Page 1

KASPERSKY LABS
Kaspersky Anti-Hacker 1.5
USER GUIDE
Page 2

KASPERSKY ANTI-HACKER 1.5
User Guide
Kaspersky Labs Ltd.
http://www.kaspersky.com
Revision date: April 2004
Page 3

Contents
CHAPTER 1. KASPERSKY ANTI-HACKER.................................................................. 6
1.1. Introduction ............................................................................................................ 6
1.2. What’s new in v. 1.5 .............................................................................................. 7
1.3. Distribution Kit........................................................................................................ 8
1.3.1. What Is in the Distribution Kit ......................................................................... 8
1.3.2. License Agreement......................................................................................... 8
1.4. Information in the Book ......................................................................................... 9
1.5. Conventions......................................................................................................... 10
1.6. Help Desk for Registered Users ......................................................................... 11
CHAPTER 2. INSTALLING AND REMOVING THE SOFTWARE.............................. 12
2.1. Hardware and Software Requirements.............................................................. 12
2.2. Installing ............................................................................................................... 13
2.3. Removing the Program ....................................................................................... 18
CHAPTER 3. STARTING WORK .................................................................................19
CHAPTER 4. KASPERSKY ANTI-HACKER – PREVENTING HACKER
ATTACKS ................................................................................................................... 22
4.1. Kaspersky Anti-Hacker Operating Principles ..................................................... 22
4.2. Security Levels .................................................................................................... 23
4.3. Recommended Settings...................................................................................... 24
CHAPTER 5. RUNNING THE PROGRAM .................................................................. 27
5.1. Starting the Program ...........................................................................................27
5.2. System Menu....................................................................................................... 28
5.3. Main Window ....................................................................................................... 29
5.4. Menus .................................................................................................................. 30
5.5. Toolbar................................................................................................................. 32
5.6. Workspace........................................................................................................... 33
Page 4

4 Kaspersky Anti-Hacker
5.7. Status Bar ............................................................................................................ 34
5.8. Context Menu ...................................................................................................... 34
5.9. Rule Wizards ....................................................................................................... 34
5.10. Changing and Saving Interface Settings .......................................................... 35
5.11. Exiting the Program........................................................................................... 37
CHAPTER 6. ENABLING THE SECURITY SYSTEM AND DEFINING ITS
SETTINGS.................................................................................................................. 38
6.1. Enabling the Security System and Selecting the Security Level ....................... 38
6.1.1. Enabling the Security System ...................................................................... 38
6.1.2. Selecting the Security Level ......................................................................... 40
6.1.3. Network Event Warning................................................................................ 41
6.1.4. Training Window (Medium Level) ................................................................ 42
6.1.5. The Executable Module Substitution Warning ............................................ 43
6.2. How the Program Responds to Attack ............................................................... 45
6.3. Customizing Application Rules ........................................................................... 46
6.3.1. Managing the Rule List................................................................................. 46
6.3.2. Adding a New Rule....................................................................................... 49
6.3.2.1. Step 1. Customizing the Rule................................................................ 49
6.3.2.2. Step 2. Rule Conditions ......................................................................... 53
6.3.2.3. Step 3. Additional Actions...................................................................... 59
6.4. Customizing Packet Filtering Rules .................................................................... 60
6.4.1. Managing the Rule List................................................................................. 60
6.4.2. Adding a New Rule....................................................................................... 63
6.4.2.1. Step 1. Rule Conditions ......................................................................... 63
6.4.2.2. Step 2. Rule Name and Additional Actions........................................... 67
6.5. Intrusion Detection System ................................................................................. 69
6.5.1. Intrusion Detector Settings ........................................................................... 69
6.5.2. The List of Detectable Attacks...................................................................... 70
CHAPTER 7. VIEWING PERFORMANCE RESULTS................................................ 73
7.1. Viewing the Current Status ................................................................................. 73
7.1.1. Active Applications........................................................................................ 73
Page 5

Contents 5
7.1.2. Established Connections.............................................................................. 77
7.1.3. Open Ports.................................................................................................... 80
7.2. Using the Logs..................................................................................................... 83
7.2.1. Displaying the Logs Window........................................................................ 83
7.2.2. The Logs Window Layout............................................................................. 84
7.2.2.1. Menus..................................................................................................... 84
7.2.2.2. Report Table .......................................................................................... 84
7.2.2.3. Tabs........................................................................................................ 85
7.2.3. Selecting the Log .......................................................................................... 85
7.2.3.1. Security Log ...........................................................................................85
7.2.3.2. Application Activity ................................................................................. 86
7.2.3.3. Packet Filtering ...................................................................................... 87
7.2.4. Defining Log Settings ................................................................................... 88
7.2.5. Saving the Log to a File................................................................................ 89
APPENDIX A. INDEX .................................................................................................... 90
APPENDIX B. FREQUENTLY ASKED QUESTIONS ................................................. 91
APPENDIX C. KASPERSKY LABS LTD...................................................................... 92
C.1. Other Kaspersky Lab's Products........................................................................ 93
C.2. Contact Information............................................................................................. 96
Page 6

CHAPTER 1. KASPERSKY ANTI-
HACKER
1.1. Introduction
What is Kaspersky Anti-Hacker?
Kaspersky Anti-Hacker is a personal firewall that is designed to safeguard a
computer running a Windows operating system. It protects the computer against
unauthorized access to its data and external hacker attacks from the Internet or
an adjacent local network.
Kaspersky Anti-Hacker:
• Monitors the TCP/IP network activity of all applications running on your
machine. If it detects any suspicious actions, the program notifies you and
if required, blocks the suspect application from accessing the network.
This allows you to preserve confidential data on your machine. For example, if a Trojan tries to transmit any data from your computer, Kaspersky
Anti-Hacker will block this malware from accessing the Internet.
• The SmartStealth™ technique makes it difficult to detect your computer
from outside. As a result, hackers will lose the target and all their attempts
to access your computer will be doomed to fail. Besides, this allows for
prevention of the DoS (Denial of Service) attack of all types. At the same
time you will not feel any negative influence of this mode while working on
the Web: the program provides conventional transparency and accessibility of the data.
• Blocks the most common hacker network attacks by permanently filtering
the incoming and outgoing traffic, and also notifies the user about any
such attacks.
• Monitors for attempts to scan your ports (these attempts are usually followed by attacks), and prohibits any further communication with the attacking machine.
• Allows you to review the list of all established connections, open ports,
and active network applications, and if required, lets you terminate unwanted connections.
Page 7

Kaspersky Anti-Hacker 7
• Allows you to secure your machine from hacker attacks without special
configuration of program settings. The program allows simplified management by choosing one of five security levels: Block all, High, Medium,
Low, Allow all. By default the program starts with the Medium level, which
is a training mode that will automatically configure your security system
depending on your responses to various events.
• Allows flexibility of security system configuration. In particular, you can set
the program to filter network operations into wanted and unwanted, and
you can configure the Intrusion Detection System.
• Allows you to log certain security-related network events to various special-purpose logs. If required, you can define the detail level of the log entries.
The program may be used as a separate software product or as an integral
component of various Kaspersky Labs solutions.
Attention!!! Kaspersky Anti-Hacker does not protect your computer from
viruses and malicious programs that can destroy and/or corrupt your
data. It is advised that you use Kaspersky Anti-Virus Personal for this
purpose.
1.2. What’s new in v. 1.5
New features of version 1.5
The new version of this program:
• supports operations with ADSL modems;
• completely supports Stealth mode (tests passed at www.pcflank.com);
• is able to detect new network attacks: SmbDie, Helkern, and Lovesan;
• allows definition of port ranges for packet filtering and application rules;
• is more easy to configure right after installation without any degradation of
the computer security level – the most frequently used applications are allowed by default to establish network connections strictly according to
their types;
Page 8

8 Kaspersky Anti-Hacker
• has an improved graphic interface: supports XP style under Windows XP;
the rule handling lists can be resized; to add a new rule you can use the
<Ins> key.
1.3. Distribution Kit
What is in the Distribution kit License agreement.
1.3.1. What Is in the Distribution Kit
The distribution kit includes:
• A sealed envelope containing installation CD with software files for the
product
• This user guide
• Key diskette or key file on the installation CD
• License agreement
Before you unseal the CD envelope, be sure to review the license
agreement thoroughly.
1.3.2. License Agreement
The License Agreement (LA) is a legal agreement between you (either an
individual or a single entity) and the manufacturer (Kaspersky Labs Ltd.)
describing the terms on which you may employ the anti-virus product which you
have purchased.
Please ensure you read all the terms of the LA!
If you do not agree to the terms of this LA, Kaspersky Labs is not willing to
license the software product to you and you should return the unused product to
your Kaspersky Anti-Virus dealer for a full refund, making sure the envelope
containing the CD (or diskettes) is sealed.
Page 9
Kaspersky Anti-Hacker 9
By unsealing the envelope you agree to all the terms of the LA.
1.4. Information in the Book
Issues covered in this documentation
This book contains information on how to install, customize and manage
Kaspersky Anti-Hacker.
The book is divided into the following chapters:
Chapter Summary
Kaspersky Anti-Hacker What is Kaspersky Anti-Hacker? Items in the
distribution kit and information in this book.
Installing and Removing the
Software
Starting Work How to start working with the software product.
Kaspersky Anti-Hacker –
Preventing Hacker Attacks
Running the Program Screening the main program window and
Enabling the Security
System and Defining its
Settings
Viewing Performance
Results
Appendix А. Kaspersky
Labs Ltd.
Appendix В. Index Glossary of the terms used in this
System requirements. How to install the
software.
Example of the security system configuration.
Operating principles of the software product.
Main terms, and tasks to be accomplished by
the product.
working with its items.
How to enable the security system. Defining the
security settings - rules for applications and
datagram filtering rules.
Reviewing the logs - network attacks,
application activity and packet filtering.
Reviewing the list of open ports, established
connections, and active network applications.
Information about Kaspersky Labs Ltd. Contact
data.
documentation.
Page 10

10 Kaspersky Anti-Hacker
Chapter Summary
Appendix С. Frequently
Asked Questions
Answers to frequently asked questions.
1.5. Conventions
Conventions used in this book
In this book we use a number of conventions to emphasize various important
parts of the documentation.
Convention Meaning
Bold font
Note.
Attention!
To start the program, follow
these steps:
1. Step 1.
Menu titles, commands, window titles,
dialog elements, etc.
Additional information, notes.
Critical information.
Actions that must be taken.
2. …
Task:
Solution
Example of a user defined task to be
accomplished using this program.
Solution of the task.
Page 11

Kaspersky Anti-Hacker 11
1.6. Help Desk for Registered Users
Services provided by Kaspersky Labs
to registered users
Kaspersky Labs offers a large service package enabling its registered customers
to employ Kaspersky Anti-Hacker more efficiently.
If you register and purchase a subscription you will be provided with the following
services for the period of your subscription:
• New versions of this software product, provided free
• Phone and e-mail support advising on matters related to installation, con-
figuration and management of this software product
• Information about new products from Kaspersky Labs and about new
computer viruses (for those who subscribe to the Kaspersky Labs newsletter)
Kaspersky Labs does not provide information related to management
and use of your operating system, and associated technologies.
Page 12

CHAPTER 2. INSTALLING AND
REMOVING THE SOFTWARE
2.1. Hardware and Software
Requirements
System requirements to be met in
order to run the program
In order to run Kaspersky Anti-Hacker you need a system that meets the
following requirements:
• Preinstalled Microsoft Windows operating system version 98/ME/NT
4.0/2000/XP
• To install under Microsoft Windows NT 4.0/2000/XP, you must be authorized administrator
• Supported TCP/IP protocol
• Local network (Ethernet) or dial-up connection (standard or ADSL-
modem)
• Microsoft Internet Explorer (minimum 5.0 , 5.5 (SP 2) or higher recommended)
• At least 50 Mb of free space for the program files and extra space for the
program logs
• To run under Windows® 98/Me/NT 4.0, you must have:
• Intel Pentium® processor of 133MHz or higher under Windows
98 or Windows NT 4.0
• Intel Pentium® processor of 150MHz or higher under Windows
Me
Page 13

