Page 1

KASPERSKY LAB
Kaspersky Anti-Virus 5.5 for Proxy
Server
ADMINISTRATOR'S
GUIDE
Page 2

KASPERSKY ANTI-VIRUS 5.5 FOR PROXY SERVER
Administrator's Guide
© Kaspersky Lab
http://www.kaspersky.com
Revision date: June 2006
Page 3

Contents
CHAPTER 1. KASPERSKY ANTI-VIRUS FOR PROXY SERVER .............................. 5
1.1. Hardware and software requirements .................................................................. 6
1.2. Licensing policy ..................................................................................................... 7
1.3. Distribution kit ........................................................................................................ 7
1.3.1. License agreement ......................................................................................... 8
1.4. Help desk for registered users .............................................................................. 8
1.5. Conventions........................................................................................................... 9
CHAPTER 2. OPERATION ALGORITHM AND TYPICAL DEPLOYMENT
SCENARIOS .............................................................................................................. 10
2.1. The algorithm of application functioning ............................................................. 10
2.2. Typical deployment scenarios............................................................................. 13
2.2.1. Installing the application to the same server with SQUID proxy ................. 13
2.2.2. Installation on a dedicated server................................................................. 14
CHAPTER 3. INSTALLING THE APPLICATION......................................................... 15
3.1. Installing the application on a server running Linux ........................................... 15
3.2. Installing the application on a server running FreeBSD..................................... 16
3.3. Installation procedure .......................................................................................... 16
3.4. Post-install setup ................................................................................................. 17
3.5. Distribution of the application files in directories................................................. 18
CHAPTER 4. USING KASPERSKY ANTI-VIRUS....................................................... 20
4.1. Updating the anti-virus databases ...................................................................... 20
4.1.1. Automatic updating of the anti-virus databases........................................... 21
4.1.2. Manual updating of the anti-virus databases............................................... 22
4.1.3. Creating a shared directory for storing and sharing database updates...... 23
4.2. Managing license keys........................................................................................ 24
4.2.1. Viewing information about license keys....................................................... 25
4.2.2. Renewing your license .................................................................................26
4.2.3. Removing a license key ............................................................................... 27
4.3. Using a control script ........................................................................................... 28
Page 4

4 Kaspersky Anti-Virus for Proxy Server
4.4. Ensuring anti-virus protection of HTTP traffic..................................................... 29
4.5. Configuring the anti-virus scan parameters for user groups.............................. 30
CHAPTER 5. ADDITIONAL SETTINGS OF KASPERSKY ANTI-VIRUS .................. 34
5.1. Creating groups ................................................................................................... 34
5.2. Anti-virus scan settings........................................................................................ 36
5.3. The choice of actions over scanned objects ...................................................... 36
5.4. Administrator notifications ................................................................................... 38
5.5. Operation modes................................................................................................. 40
5.6. Modes of interaction with proxy via ICAP........................................................... 41
5.7. Application statistics logging ............................................................................... 41
5.8. Application reporting parameters ........................................................................ 43
5.9. Memory dump creation for detection of errors ................................................... 45
5.10. Work with Internet broadcasting stations.......................................................... 46
CHAPTER 6. UNINSTALLING THE APPLICATION ................................................... 47
APPENDIX A. APPLICATION REFERENCE............................................................... 48
A.1. kav4proxy.conf application configuration file...................................................... 48
A.2. Macros................................................................................................................. 55
A.3. kavicapserver return codes................................................................................. 56
A.4. Command line options for licensemanager ....................................................... 56
A.5. Licensemanager return codes............................................................................ 57
A.6. Keepup2date command line options.................................................................. 57
A.7. Keepup2date return codes ................................................................................. 59
APPENDIX B. KASPERSKY LAB................................................................................. 60
B.1. Other Kaspersky Lab Products .......................................................................... 61
B.2. Contact Us........................................................................................................... 69
APPENDIX C. LICENSE AGREEMENT ...................................................................... 70
Page 5

CHAPTER 1. KASPERSKY ANTI-
VIRUS FOR PROXY SERVER
Kaspersky Anti-Virus 5.5 for Proxy Server (hereinafter also referred to as
Kaspersky Anti-Virus or the Application) is intended for anti-virus protection of
traffic routed via proxy servers based on Squid versions 2.5 and 3.0 with support
for the Internet Content Adaptation Protocol (ICAP) in accordance with RFC
3507.
The application allows the user to:
• Perform anti-virus scanning of objects transferred via the proxy server.
• Cure revealed infected objects and block access to an infected object if
disinfection fails.
• Use group settings to define various filtration parameters applied
depending upon the address of the user requesting an object and the
object's address (URL).
• Log activity statistics including, in addition to other data, information about
anti-virus scanning and its results, application errors and warnings.
• Notify administrators about detection of malicious software.
• Update the anti-virus databases. The application uses update servers of
Kaspersky Lab as the source of updates. It can also be configured to
update the databases from a local directory.
The anti-virus databases are employed for detection of infected objects
and their disinfection. The application uses database records to analyze
every object checking it for virus presence: its content is compared with
code typical for specific viruses.
Please keep in mind that new viruses appear every day and therefore
we recommend maintaining the anti-virus databases in an up-to-date
state. New updates are made available on Kaspersky Lab update
servers every hour.
Page 6
6 Kaspersky Anti-Virus for Proxy Server
1.1. Hardware and software
requirements
In order to ensure normal functioning of Kaspersky Anti-Virus, the system must
meet the following hardware and software requirements:
Minimum hardware requirements
®
• Intel Pentium
• 64 MB RAM
• 50 MB of disk space for application setup
• 200 MB of available disk space for temporary files.
The configuration is intended to provide for servicing of at least 10 clients
sending at least 20 requests per minute with average request size of 15 Kb.
Optimal hardware requirements:
• for a proxy server servicing requests from 50 clients with average load of
900 requests per minute and daily traffic of 250 MB:
• Intel Pentium
• 128 MB RAM.
• 512 MB of available disk space for temporary files.
• for a proxy server servicing requests from 250 clients with average load of
1300 requests per minute and daily traffic of 1 GB:
• Intel Pentium
• 512 MB RAM.
• 1 GB of available disk space for temporary files.
Software requirements
• One of the following operating systems:
• RedHat Linux 9.0.
• RedHat Fedora Core 5.
• RedHat Enterprise Linux Advanced Server 4.
• SuSE Linux Enterprise Server 9.0.
• SuSE Linux Professional 10.1.
133 MHz processor or higher
:
for product operation:
®
II 300 MHz processor.
®
4 processor.
Page 7
Kaspersky Anti-Virus for Proxy Server 7
• Mandriva 2006.
• Debian GNU/Linux version 3.1r2.
• FreeBSD version 4.11.
• FreeBSD version 5.4 .
• FreeBSD version 6.1.
• Squid 2.5 or 3.0 proxy server with ICAP support.
• Perl 5.0 or higher (www.perl.org
• Glibc 2.2.x or higher (for Linux distributions).
).
1.2. Licensing policy
The licensing policy for Kaspersky Anti-Virus includes a system of product use
limitations based on the following criteria:
• Number of users protected by the application
• HTTP traffic processed daily (MB/day).
The licensing policy based on processed traffic takes into account the traffic
created by scanned objects only, auxiliary service traffic generated by the
application is not included into that volume.
Each type of licensing is also limited by a certain period (typically one year or two
years after the date of purchase).
You can purchase a license limited by one of the above criteria (for example, by
the daily HTTP traffic volume).
1.3. Distribution kit
You can purchase the product either from our dealers (retail box) or at one of our
online stores (for example, www.kaspersky.com
The retail box contains:
• sealed envelope containing the installation CD with the product
• a copy of this Administrator’s Guide
• license key file bundled with the distribution package or recorded to a
special floppy disk
• License Agreement.
– follow the E-store link).
Page 8

8 Kaspersky Anti-Virus for Proxy Server
Before you unseal the envelope containing the CD, make sure you
have carefully read the License Agreement.
If you purchase our application online, you will download it from Kaspersky Lab's
website. Your license key is either included in the installation package or will be
sent to you by email after payment.
1.3.1. License agreement
The license agreement constitutes a legal agreement between you and
Kaspersky Lab Ltd containing the terms and conditions subject to which you may
use the purchased software.
Please read the license agreement carefully!
If you do not agree with the terms of the license agreement you may return the
box with Kaspersky Anti-Virus to the distributor, where you have purchased it,
you will be refunded the amount you've paid for subscription, provided the CD
envelope remains sealed.
Opening the sealed envelope of the installation CD or installing the product to a
computer means your acceptance of all the terms and conditions of the license
agreement.
1.4. Help desk for registered users
Kaspersky Lab offers an extensive service package enabling registered
customers to boost the productivity of Kaspersky Mail Gateway.
If you purchase a subscription you will be provided with the following services for
the period of your subscription:
• new versions of this software product provided free of charge
• phone or email support on matters related to the installation,
configuration, and operation of the product you have purchased
• notifications about new software products from Kaspersky Lab, and about
new virus outbreaks. This service is provided to users who have
subscribed to the Kaspersky Lab email newsletter service.
Page 9
Kaspersky Anti-Virus for Proxy Server 9
Kaspersky Lab does not give advice on the performance and use of
your operating system or other technologies.
1.5. Conventions
Various formatting conventions are used throughout the text of this document
depending on the purpose of a particular element. Table 1 below lists the
formatting conventions used.
Table 1. Conventions
Style Meaning
Bold type
Note.
Attention!
In order to perform the
action,
1. Step 1.
2. …
Task, example
Solution
[key] – key purpose.
Text of information
messages and the command
line
Menu titles, menu items, window titles,
parts of dialog boxes, etc.
Additional information, notes.
Information requiring special attention.
Procedure description for user's steps
and possible actions.
Statement of a problem, example for
using the software features.
Solution to a defined problem.
Command line keys.
Text of configuration files, information
messages and the command line.
Page 10

CHAPTER 2. OPERATION
ALGORITHM AND TYPICAL
DEPLOYMENT SCENARIOS
This chapter contains essential information necessary for understanding of
application functionality, its configuration and integration with an existing network
structure.
2.1. The algorithm of application
functioning
Kaspersky Anti-Virus scans HTTP traffic using two modes of proxy operation:
REQMOD and RESPMOD.
In the RESPMOD mode the application checks objects requested by users via a
proxy server. In the REQMOD mode it scans objects transmitted from users
through the proxy. REQMOD is applied, for instance, for anti-virus scanning of email messages sent by users via a web-based mail server interface. Kaspersky
Anti-Virus scans message attachments transferred by users to mail servers.
The application performs anti-virus scanning of Internet traffic in the RESPMOD
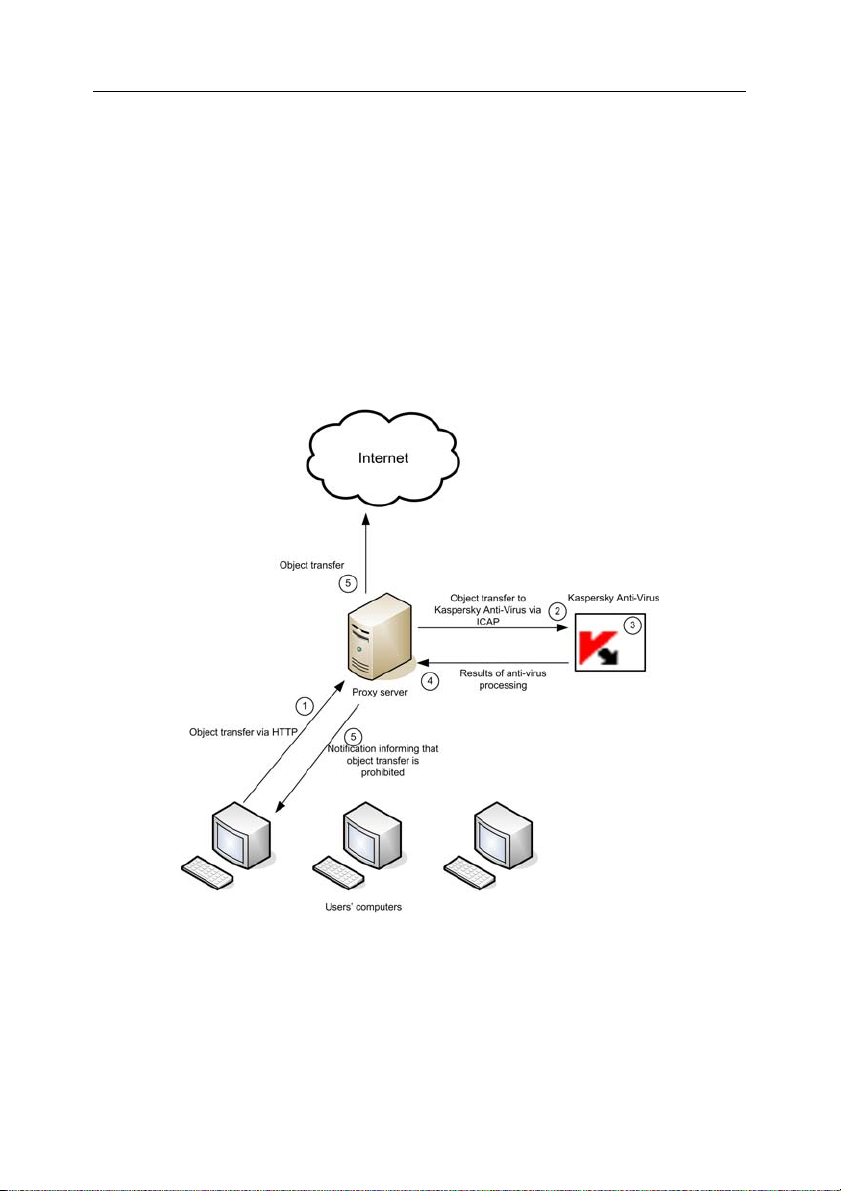
mode in accordance with the following procedure (see Fig. 1):
1. User requests an object through a Squid proxy via HTTP.
2. If the requested object is available within the Squid proxy cache, it
will be returned to the user. If the object has not been found in
cache, Squid proxy accesses a remote server and downloads the
requested object from it.
3. Squid uses ICAP to transfer the retrieved object to Kaspersky AntiVirus for an anti-virus check.
4. Kaspersky Anti-Virus verifies correspondence of request
parameters (user IP address, URL of the requested object) to any
of its groups (please refer to section 5.1 on p. 34 for details about
groups). If it finds such group, then the application scans and
processes the object as necessary in accordance with the rules
specified for that group. If a request does not match any of the
Page 11
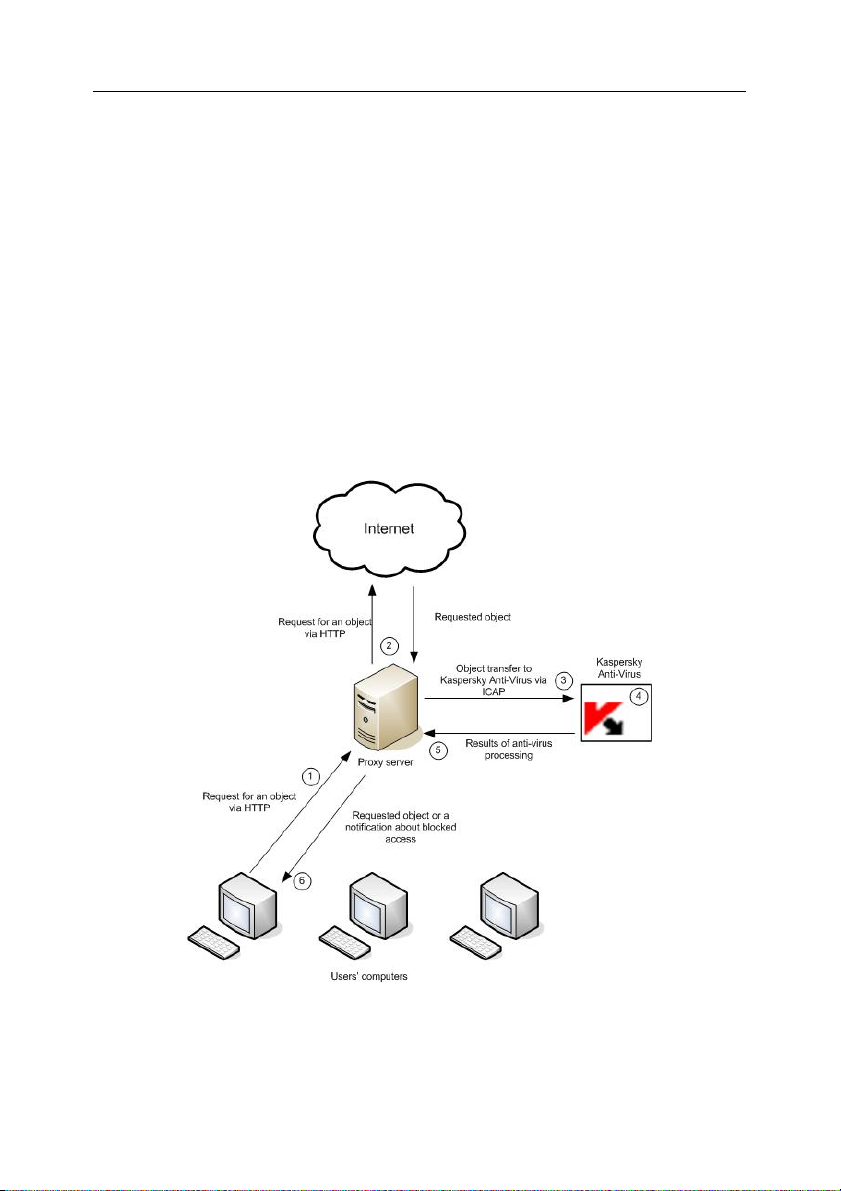
Operation algorithm and typical deployment scenarios 11
existing groups, the application will use the default group rules for
anti-virus scanning and processing.
5. The application uses the results of anti-virus scanning to assign to
a scanned object a specific status, which is employed to grant
users access to that object or block access attempts (please refer
to section 5.3 on p. 36 for details about available statuses and
actions performed by the application). Access to objects with a
specific status is granted or blocked according to the processing
group parameters (please refer to section 5.1 on p. 34 for details
about groups).
6. If access to an object has been granted, Kaspersky Anti-Virus
allows Squid proxy to cache the object and transmit it to users. If
access to an object is blocked, Kaspersky Anti-Virus prohibits
Squid proxy to cache the object and deliver it to users. Instead of
the requested object, the user will receive a notification informing
that access to that object has been blocked.
Figure 1. Anti-virus scanning of traffic in the RESPMOD mode
Page 12
12 Kaspersky Anti-Virus for Proxy Server
The application performs anti-virus scanning of Internet traffic in the REQMOD
mode in accordance with the following procedure (see Fig. 2):
1. User sends an object using HTTP via Squid proxy.
2. Squid proxy uses ICAP to transfer the received object to Kaspersky
Anti-Virus for an anti-virus scan.
3. Kaspersky Anti-Virus checks if the request parameters match any of the
existing groups (please refer to section 5.1 on p. 34 for details about
groups). If it finds such group, then the application scans and processes
the object as necessary in accordance with the rules specified for that
group. If a request does not match any of the existing groups, the
application will use the default group rules for anti-virus scanning and
processing.
Figure 2. Anti-virus scanning of traffic in the REQMOD mode
4. The application uses the results of anti-virus scanning to assign to a
scanned object a specific status, which is employed as a criterion to
allow transfer of that object or prohibit it (please refer to section 5.3 on
p. 36 for details about available statuses and actions performed by the
application). Permission or denial of transfer for objects with a specific
Page 13

