Page 1

Kaspersky Endpoint Security 8 for Mac
Administrator’s guide
APPLICATION VERSION: 8.0
Page 2
2
Dear User!
Thank you for choosing our product. We hope that this documentation will help you in your work and will provide answers
regarding this software product.
Warning! This document is the property of Kaspersky Lab and all rights to this document are reserved by the copyright
laws of the Russian Federation and international treaties. Illegal reproduction and distribution of this document or parts
hereof will result in civil, administrative or criminal liability pursuant to the laws of the Russian Federation.
Any type of reproduction and distribution of any materials, including translation thereof, is allowed only with the written
permission of Kaspersky Lab.
This document and graphic images related to it can be used exclusively for information, non-commercial or personal
purposes.
Kaspersky Lab reserves the right to change the document at any time without notice. You can find the latest version of
this document at the Kaspersky Lab website, at http://www.kaspersky.com/docs.
Kaspersky Lab assumes no liability for the content, quality, relevance, or accuracy of any materials used in this
document for which the rights are held by third parties, or for any potential damages associated with the use of such
documents.
This document contains registered trademarks and service marks, which are the property of their respective owners.
Document revision date: 10/21/2010
© 1997-2010 Kaspersky Lab ZAO. All Rights Reserved.
http://www.kaspersky.com
http://support.kaspersky.com
Page 3

3
KASPERSKY LAB END USER LICENSE AGREEMENT
IMPORTANT LEGAL NOTICE TO ALL USERS: CAREFULLY READ THE FOLLOWING LEGAL AGREEMENT BEFORE
YOU START USING THE SOFTWARE.
BY CLICKING THE ACCEPT BUTTON IN THE LICENSE AGREEMENT WINDOW OR BY ENTERING
CORRESPONDING SYMBOL(-S) YOU CONSENT TO BE BOUND BY THE TERMS AND CONDITIONS OF THIS
AGREEMENT. SUCH ACTION IS A SYMBOL OF YOUR SIGNATURE AND YOU ARE CONSENTING TO BE BOUND
BY AND ARE BECOMING A PARTY TO THIS AGREEMENT AND AGREE THAT THIS AGREEMENT IS
ENFORCEABLE LIKE ANY WRITTEN NEGOTIATED AGREEMENT SIGNED BY YOU. IF YOU DO NOT AGREE TO
ALL OF THE TERMS AND CONDITIONS OF THIS AGREEMENT, CANCEL THE INSTALLATION OF THE SOFTWARE
AND DO NOT INSTALL THE SOFTWARE.
IF LICENSE CONTRACT OR SIMILAR DOCUMENT ACCOMPANIES SOFTWARE, TERMS OF THE SOFTWARE USE
DEFINED IN SUCH DOCUMENT PREVAIL OVER CURRENT END USER LICENSE AGREEMENT.
AFTER CLICKING THE ACCEPT BUTTON IN THE LICENSE AGREEMENT WINDOW OR AFTER ENTERING
CORRESPONDING SYMBOL(-S) YOU HAVE THE RIGHT TO USE THE SOFTWARE IN ACCORDANCE WITH THE
TERMS AND CONDITIONS OF THIS AGREEMENT.
1. Definitions
1.1. Software means software including any Updates and related materials.
1.2. Rightholder (owner of all rights, whether exclusive or otherwise to the Software) means Kaspersky Lab ZAO, a
company incorporated according to the laws of the Russian Federation.
1.3. Computer(s) means hardware(s), including personal computers, laptops, workstations, personal digital assistants,
‘smart phones’, hand-held devices, or other electronic devices for which the Software was designed where the Software
will be installed and/or used.
1.4. End User (You/Your) means individual(s) installing or using the Software on his or her own behalf or who is legally
using a copy of the Software; or, if the Software is being downloaded or installed on behalf of an organization, such as an
employer, "You" further means the organization for which the Software is downloaded or installed and it is represented
hereby that such organization has authorized the person accepting this agreement to do so on its behalf. For purposes
hereof the term "organization," without limitation, includes any partnership, limited liability company, corporation,
association, joint stock company, trust, joint venture, labor organization, unincorporated organization, or governmental
authority.
1.5. Partner(s) means organizations or individual(s), who distributes the Software based on an agreement and license
with the Rightholder.
1.6. Update(s) means all upgrades, revisions, patches, enhancements, fixes, modifications, copies, additions or
maintenance packs etc.
1.7. User Manual means user manual, administrator guide, reference book and related explanatory or other materials.
2. Grant of License
2.1. You are given a non-exclusive license to store, load, install, execute, and display (to "use") the Software on a
specified number of Computers in order to assist in protecting Your Computer on which the Software is installed, from
threats described in the User Manual, according to the all technical requirements described in the User Manual and
according to the terms and conditions of this Agreement (the "License") and you accept this License:
Trial Version. If you have received, downloaded and/or installed a trial version of the Software and are hereby granted
an evaluation license for the Software, you may use the Software only for evaluation purposes and only during the single
applicable evaluation period, unless otherwise indicated, from the date of the initial installation. Any use of the Software
for other purposes or beyond the applicable evaluation period is strictly prohibited.
Multiple Environment Software; Multiple Language Software; Dual Media Software; Multiple Copies; Bundles. If you use
different versions of the Software or different language editions of the Software, if you receive the Software on multiple
media, if you otherwise receive multiple copies of the Software, or if you received the Software bundled with other
software, the total permitted number of your Computers on which all versions of the Software are installed shall
correspond to the number of computers specified in licenses you have obtained provided that unless the licensing terms
provide otherwise, each acquired license entitles you to install and use the Software on such a number of Computer(s)
as is specified in Clauses 2.2 and 2.3.
Page 4
A D M I N I S T R A T O R ' S G U I D E
4
2.2. If the Software was acquired on a physical medium You have the right to use the Software for protection of such a
number of Computer(s) as is specified on the Software package.
2.3. If the Software was acquired via the Internet You have the right to use the Software for protection of such a number
of Computers that was specified when You acquired the License to the Software.
2.4. You have the right to make a copy of the Software solely for back-up purposes and only to replace the legally owned
copy if such copy is lost, destroyed or becomes unusable. This back-up copy cannot be used for other purposes and
must be destroyed when you lose the right to use the Software or when Your license expires or is terminated for any
other reason according to the legislation in force in the country of your principal residence or in the country where You
are using the Software.
2.5. From the time of the Software activation or after license key file installation (with the exception of a trial version of
the Software) You have the right to receive the following services for the defined period specified on the Software
package (if the Software was acquired on a physical medium) or specified during acquisition (if the Software was
acquired via the Internet):
- Updates of the Software via the Internet when and as the Rightholder publishes them on its website or through other
online services. Аny Updates that you may receive become part of the Software and the terms and conditions of this
Agreement apply to them;
- Technical Support via the Internet and Technical Support telephone hotline.
3. Activation and Term
3.1. If You modify Your Computer or make changes to other vendors’ software installed on it, You may be required by the
Rightholder to repeat activation of the Software or license key file installation. The Rightholder reserves the right to use
any means and verification procedures to verify the validity of the License and/or legality of a copy of the Software
installed and/or used on Your Computer.
3.2. If the Software was acquired on a physical medium, the Software can be used, upon your acceptance of this
Agreement, for the period that is specified on the package commencing upon acceptance of this Agreement.
3.3. If the Software was acquired via the Internet, the Software can be used, upon your acceptance of this Agreement,
for the period that was specified during acquisition.
3.4. You have the right to use a trial version of the Software as provided in Clause 2.1 without any charge for the single
applicable evaluation period (30 days) from the time of the Software activation according to this Agreement provided that
the trial version does not entitle You Updates and Technical support via the Internet and Technical support telephone
hotline.
3.5. Your License to Use the Software is limited to the period of time as specified in Clauses 3.2 or 3.3 (as applicable)
and the remaining period can be viewed via means described in User Manual.
3.6. If You have acquired the Software that is intended to be used on more than one Computer then Your License to Use
the Software is limited to the period of time starting from the date of activation of the Software or license key file
installation on the first Computer.
3.7. Without prejudice to any other remedy in law or in equity that the Rightholder may have, in the event of any breach
by You of any of the terms and conditions of this Agreement, the Rightholder shall at any time without notice to You be
entitled to terminate this License without refunding the purchase price or any part thereof.
3.8. You agree that in using the Software and in using any report or information derived as a result of using this Software,
you will comply with all applicable international, national, state, regional and local laws and regulations, including, without
limitation, privacy, copyright, export control and obscenity law.
3.9. Except as otherwise specifically provided herein, you may not transfer or assign any of the rights granted to you
under this Agreement or any of your obligations pursuant hereto.
4. Technical Support
4.1. The Technical Support described in Clause 2.5 of this Agreement is provided to You when the latest Update of the
Software is installed (except for a trial version of the Software).
Technical support service: http://support.kaspersky.com
4.2. User’s Data, specified in Personal Cabinet/My Kaspersky Account, can be used by Technical Support specialists
only during processing User’s request.
5. Limitations
5.1. You shall not emulate, clone, rent, lend, lease, sell, modify, decompile, or reverse engineer the Software or
disassemble or create derivative works based on the Software or any portion thereof with the sole exception of a nonwaivable right granted to You by applicable legislation, and you shall not otherwise reduce any part of the Software to
human readable form or transfer the licensed Software, or any subset of the licensed Software, nor permit any third party
to do so, except to the extent the foregoing restriction is expressly prohibited by applicable law. Neither Software’s
binary code nor source may be used or reverse engineered to re-create the program algorithm, which is proprietary. All
rights not expressly granted herein are reserved by Rightholder and/or its suppliers, as applicable. Any such
unauthorized use of the Software shall result in immediate and automatic termination of this Agreement and the License
granted hereunder and may result in criminal and/or civil prosecution against You.
5.2. You shall not transfer the rights to use the Software to any third party.
Page 5

K A S P E R S K Y L AB E N D U S E R L I C E N S E AG R E E M E N T
5
5.3. You shall not provide the activation code and/or license key file to third parties or allow third parties access to the
activation code and/or license key which are deemed confidential data of Rightholder.
5.4. You shall not rent, lease or lend the Software to any third party.
5.5. You shall not use the Software in the creation of data or software used for detection, blocking or treating threats
described in the User Manual.
5.6. Your key file can be blocked in case You breach any of the terms and conditions of this Agreement.
5.7. If You are using the trial version of the Software You do not have the right to receive the Technical Support specified
in Clause 4 of this Agreement and You don’t have the right to transfer the license or the rights to use the Software to any
third party.
6. Limited Warranty and Disclaimer
6.1. The Rightholder guarantees that the Software will substantially perform according to the specifications and
descriptions set forth in the User Manual provided however that such limited warranty shall not apply to the following: (w)
Your Computer’s deficiencies and related infringement for which Rightholder’s expressly disclaims any warranty
responsibility; (x) malfunctions, defects, or failures resulting from misuse; abuse; accident; neglect; improper installation,
operation or maintenance; theft; vandalism; acts of God; acts of terrorism; power failures or surges; casualty; alteration,
non-permitted modification, or repairs by any party other than Rightholder; or any other third parties’ or Your actions or
causes beyond Rightholder’s reasonable control; (y) any defect not made known by You to Rightholder as soon as
practical after the defect first appears; and (z) incompatibility caused by hardware and/or software components installed
on Your Computer.
6.2. You acknowledge, accept and agree that no software is error free and You are advised to back-up the Computer,
with frequency and reliability suitable for You.
6.3. The Rightholder does not provide any guarantee that the Software will work correctly in case of violations of the
terms described in the User Manual or in this Agreement.
6.4. The Rightholder does not guarantee that the Software will work correctly if You do not regularly download Updates
specified in Clause 2.5 of this Agreement.
6.5. The Rightholder does not guarantee protection from the threats described in the User Manual after the expiration of
the period specified in Clauses 3.2 or 3.3 of this Agreement or after the License to use the Software is terminated for any
reason.
6.6. THE SOFTWARE IS PROVIDED "AS IS" AND THE RIGHTHOLDER MAKES NO REPRESENTATION AND GIVES
NO WARRANTY AS TO ITS USE OR PERFORMANCE. EXCEPT FOR ANY WARRANTY, CONDITION,
REPRESENTATION OR TERM THE EXTENT TO WHICH CANNOT BE EXCLUDED OR LIMITED BY APPLICABLE
LAW THE RIGHTHOLDER AND ITS PARTNERS MAKE NO WARRANTY, CONDITION, REPRESENTATION, OR
TERM (EXPRESSED OR IMPLIED, WHETHER BY STATUTE, COMMON LAW, CUSTOM, USAGE OR OTHERWISE)
AS TO ANY MATTER INCLUDING, WITHOUT LIMITATION, NONINFRINGEMENT OF THIRD PARTY RIGHTS,
MERCHANTABILITY, SATISFACTORY QUALITY, INTEGRATION, OR APPLICABILITY FOR A PARTICULAR
PURPOSE. YOU ASSUME ALL FAULTS, AND THE ENTIRE RISK AS TO PERFORMANCE AND RESPONSIBILITY
FOR SELECTING THE SOFTWARE TO ACHIEVE YOUR INTENDED RESULTS, AND FOR THE INSTALLATION OF,
USE OF, AND RESULTS OBTAINED FROM THE SOFTWARE. WITHOUT LIMITING THE FOREGOING PROVISIONS,
THE RIGHTHOLDER MAKES NO REPRESENTATION AND GIVES NO WARRANTY THAT THE SOFTWARE WILL BE
ERROR-FREE OR FREE FROM INTERRUPTIONS OR OTHER FAILURES OR THAT THE SOFTWARE WILL MEET
ANY OR ALL YOUR REQUIREMENTS WHETHER OR NOT DISCLOSED TO THE RIGHTHOLDER .
7. Exclusion and Limitation of Liability
7.1. TO THE MAXIMUM EXTENT PERMITTED BY APPLICABLE LAW, IN NO EVENT SHALL THE RIGHTHOLDER OR
ITS PARTNERS BE LIABLE FOR ANY SPECIAL, INCIDENTAL, PUNITIVE, INDIRECT, OR CONSEQUENTIAL
DAMAGES WHATSOEVER (INCLUDING, BUT NOT LIMITED TO, DAMAGES FOR LOSS OF PROFITS OR
CONFIDENTIAL OR OTHER INFORMATION, FOR BUSINESS INTERRUPTION, FOR LOSS OF PRIVACY, FOR
CORRUPTION, DAMAGE AND LOSS OF DATA OR PROGRAMS, FOR FAILURE TO MEET ANY DUTY INCLUDING
ANY STATUTORY DUTY, DUTY OF GOOD FAITH OR DUTY OF REASONABLE CARE, FOR NEGLIGENCE, FOR
ECONOMIC LOSS, AND FOR ANY OTHER PECUNIARY OR OTHER LOSS WHATSOEVER) ARISING OUT OF OR IN
ANY WAY RELATED TO THE USE OF OR INABILITY TO USE THE SOFTWARE, THE PROVISION OF OR FAILURE
TO PROVIDE SUPPORT OR OTHER SERVICES, INFORMATON, SOFTWARE, AND RELATED CONTENT
THROUGH THE SOFTWARE OR OTHERWISE ARISING OUT OF THE USE OF THE SOFTWARE, OR OTHERWISE
UNDER OR IN CONNECTION WITH ANY PROVISION OF THIS AGREEMENT, OR ARISING OUT OF ANY BREACH
OF CONTRACT OR ANY TORT (INCLUDING NEGLIGENCE, MISREPRESENTATION, ANY STRICT LIABILITY
OBLIGATION OR DUTY), OR ANY BREACH OF STATUTORY DUTY, OR ANY BREACH OF WARRANTY OF THE
RIGHTHOLDER AND/OR ANY OF ITS PARTNERS, EVEN IF THE RIGHTHOLDER AND/OR ANY PARTNER HAS
BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
YOU AGREE THAT IN THE EVENT THE RIGHTHOLDER AND/OR ITS PARTNERS ARE FOUND LIABILE, THE
LIABILITY OF THE RIGHTHOLDER AND/OR ITS PARTNERS SHALL BE LIMITED BY THE COSTS OF THE
SOFTWARE. IN NO CASE SHALL THE LIABILITY OF THE RIGHTHOLDER AND/OR ITS PARTNERS EXCEED THE
FEES PAID FOR THE SOFTWARE TO THE RIGHTHOLDER OR THE PARTNER (AS MAY BE APPLICABLE).
Page 6
A D M I N I S T R A T O R ' S G U I D E
6
NOTHING IN THIS AGREEMENT EXCLUDES OR LIMITS ANY CLAIM FOR DEATH AND PERSONAL INJURY.
FURTHER IN THE EVENT ANY DISCLAIMER, EXCLUSION OR LIMITATION IN THIS AGREEMENT CANNOT BE
EXLUDED OR LIMITED ACCORDING TO APPLICABLE LAW THEN ONLY SUCH DISCLAIMER, EXCLUSION OR
LIMITATION SHALL NOT APPLY TO YOU AND YOU CONTINUE TO BE BOUND BY ALL THE REMAINING
DISCLAIMERS, EXCLUSIONS AND LIMITATIONS.
8. GNU and Other Third Party Licenses
8.1. The Software may include some software programs that are licensed (or sublicensed) to the user under the GNU
General Public License (GPL) or other similar free software licenses which, among other rights, permit the user to copy,
modify and redistribute certain programs, or portions thereof, and have access to the source code ( "Open Source
Software"). If such licenses require that for any software, which is distributed to someone in an executable binary format,
that the source code also be made available to those users, then the source code should be made available by sending
the request to source@kaspersky.com or the source code is supplied with the Software. If any Open Source Software
licenses require that the Rightholder provide rights to use, copy or modify an Open Source Software program that are
broader than the rights granted in this Agreement, then such rights shall take precedence over the rights and restrictions
herein.
9. Intellectual Property Ownership
9.1. You agree that the Software and the authorship, systems, ideas, methods of operation, documentation and other
information contained in the Software, are proprietary intellectual property and/or the valuable trade secrets of the
Rightholder or its partners and that the Rightholder and its partners, as applicable, are protected by civil and criminal law,
and by the law of copyright, trade secret, trademark and patent of the Russian Federation, European Union and the
United States, as well as other countries and international treaties. This Agreement does not grant to You any rights to
the intellectual property including any the Trademarks or Service Marks of the Rightholder and/or its partners
("Trademarks"). You may use the Trademarks only insofar as to identify printed output produced by the Software in
accordance with accepted trademark practice, including identification of the Trademark owner’s name. Such use of any
Trademark does not give you any rights of ownership in that Trademark. The Rightholder and/or its partners own and
retain all right, title, and interest in and to the Software, including without limitation any error corrections, enhancem ents,
Updates or other modifications to the Software, whether made by the Rightholder or any third party, and all copyrights,
patents, trade secret rights, trademarks, and other intellectual property rights therein. Your possession, installation or
use of the Software does not transfer to you any title to the intellectual property in the Software, and you will not acquire
any rights to the Software except as expressly set forth in this Agreement. All copies of the Software made hereunder
must contain the same proprietary notices that appear on and in the Software. Except as stated herein, this Agreement
does not grant you any intellectual property rights in the Software and you acknowledge that the License, as further
defined herein, granted under this Agreement only provides you with a right of limited use under the terms and conditions
of this Agreement. Rightholder reserves all rights not expressly granted to you in this Agreement.
9.2. You agree not to modify or alter the Software in any way. You may not remove or alter any copyright notices or
other proprietary notices on any copies of the Software.
10. Governing Law; Arbitration
10.1. This Agreement will be governed by and construed in accordance with the laws of the Russian Federation without
reference to conflicts of law rules and principles. This Agreement shall not be governed by the United Nations
Convention on Contracts for the International Sale of Goods, the application of which is expressly excluded. Any dispute
arising out of the interpretation or application of the terms of this Agreement or any breach thereof shall, unless it is
settled by direct negotiation, be settled by in the International Commercial Arbitration Court at the Russian Federation
Chamber of Commerce and Industry in Moscow, the Russian Federation. Any award rendered by the arbitrator shall be
final and binding on the parties and any judgment on such arbitration award may be enforced in any court of competent
jurisdiction. Nothing in this Section 10 shall prevent a Party from seeking or obtaining equitable relief from a court of
competent jurisdiction, whether before, during or after arbitration proceedings.
11. Period for Bringing Actions
11.1. No action, regardless of form, arising out of the transactions under this Agreement, may be brought by either party
hereto more than one (1) year after the cause of action has occurred, or was discovered to have occurred, except that an
action for infringement of intellectual property rights may be brought within the maximum applicable statutory period.
12. Entire Agreement; Severability; No Waiver
12.1. This Agreement is the entire agreement between you and Rightholder and supersedes any other prior agreements,
proposals, communications or advertising, oral or written, with respect to the Software or to subject matter of this
Agreement. You acknowledge that you have read this Agreement, understand it and agree to be bound by its terms. If
any provision of this Agreement is found by a court of competent jurisdiction to be invalid, void, or unenforceable for any
reason, in whole or in part, such provision will be more narrowly construed so that it becomes legal and enforceable, and
Page 7

K A S P E R S K Y L AB E N D US E R L I C E N S E A G R E E M E N T
7
the entire Agreement will not fail on account thereof and the balance of the Agreement will continu e in full force and
effect to the maximum extent permitted by law or equity while preserving, to the fullest extent possible, its original intent .
No waiver of any provision or condition herein shall be valid unless in writing and signed by you and an authorized
representative of Rightholder provided that no waiver of any breach of any provisions of this Agreement will constitute a
waiver of any prior, concurrent or subsequent breach. Rightholder’s failure to insist upon or enforce strict performance of
any provision of this Agreement or any right shall not be construed as a waiver of any such provision or right.
13. Rightholder Contact Information
Should you have any questions concerning this Agreement, or if you desire to contact the Rightholder for any reason,
please contact our Customer Service Department at:
Kaspersky Lab ZAO, 10 build. 1, 1st Volokolamsky Proezd
Moscow, 123060
Russian Federation
Tel: +7-495-797-8700
Fax: +7-495-645-7939
E-mail: info@kaspersky.com
Web site: www.kaspersky.com
© 1997-2010 Kaspersky Lab ZAO. All Rights Reserved. The Software and any accompanying documentation are
copyrighted and protected by copyright laws and international copyright treaties, as well as other intellectual property
laws and treaties.
Page 8

8
CONTENT
KASPERSKY LAB END USER LICENSE AGREEMENT .............................................................................................. 3
ABOUT THIS GUIDE ................................................................................................................................................... 13
In this document ..................................................................................................................................................... 13
Document conventions ........................................................................................................................................... 15
ADDITIONAL SOURCES OF INFORMATION ............................................................................................................. 16
KASPERSKY ENDPOINT SECURITY 8 ...................................................................................................................... 18
Distribution kit ......................................................................................................................................................... 19
Hardware and software system requirements ........................................................................................................ 19
INSTALLING THE APPLICATION ............................................................................................................................... 20
Preparing for installation ......................................................................................................................................... 20
Installing the application ......................................................................................................................................... 20
Kaspersky Endpoint Security default installation ............................................................................................... 21
Kaspersky Endpoint Security custom installation .............................................................................................. 22
Preparing for use after installation .......................................................................................................................... 23
Deleting the application .......................................................................................................................................... 24
LICENSE MANAGEMENT ........................................................................................................................................... 25
About license .......................................................................................................................................................... 25
Viewing license information .................................................................................................................................... 26
Purchasing a license .............................................................................................................................................. 26
Renewing a license ................................................................................................................................................ 27
About End User License Agreement ...................................................................................................................... 28
About the activation code ....................................................................................................................................... 28
About the key file .................................................................................................................................................... 28
Kaspersky Endpoint Security activation .................................................................................................................. 28
Trial version activation ...................................................................................................................................... 28
Activating the application with an activation code ............................................................................................. 29
Activating the application with a key file ............................................................................................................ 30
APPLICATION INTERFACE ........................................................................................................................................ 31
Kaspersky Endpoint Security icon .......................................................................................................................... 31
Main application window ......................................................................................................................................... 33
Application preferences window ............................................................................................................................. 34
Notification windows and pop-up messages ........................................................................................................... 35
About notifications ............................................................................................................................................. 36
Methods of receiving notifications ..................................................................................................................... 36
Configuring receipt of notifications .................................................................................................................... 37
About pop-up messages ................................................................................................................................... 38
Configuring the Kaspersky Endpoint Security interface .......................................................................................... 38
STARTING AND STOPPING THE APPLICATION ...................................................................................................... 40
Closing Kaspersky Endpoint Security ..................................................................................................................... 40
Configuring the automatic startup of Kaspersky Endpoint Security ........................................................................ 40
Configuring the power-saving mode ....................................................................................................................... 41
Page 9

C O N T E N T
9
COMPUTER PROTECTION STATUS ......................................................................................................................... 42
Assessing the computer's protection status ............................................................................................................ 42
Security Assistant ................................................................................................................................................... 43
SOLVING TYPICAL TASKS ......................................................................................................................................... 44
How to perform a full scan of your computer for viruses ......................................................................................... 44
How to perform a quick scan of your computer ...................................................................................................... 45
How to scan a file, folder or disk for viruses ........................................................................................................... 45
How to configure a scheduled scan of your computer ............................................................................................ 45
How to purchase or renew license .......................................................................................................................... 46
How to update application databases and modules ............................................................................................... 46
How to export the application preferences to Kaspersky Endpoint Security installed on another computer ........... 47
What to do if file access is blocked ......................................................................................................................... 47
What to do if you suspect an object of being infected with a virus .......................................................................... 48
How to restore an object that has been deleted or disinfected by the application .................................................. 49
How to view the report on the application's operation ............................................................................................. 49
What to do when the application's notifications appear .......................................................................................... 49
ADVANCED APPLICATION SETTINGS ...................................................................................................................... 50
Creating a protection scope .................................................................................................................................... 50
Selecting malicious programs to be monitored ................................................................................................. 50
Creating a trusted zone ..................................................................................................................................... 52
File Anti-Virus ......................................................................................................................................................... 54
Disabling file protection ..................................................................................................................................... 55
Restoring protection on your computer ............................................................................................................. 57
Configuring File Anti-Virus ................................................................................................................................ 58
Selecting the security level .......................................................................................................................... 58
Specifying the types of files to scan ............................................................................................................ 59
Creating a protection scope ........................................................................................................................ 60
Configuring additional settings .................................................................................................................... 61
Selecting actions on objects ........................................................................................................................ 63
Restoring default file protection settings ........................................................................................................... 63
File protection statistics ..................................................................................................................................... 64
Virus Scan .............................................................................................................................................................. 65
Managing virus scan tasks ................................................................................................................................ 66
Launching / pausing virus scan task ............................................................................................................ 66
Creating virus scan tasks ............................................................................................................................ 68
Creating a list of objects to scan ....................................................................................................................... 70
Configuring virus scan tasks ............................................................................................................................. 71
Selecting the security level .......................................................................................................................... 72
Specifying the types of objects to scan ....................................................................................................... 73
Selecting actions on objects ........................................................................................................................ 74
Configuring the virus scan task schedule .................................................................................................... 75
Running scan tasks under user account ..................................................................................................... 76
Assigning uniform scan settings to all tasks ................................................................................................ 77
Restoring default scan settings ......................................................................................................................... 78
Virus scan statistics .......................................................................................................................................... 79
Updating the application ......................................................................................................................................... 81
Starting update .................................................................................................................................................. 82
Rolling back the last update .............................................................................................................................. 82
Page 10