Installing and Removing the Software 13
• 32 Mb RAM
• Preinstalled Service Pack v. 6.0 or higher under Windows
NT 4.0 Workstation
• To run under Windows 2000, you must have:
• Intel Pentium® processor of 133MHz or higher
• 64 Mb RAM
• To run under Windows XP, you must have:
• Intel Pentium® processor of 300MHz or higher
• 128 Mb RAM
2.2. Installing
Step-by-step installation. Setup
Wizard
Run the Setup.exe program from the CD to start the program installation. The
setup wizard operates in dialog mode. Every dialog box contains a certain set of
buttons allowing management of the setup. The main buttons are:
• OK – to accept actions
• Cancel – to cancel action(s)
• Next – to move one step forward
• Back – to move one step backward
Before installing Kaspersky Anti-Hacker please quit all programs
running on your computer.
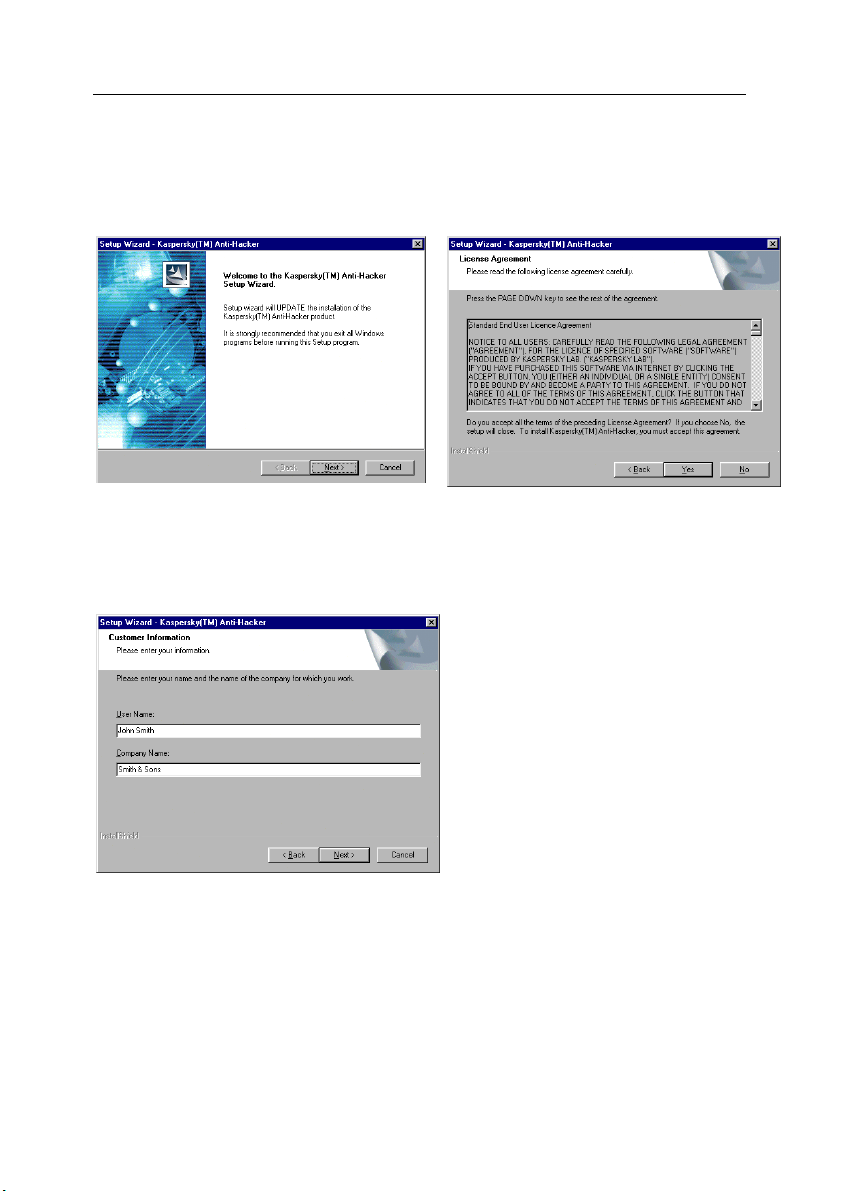
Step 1. Read general information
The first dialog box of the setup wizard (see fig. 1) contains general information
about the Kaspersky Anti-Hacker package.
Page 14
14 Kaspersky Anti-Hacker
Step 2. Read the license agreement
The License Agreement dialog box (see fig. 2) contains the agreement text.
Read it carefully and press Yes if you agree to the license agreement terms.
Otherwise, press No to abort the setup.
Fig. 1. The first dialog box of the setup wizard
Step 3. Input user information
Fig. 3. The Customer Information dialog box
Fig. 2. The License Agreement dialog box
Enter the user information in the
Customer Information dialog box
(see fig. 3). Enter the appropriate
data in the User Name field and the
Company Name field. By default the
information for these fields is taken
from the Windows registry.
Page 15

Installing and Removing the Software 15
Step 4. Select the folder the program will be installed to
In the Choose Destination
Location dialog box (see fig. 4),
select the installation folder where
the Kaspersky Anti-Hacker
program components will be
installed. The folder must be
defined in the Destination Folder
field. To do this, press Browse
and indicate the folder path in the
Choose Folder standard dialog
box.
Fig. 4. The Choose Destination Location
dialog box
Step 5. Input the program group name in the Start\Programs
menu
Define the folder name in the
Select Program Folder dialog
box (see fig. 5) for the Kaspersky
Anti-Hacker icon to appear in the
standard Program menu. Press
Next.
Fig. 5. The Select Program Folder dialog box
Step 6. Define paths to the key files*
In the Key File dialog box (see fig. 6), you must define the key file name (the
*.key file) and the path.
Page 16

16 Kaspersky Anti-Hacker
If the file is located in the setup
folder, its name will be displayed in
the list of key files to be installed.
If the key file is located in a
different folder, press Add and
define the key file name and the
path in the Select Key File
standard dialog box. If required,
the program may simultaneously
use several key files.
Fig. 6. The Key File dialog box
It is advised that you check the Select Key Association checkbox. In this case
you will be able to install new key files by double-clicking on their names. If you
leave the box unchecked you will have to copy a key file to the shared files folder
in order to install it.
The Key File is your personal key that contains the following housekeeping data,
essential for Kaspersky Anti-Hacker to apply all its features:
• Your version vendor information (company name, addresses, telephone
numbers)
• Support information (Name and location of support services)
• Product release date
• Name and number of the license
• License period of validity
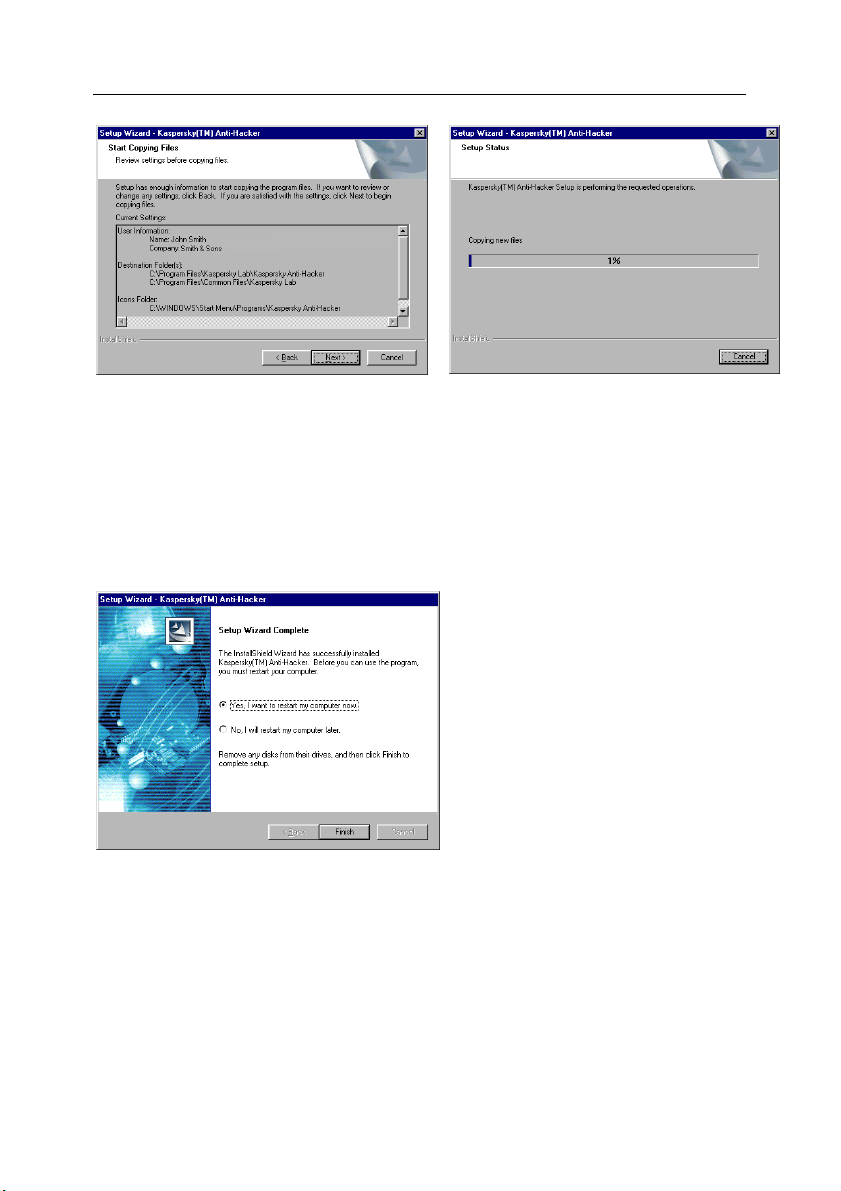
Step 7. Copying files to the hard drive
Read the setup information in the Start Copying Files dialog box (see fig. 7). If
you need to change any settings, you must return to the appropriate wizard box
by pressing the Back button. If the setup information is correct, press Next. The
program will start copying files to the hard disk. Progress is indicated by the
progress bar in the Setup Status dialog box (fig. 8).
Page 17
Installing and Removing the Software 17
Fig. 7. The Start Copying Files dialog box
Fig. 8. The Setup Status dialog box
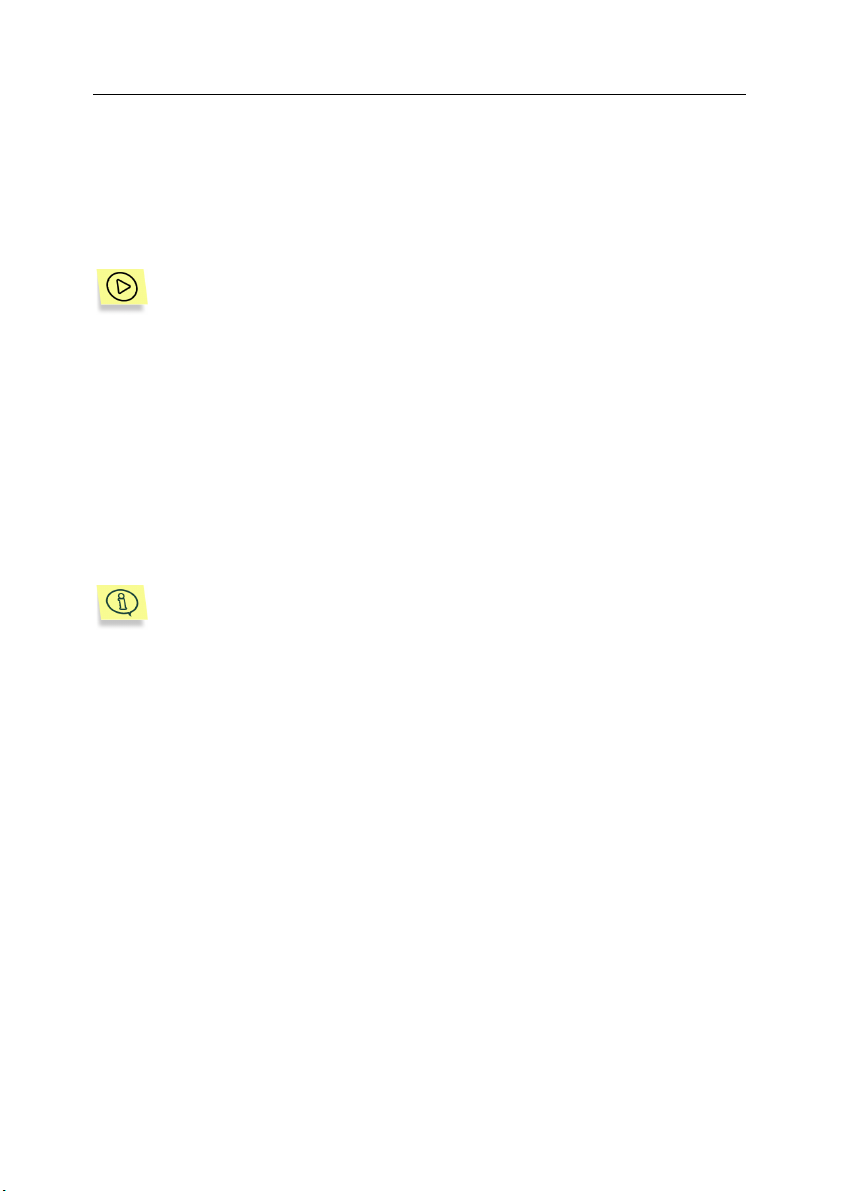
Step 8. Completing setup
Upon completion of the Kaspersky Anti-Hacker package installation the
Completing Setup Wizard dialog box appears on the screen (see fig. 9).
To complete the installation you
must restart your system. Check the
Yes, I want to restart my
computer now box to restart your
system right away, or the No, I will
restart my computer later box to
postpone the restart. Press the
Finish button to finish the
installation.
Fig. 9. The Completing Setup Wizard dialog
box
Page 18
18 Kaspersky Anti-Hacker
2.3. Removing the Program
Removing the program from your
computer
To remove the Kaspersky Anti-Hacker program follow these steps:
1. Press the Start button in the bottom left corner of your Windows
desktop and point to Programs.
2. Point to the program group that corresponds to your Kaspersky AntiHacker installation. The default name of this program group is
Kaspersky Anti-Hacker, but you may have changed it during the
installation. Then point to Kaspersky Anti-Hacker Uninstall.
3. If you wish to uninstall Kaspersky Anti-Hacker, press Yes in the
confirmation box. If you change your mind, cancel the uninstall process
by pressing the No button.
To add/remove the program you can use the Add/Remove Programs
icon in the MS Windows Control Panel.
Page 19
CHAPTER 3. STARTING WORK
How to start working with the
software product. Example of
security system configuration
As soon as you install the program and restart your computer the security system
is activated. In fact, from this very moment, Kaspersky Anti-Hacker is monitoring
for attacks against your machine and attempts by your applications to interact via
a local network or the Internet.
After you enter the system you begin to work as usual. When no network
connection is established, the security system on your machine is indicated only
by the
appear on your screen. In this window, you may review information about the
current security level and change this level if required (for details of the program
main window refer to subchapter 5.3 on page 29). By default the Medium level is
enabled. This level allows you to configure your security system conversationally.
In most cases you will not have to configure the system yourself: the most
frequently used applications are allowed by default to establish network
connections strictly according to their type. However sometimes you will have to
configure your security system manually. Let’s review the corresponding
example:
icon in the system tray. If you click on it, the program main window will
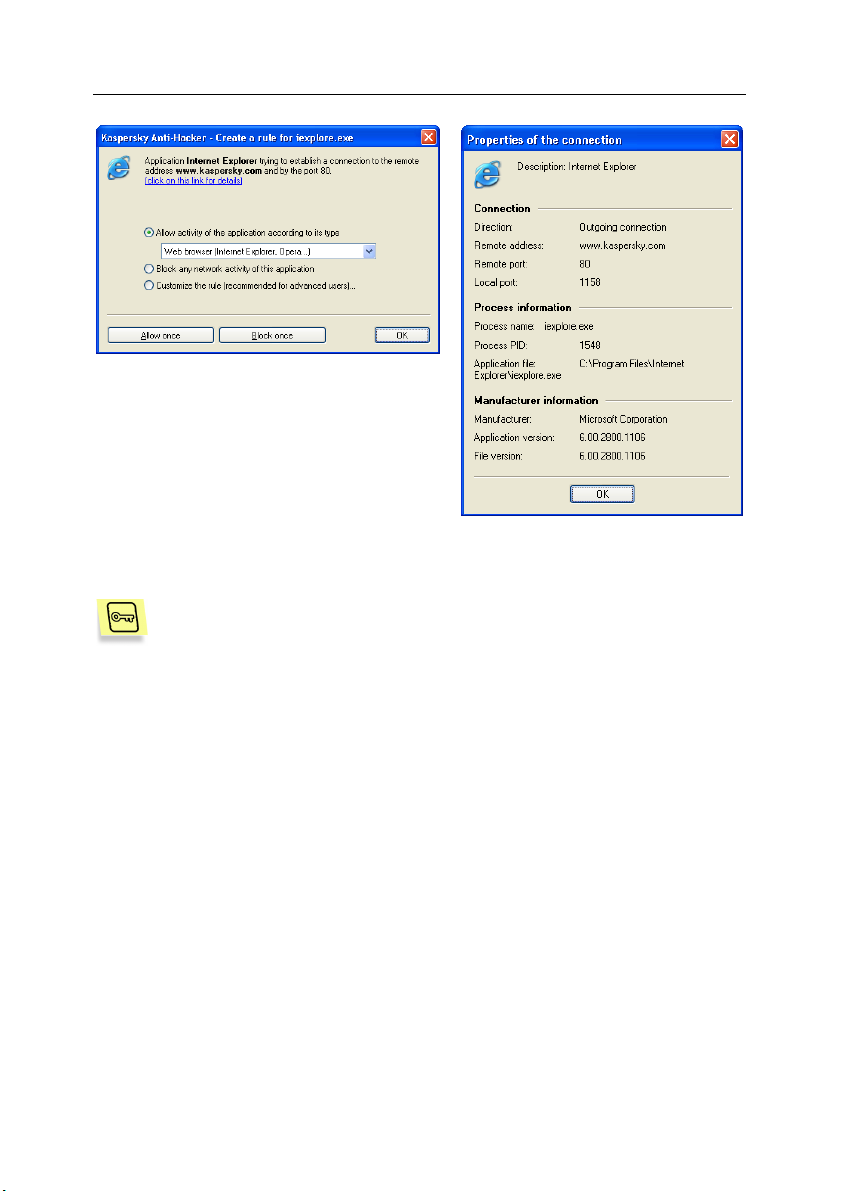
Task: Suppose your computer is connected to the Internet, and
you start Microsoft Internet Explorer and enter
www.kaspersky.com in the address field. The following message
will appear on your screen: Create a rule for IEXPLORER.EXE
(see fig. 10).
In the upper area of this dialog box you will see the icon for the
application concerned, its name (in this case Microsoft Internet
Explorer), the site address
used to establish the connection. To review more details about
this application, you just have to click on the underlined link (see
fig. 11).
The required network connection will not be established until you
select how to handle this application activity. To do this, you must
respond to the message on your screen.
www.kaspersky,com, and the port to be
Page 20
20 Kaspersky Anti-Hacker
Fig. 10. Self-training dialog box of the security
system
Fig. 11. Information about the
connection to be established
Follow these steps:
1. Select the Allow activity of this application according to its
type option button and Web browser (IE, Netscape...) from the
drop-down list.
2. Press ОК.
After this, Kaspersky Anti-Hacker will allow Microsoft Internet Explorer
to establish the connection. In addition, the application will be allowed to
establish other connections in accordance with its type.
As you have probably noticed, there are three options in the Create a rule for
IEXPLORER.EXE dialog box:
• Allow activity of this application according to its type (the option you
selected in the example above) – allows only network communication that
is compliant with the specified application category. Select the required
category from the drop-down list below the option button. You can allow
any activity of this application by selecting Allow all from the drop-down
list.
Page 21
Starting Work 21
• Block any network activity of this application – blocks the specified
application from any kind of network activity including the described operation.
• Customize the rule – allows you to specify the operations that will be al-
lowed for this application. If you select this option button and click ОК, the
rule wizard window will appear on your screen. Use the rule wizard to define requirements for the operations to be allowed for this application (for
details of the rule wizard see subchapter 6.3.2 on page 49).
If you are not sure which option to select, use the Allow once or the Block once
buttons at the bottom of the dialog box. Later on you will be able to monitor the
application behavior and decide which option to select.
If you close the training window by pressing the
right corner, the operation at issue will be blocked this time.
button in its upper-
In this way you can conversationally configure your computer security system in
an appropriate way.
To review the list of defined rules, select Application rules from the
Service menu or press the
button in the main window toolbar.
We recommend that you use the Medium level for the first few weeks after
program installation. This will allow the program to automatically configure your
security system depending on your responses to various network events. Create
the rules allowing standard network operations.
When the training period is over, you can switch the program to the High level,
and secure your computer against any unauthorized network events and hacker
attacks. However, remember the newly installed applications will by default be
disabled from accessing the local network and/or the Internet. To teach your
Kaspersky Anti-Hacker to handle these new applications you will have to switch it
back to Medium or manually define the appropriate rule for these applications.
Page 22