Operation algorithm and typical deployment scenarios 13
status defined according to the processing group parameters (please
refer to section 5.1 on p. 34 for details about groups).
5. If transfer is allowed, the proxy will transmit the object sent by the user.
If transfer is prohibited, Squid will not transmit the object. Instead, it will
send to the user a notification informing that the transfer has been
blocked.
2.2. Typical deployment scenarios
This section contains a description of two main methods available for application
deployment:
• Application setup on the same server with Squid proxy
• Application setup on a dedicated server.
General guidelines described in the examples will allow you to configure the
application in accordance with your existing network structure.
2.2.1. Installing the application to the same
server with SQUID proxy
Further in this document we shall use this variant of Kaspersky AntiVirus setup (on the same server with SQUID proxy) to describe its
operation and configuration.
Application setup on the same server with Squid allows higher speed of
processing as data transfers between Squid and Kaspersky Anti-Virus occur
locally and do not involve the network. Such deployment scheme is efficient in
case of low load on the proxy server. If the proxy is used to serve a large number
of user requests, you are advised to install the application to a dedicated server
since anti-virus scanning and processing are most resource-intensive
procedures, which can therefore influence negatively the general proxy
performance. Please refer to section 2.2.2 on p. 14 for application setup on a
dedicated server. During application setup the installer automatically configures
the following aspects:
1. Kaspersky Anti-Virus will be set up to run automatically at the operating
system start and listen for requests from Squid proxy using port 1344 for
all network interfaces of the server.
2. The following lines will be added to the ICAP OPTIONS section in the
Squid configuration file specified during application setup:
Page 14

14 Kaspersky Anti-Virus for Proxy Server
icap_enable on
icap_send_client_ip on
icap_service is_kav_resp respmod_precache 0
icap://localhost:1344/av/respmod
icap_service is_kav_req reqmod_precache 0
icap://localhost:1344/av/reqmod
icap_class ic_kav is_kav_req is_kav_resp
icap_access ic_kav allow all
They will make the proxy transmit all requested objects to Kaspersky AntiVirus via port 1344 of the local interface.
2.2.2. Installation on a dedicated server
Installing the application to a dedicated server is recommended in case of high
load on the proxy server and in situations when Kaspersky Anti-Virus is used to
process the traffic of several proxy servers.
Since such deployment scheme does not allow automatic configuring of the
application, you should set it up manually in accordance with the following
procedure:
1. After application setup use the ListenAddress parameter in the
[icapserver.network] section of the kav4proxy.conf configuration file to
specify the IP address of the network interface and port that Kaspersky
Anti-Virus will use to wait for proxy requests to process necessary
objects. By default Kaspersky Anti-Virus waits for requests to all network
interfaces of the server on port 1344.
2. Add the following lines to the ICAP OPTIONS section of the Squid proxy
configuration file
icap_enable on
icap_send_client_ip on
icap_service is_kav_resp respmod_precache 0
icap://<ip_address>:<port>/av/respmod
icap_service is_kav_req reqmod_precache 0
icap://<ip_address>:<port>/av/reqmod
icap_class ic_kav is_kav_req is_kav_resp
icap_access ic_kav allow all
where <ip_address>
Kaspersky Anti-Virus is installed; <port> is the port that Kaspersky AntiVirus uses to wait for proxy requests for anti-virus processing. Restart
Squid as soon as the changes are entered.
stands for the IP address of the server where
Page 15
CHAPTER 3. INSTALLING THE
APPLICATION
Before installing Kaspersky Anti-Virus, you are advised to:
1. Make sure that your system meets the hardware and software
requirements (see section 1.1 on p. 6).
2. Log on to the system as root.
3. Make sure that your installed Squid proxy server supports ICAP.
Unlike Squid 3.0, Squid 2.5 does not support ICAP by default.
Please see the README-SQUID.txt file in the
/opt/kav/5.5/kav4proxy/share/doc/ directory for information
about available Squid distributions, correct compilation and
proxy configuration for ICAP support.
3.1. Installing the application on a
server running Linux
Kaspersky Anti-Virus for servers running the Linux operating system is
distributed in two different installation packages:
• .rpm – for systems that support RPM Package Manager.
• .deb – for Debian distributions.
To initiate installation of Kaspersky Anti-Virus from the rpm package,
enter the following in the command line:
# rpm –i kav4proxy-linux-<version_number>.i386.rpm
To initiate installation of Kaspersky Anti-Virus from the deb package,
enter the following in the command line:
# dpkg –I
During the setup process you will have to specify additional information
necessary for connection to the Internet, downloading of the anti-virus databases
kav4proxy-linux-<version_number>.deb
Page 16
16 Kaspersky Anti-Virus for Proxy Server
and the settings for interaction with the proxy server. Please refer to section 3.4
on p. 17 for details.
3.2. Installing the application on a
server running FreeBSD
The distribution file for installation of Kaspersky Anti-Virus on servers running the
FreeBSD operating system is supplied as a .tgz package.
To initiate installation of Kaspersky Anti-Virus from a tgz-package enter
the following in the command line (depending on the version of
FreeBSD distributive):
# pkg_add kav4proxy-freebsd4-<distributive version >.tgz
or
# pkg_add
or
# pkg_add kav4proxy-freebsd6-< distributive version >.tgz
During the setup process you will have to specify additional information
necessary for connection to the Internet, downloading of the anti-virus databases
and the settings for interaction with the proxy server. Please refer to section 3.4
on p. 17 for details.
kav4proxy-freebsd5-< distributive version >.tgz
3.3. Installation procedure
Algorithms described in this section and in section 3.4 suggest that the
target server already has Squid 2.5 or 3.0 with ICAP support installed.
Kaspersky Anti-Virus must be installed in two stages. The first stage will be
performed automatically after execution of the commands described in sections
3.1, 3.2, it comprises the following steps:
1. Creation of the klusers group and the kluser account with the
necessary privileges that Kaspersky Anti-Virus will use to start and
operate.
2. Copying of the files from distribution package to computer.
3. Registration of services necessary for Kaspersky Anti-Virus functioning.
Page 17

Installing the application 17
3.4. Post-install setup
Post-install setup of Kaspersky Anti-Virus is the second stage of its installation
including configuration of the application and Squid proxy server. To initiate the
configuration process, use the postinstall.pl script located in the
/opt/kav/5.5/kav4proxy/setup/ directory. After script start you will be offered to
perform the following actions:
The postinstall.pl script should be launched manually for RPM-based
systems. In other systems (for example, such as FreeBSD) the script
will run automatically during the installation procedure.
1. Specify the path to the license key file.
2. Configure the parameters of the proxy server used for connection to the
Internet in the following format:
http://<proxy server IP address>:<port>
or
http://<user_name>:<password>@<proxy server IP
address>:<port>
depending upon the necessity to authenticate users logging on to that
proxy. The value will be used by the application updater component
(keepup2date) for connection to Kaspersky Lab's servers and
downloading of updates to the anti-virus databases.
If you are not using a proxy for Internet connection, specify no as the
value for that parameter.
3. Download updates to the anti-virus databases from update servers of
Kaspersky Lab. Specify yes or no depending upon your wish to update
immediately or later.
4. Specify full path to the configuration file of the Squid proxy transferring
the HTTP traffic, which Kaspersky Anti-Virus is supposed to scan. The
settings necessary to enable interaction via ICAP between the proxy and
the application will be added to the configuration file.
During the process of post-install configuration the task for hourly updates of the
anti-virus databases will be registered with the cron service.
If you have not installed a license key during post-install product configuration,
then after launch Kaspersky Anti-Virus will start functioning in the unlicensed
mode. If you have not downloaded the anti-virus databases during post-install
configuration, then after launch Kaspersky Anti-Virus will start functioning
Page 18

18 Kaspersky Anti-Virus for Proxy Server
without the anti-virus databases. Please see section 5.5 on p. 40 for details on
the application modes.
3.5. Distribution of the application
files in directories
After the installation of Kaspersky Anti-Virus on a server running Linux is
complete, the application files will be located in the following directories, provided
that the default paths have been accepted during the installation:
/etc/kav/5.5/kav4proxy/kav4proxy.conf – configuration file containing
application parameters.
/opt/kav/5.5/kav4proxy/bin – directory containing executable files of the
application components:
avbasestest – utility validating downloaded updates to the anti-virus
databases used by the keepup2date component.
kavicapserver – executable file of the main application component.
keepup2date – utility updating the anti-virus databases.
licensemanager – utility for management of license keys.
/opt/kav/5.5/kav4proxy/init.d/kav4proxy – service script for application
control.
/opt/kav/5.5/kav4proxy/contrib/kavproxy.wbm – Webmin plug-in module for
Kaspersky Anti-Virus management.
/opt/kav/5.5/kav4proxy/man – directory containing application manual pages.
/opt/kav/5.5/kav4proxy/share/doc/kav4proxy.groups.conf.sample – sample
file containing group-based application configuration.
/opt/kav/5.5/kav4proxy/share/doc/README-SQUID.txt – file containing
information about available Squid distributions, correct compilation and
proxy configuration for ICAP support.
/opt/kav/5.5/kav4proxy/setup – directory containing scripts used for post-
install setup and removal of the application:
keepup2date.sh – script that configures the keepup2date component.
icap_squid_setup.pl – script that configures Squid for work with
Kaspersky Anti-Virus.
postinstall.pl – post-install application setup script.
Page 19

Installing the application 19
uninstall.pl – application removal script.
/var/db/kav/5.5/kav4proxy/ – application directory including:
backup/ – directory where the updater saves backup copies of the anti-
virus databases and application modules prior to an update.
bases/ – directory containing the anti-virus databases and core
modules.
licenses/appinfo.dat – file that contains information about the current
license.
patches/ – directory where the updates for the anti-virus core modules
are stored.
/var/log/kav/5.5/kav4proxy/ – directory containing the application log files.
Page 20
CHAPTER 4. USING KASPERSKY
ANTI-VIRUS
This chapter contains solutions for typical tasks related to work with Kaspersky
Anti-Virus, such as application updating, management of license keys, anti-virus
protection of HTTP traffic, and configuration of different anti-virus scanning
parameters for various user groups. The tasks described in this section reflect
basic features of Kaspersky Anti-Virus. Their implementation in a specific
configuration will depend upon the organizational peculiarities of your network
and the existing security policy. Please refer to Chapter 5 on p. 34 for a detailed
explanation of application settings used in description of these tasks.
4.1. Updating the anti-virus
databases
Kaspersky Anti-Virus uses the anti-virus databases while processing the objects
requested by users through Squid proxy.
The anti-virus databases are employed during scanning and disinfection of
infected objects; they contain descriptions of all currently known viruses and the
methods of disinfection for objects affected by those viruses.
The keepup2date component is included into the application to provide for
software updates. The updates are retrieved from the update servers of
Kaspersky Lab, e.g.:
http://downloads1.kaspersky-labs.com/
http://downloads2.kaspersky-labs.com/
ftp://downloads1.kaspersky-labs.com/
The updcfg.xml file included in the installation package lists the URLs of all
available update servers.
etc.
The keepup2date component supports Basic authentication for
connections through a proxy server.
To update the anti-virus databases, the keepup2date component selects an
address from the list of update servers and tries to download updates from that
server. If the server is currently unavailable, the application connects to another
server, trying to download updates.
Page 21

