved.
(config-if)>[Ctrl]+[D]
(config)>
2.2 Getting Help and auto-completion
To make the conguring process as comfortable as possible, the CLI provides
auto-completion of commands and parameters, hinting the operator, which commands
are available at the current level of nesting. Auto-completion works by pressing [Tab].
Example:
(config)>in[Tab]
interface - network interface configuration
(config)> interface Fa[Tab]
Usage template:
interface {name}
Variants:
FastEthernet0
FastEthernet0/Vlan1
FastEthernet0/Vlan2
(config)> interface FastEthernet0[Tab]
Usage template:
interface {name}
Variants:
FastEthernet0/Vlan1
FastEthernet0/Vlan2
(config)> interface FastEthernet0[Enter]
(config-if)> ip[Tab]
22
address - set interface IP address
alias - add interface IP alias
dhcp - enable dhcp client
Command Reference Guide — Keenetic Lite (KN-1310)
Page 23

Chapter 2 Introduction to the CLI
mtu - set Maximum Transmit Unit size
mru - set Maximum Receive Unit size
access-group - bind access-control rules
apn - set 3G access point name
(config-if)> ip ad[Tab]
address - set interface IP address
(config-if)> ip address[Tab]
Usage template:
address {address} {mask}
(config-if)> ip address 192.168.15.43[Enter]
Configurator error[852002]: address: argument parse error.
(config-if)> ip address 192.168.15.43/24[Enter]
Network address saved.
(config-if)>
Hint for the current command can always be displayed by pressing [?]. Example:
(config)> interface FastEthernet0/Vlan2 [?]
description - set interface description
alias - add interface name alias
mac-address - set interface MAC address
dyndns - DynDns updates
security-level - assign security level
authentication - configure authentication
(config)> interface FastEthernet0/Vlan2
2.3 Prex no
Prex no is used to negate a command.
For example, the command interface is responsible for creating a network interface with
the given name. When used with this command, prex no causes the opposite action —
removing of the interface:
(config)> no interface PPPoE0
ip - set interface IP parameters
igmp - set interface IGMP parameters
up - enable interface
down - disable interface
If the command is composite, no can be placed in front of any member. For example,
service dhcp enables the DHCP service. It consists of two parts: service — the group name
in the hierarchy of commands, and dhcp — the nal command. Prex no can be placed
either at the beginning, or in the middle. The action is the same in both cases: stopping
of the service.
Keenetic Lite (KN-1310) — Command Reference Guide
23
Page 24

Chapter 2 Introduction to the CLI
(config)> no service dhcp
(config)> service no dhcp
2.4 Multiple input
Many commands have the property of idempotence, which means that multiple input of a
command has the same effect as as the single input. For example, entering service http
adds a single line “service http” to the current settings, and re-entering does not change
anything.
However, some of the commands allow you to add not a single, but multiple records, if
they are entered with different arguments. For example, static routing table entries ip
route or lters access-list are added sequentially and appear in the settings as a list:
Example 2.1. Using a command with multiple input
(config)> ip route 1.1.1.0/24 PPTP0
Network::RoutingTable: Added static route: 1.1.1.0/24 via PPTP0.
(config)> ip route 1.1.2.0/24 PPTP0
Network::RoutingTable: Added static route: 1.1.2.0/24 via PPTP0.
(config)> ip route 1.1.3.0/24 PPTP1
Network::RoutingTable: Added static route: 1.1.3.0/24 via PPTP1.
(config)> show running-config
...
ip route 1.1.1.0 255.255.255.0 PPTP0
ip route 1.1.2.0 255.255.255.0 PPTP0
ip route 1.1.3.0 255.255.255.0 PPTP1
...
Records from such tables can be removed one by one, using prex no and arguments to
identify the record you want to remove:
(config)> no ip route 1.1.2.0/24
Network::RoutingTable: Deleted static route: 1.1.2.0/24 via PPTP0.
(config)> show running-config
...
ip route 1.1.1.0 255.255.255.0 PPTP0
ip route 1.1.3.0 255.255.255.0 PPTP1
...
2.5 Saving to startup settings
Current and startup settings are stored in the les running-cong and startup-cong,
respectively. To save the current settings in the non-volatile memory, copy them as shown
below:
(config)> copy running-config startup-config
Copied: running-config -> startup-config
24
Command Reference Guide — Keenetic Lite (KN-1310)
Page 25

2.6 Delayed restart
If Keenetic Lite device is located away from the operator and is managed remotely, there
is a risk to lose control over it because of a misoperation. In this case it will be difcult to
reboot and return to the saved settings.
The system reboot command lets you set a delayed restart timer, perform “risky” settings,
then turn off the timer and save the changes. If connection to the device is lost during
conguration, the operator will be enough to wait for automatic reboot and connect to
the device again.
Chapter 2 Introduction to the CLI
Keenetic Lite (KN-1310) — Command Reference Guide
25
Page 26

Chapter 2 Introduction to the CLI
26
Command Reference Guide — Keenetic Lite (KN-1310)
Page 27
3
Command Reference
3.1 Core commands
Core commands are used to manage les on your device.
3.1.1 copy
Description Copy the contents of one le to another. Used for the rmware updating,
saving the current settings, resetting to factory, etc.
Prex no No
Change settings No
Multiple input No
Synopsis
Arguments
Example Current settings can be saved as follows:
History
(cong)> copy ‹source› ‹destination›
DescriptionValueArgument
Filenamesource
(config)> copy running-config startup-config
File names in this example are aliases. Full names of the conguration les
are system:running-config and flash:startup-config, respectively.
Version Description
The copy command has been introduced.2.00
Full path to the le to be copied in <le
system>:<path> format
Full path to the directory for the new le.Filenamedestination
3.1.2 erase
Description Delete a le from the Keenetic Lite device.
Prex no No
Change settings Yes
Keenetic Lite (KN-1310) — Command Reference Guide
27
Page 28
Chapter 3 Command Reference
Multiple input Yes
Synopsis
Arguments
Example
History
(cong)> erase ‹filename›
(config)> erase FLASH:swap
Erased FLASH:swap.
Version Description
The erase command has been introduced.2.00
3.1.3 exit
Description Leave the command node.
Prex no No
Change settings No
Multiple input No
DescriptionValueArgument
Species the le to be removed.Filenamefilename
Synopsis
Example
History
(cong)> exit
(config-dyndns)> exit
(config)>
Version Description
The exit command has been introduced.2.00
3.1.4 ls
Description Display list of les from the specied directory.
Prex no No
Change settings No
Multiple input No
Synopsis
(cong)> ls [ directory ]
28
Command Reference Guide — Keenetic Lite (KN-1310)
Page 29
Chapter 3 Command Reference
Arguments
Example
Stringdirectory
(config)> ls temp:
rel: temp:
entry, type = R:
entry, type = D:
entry, type = D:
entry, type = R:
entry, type = R:
entry, type = D:
entry, type = D:
entry, type = D:
entry, type = D:
entry, type = D:
entry, type = D:
DescriptionValueArgument
Path to the directory. Must contain the
name of the le system and path to the
folder directly in the following format <le
system>:<path>. Examples of le systems
— ash, temp, proc, usb. etc.
name: resolv.conf
size: 107
name: db
name: dhcp6c
name: TZ
size: 6
name: passwd
size: 128
name: dnscache
name: mnt
name: tmp
name: ppp
name: lib
name: run
History
Version Description
The ls command has been introduced.2.00
3.1.5 more
Description Display the contents of a text le line by line.
Prex no No
Change settings No
Multiple input No
Keenetic Lite (KN-1310) — Command Reference Guide
29
Page 30
Chapter 3 Command Reference
Synopsis
Arguments
Example
History
(cong)> more ‹filename›
DescriptionValueArgument
Full path to the le or alias.Filenamefilename
(config)> more temp:resolv.conf
nameserver 82.138.7.15
nameserver 82.138.7.251
nameserver 82.138.7.130
options timeout:1 attempts:3 rotate
Version Description
The more command has been introduced.2.00
3.2 access-list
Description Access to a group of commands to congure the selected list of packet ltering
rules. If the list is not found, the command tries to create it. Such a list can
be assigned to a network interface using interface ip access-group command.
Command with no prex removes the list of rules.
Prex no Yes
Change settings Yes
Multiple input Yes
Group entry (config-acl)
Synopsis
Arguments
History
(cong)> access-list ‹name›
(cong)> no access-list ‹name›
Version Description
DescriptionValueArgument
Stringname
The access-list command has been introduced.2.00
Filtering rules list name (Access Control List,
ACL).
3.2.1 access-list deny
Description Add a packet ltering deny rule into a specied ACL.
30
Command Reference Guide — Keenetic Lite (KN-1310)
Page 31

