Kaspersky ANTI-VIRUS PERSONAL PRO 5.0 User Manual

KASPERSKY LAB
Kaspersky Anti-Virus® Personal Pro
5.0
USER'S GUIDE

KASPERSKY ANTI-VIRUS® PERSONAL PRO 5.0
User's Guide
© Kaspersky Lab
http://www.kaspersky.com
Revision date: April, 2006

Contents
CHAPTER 1. INTRODUCTION ...................................................................................... 6
1.1. Computer viruses and malicious computer programs ......................................... 6
1.2. The purpose and major functions of Kaspersky Anti-Virus Personal Pro ......... 10
1.3. What's new in Version 5.0?................................................................................. 13
1.4. Hardware and software system requirements ................................................... 14
1.5. Distribution Kit...................................................................................................... 15
1.6. Services provided for registered users ............................................................... 16
1.7. Conventions......................................................................................................... 17
CHAPTER 2. INSTALLING THE APPLICATION......................................................... 18
CHAPTER 3. PREVENTING COMPUTER INFECTION............................................. 25
3.1. Symptoms of infection......................................................................................... 25
3.2. What should you do if you notice symptoms of infection................................... 26
3.3. Safety rules.......................................................................................................... 27
CHAPTER 4. ANTI-VIRUS PROTECTION USING KASPERSKY ANTI-VIRUS
DEFAULT SETTINGS................................................................................................ 30
4.1. Real-Time Protection........................................................................................... 31
4.2. On-Demand Scan ............................................................................................... 32
4.3. Updating the anti-virus database ........................................................................ 34
CHAPTER 5. APPLICATION INTERFACE.................................................................. 35
5.1. System Tray Icon................................................................................................. 35
5.2. Shortcut menu ..................................................................................................... 36
5.3. Main application window: general structure........................................................ 37
5.3.1. Protection tab................................................................................................ 39
5.3.2. Settings tab ................................................................................................... 40
5.3.3. Support tab.................................................................................................... 41
5.4. Scan window ....................................................................................................... 42
5.5. Application reference system.............................................................................. 44
CHAPTER 6. USING THE APPLICATION................................................................... 45

4 Kaspersky Anti-Virus
®
Personal Pro
6.1. Updating the anti-virus database ........................................................................ 45
6.1.1. When should you download updates? ........................................................ 46
6.1.2. On-demand updates..................................................................................... 47
6.2. Real-time protection ............................................................................................ 47
6.2.1. Checking the protection status..................................................................... 48
6.2.2. Stopping real-time protection ....................................................................... 48
6.3. On-demand scan................................................................................................. 49
6.3.1. When do I need to perform an anti-virus scan? .......................................... 50
6.3.2. Starting an on-demand scan........................................................................ 51
6.3.3. On-demand scan of selected objects .......................................................... 52
6.3.4. Scanning archives ........................................................................................ 55
6.3.5. Scanning removable drives.......................................................................... 57
6.4. Dealing with viruses............................................................................................. 58
CHAPTER 7. CONFIGURING THE APPLICATION.................................................... 62
7.1. Configuring updates ............................................................................................ 62
7.1.1. Selecting the updates source....................................................................... 63
7.1.2. Configuring proxy server parameters .......................................................... 65
7.1.3. Updating Kaspersky Anti-Virus application modules................................... 67
7.1.4. Which anti-virus database should be used.................................................. 69
7.2. Configuring real-time protection.......................................................................... 71
7.2.1. File protection................................................................................................ 71
7.2.2. Mail protection............................................................................................... 76
7.2.3. Macros monitoring ........................................................................................ 82
7.2.4. Scripts monitoring ......................................................................................... 83
7.2.5. Protection against network attacks ..............................................................85
7.3. Configuring on-demand scan settings ................................................................ 87
7.3.1. Creating a new task...................................................................................... 89
7.3.2. Configuring the scan settings ....................................................................... 90
7.4. Creating a list of exclusions................................................................................. 97
7.5. Monitoring software processes ......................................................................... 101
7.6. Creating a task launch schedule....................................................................... 103
7.7. Running a task on behalf of another user's account ........................................ 106
CHAPTER 8. ADDITIONAL FUNCTIONALITY.......................................................... 108
8.1. Configuring quarantine and backup storage settings....................................... 108
8.2. Working with quarantined objects..................................................................... 110

Contents 5
8.3. Working with backup copies of objects............................................................. 112
8.4. Working with reports.......................................................................................... 114
8.4.1. Displaying reports ....................................................................................... 117
8.4.2. Exporting and sending reports ................................................................... 118
8.5. Managing Kaspersky Anti-Virus configuration ................................................. 119
8.6. Additional settings of Kaspersky Anti-Virus Personal Pro................................ 120
8.7. Configuring prompts for confirmation................................................................ 125
8.8. Restricting the functionality of Kaspersky Anti-Virus........................................ 126
8.9. Working in the administrator’s and the user’s mode ........................................ 127
CHAPTER 9. RENEWING YOUR LICENSE .............................................................128
CHAPTER 10. MANAGING APPLICATION FROM COMMAND LINE.................... 132
10.1. Scanning selected objects ..............................................................................133
10.2. Full scan........................................................................................................... 135
10.3. Launching updates.......................................................................................... 136
10.4. Last update rollback ........................................................................................137
10.5. Real-time protection mode.............................................................................. 138
10.6. Starting application .......................................................................................... 138
10.7. Closing application .......................................................................................... 139
10.8. Managing tasks ...............................................................................................139
10.9. Importing/exporting settings............................................................................ 141
10.10. Adding a license key .....................................................................................141
CHAPTER 11. FREQUENTLY ASKED QUESTIONS............................................... 143
APPENDIX A. CONTACTING TECHNICAL SUPPORT .................................. 148
APPENDIX B. GLOSSARY................................................................................ 151
APPENDIX C. KASPERSKY LAB...................................................................... 157
C.1. Other Kaspersky Lab Products ....................................................................... 158
C.2. Contact Us........................................................................................................ 165
APPENDIX D. LICENSE AGREEMENT............................................................ 166