Using Kaspersky Anti-Virus 21
We strongly recommend that you set up the keepup2date component to
update the databases every hour!
After a successful update, a command specified as the value of the
PostUpdateCmd parameter in the [updater.options] section of the
configuration file will be executed. By default, this command will automatically
initiate reloading of the anti-virus databases. Incorrect modification of that
parameter may prevent the application from using the updated databases or
cause it to function erroneously.
All settings of the keepup2date component are stored in the [updater.*]
sections of the configuration file.
If your network has a complicated structure, we recommend that you download
updates from Kaspersky Lab’s update servers every hour and place them in a
network directory. To keep other networked computers constantly updated,
configure the local computers to copy the updates from that directory. For
detailed instructions on creation of a public directory, see section 4.1.3 on p. 23.
The updating process can be scheduled to run automatically using the cron
utility (see section 4.1.1 on p. 21) or started manually from the command line
(see section 4.1.2 on p. 22). Starting the keepup2date component requires root
or kluser user privileges.
4.1.1. Automatic updating of the anti-virus
databases
You can schedule regular automatic updates for the anti-virus databases using
the cron service. You can configure cron either manually or using the
keepup2date.sh script located in the /opt/kav/5.5/kav4proxy/setup/ directory.
In order to create a сron task updating the anti-virus databases every hour, enter
the following in the command line:
# /opt/kav/5.5/kav4proxy/setup/keepup2date.sh –install
To delete the cron task for hourly updating of the anti-virus databases, enter the
following in the command line:
# /opt/kav/5.5/kav4proxy/setup/keepup2date.sh –uninstall
Page 22
22 Kaspersky Anti-Virus for Proxy Server
Task
: Configure the application to update automatically your anti-virus
databases every hour. An update server should be selected from the
updcfg.xml file by default. Only errors occurring in the component
operation should be recorded in the system log. Keep a general log of
all task starts. Output no information to the console.
Solution
1. In the application configuration file, specify the following values for
2. Edit the file that sets the rules for the cron process (crontab –e) by
: to perform the above task, do the following:
the parameters below:
[updater.report]
Append=true
ReportLevel=1
entering the following string for the root or kluser user, add, for
example, the following line:
In Linux:
23 * * * * /opt/kav/5.5/kav4proxy/bin/keepup2date
-q
In FreeBSD:
23 * * * * /usr/local/share/kav/5.5/
kav4proxy/bin/keepup2date -q
The specified time setting for the cron task start is just an example. You
are advised to specify your own settings for the start time to avoid
overloading the updating servers.
4.1.2. Manual updating of the anti-virus
databases
You can start updating your anti-virus databases from the command line at any
time.
Task
: start updating of the anti-virus databases, save updating results in
the updatesreport.log file within the /var/log/kav/5.5/kav4proxy/
directory.
Solution
privileged user) and enter in the command line:
: to accomplish the task, log in as the root (or any other
Page 23

Using Kaspersky Anti-Virus 23
# keepup2date –l
/var/log/kav/5.5/kav4proxy/updatesreport.log
If you need to update the anti-virus databases on several servers, it may be more
convenient to download the updates from an update server once, save them to a
shared directory, and mount the directory within the file system of every server
running Kaspersky Anti-Virus. Then it will be sufficient to launch the update script
having specified first the mounted directory as the source of updates. FTP and
HTTP can also be used for sharing of the anti-virus databases. Please see
section 4.1.3 on p. 23 for details related to creation of a shared directory for
updates.
Task
: initiate updating of the anti-virus databases using the local
/home/kluser/bases directory as the source. Output the results to the
/tmp/updatesreport.log file.
Solution
privileged user) and perform the following steps:
1. Mount the shared directory containing updates to the anti-virus
2. Enter the following in the command line:
You can also update the application remotely using the appropriate
Webmin plug-in.
: to accomplish the task, log in as the root (or any other
databases, to the local /home/kluser/bases directory.
# keepup2date –l /tmp/updatesreport.log –g
/home/kluser/bases
4.1.3. Creating a shared directory for
storing and sharing database updates
To update the anti-virus databases correctly on local computers from the shared
directory, you need to reproduce in that directory a file system structure that is
similar to that of Kaspersky Lab’s update servers. This task deserves a detailed
explanation.
: create a shared local directory, which the local computers will use
Task
as the source to update their anti-virus databases.
Solution: to accomplish the task, log in as the root (or any other
privileged user) and do the following:
Page 24

24 Kaspersky Anti-Virus for Proxy Server
1. Create a local directory. The kluser account must have sufficient
privileges to write to it.
2. Run the keepup2date component as follows:
# keepup2date –u <dir>
where <dir> stands for a full path to the created directory.
3. Provide reading access to that directory for local computers on your
network.
4.2. Managing license keys
The right to use Kaspersky Anti-Virus is determined by the license key. The key
is included in the product’s distribution kit and entitles you to use the application
from the day you have purchased it and installed the key.
The application checks the presence of an installed license key every
time it starts or reloads its anti-virus databases.
If a license key is not installed or an error has occurred while loading the
information about the current license, the application switches into a special
unlicensed mode of operation. In that mode it does not perform anti-virus
scanning of objects transferred through a proxy server; all objects are treated
using the action specified by the LicenseErrorAction parameter (see section
A.1 on p. 48).
After the license expires, the functionality of the application will still be preserved
except for the possibility to update the anti-virus databases. You will still be able
to perform anti-virus scanning and processing of objects, but you will be unable
to use the databases issued after your license expiration date. Therefore, you
may not be protected against new viruses that have appeared after your license
expired.
In order to protect your computer against new viruses, we recommend that you
renew the license to use Kaspersky Anti-Virus.
The license key entitles you to use the application. It contains all information
related to the license you have purchased, including the type of license, license
expiry date, information about dealers, etc.
In addition to the right to use the application during the license period, you will
have the following benefits:
• twenty-four-hour technical support
• hourly updates of the anti-virus databases
Page 25
Using Kaspersky Anti-Virus 25
• timely notifications about new virus threats.
Therefore it is essential to extend in time your license to use Kaspersky AntiVirus. You can also install an additional key. The application will start using it as
soon as the current active key expires (see section 4.2.2 on p. 26).
4.2.1. Viewing information about license
keys
You can view information about the installed license keys in the reports of the
kavicapserver component. Each time the component starts, kavicapserver loads
the license key information and displays it in the report. The kavicapserver.log
report file is stored in the /var/log/kav/5.5/kav4proxy/ directory.
More detailed information about the status of the license keys may be obtained
using licensemanager, a special component of the application.
All information about keys may be viewed either on the server’s console, or
remotely from any networked computer that has access to the Webmin module.
To view information about all installed license keys, enter the following
in the command line:
# licensemanager –s
In the server console, you will see information similar to the following:
Kaspersky license manager for Linux. Version
5.5.0/RELEASE
Copyright (C) Kaspersky Lab, 1997-2006.
Portions Copyright (C) Lan Crypto
License info:
Product name: Kaspersky Anti-Virus for Proxy Server
Expiration date: 14-06-2006, expires in 117 days
Active key info:
Product name: Kaspersky Anti-Virus for Proxy Server
Key file 0009A3A3.key
Type: Commercial
Expiration date: 14-06-2006
Serial: 0007-00047E-0009A3A
Page 26

26 Kaspersky Anti-Virus for Proxy Server
To view information about a license key, enter, for example, the
following in the command line:
# licensemanager -k 00053E3D.key
where 00053E3D.key is the name of the license key file.
In the server console, you will see information similar to the following:
Kaspersky license manager. Version 5.5.0/RELEASE
Copyright (C) Kaspersky Lab, 1997-2006.
Portions Copyright (C) Lan Crypto
Product name: Kaspersky Anti-Virus for Proxy Server
Creation date: 15-03-2005
Expiration date: 14-06-2006
Serial 0007-00047E-0009A3A
Type: Commercial
Count: 1
Lifespan: 365
4.2.2. Renewing your license
Renewal of the license to use Kaspersky Anti-Virus will give you the right to reenable full product functionality. Besides, additional services listed in section 4.2
on p. 24 will be resumed.
The license term depends on the product you bought and the type of the license
you purchased.
To renew the license for Kaspersky Anti-Virus:
Contact the company that sold you the product and renew your license
for Kaspersky Anti-Virus.
or:
Purchase a license extension directly from Kaspersky Lab. Write a letter
of request to the Sales Department of our company at
sales@kaspersky.com or fill in the corresponding form on our website
(www.kaspersky.com
your payment is received, we will send a license key to the email
address indicated in the corresponding field of your license renewal
form.
), section E-Store Æ Renew Your License. After
Page 27

Using Kaspersky Anti-Virus 27
To install a new license key, enter, for example, the following in the
command line:
# licensemanager -a 00053E3D.key
where 00053E3D.key is the name of the license key file.
If the installation is successful, the following (or similar) information will
be displayed on the server console:
Kaspersky license manager. Version 5.5.0/RELEASE
Copyright (C) Kaspersky Lab. 1998-2006.
Key file 00053E3D.key is successfully registered
We recommend that you update the anti-virus databases after the installation.
If you want to install a new license key before the current license key expires,
you can add it as a backup license key. The backup key will be activated
immediately after the current one expires. The term of validity for the additional
key starts from the activation date. You can install only one backup key.
If you have installed two keys (the current and an additional one), you can view
information about the installed active and backup keys in the server console.
4.2.3. Removing a license key
To remove the current license key, enter the following in the command
line:
# licensemanager –da
If the component removes the license key successfully, the following (or similar)
information will be displayed on the server console:
Kaspersky license manager. Version 5.5.0/RELEASE
Copyright (C) Kaspersky Lab. 1998-2006.
Active key was successfully removed
To remove a backup key, enter the following in the command line:
# licensemanager –dr
The server console will display the following (or similar) information:
Kaspersky license manager. Version 5.5.0/RELEASE
Page 28

28 Kaspersky Anti-Virus for Proxy Server
Copyright (C) Kaspersky Lab. 1998-2006.
Additional key was successfully removed
4.3. Using a control script
The kav4proxy application control script located in the
/opt/kav/5.5/kav4proxy/init.d directory is used to start, stop and restart the
application. It uses the following command line keys:
• start – command to check the configuration file and launch the
application. 0 return code indicates a successful start.
• stop – command to check whether Kaspersky Anti-Virus is running (using
process ID). If the application is running, the script sends the SIGTERM
signal. If the application does not stop within three seconds, the script
sends the SIGKILL signal. 0 return code indicates a successful execution.
• restart – command to stop and start the application as provided for suing
the stop and start keys.
• reload – command to reload the application configuration and the anti-
virus databases using the SIGHUP signal.
• reload_avbase – command to reload the anti-virus databases only and
validate the license key.
• stats – command to write the results of statistics counters to a file (see
section 5.7 on p. 41) and switch to report logging to another file. Launch
of the control script with the stats command line option can be used in the
systems of automatic rotation of log files in order to initiate logging into a
new file.
Page 29
Using Kaspersky Anti-Virus 29
4.4. Ensuring anti-virus protection of
HTTP traffic
Task:
Provision for anti-virus scanning of HTTP traffic transmitted by Squid
installed on the same server with Kaspersky Anti-Virus in accordance
with the following requirements:
• General parameters of anti-virus scanning must be used for all
requests:
• Disinfection of infected objects must be enabled.
• Scanning of e-mail databases must be disabled.
• Scanning of packed and archived objects must be
enabled.
• Block access to infected, suspicious, damaged objects and
objects containing code that resembles a known virus.
• Use partial mode while processing proxy server requests.
• Disable anti-virus scanning of objects requested from the
www.trusted_company.com web server.
• Store statistics on the results of anti-virus scanning in the
/var/log/kav/5.5/statistic file.
Solution
1. Install Kaspersky Anti-Virus to the same server with Squid proxy
2. Specify the following parameter values in the kav4proxy.conf
: to accomplish the task, perform the following steps:
(see section 2.2.1 on p. 13) ad perform its post-install setup (see
section 3.4 on p. 17).
configuration file (leave the values of parameters not mentioned in
the example unchanged):
[icapserver.filter]
ExcludeURL=www.trusted_company.com/.*
[icapserver.engine.options]
Page 30

30 Kaspersky Anti-Virus for Proxy Server
ScanPacked=yes
ScanArchives=yes
ScanMailBases=no
ScanMailPlain=no
Cure=yes
[icapserver.actions]
InfectedAction=deny
SuspiciousAction=deny
WarningAction=deny
ErrorAction=skip
ProtectedAction=skip
CorruptedAction=skip
[icapserver.protocol]
AnswerMode=partial
[icapserver.statistics]
AVStatisticsFile=/var/log/kav/5.5/statistic
3. Restart Kaspersky Anti-Virus using the following command:
# /opt/kav/5.5/kav4proxy/init.d/kav4proxy reload
Please refer to Chapter 5 on p. 34 for a more detailed description of the
settings used in the solution for the task.
4.5. Configuring the anti-virus scan
parameters for user groups
The example in section 4.4 suggests that common settings are used for antivirus processing of all user requests coming through a proxy server. Kaspersky
Anti-Virus allows using groups for configuration of different parameters of antivirus protection for individual users.
Page 31

Using Kaspersky Anti-Virus 31
Task
:
Configure the application to perform anti-virus checks of HTTP traffic I
accordance with the following requirements:
• The following anti-virus scanning parameters must be specified
for the managers group that includes computers using the IP
addresses of the 192.168.1.0/255.255.255.0 subnet:
• Scanning of packed, archived files and e-mail
databases must be disabled.
• Disinfection of infected objects must be enabled.
• Access should be granted to clean and disinfected
objects only.
• The following anti-virus scanning parameters must be specified
for the sales group that includes computers using the IP
addresses of the 192.168.2.0/255.255.255.0 subnet:
• Scan all objects.
• Disinfection of infected objects must be enabled.
• Block access to infected, suspicious, damaged objects
and objects containing code that resembles a known
virus.
• The following anti-virus scanning parameters must be specified
for all other users:
• Scanning of e-mail databases must be disabled.
• Disinfection of infected objects must be disabled.
• Access should only be granted to objects that have
been assigned the OK status after a scan (please refer
to section 5.3 on p. 36 for details about statuses).
Solution
: to accomplish the task, perform the following steps:
1. In the kav4proxy.conf configuration file, create the following
sections containing the anti-virus scanning parameters for the
managers group:
[icapserver.groups:managers]
Priority=1
Page 32