A D M I N I S T R A T O R ' S G U I D E
10
Updating from a local source ............................................................................................................................ 83
Configuring the update ...................................................................................................................................... 85
Selecting the update mode and objects ...................................................................................................... 85
Selecting an update source ......................................................................................................................... 86
Configuring scheduled update task launch .................................................................................................. 88
Configuring connection to a proxy server .................................................................................................... 88
Update statistics ................................................................................................................................................ 89
Reports and Storages ............................................................................................................................................. 90
Quarantine ........................................................................................................................................................ 91
Viewing the contents of Quarantine............................................................................................................. 91
Actions on quarantined objects ................................................................................................................... 92
Scan of Quarantine after update ................................................................................................................. 93
Backup Storage ................................................................................................................................................ 94
Viewing the contents of Backup .................................................................................................................. 94
Actions on backup copies ............................................................................................................................ 95
Reports ............................................................................................................................................................. 96
Configuring reports and storages ...................................................................................................................... 98
Configuring the report settings .................................................................................................................... 98
Configuring Quarantine and Backup Storage .............................................................................................. 99
WORKING WITH THE APPLICATION FROM THE COMMAND LINE ...................................................................... 101
Viewing Help ......................................................................................................................................................... 102
Virus scan ............................................................................................................................................................. 102
Updating the application ....................................................................................................................................... 104
Rolling back the last update .................................................................................................................................. 105
Starting / stopping a protection component or a task ............................................................................................ 105
Statistics on a component's operation or a task ................................................................................................... 106
Exporting protection settings ................................................................................................................................ 107
Importing protection settings ................................................................................................................................. 107
Activating the application ...................................................................................................................................... 107
Closing the application ......................................................................................................................................... 108
Return codes of the command line ....................................................................................................................... 108
MANAGING THE APPLICATION VIA KASPERSKY ADMINISTRATION KIT ........................................................... 109
Standard deployment scheme .............................................................................................................................. 111
Installing software required for the remote administration of Kaspersky Endpoint Security .................................. 112
Installing the Kaspersky Endpoint Security management plugin ..................................................................... 112
Local installation of Network Agent ................................................................................................................. 113
Installation of Network Agent using the SSH protocol ..................................................................................... 114
Updating Network Agent via Kaspersky Administration Kit ............................................................................. 115
Uninstallation of Network Agent ...................................................................................................................... 116
Remote installation of Kaspersky Endpoint Security ............................................................................................ 117
Installing the application using the SSH protocol ............................................................................................ 117
Installing the application via Kaspersky Administration Kit .............................................................................. 118
Removing the application via Kaspersky Administration Kit ............................................................................ 119
Managing Network Agent ..................................................................................................................................... 120
Connecting a client computer to Administration Server manually. Utility tool klmover .................................... 121
Checking the connection between a client computer and Administration Server manually. Utility tool klnagchk122
Starting / stopping Network Agent on a client computer ................................................................................. 123
Administering the application ................................................................................................................................ 123
Page 11

C O N T E N T
11
Starting and stopping the application .............................................................................................................. 124
Modifying the application settings ................................................................................................................... 126
Enabling and disabling file protection ........................................................................................................ 126
Configuring the automatic startup of Kaspersky Endpoint Security ........................................................... 128
Creating a trusted zone ............................................................................................................................. 128
Selecting malicious programs to be monitored .......................................................................................... 130
Configuring the power-saving mode .......................................................................................................... 131
Configuring receipt of notifications ............................................................................................................ 132
Configuring the Kaspersky Endpoint Security icon display ........................................................................ 133
Configuring the report settings .................................................................................................................. 133
Configuring Quarantine and Backup Storage ............................................................................................ 135
Configuring connection to a proxy server .................................................................................................. 135
Managing tasks .................................................................................................................................................... 136
Starting and stopping tasks ............................................................................................................................. 138
Creating tasks ................................................................................................................................................. 139
New task wizard .............................................................................................................................................. 140
Step 1. Entering general data on the task ................................................................................................. 140
Step 2. Selecting an application and defining the task type ...................................................................... 140
Step 3. Configuring settings for the selected task type .............................................................................. 140
Step 4. Configuring a schedule ................................................................................................................. 141
Step 5. Completing task creation............................................................................................................... 141
Configuring task settings ................................................................................................................................. 141
Configuring File Anti-Virus ......................................................................................................................... 143
Configuring virus scan tasks ..................................................................................................................... 144
Configuring the update task ...................................................................................................................... 146
Managing policies ................................................................................................................................................. 147
Creating policies ............................................................................................................................................. 148
Policy Creation Wizard .................................................................................................................................... 148
Step 1. Entering general data on the policy ............................................................................................... 148
Step 2. Selecting an application ................................................................................................................ 148
Step 3. Selecting a policy status................................................................................................................ 149
Step 4. Configuring web traffic settings ..................................................................................................... 149
Step 5. Adjusting the virus scan settings ................................................................................................... 149
Step 6. Configuring update settings .......................................................................................................... 149
Step 7. Network configuration ................................................................................................................... 150
Step 8. Configuring user interaction settings ............................................................................................. 150
Step 9. Configuring reports and storages .................................................................................................. 150
Step 10. Completing creation of a policy ................................................................................................... 151
Configuring policy settings .............................................................................................................................. 151
CONTACTING TECHNICAL SUPPORT SERVICE ................................................................................................... 153
APPENDIX ................................................................................................................................................................. 155
List of objects to scan by extension ...................................................................................................................... 155
Permissible file exclusion masks .......................................................................................................................... 157
Allowed exclusion masks according to the Virus Encyclopedia classification ....................................................... 158
Page 12

A D M I N I S T R A T O R ' S G U I D E
12
GLOSSARY ............................................................................................................................................................... 159
KASPERSKY LAB ...................................................................................................................................................... 164
INFORMATION ABOUT THIRD-PARTY CODE ........................................................................................................ 165
Program code ....................................................................................................................................................... 165
ADOBE ABI-SAFE CONTAINERS 1.0 ............................................................................................................ 166
BOOST 1.39.0 ................................................................................................................................................ 166
CURL 7.19.3 ................................................................................................................................................... 166
EXPAT 1.2 ...................................................................................................................................................... 166
FMT.H ............................................................................................................................................................. 167
GROWL 1.1.5 ................................................................................................................................................. 167
INFO-ZIP 5.51 ................................................................................................................................................. 168
LIBPNG 1.2.8 .................................................................................................................................................. 168
LIBUTF............................................................................................................................................................ 168
LZMALIB 4.43 ................................................................................................................................................. 169
MD5.H ............................................................................................................................................................. 169
MD5.H ............................................................................................................................................................. 169
RFC1321-BASED (RSA-FREE) MD5 LIBRARY ............................................................................................. 169
SHA1.C 1.2 ..................................................................................................................................................... 169
STLPORT 5.2.1 .............................................................................................................................................. 170
TINYXML 2.5.3 ............................................................................................................................................... 170
ZLIB 1.0.8, 1.2.3 ............................................................................................................................................. 170
Development tools ................................................................................................................................................ 170
GCC 4.0.1 ....................................................................................................................................................... 170
Other information .................................................................................................................................................. 174
INDEX ........................................................................................................................................................................ 176
Page 13
13
ABOUT THIS GUIDE
IN THIS SECTION:
In this document .............................................................................................................................................................. 13
Document conventions .................................................................................................................................................... 15
This document is a guide to the installation, setup and operation of Kaspersky Endpoint Security 8 for Mac, as well as for
remote administration of the application through Kaspersky Administration Kit. This document is intended both for a wide
audience and for system administrators. Users should have a basic knowledge of working with an Apple Macintosh. They
should be familiar with the interface of the Mac OS X operating system, have basic skills of working with it and be able to
use email programs and the Internet.
The aim of the document is:
to help users to install the application on the computer on their own, and activate and configure it with regard to
their needs;
to help an administrator in solving problems related to remote administration of the application through
Kaspersky Administration Kit;
to provide a quick search of the information on application related issues;
to tell users about additional sources of information about the application and explain how to contact Kaspersky
Lab Technical Support Service.
IN THIS DOCUMENT
The user guide for Kaspersky Endpoint Security 8 is comprised of the following sections:
Additional sources of information
This sections lists sources of additional information about the application and Internet resources where you can discuss
it, share your ideas, ask questions, and receive answers.
Kaspersky Endpoint Security 8
This section contains a description of the application's new features, and brief information on its components and
functionality. It shows the function of each part of the package supplied and a range of services available to registered
users of the application. This section contains hardware and software requirements which the computer must meet for
the installation of Kaspersky Endpoint Security.
Installing the application
This section contains instructions that will help you to install the application on the computer locally. This section also
describes the application uninstall procedure.
License management
This section contains information regarding the basic concepts used in the context of the application licensing. This
section describes how to activate the application, where to view information about the current license, and how to
purchase and renew a license.
Page 14

A D M I N I S T R A T O R ' S G U I D E
14
Application interface
This section contains description of the basic GUI components of the application: icon and context menu, main
application window, settings window, and notification windows.
Starting and stopping the application
This section provides you with information about how to launch the application and close it.
Computer protection status
This section contains information about how to know whether your computer is protected at the moment, or if its security
is under threat, as well as how to eliminate emerging threats with the help of Security Assistant.
Solving typical tasks
This section describes the tasks encountered by the most users when working with the application as well as the
procedures developed for carrying out these tasks.
Advanced application settings
This section provides detailed information about each application component and describes the operation and
configuration algorithms for each component.
Working with the application from the command line
This section contains description of the use of the application and its components involving the command line.
Administering the application via Kaspersky Administration Kit
This section contains a detailed description of the installation of Kaspersky Endpoint Security onto a remote user
computer, as well as the installation of software required for remote administration of the application through Kaspersky
Administration Kit. This section discusses application deployment over the network and remote administration of the
application through Kaspersky Administration Kit using tasks and group policies.
Contacting Technical Support Service
This section contains instructions for contacting Kaspersky Lab support services.
Appendix
This section includes reference information which complements the document text.
Glossary
This section contains the list of terms used in the document and their definitions.
Page 15
A B O U T T H I S GU I D E
15
SAMPLE TEXT
DOCUMENT CONVENTIONS DESCRIPTION
Please note that...
Warnings are highlighted in red and enclosed in frames. Warnings contain
important information, for example, on safety-critical computer operations.
It is recommended to use...
Notes are enclosed in frames. Notes contain additional and reference
information.
Example:
...
Examples are given in section, on a yellow background, and under the heading
"Example".
A virus is...
New terms are marked in italics.
Command-A
Names of keyboard keys appear in a bold typeface.
Key names joined by a "minus" sign represent key combinations.
Enable
Names of interface components, for example, input fields, menu commands,
buttons, etc., are indicted in bold.
To configure a task schedule:
Instructions are marked by the arrow symbol.
Introductory phrases to introductions are marked in italics.
kav update
Text in the command line or text of messages displayed on screen has a special
font.
<IP address of your computer>
Variables are enclosed in angle brackets. Instead of a variable, the
corresponding value is placed in each case, and the angle brackets are omitted.
DOCUMENT CONVENTIONS
The document conventions described in the table below are used in this Guide.
Table 1. Document conventions
Page 16

16
ADDITIONAL SOURCES OF INFORMATION
You can refer to the following sources of information about the application:
application page at the Kaspersky Lab website;
application page at the Technical Support Service website (Knowledge Base);
Kaspersky Lab products users forum;
help system.
Application page at the Kaspersky Lab website
This page (http://www.kaspersky.com/endpoint-security-mac) will provide you with general information on Kaspersky
Endpoint Security 8 and its features and options. You can purchase Kaspersky Endpoint Security 8 or extend your
license in our eStore.
Application page at the Technical Support Service website (Knowledge Base)
Knowledge Base is a separate section of the Technical Support Service website
(http://support.kaspersky.com/kes8mac), which provides recommendations for using Kaspersky Lab products. This
page contains articles published by Technical Support Service.
These articles provide useful information, recommendations and answers to frequently asked questions related to
the purchase, installation and use of Kaspersky Endpoint Security 8. They are grouped by topics, for example:
"Troubleshooting", "Configuring the update", or "Configuring File Anti-Virus". The articles may answer questions,
which are related not only to Kaspersky Endpoint Security 8 but also to other Kaspersky Lab products; they also
may contain Technical Support Service news.
To switch to the Knowledge Base, open the main application window (on page 33), click the button and click the
Technical Support Service button in the window that opens.
Users forum
If your question does not require an urgent answer, you can discuss it with Kaspersky Lab specialists and other
users in our forum (http://forum.kaspersky.com). It is also a separate section on the Technical Support Service
website and contains Kaspersky Endpoint Security 8 users' questions, feedback, and requests.
In this forum you can view existing topics, leave comments, create new topics, and use the search engine.
To go to this resource, open the main application window (on page 33), click the button and in the window that
opens click the Forum button.
Help system
The application includes the full help and context help files. The full help file contains information about how to
manage the protection of your computer: view the protection status, scan various areas of your computer for viruses,
perform updates, handle reports and storages. Besides that, the context help file provides you with information about
all windows of the application, listing and describing the settings and tasks related to each of them.
To open the full help, open the main application window (on page 33) and click the button. To open the context
help, open the required window or the tab, and click the button.
Page 17

A D D I T I O N A L S O U R C E S O F I N F O R M A T I O N
17
If you cannot find a solution to your problem in the Knowledge Base, in the Users forum, in the help system or
documentation, we recommend that you contact Kaspersky Lab Technical Support Service (see section "Contacting
Technical Support Service" on page 153).
Page 18

18
KASPERSKY ENDPOINT SECURITY 8
Kaspersky Endpoint Security 8 for Mac (hereinafter Kaspersky Endpoint Security) is intended for use under the Mac OS
X operating system to protect your computer from viruses and malware. The following options are implemented in the
application:
File Anti-Virus
Real-time protection of the computer's file system: interception and analysis of attempts to access the file system;
disinfection, deletion of malicious objects and isolation of potentially infected objects for further analysis.
Virus Scan
Search and deactivation of malicious code at the user's request: search and analysis of malicious and potentially
infected objects in the designated protection areas; disinfection, deletion, or isolation of objects for further analysis.
The most useful virus scan tasks are included in the Kaspersky Endpoint Security package: full computer scan and
quick scan of critical areas.
Update
Updating of databases and modules of Kaspersky Endpoint Security from Kaspersky Lab's update servers and from
Kaspersky Administration Kit Administration Server, creation of backup copies of all the updated files to allow a
future roll back; copying of updates into a local source to allow other networked computers to access them, thereby
reducing Internet traffic.
Quarantine
Moving potentially infected objects to Quarantine: storage of potentially infected objects in the Quarantine folder,
further scan using updated databases, restoration of objects from the storage upon the user's request.
Backup Storage
Creation of a copy of each infected object to store in Backup Storage before disinfecting or deleting it, so that it can
later be restored or further analyzed for investigation.
Reports
Compilation of a detailed report on the performance of each Kaspersky Endpoint Security component.
Notifications
Notification of the user about certain events which occur during the operation of Kaspersky Endpoint Security. You
can select the notification for each event type, whether an audio or pop-up message.
You can change the appearance of the Kaspersky Endpoint Security by using various graphic elements and selected
color solutions.
When working with Kaspersky Endpoint Security, you will be provided with complete information support: application
returns messages on the protection status and offers detailed guidance. Security Assistant (on page 43), included in the
application package, provides a complete picture of the computer's current protection status and troubleshooting options.
Page 19

K A S P E R S K Y E N D P O I N T SE C U RI T Y 8
19
IN THIS SECTION:
Distribution kit .................................................................................................................................................................. 19
Hardware and software system requirements ................................................................................................................. 19
DISTRIBUTION KIT
You can purchase Kaspersky Endpoint Security (boxed edition) from our resellers or in an online store (such as
www.kaspersky.com, eStore section).
If you buy the boxed version of the program, the package will include:
A sealed envelope containing the installation CD containing the program files and documentation in PDF format.
The end-user license agreement (EULA).
In addition, the package may include:
A printed User Guide (if this item was included in the order) or a Product Guide.
The program activation code, attached to the installation CD envelope.
Registration card (with product serial number).
Before breaking the seal on the installation disk envelope, carefully read through the License Agreement. By unsealing
the envelope with the installation CD, you accept all the provisions of the License Agreement.
When purchasing Kaspersky Endpoint Security online, you download the product from the Kaspersky Lab website, which
includes this documentation. You will be sent a key file or activation code by email once payment has been made.
HARDWARE AND SOFTWARE SYSTEM REQUIREMENTS
For the proper functioning of Kaspersky Endpoint Security, a computer should meet the following minimum requirements:
Intel-based Apple Macintosh computer (PowerPC processor not supported);
1 GB RAM;
500 MB of free hard drive space;
Mac OS X 10.5 operating system, or higher, or Mac OS X Server 10.6.
To install Network Agent required for remote administration of Kaspersky Endpoint Security through Kaspersky
Administration Kit, the user's computer must meet the following minimum requirements:
Intel-based Apple Macintosh computer (PowerPC processor not supported);
512 MB RAM;
500 MB free hard drive space;
Mac OS X 10.5 operating system, or higher, or Mac OS X Server 10.6.
Page 20

20
INSTALLING THE APPLICATION
IN THIS SECTION:
Preparing for installation.................................................................................................................................................. 20
Installing the application .................................................................................................................................................. 20
Preparing for use after installation ................................................................................................................................... 23
Deleting the application ................................................................................................................................................... 24
This section contains instructions that will help you to install the application on the computer locally. This section also
describes the application uninstall procedure.
The Kaspersky Endpoint Security installation package includes the Installation Assistant and the Uninstall Assistant.
Remote administration of Kaspersky Endpoint Security through Kaspersky Administration Kit requires the Kaspersky
Endpoint Security plugin to be installed on the administrator's workstation, and Network Agent to be installed on the
user's computer (see section "Installing software required for remote administration of Kaspersky Endpoint Security" on
page 112). It is also possible to remotely install Kaspersky Endpoint Security on the user's computer (see section
"Remote installation of Kaspersky Endpoint Security" on page 117).
PREPARING FOR INSTALLATION
Before installing Kaspersky Endpoint Security on your computer, follow these preparatory steps:
Make sure that your computer meets the minimum system requirements (see section "Hardware and software
requirements" on page 19).
Check your computer's connection to the Internet. Internet access is needed to activate the application using
the activation code and to download updates.
Delete any existing anti-virus software to avoid system conflicts and maximize performance.
INSTALLING THE APPLICATION
Two methods of Kaspersky Endpoint Security installation are available:
Default installation (see section "Kaspersky Endpoint Security default installation" on page 21).
The default set of application components will be installed.
Custom installation (see section "Kaspersky Endpoint Security custom installation" on page 22).
Recommended for experienced users and allows customizing installation of components.
Page 21

I N S T A L L I N G T H E A P P L I C A T I O N
21
KASPERSKY ENDPOINT SECURITY DEFAULT INSTALLATION
To install Kaspersky Endpoint Security 8 using the default settings:
1. Open the contents of the Kaspersky Endpoint Security installation file. To do this, insert an installation CD into
the disk drive.
If you purchased Kaspersky Endpoint Security in an online store, then an application installation package in .zip
format will be available to download on the Kaspersky Lab website. Extract it and run the .dmg file to view the
package contents.
2. Launch the Kaspersky Endpoint Security Installation Assistant. To do this, open the Kaspersky Endpoint
Security installation package in the window containing the distribution package.
Follow the Installation Assistant's instructions to install the application.
3. In the Introduction window, click Continue.
4. In the Information window, read the information about the application.
Make sure that your computer meets the minimum system requirements. To print the information, click the Print
button. To save the information as a text file, click the Save button. To proceed with the installation, click
Continue.
5. In the License window, you can read the text of the Kaspersky Endpoint Security licensing agreement between
you and Kaspersky Lab. The text of the agreement is available in several languages. To print the text of the
agreement, click the Print button. To save the agreement as a text file, click the Save button.
If you agree with all the clauses in the agreement, click Continue. A window opens to request confirmation of
your consent to the conditions of the licensing agreement. You can perform the following actions:
Proceed with the installation of Kaspersky Endpoint Security. To do so, click the Agree button.
Return to the text of the agreement. To do this, click the Read license button.
Stop the installation. To do so, click the Disagree button.
6. In the Type of installation window, read the information about the drive on which the application will be
installed and the volume of free disk space required.
To install the application using the recommended settings, click the Install button and enter the administrator's
password to confirm your choice.
To select a different drive for installation, click the Change location button, select a different drive and then
click Continue.
The drive used to install the application must be bootable. The minimum version, or higher, of the operating
system specified in the system requirements (see section "Hardware and software requirements" on page 19)
must be installed on the hard drive.
Wait until the Kaspersky Endpoint Security Installation Assistant installs the application components.
7. In the Summary window, read the information about the installation process and click the Close button to exit
the Installation Assistant.
Kaspersky Endpoint Security starts up automatically when installation is complete. You do not have to restart
the computer.
Page 22

A D M I N I S T R A T O R ' S G U I D E
22
KASPERSKY ENDPOINT SECURITY CUSTOM INSTALLATION
To perform Kaspersky Endpoint Security custom installation:
1. Open the contents of the Kaspersky Endpoint Security installation file. To do this, insert an installation CD into
the disk drive.
If you purchased Kaspersky Endpoint Security in an online store, then an application installation package in .zip
format will be available to download on the Kaspersky Lab website. Extract it and run the .dmg file to view the
package contents.
2. Launch the Kaspersky Endpoint Security Installation Assistant. To do this, open the Kaspersky Endpoint
Security installation package in the window containing the distribution package.
Follow the Installation Assistant's instructions to install the application.
3. In the Introduction window, click Continue.
4. In the Information window, read the information about the application.
Make sure that your computer meets the minimum system requirements. To print the information, click the Print
button. To save the information as a text file, click the Save button. To proceed with the installation, click
Continue.
5. In the License window, you can read the text of the Kaspersky Endpoint Security licensing agreement between
you and Kaspersky Lab. The text of the agreement is available in several languages. To print the text of the
agreement, click the Print button. To save the agreement as a text file, click the Save button.
If you agree with all the clauses in the agreement, click Continue. A window opens to request confirmation of
your consent to the conditions of the licensing agreement. You can perform the following actions:
Proceed with the installation of Kaspersky Endpoint Security. To do so, click the Agree button.
Return to the text of the agreement. To do this, click the Read license button.
Stop the installation. To do so, click the Disagree button.
6. In the Type of installation window, read the information about the drive on which the application will be
installed and the volume of free disk space required.
To select a different drive for installation, click the Change location button, select a different drive and then
click Continue.
The drive used to install the application must be bootable. The minimum version, or higher, of the operating
system specified in the system requirements (see section "Hardware and software requirements" on page 19)
must be installed on the hard drive.
Click the Preferences button to select application components for custom installation.
7. In the window that opens, specify which components are to be installed on the computer. Check the boxes next
to the components that are not to be installed.
Virus Scan. Scans objects in the user-defined scopes.
This component of Kaspersky Endpoint Security is always installed by default.
File Anti-Virus. Scans all objects opened, executed or saved in real-time.
Page 23

I N S T A L L I N G T H E A P P L I C A T I O N
23
Finder Context Menu. Scans objects displayed in Finder. Scans are started from the object context menu.
Connector for Network Agent. Necessary for remote administration of the program through Kaspersky
Administration Kit.
Once the components are selected, click the Install button and enter the administrator's password to confirm
the installation. To return to the default installation settings (see section "Kaspersky Endpoint Security default
installation" on page 21), click the Default installation button.
Wait until the Kaspersky Endpoint Security Installation Assistant installs the selected application components.
8. In the Summary window, read the information about the installation process and click the Close button to exit
the Installation Assistant.
Kaspersky Endpoint Security starts up automatically when installation is complete. You do not have to restart
the computer.
PREPARING FOR USE AFTER INSTALLATION
After Kaspersky Endpoint Security has been installed, we recommend that you take the following actions:
Activate Kaspersky Endpoint Security (see section "Kaspersky Endpoint Security activation" on page 28). Using
a licensed version will let you update the application's databases on a regular basis and access Technical
Support Service.
Assess the current protection status (see section "Protection status overview" on page 42) to make sure that
Kaspersky Endpoint Security is set at the right protection level.
Update Kaspersky Endpoint Security (see section "How to update databases and application modules" on
page 46). It is important to keep the Kaspersky Endpoint Security databases up-to-date so that the application is
able to detect and deal with malware.
Run a full computer virus scan (see section "How to perform a full computer virus scan" on page 44).
If you encounter any problems or errors in the operation of the application, open the Kaspersky Endpoint Security
operation report window (see section "Reports" on page 96). The cause may be described in the report. If you cannot
solve the problem on your own, please contact Kaspersky Lab Technical Support Service (see section "Contacting
Technical Support Service" on page 153).
Page 24
A D M I N I S T R A T O R ' S G U I D E
24
DELETING THE APPLICATION
By uninstalling Kaspersky Endpoint Security, you will expose your computer to a serious risk of infection.
Before uninstalling the application, we recommend that you process all objects stored in Quarantine and Backup
Storage. All stored objects that have not been processed will be deleted without any opportunity to restore them in the
future.
To uninstall Kaspersky Endpoint Security from your computer:
1. Open the contents of the Kaspersky Endpoint Security installation file. To do this, insert an installation CD into
the disk drive
If you purchased Kaspersky Endpoint Security in an online store, then an application installation package in .zip
format will be available to download on the Kaspersky Lab website. Extract it and run the .dmg file to view the
package contents.
2. Launch the Kaspersky Endpoint Security Uninstaller. To do this, select the Kaspersky Endpoint Security
Uninstaller in the window that contains the contents of the installation file.
Follow the steps to uninstall the application.
3. In the Introduction window, click Continue.
4. In the Information window, read the important information. To start the uninstallation procedure, click the
Delete button and enter the administrator's password to confirm. Wait until the application removal is complete.
5. In the Summary window, read the information about the uninstallation process termination and click the Finish
button to exit the Uninstall Assistant.
There is no need to reboot the computer after the Kaspersky Endpoint Security uninstall process.
Page 25