CHAPTER 1. INTRODUCTION
1.1. Computer viruses and malicious
computer programs
As modern computer technology and communications tools develop, hackers
have more opportunities for spreading threats. Let’s take a closer look at them:
The Internet
The Internet is unique, since it is no one’s property and has no geographical borders. In many ways, this has promoted development of
countless web resources and the exchange of information. Today, anyone
can access data on the Internet or create their own webpage.
However, these very features of the worldwide web give hackers the ability to commit crimes on the Internet, making them difficult to detect and
punish as they go.
Hackers place viruses and other malicious programs on Internet sites and
disguise it as useful freeware. Furthermore, scripts that run automatically
when you open a webpage can execute dangerous actions on your computer, including modifying the system registry, stealing personal data, and
installing malicious software.
By using network technologies, hackers can attack remote PCs and company servers. These attacks can cause parts of your system to malfunction or could provide hackers with complete access to your system and
thereby to the information stored on it. They can also use it as part of a
zombie network.
Ever since it became possible to use credit cards and e-money through
the Internet in online stores, auctions, and bank homepages, online
scams have surfaced as one of the most common crimes.
Intranet
Your intranet is your internal network, specially designed for handling information within a company or a home network. An intranet is a unified
space for storing, exchanging, and accessing information for all the computers on the network. This means that if one computer on the network is
infected, the others are at great risk of infection. To avoid such situations,
both the network perimeter and each individual computer must be protected.

Introduction 7
E-mail
Since practically every computer has mail clients installed on it and since
malicious programs exploit the contents of electronic address books, conditions are usually right for spreading malicious programs. The user of an
infected computer, himself oblivious to the fact, might send infected emails to friends or coworkers who in turn send more infected e-mails. It is
common that infected file documents go undetected at are sent out with
business information from a large company. When this occurs, more than
a handful of people are infected. It could be hundreds or thousands, all of
whom then send the infected files to tens of thousands of subscribers.
Beyond the threat of malicious programs lies the program of electronic
junk mail, or spam. Although not a direct threat to your computer, spam
increases the load on mail servers, eats up bandwidth, fills up your mailbox, and wastes working hours, thereby incurring financial harm.
Also, note that hackers have begun using mass mailing programs and social engineering methods to convince users to open e-mails or click a link
to a certain website. It follows that spam filtration capabilities are both for
stopping junk mail and for counteracting new types of online scans, such
as phishing, and for stopping the spread of malicious programs.
Removable storage media
Removable media (floppies, CD-ROMs, and USB flash drives) are widely
used for storing and transmitting information.
When you open a file that contains malicious code from a removable
storage device, you can damage data stored on your computer and
spread the virus to your computer’s other drives or other computers on
the network.
There are a vast number of threats that could affect your computer today. This
section will go over the threats that Kaspersky Internet Security blocks.
Worms
This malicious program category largely exploits operating system vulnerabilities to spread itself. The class was named for the way the worms
crawl from computer to computer, using networks, e-mail, and other data
channels. This feature gives many worms a rather high speed in spreading themselves.
Worms penetrate a computer, calculate the network addresses of other
computers, and send a burst of self-made copies to these addresses. In
addition to network addresses, worms often utilize data from e-mail client
address books. Some of these malicious programs occasionally create
working files on system disks, but they can run without any system resources at all (with the exception of RAM).

8 Kaspersky Anti-Virus
®
Personal Pro
Viruses
Programs that infected other programs, adding their own code to them to
gain control of the infected files when they are opened. This simple definition explains the fundamental action performed by a virus – infection.
Trojans
Programs that carry out unauthorized actions on computers, such as deleting information on drives, making the system hang, stealing confidential
information, etc. This class of malicious program is not a virus in the traditional sense of the word (meaning it does not infect other computers or
data). Trojans cannot break into computers on their own and are spread
by hackers, who disguise them as regular software. The damage that they
incur can exceed that done by traditional virus attacks by several fold.
Recently, the most widespread type of malicious program damaging computer
data has been worms. Then follow viruses and Trojans. Some malicious
programs combine features of two or even three of these classes.
Adware
Program code included in software, unbeknownst to the user, designed to
display advertisements. Adware is usually built into software that is distributed free. The advertisement is situated in the program interface.
These programs often also collect personal data on the user and send it
back to their developer, change browser settings (start page and search
pages, security levels, etc.) and create traffic that the user cannot control.
All this can lead to breach of the security policy and to direct financial
losses.
Spyware
Software that collects information about a particular user or organization
without their knowledge. You might never guess that you have spyware
installed on your computer. In general, the goal of spyware is to:
• trace user actions on a computer;
• gather information on the contents of your hard drive; in such
cases, this more often than not involves scanning several
directories and the system registry in order to compile a list of
the software installed on the computer;
• gather information on the quality of the connection, bandwidth,
modem speed, etc.
Riskware
Potentially dangerous software that does not have a malicious function
but can be used by hackers as an auxiliary component for a malicious
code, since it contains holes and errors. Under certain conditions, having