Command with no prex removes the rule.
Prex no Yes
Change settings Yes
Multiple input Yes
Chapter 3 Command Reference
Synopsis
Arguments
(cong-acl)> deny (tcp | udp) ‹source› ‹source-mask›
[ port( ( ‹src-port-operator› ‹source-port› )|
( range ‹source-port› ‹source-end-port› ))]
‹destination› ‹destination-mask›
[ port( ( ‹dst-port-operator› ‹destination-port› )|
( range ‹destination-port› ‹destination-end-port› ))]
(cong-acl)> deny (icmp | esp | gre | ipip | ip) ‹source› ‹source-mask›
‹destination› ‹destination-mask›
(cong-acl)> no deny (tcp | udp) ‹source› ‹source-mask›
[ port( ( ‹src-port-operator› ‹source-port› )|
( range ‹source-port› ‹source-end-port› ))]
‹destination› ‹destination-mask›
[ port( ( ‹dst-port-operator› ‹destination-port› )|
( range ‹destination-port› ‹destination-end-port› ))]
(cong-acl)> no deny (icmp | esp | gre | ipip | ip) ‹source› ‹source-mask›
‹destination› ‹destination-mask›
DescriptionValueArgument
TCP protocol.Keywordtcp
Keenetic Lite (KN-1310) — Command Reference Guide
UDP protocol.Keywordudp
ICMP protocol.Keywordicmp
ESP protocol.Keywordesp
GRE protocol.Keywordgre
IP in IP protocol.Keywordipip
Keywordip
IP-addresssource
IP-masksource-mask
IP protocol (include TCP, UDP, ICMP
and other).
The source address in the header
of IP-packet.
Mask to be applied to the source
address in the header of IP-packet
before comparison with source.
There are two ways to enter the
mask: the canonical form (for
example, 255.255.255.0) and the
form of prex bit length (for
example, /24).
31
Page 32
Chapter 3 Command Reference
src-port-operator Operator “less” to compare the
Integersource-port
Integersource-end-port
lt
DescriptionValueArgument
Source port in the TCP or UDP
header.
The end of the source range of
ports.
port with the specied
source-port.
eq
Operator “equal” to compare the
port with the specied
source-port.
gt
Operator “greater” to compare the
port with the specied
source-port.
IP-addressdestination
The destination address in the
header of IP-packet.
IP-maskdestination-mask
Mask to be applied to the
destination address in the header
of IP-packet before comparison
with destination. There are two
ways to enter the mask: in the
canonical form (for example,
255.255.255.0) and in the form of
prex with bit length (for example,
/24).
Integerdestination-port
Destination port in the TCP or UDP
header.
Integerdestination-end-port
The end of the destination range
of ports.
dst-port-operator Operator “less” to compare the
lt
port with the specied
destination-port.
Example
History
32
eq
gt
(config-acl)> deny icmp 192.168.0.0
255.255.255.0 192.168.1.1 255.255.255.0
ACL rule added.
Version Description
The access-list deny command has been introduced.2.00
Command Reference Guide — Keenetic Lite (KN-1310)
Operator “equal” to compare the
port with the specied
destination-port.
Operator “greater” to compare the
port with the specied
destination-port.
Page 33
Chapter 3 Command Reference
New value ip was added to the protocol argument.2.06
New protocols esp, gre and ipip were added.2.08
Port ranges were added.2.09.A.2.1
3.2.2 access-list permit
Description Add a packet ltering permit rule into a specied ACL.
Command with no prex removes the rule.
Prex no Yes
Change settings Yes
Multiple input Yes
Synopsis
Arguments
(cong-acl)> permit (tcp | udp) ‹source› ‹source-mask›
[ port( ( ‹src-port-operator› ‹source-port› )|
( range ‹source-port› ‹source-end-port› ))]
‹destination› ‹destination-mask›
[ port( ( ‹dst-port-operator› ‹destination-port› )|
( range ‹destination-port› ‹destination-end-port› ))]
(cong-acl)> permit (icmp | esp | gre | ipip | ip) ‹source› ‹source-mask›
‹destination› ‹destination-mask›
(cong-acl)> no permit (tcp | udp) ‹source› ‹source-mask›
[ port( ( ‹src-port-operator› ‹source-port› )|
( range ‹source-port› ‹source-end-port› ))]
‹destination› ‹destination-mask›
[ port( ( ‹dst-port-operator› ‹destination-port› )|
( range ‹destination-port› ‹destination-end-port› ))]
(cong-acl)> no permit (icmp | esp | gre | ipip | ip) ‹source› ‹source-mask›
‹destination› ‹destination-mask›
DescriptionValueArgument
TCP protocol.Keywordtcp
Keenetic Lite (KN-1310) — Command Reference Guide
UDP protocol.Keywordudp
ICMP protocol.Keywordicmp
ESP protocol.Keywordesp
GRE protocol.Keywordgre
IP in IP protocol.Keywordipip
Keywordip
IP protocol (include TCP, UDP, ICMP
and other).
33
Page 34
Chapter 3 Command Reference
DescriptionValueArgument
IP-addresssource
The source address in the header
of IP-packet.
IP-masksource-mask
Mask to be applied to the source
address in the header of IP-packet
before comparison with source.
There are two ways to enter the
mask: the canonical form (for
example, 255.255.255.0) and the
form of prex bit length (for
example, /24).
Integersource-port
Source port in the TCP or UDP
header.
Integersource-end-port
The end of the source range of
ports.
src-port-operator Operator “less” to compare the
lt
port with the specied
source-port.
eq
Operator “equal” to compare the
port with the specied
source-port.
gt
Operator “greater” to compare the
port with the specied
source-port.
IP-addressdestination
The destination address in the
header of IP-packet.
IP-maskdestination-mask
Mask to be applied to the
destination address in the header
of IP-packet before comparison
with destination. There are two
ways to enter the mask: in the
canonical form (for example,
255.255.255.0) and in the form of
prex with bit length (for example,
/24).
34
Integerdestination-port
Destination port in the TCP or UDP
header.
Integerdestination-end-port
The end of the destination range
of ports.
dst-port-operator Operator “less” to compare the
lt
port with the specied
destination-port.
eq
Operator “equal” to compare the
port with the specied
destination-port.
Command Reference Guide — Keenetic Lite (KN-1310)
Page 35
gt
Chapter 3 Command Reference
DescriptionValueArgument
Operator “greater” to compare the
port with the specied
destination-port.
Example
History
(config-acl)> permit icmp 192.168.0.0
255.255.255.0 192.168.1.1 255.255.255.0
ACL rule added.
Version Description
The access-list permit command has been introduced.2.00
New value ip was added to the protocol argument.2.06
New protocols esp, gre and ipip were added.2.08
Port ranges were added.2.09.A.2.1
3.3 cloud control client connect
Description Register new client. The maximum number of clients is 5.
Command with no prex removes client.
Prex no Yes
Change settings Yes
Multiple input Yes
Synopsis
Arguments
(cong)> cloud control client ‹id› connect ‹name› ‹mag› ‹app› [
‹modulus› ‹exponent› ]
(cong)> no cloud control client [‹id›] connect
DescriptionValueArgument
Stringid
Stringname
Integermodulus
Integerexponent
256-bit identier of client recorded in
hexadecimal format with a xed length.
An arbitrary name, which length does not
exceed 64 UTF-8 character.
TBDStringmag
The component of the open RSA-key of
client. Its size should be in the range [1024,
1536] bit. If not specied, the encryption
will not be performed.
The component of the open RSA-key of
client. If not specied, the encryption will
not be performed.
Keenetic Lite (KN-1310) — Command Reference Guide
35
Page 36
Chapter 3 Command Reference
DescriptionValueArgument
TBDStringapp
Example
History
(config)> cloud control client a78d...30ab connect test_client
connect:
PHJlc3VsdD48Y2lkPmRhMDQ1MGNiNzhjOTNhZmMwZWZjNGNmMGIyY2MyNDE2YjF
jNDAzNTZmODRlYWNkZDE3Mzc1OWI2OWUwNTExZGY8L2NpZD48ZGV2aWNlX25hbW
U+S2VlbmV0aWMgVml2YTwvZGV2aWNlX25hbWU+PC9yZXN1bHQ+
CloudControl::Agent: Client connection initiated.
Version Description
2.05
The cloud control client connect command has been
introduced.
3.4 cloud control client name
Description Rename the registered client.
Prex no No
Change settings Yes
Multiple input No
Synopsis
Arguments
Example
History
(cong)> cloud control client ‹id› name ‹name›
DescriptionValueArgument
Stringid
Stringname
(config)> cloud control client a78d...30ab name "New Client"
CloudControl::Agent: A client name changed.
Version Description
2.05
The cloud control client name command has been
introduced.
256-bit identier of client recorded in
hexadecimal format with a xed length.
An arbitrary name, which length does not
exceed 64 UTF-8 character.
36
Command Reference Guide — Keenetic Lite (KN-1310)
Page 37
Chapter 3 Command Reference
3.5 cloud control client session timeout
Description Set timeout of the client session in seconds.
Command with no prex resets value to default (300 seconds).
Prex no Yes
Change settings Yes
Multiple input Yes
Synopsis
Arguments
Example
History
(cong)> cloud control client ‹id› session timeout ‹seconds›
(cong)> no cloud control client [‹id›] session timeout
DescriptionValueArgument
Stringid
Integerseconds
(config)> cloud control client a78d...30ab session timeout 35
CloudControl::Agent: "test_client" session timeout set to 35 ►
seconds.
Version Description
2.05
The cloud control client session timeout command has
been introduced.
256-bit identier of client recorded in
hexadecimal format with a xed length.
The period of time that a session can
remain idle, without any end-user
interaction. Can take values in the range
from 30 to 600 inclusively.
3.6 components
Description Access to a group of commands to manage rmware components.
Prex no No
Change settings No
Multiple input No
Group entry (config-comp)
Synopsis
Keenetic Lite (KN-1310) — Command Reference Guide
(cong)> components
37
Page 38
Chapter 3 Command Reference
History
Version Description
The components command has been introduced.2.00
3.6.1 components commit
Description Apply the changes made by components install and components remove
commands.
Prex no No
Change settings Yes
Multiple input No
Synopsis
History
(cong-comp)> commit
Version Description
2.00
The components commit command has been
introduced.
3.6.2 components install
Description Mark component to install. Final installation carried out with components
commit command.
Prex no No
Change settings Yes
Multiple input Yes
Synopsis
Arguments
Example
History
(cong-comp)> install ‹component›
DescriptionValueArgument
Stringcomponent
(config-comp)> install ntfs
Component is queued for installation: ntfs
Version Description
The components install command has been introduced.2.00
Component name. List of available
components for installation can be
displayed with the components list
command.
38
Command Reference Guide — Keenetic Lite (KN-1310)
Page 39
Chapter 3 Command Reference
3.6.3 components list
Description Display the list of installed components, and components available for
installation. If there is no Internet connection, only the list of installed
components will be displayed.
Prex no No
Change settings No
Multiple input No
Synopsis
Arguments
Example
(cong-comp)> list [ sandbox ]
DescriptionValueArgument
Remote sandbox, such as stable or beta.Stringsandbox
(config-comp)> list
firmware:
version: 2.12.A.1.0-1
sandbox: draft
component:
name: storage
group: USB storage
libndm: Swap
priority: normal
depend: usb
size: 363447
order: 0
version: 3.4.113-1
hash: 2db7d67820f1598186dd939ff08a6531
installed: 3.4.113-1
preset: minimal
preset: recommended
queued: yes
...
History
Version Description
The components list command has been introduced.2.00
2.06.A.6
The sandbox parameter has been introduced. The
command components list should be used in favour of
components sync.
Keenetic Lite (KN-1310) — Command Reference Guide
39
Page 40
Chapter 3 Command Reference
3.6.4 components preset
Description Select a predened set of components. Installation of preset is carried out
with components commit command.
Before preset installation check the latest versions of components on the
update server with components list command. Internet connection required.
Prex no No
Change settings Yes
Multiple input No
Synopsis
Arguments Number and names of presets can be changed, so check the list of available
Example
History
(cong-comp)> preset ‹preset›
presets with help of preset ? command.
DescriptionValueArgument
preset Minimal set of components will be marked.minimal
recommended
(config-comp)> preset recommended
lib::libndmComponents error[268369922]: updates are available ►
for this system.
(config-comp)> commit
Core::System::UConfig: done.
Version Description
The components preset command has been introduced.2.00
Recommended set of components will be
marked for installation.
3.6.5 components preview
Description Show size of rmware as current set of components selected with
components install command.
Prex no No
Change settings Yes
Multiple input No
Synopsis
Example
40
(cong-comp)> preview
(config-comp)> preview
Command Reference Guide — Keenetic Lite (KN-1310)
Page 41
preview:
Chapter 3 Command Reference
size: 7733308
History
Version Description
2.06
The components preview command has been
introduced.
3.6.6 components remove
Description Mark component to remove. Final removal carried out with components
commit command.
Prex no No
Change settings Yes
Multiple input Yes
Synopsis
Arguments
(cong-comp)> remove ‹component›
DescriptionValueArgument
Stringcomponent
Component name. List of available
components for removal can be displayed
with the components list command.
Example
History
(config-comp)> remove ntfs
Component is queued for removal: ntfs
Version Description
2.00
The components remove command has been
introduced.
3.6.7 components validity-period
Description Set a validity period of a local component list. After this time the command
components list will be automalically executed to get actual list of
components from update server.
Command with no prex resets period to default. By default, value 1800 is
used.
Prex no Yes
Change settings Yes
Multiple input No
Keenetic Lite (KN-1310) — Command Reference Guide
41
Page 42