CHAPTER 4. KASPERSKY ANTI-
HACKER – PREVENTING
HACKER ATTACKS
4.1. Kaspersky Anti-Hacker
Operating Principles
How does Kaspersky Anti-Hacker
operate? Application rules. Packet
filtering rules. Intrusion Detection
System.
Kaspersky Anti-Hacker protects your computer from network attacks and
preserves your confidential data. To do this, Kaspersky Anti-Hacker monitors all
network operations on your computer. There are two types of network operation:
• Operations on the application level (high-level). At this level, Kaspersky
Anti-Hacker analyses activity of network applications, including web
browsers, mail programs, file transferring programs and others.
• Operations on the packet level (low-level). At this level, Kaspersky AntiHacker analyses data packet sent/received by your netcard or modem.
You work with Kaspersky Anti-Hacker by creating special filtering rules for
network operations. Some filtering is performed automatically by the Intrusion
Detection System, which can detect port scanning, DOS attacks, etc., and can
then block the assaulter. In addition, you can define your own filtering rules to
reinforce protection of your machine.
For every type of network operation there are separate lists of Kaspersky AntiHacker rules.
• Application rules. Here you can select the required application and allow
an activity that is compliant with the application type. You can define any
number of rules for every application, as required. If any network activity
not meeting conditions of the rule is detected on your machine, the program will notify you and allow you to block the unwanted action (if Me-
Page 23

Kaspersky Anti-Hacker – Preventing Hacker Attacks 23
dium level is enabled). In order to define the simplest rule for an application, you can simply select its type from the drop-down list (for details see
subchapter 6.3.2.1 on page 49). To define a more complicated rule, you
can specify the remote services and addresses allowed for this application.
• Packet filtering rules allow or block network packets sent or received by
your machine. These rules review the packet header (the protocol used,
the port numbers, the IP addresses etc.), and take decisions on the basis
of this data. These rules are applied to all network applications running on
your machine. For example, if you create a rule to block a certain IP address, all network communications to this address will be prohibited.
Packet filtering rules have a higher priority than application rules, i.e.
these rules are instigated first. For example, if you create a rule to block
all incoming and outgoing data packets, then the program will apply no
application rules while filtering data packets.
4.2. Security Levels
What security levels are supported
by Kaspersky Anti-Hacker?
The program allows you to select one of the following security levels:
• Allow all – disables the security system on your machine. When this level
of security is selected, any network activity is allowed on your machine.
• Low – allows network activity of all applications except those explicitly
prohibited by user defined application rules.
• Medium – notifies you about network events related to your applications
and allows you to configure your security system for optimal performance.
If a network application on your computer tries to connect to the local
network or the Internet, the training mode will be activated. The application and the network operation details will be displayed on your screen.
On the basis of this data the program will prompt you to select one of the
following courses of action: to allow or to block this event once, to completely block activity of this application, to allow the application activity according to its type, or to define additional network communication settings.
Depending on your answer, the program will create a rule for this application that will subsequently be applied by the program automatically.
• High – prohibits network activity for all applications except for those ex-
plicitly allowed by user defined application rules. When this security level
Page 24

24 Kaspersky Anti-Hacker
is enabled, the program training dialog box does not appear on your
screen, and all attempts to establish connections not defined in the user
rules are blocked.
Remember that all applications installed after you switch to this
security level are by default disabled from accessing the Internet
or the local network.
• Block all – disables your computer from accessing the Internet or the lo-
cal network. This level creates a situation in which all attempts to establish connection via the Internet or the local network are blocked as if your
computer is physically disconnected.
With the High, Medium or Low level enabled you can set the
supplementary security tool – Stealth mode (see subchapter 5.6 on
page 33). This mode allows only the network activity initiated by you, all
other types of activity (remote access to your machine, checking of your
machine using the ping utility and so on) are prohibited, if not explicitly
allowed by the user rules.
Actually it means that you computer becomes "invisible" from the
external environment. Hackers lose the target and all their attempts to
access your computer are doomed to fail. Besides, this allows for
prevention of the DoS (Denial of Service) attack of all types.
At the same time you will not feel any negative influence of this mode
while working on the Web: Kaspersky Anti-Hacker allows the network
activity initiated from your machine.
Attention! The intrusion detection system is enabled for all security
levels except for Allow all. However, if required, you can manually
disable it (see subchapter 6.5.1 on page 69).
4.3. Recommended Settings
How to select proper security levels,
and define rules for various
situations?
What components of Kaspersky Anti-Hacker should be used and what security
level should be selected? The answer depends on the task you want to
accomplish.
Task 1. How to protect your data from external attacks via the
Internet?
Page 25

