Page 1

KASPERSKY LAB
Kaspersky Anti-Virus 5.6 for Linux
Mail Server
ADMINISTRATOR'S
GUIDE
Page 2

KASPERSKY A N TI-VI R U S 5. 6 FOR L I N UX MA I L SERV E R
Administrator's Guide
Kaspersky Lab
http://www.kaspersky.com
Revision date: November, 2008
Page 3

Contents
CHAPTER 1. INTRODUCTION ...................................................................................... 7
1.1. What‟s new ............................................................................................................ 8
1.2. Product requirements ............................................................................................ 9
1.3. Service for registered users ................................................................................ 10
CHAPTER 2. THE STRUCTURE AND OPERATING ALGORITHM OF THE
APPLICATION ............................................................................................................... 11
CHAPTER 3. INSTALLING AND UNINSTALLING THE APPLICATION ................... 14
3.1. Installing the application on a server running Linux ........................................... 14
3.2. Installing the application on a server running FreeBSD ..................................... 15
3.3. Location of application files ................................................................................. 16
3.3.1. Location of files on a server running Linux .................................................. 16
3.3.2. Location of files on a server running FreeBSD ............................................ 18
3.4. Post-installation setup ......................................................................................... 19
3.5. Configuration of permission rules in SELinux and AppArmor systems ............. 22
3.6. Installing the Webmin module to manage Kaspersky Anti-Virus ....................... 24
3.7. Application removal ............................................................................................. 26
CHAPTER 4. INTEGRATION WITH MTA .................................................................... 28
4.1. Integration with Exim ........................................................................................... 29
4.1.1. Post-queue integration using modification of routers .................................. 29
4.1.2. Pre-queue integration using dynamically loaded library .............................. 32
4.2. Integration with Postfix ........................................................................................ 34
4.2.1. Post-queue integration ................................................................................. 35
4.2.2. Pre-queue integration ................................................................................... 37
4.2.3. Integration with Milter .................................................................................... 39
4.3. Integration with qmail ........................................................................................... 41
4.4. Integration with Sendmail .................................................................................... 42
4.4.1. Integration with Sendmail using .cf file ......................................................... 43
4.4.2. Integration with Sendmail using .mc file ....................................................... 44
Page 4

4 Kaspersky Anti-Virus 5.6 for Linux Mail Server
CHAPTER 5. ANTI-VIRUS PROTECTION OF E-MAIL .............................................. 46
5.1. Setting up groups ................................................................................................ 46
5.2. Definition of e-mail analysis policy ...................................................................... 48
5.3. E-mail scanning mode ......................................................................................... 48
5.3.1. Anti-virus scanning ....................................................................................... 49
5.3.2. Content filtering ............................................................................................. 50
5.4. Actions over objects ............................................................................................ 52
5.5. Predefined security profiles ................................................................................. 53
5.5.1. Recommended profile .................................................................................. 54
5.5.2. Maximum protection profile .......................................................................... 54
5.5.3. Maximum performance profile ..................................................................... 55
5.6. Backup ................................................................................................................. 56
5.7. Notifications ......................................................................................................... 57
5.7.1. Setting up notifications .................................................................................. 57
5.7.2. Notification templates ................................................................................... 59
5.7.3. Customizing notification templates............................................................... 62
CHAPTER 6. ANTI-VIRUS PROTECTION OF FILE SYSTEMS ................................ 70
6.1. Scan scope .......................................................................................................... 71
6.2. Object scan and disinfection mode ..................................................................... 72
6.3. Actions to be performed on objects .................................................................... 72
6.4. On-demand scan of an individual directory ........................................................ 74
6.5. Scheduled scan ................................................................................................... 74
6.6. Sending notifications to the administrator ........................................................... 75
CHAPTER 7. UPDATING THE ANTI-VIRUS DATABASES ....................................... 76
7.1. Automatically updating the anti-virus database .................................................. 77
7.2. On-demand updating of the anti-virus database ................................................ 78
7.3. Creating a network directory to store the updates.............................................. 79
CHAPTER 8. KEY MANAGEMENT ............................................................................. 81
8.1. Viewing key details .............................................................................................. 82
8.2. Renewing your key .............................................................................................. 84
CHAPTER 9. REPORTING AND STATISTICS ........................................................... 85
9.1. Application logging .............................................................................................. 85
9.2. Application statistics ............................................................................................ 87
Page 5

Contents 5
CHAPTER 10. ADVANCED SETTINGS ...................................................................... 91
10.1. Monitoring of protection status via SNMP ........................................................ 91
10.2. Using the application‟s setup script ................................................................... 95
10.3. Managing the application from the command line ........................................... 97
10.4. Additional informational fields in messages...................................................... 99
10.5. Localization of displayed date and time format .............................................. 100
CHAPTER 11. TESTING THE APPLICATION .......................................................... 101
APPENDIX A. ADDITIONAL INFORMATION ............................................................ 103
A.1. Application configuration file kav4lms.conf....................................................... 103
A.1.1. Section [kav4lms:server.settings] .............................................................. 103
A.1.2. Section [kav4lms:server.log] ...................................................................... 106
A.1.3. Section [kav4lms:server.statistics] ............................................................. 107
A.1.4. Section [kav4lms:server.snmp] .................................................................. 108
A.1.5. Section [kav4lms:server.notifications] ....................................................... 110
A.1.6. Section [kav4lms:filter.settings] .................................................................. 111
A.1.7. Section [kav4lms:filter.log] ......................................................................... 114
A.1.8. Section [kav4lms:groups] ........................................................................... 115
A.1.9. Section [path] .............................................................................................. 115
A.1.10. Section [locale] ......................................................................................... 116
A.1.11. Section [options] ....................................................................................... 117
A.1.12. Section [updater.path] .............................................................................. 117
A.1.13. Section [updater.options] ......................................................................... 117
A.1.14. Section [updater.report]............................................................................ 119
A.1.15. Section [updater.actions] ......................................................................... 119
A.1.16. Section [scanner.display] ......................................................................... 121
A.1.17. Section [scanner.options] ......................................................................... 121
A.1.18. Section [scanner.report] ........................................................................... 124
A.1.19. Section [scanner.container] ..................................................................... 125
A.1.20. Section [scanner.object] ........................................................................... 126
A.1.21. Section [scanner.path] ............................................................................. 127
A.2. Group configuration file ..................................................................................... 127
A.2.1. Section [kav4lms:groups.<group_name>.definition] ................................. 128
A.2.2. Section [kav4lms:groups.<group_name>.settings] ................................... 129
A.2.3. Section [kav4lms:groups.<group_name>.actions] .................................... 131
A.2.4. Section [kav4lms:groups.<group_name>.contentfiltering] ....................... 132
Page 6

6 Kaspersky Anti-Virus 5.6 for Linux Mail Server
A.2.5. Section [kav4lms:groups.<group_name>.notifications] ............................ 136
A.2.6. Section [kav4lms:groups.<group_name>.backup] ................................... 138
A.3. Command line parameters for component kav4lms-licensemanager ............ 138
A.4. Return codes of the kav4lms-licensemanager component ............................. 139
A.5. Command line parameters for component kav4lms-keepup2date ................. 140
A.6. Return codes of the kav4lms-keepup2date component .................................. 141
APPENDIX B. KASPERSKY LAB ............................................................................... 142
B.1. Other Kaspersky Lab Products ........................................................................ 143
B.2. Contact Us ......................................................................................................... 153
APPENDIX C. THIRD-PARTY SOFTWARE .............................................................. 154
C.1. Pcre library ........................................................................................................ 154
C.2. Expat library ...................................................................................................... 155
C.3. AgentX++v1.4.16 library ................................................................................... 155
C.4. Agent++v3.5.28a library ................................................................................... 162
C.5. Boost v 1.0 library ............................................................................................. 163
C.6. Milter library ....................................................................................................... 164
C.7. Libkavexim.so library ........................................................................................ 166
Page 7

CHAPTER 1. INTRODUCTION
Kaspersky Anti-Virus® 5.6 for Linux Mail Server (hereinafter referred to as
Kaspersky Anti-Virus or the application) provides anti-virus processing of mail
traffic and file systems of servers running the Linux or FreeBSD operating systems, and using the Sendmail, Postfix, qmail, or Exim MTA.
This application allows the user to:
Check for the presence of threats all server file systems as well as in-
coming and outgoing mail messages.
Detect infected, suspicious, corrupted, and password-protected objects
as well as objects that cannot be scanned.
Neutralize threats detected in files and mail messages. Disinfect in-
fected objects.
Back up e-mail messages prior to their anti-virus processing and filtra-
tion.
Process mail traffic according to rules preset for groups of senders and
recipients.
Provide content filtering of mail traffic by name, type and size of at-
tached files, and use individual processing rules for the filtered objects.
Notify the sender, recipients, and administrator about detection of mail
messages that contain infected, suspicious, password protected objects
or objects that cannot be scanned.
Generate statistics and reports on application performance.
Update the anti-virus databases, either using a schedule or on demand,
by downloading update files from Kaspersky Lab‟s update servers.
The anti-virus database is used to search for and attempt to cure in-
fected objects. During the scan each file is analyzed for the presence of
threats by comparing the file‟s code with code typical of various threats.
Configure and manage Kaspersky Anti-Virus both locally (using stan-
dard OS means including command line options, signals and modification of the application configuration file) and remotely via the web-based
interface provided by the Webmin program.
Obtain information about product configuration and activity statistics via
SNMP and configure the application to generate SNMP traps when
specified events occur.
Page 8

8 Kaspersky Anti-Virus 5.6 for Linux Mail Server
1.1. What’s new
Version 5.6 of Kaspersky Anti-Virus for Linux Mail Server merges the features
of Kaspersky Anti-Virus 5.5 for Linux and FreeBSD Mail Server and Kaspersky
Anti-Virus 5.6 for Sendmail with Milter API and adds the following improvements:
Both pre-queue and post-queue integration is supported for Exim. In case
of pre-queue integration, e-mail is transferred for scanning before its addition to the mail system queue while post-queue integration means that
messages are scanned after addition to the queue. Automatic integration
using the application configuration script is now available. See Chapter 4
on p. 28 for details on the integration procedure.
Opportunities for configuration of mail scanning functionality have been
enhanced: two scanning methods are now available. A message can be
scanned as a single object or using combined approach – first as a single
object and then as a collection of its parts. These methods differ in terms
of the provided protection level. See 5.2 on p. 48 for details.
The application‟s configuration has changed. Individual configuration of
separate groups of senders and recipients is now supported. See 5.1 on
p.46 for details of configuring groups.
The list of actions performed over messages has been extended. New ac-
tion type depending upon the detected malware has been added. See 5.4
on p. 52 for details.
Content filtering capabilities have been extended by adding filtering by at-
tachment size criterion. See 5.3.2 on p. 50 for details.
The library of notification templates has been supplemented with added
administrator templates. Templates are now stored in a separate directory.
The opportunity to place infected objects in Backup is no longer sup-
ported.
Backup functionality has been extended – information files can be created
for each backup entry. See 5.6 on p.56 for details.
Reporting has been improved by increasing the logging setup thorough-
ness. See 9.1 on p.85 for details.
Statistics functionality has been extended by adding per-message statis-
tics. See 9.2 on p.87 for details.
SNMP-queries for configuration, statistics, application status are now
supported. SNMP-traps are also supported. See 10.1 on p. 91 for details.
Page 9

