Page 1

KASPERSKY LAB
Kaspersky® Mail Gateway 5.5
ADMINISTRATOR’S
GUIDE
Page 2

KASPERSKY® MAIL GATEWAY 5.5
Administrator’s Guide
© Kaspersky Lab
http://www.kaspersky.com
Revision date: June, 2006
Page 3

Contents
CHAPTER 1. KASPERSKY® MAIL GATEWAY 5.5....................................................... 7
1.1. What’s new in Kaspersky Mail Gateway 5.5........................................................ 8
1.2. Licensing policy ..................................................................................................... 9
1.3. Hardware and software requirements .................................................................. 9
1.4. Distribution kit ...................................................................................................... 10
1.5. Help desk for registered users ............................................................................ 11
1.6. Conventions......................................................................................................... 11
CHAPTER 2. APPLICATION STRUCTURE AND TYPICAL DEPLOYMENT
SCENARIOS .............................................................................................................. 13
2.1. Application architecture ....................................................................................... 13
2.2. The algorithm of application functioning ............................................................. 15
2.3. Typical deployment scenarios............................................................................. 17
2.3.1. Installing the application along corporate network perimeter ...................... 17
2.3.2. Installing the application inside your mail system........................................ 19
CHAPTER 3. INSTALLING THE APPLICATION......................................................... 21
3.1. Installing the application on a server running Linux ........................................... 21
3.2. Installing the application on a server running FreeBSD..................................... 22
3.3. Installation procedure .......................................................................................... 23
3.4. Configuring the application.................................................................................. 24
3.5. Installing the Webmin module to manage Kaspersky Mail Gateway ................ 26
CHAPTER 4. THE PRINCIPLES OF PROGRAM OPERATION................................ 29
4.1. Creating groups of recipients/senders................................................................ 29
4.2. General message processing algorithm............................................................. 32
4.3. Operation of the Spamtest filter .......................................................................... 35
4.3.1. Message header analysis ............................................................................ 36
4.3.2. Analysis of message content ....................................................................... 36
4.3.3. Spamtest filter actions .................................................................................. 37
4.4. Operation of the AV module................................................................................ 38
CHAPTER 5. ANTI-VIRUS PROTECTION AND SPAM FILTRATION....................... 40
Page 4

4 Kaspersky
®
Mail Gateway 5.5
5.1. Updating the anti-virus and content filtration databases .................................... 40
5.1.1. Automatic updating of the anti-virus and content filtration databases ........ 42
5.1.2. Manual updating of the anti-virus and content filtration databases............. 43
5.1.3. Creating a shared directory for storing and sharing database updates...... 44
5.2. Spam filtration...................................................................................................... 44
5.2.1. Marking of messages containing spam ....................................................... 45
5.2.2. Blocking delivery of spam messages........................................................... 46
5.2.3. Storage of spam message copies in the quarantine directory.................... 46
5.3. Anti-virus protection of email traffic ..................................................................... 47
5.3.1. Delivery of messages with clean or disinfected objects only ...................... 48
5.3.2. Replacement of infected objects with standard notifications....................... 49
5.3.3. Blocking delivery for messages containing suspicious objects................... 49
5.3.4. Delivery of notifications to the sender, administrator and recipients........... 50
5.3.5. Additional filtering of objects by name and type .......................................... 51
5.3.6. Saving messages in the quarantine directory.............................................. 52
5.4. Combining spam filtration and anti-virus protection ...........................................54
5.4.1. Maximum speed ........................................................................................... 54
5.4.2. Recommended mode................................................................................... 55
5.4.3. Maximum protection ..................................................................................... 56
5.5. Additional features of Kaspersky Mail Gateway................................................. 58
5.5.1. Automatically add incoming and outgoing mail to archives ........................ 58
5.5.2. Protection from hacker attacks and spam ................................................... 59
5.6. Managing license keys........................................................................................ 60
5.6.1. Viewing information about license keys....................................................... 60
5.6.2. Renewing your license .................................................................................62
5.6.3. Removing a license key ............................................................................... 63
CHAPTER 6. ADVANCED APPLICATION SETTINGS .............................................. 64
6.1. Configuring anti-virus protection of mail traffic.................................................... 64
6.1.1. Using the iChecker™ technology................................................................. 64
6.1.2. Setting up application timeouts .................................................................... 65
6.1.3. Setting performance restrictions .................................................................. 66
6.2. Setting up connection receiving interfaces ......................................................... 67
6.3. Setting up the routing table ................................................................................. 68
6.4. Checking the configuration file syntax ................................................................ 69
6.5. Syntax check in notification templates................................................................ 70
6.6. Work with email archive and the quarantine directory ....................................... 70
Page 5

Contents 5
6.7. Management of application working queue........................................................ 73
6.8. Managing the application .................................................................................... 75
6.9. Control of application activity............................................................................... 77
6.10. Customizing date and time formats .................................................................. 77
6.11. Reporting options .............................................................................................. 78
6.12. Additional informational header fields in messages......................................... 80
CHAPTER 7. TESTING APPLICATION OPERABILITY ............................................. 81
7.1. Testing the application using Telnet ................................................................... 81
7.2. Testing the Spamtest filter................................................................................... 83
7.3. Testing the application using EICAR ..................................................................84
CHAPTER 8. UNINSTALLING THE APPLICATION ................................................... 86
CHAPTER 9. FREQUENTLY ASKED QUESTIONS................................................... 88
APPENDIX A. SUPPLEMENTARY INFORMATION ABOUT THE PRODUCT......... 95
A.1. Distribution of the application files in directories................................................. 95
A.2. Kaspersky Mail Gateway configuration file ........................................................ 99
A.3. Use of external configuration files..................................................................... 116
A.4. Control signals for the smtpgw component...................................................... 117
A.5. Control files........................................................................................................ 118
A.6. Application statistics.......................................................................................... 118
A.7. Command line options for the smtpgw component ......................................... 124
A.8. Smtpgw return codes........................................................................................ 125
A.9. Command line options for licensemanager ..................................................... 126
A.10. Licensemanager return codes........................................................................ 127
A.11. Keepup2date command line options ............................................................. 128
A.12. Keepup2date return codes ............................................................................. 129
A.13. Format of messages about template syntax check-up.................................. 129
A.14. Return codes for the kltlv utility....................................................................... 131
A.15. Command line options of the klmailq utility.................................................... 132
A.16. Command line options for the klmaila utility................................................... 133
A.17. Return codes for the klmaila and klmailq utilities ........................................... 134
A.18. Special headers added by the Spamtest filter ............................................... 134
A.19. Format of messages about anti-virus scanning and spam filtration.............. 136
A.20. Notifications about actions applied to the message ...................................... 137
Page 6

6 Kaspersky
®
Mail Gateway 5.5
APPENDIX B. KASPERSKY LAB............................................................................... 140
B.1. Other Kaspersky Lab Products ........................................................................ 141
B.2. Contact Us......................................................................................................... 148
APPENDIX C. LICENSE AGREEMENT .................................................................... 150
Page 7

CHAPTER 1. KASPERSKY® MAIL
GATEWAY 5.5
Kaspersky® Mail Gateway 5.5 is designed to filter SMTP mail traffic protecting mail system users from viruses and unwanted messages (spam). The application is a full-featured mail relay (compliant with IETF RFC internet standards) that runs under Linux and FreeBSD operating systems.
The application allows the user to:
• Check email messages for presence of spam signs, including attached
objects and message bodies.
• Use the technology of DNS black lists (RBL) to filter spam.
• Create white lists and black lists of senders/recipients for use by the
application while processing email traffic.
• Scan email messages for viruses, including attached objects and
message bodies.
• Detect infected, suspicious, corrupted, and password-protected
attachments and message bodies.
• Perform anti-virus processing (including disinfection) of infected objects
revealed in email messages by scanning.
• Provide additional email traffic filtering by names and MIME types of
attachments and apply certain processing rules to the filtered objects.
• Maintain archives of all email messages sent and/or received by the
application, if this is required by the internal security policy of the
company.
• Enable restrictions for SMTP connections providing protection against
hacking attacks and preventing application use as an open mail relay for
unsolicited email messages.
• Limit the load on your server by configuring the application settings and
SMTP parameters.
• Notify senders, recipients, and the administrator about messages
containing infected, suspicious, or corrupted objects.
• Quarantine messages identified as spam or probable spam as well as
messages containing infected, suspicious or corrupted objects.
• Update the anti-virus and content filtration databases. The application
retrieves updates from the update servers of Kaspersky Lab. You can
also set the application up to update the databases from a local directory.
Page 8

8 Kaspersky
The application detects and cures infected objects using the anti-virus
database. During scans, the contents of each file are compared to the
sample code of known viruses contained in the database.
Please keep in mind that new viruses appear every day and
therefore we recommend maintaining the anti-virus databases
in an up-to-date state. New updates are made available on
Kaspersky Lab update servers every hour.
The content filtration databases are employed for analysis of message
contents (including Subject and other headers) and attached files. The
application uses to that effect linguistic algorithms based on comparison
with sample messages and search for typical terms (words and word
combinations).
The linguistic laboratory continues to work on improving and
supplementing the corpus of data used for spam detection.
Efficient spam fighting requires regular updating of the
content filtration databases. Updates for the databases are
made available on Kaspersky Lab update servers every 20
minutes.
The keepup2date component serves for updating of the anti-virus and
content filtration databases (see section 5.1 on p. 40).
• Configure and manage Kaspersky Mail Gateway either from a remote
location using Webmin web-based interface, or locally, using standard OS
tools such as command line options, signals, by creating special
command files or by modifying the configuration file of the application.
• Monitor the antivirus protection, and spam filtering status, view the
application statistics and logs both locally and remotely using Webmin
interface.
®
Mail Gateway 5.5
1.1. What’s new in Kaspersky Mail
Gateway 5.5
Kaspersky Mail Gateway has been enhanced with the following additional
features as compared with Kaspersky SMTP-Gateway 5.5:
• Checking email traffic for spam presence using the content filtration
databases with an opportunity to specify the degree of filtering intensity.
• Marking of messages identified as spam or probable spam using special
headers including an opportunity to use different methods with various
groups of senders/recipients.
Page 9

9
• Storage of messages identified as spam or probable spam in the
quarantine directory.
• Blocking of delivery to recipients for messages identified as spam or
probable spam.
1.2. Licensing policy
The licensing policy for Kaspersky Mail Gateway includes a system of product
use limitations based on the following criteria:
• Number of users protected by the application
• Email traffic processed daily (MB/day).
Each type of licensing is also limited by a certain period (typically one year or two
years after the date of purchase).
You can purchase a license limited by one of the above criteria (for example, by
the daily mail traffic volume).
In addition, you can define during product purchase whether your Kaspersky Mail
Gateway will only perform anti-virus scanning of email traffic or it will also filter
spam.
The application has slightly different configuration parameters, depending on the
type of license you have purchased. Thus, if the license is issued for a certain
number of users, you will have to create a list of addresses (domains) that will
be protected by the application against viruses and spam The application will
notify the administrator when the traffic volume reaches critical values or the
number of protected accounts is exceeded.
1.3. Hardware and software
requirements
Minimum system requirements for normal operation of Kaspersky Mail Gateway
are as follows:
• Intel Pentium
• At least 256 МB of available RAM
• At least 100 MB of available space on your hard drive to install the
application.
®
processor (Pentium III or Pentium IV recommended).
Please note that the application working queue, quarantine
directory, and archives of incoming and outgoing email are
not included in the hard disk space required. If your network
Page 10
10 Kaspersky
security policy requires the use of the above features,
additional disk space will be needed.
• at least 500 MB of available space in the /tmp file system.
• One of the following operating systems:
• Red Hat Enterprise Linux Advanced Server 4.
• Red Hat Linux 9.0.
• Fedora Core 4.
• SuSE Linux Enterprise Server 9.0 (SP3).
• SuSE Linux Professional 10.0.
• Debian GNU/Linux 3.1r1.
• Mandriva 2006.
• FreeBSD 4.11, 5.4, 6.0.
• Perl interpreter, version 5.0 or higher (www.perl.org
) and the which utility
to install the application.
• Webmin version 1.070 or higher (www.webmin.com
) to install the remote
administration module (optional.
1.4. Distribution kit
®
Mail Gateway 5.5
You can purchase the product either from our dealers (retail box) or at one of our
online stores (for example, www.kaspersky.com
– follow the E-store link).
The retail box contains:
• sealed envelope containing the installation CD with the product
• a copy of this Administrator’s Guide
• license key file bundled with the distribution package or recorded to a
special floppy disk
• License Agreement.
Before you unseal the envelope containing the CD, make sure you
have carefully read the License Agreement .
If you purchase our application online, you will download it from Kaspersky Lab's
website; the copy also contains this manual. Your license key is either included
in the installation package or will be sent to you by email after payment.
Page 11
11
The License Agreement constitutes a legal agreement between you and
Kaspersky Lab containing the terms and conditions under which you may use the
purchased software.
Please review the License Agreement carefully!
If you do not agree to the terms of the License Agreement, you may return the
box containing Kaspersky Mail Gateway to your dealer where you have
purchased it for a full refund provided that the envelope with the installation CD
has not been unsealed.
By opening the sealed envelope containing the installation CD, or by installing
the application, you confirm that you have accepted all the terms and conditions
of the License Agreement.
1.5. Help desk for registered users
Kaspersky Lab offers an extensive service package enabling registered
customers to boost the productivity of Kaspersky Mail Gateway.
If you purchase a subscription you will be provided with the following services for
the period of your subscription:
• new versions of this software product provided free of charge
• phone or email support on matters related to the installation,
configuration, and operation of the product you have purchased
• notifications about new software products from Kaspersky Lab, and about
new virus outbreaks. This service is provided to users who have
subscribed to the Kaspersky Lab email newsletter service.
Kaspersky Lab does not give advice on the performance and use of
your operating system or other technologies.
1.6. Conventions
Various formatting conventions are used throughout the text of this document
depending on the purpose of a particular element. Table 1 below lists the
formatting conventions used.
Page 12
12 Kaspersky
Table 1. Conventions
Style Meaning
®
Mail Gateway 5.5
Bold type
Note.
Attention!
In order to perform the
action,
1. Step 1.
2. …
Task, example
Solution
[key] – key purpose.
Text of information
messages and the command
line
Menu titles, menu items, window titles,
parts of dialog boxes, etc.
Additional information, notes.
Information requiring special attention.
Procedure description for user's steps
and possible actions.
Statement of a problem, example for
using the software features.
Solution to a defined problem.
Command line keys.
Text of configuration files, information
messages and the command line.
Page 13