32 Kaspersky Anti-Virus for Proxy Server
ClientIP=192.168.1.0/255.255.255.0
URL=.*
[icapserver.engine.options:managers]
ScanPacked=no
ScanArchives=no
ScanMailBases=no
ScanMailPlain=no
Cure=yes
[icapserver.actions:managers]
InfectedAction=deny
SuspiciousAction=deny
WarningAction=deny
ErrorAction=deny
ProtectedAction=deny
CorruptedAction=deny
2. In the kav4proxy.conf configuration file, create the following
sections containing the anti-virus scanning parameters for the
sales group:
[icapserver.groups:managers]
Priority=2
ClientIP=192.168.2.0/255.255.255.0
URL=.*
[icapserver.engine.options:managers]
ScanPacked=yes
ScanArchives=yes
ScanMailBases=yes
ScanMailPlain=yes
Cure=yes
[icapserver.actions:managers]
InfectedAction=deny
SuspiciousAction=deny
WarningAction=deny
Page 33

Using Kaspersky Anti-Virus 33
ErrorAction=skip
ProtectedAction=skip
CorruptedAction=deny
3. Specify the following parameters for the default group:
[icapserver.engine.options]
ScanPacked=yes
ScanArchives=yes
ScanMailBases=no
ScanMailPlain=no
Cure=no
[icapserver.actions]
InfectedAction=deny
SuspiciousAction=deny
WarningAction=deny
ErrorAction=deny
ProtectedAction=deny
CorruptedAction=deny
4. Restart Kaspersky Anti-Virus using the following command:
# /opt/kav/5.5/kav4proxy/init.d/kav4proxy reload
Please refer to Chapter 5 on p. 34 for a more detailed description of the
settings used in the solution for the task.
Page 34

CHAPTER 5. ADDITIONAL
SETTINGS OF KASPERSKY
ANTI-VIRUS
This section contains a detailed explanation of basic parameters of Kaspersky
Anti-Virus. Unlike the required settings essential for application functioning and
specified during product installation and post-install setup, additional
configuration can be performed at the administrator's discretion. It is aimed to
extend the functionality of the application and its customization to your corporate
security policy.
5.1. Creating groups
The use of groups allows an administrator to define various parameters for antivirus processing of objects for different user groups being requested or
transferred through a proxy server. A request is associated with a specific group
according to the IP address of the client computer requesting an object through a
proxy server and the URL of that object.
Ensure that the icap_send_client_ip parameter in Squid configuration
file is set to on. The value means that Squid will transfer the client's IP
address to Kaspersky Anti-Virus.
If request parameters do not match any of the existing groups, the application will
process requested objects in accordance with the rules specified for the default
group.
Parameters of each group are stored in the following five sections of the
application configuration file:
• [icapserver.groups:<group name>] contains the parameters that define
the group applicability range (IP addresses of clients, object URLs) and
group priority.
• [icapserver.filter:<group name>] contains filtration rules for the <group
name> group.
• [icapserver.engine.options:<group name>] contains the parameters of
anti-virus scanning used to process the objects associated with that
group.
Page 35
Additional settings of Kaspersky Anti-Virus 35
• [icapserver.actions:<group name>] contains the parameters that define
actions performed by the application over objects depending upon the
status assigned to them during an anti-virus check.
• [icapserver.notify:<group name>] contains the parameters used to
notify administrators about blocked objects that the application has
applied the deny action to.
The default group parameters are specified in the [icapserver.groups],
[icapserver.filter], [icapserver.options], [icapserver.actions] and
[icapserver.notify] sections.
You do not have to specify all group parameters while creating a new one. If
some parameters are missing, the application uses its default settings
(see Appendix A.1 on p. 48).
Example
of objects requested by client computers using the
192.168.10.0/255.255.255.0 subnet. Prohibit for the group access to all
: create the managers group to define the rules for processing
objects other than clean, disinfected and password-protected. Set the
group priority to 2. Use default values for all other parameters.
Solution
privileged user) and create the following sections in the kav4proxy.conf
configuration file:
: to accomplish the task, log in as the root (or any other
[icapserver.groups:managers]
Priority=2
ClientIP=192.168.10.0/255.255.255.0
URL=.*
[icapserver.engine.options:managers]
Cure=yes
[icapserver.actions:managers]
CuredAction=skip
ErrorAction=deny
ProtectedAction=skip
Page 36

36 Kaspersky Anti-Virus for Proxy Server
5.2. Anti-virus scan settings
Anti-virus engine parameters in the [icapserver.engine.options:<group
name>] define the modes for scanning and disinfection of requested objects
within a corresponding group as follows:
• ScanPacked=yes|no – enables/ disables scanning of packed files. If the
mode is disabled, all packed objects are considered to be clean.
• ScanArchives=yes|no – enables/ disables scanning of objects inside
archives. If the mode is disabled, all archive files are considered to be
clean.
• ScanMailBases=yes|no – enables/ disables scanning of mail databases
(requested or transferred via a proxy server). If the mode is disabled, all
mail databases are considered to be clean.
• ScanMailPlain=yes|no – enables/ disables scanning of mail messages in
plain text format (requested or transferred via a proxy server). If the mode
is disabled, all databases of plain text mail are considered to be clean.
• UseHeuristic=yes|no – enables/ disables heuristic analyzer used for
anti-virus scanning.
• Cure=yes|no – enables/ disables disinfection of infected objects. If the
mode is disabled, the application will not attempt to cure an infected file.
The [icapserver.engine] section contains common parameters of the anti-virus
engine applicable to all groups:
• UseAVbasesSet=standard|extended – the set of the anti-virus
databases used by the application. The extended set contains, in
addition to the records of the standard set, the signatures of potentially
dangerous software such as adware, remote administration utilities, etc.
5.3. The choice of actions over
scanned objects
Actions performed by the application on scanned objects are defined by the
status assigned to those objects as a result of an anti-virus check.
Kaspersky Anti-Virus uses the following statuses:
• OK – clean object that has successfully passed the scanning procedure.
Page 37

Additional settings of Kaspersky Anti-Virus 37
• INFECTED – the object is infected and cannot be cured or disinfection
has not been attempted.
• CURED – the object was infected; it has been cured successfully.
• WARNING – the object contains code that resembles a known virus.
• SUSPICIOUS – the object is suspected of being infected with an
unknown virus.
• PROTECTED – the object is password-protected and therefore it cannot
be scanned.
• CORRUPTED – the object is damaged.
• ERROR – object scanning resulted in an error.
Actions performed by Kaspersky Anti-Virus over objects with a specific status are
determined by the parameters in the [icapserver.actions] section (for the
default group) and [icapserver.actions:<group name>] section (for groups
created by the administrator):
• InfectedAction – action over an infected object that has not been cured
or cannot be cured.
• SuspiciousAction – action over an objects suspected of being infected
with an unknown virus.
• WarningAction – action over an object containing code that resembles a
known virus.
• ErrorAction – action over an object that has been assigned the ERROR
status.
• ProtectedAction – action over a password-protected object.
• CorruptedAction – action over a damaged object.
• CuredAction – action over a disinfected object.
The listed parameters can take the following values:
• skip – allows object transfer.
• deny – prohibits object transfer replacing such object with a
corresponding notification file.
If deny is the action used on an object, then, depending upon the object's status,
it will be replaced with one of the following placeholder files located in the
/opt/kav/5.5/kav4proxy/share/notify: directory:
• object_infected – template containing a notification about detection of an
infected object.
Page 38

38 Kaspersky Anti-Virus for Proxy Server
• object_suspicious – template containing a notification about detection of
an object suspected of being infected with an unknown virus.
• object_warning – template containing a notification about detection of an
object that resembles the code of a known virus.
• object_protected – template containing a notification about detection of
a password-protected object.
• object_error – template containing a notification about detection of an
object, which has caused a scanning error.
• object_corrupted – template containing a notification about detection of
a damaged object.
• object_cured – template containing a notification about detection of an
infected object that has been successfully cured.
Administrators can modify the text of these templates at their discretion including
addition of special macros (see Appendix A.2 on p. 55).
Example
default group:
Solution
privileged user) and specify the following parameter values in the
[icapserver.actions] section:
[icapserver.actions]
CuredAction=skip
ProtectedAction=skip
InfectedAction=deny
SuspiciousAction=deny
WarningAction=deny
ErrorAction=deny
CorruptedAction=deny
: Specify the following actions over scanned objects for the
• allow transfer of the objects that have been assigned the
CURED and PROTECTED status
• prohibit transfer of all other objects.
: to accomplish the task, log in as the root (or any other
5.4. Administrator notifications
Every time when the application performs the deny action over an object
transferred through the proxy, it also runs a special script. The string launching
Page 39

Additional settings of Kaspersky Anti-Virus 39
the script is defined by the NotifyScript parameter in the
[icapserver.notify:<group name>] section of the application configuration file.
Below you can examine a sample notification script and the steps necessary to
configure the application to run the script.
Administrators can use SHELL syntax to create their own custom
scripts, which will be executed every time when the application blocks
an object transfer via proxy after its scanning. Every group created by
the administrator can be assigned its own notification script (please
refer to section 5.1 on p. 34 for details about groups).
In order to configure the application to send notifications about blocked
objects to admin@test.local, perform the following steps
1. Create an executable script file with the following contents:
#!/bin/sh
recipients='admin@test.local'
/usr/lib/sendmail -t -i<<EOT
From: Kaspersky Anti-Virus For Proxy Server
<root@$HOSTNAME>
To: $recipients
Subject: %VERDICT% object requested
Action applied: %ACTION%
Verdict: %VERDICT%
Requested URL: %URL%
Client IP: %CLIENT_ADDR%
Found:
Infected: %VIRUS_LIST%
Cured: %CURED_LIST%
Suspicios: %SUSP_LIST%
Warnings: %WARN_LIST%
This message generated by %PRODUCT% at %DATE% on
$HOSTNAME
EOT
Page 40

40 Kaspersky Anti-Virus for Proxy Server
During script creation you can use special macros, such
as %URL%, %CLIENT_ADDR%, etc. to specify
additional information. Please refer to section A.2 on p. 55
for details on macros.
2. Save the script file and make sure that the kluser user account has
sufficient privileges for its execution.
3. Set the script launch string as the value of the NotiftyScript
parameter. E.g., if the script has been saved to the
/usr/local/bin/notify.sh file, and it should be executed whenever
objects processed according to the default group rules get
blocked, specify the following value for the NotiftyScript parameter
in the [icapserver.notify] section:
[icapserver.notify]
NotifyScript=/usr/local/bin/notify.sh
5.5. Operation modes
Depending upon the status of the license and the anti-virus databases, the
application can function in one of the following modes:
• Basic mode – fully functional mode of application operation. In that mode
the application performs anti-virus scanning of proxy traffic and
disinfection of infected objects (if enabled).
• Operation without updates – the mode used by the application when
the current license expires. In that mode the application performs antivirus scanning of proxy traffic and, if enabled, disinfection of infected
objects using the anti-virus databases current at the moment of license
expiry.
• Unlicensed operation – the mode used by the application in cases when
the license key is not installed or an error has occurred while loading the
information about the current license. In such situation the application
does not perform anti-virus scanning of proxy traffic and applies to all
objects the action defined by the LicenseErrorAction parameter.
• Operation without the anti-virus databases – the mode used by the
application if its anti-virus databases are not installed or if an error has
occurred while loading them. In that mode the application does not
perform anti-virus scanning of proxy traffic and applies to all objects the
action defined by the BasesErrorAction parameter.
Page 41

Additional settings of Kaspersky Anti-Virus 41
5.6. Modes of interaction with proxy
via ICAP
The mode used by Kaspersky Anti-Virus for work with a proxy server is defined
by the AnswerMode parameter, which can take the following values:
• partial – in that mode Kaspersky Anti-Virus sends to proxy parts of the
object being scanned with the frequency determined by the
MaxSendDelayTime parameter for their further transfer to the user. The
last part of an object will only be sent to user when the anti-virus scanning
of the object is complete and only if the resulting status does not mean
that the deny action should be applied to that object. If the deny action is
applied to the object, then the application in that mode does not send a
template-based file to the user (see section 5.3 on p. 36); instead, the
application will initiate disconnection.
The mode described above is convenient when large files are
downloaded. In that case users begin receiving objects before
completion of an anti-virus check because otherwise a user
may terminate connection before he/she receives response
because of a long waiting period.
• complete – in that mode Kaspersky Anti-Virus returns an object to proxy
server only after it is downloaded and tested completely, and provided
that the deny action does not apply to its resulting status. If the deny
action is applied to the object according to the results of anti-virus
scanning, then the application will return to the user a template-based file
instead of the requested object (see section 5.3 on p. 36).
When the complete mode is used, please keep in mind that
after a click on an object in browser the user will not see a
window with an offer to save the object or cancel scanning
until that object is completely downloaded by the proxy server
and scanned by Kaspersky Anti-Virus. User can only cancel
the download by closing the browser window thus terminating
the connection.
5.7. Application statistics logging
Kaspersky Anti-Virus provides two types of statistical information for
administrators:
• Statistics on the results of anti-virus scanning and processing
Page 42