Kaspersky Anti-Hacker – Preventing Hacker Attacks 25
The following are two of the main methods used by hackers to steal
or corrupt user data via the Internet: penetration into a target computer system using computer software errors, and infection of a target
computer by Trojans.
If you learn about an error in one of the programs installed on your
machine, be sure to create a blocking rule for this application. It is
advised that you create a complex blocking rule (see
subchapter 6.3.2.1 on page 49) that will take into account features of
this error.
Suppose your computer is infected by a Trojan via a diskette or by
email, and the malicious program attempts to send some data via the
Internet. Kaspersky Anti-Hacker will easily preserve your data by
blocking this operation (at the High level), or by issuing an
appropriate notification (at the Medium level).
Attention!!! Kaspersky Anti-Hacker does not protect your computer
from viruses and malicious programs.
For example, a Trojan may use a standard mail program on your
computer to send out your confidential data. In this case Kaspersky
Anti-Hacker will not be able to prevent the action. Moreover, if your
computer is infected by a virus or a malicious program, your data may
simply be destroyed and the computer may become a virus source. In
this case Kaspersky Anti-Hacker may only partially eliminate consequences of the infection. To effectively protect your system from viruses and malicious programs it is advisable that you use the
Kaspersky Anti-Virus Personal/Personal anti-virus program in combination with Kaspersky Anti-Hacker. Also, we recommend that you
create application rules allowing your computer applications to engage in activity strictly according to their type. It is also advisable that
you use the list of application rules to assign those types of activities
to the applications that strictly correspond to operations allowed for
these applications. This way, the risk of unauthorized network operations performed on your machine will be minimized.
Suppose, you learn that your computer is constantly attacked by a
remote machine.
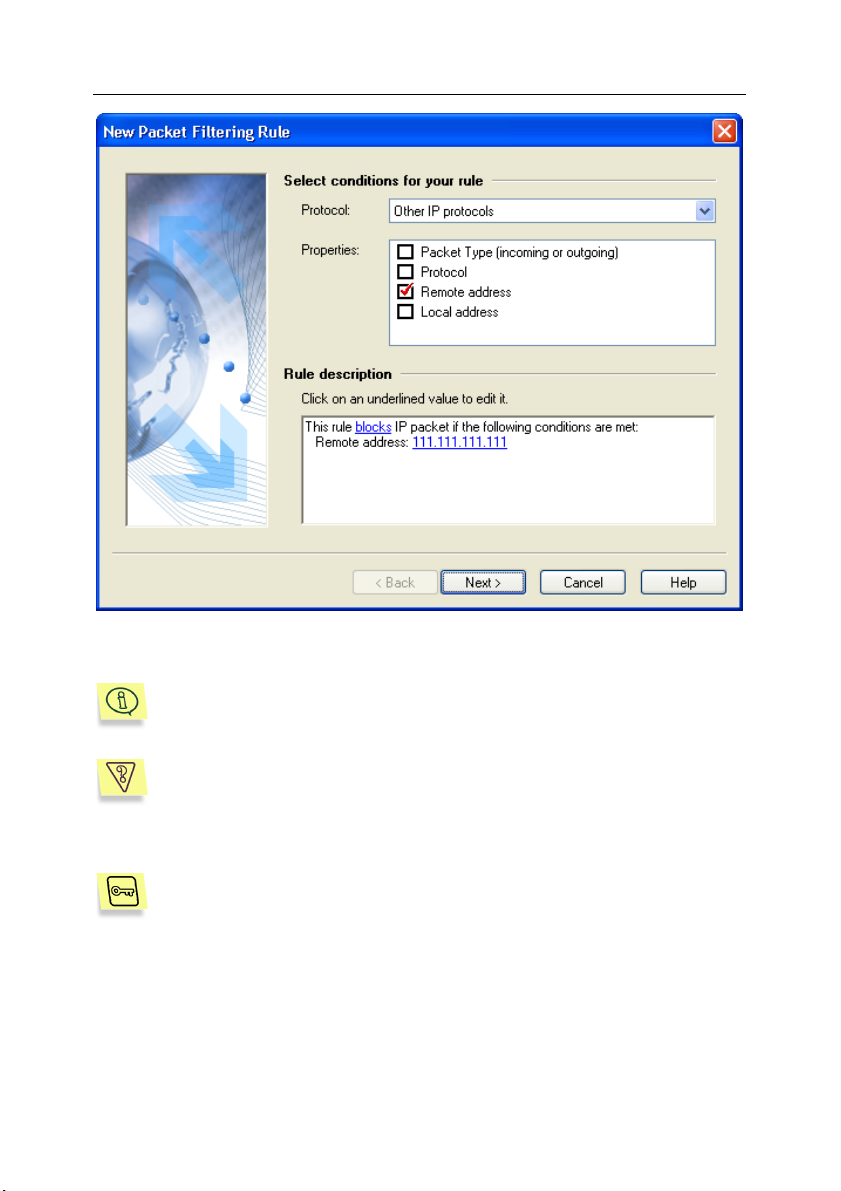
Task 2. How to block attacks from certain Internet addresses?
You may prohibit your computer from communication with certain
remote addresses by configuring appropriate packet filtering rules.
For example, in figure 12 you can see a rule blocking communication
with the 111.111.111.111 address.
To prevent from such situations, it is advisable that you keep your
Intrusion Detection System enabled.
Page 26
26 Kaspersky Anti-Hacker
Fig. 12. The rule blocking communication with certain unreliable addresses
For example, you may use Kaspersky Anti-Hacker to block banner
display on web pages. To do this, create a packet filtering rule to block
communication with web sites from where the banners are usually
downloaded (for example, linkexchange.ru).
Suppose you are afraid of attacks from the local network or want to
protect your personal data from thieves.
Task 3. You must monitor operations on the local network
The computer communicates with a local network at the operating system level, therefore it is not always possible to identify the application
involved. In this case you must create an appropriate packet filtering
rule to secure your data.
In order to simplify configuration of the security system, Kaspersky AntiHacker preinstalls some packet filtering rules allowing communication
via the local network. By default the local network is allowed. However,
you can redefine the default packet filtering rules to completely block
access to the local network, or allow it only for certain computers.
Page 27
CHAPTER 5. RUNNING THE
PROGRAM
How to start the program? The
program main window and its items.
Exiting the program.
5.1. Starting the Program
Kaspersky Anti-Hacker is started automatically as soon as you enter your
operating system. If you close the program, you can manually start it again.
To start Kaspersky Anti-Hacker, follow these steps:
1. Press the Start button in the bottom left corner of your Windows
desktop and point to Programs.
2. Point to the program group that corresponds to your Kaspersky AntiHacker installation. The default name of this program group is
Kaspersky Anti-Hacker, but you may have changed it during
installation. Then point to Kaspersky Anti-Hacker.
3. Left click on the
and select Open Kaspersky Anti-Hacker from the menu on your
screen.
The Kaspersky Anti-Hacker main window will appear on your screen (see
subchapter 5.3 on page 29).
You may also start the program directly from its directory. To do this,
start Windows Explorer and go to the Kaspersky Anti-Hacker directory
(the default program directory is C:\Program Files\Kaspersky
Lab\Kaspersky Anti-Hacker). Double-click on the KAVPF.exe file
located in this directory.
icon that appears in your system tray, or right click it
Page 28
28 Kaspersky Anti-Hacker
5.2. System Menu
Icon in the system tray.
System menu.
After the program is started, the icon appears in the system tray.
By right clicking on this icon you can display the system menu (see fig. 13). The
system menu includes the following commands:
Table 1
Menu !commands Function
(The command allows you to:)
Open Kaspersky Anti-Hacker…
Security level
About Kaspersky Anti-Hacker ...
Exit
Fig. 13. System menu
Display the program main window.
Switch to another security level:
Block all, High, Medium, Low, Allow
all. For details about the security
levels see subchapter 4.2 on page 23.
Display an information box with
program details and information about
the keys used.
Unload the program from computer
memory.
Page 29
Running the Program 29
5.3. Main Window
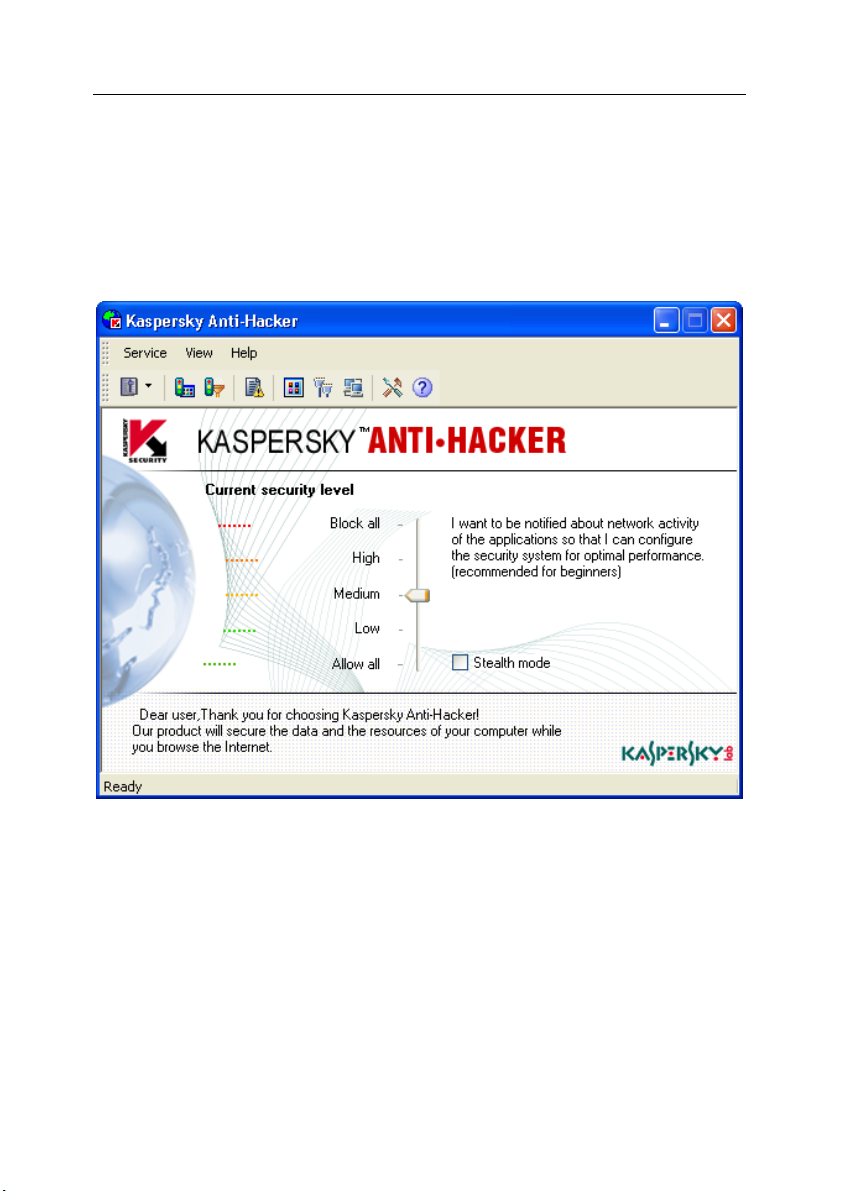
When the program is started, the main window appears on your screen (see
fig. 14). The Kaspersky Anti-Hacker main window allows you to select the current
security level, to review the current status of your security system, to change the
packet filtering settings, and to review/configure the program logs.
Fig. 14. The Kaspersky Anti-Hacker main window
The Kaspersky Anti-Hacker main window includes the following items:
• Menu
• Toolbar
• Workspace
• Status bar
Page 30
30 Kaspersky Anti-Hacker
5.4. Menus
At the top of the main window you can see a menu bar. You can drag it with your
mouse to any position within or outside the main window.
Some menu commands can also be activated using appropriate buttons in the
toolbar. For details of the matching functions of toolbar buttons and menu
commands see subchapter 5.5 on page 32.
Table 2
Menu !command Function
(The command allows you to:)
Service Application rules Display the application rule window.
Service Packet filtering rules Display the packet filtering rule window.
Service Security level Select the required security level:
• Block all
• High
• Medium
• Low
• Allow all
You can also select the required security
level from options in the window
workspace. For details see subchapter 4.2
on page 23.
Service Settings Display a window where you can
configure your security logs, security
system startup, and attack detection
settings.
Service Exit Unload the program from computer
memory.
Page 31

Running the Program 31
Menu !command Function
(The command allows you to:)
View Toolbars Choose from the following program
graphic interface options:
• Standard toolbar – displays/hides
the standard toolbar
• Customize – displays a dialog box
where you can customize the program graphic interface
View Status Bar Display/hide the status bar.
View Logs Display the log window for:
• Security
• Application activity
• Packet filtering
View Show Display information boxes with system
details.
• Active applications is the list of
active network applications
• Open ports is the list of open ports
on your machine
• Established connections is the
list of established connections
Help About Kaspersky AntiHacker...
Display an information box with program
details and information about the keys
used.
Help Kaspersky Anti-Hacker
on the Web
Open the Kaspersky Labs official web site
page
Help Contents ... Display the Help topics.
Page 32

32 Kaspersky Anti-Hacker
5.5. Toolbar
The program toolbar is located under the menu bar. If required, you can drag it
with your mouse to any position within or outside the main window.
The toolbar includes buttons. By pressing them you can initiate various commands. You can also hide and display the toolbar by selecting the Standard command from the Toolbars submenu of the View menu.
You can add or remove buttons from the toolbar (see subchapter 5.10 on
page 35).
Table 3
Button Menu ! Command Function
(The button allows you to)
Service
Service
Application rules
Service
Packet filtering rules
View
Security
View
Active applications
Security level Select the required security level:
• Block all
• High
• Medium
• Low
• Allow all
For details see subchapter 4.2 on
page 23.
Logs
Show
Display the application rule window.
Display the packet filtering rule
window.
Display the log window for Security
Log.
Show the list of active network
applications.
Page 33

Running the Program 33
Button Menu ! Command Function
(The button allows you to)
View
Open ports
View
Established connections
Service
Help
Show
Show
Settings Display a window where you can
Contents ... Display the Help topics.
Show the list of open ports on your
machine.
Show the list of established
connections.
configure your security logs, security
system startup, and attack detection
settings.
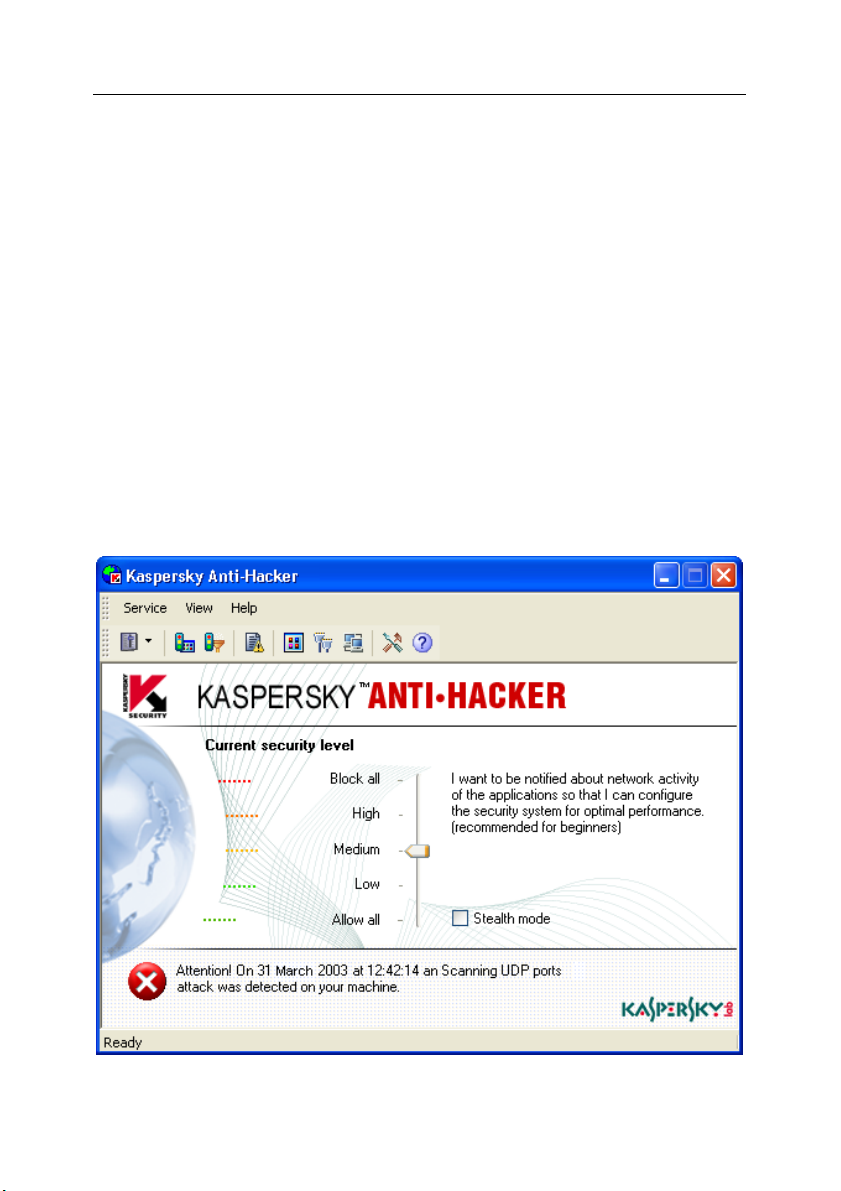
5.6. Workspace
The main window workspace includes the security scale and information about
the current status of your security system.
The security scale allows you to select one of the following security levels:
• Block all
• High
• Medium
• Low
• Allow all
You can switch to another security level by dragging the slider along the scale. If
you do this, a detailed description of the new current security level will appear to
the right of the new slider position (for details see subchapter 4.2 on page 23).
and the new mode will be applied immediately.
With the High, Medium or Low level enabled you can set the supplementary
security tool – Stealth mode (see subchapter 4.2 on page 23).
Page 34

34 Kaspersky Anti-Hacker
Below the scale you can see details of the last hacker attack detected by the
program. Information includes the attack date and time, the attack type, and the
source computer address.
5.7. Status Bar
At the bottom of the main window you can see the status bar. It displays tips for the user about the main window item currently selected. You can also hide and display the bar by selecting the Status Bar command from the View menu.
5.8. Context Menu
Context menus in the program dialog boxes allow you to initiate commands that
are applicable to the particular dialog box.
To display the dialog box context menu, right click within it.
5.9. Rule Wizards
The program wizard allowing creation/editing of the user rules includes several
dialog boxes. Each dialog box contains a set of buttons allowing the user to
manage the process of rule creation/modification. These buttons are:
• Finish – applies the defined settings and creates the rule.
• Cancel – cancels the procedure.
• Next > – takes you to the next wizard box.
• < Back – takes you to the previous wizard box.
• Help – displays the Help topics.
Page 35