CHAPTER 2. APPLICATION
STRUCTURE AND TYPICAL
DEPLOYMENT SCENARIOS
Correct application setup and its efficient operation require knowledge of its
structure and internal algorithms. It is also important for application deployment
within an existing corporate email system. This chapter contains a detailed
discussion of the application’s structure, architecture and operating principles as
well as typical scenarios of its deployment.
2.1. Application architecture
The review of the application functionality must be preceded by a description of
its internal architecture.
Kaspersky Mail Gateway is a full-featured Mail Transfer Agent (MTA) able to
receive and route email traffic scanning email messages for viruses and filtering
spam.
Kaspersky Mail Gateway uses SMTP protocol commands (RFC 2821), Internet
message format (RFC 2822), MIME format (RFC 2045-2049, 2231, 2646), and
satisfies the requirements to mail relays (RFC 1123). In compliance with antispam recommendations (RFC 2505 standard), the application employs access
control rules for SMTP clients to prevent the use of this application as an open
relay. In addition, Kaspersky Mail Gateway supports the following SMTP protocol
extensions:
• Pipelining – enhances performance of servers supporting this mode of
operation (RFC 2920).
• 8-bit MIME Transport – processes national language characters code
tables (RFC 1652).
• Enhanced Error Codes – provides more informative explanations of
protocol errors (RFC 2034).
• DSN (Delivery Status Notifications) – decreases bandwidth usage and
provides more reliable diagnostics (RFC 1891, 3461-3464).
• SMTP Message Size – Decreases the load and increases transfer rate
(RFC 1870).
Page 14
14 Kaspersky
®
Mail Gateway 5.5
RFC documents mentioned above are available at:
http://www.ietf.org.
The application includes the following components:
• smtpgw – the main component – a full-featured mail relay with built-in
anti-virus protection and spam filtering.
• licensemanager – component for managing license keys (installation,
removal, viewing statistics).
• keepup2date – component that updates the anti-virus and content
filtration databases by downloading the updates from the Kaspersky Lab’s
update servers or a local directory.
• Webmin module for remote administration of the application using a
web-based interface (optional installation). This component allows the
user to configure and manage the anti-virus and content filtration
databases updates, specify actions to be performed on the objects
depending on their status and monitor the results of the application’s
operation.
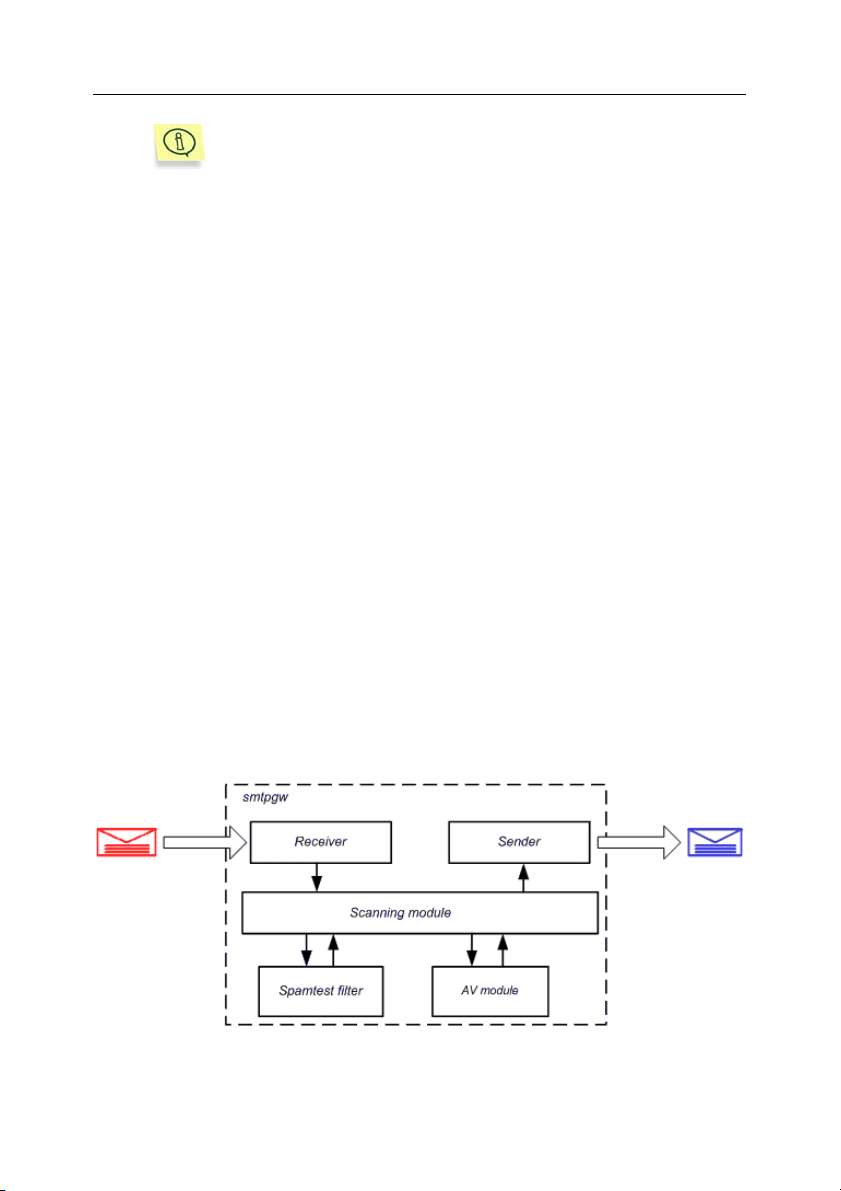
The smtpgw component (see Fig.1), in its turn, consists of the following modules:
• Receiver (incoming mail receiver).
• Sender (module for sending scanned messages, which have passed anti-
virus scanning and spam filtering).
• Spamtest filter (module filtering spam messages).
• AV module (the anti-virus engine).
• Scanning module, which acts in combination with the Spamtest filter and
AV module to process messages, including anti-virus scanning and spam
filtering of mail traffic.
Figure 1. General architecture of Kaspersky Mail Gateway
Page 15
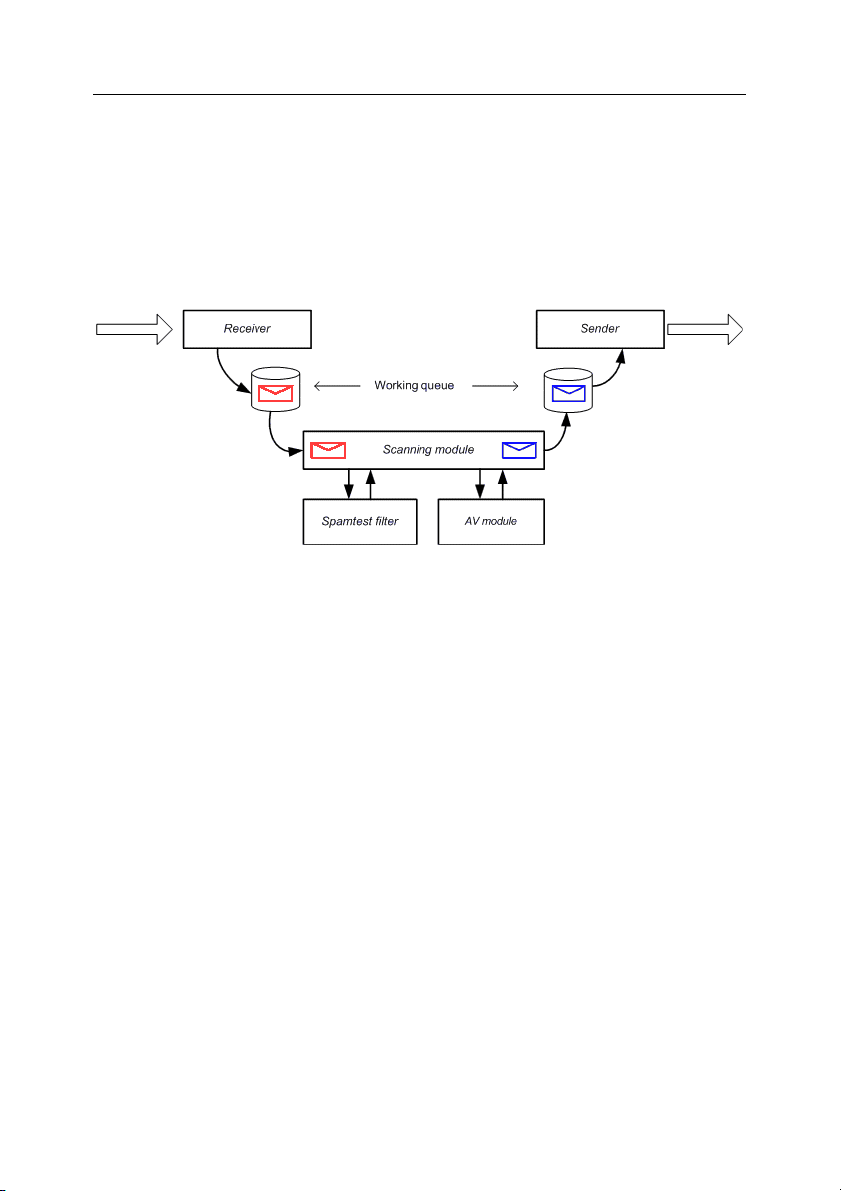
Application structure and typical deployment scenarios 15
2.2. The algorithm of application
functioning
The application works as follows (see Fig. 2):
1. The mail agent receives email messages via the SMTP protocol and
passes them to the Receiver module.
Figure 2. Working queue of Kaspersky Mail Gateway
2. The Receiver module performs preliminary email processing using the
following criteria:
• presence of the sender’s IP address in the list of blocked and/or
trusted addresses including masks;
• compliance with the access restrictions specified for SMTP
connections (see section 5.5.2 on p. 59);
• compliance of the email message size (as well as the mail
session in general and the total number of messages within the
session) with the limits specified in the application settings;
• compliance of the number of open sessions (both from all IP
addresses and a single IP address) with the limits specified in
the application settings.
If the message satisfies the preliminary processing requirements, it is
sent to the working queue to be processed by the scanning module.
If all incoming mail should be archived, a copy of any message added to
the working queue will be automatically preserved in the archive of
received messages.
3. The scanning module receives a message from the working queue and
transfers it to the Spamtest filter for inspection. The filter assigns to it a
Page 16

16 Kaspersky
®
Mail Gateway 5.5
specific status and returns the message to the scanning module, which
then breaks it into individual components and passes them to the AV
module for analysis.
If you have only purchased a license for anti-virus scanning of
email traffic, spam filtering will not be performed. Messages
will be immediately delivered to the AV module for analysis.
The application will ignore then configuration parameters,
which apply to the Spamtest filter.
4. The AV module scans the objects and, if this option is enabled,
disinfects them, when necessary.
5. The scanning module handles messages according to the status (see
section 4.2 on p. 32) assigned to each object or message during
analysis by the Spamtest filter and the AV module (blocks message
delivery, deletes infected objects, modifies message headers, adds
messages to the quarantine directory, etc.). The actions to be applied
are defined in the application configuration file. Each processed
message is then added to the ready-to-send message queue.
6. If saving in the quarantine is specified as the action to be performed on
a message, a copy of the scanned message will be saved in the
quarantine directory concurrently with its transfer to the ready-to-send
queue. The application creates a separate quarantine directory for
messages identified as spam or probable spam and messages
containing infected, suspicious or corrupted objects.
Creation of message copy in backup storage or quarantine
directory does not block delivery of the original message to
the recipient. An additional action blocking its delivery has to
be specified, if you want to prevent message delivery to the
recipient.
7. The Sender module receives each message from the ready-to-send
queue and transfers it via the SMTP protocol to the onward mail agent
to be delivered to local end users or rerouted to other mail servers.
8. If your network security policy requires logging of all outgoing email
traffic, a copy of each message will be automatically saved after its
delivery to the archive of sent messages (see Fig. 3).
Page 17
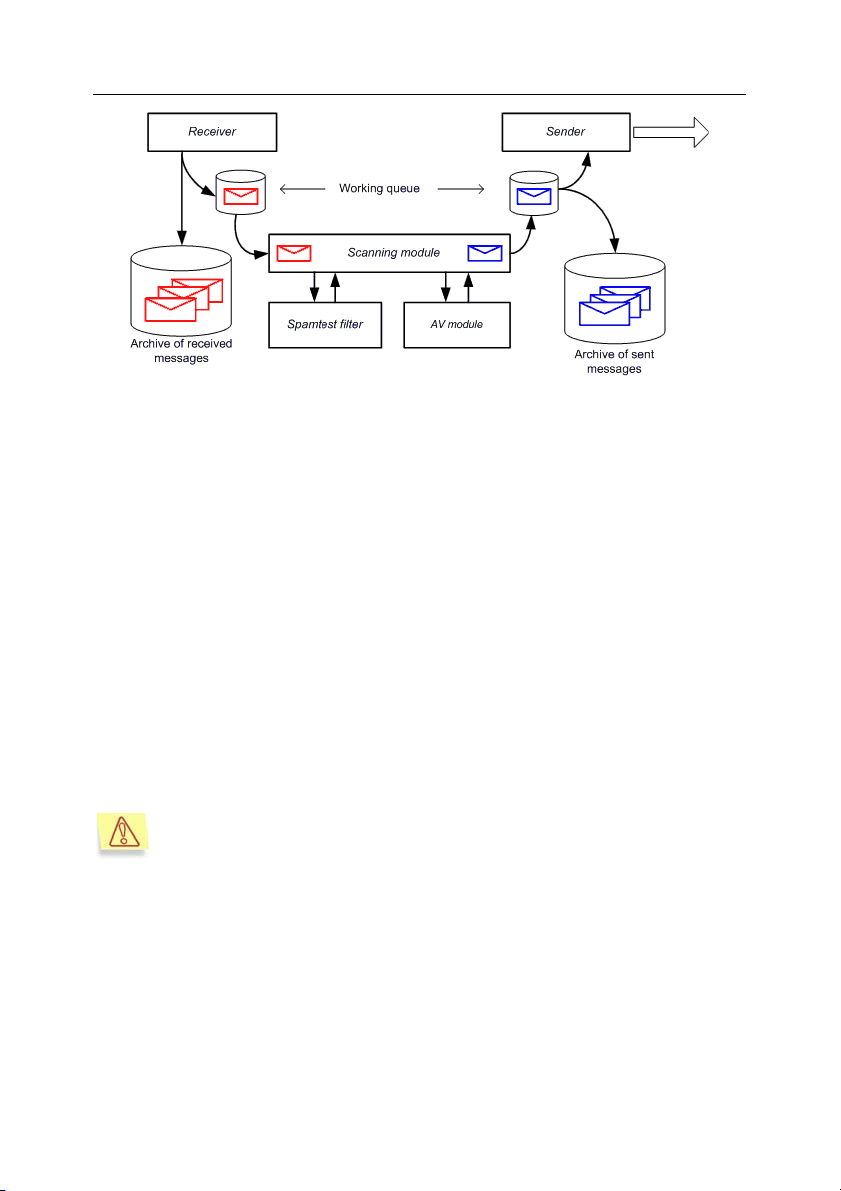
Application structure and typical deployment scenarios 17
Figure 3. Saving messages to the archives of received / sent messages
2.3. Typical deployment scenarios
Depending upon the network architecture, the following options for installation of
Kaspersky Mail Gateway are possible:
• install the application along corporate network perimeter in the
demilitarized zone (DMZ) acting as a buffer between internal corporate
LAN and external network);
• install the application inside your existing mail system.
In each of the above cases the application can be installed:
• to the same server with a running email system;
• to a dedicated server.
The sections below discuss in detail the above scenarios and describe their
advantages.
The application, being a mail relay, does not include a local mail
delivery agent (MDA). Therefore, no matter which of the deployment
scenarios is used, a mail system (or mail systems) that delivers email
messages to the local users within the protected domains is required!
2.3.1. Installing the application along
corporate network perimeter
The main advantage of this option is that it improves the overall performance of
your mail system because it minimizes the number of transfer cycles for email
messages.
Page 18
18 Kaspersky
®
Mail Gateway 5.5
In this case the existing corporate mail server has no connection to the Internet;
that means additional protection of your data. Moreover, demilitarized zones
(DMZ) may be set up.
To install the application and the mail system on the same server, the following
algorithm is provided to ensure their joint operation:
1. Configure all interfaces of Kaspersky Mail Gateway to listen on port
25 for incoming email traffic from all IP addresses matching the
relevant MX records for the protected domain.
2. The application filters spam and scans email. Then it transfers the
processed messages to the corporate mail system via a different
port (e.g., 1025).
You have to set up restrictions for the mail transfer agent
(MTA) receiving mail from Kaspersky Mail Gateway via port
1025 so that it accepts messages exclusively from Kaspersky
Mail Gateway. Otherwise, there will be an opportunity to
bypass the protection with a connection established directly
from external network through port 1025.
3. The mail system, configured to use a local interface, will deliver
messages to users.
The following steps are to be followed in order to install the application
and the mail system on the same server:
• Configure the application for mail receipt via port 25 on all network
interfaces of the server. In order to do this, specify the following value in
the [smtpgw.network] section of the configuration file:
ListenOn=0.0.0.0:25
• Specify in the routing table transfer of all scanned messages to the mail
system via port 1025. In order to do this, specify the following value in the
[smtpgw.forward] section of the application configuration file:
ForwardRoute=*@company.com [host:1025]
where: *@company.com is the mask for recipient addresses
host – name of the your corporate mail server.
• Change the settings of the existing mail system for receiving messages
from the application via port 1025. This will ensure receipt of all incoming
mail messages and delivery of these messages to the local users within
the protected domains of the company.
• Set up the existing mail system to transfer all messages it receives to the
application via port 25. This will ensure anti-virus scanning and antispam
filtering of all outgoing mail messages from the local users.
Page 19

Application structure and typical deployment scenarios 19
• Specify the list of all corporate local domains as a value for the
ProtectedDomains option in the [smtpgw.forward] section of the
application configuration file ("*" and "?" wildcards can be used). Mail
messages for the specified domains will be scanned.
Application configuration for this deployment scenario will be
implemented by default during the installation process.
The operation algorithm of the application, when the latter is installed on a
dedicated server, is identical to its operation on the same server with an email
system, but the settings for this scenario will differ. IP address of the server,
where the application is installed must be included in MX records corresponding
to the protected domain.
In order to install the application on a dedicated server:
• Configure the application for mail receipt via port 25 on all network
interfaces of the server. In order to do this, specify the following value in
the [smtpgw.network] section of the application configuration file:
ListenOn=0.0.0.0:25
• Specify in the routing table transfer of all scanned messages to the mail
system via port 25. In order to do this, specify the following value in the
[smtpgw.forward] section of the application configuration file:
ForwardRoute=*@company.com [host:25]
where: *@company.com is the mask for recipient addresses
host – name of the your corporate mail server.
• Specify the list of all corporate local domains as a value for the
ProtectedDomains option in the [smtpgw.network] section of the
application configuration file ("*" and "?" wildcards can be used). Mail
messages for the specified domains will be scanned.
This deployment scenario is the most convenient one, especially if the
installation of Kaspersky Mail Gateway is performed at the same time
with the deployment of the network and of the company’s mail system.
2.3.2. Installing the application inside your
mail system
If the application is installed inside your mail system, there is no access from
outside to the information about the application running on the server and its
Page 20

20 Kaspersky
®
Mail Gateway 5.5
configuration. Besides, if the application is installed inside the mail system on a
dedicated server, this provides for the possibility to distribute the load among
several servers performing anti-virus scanning.
The following algorithm is provided for joint operation of the application and the
mail system installed on the same server:
1. Duplicate your mail system and configure one of the copies to listen
on port 25 and receive email messages via all available interfaces.
2. This mail system forwards all incoming messages through the local
interface via a different port (port 1025, for instance) to the
application for scanning and spam filtering.
3. The application filters spam, scans the email messages for viruses
and forwards scanned and processed messages to the second mail
system copy, which receives mail on a different port (e.g., port
1026).
4. The second mail system delivers email to the local users.
This deployment scenario is recommended if you are sure of the
reliability of your mail system. The installation of the application will not
affect the stability of your mail system.
Application setup on a dedicated server is similar to the above procedure.
Besides, when installing the application on a dedicated server, you can create
and run several copies of the application on different servers. This can help you
distribute the anti-virus processing and spam filtering load among several
servers.
To implement this scenario of application deployment:
Specify the list of all corporate local domains as a value for the
ProtectedDomains option in the [smtpgw.network] section of the
application configuration file ("*" and "?" wildcards can be used). Mail
messages for the specified domains will be scanned.
Deploying Kaspersky Mail Gateway may require changes of the settings
for the mail clients throughout the company so that all outgoing mail
messages are delivered to the application, which will transfer the
messages to the external network after an anti-virus scan and spam
filtration.
If the network includes installed firewalls or demilitarized zones
(DMZ’s), it is necessary to provide mail clients and internal and external
networks servers with access to the installed application to ensure joint
operation and routing of the mail traffic.
Page 21