42 Kaspersky Anti-Virus for Proxy Server
• General statistics of application activity.
Statistics of anti-virus processing can be written to a local file or to a network
socket. In order to make the application log its statistics to a local file, specify the
path to that file as the value for the AVStatisticsFile parameter. The
AVStatisticsAddress parameter is intended to specify a network socket.
Every line in the resulting statistics file will contain information about a single
tested object in the following format:
Time Size Verdict Virus_info IP URL
Table 2 contains a summary of all these parameters.
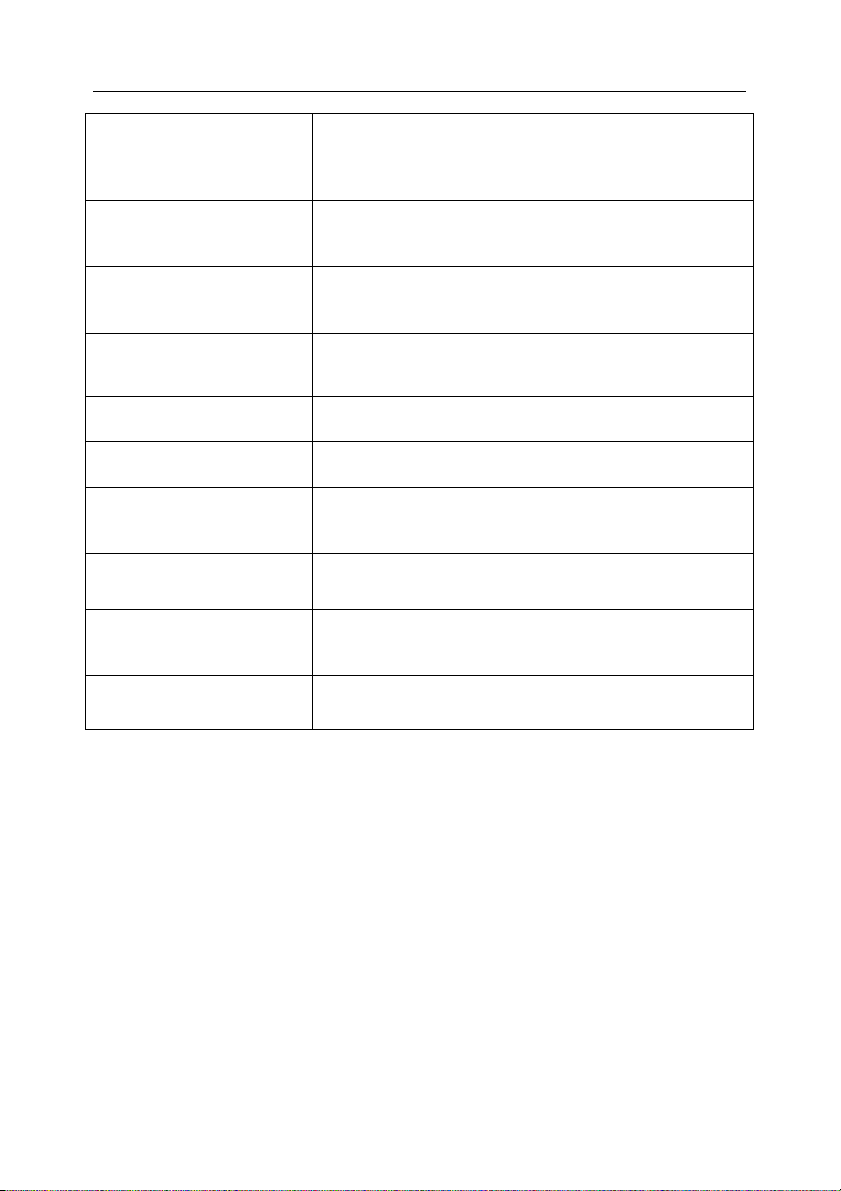
Table 2. Statistics parameters
Alias Meaning
Time Date of object scanning.
Size Object size.
Verdict Status assigned to an object after an anti-
virus check.
Virus_info List of revealed viruses.
IP IP address of the client that has requested
an object.
URL URL of a requested object.
If for some reason output of a report on a processed object is impossible,
information about such object will not be logged.
In addition to the statistics of anti-virus scanning, the application also uses
special counters, which return statistical information about its activity. Counter
values can be output to a file specified as the CounterStatisticsFile parameter
in the application configuration file. The resulting file will contain a log of values
returned by counters described in Table 3.
Table 3. Counters of application activity
Counter
Total_requests
Description
Total number of processed scan requests.
Page 43
Additional settings of Kaspersky Anti-Virus 43
Infected_requests The number of requests, which returned infected,
suspicious objects or objects resembling a known
virus identified during processing.
Protected_requests The number of requests, which returned protected
objects identified during processing.
Error_requests The number of requests, which returned objects
causing processing errors.
Total_traffic
Infected_traffic The total volume of infected traffic (MB).
Traffic_per_min Average MB per minute.
Request_per_min Average number of ICAP requests processed per
Total_connections
Total_processes The total number of running processes working on
Idle_processes
The total volume of processed traffic (MB).
minute.
The number of active connections to ICAP server.
user requests.
The number of idle processes waiting for requests.
5.8. Application reporting
parameters
Results of operations performed by Kaspersky Anti-Virus components are
summarized in a report output to a log file in text format (ReportFileName
parameter in the [icapserver.report] section) or to the system log (syslog). If an
empty string is set as the value of the ReportFileName parameter
(ReportFileName=), no information of application activity will be logged.
The amount of output information can be altered by changing the report detail
level (ReportLevel parameter in the [icapserver.report] section).
Page 44

44 Kaspersky Anti-Virus for Proxy Server
The level of detail is a number that sets the level of verboseness for information
regarding the components’ work. Each subsequent level includes information of
the previous level together with some additional data.
Possible levels of report details are listed in the table 4 below.
Table 4. Levels of report details
Level
Level
name
Level letter
symbol
Meaning
0 Fatal
Errors
1 Errors E Information about other errors
2 Warning W Notifications about errors that may
3 Info,
Notice
F Information about critical errors
only (i.e. errors, which cause
program termination because
some actions cannot be
performed). E.g., component
infection or an error while
initializing or loading databases
and license keys.
including those, which do not
cause termination of components'
activity, for example, information
about an error encountered during
file scanning.
lead to the application shutdown
(license key expiration warning,
out-of-disk-space warning, etc.).
I Important informational
messages, such as whether a
component is running or inactive,
the path to the configuration file,
latest changes in scan area,
database updates, license keys,
statistics summary.
4 Activity A Messages about scanning of files
in accordance with the level of
details defined for the report.
9 Debug D All debug messages.
Page 45

Additional settings of Kaspersky Anti-Virus 45
Information about fatal errors is displayed always, regardless of the report detail
level. The optimal level is level 4, which is also the default level.
Information messages may be subdivided into the following types:
• Messages pertaining to anti-virus checks.
• Messages pertaining to the operation of the application.
The output format for each of the detail levels listed above is as follows:
[DD-MM-YY HH:MM:SS L] STRING
where
DD-MM-YY HH:MM:SS stand for the date and time of record creation in the
format defined by the DateFormat and TimeFormat parameters.
L – letter symbol indicating the selected level of details in report.
STRING – test containing information about an event that has occurred.
E.g., information about the results of anti-virus scan for an object will be logged
in the following format:
[DD-MM-YY HH:MM:SS A] CLIENT_IP URL VERDICT [INFO]
where
DD-MM-YY HH:MM:SS stand for the date and time of record creation in the
format defined by the DateFormat and TimeFormat parameters.
А means the Activity level.
CLIENT_IP – IP address of the client that has requested on object.
URL – URL of the requested object.
VERDICT – object status according to the results of its anti-virus scanning.
INFO – additional information, for instance, name of a detected virus.
5.9. Memory dump creation for
detection of errors
Memory dump files or core files are created during an emergency shutdown of
the application process; they can be used later by experts at Kaspersky Lab to
identify the cause of problems in the operation of Kaspersky Anti-Virus.
Creation of core files is disabled by default, it is only recommended for detection
of problems causing abnormal termination of the application processes.
Page 46

46 Kaspersky Anti-Virus for Proxy Server
In order to enable creation of memory dump files, specify the
/var/log/kav/5.5/kav4proxy/core path as the value for the CorePath parameter
in the [icapserver.path] of the application configuration file.
Make sure that the partition where the
/var/log/kav/5.5/kav4proxy/core directory is located has sufficient free
disk space for storage of core files.
In addition, in FreeBSD-based systems a modification of system kernel
parameters may be necessary. It can be performed by running the following
command as root:
# sysctl -w kern.sugid_coredump=1
Now in case of an emergency shutdown of the application processes a file
containing a dump of its memory will be created in the
/var/log/kav/5.5/kav4proxy/core directory.
As soon as the core files have been used to collect the necessary information,
you are advised to disable their creation and roll back the modifications (if any) to
the system kernel in FreeBSD-based systems:
# sysctl -w kern.sugid_coredump=0
5.10. Work with Internet
broadcasting stations
Anti-virus processing by Kaspersky Anti-Virus of web traffic generated by Internet
radio stations can interrupt the data stream transfer or the proxy server operation
making thus listening to broadcasts via a proxy a bit complicated. In such cases
it is recommended to exclude such traffic from the scope of anti-virus scanning
using the ExcludeMimeType parameter, for example:
[icapserver.filter]
ExcludeMimeType=^audio/mpeg$
ExcludeMimeType=^application/vnd.ms.wms-hdr.asfv1$
ExcludeMimeType=^application/x-mms-framed$
The settings above will exclude from the scope of anti-virus scanning data
streams in MPEG, ASF and Microsoft Windows Media formats. Add to the
excluded MIME types of data streams the format used by the Internet radio
station that you would like to listen to.
Page 47

CHAPTER 6. UNINSTALLING
THE APPLICATION
Depending upon the distribution package selected for installation of the
application, removal of Kaspersky Anti-Virus from a server running Linux will
require one of the following steps:
• To uninstall the application installed from an .rpm package, type the
following in the command line:
# rpm –e <distribution_package_name>
• To uninstall the application installed from a .deb package, type the
following in the command line:
# dpkg –r <distribution_package_name>
In order to remove Kaspersky Anti-Virus from a server running FreeBSD, type
the following in the command line:
# pkg_delete <distribution_package_name>
The procedure removing Kaspersky Anti-Virus runs automatically; it successively
performs the following operations:
1. Removal of the cron task updating the anti-virus databases from the list
of tasks for the kluser user.
2. Restoration of the original settings in the configuration file of Squid proxy
(used before installation of Kaspersky Anti-Virus), and proxy restart.
3. Termination of the application services.
4. Roll-back of the registration for automatic start-up of application services
in the system.
5. Removal of temporary files and directories created while Kaspersky Anti-
Virus was running.
6. Removal of application files: the procedure deletes all directories and
files of the Anti-Virus including the anti-virus databases installed with the
package. The only exception includes reports, configuration files and
backup directory, which will not be deleted.
Page 48

APPENDIX A. APPLICATION
REFERENCE
A.1.
kav4proxy.conf
application
configuration file
This appendix is devoted to a detailed description of the kav4proxy.conf file
containing default settings used immediately after Kaspersky Anti-Virus
installation on a server.
The [path] section contains the parameters that define paths to the directories
essential for the application's functioning:
BasesPath – full path to the directory where the anti-virus databases are
stored.
LicensePath – full path to the directory where the license keys for the
application are stored.
TempPath – full path to the directory where the temporary files of the
application are stored.
The [options] section contains the parameters that define the user and the
group used to run the application:
User – name of the user whose privileges the application uses to run.
Group – name of the group whose privileges the application uses to run.
The [locale] section contains the parameters that define the date and time
format in reports and application statistics:
DateFormat=%d-%m-%Y – date format in application activity report.
TimeFormat=%H:%M:%S – time format in report.
The [icapserver.engine] section contains the parameters of the anti-virus
engine:
UseAVbasesSet=standard|extended – the set of the anti-virus databases
used by the application. The extended set contains, in addition to the
Page 49

Appendix A 49
records of the standard set, the signatures of potentially dangerous
software such as adware, remote administration utilities, etc.
The [icapserver.network] section contains network settings of the application:
ListenAddress – IP address and the port that Kaspersky Anti-Virus uses to
wait for proxy requests sent via ICAP. Default value: 0.0.0.0:1344 (the
application listens on port 1344 using all network interfaces of the
server).
Timeout – network timeout for interaction via ICAP.
The [icapserver.process] section contains advanced settings for the processes
of Kaspersky Anti-Virus:
MaxChildren – maximum number of running child processes working on
requests sent via ICAP.
IdleСhildren – maximum number of running child processes waiting for
requests sent via ICAP.
MaxReqsPerChild – maximum number of requests to scan objects that a
child process can serve. After processing of the specified number of
requests a child process terminates and the application initiates a new
child process.
MaxEnginesPerChild – maximum number of scanning modules used
simultaneously by child processes for anti-virus scanning of objects.
Larger number of scanning modules allows faster anti-virus
scanning of objects. However, if affects server performance.
Please take into account the hardware of your server while
setting the value of this parameter.
The [icapserver.protocol] section contains the settings for interaction between
Kaspersky Anti-Virus and proxy server via ICAP:
AnswerMode=partial|complete – the method of interaction with the proxy.
The partial value means that Kaspersky Anti-Virus will allow transfer of
scanned object's parts to client before the object is downloaded from
the Internet completely and scanned. The complete value means that
Kaspersky Anti-Virus will only allow transfer of a requested object to
client after it is downloaded completely and scanned.
MaxSendDelayTime – time interval (seconds) that determines the
frequency used to send parts of a requested object to client in partial
mode.
Page 50

50 Kaspersky Anti-Virus for Proxy Server
HTTPClientIpField – name of the HTTP field to be used for identification of
client's IP address.
The [icapserver.statistics] section contains the parameters pertaining to the
generation of application statistics:
CounterStatisticsFile – path to the file where the values of statistics
counters will be stored.
AVStatisticsFile – path to the file where anti-virus scanning statistics will be
stored.
AVStatisticsAddress – network socket for logging of the anti-virus
scanning statistics.
The [icapserver.report] section contains the parameters pertaining to report
generation by the application:
ReportFileName – file for a report on application activity.
Buffered=yes|no – buffer mode for recording to the report file. In order to
disable the mode, set no as the parameter value.
ReportLevel – level of details in report.
ShowOk=yes|no – the logging mode for information about objects where
scanning revealed no malicious code.
Append=yes|no – report generation mode in which the report is created
anew each time the application starts. If you wish to add new
information to an existing report instead of overwriting it, set the
parameter value to yes.
Sections described above contain the anti-virus processing parameters
for the default group. Please refer to section 5.1 on p. 34 for details
about creation of your own groups.
The [icapserver.path] section contains parameters that define the paths to
special application files:
PidFile – path to the PID file of the application. Default value:
/var/run/kavicapserver.pid.
CorePath – directory for storage of memory dump files (core files) created in
case of emergency termination of the application. The default empty
value disables creation of core files. To enable memory dump creation,
specify /var/log/kav/5.5/kav4proxy/core as the value for that
parameter.
Page 51

Appendix A 51
The [icapserver.groups] section contains the default group parameters:
Priority – group priority. If request parameters match several groups then
the processing will use the rules of the group with the highest priority.
ClientIP – IP address of the client that has requested an object through
proxy. Objects requested from a specified IP address and located at an
address defined by the URL parameter will be processed using the
rules of this group. The following information can be used to specify the
value for the ClientIP parameter:
• IP addresses
ClientIP=192.168.12.1
• Network addresses
ClientIP=192.168.12.0/24
ClientIP=192.168.12.1/255.255.255.0
Regular expressions are also allowed as the values, e.g.:
ClientIP=^192\.168\.12\..*
- the value will represent all addresses within the 192.168.12.0 –
192.168.12.255 range.
To define different IP addresses, you can specify the ClientIP parameter
several times, for example:
[icapserver.groups]
ClientIP=192.168.20.1/24
ClientIP=192.168.30.1
URL – URL of a requested object. Objects with a specified URL and
requested from an IP address defined by the ClientIP parameter will be
processed using the rules of this group.
While a URL has to be specified, you should enter the
^ . [ $ ( ) | * + ? { \ symbols between the \. escape characters.
Thus, for example, the correct form of the www.example.com
address will look as follows:
URL=www\.example\.com
The notation is compliant with the POSIX Extended Regular
Expression syntax.
Page 52