Chapter 3 Command Reference
Synopsis
Arguments
Example
History
(cong-comp)> validity-period ‹seconds›
(cong-comp)> no validity-period
Integerseconds
(config-comp)> validity-period 500
Core::Configurator: done.
Version Description
2.03
The components validity-period command has been
introduced.
3.7 crypto ike key
Description Add IKE key with remote side ID.
DescriptionValueArgument
Validity period of a local
component list in seconds.
Command with no prex removes specied key.
Prex no Yes
Change settings Yes
Multiple input Yes
Synopsis
Arguments
(cong)> crypto ike key ‹name› ‹psk› ( ‹type› ‹id› | any)
(cong)> no crypto ike key ‹name›
type ID type is IP-address.address
DescriptionValueArgument
Stringname
Name of the key. Latin letters, numbers, dots,
hyphens and underscores are acceptable.
Password for authentication.Stringpsk
ID type is full domain name.fqdn
ID type is domain name.dn
ID type is e-mail address.email
Value of the remote side ID.Stringid
42
Allow the key usage for any remote side.Keywordany
Command Reference Guide — Keenetic Lite (KN-1310)
Page 43

Chapter 3 Command Reference
Example
History
(config)> crypto ike key test 12345678 email ipsec@example.org
IpSec::Manager: Crypto ike key "test" successfully added.
Version Description
The crypto ike key command has been introduced.2.06
3.8 crypto ike nat-keepalive
Description Set the timeout between keepalive packets in case of NAT between the client
and server IPsec. By default, 90 value is set.
Command with no prex resets setting to default.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
(cong)> crypto ike nat-keepalive ‹nat-keepalive›
(cong)> no crypto ike nat-keepalive
Arguments
Example
History
Integernat-keepalive
(config)> crypto ike nat-keepalive 20
IpSec::Manager: Set crypto ike nat-keepalive timeout to 20 s.
Version Description
2.06
The crypto ike nat-keepalive command has been
introduced.
DescriptionValueArgument
Timeout between keepalive
packets in seconds. Can take
values from 5 to 3600 inclusively.
3.9 crypto ike policy
Description Access to a group of commands to congure selected IKE policy. If IKE policy
is not found, the command tries to create it.
Command with no prex removes IKE policy. At the same time references to
this IKE policy are automatically deleted from all IPsec proles.
Prex no Yes
Change settings Yes
Keenetic Lite (KN-1310) — Command Reference Guide
43
Page 44

Chapter 3 Command Reference
Multiple input Yes
Group entry (config-ike-policy)
Synopsis
Arguments
Example
History
(cong)> crypto ike policy ‹name›
(cong)> no crypto ike policy ‹name›
DescriptionValueArgument
Stringname
(config)> crypto ike policy test
IpSec::Manager: Crypto ike policy "test" successfully created.
Version Description
The crypto ike policy command has been introduced.2.06
IKE policy name. Latin letters,
numbers, dots, hyphens and
underscores are acceptable.
3.9.1 crypto ike policy lifetime
Description Set lifetime of IPsec IKE association. By default, the value 86400 is used.
Command with no prex resets setting to default.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
Example
History
(cong-ike-policy)> lifetime ‹lifetime›
(cong-ike-policy)> no lifetime
(config-ike-policy)> lifetime 3600
IpSec::Manager: Crypto ike policy "test" lifetime set to 3600 s.
Version Description
2.06
DescriptionValueArgument
Integerlifetime
The crypto ike policy lifetime command has been
introduced.
Lifetime of IPsec IKE association in
seconds. Can take values from 60
to 2147483647.
44
Command Reference Guide — Keenetic Lite (KN-1310)
Page 45

Chapter 3 Command Reference
3.9.2 crypto ike policy mode
Description Set IKE protocol version. By default, the value ikev1 is used.
Command with no prex resets setting to default.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
Example
History
(cong-ike-policy)> mode ‹mode›
(cong-ike-policy)> no mode
DescriptionValueArgument
mode Protocol version IKEv1.ikev1
Protocol version IKEv2.ikev2
(config-ike-policy)> mode ikev1
IpSec::Manager: Crypto ike policy "test" mode set to "ikev1".
Version Description
2.06
The crypto ike policy mode command has been
introduced.
3.9.3 crypto ike policy negotiation-mode
Description Set exchange mode for IKEv1 (see crypto ike policy mode command). By
default, the value main is used.
Command with no prex resets setting to default.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
Keenetic Lite (KN-1310) — Command Reference Guide
(cong-ike-policy)> negotiation-mode ‹negotiation-mode›
(cong-ike-policy)> no negotiation-mode
negotiation-mode Main mode, protects the identity of the
DescriptionValueArgument
main
peers.
45
Page 46

Chapter 3 Command Reference
aggressive
DescriptionValueArgument
Aggressive mode, does not protect the
identity of the peers.
Example
History
(config-ike-policy)> negotiation-mode aggressive
IpSec::Manager: Crypto ike policy "test" negotiation-mode set ►
to "aggressive".
Version Description
2.06
The crypto ike policy negotiation-mode command has
been introduced.
3.9.4 crypto ike policy proposal
Description Add reference on existing IKE proposal to IKE policy. The order of adding has
a value for data exchange on the IKE protocol.
Command with no prex removes reference on IKE proposal.
Prex no Yes
Change settings Yes
Multiple input Yes
Synopsis
(cong-ike-policy)> proposal ‹proposal›
Arguments
Example
History
(cong-ike-policy)> no proposal ‹proposal›
DescriptionValueArgument
Stringproposal
(config-ike-policy)> proposal test
IpSec::Manager: Crypto ike policy "test" proposal "test" ►
successfully added.
Version Description
2.06
The crypto ike policy proposal command has been
introduced.
IKE proposal name. Latin letters,
numbers, dots, hyphens and
underscores are acceptable.
46
Command Reference Guide — Keenetic Lite (KN-1310)
Page 47

Chapter 3 Command Reference
3.10 crypto ike proposal
Description Access to a group of commands to congure selected IKE proposal. If IKE
proposal is not found, the command tries to create it.
Command with no prex removes IKE proposal. At the same time references
to this IKE proposal are automatically deleted from all IKE policy.
Prex no Yes
Change settings Yes
Multiple input Yes
Group entry (config-ike-proposal)
Synopsis
Arguments
Example
History
(cong)> crypto ike proposal ‹name›
(cong)> no crypto ike proposal ‹name›
DescriptionValueArgument
Stringname
(config)> crypto ike proposal test
IpSec::Manager: Crypto ike proposal "test" successfully created.
Version Description
The crypto ike proposal command has been introduced.2.06
IKE proposal name. Latin letters,
numbers, dots, hyphens and
underscores are acceptable.
3.10.1 crypto ike proposal dh-group
Description Add the selected DH group to IKE proposal to work in the PFS mode. The order
of adding has a value for data exchange on the IKE protocol.
Command with no prex removes the selected group.
Prex no Yes
Change settings Yes
Multiple input Yes
Synopsis
Keenetic Lite (KN-1310) — Command Reference Guide
(cong-ike-proposal)> dh-group ‹dh-group›
(cong-ike-proposal)> no dh-group ‹dh-group›
47
Page 48

Chapter 3 Command Reference
Arguments
Example
History
DescriptionValueArgument
DH group to work in the PFS mode.dh-group 1
2
5
14
15
16
17
18
(config-ike-proposal)> dh-group 14
IpSec::Manager: Crypto ike proposal "test" DH group "14" ►
successfully added.
Version Description
2.06
The crypto ike proposal dh-group command has been
introduced.
3.10.2 crypto ike proposal encryption
Description Add the selected type of encryption to IKE proposal. The order of adding has
a value for data exchange on the IKE protocol.
Command with no prex removes the selected type of encryption.
Prex no Yes
Change settings Yes
Multiple input Yes
Synopsis
Arguments
(cong-ike-proposal)> encryption ‹encryption›
(cong-ike-proposal)> no encryption ‹encryption›
DescriptionValueArgument
Type of IKE encryption.encryption des
3des
aes-128-cbc
aes-192-cbc
48
aes-256-cbc
Command Reference Guide — Keenetic Lite (KN-1310)
Page 49
Chapter 3 Command Reference
Example
History
(config-ike-proposal)> encryption des
IpSec::Manager: Crypto ike proposal "test" encryption algorithm ►
"des" added.
Version Description
2.06
The crypto ike proposal encryption command has been
introduced.
3.10.3 crypto ike proposal integrity
Description Add the selected value of HMAC signature algorithm to IKE proposal. The
order of adding has a value for data exchange on the IKE protocol.
Command with no prex removes the selected algorithm.
Prex no Yes
Change settings Yes
Multiple input Yes
Synopsis
(cong-ike-proposal)> integrity ‹integrity›
Arguments
Example
History
(cong-ike-proposal)> no integrity ‹integrity›
DescriptionValueArgument
integrity md5
sha1
sha256
sha384
sha512
(config-ike-proposal)> integrity sha256
IpSec::Manager: Crypto ike proposal "test" integrity algorithm ►
"sha256" successfully added.
Version Description
2.06
The crypto ike proposal integrity command has been
introduced.
HMAC signature algorithm of IKE
messages.
Keenetic Lite (KN-1310) — Command Reference Guide
49
Page 50
Chapter 3 Command Reference
3.11 crypto ipsec transform-set
Description Access to a group of commands to congure selected IPsec ESP transformation
during Phase 2. If transformation is not found, the command tries to create
it.
Command with no prex removes transformation. At the same time references
to this transformation are automatically deleted from all IPsec crypto maps.
Prex no Yes
Change settings Yes
Multiple input Yes
Group entry (config-ipsec-transform)
Synopsis
Arguments
Example
History
(cong)> crypto ipsec transform-set ‹name›
(cong)> no crypto ipsec transform-set ‹name›
DescriptionValueArgument
Stringname
(config)> crypto ipsec transform-set test
IpSec::Manager: Crypto ipsec transform-set "test" successfully ►
created.
Version Description
2.06
The crypto ipsec transform-set command has been
introduced.
IPsec transformation name. Latin
letters, numbers, dots, hyphens
and underscores are acceptable.
3.11.1 crypto ipsec transform-set cypher
Description Add the selected type of encryption to IPsec transformation. The order of
adding has a value for data exchange on the IKE protocol.
Prex no Yes
Change settings Yes
Multiple input Yes
Synopsis
50
Command with no prex removes the selected type of encryption.
(cong-ipsec-transform)> cypher ‹cypher›
Command Reference Guide — Keenetic Lite (KN-1310)
Page 51
(cong-ipsec-transform)> no cypher ‹cypher›
Chapter 3 Command Reference
Arguments
Example
History
esp-3des
esp-aes-128
esp-aes-192
esp-aes-256
(config-ipsec-transform)> cypher esp-3des
IpSec::Manager: Crypto ipsec transform-set "test" cypher ►
"esp-3des" successfully added.
Version Description
2.06
The crypto ipsec transform-set cypher command has
been introduced.
DescriptionValueArgument
Type of IPsec ESP encryption.cypher esp-des
3.11.2 crypto ipsec transform-set dh-group
Description Add the selected DH group to IPsec transformation to work in the PFS mode.
The order of adding has a value for data exchange on the IKE protocol.
Command with no prex removes the selected group.
Prex no Yes
Change settings Yes
Multiple input Yes
Synopsis
Arguments
(cong-ipsec-transform)> dh-group ‹dh-group›
(cong-ipsec-transform)> no dh-group ‹dh-group›
DescriptionValueArgument
DH group to work in the PFS mode.dh-group 1
2
5
14
15
16
17
Keenetic Lite (KN-1310) — Command Reference Guide
51
Page 52
Chapter 3 Command Reference
DescriptionValueArgument
18
Example
History
(config-ipsec-transform)> dh-group 14
IpSec::Manager: Crypto ipsec transform-set "test" dh-group "14" ►
successfully added.
Version Description
2.06
The crypto ipsec transform-set dh-group command
has been introduced.
3.11.3 crypto ipsec transform-set hmac
Description Add the selected value of HMAC signature algorithm to IPsec transformation.
The order of adding has a value for data exchange on the IKE protocol.
Command with no prex removes the selected algorithm.
Prex no Yes
Change settings Yes
Multiple input Yes
Synopsis
(cong-ipsec-transform)> hmac ‹hmac›
Arguments
Example
History
(cong-ipsec-transform)> no hmac ‹hmac›
DescriptionValueArgument
hmac esp-md5-hmac
esp-sha1-hmac
esp-sha256-hmac
(config-ipsec-transform)> hmac esp-sha1-hmac
IpSec::Manager: Crypto ipsec transform-set "test" hmac ►
"esp-sha1-hmac" successfully added.
Version Description
2.06
The crypto ipsec transform-set hmac command has
been introduced.
HMAC signature algorithm of IPsec ESP
transformation.
52
Command Reference Guide — Keenetic Lite (KN-1310)
Page 53