CHAPTER 3. INSTALLING THE
APPLICATION
Before installing Kaspersky Mail Gateway, it is necessary to:
• Make sure that your system meets the hardware and software
requirements (see section 1.3 on p. 9).
• Configure your Internet connection. The application distribution package
does not contain the anti-virus and content filtration databases required to
perform anti-virus protection and filter spam.
• Log on to the system as root or as a privileged user.
3.1. Installing the application on a
server running Linux
For servers running the Linux operating system, Kaspersky Mail Gateway is
distributed in three different installation packages, depending on the type of your
Linux distribution.
You can use an rpm package to install the application under Red Hat Linux and
SuSE Linux.
To initiate installation of Kaspersky Mail Gateway from the rpm
package, enter the following in the command line:
# rpm –i scm-smtpgw-linux-<version_number>.i386.rpm
If you are installing the application from the rpm package, after the files
have been copied to your server, run the postinstall.pl script to perform
post-installation configuration. By default the postinstall.pl script is
located in the /opt/kav/5.5/scm-smtpgw/setup/ directory.
In Debian Linux, the installation is performed from a deb package.
To initiate installation of Kaspersky Mail Gateway from the deb
package, enter the following command in the command line:
# dpkg –i scm-smtpgw-linux-<version_number>.deb
After you enter the command, the application will be installed automatically.
Page 22

22 Kaspersky
You can also use a universal distribution file for all Linux OS. Use this distribution
file if your Linux version does not support the rpm or deb formats or if your
administrator does not wish to use (or cannot use) a built-in package manager.
The universal Kaspersky Mail Gateway distribution file is supplied as an archive
(tar.gz).
To initiate installation of Kaspersky Mail Gateway from the universal
distribution file, do the following:
1. Copy the archive of the distribution file to a directory within the file
system of your server.
2. Extract the archive using the following command:
# tar zxvf scm-smtpgw-linux-<version_number>.tar.gz
The archive contains the installer and the file tree of the application
files that will be extracted by the above command.
3. Run the following installation script:
# cd <package_directory>
# ./install.sh
After you enter the command, the application will be installed automatically.
The procedure of application setup under Mandriva 2006 distributions
has some peculiarities. You might have to perform some additional
actions to ensure correct functioning of the application in such systems
(please see Chapter 9 on p. 88 for details).
®
Mail Gateway 5.5
3.2. Installing the application on a
server running FreeBSD
The distribution file for installation of Kaspersky Mail Gateway on servers running
FreeBSD OS is supplied as a pkg package.
To initiate installation of Kaspersky Mail Gateway from a pkg package,
enter the following in the command line, depending upon the version of
your FreeBSD distribution:
# pkg_add scm-smtpgw-freebsd-4.x-<version_number>.tgz
or:
# pkg_add scm-smtpgw-freebsd-5.x-<version_number>.tgz
or:
# pkg_add scm-smtpgw-freebsd6.x-<version_number>.tgz
Page 23

Installing the application 23
After you enter the command, the application will be installed automatically.
In order to function correctly in FreeBSD 5.x and 6.x distributions, the
Spamtest filter needs the following line in the configuration file of the
working kernel:
options COMPAT_FREEBSD4
3.3. Installation procedure
Installation errors can occur for a number of reasons. If an error
message is displayed, make sure that your computer satisfies the
hardware and software requirements (see section 1.3 on p. 9) and that
you have logged into the system as a root.
To install the application on the server, follow the steps below:
Step 1. Preparing the system
At this stage, the system creates the system group and user account for the
application. The default group is kavusers and the default user account is
kavuser. In future, the application will start under this user account (not root) to
provide additional security for your system.
Step 2. Copying application files to destination directories
on your server
The installer starts copying the application files to the destination directories on
your server. For a detailed description of the directories where the application
files will be copied, see section A.1 on p. 95.
If you installed the application from an rpm package, then you should
run the postinstall.pl script (present by default in the /opt/kav/5.5/scm-
smtpgw/setup/ directory) to perform the following steps.
Step 3. Post-installation tasks
The post-installation configuration includes the following steps:
• Configuring the smtpgw component (see section 3.4 on p. 24).
• Installing and registering the license key.
If you have no license key at the time of installation (for example, if you
purchased the application via the Internet and have not received the
Page 24

24 Kaspersky
®
Mail Gateway 5.5
license key yet), you can activate the application after installation before
its first use. For details see section 5.6 on p. 60. Please note that if the
license key is not installed, the anti-virus and content filtration databases
cannot be updated and the smtpgw component cannot be started during
the installation process. You will have to do it manually, after the key is
installed.
• Configuring the keepup2date component.
• Installation (updating) of the anti-virus and content filtering databases.
You must install the anti-virus and content filtration databases
before using the application. The procedure of detecting and
disinfecting viruses relies on the use of the anti-virus database
records that contain description of viruses known at the moment
and the methods of disinfecting these viruses. Anti-virus scanning
and processing of email messages cannot be performed without
the anti-virus database.
The application employs its content filtering database for spam
detection (analysis of message contents and attached files used to
identify the signs of unsolicited mail).
• Installing the Webmin module.
The Webmin module for remote management of the application can be
installed correctly only if the Webmin application is located in the default
directory. After the module is installed, you will receive detailed
instructions on how to configure it to work with the application.
• Launching the smtpgw component.
If, after installation, Kaspersky Mail Gateway has not started working as
required, check the configuration settings. Pay special attention to the
port number you specified for receiving mail traffic. You may also view
the application log file.
After you properly complete these steps, a corresponding message on the server
console will appear as soon as the installation procedure is over.
3.4. Configuring the application
Immediately after the files have been copied to your server, system configuration
process will start. Depending on the package manager you use, the configuration
process will either be started automatically or (if the package manager does not
allow the use of interactive scripts, such as rpm), some additional actions will
have to be performed by the administrator. All settings are stored in the
smtpgw.conf file installed by default in the /etc/kav/5.5/scm-smtpgw/ directory.
Page 25

Installing the application 25
If you are using the rpm installation package, enter the following
command to start configuration after the files are copied to your server:
# /opt/kav/5.5/scm-smtpgw/setup/postinstall.pl
The configuration procedure includes the following tasks:
• Setting up (by the administrator) of the server name that will be used to
identify the application in the SMTP commands when creating the DSN
and notifications (the Hostname parameter in the [smtpgw.network]
section of the smtpgw.conf configuration file). Full domain name of the
server must be specified as the parameter value.
• Setting up the domain name that will be used to:
• Assign the Postmaster address ([smtpgw.network] section,
Postmaster parameter)
• Assign the sender’s return address for notifications
([smtpgw.policy] section, NotifyFromAdress parameter)
• Define the administrator’s address ([smtpgw.policy] section,
AdminNotifyAddress parameter)
• Allow incoming mail to this domain ([smtpgw.options] section,
RelayRule parameter).
• Defining the interface and port to listen to the incoming email traffic
([smtpgw.network] section, ListenOn parameter). Type the port name
and the IP address in the <x.x.x.x:z> format, where:
x.x.x.x is the IP address, and
z is the port number.
• Specifying local network identifiers ([smtpgw.access] section,
RelayRule parameter). This value is used to assign rules for message
delivery and processing, for example, rules specific for your organization
concerning mail processing, or blocking email messages from certain
domains, etc. Specify the values using the following formats: <x.x.x.x>
or <x.x.x.x/y.y.y.y>, or <x.x.x.x/y>,where:
x.x.x.x is the IP address, and
y.y.y.y or y is the subnet mask.
• Specifying (when necessary) the server to which all processed messages
will be forwarded ([smtpgw.forward] section, the ForwardRoute
parameter). Type the host name in the format: <x.x.x.x:z>, where:
x.x.x.x is the IP address, and
z is the port number.
Page 26

26 Kaspersky
• Specifying the proxy server name ([updater.options] section,
ProxyAddress parameter). This option is necessary for computers
connected to the Internet via a proxy server.
• Modifying the application configuration file to fine-tune the operation of the
AV module and the Spamtest filter (optional).
If all the above steps have been successfully completed, the configuration file will
contain all settings that are required to start working with the application.
After the system is installed and configured, it is recommended that you
check the settings for Kaspersky Mail Gateway and test its
performance. For more details, see Chapter 7 on page 81.
®
Mail Gateway 5.5
3.5. Installing the Webmin module to
manage Kaspersky Mail
Gateway
The activity of Kaspersky Mail Gateway can be controlled remotely via a web
browser using Webmin.
Webmin is a program, which simplifies administration of Linux/Unix systems. The
software is based on modular structure and supports connection of new modules
as well as development of your own customized ones. You can obtain additional
information about Webmin and download its distribution package from the official
program web site at: www.webmin.com.
The distribution package of Kaspersky Mail Gateway includes a Webmin module
that you can either connect during application setup following its installation (see
section 3.3 on p. 23) if your system already has Webmin installed, or at any time
later as soon as you install Webmin.
The following part of this manual contains a detailed description of the procedure
necessary to connect the Webmin module for administration of Kaspersky Mail
Gateway.
If the default settings have been used during Webmin installation, then you can
access the program from your web browser using HTTP / HTTPS to connect to
port 10000 as soon as the installation procedure is finished.
Page 27
Installing the application 27
In order to install the Webmin module to control Kaspersky Mail
Gateway:
1. Use your web browser to access Webmin with the privileges of its
administrator.
2. Select the Webmin Configuration tab in the program menu, and
then proceed to the Webmin Modules section.
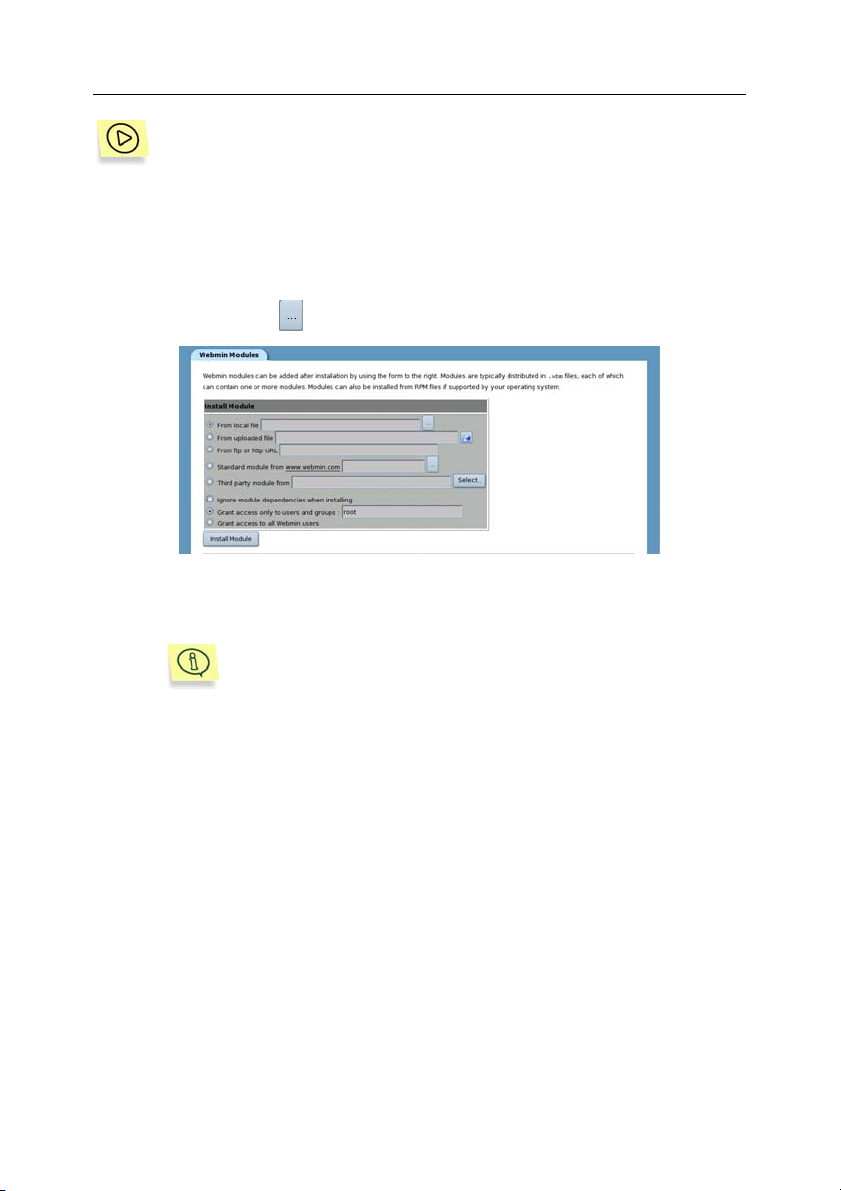
3. Select the From Local File option in the Install Module section
and click (see Figure 4).
Figure 4. Install Module section
4. Enter the path to the Webmin module of the product and click ОК.
Webmin module is located in the scm-smtpgw.wbm file
installed by default to the /opt/kav/5.5/scm-smtpgw/setup/
directory (in Linux distributions) or the
/usr/local/share/kav/5.5/scm-smtpgw/setup directory (for
FreeBSD distributions).
If the Webmin module is installed successfully, you will see a corresponding
message on the display.
You can access the settings of Kaspersky Mail Gateway by clicking its icon
within the Others tab (see Figure 5).
Page 28
28 Kaspersky
Figure 5. The icon of Kaspersky Mail Gateway in the Others tab
®
Mail Gateway 5.5
Page 29

CHAPTER 4. THE PRINCIPLES
OF PROGRAM OPERATION
This chapter contains information necessary for better understanding of the
algorithm of application functioning and interaction between its components as
well as information required for correct software setup.
4.1. Creating groups of
recipients/senders
Recipients/Senders group is defined as pairs of recipient/sender email
addresses. A particular email message may be assigned to a particular group
depending on whether this group contains the sender’s or the recipient’s address
present in the MAIL FROM and RCPT TO commands.
The administrator can specify individual rules for processing of each mail
message depending on the group of recipients/senders. Therefore, it is
particularly important that the addresses must be associated with a correct
group.
While processing a message, the application searches through the list of
addresses for each specific group. If it finds a matching combination of the
sender/recipient addresses, the rules defined for this group will be applied to the
email message.
The anti-virus and spam filtering functionality of Kaspersky Mail
Gateway depends on the configuration file settings. You can make
configuration changes to the file either locally or remotely (using the
Webmin remote administration module).
The configuration file contains the [smtpgw.policy] section that implicitly defines
the policy group, which determines the default rules for processing of email
messages.
All parameters specified in that section and the section itself are
mandatory.
The [smtpgw.policy] section does not contain the names of senders and
recipients. Rules defined in [smtpgw.policy] are applied to all messages, except
for those belonging to other groups explicitly described as
[smtpgw.group:group_name] sections.
Page 30
30 Kaspersky
®
Mail Gateway 5.5
All parameters in [smtpgw.group:group_name] sections are optional. If a
parameter value in such section is not specified, it will be taken from an identical
option in the [smtpgw.policy] section.
If the configuration file included into the application installation package is used,
then the mail messages will be processed according to the following rules
(defined by the policy group):
• Check all mail messages for presence of spam signs.
• Modify the Subject field for messages identified as spam or probable
• Scan all mail messages for viruses.
• Deliver to the recipients messages containing clean or disinfected objects
spam
1
.
only.
• Infected objects and objects, which caused errors during their analysis,
must be removed from messages as well as suspicious, passwordprotected and damaged objects.
• Notify recipients and the administrator about infected, suspicious,
corrupted, protected or filtered objects in messages and the objects,
which caused errors during their analysis.
You can change the parameters of the policy group or create new groups. If you
would like to process email messages belonging to different groups of
recipients/senders using different rules, you will have to create several groups.
To create a new group of user addresses,
1. Create section [smtpgw.group:group_name] in the configuration
file.
2. Specify sender and recipient addresses as the values of Senders
and Recipients parameters (masks of addresses). In order to
define several addresses or address masks, use the following
construction:
Senders=user1@example.com
Senders=*@internal.local
1
A special label is added to the Subject field depending upon the status and identified
content category. Please see section 4.3.3 on page 37 for details.
Page 31

Anti-virus protection and spam filtration 31
Recipients=*@management.local
Recipients=help@helpdesk.local
"*" and "?" wildcards may be used for definition of masks. If a group
description contains no Recipients or Senders parameter, then the
application will use instead the default value: "
*@*". At least one of
the Senders or Recipients parameters must be specified.
If you leave the Senders or Recipients parameter in a
group description empty, e.g.:
Senders=
then no messages will be processed using the rules
specified for that group. If you wish to use the default
value, delete the respective parameter from group
description.
If you have added other groups to the configuration file, the application will
process messages from these groups as follows:
1. The application first compares the message address(es) with
addresses in the groups created by the administrator. If the
recipient/senders addresses pair is found in a specific group, the
rules defined for that group will be applied to the message.
If a sender/recipient address fits the address ranges of
several groups, the application will use the rules for the
first of those groups.
2. If the message addresses do not match any group, created by the
administrator, the message will be processed according to the rules
described in the policy group.
If a message has several recipients belonging to different
groups, virtual copies of the initial message will be created
to match the number of such groups. Each copy will be
processed individually according to the rules specified by
the particular group.
Figure 6 demonstrates the sequence of actions applied by Kaspersky Mail
Gateway to a received email message.
Page 32

32 Kaspersky
®
Mail Gateway 5.5
Figure 6. Message processing
4.2. General message processing
algorithm
In this section, we shall examine how the application processes email messages.
When the server receives an email message, the scanning module:
1. Determines the group of recipients this message belongs to.
Page 33

Anti-virus protection and spam filtration 33
2. If the message has multiple recipients belonging to different groups,
before its further processing with a Spamtest filter and anti-virus
scanning, the application creates several virtual copies of this message to
match the number of groups and applies respective group rules to each of
such copies.
3. Then the application transfers the message for analysis by the Spamtest
filter.
If you have only purchased a license for anti-virus scanning of
email traffic, spam filtering will not be performed. Messages
will be immediately delivered to the AV module for analysis
(Step 4). The application will ignore then configuration
parameters, which apply to the Spamtest filter.
During the process the filter assigns to the message one of the following
statuses:
• Spam – message identified as spam.
• Probable Spam – the message is very likely to be spam but
detected signs of unsolicited email do not allow stating that with
sufficient confidence.
• Not detected – the message has no signs sufficient to assign
the SPAM or Probable Spam status to it.
The information about the status assigned to a message is recorded in a
special X-SpamTest-Status header appended to that message after
processing. Moreover, the Spamtest filter may append the following
additional headers to a message:
• X-SpamTest-Method.
• X-SpamTest-Info.
• X-SpamTest-Categories.
• Keywords.
Please see section A.18 on p. 134 for a detailed description of the above
headers.
The Spamtest filter may also modify the Subject header adding a label
corresponding to the message status and the category assigned to it (see
section 4.3.3 on p. 37).
After processing, the Spamtest returns messages to the scanning
module.
If a message has been assigned the Spam or Probable Spam status,
and the application is configured to block such messages (the
BlockMessage parameter is assigned the as/spam or as/probable
Page 34