Introduction 9
Command line administration tool is added to the application‟s package. It
is capable of managing various aspects of the application‟s functionality.
See 10.3 on p. 97 for details.
1.2. Product requirements
The system requirements for Kaspersky Anti-Virus are:
Hardware requirements for a mail server with about 200 MB of traffic
per day:
Intel Pentium IV, 3 GHz processor or higher;
1 GB RAM;
200 MB available space on your hard drive (this amount does not
include space necessary for storing backup message copies).
Software requirements:
One of the following 32-bit operating systems:
o Red Hat Enterprise Linux Server 5.2;
o Fedora 9;
o SUSE Linux Enterprise Server 10 SP2;
o openSUSE 11.0;
o Debian GNU/Linux 4.0 r4;
o Mandriva Corporate Server 4.0;
o Ubuntu 8.04.1 Server Edition;
o FreeBSD 6.3, 7.0.
One of the following 64-bit operating systems:
o Red Hat Enterprise Linux Server 5.2;
o Fedora 9;
o SUSE Linux Enterprise Server 10 SP2;
o openSUSE Linux 11.0.
One of the following mail systems: Sendmail 8.12.x or higher, qmail
1.03, Postfix 2.x, Exim 4.x;
Optional - the Webmin program (www.webmin.com) for remote
administration of Kaspersky Anti-Virus;
Perl version 5.0 or higher (www.perl.org).
Page 10
10 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Note:
Kaspersky Lab does not give advice on the performance and use of your operating system, third party software or various other technologies.
1.3. Service for registered users
Kaspersky Lab offers its legal users a broad range of services maximizing the
efficiency of Kaspersky Anti-Virus software.
By purchasing a subscription you become a registered software user entitled to
the following services throughout the license period:
software upgrades for this software application;
consultations regarding issues pertaining to installation, configuration
and use of this software, available over the telephone or via e-mail;
notifications about new software products from Kaspersky Lab, and
about new virus outbreaks. This service is provided to users who have
subscribed to the Kaspersky Lab e-mail newsletter service.
Page 11

CHAPTER 2. THE STRUCTURE
AND OPERATING
ALGORITHM OF THE
APPLICATION
Kaspersky Anti-Virus consists of the following components:
Filter – the service for connection to the mail system, a separate pro-
gram providing for interaction between Kaspersky Anti-Virus and a specific MTA. The product distribution package includes modules for each
supported mail systems:
kav4lms-milter – Milter service for connection with Sendmail and
Postfix via Milter API.
kav4lms-filter – SMTP service for connection with Postfix and Exim.
kav4lms-qmail – mail queue handler for qmail.
kavmd - central service of the application, listening to the filter requests
and implementing the anti-virus functionality of the application protecting e-mail traffic.
kav4lms-kavscanner – provides for anti-virus protection of server file
systems.
kav4lms-keepup2date – provides for updating of the anti-virus database
downloading new data from update servers of Kaspersky Lab or a local
directory.
kav4lms-licensemanager – component for operations with product keys:
installation, removal, viewing statistical information.
kav4lms.wbm – Webmin plug-in module for remote management of the
application via web-based interface (optional), which allows configuration and launch of updates for the anti-virus database, viewing of statistical information, definition of actions over objects depending upon their
status, and monitoring of application activity results.
kav4lms-cmd – utility for Anti-Virus management via the command line.
Page 12

12 Kaspersky Anti-Virus 5.6 for Linux Mail Server
The application uses the following algorithm to check e-mail:
1. The filter receives a message from MTA. If the filter and the central service are running on the same computer, then names of message files
are passed instead of the actual messages for analysis.
2. The filter determines the groups that the message belongs to, selects
the group with the highest priority (see 5.1 on p. 46) and transfers the
letter for analysis to the central service of the application. If there is no
such group, then the application will process that message using the
rules for the Default group included into its distribution package.
The central service scans the message using the parameters specified
in the configuration file of the group. Depending upon the method defined in the policy, the application can scan the message as a single
solid object or use combined approach scanning it first as a whole and
then checking its individual parts (see 5.2 on p. 48).
Combined analysis is more thorough and provides for higher protection
level although its performance is somewhat lower assumes checking
the message as a whole or as a whole and then part-by-part (combined
policy).
3. If anti-virus mail scanning is enabled (see 5.3 on p. 48), the central service checks a message as a single object. In accordance with the status
assigned after that check (see 5.3.1 on p. 49) the central service: blocks
delivery, rejects or allows the message, replaces it with a warning,
modifies its headers (see 5.4 on p. 52). If special processing is defined
for individual malware types (the VirusNameList option), the specified
actions will be performed if they are detected (VirusNameAction option). Message processing order is specified in the configuration file of
the group.
The application creates a backup copy of the original message before
its processing if that step is enabled in the group settings.
4. After anti-virus message scan the application performs its filtering if it is
enabled in the group settings.
Filtration can be performed by attachment name, type and size (see
5.3.2 on p. 50). The check results in the actions defined by the filtration
settings in the configuration file of the group. Processed objects matching the filtration criteria are passed over for further analysis part by part,
if combined processing method is enabled in the group settings.
5. During e-mail inspection part by part the application parses its MIME
structure and processes message components.
Page 13

The structure and operating algorithm of the application 13
Message objects are treated in accordance with the status assigned to
each individual object irrespectively of the status assigned to the message as a whole.
If a message is recognized as infected after its processing as a single
object while no threat is found after examination of its parts, the application will handle the whole message using the action defined for infected
mail (InfectedAction option). If the nesting level of an object attached
to a clean message exceeds the limit specified in group settings (Max-
ScanDepth option), the application will handle the whole message using the action defined for letters causing errors during scan (ErrorAc-
tion option).
While processing message objects, the central service renames, deletes or replaces an object with a warning, adds informational headers
or allows a message to pass (see 5.4 on p. 52). Infected messages get
disinfected. The application creates a backup copy of the whole original
message prior to processing of its object (unless it has been made earlier) if that step is enabled in the group settings.
6. After scanning and processing, the central service returns the message
to filter. The processed message together with the notifications about
results of scanning and disinfection is conveyed to the MTA, which delivers the e-mail message to local users or relays it to other mail servers.
Page 14
Warning!
We advise that you install the application in off hours or when the mail traffic has
the lowest intensity!
CHAPTER 3. INSTALLING AND
UNINSTALLING THE
APPLICATION
Before installing Kaspersky Anti-Virus, you are advised to make the following
preparations for your system:
Make sure your system meets the hardware and software requirements
listed in section 1.2 on page 9.
Make backup copies of configuration files of the mail system installed on
your server.
Set up an Internet connection.
Log in to the system with root access rights or any other account with
superuser privileges.
3.1. Installing the application on a
server running Linux
For servers running the Linux operating system, Kaspersky Anti-Virus is distributed in two different installation packages, depending on the type of your Linux
distribution.
To install the application under Red Hat Enterprise Linux, Fedora, SUSE Linux
Enterprise Server, openSUSE and Mandriva Linux, use the rpm package.
To initiate installation of Kaspersky Anti-Virus from the .rpm package, enter the
following on the command line:
# rpm -i <package_name>
Page 15
Installing and uninstalling the application 15
Warning!
After installing the application from the rpm package, you must run the postinstall.pl script to perform post-installation configuration. The default location of the
postinstall.pl script is in the /opt/kaspersky/kav4lms/lib/bin/setup/ directory (in
Linux) and in the
/usr/local/libexec/kaspersky/kav4lms/setup/ directory (in FreeBSD)!
Warning!
The procedure of application setup under Mandriva distributions has some peculiarities.
To allow correct launch of Kaspersky Anti-Virus after installation, you will have to
make sure that the /root/tmp/ directory is used for storage of temporary files in
the operating system and the account used to run the application (by default,
kluser) has the right to write to the directory.
You might have to change the access rights for the directory, or redefine or delete the TMP, TEMP environment variables to make the system use another directory (e.g., /tmp/) with the rights required for application functioning.
In Debian GNU/Linux and Ubuntu, the installation is performed from a deb package.
To initiate installation of Kaspersky Anti-Virus from the .deb package, enter the
following on the command line:
# dpkg -i <package_name>
After you enter the command, the application will be installed automatically.
Once the installation completes, information about post-install configuration will
be displayed (see 3.4 on p. 19).
3.2. Installing the application on a
server running FreeBSD
The distribution file for installing Kaspersky Anti-Virus on servers running
FreeBSD OS is supplied as a pkg package.
To initiate installation of Kaspersky Anti-Virus from a pkg package, enter one of
the following at the command line:
# pkg_add <package_name>
After you enter the command, the application will be installed automatically.
Once the installation completes, information about post-install configuration will
be displayed (see 3.4 on p. 19).
Page 16
16 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Attention!
To make the man pages for the application available upon the man
<man_page_name> command, the following steps are necessary:
for Debian Linux, Ubuntu Linux, SUSE Linux distributions, add the line
below to the /etc/manpath.config file:
MANDATORY_MANPATH /opt/kaspersky/kav4lms/share/man
for Red Hat Linux and Mandriva Linux distributions, add the line below
to the /etc/man.config file:
MANPATH /opt/kaspersky/kav4lms/share/man
for FreeBSD distributions, add the line below to the /etc/manpath.config
file:
MANDATORY_MANPATH /usr/local/man
If your system uses the MANPATH variable, add to the list of its values the path
to the directory containing man pages of the application by running the following
command:
# export MANPATH=$MANPATH:<path to the man pages directory>
3.3. Location of application files
During Kaspersky Anti-Virus setup the product installer copies application files to
program directories on server.
3.3.1. Location of files on a server running
Linux
The default locations of Kaspersky Anti-Virus files on a server running Linux OS
are as follows:
/etc/opt/kaspersky/kav4lms.conf – main configuration file of application;
/etc/opt/kaspersky/kav4lms/ – directory containing the Kaspersky Anti-Virus con-
figuration files:
groups.d/ - directory containing the groups‟ configuration files;
default.conf – configuration file, containing the default group‟s settings;
locale.d/strings.en – file, containing strings, used by the application;
profiles/ – directory containing predefined configuration profiles:
default_recommended/ – directory containing the default configuration
files;
Page 17

Installing and uninstalling the application 17
high_overall_security/ – directory containing the configuration files for
high security profile;
high_scan_speed/ – directory containing the configuration files for high
scan speed profile;
templates/ – directory containing notification templates;
templates-admin/ – directory containing administrator‟s notifications tem-
plates;
kav4lms.conf – the application‟s main configuration file;
/opt/kaspersky/kav4lms/ – main directory of Kaspersky Anti-Virus, containing:
bin/ – a directory that contains executable files of all Kaspersky Anti-Virus
components:
kav4lms-cmd – executable file of the command line tool;
kav4lms-setup.sh – the application‟s setup script;
kav4lms-kavscanner – executable file of the file system scan compo-
nent;
kav4lms-licensemanager – executable file of the keys management
component;
kav4lms-keepup2date – executable file of the updater component;
sbin/ – a directory that contains executable files of application‟s services;
lib/ - directory containing Kaspersky Anti-Virus library files;
bin/avbasestest – utility validating downloaded updates to the anti-virus
databases used by the kav4lms-keepup2date component;
share/doc/ – directory containing license agreement and deployment docu-
mentation;
share/man/ – directory containing manual files;
share/scripts/ – directory containing the application‟s scripts;
share/snmp-mibs/ – directory containing the Kaspersky Anti-Virus MIB;
share/webmin/ – directory containing plug-in to Webmin application;
/etc/init.d/ – directory containing control scripts for application services:
kav4lms – control script for the central service of the application;
kav4lms-filters – control script for Kaspersky Anti-Virus filter;
/var/opt/kaspersky/kav4lms/ - directory containing variable data of Kaspersky
Anti-Virus:
backup/ – directory containing messages‟ backup copies and information
files;
bases/ – directory containing anti-virus databases;
bases.backup/ – directory containing backup copy of the anti-virus data-
bases;
Page 18