52 Kaspersky Anti-Virus for Proxy Server
The [icapserver.filter] section contains filtration parameters for the default
group:
ExcludeMimeType – exception mask for filtering by MIME type (regular
expressions can be used). The application will not perform anti-virus
scanning of objects with MIME type, which does not match the specified
mask.
ExcludeURL – exception mask for filtering by URL type (POSIX Extended
Regular Expressions can be used). The application will not perform antivirus scanning of objects with URL which matches the specified mask.
You can define more than one exception mask using masks
with ExcludeURL and ExcludeMimeType if you specify
these parameters several times in a section, for example:
ExcludeURL=www\.example\.com.*
ExcludeURL=www\.localsite\.local.*
MaxScanTime – maximum duration of single object scanning. If an object is
not checked within the specified interval, such object will be assigned
the OK status.
MaxRequestLength – maximum size of the objects to be scanned.
The [icapserver.engine.options] section contains the anti-virus scanning
parameters for the default group:
ScanPacked=yes|no – instruction to scan packed files. To disable this
mode, set the parameter to no.
ScanArchives=yes|no – instruction to check archived objects. To disable
this mode, set the parameter to no.
ScanMailBases=yes|no – instruction to scan e-mail databases (requested
or transferred through proxy server). To disable this mode, set the
parameter to no.
ScanMailPlain=yes|no – instruction to scan databases of mail messages in
plain text format (requested or transferred through proxy server). To
disable this mode, set the parameter to no.
UseHeuristic=yes|no – instruction to use heuristic analyzer during anti-
virus scanning. To disable this mode, set the parameter to no.
Cure=yes|no – instruction to cure infected objects. To disable this mode,
set the parameter to no.
Page 53

Appendix A 53
The [icapserver.actions] section contains the settings for actions over scanned
objects for the default group:
CuredAction – action over disinfected objects.
InfectedAction – action over infected objects.
SuspiciousAction – action over suspicious objects.
WarningAction – action over an object resembling a known virus.
ErrorAction – action over an object, which has caused a scanning error.
ProtectedAction – action over password-protected objects.
CorruptedAction – action over damaged objects.
LicenseErrorAction – action over scanned objects if the application has
failed to load the license key information.
BasesErrorAction – action performed over objects in cases, when the
application fails to load the anti-virus databases.
The [icapserver.notify] section contains notification parameters for the default
group:
NotifyTemplateDir – directory where the notification templates are stored.
NotifyScript – script used by the application to notify the administrator
about objects prohibited for transfer through the proxy server.
The [updater.path] section contains the paths to directories and files necessary
for the functioning of the keepup2date component:
BackUpPath – path to the directory where an archive of the anti-virus databases
is preserved during their update. This is a mandatory parameter.
UploadPatchPath – path to the directory containing application patches.
PidFile – path to PID file. It is used to prevent simultaneous launch of several
instances of the keepup2date component. If the parameter is missing, the
PID file will not be created. Consequently, no checks for other running
instances of the component will be performed.
AVBasesTestPath – full path to the avbasestest utility validating the anti-virus
databases. The application uses it immediately after downloading of
updates. Only if the received updates are intact, they will be copied from a
temporary folder to the storage directory. If this parameter is not specified,
then during an update the updater will output to the console and log file a
message informing about inability to check the downloaded anti-virus
databases; the updates will be installed then without further validation.
Page 54

54 Kaspersky Anti-Virus for Proxy Server
The avbasestest utility starts automatically, it does not require
user participation.
The [updater.options] section contains various parameters of the keepup2date
component:
KeepSilent=yes|no – the mode used for output of component messages to the
console. When the parameter is set to yes the component does not output
reports to the console. Default value: no.
PostUpdateCmd – command performed immediately after an update of the anti-
virus databases. The value specified in the configuration file included into
the product package forces the application to reload the updated anti-virus
databases automatically. Modification of this parameter is not
recommended.
UseUpdateServerUrl=yes|no – parameter, which defines whether the updater
will use for its purposes the address defined by the UpdateServerUrl
parameter. Default value: no.
UseUpdateServerUrlOnly=yes|no – parameter, which defines whether the
application will use for updates the address defined by the UpdateServerUrl
parameter only. When set to no, a failed attempt to update databases using
the UpdateServerUrl address as the source will be followed by an attempt
to use another address from the list of update servers. Default value: no.
UpdateServerUrl=http://url/ | ftp://url/ | /local_path/ – source address for
updating of the anti-virus databases.
RegionSettings – the region where the user is located. It is used to select an
update server of Kaspersky Lab, which is more convenient for downloading
of updates to the anti-virus databases. Default value: Russia. In order to
receive a list of all regions, run the keepup2date utility with the –s command
line option.
ConnectTimeout – timeout (seconds) for network operations during updates of
the anti-virus databases. Default value: 30.
UseProxy=yes|no – the mode of proxy use during connection with an update
server of Kaspersky Lab. When set to no, proxy server will not be used. If
the parameter is set to yes, the component will use the proxy address
defined by the ProxyAddress parameter. If the ProxyAddress parameter
value is undefined, then the http_proxy environment variable will be used. If
the environment variable is not defined, proxy server will not be used.
ProxyAddress – address of the proxy server used for connection. This
parameter is defined as
http://username:password@url:port. Username
and/or password may be missing in a proxy address. If no address is
specified, its value will be taken from the http_proxy environment variable.
Page 55

Appendix A 55
PassiveFtp=yes|no – the parameter determines the use of passive FTP mode.
Default value: no.
The [updater.report] section contains the settings for output of reports by the
keepup2date component:
ReportFilename – name of the file used for logging of a report on the
component's activity.
ReportLevel=0|1|2|3|4|9 – level of details in the report on the component's
activity (0 – Fatal, 1 – Error, 2 – Warning, 3 – Info, 4 – Activity,
9 – Debug). Default value: 4.
Append=yes|no – instruction to append a report to the end of an existing report
file. When the parameter is set to no, previous file contents will be deleted
after logging to it. Default value: yes.
A.2. Macros
Kaspersky Anti-Virus allows using special macros in template-based placeholder
files sent to users instead of blocked objects (see section 5.3 on p. 36) and in the
text of the notification script (the NotifyScript parameter). Table 5 contains a
description of these macros.
Table 5. Macros
Macro syntax Description
%VIRUS_LIST% List of viruses that an object is infected with.
%WARN_LIST% List of objects containing code that
resembles a known virus.
%SUSP_LIST% List of objects suspected of infection with an
unknown virus.
%CURED_LIST% List of removed viruses.
%CLIENT_ADDR% IP address of the client computer that has
requested an object.
%URL% Requested object URL
Page 56

56 Kaspersky Anti-Virus for Proxy Server
%ACTION% Action performed on an object.
%VERDICT% Object status.
%PRODUCT% Product description.
%DATE% Time of message creation.
A.3.
30
65
66
70
0
kavicapserver
Fatal system error.
Error loading the configuration file (file not found).
Error in the configuration file or command line parameters.
The component executable file is corrupted.
No errors detected at component start.
return codes
A.4. Command line options for
licensemanager
Help options
-h
Command line options for managing license keys
Display on the console reference information about
the command line options supported by the
component and exit.
-s
-c (С) <path_to_file> Use the alternative configuration file <path_to_file>.
Output information about all installed license keys to
the console.
Page 57

Appendix A 57
-k
<key_file_name>
-a <path_to_file>
-d <a|r>
A.5.
The licensemanager component may return any of the following codes while
running:
0
30
64
65
66
70
Licensemanager
The component has successfully completed its operation.
Fatal system error.
Licensing error.
Error reading the configuration file.
Error in command line options.
The component executable file is corrupted.
Output to the console information about the license
key.
Install a license key.
Delete the current/additional key.
return codes
A.6.
Keepup2date
options
Help options
-h
-v
-s
command line
Display on the console reference information about the command line
options supported by the component and exit.
Display the application version on the console and exit.
Display a list of update servers with information about their respective
regions.
Page 58

58 Kaspersky Anti-Virus for Proxy Server
Update options
-c <path_to_file> Use the alternative configuration file <path_to_file>.
-u <directory> Copy the application update to the local <directory>.
Within the specified directory, the utility will reproduce a
structure identical to the internal structure of an update
server, thus enabling local computers to update from
that directory.
-x <directory>
Copy updates for all products of Kaspersky Lab to the
local <directory>. Within the specified directory, the
utility will reproduce a structure identical to the internal
structure of an update server, thus enabling local
computers to update from that directory.
-b <path> When updating, create in the <path> directory a
backup copy of the anti-virus databases being updated.
-t <path> Use the <path> directory to store temporary files.
-r
Cancel the last update. Updated databases will be
replaced by their previous versions.
-k
Disable execution of the command defined by the
PostUpdateCmd parameter.
-d <path_to_file>
-g <url>
Use the specified PID file.
Use the server with the specified URL as the source of
updates.
Report generation options
-l <path_to_file> Log work results in file <path_to_file>.
-q
-e
Disable output of messages about the operation of the
utility.
Output fatal error messages only.
Page 59
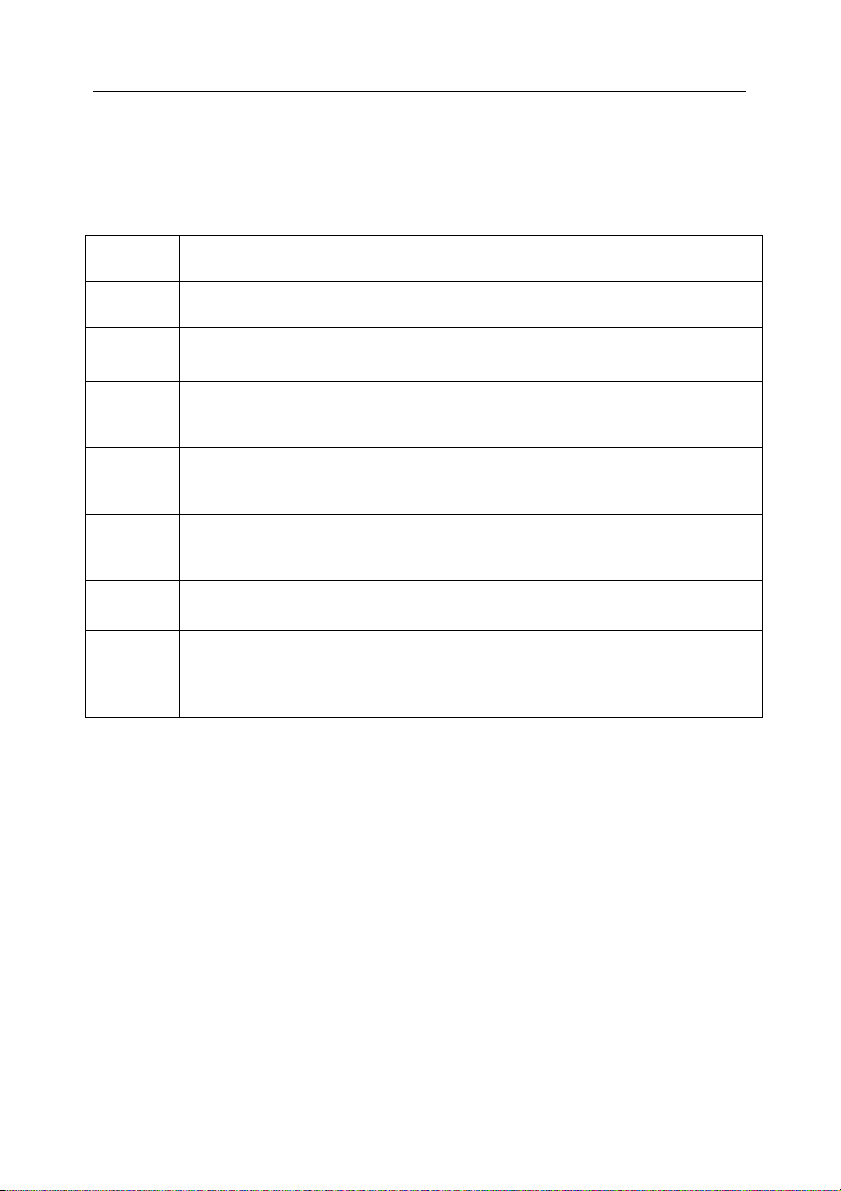
Appendix A 59
A.7.
The keepup2date component may return any of the following codes while
running:
0
1
10
12
30 The PostUpdaterCmd command could not be executed after the
60
75
128 +
signal
code
Keepup2date
The anti-virus databases do not need an update.
The anti-virus databases were updated successfully.
A fatal error occurred; updating was interrupted.
An error while rolling back to the previous version of the anti-virus
databases. Rollback has been interrupted.
databases were updated.
License information is missing or no license key was found using the
path specified in the configuration file.
The configuration file cannot be loaded or contains errors.
Application has exited upon a signal with the corresponding code.
return codes
Page 60

APPENDIX B. KASPERSKY LAB
Founded in 1997, Kaspersky Lab has become a recognized leader in information
security technologies. It produces a wide range of data security software and
delivers high-performance, comprehensive solutions to protect computers and
networks against all types of malicious programs, unsolicited and unwanted email messages, and hacker attacks.
Kaspersky Lab is an international company. Headquartered in the Russian
Federation, the company has representative offices in the United Kingdom,
France, Germany, Japan, USA (CA), the Benelux countries, China, Poland, and
Romania. A new company department, the European Anti-Virus Research
Centre, has recently been established in France. Kaspersky Lab's partner
network incorporates more than 500 companies worldwide.
Today, Kaspersky Lab employs more than 450 specialists, each of whom is
proficient in anti-virus technologies, with 10 of them holding M.B.A. degrees, 16
holding Ph.Ds, and senior experts holding membership in the Computer AntiVirus Researchers Organization (CARO).
Kaspersky Lab offers best-of-breed security solutions, based on its unique
experience and knowledge, gained in over 14 years of fighting computer viruses.
A thorough analysis of computer virus activities enables the company to deliver
comprehensive protection from current and future threats. Resistance to future
attacks is the basic policy implemented in all Kaspersky Lab's products. At all
times, the company’s products remain at least one step ahead of many other
vendors in delivering extensive anti-virus coverage for home users and corporate
customers alike.
Years of hard work have made the company one of the top security software
manufacturers. Kaspersky Lab was one of the first businesses of its kind to
develop the highest standards for anti-virus defense. The company’s flagship
product, Kaspersky Anti-Virus, provides full-scale protection for all tiers of a
network, including workstations, file servers, mail systems, firewalls, Internet
gateways, and hand-held computers. Its convenient and easy-to-use
management tools ensure advanced automation for rapid virus protection across
an enterprise. Many well-known manufacturers use the Kaspersky Anti-Virus
kernel, including Nokia ICG (USA), F-Secure (Finland), Aladdin (Israel), Sybari
(USA), G Data (Germany), Deerfield (USA), Alt-N (USA), Microworld (India) and
BorderWare (Canada).
Kaspersky Lab's customers benefit from a wide range of additional services that
ensure both stable operation of the company's products, and compliance with
specific business requirements. Kaspersky Lab's anti-virus database is updated
every hour. The company provides its customers with a 24-hour technical
support service, which is available in several languages to accommodate its
international clientele.
Page 61