25
LICENSE MANAGEMENT
IN THIS SECTION:
About license ................................................................................................................................................................... 25
Viewing license information ............................................................................................................................................. 26
Purchasing a license ....................................................................................................................................................... 26
Renewing a license ......................................................................................................................................................... 27
About End User License Agreement ............................................................................................................................... 28
About the activation code ................................................................................................................................................ 28
About the key file ............................................................................................................................................................. 28
Kaspersky Endpoint Security activation .......................................................................................................................... 28
This section contains information regarding the basic concepts used in the context of the application licensing. This
section describes how to activate the application, where to view information about the current license, and how to
purchase and renew a license.
ABOUT LICENSE
License – this is the right to use Kaspersky Endpoint Security and the additional related services provided by Kaspersky
Lab and its partners.
Each license is defined by its validity period and type.
License term – a period during which the additional services are offered:
technical support;
update databases and application modules.
The services available depend on the type of license.
There are two types of license:
Trial – a free license with a limited validity period, for example, 30 days, offered as an introduction to Kaspersky
Endpoint Security.
Trial license can be used only once.
If you have a trial license, you may contact Technical Support Service only if your question is about activating
the product or purchasing a commercial license. When the trial license expires, Kaspersky Endpoint Security
keeps performing all of its functions, but anti-virus databases of the application are no longer updated. To
proceed with the application, you should activate it (see section "Kaspersky Endpoint Security activation" on
page 28).
Page 26

A D M I N I S T R A T O R ' S G U I D E
26
Commercial – paid license with a limited validity period (for example, one year).
All functions and additional services are available during the validity period of a commercial license.
As soon as a commercial license expires, Kaspersky Endpoint Security remains a full-featured application, but
the anti-virus databases are not updated. As before, you will be able to scan your computer for viruses and use
the protection components, but using only the anti-virus databases you had when the license expired. To protect
your computer from infection with new viruses, we recommend that you renew your application license.
After you have activated the application with the commercial license, you can purchase the additional license for
Kaspersky Endpoint Security and activate it. In this case, when the active license expires, the additional license
will automatically replace it, thus allowing the application to keep running without any changes. Only one
additional license can be activated for Kaspersky Endpoint Security.
VIEWING LICENSE INFORMATION
To view information about your current license,
open the main application window (on page 33) and click the button.
License number and type (commercial or trial), maximum number of hosts, expiration date and time, and days remaining
until the expiration are all displayed in the window that opens (see figure below).
If there is no license, Kaspersky Endpoint Security will notify you of this. If the application is not activated, you can start
the activation procedure (see section "Kaspersky Endpoint Security activation" on page 28). If the trial version of the
application is activated, you can purchase the commercial license (see section "Purchasing a license" on page 26). If
your commercial license expires, you can renew it (see section "Renewing a license" on page 27).
PURCHASING A LICENSE
To purchase a new license:
1. Open the main application window (on page 33) and click the button.
2. In the window that opens (see figure below), click the Purchase button.
Figure 1. License management
Page 27
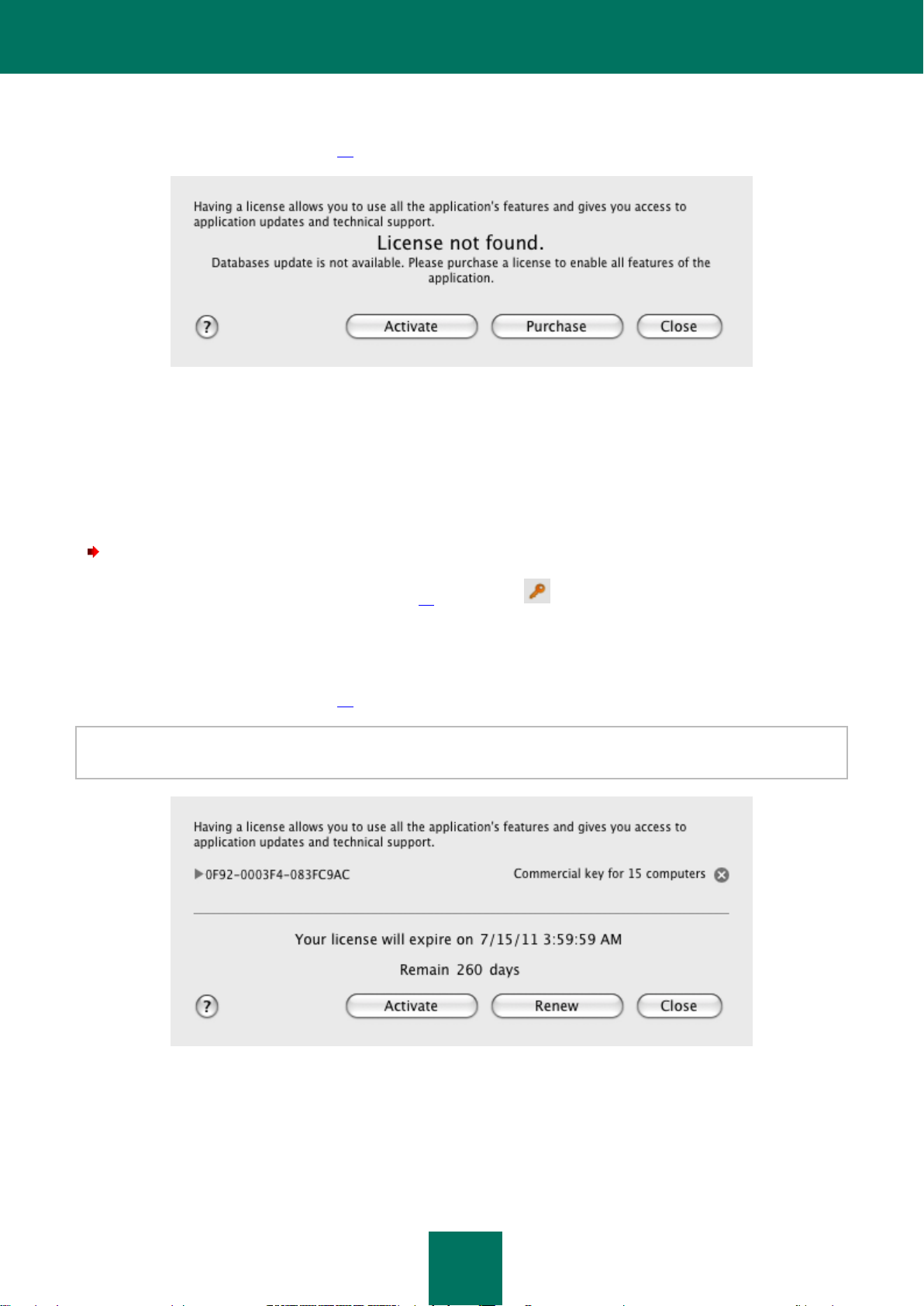
L I C E N S E M A N A G E M E N T
27
The web page that opens contains all the information on purchasing a key through Kaspersky Lab eStore or corporate
partners. On purchasing a license at Kaspersky Lab eStore, an activation code for Kaspersky Endpoint Security (see
section "About activation code" on page 28) will be sent to the email address that you have specified in the order form.
Figure 2. Purchasing a license
RENEWING A LICENSE
The application license needs to be renewed when the current license expires. In this case, Kaspersky Endpoint Security
keeps performing all of its operations but anti-virus databases are no longer updated.
To renew your current license:
1. Open the main application window (on page 33) and click the button.
2. In the window that opens (see figure below), click the Renew button.
The web page that opens contains all the information on license renewal through Kaspersky Lab eStore or corporate
partners. On renewing a license at Kaspersky Lab eStore, an activation code for Kaspersky Endpoint Security (see
section "About activation code" on page 28) to the email address that you have specified in the order form.
Kaspersky Lab regularly organizes special pricing offers on license renewals for our products. Check for special offers at
Kaspersky Lab website, in the Products → Sales and special offers section.
Figure 3. License management
Page 28
A D M I N I S T R A T O R ' S G U I D E
28
ABOUT END USER LICENSE AGREEMENT
IN THIS SECTION:
Trial version activation..................................................................................................................................................... 28
Activating the application with an activation code ........................................................................................................... 29
Activating the application with a key file .......................................................................................................................... 30
End User License Agreement – is an agreement between a natural or legal person lawfully in possession of a copy of
Kaspersky Endpoint Security and Kaspersky Lab. The EULA is included in each Kaspersky Lab application. It provides
detailed information on the rights and usage restrictions of Kaspersky Endpoint Security.
ABOUT THE ACTIVATION CODE
Activation code is a code supplied with Kaspersky Endpoint Security commercial license. This code is required for
application activation.
The activation code represents a sequence of Latin characters and digits divided by hyphens into four groups of five
symbols without spaces. For example, 11111-11111-11111-11111.
ABOUT THE KEY FILE
The availability of Kaspersky Endpoint Security is ensured by a key file. You are provided with a key file on the basis of
the activation code (see section "About the activation code" on page 28) obtained when purchasing the application; it
entitles you to use the latter starting from the day of activation. The key file contains information about the license: the
type, date of expiry and number of hosts.
KASPERSKY ENDPOINT SECURITY ACTIVATION
Before activating Kaspersky Endpoint Security, make sure that the current system date value on your computer matches
the actual date and time.
The activation procedure consists of installing a key file (see section "About the key file" on page 28) that Kaspersky
Endpoint Security applies to verify the rights for the use of the application and define the term of its use.
The application is activated using the Activation Assistant. Follow these steps to activate the application.
At any stage in the Activation Wizard you can click the Cancel button to interrupt the activation. The Activation Wizard
will close. If the application has not been activated, all options of Kaspersky Endpoint Security are available, except the
retrieval of updates. The application can be updated only once after installation.
TRIAL VERSION ACTIVATION
The Activation Assistant only offers you to activate the trial version if this version of Kaspersky Endpoint Security has
never been installed on your computer.
Page 29
L I C E N S E M A N A G E M E N T
29
Select this activation option if you want to install the trial version of the application before deciding whether to purchase
the commercial version. You will be granted a free license key with validity period limited by the trial license.
Your computer must be connected to the Internet. If the Internet connection is currently unavailable, you can activate the
trial version later.
To activate the trial version of the application:
1. Open the main application window (on page 33) and click the button.
2. In the window that opens, click the Activate button. This launches the Activation Assistant. Follow these steps
to activate the application.
3. In the Activation method window, select Activate trial version.
4. In the Obtaining key file window, wait until the Activation Assistant establishes connection with Kaspersky Lab
servers and sends data for verification. If the data are successfully verified, the Assistant receives and installs a
key file with a validity period limited by the trial license.
If the validity period of the trial license has expired, an onscreen notification will appear.
5. In the Key file information window, the Activation Assistant notifies you of the successful completion of the
activation process. In addition, information about the installed key is displayed, including the key number, key
type (trial), and the license key's expiration date. Click the Finish button to close the Activation Assistant.
ACTIVATING THE APPLICATION WITH AN ACTIVATION CODE
Select this activation option if you have purchased a commercial version of the application, and you have been provided
an activation code. Using this activation code, you will obtain a key file which provides access to the functionality of
Kaspersky Endpoint Security throughout the license validity period.
Your computer must be connected to the Internet. If the Internet connection is currently unavailable, you can activate the
trial version later.
To activate the application with your activation code, do the following:
1. Open the main application window (on page 33) and click the button.
2. In the window that opens, click the Activate button. This launches the Activation Assistant. Follow these steps
to activate the application.
3. In the Activation method window, select Activate with activation code.
4. In the Enter activation code window, enter the activation code that you received when you purchased
Kaspersky Endpoint Security.
The activation code is a sequence of numbers and letters delimited with hyphens in four groups of five symbols
without spaces, for example: 11AA1-11AAA-1AA11-1A111. Please note that the activation code should only be
entered in Latin characters.
5. In the Obtaining key file window, wait until the Activation Assistant establishes connection with Kaspersky Lab
servers and sends data for verification. If the activation code is verified, the Assistant downloads the key file.
Kaspersky Endpoint Security does not download a physical key file (with key extension) from the server, but
receives the relevant information to save in the operating system. To obtain a real key file, you should go
through the registration procedure on the Kaspersky Lab website (http://support.kaspersky.com/).
Page 30
A D M I N I S T R A T O R ' S G U I D E
30
If the activation code is not verified, the Assistant will display this information on the screen. In this case, contact
the software vendor you purchased Kaspersky Endpoint Security from for details.
6. In the Key file information window, the Activation Assistant notifies you of the successful completion of the
activation process. In addition, information about the installed key is displayed, including the key number, key
type (commercial), and the license key's expiration date. Click the Finish button to close the Activation
Assistant.
ACTIVATING THE APPLICATION WITH A KEY FILE
Use this option to activate the application with an existing key file.
If you have selected the activation using a key file, no Internet connection is required. We recommend that you use this
method of application activation if the Internet connection cannot be established, or if it is temporarily unavailable.
To activate the application with an existing key file:
1. Open the main application window (on page 33) and click the button.
2. In the window that opens, click the Activate button. This launches the Activation Assistant. Follow these steps
to activate the application.
3. In the Activation method window, select Use existing key file.
4. In the Select key file window, click the Select button and select the key file in the window that opens.
Information about the current key will be displayed in the bottom part of the window, including the key number,
the key type (commercial), and the license key expiration date.
5. In the Key file information window, the Activation Assistant notifies you of the successful completion of the
activation process. In addition, information about the installed key is displayed, including the key number, key
type, and the license key's expiration date. Click the Finish button to close the Activation Assistant.
Page 31

31
APPLICATION INTERFACE
IN THIS SECTION:
Kaspersky Endpoint Security icon ................................................................................................................................... 31
Main application window ................................................................................................................................................. 33
Application preferences window ...................................................................................................................................... 34
Notification windows and pop-up messages ................................................................................................................... 35
Configuring the Kaspersky Endpoint Security interface .................................................................................................. 38
This section contains description of the basic GUI components of the application: icon and context menu, main
application window, settings window, and notification windows.
KASPERSKY ENDPOINT SECURITY ICON
Immediately after Kaspersky Endpoint Security is installed, its icon appears in the Menu Bar. This icon is an indicator of
the application's operation. If the icon is active, it means that real-time protection against malware is enabled for the
computer's file system. The inactive icon indicates that the protection is disabled. In addition, the icon's context menu
provides access to the basic commands in Kaspersky Endpoint Security: enabling and updating the computer's file
system protection, launching update task or anti-virus scan, opening the settings window, etc.
By default, the icon is located on the Menu Bar. You can modify the application's preferences so that the Kaspersky
Endpoint Security icon is displayed in the Dock panel or not displayed at all.
To display the application icon in the Dock quick launch panel, do the following:
1. Open the application preferences window (on page 34) and select the Appearance section (see figure below).
2. In the Show application icon section select the In Dock option.
To remove the application icon:
1. Open the application preferences window (on page 34) and select the Appearance section (see figure below).
2. In the Show application icon section, select Nowhere.
Note that this modification will take place only after Kaspersky Endpoint Security is restarted.
Page 32

A D M I N I S T R A T O R ' S G U I D E
32
Figure 4. Application preferences window. Appearance
If you selected the option to display the application icon in the menu bar, the icon will not appear in Dock when the
application is started or the main window is opened. The Command-Tab key combination to switch to the application is
also unavailable.
If the application icon is disabled, the program will run in background mode. To open the main application window (on
page 33), click the Kaspersky Endpoint Security icon on the list of applications installed on the computer.
Figure 5. Context menu of the Kaspersky Endpoint Security icon in the Menu Bar
Page 33

A P P L I C A T I O N I N T E R F A C E
33
Figure 6. Context menu of the Kaspersky Endpoint Security icon in the Dock
MAIN APPLICATION WINDOW
To open the main application window,
click the Kaspersky Endpoint Security icon in the Menu Bar or in the Dock (see figure above), and select Endpoint
Security from the context menu that opens.
The basic task of the Kaspersky Endpoint Security main window (see figure below) is to inform the user of the computer's
protection status and any related problems, to provide information about software components (File Anti-Virus, Virus
Scan and Update task), and to ensure access to the main tasks and the settings window.
Figure 7. Kaspersky Endpoint Security 8 main window
Page 34

A D M I N I S T R A T O R ' S G U I D E
34
There are three possible protection status values (see section "Protection status overview" on page 42), which use a
Launch Kaspersky Endpoint Security update. At the end of the update the report window (see section "Reports"
on page 96) will show detailed information about the task execution.
Switch to virus scan tasks: Quick Scan, Full Scan, and Virus Scan in an area specified by the user, as well as
all custom virus scan tasks if any of them have been created. At the end of the update the report window (see
section "Reports" on page 96) will show detailed information about the task execution.
Switch to the window that displays information about the current license.
Open the report window (see section "Reports" on page 96) of Kaspersky Endpoint Security and obtain access
to Quarantine (see section "Quarantine" on page 91) and Backup (see section "Backup Storage" on page 94).
Open the application preferences window (on page 34).
Open the Kaspersky Endpoint Security help system.
Open the Technical Support window (see section "Contacting Technical Support Service" on page 153).
traffic-light color scheme. The color of the main window indicator shows the current protection status. Green indicates
that your computer's protection is at an optimal level, while yellow and red warn of the presence of various problems
related to Kaspersky Endpoint Security configuration or operation. For more detailed information on these problems and
how to fix them, use the Security Assistant (see section "Security Assistant" on page 43) that opens when you click on
the color indicator.
In addition to the color indicator, the left part of the main window contains a block of text which describes the protection
status, and lists any security threats logged by the Security Assistant. If a virus scan or update task is running,
information on their progress (percentage completion) will also be displayed in the left part of the main window.
The lower part of the window displays summary statistics on the operation of File Anti-Virus and information about the
databases used by the application.
You can update Kaspersky Endpoint Security, start a user-defined virus scan and switch to the license management
area from the main window. To do so, use the following buttons:
The top part of the main window contains a navigation panel with the following buttons:
APPLICATION PREFERENCES WINDOW
The Kaspersky Endpoint Security preferences window (see figure below) can be opened as follows:
by clicking the button in the main application window (see section "Main application window" on page 33);
Page 35
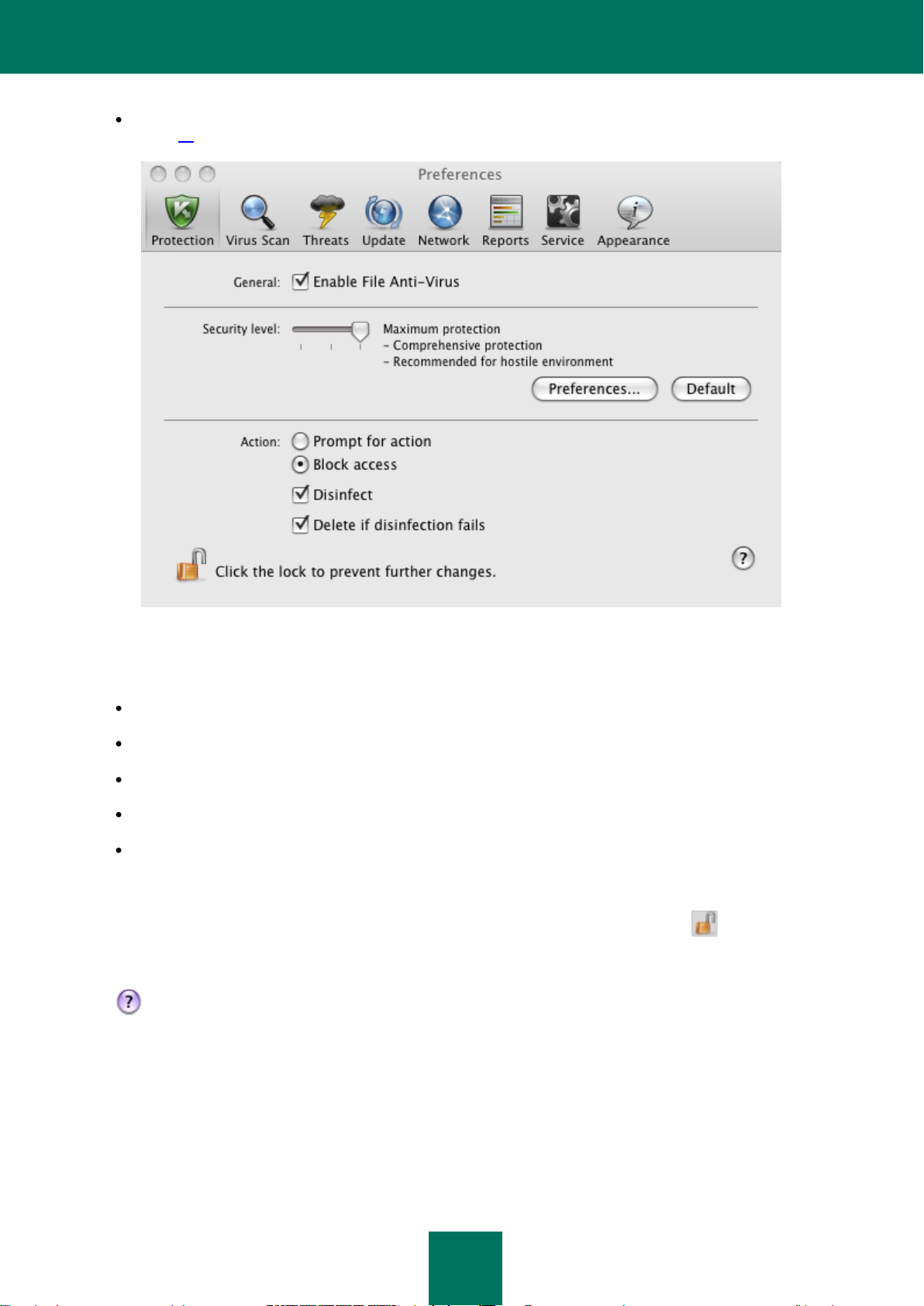
A P P L I C A T I O N I N T E R F A C E
35
by selecting Preferences in the context menu that opens on clicking the Kaspersky Endpoint Security icon (on
page 31) in the Dock or Menu Bar.
Figure 8. Application preferences window. Protection
The tabs in the top part of the window provide quick access to the following options of the application:
configuration of File Anti-Virus;
configuration of virus scan tasks;
configuration of application updates;
selection of malicious programs to control and creation of a trusted zone;
service settings of Kaspersky Endpoint Security.
To fine-tune certain settings, you will need to open the second- and third-level settings windows.
To prevent unauthorized users from modifying the Kaspersky Endpoint Security settings, click the button in the
bottom part of the window. You will need to enter the administrator's username and password to remove the restrictions
on modifying the settings.
The button provides access to the Kaspersky Endpoint Security help system with a description of the settings for the
current application window.
NOTIFICATION WINDOWS AND POP-UP MESSAGES
Different events can occur during the operation of Kaspersky Endpoint Security. They may be of an informative nature or
contain important information. For example, an event may notify the user of a successful update or of an error in File
Anti-Virus or during a virus scan that requires urgent attention. The application will inform you of new events with
notification windows and pop-up messages.
Page 36

A D M I N I S T R A T O R ' S G U I D E
36
IN THIS SECTION:
About notifications ........................................................................................................................................................... 36
Methods of receiving notifications ................................................................................................................................... 36
Configuring receipt of notifications .................................................................................................................................. 37
About pop-up messages ................................................................................................................................................. 38
ABOUT NOTIFICATIONS
When active, Kaspersky Endpoint Security notifies you of new events of the following types:
Critical notifications are events of critical importance, notifications about which should be received since they
indicate problems in the operation of Kaspersky Endpoint Security operation or vulnerabilities in the protection
of your computer: for example, application databases are out of date or license expired.
Functional Failure – events that disable Kaspersky Endpoint Security: for example, application databases
corrupted.
Important events are events that should be paid attention to since they reflect important situations in the
operation of Kaspersky Endpoint Security: for example, protection is disabled or the computer has not been
scanned for viruses for a long time.
Information notifications are reference-type messages, for example, all dangerous objects disinfected.
To keep track of events that occur during operation of Kaspersky Endpoint Security, use the notification service.
METHODS OF RECEIVING NOTIFICATIONS
Notifications can delivered using one or both of the following:
pop-up messages on screen;
audio message.
Kaspersky Endpoint Security supports Growl notifications. If Growl is enabled, it is used to display on screen messages.
Page 37

A P P L I C A T I O N I N T E R F A C E
37
CONFIGURING RECEIPT OF NOTIFICATIONS
To receive notifications about events, do the following:
1. Open the application preferences window (on page 34) and select the Appearance section (see figure below).
Figure 9. Application preferences window. Appearance
2. Check the Enable notifications box in the Events notification section and switch to advanced settings. To do
so, click the Additional button.
In the window that opens (see figure below), you may configure the following types of notifications about events listed
above:
Pop-up message on screen, which contains information about an event that has occurred.
To use this notification type, check the box in the Balloon field next to the event you want to be notified of.
Audio message.
If you want this notification to be accompanied by a sound file, check the box in the Sound field next to the
event name.
Page 38

A D M I N I S T R A T O R ' S G U I D E
38
Figure 10. Configuring receipt of notifications
ABOUT POP-UP MESSAGES
Pop-up messages are displayed on the screen by Kaspersky Endpoint Security to inform you of events that do not
require the obligatory selection of an action. Pop-up messages appear under the application icon in the Menu Bar and
automatically disappear from the screen shortly after.
CONFIGURING THE KASPERSKY ENDPOINT SECURITY
INTERFACE
You can change the appearance of Kaspersky Endpoint Security by creating and using various graphics and color
schemes. All the colors, fonts, icons and texts used in the application interface can be changed.
To enable the graphics shell, do the following:
1. Open the application preferences window (on page 34) and select the Appearance section (see figure below).
Page 39

A P P L I C A T I O N I N T E R F A C E
39
2. In the Skin section, click the Select button and in the window that opens select the folder containing the skin
files.
Figure 11. Application preferences window. Appearance
Page 40

40
STARTING AND STOPPING THE
IN THIS SECTION:
Closing Kaspersky Endpoint Security ............................................................................................................................. 40
Configuring the automatic startup of Kaspersky Endpoint Security ................................................................................. 40
Configuring the power-saving mode ................................................................................................................................ 41
APPLICATION
This section provides you with information about how to launch the application and close it.
The application launches immediately after the installation, and the Kaspersky Endpoint Security icon (on page 31)
appears in the Menu Bar.
CLOSING KASPERSKY ENDPOINT SECURITY
If you need to close Kaspersky Endpoint Security for any reason, click the Kaspersky Endpoint Security icon (on
page 31) in the Mac OS Menu Bar or in the Dock, and in the menu that opens, select the Exit command. The
application's operation will be stopped, the process will be discarded from the computer's RAM.
After Kaspersky Endpoint Security shuts down, the computer will continue to operate in unprotected mode and may be at
risk of infection.
CONFIGURING THE AUTOMATIC STARTUP OF KASPERSKY ENDPOINT SECURITY
By default, Kaspersky Endpoint Security starts up automatically when the computer is switched on or rebooted.
To disable automatic start-up, do the following:
1. Open the application settings window (on page 34) and select the Service tab (see figure below).
Page 41