18 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Warning!
Linux-related paths are used further in this document.
licenses/ – directory containing key files;
nqueue/ – directory containing the mail queue files;
patches/ – directory containing application modules‟ updates;
stats/ – directory containing statistics files;
updater/ – directory containing information file about the last update.
3.3.2. Location of files on a server running
FreeBSD
The default locations of Kaspersky Anti-Virus files on a server running FreeBSD
OS are as follows:
/usr/local/etc/kaspersky/kav4lms.conf – main configuration file of application;
/usr/local/etc/kaspersky/kav4lms/– directory containing the Kaspersky Anti-Virus
configuration files:
groups.d/ - directory containing the groups‟ configuration files;
default.conf – configuration file, containing the default group‟s settings;
locale.d/strings.en – file containing strings used by the application;
profiles/ – directory containing predefined configuration profiles:
default_recommended/ – directory containing the default configuration
files;
high_overall_security/ – directory containing the configuration files of
the high security profile;
high_scan_speed/ – directory containing the configuration files of the
high speed profile;
templates/ – directory containing notification templates;
templates-admin/ – directory containing administrator‟s notifications tem-
plates;
kav4lms.conf – the application‟s main configuration file.
/usr/local/bin/ – a directory that contains executable files of all Kaspersky Anti-
Virus components:
kav4lms-cmd – executable file of the command line tool;
kav4lms-setup.sh – the application‟s setup script;
kav4lms-kavscanner – executable file of the file system scan component;
Page 19

Installing and uninstalling the application 19
kav4lms-licensemanager – executable file of the keys management compo-
nent;
kav4lms-keepup2date – executable file of the updater component;
/usr/local/sbin/ – a directory that contains executable files of application‟s ser-
vices;
/usr/local/etc/rc.d/ – directory containing control scripts for application services:
kav4lms.sh – control script for the central service of the application;
kav4lms-filters.sh – control script for Kaspersky Anti-Virus filter;
/usr/local/lib/kaspersky/kav4lms/ - directory containing Kaspersky Anti-Virus li-
brary files;
/usr/local/libexec/kaspersky/kav4lms/avbasestest – utility validating downloaded
updates to the anti-virus databases used by the kav4lms-keepup2date component;
/usr/local/share/doc/kav4lms/ – directory containing license agreement and de-
ployment documentation;
/usr/local/man/ – directory containing manual files;
/usr/local/share/kav4lms/scripts/ – directory containing the application‟s scripts;
/usr/local/share/kav4lms/snmp-mibs/ – directory containing the Kaspersky Anti-
Virus MIB;
/usr/local/share/kav4lms/webmin/ – directory containing plug-in to Webmin appli-
cation;
/var/db/kaspersky/kav4lms/ - directory containing variable data of Kaspersky
Anti-Virus:
backup/ – directory containing messages‟ backup copies and information
files;
bases/ – directory containing anti-virus databases;
bases.backup/ – directory containing backup copy of the anti-virus data-
bases;
licenses/ – directory containing key files;
nqueue/ – directory containing the mail queue files;
patches/ – directory containing the application modules‟ updates;
stats/ – directory containing statistics files;
updater/ – directory containing information file about the last update.
3.4. Post-installation setup
Immediately after the application files have been copied to your server, the system configuration process will start. The configuration procedure will either be
Page 20

20 Kaspersky Anti-Virus 5.6 for Linux Mail Server
started automatically or, if the package manager (such as rpm) does not allow
the use of interactive scripts, you will have to initiate it manually.
To start product configuration manually, enter the following in the command line:
In Linux:
# /opt/kaspersky/kav4lms/lib/bin/setup/postinstall.pl
In FreeBSD:
# /usr/local/libexec/kaspersky/kav4lms/setup/postinstall.pl
You will see an offer to perform the following operations:
1. If the application finds on the computer configuration files of Kaspersky
Anti-Virus 5.5 for Linux Mail Server or Kaspersky Anti-Virus 5.6 for
Sendmail with Milter API, it will offer during this step to choose the file
for conversion and saving in the format of the current product version. If
you select one of the files, you will be offered to replace the default configuration file included into the distribution package with this restored
and converted file.
To replace the configuration file from the distribution package with the
restored file, enter yes as your response. To cancel the replacement,
enter no.
By default converted configuration files are saved in the following directories:
kav4mailservers /etc/opt/kaspersky/kav4lms/profiles/kav4mailservers5.
5-converted
kavmilter /etc/opt/kaspersky/kav4lms/profiles/kavmilter5.6converted
2. Specify the path to the key file.
Please note, that if the product key is not installed, the anti-virus will not
update its databases and create the protected domains list during installation. In that case you will have to perform those steps manually after
key installation.
3. Specify the parameters of the proxy server used for connection to the
Internet in the following format:
http://<IP-proxy_server_address>:<port>
or
Page 21
Installing and uninstalling the application 21
Note:
The anti-virus databases can only be updated with the installed product key.
Warning!
In case of product integration with qmail automatic updates should be
configured as follows:
# /opt/kaspersky/kav4lms/bin/kav4lms-setup.sh \
--install-cron=updater --user=root
http://<user_name>:<password>@<proxy_server_IP_addres
s>:<port>
if the proxy server requires authentication.
If no proxy server is used to connect to the Internet, enter no as your
response.
The kav4lms-keepup2date update component will use the value to con-
nect to the source of updates.
4. Update the anti-virus databases. To do that, enter yes as your re-
sponse. If you wish to skip updates during this step, enter no. You will
be able to run the update procedure later using the kav4lms-
keepup2date component (see 7.2 on p. 78 for details).
5. Configure automatic updates of the anti-virus databases. To do that, en-
ter yes as your response. To skip configuration of automatic updates
during this step, enter no. You will be able to configure updates later using the kav4lms-setup component (see 7.1 on p. 77) or manually (see
10.2 on p. 95 for details).
6. Install the webmin module for management of Kaspersky Anti-Virus
within the web-based interface of Webmin.
The remote management plug-in will only be installed provided that
Webmin is installed in the default directory. After plug-in installation you
will see appropriate guidelines for configuration of its interaction with the
application.
Enter yes to install the Webmin module or no to cancel its installation.
7. Determine the list of domains whose e-mail traffic will be protected
against viruses. The default value is localhost, localhost.localdomain.
To use it, press Enter.
To specify the list of domains manually, enter them in the command
line. You can define several comma-delimited values; masks and regu-
Page 22
22 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Warning!
During automatic integration with Sendmail the script always tries to
modify the .mc file because any subsequent update will preserve the
entered changes. If the .mc file contains include directions referring to
.mc files that do not exist, then such file cannot be used for integration
of Kaspersky Anti-Virus. In such case install the sendmail-cf package
for integration using .cf file.
If the .mc file cannot be used for integration of the application, then .cf
file will be used for that purpose.
lar expressions are supported. Dots should be escaped by slash symbol.
E.g.:
re:.*\.example\.com
8. Integrate Kaspersky Anti-Virus with MTA. You can agree to the default
suggested method of integration with the MTA found on the computer or
cancel integration and perform it manually. Please see Chapter 4 on p.
28 for a detailed description of integration with MTA.
By default, the post-queue integration is used for Exim and Postfix mail
systems (see 4.1.1 on p. 29 and 4.2.1 on p. 35).
3.5. Configuration of permission
rules in SELinux and AppArmor
systems
To create a SELinux module with the rules necessary for Kaspersky Anti-Virus
operation, perform the following steps after application setup and its integration
with the e-mail system:
1. Switch SELinux into permissive mode:
# setenforce Permissive
2. Send one or more test messages and make sure that they have passed
anti-virus scanning and have been delivered to recipients.
3. Create a rules module based on the blocking records:
For Fedora:
# audit2allow -l –M kav4lms -i /var/log/messages
Page 23

Installing and uninstalling the application 23
For RHEL:
# audit2allow -l -M kav4lms –i\
/var/log/audit/audit.log
4. Load the resulting rules module:
# semodule -i kav4lms.pp
5. Switch SELinux into enforcement mode:
# setenforce Enforcing
If new audit messages pertaining to Kaspersky Anti-Virus appear, the rules module file should be updated:
For Fedora:
# audit2allow -l –M kav4lms -i /var/log/messages
# semodule -u kav4lms.pp
For RHEL:
# audit2allow -l -M kav4lms -i /var/log/audit/audit.log
# semodule -u kav4lms.pp
For additional information please refer to:
RedHat Enterprise Linux: «Red Hat Enterprise Linux Deployment
Guide», chapter «44. Security and SELinux».
Fedora: Fedora SELinux Project Pages.
Debian GNU/Linux: «Configuring the SELinux Policy» manual from the
«Documentation for Security-Enhanced Linux» selinux-doc package.
To update AppArmor profiles necessary for operation of Kaspersky Anti-Virus,
perform the following steps after application setup and its integration with the email system:
1. Switch all application rules into complain mode:
# aa-complain /etc/apparmor.d/*
# /etc/init.d/apparmor reload
2. Restart the e-mail system:
# /etc/init.d/postfix restart
3. Restart kav4lms and kav4lms-filters:
# /etc/init.d/kav4lms restart
# /etc/init.d/kav4lms-filters restart
Page 24