Appendix B 61
B.1. Other Kaspersky Lab Products
Kaspersky Anti-Virus® Personal
®
Kaspersky Anti-Virus
protection to personal computers running Microsoft Windows 98/ME or Microsoft
Windows 2000/NT/XP against all known viruses, including potentially dangerous
software. Kaspersky Anti-Virus Personal provides real-time monitoring of all
sources of virus intrusion - e-mail, Internet, floppy disks, CD, etc. The unique
system of heuristic data analysis allows efficient neutralization of yet unknown
viruses. This application can work in the following modes (that can be used
separately or jointly):
• Real-time computer protection - anti-virus scanning of all objects run,
opened on or saved to the user’s computer.
• On-demand computer scan - scanning and disinfection of the entire
user’s computer or of individual disks, files or folders. You can start such
scan manually or configure an automatic scheduled scan.
Kaspersky Anti-Virus
scanned during a previous scan and have not changed since then not only when
performing real-time protection, but also during an on-demand scan. This feature
considerably increases the speed of the program’s operation.
The application creates a reliable barrier against viruses when they attempt to
intrude your computer via e-mail. Kaspersky Anti-Virus
automatic scan and disinfection of all incoming and outgoing mail sent or
received using POP3 and STMP protocols and provides highly efficient detection
of viruses in mail databases.
The application supports over 700 formats of archived and compressed files and
provides automatic scanning of their content as well as removal of malicious
code from ZIP, CAB, RAR, ARJ, LHA and ICE archives.
Configuring the application is made simple and intuitive due to the possibility to
select one of three preset protection levels: Maximum Protection,
Recommended or High Speed.
The anti-virus database is updated every hour and its delivery to your computer
is guaranteed even when your computer gets temporarily disconnected from the
Internet or the connection has to be changed.
Kaspersky Anti-Virus
This package has been designed to deliver comprehensive anti-virus protection
to home computers running Microsoft Windows 98/ME, Microsoft Windows
2000/NT, Microsoft Windows XP as well as MS Office applications. Kaspersky
Anti-Virus Personal Pro includes an easy-to-use application for automatic
Personal has been designed to provide anti-virus
®
Personal does not re-scan objects that had already been
®
Personal performs
®
Personal Pro
Page 62

62 Kaspersky Anti-Virus for Proxy Server
retrieval of daily updates for the anti-virus database and the program modules. A
unique second-generation heuristic analyzer efficiently detects unknown viruses.
A simple and convenient interface allows users to configure the program quickly
making work with it easier than ever.
®
Kaspersky Anti-Virus
Personal Pro has the following features:
• On-demand scan of local disks.
• Real-time automatic protection of all accessed files from viruses.
• Mail Filter automatically scans and disinfects all incoming and outgoing
mail for any mail client that uses POP3 and SMTP protocols and
effectively detects viruses in mail databases.
• Behavior blocker that provides maximum protection of MS Office
applications against viruses.
• Archive scanning – Kaspersky Anti-Virus recognizes over 900 formats of
archived and compressed files and ensures automatic anti-virus scanning
of their content and removal of malicious code from files within ZIP, CAB,
RAR, ARJ, LHA and ICE archives.
Kaspersky
Kaspersky
®
Anti-Hacker
®
Anti-Hacker is a personal firewall that is designed to safeguard a
computer running any Microsoft Windows operating system. It protects your
computer against unauthorized access and external hacker attacks from either
the Internet or the local network.
®
Kaspersky
running on your machine. When it detects a suspicious action, Kaspersky
Anti-Hacker monitors the TCP/IP network activity of all applications
®
AntiHacker blocks the suspicious application from accessing the network. This helps
ensure enhanced privacy and 100% security of confidential data stored on your
computer.
The product’s SmartStealth™ technology prevents hackers from detecting your
computer from the outside. In this stealthy mode, the application works
seamlessly to keep your computer protected while you are on the Web. The
application provides conventional transparency and accessibility of information.
Kaspersky
®
Anti-Hacker also blocks most common network hacker attacks and
monitors attempts to scan computer ports.
Configuration of the application is simply a matter of choosing one of five security
levels. By default, the application starts in self-learning mode, which will
automatically configure your security system depending on your responses to
various events. This makes your personal guard adjustable to your specific
preferences and your particular needs.
Page 63

Appendix B 63
Kaspersky® Personal Security Suite
Kaspersky® Personal Security Suite is a software suite designed for organizing
comprehensive protection of personal computers running Microsoft Windows.
The suite prevents malicious and potentially dangerous programs from
penetrating through any possible data sources and protects you from
unauthorized attempts to access your computer’s data, as well as blocking spam.
Kaspersky Personal Security Suite has the following features:
• anti-virus protection of data saved on your computer
• protection against spam for users of Microsoft Office Outlook and
Microsoft Outlook Express
• protection of your computer from unauthorized access, and also from
network hacker attacks from your LAN or the Internet.
Kaspersky Lab News Agent
The News Agent is intended for timely delivery of news published by Kaspersky
Lab, for notifications about the current status of virus activity and fresh news. The
program reads the list of available news channels and their content from news
server of Kaspersky Lab with specified frequency.
The product performs the following functions:
• It visualizes in the system tray the current status of virus activity.
• The product allows the users to subscribe and unsubscribe from news
channels.
• It retrieves news from each subscribed channel with the specified
frequency and notifies about fresh news.
• It allows reviewing news on the subscribed channels.
• It allows reviewing the list of channels and their status.
• It allows opening pages with news details in your browser.
News Agent is a stand-alone Microsoft Windows application, which can be used
independently or may be bundled with various integrated solutions offered by
Kaspersky Lab Ltd.
®
Kaspersky
OnLine Scanner
The program is a free service offered to the visitors of Kaspersky Lab's corporate
website. The service allows an efficient online anti-virus scan of your computer.
Kaspersky OnLine Scanner runs within your web browser using Microsoft
ActiveX
®
technology. Thus, users can quickly test their computers in case of a
slightest suspicion of malicious infection. Using the service, visitors can:
Page 64

64 Kaspersky Anti-Virus for Proxy Server
• Exclude archives and e-mail databases from scanning.
• Select standard/extended anti-virus databases for scanning.
• Save a report on the scanning results in txt or html formats.
®
Kaspersky
OnLine Scanner Pro
The program is a subscription service offered to the visitors of Kaspersky Lab's
corporate website. The service allows an efficient online anti-virus scan of your
computer and disinfection of dangerous files. Kaspersky OnLine Scanner Pro
runs within your web browser using Microsoft ActiveX
®
technology. Using the
service, visitors can:
• Exclude archives and e-mail databases from scanning.
• Select standard/extended anti-virus databases for scanning.
• Save a report on the scanning results in txt or html formats.
®
Kaspersky Anti-Virus
6.0
Kaspersky Anti-Virus 6.0 is designed to safeguard personal computers against
malicious software as an optimal combination of conventional methods of antivirus protection and new proactive technologies.
The program provides for complex anti-virus checks including:
• Anti-virus scanning of e-mail traffic on the level of data transmission
protocol (POP3, IMAP and NNTP for incoming mail and SMTP for
outgoing messages) irrespectively of the mail client being used as well
as disinfection of e-mail databases.
• Real-time anti-virus scanning of Internet traffic transferred via HTTP.
• Anti-virus scanning of individual files, directories or drives. In addition, a
preset scan task can be used to initiate anti-virus analysis exclusively
for critical areas of the operating system and start-up objects of
Microsoft Windows.
Proactive protection offers the following features:
• Control of changes within file system. The program allows users to
create a list of applications, which it will control on a per component basis.
It helps protect application integrity against the influence of malicious
software.
• Monitoring of processes in random-access memory. Kaspersky Anti-
Virus 6.0 in a timely manner notifies users whenever it detects dangerous,
suspicious or hidden processes or in case when unauthorized changes in
standard processes occur.
Page 65

Appendix B 65
• Monitoring of changes in OS registry due to internal system registry
control.
• Blocking of dangerous VBA macros in Microsoft Office documents.
• System restoration after malicious spyware influence accomplished due
to recording of all changes in the registry and computer file system and an
opportunity to perform their roll-back at user's discretion.
Kaspersky
Kaspersky
®
Internet Security 6.0
®
Internet Security 6.0 is an integrated solution for protection of
personal computers against the main information-related threats, i.e. viruses,
hackers, spam and spyware. A common user interface allows configuration and
management of all solution components.
The anti-virus protection feature includes:
• Anti-virus scanning of e-mail traffic on the level of data transmission
protocol (POP3, IMAP and NNTP for incoming mail and SMTP for
outgoing messages) irrespectively of the mail client being used. The
program includes plug-ins for popular e-mail clients (Microsoft Office
Outlook, Microsoft Outlook Express and The Bat!) and supports
disinfection of their e-mail databases.
• Real-time anti-virus scanning of Internet traffic transferred via HTTP.
• File system protection: anti-virus scanning of individual files, directories
or drives. In addition, the application can perform anti-virus analysis
exclusively for critical areas of the operating system and start-up objects
of Microsoft Windows.
• Proactive protection: the program performs constant monitoring of
application activity and processes running in random-access memory
preventing dangerous changes to the file system and registry, and
restores the system after malicious influence.
Protection against Internet-fraud is guaranteed owing to the ability to
recognize phishing attacks, which helps prevent confidential data leaks (first of
all, your passwords, bank account and credit card numbers), and block execution
of dangerous scripts on web pages, pop-up windows and advertisement
banners. The feature blocking charged phone calls helps identify software that
attempts to use your modem for hidden unauthorized connection to paid phone
services and prevents such activity.
Kaspersky
®
Internet Security 6.0 registers attempts to scan the ports of your
computer, which frequently precede network attacks, and successfully defends
against typical hacker attacks. The program uses defined rules as a basis for
control over all network transactions tracking all incoming and outgoing data
packets. Stealth mode (owing to the SmartStealth™ technology) prevents
Page 66

66 Kaspersky Anti-Virus for Proxy Server
computer detection from outside. When you switch into that mode, the system
will block all network activity except for a few transactions allowed in userdefined rules.
The program employs complex approach to anti-spam filtering of incoming e-mail
messages:
• Verification against black and white lists of recipients (including addresses
of phishing sites).
• Inspection of phrases in message body.
• Analysis of message text using a self-learning algorithm.
• Recognition of spam sent in image files.
Kaspersky
Kaspersky
®
Security for PDA
®
Security for PDA provides reliable anti-virus protection for data
saved on various types of hand-held computers and smartphones. The program
includes an optimal set of anti-virus defense tools:
• anti-virus scanner that scans information (saved both in internal memory
of PDA and smartphones or on memory cards of any type) on user
demand;
• anti-virus monitor to intercept viruses in files that are either copied from
other handhelds or are transferred using HotSync™ technology.
Kaspersky
intrusion by
cards
®
Security for PDA protects your handheld (PDA) from unauthorized
encrypting both access to the device and data stored on memory
.
Kaspersky Anti-Virus® Business Optimal
This package provides a unique configurable security solution for small- and
medium-sized corporate networks.
®
Kaspersky Anti-Virus
protection
1
for:
Business Optimal guarantees full-scale anti-virus
• Workstations running Microsoft Windows 98/ME, Microsoft Windows
NT/2000/XP Workstation and Linux.
• File servers running Microsoft Windows NT 4.0 Server, Microsoft
Windows 2000/2003 Server/Advanced Server, Microsoft Windows 2003
Server, Novell Netware, FreeBSD and OpenBSD, Linux, Samba Servers.
1
Depending on the type of distribution kit.
Page 67

Appendix B 67
• E-mail systems including Microsoft Exchange 2000/2003, Lotus
Notes/Domino, Postfix, Exim, Sendmail, and Qmail.
• Internet gateways: CheckPoint Firewall –1; Microsoft ISA Server 2000
Standard Edition.
The Kaspersky Anti-Virus
®
Business Optimal distribution kit includes Kaspersky®
Administration Kit, a unique tool for automated deployment and administration.
You are free to choose from any of these anti-virus applications, according to the
operating systems and applications you use.
Kaspersky
®
Corporate Suite
This package provides corporate networks of any size and complexity with
comprehensive, scalable anti-virus protection. The package components have
been developed to protect every tier of a corporate network, even in mixed
computer environments. Kaspersky
®
Corporate Suite supports the majority of
operating systems and applications installed across an enterprise. All package
components are managed from one console and have a unified user interface.
Kaspersky
®
Corporate Suite delivers a reliable, high-performance protection
system that is fully compatible with the specific needs of your network
configuration.
Kaspersky® Corporate Suite provides comprehensive anti-virus protection for:
• Workstations running Microsoft Windows 98/ME, Microsoft Windows
NT/2000/XP Workstation and Linux;
• File servers running Microsoft Windows NT 4.0 Server, Microsoft
Windows 2000, 2003 Server/Advanced Server, Novell Netware,
FreeBSD, OpenBSD, Linux and Samba Servers;
• E-mail systems, including Microsoft Exchange Server 2000/2003, Lotus
Notes/Domino, Sendmail, Postfix, Exim and Qmail;
• Internet gateways: CheckPoint Firewall –1; Microsoft ISA Server 2004
Enterprise Edition;
• Hand-held computers (PDAs), running Microsoft Windows CE and Palm
OS, and also smartphones running Microsoft Windows Mobile 2003 for
Smartphone and Microsoft Smartphone 2002.
The Kaspersky
®
Corporate Suite distribution kit includes Kaspersky®
Administration Kit, a unique tool for automated deployment and administration.
You are free to choose from any of these anti-virus applications, according to the
operating systems and applications you use.
Page 68

68 Kaspersky Anti-Virus for Proxy Server
Kaspersky® Anti-Spam
Kaspersky® Anti-Spam is a cutting-edge software suite that is designed to help
organizations with small- and medium-sized networks wage war against the
onslaught of unsolicited e-mail messages (spam). The product combines the
revolutionary technology of linguistic analysis with modern methods of e-mail
filtration, including DNS Black Lists and formal letter features. Its unique
combination of services allows users to identify and wipe out up to 95% of
unwanted traffic.
Installed at the entrance to a network, where it monitors incoming e-mail traffic
streams for spam, Kaspersky
®
Anti-Spam acts as a barrier to unsolicited e-mail.
The product is compatible with any mail system and can be installed on either an
existing mail server or a dedicated one.
Kaspersky® Anti-Spam’s high performance is ensured by daily updates to the
content filtration database adding samples provided by the Company’s linguistic
laboratory specialists. Databases are updated every 20 minutes.
Kaspersky
Kaspersky
®
SMTP Gateway
®
SMTP-Gateway for Linux/Unix is a solution designed for anti-virus
processing of e-mail transmitted via SMTP. The application contains a number of
additional tools for filtering e-mail traffic by name and MIME type of attachments
and a number of tools reducing the load on the mail system and preventing
hacker attacks. DNS Black List support provides protection against e-mails
coming from servers entered in these lists as sources distributing unwanted email (spam).
Kaspersky Security
®
for Microsoft Exchange 2003
Kaspersky Security for Microsoft Exchange performs anti-virus processing of
incoming and outgoing mail messages as well as messages stored at the server,
including letters in public folders and filters out unsolicited correspondence using
"smart" spam recognition techniques in combination with Microsoft technologies.
The application scans all messages arriving at an Exchange Server via SMTP
protocol checking them for the presence of viruses using Kaspersky Lab's antivirus technologies and for the presence of SPAM attributes. It filters out spam
based on formal attributes (mail address, IP address, letter size, heading) and
analyzes the content of messages and of their attachments using "smart'
technologies, including unique graphic signatures for identifying graphic SPAM.
The application scans both the message body and the attached files.
Kaspersky® Mail Gateway
Kaspersky Mail Gateway is a comprehensive solution that provides complete
protection for users of mail systems. This application installed between the
corporate network and the Internet scans all components of e-mail messages for
Page 69