Running the Program 35
5.10. Changing and Saving Interface
Settings
To change the interface settings, select Customize from the Toolbars
submenu of the View menu.
The Customize dialog box will appear on your screen (see fig. 15).
Fig. 15. The Customize dialog box
While changing the interface it is advisable that you arrange your screen so that
the Customize dialog box does not overlay the main window menu bar and
toolbar.
You can use the Commands page to change the main window menu and toolbar
layouts. To add new commands you should drag the required command from the
list to the menu bar or the toolbar. To remove a command from the menu bar or
the toolbar you should drag it outside of the main window.
The Toolbars and Menu pages allow you to restore the original appearance of
your toolbars and menus.
Page 36

36 Kaspersky Anti-Hacker
The Settings page allows you to enable/disable screen tips for the toolbar
buttons, to select their size, and to define the layout of your menu bar.
If required, you may change the titles of menu commands and buttons, and
display toolbar buttons as images or as text.
To change the title and/or other properties of a command or a button,
follow these steps:
1. Display the Customize dialog box and select the required command or
button within the main window.
2. Press the right mouse button. Select the required command from the
context menu on your screen:
• Delete – removes the selected menu command or button.
• Button Appearance – allows you to change the title. A dialog
box with the same name will appear on your screen. Change
the button/menu command title in the Button text field (see
fig. 16). Press the OK button.
• Image – displays the selected menu command/button as an
image.
• Text – displays the selected menu command/button as an im-
age.
• Image and Text – displays the selected menu command/button
as an image with text.
• Start Group – inserts a separator before the selected menu
command/button.
Page 37

Running the Program 37
Fig. 16. Changing command properties
The new interface settings are saved automatically and applied immediately after
the changes are made. These changes will be preserved during all subsequent
program sessions.
5.11. Exiting the Program
To unload the program from computer memory, select Exit from the system or
the main window Service menu. You can also close the main window by clicking
on the
button in the right upper corner of the window.
However, closing the main program window does not unload the
program from computer memory if the Minimize the program main
window to the system tray on closing checkbox is checked. By
default, this box is checked, but you may uncheck it if required (see
subchapter 6.1.1 on page 38). By placing the icon in the system tray the
program indicates that it is loaded into your computer memory.
Page 38

CHAPTER 6. ENABLING THE
SECURITY SYSTEM AND
DEFINING ITS SETTINGS
6.1. Enabling the Security System
and Selecting the Security
Level
How to enable security of your
computer using Kaspersky AntiHacker? How to select the required
security level?
6.1.1. Enabling the Security System
Your security system is enabled as soon as you install Kaspersky Anti-Hacker on
your computer and reboot the operating system. After the program is started, the
icon appears in the system tray. By default, the program implements the
Medium level and if a network application on your computer attempts to connect
to a local network or the Internet, the training mode is activated. The application
and the network operation details are displayed on your screen. On the basis of
this data the program will prompt you to choose one of the following courses of
action: to allow or to block this event once, to completely block activity of this
application, to allow the application activity according to type, or to define a
complex rule for this event. Depending on your answer, the program will create a
rule for this application that will subsequently be applied by the program
automatically.
Kaspersky Anti-Hacker starts protecting your computer after user's logon.
However, you may set the program to enable security as soon as the Windows
operating system starts.
Page 39

Enabling the Security System and Defining its Settings 39
To enable Kaspersky Anti-Hacker to start immediately after the operating system is booted, follow these steps:
1. Select Settings from the Service menu.
2. On the General page of the Settings dialog box (see fig. 17), check the
Launch the security system when the operation system starts
checkbox. In this case, the program will start with the user settings
immediately after the operating system is booted, but the logs will be
disabled. If the program implements the Medium level, all network
communications will automatically be permitted until you enter the
operating system because the training window cannot be displayed
without a user in the system. At the Low or the Allow all level the
program will permit unknown network communications for this time
period, and at the other security levels all unknown network
communications will be blocked.
Suppose your computer is connected to a local network and you enable
the program to launch the security system as soon as the operating
system starts. Suppose also that you block all network traffic by selecting the Block all security level, or by creating an appropriate packet
filtering rule at any security level (except for Allow all). In this case, you
will have to wait longer than usual before entering the system and after
entering you will find that the local network is not available.
Fig. 17. The Settings dialog box
You can change the assignment of the button in the upper right corner of the
main window. By default, this button minimizes the main window to the system
tray while the program remains in your computer memory.
Page 40

40 Kaspersky Anti-Hacker
To change the assignment of the
gram from computer memory when the main window closes, follow
these steps:
1. Select Settings from the Service menu.
2. On the General page of the Settings dialog box (see fig. 17) uncheck
Minimize the program main window to the system tray on
the
closing checkbox.
By default, if the program detects an attack on your machine, the main window
appears on your screen with an appropriate message.
To disable the main window display every time an intrusion is detected,
follow these steps:
1. Select Settings from the Service menu.
2. On the General page of the Settings dialog box (see fig. 17) uncheck
Show main window when an intrusion is detected checkbox.
the
button so that it unloads the pro-
6.1.2. Selecting the Security Level
You can change the security level by dragging the slider along the security scale
within the program main window or by selecting the Security level command
from the Service menu. Alternatively, you can select the appropriate command
from the system menu.
You can switch to one of the following security levels:
• Block all
• High
• Medium
• Low
• Allow all
With the High, or the Medium, or the Low level enabled you can enable a
supplementary security tool by checking the Stealth mode checkbox.
Page 41

Enabling the Security System and Defining its Settings 41
Security levels are applied right after the user selects them.
For details of the available security levels see subchapter 4.2 on page 23.
6.1.3. Network Event Warning
If you created a rule and checked the Display warning checkbox (see
subchapter 0 on page 59, subchapter 6.4.2.2 on page 67), when the program
applies this rule, an appropriate message will appear on your screen (see
fig. 18).
See figure 18 for an example of such a message, which appears after an
appropriate packet filtering rule is applied. The message describes the related
remote and local addresses, and also the ports used.
You can review the corresponding packet filtering rule by clicking on the
hyperlink.
You can also disable subsequent warnings for this event by checking the Do not
show this warning checkbox.
Fig. 18. An example of a Kaspersky Anti-Hacker warning
When creating a rule you can check the Log event checkbox to log the
corresponding event.
Page 42

42 Kaspersky Anti-Hacker
6.1.4. Training Window (Medium Level)
The program displays its training window (see fig. 19) when it detects an
unknown event while running with the Medium level selected.
Fig. 19. An example of a training window
At the top of this box you can see the name of the application requesting
connection with a remote machine, the remote machine address, and the port
numbers. If required, you can display more details of the requested connection
by clicking on the … details hyperlink.
You can allow or block this specific operation by clicking on the Allow once or
Block once buttons, respectively.
If you close the training window by pressing the
right corner, the operation at issue will be blocked this time.
To define a rule that will later handle events initiated by this application, select
one of the actions listed below and click on the ОК button. After this, the new rule
will be added to your list of application rules.
• Allow activity of the application according to its type – allows only
network communication that is compliant with the specified application
button in its upper-
Page 43

Enabling the Security System and Defining its Settings 43
type. Select the required type from the drop-down list below the option
button (for details see subchapter 6.3.2.1 on page 49).
• Disable all activities of the application – blocks the specified applica-
tion from any kind of network activity including the described operation.
• Customize the rule ... – allows you to specify the operations that will be
allowed for this application. If you select this option button and click ОК,
the Rule Wizard box will appear on your screen (for details of the wizard
see subchapter 6.3.2 on page 49).
If you create a rule that does not correspond to the described event, an
appropriate message will appear on your screen (see fig. 20). Then you
may press the Yes button to add the created rule to the list, or the No
button if this rule was created by mistake. In both cases you will be
prompted to select another option from the list in the training window.
Fig. 20. The rule you created does not correspond to the current event
Note that if several programs on your computer within a short period of
time will attempt to perform network operations that are not described
by the user rules, the queue of requests for rule creation will be generated. These requests will be successively displayed within the training
window: first you will have to define the program response to actions of
the first network application, then the second and so on. All the programs in this queue will be waiting for your reaction.
6.1.5. The Executable Module Substitution
Warning
Kaspersky Anti-Hacker protects your network applications from the unauthorized
attempts to substitute their original executable files. If this kind of substitution
detected Kaspersky Anti-Hacker displays the appropriate warning (see
figure 21).
You can select one of the following options:
Page 44

44 Kaspersky Anti-Hacker
• Block any further network activity of this application – all the fur-
ther network operations of this application will be prohibited: the appropriate blocking rule will be added to the beginning of the application rule list and all other rules in this list will be disabled. It is advisable that you start your anti-virus program to check for viruses in this
application, or restore this application from the archive, or rein-
stall it. After you did this, please delete the blocking rule from
the application rule list and enable all other rules in this list.
If
Kaspersky Anti-Hacker display the “executable module substituted” message again, please select the below option.
• I know that the file was modified, and continue to trust to this
application
will be also valid for the modified file.
Press the ОК button.
– all the user rules available currently for this application
Fig. 21. The Executable Module Substitution Warning
Page 45
Enabling the Security System and Defining its Settings 45
6.2. How the Program Responds to
Attack
What happens when an external
attack is detected by your security
system?
If your security system detects a hacker attack on your machine, the program
main window appears on your screen (as long as you have not unchecked the
Show main window when an intrusion is detected checkbox – see
subchapter 6.1.1 on page 38). If this happens, be sure to read thoroughly the
attack details at the bottom of the window workspace; the program displays the
date, the time and the attack type (see fig. 24).
This attack will be blocked. The program will also block the assaulting machine
for the time period defined by settings (see subchapter 6.5 on page 69).
Fig. 22. An example of an attack-detected message
Page 46
46 Kaspersky Anti-Hacker
Suppose you discover that your computer is constantly being attacked from
some remote machine. You may prohibit your computer from communication
with certain remote addresses by configuring appropriate packet filtering rules
(see subchapter 6.4 on page 60).
If attacks from a certain remote address are frequent, it is advisable that you
switch to the Block all security level and refer to your system administrator or IP.
6.3. Customizing Application Rules
How to create an application rule?
The application rule wizard
6.3.1. Managing the Rule List
To display the application rule list on your screen,
Select Application rules from the Service menu.
The Application rules dialog box will appear on your screen (see fig. 23).
Page 47

Enabling the Security System and Defining its Settings 47
Fig. 23. The Application rules dialog box
In the upper section of the dialog box, you will find the list of application rules.
The Application column includes the related application icons, their names, and
the checkboxes allowing you to enable/disable these rules. The Action column
includes details of the action performed by the corresponding rule; Allow, for
rules permitting some events, and Block, for rules blocking some events.
The rules are listed according to their priority. The rule at the top of the list will be
applied first, and only then will the program apply the second rule etc. If an
application attempts to perform some network operation, the program compares
this activity against the list of rules, looking through the list from its top to the
bottom until it finds the rule corresponding to this operation or until it looks the
entire list through. If the corresponding rule is not detected, the default action is
applied (see subchapter 4.2 on page 23). Thus, if you want to block only some
operations for an application, you should create two rules for this application: the
first rule should allow the desired operations for this application while the second
rule should block all the operations for this application. Besides, the first rule
Page 48

48 Kaspersky Anti-Hacker
must be located above the second in the rules’ list. If you do so and the
application will attempt to perform an allowed operation, Kaspersky Anti-Hacker
will search the list of rules and detect the rule allowing this operation. If the
operation is unwanted, Kaspersky Anti-Hacker will use the second rule blocking
all the operations for this application.
For example, as you can see in figure 23, the third application rule blocks
Internet Explorer from accessing the Internet, but the second rule allows this
program to communicate via the Internet by using the HTTP protocol. Since the
second rule is higher priority than the third one, Internet Explorer is allowed to
communicate with remote HTTP servers (but only these).
Remember that only the rules with checked boxes are applied. For example, in
figure 23 the fourth and the fifth rule boxes are disabled.
To enable/disable an application rule,
Check/uncheck the corresponding checkbox in the list of application
rules.
To the right of the rule list you can see the following buttons:
• New... – allows you to create a new rule. If you press this button, the ap-
plication rule wizard box will appear on your screen.
• Modify – allows you to edit the selected rule. If you press this button, the
application rule wizard box will appear on your screen.
• Remove – removes the selected rule from the list.
• Move up – moves the selected rule up one line, i.e. increases the rule
priority.
• Move down – moves the selected rule down one line, i.e. reduces the
rule priority.
To modify a rule selected from the list, you can also press the <ENTER> key or
double-click on it; to remove the selected rule from the list - the <D
to add a new rule to the list - the <I
NS> key.
EL> key; and
You can also modify the list from the context menu, which includes the following
commands:
• Modify… – allows you to edit the selected rule.
• Remove – removes the selected rule from the list.
Page 49

Enabling the Security System and Defining its Settings 49
• Duplicate rule – creates a copy of the selected rule. The created copy
will be placed right below the selected rule.
Below the list, you can see the Rule description section displaying details of the
rule selected from the upper frame list. The same section is located in the rule
wizard boxes so we shall describe this frame in detail.
The rule description includes black text that cannot be modified, and blue text
that must be substituted with appropriate values. If a setting is written in a bold
font it means that its value is critical for this rule.
To enter or modify the required value in the rule description,
1. Click on the appropriate underlined link in the Rule description frame.
2. Select the required value in the dialog box on your screen (for details
see the subchapters below).
At the bottom of the Application rules dialog box you will see the following
buttons:
• ОК – closes the dialog box and saves the changes you made.
• Cancel – closes the dialog box without saving the changes.
All the changes you made to the list will be applied immediately after
these are saved.
6.3.2. Adding a New Rule
To launch the application rule wizard:
Press the New... button in the Application rules dialog box (see
fig. 23).
6.3.2.1. Step 1. Customizing the Rule
When you start the wizard, a dialog box similar to that in fig. 24 will appear on
your screen.
Page 50

50 Kaspersky Anti-Hacker
Fig. 24. The first dialog box of the application rule wizard
The Action options list allows you to select one of the following three options:
Action Rule description
• Allow activity of the
application
according to its
type.
• Disable all activities
of the application.
• Customize the rule.
If you select Customize the rule, the next wizard box may prompt you
to define additional settings.
• Internet-application type (client or server)
Page 51