24 Kaspersky Anti-Virus 5.6 for Linux Mail Server
4. Send one or more test messages and make sure that they have passed
anti-virus scanning and have been delivered to recipients.
5. Launch the profiles updating utility:
# aa-logprof
6. Reload AppArmor rules:
# /etc/init.d/apparmor reload
7. Switch all application rules into enforcement mode:
# aa-enforce /etc/apparmor.d/*
# /etc/init.d/apparmor reload
If new audit messages pertaining to Kaspersky Anti-Virus appear, the steps 5
and 6 should be repeated.
For additional information please refer to:
openSUSE and SUSE Linux Enterprise Server: «Novell AppArmor
Quick Start», «Novell AppArmor Administration Guide».
Ubuntu: «Ubuntu Server Guide», chapter «8. Security».
3.6. Installing the Webmin module to
manage Kaspersky Anti-Virus
The activity of Kaspersky Anti-Virus can be controlled remotely via a web
browser using Webmin.
Webmin is a program which simplifies the administration of Linux/Unix systems.
The software has a modular structure, and supports connection of new or customized modules. Additional information about Webmin can be obtained, and its
distribution package downloaded, from the official program web site at:
www.webmin.com.
The distribution package of Kaspersky Anti-Virus contains a Webmin module that
can either be connected during the application‟s post-installation configuration
(see 3.4 on p. 19) if the system already has Webmin installed, or at any time later
after Webmin is installed.
The following part of this manual contains a detailed description of the procedure
necessary to connect the Webmin module for administration of Kaspersky AntiVirus.
Page 25
Installing and uninstalling the application 25
Note:
The Webmin module is the file mailgw.wbm, which is installed by default in the
/opt/kaspersky/kav4lms/share/webmin/ directory (for Linux distributions), or the
/usr/local/share/kav4lms/webmin/ directory (for FreeBSD distributions).
If default settings were selected during Webmin installation, then you can access
the program after setup in a web browser connecting to port 10000 via
HTTP/HTTPS.
To install the Webmin module for Kaspersky Anti-Virus management:
1. Use your web browser to access Webmin with administrator privileges.
2. Select the Webmin Configuration tab in the program menu, and then
proceed to the Webmin Modules section.
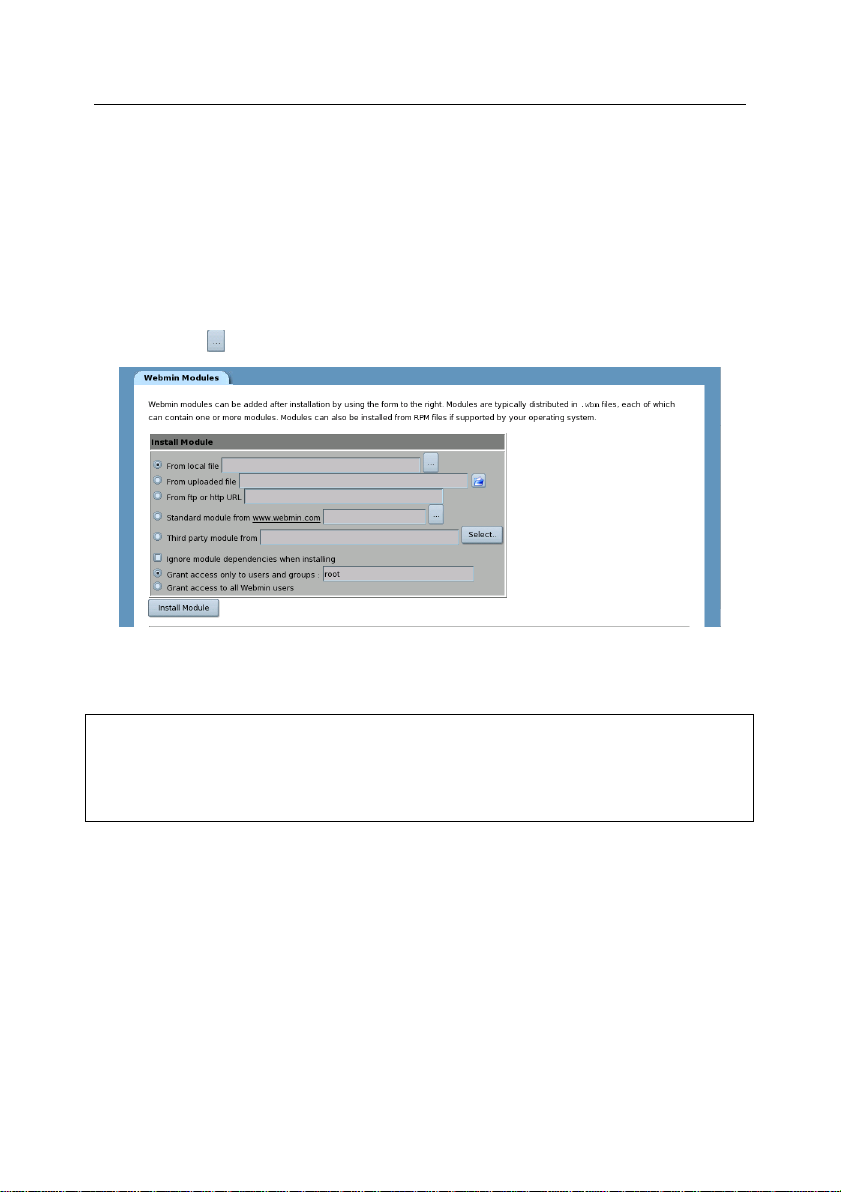
3. Select the From Local File option in the Install Module section and
click (see Figure 1).
Figure 1. Install Module section
4. Select the path to the Webmin module of the product and click OK.
A message on the display will confirm the successful installation of the Webmin
module.
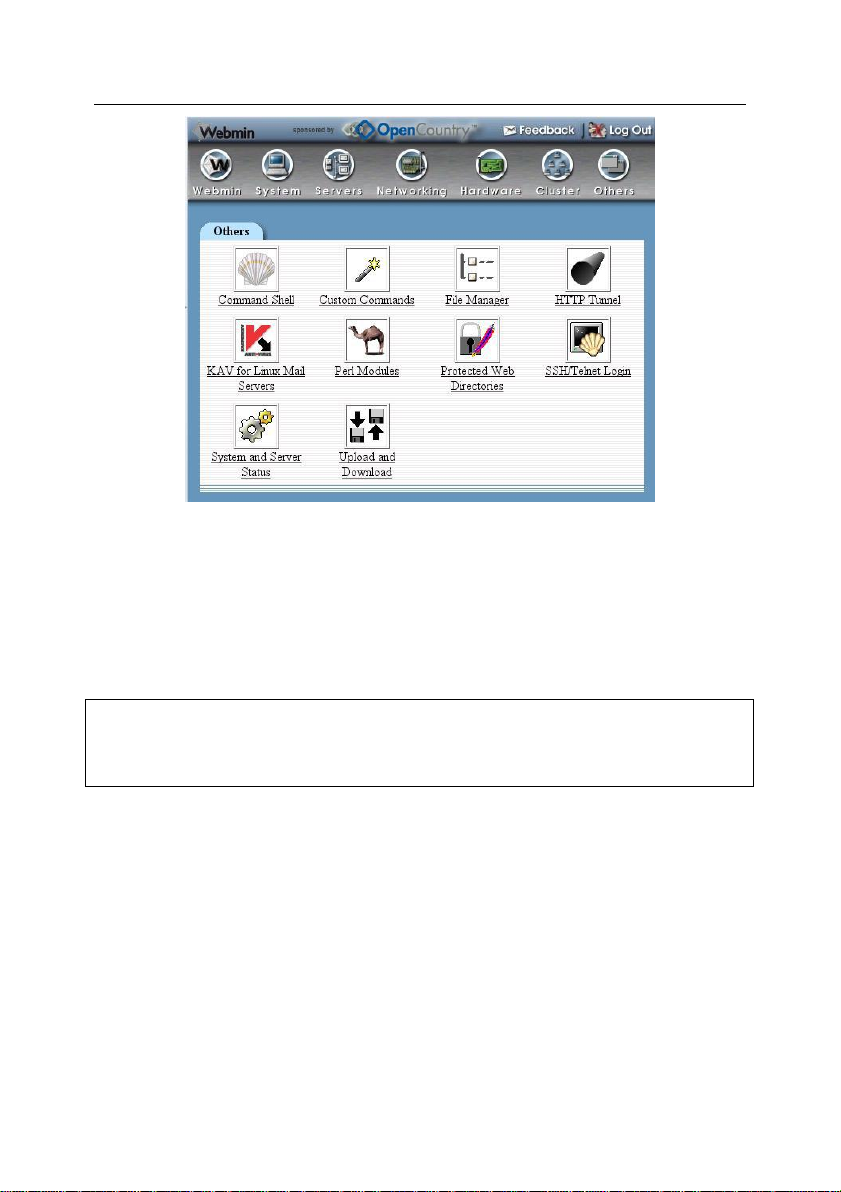
You can access the settings of Kaspersky Anti-Virus by clicking its icon within the
Others tab (see Figure 2).
Page 26
26 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Warning!
The removal procedure will stop the application without additional user participation!
Figure 2. The icon of Kaspersky Anti-Virus in the Others tab
3.7. Application removal
Removal of Kaspersky Anti-Virus from server requires superuser (root) privileges. If you have no such privileges when you start the removal procedure, you
will have to log on as root first.
During removal the application will be stopped, its files and directories created at
product installation will be deleted. However, files and directories created or
modified by the administrator (configuration file of the application, configuration
files of groups, template notification files, backup directories, key file), will be
preserved.
The application removal procedure can be initiated using different methods depending upon the system package manager. Let us examine those methods
closely.
In order to remove Kaspersky Anti-Virus installed from a rpm package, enter the
following text in the command line:
# rpm -e <package_name>
Page 27

Installing and uninstalling the application 27
In order to remove Kaspersky Anti-Virus installed from a deb package, enter the
following in the command line:
# dpkg -P <package_name>
if you wish to remove the application together with its configuration files, or:
# dpkg -r <package_name>
if you wish to uninstall the application but keep its configuration files.
In order to remove Kaspersky Anti-Virus installed from a pkg package, enter the
following in the command line:
# pkg_delete <package_name>
A message on the display will confirm the successful removal of the application.
If a plug-in for remote management of the application (Webmin module) was
installed, it must be removed manually using standard Webmin tools.
Page 28
Note:
MTA does not allow mail rejection if post-queue integration is used. However, if
reject is selected as the action over objects in Kaspersky Anti-Virus settings, the
sender will receive a notification about message rejection. Notification text is
defined by the RejectReply option in the [kav4lms: groups.
<group_name>.settings] section of the group configuration file.
Warning!
Two rules must be observed while using a socket:
The port number, which is a part of network socket definition, must be
greater than 1024.
Both filter and central services must have sufficient privileges to access
the local socket used.
CHAPTER 4. INTEGRATION
WITH MTA
After installation the Anti-Virus must be integrated with the host e-mail system.
To do that, the parameters in the configuration files of the application and MTA
have to be modified. You can perform integration using the product configuration
script included into the distribution package (see 3.4 on p. 19 and 10.2 on p. 95),
or modify the configuration files of Kaspersky Anti-Virus and MTA manually.
For Exim and Postfix the Anti-Virus supports both pre-queue and post-queue
integration. In case of pre-queue integration messages are transferred for analysis before their addition to MTA queue, post-queue integration means that they
are checked after addition to the mail queue.
The sockets used for data exchange between MTA, filter and the central service
of Kaspersky Anti-Virus are assigned using the following rules:
inet:<port>@<ip_address> – for a network socket
local:<socket_path> – for a local socket.
Page 29

Integration with MTA 29
Warning!
In case of post-queue integration with Exim the FilterSocket, Ser-
viceSocket and ForwardSocket options must point to the network
socket.
4.1. Integration with Exim
The Anti-Virus can use two methods for integration with Exim:
post-queue integration using modification of routers: all e-mail traf-
fic passing the protected server will be transferred for scanning after its
addition to the MTA queue (post-queue filtering).
pre-queue integration using dynamically loaded library: messages
will be transferred for scanning before their addition to the MTA queue
(pre-queue filtering).
4.1.1. Post-queue integration using
modification of routers
Integration using modification of routers implies that messages will be sent for
scanning from all e-mail transfers. To accomplish that, kav4lms_filter must be
specified as the value of the pass_router option for each Exim router.
In case of post-queue integration correct e-mail transfer to the Anti-Virus and its
return to MTA requires observance of the following conditions:
1. The filter must be configured to intercept messages from MTA. The
endpoint of the «filter - MTA» connection is the socked defined by the
FilterSocket option in the [kav4lms:filter.settings] section of the main
application configuration file.
2. The filter must pass messages over for scanning to the central
application service. The endpoint of the «filter – central service»
connection is the socket defined by the ServiceSocket option in the
[kav4lms:server.settings] section of the main application configuration
file.
3. The filter must return messages to the MTA. The endpoint of the «appli-
cation – MTA» connection is the socket defined by the ForwardSocket
option in the [kav4lms:filter.settings] section of the main application
configuration file.
Page 30

30 Kaspersky Anti-Virus 5.6 for Linux Mail Server
To integrate Kaspersky Anti-Virus with Exim using the application configuration
script:
run the following command:
in Linux:
# /opt/kaspersky/kav4lms/bin/kav4lms-setup.sh \
--install-filter=exim
in FreeBSD:
# /usr/local/bin/kav4lms-setup.sh \
--install-filter=exim
To integrate the application with Exim manually:
1. Make a backup copy of Exim configuration files.
2. Add the following lines in the main configuration settings section of
the Exim configuration file:
#kav4lms-filter-begin-1
local_interfaces=0.0.0.0.25:<forward_socket_ip>.\
<forward_socket_port_number>
#kav4lms-filter-end-1
where <forward_socket_ip>.<forward_socket_port_number>
is the IP-address and port of the socket, to which mail is routed by application after checking.
3. Add the following lines to the routers section of the Exim configuration
file:
#kav4lms-filter-begin-2
kav4lms_dnslookup:
driver = dnslookup
domains = ! +local_domains
ignore_target_hosts = 0.0.0.0 : 127.0.0.0/8
verify_only
pass_router = kav4lms_filter
no_more
kav4lms_system_aliases:
driver = redirect
allow_fail
allow_defer
Page 31