S T A R T I N G A N D S T O P P I N G T H E A P P L I C A T I O N
41
2. In the Autorun section uncheck the Launch application at computer startup box.
Figure 12. Application preferences window. Service
Disabling the automatic launch mode of Kaspersky Endpoint Security results in unprotected operation mode of your
computer next time it is turned on, which may expose it to a risk of being infected.
CONFIGURING THE POWER-SAVING MODE
By default, Kaspersky Endpoint Security runs in power-saving mode. In this mode, the virus scan task for which the
schedule is set will not start if a computer is powered with a battery.
To disable the power-saving mode:
1. Open the application preferences window (on page 34), select the Service tab (see figure below).
2. In the Battery section, uncheck the Disable scheduled scans while running on battery power box.
Figure 13. Application preferences window. Service
Page 42
42
COMPUTER PROTECTION STATUS
IN THIS SECTION:
Assessing the computer's protection status .................................................................................................................... 42
Security Assistant ............................................................................................................................................................ 43
Your computer's protection state gives you a summary of your computer's overall security level. These threats include
malicious programs, outdated databases, the disabling of File Anti-Virus, the use of minimum Kaspersky Endpoint
Security protection settings, etc.
The Security Assistant lets you review all the current threats and begin to eliminate them.
ASSESSING THE COMPUTER'S PROTECTION STATUS
The computer's protection status is displayed in the main application window (see section "Main application window" on
page 33) in the form of a traffic-light color scheme. Depending on the situation, the color scheme of the window will
change. If any security threats are detected, the change of the color is supplemented by a text message.
The main application window's color, acting as a security indicator, can take the following values:
Green. Your computer's protection is at the appropriate level.
This means that the databases have been recently updated, File Anti-Virus is enabled, Kaspersky Endpoint
Security is running with the settings recommended by Kaspersky Lab, and either no malicious objects have
been discovered by a virus scan or all detected malicious objects have been disinfected.
Yellow. Your computer's protection level is reduced.
This protection status indicates certain problems with the performance or settings of Kaspersky Endpoint
Security. Such problems include, for example: slight deviations from the recommended operation settings, or
the Kaspersky Endpoint Security databases have not been updated for several days.
Red. Your computer is at risk of infection.
This state indicates that there are problems which may lead to the infection of your computer and the loss of
data. Such problems include, for example: a failure in File Anti-Virus's operation; the Kaspersky Endpoint
Security databases have not been updated for a long time; malicious objects have been detected and urgently
need to be disinfected, or the application has not been activated.
If there are problems in the protection system, you are advised to fix them immediately. To do this, click the color
indicator in the main window to launch the Security Assistant (on page 43).
Page 43
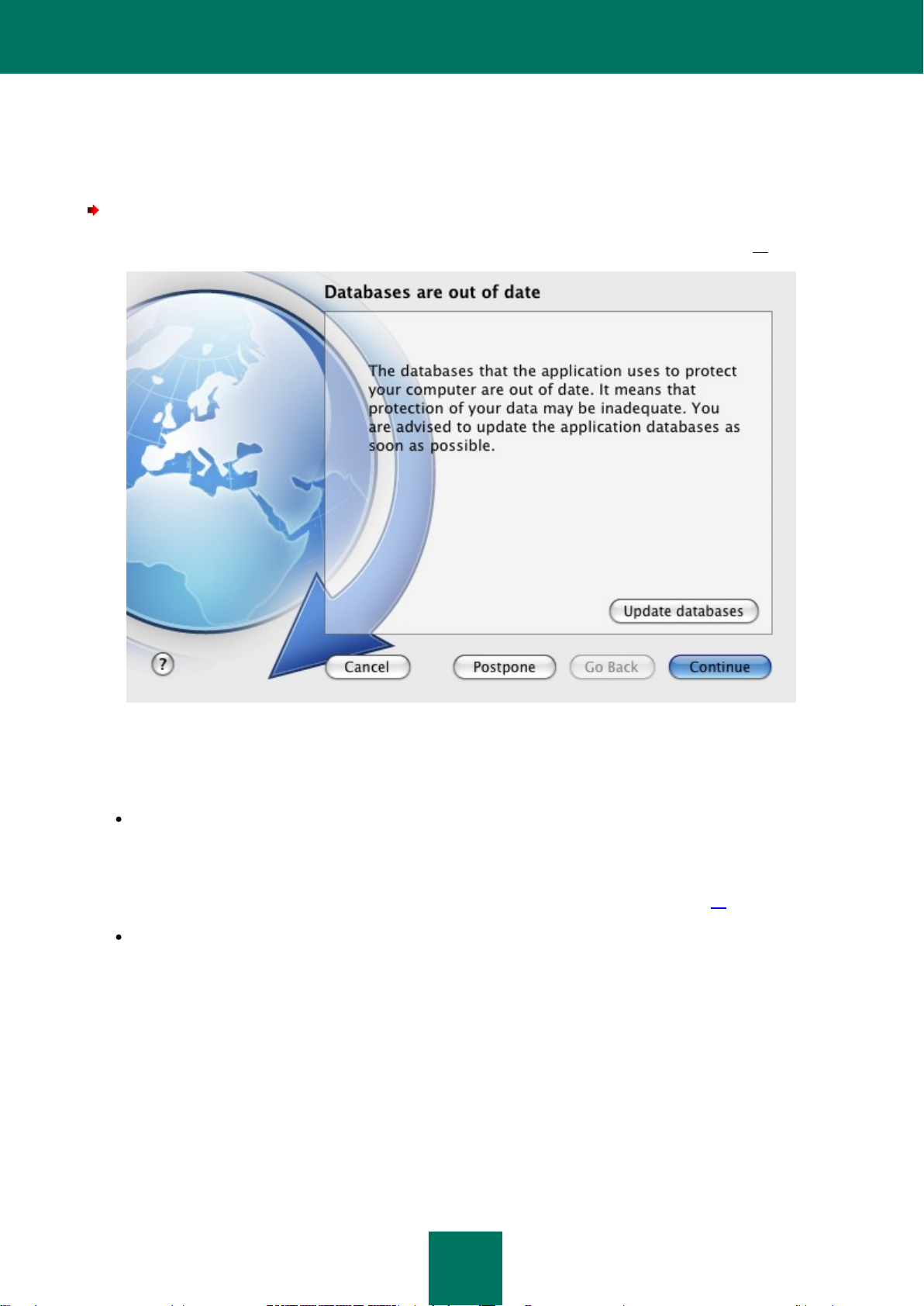
C O M P U T E R P R O T E C T I O N S T A T U S
43
SECURITY ASSISTANT
Security Assistant is a service that allows users to analyze existing threats and troubleshoot them (see figure below).
To launch the Security Assistant,
click the color indicator in the main application window (see section "Main application window" on page 33).
Figure 14. Security Assistant interface
To browse the list of existing threats, click the Continue or Back buttons. A detailed description is provided for each
threat, and the following actions are available:
Eliminate threat immediately.
To eliminate a threat, click the button with the recommended action. For example, if infected objects have been
detected on the computer, the recommended action will be Disinfect infected objects. If the anti-virus
database used by the application are out of date, the recommended action is Update databases. Detailed
information about threats can be found in the report window (see section "Reports" on page 96).
Postpone threat elimination.
If you do not want to eliminate the threat immediately for some reason, you can postpone the action and return
to it later. To do so, use the Postpone button. Note that this feature does not cover such dangerous threats as
persistence of malicious objects that have not been processed, failures in File Anti-Virus operation, or corruption
of Kaspersky Endpoint Security databases.
If you close the Security Assistant without eliminating all serious threats, the color indicator in the main application
window will signalize that there is a problem. If you postpone the elimination of some threats, they will not be present in
the list of active threats when Security Assistant is opened for the next time. However, you can still return to view and
eliminate postponed threats by clicking the View postponed threats button in the last window of the Security Assistant.
Page 44

44
SOLVING TYPICAL TASKS
IN THIS SECTION:
How to perform a full scan of your computer for viruses ................................................................................................. 44
How to perform a quick scan of your computer ............................................................................................................... 45
How to scan a file, folder or disk for viruses .................................................................................................................... 45
How to configure a scheduled scan of your computer ..................................................................................................... 45
How to purchase or renew license .................................................................................................................................. 46
How to update application databases and modules ........................................................................................................ 46
How to export the application preferences to Kaspersky Endpoint Security installed on another computer ................... 47
What to do if file access is blocked ................................................................................................................................. 47
What to do if you suspect an object of being infected with a virus .................................................................................. 48
How to restore an object that has been deleted or disinfected by the application ........................................................... 49
How to view the report on the application's operation ..................................................................................................... 49
What to do when the application's notifications appear ................................................................................................... 49
This section describes the tasks encountered by the most users when working with the application as well as the
procedures developed for carrying out these tasks.
HOW TO PERFORM A FULL SCAN OF YOUR COMPUTER FOR
VIRUSES
The full scan task created by default is included in Kaspersky Endpoint Security. While running this task, the application
scans all hard drives for viruses.
To launch a full computer scan, do the following:
1. Open the main application window (on page 33) and click the button.
2. In the menu that opens, select the Full Scan task.
You can view the scan results in the report window (see section "Virus scan statistics" on page 79).
Page 45

S O L V I N G T Y P I C A L T A S K S
45
HOW TO PERFORM A QUICK SCAN OF YOUR COMPUTER
The quick scan task created by default is included in Kaspersky Endpoint Security. While running this task, the
application performs virus scan of critical areas of your computer, such as folders containing operating system files and
system libraries, which may, when infected with malware, cause corruption of your operating system.
To launch a full computer scan, do the following:
1. Open the main application window (on page 33) and click the button.
2. In the menu that opens, select Quick scan.
You can view the scan results in the report window (see section "Virus scan statistics" on page 79).
HOW TO SCAN A FILE, FOLDER OR DISK FOR VIRUSES
If you want to scan an individual object (such as a hard drive, folder, file, or removable device) for viruses, use the
integrated Virus Scan task.
To scan an individual object for viruses, do the following:
1. Open the main application window (on page 33) and click the button.
2. In the menu that opens, select the Virus Scan task. A window opens to select objects to be scanned.
3. Create a list of objects to be scanned (see section "Creating a list of objects to scan" on page 70) and click the
Start button to run the virus scan.
You can view the scan results in the report window (see section "Virus scan statistics" on page 79).
You can launch a virus scan of any object on your computer from the Finder application if the Finder Contextual Menu
application component has been installed (see section "Kaspersky Endpoint Security custom installation" on
page 22). To do this, open the context menu of the object and select Scan for viruses1.
HOW TO CONFIGURE A SCHEDULED SCAN OF YOUR
COMPUTER
Timely virus scans ensure your computer is kept secure. You can create a scheduled virus scan using the tasks: Quick
scan and Full scan. In accordance with set mode, the application will automatically perform a scan of the whole
computer or the most critical areas of its file system.
To configure a scheduled Quick Scan or Full Scan task:
1. Open the application preferences window (on page 34) and select the Virus Scan tab.
2. In the list to the left, select a task name and enable scheduled run of the task in the Run mode section. To edit
the startup schedule, click the Edit button.
3. In the window that opens, set the frequency with which the scan task will run.
1
In Mac OS X operating systems (version 10.6 or earlier), the startup procedure may differ.
Page 46
A D M I N I S T R A T O R ' S G U I D E
46
You can view the task completion results in the report window (see section "Virus scan statistics" on page 79).
HOW TO PURCHASE OR RENEW LICENSE
If you have installed Kaspersky Endpoint Security without a license, you can purchase one after installation. When your
current license expires, you can renew it. When purchasing or renewing a license, you receive an activation code that
you should use to activate the application (see section "Kaspersky Endpoint Security activation" on page 28).
To purchase a license:
1. Open the main application window (on page 33) and click the button.
2. In the window that opens, click the Purchase button.
The eStore web page opens where you can purchase a license.
To renew a license:
1. Open the main application window (on page 33) and click the button.
2. In the window that opens, click the Renew button.
HOW TO UPDATE APPLICATION DATABASES AND
MODULES
Kaspersky Lab updates anti-virus databases and modules of Kaspersky Endpoint Security using dedicated update
servers and Kaspersky Administration Kit Administration Server. Kaspersky Lab's update servers are Kaspersky Lab's
Internet sites to which the Kaspersky Endpoint Security updates are uploaded on regular bases.
An Internet connection is required to download updates from the servers.
By default, Kaspersky Endpoint Security periodically checks for updates on Kaspersky Lab's servers. If Kaspersky
Endpoint Security detects new updates, it downloads them in the background and installs on the computer.
To launch Kaspersky Endpoint Security update manually,
open the main application window (on page 33) and click the button.
You can view the scan results in the report window (see section "Virus scan statistics" on page 89).
The eStore web page opens where you can renew a license.
Page 47

S O L V I N G T Y P I C A L T A S K S
47
HOW TO EXPORT THE APPLICATION PREFERENCES TO
KASPERSKY ENDPOINT SECURITY INSTALLED ON
ANOTHER COMPUTER
Kaspersky Endpoint Security allows to export and import its settings. This is useful if, for example, when the application
is installed both on your home and office computers. You can configure the application in a convenient mode at home,
save those settings in a special configuration file on a disk, and then import them quickly onto your office workstation.
The settings are stored in a special configuration file.
To save the current Kaspersky Endpoint Security settings in a file, do the following:
1. Open application settings window (on page 34) and select the Service tab.
2. In the Configuration section, click the Save button. The Save window opens.
3. In the Save as field enter the file name and select the folder in which it will be saved.
To import settings from a Kaspersky Endpoint Security configuration file, do the following:
1. Open the application preferences window (on page 34) and select the Service tab.
2. In the Configuration section, click the Load button and in the window that opens select the file containing the
Kaspersky Endpoint Security settings.
WHAT TO DO IF FILE ACCESS IS BLOCKED
Kaspersky Endpoint Security blocks access to a file or program if File Anti-Virus (on page 54) suspects the object of
being infected or potentially infected by a malicious program, and the Block access option has been selected.
To process the dangerous objects listed on the Detected tab of the report window:
1. Open the main application window (on page 33) and click the button. The Kaspersky Endpoint Security
report window opens.
2. In the left part of the report window, select Detected. The right part of the window displays a list of dangerous
objects that have been detected with their status.
3. Press the Disinfect all button. After each object is processed, a notification will appear on screen to prompt for
further action. If you check the Apply to all box in the notification window, the selected action will be applied to
all objects with the same status.
To process potentially infected objects in Quarantine:
1. Open the main application window (on page 33) and click the button. The Kaspersky Endpoint Security
report window opens.
2. In the left part of the report window, select Quarantine. The contents of Quarantine are displayed in the righthand part of the window.
3. Click the Scan all button to scan and cure all potentially infected objects in Quarantine using the current
Kaspersky Endpoint Security databases.
The status of an object in Quarantine is changed only after it is scanned using anti-virus databases released no
earlier than three days after the file was placed in Quarantine.
Page 48
A D M I N I S T R A T O R ' S G U I D E
48
4. Click the Restore button to restore the files to the folder specified by the user or the folder from which they were
moved to Quarantine (by default).
We recommend that you only restore objects with the false positive, OK, and disinfected statuses since
restoring other objects can lead to your computer becoming infected.
5. Click the Delete or Clear all button to delete the selected object from Quarantine or clear Quarantine
completely.
If you are confident that the objects being blocked by File Anti-Virus are safe, include them in a trusted zone by creating
an exclusion rule (see section "Creating a trusted zone" on page 52).
WHAT TO DO IF YOU SUSPECT AN OBJECT OF BEING
INFECTED WITH A VIRUS
If you suspect an object of being infected, first scan it for viruses (see section "How to scan a file, folder or disk for
viruses" on page 45).
If the virus scan performed by Kaspersky Endpoint Security reveals that the object is not infected, though you suspect
the opposite, move the object to Quarantine. Objects once moved in Quarantine are stored as archives, thus causing no
risk to your computer. After the databases are updated, Kaspersky Endpoint Security will probably be able to clearly
identify and eliminate the threat.
To move an object to Quarantine:
1. Open the main application window (on page 33) and click the button. The Kaspersky Endpoint Security
report window opens.
2. In the left part of the report window, select Quarantine. The contents of Quarantine are displayed in the righthand part of the window.
3. Click the Add button and in the window that opens select the required file. It is added to the list with the added
by user status.
Kaspersky Endpoint Security can change the status of a file moved to Quarantine manually after it is scanned with
updated databases only if at least three days have passed since it had been scanned in Quarantine for the first time. If a
file is assigned the false operation status, it will be automatically restored. If a file is identified as infected, it is deleted
from Quarantine and a copy is stored in Backup Storage.
Page 49

S O L V I N G T Y P I C A L T A S K S
49
HOW TO RESTORE AN OBJECT THAT HAS BEEN DELETED
OR DISINFECTED BY THE APPLICATION
We recommend that you avoid restoring deleted and disinfected objects unless it is extremely necessary, because they
may threaten your computer.
Sometimes it is not possible to save objects in their entirety during the disinfection process. If a disinfected file contained
important information that is partly or completely inaccessible following disinfection, you can attempt to restore the
original object from its backup copy.
To restore an object that has been deleted or modified by the application:
1. Open the main application window (on page 33) and click the button. The Kaspersky Endpoint Security
report window opens.
2. In the left part of the report window, select the Backup Storage section. The right part of the window displays
the contents of Backup in the form of a list of copies of objects.
3. Select the copy of the object you require in the list and click the Restore button. Confirm the action. The object
is restored to its original location with its original name. If there is an object with the same name in the original
location (this situation is possible when restoring an object with a copy created prior to disinfection), a warning
will pop up on screen. You can change the location of the object being restored or rename it.
We recommend that you scan the object for viruses immediately after restoring it. It is possible that the object
will be disinfected using the updated databases without losing its integrity.
HOW TO VIEW THE REPORT ON THE APPLICATION'S
OPERATION
Information about events that occur during the operation of File Anti-Virus (see section "File Anti-Virus" on page 54),
during a virus scan (see section "Scanning for viruses" on page 65) or during an update (see section "Updating the
application" on page 81) is displayed in the reports window (see section "Reports" on page 96).
To open the report window,
open the main application window (on page 33) and click the button.
WHAT TO DO WHEN THE APPLICATION'S NOTIFICATIONS
APPEAR
Application notifications (see section "Notification windows and pop-up messages" on page 35) in the form of pop-up onscreen messages inform you of events that occur during the application's operation, that require your attention.
If such notification is displayed on the screen, you should select one of the suggested options. Optimum option is the one
recommended by Kaspersky Lab experts by default.
Page 50

50
ADVANCED APPLICATION SETTINGS
IN THIS SECTION:
Creating a protection scope ............................................................................................................................................ 50
File Anti-Virus .................................................................................................................................................................. 54
Virus Scan ....................................................................................................................................................................... 65
Updating the application .................................................................................................................................................. 81
Reports and Storages ..................................................................................................................................................... 90
IN THIS SECTION:
Selecting malicious programs to be monitored ................................................................................................................ 50
Creating a trusted zone ................................................................................................................................................... 52
This section provides detailed information about each application component and describes the operation and
configuration algorithms for each component.
CREATING A PROTECTION SCOPE
The scope of protection for your computer is defined by the following settings:
the list of malware programs which the application protects against;
list of objects in the trusted zone which are excluded from the protection scope.
SELECTING MALICIOUS PROGRAMS TO BE MONITORED
Kaspersky Endpoint Security protects against various types of malware. Regardless of your settings, the application
protects your computer against the most dangerous types of malware such as viruses, Trojans, and hacking tools. These
programs may cause significant damage to your computer. To achieve a greater level of security for your computer, you
can expand the list of threats that the application will detect, turning on monitoring of various potentially dangerous
programs.
Malware and potentially dangerous programs against which Kaspersky Endpoint Security protects you are grouped as
follows:
Viruses, worms, Trojans, hack tools. This group contains the most common and dangerous categories of
malware. This is the minimum admissible security level. In accordance with the recommendations of Kaspersky
Lab experts, Kaspersky Endpoint Security always monitors this group of malware.
Spyware and Adware. This group includes potentially dangerous software that may cause inconvenience to
the user or even cause damage.
Auto-dialers. This group includes programs, which set up hidden dial-up connections, such as adult services
auto-dialers.
Page 51

A D V A N C E D A P P L I C A T I O N S E T T I N G S
51
Other programs. This group includes programs that are not malicious or dangerous, but which under certain
circumstances could be used to cause harm to your computer.
To select the groups of malware that Kaspersky Endpoint Security will protect your computer against:
1. Open the application preferences window (on page 34) and select the Threats tab (see figure below).
2. In the Malware categories section, check the boxes next to the names of the malware groups against which
Kaspersky Endpoint Security should protect your computer.
Kaspersky Endpoint Security always protects your computer against viruses, worms, Trojans, and hack tools.
Therefore, it is not possible to uncheck the box for this group.
Depending on the selected groups, Kaspersky Endpoint Security will fully or partially use the anti-virus databases while
File Anti-Virus is running (see section "File Anti-Virus" on page 54) and during virus scans (see section "Scanning for
viruses" on page 65).
If all groups of malware are selected, Kaspersky Endpoint Security provides the maximum level of anti-virus protection
for your computer. If only protection against viruses, worms, Trojans and hacking tools is selected, Kaspersky Endpoint
Security does not control potentially dangerous programs and other malware that may be installed on your computer and
could cause moral or material damage.
Figure 15. Application preferences window. Threats
Kaspersky Lab does not recommend disabling monitoring of spyware, adware and auto-dialers. If Kaspersky Endpoint
Security classifies a program, which you do not consider to be dangerous, as unwanted, you can configure an exclusion
rule for it (see section "Creating a trusted zone" on page 52).
Page 52

A D M I N I S T R A T O R ' S G U I D E
52
CREATING A TRUSTED ZONE
Trusted zone is a user-created list of objects that Kaspersky Endpoint Security does not monitor.
The user creates a trusted zone with regard to the objects he/she works with and the programs installed on the
computer. You might need to create such an exclusion list if, for example, Kaspersky Endpoint Security blocks access to
an object or program which you know is safe.
Exclusion rules are sets of conditions under which Kaspersky Endpoint Security does not scan objects. It is possible to
exclude from a scan files of a certain format (see section "List of objects scanned by their extension" on page 155), files
by their mask (see "Permissible file exclusion masks" on page 157), a particular area (for example, a folder or program),
application processes or objects by the type of threat in accordance with the Virus Encyclopedia
(http://www.securelist.com).
An exclusion object will not be scanned when the disk or folder where it is located is being scanned. However, if you
select that object specifically, the exclusion rule will not be applied to it.
Threat type is the status that Kaspersky Endpoint Security assigns to an object during the scan. The status is assigned
based on the classification of malware and riskware listed in the Kaspersky Lab Virus Encyclopedia.
Riskware does not have any malicious features but can be used as an auxiliary component by malicious software, since
such programs can contain holes and errors. This category includes, for example, remote administration programs, IRC
clients, FTP servers, various utilities for stopping processes or hiding them, keyloggers, password macros, and autodialers. Such programs are classified in not-a-virus group. They can be divided into several types such as Adware, Joke,
and Riskware. (for detailed information about unwanted programs detected by Kaspersky Endpoint Security, see the
Virus Encyclopedia (http://www.securelist.com)). Such programs may be blocked after the scan. Since several of them
are popular with users, you have the option of excluding them from the scan.
To create a new exclusion rule or view and modify an existing one, do the following:
1. Open the application preferences window (on page 34) and select the Threats tab (see figure below).
Figure 16. Application preferences window. Threats
Page 53