Chapter 3 Command Reference
3.11.4 crypto ipsec transform-set lifetime
Description Set lifetime of selected IPsec transformation. By default, the value 3600 is
used.
Command with no prex resets setting to default.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
Example
History
(cong-ipsec-transform)> lifetime ‹lifetime›
(cong-ipsec-transform)> no lifetime
Integerlifetime
(config-ipsec-transform)> lifetime 8640
IpSec::Manager: Crypto ipsec transform-set "test" lifetime set ►
to 8640 s.
Version Description
2.06
The crypto ipsec transform-set lifetime command has
been introduced.
3.12 crypto ipsec prole
DescriptionValueArgument
Lifetime of IPsec transformation in
seconds. Can take values from 60
to 2147483647.
Description Access to a group of commands to congure selected IPsec prole. If prole
is not found, the command tries to create it.
Command with no prex removes prole. At the same time references to
this prole are automatically deleted from all IPsec crypto maps.
Prex no Yes
Change settings Yes
Multiple input Yes
Group entry (config-ipsec-profile)
Synopsis
Keenetic Lite (KN-1310) — Command Reference Guide
(cong)> crypto ipsec profile ‹name›
53
Page 54
Chapter 3 Command Reference
(cong)> no crypto ipsec profile ‹name›
Arguments
Example
History
Stringname
(config)> crypto ipsec profile test
IpSec::Manager: Crypto ipsec profile "test" successfully created.
Version Description
The crypto ipsec prole command has been introduced.2.06
DescriptionValueArgument
IPsec prole name. Latin letters,
numbers, dots, hyphens and
underscores are acceptable.
3.12.1 crypto ipsec prole authentication-local
Description Set authentication type for local host. By default, value pre-share is used.
Command with no prex resets setting to default.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
Example
History
(cong-ipsec-prole)> authentication-local ‹auth›
(cong-ipsec-prole)> no authentication-local
DescriptionValueArgument
auth A single available type of authorization for
(config-ipsec-profile)> authentication-local pre-share
IpSec::Manager: Crypto ipsec profile "test" authentication-local ►
type "pre-share" is set.
Version Description
2.06
pre-share
now.
The crypto ipsec prole authentication-local command
has been introduced.
3.12.2 crypto ipsec prole authentication-remote
Description Set authentication type for remote host. By default, value pre-share is used.
54
Command Reference Guide — Keenetic Lite (KN-1310)
Page 55
Command with no prex resets setting to default.
Prex no Yes
Change settings Yes
Multiple input No
Chapter 3 Command Reference
Synopsis
Arguments
Example
History
(cong-ipsec-prole)> authentication-remote ‹auth›
(cong-ipsec-prole)> no authentication-remote
DescriptionValueArgument
auth A single available type of authorization for
(config-ipsec-profile)> authentication-remote pre-share
IpSec::Manager: Crypto ipsec profile "test" authentication-remote ►
type "pre-share" is set.
Version Description
2.06
pre-share
now.
The crypto ipsec prole authentication-remote
command has been introduced.
3.12.3 crypto ipsec prole dpd-interval
Description Set parameters of method to detect a dead IKE peer. By default, interval is
set to 30, retry-count is set to 3.
Command with no prex resets settings to default.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
Keenetic Lite (KN-1310) — Command Reference Guide
(cong-ipsec-prole)> dpd-interval ‹interval› [retry-count]
(cong-ipsec-prole)> no dpd-interval
DescriptionValueArgument
Integerinterval
The interval of sending DPD
packets in seconds. Can take
values from 2 to 3600.
55
Page 56

Chapter 3 Command Reference
DescriptionValueArgument
Integerretry-count
Number of attempts to send DPD
packets. Can take values from 3 to
60.
Example
History
(config-ipsec-profile)> dpd-interval 5 30
IpSec::Manager: crypto ipsec profile "test" dpd-interval is set ►
to 5 s.
IpSec::Manager: crypto ipsec profile "test" dpd retry count is ►
set to 30
Version Description
2.06
The crypto ipsec prole dpd-interval command has
been introduced.
3.12.4 crypto ipsec prole identity-local
Description Set a local identier of IPsec prole.
Command with no prex removes the local identier.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
Example
(cong-ipsec-prole)> identity-local ‹type› ‹id›
(cong-ipsec-prole)> no identity-local
DescriptionValueArgument
type ID type is IP-address.address
ID type is full domain name.fqdn
ID type is domain name.dn
ID type is e-mail address.email
Local ID value.Stringid
(config-ipsec-profile)> identity-local address 10.10.10.5
IpSec::Manager: Crypto ipsec profile "test" identity-local is ►
set to "10.10.10.5" with type "address".
56
Command Reference Guide — Keenetic Lite (KN-1310)
Page 57
Chapter 3 Command Reference
History
Version Description
2.06
The crypto ipsec prole identity-local command has
been introduced.
3.12.5 crypto ipsec prole match-identity-remote
Description Set remote host identier for IPsec prole.
Command with no prex removes remote host ID.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
(cong-ipsec-prole)> match-identity-remote ( ‹type› ‹id› | any)
(cong-ipsec-prole)> no match-identity-remote
DescriptionValueArgument
type ID type is IP-address.address
ID type is full domain name.fqdn
ID type is domain name.dn
ID type is e-mail address.email
Remote host ID value.Stringid
Allow usage of any remote host.Keywordany
Example
History
(config-ipsec-profile)> match-identity-remote any
IpSec::Manager: Crypto ipsec profile "test" match-identity-remote ►
is set to any.
Version Description
2.06
The crypto ipsec prole match-identity-remote
command has been introduced.
3.12.6 crypto ipsec prole mode
Description Set the mode of operation IPsec. By default, tunnel value is set.
Command with no prex resets setting to default.
Prex no Yes
Change settings Yes
Keenetic Lite (KN-1310) — Command Reference Guide
57
Page 58

Chapter 3 Command Reference
Multiple input No
Synopsis
Arguments
Example
History
(cong-ipsec-prole)> mode ‹mode›
(cong-ipsec-prole)> no mode
mode Tunnel mode, when the entire IP packet
(config-ipsec-profile)> mode tunnel
IpSec::Manager: Crypto ipsec profile "test" mode set to "tunnel".
Version Description
2.06
tunnel
transport
The crypto ipsec prole mode command has been
introduced.
3.12.7 crypto ipsec prole policy
DescriptionValueArgument
is encrypted and/or authenticated.
Transport mode, when only the payload
of the IP packet is encrypted and/or
authenticated.
Description Set the reference to existing IKE policy (see crypto ike policy command).
Command with no prex removes the reference.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
Example
(cong-ipsec-prole)> policy ‹policy›
(cong-ipsec-prole)> no policy
DescriptionValueArgument
Stringpolicy
(config-ipsec-profile)> policy test
IpSec::Manager: Crypto ipsec profile "test" policy set to "test".
IKE policy name. You can see the
list of available policies with help
of policy ? command.
58
Command Reference Guide — Keenetic Lite (KN-1310)
Page 59

Chapter 3 Command Reference
History
Version Description
2.06
The crypto ipsec prole policy command has been
introduced.
3.12.8 crypto ipsec prole preshared-key
Description Set pre-shared key for IPsec prole.
Command with no prex removes pre-shared key.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
(cong-ipsec-prole)> preshared-key ‹preshare-key›
(cong-ipsec-prole)> no preshared-key
DescriptionValueArgument
Pre-shared key value.Stringpreshare-key
Example
History
(config-ipsec-profile)> preshared-key testkey
IpSec::Manager: Crypto ipsec profile "test" preshared key was set.
Version Description
2.06
The crypto ipsec prole preshared-key command has
been introduced.
3.12.9 crypto ipsec prole xauth
Description Enable additional authentication XAuth for IKEv1 mode. By default, function
is disabled.
Command with no prex disables additional authentication.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
(cong-ipsec-prole)> xauth ‹type›
(cong-ipsec-prole)> no xauth
Keenetic Lite (KN-1310) — Command Reference Guide
59
Page 60

Chapter 3 Command Reference
Arguments
Example
History
type Client mode.client
(config-ipsec-profile)> xauth client
IpSec::Manager: Crypto ipsec profile "test" xauth set to "client".
Version Description
2.06
The crypto ipsec prole xauth command has been
introduced.
DescriptionValueArgument
Server mode.server
3.12.10 crypto ipsec prole xauth-identity
Description Set login for additional authentication XAuth in client mode.
Command with no prex removes the login.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
Example
History
(cong-ipsec-prole)> xauth-identity ‹identity›
(cong-ipsec-prole)> no xauth-identity
DescriptionValueArgument
Login for XAuth client mode.Stringidentity
(config-ipsec-profile)> xauth-identity ident
IpSec::Manager: Crypto ipsec profile "test" xauth-identity is ►
set to "ident".
Version Description
2.06
The crypto ipsec prole xauth-identity command has
been introduced.
3.12.11 crypto ipsec prole xauth-password
Description Set password for additional authentication XAuth in client mode.
60
Command with no prex removes the password.
Command Reference Guide — Keenetic Lite (KN-1310)
Page 61