Introduction 9
such programs on your computer can put your data at risk. These programs include, for instance, some remote administration utilities, keyboard layout togglers, IRC clients, FTP servers, and all-purpose utilities
for stopping process or hiding their operation.
Yet another type of malicious program that goes along with programs like
adware, spyware, and riskware is programs that plug into your web browser and
redirect traffic. You have most certainly encountered such programs if you have
ever opened one web site when you thought you were pulling up another.
Jokes
Software that does not do any direct damage but displays messages stating that damage has already been done or will be under certain conditions. These programs often warn the user of dangers that do not exist,
such as messages that pop up about formatting the hard drive (although
no formatting actually takes place) or detecting viruses in uninfected files.
Rootkits
Utilities used to conceal malicious activity. They mask malicious programs
to keep anti-virus programs from detecting them. Rootkits modify the operating system on the computer and alter its basic functions to hide its
own existence and actions that the hacker undertakes on the infected
computer.
Other dangerous programs
Programs created to set up DoS attacks on remote servers, hacking into
other computers, and programs that are part of the development environment for malicious programs. These programs include hack tools, virus builders, vulnerability scanners, password-cracking programs, and
other types of programs for cracking network resources or penetrating a
system.
Hacker attacks
Hacker attacks can be initiated by hackers or by malicious programs.
They are aimed at stealing information from a remote computer, causing
the system to malfunction, or gaining full control of the system's resources.
Some types of online scams

10 Kaspersky Anti-Virus
Phishing is an online scam that uses mass mailings to steal confidential
information from the user, generally of a financial nature. Phishing e-mails
are designed to maximally resemble informative e-mails from banks and
well-known companies. These e-mails contain links to fake sites set up by
hackers to copy the site of the organization that they claim to represent.
On this site, the user is asked to enter, for example, his credit card number and other confidential information.
Dialers to pay-per-use websites – type of online scam using unauthorized use of pay-per-use Internet services (these are commonly web sites
of a pornographic nature). The dialers installed by hackers initiate modem
connections from your computer to the number for the pay service. These
numbers often have very high rates and the user is forced to pay enormous telephone bills.
Intrusive advertising
This includes popup windows and banner ads that open when using your
web browser. The information in these windows is generally not of benefit
to you. Popup windows and banner ads distract the user from the task
and take up bandwidth.
Spam
Spam is anonymous junk e-mail. Spam includes mailings that are marketing, political and provocative in nature and e-mails asking for assistance.
Another category of spam includes e-mails that ask one to invest large
amounts of money or to get involved in pyramid schemes, e-mails aimed
at stealing passwords and credit card numbers, and e-mails that ask to be
sent to friends (chain letters).
®
Personal Pro
Henceforth in the text of this User's Guide the term "virus" will be used
to refer to malicious software and the term “dangerous objects” will be
used to refer to objects infected with such software. A particular type of
malware will be mentioned only when it is required.
1.2. The purpose and major
functions of Kaspersky AntiVirus Personal Pro
Kaspersky Anti-Virus Personal Pro (hereinafter referred to as Kaspersky AntiVirus or the application) is designed to provide anti-virus protection for personal
computers running Microsoft Windows (see section 1.4 on page 14).

Introduction 11
When installed on your computer, the application performs the following
functions:
• Protection against viruses and malicious computer programs – the
application detects and eradicates malware present in your computer.
When using the application, the following two major modes can be used
(either jointly or separately):
• Real-time anti-virus protection – performs an anti-virus scan
of all objects being run, opened or saved.
• On-demand scan – performs an anti-virus scan of your entire
computer or of selected disks, files, or folders. You can launch
an on-demand scan manually or set up a regular scheduled
scan.
• Recovery from a virus attack – performing a full scan and disinfection
using settings recommended by Kaspersky Lab will allow you to detect
any viruses that have infected your files during a virus attack.
• Scanning and disinfecting of incoming/outgoing email traffic – real-
time protection performs a real-time anti-virus scan and disinfection of
incoming and outgoing email messages1. In addition, the application
provides on-demand scanning and disinfection of the email databases of
email clients2 (see section 6.3.3 on page 52).
• Protection of the user’s computer against network attacks – analysis
of all data entering the user's computer from the network (either LAN or
internet) to determine whether these data is a part of an internet attack. If
an internet attack is detected, the attack will be repelled the attacking
computer can be blocked. Additionally, the program provides for the
operation in the stealth (invisible) mode when the user’s computer
receives data from other computers only when the data exchange with the
particular machine has been initiated by the user.
• Updating of the anti-virus database, network attacks database and
application modules – updating the anti-virus database and network
attacks database with information about new viruses and attacks and with
methods used for disinfecting objects infected with viruses and updating
the application modules (if this option is not disabled). Updates are
1
The application scans all mail sent or received by Microsoft Office Outlook irrespective of the mail protocols used as well as mail sent or received by any mail client application via SMTP and POP3 protocols.
2
Kaspersky Anti-Virus® can scan email databases for any email client program, but can
disinfect only Microsoft Office Outlook and Microsoft Outlook Express email databases.