A D V A N C E D A P P L I C A T I O N S E T T I N G S
53
2. Under Exclusions, click the Trusted zone button (see figure above). A window (see figure below) opens,
displaying a list of objects that Kaspersky Endpoint Security will not control when running.
Figure 17. The list of exclusion objects
You can perform the following actions:
Create new exclusion rule.
Click the button and in the Exclusion rule window that opens (see figure below) set the conditions.
Modify existing exclusion rule.
Select the exclusion rule in the list and click the Edit button. In the Exclusion rule window that opens
(see figure below), modify the conditions.
Temporarily disable exclusion rule.
Select the exclusion rule in the list and uncheck the box next to it. The exclusion rule will be disabled until
the box is checked again.
Delete exclusion rule.
Select the exclusion rule in the list and click the Modify button .
Creating an exclusion rule
In the Exclusion rule window that opens, specify the conditions for the exclusion rule in accordance with the following
settings:
Object / All objects. Specify a file, folder or file mask (see section "Permissible file exclusion masks" on
page 157) as an exclusion object. You can enter the name / name mask of the object in the field manually or by
clicking the Select button and selecting the object in the window that opens.
If the All objects option is selected, all objects on your computer which are of the threat type specified in the
field below will be excluded from scan.
Page 54
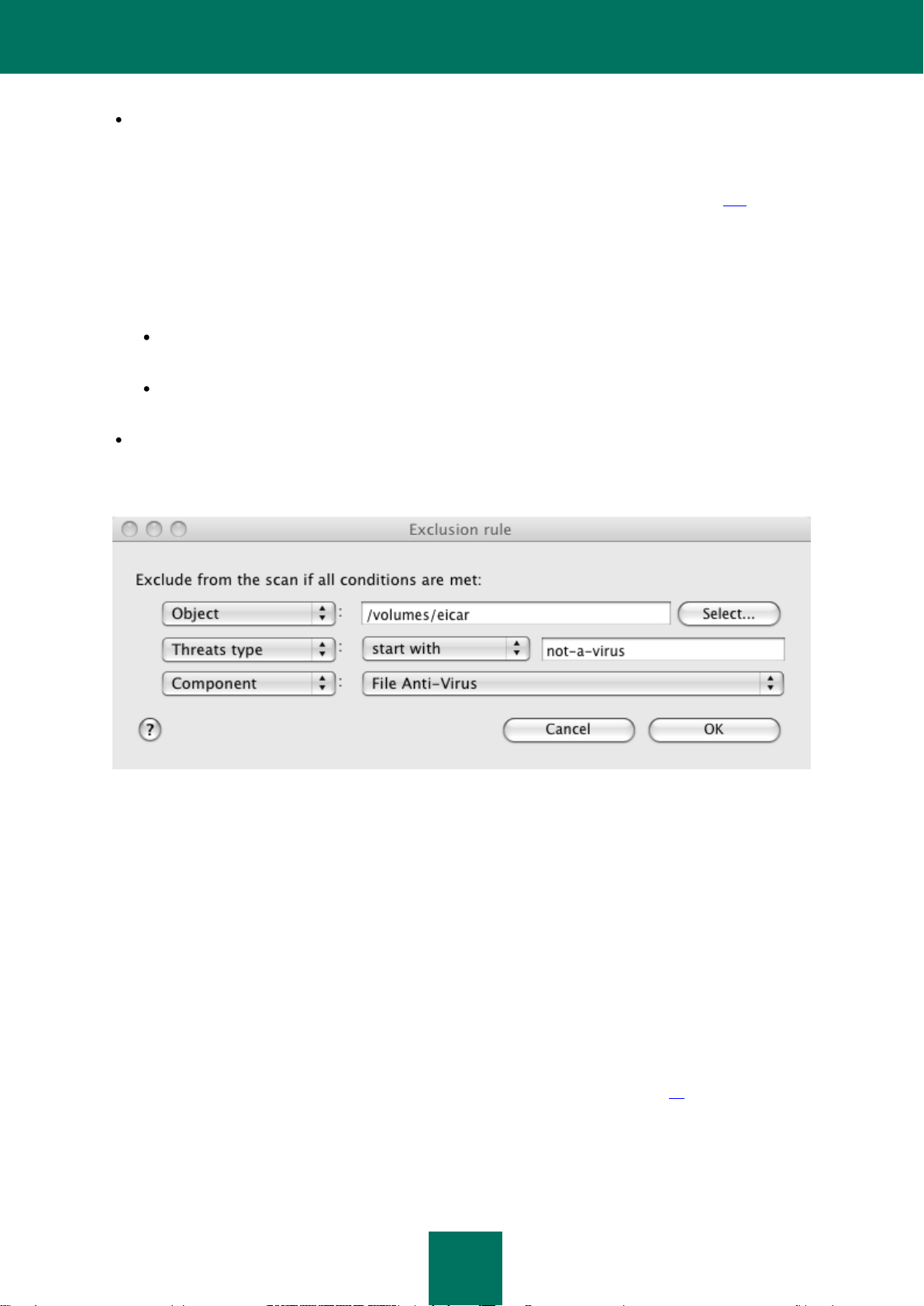
A D M I N I S T R A T O R ' S G U I D E
54
Threats type / All threats. The setting allows to exclude objects from scan based on the threat type assigned
according to the Virus Encyclopedia classification. To enter the name of the threat, use the values in the
dropdown list: start with, end with, contain, whole word, and specify the corresponding fragment of the name
in the field to the right of the list. For example, if the start with not-a-virus value is selected, then legal but
potentially dangerous programs will be excluded from scan. Specifying the name of the threat by mask (see
section "Allowed exclusion masks according to the Virus Encyclopedia classification" on page 158) is also
admissible.
If the All threats value is selected, then all objects specified in the Object field above will be excluded from
scan, regardless of the threat type assigned to them.
If both the exclusion object and the threat type are selected, the rule will apply as follows:
If you specify a certain file as the object and a certain status as the threat type, the specified file will only be
excluded if during the scan it is assigned the selected threat status.
If you select an area or folder as the object and a status (or a mask) as the threat type, objects with that
status will be excluded from the scan only in that area or folder.
Component / All components. Select the Kaspersky Endpoint Security components that should apply the rule
being created: File Anti-Virus or Virus Scan.
If the All components option is selected, then all virus scan tasks and File Anti-Virus will use this rule.
Figure 18. Creating an exclusion rule
FILE ANTI-VIRUS
The computer's file system may contain viruses and other malicious programs that have persisted for years, having
initially penetrated the computer from a removable disk drive or from the Internet and never causing any trouble.
File Anti-Virus is the component that monitors the computer's file system in real-time mode. By default, it is launched during startup of the operating system, persists continuously in RAM, and scans all files that are opened, started or saved on your computer and all associated disk drives.
File Anti-Virus works with files in the following manner:
1. The component intercepts every attempt by the user or by any program to access any file.
2. File Anti-Virus scans the iSwift (see section "Configuring additional settings" on page 61) database for
information about the file. A decision is made whether to scan the file based on the information retrieved.
3. The file is analyzed for viruses. Malicious objects are detected using the Kaspersky Endpoint Security
databases. These databases contain descriptions of all the currently known malicious programs along with
instructions to neutralize them.
Page 55

A D V A N C E D A P P L I C A T I O N S E T T I N G S
55
IN THIS SECTION:
Disabling file protection ................................................................................................................................................... 55
Restoring protection on your computer ........................................................................................................................... 57
Configuring File Anti-Virus ............................................................................................................................................... 58
Restoring default file protection settings.......................................................................................................................... 63
File protection statistics ................................................................................................................................................... 64
Depending on the results of the analysis, the following options of Kaspersky Endpoint Security are available:
If no malicious code is detected in the file, it will immediately become accessible.
If malicious code is detected in a file, File Anti-Virus blocks the file and attempts to disinfect it. After successful
disinfection, the file will become accessible. If disinfection fails, the file will be deleted. A copy of the file will be
moved to Backup Storage (on page 94).
If a malicious code is detected in the file, it is moved to a special storage area known as Quarantine (on
page 91). An attempt can be made later to cure it using the updated anti-virus databases.
By default, Kaspersky Endpoint Security is launched when the operating system starts, and protects your computer
during the entire session. The Kaspersky Endpoint Security icon shows that File Anti-Virus is running (on page 31). If the
icon is active, your computer's protection is enabled; if the icon is inactive, protection is disabled.
DISABLING FILE PROTECTION
Kaspersky Lab strongly recommends that you do not disable Anti-Virus real-time protection since this could lead to your
computer becoming infected and loss of data.
Note that the icon indicates the protection status provided by File Anti-Virus (see section "Anti-virus protection of
computer's file system" on page 54). Disabling or pausing File Anti-Virus does not impact the execution of virus scan
tasks (see section "Scanning for viruses" on page 65) or application updates (see section "Updating the application" on
page 81).
There are several ways to disable File Anti-Virus. However, before doing so you should know why you want to disable
the component.
There is likely to be a different solution to the problem: change the security level (see section "Setting the security level"
on page 58) or disable protection only for certain files by creating an exclusion rule (see section "Creating a trusted zone"
on page 52). For example, if you are working with a database that you believe is free from viruses, just specify the folder
containing its files as an exclusion. You may need to stop File Anti-Virus temporarily if Kaspersky Endpoint Security
conflicts with other programs installed on your computer.
Page 56
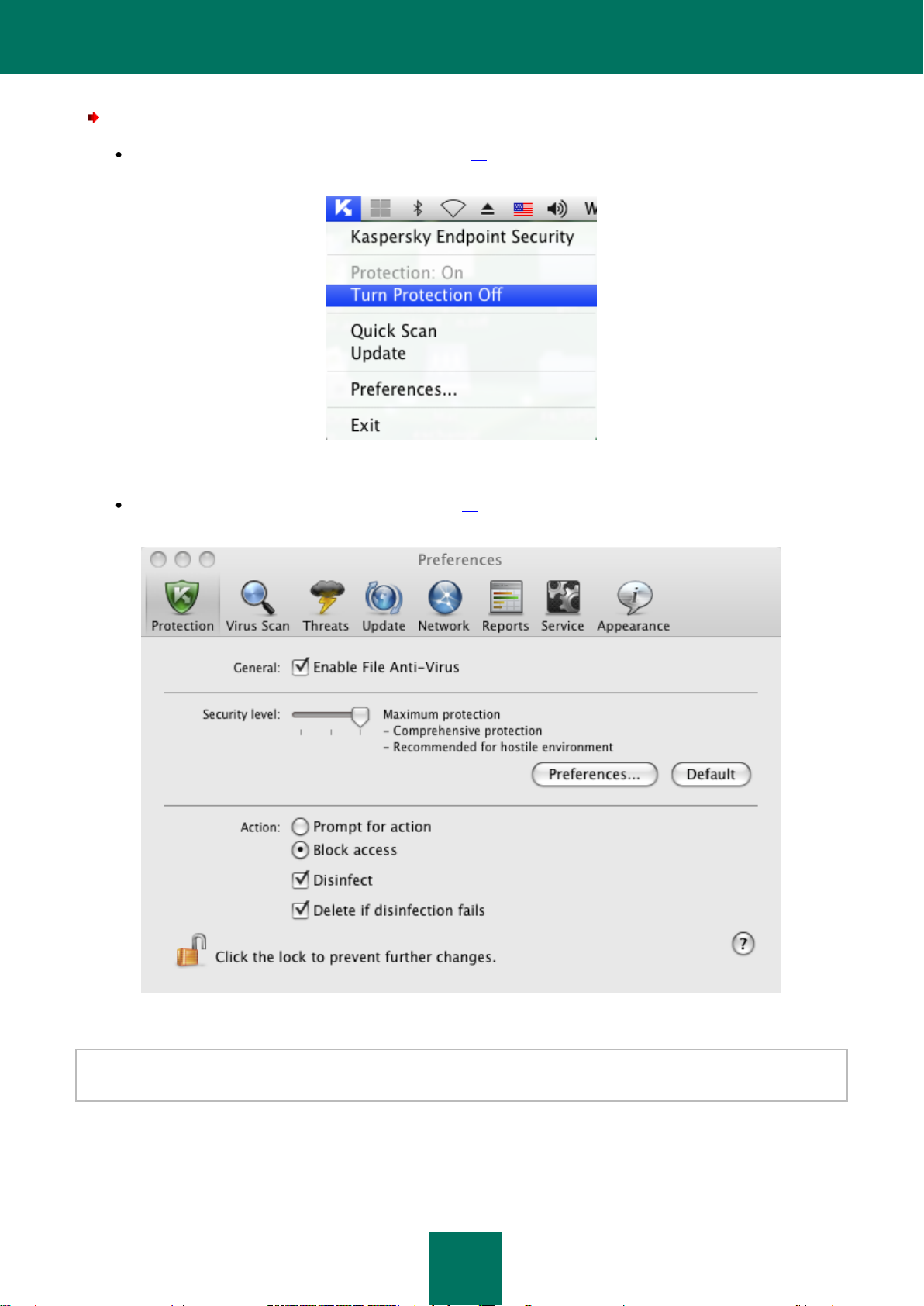
A D M I N I S T R A T O R ' S G U I D E
56
The following methods can be used to disable File Anti-Virus:
Click the Kaspersky Endpoint Security icon (on page 31) and select Turn Protection Off from the context menu
(see figure below).
Figure 19. Disabling File Anti-Virus
Open the application preferences window (on page 34), select the Protection tab and uncheck the Enable File
Anti-Virus box (see figure below).
If you have disabled File Anti-Virus, it will not be turned on automatically when Kaspersky Endpoint Security restarts. You
will need to enable file system protection manually (see section "Enabling file system protection" on page 57).
Figure 20. Application preferences window. Protection
Page 57

A D V A N C E D A P P L I C A T I O N S E T T I N G S
57
RESTORING PROTECTION ON YOUR COMPUTER
If File Anti-Virus is disabled, it can be enabled only manually at the user's request. In this case, File Anti-Virus will not be
automatically enabled after the system or Kaspersky Endpoint Security restarts.
The following methods can be used to enable File Anti-Virus:
Click the Kaspersky Endpoint Security icon (on page 31) and select Turn Protection On from the context menu
(see figure below).
Figure 21. Enabling File Anti-Virus
Open the application preferences window (on page 34), select the Protection tab and check the Enable File
Anti-Virus box (see the figure below).
Figure 22. Application preferences window. Protection
Page 58

A D M I N I S T R A T O R ' S G U I D E
58
Use the Security Assistant (see section "Security Assistant" on page 43). You significantly increase the risk of
infecting your computer if you pause or stop protection, therefore this threat is immediately logged by the
Security Assistant.
CONFIGURING FILE ANTI-VIRUS
File Anti-Virus is controlled using the following settings:
Security level.
The security level is a set of parameters that define the balance between the thoroughness and speed of
scanning objects. There are three predefined security levels (see section "Selecting the security level" on
page 58) with settings developed by Kaspersky Lab.
Action on detected object.
This action (see section "Selecting actions on objects" on page 63) defines how Kaspersky Endpoint Security
SELECTING THE SECURITY LEVEL
File Anti-Virus provides protection for your computer's file system at one of the following levels:
will react when an infected or potentially infected object is detected.
Maximum protection provides the most complete scan of the files you open, save, or start.
Recommended contains the settings recommended by Kaspersky Lab.
Maximum Speed - this level enables you to comfortably use other applications that require significant system
resources, since the range of files scanned is smaller.
By default, File Anti-Virus uses the Recommended security level. You can increase or decrease the level of file system
protection by selecting Maximum protection or Maximum speed accordingly, or by modifying the current settings.
To change the defined security level, do the following:
1. Open the application settings window (on page 34) and select the Protection tab (see figure below).
2. In the Security level section, move the slider bar to the required position. Modifying the security level changes
the balance between the scan speed and the total number of files scanned: the fewer files scanned for viruses,
the higher the scan speed.
If none of the preset security levels meets your needs, you can customize the scan settings. You are advised to select
the level closest to your requirements as a basis and then modify its settings. This will change the name of the security
level to User.
To modify the settings for the current security level, do the following:
1. Open the application preferences window (on page 34) and select the Protection tab (see figure below).
2. In the Security level section, click the Preferences button.
3. In the window that opens edit the file protection settings:
on the General tab (see section "Specifying the types of files to scan" on page 59), specify the types of files
to be scanned.
on the Protection scope tab (see section "Creating a protection scope" on page 60), specify the drives or
folders that are to be checked by File Anti-Virus.
Page 59

A D V A N C E D A P P L I C A T I O N S E T T I N G S
59
on the Additional tab (see section "Configuring additional settings" on page 61), set the run mode of the
component.
4. Click OK to save changes.
Figure 23. Application preferences window. Protection
SPECIFYING THE TYPES OF FILES TO SCAN
By specifying the types of files to scan, you define which files by format and size File Anti-Virus will scan for viruses when
they are opened, used and saved. You can also set the scan performance.
To specify the type of objects to be scanned by File Anti-Virus and set the scan performance:
1. Open the application preferences window (on page 34) and select the Protection tab.
2. In the Security level section, click the Preferences button.
3. In the window that opens select the General tab (see figure below) and configure the following settings:
In the File types section, specify which formats of objects should be scanned for viruses by Kaspersky
Endpoint Security when they are opened, run, or saved.
In the Optimization section, set the scan performance.
Page 60
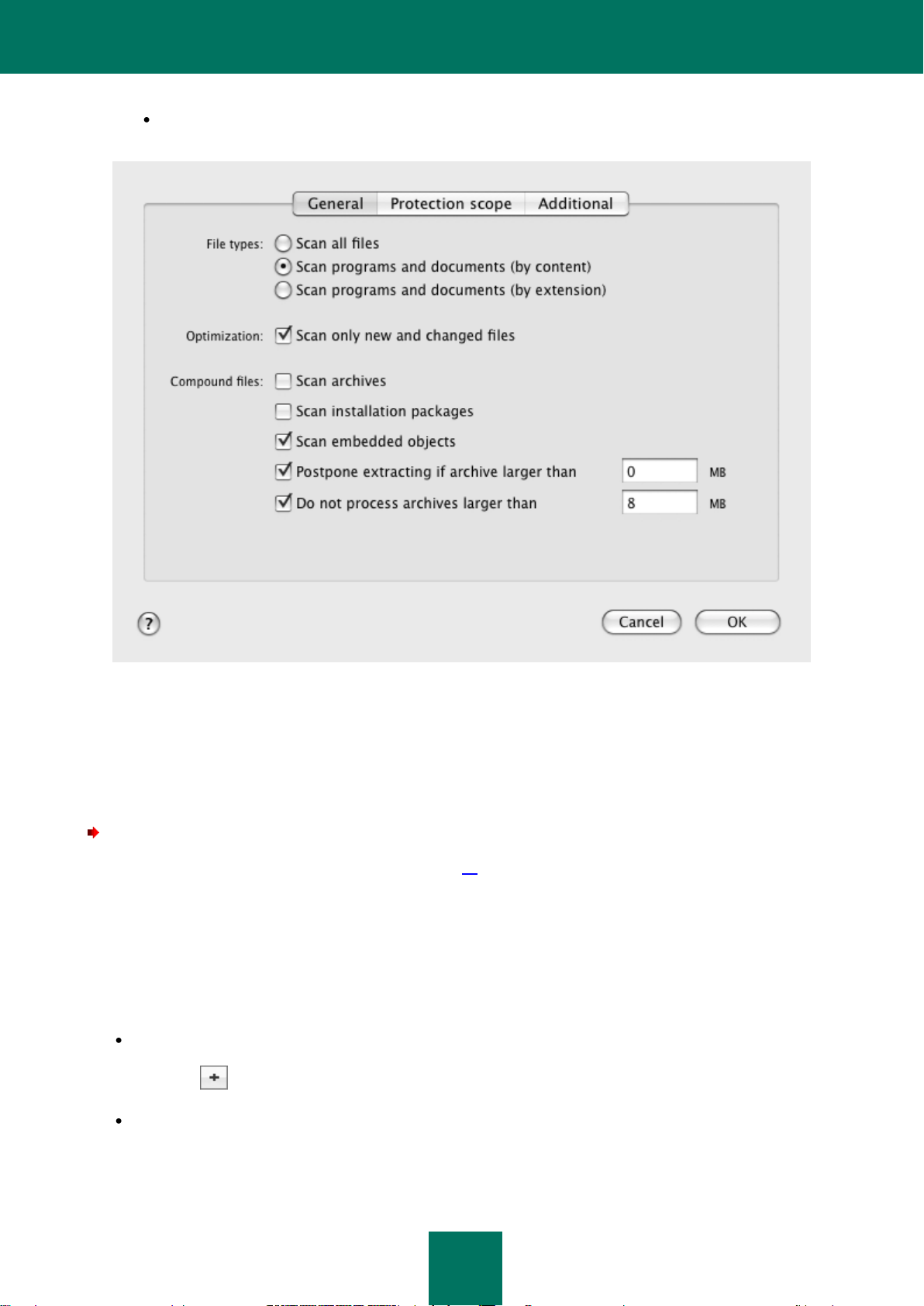
A D M I N I S T R A T O R ' S G U I D E
60
In the Compound files section, select which compound files should be scanned for viruses, and set a
restriction on the scan of large-sized objects.
Figure 24. File Anti-Virus. Configuring scan settings
CREATING A PROTECTION SCOPE
By default, File Anti-Virus scans all files at the moment they are accessed, regardless of the media they are stored on,
whether it is a hard disk drive, a CD / DVD-ROM, or a flash card.
To create a list of objects covered by the protection scope, do the following:
1. Open the application preferences window (on page 34) and select the Protection tab.
2. In the Security level section, click the Preferences button.
3. Select the Protection scope tab in the window that opens. (see figure below). The tab displays a list of objects
that will be scanned by File Anti-Virus. By default, all objects located on the hard, removable and network disk
drives connected to your computer are protected.
You can perform the following actions:
Add object to be scanned.
Click the button and in the window that opens select a folder or file.
Edit an object on the list (only available for user-added objects).
Select the object and click the Edit button. Make the required changes in the window that opens.
Page 61

A D V A N C E D A P P L I C A T I O N S E T T I N G S
61
Temporarily disable scanning of object.
Select the object and uncheck the box next to it. File Anti-Virus will not control this object until the box is
checked again.
Delete an object (only available for user-added objects).
Select the object and click the button.
Figure 25. File Anti-Virus. Creating a protection scope
To limit the number of protected objects, you can:
specify only the folders, disk drives, or files you want to protect;
create a list of objects that do not need protection (see section "Creating a trusted zone" on page 52);
combine the first and second methods, i.e. create a protection scope and exclude a number of objects from it.
CONFIGURING ADDITIONAL SETTINGS
You can configure the following additional settings for File Anti-Virus: scan mode for file system objects, iSwift to improve
performance, and the component's schedule.
To configure additional settings of File Anti-Virus, do the following:
1. Open the application preferences window (on page 34) and select the Protection tab.
2. In the Security level section, click the Preferences button.
Page 62
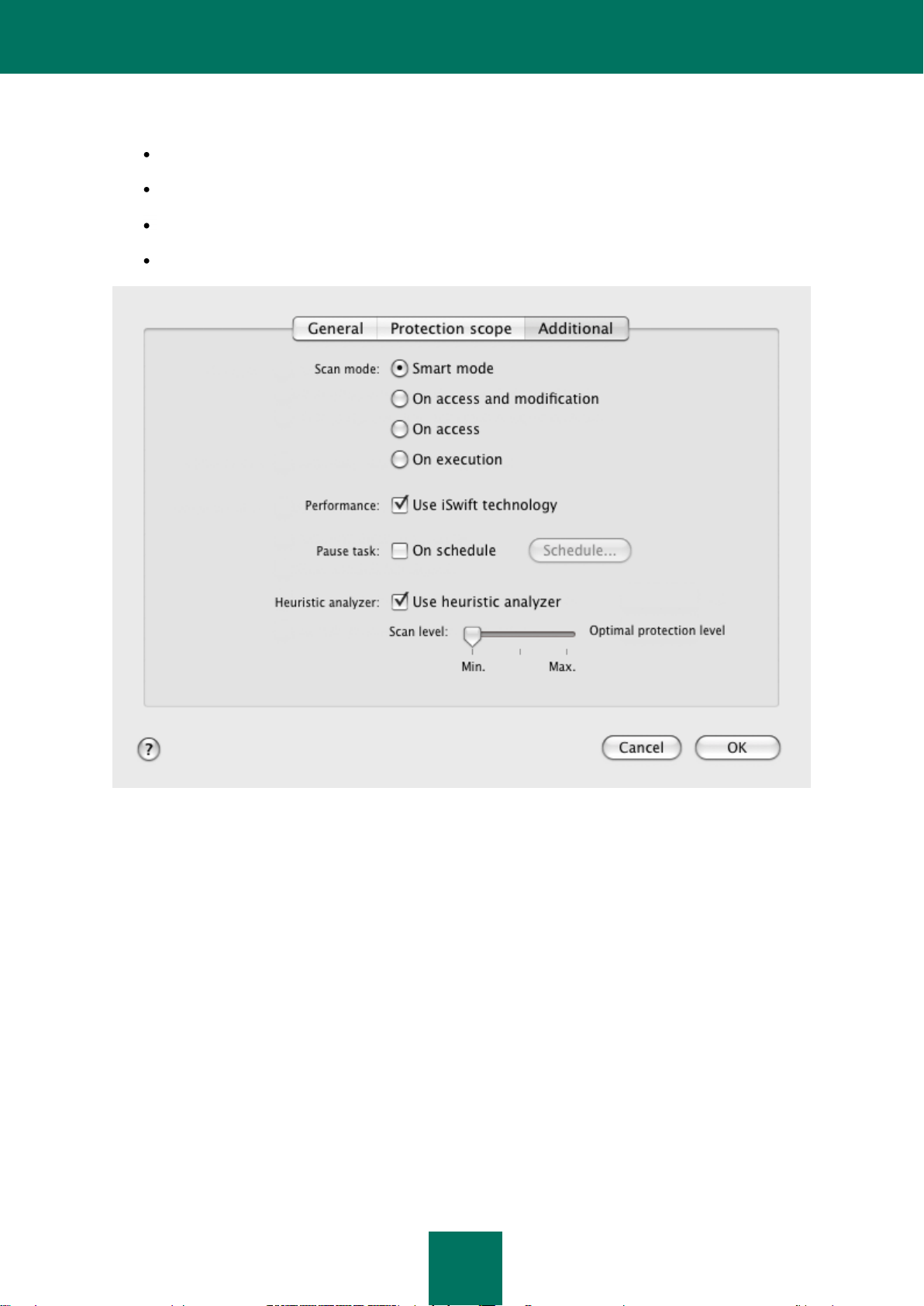
A D M I N I S T R A T O R ' S G U I D E
62
3. In the window that opens select the Additional tab (see figure below) and configure the following settings:
Select File Anti-Virus operation mode in the Scan mode section.
In the Performance section, select a scan technology.
In the Pause task section, enable the scheduled pausing of File Anti-Virus and configure the schedule.
In the Heuristic analyzer section, configure the use of the heuristic analyzer by File Anti-Virus.
Figure 26. File Anti-Virus. Configuring additional settings
Page 63
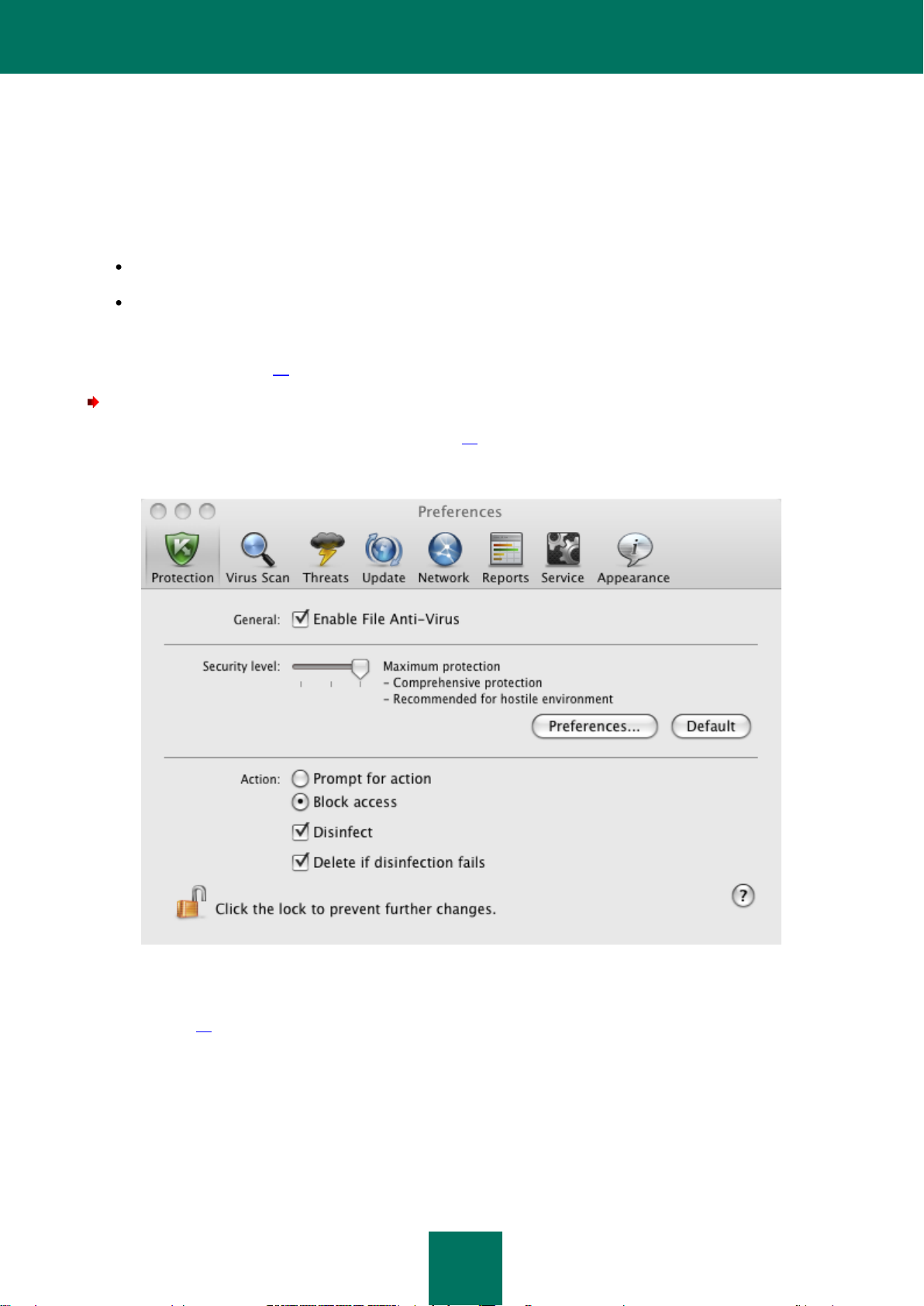
A D V A N C E D A P P L I C A T I O N S E T T I N G S
63
SELECTING ACTIONS ON OBJECTS
If a virus scan reveals that a file is infected or potentially infected, the subsequent behavior of File Anti-Virus depends on
the status of the object and the selected action.
When the scan is complete, the object may be identified as:
malicious, for example, a virus or Trojan;
potentially infected when the scan cannot determine whether the object is infected or not. The application has
probably found in the file a sequence of code from an unknown virus or modified code from a known virus.
By default, all malicious objects undergo disinfection and all potentially infected objects are placed in Quarantine (see
section "Quarantine" on page 91).
To select action which File Anti-Virus needs to perform on detecting an infected or potentially infected object:
1. Open the application preferences window (on page 34) and select the Protection tab (see figure below).
2. In the Action section, select the File Anti-Virus action.
Figure 27. Application preferences window. Protection
Before disinfecting the object or deleting it, Kaspersky Endpoint Security creates a backup copy and places it in the
backup (on page 94) in case the object needs to be restored, or it becomes possible to disinfect it.
RESTORING DEFAULT FILE PROTECTION SETTINGS
You can restore the File Anti-Virus default settings at any time. Kaspersky Lab considers these settings to be optimal and
has used them in its Recommended security level.
Page 64
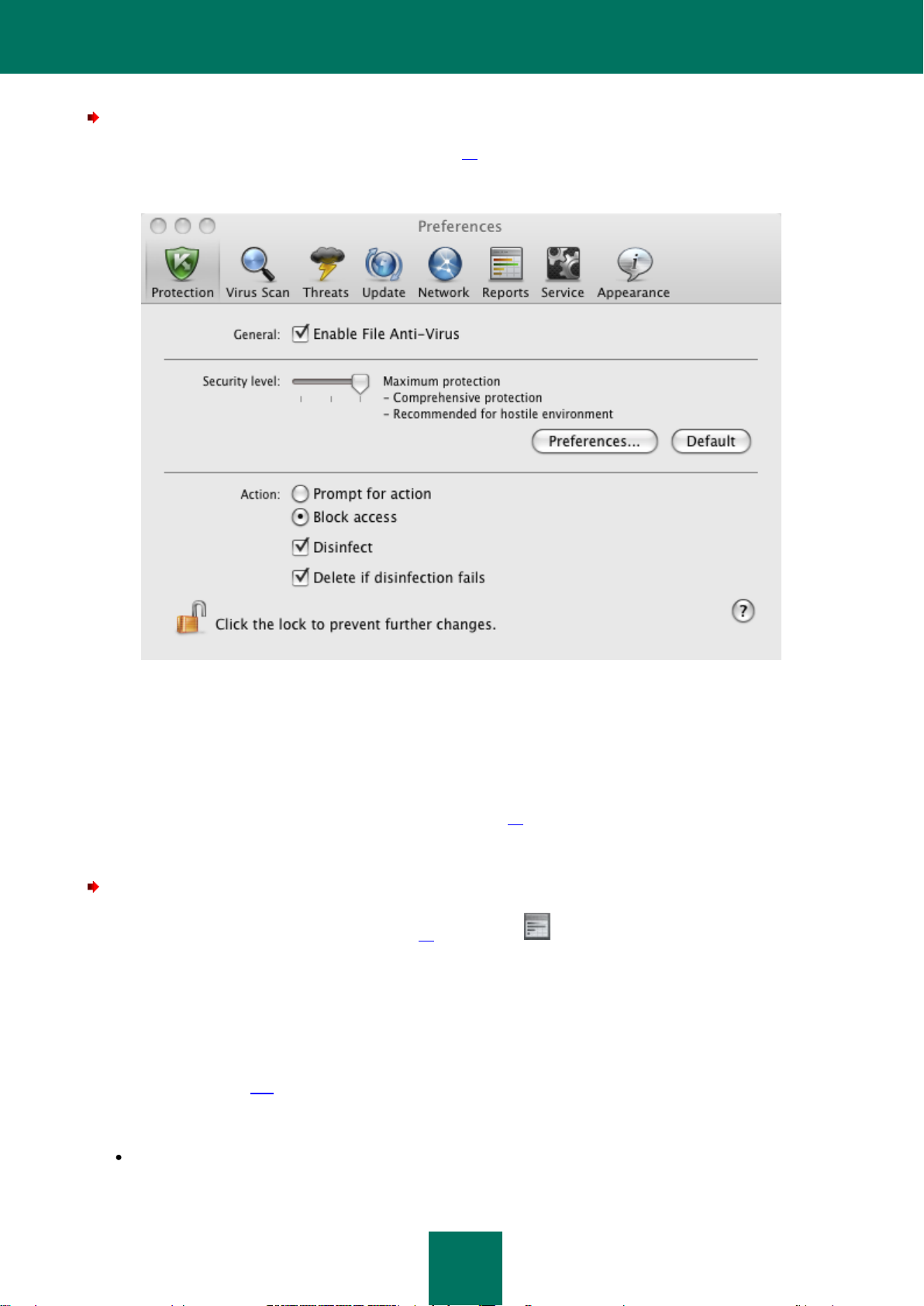
A D M I N I S T R A T O R ' S G U I D E
64
To restore the default File Anti-Virus settings:
1. Open the application preferences window (on page 34) and select the Protection tab (see figure below).
2. In the Security level section, click the Default button.
Figure 28. Application preferences window. Protection
FILE PROTECTION STATISTICS
Summary statistics on File Anti-Virus (number of objects scanned since its most recent launch, number of dangerous
objects detected and disinfected, name of the most recently scanned file) are displayed in the bottom part of the main
application window (see section "Main application window" on page 33).
Also, Kaspersky Endpoint Security provides a detailed report of File Anti-Virus operation.
To view the report:
1. Open the main application window (on page 33) and click the button.
2. In the Running tasks section of the report window that opens, select File Anti-Virus.
If File Anti-Virus is currently disabled, you can view a detailed report on the results of its most recent launch in the
Completed tasks section.
If File Anti-Virus returns an error when closing, view the report and try to restart the component. If you cannot solve the
problem on your own, please contact Kaspersky Lab Technical Support Service (see section "Contacting Technical
Support Service" on page 153).
Detailed information about File Anti-Virus is provided in the report window to the right on the following tabs:
The Detected tab lists all dangerous objects detected by File Anti-Virus. For each object the name and path to
the folder where it is stored are displayed, as well as the status it has been assigned by File Anti-Virus. If the
Page 65