Prex no Yes
Change settings Yes
Multiple input No
Chapter 3 Command Reference
Synopsis
Arguments
Example
History
(cong-ipsec-prole)> xauth-password ‹password›
(cong-ipsec-prole)> no xauth-password
DescriptionValueArgument
Password for XAuth client mode.Stringpassword
(config-ipsec-profile)> xauth-password password
IpSec::Manager: Crypto ipsec profile "test" xauth-password is set.
Version Description
2.06
The crypto ipsec prole xauth-password command has
been introduced.
3.13 crypto map
Description Access to a group of commands to congure selected IPsec crypto map. If
crypto map is not found, the command tries to create it.
Command with no prex removes crypto map.
Prex no Yes
Change settings Yes
Multiple input Yes
Group entry (config-crypto-map)
Synopsis
Arguments
Example
(cong)> crypto map ‹name›
(cong)> no crypto map ‹name›
(config)> crypto map test
IpSec::Manager: Crypto map "test" successfully created.
DescriptionValueArgument
Stringname
IPsec crypto map name. Latin
letters, numbers, dots, hyphens
and underscores are acceptable.
Keenetic Lite (KN-1310) — Command Reference Guide
61
Page 62

Chapter 3 Command Reference
History
Version Description
The crypto map command has been introduced.2.06
3.13.1 crypto map connect
Description Enable automatic unconditional IPsec connection to the remote host. Setting
has no meaning if basic remote host was set to any (see crypto map set-peer
command). By default, setting is disabled and connection is established when
attempting to transmit trafc through the IPsec ESP transformation.
Command with no prex disables automatic unconditional connection.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
(cong-crypto-map)> connect
(cong-crypto-map)> no connect
Example
History
(config-crypto-map)> connect
IpSec::Manager: Crypto map "test" autoconnect enabled.
Version Description
The crypto map connect command has been introduced.2.06
3.13.2 crypto map enable
Description Enable selected IPsec crypto map. By default, setting is enabled.
Command with no prex disables crypto map.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
(cong-crypto-map)> enable
(cong-crypto-map)> no enable
Example
62
(config-crypto-map)> enable
IpSec::Manager: Crypto map "test" enabled.
Command Reference Guide — Keenetic Lite (KN-1310)
Page 63

Chapter 3 Command Reference
History
Version Description
The crypto map enable command has been introduced.2.06
3.13.3 crypto map fallback-check-interval
Description Enable periodic checking of basic host availability and return to it in case of
presence basic and backup remote hosts both. By default, setting is disabled.
Command with no prex disables checking.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
(cong-crypto-map)> fallback-check-interval ‹interval-value›
(cong-crypto-map)> no fallback-check-interval
DescriptionValueArgument
Integerinterval-value
Period of checking in seconds. Can
take values from 60 to 86400.
Example
History
(config-crypto-map)> fallback-check-interval 120
IpSec::Manager: Crypto map "test" fallback check interval is set ►
to 120.
Version Description
2.06
The crypto map fallback-check-interval command has
been introduced.
3.13.4 crypto map force-encaps
Description Enforce the ESP packet wrapping mode in UDP to bypass the rewall and NAT.
Command with no prex disables the mode.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
(cong-crypto-map)> force-encaps
(cong-crypto-map)> no force-encaps
Keenetic Lite (KN-1310) — Command Reference Guide
63
Page 64
Chapter 3 Command Reference
Example
History
(config-crypto-map)> force-encaps
IpSec::Manager: "test": crypto map force ESP in UDP encapsulation ►
enabled.
(config-crypto-map)> no force-encaps
IpSec::Manager: "test": crypto map force ESP in UDP encapsulation ►
disabled.
Version Description
2.08
The crypto map force-encaps command has been
introduced.
3.13.5 crypto map match-address
Description Set the reference to existing list of packet ltering rules (see access-list
command). The rst rule in the list will be used for IPsec Phase 2.
Command with no prex removes the reference.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
Example
History
(cong-crypto-map)> match-address ‹access-list›
(cong-crypto-map)> no match-address
(config-crypto-map)> match-address acl1
IpSec::Manager: Crypto map "test" match-address set to "acl1".
Version Description
2.06
3.13.6 crypto map nail-up
DescriptionValueArgument
Stringaccess-list
The crypto map match-address command has been
introduced.
Packet ltering rules list name. You
can see the list of available lists
with help of match-address ?
command.
Description Enable automatic renegotiation of IPsec ESP transformations at their
obsolescence. By default, setting is disabled.
64
Command Reference Guide — Keenetic Lite (KN-1310)
Page 65
Command with no prex disables automatic renegotiation.
Prex no Yes
Change settings Yes
Multiple input No
Chapter 3 Command Reference
Synopsis
Example
History
(cong-crypto-map)> nail-up
(cong-crypto-map)> no nail-up
(config-crypto-map)> nail-up
IpSec::Manager: Crypto map "test" SA renegotiation enabled.
Version Description
The crypto map nail-up command has been introduced.2.06
3.13.7 crypto map set-peer
Description Set basic remote host for IPsec connection.
Command with no prex removes the setting.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
Example
History
Keenetic Lite (KN-1310) — Command Reference Guide
(cong-crypto-map)> set-peer ‹remote-ip›
(cong-crypto-map)> no set-peer
remote-ip IP-address or domain name of remote host.String
(config-crypto-map)> set-peer ipsec.test.com
IpSec::Manager: Crypto map "test" primary remote peer is set to ►
"ipsec.test.com".
Version Description
The crypto map set-peer command has been introduced.2.06
DescriptionValueArgument
Accept any incoming connections.any
65
Page 66
Chapter 3 Command Reference
3.13.8 crypto map set-peer-fallback
Description Set backup remote host for IPsec connection. This setting can be made after
assignment of basic host (see crypto map set-peer command).
Command with no prex removes the setting.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
Example
History
(cong-crypto-map)> set-peer-fallback ‹remote-ip›
(cong-crypto-map)> no set-peer-fallback
DescriptionValueArgument
Stringremote-ip
(config-crypto-map)> set-peer-fallback test.com
IpSec::Manager: Crypto map "test" fallback remote peer is set ►
to "test.com".
Version Description
2.06
The crypto map set-peer-fallback command has been
introduced.
IP-address or domain name of
remote host.
3.13.9 crypto map set-prole
Description Set the reference to existing IPsec prole (see crypto ipsec prole command).
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
66
Command with no prex removes the reference.
(cong-crypto-map)> set-profile ‹profile›
(cong-crypto-map)> no set-profile
Command Reference Guide — Keenetic Lite (KN-1310)
Page 67
Chapter 3 Command Reference
Arguments
Example
History
Stringprofile
(config-crypto-map)> set-profile test
IpSec::Manager: Crypto map "test" ipsec profile is set to "test".
Version Description
2.06
The crypto map set-prole command has been
introduced.
DescriptionValueArgument
IPsec prole name. You can see the
list of available proles with help
of set-prole ? command.
3.13.10 crypto map set-tcpmss
Description Set the limit on the segment size of outgoing TCP sessions within IPsec tunnel.
If the MSS value, which is transmitted in the header of SYN-packets, exceeds
the specied limit, command changes it. Path MTU Discovery mode allows
automatically identiy MSS limit.
Command with no prex removes all limits from MSS.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
Example
History
(cong-crypto-map)> set-tcpmss ‹mss-value›
(cong-crypto-map)> no set-tcpmss
mss-value MSS upper limit. Can take values from 576 to
(config-crypto-map)> set-tcpmss 1280
IpSec::Manager: Crypto map "test" tcpmss set to 1280.
Version Description
2.06
DescriptionValueArgument
Integer
1500.
Enable Path MTU Discovery mode.pmtu
The crypto map set-tcpmss command has been
introduced.
Keenetic Lite (KN-1310) — Command Reference Guide
67
Page 68
Chapter 3 Command Reference
3.13.11 crypto map set-transform
Description Set the reference to existing IPsec ESP transformation (see crypto ipsec
transform-set command).
Command with no prex removes the reference.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
Example
History
(cong-crypto-map)> set-transform ‹transform-set›
(cong-crypto-map)> no set-transform
DescriptionValueArgument
Stringtransform-set
(config-crypto-map)> set-transform test
IpSec::Manager: Crypto map "test" ipsec transform-set is set to ►
"test".
Version Description
2.06
The crypto map set-transform command has been
introduced.
IPsec transformation name. You
can see the list of available
transformations with help of
transform-set ? command.
3.13.12 crypto map virtual-ip dns-server
Description Set DNS-server issued to clients in Virtual IP server mode.
Command with no prex deletes the address.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
68
(cong-crypto-map)> virtual-ip dns-server ‹address›
(cong-crypto-map)> no virtual-ip dns-server
Command Reference Guide — Keenetic Lite (KN-1310)
Page 69