12 Kaspersky Anti-Virus
®
Personal Pro
downloaded from Kaspersky Lab’s update servers, server specified by the
user or copied from a network/local folder.
• Recommendations on application setup and operation – the
application will display tips from Kaspersky Lab’s experts and
recommendations on the settings that correspond to the optimal anti-virus
protection level.
When a dangerous object is found, if the anti-virus database have been
not updated for a critically long time, or your computer has not been
scanned for a long time, the main window of Kaspersky Anti-Virus will
recommend a course of action and give a supporting explanation.
Kaspersky Lab’s experts have configured the application for optimal performance based on the extensive expertise in the anti-virus protection
business, and on analysis of our users’ feedback. The recommended antivirus protection settings are installed as the default application settings.
• Using various application configuration profiles – creating and using
special configuration files (profiles) that store the application’s operation
settings. You can easily alter the Kaspersky Anti-Virus configuration by
specifying the application’s settings and saving such changes in the
profiles. For example, you can configure the application to work in the
real-time protection mode only or to perform on-demand scan and then
use such configurations when you feel it is necessary. You can also
return to the recommended settings any time while using Kaspersky AntiVirus.
• Moving to quarantine – moving objects that are possibly infected with
viruses or their modifications to a special secure storage area. You can
then disinfect or delete the quarantined objects, restore them to their
initial folders or send them to Kaspersky Lab for analysis. Quarantined
files are stored using a special format and do not constitute any danger to
your computer.
• Creating backup copies of objects – creating backup copies of objects
in a special backup storage prior to disinfection or deletion of such
objects. Such copies are created for the cases when it is necessary to
restore an original object if it contains valuable information or in order to
restore the infection situation for analysis purposes. Backup copies are
stored in a special format and do not impose any threat.
• Reporting – results of all actions performed by Kaspersky Anti-Virus are
documented in reports. A detailed scan report contains statistics of all
scanned objects, stores information about settings used for each task and
the history of actions performed on each individual file. Reports are also
generated during real-time protection, and after updating the anti-virus
database and application modules.

Introduction 13
Some functions of Kaspersky Anti-Virus are available only from the
command line (details see Chapter 10 on page 132).
1.3. What's new in Version 5.0?
Kaspersky Anti-Virus Personal Pro 5.0 has the following features not found in
Version 4.5:
• The use of anti-virus scan acceleration technologies iChecker™ and
iStreams™. Version 5.0 does not scan previously analyzed objects that
have not changed since their last scan. This applies both to real-time
protection and to the on-demand scan. This feature greatly improves the
application’s speed and performance.
• Scanning and disinfecting mail sent and received by any email client that
via SMTP and POP3 protocol. The previous version protected only mail
sent and received by Microsoft Office Outlook.
• Disinfecting infected archives. Version 5.0 disinfects infected files in zip,
arj, cab, rar, lha and ice archives. The previous version provided detection
and disinfection of infected files in zip archives only.
Kaspersky Anti-Virus only scans multiple volume archives of
the specified types as well as self-extracting archives but does
not disinfect them.
• Anti-virus updating function has become faster due to finding the
geographically closest Kaspersky updates server. The ability to receive
the remaining part of the update after restoring failed connection has
been implemented.
• Protection against network attacks. This version of Kaspersky Anti-Virus
protects your computer against most network or hacking attacks that are
currently widespread.
• User-friendly interface. This version is a single application, whereas the
previous release consisted of several components each performing their
own anti-virus protection function. This new approach simplifies control
over the most important Kaspersky Anti-Virus functions.
• Improved compatibility of Kaspersky Anti-Virus with other anti-virus
products. During the installation of the application you can choose not to
enable file system mail and network protection and script monitoring if
these protection functions are performed by other applications installed on
your computer.

14 Kaspersky Anti-Virus
• Recommended settings and experts' tips. To simplify application
operation, the default settings of this version of the application match the
settings recommended by Kaspersky Lab and in most cases there is no
need to configure the application before use. When the anti-virus
protection level is set to High Speed, the user is prompted to switch to a
higher level of anti-virus protection.
• Application operation profiles management. A possibility to store the
application’s settings in a special file so that you can use them any time
later. If you are not satisfied with the recommended Kaspersky Anti-Virus
settings, configure the application based on your requirements and save
this configuration in a profile file.
• Product license renewal. Users of Version 5.0 can now install a new
license key, extending the license period.
• Sending your files for analysis to Kaspersky Lab. Now you can send us
possibly infected files detected by Version 5.0 or files that you suspect
may be infected.
• The ability to delete infected composite objects has been removed. You
cannot inadvertently delete infected composite objects (archives, email
clients' databases or email format files) using Version 5.0. However, you
can still delete such objects using standard Windows tools such as
Windows Explorer. The exception is self-extracting archives.
• The ability to create lists of trusted processes. The file activities of the
trusted processes are not monitored by Kaspersky Anti-Virus when it
functions in the real-time protection mode.
• Access to the Kaspersky Anti-Virus settings is now password-protected.
You can setup a password that will be asked for by the application every
time when switching between the user’s and the administrator’s mode.
The user’s mode does not allow modification of the application’s settings,
disabling the real-time protection and closing Kaspersky Anti-Virus
Personal Pro on your computer..
®
Personal Pro
1.4. Hardware and software system
requirements
For normal performance of Kaspersky Anti-Virus Personal Pro 5.0, your
computer must meet the following minimum requirements:
General Requirements:
• 50 MB available space on your hard drive

Introduction 15
• CD-ROM drive (for installation of Kaspersky Anti-Virus from CD) or
floppy drive (for installation from floppy disks, and to read license key)
• Microsoft Internet Explorer 5.5 or higher (for updating anti-virus database
and application modules via the Internet)
Microsoft Windows 98, Microsoft Windows ME, Microsoft Windows NT
Workstation 4.0 (Service Pack 6a):
• Intel Pentium 300 MHz processor
• 64 MB RAM
Microsoft Windows ME:
• Intel Pentium 150 MHz processor
• 32 MB RAM
Microsoft Windows NT Workstation 4.0 (Service Pack 6a):
• Intel Pentium 133 MHz processor
• 32 MB RAM
Microsoft Windows 2000 Professional (Service Pack 2 or later), Microsoft
Windows XP Home Edition, Microsoft Windows XP Professional (Service Pack 1
or later):
• Intel Pentium 300 MHz processor
• 128 MB RAM
Microsoft Windows XP Home Edition or XP Professional (Service Pack 1 or
later):
• Intel Pentium 300 MHz processor
• 128 MB RAM
1.5. Distribution Kit
You can purchase Kaspersky Anti-Virus either from our dealers (retail box) or
online (for example, you may visit http://www.kaspersky.com, and go to E-Store
section).
The contents of the retail box package include:
• Sealed envelope with an installation CD, or set of floppy disks,
containing the application files.
• User's Guide.