A D V A N C E D A P P L I C A T I O N S E T T I N G S
65
malicious program that has infected the object is revealed, the object is assigned the corresponding status, for
example, virus, Trojan, etc. If the type of malicious effect cannot be established precisely, the object is assigned
the suspicious status. The action taken on the object is also specified next to the status (detected, disinfected).
The Events tab provides a full list of events logged during operation of File Anti-Virus, specifying the time,
name, status and cause of each event. The events can have the following statuses:
information (for example, object not processed, skipped by type);
warning (for example, a virus is detected);
comment (for example, archive is password-protected).
The Statistics tab provides information about the total number of scanned objects and, in separate columns,
how many objects out of the total number scanned are archives, how many are dangerous, how many have
been disinfected, how many have been placed in Quarantine, etc.
The Preferences tab lists the main settings used by File Anti-Virus. To configure a component quickly, click the
Change options button.
Figure 29. Report window. File Anti-Virus
VIRUS SCAN
In addition to the file system protection provided by File Anti-Virus (see section "File Anti-Virus" on page 54) in real-time
mode, it is extremely important to scan your computer for viruses. This is required to stop the spread of malicious
programs that have gone undetected by File Anti-Virus, because, for instance, the level of protection selected is low.
Kaspersky Endpoint Security comprises the following integrated virus scan tasks:
Virus Scan
Page 66

A D M I N I S T R A T O R ' S G U I D E
66
Scan individual items for viruses, such as files, folders, disks, plug-and-play devices.
IN THIS SECTION:
Managing virus scan tasks .............................................................................................................................................. 66
Creating a list of objects to scan ..................................................................................................................................... 70
Configuring virus scan tasks ........................................................................................................................................... 71
Restoring default scan settings ....................................................................................................................................... 78
Virus scan statistics ......................................................................................................................................................... 79
Full Scan
Search for viruses on your computer with a thorough scan of all hard drives.
Quick Scan
Scans only critical areas of the computer for viruses, including folders with operating system files and system
libraries.
By default, these tasks are executed using the recommended settings. You can edit these settings (see section
"Configuring virus scan tasks" on page 71), or create a schedule for running virus scan tasks (see section "Configuring
the virus scan task schedule" on page 75).
MANAGING VIRUS SCAN TASKS
You can run virus scan tasks manually (see section "Launching / pausing virus scan task" on page 66) or automatically,
by a schedule (see section "Configuring the virus scan task schedule" on page 75). You also have the option of creating
user tasks in Kaspersky Endpoint Security(see section "Creating virus scan tasks" on page 68).
LAUNCHING / PAUSING VIRUS SCAN TASK
To start a virus scan task manually, do the following:
1. Open the main application window (on page 33) and click the button.
Page 67
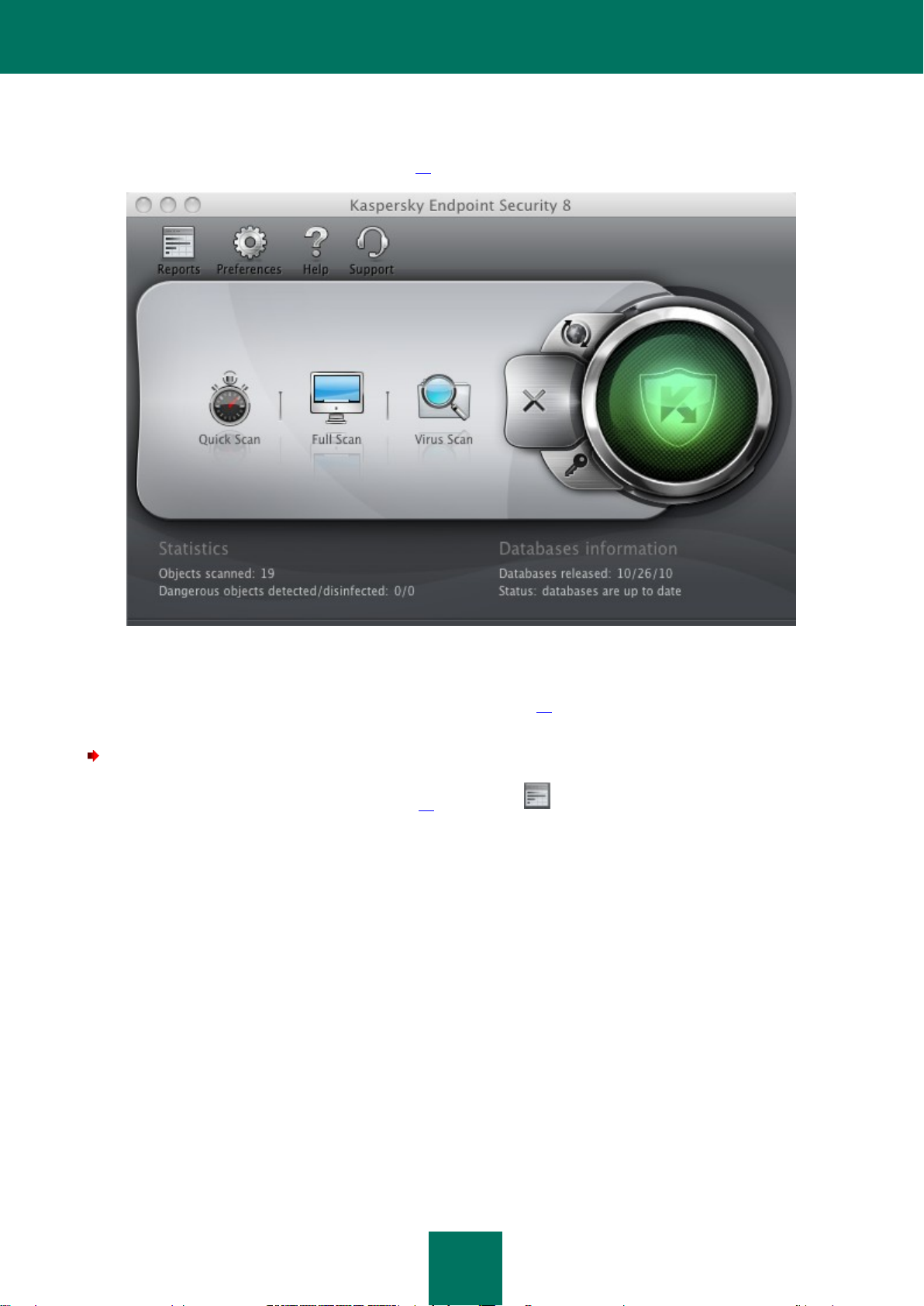
A D V A N C E D A P P L I C A T I O N S E T T I N G S
67
2. In the window that opens (see figure below), select the required task Full Scan, Quick Scan or Virus Scan. If
you have selected the Virus Scan task, Kaspersky Endpoint Security offers you to specify the scan scope. In
addition to the pre-set tasks included in the application, the menu displays the user virus scan tasks (see
section "Creating virus scan tasks" on page 68) that have been created.
Figure 30. Virus scan tasks
Information on currently running tasks is displayed in the left part of the main window, and also in the Running
tasks section of the reports window (see section "Reports" on page 96). Information about executed tasks is
displayed in the Completed tasks section of the report window (see figure below).
To pause a virus scan task, do the following:
1. Open the main application window (on page 33) and click the button. The Kaspersky Endpoint Security
report window opens.
Page 68

A D M I N I S T R A T O R ' S G U I D E
68
2. In the Running tasks (see figure below) section select the name of the virus scan task and click the Stop
button. This will pause the scan until you start the task again manually or it starts again automatically according
to the schedule. To restart the scan, click the Start button. A window opens in which Kaspersky Endpoint
Security offers you to resume the scan that has been interrupted, or start it from the beginning.
Figure 31. Report window. Virus Scan
CREATING VIRUS SCAN TASKS
To scan objects in your computer for viruses, not only can you use the virus scan tasks integrated into Kaspersky
Endpoint Security, but also create your own custom tasks. New tasks are created by modifying existing ones.
To create a new virus scan task, please do the following:
1. Open the application preferences window (on page 34).
Page 69

A D V A N C E D A P P L I C A T I O N S E T T I N G S
69
2. Select the Virus Scan tab in the list to the left (see figure below) and select Quick Scan task or Full Scan task
whose settings most closely match your requirements.
Figure 32. Application preferences window. The Full Scan task
3. Click the button under the list of virus scan tasks and in the window that opens select the Copy
command.
4. Enter the name of the new task in the window that opens and click OK. A task with the name you have specified
appears in the task list.
The new task inherits all the properties of the task from which it was created. Therefore, you may need to configure some
additional settings:
modify the list of objects to scan (see section "Creating a list of objects to scan" on page 70);
specify the settings (see section "Configuring virus scan tasks" on page 71) to be used to execute the task;
create an automatic run schedule (see section "Configuring the virus scan task schedule" on page 75).
In addition to the pre-set virus scan tasks, Kaspersky Endpoint Security allows you to create up to six user scan tasks.
Page 70

A D M I N I S T R A T O R ' S G U I D E
70
You can rename and remove scan tasks.
Only user tasks can be renamed or deleted.
To rename a created task, do the following:
1. Open the application preferences window (on page 34).
2. Select the task in the list to the left (see figure above).
3. Click the button under the list of virus scan tasks and in the window that opens select the Rename
command.
4. Enter the name of the task in the window that opens and click OK. The task is renamed.
To delete a created task, do the following:
1. Open the application preferences window (on page 34).
2. Select the task in the list to the left (see figure above).
3. Click the button under the list of virus scan tasks and in the window that opens select the Delete
command. Confirm the action. The task is deleted from the list.
CREATING A LIST OF OBJECTS TO SCAN
The pre-set Full Scan and Quick Scan tasks already contain lists of objects to scan. The Full Scan task allows you to
scan all files stored on all hard drives of your computer. While running the Quick Scan task, Kaspersky Endpoint
Security only scans vulnerable objects: folders containing operating system files and system libraries.
The Virus scan task requires you to create a list of objects to scan (files, folders, drives, removable devices).
To view the list of objects to scan during execution of the Full Scan and Quick Scan tasks or edit it:
1. Open the application preferences window (on page 34) and select the Virus Scan tab.
2. In the list to the left, select the task name: Full Scan or Quick Scan.
3. To the right under Objects to scan click the Edit button. A window will open containing the list of objects
(see figure below). Edit the list of objects, if necessary.
You can perform the following actions:
Add an object to the list.
Drag an object into the window, click the button and select a more suitable option (File or folder, All
drives, Quarantine, etc.). If the object being added contains subfolders that should also be scanned, check
the Include subfolders box in the file selection window. If the object being added contains symbolic links
to other objects requiring a scan, check the Include symbolic links box in the file selection window that
opens.
Edit an object on the list (only available for user-added objects).
Select the object and click the Edit button. Make the required changes in the window that opens.
Temporarily disable scanning of object.
Page 71

A D V A N C E D A P P L I C A T I O N S E T T I N G S
71
Select the object and uncheck the box next to it. The virus scan task will not be executed for this object until
the box is checked again.
Delete an object (only available for user-added objects).
Select the object and click the button.
When creating user tasks (see section "Creating virus scan tasks" on page 68) the same procedure is used to generate
or modify the list of objects to scan.
Figure 33. Creating a list of objects to scan
To select one or several objects to scan while running the Virus Scan task:
1. Open the main application window (on page 33) and click the button.
2. In the menu that opens select the Virus scan task. A window will open in which to create a list of objects
(see figure above). Edit the list using the algorithm described above.
CONFIGURING VIRUS SCAN TASKS
Tasks are executed on your computer according to the following settings:
Security level
The security level is a set of parameters that define the balance between the thoroughness and speed of
scanning objects. There are three preset security levels (see section "Selecting the security level" on page 72)
with settings developed by Kaspersky Lab.
Action on detected object
This action (see section "Selecting actions on objects" on page 74) defines how Kaspersky Endpoint Security
will react when an infected or potentially infected object is detected.
Page 72

A D M I N I S T R A T O R ' S G U I D E
72
Run mode
Automatically running virus scan according to a schedule (see section "Configuring the virus scan task
schedule" on page 75) enables you to scan your computer for viruses in due time. Only available for the Quick
Scan, Full Scan tasks, and custom tasks.
Launching task under user account
Launching the task under a privileged user account (see section "Launching scan task under user account" on
page 76) enables you to perform a timely scan, regardless of the rights of the current user. Only available for
the Quick Scan, Full Scan tasks, and custom tasks.
In addition, you can set uniform values for the Security level and Action to be taken on detected objects for all virus
scan tasks (see section "Assigning uniform values for all virus scan tasks" on page 77).
SELECTING THE SECURITY LEVEL
Each scan task ensures objects are scanned at one of the following levels:
Maximum protection - the most complete scan of the entire computer or individual disks, folders, or files. We
recommend this level if you suspect that your computer is infected with a virus.
Recommended contains the settings recommended by Kaspersky Lab.
Maximum speed - this level enables you to comfortably use other applications that require significant system
resources, since the range of files scanned is smaller.
By default, virus scan tasks are executed at the Recommended security level. You can increase or decrease the
thoroughness of the scan by selecting Maximum protection or Maximum speed accordingly, or by modifying the
current settings.
To modify the security level of a virus scan task, do the following:
1. Open the application preferences window (on page 34) and select the Virus Scan tab (see figure below).
2. Select the task in the list to the left.
3. In the Security level section, move the slider bar to the required position. Changing the security level changes
the balance between the scan speed and the total number of files scanned: the fewer files scanned for viruses,
the higher the scan speed.
If none of the preset security levels meets your needs, you can customize the scan settings. You are advised to select
the level closest to your requirements as a basis and then modify its settings. This will change the name of the security
level to User.
To modify the settings for the current security level, do the following:
1. Open the application preferences window (on page 34) and select the Virus Scan tab (see figure below).
2. Select the task in the list to the left.
3. In the Security level section, click the Preferences button.
Page 73

A D V A N C E D A P P L I C A T I O N S E T T I N G S
73
4. In the window that opens modify the settings (see section "Defining the types of objects to scan" on page 73)
and click OK to save the changes.
Figure 34. Application preferences window. The Virus Scan task
SPECIFYING THE TYPES OF OBJECTS TO SCAN
By specifying the types of objects to scan, you define the size and format of the files that Kaspersky Endpoint Security
will scan when the task is executed.
To specify the types of objects to scan during the virus scan task, do the following:
1. Open the application preferences window (on page 34) and select the Virus Scan tab (see figure below).
2. Select the task in the list to the left.
3. In the Security level section, click the Preferences button. In the window that opens (see figure below)
configure the following settings:
In the File types section, specify file formats that should be scanned by Kaspersky Endpoint Security when
running the virus scan tasks.
In the Optimization section, configure the scan performance and use of scan technology.
Page 74

A D M I N I S T R A T O R ' S G U I D E
74
In the Compound files section, specify which compound files should be scanned for viruses.
In the Heuristic analyzer section, configure the use of the heuristic analyzer in virus scan tasks.
Figure 35. Virus Scan. Configuring scan settings
SELECTING ACTIONS ON OBJECTS
If a virus scan task reveals that an object is infected or potentially infected, the subsequent behavior of Kaspersky
Endpoint Security depends on the status of the object and the selected action.
When the scan is complete, the object may be identified as:
malicious, for example, a virus or Trojan;
potentially infected when the scan cannot determine whether the object is infected or not. The application has
probably found in the file a sequence of code from an unknown virus or modified code from a known virus.
By default, all malicious objects undergo disinfection and all potentially infected objects are placed in Quarantine (see
section "Quarantine" on page 91).
To select action which Kaspersky Endpoint Security needs to perform on detecting an infected or potentially infected
object:
1. Open the application preferences window (on page 34), select the Virus Scan tab and the name of the task in
the list to the left (see figure below).
Page 75