Chapter 3 Command Reference
Arguments
Example
History
(config-crypto-map)> virtual-ip dns-server 10.5.5.5
IpSec::Manager: crypto map "test" Virtual IP DNS server set to ►
"10.5.5.5".
(config-crypto-map)> no virtual-ip dns-server
IpSec::Manager: crypto map "test" Virtual IP DNS server deleted.
Version Description
2.08
The crypto map virtual-ip dns-server command has
been introduced.
DescriptionValueArgument
IP-address of DNS-server.IP-addressaddress
3.13.13 crypto map virtual-ip enable
Description Enable Virtual IP server mode, when clients receive addresses from a given
range. The value of a remote subnet, specied in the corresponding access-list,
will be ignored. By default, the setting is disabled.
Command with no prex disables the setting.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Example
History
(cong-crypto-map)> virtual-ip enable
(cong-crypto-map)> no virtual-ip enable
(config-crypto-map)> virtual-ip enable
IpSec::Manager: crypto map "test" Virtual IP mode enabled.
(config-crypto-map)> no virtual-ip enable
IpSec::Manager: Crypto map "test" Virtual IP mode disabled.
Version Description
2.08
The crypto map virtual-ip enable command has been
introduced.
3.13.14 crypto map virtual-ip nat
Description Enable translation for remote network of Virtual IP extension server.
Command with no prex removes the rule.
Keenetic Lite (KN-1310) — Command Reference Guide
69
Page 70
Chapter 3 Command Reference
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Example
History
(cong-crypto-map)> virtual-ip nat
(cong-crypto-map)> no virtual-ip nat
(config-crypto-map)> virtual-ip nat
IpSec::Manager: crypto map "test" Virtual IP NAT rule enabled.
(config-crypto-map)> no virtual-ip nat
IpSec::Manager: Crypto map "test" Virtual IP NAT rule disabled.
Version Description
2.08
The crypto map virtual-ip nat command has been
introduced.
3.13.15 crypto map virtual-ip range
Description Congure the range of addresses issued to clients in Virtual IP server mode.
Command with no prex removes the range.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
Example
(cong-crypto-map)> virtual-ip range ‹begin› ( ‹end› | ‹size› )
(cong-crypto-map)> no virtual-ip range
(config-crypto-map)> virtual-ip range 10.5.0.0 20
IpSec::Manager: Crypto map "test" Virtual IP pool range set from ►
"10.5.0.0" to "10.5.0.20".
(config-crypto-map)> no virtual-ip range
IpSec::Manager: Crypto map "test" Virtual IP pool range deleted.
DescriptionValueArgument
The beginning of the address range.IP-addressbegin
The end of the address range.IP-addressend
Address range size.Integersize
70
Command Reference Guide — Keenetic Lite (KN-1310)
Page 71
Chapter 3 Command Reference
History
Version Description
2.08
The crypto map virtual-ip range command has been
introduced.
3.14 dns-proxy
Description Access to a group of commands to manage DNS proxy service.
Prex no No
Change settings No
Multiple input No
Group entry (config-dnspx)
Synopsis
History
(cong)> dns-proxy
Version Description
The dns-proxy command has been introduced.2.04
3.14.1 dns-proxy bantime
Description Set bantime for DNS server. By default, 30000 value is used.
Command with no prex resets bantime to default.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
Example
(cong-dnspx)> bantime ‹bantime›
(cong-dnspx)> no bantime
DescriptionValueArgument
Integerbantime
(config-dnspx)>bantime 25
Dns::Proxy: Dns-proxy set 25 msec. bantime.
(config-dnspx)>no bantime
Dns::Proxy: Dns-proxy bantime reset.
The bantime value in milliseconds.
Can take values from 1 to 30000.
Keenetic Lite (KN-1310) — Command Reference Guide
71
Page 72
Chapter 3 Command Reference
History
Version Description
The dns-proxy bantime command has been introduced.2.04
3.14.2 dns-proxy max-ttl
Description Set maximum TTL for DNS proxy cached entries.
Command with no prex removes maximum TTL value.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
(cong-dnspx)> max-ttl ‹max-ttl›
(cong-dnspx)> no max-ttl
Integermax-ttl
DescriptionValueArgument
The maximum value of TTL. Can
take values from 1 to 604800000
milliseconds (1 week).
Example
History
(config-dnspx)>max-ttl 10000
Dns::Proxy: Dns-proxy set max-ttl to 10000.
(config-dnspx)>no max-ttl
Dns::Proxy: Dns-proxy max-ttl cleared.
Version Description
The dns-proxy max-ttl command has been introduced.2.05
3.14.3 dns-proxy proceed
Description Set interval between concurrent requests, which is sent by DNS proxy to
multiple DNS servers. By default, 500 value is used.
Command with no prex resets proceed to default.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
(cong-dnspx)> proceed ‹proceed›
72
Command Reference Guide — Keenetic Lite (KN-1310)
Page 73
(cong-dnspx)> no proceed
Chapter 3 Command Reference
Arguments
Example
History
Integerproceed
(config-dnspx)>proceed 600
Dns::Proxy: Dns-proxy set 600 msec. proceed.
(config-dnspx)>no proceed
Dns::Proxy: Dns-proxy proceed timeout reset.
Version Description
The dns-proxy proceed command has been introduced.2.04
DescriptionValueArgument
The value of DNS proxy proceed in
milliseconds. Can take values from
1 to 50000.
3.14.4 dns-proxy threshold
Description Set number of consequent failed requests to ban DNS server. By default, 3
value is used.
All DNS servers can not be banned.
Command with no prex resets threshold to default.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
Example
History
(cong-dnspx)> threshold ‹threshold›
(cong-dnspx)> no threshold
(config-dnspx)>threshold 5
Dns::Proxy: Dns-proxy set 5 threshold.
(config-dnspx)>no threshold
Dns::Proxy: Dns-proxy threshold cleared.
Version Description
DescriptionValueArgument
Integerthreshold
The dns-proxy threshold command has been introduced.2.04
The value of DNS proxy threshold.
Can take values from 1 to 10.
Keenetic Lite (KN-1310) — Command Reference Guide
73
Page 74

Chapter 3 Command Reference
3.15 dyndns prole
Description Access to a group of commands to congure DynDns prole. If the prole is
not found, the command tries to create it. You can enter up to 32 proles.
Command with no prex removes DynDns prole.
Prex no Yes
Change settings Yes
Multiple input Yes
Group entry (config-dyndns)
Synopsis
Arguments
History
(cong)> dyndns profile ‹name›
(cong)> no dyndns profile ‹name›
Stringname
Version Description
The dyndns prole command has been introduced.2.00
DescriptionValueArgument
The prole name. Maximum name length
is 64 characters.
3.15.1 dyndns prole domain
Description Assign permanent domain name to the computer. You need to register this
domain name on the site dyndns.com1or no-ip.com2before execution.
Command with no prex removes the setting.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
1
http:\\www.dyndns.com
2
http:\\www.no-ip.com
74
(cong-dyndns)> domain ‹name›
(cong-dyndns)> no domain
DescriptionValueArgument
Stringdomain
Command Reference Guide — Keenetic Lite (KN-1310)
The domain name. Maximum domain
name length is 254 characters.
Page 75

Chapter 3 Command Reference
Example
History
(config-dyndns)> domain systems
DynDns::Profile: "test": domain saved.
Version Description
2.00
The dyndns prole domain command has been
introduced.
3.15.2 dyndns prole password
Description Set password for access via DynDns.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
(cong-dyndns)> password ‹password›
(cong-dyndns)> no password
Arguments
Example
History
Stringpassword
(config-dyndns)> password 1234
DynDns::Profile: "test": password saved.
Version Description
2.00
The dyndns prole password command has been
introduced.
DescriptionValueArgument
The password for authentication.
Maximum password length is 64
characters.
3.15.3 dyndns prole send-address
Description Enable the necessity of connection IP-address indication in DynDns request.
Command with no prex removes the setting.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Keenetic Lite (KN-1310) — Command Reference Guide
(cong-dyndns)> send-address
75
Page 76

Chapter 3 Command Reference
(cong-dyndns)> no send-address
Example
History
(config-dyndns)> send-address
DynDns::Profile: a send address enabled.
Version Description
2.03
The dyndns prole send-address command has been
introduced.
3.15.4 dyndns prole type
Description Set DynDns type depending on the site where the domain name was
registered.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
(cong-dyndns)> type ‹type›
(cong-dyndns)> no type
Arguments
Example
History
3
http:\\www.dyndns.com
4
http:\\www.no-ip.com
5
http:\\www.dns-master.ru
DescriptionValueArgument
type Used if the domain name was registered
dyndns
on the dyndns.com3site.
noip
Used if the domain name was registered
on the no-ip.com4site.
rucenter
Used if the domain name was registered
on the rucenter5site.
custom
Used if the domain name was registered
on the other site (dened with dyndns
prole url command).
(config-dyndns)> type dyndns
DynDns::Profile: "test": type saved.
Version Description
The dyndns prole type command has been introduced.2.00
76
Command Reference Guide — Keenetic Lite (KN-1310)
Page 77

3.15.5 dyndns prole update-interval
Description Set the address update interval for DynDns.
Command with no prex cancels the ability to update.
Prex no Yes
Change settings Yes
Multiple input No
Chapter 3 Command Reference
Synopsis
Arguments
Example
History
(cong-dyndns)> update-interval ‹days› days [ ‹hours› hours ]
[ ‹minutes› minutes ] [ ‹seconds› seconds ]
(cong-dyndns)> no update-interval
DescriptionValueArgument
Interval time in days.Integerdays
Interval time in hours.Integerhours
Interval time in minutes.Integerminutes
Interval time in seconds.Integerseconds
(config-dyndns)> update-interval 7 days
DynDns::Profile: a timeout set to 604800.
Version Description
2.03
The dyndns prole update-interval command has been
introduced.
3.15.6 dyndns prole url
Description Set dynamic DNS service custom URL.
Prex no Yes
Change settings Yes
Multiple input Yes
Synopsis
Arguments
Keenetic Lite (KN-1310) — Command Reference Guide
(cong-dyndns)> url ‹url›
(cong-dyndns)> no url
DescriptionValueArgument
Custom URL of DNS service.Stringurl
77
Page 78

Chapter 3 Command Reference
Example
History
(config-dyndns)> url http://members.dyndns.org/nic/update
DynDns::Profile: "test": url saved.
Version Description
The dyndns prole url command has been introduced.2.05
3.15.7 dyndns prole username
Description Set username for access via DynDns.
Prex no Yes
Change settings Yes
Multiple input Yes
Synopsis
Arguments
(cong-dyndns)> username ‹username›
(cong-dyndns)> no username
DescriptionValueArgument
Stringusername
Username for authentication. Maximum
name length is 64 characters.
Example
History
(config-dyndns)> username test_user
DynDns::Profile: "test": username saved.
Version Description
2.00
The dyndns prole username command has been
introduced.
3.16 interface
Description Access to a group of commands to congure the selected interface. If the
interface is not found, the command tries to create it.
The interface name species its class that inherits certain properties, see the
diagrams in the Appendix. The commands work in relation to classes. The
corresponding interface class is specied in the command description.
Command with no prex deletes the interface.
Prex no Yes
Change settings Yes
Multiple input Yes
78
Command Reference Guide — Keenetic Lite (KN-1310)
Page 79