34 Kaspersky
®
Mail Gateway 5.5
value), then anti-virus message scanning will be skipped. Further actions
of the application are described in Step 8.
4. Using a built-in MIME format identifier (MIME, RFC2822, UUE), the
application divides the message into its components, such as message
body, attachments, etc.
5. If the application is configured to filter objects by name and/or attachment
type, it applies the specified filtering rules for this message. If the
message meets the filter conditions, the object will be assigned the
Filtered status and will not be subjected to further anti-virus scanning.
6. Then each of the received objects will be sent to the AV module that
analyzes the received object and returns the status assigned to it.
An object may be assigned one of the following statuses in the process of
checking:
• Clean – object is clean.
• Infected – object is infected and cannot be disinfected or its
disinfection has not been attempted.
• Disinfected – infected object has been successfully disinfected.
An object can be assigned the Disinfected status only
if the cure mode has been enabled for infected
objects.
• Suspicious – object is suspected of being infected with an
unknown virus or with a new modification of a known virus.
• Protected – scanning failed because the object is password-
protected (e.g., it is an archive).
• Error – object is corrupted or an error occurred during the scan.
• Not_check – object has not been scanned because anti-virus
checks have been disabled.
7. Depending on the status assigned to each object, the application
performs actions as specified in the settings for the respective group
(basic actions of the AV module) in the configuration file.
8. After the anti-virus scan of all message components and execution of
basic actions on those components, an additional action can be
performed on the message as a whole.
The basic actions include operations performed by the Spamtest filter and the AV
module.
• Basic actions of the Spamtest filter (see section 4.3.3 on p. 37 for details):
Page 35

Anti-virus protection and spam filtration 35
• subject – addition to the Subject header of a label
corresponding to the assigned status and content category.
• keywords – addition to the Keywords header of a label
corresponding to the assigned status and content category.
• none – addition of service headers (X-SpamTest-*) only to a
message.
• Basic actions of the AV module (see section 4.4 on p. 38 for details):
• pass – deliver an object without changes.
• cure – replacement of an infected object with a disinfected one.
• remove – delete infected object.
• placeholder – replace infected attachments with messages
created using templates.
• Additional actions:
• Append additional informational fields to message header or
body (see section 6.12 on p. 80).
• Block delivery of messages to the recipients; see section 5.2.2
on p. 46 for a sample method to block delivery for spam
messages, and section 5.3.3 on p. 49 for messages containing
infected objects.
• Create and send alerts to the sender, administrator, and
recipient (see example in section 5.3.4 on p. 50).
• Quarantine a message; see section 5.2.3 on p. 46 for a sample
method to quarantine spam messages and section 5.3.6 on p.
52 for messages containing infected objects.
4.3. Operation of the Spamtest filter
Spam filtering by Spamtest is performed during the third step of the procedure
described in section 4.2 on p. 32. Every message passes the following analysis
stages:
• analysis of message headers using formal signs (see section 4.3.1 on
p. 36)
• analysis of message contents using the content filtration database (see
section 4.3.2 on p. 36).
Page 36

36 Kaspersky
During all those stages, the message analysis is performed according to the
degree of filtering intensity defined in the application configuration file
(SpamDetection option in the [smtpgw.antispam] section).
The following filtering intensity degrees are available:
• Spam Detection Soft (SpamDetection=soft).
• Spam Detection Standard (SpamDetection=standard).
• Spam Detection Hard (SpamDetection=hard).
These degrees differ regarding the strictness of spam evaluation (the soft
degree will identify as spam fewer messages than the hard degree).
®
Mail Gateway 5.5
4.3.1. Message header analysis
During this stage, the application searches for formal spam signs, i.e. suspicious
headers and combinations thereof. The application uses a number of special
rules for analysis. E.g., the following situations are considered suspicious:
• There are multiple spaces in the end of the Subject header and then a
meaningless combination of characters follows, e.g., 'TVIWEGEQO'.
• The message lacks the To or From header.
• Invalid addresses in the To or From headers and presence therein of
suspicious addresses containing combinations of numbers and letters,
e.g., 167nk46s76@yahoo.com;
• An empty X-Mailer header;
• Asian encodings used in the message.
This is not a complete list of rules used during analysis of message headers. The
list of rules applied during the current stage is determined by the specified
degree of filtration intensity.
4.3.2. Analysis of message content
Message analysis employs the algorithms of content filtering: the application
uses artificial intelligence technologies to analyze the actual message content
(including the Subject header), and its attachments (attached files) in the
following formats:
• plain text (ASCII, not multiyear)
• HTML (2.0, 3.0, 3.2, 4.x, XHTML 1.0)
• Microsoft Word (versions 6.0, 95/97/2000/XP)
• RTF.
Page 37

Anti-virus protection and spam filtration 37
The purpose of spam filtering is to decrease the volume of unwanted
messages in the mailboxes of your users. It is impossible to guarantee
detection of all spam messages because too strict criteria would
inevitably cause filtering of some normal messages as well.
The application uses two main methods to detect messages with suspicious
content:
• comparison with sample messages (by matching their lexicons)
• detection of typical terms, i.e. words and word combinations.
All the data employed by the Spamtest for content filtering: hierarchical list of
categories, typical terms, etc. are stored in the content filtration databases.
Our linguistic laboratory constantly works to supplement and improve
the content filtration databases. Therefore, you are advised to update
the databases regularly (see section 5.1 on p. 40).
A message may be referred to one or several classification categories of the
content filtration database according to the results of content analysis.
Preservation of all useful mail must be the top priority for the system
administrator because the loss of a single important message may
cause more trouble for the end user than receipt of a dozen of spam
messages. To avoid the loss of necessary mail, you are advised to use
only non-destructive actions with mail identified after content analysis
as spam or probable spam. E.g.:
• append labels to the Subject header, such as [!! SPAM] or [??
Probable Spam];
• append an additional Keywords=... header, which would allow the
users to transfer such messages to special folders using their own
mail user agents (MUA).
4.3.3. Spamtest filter actions
Actions performed over a message processed by the Spamtest filter is
determined by the ActionSpam option in the [smtpgw.policy] (or
[smtpgw.group:group_name]) section of the application configuration file. The
action result depends on the status assigned to that message during analysis.
Please see section 4.2 on p. 32 for a description of statuses assigned by the
Spamtest filter to messages.
If ActionSpam=subject has been specified as the action in the configuration file:
• Messages with the Spam status will be marked with the [!! SPAM] label
added to the Subject header.
Page 38

38 Kaspersky
®
Mail Gateway 5.5
• Messages with the Probable Spam status will be marked with the
[?? Probable Spam] label added to the Subject header (the label may
vary depending upon the identified content category, e.g., if the message
has been identified as one belonging to the Invitations to workshops,
conferences, exhibitions category, it will be replaced with the
[?? Seminars etc.] label).
• Messages with the Not detected status may be marked with a respective
label in the Subject header ([--Obscene--] if the message belongs to the
Obscene category (contains invectives), or
[--Formal Messages--] if the message is an autoreply, mail robot letter,
etc.).
If ActionSpam=keywords has been specified as the action in the configuration
file:
• Messages with the Spam status will be marked with the Keywords header
containing message status and/or content categories assigned to them.
• Messages with the Probable Spam status will be marked with the
Keywords header containing message status and/or content categories
assigned to them.
• Messages with the Not detected status will be marked with the Keywords
header containing content category assigned to them provided that there
is at least one such category.
If ActionSpam=none has been specified as the action in the configuration file,
the application will not modify the Keywords or Subject headers. It will only add
X-SpamTest-* informational headers.
4.4. Operation of the AV module
The AV module checks message components for virus presence.
During the process of scanning and disinfection of detected infected objects, the
AV module uses the anti-virus databases containing descriptions of currently
known viruses and methods of disinfection for objects containing them.
You are advised to update the anti-virus databases regularly to
maximize the efficiency of anti-virus functionality as regards new
viruses. Updates for the anti-virus databases are made available on the
update servers of Kaspersky Lab every hour.
By default, the AV module of the application only scans your email traffic; it does
not cure infected objects.
To enable disinfection, set the Cure parameter in the [smtpgw.ave] section of
the configuration file to true. If disinfection has been successful, the object is
Page 39

Anti-virus protection and spam filtration 39
assigned the Disinfected status. Please see section 4.2 on p. 32 for details
regarding other statuses that the AV module can assign to objects.
The actions performed by the AV module with an object, which has passed
scanning, are determined by the respective options in the configuration file
(ActionInfected, ActionSuspicious, etc.). Each status corresponds to its
respective option. The following actions are available:
• cure – replace the infected object in a message with a disinfected one;
The action can be defined for objects with the Disinfected
status only (ActionDisinfected parameter).
• pass – transfer the object without modifications, no actions will be applied
to the object;
• remove – remove the object from mail message;
• placeholder – replace the object with a notification generated according
to a template.
Page 40

CHAPTER 5. ANTI-VIRUS
PROTECTION AND SPAM
FILTRATION
Using Kaspersky Mail Gateway, you can arrange anti-virus protection and spam
filtering for email traffic transferred through the mail server of your organization.
The anti-virus protection and spam filtering system is based on the performance
of tasks that represent major functionality of the application.
The tasks implemented by Kaspersky Mail Gateway may be divided into three
major groups:
1. Updates of the content filtration and anti-virus databases used for
spam filtering, anti-virus scanning and disinfection of objects.
2. Spam filtering.
3. Anti-virus protection of email traffic.
Each of the above groups includes more specific tasks. In this chapter, we will
discuss the most typical tasks that the administrator can combine and enhance
depending on the needs of his/her organization.
Performance of the tasks described further requires introduction of
some changes into the configuration file of the application. You will
have to restart the application to apply the modifications.
This guide contains a description of how to locally configure and start tasks from
the command line. Issues related to starting and managing tasks from remote
computers using the Webmin application are not discussed in this document.
In all examples below, it is assumed that the administrator has
completed all required post-installation tasks and the application
operates correctly.
5.1. Updating the anti-virus and
content filtration databases
Kaspersky Mail Gateway uses the anti-virus and content filtration databases
while processing email traffic.
Page 41

Anti-virus protection and spam filtration 41
The content filtration database is employed for spam filtering (analysis of
message content and attached files used to identify unsolicited mail).
The anti-virus databases are employed during scanning and disinfection of
infected objects; they contain descriptions of all currently known viruses and the
methods of disinfection for objects affected by those viruses.
The keepup2date component is included into Kaspersky Mail Gateway to provide
for software updates. The updates are retrieved from the update servers of
Kaspersky Lab, e.g.:
http://downloads1.kaspersky-labs.com/
http://downloads2.kaspersky-labs.com/
ftp://downloads1.kaspersky-labs.com/ etc.
The updcfg.xml file included in the installation package lists the URLs of all
available update servers.
The keepup2date component supports Basic authentication for
connections through a proxy server.
To update the anti-virus and content filtration databases, the keepup2date
component selects an address from the list of update servers and tries to
download updates from that server. If the server is currently unavailable, the
application connects to another server, trying to download updates.
Updates for the content filtration database are made available on
Kaspersky Lab’s update servers every twenty minutes. Updates for the
anti-virus databases are made available on Kaspersky Lab’s update
servers every hour.
After connection to an update server the keepup2date identifies available
updates and downloads them.
We strongly recommend that you set up the keepup2date component to
update the databases every twenty minutes!
After a successful update, a command specified as the value of the
PostUpdateCmd parameter in the [updater.options] section of the
configuration file will be executed. By default, this command will automatically
restart the application. The restart is necessary to make the application use the
updated databases. Incorrect modification of that parameter may prevent the
application from using the updated databases or cause it to function erroneously.
All settings of the keepup2date component are stored in the [updater.*]
sections of the configuration file.
If you have purchased a license to use Kaspersky Mail Gateway, which allows
anti-virus scanning of mail traffic only, you can disable downloading of updates
Page 42

42 Kaspersky
for the content filtration databases. To do so, assign the av value to the
UpdateBases parameter in the [updater.options] section:
[updater.options]
UpdateBases=av
If your network has a complicated structure, we recommend that you download
updates from Kaspersky Lab’s update servers every twenty minutes and place
them in a network directory. To keep other networked computers constantly
updated, configure the local computers to copy the updates from that directory.
For detailed instructions on how to implement this updating scenario, see
section 5.1.3 on p. 44.
The updating process can be scheduled to run automatically using the cron
utility (see section 5.1.1on p. 42) or started manually from the command line (see
section 5.1.2 on p. 43). Starting the keepup2date component requires root user
privileges.
®
Mail Gateway 5.5
5.1.1. Automatic updating of the anti-virus
and content filtration databases
You can schedule regular automatic updates for the anti-virus and content
filtration databases using the cron utility.
Task
: Configure the application to update automatically your anti-virus
and content filtration databases every twenty minutes. An update server
should be selected from the updcfg.xml file by default. Only errors
occurring in the component operation should be recorded in the system
log. Keep a general log of all task starts. Output no information to the
console.
Solution: to perform the above task, do the following:
1. In the application configuration file, specify the following values for
the parameters below:
[updater.options]
KeepSilent=true
[updater.report]
Append=true
ReportLevel=1
2. Edit the file that sets the rules for the cron process (crontab –e) by
entering the following string for the root user (or any other
privileged user), add the following line:
Page 43

Anti-virus protection and spam filtration 43
In Linux:
*/20 * * * * /opt/kav/5.5/scmsmtpgw/bin/keepup2date
In FreeBSD:
*/20 * * * * /usr/local/share/kav/5.5/scmsmtpgw/bin/keepup2date
5.1.2. Manual updating of the anti-virus and
content filtration databases
You can start updating your anti-virus and content filtration databases from the
command line at any time.
Task
If you need to update the anti-virus and content filtration databases on several
servers, it may be more convenient to download the updates from an update
server once, save them to a shared directory, and mount the directory within the
file system of every server running Kaspersky Mail Gateway. Then it will be
sufficient to launch the update script having specified first the mounted directory
as the source of updates. Please see section 5.1.3 on p. 44 for details related to
creation of a shared directory for updates.
: start updating of the anti-virus and content filtration databases,
save updating results in the /tmp/updatesreport.log file.
Solution
privileged user) and enter in the command line:
# keepup2date –l /tmp/updatesreport.log
: to accomplish the task, log in as the root (or any other
Task
: start the updating of the anti-virus and content filtration databases
from the /home/kavuser/bases local directory. If the directory is
inaccessible or empty, update the databases from Kaspersky Lab’s
update servers. Save the results to the /tmp/updatesreport.log file.
Solution
privileged user) and do the following:
1. Mount the shared directory containing updates to the anti-virus
2. In the application configuration file, specify the following values for
: to accomplish the task, log in as the root (or any other
databases, to the local /home/kavuser/bases directory.
the parameters below:
[updater.options]
UpdateServerUrl=/home/kavuser/bases
UseUpdateServerUrl=true
Page 44

44 Kaspersky
UseUpdateServerUrlOnly=false
3. Enter the following in the command line:
# keepup2date –l /tmp/updatesreport.log
You can accomplish these or similar tasks remotely using the Webmin
remote administration module.
®
Mail Gateway 5.5
5.1.3. Creating a shared directory for
storing and sharing database
updates
To update the anti-virus and content filtration databases correctly on local
computers from the shared directory, you need to reproduce in that directory a
file structure that is similar to that of Kaspersky Lab’s update servers. This task
deserves a detailed explanation.
: create a shared local directory, which the local computers will use
Task
as the source to update their anti-virus and content filtration databases.
Solution
privileged user) and do the following:
1. Create a local directory.
2. Run the keepup2date component as follows:
3. Provide reading access to that directory for local computers on your
: to accomplish the task, log in as the root (or any other
# keepup2date –u <rdir>
where <rdir> is the full path to the directory created.
network.
5.2. Spam filtration
This section contains sample tasks demonstrating the application functionality
related to spam filtering. The examples show the main mechanisms of spam
fighting employed in the application, in particular:
• marking of messages identified as spam or probable spam with special
labels in the Subject header
• marking of messages identified as spam or probable spam with the
Keywords header
Page 45

Anti-virus protection and spam filtration 45
Users may set up their mail clients to transfer the labeled
messages to corresponding directories.
• blocking of delivery for messages identified as spam or probable spam
• saving of messages identified as spam or probable spam in the
quarantine directory.
5.2.1. Marking of messages containing
spam
:
Task
• Filter spam; specify the standard degree of filtering intensity.
• Modify the Keywords header of messages identified as spam or
probable spam for users in the managers group.
• Modify the Subject header of messages identified as spam or
probable spam for all other users.
Solution
1. Specify the level of filtering intensity. To do so, specify the following
2. Create the [smtpgw.group:managers] section, which should
: to perform the above task, do the following:
parameter value in the [smtpgw.antispam] section of the
configuration file:
SpamDetection=standard
define the rules of mail processing for users included into the
managers group:
[smtpgw.group:managers]
Recipients=*@managers.mycompany.com
CheckSpam=true
ActionSpam=keywords
Mail processing rules for all other users will be defined by the
[smtpgw.policy] section:
[smtpgw.policy]
CheckSpam=true
ActionSpam=subject
Page 46