Integration with MTA 31
data = ${lookup{$local_part}lsearch{/etc/aliases}}
verify_only
pass_router = kav4lms_filter
kav4lms_localuser:
driver = accept
check_local_user
verify_only
pass_router = kav4lms_filter
failed_address_router:
driver = redirect
verify_only
condition = "{0}"
allow_fail
data = :fail: Failed to deliver to address
no_more
kav4lms_filter:
driver = manualroute
condition = "${if or {{eq {$interface_port}\
{<forward_socket_port_number>}} \
{eq {$received_protocol}{spam-scanned}} \
}{0}{1}}"
transport = kav4lms_filter
route_list = "* localhost byname"
self = send
#kav4lms-filter-end-2
where <forward_socket_port_number> is the number of port, to
which mail is routed by application after checking.
4. Add the following lines to the Exim‟s transports definition section:
#kav4lms-filter-begin-3
kav4lms_filter:
driver = smtp
port = <filter_socket_port_number>
delay_after_cutoff = false
Page 32

32 Kaspersky Anti-Virus 5.6 for Linux Mail Server
allow_localhost
#kav4lms-filter-end-3
where <filter_socket_port_number> is the number of port, on
which the application‟s filter service is listening.
5. Set the ForwardSocket parameter to
<forward_socket_ip>.<forward_socket_port_number> value
from step 2. The ForwardSocket parameter resides in the
[kav4lms:filter.settings] section of the kav4lms.conf configuration file.
6. Stop the kav4lms-filter service.
7. Add the following line to the [1043] section of the
/var/opt/kaspersky/applications.setup (in Linux)
/var/db/kaspersky/applications.setup (in FreeBSD) file:
FILTER_SERVICE=true
FILTER_PROGRAM=kav4lms-filter
8. Start the kav4lms-filter service.
9. Restart exim.
4.1.2. Pre-queue integration using
dynamically loaded library
The filter must pass messages for scanning to the central service of the
application. The endpoint of the «filter – central service» connection is the socket
defined by the ServiceSocket option in the [kav4lms:server.settings] section
of the main product configuration file.
To integrated Kaspersky Anti-Virus with Exim using the application configuration
script:
run the following command:
in Linux:
# /opt/kaspersky/kav4lms/bin/kav4lms-setup.sh \
--install-filter=exim-dlfunc
in FreeBSD:
# /usr/local/bin/kav4lms-setup.sh \
--install-filter=exim-dlfunc
Page 33

Integration with MTA 33
To integrate Kaspersky Anti-Virus with Exim manually:
1. Make sure that Exim supports the dlfunc content filtration function. To
do that, run the following command:
exim -bV
Positive response will look like:
Expand_dlfunc
2. Make a backup copy of Exim configuration files.
3. Add the following lines in the main configuration settings section of
Exim configuration file:
#kav4lms-filter-begin
acl_smtp_data = acl_check_data
#kav4lms-filter-end
4. Add the following lines in the ACL section of Exim configuration file:
acl_check_data:
#kav4lms-dlfunc-begin
warn set acl_m0 = \
${dlfunc{<libkavexim.so>}{kav}{<socket>}\
{/var/tmp//.kav4lms-exim}}
accept condition = ${if match{$acl_m0}{\N^kav4lms: \
continue\N}{yes}{no}}
logwrite = kav4lms returned continue
deny condition = ${if match{$acl_m0}{\N^kav4lms: \
reject.*\N}{yes}{no}}
logwrite = kav4lms returned reject
message = Kaspersky Anti-Virus rejected the mail
discard condition = ${if match{$acl_m0}\
{\N^kav4lms: drop.*\N}{yes}{no}}
logwrite = kav4lms returned drop
message = Kaspersky Anti-Virus dropped the mail
defer condition = ${if match{$acl_m0}\
{\N^kav4lms: temporary failure.*\N}{yes}{no}}
logwrite = kav4lms returned temporary failure
message = Kaspersky Anti-Virus returned \
temporary failure
accept
#kav4lms-dlfunc-end
Page 34

34 Kaspersky Anti-Virus 5.6 for Linux Mail Server
where <socket> stands for the socket used for communication between
the filter and central service of Kaspersky Anti-Virus defined by the Ser-
viceSocket option in the [kav4lms:server.settings] section of the
main Kaspersky Anti-Virus configuration file; <libkavexim.so> - path
to the libkavexim.so library:
in 32-bit Linux distributives:
/opt/kaspersky/kav4lms/lib/libkavexim.so
in 64-bit Linux distributives:
/opt/kaspersky/kav4lms/lib64/libkavexim.so
in FreeBSD:
/usr/local/lib/kaspersky/kav4lms/libkavexim.so
5. Stop the kav4lms-filter service.
6. Add the following line to the [1043] section of the
/var/opt/kaspersky/applications.setup (in Linux)
/var/db/kaspersky/applications.setup (in FreeBSD) file:
in Linux:
FILTER_SERVICE=false
FILTER_PROGRAM=/opt/kaspersky/kav4lms/lib/libkavexim\
.so
in FreeBSD:
FILTER_SERVICE=false
FILTER_PROGRAM=/usr/local/lib/kaspersky/kav4lms/\
libkavexim.so
7. Restart exim.
4.2. Integration with Postfix
The Anti-Virus can use three methods for integration with Postfix:
post-queue integration: all mail traffic going through a protected server
is transferred for scanning after being added to the mail system queue;
Page 35

Integration with MTA 35
Warning!
In case of integration with Postfix the FilterSocket, ServiceSocket and
ForwardSocket options can point to a network or local socket.
Note:
While copying strings from the manual to the Postfix configuration file delete the
«\» symbols and the line breaks that follow.
pre-queue integration: messages are transferred for scanning before
being added to the mail system queue;
integration with Milter: messages are transferred for scanning using
the Milter program interface.
4.2.1. Post-queue integration
Correct e-mail transfer to the Anti-Virus and its return to MTA requires observance of the following conditions:
1. The filter must be configured to intercept messages from MTA. The
endpoint of the «filter - MTA» connection is the socked defined by the
FilterSocket option in the [kav4lms:filter.settings] section of the main
application configuration file.
2. The filter must pass messages over for scanning to the central
application service. The endpoint of the «filter – central service»
connection is the socket defined by the ServiceSocket option in the
[kav4lms:server.settings] section of the main application configuration
file.
3. The filter must return messages to the MTA. The endpoint of the
«application – MTA» connection is the socket defined by the
ForwardSocket option in the [kav4lms:filter.settings] section of the
main application configuration file.
To integrate Kaspersky Anti-Virus with Postfix using the application configuration
script:
run the command:
# /opt/kaspersky/kav4lms/bin/kav4lms-setup.sh \
--install-filter=postfix
in FreeBSD:
# /usr/local/bin/kav4lms-setup.sh \
--install-filter=postfix
Page 36

36 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Note:
If local sockets are used with Postfix 2.3 or higher, also add to the line
above the option 'no_milters', i.e.:
-o receive_override_options=\
no_unknown_recipient_checks,no_header_body_checks,\
no_address_mappings,no_milters
To integrate application with Postfix manually:
1. Add the following lines to master.cf file:
#kav4lms-filter-begin
kav4lms_filter unix - - n\
- 10 smtp
-o smtp_send_xforward_command=yes
<forward_socket_ip_address>:<forward_socket_port>\
inet n - n - 10\
smtpd
-o content_filter=
-o receive_override_options=\
no_unknown_recipient_checks,no_header_body_checks,\
no_address_mappings
-o smtpd_helo_restrictions=
-o smtpd_client_restrictions=
-o smtpd_sender_restrictions=
-o smtpd_recipient_restrictions=\
permit_mynetworks,reject
-o mynetworks=127.0.0.0/8,[::1]/128
-o smtpd_authorized_xforward_hosts=\
127.0.0.0/8,[::1]/128
#kav4lms-filter-end
where <forward_socket_ip_address>:<forward_socket_
port> is the address and port of the socket, to which mail is forwarded
after checking by application.
2. Add the following lines to main.cf file:
#kav4lms-filter-begin
content_filter = \
kav4lms_filter:<filter_socket_ip_address>:\
<filter_socket_port>
#kav4lms-filter-end
Page 37

Integration with MTA 37
Warning!
In case of integration with Postfix the FilterSocket, ServiceSocket and
ForwardSocket options can point to a network or local socket.
Note:
While copying strings from the manual to the Postfix configuration file delete the
«\» symbols and the line breaks that follow.
where <filter_socket_ip_address>:<filter_socket_port>
is the address and port of the socket, where the filter process is listening.
3. Stop the kav4lms-filter service.
4. Add the following line to the [1043] section of the
/var/opt/kaspersky/applications.setup (in Linux)
/var/db/kaspersky/applications.setup (in FreeBSD) file:
FILTER_SERVICE=true
FILTER_PROGRAM=kav4lms-filter
5. Start the kav4lms-filter service.
6. Restart Postfix.
4.2.2. Pre-queue integration
Correct e-mail transfer to the Anti-Virus and its return to MTA requires observance of the following conditions:
1. The filter must be configured to intercept messages from MTA. The
endpoint of the «filter - MTA» connection is the socked defined by the
FilterSocket option in the [kav4lms:filter.settings] section of the main
application configuration file.
2. The filter must pass messages over for scanning to the central
application service. The endpoint of the «filter – central service»
connection is the socket defined by the ServiceSocket option in the
[kav4lms:server.settings] section of the main application configuration
file.
3. The filter must return messages to the MTA. The endpoint of the
«application – MTA» connection is the socket defined by the
ForwardSocket option in the [kav4lms:filter.settings] section of the
main application configuration file.
Page 38

38 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Note:
If local sockets are used with Postfix 2.3 or higher, also add to the line
above the option 'no_milters', i.e.:
-o receive_override_options=\
no_unknown_recipient_checks,no_header_body_checks,\
no_address_mappings,no_milters
To integrate Kaspersky Anti-Virus with Postfix using the application configuration
script:
run the command:
# /opt/kaspersky/kav4lms/bin/kav4lms-setup.sh \
--install-filter=postfix-prequeue
in FreeBSD:
# /usr/local/bin/kav4lms-setup.sh \
--install-filter=postfix-prequeue
To integrate application with Postfix manually:
1. Add the following lines to master.cf file:
#kav4lms-prequeue-begin
kav4lms_filter unix - - n\
- 10 smtp
-o smtp_send_xforward_command=yes
<forward_socket_ip_address>:<forward_socket_port>\
inet n - n - 10\
smtpd
-o content_filter=
-o receive_override_options=\
no_unknown_recipient_checks,no_header_body_checks,\
no_address_mappings
-o smtpd_helo_restrictions=
-o smtpd_client_restrictions=
-o smtpd_sender_restrictions=
-o smtpd_recipient_restrictions=\
permit_mynetworks,reject
-o mynetworks=127.0.0.0/8,[::1]/128
-o smtpd_authorized_xforward_hosts=\
127.0.0.0/8,[::1]/128
#kav4lms-prequeue-end
Page 39

Integration with MTA 39
Warning!
In case of integration with Postfix the FilterSocket and ServiceSocket
options can point to a network or local socket.
where <forward_socket_ip_address>:<forward_socket_
port> is the address and port of the socket, to which mail is forwarded
after checking by application.
2. Add the following lines to master.cf file:
smtp inet n - n - 20 smtpd
add the parameter
#kav4lms-prequeue-begin
-o smtpd_proxy_filter=:<filter_socket_port>
#kav4lms-prequeue-end
3. Stop the kav4lms-filter service.
4. Add the following line to the [1043] section of the
/var/opt/kaspersky/applications.setup (in Linux)
/var/db/kaspersky/applications.setup (in FreeBSD) file:
FILTER_SERVICE=true
FILTER_PROGRAM=kav4lms-filter
5. Start the kav4lms-filter service.
6. Restart Postfix.
4.2.3. Integration with Milter
Correct e-mail transfer to the Anti-Virus and its return to MTA requires observance of the following conditions:
1. The filter must be configured to intercept messages from MTA. The
endpoint of the «filter - MTA» connection is the socked defined by the
FilterSocket option in the [kav4lms:filter.settings] section of the main
application configuration file.
2. The filter must pass messages over for scanning to the central
application service. The endpoint of the «filter – central service»
connection is the socket defined by the ServiceSocket option in the
[kav4lms:server.settings] section of the main application configuration
file.
Page 40