A D V A N C E D A P P L I C A T I O N S E T T I N G S
75
2. In the Action section, select an action to be performed by Kaspersky Endpoint Security.
Figure 36. Application preferences window. The Full Scan task
Before disinfecting the object or deleting it, Kaspersky Endpoint Security creates a backup copy and places it in the
backup (on page 94) in case the object needs to be restored, or it becomes possible to disinfect it.
CONFIGURING THE VIRUS SCAN TASK SCHEDULE
All virus scan tasks on your computer can be run manually (see section "Launching / pausing virus scan tasks" on
page 66). In addition, the Quick Scan and Full Scan tasks, and user-created tasks can be run in Kaspersky Endpoint
Security according to a pre-defined schedule.
To configure the startup of the Quick Scan and Full Scan tasks as well as custom virus scan tasks upon a
schedule:
1. Open the application preferences window (on page 34) and select the Virus Scan tab.
2. In the list to the left, select the name of a virus scan task and enable the scheduled task run in the Run mode
section. Click the Edit button to configure the task settings.
Page 76
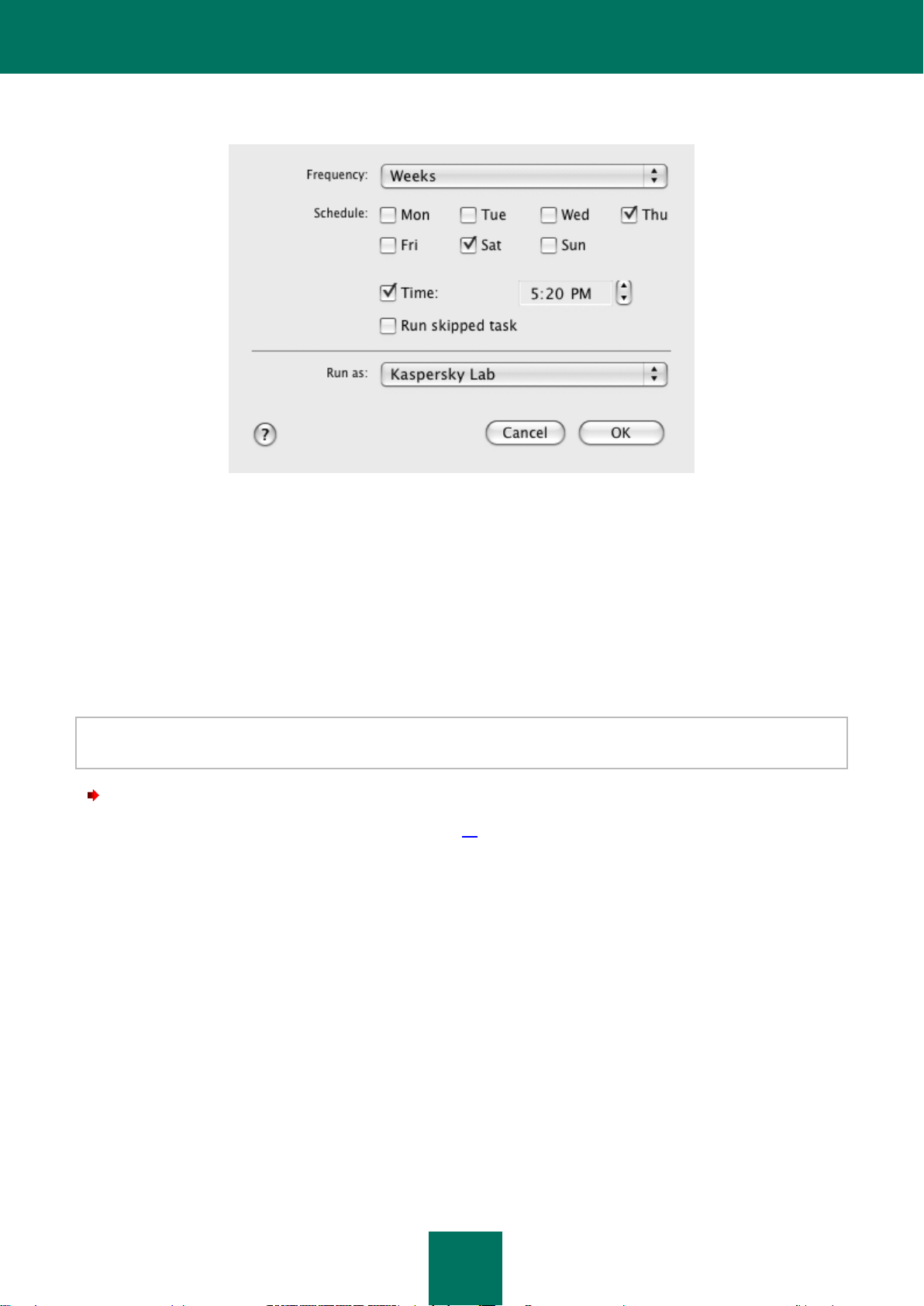
A D M I N I S T R A T O R ' S G U I D E
76
3. In the window that opens (see figure below), set the frequency with which the task will be launched.
Figure 37. Configuring a virus scan task schedule
RUNNING SCAN TASKS UNDER USER ACCOUNT
The application allows the user to run virus scan tasks under a different user account. This ensures that the computer is
scanned in due time, regardless of the rights of the current user. For example, you might need access rights to a certain
object during a scan. By using this feature, you can configure tasks to run under a user account with the necessary
privileges.
This service is disabled by default so that tasks are started under the current account, under which you have been
logged in the operating system.
You can configure the Quick scan and Full scan tasks under a privileged user account, as well as user virus scan tasks
created on their basis.
To specify an account, under which virus scan tasks should be started:
1. Open the application preferences window (on page 34) and select the Virus Scan tab.
2. In the list to the left, select the name of a virus scan task and enable the scheduled task run in the Run mode
section. Click the Edit button to configure the task under a user account.
Page 77
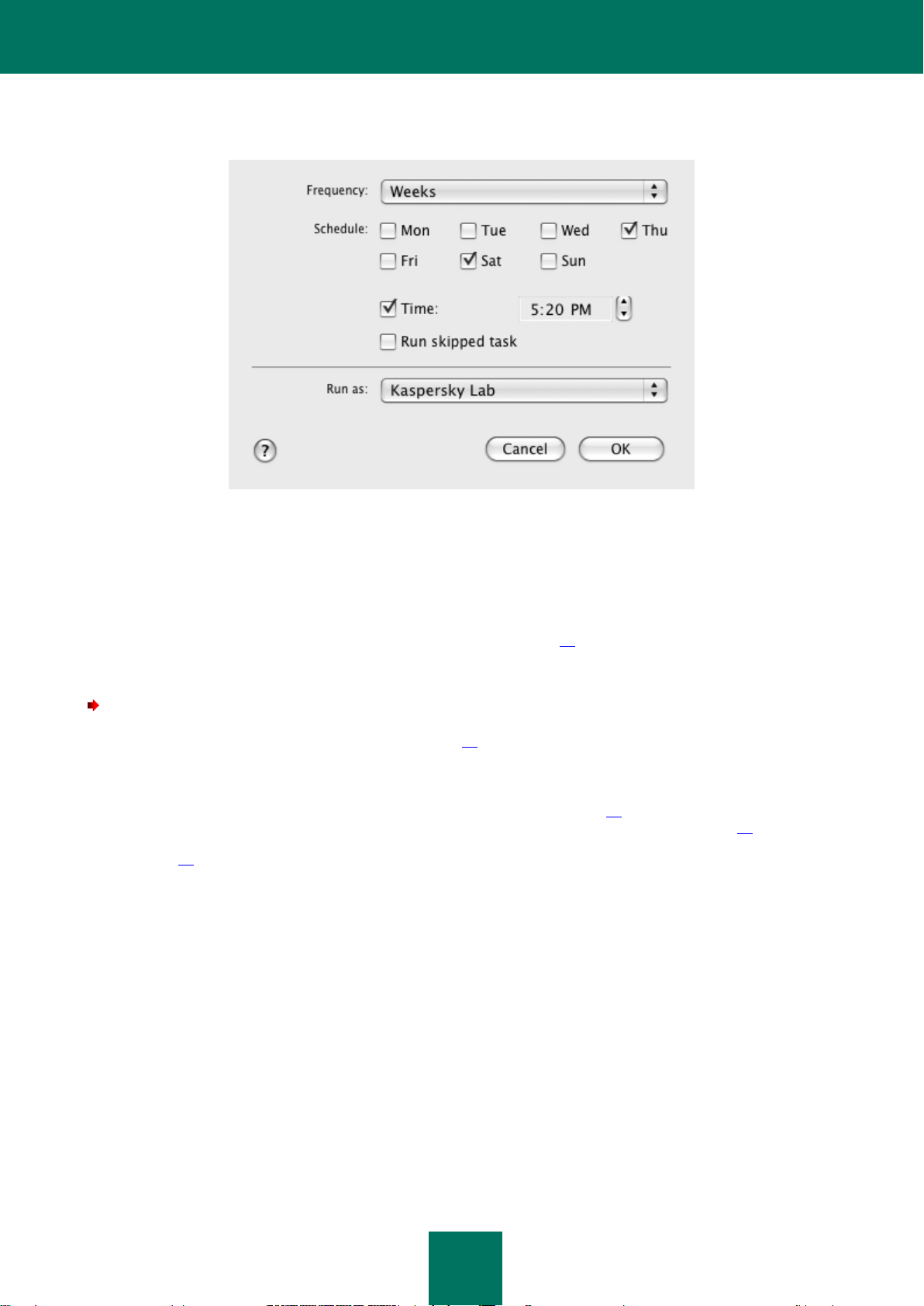
A D V A N C E D A P P L I C A T I O N S E T T I N G S
77
3. In the window that opens (see figure below), in the Run as section, select the account, under which the task will
be started, from the dropdown list.
Figure 38. Configuring a virus scan task schedule
ASSIGNING UNIFORM SCAN SETTINGS TO ALL TASKS
By default, virus scan tasks included in the Kaspersky Endpoint Security installation package are run according to the
settings recommended by Kaspersky Lab experts. User tasks created on their basis inherit all the settings. You can not
only modify the settings (see section "Configuring virus scan tasks" on page 71) of each task separately, but assign
uniform values for all virus scan tasks. The Security level and Action settings in the Virus Scan task assigned to scan
a particular object are used as a basis.
To assign uniform scan settings for all tasks:
1. Open the application preferences window (on page 34) and select the Virus Scan tab.
2. In the list to the left select the Virus Scan task (see figure below).
3. Select the security level (see section "Selecting the security level" on page 72) that most closely matches your
requirements, modify the settings (see section "Specifying the types of objects to scan" on page 73) and select
the action to take on infected or potentially infected objects (see section "Selecting actions on objects" on
page 74).
Page 78
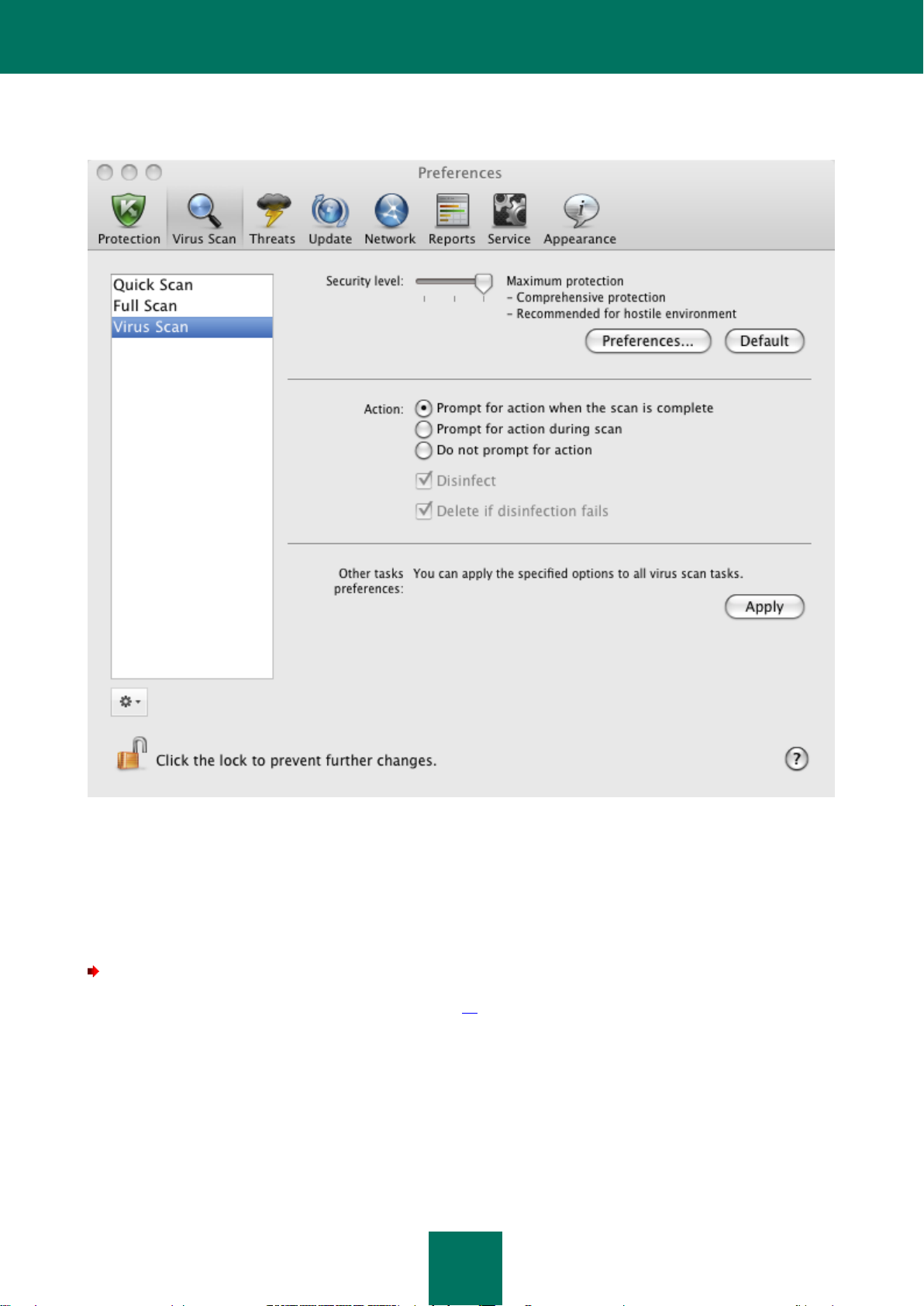
A D M I N I S T R A T O R ' S G U I D E
78
4. In the Other task preferences section, click the Apply button. Kaspersky Endpoint Security applies the values
of the Security level and Action preferences to other virus scan tasks, including custom ones.
RESTORING DEFAULT SCAN SETTINGS
You can restore the default virus scan settings at any time. They are considered optimal, recommended by Kaspersky
Lab, and grouped in the Recommended security level.
To restore the default scan settings, do the following:
1. Open the application preferences window (on page 34), select the Virus Scan tab and then the name of the
required task from the list on the left.
Figure 39. Application preferences window. The Virus Scan task
Page 79

A D V A N C E D A P P L I C A T I O N S E T T I N G S
79
2. Under Security level (see figure below) click the Default button. This restores the recommended task settings.
Figure 40. Application preferences window. The Virus Scan task
VIRUS SCAN STATISTICS
A brief summary on the execution of every current task (in percentages) is provided in the main application window (see
section "Main application window" on page 33).
Also, Kaspersky Endpoint Security provides you with a detailed report of virus scan tasks run.
To view a report on the run of the current task:
1. Open the main application window (on page 33) and click the button.
2. In the Running tasks section of the report window that opens, select the name of the required task.
If the task is already complete, information about the results are provided in the Completed tasks section.
Information about the progress of the current task or brief statistics on the results of the completed task are displayed in
the lower part of the report window. It contains information on the number of objects scanned, the number of malicious
Page 80

A D M I N I S T R A T O R ' S G U I D E
80
objects detected and the number of objects to be processed. Scan start time, estimated completion time, and duration
are also displayed.
If any errors occur during the scan, run the task again. If the attempt to re-run the task also results in an error, contact
Kaspersky Lab Technical Support Service (see section "Contacting Technical Support Service" on page 153).
Detailed information about the execution of virus scan tasks is provided in the report window to the right on the following
tabs:
The Detected tab lists all the dangerous objects detected while the task was running. For each object the name
and path to the folder where it is stored are displayed, as well as the status it has been assigned by Kaspersky
Endpoint Security. If the malicious program that has infected the object is revealed, the object is assigned the
corresponding status, for example, virus, Trojan, etc. If the type of malicious effect cannot be established
precisely, the object is assigned the suspicious status. The action taken on the object is also specified next to
the status (detected, disinfected).
The Events tab keeps a full list of events that occur while the virus scan task is running with the time, name,
status and cause of each event. The events can have the following statuses:
information (for example, object not processed, skipped by type);
warning (for example, a virus is detected);
comment (for example, archive is password-protected).
The Statistics tab provides information about the total number of scanned objects and, in separate columns,
how many objects out of the total number scanned are archives, how many are dangerous, how many have
been disinfected, how many have been placed in Quarantine, etc.
The Preferences tab lists the main settings used to run the virus scan task. To configure a component quickly,
click the Change options button.
Figure 41. Report window. Virus Scan
Page 81

A D V A N C E D A P P L I C A T I O N S E T T I N G S
81
UPDATING THE APPLICATION
Keeping anti-virus databases up-to-date is vital for the security of your computer. As new viruses, Trojans, and malicious
software emerge daily, it is extremely important to update the application regularly to keep your data permanently
protected.
Kaspersky Endpoint Security update means that the following components will be downloaded and installed on your
computer:
Anti-virus databases
The Anti-virus databases protect the data on your computer. File Anti-Virus (on page 54) and virus scan tasks
(see section "Scanning for viruses" on page 65) use them to find and deal with malicious objects on your
computer. Virus databases are updated hourly with new threats and ways to fight them, so it's important to
update them regularly.
Application modules
In addition to the databases, you can update the internal modules of Kaspersky Endpoint Security. Kaspersky
Lab regularly releases update packages.
Main update sources of Kaspersky Endpoint Security are dedicated Kaspersky Lab update servers and Kaspersky
Administration Kit Administration Server.
An Internet connection is required to download updates from the servers. If the Internet connection is established using a
proxy server, adjust the network settings (see section "Configuring connection to a proxy server " on page 88).
If you cannot access the Kaspersky Lab update servers (for example, your Internet connection is down), contact
Kaspersky Lab Technical Support Service (see section "Contacting Technical Support Service" on page 153) to receive
the Kaspersky Endpoint Security updates on disk in ZIP format.
Updates can be downloaded in one of the following modes:
Automatically. Kaspersky Endpoint Security regularly checks for an update package in the update source.
During a virus outbreak the frequency of the checks may increase and decrease afterwards. If Kaspersky
Endpoint Security detects new updates, it downloads them in the background and installs on the computer. This
is the default mode.
By schedule. Kaspersky Endpoint Security is automatically updated according to a schedule.
Manually. In this case, you launch the Kaspersky Endpoint Security update manually.
During an update the application modules and anti-virus databases are compared with the ones currently available at the
update source. If the most recent version of the databases and modules are installed on your computer, the bottom part
of the main application window (see section "Main application window" on page 33) displays a message that the antivirus databases are up-to-date. If the bases and modules differ from those currently available at the update source, only
the missing components of the update will be installed on your computer. Databases and modules are not copied in their
entirety, which allows increasing update speed and reducing Internet traffic.
Prior to updating the databases and modules, Kaspersky Endpoint Security creates backup copies of them in case you
need to rollback. Update rollback feature (see section "Rolling back the last update" on page 82) may be useful if a new
version of the databases contains an invalid signature that makes Kaspersky Endpoint Security block a safe application.
In case of Kaspersky Endpoint Security database corruption, it is recommended to run the update task to download a
valid set of databases for up-to-date protection.
At the same time as updating Kaspersky Endpoint Security, you can copy the downloaded updates to a local source (see
section "Updating from a local source" on page 83). The service allows you to update Kaspersky Endpoint Security
databases and modules used by the application locally on other computers to reduce Internet traffic.
Page 82

A D M I N I S T R A T O R ' S G U I D E
82
IN THIS SECTION:
Starting update ................................................................................................................................................................ 82
Rolling back the last update ............................................................................................................................................ 82
Updating from a local source ........................................................................................................................................... 83
Configuring the update .................................................................................................................................................... 85
Update statistics .............................................................................................................................................................. 89
STARTING UPDATE
Updating Kaspersky Endpoint Security in a timely manner keeps your computer protected at a due level. If the anti-virus
databases and modules are not updated, the information on your computer is at serious risk.
The bottom part of the main application window (see section "Main application window" on page 33) displays the latest
information about Kaspersky Endpoint Security updates: the release date of anti-virus databases, the number of records
contained in the databases installed on your computer, and information about their actuality. The number of records in
the databases reflects the number of currently known threats against which the computer is protected.
While using Kaspersky Endpoint Security, you can run the application update at any moment. To do so, click the
button in the main window. Detailed information about the execution of this task is displayed in the report window (see
section "Reports" on page 96).
At the same time as updates are downloaded from the Kaspersky Lab servers or from Kaspersky Administration Kit
Administration Server, they will be copied to a local source (see section "Updating from a local source" on page 83),
given that the service is enabled.
ROLLING BACK THE LAST UPDATE
Every time you run the application update, Kaspersky Endpoint Security first creates a backup copy of the databases and
modules in use, and only after that starts updating them. This operation procedure allows you to return to the previous
version of the databases, if necessary. Update rollback feature may be useful in case a new version of the databases
contain an invalid signature that makes Kaspersky Endpoint Security block a safe application.
In case of Kaspersky Endpoint Security database corruption, it is recommended to run the update task to download a
valid set of databases for up-to-date protection.
To rollback the anti-virus databases, do the following:
1. Open the application preferences window (on page 34) and select the Update tab (see figure below).
2. In the Rollback update section, click the Rollback update button.
Page 83

A D V A N C E D A P P L I C A T I O N S E T T I N G S
83
You can view the results of the rollback in the report window (see section "Virus scan statistics" on page 89).
Figure 42. Application preferences window. Update
UPDATING FROM A LOCAL SOURCE
If several computers are connected via a local network, there is no need to download Kaspersky Endpoint Security
updates for each of them separately since this would significantly increase the network traffic. You can use the update
distribution service to locally update the Kaspersky Endpoint Security anti-virus databases and modules used by the
application on other computers, thereby reducing Internet traffic. To do so, set up update distribution as follows:
1. One of the computers on the network retrieves the Kaspersky Endpoint Security update package from the
Kaspersky Lab web servers or from Kaspersky Administration Kit Administration Server, or from another web
resource hosting the current set of updates. The updates retrieved are placed in a shared folder.
Shared folder should be created in advance.
2. Other computers on the network refer to the shared folder as the update source.
To enable the update distribution service, do the following:
1. Open the application preferences window (on page 34) and select the Update tab (see figure below).
Page 84

A D M I N I S T R A T O R ' S G U I D E
84
2. In the Update section, click the Preferences button.
Figure 43. Application preferences window. Update
3. In the window that opens, select the Additional tab in the window that opens (see the figure below). Check
the Copy updates to folder box and click the Select button.
4. In the standard window that opens, select a shared folder in which retrieved updates should be saved.
Kaspersky Endpoint Security only retrieves its own exclusive update package from Kaspersky Lab update servers or
Kaspersky Administration Kit Administration Server.
Figure 44. Configuring settings for the update distribution service
Page 85

A D V A N C E D A P P L I C A T I O N S E T T I N G S
85
CONFIGURING THE UPDATE
Kaspersky Endpoint Security is only updated in accordance with the following settings:
Run mode
The choice of update mode determines whether the update is launched automatically (recommended by
Kaspersky Lab), manually or scheduled. If the latter option is selected, you should create an update task launch
schedule (see section "Configuring scheduled update task launch" on page 88).
Update object
The update object determines what is to be updated: only the anti-virus databases or the application databases
and the modules. Kaspersky Endpoint Security databases are always updated, and the application modules are
only updated if the corresponding box is checked (see section "Selecting the update mode and objects" on
page 85).
Update source
Update source is a resource that contains actual files of anti-virus databases and modules for Kaspersky
Endpoint Security. Update sources can be HTTP and FTP servers, local or network folders.
Network settings
To download updates from Kaspersky Lab's update servers or sources other than local or network folders, your
computers needs to be connected to the Internet. If the Internet connection is established using a proxy server,
you should adjust the network settings (see section "Configuring connection to a proxy server" on page 88).
SELECTING THE UPDATE MODE AND OBJECTS
When configuring the update settings of Kaspersky Endpoint Security, it is very important to define the update object and
run mode.
To configure the update task run schedule:
1. Open the application preferences window (on page 34) and select the Update tab (see figure below).
2. In the Run mode section, select the update task run mode.
To allow the application to copy and install not only anti-virus databases but also application modules when running
the update:
1. Open the application preferences window (on page 34), select the Update tab (see figure below).
2. In the Update section, check the Update application modules box.
Page 86

A D M I N I S T R A T O R ' S G U I D E
86
If module updates are available during execution of the update task, Kaspersky Endpoint Security retrieves and
applies them after rebooting your computer. The downloaded module updates will not be installed until the
computer restarts. If the next application update becomes available before the computer is restarted and the
program module updates downloaded earlier are installed, the databases are only updated.
Figure 45. Application preferences window. Update
SELECTING AN UPDATE SOURCE
The update source is a resource containing current files in the Kaspersky Endpoint Security anti-virus databases and
modules. Update sources can be HTTP and FTP servers, local or network folders.
The main update source is Kaspersky Lab's update servers. These are special websites where updates of databases
and internal modules for all Kaspersky Lab products are stored. Kaspersky Administration Kit Administration Server is
also employed as update source for Kaspersky Endpoint Security.
If you cannot access Kaspersky Lab's update servers (for example, there is no Internet connection), contact Technical
Support Service to receive the updates in ZIP format. You can copy the updates and upload them to an FTP or HTTP
site, or save them in a local or network folder.
When ordering updates on removable media, please specify if you want to receive the updates for internal Kaspersky
Endpoint Security modules as well.
To select an update source for Kaspersky Endpoint Security:
1. Open application settings window (on page 34) and select the Update tab.
2. In the Update section, click the Preferences button.
3. In the window that opens, select the Update source tab (see the figure below). Edit the list of update sources, if
necessary.
Page 87

A D V A N C E D A P P L I C A T I O N S E T T I N G S
87
By default, the list of update sources only contains Kaspersky Lab update servers and Kaspersky Administration
Kit Administration Server. When running an update, Kaspersky Endpoint Security refers to this list for the
address of the first server on it and attempts to download the updates from this server. If the updates cannot be
downloaded from the selected server, the application tries to connect and retrieve the updates from the next
server. This continues until a connection is successfully established, or until all the available update servers
have been tried. For subsequent updates the application first of all tries to access the server from which the
most recent update was successfully made.
You can perform the following actions:
Add a new update source to the list.
Click the button and select the most suitable option from the dropdown list (Path – for a local or
network folder or URL – for a HTTP or FTP server). In the window that opens specify the location of the
new update source.
Change the update source.
Select the update source in the list and click the Edit button. Make the required changes in the window that
opens.
Note that such update sources as Kaspersky Lab update servers and Kaspersky Administration Kit
Administration Server cannot be edited or deleted.
Temporarily disable retrieval of updates from the source.
Select the update source in the list and uncheck the box next to it. Kaspersky Endpoint Security will not be
updated from this source until the box is checked again.
Delete update source.
Select the update source in the list and click the button.
Figure 46. Selecting an update source
Page 88