16 Kaspersky Anti-Virus
• License key written on a special floppy disk.
• License Agreement.
Before you open the envelope with the CD (or a set of floppy disks)
make sure that you have carefully read the license agreement.
If you buy Kaspersky Anti-Virus online, you will download the application from the
Kaspersky Lab website. In this case, the distribution kit will include this User's
Guide along with the application. The license key will be emailed to you upon
receipt of your payment.
The License Agreement is a legal contract between you and Kaspersky Lab that
describes the terms and conditions under which you may use the anti-virus
product that you have purchased.
Please read the License Agreement carefully!
If you do not agree with the terms and conditions of the License Agreement,
return the retail box to the Kaspersky Anti-Virus dealer you purchased it from and
the money you paid for the product will be refunded to you on the condition that
the envelope with the installation CD (or set of floppy disks) is still sealed.
By opening the sealed envelope with the installation CD (or set of floppy disks),
you confirm that you agree with all the terms and conditions of the License
Agreement.
®
Personal Pro
1.6. Services provided for registered
users
Kaspersky Lab offers all registered users an extensive service package enabling
them to use Kaspersky Anti-Virus more efficiently.
After purchasing a license you become a registered user and during the license
period you can enjoy the following services:
• application module and anti-virus database updates;
• support on issues related to the installation, configuration and use of the
application. Services will be provided by phone or via email;
• information about new Kaspersky Lab products. You can also subscribe
to the Kaspersky Lab newsletter which provides information about new
computer viruses as they appear.
Introduction 17
Kaspersky Lab does not provide support on issues related to the performance and the use of operating systems or other technologies.
1.7. Conventions
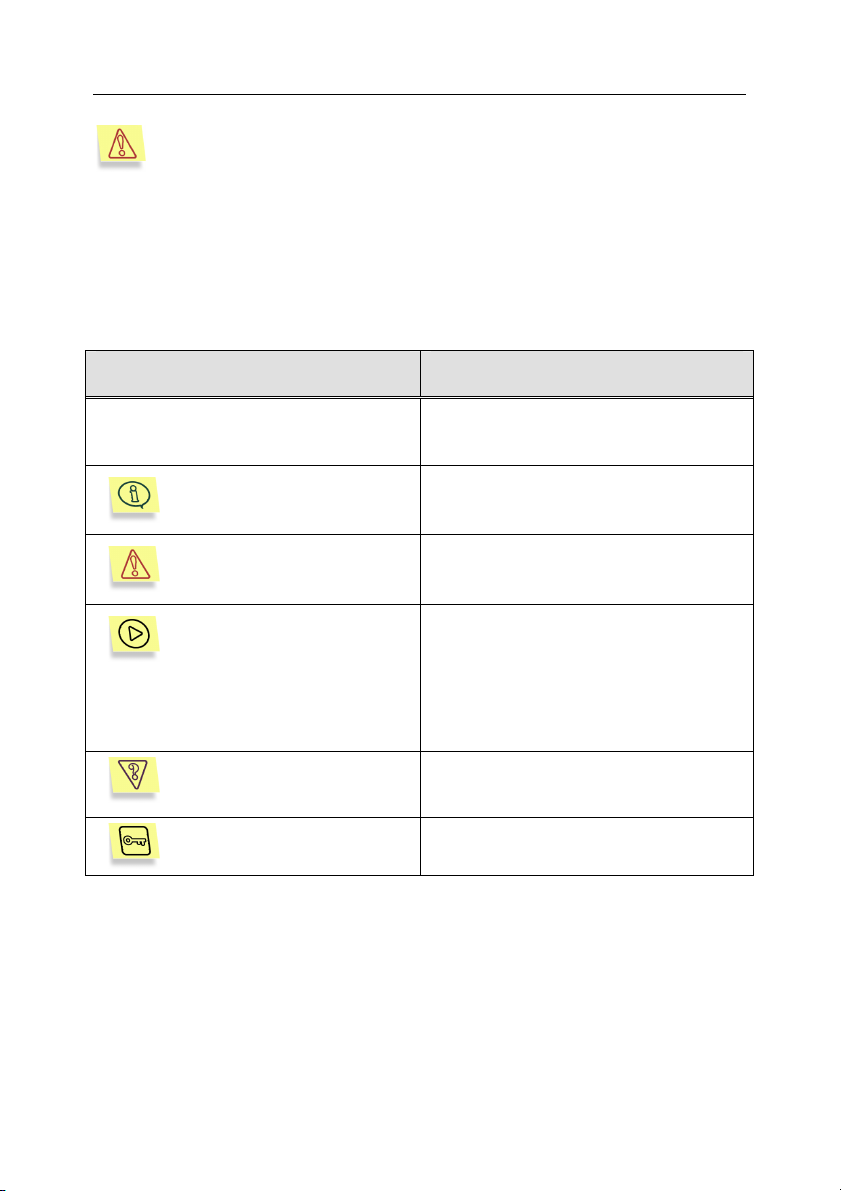
In this book we use various conventions to emphasize different meaningful parts
of the documentation. The table below lists the conventions used in this
document.
Convention Meaning
Bold font
Step 1.
…
Note
Attention
To run a program:
Task:
Solution
Menu titles, commands, window titles,
dialog elements, etc.
Additional information, notes.
Critical information.
Actions that must be taken to run a
program.
Task statement as an example of
parameter definitions, functions, etc.
Solution to the task formulated.