Group entry (config-if)
Chapter 3 Command Reference
Synopsis
Arguments
History
(cong)> interface ‹name›
(cong)> no interface ‹name›
name
Version Description
Interface
name
The interface command has been introduced.2.00
DescriptionValueArgument
Full interface name or an alias. You can see
the list of available interfaces with help of
interface ? command.
3.16.1 interface authentication chap
Description Enable CHAP authentication support.
Command with no prex disables CHAP.
Prex no Yes
Change settings Yes
Multiple input No
Interface type Secure
Synopsis
Example
History
(cong-if)> authentication chap
(cong-if)> no authentication chap
(config-if)> authentication chap
CHAP authentication enabled.
Version Description
2.00
The interface authentication chap command has been
introduced.
3.16.2 interface authentication eap-md5
Description Enable EAP-MD5 authentication support.
Command with no prex disables EAP-MD5.
Prex no Yes
Keenetic Lite (KN-1310) — Command Reference Guide
79
Page 80
Chapter 3 Command Reference
Change settings Yes
Multiple input No
Interface type Secure
Synopsis
Example
History
(cong-if)> authentication eap-md5
(cong-if)> no authentication eap-md5
(config-if)> authentication eap-md5
EAP-MD5 authentication enabled.
Version Description
2.00
The interface authentication eap-md5 command has
been introduced.
3.16.3 interface authentication eap-ttls
Description Enable EAP-TTLS authentication support.
Command with no prex disables EAP-TTLS.
Prex no Yes
Change settings Yes
Multiple input No
Interface type Secure
Synopsis
Example
History
(cong-if)> authentication eap-ttls
(cong-if)> no authentication eap-ttls
(config-if)> authentication eap-ttls
EAP-TTLS authentication enabled.
Version Description
2.00
The interface authentication eap-ttls command has
been introduced.
3.16.4 interface authentication identity
Description Specify user name for device authentication on the remote system. Equally
often used on PPTP, PPPoE and L2TP connections.
Command with no prex deletes the previously specied user name.
80
Command Reference Guide — Keenetic Lite (KN-1310)
Page 81
Prex no Yes
Change settings Yes
Multiple input No
Interface type Secure
Chapter 3 Command Reference
Synopsis
Arguments
Example
History
(cong-if)> authentication identity ‹identity›
(cong-if)> no authentication identity
DescriptionValueArgument
User name for authentication.Stringidentity
(config-if)> authentication identity test
Identity saved.
Version Description
2.00
The interface authentication identity command has
been introduced.
3.16.5 interface authentication mschap
Description Enable MS-CHAP authentication support.
Command with no prex disables MS-CHAP.
Prex no Yes
Change settings Yes
Multiple input No
Interface type Secure
Synopsis
Example
History
Keenetic Lite (KN-1310) — Command Reference Guide
(cong-if)> authentication mschap
(cong-if)> no authentication mschap
(config-if)> authentication mschap
MSCHAP authentication enabled.
Version Description
2.00
The interface authentication mschap command has
been introduced.
81
Page 82

Chapter 3 Command Reference
3.16.6 interface authentication mschap-v2
Description Enable MS-CHAPv2 authentication support.
Command with no prex disables MS-CHAPv2.
Prex no Yes
Change settings Yes
Multiple input No
Interface type Secure
Synopsis
Example
History
(cong-if)> authentication mschap-v2
(cong-if)> no authentication mschap-v2
(config-if)> authentication mschap-v2
MSCHAPv2 authentication enabled.
Version Description
2.00
The interface authentication mschap-v2 command has
been introduced.
3.16.7 interface authentication pap
Description Enable PAP authentication support.
Command with no prex disables PAP.
Prex no Yes
Change settings Yes
Multiple input No
Interface type Secure
Synopsis
Example
History
(config-if)> authentication pap
PAP authentication enabled.
Version Description
2.00
82
(cong-if)> authentication pap
(cong-if)> no authentication pap
The interface authentication pap command has been
introduced.
Command Reference Guide — Keenetic Lite (KN-1310)
Page 83
Chapter 3 Command Reference
3.16.8 interface authentication password
Description Specify password for device authentication on the remote system. Equally
often used on PPTP, PPPoE and L2TP connections.
Command with no prex deletes the password.
Prex no Yes
Change settings Yes
Multiple input No
Interface type Secure
Synopsis
Arguments
Example
History
(cong-if)> authentication password ‹password›
(cong-if)> no authentication password
DescriptionValueArgument
Password for authentication.Stringpassword
(config-if)> authentication password 1234
Password saved.
Version Description
2.00
The interface authentication password command has
been introduced.
3.16.9 interface authentication shared
Description Enable authentication with a shared key. This mode is used only in conjunction
with WEP encryption. Shared keys are specied by interface encryption key
command.
Command with no prex turns authentication to open mode.
Prex no Yes
Change settings Yes
Multiple input No
Interface type WiFi
Synopsis
Keenetic Lite (KN-1310) — Command Reference Guide
(cong-if)> authentication shared
(cong-if)> no authentication shared
83
Page 84
Chapter 3 Command Reference
Example
History
(config-if)> authentication shared
Shared authentication enabled.
Version Description
2.00
The interface authentication shared command has
been introduced.
3.16.10 interface authentication wpa-psk
Description Specify the pre-agreed key for authentication via WPA-PSK protocol. It is
possible to specify the key as a 256-bit hexadecimal number or as a string of
ASCII-characters. In the second case, the string is used as a code phrase to
generate the key (passphrase).
Command with no prex removes setting.
Prex no Yes
Change settings Yes
Multiple input No
Interface type WiFi
Synopsis
Arguments
Example
History
(cong-if)> authentication wpa-psk ‹psk›
(cong-if)> no authentication wpa-psk
Stringpsk
(config-if)> authentication wpa-psk 12345678
Pre-shared key saved.
Version Description
2.00
The interface authentication wpa-psk command has
been introduced.
3.16.11 interface bandwidth-limit
DescriptionValueArgument
Pre-agreed key in the form of a 256-bit
hexadecimal number, which consists of
64 hexadecimal digits, or in the form of
ASCII string of 8 to 63 characters length.
Description Set tariff speed of Internet connection for the interface. It is used to determine
the bandwidth usage in the trafc analysis (see service ntce command).
Command with no prex removes setting.
84
Command Reference Guide — Keenetic Lite (KN-1310)
Page 85

Prex no Yes
Change settings Yes
Multiple input No
Chapter 3 Command Reference
Synopsis
Arguments
Example
History
(cong-if)> bandwidth-limit ‹limit›
(cong-if)> no bandwidth-limit
DescriptionValueArgument
The value of the tariff speed in Kbps.Integerlimit
(config-if)> bandwidth-limit 50000
Ntce::BandwidthLimits: Set bandwidth limit 50000 Kbps to ISP.
Version Description
2.06
The interface bandwidth-limit command has been
introduced.
3.16.12 interface ccp
Description Enable CCP support during establishing connection.
Command with no prex disables CCP.
Prex no Yes
Change settings Yes
Multiple input No
Interface type PPP
Synopsis
Example
History
(cong-if)> ccp
(cong-if)> no ccp
(config-if)> ccp
CCP enabled.
Version Description
The interface ccp command has been introduced.2.00
Keenetic Lite (KN-1310) — Command Reference Guide
85
Page 86
Chapter 3 Command Reference
3.16.13 interface channel
Description Set the radio channel (broadcasting frequency band) for wireless interfaces.
Wi-Fi interfaces take integers from 1 to 14 (frequency range from 2.412 GHz
to 2.484 GHz). By default, auto value is used.
Command with no prex resets to default.
Prex no Yes
Change settings Yes
Multiple input No
Interface type Radio
Synopsis
Arguments
Example
History
(cong-if)> channel ‹channel›
(cong-if)> no channel
channel Number of radio channel.number
auto
(config-if)> channel 8
Channel saved.
Version Description
The interface channel command has been introduced.2.00
DescriptionValueArgument
Radio channel number is detected
automatically.
3.16.14 interface channel auto-rescan
Description Set a schedule for radio channel automatic scanning. By default, the setting
is disabled.
Command with no prex disables the setting.
Prex no Yes
Change settings Yes
Multiple input No
Interface type Radio
Synopsis
86
(cong-if)> channel auto-rescan ‹hh›:‹mm› interval ‹interval›
Command Reference Guide — Keenetic Lite (KN-1310)
Page 87
(cong-if)> no channel auto-rescan
Chapter 3 Command Reference
Arguments
Example
History
12
24
(config-if)> channel auto-rescan 03:00 interval 12
Network::Interface::Rtx::WifiMaster: Scheduled auto rescan, ►
interval 12 hours.
Version Description
2.07
The interface channel auto-rescan command has been
introduced.
DescriptionValueArgument
Rescan interval in hours.interval 6
3.16.15 interface channel width
Description Set the bandwidth for a specied channel. By default, 40-below value is used.
Command with no prex resets to default.
Prex no Yes
Change settings Yes
Multiple input No
Interface type Radio
Synopsis
Arguments
Example
(cong-if)> channel width ‹width›
(cong-if)> no channel width
width Set bandwidth equal to 20 MHz.20
(config-if)> channel width 20
Network::Interface::Rtx::WifiMaster: a channel bandwidth setting ►
applied.
40-above
40-below
DescriptionValueArgument
Expand the bandwidth up to 40 MHz using
next channel.
Expand the bandwidth up to 40 MHz using
previous channel.
Keenetic Lite (KN-1310) — Command Reference Guide
87
Page 88
Chapter 3 Command Reference
History
Version Description
2.04
The interface channel width command has been
introduced.
3.16.16 interface compatibility
Description Set the standard for wireless communications, with which a given wireless
adapter (the interface) must be compatible. For Wi-Fi interfaces, the
compatibility is set by string of Latin letters B, G, N, that denote extentions
to the standard IEEE 802.11. For example, the presence 'N' in the compability
line will imply that the given adapter will be able to deal with the
802.11n-compatible devices via radio channel. The set of admissible
compatibility lines is dened by the hardware capabilities of a particular
adapter and provisions of the relevant additions to the IEEE 802.11 standard.
By default, “BGN” value is used for 2.4 GHz.
Prex no No
Change settings Yes
Multiple input No
Interface type Radio
Synopsis
Arguments
Example
History
(cong-if)> compatibility ‹annex›
DescriptionValueArgument
annex For 2,4 GHz.B, G, N
(config-if)> compatibility GN
Compatibility set.
Version Description
2.00
The interface compatibility command has been
introduced.
3.16.17 interface connect
Description Start the process of connecting to a remote node.
Command with no prex terminates the connection.
Prex no Yes
Change settings Yes
Multiple input No
88
Command Reference Guide — Keenetic Lite (KN-1310)
Page 89
Interface type PPP, IP
Chapter 3 Command Reference
Synopsis
Arguments
Example
History
(cong-if)> connect [ via ‹interface› ]
(cong-if)> no connect
DescriptionValueArgument
via
(config-if)> connect via UsbModem3
PPP connection enabled.
Version Description
Interface
name
The interface connect command has been introduced.2.00
Interface through which remote node is
accessed. For PPPoE this option is
mandatory.
3.16.18 interface country-code
Description Assign to the interface a literal country code, which inuences the set of radio
channels. By default, RU value is used.
Prex no No
Change settings Yes
Multiple input No
Interface type Radio
Synopsis
Arguments
Example
History
(cong-if)> country-code ‹code›
(config-if)> country-code RU
Country code set.
Version Description
2.00
DescriptionValueArgument
The country code.Stringcode
The interface country-code command has been
introduced.
Keenetic Lite (KN-1310) — Command Reference Guide
89
Page 90