Enabling the Security System and Defining its Settings 51
• Protocol
• Remote address
• Remote port
• Local port
To create a rule allowing activity of the application according to its type:
1. Select Allow activity of the application according to its type from
the list of options in the Action section.
2. Click on the specify the application name
hyperlink in the Rule
description section. Specify the required application name in the
Select the application dialog box on your screen.
3. Define the application type by clicking on the appropriate hyperlink in
the Rule description section. The default value is Allow all,
which
does not limit the application rights in any way. To change it, click on it
and select another value from the drop-down list within the Specify the
application type dialog box (see fig. 25). Then press the ОК button.
• Web browser – for Internet browsers such as Netscape Navigator and others. Communication via HTTP, HTTPS, FTP protocols, and proxy servers is allowed.
• File transferring – for Reget, Gozilla and similar programs.
Communication via HTTP, HTTPS, FTP, TFTP protocols, and
standard proxy servers is allowed.
• Mail – for MS Outlook, MS Outlook Express, the Bat, and other
mail programs. Communication via SMTP, NNTP, POP3, and
IMAP4 protocols is allowed.
• News – for Forte Agent and other news programs. Communication via SMTP and NNTP protocols is allowed.
• Instant messaging – for ICQ, AIM, and other chat programs.
Communication via standard proxy server and direct computerto-computer link is allowed.
• Internet Rely Chat – for mIRC and similar programs. Standard
user authentication for IRC networks and access to IRC server
ports is allowed.
Page 52

52 Kaspersky Anti-Hacker
• Business Conferences – for MS NetMeeting and similar programs. Communication via HTTP and HTTPS protocols, and
also via standard proxy servers is allowed. The type also supports communication within the local network (LDAP and others).
• Remote Management – for Telnet, etc. Communication via Telnet and SSH protocols is allowed.
• Time Synchronization – for Timehook and similar programs.
Connection to time and daytime servers is allowed.
Fig. 25. Selecting the application type
To block the application from any network communication,
1. Select Disable all activities of the application from the list of options
in the Action section.
2. Click on the specify the application name
hyperlink in the Rule
description section. Specify the required application name in the
Select the application dialog box on your screen.
If the settings described above do not allow you to create the required rule (for
example, if you want to allow communication to a certain IP address), you can
configure a more complicated rule.
To configure a more complicated rule, follow these steps:
1. Select Customize the rule from the list of options in the Action section.
Page 53

Enabling the Security System and Defining its Settings 53
2. Click on the specify the application name hyperlink in the Rule
description section. Specify the required application name in the
Выбор приложения dialog box on your screen.
3. Click on the Allow all hyperlink in the Rule description section. Select
the required action from the following list of options in the Specify
Action dialog box (see fig. 26) and press the ОК button:
• Block all
• Allow all
4. Select the application activity to be monitored and regulated by this rule;
establishment (default) or receipt of connection. To change the default
activity, click on the establish connections
hyperlink in the Rule
description section. Select the Receiving an incoming network
connection from a remote machine option in the Select the
application activity type dialog box (see fig. 27) and press the ОК
button.
When you have finished selecting options in the first wizard box, press the
Next > button.
Fig. 26. Selecting the action
Fig. 27. Selecting the application activity type
If you press Next > without selecting an application, a message
prompting you to do so will appear on your screen.
6.3.2.2. Step 2. Rule Conditions
The rule conditions wizard box appears on your screen only if you selected the
Customize the rule option button in the first wizard box.
Page 54

54 Kaspersky Anti-Hacker
In this wizard box you can specify the protocol, the remote machine address, and
the ports.
The Protocol: a drop-down list on this dialog box includes the following
predefined protocols and the corresponding port numbers:
• HTTP
• SMTP
• POP3
• IMAP
• NNTP
• DNS
If you want to define another port number, select one of the following items from
this drop-down list:
• Other TCP based protocol – for services based on the TCP protocol
• Other UDP based protocol – for services based on the UDP protocol
The Settings list includes additional settings and its content fully depends on the
protocol selected from the above drop-down list.
Remote address – the address of the remote computer involved in the
communication. To define the address, click on the corresponding specify
the address hyperlink in the Rule description section. To specify more
than one address hold down the <C
TRL> key and click on the hyperlink. For
details see subchapter 6.3.2.2.1 on page 55.
Remote port – the remote port number. To specify the port click on the cor-
responding specify the port
specify more than one port, hold down the <C
hyperlink in the Rule description section. To
TRL> key and click on the hy-
perlink. For details see number. To specify the port click on the corresponding specify the port hyperlink subchapter 6.3.2.2.2 on page 58.
Local port – the local port in the Rule description section. To specify more
than one port hold down the <C
TRL> key and click on the hyperlink. For de-
tails see number. To specify the port click on the corresponding specify the
port hyperlink subchapter 6.3.2.2.2 on page 58.
Page 55

Enabling the Security System and Defining its Settings 55
Fig. 28. Defining the rule conditions
6.3.2.2.1. Defining the Address or the Address Range
To define the required addresses you must use two dialog boxes.
The Specify the address or the address range dialog box (see fig. 29) appears
on your screen when you hold down the <C
address hyperlink in the second rule wizard box.
TRL> key and click on specify the
Page 56

56 Kaspersky Anti-Hacker
Fig. 29. The Specify the address or the address range dialog box
Here you can use the Add and Remove buttons to add the required number of
computer addresses, address ranges, and subnet addresses. When you have
finished configuring the address list, press the OK button and return to the rule
wizard box.
When you press Add in the Specify the address or the address range dialog
box, the Specify the address dialog box (see fig. 30) will appear on your screen.
The same dialog box appears on your screen when you click on specify the
address hyperlink in the second rule wizard box without holding down the
<C
TRL> key.
The Specify the address dialog box allows you to specify the address, the
address range, or the subnet address to be used in your rule (see fig. 30).
Page 57

Enabling the Security System and Defining its Settings 57
Fig. 30. The Specify the address dialog box with The computer address option selected.
Here you can select one of the following options:
• The computer address – allows you to specify the computer by its sym-
bolic (e.g. www.kaspersky.com) or IP (e.g. 192.168.1.1) address.
• The range of IP addresses – allows you to specify the address range by
using the Begins from: and the Ends by: fields (see fig. 31).
• The subnet address – allows you to specify the subnet address in the
Subnet address: field, and/or the subnet mask in the Subnet mask: field
(see fig. 32).
When you have specified the required address, press the ОК button.
Page 58

58 Kaspersky Anti-Hacker
Fig. 31. The Specify the address dialog
box with The range of IP addresses option
selected
Fig. 32. The Specify the address dialog
box with The subnet address option
selected
6.3.2.2.2. Defining the Port or the Port Range
To define the required port(s) you must use two dialog boxes.
The Specify the port or the port range dialog box (see fig. 33) appears on your
screen when you hold down the <C
hyperlink in the second rule wizard box.
TRL> key and click on specify the port
Fig. 33. The Specify the port or the port range dialog box
Page 59
Enabling the Security System and Defining its Settings 59
Here you can use the Add and Remove buttons to add the required number of
computer ports and port ranges. When you have finished configuring the port list,
press the OK button and return to the rule wizard box.
When you press Add in the Specify the port or the port range dialog box, the
Port dialog box (see fig. 30) appears on your screen. The same dialog box
appears on your screen when you click on specify the port hyperlink in the
second rule wizard box without holding down the <C
TRL> key.
The Port dialog box allows you to specify the port or the port to be used in your
rule (see fig. 34).
Here you can select one of the following two options:
• Specify the port number – allows you to select one of the predefined
values from the drop-down list or to enter the port number from your keyboard.
• Specify the port range – allows you to specify the required port range by
entering the starting port in the first text field, and the last port in the second text field (see fig. 35).
Fig. 34. The Port dialog box
Fig. 35. Defining the port range
When you have specified the required port(s), press the OK button.
6.3.2.3. Step 3. Additional Actions
The third wizard box allows you to enable additional actions for your rule. It
contains the following two checkboxes: Log event - if checked, this logs
Page 60

60 Kaspersky Anti-Hacker
detected events, and Display warning – if checked, this displays a message
about the detected event (see fig. 36).
Fig. 36. Additional actions for your rule
6.4. Customizing Packet Filtering
Rules
How to create a packet filtering rule?
The packet filtering rule wizard
6.4.1. Managing the Rule List
Management of the packet filtering rule list is similar in many respects to
management of the application rule list.
Page 61
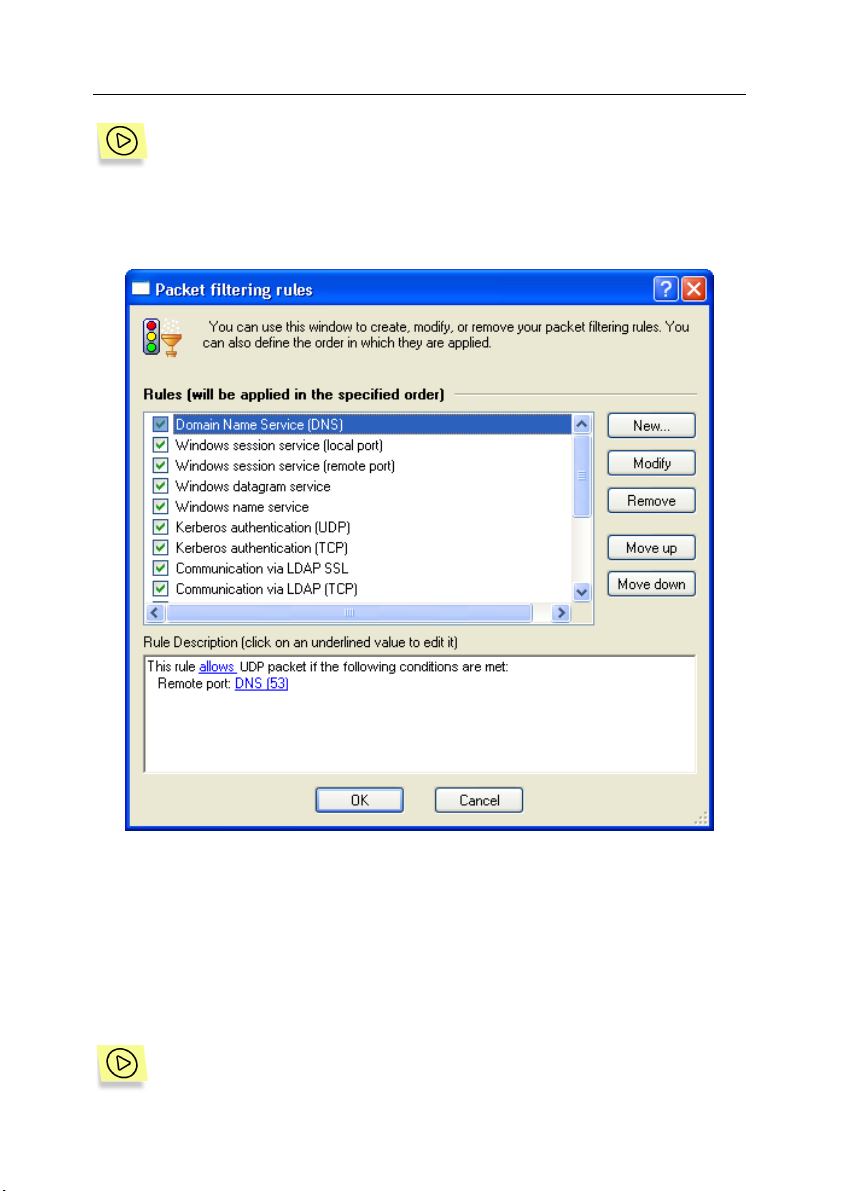
Enabling the Security System and Defining its Settings 61
To display the packet filtering rule list on your screen,
select Packet filtering rules from the Service menu.
The Packet filtering rules dialog box will appear on your screen (see fig. 37).
Fig. 37. The Packet filtering rules dialog box
In the upper section of the dialog box, you will find the list of packet filtering rules.
Checkboxes to the right of each rule allow you to enable/disable these rules.
The rules are listed according to their priority; the rule at the top of the list will be
applied first, then the program will apply the second rule etc. Remember that only
rules with checked boxes are applied.
To enable/disable a packet filtering rule,
check/uncheck the corresponding checkbox in the list of packet filtering
rules.
Page 62

62 Kaspersky Anti-Hacker
To the right of the rule list you can see the following buttons:
• New... – allows you to create a new rule. If you press this button the
packet filtering rule wizard box will appear on your screen.
• Modify – allows you to edit the selected rule. If you press this button the
packet filtering rule wizard box will appear on your screen.
• Remove – removes the selected rule from the list.
• Move up – moves the selected rule up one line, i.e. increases the rule
priority.
• Move down – moves the selected rule down one line, i.e. reduces the
rule priority.
To modify a rule selected from the list, you can also press the <E
double-click on it; to remove the selected rule from the list - the <D
to add a new rule to the list - the <I
NS> key.
NTER> key or
EL> key; and
You can also modify the list from the context menu, which includes the following
commands:
• Modify – allows you to edit the selected rule.
• Remove – removes the selected rule from the list.
• Duplicate rule – creates a copy of the selected rule. The copy will be
placed right below the selected rule.
Below the list, you can see the Rule description section displaying details of the
rule selected from the upper frame list. The same section is located in the rule
wizard boxes so we shall describe this frame in detail.
The rule description includes black text that cannot be modified, and blue text
that must be substituted with appropriate values. If a setting is written in a bold
font it means that its value is critical for this rule.
To enter or modify the required value in the rule description,
1. Click on the appropriate underlined link in the Rule description sec-
tion.
2. Select the required value in the dialog box on your screen (for details
see the subchapters below).
At the bottom of the Packet filtering rules dialog box you will see the following
buttons:
Page 63

Enabling the Security System and Defining its Settings 63
• ОК – closes the dialog box and saves the changes you made.
• Cancel – closes the dialog box without saving the changes.
All the changes you made to the list will be applied immediately after
they are saved.
The packet filtering rules are of higher priority than the application rules and
therefore will be executed first.
6.4.2. Adding a New Rule
The packet filtering rule wizard is in many respects similar to the application rule
wizard. However it includes only two wizard boxes.
6.4.2.1. Step 1. Rule Conditions
The first rule wizard box allows you to specify:
• The protocol used (TCP, UDP, ICMP, other IP protocols)
• The packet destination address
• The traffic direction (outgoing, incoming)
• The protocol-dependent settings (the ports for the TCP and UDP proto-
cols, the message types for the ICMP protocol, the protocol number for
other IP protocols)
• The action (allow/block)
Page 64