Appendix B 69
the presence of viruses and other malware (Spyware, Adware, etc.) and
performs centralized anti-spam filtration of e-mail stream. This solution also
includes some additional mail traffic filtration features.
B.2. Contact Us
If you have any questions, comments, or suggestions, please refer them to one
of our distributors or directly to Kaspersky Lab. We will be glad to assist you in
any matters related to our product by phone or via e-mail. Rest assured that all of
your recommendations and suggestions will be thoroughly reviewed and
considered.
Technical
support
General
information
Please find the technical support information at
http://www.kaspersky.com/supportinter.html
Helpdesk: www.kaspersky.com/helpdesk.html
WWW: http://www.kaspersky.com
http://www.viruslist.com
E-mail: info@kaspersky.com
Page 70

APPENDIX C. LICENSE
AGREEMENT
End User License Agreement
NOTICE TO ALL USERS: CAREFULLY READ THE FOLLOWING
LEGAL AGREEMENT ("AGREEMENT") FOR THE LICENSE OF
SPECIFIED SOFTWARE ("SOFTWARE") PRODUCED BY KASPERSKY
LAB ("KASPERSKY LAB").
IF YOU HAVE PURCHASED THIS SOFTWARE VIA THE INTERNET BY
CLICKING THE ACCEPT BUTTON, YOU (EITHER AN INDIVIDUAL OR
A SINGLE LEGAL ENTITY) CONSENT TO BE BOUND BY AND
BECOME PARTY TO THIS AGREEMENT. IF YOU DO NOT AGREE TO
ALL OF THE TERMS OF THIS AGREEMENT, CLICK THE BUTTON
THAT INDICATES THAT YOU DO NOT ACCEPT THE TERMS OF THIS
AGREEMENT, AND DO NOT INSTALL THE SOFTWARE.
IF YOU HAVE PURCHASED THIS SOFTWARE ON A PHYSICAL
MEDIUM, HAVING BROKEN THE CD'S SLEEVE YOU (EITHER AN
INDIVIDUAL OR A SINGLE ENTITY) ARE CONSENTING TO BE
BOUND BY THIS AGREEMENT. IF YOU DO NOT AGREE TO ALL OF
THE TERMS OF THIS AGREEMENT DO NOT BREAK THE CD's
SLEEVE, DOWNLOAD, INSTALL OR USE THIS SOFTWARE.
IN ACCORDANCE WITH THE LEGISLATION, REGARDING
KASPERSKY SOFTWARE INTENDED FOR INDIVIDUAL CONSUMERS
(KASPERSKY ANTI-VIRUS PERSONAL, KASPERSKY ANTI-VIRUS
PERSONAL PRO, KASPERSKY ANTI-HACKER, KASPERSKY ANTISPAM PERSONAL, KASPERSKY SECURITY SUITE PERSONAL,
KASPERSKY SECURITY FOR PDA) PURCHASED ON LINE FROM
THE KASPERSKY LAB INTERNET WEB SITE, CUSTOMER SHALL
HAVE A PERIOD OF 7 WORKING DAYS AS FROM THE DELIVERY OF
PRODUCT TO MAKE RETURN OF IT TO THE MERCHANT FOR
EXCHANGE OR REFUND, PROVIDED THE SOFTWARE IS NOT
UNSEALED.
REGARDING THE KASPERSKY SOFTWARE INTENDED FOR
INDIVIDUAL CONSUMERS (KASPERSKY ANTI-VIRUS PERSONAL,
KASPERSKY ANTI-VIRUS PERSONAL PRO, KASPERSKY ANTIHACKER, KASPERSKY ANTI-SPAM PERSONAL, KASPERSKY
SECURITY SUITE PERSONAL, KASPERSKY SECURITY FOR PDA)
NOT PURCHASED ONLINE VIA INTERNET, THIS SOFTWARE
NEITHER WILL BE RETURNED NOR EXCHANGED EXCEPT FOR
CONTRARY PROVISIONS FROM THE PARTNER WHO SELLS THE
Page 71

Appendix C 71
PRODUCT. IN THIS CASE, KASPERSKY LAB WILL NOT BE HELD BY
THE PARTNER'S CLAUSES.
THE RIGHT TO RETURN AND REFUND EXTENDS ONLY TO THE
ORIGINAL PURCHASER.
All references to "Software" herein shall be deemed to include the software
activation key ("Key Identification File") with which you will be provided by
Kaspersky Lab as part of the Software.
1. License Grant. Subject to the payment of the applicable license fees, and
subject to the terms and conditions of this Agreement, Kaspersky Lab hereby
grants you the non-exclusive, non-transferable right to use one copy of the
specified version of the Software and the accompanying documentation (the
"Documentation") for the term of this Agreement solely for your own internal
business purposes. You may install one copy of the Software on one computer,
workstation, personal digital assistant, or other electronic device for which the
Software was designed (each a "Client Device"). If the Software is licensed as a
suite or bundle with more than one specified Software product, this license
applies to all such specified Software products, subject to any restrictions or
usage terms specified on the applicable price list or product packaging that apply
to any such Software products individually.
1.1 Use. The Software is licensed as a single product; it may not be used on
more than one Client Device or by more than one user at a time, except as set
forth in this Section.
1.1.1 The Software is "in use" on a Client Device when it is loaded into the
temporary memory (i.e., random-access memory or RAM) or installed into the
permanent memory (e.g., hard disk, CD-ROM, or other storage device) of that
Client Device. This license authorizes you to make only as many back-up copies
of the Software as are necessary for its lawful use and solely for back-up
purposes, provided that all such copies contain all of the Software's proprietary
notices. You shall maintain records of the number and location of all copies of
the Software and Documentation and will take all reasonable precautions to
protect the Software from unauthorized copying or use.
1.1.2 If you sell the Client Device on which the Software is installed, you will
ensure that all copies of the Software have been previously deleted.
1.1.3 You shall not decompile, reverse engineer, disassemble or otherwise
reduce any part of this Software to a humanly readable form nor permit any third
party to do so. The interface information necessary to achieve interoperability of
the Software with independently created computer programs will be provided by
Kaspersky Lab by request on payment of its reasonable costs and expenses for
procuring and supplying such information. In the event that Kaspersky Lab
notifies you that it does not intend to make such information available for any
reason, including (without limitation) costs, you shall be permitted to take such
Page 72

72 Kaspersky Anti-Virus for Proxy Server
steps to achieve interoperability, provided that you only reverse engineer or
decompile the Software to the extent permitted by law.
1.1.4 You shall not make error corrections to, or otherwise modify, adapt, or
translate the Software, nor create derivative works of the Software, nor permit
any third party to copy the Software (other than as expressly permitted herein).
1.1.5 You shall not rent, lease or lend the Software to any other person, nor
transfer or sub-license your license rights to any other person.
1.1.6 You shall not use this Software in automatic, semi-automatic or manual
tools designed to create virus signatures, virus detection routines, any other data
or code for detecting malicious code or data.
1.2 Server-Mode Use. You may use the Software on a Client Device or on a
server ("Server") within a multi-user or networked environment ("Server-Mode")
only if such use is permitted in the applicable price list or product packaging for
the Software. A separate license is required for each Client Device or "seat" that
may connect to the Server at any time, regardless of whether such licensed
Client Devices or seats are concurrently connected to or actually accessing or
using the Software. Use of software or hardware that reduces the number of
Client Devices or seats directly accessing or utilizing the Software (e.g.,
"multiplexing" or "pooling" software or hardware) does not reduce the number of
licenses required (i.e., the required number of licenses would equal the number
of distinct inputs to the multiplexing or pooling software or hardware "front end").
If the number of Client Devices or seats that can connect to the Software
exceeds the number of licenses you have obtained, then you must have a
reasonable mechanism in place to ensure that your use of the Software does not
exceed the use limits specified for the license you have obtained. This license
authorizes you to make or download such copies of the Documentation for each
Client Device or seat that is licensed as are necessary for its lawful use, provided
that each such copy contains all of the Documentation’s proprietary notices.
1.3 Volume Licenses. If the Software is licensed with volume license terms
specified in the applicable product invoicing or packaging for the Software, you
may make, use or install as many additional copies of the Software on the
number of Client Devices as the volume license terms specify. You must have
reasonable mechanisms in place to ensure that the number of Client Devices on
which the Software has been installed does not exceed the number of licenses
you have obtained. This license authorizes you to make or download one copy of
the Documentation for each additional copy authorized by the volume license,
provided that each such copy contains all of the Document's proprietary notices.
2. Duration. This Agreement is effective for the period specified in the Key File
(the unique file which is required to fully enable the Software, please see Help/
about Software or Software about, for Unix/Linux version of the Software see the
notification about expiration date of the Key File) unless and until earlier
terminated as set forth herein. This Agreement will terminate automatically if you
fail to comply with any of the conditions, limitations or other requirements
Page 73

Appendix C 73
described herein. Upon any termination or expiration of this Agreement, you
must immediately destroy all copies of the Software and the Documentation. You
may terminate this Agreement at any point by destroying all copies of the
Software and the Documentation.
3. Support.
(i) Kaspersky Lab will provide you with the support services ("Support Services")
as defined below for a period of one year following:
(a) Payment of its then current support charge, and:
(b) Successful completion of the Support Services Subscription Form as
provided to you with this Agreement or as available on the Kaspersky Lab
website, which will require you to produce the Key Identification File which will
have been provided to you by Kaspersky Lab with this Agreement. It shall be at
the absolute discretion of Kaspersky Lab whether or not you have satisfied this
condition for the provision of Support Services.
(ii) Support Services will terminate unless renewed annually by payment of the
then-current annual support charge and by successful completion of the Support
Services Subscription Form again.
(iii) By completion of the Support Services Subscription Form you consent to the
terms of the Kaspersky Lab Privacy Policy, which is deposited on
ww.kaspersky.com/privacy, and you explicitly consent to the transfer of data to
other countries outside your own as set out in the Privacy Policy.
(iv) "Support Services" means:
(a) Daily updates of the anti-virus database;
(b) Free software updates, including version upgrades;
(c) Extended technical support via e-mail and phone hotline provided by Vendor
and/or Reseller;
(d) Virus detection and disinfection updates 24 hours per day.
4. Ownership Rights. The Software is protected by copyright laws. Kaspersky
Lab and its suppliers own and retain all rights, titles and interests in and to the
Software, including all copyrights, patents, trademarks and other intellectual
property rights therein. Your possession, installation, or use of the Software does
not transfer any title to the intellectual property in the Software to you, and you
will not acquire any rights to the Software except as expressly set forth in this
Agreement.
5. Confidentiality. You agree that the Software and the Documentation, including
the specific design and structure of individual programs and the Key Identification
File, constitute confidential proprietary information of Kaspersky Lab. You shall
not disclose, provide, or otherwise make available such confidential information
in any form to any third party without the prior written consent of Kaspersky Lab.
Page 74

74 Kaspersky Anti-Virus for Proxy Server
You shall implement reasonable security measures to protect such confidential
information, but without limitation to the foregoing shall use best endeavours to
maintain the security of the Key Identification File.
6. Limited Warranty.
(i) Kaspersky Lab warrants that for six (6) months from first download or
installation the Software purchased on a physical medium will perform
substantially in accordance with the functionality described in the Documentation
when operated properly and in the manner specified in the Documentation.
(ii) You accept all responsibility for the selection of this Software to meet your
requirements. Kaspersky Lab does not warrant that the Software and/or the
Documentation will be suitable for such requirements nor that any use will be
uninterrupted or error free.
(iii) Kaspersky Lab does not warrant that this Software identifies all known
viruses, nor that the Software will not occasionally erroneously report a virus in a
title not infected by that virus.
(iv) Your sole remedy and the entire liability of Kaspersky Lab for breach of the
warranty at paragraph (i) will be at Kaspersky Lab option, to repair, replace or
refund of the Software if reported to Kaspersky Lab or its designee during the
warranty period. You shall provide all information as may be reasonably
necessary to assist the Supplier in resolving the defective item.
(v) The warranty in (i) shall not apply if you (a) make or cause to be made any
modifications to this Software without the consent of Kaspersky Lab, (b) use the
Software in a manner for which it was not intended, or (c) use the Software other
than as permitted under this Agreement.
(vi) The warranties and conditions stated in this Agreement are in lieu of all other
conditions, warranties or other terms concerning the supply or purported supply
of, failure to supply or delay in supplying the Software or the Documentation
which might but for this paragraph (vi) have effect between the Kaspersky Lab
and you or would otherwise be implied into or incorporated into this Agreement
or any collateral contract, whether by statute, common law or otherwise, all of
which are hereby excluded (including, without limitation, the implied conditions,
warranties or other terms as to satisfactory quality, fitness for purpose or as to
the use of reasonable skill and care).
7. Limitation of Liability.
(i) Nothing in this Agreement shall exclude or limit Kaspersky Lab's liability for (a)
the tort of deceit, (b) death or personal injury caused by its breach of a common
law duty of care or any negligent breach of a term of this Agreement, or (c) any
other liability which cannot be excluded by law.
(ii) Subject to paragraph (i) above, the Supplier shall bear no liability (whether in
contract, tort, restitution or otherwise) for any of the following losses or damage
Page 75

Appendix C 75
(whether such losses or damage were foreseen, foreseeable, known or
otherwise):
(a) Loss of revenue;
(b) Loss of actual or anticipated profits (including for loss of profits on contracts);
(c) Loss of the use of money;
(d) Loss of anticipated savings;
(e) Loss of business;
(f) Loss of opportunity;
(g) Loss of goodwill;
(h) Loss of reputation;
(i) Loss of, damage to or corruption of data, or:
(j) Any indirect or consequential loss or damage howsoever caused (including,
for the avoidance of doubt, where such loss or damage is of the type specified in
paragraphs (ii), (a) to (ii), (i).
(iii) Subject to paragraph (i), the liability of Kaspersky Lab (whether in contract,
tort, restitution or otherwise) arising out of or in connection with the supply of the
Software shall in no circumstances exceed a sum equal to the amount equally
paid by you for the Software.
8. (i) This Agreement contains the entire understanding between the parties
with respect to the subject matter hereof and supersedes all and any prior
understandings, undertakings and promises between you and Kaspersky Lab,
whether oral or in writing, which have been given or may be implied from
anything written or said in negotiations between us or our representatives prior to
this Agreement and all prior agreements between the parties relating to the
matters aforesaid shall cease to have effect as from the Effective Date. Save as
provided in paragraphs (ii) - (iii) below, you shall not have any remedy in respect
of an untrue statement made to you upon which you relied in entering into this
Agreement ("Misrepresentation") and Kaspersky Lab shall not have any liability
to the other than pursuant to the express terms of this Agreement.
(ii) Nothing in this Agreement shall exclude or limit Kaspersky Lab's liability
for any Misrepresentation made thereby if aware that it was untrue.
(iii) The liability of Kaspersky Lab for Misrepresentation as a fundamental
matter, including a matter fundamental to the maker's ability to perform its
obligations under this Agreement, shall be subject to the limitation of liability set
out in paragraph 7(iii).
 Loading...
Loading...