40 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Note:
While copying strings from the manual to the Postfix configuration file delete the
«\» symbols and the line breaks that follow.
To integrate Kaspersky Anti-Virus with Postfix using the application configuration
script:
run the command:
# /opt/kaspersky/kav4lms/bin/kav4lms-setup.sh \
--install-filter=postfix-milter
in FreeBSD:
# /usr/local/bin/kav4lms-setup.sh \
--install-filter=postfix-milter
To integrate application with Postfix manually:
1. Add the following lines to main.cf file:
smtpd_milters = inet:127.0.0.1:10025,
#kav4lms-milter-begin
milter_connect_macros = j _ {daemon_name} {if_name} \
{if_addr}
milter_helo_macros = {tls_version} {cipher} \
{cipher_bits} {cert_subject} {cert_issuer}
milter_mail_macros = i {auth_type} {auth_authen} \
{auth_ssf} {auth_author} {mail_mailer} {mail_host} \
{mail_addr}
milter_rcpt_macros = {rcpt_mailer} {rcpt_host} \
{rcpt_addr}
milter_default_action = tempfail
milter_protocol = 3
milter_connect_timeout=180
milter_command_timeout=180
milter_content_timeout=600
#kav4lms-milter-end
2. Stop the kav4lms-milter service.
3. Add the following line to the [1043] section of the
/var/opt/kaspersky/applications.setup (in Linux)
/var/db/kaspersky/applications.setup (in FreeBSD) file:
FILTER_SERVICE=true
FILTER_PROGRAM=kav4lms-milter
Page 41

Integration with MTA 41
Warning!
In case of integration with qmail the ServiceSocket option can point to a network
or local socket.
4. Start the kav4lms-milter service.
5. Restart Postfix.
4.3. Integration with qmail
The qmail MTA does not provide support for filtering extensions. Filtering is implemented by the /opt/kaspersky/kav4lms/lib/bin/kav4lms-qmail
(/usr/local/libexec/kaspersky/kav4lms/kav4lms-qmail for FreeBSD) binary, provided with the application, which replaces the original qmail-queue binary. The
replacing file implements filtering and passes the mail traffic to the original qmailqueue for delivery. Messages are transferred for analysis before their addition to
MTA queue (pre-queue filtration).
To integrate Kaspersky Anti-Virus with qmail using the application configuration
script:
run the command:
# /opt/kaspersky/kav4lms/bin/kav4lms-setup.sh \
--install-filter=qmail
in FreeBSD:
# /usr/local/bin/kav4lms-setup.sh \
--install-filter=qmail
To integrate the application with qmail manually:
1. Rename the qmail-queue file in the /var/qmail/bin directory to qmail-
queue-real.
2. Copy the /opt/kaspersky/kav4lms/lib/bin/kav4lms-qmail
(/usr/local/libexec/kaspersky/kav4lms/kav4lms-qmail for FreeBSD) file to
the /var/qmail/bin directory and rename it to qmail-queue.
3. Set the following permissions for qmail-queue and qmail-queue-real
files:
-rws—x--x 1 qmailq qmail
4. Stop the kav4lms-filter service.
5. Change the owner and group to qmailq:qmail for the following direc-
tories and their contents:
Page 42

42 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Note:
If you enter changes into cf file only, they will be lost the next time when generation of the cf file from the mc file is initiated.
for Linux:
# /opt/kaspersky/kav4lms/bin/kav4lms-setup.sh \
--switch-credentials=qmailq,qmail
for FreeBSD:
# /usr/local/bin/kav4lms-setup.sh \
--switch-credentials=qmailq,qmail
6. Add the following line to the [1043] section of the
/var/opt/kaspersky/applications.setup (in Linux)
/var/db/kaspersky/applications.setup (in FreeBSD) file:
in Linux:
FILTER_SERVICE=false
FILTER_PROGRAM=/opt/kaspersky/kav4lms/lib/bin\
/kav4lms-qmail
in FreeBSD:
FILTER_SERVICE=false
FILTER_PROGRAM=/usr/local/libexec/kaspersky/kav4lms\
/kav4lms-qmail
7. Restart qmail.
4.4. Integration with Sendmail
Sendmail provides the Milter API to implement integration with custom filters.
The mail traffic should be passed from Sendmail to Kaspersky Anti-Virus and
back using the Milter interface calls. Messages are transferred for analysis before their addition to MTA queue (pre-queue integration).
As a rule, in case of product integration with Sendmail changes are made to the
MTA configuration file in mc format, the cf file changes automatically. If such
functionality is not supported, then after modification of the appropriate mc file,
the corresponding cf file should be modified, too.
Page 43

Integration with MTA 43
Warning!
In case of integration with Sendmail the FilterSocket and ServiceSocket options can point to a network or local socket.
4.4.1. Integration with Sendmail using
.cf
file
To integrate Kaspersky Anti-Virus with Sendmail using the application configuration script:
run the command:
# /opt/kaspersky/kav4lms/bin/kav4lms-setup.sh \
--install-filter=sendmail-milter
in FreeBSD:
# /usr/local/bin/kav4lms-setup.sh \
--install-filter=sendmail-milter
To integrate the application with Sendmail manually:
1. Make backup copy of sendmail.cf file.
2. Add the following strings to the sendmail.cf file:
#kav4lms-milter-begin-filter
O InputMailFilters=kav4lms_filter
O Milter.macros.connect=j, _, {daemon_name}, \
{if_name}, {if_addr}
O Milter.macros.helo={tls_version}, {cipher}, \
{cipher_bits}, {cert_subject}, {cert_issuer}
O Milter.macros.envfrom=i, {auth_type}, \
{auth_authen}, {auth_ssf}, {auth_author}, \
{mail_mailer}, {mail_host}, {mail_addr}
O Milter.macros.envrcpt={rcpt_mailer}, {rcpt_host}, \
{rcpt_addr}
#kav4lms-milter-end-filter
3. Add the following lines to the sendmail.cf file:
a) if integrating via network socket:
#kav4lms-milter-begin-socket
Page 44

44 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Xkav4lms_filter,
S=inet:<filter_port>@<filter_address>,F=T,\
T=S:3m;R:5m;E:10m
#kav4lms-milter-end-socket
where <filter_port> is the port number of the network socket,
where the filter service is listening, <filter_address> is the
name or IP-address of the server, where filter service is running.
b) If the local socket is required for connection, change the socket
definition section to the following:
#kav4lms-milter-begin-socket
Xkav4lms_filter,
S=unix:<filter_socket_file_path>,F=T,T=S:3m;\
R:5m;E:10m
#kav4lms-milter-end-socket
where <socket_file_path> is the path to the local socket.
4. Stop the kav4lms-milter service.
5. Add the following line to the [1043] section of the
/var/opt/kaspersky/applications.setup (in Linux)
/var/db/kaspersky/applications.setup (in FreeBSD) file:
FILTER_SERVICE=true
FILTER_PROGRAM=kav4lms-milter
6. Start the kav4lms-milter service.
7. Restart Sendmail.
4.4.2. Integration with Sendmail using
file
To integrate the application with Sendmail via the .mc file:
1. Make backup copy of .mc file.
2. Add the following strings to the .mc file:
dnl kav4lms-milter-begin dnl
define(`_FFR_MILTER', `true')dnl
INPUT_MAIL_FILTER(`kav4lms_filter',\
`S=inet:10025@127.0.0.1,F=T,T=S:3m;R:5m;E:10m')dnl
dnl kav4lms-milter-end dnl
.mc
Page 45

Integration with MTA 45
3. Compile the .cf configuration file according to your operation system‟s
rules.
4. Stop the kav4lms-filter service.
5. Add the following line to the [1043] section of the
/var/opt/kaspersky/applications.setup (in Linux)
/var/db/kaspersky/applications.setup (in FreeBSD) file:
FILTER_SERVICE=true
FILTER_PROGRAM=kav4lms-milter
6. Start the kav4lms-filter service.
7. Restart Sendmail.
Page 46

CHAPTER 5. ANTI-VIRUS
PROTECTION OF E-MAIL
5.1. Setting up groups
A group consists of multiple addresses of senders and recipients whose messages are processed using the same settings of Kaspersky Anti-Virus.
Custom mail scanning settings can be specified for each group to define, for example:
E-mail scanning method (see 5.2 on p. 48).
E-mail scanning mode (see 5.3 on p. 48).
Actions over messages and their objects (see 5.4 on p. 52).
Backup e-mail copying before processing (see 5.6 on p. 56).
Notifications about found objects (see 5.7 on p. 57).
Each group‟s settings are stored in a separate configuration file (see A.2 on p.
127). All group configuration files must be specified using the _include directive in the [kav4lms:groups] section of the main application‟s configuration file
kav4lms.conf. Group configurations can be included by indicating a configuration
file name or the name of a directory, containing all group configuration files.
By default, group configuration files should be located in the
/etc/opt/kaspersky/kav4lms/groups.d/ directory.
The product distribution package includes the Default group configuration file -
default.conf. After product installation it appears in the
/etc/opt/kaspersky/kav4lms/groups.d/ directory. Values defined in that file are
used as defaults if they are not specified in appropriate group configuration file.
Parameters of the Default group configuration file are used if there are no existing groups.
The Anti-Virus scans a message using the settings of the group in which its
sender or recipient are found (from the MAIL FROM and RCPT TO commands).
If the sender and all recipients belong to different groups, the application selects
the group with the highest priority. If no groups are found, such message will be
processed using the settings specified in the Default group configuration file,
which has the lowest priority of 0. Therefore, it is recommended to specify higher
protection level for groups with higher priority.
Page 47

Anti-virus protection of e-mail 47
Note:
You are advised to use the default.conf file as a template when creating group configuration file. Run the following commands to replace
the group name quickly :
# cd /etc/opt/kaspersky/kav4lms/groups.d
# sed 's|groups.default|groups.<group_name>|'
default.conf > <group_name>.conf
Warning!
Regular expressions are case insensitive.
Priority is a unique group identifier. It is defined by the Priority option in the
[kav4lms:groups.<group_name>.definition] section of the group configuration
file.
Senders and recipients are defined using the Senders and Recipients options in
the [kav4lms:groups.<group_name>.definition] section of a group configuration file.
To create a new group,
1. Create group configuration file in the directory specified in the
[kav4lms:groups] section of the main product configuration file. The
default directory is /etc/opt/kaspersky/kav4lms/groups.d/
2. Define group priority in its configuration file setting the Priority option in
the [kav4lms:groups.<group_name>.definition] section. Any natural
value can be entered as the value. Groups with the same priority and 0
priority are not allowed.
3. Define the addresses of senders and recipients in the group configura-
tion file settings the Senders and Recipients options in the
[kav4lms:groups.<group_name>.definition] section.
«*» and «?» wildcards in masks are supported as well as regular expressions beginning with the «re:» prefix. To specify several addresses
(address masks), each new record must begin in a new line:
Senders=reporter@*.mydomain.com
Recipients=re:office\d+@central\.mydomain\.com
At least one of the Senders or Recipients options must be defined. If
Recipients or Senders option in group definition is missing, the appli-
cation will use for that parameter the default value specified in the default.conf - «*@*» (all addresses).
Page 48