64 Kaspersky Anti-Hacker
Fig. 38. The first wizard box for packet filtering rules
To configure a packet filtering rule, follow these steps:
1. Select the protocol to be filtered from the Protocol drop-down list. The
available values are TCP (Transmission Control Protocol), UDP
(User Datagram Protocol), ICMP (Internet Control Message Protocol), and Other IP protocols. The default value is TCP.
2. Check the following checkboxes in the Properties section:
Packet Type (incoming or outgoing) – this concerns traffic direction.
By default the checkbox is unchecked, which allows filtering of both the
incoming and outgoing traffic. If you want to control only the incoming or
the outgoing traffic check this checkbox and specify the required packet
type in the Rule description section. To enter the required value click
on the packet type
hyperlink and select the required option in the
Specify the direction of the packet dialog box, then click the ОК but-
ton.
Page 65

Enabling the Security System and Defining its Settings 65
Fig. 39. The Specify the direction of the packet dialog box
3. Some checkboxes in the Properties section are protocol dependent.
• For the TCP and UDP protocols you must specify the Remote
port and the Local port.
• For the ICMP protocol you must specify the ICMP message
type.
• For other IP based protocols you can specify the Protocol.
Remote address – the remote machine address (for all the proto-
cols).
Local address – the local machine address (for all protocols).
To define the address (whether local or remote), click on the corresponding specify the address
section. To specify more than one address, hold down the <C
hyperlink in the Rule description
TRL>
key and click on the hyperlink. For details see subchapter 6.3.2.2.1
on page 55.
Remote port – the remote port number (for the TCP and UDP pro-
tocols).
Local port – the local port number (for the TCP and UDP proto-
cols).
To define the port (whether local or remote), click on the corresponding specify the address
section. To specify more than one address, hold down the <C
hyperlink in the Rule description
TRL>
key and click on the hyperlink. For details see number. To specify
the port click on the corresponding specify the port hyperlink subchapter 6.3.2.2.2 on page 58.
Page 66

66 Kaspersky Anti-Hacker
ICMP message type – the ICMP message type (only for the ICMP
protocol). To specify the message type, click on the corresponding
specify the ICMP message type
hyperlink in the Rule description section and select the required value from the Specify the
ICMP message type dialog box drop-down list (see fig. 40), then
click on the ОК button.
" Echo request
" Echo reply
" Trace route (TTL exceed)
" Net unreachable
" Host unreachable
" Protocol unreachable
" Port unreachable
" Redirect for host
" Redirect for net
" Redirect for TOS and net
" Redirect for TOS and host
Fig. 40. The Specify the ICMP message type dialog box
Protocol – the protocol name or number (only for IP protocols). If
you leave this checkbox unchecked, the program handles all the IP
protocols. To specify the required protocol name or number, click
on the specify the protocol
hyperlink in the Rule description sec-
tion and select the required value from the Specify the protocol
dialog box drop-down list (see fig. 41) then press the ОК button. In
the list of available protocols below you can see the protocol numbers enclosed with brackets.
Page 67

Enabling the Security System and Defining its Settings 67
• IGMP,RGMP(2)
• GGP(3)
• IP in IP encapsulation(4)
• TCP(6)
• IGRP(9)
• UDP(17)
Fig. 41. The Specify the protocol dialog box
• GRE(47)
• ESP(50)
• AH(51)
• IP with encryption(53)
4. Specify the action to be applied to packets meeting the above defined
conditions - block or allow. By default, the Block option is selected. To
change the value, click on the corresponding hyperlink in the Rule de-
scription section and select the required value in the Specify Action
dialog box, then press the ОК button (see fig. 42).
Fig. 42. The Specify Action dialog box
6.4.2.2. Step 2. Rule Name and Additional
Actions
You must specify the packet filtering rule name in the Name of the rule text field
of the second wizard box. By default, the program suggests a unique name, such
as Packet filtering rule #<serial number of the rule>. However, it is advisable that
you specify a meaningful name that will make it easy for you to identify the
required rule in the list.
Page 68

68 Kaspersky Anti-Hacker
You can also enable additional actions for your rule. The wizard contains the
following two checkboxes: Log event - if checked, this logs detected events, and
Display warning – if checked, this displays a message about the detected event
(see fig. 18).
Fig. 43. Defining the rule name and additional actions
Page 69

Enabling the Security System and Defining its Settings 69
6.5. Intrusion Detection System
How to configure the intrusion
detection system for optimal
performance?
6.5.1. Intrusion Detector Settings
To display the intrusion detector settings,
select Settings from the Service menu and switch to the Intrusion
Detection System page (see fig. 44).
It is advisable that you always keep the checkbox located on the Intrusion Detection System page checked. This checkbox allows you to enable/disable detection of external intrusions on your machine.
Below this checkbox you can see the Assaulter blocking time (min.) spin box,
which allows you to define the time period for the assaulter machine to be
blocked when a remote address is detected. This setting is applied to all attack
types.
If you change the Assaulter blocking time parameter, it will be applied
for all new attacks immediately after pressing the OK button in the
Settings window. As regards computers which were blocked due to
previous attacks their blocking time period won't be changed.
The set of fields located at the bottom of this page depends on the attack type
selected from the Attack type drop-down list.
Check the Enable detection of this attack checkbox if you want the program to
detect the selected type of attack. Below the checkbox you can see information
on attack types, which may be useful if you are not sure which option to choose.
Enable Intrusion Detection System
Page 70

70 Kaspersky Anti-Hacker
Fig. 44. The Intrusion Detection System page of the Settings dialog box
6.5.2. The List of Detectable Attacks
Kaspersky Anti-Hacker is able to detect the most commonly used DoS attacks
(SYN Flood, UDP Flood, ICMP Flood), the Ping of death, Land, Helkern,
SmbDie, and Lovesan attacks, and also to detect port scanning operations,
which are usually followed by a more powerful attack:
• The Ping of death attack involves sending of an ICMP packet exceeding
64 Kb (threshold value) to your computer. It may result in emergency
shutdown of some operating systems.
• The Land attack involves transmission of a self-connection request (when
a computer is requested to connect to itself) to your computer. It results in
an endless loop as your computer attempts to connect to itself. Conse-
Page 71

Enabling the Security System and Defining its Settings 71
quently, the CPU load and the probability of emergency shutdown increase drastically.
• The Scanning TCP ports attack involves detection of open TCP ports on
your computer. This type of attack is used to search a computer for weak
points and is usually followed by more dangerous attack types. You can
define the following settings for this attack type: Port count: – the number
of ports the remote machine attempts to open, and Time (sec): – the time
it takes.
• The Scanning UDP ports attack involves detection of open UDP ports on
your computer. The attack is detected by the quantity of UDP packets
sent to various computer ports over a certain time period. This type of attack is used to search a computer for weak points and is usually followed
by more dangerous attack types. You can define the following settings for
this attack type: Port count: – the number of ports the remote machine
attempts to open, и Time (sec): – the time it takes.
• The SYN Flood attack involves sending of a false connection request set
to your computer. The system reserves certain resources for every connection request. As a result the computer does not respond to connection
requests from other sources. You can define the following settings for this
attack type: Connection count: – the number of connections the remote
machine attempts to establish, and Time (sec): – the time it takes.
• The UDP Flood attack involves sending of special UDP packets to your
computer. These packets are endlessly transmitted between the affected
machines. Consequently, this attack consumes substantial resources and
overloads the communication link. You can define the following settings
for this attack type: UDP packet count: – the number of incoming UDP
packets, and Time (sec): – the time it takes.
• The ICMP Flood attack involves sending of ICMP packets to your com-
puter. It results in an increase in the CPU load of the affected machine as
it responds to every packet. You can define the following settings for this
attack type: ICMP packet count: – the number of incoming ICMP pack-
ets, and Time (sec): – the time it takes.
• The Helkern attack involves sending of special UDP packets (able to exe-
cute a malicious code) to an attacked machine. This attack results in
slowdown of the Internet connection.
• The SmbDie attack involves an attempt to establish an SMB connection;
if the attack is successful, a special packet overflowing the machine buffer
is delivered to an attacked machine. As a result the user will have to restart the operating system. Windows 2k/XP/NT operating systems are
susceptible to this kind of attack.
Page 72

72 Kaspersky Anti-Hacker
• The Lovesan attack attacks a vulnerability in the DCOM RPC service of
Windows NT 4.0/NT 4.0 Terminal Services Edition/2000/XP/Server (tm)
2003 operating systems of your computer. When the vulnerability is detected, the worm, which includes malware allowing the sender to perform
any desired manipulations on your computer, is downloaded to the victim
machine.
Page 73

CHAPTER 7. VIEWING
PERFORMANCE RESULTS
7.1. Viewing the Current Status
Viewing the list of active
applications, open ports and
established connections
Performance of all network applications running on your machine is permanently
monitored and recorded by Kaspersky Anti-Hacker. You can review the following
network activity statistics:
• Active applications. Network operations are classified on the basis of in-
volved applications. For every application on your machine you can review the ports and connections that are handled by this application.
• Established connections. Displays all incoming and outgoing connec-
tions, remote computer addresses, and port numbers.
• Open ports. Displays all ports that are open on your machine.
7.1.1. Active Applications
To review the list of network applications that are currently active,
select Active applications from the Show submenu of the View menu
(see fig. 45). You can also press the button in the toolbar.
The Active network applications dialog box will appear on your screen.
Page 74

74 Kaspersky Anti-Hacker
Fig. 45. The Active network applications dialog box
This dialog box allows you to review the list of active network applications and
the network resources used by them. The application names are sorted
alphabetically, which allows you to navigate easily through the list. To the left of
every application name in the list you can see the application icon.
By expanding the required application joint you can display the list of
corresponding ports open on your machine and the connections established by
this application. Indicators are as follows:
• Open ports are indicated by the TCP or the UDP icon, depending on the
port type. To the right of every port you can see its number.
• Established connections are indicated by the
your machine, or by the
icon, if received from outside. The connection
icon, if established by
Page 75

Viewing Performance Results 75
settings are described to the right of the icon:
<source address>:<source port> !
<destination address>:<destination port>
The list of active network applications is refreshed automatically twice a second.
The list has a context menu that includes the following commands:
• Refresh – refreshes the active applications list on user demand.
• Create rule – allows you to create a rule for a selected port or connec-
tion. The program launches the application rule wizard, and automatically
enters the selected port or connection details in the appropriate fields.
• Break connection – breaks the connection selected (this command is
available only if you have selected a connection from the list).
Attention! If you force a connection to break, the related application may
function incorrectly.
• Properties – displays more details of the item selected from the list,
namely, application (see fig. 46), connection (see fig. 48) or port (see
fig. 50).
The list may contain more than one string for the same application. This
means that more than one copy of this application is running. When you
expand joints of the application copies, you may see different lists of
open ports and established connections.
Page 76

76 Kaspersky Anti-Hacker
Fig. 46. The Properties of the application dialog box
In the application properties dialog box you will see the Application information
section, which includes the following items:
• Application name – the executable file name
• Application ID – the application identifier
• Application file – the full path to the executable file
Below the Application information section you will find another section called
Manufacturer information, which includes the following items:
• Manufacturer – the manufacturer name
• Application version – the program version
• File version – the executable file version
Page 77

Viewing Performance Results 77
7.1.2. Established Connections
To review the list of network connections currently established,
select Established connections from the Show submenu of the View
menu (see fig. 47). You can also press the
The Established Connections dialog box will appear on your screen.
Each line on this list includes details of a single established connection. These
connections are indicated by the
icon, if received from outside.
the
The list also includes the following connection details:
• Remote address – the address and the port of a remote machine with
which a connection is established.
• Local adress – your computer address and port.
• Application – the application that established this connection.
You may sort the list by any of the titles described above.
icon, if established by your machine, or by
button in the toolbar.
Page 78

78 Kaspersky Anti-Hacker
Fig. 47. The Established Connections dialog box
The list of established connections is refreshed automatically twice a second.
If required, you may break unwanted connections and/or create appropriate rules
to inhibit this activity in future. To do this, use appropriate commands in the
dialog box context menu:
• Refresh – refreshes the established connections list on user demand.
• Create rule – allows you to create a rule for a selected connection. The
program launches the application rule wizard, and automatically enters
the selected connection details in the appropriate fields.
• Break connection – breaks the connection selected from the list.
Page 79

Viewing Performance Results 79
Attention! If you force a connection to break, the related application may
function incorrectly.
• Properties – displays more details of the connection selected from the list
(see fig. 48).
Fig. 48. The Properties of the connection dialog box
The Connection section of the Properties of the connection dialog box
includes the following items:
• Direction – the connection type: outgoing or incoming
• Remote address – the remote machine symbolic name or IP address
• Remote port – the remote port number
Page 80

80 Kaspersky Anti-Hacker
• Local port – the local port number
Below the Connection section you can see the Application information and
the Manufacturer information sections (see subchapter 7.1.1 on page 73).
7.1.3. Open Ports
To review the list of ports that are currently open,
select Open ports from the Show submenu of the View menu (see fig. 49).
You can also press the button in the toolbar.
The Open ports dialog box will appear on your screen.
Each line of this list includes details of a single open port. Open ports are
indicated by the TCP or the UDP icon, depending on the port type.
The list also includes the following port details:
• Local port – the port number
• Application – the involved application
• Application location – the full path to the executable file
You may sort the list by any of the titles described above.
Page 81

Viewing Performance Results 81
Fig. 49. The Open ports dialog box
The list of open ports is refreshed automatically twice a second.
If required, you can create a rule inhibiting connection at the selected port. To do
this, use appropriate commands in the dialog box context menu:
• Refresh – refreshes the open ports list on user demand.
• Create rule – allows you to create a rule for the selected port. The pro-
gram launches the application rule wizard, and automatically enters the
selected port details in the appropriate fields.
• Properties – displays more details of the port selected from the list (see
fig. 50).
Page 82