Chapter 3 Command Reference
3.16.19 interface debug
Description Enable debug mode of PPP connection. Detailed info about connection
progress is saved to the system log. By default, setting is disabled.
Command with no prex disables the debug mode.
Prex no Yes
Change settings Yes
Multiple input No
Interface type PPP
Synopsis
Example
History
(cong-if)> debug
(cong-if)> no debug
(config-if)> debug
Debug enabled.
Version Description
The interface debug command has been introduced.2.00
3.16.20 interface description
Description Assign arbitrary descrption to the specied network interface.
Command with no prex deletes the description.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Arguments
Example
90
(cong-if)> description ‹description›
(cong-if)> no description
DescriptionValueArgument
Arbitrary description of the interface.Stringdescription
(config-if)> description 111_2222_33333
Interface description saved.
Command Reference Guide — Keenetic Lite (KN-1310)
Page 91
Chapter 3 Command Reference
History
Version Description
2.00
The interface description command has been
introduced.
3.16.21 interface down
Description Disable the network interface and persist the state “down” to the settings.
Command with no prex enables the network interface and deletes “down”
from settings.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
Example
(cong-if)> down
(cong-if)> no down
(config-if)> down
Interface disabled.
History
Version Description
The interface down command has been introduced.2.00
3.16.22 interface duplex
Description Set the duplex mode of the Ethernet port. By default, auto value is set.
Command with no prex resets setting to default.
Prex no Yes
Change settings Yes
Multiple input No
Interface type Ethernet
Synopsis
Arguments
(cong-if)> duplex ‹mode›
(cong-if)> no duplex
DescriptionValueArgument
mode Full duplex mode.full
Keenetic Lite (KN-1310) — Command Reference Guide
91
Page 92
Chapter 3 Command Reference
DescriptionValueArgument
Half duplex mode.half
Auto duplex mode.auto
Example
History
(config-if)> duplex full
Network::Interface::Ethernet: Duplex set to "full".
Version Description
The interface duplex command has been introduced.2.06.B.1
3.16.23 interface dyndns prole
Description Assign the DynDns prole to the interface. Prole must be created and
customized with dyndns prole commands before execution.
Command with no prex unbinds the prole.
Prex no Yes
Change settings Yes
Multiple input No
Synopsis
(cong-if)> dyndns profile ‹profile›
(cong-if)> no dyndns profile
Arguments
Example
History
(config-if)> dyndns profile test
Core::Configurator: done.
Version Description
2.02
The interface dyndns prole command has been
introduced.
DescriptionValueArgument
The name of DynDns prole.Stringprofile
3.16.24 interface dyndns update
Description Update IP-address for DynDns manually. By default command works in
accordance with the policy of the DynDns service provider, that is not allows
to update too often. Using the keyword force allows you to update excluding
policy of the service provider.
92
Command Reference Guide — Keenetic Lite (KN-1310)
Page 93

Prex no No
Change settings Yes
Multiple input No
Chapter 3 Command Reference
Synopsis
Arguments
Example
History
(cong-if)> dyndns update [ force ]
DescriptionValueArgument
Keywordforce
(config-if)> dyndns update
DynDns::Profile: "test" update started.
Version Description
2.00
The interface dyndns update command has been
introduced.
Not take into account the update rate
recommended by service provider.
3.16.25 interface encryption disable
Description Disable encryption on the wireless interface.
Prex no No
Change settings Yes
Multiple input No
Interface type WiFi
Synopsis
Example
History
(cong-if)> encryption disable
(config-if)> encryption disable
wireless encryption disabled
Version Description
2.00
The interface encryption disable command has been
introduced.
3.16.26 interface encryption enable
Description Enable encryption on the wireless interface. By default, WEP encryption is
used.
Command with no prex disables wireless interface encryption.
Keenetic Lite (KN-1310) — Command Reference Guide
93
Page 94

Chapter 3 Command Reference
Prex no Yes
Change settings Yes
Multiple input No
Interface type WiFi
Synopsis
Example
History
(cong-if)> encryption enable
(cong-if)> no encryption enable
(config-if)> encryption enable
wireless encryption enabled
Version Description
2.00
The interface encryption enable command has been
introduced.
3.16.27 interface encryption key
Description Specify the WEP encryption keys. Depending on the bit, the key can be
standard 64-bit WEP uses a 40 bit key (also known as WEP-40), or 128-bit WEP
uses a 26 hexadecimal characters (13 characters ASCII). Overall, there can be
1 to 4 encryption keys, with one of them default key must be assigned.
Command with no prex removes key.
Prex no Yes
Change settings Yes
Multiple input Yes
Interface type WiFi
Synopsis
Arguments
94
(cong-if)> encryption key ‹id› ( ‹value› [default] | default)
(cong-if)> no encryption key ‹id›
DescriptionValueArgument
Integerid
Stringvalue
Keyworddefault
Command Reference Guide — Keenetic Lite (KN-1310)
The key number. Overall, up to 4 keys
could be specied.
The key value as a hexadecimal number,
consisting of 10 or 26 digits.
Indicates that this key will be used by
default.
Page 95

Chapter 3 Command Reference
Example
History
(config-if)> encryption key 1 1231231234
Encryption key saved.
Version Description
2.00
The interface encryption key command has been
introduced.
3.16.28 interface encryption mppe
Description Enable MPPE encryption support.
Command with no prex disables MPPE encryption.
Prex no Yes
Change settings Yes
Multiple input No
Interface type PPTP
Synopsis
(cong-if)> encryption mppe
(cong-if)> no encryption mppe
Example
History
(config-if)> encryption mppe
MPPE enabled.
Version Description
2.00
The interface encryption mppe command has been
introduced.
3.16.29 interface encryption wpa
Description Enable WPA security algorithms on the wireless interface. Wireless interface
can support the joint use of WPA and WPA2, but supporting WEP automatically
disables when any of the WPA is enabled.
Command with no prex disables WPA support.
Prex no Yes
Change settings Yes
Multiple input No
Interface type WiFi
Keenetic Lite (KN-1310) — Command Reference Guide
95
Page 96
Chapter 3 Command Reference
Synopsis
Example
History
(cong-if)> encryption wpa
(cong-if)> no encryption wpa
(config-if)> encryption wpa
WPA algorithms enabled.
Version Description
2.00
The interface encryption wpa command has been
introduced.
3.16.30 interface encryption wpa2
Description Enable WPA2 (IEEE 802.11i, RSN) security algorithms on the wireless interface.
Wireless interface can support the joint use of WPA and WPA2, but supporting
WEP automatically disables when any of the WPA is enabled.
Command with no prex disables WPA2 support.
Prex no Yes
Change settings Yes
Multiple input No
Interface type WiFi
Synopsis
Example
History
(cong-if)> encryption wpa2
(cong-if)> no encryption wpa2
(config-if)> encryption wpa2
WPA2 algorithms enabled.
Version Description
2.00
The interface encryption wpa2 command has been
introduced.
3.16.31 interface owcontrol
Description Congure Ethernet ow control Tx/Rx. By default, the feature is enabled.
Command with no prex disables the feature.
Prex no Yes
Change settings Yes
96
Command Reference Guide — Keenetic Lite (KN-1310)
Page 97

Multiple input No
Interface type Ethernet
Chapter 3 Command Reference
Synopsis
Arguments
Example
History
(cong-if)> flowcontrol on
(cong-if)> no flowcontrol [send]
(config-if)> flowcontrol on
Network::Interface::Ethernet: "GigabitEthernet0/0": flow control ►
enabled.
(config-if)> no flowcontrol send
Network::Interface::Ethernet: "GigabitEthernet0/0": flow control ►
send disabled.
Version Description
2.08
3.16.32 interface hide-ssid
DescriptionValueArgument
Flow control works asynchronously.Keywordsend
The interface owcontrol command has been
introduced.
Description Enable hidden SSID mode. When using this feature, Access Point will not be
displayed in the list of available wireless networks. But if user informed of
the existence of this network and know its SSID, than he can connect to it.
The mode is disabled by default.
Command with no prex disables the mode.
Prex no Yes
Change settings Yes
Multiple input No
Interface type Access Point
Synopsis
Example
(cong-if)> hide-ssid
(cong-if)> no hide-ssid
(config-if)> hide-ssid
SSID broadcasting disabled.
Keenetic Lite (KN-1310) — Command Reference Guide
97
Page 98
Chapter 3 Command Reference
History
Version Description
The interface hide-ssid command has been introduced.2.00
3.16.33 interface igmp downstream
Description Enable IGMP mode on the interface in the direction of the multicast recipients.
service igmp-proxy must be enabled on the device. There can be several
downstream interfaces.
Command with no prex disables the mode.
Prex no Yes
Change settings Yes
Multiple input No
Interface type IP
Synopsis
(cong-if)> igmp downstream
(cong-if)> no igmp downstream
Example
History
(config-if)> igmp downstream
added downstream interface ISP.
Version Description
2.00
The interface igmp downstream command has been
introduced.
3.16.34 interface igmp fork
Description Enable the duplication of outgoing packets IGMPupstream to the specied
interface. There can be only one fork interface.
Command with no prex disables the mode.
Prex no Yes
Change settings Yes
Multiple input No
Interface type IP
Synopsis
98
(cong-if)> igmp fork
(cong-if)> no igmp fork
Command Reference Guide — Keenetic Lite (KN-1310)
Page 99
Chapter 3 Command Reference
Example
History
(config-if)> igmp fork
fork role assigned to ISP.
Version Description
The interface igmp fork command has been introduced.2.00
3.16.35 interface igmp upstream
Description Enable IGMP mode on the interface in the direction of the multicast source.
service igmp-proxy must be enabled on the device. Only one upstream
interface is allowed.
Command with no prex disables the mode.
Prex no Yes
Change settings Yes
Multiple input No
Interface type IP
Synopsis
Example
History
(cong-if)> igmp upstream
(cong-if)> no igmp upstream
(config-if)> igmp upstream
upstream role assigned to ISP.
Version Description
2.00
The interface igmp upstream command has been
introduced.
3.16.36 interface include
Description Specify Ethernet-interface name which will be added to the software bridge
as a port.
Command with no prex removes the interface from the bridge.
Prex no Yes
Change settings Yes
Multiple input Yes
Interface type Bridge
Keenetic Lite (KN-1310) — Command Reference Guide
99
Page 100
Chapter 3 Command Reference
Synopsis
Arguments
Example
History
(cong-if)> include ‹interface›
(cong-if)> no include ‹interface›
DescriptionValueArgument
interface
(config-if)> include WifiStation0
Interface acquired.
Version Description
Interface
name
The interface include command has been introduced.2.00
Name or alias of the Ethernet-interface
that should be plugged into the bridge.
3.16.37 interface inherit
Description Specify the name of the Ethernet-interface which will be added to the program
bridge as a port. In contrast with the include command, inherit command
transfers some settings of the interface being added to the bridge, such as
IP-address, mask and IP-aliases. On removing either the bridge itself or the
bridge interface, these settings, even if they have been changed will be copied
back to the vacant interface.
The command allows one to add the device control interface to the bridge
so that control is not lost.
Command with no prex removes the interface from the bridge, returns the
settings that have earlier been inherited by the bridge back to the interface,
and resets these settings on the bridge.
Prex no Yes
Change settings Yes
Multiple input Yes
Interface type Bridge
Synopsis
Arguments
(cong-if)> inherit ‹interface›
(cong-if)> no inherit ‹interface›
interface
Interface
name
DescriptionValueArgument
Name or alias of the Ethernet-interface
that should be plugged into the bridge.
100
Command Reference Guide — Keenetic Lite (KN-1310)
 Loading...
Loading...