CHAPTER 2. INSTALLING THE
APPLICATION
To install Kaspersky Anti-Virus on your computer, run the executable file from the
installation CD.
Installation of the application using the distribution kit downloaded from
the internet is identical to the installation from the distribution kit on CD.
The installation wizard operates in an interactive mode. Each dialog box has the
following buttons that you can use to navigate through the installation process:
• Next> – accept and proceed with the installation.
• <Back – return to the previous stage of the installation process.
• Cancel – cancel the application installation.
• Finish – finish the application installation.
A detailed discussion of each step of the installation process is provided below.
Step 1. Checking the version of the operating system in-
stalled on your computer
Before the installation of the application, the operating system and Service Packs
installed on your computer are checked for the conformity with the minimum
system requirements for the installation of Kaspersky Anti-Virus Personal Pro.
Should the application determine that any of the requirements is not met, the
corresponding message will be displayed. We advise to install the required
programs and update packages of Microsoft Windows using Windows Update
(or other utilities) or before proceeding with the installation of Kaspersky AntiVirus.
Step 2. Search for other anti-virus software
The next step involves a search for other installed anti-virus software (including
Kaspersky Lab applications). This is performed because the simultaneous use of
these applications with Kaspersky Anti-Virus may cause conflicts.

Installing the application 19
If an earlier version of Kaspersky Anti-Virus is found (as for example version 4.5),
you will be asked if you would like to keep the license key for this product if such
license key is still valid.
We recommend that you keep the valid license key that was used earlier as this key can be used with Kaspersky Anti-Virus Personal Pro 5.0.
After you save the key, you will be prompted to uninstall the earlier version of the
product as it is in conflict with Kaspersky Anti-Virus Personal Pro 5.0.
Click OK button in order to abort the installation. After this uninstall the earlier
version of Kaspersky Anti-Virus and run the product installation wizard again.
If during the previous step you saved a valid license key used for
Kaspersky Anti-Virus 4.x to be used in version 5.0, then the license key
installation window will not be displayed during the installation procedure (see Step 8. on page 21). The key will be used for the program
operation.
If any anti-virus software from a different vendor is found installed on your
computer, you will be prompted to uninstall this program before proceeding with
the installation of Kaspersky Anti-Virus.
We recommend that you uninstall such program(s). To do this, click the No
button, in order to abort the installation. Then uninstall the program and run the
product installation wizard again.
Kaspersky Lab's specialists do not recommend installing several antivirus products on one computer as their joint use may cause conflicts.
If it is determined that Kaspersky Anti-Virus Personal Pro 5.0 has already been
installed on your computer, a message will be displayed with a warning that if
you proceed with the installation, the application that was installed earlier will be
updated by the new installation.
If you are upgrading version 5.0, the license key installation window
(see Step 8. on page 21) will not contain information about they key,
but the key installed earlier will be used for the program operation.
Step 3. Start the Installation Wizard
If no other anti-virus software is found installed on your computer, immediately
after the executable file is run, an installation startup window will appear to inform
you that the installation of Kaspersky Anti-Virus Personal Pro on your computer
began.

20 Kaspersky Anti-Virus
To proceed with the installation, click Next>. To cancel the installation, click
Cancel.
®
Personal Pro
Step 4. Read the license agreement
The next dialog box contains a License Agreement between you and Kaspersky
Lab. Read it carefully and click I Agree if you agree with all terms and conditions
of the Agreement. The installation process will continue.
Step 5. Provide user information
At this point the user name and the user's company name will be determined.
Default information will be copied from the operating system registry. You can
alter it if you wish.
To proceed with the installation, click Next>.
Step 6. Read important information about the application
During this stage of the installation process you will be asked to read important
information about the application before you start using Kaspersky Anti-Virus.
This dialog box contains information about the major features and functionality of
Kaspersky Anti-Virus.
In order to proceed to the next step of the setup process, click Next >.
Step 7. Using the proprietary Kaspersky Lab's technology
During this step of the Kaspersky Anti-Virus setup process you will have to make
a decision whether you want the program to use the following technologies:
Real-time file system protection – scanning all objects that are run, opened and
saved on your computer for viruses. By default the file protection is enabled.
If you do not want Kaspersky Anti-Virus to scan files when you access them,
uncheck the
Real-time mail protection – scanning all messages received by your computer,
messages you send and your mail databases for viruses. By default mail
protection is enabled. If you do not want Kaspersky Anti-Virus to scan mail
messages for viruses, uncheck the Use real-time mail protection box.
Monitoring of executed scripts – anti-virus analysis of all VBScripts and
JavaScripts before their execution. By default script monitoring function is
enabled. If you do not wish to use Kaspersky Anti-Virus for script monitoring,
uncheck the
Use real-time file system protection box.
Use script monitoring box.

Installing the application 21
Macros monitoring – scanning all VBA macros run on your computer for the
presence of malicious code. By default this protection is enabled. In order to
disable macros monitoring, uncheck the Use macros monitoring box.
Real-time protection against network attacks – technology used to protect your
computer against hackers attacks. This technology protects your computer
against network attacks and prevents corruption, theft of or unauthorized
access to your data. By default the real-time protection against network
attacks is enabled. In order to disable real-time protection, uncheck the
Use real-time protection against network attacks box.
iStreams™ Technology – an anti-virus scan acceleration technology (details see
Appendix B on page 151). In order to disable this technology uncheck the
Use the iStreams™ technology checkbox.
This technology can only be used on partitions with the NTFS
file system.
If you disable the use of the above technologies during the installation,
you will have to run the installer again and select technologies that you
would like to use.
If, while working with Kaspersky Anti-Virus, you decide to disable one of
the real-protection types or to disable Streams™ technology you will
have to run the installer again and uncheck the corresponding box.
In order to proceed with the setup process, press Next>.
Step 8. Install the license key
Perform this step only if the Kaspersky Anti-Virus Installation Wizard
fails to find the key file automatically
During this step, the license key for Kaspersky Anti-Virus will be installed. The
license key is your personal "key" that stores all service information required for
proper full-featured operation of the application, including the following reference
information:
• Technical support information (support service provider and contact
information).
• License name, number, and expiry date.
The application will not work without the license key.