46 Kaspersky
®
Mail Gateway 5.5
5.2.2. Blocking delivery of spam messages
Task:
• Filter spam; specify the standard degree of filtering intensity.
• Block the delivery of messages identified as spam or probable
spam for users in the managers group.
• Block the delivery of spam messages only for all other users.
Solution
1. Specify the level of filtering intensity. To do so, specify the following
2. Create the [smtpgw.group:managers] section, which should
: to perform the above task, do the following:
parameter value in the [smtpgw.antispam] section of the
configuration file:
SpamDetection=standard
define the rules of mail processing for users included into the
managers group:
[smtpgw.group:managers]
Recipients=*@managers.mycompany.com
CheckSpam=true
ActionSpam=none
BlockMessage=as/spam,as/probable
Mail processing rules for all other users will be defined by the
[smtpgw.policy] section:
[smtpgw.policy]
CheckSpam=true
ActionSpam=none
BlockMessage=as/spam
5.2.3. Storage of spam message copies in
the quarantine directory
Storage of message copies in the quarantine directory can be combined with
blocking of mail delivery or used individually. In the first case messages identified
by the application as spam or probable spam will not reach the mailboxes of
recipients; instead, they will be saved in the quarantine directory. In the second
Page 47

Anti-virus protection and spam filtration 47
case, the messages will be delivered to end users and their copies will be
preserved in quarantine.
Task:
• Filter spam; specify the standard degree of filtering intensity.
• Copy all messages identified as spam or probable spam to the
quarantine directory.
• Block the delivery of messages identified as spam or probable
spam.
Solution
1. Specify the level of filtering intensity. To do so, specify the following
2. Specify the following parameter values in the [smtpgw.policy]
Blocked and quarantined messages that have been assigned the Spam
or Probable Spam status by the Spamtest module may contain viruses
as their anti-virus scanning will be skipped after performance of the
above actions.
: to perform the above task, do the following:
parameter value in the [smtpgw.antispam] section of the
configuration file:
SpamDetection=standard
section of the configuration file:
[smtpgw.policy]
CheckSpam=true
ActionSpam=none
BlockMessage=as/spam,as/probable
QuarantineMessage=as/spam,as/probable
5.3. Anti-virus protection of email
traffic
This section contains examples of the functionality offered by Kaspersky Mail
Gateway as regards anti-virus protection of email traffic. The settings described
in the examples can be combined to produce more sophisticated schemes of
mail traffic protection.
Page 48

48 Kaspersky
®
Mail Gateway 5.5
5.3.1. Delivery of messages with clean or
disinfected objects only
Task:
• Scan for viruses all incoming and outgoing mail traffic on the
server.
• Cure infected objects.
• Remove from mail messages all infected objects, which could
not be cured.
• Deliver to recipients messages containing clean and disinfected
objects only.
Solution
1. Enable the cure mode for infected objects. To do so, specify the
2. Specify the following parameter values in the [smtpgw.policy]
You can also arrange delivery of notifications to the administrator,
message recipient and sender informing them about detection of
infected or suspicious objects (see section 5.3.4 on p. 50). You can also
save messages containing infected, suspicious or password-protected
objects in the quarantine directory (see section 5.3.6 on p. 52).
: to perform the above task, do the following:
following parameter value in the [smtpgw.ave] section of the
configuration file:
Cure=true
section of the configuration file:
CheckAV=true
ActionDisinfected=cure
ActionInfected=remove
ActionSuspicious=remove
ActionProtected=remove
ActionError=remove
BlockMessage=
Page 49

Anti-virus protection and spam filtration 49
5.3.2. Replacement of infected objects
with standard notifications
Task
:
• Scan for viruses all mail traffic on the server and cure infected
objects in email messages.
• Objects, which cannot be cured, must be deleted and replaced
with a standard notification as well as suspicious, damaged or
password-protected objects.
Solution: to perform the above task, do the following:
1. Enable the cure mode for infected objects. To do so, specify the
following parameter value in the [smtpgw.ave] section of the
configuration file:
Cure=true
2. Specify the following parameter values in the [smtpgw.policy]
section of the configuration file:
CheckAV=true
ActionDisinfected=cure
ActionInfected=placeholder
ActionSuspicious=placeholder
ActionProtected=placeholder
ActionError=placeholder
BlockMessage=
In addition to the replacement of infected and suspicious objects with
standard messages you can also set up the application to deliver to the
administrator notifications informing about detection of those objects
(see section 5.3.4 on p. 50) and save the messages containing those
objects in the quarantine directory (see section 5.3.6 on p. 52).
5.3.3. Blocking delivery for messages
containing suspicious objects
Task:
• Scan for viruses all mail traffic on the server and cure infected
Page 50

50 Kaspersky
objects in email messages;
• Block the delivery of messages containing objects, which cannot
be cured, as well as suspicious, damaged or passwordprotected objects.
While implementing the task, please keep in mind that if a message
contains several objects and one of them cannot be disinfected or it is
suspicious or password-protected, then the delivery of the whole
message will be blocked.
®
Mail Gateway 5.5
Solution
1. Enable the cure mode for infected objects. To do so, specify the
2. Specify the following parameter values in the [smtpgw.policy]
You can also set up the application to send to the administrator
notifications informing about detection of infected or suspicious objects
(see section 5.3.4 on p. 50) and save the messages containing those
objects in the quarantine directory for further delivery to Kaspersky Lab
for examination (see section 5.3.6 on p. 52).
: to perform the above task, do the following:
following parameter value in the [smtpgw.ave] section of the
configuration file:
Cure=true
section of the configuration file:
CheckAV=true
ActionDisinfected=cure
ActionInfected=pass
ActionSuspicious=pass
ActionProtected=pass
ActionError=pass
BlockMessage=infected,suspicious,protected,
error
5.3.4. Delivery of notifications to the
sender, administrator and recipients
Task
:
• Scan for viruses all mail traffic on the server and cure all infected
objects.
• Deliver to the recipients messages containing clean and
Page 51

Anti-virus protection and spam filtration 51
disinfected objects only.
• Objects, which cannot be cured, must be deleted as well as
suspicious, damaged or password-protected objects.
• Notify the senders, recipients and the administrator about cured,
incurable, deleted, suspicious and damaged objects in email
messages.
Solution: to perform the above task, do the following:
1. Enable the cure mode for infected objects. To do so, specify the
following parameter value in the [smtpgw.ave] section of the
configuration file:
Cure=true
2. Specify the following parameter values in the [smtpgw.policy]
section of the configuration file:
ActionDisinfected=cure
ActionInfected=delete
ActionSuspicious=delete
ActionProtected=delete
ActionError=delete
BlockMessage=
NotifyAdmin=disinfected,infected,suspicious,
protected,error
NotifyRecipient=disinfected,infected,
suspicious,protected,error
NotifySender=disinfected,infected,suspicious,
protected,error
5.3.5. Additional filtering of objects by
name and type
Email messages frequently contain objects where virus infection is highly
probable (e.g., executable files). To avoid infection, we recommend that you
configure the application to filter email by name and/or attachment types and
save such objects in a separate directory.
There are also objects, which cannot be infected with viruses (e.g., plain text
files). To reduce the load on the server during anti-virus scanning of email
messages we recommend that you specify the types and/or the names of such
attachments in advance so that the application does not scan them.
Page 52

52 Kaspersky
Filtering of objects is performed using name masks (IncludeByName,
ExcludeByName parameters) and MIME types (IncludeByMime,
ExcludeByMime parameters).
Task:
• Delete .exe and .reg attachments from mail of users included in
the managers group.
• For users included in the accounts group, delete all attached
objects except for files with .doc extension.
• For users included in the sales group, block messages
containing attached .exe files.
Solution: to perform the above task, do the following:
Create in the configuration application file three
[smtpgw.group:group_name] sections, which should contain the
processing rules for the mail of users in the managers, accounts and
sales groups respectively:
[smtpgw.group:managers]
Recipients=*@managers.mycompany.com
IncludeByName=*.exe
IncludeByName=*.reg
ActionFiltered=remove
…
[smtpgw.group:accounts]
Recipients=*@accounts.mycompany.com
ExcludeByName=*.doc
ActionFiltered=remove
…
[smtpgw.group:sales]
Recipients=*@sales.mycompany.com
IncludeByName=*.exe
BlockMessage=filtered
®
Mail Gateway 5.5
5.3.6. Saving messages in the quarantine
directory
You can configure Kaspersky Mail Gateway to preserve messages with certain
statuses to the quarantine directory.
Page 53

Anti-virus protection and spam filtration 53
This feature may be used, for example, if an infected attachment that contains
important data was detected during anti-virus scanning. A disinfection attempt
may corrupt a part of the data. The message can also be isolated in a separate
directory and then sent to Kaspersky Lab for analysis. Our experts will probably
be able to disinfect the file and preserve the integrity of data in it.
Task
:
• Scan for viruses all mail traffic on the server and cure all infected
objects.
• Deliver to the recipients messages containing clean and
disinfected objects only.
• Messages with incurable attachments or suspicious, damaged or
password-protected objects must be saved in the quarantine
directory specified as /opt/quarantine.; their delivery must be
blocked.
Solution: to perform the above task, do the following:
1. Create the /opt/quarantine directory, which will contain the blocked
messages and grant the right to write to that directory to the
account used to run the application (kavuser by default).
2. Enable the cure mode for infected objects. To do so, specify the
following parameter value in the [smtpgw.ave] section of the
configuration file:
Cure=true
3. Specify the following parameter values in the [smtpgw.policy]
section of the configuration file:
ActionDisinfected=cure
ActionInfected=pass
ActionSuspicious=pass
ActionProtected=pass
ActionError=pass
BlockMessage=infected,suspicious,protected,
error
QuarantineMessage=infected,suspicious,
protected,error
AVQuarantinePath=/opt/quarantine
Page 54

54 Kaspersky
®
Mail Gateway 5.5
5.4. Combining spam filtration and
anti-virus protection
The choice of application mode, level of anti-virus scanning and spam filtering
intensity depend on the volume of mail traffic processed by the application and
the corporate security policy. Three modes demonstrated in this section provide
insight into the opportunities for combining spam filtration with anti-virus
protection of email traffic.
The application settings described in this section are provided as
examples only; the administrator may change them as necessary.
5.4.1. Maximum speed
The mode allows high performance of anti-virus scanning and spam filtration,
which may be necessary while processing large volume of email messages. The
security level in that case is somewhat lower because the application does not
cure infected objects; instead, it just notifies about their detection.
The application in that mode:
• filters mail traffic looking for spam; the degree of filtering intensity is soft
• marks messages identified as spam or probable spam using special
labels in the Subject header;
• performs anti-virus scanning of mail attachments; it does not attempt to
cure infected objects
• filters and blocks delivery for messages containing the most dangerous
attachment types (an external file is used to define the list of dangerous
objects) and for messages containing infected attachments
• notifies the recipients about messages, which have been blocked.
To enable that mode:
1. Specify the following parameter value in the [smtpgw.antispam]
section of the configuration file:
SpamDetection=soft
2. Specify the following parameter values in the [smtpgw.ave]
section:
Cure=false
Page 55

Anti-virus protection and spam filtration 55
ScanArchives=false
ScanMailBases=false
UseIChecker=true
3. Create List1 file containing the list of the most frequent dangerous
objects from the viewpoint of anti-virus protection. E.g.:
*.exe
*.bat
*.com
*.bin
4. Specify the following parameter values in the [smtpgw.policy]
section of the configuration file:
CheckAV=true
CheckSpam=true
IncludeByName=file:<path_to_file>/List1
ActionSpam=Subject
ActionFiltered=pass
ActionInfected=pass
ActionSuspicious=pass
ActionProtected=pass
ActionError=pass
BlockMessage=infected,filtered
NotifyRecipient=infected,filtered
The presence of several groups of senders/recipients
([smtpgw.group:group_name] sections) slows down processing of
email traffic. When high performance is required, you are advised to
use the default group only ([smtpgw.policy] section) to specify the mail
processing rules.
5.4.2. Recommended mode
The mode allows optimal balance between server performance and provided
level of security. The application in that mode:
• filters mail traffic looking for spam; the degree of filtering intensity is
standard
• marks messages identified as spam or probable spam using special
labels in the Subject header
• performs anti-virus scanning and disinfection of mail attachments
Page 56

56 Kaspersky
®
Mail Gateway 5.5
• replaces suspicious objects and infected objects, which cannot be cured,
with a standard notification
• blocks delivery for messages containing password-protected attachments
and objects that cause errors while scanning adding them to the
quarantine directory
• notifies the recipients about blocked messages.
To enable that mode:
1. Specify the following parameter value in the [smtpgw.antispam]
section of the configuration file:
SpamDetection=standard
2. Specify the following parameter values in the [smtpgw.ave]
section:
Cure=true
ScanArchives=true
ScanMailBases=true
UseIChecker=true
3. Specify the following parameter values in the [smtpgw.policy]
section of the configuration file:
CheckAV=true
CheckSpam=true
ActionSpam=Subject
ActionDisinfected=cure
ActionInfected=placeholder
ActionSuspicious=placeholder
ActionProtected=pass
ActionError=pass
BlockMessage=protected,error
QuarantineMessage=protected,error
NotifyRecipient=protected,error
5.4.3. Maximum protection
In the maximum protection mode the speed of mail traffic processing becomes
lower. However, the mode provides for the best protection of users against spam
and viruses. The application in that mode:
Page 57

Anti-virus protection and spam filtration 57
• filters mail traffic looking for spam; the degree of filtering intensity is hard
• blocks delivery for messages identified as spam or probable spam adding
them to the quarantine directory
• performs anti-virus scanning and disinfection of mail attachments
• removes from messages infected attachments, which cannot be cured as
well as suspicious, password-protected objects and objects causing
errors during scanning
• notifies message recipients and the administrator about infected,
suspicious and password-protected attachments and objects, which
caused errors during scanning.
To enable that mode:
1. Specify the following parameter value in the [smtpgw.antispam]
section of the configuration file:
SpamDetection=hard
2. Specify the following parameter values in the [smtpgw.ave]
section:
Cure=true
ScanArchives=true
ScanMailBases=true
UseIChecker=false
3. Specify the following parameter values in the [smtpgw.policy]
section of the configuration file:
CheckAV=true
CheckSpam=true
ActionSpam=none
ActionDisinfected=cure
ActionInfected=remove
ActionSuspicious=remove
ActionProtected=remove
ActionError=remove
BlockMessage=as/all
QuarantineMessage=as/all
NotifyRecipient=infected,suspicious,protected,
error
NotifyAdmin=infected,suspicious,protected,
Page 58

58 Kaspersky
error
®
Mail Gateway 5.5
5.5. Additional features of
Kaspersky Mail Gateway
In addition to its main functions, i.e. spam filtering and anti-virus protection of
mail traffic, the application can perform the following tasks:
• logging of received and sent email
• enabling restrictions for SMTP connections preventing hacker attacks and
application use as an open relay for sending of unauthorized email.
5.5.1. Automatically add incoming and
outgoing mail to archives
If the security policy of your organization includes archiving email traffic
processed by the server, you can set the application to add automatically email
messages to archives. If necessary, the administrator can view all messages in
archives.
If the auto archiving option is enabled, copies of the following messages will be
archived:
• All incoming messages, including spam or infected objects, without
additionally notifying the administrator. Archiving of such messages is
enabled when the path to the archive directory is specified as the value of
the IncomingArchivePath parameter in the [smtpgw.path] section).
• Outgoing messages, including those delivered to recipients, blocked
because of a virus or spam, and notifications generated by the
application. Archiving of such messages is enabled when the path to the
archive directory is specified as the value of the OutgoingArchivePath
parameter in section [smtpgw.path]).
Before you enable automatic archiving, make sure that there is enough
space in your server’s file system to accommodate the archive.
Do not forget to purge this directory from time to time to remove old
messages and compress necessary files (the frequency of that
procedure depends on the mail traffic intensity within your network).
Page 59

Anti-virus protection and spam filtration 59
5.5.2. Protection from hacker attacks and
spam
To provide the highest level of security for your mail system, we recommend that
you modify the Kaspersky Mail Gateway configuration file to extend the anti-virus
functionality of the application. To protect your server from hacker attacks or, for
example, to prevent spam being relayed through your server, configure the
following options:
• ConnectRule in the [smtpgw.access] section. The parameter defines
application behaviour during establishment of an SMTP session.
• HeloRule in the [smtpgw.access] section. The parameter defines
application response to HELO/EHLO command received from a client.
• MailfromRule in the [smtpgw.access] section. The parameter defines
application behaviour at an attempt to send a message from a source
(passed with MAIL FROM command) with a domain name, which does
not match the actual IP address or MX host corresponding to that domain.
• RelayRule in the [smtpgw.access] section. The parameter defines the
rules for client access to gateway. Correct settings of that option are
essential for prevention of application use as a publicly open mail relay.
A detailed discussion of the syntax of these parameters is provided in
the description of the configuration file (see A.2 on p. 99).
You are also advised to enable restrictions for SMTP connections (see section
6.1.3 on p. 66).
Furthermore, application version 5.5 supports the technology of DNS black lists.
That technology allows blocking of mail receipt from unsafe servers registered in
the RBL database as servers sending spam. The list of DNS Black List services
is specified in the DNSBlackList parameter, [smtpgw.access] section of the
application configuration file.
DNS black list service (RBL, real time black hole list) is a database
of IP addresses of mail servers performing unchecked mail delivery.
Various RBL services use different policies for generation of such lists.
Please examine carefully the policy of each service before you start
using it for mail filtration.
If a certain address is constantly being used for sending spam and
administration of the server used for spam distribution takes no steps to
prevent that, you can inform RBL about the spammer. The latter will be
added to the database and the record will allow automatic blocking of
mail receipt from that mail server.
Page 60