48 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Note:
If an action applicable to a message part is selected as action over a whole
message (see 5.4 on p. 52), then such letter will be scanned part-by-part regardless of the analysis method chosen.
4. If necessary, specify the options for e-mail scanning in the correspond-
ing sections of the group configuration file (see A.2 on p. 127 for details). If an option is not defined in group configuration file, the application uses the value specified for that parameter in the Default group
configuration file - default.conf.
5.2. Definition of e-mail analysis
policy
The Anti-Virus supports the following methods of e-mail analysis:
Scanning of the whole message as a single solid object – message
header and body are analyzed as a whole.
Combined approach – a message is scanned first as a single object,
then the application parses it into objects (message body, attachments,
etc.) and checks each of them individually. That method provides for
higher protection level and reliability.
The method of e-mail scanning is determined by the policy and defined by the
ScanPolicy option in the [kav4lms:groups.<group_name>.settings] section of
the group configuration file.
To scan messages as single objects,
set the ScanPolicy option to message.
To use combined approach while scanning messages,
set the ScanPolicy option to combined.
5.3. E-mail scanning mode
The next step of group setup is to select the mode of e-mail scanning. Kaspersky
Anti-Virus offers the following scanning modes:
Scanning for the presence of malware.
Content filtering.
Page 49

Anti-virus protection of e-mail 49
The scanning mode for a group is specified via the Check option in the
[kav4lms:groups.<group_name>.settings] section of the group configuration
file. It can take the following values:
anti-virus – perform anti-virus mail scanning;
content-filter – filter by name, type and size of attachments;
all – perform both anti-virus check and content filtration;
none – disable mail scanning.
If both anti-virus scanning and filtration are enabled, then analysis is performed
in the following order:
1. anti-virus scan of a message as a whole object;
2. filtration of attachments;
3. message scan part-by-part (if combined scanning method is selected
ScanPolicy=combined).
5.3.1. Anti-virus scanning
Anti-virus scanning is enabled by setting the Check option in the
[kav4lms:groups.<group_name>.settings] section of the group configuration
file to anti-virus or all.
After a message has been scanned for viruses, the application assigns a certain
status to the message or its object:
clean – message contains no malware;
infected – message (or its part) contains harmful objects;
suspicious – message (or its part) contains a suspicious object (as-
signed only when heuristics analyzer is enabled);
protected – message (or its part) is password-protected or encrypted;
error – message is corrupted or scanning process generated an error.
The status assigned after scan is used for further processing of messages and
their objects (see 5.4 on p. 52).
For infected messages (infected) specific handling procedure can be defined
depending upon the name of the detected threat (VirusNameAction option in
the [kav4lms:groups.<group_name>.actions] section of the group
configuration file). Kaspersky Anti-Virus returns the names of recognized threats
in Kaspersky Lab‟s notation, which can be learned from www.viruslist.com. The
list of virus names that are subject to action is specified via the VirusNameList
Page 50

50 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Note:
Setting this parameter to yes enables the suspicious verdict, which is
unavailable otherwise.
Warning!
There are situations, when actual content does not correspond to the
MIME type declared. The application does not perform content identification.
parameter in the [kav4lms:groups.<group_name>.contentfiltering] section.
This parameter excerpts virus names as-is or as regular expressions (POSIX
standard).
The scanning capabilities of the application can be customized to increase the
thoroughness or speed of scanning. Settings, regarding the scan engine
performance are located in [kav4lms:groups.<group_name>.settings] section
of the group‟s configuration file. These settings are:
whether to scan archives (ScanArchives parameter);
whether to scan packed executables (ScanPacked parameter);
whether to perform the heuristic analysis (UseCodeAnalyzer parame-
ter);
how much time to spend on message or message‟s object scan
(MaxScanTime parameter). If the scan time exceeds the specified limit,
the scan ends with error verdict;
whether the application should decode MIME objects that do not comply
with RFC standards using heuristic algorithms (MIMEEncodingHeuris-
tics option);
what malware types are detected (UseAVBasesSet parameter in the
[kav4lms:server.settings] section of the kav4lms.conf file).
5.3.2. Content filtering
Content filtering service is enabled by setting the Check parameter in the
[kav4lms:groups.<group_name>.settings] section of the group configuration
file to content-filter or all.
The Anti-Virus can use the following criteria for content filtering:
MIME type of attachments (applies to the “Content-Type” headers);
Page 51

Anti-virus protection of e-mail 51
Note:
If both anti-virus scanning and content filtering are enabled, the content filtering
is performed before scanning.
Warning!
If the include rule is empty and the exclude rule is not, then all objects, not
matching the exclude rule, are included into filtering.
If both rules are empty, then content filtering is not performed, regardless of the
Check parameter value.
attachment name (applies to the names and extensions of attach-
ments);
attachment size (applies to the size of message parts, the part size is
calculated after attachment decompression).
Filtration criteria are defined in the
[kav4lms:groups.<group_name>.contentfiltering] section of group configuration file.
Two rules can be set up for each filter criterion:
Include rule. This rule specifies objects that are subject to filtering and
described using the following parameters:
IncludeMime – specifies the list of MIME types;
IncludeName – specifies the list of attachment names;
IncludeSize – specifies the list of objects‟ size.
Exclude rule. This rule specifies objects that are not subject to filtering
and described using the following parameters:
ExcludeMime – specifies the list of MIME types;
ExcludeName – specifies the list of attachment names;
ExcludeSize – specifies the list of objects‟ size.
Rules for MIME type and attachment name filtering criteria must be specified as
the list of as:
strings;
wildcard (UNIX standard);
regular (POSIX standard) expressions.
Page 52

52 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Warning!
Regular expressions are case insensitive; they must begin with the «re:» prefix.
Rules for object size must be specified as:
number of bytes;
numbers with the size mark („KB‟ or „MB‟);
comparison signs.
5.4. Actions over objects
After the scan and content filtering is performed, Kaspersky Anti-Virus performs
specific actions over messages and their parts. Some actions are applicable to
whole messages only while others can apply just to message parts. The parameters that determine application actions can take the following values:
warn – message is replaced completely with text warning about the
presence of a dangerous object;
drop – message is accepted, but silently dropped without delivery to the
recipient;
reject – message delivery is rejected (this action is not performed when
using the application with Postfix (post-queue integration) or Exim, the
bounce action is produced in that case). If this action is chosen, the
sender receives a notification defined by the RejectReply option;
skip – the message or its part is allowed to pass unchanged, the scan
result is recorded into application log;
cure (available only after anti-virus scan for message parts) – the appli-
cation attempts to cure infected objects. If disinfection fails, the delete
action is taken;
rename (available only after content filtering for message parts) – the
application adds to attachment name the RenameTo parameter‟s value.
If the value defines an extension (for instance, .vir), then this value is
added to the attachment‟s name. Otherwise, this value is assumed to
be the whole name, so the entire attachment name is replaced;
delete – the message part is removed and (if the UsePlaceholderNo-
tice parameter is set to yes) replaced by a notification. The notification
text is taken from a template file named part_<action>.
The actions performed after anti-virus scanning are specified by the
InfectedAction, SuspiciousAction, ProtectedAction, ErrorAction and
Page 53

Anti-virus protection of e-mail 53
Warning!
The fact, that content filtering takes place before scan, may lead to a situation,
when the whole message scan results with infected verdict, but part-by-part
scan results with no infected part found. This can happen, if the delete action is
chosen as the result for content filtering, and the message part is deleted after
filtering.
VirusNameAction parameters. The actions performed after filtering are
specified by the FilteredMimeAction, FilteredNameAction and
FilteredSizeAction parameters.
Action-related parameters are available in the
[kav4lms:groups.<group_name>.actions] section of the group configuration
file.
5.5. Predefined security profiles
Distribution package of Kaspersky Anti-Virus includes preset configuration profiles providing for different e-mail protection levels:
recommended – stored in the default_recommended directory (see
5.5.1 on p. 54 for details);
maximum protection – stored in the high_overall_security directory
(see 5.5.2 on p. 54 for details);
maximum performance – stored in the high_scan_speed directory
(see 5.5.3 on p. 55 for details).
Each profile consists of two configuration files: kav4lms.conf and default.conf
(located in the groups.d subdirectory). Profiles are stored in the subdirectories
matching their names within the
/etc/opt/kaspersky/kav4lms/profiles directory.
You can select one of the preset profiles or configure e-mail protection settings
manually in the configuration files of the application.
To use a preset profile:
1. Create the backup copy of application‟s configuration files
(kav4lms.conf and groups.d/default.conf).
2. Copy the contents of required profile‟s directory to the
/etc/opt/kaspersky/kav4lms directory.
3. Apply the new configuration by running the following command:
/etc/init.d/kav4lms reload
Page 54

54 Kaspersky Anti-Virus 5.6 for Linux Mail Server
5.5.1.
This profile provides the optimal balance between anti-virus protection level and
scan speed. This profile has the following characteristics:
Recommended
E-mail messages are scanned using the message scan policy: each
message is scanned for viruses as a whole.
Extended anti-virus databases are used while scanning.
Maximum message nesting level allowed for MIME objects is 10.
A backup copy and information file are created for every message that
undergoes anti-virus processing.
Infected messages are cured.
Filtration of attachments by MIME type is enabled. The application re-
moves from messages links to external objects (message/external-body
type) and attachments with the .pif, .com, .bat and .exe extension.
Warnings are issued about all messages, which are suspicious, password
protected, erroneous, filtered by MIME type and attachment name. If a
specific threat is detected, the message is dropped.
The application adds to message header and body information about the
results of its processing.
The application sends notifications about message scanning to its recipi-
ents. No notifications are delivered to the sender or administrator.
All application messages except for debug information are recorded in the
report.
profile
Statistics are gathered for all aspects of the application functionality.
5.5.2.
This profile offers the most comprehensive protection of your mail traffic. This
profile includes the following functions:
Maximum protection
The application scans e-mail messages using a combined scan policy:
each message is first scanned for viruses as a whole and then each message object is scanned separately, regardless of whether infected objects
are found or not.
The application parses messages that do not comply to RFC standards
using heuristic algorithms; after successful decoding it passes them for
scanning.
profile
Page 55

Anti-virus protection of e-mail 55
Extended anti-virus databases are used while scanning.
E-mail messages are filtered by MIME type. The application filters e-mails
which have references to external objects (message/external-body) type
and deletes them. Also .pif, .com, .bat and .exe-attachments are removed.
Maximum message nesting level is unlimited.
An information file is created for every message that undergoes anti-virus
processing or filtering.
Infected objects are cured.
The application deletes all suspicious, protected and filtered objects in the
messages. Messages, containing threats from a specified list are
dropped.
If a message contains objects, which cause an error when scanned, its
content will be replaced with a notification.
The application sends notifications about message scanning to its recipi-
ents. No notifications are delivered to the sender or administrator.
All application messages except for debug information are recorded in the
report.
Statistics is not preserved.
5.5.3.
This profile provides maximum application performance, at some cost to the reliability of anti-virus protection. The profile has the following characteristics:
Maximum performance
E-mail messages are scanned using the message scan policy: each
message is scanned for viruses as a whole.
Message object filtering is disabled.
The application saves a backup copy for every message to which it ap-
plies the drop and warn actions. No information file is created.
Warnings are issued about infected, suspicious, protected and erroneous
objects of mail messages. If a threat from specified list is detected, the
message is dropped.
The application adds to message header the information about the results
of its processing.
profile
Page 56