22 Kaspersky Anti-Virus
®
In order to install a license key,
1. Press the Browse button and browse to the folder containing the li-
cense key file:
• If you purchased a retail box version of Kaspersky Anti-Virus,
you will find the license key written or a special floppy disk. You
will have to insert the disk into the drive and select this drive
(see Figure 1).
Personal Pro
Figure 1. Selecting path to the license key file
• If the license was purchased online, then the license key file
that you received by via e-mail shall be saved in any folder on
your computer’s hard drive. You will have to open this folder.
The selected folder will display the list of available license keys.

Installing the application 23
2. Select the required license key (a file with .key extension) and press the
Open button (see Figure 2).
Figure 2. Selecting the license key file
As the result, the installation wizard will display general information about the
license and the path to the license key file.
In order to proceed with the installation press Next >.
If you do not have the license key at the time of installation (for example, if you
ordered via the Internet but have not received it yet), you may install it later,
when you run the application for the first time or using a special license key
installation utility (see Chapter 9 on page 128). Remember that you cannot start
using Kaspersky Anti-Virus without the license key.
Step 9. Select the installation folder
During this step, the destination folder will be selected for the installation of the
application files. The default path is: <Disk>\Program Files\Kaspersky
Lab\Kaspersky Anti-Virus Personal Pro.
You can type in the path to this folder or press the Browse button and use the
standard Select Folder dialog box to locate and select the folder.
Press the Install button in order to proceed with the installation. After this,
Kaspersky Anti-Virus application files will be copied to your computer.

24 Kaspersky Anti-Virus
®
Personal Pro
Step 10. Finish setup
A Completing the Setup dialog box informs you that installation of Kaspersky
Anti-Virus on your computer has been completed.
If registration of system services is required, you will be asked to restart your
computer. This is a MANDATORY step for the correct completion of the
application installation.
To complete the setup:
1. Choose one of the following options:
Yes, I want to restart my computer now
No, I will restart my computer later
2. Click Finish.
If your computer does not need to be restarted to complete the setup, you
can begin using the program immediately. Perform the following steps to
finish the installation:
1. If you do not want to enable anti-virus protection of your computer
immediately after the installation is completed, uncheck the box
Start Kaspersky Anti-Virus Personal Pro 5.0.
If you uncheck this box, the anti-virus protection of your computer will be automatically enabled after reboot. Before that time
you can manually enable anti-virus protection from the Microsoft
Windows main menu (Start ! Programs ! Kaspersky Anti-
Virus Personal Pro).
2. Click the Finish button.
As a result of installation and launch of Kaspersky Anti-Virus:
• The application icon will be added to the system tray
• Application shortcuts will be added to the main Microsoft Windows menu
(Start! Programs! Kaspersky Anti-Virus Personal Pro).

CHAPTER 3. PREVENTING
COMPUTER INFECTION
Sometimes it is not apparent, even to a knowledgeable user, that a computer is
infected with a virus because viruses efficiently camouflage themselves among
regular files. This chapter contains a detailed discussion of virus infection
symptoms, methods of data recovery after a virus attack and measures aimed at
prevention of data corruption by viruses.
3.1. Symptoms of infection
There are a number of symptoms indicating that your computer has probably
been infected. If you are noticing "strange things" happening to your computer,
for example:
• unexpected messages or images are suddenly displayed;
• unusual sounds or music played at random;
• your CD-ROM tray mysteriously opens and closes;
• programs suddenly start on your computer;
• if Kaspersky Anti-Hacker is installed on your computer, it notifies you of
attempts by some programs to connect to the Internet although you did
not initiate this.
If any of the above symptoms appear, it is very likely your computer has been
infected with a virus.
In addition, there are some typical symptoms indicating that your computer has
been infected via email:
• your friends mention that they receive messages although you never
sent such messages;
• your mailbox contains many messages without the sender’s email
address or header.
Note that these problems may be caused by reasons other than viruses. For
example, infected messages which have your address as the sender can actually
be sent from a different computer.

26 Kaspersky Anti-Virus
There are also indirect symptoms that indicate your computer has possibly been
infected:
• your computer freezes frequently or encounters errors;
• your computer slows down when programs are started;
• you are unable to load the operating system;
• files and folders are suddenly missing or their content changes;
• your hard drive is accessed too often (the light on your main unit flashes
rapidly);
• Microsoft Internet Explorer "freezes" or displays unpredictable behavior,
(for example you cannot close the application window).
In most cases such indirect symptoms indicate that there is a hardware or
software problem, but although such symptoms are unlikely to be caused by an
infection, we recommend that you perform a full scan of your computer using the
default settings recommended by Kaspersky Lab experts if your encounter any of
these problems.
®
Personal Pro
3.2. What should you do if you notice
symptoms of infection
If you notice that your computer displays "suspicious" behavior:
1. Don’t panic! This golden rule may prevent the loss of important data
stored on your computer and help you avoid unnecessary stress.
2. Disconnect your computer from the Internet.
3. Disconnect your computer from the Local Area Network if it is con
4. If the symptom of an infection is that you cannot boot from your hard
drive (your computer encounters an error at startup), try to start the
system in Safe Mode or from the Microsoft Windows boot disk that you
created during the installation of the operating system on your
computer.
5. Before taking any action, back up all critical data to an external drive (a
floppy disk, CD, flash card, etc.)