82 Kaspersky Anti-Hacker
Fig. 50. The Properties of the port dialog box
The Port section of the Properties of the port dialog box includes the following
items:
• Protocol – the name of the protocol used
• Local port – the local port number
Below the Port section you can see the Application information and the
Manufacturer information sections (see subchapter 7.1.1 on page 73).
Page 83

Viewing Performance Results 83
7.2. Using the Logs
Displaying the log window. The log
window layout. Selecting the log
type. Saving the log to a file
Network events that occur on your machine are monitored and saved to the logs.
Different event types are saved to different logs:
• The Security log contains details of the latest attacks on your machine
(see subchapter 6.5 on page 69).
• The Application activity log contains details of the events to be logged,
as defined by the application rule wizard (see subchapter 0 on page 59).
• The Packet filtering log contains details of the events to be logged, as
defined by the packet filtering rule wizard (see subchapter 6.4.2.2 on
page 67).
All logs can be reviewed and configured in a single window (the Logs window).
You can use this window to limit log sizes, to set the logs to be cleared every
time the program starts, or to store results of more then one session (see
subchapter 7.2.4 on page 88).
If required, you can clear the logs on demand.
You can also save these logs to files on your hard drive.
7.2.1. Displaying the Logs Window
To display the Logs window,
select the required log type from the Logs submenu of the View menu.
The Logs window will appear on your screen (see fig. 51).
Page 84

84 Kaspersky Anti-Hacker
7.2.2. The Logs Window Layout
The Logs window includes the following three items:
• Menus
• Report table
• Tabs allowing you to switch between various types of log.
7.2.2.1. Menus
At the top of the Logs window you will find the menu bar.
Table 4
Menu !commands Function
(The command allows you to :)
File Save to file Save the current log to a file
Help Contents ... Display Help topics
Help Kaspersky Anti-Hacker
on the Web
Help About Kaspersky AntiHacker
Open the Kaspersky Labs official web site
page
Display a box with the program details and
information about the keys used
7.2.2.2. Report Table
The report table displays information saved to the selected log type. You can
review this log by using the scroll bar to the right.
The report table has a context menu that includes by default the following two
commands and can be extended depending on the selected log type:
• Clear the log – clears the selected log.
Page 85

Viewing Performance Results 85
• Auto-scroll the log – always displays the last event record at the bottom
of the report table.
• Don't log this event – disables further logging of the selected event. This
command is available in all logs except the hacker attacks log.
• Create rule – allows you to create a rule for a selected event. The newly
created rule is placed at the beginning of the rule list, with the highest priority.
7.2.2.3. Tabs
The following tabs at the bottom of the Logs window allow you to switch between
log types:
• Security
• Application activity
• Packet filtering
7.2.3. Selecting the Log
7.2.3.1. Security Log
The Security log allows you to review the list of all detected attacks on your
machine (see subchapter 6.5 on page 69).
To display the Security log,
select Security from the Logs submenu of the View menu.
The Logs window switched to Security tab mode will appear on your screen
(see fig. 51). The log includes the following data:
• Date and time – the date and the time when your computer was at-
tacked.
• Event description – the attack description including attack type and ad-
dress of the assaulter, if detected.
Page 86

86 Kaspersky Anti-Hacker
The list of events can be sorted only by date and time.
Fig. 51. The Security log page
7.2.3.2. Application Activity
The Application Activity log allows you to review details of applications with the logging option enabled by the application rule wizard (see subchapter 0 on page 59).
To display the Application activity log,
select Application activity from the Logs submenu of the View menu.
The Logs window switched to Application activity tab mode will appear on your
screen (see fig. 52). The log includes the following data:
• Date and time – the date and the time the event occurred.
• Application – the related application name and the full path to its execu-
table file.
• Activity description – the activity details.
• Local address – the local address.
• Remote address – the remote address.
The list of events can be sorted only by date and time.
Page 87

Viewing Performance Results 87
Fig. 52. The Application Activity log page
7.2.3.3. Packet Filtering
The Packet filtering log allows you to review details of packet filtering events for which the logging option was enabled by the packet filtering rule wizard (see subchapter 6.4.2.2 on page 67).
To display the Packet filtering log,
select Packet filtering from the Logs submenu of the View menu.
The Logs window switched to Packet filtering tab mode will appear on your
screen (see fig. 53). The log includes the following data:
• Date and time – the date and the time the event occurred.
• Direction – the packet type: incoming or outgoing.
• Protocol – the protocol name.
• Local address – the local address.
• Remote address – the remote address.
• Rule used – the name of the rule employed.
Entries for allowed packets are colored black, while entries for blocked packets
are red.
Page 88

88 Kaspersky Anti-Hacker
The list of events can be sorted only by date and time.
Fig. 53. The Packet filtering log page
7.2.4. Defining Log Settings
To define the log settings,
select Settings from the Service menu and switch to the Logs tab (see
fig. 54).
You can define values for the following two options:
Clear logs when the program starts – if checked, this clears all program
logs when the program starts.
Limit the log size to (Kb) – if checked, this allows log file size to be limited.
Specify the maximum size for your log file in the text field. When the log size
reaches its maximum, the program will start removing the oldest entries as
new entries are added.
Note that the above checkbox allows you to define the size of a
SINGLE log file only. When calculating the hard disk space required for
normal performance of the program, remember that this figure must be
multiplied by three.
Page 89

Viewing Performance Results 89
Fig. 54. The Settings dialog box switched to the Logs tab mode
7.2.5. Saving the Log to a File
To save the log selected in the Logs window to a file,
select Save to file from the File menu. Specify the file name in the
dialog box on your screen. The log will be saved as plain text.
Page 90

APPENDIX A. INDEX
Application rules ...........................................................................................22, 46
Event warning..................................................................................................... 41
Installation CD ......................................................................................................7
Intrusion Detection System................................................................. 6, 24, 26, 69
License agreement ............................................................................................... 7
Packet filtering rules .....................................................................................23, 60
Security levels ........................................................................6, 19, 23, 24, 38, 40
Security scale ...............................................................................................33, 40
Technical support service .............................................................................10, 95
Training window...................................................................................... 23, 39, 42
Page 91

APPENDIX B. FREQUENTLY
ASKED QUESTIONS
When performing a task your computer displays an error, and you
would like to check whether the error is caused by Kaspersky AntiHacker.
Temporarily select the Allow all security level or unload Kaspersky
Anti-Hacker from computer memory. Check whether the situation
changes. If the same error occurs again, it is not related to Kaspersky
Anti-Hacker. If you computer does not display any error, contact Kaspersky Labs Technical Support Department.
Page 92

APPENDIX C. KASPERSKY LABS
LTD.
About Kaspersky Labs
Kaspersky Labs is a privately-owned, international, anti-virus softwaredevelopment group of companies headquartered in Moscow (Russia), and
representative offices in the United Kingdom, United States of America, China,
France and Poland. Founded in 1997, Kaspersky Labs concentrates its efforts on
the development, marketing and distribution of leading-edge information security
technologies and computer software.
Kaspersky Labs is one the world leaders in data-security and anti-virus
technologies. The Company was the first to develop many features that are now
an essential part of all modern anti-virus protection: an external anti-virus
database with embedded specialized modules, a search capability within
archived and compressed files, integrated anti-virus protection for Linux, etc. In
addition to anti-virus software, Kaspersky Labs is committed to the development
of general data-security software. Our current product line includes Kaspersky™
Inspector and Kaspersky™ WEB Inspector, whose unique capabilities allow
users full control over any unauthorized alteration to the file system and content
of a Web server.
Upcoming add-on features include Kaspersky™ Anti-Hacker for general
workplace defense against any hacker attacks, and Kaspersky™ Anti-Spam for
enterprise-wide prevention of incoming "spam" messages and internal e-mail
misusing. Kaspersky Labs' flagship product, Kaspersky™ Anti-Virus (formerly
known as AVP), has been in constant development since 1989, and has been
rated consistently by numerous computer magazines and virus research centers
as the best anti-virus product on the market.
Kaspersky™ Anti-Virus covers all reliable methods of anti-virus protection: antivirus scanners, resident "on-the-fly" virus interceptors, integrity checkers and
behavior blockers. Kaspersky™ Anti-Virus supports all of the most popular
operating systems and applications. It provides strong anti-virus defense for email gateways (MS Exchange Server, Lotus Notes/ Domino, Sendmail, Qmail,
Postfix, and Exim), firewalls and WEB servers. All Kaspersky Labs products rely
on Kaspersky's own database of over 60,000 known viruses and all other types
of malicious code. The product is also powered by a unique heuristic technology
combating even future threats: the built-in heuristic code analyzer, which is able
to detect up to 92% of unknown viruses and the world's only behavior blocker for
MS Office 2000 providing 100% guaranteed protection against any macroviruses.
Page 93

Appendix C. 93
C.1. Other Kaspersky Lab's Products
Kaspersky® Anti-Virus Lite
The program is the most easy-to-use Kaspersky Lab’s anti-virus product that is
developed for protection of home computers running Windows 95/98/Me,
Windows 2000/NT Workstation, Windows XP.
Kaspersky® Anti-Virus Lite includes:
• an anti-virus scanner that provides a comprehensive check of all
local and network drives on demand;
• an anti-virus monitor that automatically checks all used files in real-
time;
• an MS Outlook Express mail databases checking module for
checking for viruses on demand.
Kaspersky® Anti-Virus Personal/Personal Pro
The package has been developed to provide the full-scale anti-virus protection
for home computers running the Windows 95/98/ME, or the Windows 2000/NT,
or the Windows XP operation system, MS Office 2000 business applications and
the Outlook and Outlook Express mail programs. Kaspersky® Anti-Virus
Personal/Personal Pro includes a program to retrieve daily updates via the
Internet, an integrated module of management and automation of your anti-virus
protection. The unique second-generation heuristic-analysis system effectively
neutralizes unknown viruses. The simple and easy-to-use interface allows you to
quickly change the program settings and makes you feel maximum comfort while
working with the program.
Kaspersky® Anti-Virus Personal includes:
• an anti-virus scanner that provides a comprehensive check of all
local and network drives on demand;
• an anti-virus monitor that automatically checks all used files in real-
time;
• a mail filter that automatically checks all incoming and outgoing
messages in the background;
Page 94

94 Kaspersky Anti-Hacker
• a control center that automatically starts Kaspersky® Anti-Virus by
schedule, enables you to centrally manage the program and to automatically broadcast notifications on virus attacks.
Kaspersky® Anti-Virus Personal Pro includes all the above components plus:
• an integrity checker that traces content changes on your hard drive
and allows the complete recovery of modified files and boot sectors
on demand;
• a behavior blocker that guarantees 100% protection from destruc-
tive macro-viruses.
Kaspersky® Security for PDA
Kaspersky® Security for PDA provides reliable virus protection for the data
stored on PDA running Palm OS or Windows CE, as well as for any information
transferred from a PC or extension card, ROM files and databases. Software
contains an optimal combination of anti-virus tools:
• an anti-virus scanner that provides a comprehensive check of all
stored data (on both the PDA itself as well as on any extension
cards) on user demand;
• an anti-virus monitor that intercepts viruses in data transferred us-
ing the HotSync™ utility or portable devices.
Kaspersky® Security for PDA also provides
computers (PDAs) against unauthorized access.
protection of data stored in pocket
It supports the encrypted
access to the device and encrypts all the data stored on the device and on
memory cards.
Kaspersky® Anti-Virus Business Optimal
The package has been developed to provide full-scale data-protection for small
and medium-size corporate networks.
Kaspersky® Anti-Virus Business Optimal includes full-scale anti-virus protection
for:
• workstations running Windows 95/98/ME, Windows NT/2000 Workstation,
Windows XP, Linux;
• file and application servers running Windows NT/2000 Server, Linux, Solaris, Novell NetWare, FreeBSD, BSDi, OpenBSD;
Page 95

Appendix C. 95
• mail gateways MS Exchange Server 5.5/2000, Lotus Notes/Domino,
Sendmail, Postfix, Qmail, Exim.
You are free to choose any of the anti-virus programs according to the operation
systems and applications you use.
Kaspersky® Corporate Suite
The package has been developed to provide the full-scale data-protection for
corporate networks of any size and complexity. The package components allow
protection of all nodes on a corporate network. The product can be ideally
integrated into your corporate network regardless of the software and hardware
from other manufacturers that you use on it. The flexibility of this anti-virus
solution allows you to create an effective data-protection system that is fully
appropriate and compatible for your network configurations.
Kaspersky® Corporate Suite includes full-scale anti-virus protection of:
• workstations running Windows 95/98/ME, Windows NT/2000 Workstation,
Windows XP, Linux, OS/2;
• file and application servers running Windows NT/2000 Server, Linux, Solaris, Novell NetWare, FreeBSD, BSDi; OpenBSD;
• mail gateways MS Exchange Server 5.5/2000, Lotus Notes/Domino,
Sendmail, Postfix; Exim, Qmail;
• CVP compatible firewalls;
• Web servers;
• personal computers (PDA) running Palm OS.
You are free to choose any of the anti-virus programs according to the operation
systems and applications you use.
Kaspersky® Anti-Spam
Kaspersky® Anti-Spam is a cutting edge software suite designed to protect small
and medium size networks from undesired e-mail (spam). The product combines
the revolutionary technology of linguistic analyses of message text, all modern
methods of e-mail filtration (including RBL lists) and a unique collection of
services that allows users to identify and wipe out up to 95% of unwanted traffic.
Kaspersky® Anti-Spam acts as a filter installed at a network’s entrance where it
verifies incoming e-mail traffic streams for objects identified as spam. Software is
Page 96

96 Kaspersky Anti-Hacker
compatible with any mail system, already used on the customer network, and
can be installed both on existing mail server or dedicated one.
The high effectiveness of Kaspersky® Anti-Spam is enabled by the daily update
of content filtration database with the samples provided by the specialists of
linguistic laboratory.
C.2. Contact Information
If you have any questions, comments or suggestions please refer them to our
distributors or directly to Kaspersky Labs. We will be glad to advise you on any
matters related to our product by phone or e-mail and all your recommendations
and suggestions will be thoroughly reviewed and considered.
Technical
support
General
information
Please find the technical support information at
http://www.kaspersky.com/supportinter.html
WWW: http://www.kaspersky.com
http://www.viruslist.com
E-mail: sales@kaspersky.com
 Loading...
Loading...