60 Kaspersky
®
Mail Gateway 5.5
5.6. Managing license keys
The right to use Kaspersky Mail Gateway is determined by the license key. The
key is included in the product’s distribution kit and entitles you to use the
application from the day you have purchased it and installed the key.
Kaspersky Mail Gateway WILL NOT work without a license key!
After the license expires, the functionality of the application will still be preserved
except for the possibility to update the anti-virus and content filtration databases.
You will still be able to scan email messages for viruses, filter spam and disinfect
infected objects, but you will be unable to use the databases issued after your
license expiration date. Therefore, you may not be protected against new viruses
that have appeared after your license expired and the Spamtest filter will be
unable to filter new spam types without updates to the content filtration database.
In order to protect your computer against new viruses and efficiently filter spam,
we recommend that you renew the license to use Kaspersky Mail Gateway.
The license key gives you the right to use the application. It contains all
information related to the license you have purchased, including the type of
license, license expiry date, information about dealers, etc.
In addition to the right to use the application during the license period, you will
have the following benefits:
• twenty-four-hour technical support
• hourly updates of the anti-virus databases and updates to the content
filtration database made available every 20 minutes
• timely notifications about new virus threats.
Therefore it is essential to extend in time your license to use Kaspersky Mail
Gateway. You can also install an additional key. The application will start using it
as soon as the current active key expires (see section 5.6.2 on p. 62).
5.6.1. Viewing information about license
keys
You can view information about the installed license keys in the reports of the
smtpgw component. Each time the component starts, smtpgw loads the license
key information and displays it in the report.
A more detailed information about the status of the license keys may be obtained
using licensemanager, a special component of the application.
Page 61

Anti-virus protection and spam filtration 61
All information about keys may be viewed either on the server’s console, or
remotely from any networked computer that has access to the Webmin module.
To view information about all installed license keys, enter the following
in the command line:
# licensemanager –s
In the server console, you will see information similar to the following:
Kaspersky license manager for Linux. Version 5.5.0/RELEASE
Copyright (C) Kaspersky Lab, 1997-2006.
Portions Copyright (C) Lan Crypto
License info:
Product name: Kaspersky Mail Gateway
Expiration date: 02-06-2006, expires in 34 days
Active key info:
Product name: Kaspersky Mail Gateway
Key file 00086CA1.key
Type: Commercial
Expiration date: 02-06-2006
Serial: 0007-000487-00086CA
To view information about a license key, enter, for example, the
following in the command line:
# licensemanager -k 00053E3D.key
where 00053E3D.key is the name of the license key file.
In the server console, you will see information similar to the following:
Kaspersky license manager. Version 5.5.0/RELEASE
Copyright (C) Kaspersky Lab. 1998-2006.
Portions Copyright (C) Lan Crypto
Product name: Kaspersky Mail Gateway
Creation date: 02-12-2005
Expiration date: 02-06-2006
Serial 0007-000487-00086CA
Serial 02B1-000454-00053E3
Type: Commercial
Lifespan: 91
Page 62

62 Kaspersky
®
Mail Gateway 5.5
5.6.2. Renewing your license
Renewal of the license to use Kaspersky Mail Gateway will give you the right to
re-enable full product functionality. Besides, additional services listed in
section 5.6 on p. 60 will be resumed.
The license term depends on the product you bought and the type of the license
you purchased. The license for Kaspersky Mail Gateway is usually issued for one
year.
To renew the license for Kaspersky Mail Gateway:
Contact the company that sold you the product and renew your license
for Kaspersky Mail Gateway.
or:
Purchase a license directly from Kaspersky Lab. Write a letter of
request to the Sales Department of our company at
sales@kaspersky.com
(www.kaspersky.com), section E-Store Æ Renew Your License. After
your payment is received, we will send a license key to the email
address indicated in the corresponding field of your license renewal
form.
To install a new license key, enter, for example, the following in the
command line:
# licensemanager -a 00053E3D.key
where 00053E3D.key is the name of the license key file.
If the installation is successful, the following (or similar) information will be
displayed on the server console:
Kaspersky license manager. Version 5.5.0/RELEASE
Copyright (C) Kaspersky Lab. 1998-2006.
Portions Copyright (C) Lan Crypto
Key file 00053E3D.key is successfully registered
We recommend that you update the anti-virus database after the installation.
If you want to install a new license key before the current license key expires,
you can add it as a backup license key. The backup key will be activated
immediately after the current one expires. The term of validity for the additional
key starts from the activation date. You can install only one backup key.
If you have installed two keys (the current and an additional one), you can view
information about the installed active and backup keys in the server console.
or fill in the corresponding form on our website
Page 63

Anti-virus protection and spam filtration 63
5.6.3. Removing a license key
To remove the current license key and the backup key (if it is installed),
enter the following in the command line:
# licensemanager –da
If the component removes the license key successfully, the following (or similar)
information will be displayed on the server console:
Kaspersky license manager. Version 5.5.0/RELEASE
Copyright (C) Kaspersky Lab. 1998-2006.
Portions Copyright (C) Lan Crypto
Active key was successfully removed
To remove a backup key, enter the following in the command line:
# licensemanager –dr
The server console will display the following (or similar) information:
Kaspersky license manager. Version 5.5.0/RELEASE
Copyright (C) Kaspersky Lab. 1998-2006.
Portions Copyright (C) Lan Crypto
Additional key was successfully removed
Page 64

CHAPTER 6. ADVANCED
APPLICATION SETTINGS
This chapter discusses in detail the advanced settings of Kaspersky Mail
Gateway. In contrast to main settings that provide the application functionality,
advanced settings can be configured optionally at the administrator’s discretion.
Restart the application to apply its modified settings.
6.1. Configuring anti-virus protection
of mail traffic
Application parameters in the [smtpgw.ave] section define the mode of
message scanning and disinfection, the use of the iChecker™ technology
accelerating anti-virus processing, and enable/disable scanning of archives and
mail attachments (the ScanArchives and ScanMailBases parameters
respectively).
6.1.1. Using the iChecker™ technology
While performing anti-virus scan, the application may use the iChecker™
technology (UseIChecker parameter, section [smtpgw.ave]) that eliminates the
need to scan identical objects each time they are detected in the flow of email
messages and, if possible, perform only one comparison with the existing data.
The object anti-virus scan algorithm will be changed as follows:
When a message is scanned for the first time
status), data about the message (name, checksum, date) is saved to the
iChecker database. The database path is defined by the ICheckerDBFilename
option in the [smtpgw.options] section.
Next time the message is sent to the AV module for scanning
first looks for that file in the iChecker database. If it finds a match, the current
object is compared with the database record. If the current status of the object
and its description in the database are fully identical, then the object is
considered to be unchanged and is not scanned for viruses.
(if it has been assigned the Clean
, the application
Page 65

Advanced application settings 65
To have the application use the iChecker™ technology, set the
UseIChecker parameter in the [smtpgw.ave] section of the
configuration file to true.
6.1.2. Setting up application timeouts
All timeout settings are located in the [smtpgw.timeouts] section of the
application configuration file.
By setting up various timeouts, the administrator can:
• Limit the maximum period after which the application will attempt to
deliver outgoing messages that have not been sent yet
(MaximalBackoffTime parameter, in seconds).
• Limit the minimum time, which should elapse before the application will
attempt to send again an undelivered message (MinimalBackoffTime
parameter).
• Specify the interval during which the application will try to deliver a
message with the frequency defined by the MinimalBackoffTime and
MaximalBackoffTime parameters (MaximalQueueLifetime option).
After this period elapses, the unsent message will be removed from the
ready-to-send queue. If necessary, a DSN message about the initial
message delivery failure will be generated.
• Specify timeouts for intercepting various network operations (for the
Sender and Receiver modules), such as:
• Network reading timeout (ReadTimeout option). The default
timeout specified in the configuration file of the application is the
optimal value for most cases and it is not recommended to alter
it.
• Network writing timeout (WriteTimeout option). The default
timeout specified in the configuration file of the application is the
optimal value for most cases and it is not recommended to alter
it.
• Specify timeouts used by the application to send messages:
• Maximum time for receiving data from the remote server when
establishing an SMTP session (SendingInitialTimeout option).
• Maximum time to start a mail session (command HELO/EHLO)
(SendingHelloTimeout option).
Page 66

66 Kaspersky
• Timeout for waiting for the response from the remote server to
the MAIL FROM command (SendingMailTimeout option).
• Timeout for defining the recipient (RCPT TO command)
(SendingRcptTimeout option).
• Timeout for initiating data transfer (DATA command)
(SendingDataInitiationTimeout option).
• Timeout for stopping the data transfer (CRLF.CRLF sequence)
to the remote server (SendingDataTerminationTimeout
option).
• Timeout for quitting the current mail session (QUIT command)
(SendingQuitTimeout option).
• Specify timeouts used by the application to receive messages:
• Timeout for starting the DATA command
(ReceivingDataInitiationTimeout option).
• Timeout for stopping the data transfer by the remote server
(ReceivingDataTerminationTimeout option).
• Timeout for waiting for the HELO/EHLO, MAIL FROM, RCPT
TO, QUIT commands from the remote server
(ReceivingCommandTimeout option).
®
Mail Gateway 5.5
6.1.3. Setting performance restrictions
Kaspersky Mail Gateway provides the administrator with the possibility to setup
certain limits when working with the application. In some cases, this may help
reduce the load on your server and increase performance. In addition, using
network restrictions, it is possible to prevent some types of virus outbreaks and
DOS attacks aimed at paralyzing your mail server with huge volumes of mail
traffic.
You can find all restriction settings in the [smtpgw.limits] section
of the application configuration file.
You can set the following restrictions:
• Number of objects simultaneously processed by the Receiver, Sender
and the AV modules (the IncomingSessions, OutgoingSessions, and
AntiviralSessions options, respectively).
• Maximum number of message hops (MaximalIncomingHops option).
Set this parameter to avoid looping due to incorrect configuration of the
routing table.
Page 67

Advanced application settings 67
• Limit the maximum size for messages received by the server (Maximal-
IncomingMessageSize option) and the total number of messages
received during one mail session (MaximalIncomingMessagesPerSession option).
• Limit the number of recipients of a single message (MaximalIncoming-
RcptsPerMessage option). This parameter prevents spam addressed to
your users).
• Maximum size of a single mail session (MaximalIncomingSessionSize
option).
• Maximum number of simultaneous connections from
the same IP (or host) that are processed by the Receiver and by the
Sender modules (MaximalIncomingSessionsPerlP and
MaximalOutgoingSessionsPerHost options respectively).
• Minimum size of available disk space on the partition where the working
queue of the application is preserved (the MinimalQueueFreeSpaceSize
option). If during application operation the queue size increases making
available space smaller than this value, the application will temporarily
suspend receipt of new messages until the value returns to the specified
limits.
If the mail traffic at your server exceeds the specified limits, we recommend that
you decrease the number of objects simultaneously processed by the AV module
(AntiviralSessions parameter) and the number of hops for a single message
(MaximalIncomingMessageSize option). This increases application
performance and message processing speed.
If your server has a low-speed Internet connection, the following actions are
recommended:
• Decrease the number of objects simultaneously processed by the
Receiver and Sender modules (IncomingSessions and
OutgoingSessions options).
• Decrease the maximum number of incoming messages received during a
single session (MaximalIncomingMessagesPerSession option).
6.2. Setting up connection receiving
interfaces
The set of interfaces and ports, used by the application to receive the
connections, is defined by ListenOn parameter in the [smptgw.network]
section of the application configuration file. By default, Kaspersky Mail Gateway
listens for connection on port 25 using all available interfaces.
Page 68

68 Kaspersky
If a particular interface is to be used rather than all available interfaces or if it is
necessary to use a port other than 25, additional settings configuration must be
performed.
To make the application wait for connection on port 1025 of interface
192.168.0.1:
assign the following value to the ListenOn parameter in the
[smtpgw.network] section:
ListenOn=192.168.0.1:1025
In order to use several particular interfaces, create several ListenOn parameter
records in the configuration file. E.g.:
ListenOn=192.168.0.1:25
ListenOn=10.0.0.1:25
®
Mail Gateway 5.5
6.3. Setting up the routing table
The application does not include a local agent used for message delivery,
therefore all incoming mail messages must be transferred to the local host where
such an agent is installed.
The rules for transferring (routing) are set by the ForwardRoute parameter in the
[smtpgw.forward] section.
This parameter is specified using one of the following formats:
ForwardRoute=<address_mask> <recipient>
ForwardRoute=<address_mask> [<recipient>]
ForwardRoute=<address_mask> [<recipient>:<port>]
where:
<address_mask> – the address of the recipient of the messages
(wildcards "*" and "?" can be used; if the parameter is assigned any
value, then any recipient’s address may be used).
<recipient> is the name of the domain containing the mail server,
where (according to MX records) the email must be sent.
[<recipient>:<port>] is the delivery point (IP address or host
name, port).
For example, if you create the following record in section [smtpgw.forward]:
ForwardRoute=*@domain.com [localhost:1025]
then all mail messages to domain.com will be sent to port 1025 of the local host
after an anti-virus scan and spam filtering.
Page 69

Advanced application settings 69
If several routing rules must be specified, create several copies of the
ForwardRoute parameter in the configuration file.
For example, record created in section [smtpgw.forward]:
ForwardRoute=*@domain1.com [localhost:1025]
ForwardRoute=*@domain2.com [somehost.somedomain.com]
ForwardRoute=*@domain3.com otherdomain.com
will mean the following processing rules
• forward all email messages for domain domain1.com to port 1025 of the
local host after anti-virus scanning and spam filtering.
• forward all email messages for domain domain2.com to port 25 of host
somehost.somedomain.com after anti-virus scanning and spam
filtering.
• forward all email messages for domain domain3.com to MX-host of
domain otherdomain.com after anti-virus scanning and spam filtering
(the domain will be determined at the time the message is sent).
• forward all other messages to the corresponding MX-hosts after anti-virus
scanning and spam filtering.
When determining the routing rules the first record will be used out
of those where the specified domain matches the domain of
message recipient.
:
6.4. Checking the configuration file
syntax
Use the -k or --check-config key in the application command line to check
the syntax of its configuration file.
If the configuration file contains no errors, the following line will be displayed in
the server console:
Config OK !
If the check reveals errors, the following line will appear in the server console:
Config is invalid see log for detail.
Page 70

70 Kaspersky
®
Mail Gateway 5.5
6.5. Syntax check in notification
templates
The application allows syntax checks of notification templates accomplished
using the kltlv utility installed by default in the /opt/kav/5.5/scm-smtpgw/bin
directory (in Linux distributions) or in /usr/local/share/kav/5.5/scm-smtpgw/bin (for
FreeBSD distributions)).
The kltlv utility can be started by a privileged user (root) only.
To check the syntax of a notification template, enter the following in the
command line:
# /opt/kav/5.5/scm-smtpgw/bin/kltlv ./dsn.tmpl
The utility will output to server console a report similar to the example below:
Kaspersky Template Language Verifier for Linux GLIBC 2.2
version 5.5.53/RELEASE,
Copyright (C) Kaspersky Lab, 1997-2006
Parsing error: Unexpected end of line in the declaration,
line 63
If a template check is successful, the utility will report that template syntax is
correct. In case of errors it will display a description of possible failure causes
(see section A.13 on p. 129). Utility return codes are described in section A.14 on
p. 131.
6.6. Work with email archive and the
quarantine directory
The klmaila utility allows management of objects preserved in the quarantine
directories and the archives of incoming/outgoing messages.
The klmaila utility can be started by a privileged user (root) only.
It offers the following opportunities:
• Reviewing of the whole storage contents or information on certain
messages, e.g.:
Page 71

Advanced application settings 71
>./klmaila --show-all --archivepath=/var/db/kav/5.5/scm-smtpgw/arch_in
Kaspersky Mail Archives Manager for Linux GLIBC
2.2 version 5.5.53/RELEASE,
Copyright (C) Kaspersky Lab, 1997-2006
--QueueID--Status-Size-------ArrivalTime-------
--------Sender.../Recipient...
iCMnF8AX05033 RCV 6375 Tue, 28 Dec 2004
12:22:49 +0000 172.16.10.16
<test2@smtpgw.avp.ru> -> <test1@smtpgw.avp.ru>
iCMmF84m00443 RCV 5050 Tue, 28 Dec 2004
12:22:48 +0000 172.16.10.16
<test2@smtpgw.avp.ru> -> <test1@smtpgw.avp.ru>
Total: 2 archived messages, 11425 bytes.
The application outputs information about messages preserved in storage
directory in the following format:
ID STATUS SIZE DATE IP <SENDER> -> <RECIPIENT>
where:
ID – identification number of a stored message
STATUS – message status reflecting its current state.
A stored message may have any of the following statuses:
as/spam – message with the Spam status assigned by the
Spamtest filter.
as/probable – message with the Probable Spam status
assigned by the Spamtest filter.
av/clean – message with the Clean status assigned by the AV
module.
av/disinfected – message with the Disinfected, status
assigned by the AV module.
av/infected – message with the Infected status assigned by
the AV module.
av/suspicious – message with the Suspicious status
assigned by the AV module.
av/protected – message with the Protected status assigned
by the AV module.
Page 72

72 Kaspersky
®
Mail Gateway 5.5
av/error – message with the Error status assigned by the
AV module.
av/filtered – message with the Filtered status assigned by
the AV module.
SIZE – message size (may be specified in bytes, kilobytes, and
megabytes as determined by the respective prefixes)
DATE – time and date of message receipt by the application
IP – IP address of message sender
SENDER – message sender’s address
RECIPIENT – message recipient’s address (the field may contain
several values).
• Removal of all messages or a specified message from storage, e.g,:
> ./klmaila --remove-all --archivepath=/var/db/kav/5.5/scm-smtpgw/arch_in
Kaspersky Mail Archives Manager for Linux GLIBC
2.2 version 5.5.53/RELEASE,
Copyright (C) Kaspersky Lab, 1997-2006
Total: 4586 archived messages have been
removed.
• Sending of all messages/certain messages from storage directories to
their original recipients, e.g.:
> ./klmaila --send-id=jHrWPC7s86253 --archivepath=/var/db/kav/5.5/scm-smtpgw/arch_in
Kaspersky Mail Archives Manager for Linux GLIBC
2.2 version 5.5.53/RELEASE,
Copyright (C) Kaspersky Lab, 1997-2006
Message with QueueID jHrWPC7s86253 will be sent
asap.
If the --send-id command line option is specified, the selected
message will pass anti-virus scanning and antispam filtering
procedure before it is delivered to the recipient. In order to
send a message from storage without its anti-virus scanning
and antispam filtration, use the --send-id-without-check
command line option.
Descriptions of command line options for klmaila utility can be
found in section A.16 on p. 133, its return codes are
Page 73