A D M I N I S T R A T O R ' S G U I D E
88
CONFIGURING SCHEDULED UPDATE TASK LAUNCH
By default, Kaspersky Endpoint Security is updated automatically. You can select another update run mode: manual or
scheduled.
To configure the startup of the scheduled update task for Kaspersky Endpoint Security:
1. Open the application preferences window (on page 34) and select the Update tab.
2. In the Run mode section, select the option to run a scheduled update and click the Edit button.
3. In the window that opens (see figure below), set the frequency with which the task will be launched.
Figure 47. Configuring the update task schedule
CONFIGURING CONNECTION TO A PROXY SERVER
If your computer connects to the Internet through a proxy server, configure the settings for it. Kaspersky Endpoint
Security uses these settings for updating anti-virus databases and modules.
To configure a connection to a proxy server, do the following:
1. Open the application settings window (on page 34) and select the Network tab (see figure below).
2. In the General section, check the Use proxy server box.
Page 89
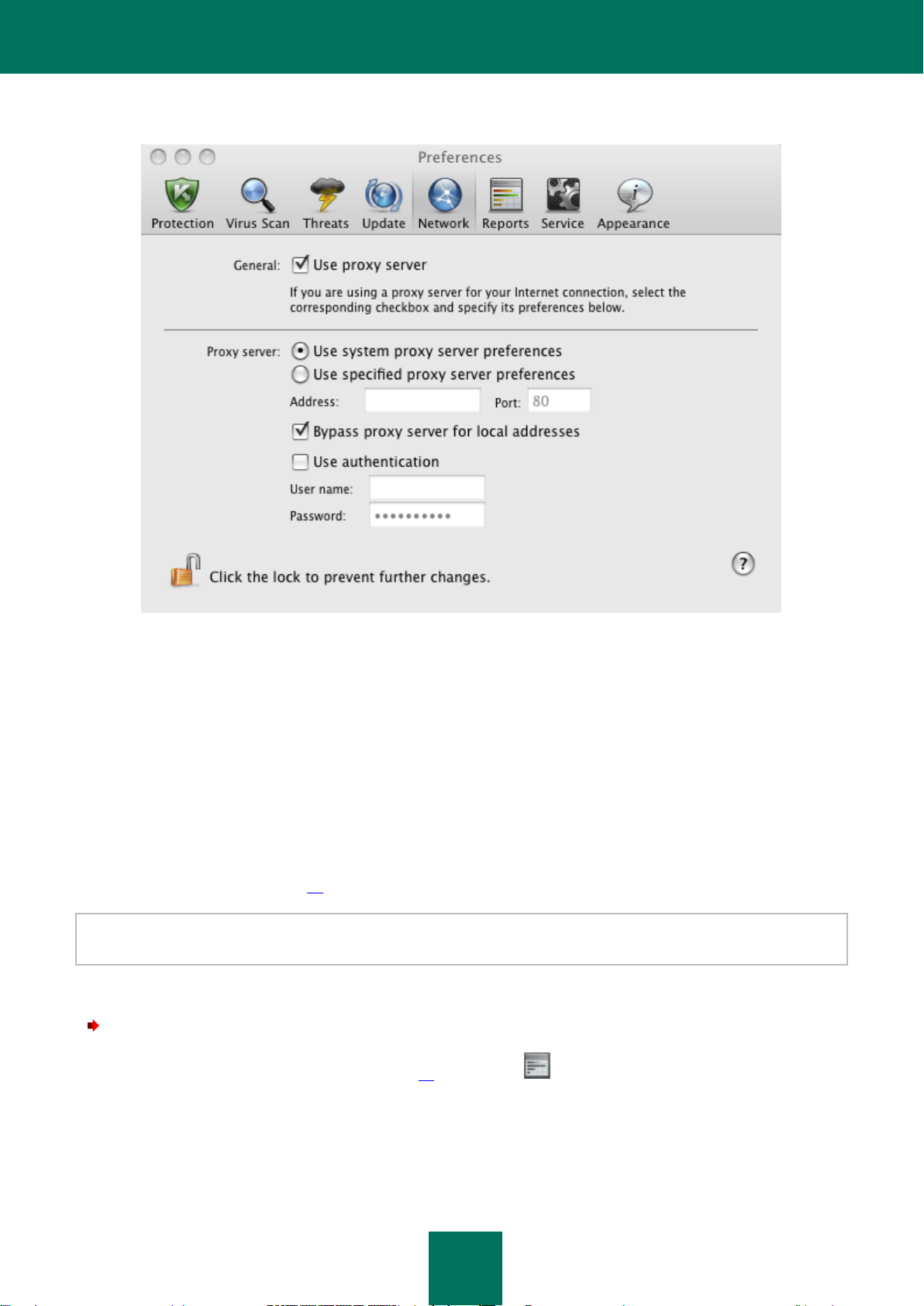
A D V A N C E D A P P L I C A T I O N S E T T I N G S
89
3. In the Proxy server section, configure the proxy server.
Figure 48. Application preferences window. Network
If you are downloading the update from an FTP server, connection to the server is in passive mode by default. If this
connection fails, it will attempt to connect in active mode.
By default, the time assigned to connect to an update server is one minute. If a connection cannot be established, after
this period an attempt is made to connect to the next update source in the list. This continues until a connection is
successfully established, or until all the available update servers have been tried.
UPDATE STATISTICS
Brief statistics on the current update service (release date of anti-virus databases, number of database records,
information about the actuality of databases) are provided in the lower part of the main application window (see section
"Main application window" on page 33).
If you have not previously updated Kaspersky Endpoint Security, there will be no information about the most recent
update.
Also, Kaspersky Endpoint Security provides you with a detailed report on the update task run.
To view a report on the run of the current task:
1. Open the main application window (on page 33) and click the button.
2. In the Running tasks section of the report window that opens, select the Update task.
Information about the results of the latest updates can be viewed in the Completed tasks section.
Page 90
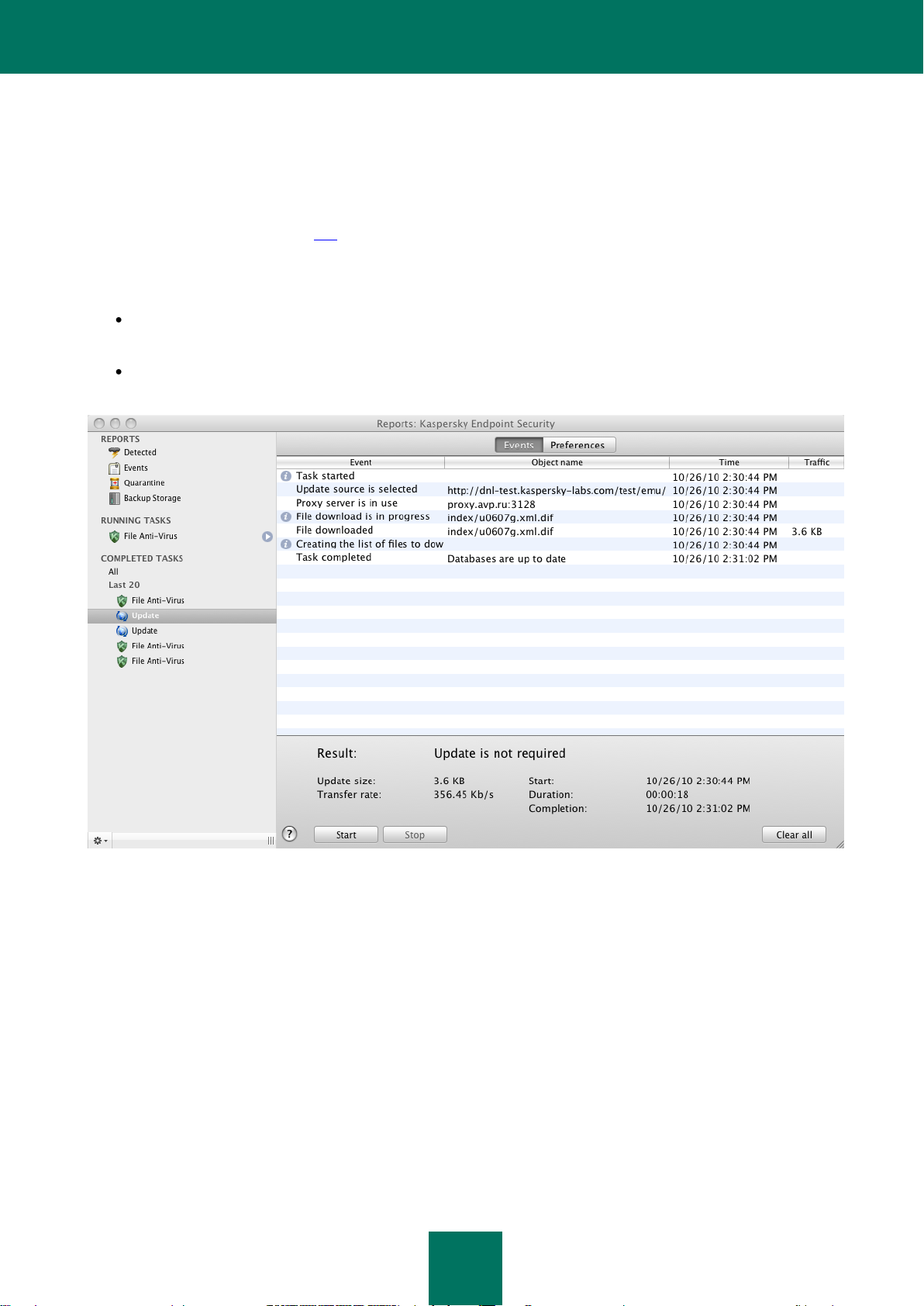
A D M I N I S T R A T O R ' S G U I D E
90
Information about the progress of the current task or brief statistics on the results of the completed task are displayed in
the lower part of the report window. If the update is completed successfully, the statistics include information about the
size of the updates copied and installed, the speed with which they were performed, the start and completion time, and
the duration of the task.
If the operation fails, make sure that the update settings are correct and that the update source is available. Restart the
update. If the attempt also results in an error, contact Kaspersky Lab Technical Support Service (see section "Contacting
Technical Support Service" on page 153).
Detailed information about the execution of virus scan tasks is provided in the report window to the right on the following
tabs:
The Events tab lists all operations performed during the update process in sequence, with the names of the
updated objects, the paths to the folders in which they are stored, and the time taken to access them.
The Preferences tab lists the main settings used to perform the update. To configure a component quickly, click
the Change options button.
REPORTS AND STORAGES
Kaspersky Endpoint Security allows you to move potentially infected objects to Quarantine, create copies of infected
objects in Backup Storage before disinfection or deletion, and create detailed reports on any application component's
operation.
Figure 49. Report window. Update
Page 91

A D V A N C E D A P P L I C A T I O N S E T T I N G S
91
IN THIS SECTION:
Quarantine ...................................................................................................................................................................... 91
Backup Storage ............................................................................................................................................................... 94
Reports............................................................................................................................................................................ 96
Configuring reports and storages .................................................................................................................................... 98
QUARANTINE
Quarantine is a special repository containing the objects that are potentially infected with viruses.
Potentially infected objects are objects suspected by Kaspersky Endpoint Security of being infected with viruses or their
modifications. The potentially infected status can be assigned to an object in the following cases:
The code of the object being analyzed resembles a known threat but is partially altered.
Kaspersky Endpoint Security anti-virus databases contain threats that have been already analyzed by
Kaspersky Lab specialists. If the databases do not yet contain any information about this modification of a
malicious program, Kaspersky Endpoint Security recognizes objects infected with this modification as potentially
infected ones and finds a threat that seems the most similar to this type of infection.
The code of the detected object resembles a malicious program in terms of its structure, but Kaspersky
Endpoint Security does not contain any records similar to it.
It is quite possible that this is a new type of threat, so Kaspersky Endpoint Security classifies that object as a
potentially infected object.
Potentially infected objects can be detected and placed in Quarantine by File Anti-Virus (see section "File Anti-Virus" on
page 54) or during a virus scan (see section "Scanning for viruses" on page 65).
Additionally, you can move an object to Quarantine manually by clicking the Quarantine button in a special notification
(see section "What to do when the application's notifications appear" on page 49) that appears on the screen when a
potentially infected object is detected.
When Kaspersky Endpoint Security moves a potentially infected object to Quarantine, it deletes it from the current folder
and saves it in the Quarantine folder. Files in Quarantine are stored in a special format and are not dangerous.
VIEWING THE CONTENTS OF QUARANTINE
You can view the contents of Quarantine in the Quarantine section in the report window (see figure below).
To view the contents of Quarantine, do the following:
1. Open the main application window (on page 33) and click the button. The Kaspersky Endpoint Security
report window opens.
Page 92
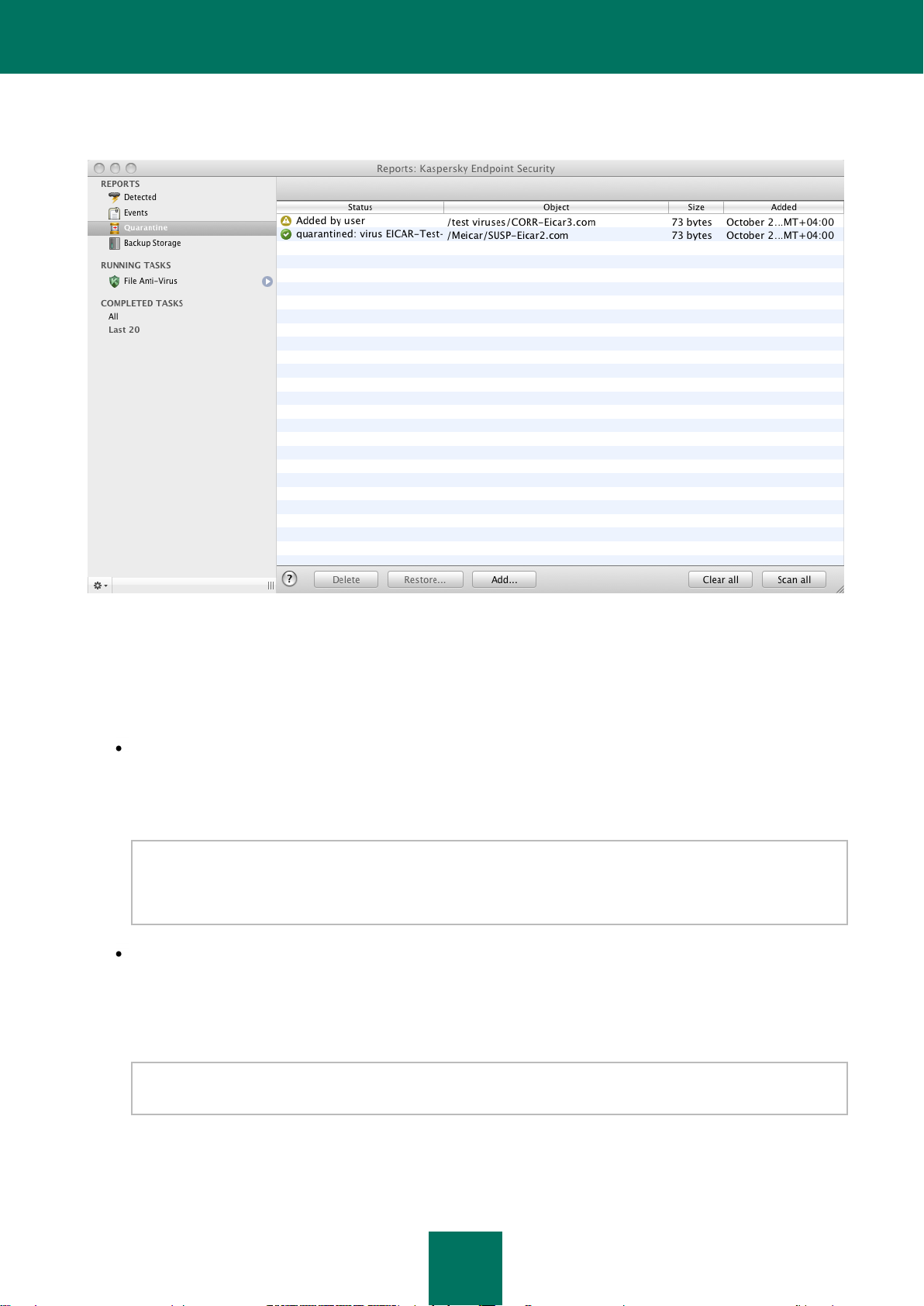
A D M I N I S T R A T O R ' S G U I D E
92
2. In the left part of the report window, select Quarantine. The contents of Quarantine are displayed in the righthand part of the window.
Figure 50. Report window. Quarantine
ACTIONS ON QUARANTINED OBJECTS
Kaspersky Endpoint Security allows you to carry out the following actions on potentially infected objects:
Manually move to Quarantine files that you suspect are infected but have not been detected by Kaspersky
Endpoint Security.
To do this, in the Quarantine window (see figure below), click the Add button and select the required file in the
standard window that opens. It is added to the list with the added by user status.
Files moved to Quarantine manually may change their status if they have been scanned using the most recent
databases no earlier than three days after they were scanned for the first time in Quarantine. If a file is assigned
the false operation status, it will be automatically restored. If a file is identified as infected, it is deleted from
Quarantine and a copy is stored in Backup Storage.
Scan and disinfect all potentially infected quarantined objects , using the current version of Kaspersky Endpoint
Security databases.
To do this, in the Quarantine window (see figure below), click the Scan all button. After scanning and
disinfecting any quarantined object, its status can change to infected, potentially infected, false operation, OK,
etc.
The status of an object in Quarantine is changed only after it is scanned using anti-virus databases released no
earlier than three days after the file was placed in Quarantine.
The infected status means that the object was identified as infected but the application did not manage to treat
it. Kaspersky Endpoint Security deletes such objects from Quarantine, saving copies of them in Backup. All
objects with the false operation status are restored to their original locations.
Page 93
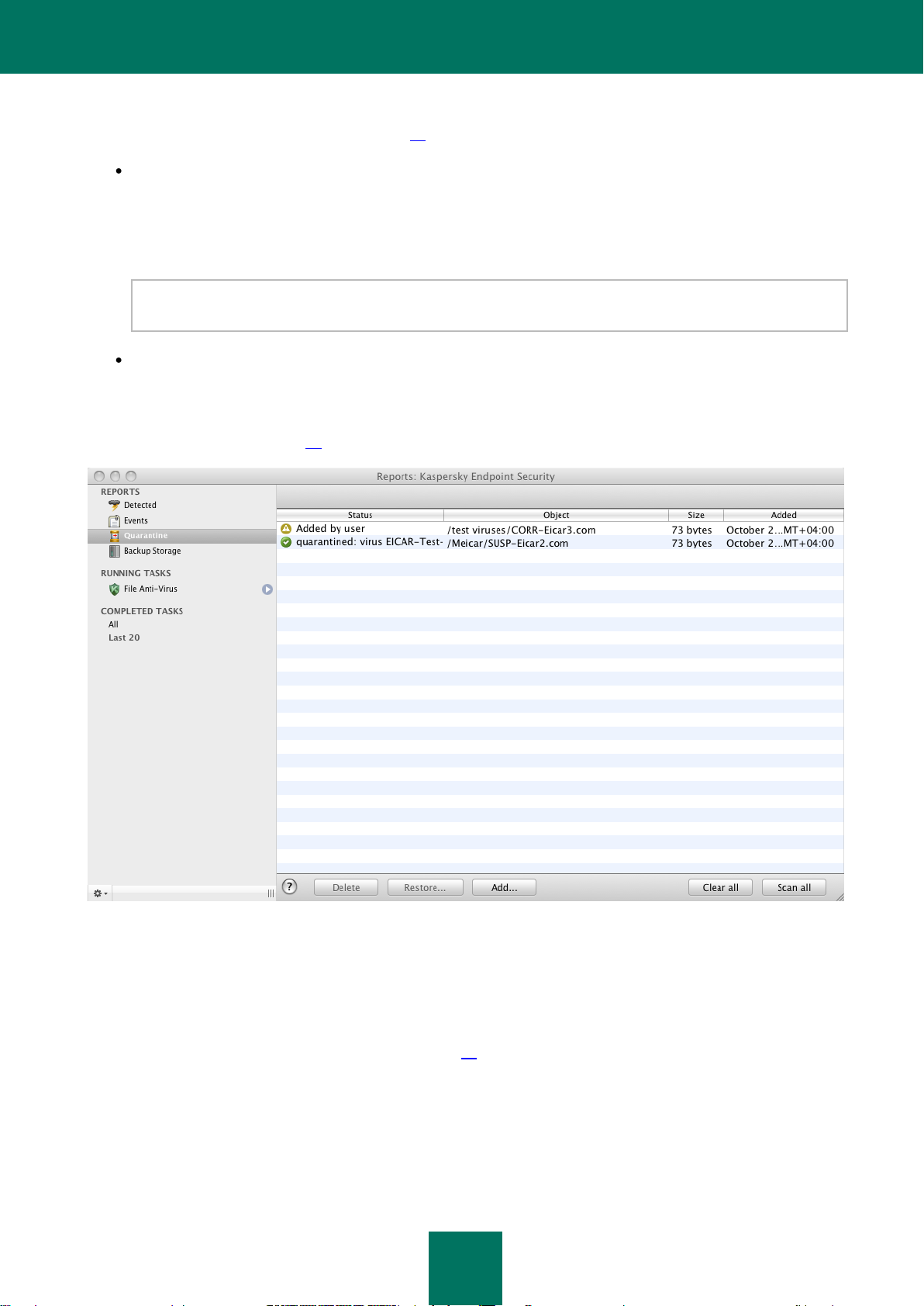
A D V A N C E D A P P L I C A T I O N S E T T I N G S
93
By default, Kaspersky Endpoint Security automatically scans quarantined objects after each update (see section
"Scan of Quarantine after update" on page 93).
Restore files to the folder specified by the user or the folder from which they were moved to Quarantine (by
default).
To restore an object, select it in the Quarantine window (see figure below) and click the Restore button. Confirm
the action. When restoring objects quarantined from archives, mail databases or mail format files, you should
also specify the directory in which they will be restored.
We recommend that you only restore objects with the false positive, OK, and disinfected statuses since
restoring other objects can lead to your computer becoming infected.
Delete any object in Quarantine.
Only delete objects that cannot be disinfected. To delete an object, select one in the Quarantine window
(see figure below) and click the Delete button. To clear Quarantine storage, click the Clear all button. You can
also configure automatic deletion of the oldest objects in Quarantine (see section "Configuring Quarantine and
Backup Storage" on page 99).
Figure 51. Report window. Quarantine
SCAN OF QUARANTINE AFTER UPDATE
Each package of anti-virus database updates contains new records to protect your computer from the most recent
threats. Kaspersky Lab specialists recommend that you scan potentially infected objects stored in Quarantine
immediately after update (see section "Quarantine" on page 91).
Quarantine stores objects whose contents include malware that was not properly identified by File Anti-Virus or during a
virus scan task. After the databases are updated, Kaspersky Endpoint Security will probably be able to clearly identify
and eliminate the threat.
Page 94
A D M I N I S T R A T O R ' S G U I D E
94
By default, Kaspersky Endpoint Security scans quarantined objects after each update. If an object still has the potentially
infected status, it remains in storage. If the status changes to infected, the object is processed according to the selected
action and removed from Quarantine. A copy of it is placed in Backup Storage (on page 94). If the scan has considered
the object as not infected and more than three days have passed since the most recent update of the databases, the
object is restored from Quarantine to its current location. If the databases have been updated within the last three days,
the object remains in storage.
Kaspersky Endpoint Security will not be able to scan quarantined objects immediately after updating the databases if you
are using Quarantine at that moment.
You can disable scan of quarantined objects after each update of the application by unchecking the corresponding box
on the Update tab of the application preferences window.
BACKUP STORAGE
Sometimes it is not possible to save objects in their entirety during the disinfection process. If a disinfected file contained
important information that is partly or completely inaccessible following disinfection, you can attempt to restore the
original object from its backup copy.
Backup copy is a copy of the original dangerous object that is created when first disinfecting or deleting the object, and
saved in Backup Storage.
Backup Storage is a dedicated storage area containing backup copies of dangerous objects that have been processed or deleted. The main function of Backup is the ability to restore an original object at any time. Files in Backup are saved in a special format and are not dangerous for the operating system.
VIEWING THE CONTENTS OF BACKUP
You can view the contents of Backup Storage in the Backup Storage section of the report window (see figure below).
To view the contents of Backup, do the following:
1. Open the main application window (on page 33) and click the button. The Kaspersky Endpoint Security
report window opens.
2. In the left part of the report window, select the Backup Storage section. The contents of Quarantine are
displayed in the right-hand part of the window.
Page 95

A D V A N C E D A P P L I C A T I O N S E T T I N G S
95
The following information is provided for each backup copy: the full name of the object with the path to its
original location, the time when it was moved, the status assigned after the scan, and its size.
Figure 52. Report window. Backup Storage
ACTIONS ON BACKUP COPIES
Kaspersky Endpoint Security allows you to carry out the following actions on backup copies of objects:
Restore selected backup copies from Quarantine.
To do this, in the Backup Storage window (see figure below), select the backup copy of the required object from
the list and click the Restore button. Confirm the action. The object is restored to its original location with its
original name. If there is an object with the same name in the original location (this situation is possible when
restoring an object with a copy created prior to disinfection), a warning will pop up on screen. You can change
the location of the object being restored or rename it.
We recommend that you scan the object for viruses immediately after restoring it. It is possible that the object
will be disinfected using the updated databases without losing its integrity.
We do not recommend that you restore backup copies of objects unless absolutely necessary. This could lead
to an infection on your computer.
Page 96

A D M I N I S T R A T O R ' S G U I D E
96
Delete backup copies of objects in Quarantine.
We recommend that you periodically view Quarantine and clear it. To delete an object, select it in the
Quarantine window (see figure below) and click the Delete button. To clear Backup completely, click the Clear
all button. You can also configure automatic deletion of the oldest objects in Backup Storage (see section
"Configuring Quarantine and Backup Storage" on page 99).
Figure 53. Report window. Backup Storage
REPORTS
Kaspersky Endpoint Security can provide a detailed report on its overall operation with a list of all events that occurred
while it was running. Besides that, a dedicated detailed report will be created for each application component: File AntiVirus (see section "File protection statistics" on page 64), virus scan tasks (see section "Virus scan statistics" on
page 79), and update tasks (see section "Update statistics" on page 89).
Page 97

A D V A N C E D A P P L I C A T I O N S E T T I N G S
97
To open the report window,
open the main application window (on page 33) and click the button.
Figure 54. The Kaspersky Endpoint Security report window.
The report window contains the following sections:
Reports. Statistical information about dangerous objects detected and objects placed in Quarantine and
Backup Storage, and a list of events logged during operation. All statistics are divided into subsections:
Detected. This is a list of all dangerous and suspicious objects detected by File Anti-Virus and virus scan
tasks. To disinfect the dangerous objects immediately, click the Disinfect all button. To remove the records
on detected objects from the report, click the Clear button. Note that this will not remove the dangerous and
suspicious objects from your computer.
Events. List of all events logged during Kaspersky Endpoint Security operation. To delete information from
the list, click the Clear all button.
Quarantine. A list of objects moved to Quarantine (see section "Quarantine" on page 91).
Backup Storage. A list of objects placed in Backup Storage (on page 94).
Running tasks. List of tasks being performed by Kaspersky Endpoint Security at the moment. If no task is
active and File Anti-Virus is disabled, the list will be empty.
Completed tasks. This a list of completed tasks. You may view all completed tasks or the twenty most recent
ones. To clear the list, click the button in the bottom-left corner of the report window and select the Delete
all completed tasks command.
From the report window you can manage the operation of File Anti-Virus, virus scans and update tasks: start and stop
them. To do so, use the corresponding buttons in the component or task report window.
Kaspersky Endpoint Security allows saving the operation report in text format. This may be required if File Anti-Virus or
another task returned a runtime error that cannot be deleted by the user. In such case, you can contact Kaspersky Lab
Page 98

A D M I N I S T R A T O R ' S G U I D E
98
Technical Support Service (see section "Contacting Technical Support Service" on page 153). In this case, you need to
send a text report to Technical Support Service so that our specialists can study the problem in detail and fix it as quickly
as possible.
To export a Kaspersky Endpoint Security operational report to a text file:
1. Select the required report or task in the report window.
2. In the bottom-left corner of the window click the button, select the Export command, and in the window
that opens specify the filename and the folder in which it will be saved.
CONFIGURING REPORTS AND STORAGES
On the Reports tab of the application preferences window (see section "Application preferences window" on page 34),
you can adjust the settings for the creation and storage of reports as well as set the maximum storage time for objects in
Quarantine and Backup Storage.
CONFIGURING THE REPORT SETTINGS
To configure the settings for creating and saving reports, do the following:
1. Open the application preferences window (on page 34) and select the Reports tab (see figure below).
2. In the Reports section, adjust the following settings:
Allow informational events to be logged.
As a rule, these events are not important for security. To log these events in the report, check Log non-
critical events box.
Save only important events in the report that occurred during the most recent task.
This saves disk space by reducing the size of the report. If the Keep only recent events box is checked,
the information in the report will be updated every time you restart the task: in this case important
information (such as records about malicious objects detected) will be saved, and non-critical information
will be overwritten.
Set the storage period for reports.
Page 99

A D V A N C E D A P P L I C A T I O N S E T T I N G S
99
The default storage duration for reports is 30 days. Then the reports will be deleted. You can change the
maximum storage period or remove this restriction.
Figure 55. Application preferences window. Reports
CONFIGURING QUARANTINE AND BACKUP STORAGE
By default, the storage term for objects in Quarantine and Backup is 30 days; when it expires, objects are deleted. You
can change the maximum storage period for objects or remove this restriction at all.
To configure the settings for storing objects, do the following:
1. Open the application preferences window (on page 34) and select the Reports tab (see figure below).
Page 100

A D M I N I S T R A T O R ' S G U I D E
100
2. In the Quarantine and Backup Storage section, check the Delete objects after box and specify the period
after which objects in storage are automatically deleted.
Figure 56. Application preferences window. Reports
 Loading...
Loading...