Preventing computer infection 27
Later, before you move saved date to the computer after it has
been disinfected, make sure that you have scanned this data with
Kaspersky Anti-Virus (see section 6.3.5 on page 57).
6. Install Kaspersky Anti-Virus Personal Pro.
7. Download the latest anti-virus database updates. If possible, do not use
the infected computer to download the updates, but instead use a
friend’s computer, or a computer at your office or an Internet café. It is
preferred that you use a different computer because when you connect
to the internet using an infected computer some important information
stored on your computer may be sent to the malefactors or the virus
may be sent to the contacts stored in your address book. Therefore, if
you suspect an infection it is the best to immediately disconnect from
the Internet and from any local area network you are connected to. You
can also obtain the anti-virus database on a CD-ROM or a floppy disk
from Kaspersky Lab or its authorized dealers and update your
databases from this disk (for more details see section 7.1.1 on page
63).
8. Apply the recommended application settings (see Chapter 4 on page
30).
9. Perform a full system scan (see section 6.3.2 on page 51).
3.3. Safety rules
Even proven and trusted preventative actions cannot ensure 100% protection
against computer viruses and Trojans, but you can considerably minimize the
risk of being affected by a virus attack and thus reduce the losses from a
possible infection if you develop and follow certain rules.
Similar to health care, one of the main methods of fighting viruses is the
prevention of infection. For computers, prevention of a virus infection includes a
few rules that must be followed to reduce the risk of infection and data loss.
Listed below are the main security rules that you should follow to prevent virus
attacks.
Rule 1: keep your computer protected with an anti-virus program and Internet
security software. To do this:
• Install Kaspersky Anti-Virus Personal Pro.
• Update your anti-virus database on a regular basis. During periods of
virus outbreaks you should retrieve updates several times each day
because during such periods the anti-virus database on Kaspersky Lab’s
update servers is updated constantly.

28 Kaspersky Anti-Virus
®
Personal Pro
• Apply the real-time protection settings recommended by Kaspersky Lab.
Real-time protection is enabled immediately after system startup and
prevents the penetration of viruses into your computer.
• Apply the on-demand scan settings recommended by Kaspersky Lab
and schedule the scan to be run at least once a week.
• We also recommend that you install Kaspersky Anti-Hacker for
comprehensive computer protection while you are surfing the Internet.
Rule 2: be careful when copying any new data to your computer:
• Always scan all removable drives (floppy disks, CD-ROM drives, flash
cards, etc.) for viruses before using them.
• Be careful with email messages. Never open an email attachment, even
if it was sent to you by a person you know, unless you are expecting it. In
particular, do not trust emails that claim to be sent by anti-virus
companies.
• Be careful with any data downloaded from the Internet. If you are
prompted to download a program, always check that it comes with a
security certificate.
• If you download an executable file from the Internet or from a LAN, scan
it with Kaspersky Anti-Virus.
• Be selective about the websites you visit. Some websites contain
dangerous scripts or Internet worms.
Rule 3: Read carefully all information supplied by Kaspersky Lab.
In most cases, Kaspersky Lab warns users about new virus outbreaks
long before they reach their peak. The risk of getting infected is still low at
this time and if you download the up-to-date anti-virus database, you will
be able to protect your computer.
Rule 4: Be suspicious about hoax virus warnings - email messages that claim to
be warnings of virus threats.
Rule 5: Regularly update your operating system using the Microsoft Windows
Update utility.
Rule 6: Always buy licensed copies of your software from authorized dealers.
Rule 7: Limit the number of people who have access to your computer.
Rule 8: Minimize potential losses from a possible infection:
• Backup your data on a regular basis, so that in the event of data loss,
your system may be fairly quickly restored using backup copies. Your
distribution disks, floppy disks and other media with software installation
and other important data should be kept in a safe place.

Preventing computer infection 29
• Always create a bootable rescue disk from which you can boot using a
"clean" operating system.
Rule 9: Inspect the list of applications installed on your computer on a regular
basis.
You can access this list using the Add/Remove programs utility in the
Control Panel or simply view the contents of the Program Files folder,
startup folder. This way you can detect software that was installed onto
your computer without your knowledge while you were using Internet or
installing some software you needed. There is a very high chance that
some of these programs are riskware.

CHAPTER 4. ANTI-VIRUS
PROTECTION USING
KASPERSKY ANTI-VIRUS
DEFAULT SETTINGS
Real-time protection of your computer is provided only if you did not
disable it during the installation of the application.
You can use Kaspersky Anti-Virus immediately upon installation. There is no
need to customize the application before using it for the first time because the
default settings provide the optimal balance between protection and
performance.
Below, we describe the default settings in detail.
According to the default settings, the anti-virus protection becomes active
immediately after the application is installed on your computer. The default
settings are recommended by Kaspersky Lab's experts to ensure the optimal
protection of your computer.
Additionally, the application includes a tool for quick altering the settings by
selecting one of the three protection levels, pre-defined by the Kaspersky Lab’s
experts.
• Maximum protection – computer protection level that ensures
maximum possible protection with some decrease in the system
performance.
• Recommended – second anti-virus protection level based on the
settings recommended by Kaspersky Lab’s experts that ensure optimal
protection of your computer.
• High speed – anti–virus protection level that ensures maximum speed of
operation with somewhat lower extent of the anti-virus protection due to
some reduction in the number of scanned objects.
Following below is a detailed discussion of how Kaspersky Anti-Virus performs in
accordance with the experts' recommendations.
 Loading...
Loading...