Advanced application settings 73
described in section A.17 on p. 134.
6.7. Management of application
working queue
While the application is running, it creates a working queue of messages for
processing by the Spamtest filter and the AV module.
The klmailq utility (installed by default in the /opt/kav/5.5/scm-smtpgw/bin
directory (in Linux distributions) or in /usr/local/share/kav/5.5/scm-smtpgw/bin (for
FreeBSD distributions)) allows management of messages in working queue.
The klmailq utility can be started by a privileged user (root) only.
It offers the following opportunities:
• Reviewing the contents of working queue or information on specific
messages in it.
To display the information about all messages in the working
queue, enter the following in the command line:
# ./klmailq --show-all
The utility will output to server console a report similar to the example
below:
Kaspersky Mail Queue Manager for Linux GLIBC
2.2 version 5.1.53/RELEASE,
Copyright (C) Kaspersky Lab, 1997-2006
--QueueID--Status-Size-------ArrivalTime-------
--------Sender.../Recipient...
iAgUF4Oi21098 WFS 1570 Tue, 12 Feb 2005
10:42:30 +0000 10.0.0.28
<test2@scmsmtpgw1.test.ru> ->
<test1@scmsmtpgw1.test.ru>
iAgVF4Qs38118 WFC 897 Tue, 12 Feb 2005
10:42:31 +0000 10.0.0.16
<test2@scmsmtpgw1.test.ru> ->
<test1@scmsmtpgw1.test.ru>
iAgTF45Y97588 SND 1048 Tue, 12 Feb 2005
10:42:29 +0000 10.0.0.16
Page 74

74 Kaspersky
®
Mail Gateway 5.5
<test2@scmsmtpgw1.test.ru> ->
<test1@scmsmtpgw1.test.ru>
Total: 3 queued messages, 3515 bytes.
The application outputs information about messages in working queue
in the following format:
ID STATUS SIZE DATE IP <SENDER> -> <RECIPIENT>
where:
ID – identification number of a queued message
STATUS – message status reflecting its current state.
A message in working queue may have any of the following
statuses:
WFC – message waiting for antispam filtration and anti-virus
scanning
CHK – message being scanned for virus presence
WFS – message waiting for creation of its virtual copies
SPL – message being used for creation of virtual copies
QUE – message waiting to be sent to its recipient
SND – message being sent.
SIZE – message size (may be specified in bytes, kilobytes, and
megabytes as determined by the respective prefixes)
DATE – time and date of message addition into the queue
IP – IP address of message sender
SENDER – message sender’s address
RECIPIENT – message recipient’s address (the field may contain
several values).
• Removal of all messages or a specified message from working queue.
below:
To remove all messages from the working queue, enter the
following in the command line:
# ./klmailq --remove-all
The utility will output to server console a report similar to the example
Kaspersky Mail Queue Manager for Linux GLIBC
2.2 version 5.1.53/RELEASE,
Copyright (C) Kaspersky Lab, 1997-2006
Page 75

Advanced application settings 75
Total: 12 queued messages have been removed.
A message can be removed from queue if it has WFC, WFS
or QUE status only.
• Send all or selected messages ahead of the general queue, e.g.:
> ./klmailq --send-id=jHrWPC7s86253
Kaspersky Mail Queue Manager for Linux GLIBC
2.2 version 5.1.53/RELEASE,
Copyright (C) Kaspersky Lab, 1997-2006
Message with QueueID jHrWPC7s86253 will be sent
asap.
A message can be sent ahead of the general queue only if it
has QUE status (expects delivery to the recipient).
Descriptions of command line options for klmailq utility can be
found in section A.15 on p. 132, its return codes are
described in section A.17 on p. 134.
6.8. Managing the application
While Kaspersky Mail Gateway is running, you can manage the application using
scripts, signals, and special control files.
This section describes how to manage the application using scripts (about
management options using signals, see section A.4 on p. 117; about using files
see A.5 on p. 118).
Application management using scripts requires privileged user (root)
rights.
If you use Linux distribution package (except for installations made
using the tar.gz package), to run the management script, enter the
following in the command line:
# /opt/kav/5.5/scm-smtpgw/init.d/smtpgw <action>
or use the link:
# /etc/init.d/scm-smtpgw <action>
Page 76

76 Kaspersky
If you use FreeBSD distribution package, to run the management script,
enter the following:
# /usr/local/etc/rc.d/scm-smtpgw.sh <action>
The /etc/init.d/scm-smtpgw link will not be created if you install the
application from a tar.gz package. You will have to create manually the
link pointing to the /opt/kav/5.5/scm-smtpgw/init.d/smtpgw management
script.
Table 2 contains possible values of the <action> parameter:
Table 2. Management script parameters
Value Meaning
®
Mail Gateway 5.5
start
stop
restart
reload
reloadbases
status
stats
recv-off
recv-on
send-off
send-on
chck-off
Start the application.
Stop the application.
Stop and then start the application.
Reinitialize the smtpgw component and reload the anti-virus
database and the configuration file, restart the Spamtest
filter.
Reload the anti-virus databases and restart the Spamtest
filter.
Request the application status.
Request the application statistics.
Suspend the operation of the Receiver module.
Resume the operation of the Receiver module.
Suspend the operation of the Sender module.
Resume the operation of the Sender module.
Suspend the operation of the scanning module.
chck-on
Resume the operation of the scanning module.
Page 77

Advanced application settings 77
After the Receiver module is suspended, mail servers will be unable to establish
connection with Kaspersky Mail Gateway to transfer messages to recipients
within your mail system. Messages added to the work queue will be scanned for
the presence of malicious objects and spam signs, processed in accordance with
the existing rules and forwarded to the recipients (unless the rules block their
delivery).
After the Sender module is suspended, Kaspersky Mail Gateway stops
transmitting processed messages. Processed messages will be preserved in the
work queue of outgoing messages. Suspension of the Sender module does not
affect the Receiver module. Receipt of messages from mail servers will not be
suspended.
After the scanning module is suspended, mail messages accepted by the
Receiver module will be transferred directly to the Sender module for subsequent
delivery to recipients. Anti-virus scanning, spam filtering and message
processing will not be performed.
6.9. Control of application activity
A special watchdog process controls correct functioning of individual application
modules while the software is running. As soon as the application starts, it
creates a child process monitoring the application. If upon a specified interval the
parent process receives no confirmation of correct operation from any module,
the watchdog process restarts the application.
You can control timeouts of the watchdog process using the
application command line options. See section A.7 on p. 124 for
details.
6.10. Customizing date and time
formats
Kaspersky Mail Gateway generates reports on the activity of every component.
This information always contains the date and time of report generation.
By default, Kaspersky Mail Gateway displays the date and time according to the
strftime standard:
%H:%M:%S – displayed time format.
%d/%m/%y – displayed date format.
Page 78

78 Kaspersky
The administrator can customize how the time and date are displayed in the
[locale] section of the application configuration file. You can specify one of the
following formats:
%I:%M:%S %P – display time in 12-hour format (TimeFormat parameter).
%y/%m/%d or %m/%d/%y – display date (DateFormat parameter) as
yy/mm/dd or mm/dd/yy, respectively).
®
Mail Gateway 5.5
6.11. Reporting options
The performance of the smtpgw component is recorded in the report file that is
output into the application log file in plain text format (LogFilename option in the
[smtpgw.options] section) or in the system log (syslog). The data is not logged
if the LogFilename option is not defined (LogFilename=).
To customize the output data, change the report detail level (LogLevel option in
the [smtpgw.options] section).
Report detail level is a number that defines the level of reported details for
application performance data. Each subsequent level of detail contains all the
details from the previous level and adds some new information.
Table 3 below lists possible report detail levels.
Table 3. Report detail levels
Level
0 Fatal Errors F
1 Errors E
2 Warning W
3 Info, Notice I
Level
description
Letter symbol
Meaning
Only information regarding critical
errors (that terminate the program
due to impossibility of executing
an action). For example, the
component is infected, or
scanning, database loading, or
license key loading failed.
Information about other errors that
may or may not lead to application
shutdown, for example, file scan
errors.
Notifications about errors that may
lead to the application shutdown
(license key expiration warning,
out-of-disk-space warning, etc.).
Important informational
messages, such as whether a
Page 79

Advanced application settings 79
Level
Level
description
Letter symbol
Meaning
component is running or inactive,
the path to the configuration file,
latest changes in scan area,
database updates, license keys,
statistics summary.
4 Activity A
Messages on scanning of files
according to the report detail level.
9 Debug D All debug messages.
Information about fatal errors is always displayed, regardless of the report detail
level. The optimal level is level 4, which is also the default level.
Information messages may be divided into the following types:
• Messages about the actions applied to email messages
• Notifications about system events
• Other messages (component start, loading of databases, return codes,
etc.).
The output format for each of the detail level listed above is as follows :
• for messages about the actions applied to email messages:
[date time detail_level] envelope-id: MESSAGE;
• for all other types of messages:
[date time detail_level]: MESSAGE,
where:
• [date time detail_level] is the record that contains the
date and the time (in the format specified by the administrator in
the [locale]) section and the letter indicating the report detail
level.
• envelope-id – email message identifier in the working queue
of the application, to which the email message corresponds.
• MESSAGE – message text that may have different formats
depending on the type of the message.
For the text of messages containing information about actions applied to email
messages see section A.20 on p. 137.
Page 80

80 Kaspersky
®
Mail Gateway 5.5
6.12. Additional informational
header fields in messages
Application allows addition of some supplementary information to mail
messages. Let us examine closer two methods of adding new informational
header fields to a message:
• Add extension header field to mail message.
The information may describe application version, date when the antivirus databases were last updated, time and result of message scanning
(determined by the AddXHeader parameter in the [smtpgw.policy]
section of the application configuration file).
Header format:
X-Anti-Virus: <product name and version>, bases: <date
of the last update to anti-virus databases in YYYYMMDD
format> #<the number of records in AV databases>,
check: <scan date in YYYYMMDD format> <scanning status
or not_checked>
E.g.:
X-Anti-Virus:Kaspersky Mail Gateway for Linux GLIBC
2.2 version 5.5.58/RELEASE, bases: 20041101 #102746,
check: 20041210 clean
• Add disclaimer text to mail message body.
The information will be added as plain text; it may contain any statement
generated in accordance with the security policy (or other rules) of a
specific organization (the AddDisclaimer parameter in the
[smtpgw.policy] section). The default message text notifies that the
message has been scanned by Kaspersky Mail Gateway. Upon
administrator’s demand the application can modify the information format
(e.g., generate disclaimer message as a HTML text).
Page 81

CHAPTER 7. TESTING
APPLICATION OPERABILITY
After you install and configure Kaspersky Mail Gateway, it is recommended that
you test its settings and operability by using the following three methods:
• Telnet program
• Mail messages containing test phrases in the Subject header
• EICAR test virus.
7.1. Testing the application using
Telnet
To test the application operation using Telnet it is necessary to:
1. Configure the connection to the server with the installed application
using Telnet. To do so, enter the following in the command line:
telnet <smtpgw host address> <port>
where the host address and port are values assigned to the
ListenOn option in the [smtpgw.network] section of the
application configuration file.
2. After the connection is established, wait for a response from the
smtpgw component. You will see the following information:
220 smtpgw.company.com ESMTP
where smtpgw.company.com is the name of the server being
tested.
3. After the connection to the server is confirmed, type the following in
the command line:
EHLO <fqdn>
where <fqdn> stands for a full domain name of the host, which
establishes connection.
You will see the following (or similar) information:
Page 82

82 Kaspersky
250-smtpgw.company.com hello user [127.0.0.1]
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-8BITMIME
250-SIZE 10485760
250 DSN
where:
smtpgw.company.com is the name of the server being tested
user is the client host name
[127.0.0.1] is the client IP address.
Enter in the command line:
MAIL FROM: <sender_address>
You will see the following (or similar) information:
250 2.1.0 OK
Enter in the command line:
RCPT TO: <recipient_address>
You will see the following (or similar) information:
250 2.1.0 OK
Enter in the command line:
DATA
You will see the following (or similar) information:
354 Start mail input; end with <CRLF>.<CRLF>
Enter in the command line:
Subject: test
test
.
You will see the following (or similar) information:
250 2.1.0 OK
4. If the response is 250 2.1.0 OK, the test message has been
successfully accepted by the server. After this, the message must
be checked by Spamtest, scanned for viruses and then sent to the
recipient in accordance with the routing table. It is recommended
that you check message delivery. To verify the results, view the
®
Mail Gateway 5.5
Page 83

Testing application operability 83
application statistics. One message will be added to the totals of
scanned and sent messages.
7.2. Testing the Spamtest filter
In order to test the Spamtest filter functionality, you have to create email
messages containing specific phrases in the Subject header. Table 4 below
contains a summary of test phrases and Spamtest responses thereto.
Table 4. Test messages
Test phrase in the Subject
header
Subject: spam is bad do
not send it
or
Subject: t h i s i s n o
t s p a m
Subject: News and
special events May
Subject: Out of Office
AutoReply
Text of the Subject header
contains an invective.
Having sent a message containing a test phrase in the header, make sure that
the message has been processed in accordance with the specified rules (the
application has changed respective message headers; the message has been
added to the quarantine directory, etc.). If the application does not function
properly, you should consult the Technical Support service of Kaspersky Lab.
Based on performed analysis, the
message will be assigned the Spam
status. It will be processed according to
the action specified by the ActionSpam
option.
Based on performed analysis, the
message will be assigned the Probable
Spam status It will be processed
according to the action specified by the
ActionSpam option.
Based on performed analysis, the
message will be assigned the Not
detected status. The [--Formal
Messages--] label will be added to its
Subject header
Based on performed analysis, the
message will be assigned the Not
detected status. The [--Obscene--] label
will be added to its Subject header/
Spamtest filter response
Page 84

84 Kaspersky
®
Mail Gateway 5.5
7.3. Testing the application using
EICAR
This test "virus" has been developed by (The European Institute for
Computer Anti-Virus Research) specifically for the purpose of verification of the
anti-virus software operation.
It IS NOT A VIRUS and contains no code that may harm your computer.
However, most products of anti-virus vendors identify it as a virus (The European
Institute for Computer Antivirus Research).
Never use real viruses to test the operation of your anti-virus
application!
The test "virus" can be downloaded from the official site of EICAR at:
http://www.eicar.org/anti_virus_test_file.htm
can create a test "virus" manually. To do so, enter the line below in any text
editor and save the file as eicar.com:
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TESTFILE!$H+H*
The file that you downloaded from the EICAR site or created in a text editor as
described above, contains the body of a standard test "virus". The anti-virus
application will detect it, flag it as Infected and perform the specified action for
objects with this status.
To test the application's response to other types of objects, modify the body of
the standard test "virus" by adding one of the prefixes below (see Table 5).
You can verify the proper operation of Kaspersky Mail Gateway using
modifications of the EICAR "virus" only if your anti-virus databases
were last updated on or after October 24, 2003, or has the cumulative
updates for October 2003.
. If you have no Internet access, you
Table 5. Test "virus" modifications
Prefix Object type
No prefix,
standard test
"virus""
CORR–
SUSP–
Infected. An error occurs during disinfection. The object will
then be deleted.
Corrupted.
Suspicious (unknown virus code).
Page 85

Testing application operability 85
Prefix Object type
WARN–
ERRO–
Suspicious (modified code of a known virus).
Causes a scanning error identical to the detection of a
corrupted object.
CURE–
Infected. The object will be disinfected and the text in the
infected file will be changed to CURE.
DELE–
Infected. The object will be deleted automatically.
The first column of the table contains the prefixes that should be added to the
beginning of the line in the standard test "virus" file (e.g.,
DELE–X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUSTEST-FILE!$H+H*).
After adding a prefix to the test “virus”, save it to a file with another name, for
example eicar_dele.com; assign names to all the modified “viruses” in the same
manner.
The second column contains the types of objects identified by the anti-virus
application after you added a prefix. The actions for each type of object are
defined by the application's settings customized by the administrator.
Page 86

CHAPTER 8. UNINSTALLING
THE APPLICATION
To uninstall Kaspersky Mail Gateway from server, you must be a privileged
(root) user. If you are currently logged under a user account with lesser
privileges, log on as root.
The uninstallation process will automatically stop the application!
When you are uninstalling the product, the application will be stopped, and all
files and directories created during installation will be deleted. However, files and
directories created or modified by the administrator, such as the application
configuration file, notification templates, the quarantine directories, archives of
received and sent messages, anti-virus and content filtration databases, license
key file, will remain.
There are several different ways to run the uninstall procedure, depending on the
package manager you used. Below is a detailed description of these options.
If you installed the application from the rpm package, type the
following in the command line to uninstall Kaspersky Mail Gateway:
# rpm -e <package_name>
If you installed the application from the deb package, type the following
in the command line to uninstall Kaspersky Mail Gateway:
# dpkg -P <package_name>
if you wish to remove the application together with its configuration
files, or:
# dpkg -r <package_name>
if you wish to remove the application but preserve its configuration
files.
If you installed the application from the universal package (tar.gz), type
the following in the command line to uninstall Kaspersky Mail
Gateway:
# /opt/kav/5.5/scm-smtpgw/setup/uninstall.pl
Page 87

Testing application operability 87
If you installed the application from the pkg package, type the following
in the command line to uninstall Kaspersky Mail Gateway:
# pkg_delete <package_name>
After the application has been successfully removed from your server, you will
see a corresponding message on your screen.
Page 88

CHAPTER 9. FREQUENTLY
ASKED QUESTIONS
This chapter contains a discussion of questions most frequently asked by our
users regarding the installation, configuration and operation of the application.
Question
products of other vendors?
No. We recommend uninstalling anti-virus products of other vendors
prior to installation of Kaspersky Mail Gateway to avoid software
conflicts.
Question
been scanned earlier. Why?
This is true. The application does not rescan files that have not changed
since the last scan.
That has become possible due to new iChecker™. The technology is
implemented in the program using a database of file checksums.
Question: Why does Kaspersky Mail Gateway cause a certain decrease
in server performance, noticeably loading the CPU?
Virus detection is a computationally intensive mathematical problem
requiring structural analysis, checksum calculation and mathematical
data conversions. Processor time is therefore the main resource
consumed by the program, and each new virus added to the anti-virus
databases increases the overall scanning time. This is a necessary
sacrifice for the security and safety of your data.
Other anti-virus products speed up scanning by excluding both viruses
which are less easily detectable or less frequent in the geographic
location of the anti-virus vendor, and file formats that require
complicated analysis (e.g. PDF) from their databases.
In contrast, Kaspersky Lab believes that the purpose of its products is to
establish real and complete security for its users.
Kaspersky Mail Gateway gives its users maximum protection.
Experienced users can accelerate anti-virus scanning to the detriment
of overall security by disabling scanning of various file types, but we do
not recommend doing so for users who want the best protection.
: Is it possible to use Kaspersky Mail Gateway with anti-virus
: Kaspersky Mail Gateway does not rescan files that have
Page 89

Frequently asked questions 89
For maximum user protection, Kaspersky Mail Gateway recognizes
more than 700 formats of archived and compressed files. This is
essential for anti-virus security, because harmful executable code may
be hidden inside files of any recognized format. However, despite the
daily growth in the number of viruses detected by Kaspersky Mail
Gateway (approximately 30 new viruses appear daily) as well as the
ever increasing number of recognized file formats, each subsequent
version of our product functions faster than the previous one. That is
achieved through the use of new, exclusive technologies, such as
iChecker™, developed at Kaspersky Lab.
Question: Why do I need the key file? Will my Kaspersky Mail Gateway
work without it?
No, Kaspersky Mail Gateway does not work without a license key.
If you are still deciding whether or not to purchase Kaspersky Mail
Gateway, we can provide you with a temporary key file (trial key), which
will only work either for two weeks or for a month. When this period
expires, the key will be blocked.
Question: What happens when the license expires?
After expiration of the license, Kaspersky Mail Gateway will continue
operating, but updating of the anti-virus and content filtration databases
will be disabled. The Kaspersky Mail Gateway will continue cleaning
infected objects but only using the old anti-virus databases.
If such a situation arises, notify your system administrator and contact
the company where you have purchased Kaspersky Mail Gateway or
Kaspersky Lab directly for license renewal.
Question: The application does not work. What should I do?
First, check if a solution for your problem is provided in this
documentation, especially in this section or on our website.
In addition, we recommend that you apply for support to the distributor
from whom you purchased Kaspersky Mail Gateway or write to our
Technical support service (support@kaspersky.com
) or to the address
contained in the license key information.
To make sure your request is answered as soon as possible, follow
these suggestions:
Page 90

90 Kaspersky
1. In the message header, specify your operating system, the name
of Kaspersky Lab product you are experiencing problems with, and
briefly describe the problem. For example:
FreeBSD 5.3, Kaspersky Mail Gateway 5.5, updating of the
anti-virus databases does not function.
2. Compose your messages in plain text format.
3. At the beginning of the message, specify the exact versions of the
operating system and Kaspersky Mail Gateway distribution
package and provide the number of your license key file.
4. Clearly describe the problem in brief. Keep in mind that, when
reading your mail, the technical support service officers do not yet
know about your problem. They can only help after fully
understanding and reproducing it.
5. Send the following data, packed into one archive, to the Technical
Support Service:
• log file (report file) produced by Kaspersky Mail Gateway while
running.
• configuration file of Kaspersky Mail Gateway
• your license key file.
6. Make sure to specify in your mail if your computer system contains
any of the following:
• a very old or very new processor, or more than one processor
• less than 64 MB or more than 2 GB of RAM.
7. Specify the approximate amount of daily traffic and whether or not
the server has peak loads.
®
Mail Gateway 5.5
Question: What are the daily updates for?
A few years ago viruses were transmitted on floppy disks, and adequate
computer protection could be achieved by installation of an anti-virus
program followed by rare updates to its anti-virus database. However,
recent virus epidemics spread around the world in several hours, and
anti-virus protection with old databases may be helpless against a new
threat. In order to resist new viruses, you should update the anti-virus
databases every hour.
Every year Kaspersky Lab increases the frequency of its updates issued
for the anti-virus databases. Currently they are updated every hour.
Page 91

Frequently asked questions 91
Spam is a serious problem for all network users being a direct and
obvious threat to businesses. According to the latest data, the volume of
spam in the Internet is about 75-80 percents of the total mail volume
and new types of spam appear constantly. Fast response to
appearance of such unwanted message types and blocking of their
spreading requires timely updates to the content filtration database
employed for spam filtering. New updates to the content filtration
database are made available on the update servers of Kaspersky Lab
every 20 minutes.
Since the update frequency of the anti-virus and content filtration
databases are different, you are advised to set up the updates to run at
a 20 minutes interval. After connection, the application identifies
available updates automatically and downloads them.
Question: What are the changes to the updating service of version 5.0?
The Kaspersky Lab 5.0 product suite features a new updating service,
which has been developed in accordance with the requests of our
users. It automates the whole updating procedure, from the preparation
of updates in Kaspersky Lab to the moment that relevant files are
updated on clients' computers.
Advantages of the new updating service include:
• Ability to resume downloading of files after disconnection. Upon
reconnection only files which have not been downloaded are
retrieved.
• Cumulative updates are now half the size. A cumulative update
contains the whole anti-virus database, therefore its size
exceeds considerably the size of typical updates. The new
service employs a special technology which allows using
already existing anti-virus database for a cumulative update.
• Accelerated downloading from the Internet. Kaspersky Mail
Gateway picks up a Kaspersky Lab's updates server located in
your region. Furthermore, servers are allocated according to
their performance, so you will not be sent to an overloaded
server while there is another idle server available.
• Use of key «black lists». Unlicensed and illegal users of
Kaspersky Mail Gateway are now prevented from using the
updating service. Licensed users therefore do not suffer from
inability to contact overloaded updates’ servers.
• Corporate enterprises can now create a local updates' server.
This feature is designed for organizations where a single LAN
Page 92

92 Kaspersky
unites computers protected by Kaspersky Lab products. Any
computer on the LAN can be turned into an updates’ server that
retrieves updates from the Internet and shares them with the
other networked computers.
Question: Can an intruder deliberately replace the anti-virus or content
filtration databases?
Every anti-virus and content filtration database has a unique signature
verified by Kaspersky products while accessing the database. If the
signature does not correspond to the one assigned at the Kaspersky
Lab, or the date of the database is later than that of the license expiry,
Kaspersky Mail Gateway will not use it.
Question: The application cannot be started, the Sender module does
not work, etc. What should I do?
If, due to incorrect settings, the number of running processes (threads)
exceeds the maximum number permitted by the system, the application
performance may be affected or your system will freeze.
To solve this problem, it is recommended to decrease the number of
concurrently active incoming and outgoing mail sessions and the
number of objects scanned simultaneously by the anti-virus module
(AntiviralSessions, IncomingSessions, and OutgoingSessions
parameters in the [smtpgw.limits] section of the application
configuration file).
The second solution for the problem would be to decrease the stack
size.
®
Mail Gateway 5.5
This command works in Linux operating system only.
Enter the following in the command line:
#ulimit –s
The maximum stack size will be displayed on the console. Set the new
value equal to the quarter of the current value by entering the following:
#ulimit –s <number>
where <number>
is a new maximum stack size.
Page 93

Frequently asked questions 93
Question: What should I do to make man pages of the application
available by the command man <name>?
To make application man pages available for the man <name>
command, do the following:
• For Debian and SuSE Linux distributions, the following line
should be added to the /etc/manpath.config file:
MANDATORY_MANPATH /opt/kav/5.5/scm-smtpgw/man
• For RedHat and Mandriva Linux distributions, the following line
should be added to the /etc/man.config file:
MANPATH /opt/kav/5.5/scm-smtpgw/man
• For FreeBSD distributions, the following line should be added to
the /etc/manpath.config file:
MANDATORY_MANPATH /usr/local/share/kav/5.5/scmsmtpgw/man
In addition, if the MANPATH variable is used in your system, add into
the list of its values a path to the directory containing the application's
man pages by running the following command:
# export MANPATH=$MANPATH:<path to the man pages
directory>
Question
occurs during operation of the application or the following message
appears at application startup: "smtpgw could not be started",
: What should I do if error LibKAVEngine Init error: err_no=3
accompanied by return codes 46 or 48?
The error may occur if you are using a non-standard directory for
storage of temporary files (by setting the values of the TMP or TEMP
environment variables) and user account employed by the application
(kavuser by default) is not allowed to access that directory for writing.
E.g., such error may be encountered when the application is installed
under Mandriva Linux distribution (which uses /root/tmp/ as the default
directory for storage of temporary files of root user).
To resolve the problem, you should either change access rights for the
directory or redefine/delete the TMP and TEMP environment variables
to force the use of another directory (e.g., /tmp/) with the access rights
necessary for normal operation of the application.
Page 94

94 Kaspersky
®
Mail Gateway 5.5
Question: What should I do if the application does not start and the
"Unable to connect to: unix:
/var/db/kav/5.5/scm-smtpgw/spamtest/control/spamtest.socket,
sts_init() failed(err=Cannot connect to specified address)" error
occurs?
Such errors are caused by very strict limitations of default privileges for newly
created files (the umask system parameter is assigned the 0222 value). Define
less strict limitations of privileges by specifying another value for the said
parameter.
Page 95

APPENDIX A.
SUPPLEMENTARY INFORMATION ABOUT THE PRODUCT
This annex describes the distribution of the application files after installation
including a detailed description of the configuration file, command line keys for
every component and their return codes, and generation of operational statistics.
A.1. Distribution of the application
files in directories
After the installation of Kaspersky Mail Gateway is complete, the application files
will be located in the following directories, provided that the default paths have
been accepted during the installation:
Linux distribution kit:
/opt/kav/5.5/scm-smtpgw/ – main application directory. This directory includes:
/bin/ – directory containing executable files of the application components:
smtpgw – executable file of the anti-virus protection component.
keepup2date – executable file of the component responsible for
updating the anti-virus and content filtration databases.
licensemanager – executable file of the component responsible for
management of license keys.
kltlv – utility employed for template syntax checks.
klmailq – utility for management of the application working queue.
klmaila – utility for management of message archives.
avbasestest – utility validating downloaded updates to the anti-virus
databases prior to their installation.
/spamtest/ – directory containing the executable files of the Spamtest
filter.
Page 96

96 Kaspersky
®
Mail Gateway 5.5
/setup/ – directory containing scripts and executable files used during the
installation, post-install setup and removal of the application.
/init.d/ – directory containing scripts used to control the application. Link to
controlling script is also added to the /etc/init.d/ directory.
/man/ – directory containing application manual pages.
/etc/kav/5.5/scm-smtpgw/ – directory containing the smtpgw.conf default
application configuration file.
/var/db/kav/5.5/scm-smtpgw/ – directory containing application data and
including the following subdirectories and files:
/bases/ – directory containing the anti-virus databases and the
updcfg.xml configuration file of the keepup2date component.
/bases.backup/ – directory where the keepup2date component saves
backup copies of the anti-virus and content filtration databases.
/licenses/ – directory where the license key files are installed.
/patches/ – directory where the updates for the application components
are saved.
/quarantine/av/ – directory used by the application to store messages
that have been assigned statuses specified in the
QuarantineMessage parameter of the application configuration
file.
/quarantine/spam/ – directory used by the application to store messages
that have been assigned statuses specified in the
QuarantineMessage parameter of the application configuration
file.
/arch_in/ – directory for storing the archive of all received email
messages.
/arch_out/ – directory for storing the archive of all sent email messages.
/stat/ – directory for storing the statistics file.
/templates/ – directory where the default application template files are
installed:
notify.tmpl – template for notification messages.
placeholder.tmpl – template used for replacing an infected
object with a message.
dsn.tmpl – template used for DSN messages generated by the
application.
Page 97

Appendix A 97
disclaimer.tmpl – template used for generation of the
disclaimer text appended to mail messages.
/ichecker/ – directory for storing the working files of the iChecker
database.
/spamtest/ – directory containing the files required for operation of the
Spamtest filter.
/var/spool/kav/5.5/scm-smtpgw/ – directory used by the application to store the
working queue of messages.
/var/log/kav/5.5/scm-smtpgw/ – directory for storing log files.
FreeBSD distribution kit:
/usr/local/share/kav/5.5/scm-smtpgw/ – main application directory. This directory
includes:
/bin/ – directory containing executable files of the application components:
smtpgw – executable file of the anti-virus protection component;
keepup2date – executable file of the component responsible for
updating the anti-virus and content filtration databases.
licensemanager – executable file of the component collecting
information about license keys.
kltlv – utility employed for template syntax checks.
klmailq – utility for management of the application working queue.
klmaila – utility for management of message archives.
avbasestest – utility validating downloaded updates to the anti-virus
databases prior to their installation.
/spamtest/ – directory containing the executable files of the Spamtest
filter.
/setup/ – directory containing scripts and executable files used during the
installation, post-install setup and removal of the application.
/man/ – directory containing application manual pages.
/usr/local/etc/rc.d/ – directory containing scripts used to control the application.
/etc/kav/5.5/scm-smtpgw/ – directory containing the smtpgw.conf default
application configuration file.
/var/db/kav/5.5/scm-smtpgw/ – directory that contains application data including
the following directories and files:
Page 98

98 Kaspersky
®
Mail Gateway 5.5
/bases/ – directory containing the anti-virus databases and the
updcfg.xml configuration file of the keepup2date component.
/bases.backup/ – directory where the keepup2date component saves
backup copies of the anti-virus and content filtration databases.
/licenses/ – directory where the license key files are installed.
/patches/ – directory where the updates for the application components
are saved.
/quarantine/av/ – directory used by the application to store messages
that have been assigned statuses specified in the
QuarantineMessage parameter of the application configuration
file.
/quarantine/spam/ – directory used by the application to store messages
that have been assigned statuses specified in the
QuarantineMessage parameter of the application configuration
file.
/arch_in/ – directory for storing the archive of all received email
messages.
/arch_out/ – directory for storing the archive of all sent email messages.
/stat/ – directory for storing the statistics file.
/templates/ – directory where the default application template files are
installed:
notify.tmpl – template for notification messages.
placeholder.tmpl – template used for replacing an infected
object with a message.
dsn.tmpl – template used for DSN messages generated by the
application.
disclaimer.tmpl – template used for generation of the
disclaimer text appended to mail messages.
/ichecker/ – directory for storing the working files of the iChecker
database.
/spamtest/ – directory containing the executable files of the Spamtest
filter.
/var/spool/kav/5.5/scm-smtpgw/ – directory used by the application to store the
working queue of messages.
/var/log/kav/5.5/scm-smtpgw/ – directory for storing log files.
Page 99

Appendix A 99
A.2. Kaspersky Mail Gateway
configuration file
The default installation package of Kaspersky Mail Gateway includes the
smtpgw.conf file containing the application settings.
This configuration file is divided into sections that describe parameters of all
individual groups of application features.
Each section is described in the following way: first line – the heading [section
name], then follow the lines containing the description of the parameter
represented as parameter=description. The description of each section of the
configuration file is completed by the header of the next section.
Instead of true|false values for Boolean settings in the configuration
file, you may also use equivalent values: yes|no, y|n or 1|0.
The options described as “required parameters” are critical for normal
functioning of the application. Without these parameters, the
configuration file is invalid!
The [path] section contains options that define the path to the critical files, which
are necessary for the application to work properly:
BasesPath – full path to the directory containing the anti-virus and content
filtration databases. Required parameter.
LicensePath – full path to the directory containing license keys. Required
parameter.
The [locale] section contains date and time formats:
DateFormat – format used by the components to display date in the report
(strftime).
You can change the date format to be displayed in email
messages, e.g.: %y/%m/%d or %m/%d/%y.
TimeFormat – format used by the components to display time in the report
(strftime).
You can alter the time presentation to 12-hour format (a.m.,
p.m.) using the string: %I:%M:%S %P
The [smtpgw.access] section includes the following options used to control the
access for SMTP clients:
Page 100

100 Kaspersky
®
Mail Gateway 5.5
ConnectRule – defines application behaviour during establishment of an
SMTP session.
Syntax:
ConnectRule=allow|deny from in_dnsbl|out_dnsbl to
<rcpt>|<rcpt_mask>
or
ConnectRule=allow|deny from has_name|no_name to
<rcpt>|<rcpt_mask>
or
ConnectRule=allow|deny from any to <rcpt>|<rcpt_mask>
where has_name|no_name corresponds to a situation, when the
program can/cannot obtain host name at the specified address,
in_dnsbl|out_dnsbl corresponds to the situation, when host address is
included/not included into the black lists of DNS BL services specified
by the DNSBlackList parameter. The <rcpt>|<rcpt_mask> value
determines the mail recipient or a mask for email addresses of
recipients. The any keyword allows any recipient’s address. During rule
selection from a list the program will use the first one matching the
recipient’s address mask.
If a rule has been applied, the establishment/termination of an email
session will be determined by the specified allow|deny value.
HeloRule – defines application response to HELO/EHLO command
received from a client.
Syntax:
HeloRule=allow|deny from has_ip|no_ip to
<rcpt>|<rcpt_mask>
or
HeloRule=allow|deny from same_ip|diff_ip to
<rcpt>|<rcpt_mask>
or
HeloRule=allow|deny from any to <rcpt>|<rcpt_mask>
where has_ip|no_ip corresponds to a situation, when it is
possible/impossible to receive an address from the host name
transferred by client as a parameter for the HELO/EHLO SMTP
command, while same_ip|diff_ip corresponds to a situation, when an
address received from that name matches/doesn't match the actual
address of the client that has established the connection. The
<rcpt>|<rcpt_mask>value determines the mail recipient or a mask for
email addresses of recipients. The any keyword allows any recipient’s
address. During rule selection from a list the program will use the first
one matching the recipient’s address mask.
 Loading...
Loading...