56 Kaspersky Anti-Virus 5.6 for Linux Mail Server
The application sends notifications about message scanning to its recipi-
ents. No notifications are delivered to the sender or administrator.
The application logs in the activity report information about all aspects of
its functionality; level of details: fatal and other errors, and important informational messages.
Statistics is gathered about detected viruses.
The maximum number of client requests to the central service is doubled
in comparison to the recommended and maximum protection profiles. The
maximum number of concurrent scanning requests is unlimited.
5.6. Backup
The application supports backup copying of messages prior to their processing.
Backup settings are specified in the [kav4lms:groups.<group_name>.backup]
section of the group configuration file.
Mail backup mode is determined by Policy option, which can take the following
values:
message – only message copy is created;
info – the information file is created together with message copy. This
file contains the following information:
MTA client IP address (or host if available.);
MTA connector IP address (or host if available.);
the sender of the message, as provided from the MTA connector;
the address of processing server;
the name of the matching group under which the messages was
analyzed;
the recipients list of the message, as provided from the MTA con-
nector;
the cause of the backup action (cured, deleted, rejected, filtered
etc.);
the path to the original file, relative to backup destination;
application instance information (process id and thread id.).
none – no message backup.
Page 57

Anti-virus protection of e-mail 57
The Options parameter specifies which application activity is the backup reason:
cured – when the original message object has been cured;
deleted – when the original message object has been deleted;
rejected – when the original message has been rejected (the MTA cli-
ent receives the error code), but the administrator may decide to backup
the infected message;
dropped – when the original message has been dropped;
warning – when the original message has been replaced with a warn-
ing;
renamed – when the message has least one object (MIME part) that
had matched the filtering rules and has been renamed;
all – all above mentioned.
The Options parameter can take one of the above values or their list, delimited
by commas.
Messages‟ backup copies and information files are stored under a directory,
specified via the Destination parameter.
5.7. Notifications
Notification is an e-mail message containing a description of processed message
and sent to its recipient, sender or server administrator.
Apart from the message description, notification also contains descriptions of
objects that have been removed from the message for some reason.
The application also supports appending of the original e-mail to notification.
However, that is only possible for notifications to the recipient. For administrators
and senders the application generates new e-mail letters containing just the notification text.
5.7.1. Setting up notifications
Notifications-related application parameters are stored:
in the [kav4lms:server.notifications] section of the kav4lms.conf
configuration file of the application;
in the [kav4lms:groups.<group_name>.notifications] section of each
group‟s configuration file.
Page 58

58 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Notifications setup consists of two steps.
Step 1. Who will be notified?
Notifications can be sent to:
message sender (NotifySender parameter in the group configuration
file);
message recipients (NotifyRecipients parameter in the group configu-
ration file);
security administrators (NotifyAdmin parameter in group‟s configura-
tion). The security administrators‟ e-mail addresses list is specified via
the AdminAdresses parameter in group‟s configuration;
product administrators (defined by the ProductNotify parameter in the
kav4lms.conf file). Product administrators‟ addresses list is specified via
the ProductAdmins parameter in the kav4lms.conf file.
Message sender notifications are enabled by setting these parameters to a
value, other than none. Otherwise, notifications are disabled.
Step 2. What will be the notifications’ subject?
Message senders, recipients and security administrators can be notified about:
the InfectedAction (see 5.4 on p. 52 for details) taken (at least one ob-
ject was infected). This notification type is enabled by setting the required parameter to infected value;
the ProtectedAction (see 5.4 on p. 52 for details) taken (at least one
object was protected). This notification type is enabled by setting the
required parameter to protected value;
the ErrorAction (see 5.4 on p. 52 for details) taken (at least one object
was erroneous). This notification type is enabled by setting the required
parameter to error value;
a filtering rule matched (see 5.3.2 on p. 50 for details). This notification
type is enabled by setting the required parameter to filtered value;
all above mentioned. This notification type is enabled by setting the re-
quired parameter to all value.
Product administrators can be notified about:
a new update of anti-virus databases has been downloaded. This notifi-
cation type is enabled by setting the ProductNotify parameter to the
update value;
Page 59

Anti-virus protection of e-mail 59
a critical failure in the application (which was recoverable or not). This
notification type is enabled by setting the ProductNotify parameter to
the fault value;
licensing related notifications. This notification type is enabled by setting
the ProductNotify parameter to the license value;
all above mentioned. This notification type is enabled by setting the
ProductNotify parameter to the all value.
The license notifications is an exceptional case and cannot be excluded from the
list. These kind of notifications will always be sent, and when the notifications are
turned off, only log entries will be generated.
Licensing notifications are sent upon:
key expiration – first notification is issued on the 14 day before the expi-
ration date, then daily up to the expiration date. On the next day, the
expired key notification is issued;
license limit violation – when the number of users or amount of traffic
permitted by the key was exceeded.
5.7.2. Notification templates
The following templates can be used to create notifications (the templates are
stored in the directory defined by the Templates parameter in the application
configuration file):
Template for notifications about deleted objects – text added to the
original message if one of the message parts is deleted during anti-virus
processing or filtering. This text might contain a macro describing the
reasons for deletion. The following templates are available:
part_infected – text replacing the object that was deleted after an
unsuccessful disinfection attempt;
part_filtered – text replacing the MIME object that was deleted
based on MIME object filtration results;
part_suspicious – text replacing the object that was detected as
suspicious and deleted;
part_filtered – text that replaces an original e-mail object, renamed
as the result of filtering;
part_protected – text replacing an object that was deleted because
it was protected and therefore could not be scanned for viruses;
Page 60

60 Kaspersky Anti-Virus 5.6 for Linux Mail Server
part_error – text replacing the object that generated a scan error
and was therefore deleted.
Standard notification template – text of the notification that is sent to
the sender, recipient, and administrator using the filter or a newly generated message sent by the SMTP component. This text might contain
a macro describing the reasons for deletion. The following templates
are available:
notify_common – text sent by default to the recipient, sender, and
administrators about the actions applied to the message;
notify_infected – text that replaces the infected message;
notify_suspicious – text that replaces the message containing sus-
picious objects;
notify_filtered – text that replaces the filtered e-mail message;
notify_error – text that replaces a message that generated a scan
error;
notify_protected – text that replaces a message that was protected
from scanning;
disclaimer – text, added to all processed and generated messages.
By default this template includes the following notification: "This
message has been scanned by Kaspersky Anti-Virus. For more in-
formation about data security please visit
http://www.kaspersky.com and http://www.viruslist.com".
Detailed notification template – text notifying a person interested in
knowing more about the anti-virus processing of an e-mail message.
There are separate templates for notifications sent to the recipient,
sender and administrator. Set the UseCustomTemplates parameter to
yes in order to use these templates. The following templates are available:
sender‟s notifications:
o notify_ sender_common – text of the notification sent to the
sender about actions applied to the original message;
o notify_sender_infected – text that replaces the infected mes-
sage;
o notify_sender_suspicious – text that replaces the message
containing suspicious objects;
o notify_sender_filtered – text that replaces the filtered e-mail
message;
Page 61

Anti-virus protection of e-mail 61
o notify_sender_error – text that replaces a message that gener-
ated a scan error;
o notify_sender_protected – text that replaces a message that
was protected from scanning;
recipients‟ notifications:
o notify_recipients_common – text of the notification sent to the
recipient about actions applied to the original message;
o notify_recipients_infected – text that replaces the infected
message;
o notify_recipients_suspicious – text that replaces the message
containing suspicious objects;
o notify_recipients_filtered – text that replaces the filtered e-mail
message;
o notify_recipients_error – text that replaces a message that
generated a scan error;
o notify_recipients_protected – text that replaces a message that
was protected from scanning;
administrator‟s notifications:
o notify_admin_common – text of the notification sent to the ad-
ministrator about actions applied to the original message;
o notify_admin_infected – text that replaces the infected mes-
sage;
o notify_admin_suspicious – text that replaces the message con-
taining suspicious objects;
o notify_admin_filtered – text that replaces the filtered e-mail
message;
o notify_admin_error – text that replaces a message that gener-
ated a scan error;
o notify_admin_protected – text that replaces a message that
was protected from scanning.
Special administrator notification template – text added to special
notifications sent upon critical events that require administrator‟s special
attention. Administrator templates are stored in a directory, specified by
the Templates parameter in the [kav4lms:server.notifications] section of the application configuration file. The following templates are
available:
Page 62

62 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Warning!
When the application is started, the presence of all the above templates is verified. If even one of these templates is missing, the application will return an
error.
The application also verifies that the size of each template does not
exceed 8 KB.
Warning!
The first line of any template must not contain ':' as it will be interpreted as
header. You can start with a line feed (press Enter) to be sure it will not be misinterpreted as notification header.
product_update – the text used to notify the administrator about re-
ceipt of updates to the anti-virus databases for the application;
product_fault – text notifying the administrator that a critical error
has occurred while Kaspersky Anti-Virus was running;
product_license – text notifying the administrator about license
agreement violation or end of licensing period.
5.7.3. Customizing notification templates
Kaspersky Anti-Virus gives users the flexibility to customize the default notification templates that will be sent to administrators, senders, and recipients. The
templates are customized using a special notification language.
The template language is a set of control statements and macros.
Below, we consider the rules of this language, its syntax and examples of use in
detail.
5.7.3.1. Macros
A macro is a substitution element used in e-mail notification templates. In a notification text created using a template, the macro is replaced with a certain value.
The syntax for macros is %macro_name%.
If a macro name contains „%‟, it should be escaped (see section 5.7.3.5 on
page 66).
Several values can be assigned to a macro. In this case, the simple input of
"%macro_name%" will output the last assigned value.
Page 63

Anti-virus protection of e-mail 63
To assign several values to one macro, use iterative statements.
5.7.3.2. Iteration constructs
An iteration construct (IC) is the main element of the template language.
The syntax for an iteration construct is
<FOR INAME IOP IVALUE>BODY</FOR>
where:
<FOR – the beginning of IC definition. The < symbol that is not the begin-
ning of an IC definition should be screened (see section 5.7.3.5 on
page 66).
INAME – IC name in the format 1*(nchar)*(nchar); the maximum length is
64 bytes.
IOP – comparison operation in the format == | !=; the maximum length is 2
bytes.
IVALUE – value of IC in the format 1*(vchar)*(vchar); the maximum length
is 4096 bytes. IC values only work in double quotes. When comparing
with a value that contains a quotation mark, use the relevant screening
escape symbol (see section 5.7.3.5 on page 66). Example:
<FOR _macro_name_parent_ == "\"_value_1\"">
> – end of IC definition and the beginning of iterator body. The < symbol that
is not the end of IC definition must be hidden (see section 5.7.3.5 on
page 66).
BODY – iterator body in the format *(char).
</FOR> – end of the iterator body definition. The < symbol that is not the
end symbol of the iterator body definition must be screened (see section 5.7.3.5 on page 66).
… – separator in the format *( )*(\t)
nchar – characters from set a-z, A-Z, 0-9, -, _
vchar –symbols from set nchar, *, ?
char – – symbols from the set of values 32 – 255
Example of an iteration construct:
<FOR _macro_name_ == "*">%_macro_name_%</FOR>
When executing this construct, the parser transforms the above command into
the condition constructs:
<FOR _macro_name_ == "_value_1">%_macro_name_%</FOR>
Page 64

64 Kaspersky Anti-Virus 5.6 for Linux Mail Server
<FOR _macro_name_ == "_value_2">%_macro_name_%</FOR>
<FOR _macro_name_ == "_value_3">%_macro_name_%</FOR>
<FOR _macro_name_ == "_value_N">%_macro_name_%</FOR>
These condition constructs are parsed sequentially.
Thus, iteration constructs are used to distinguish both the single and multiple
values of a macro.
For example, if the macro %FILTERNAME% has the values of KAVFilter1,
KAVFilter2, KAVFilter3, and SimpleFilter, then
the construct:
<FOR FILTERNAME == "KAVFilter1">%FILTERNAME%</FOR>
will produce the text:
KAVFilter1
the construct:
<FOR FILTERNAME == "KAVFilter?">%FILTERNAME%, </FOR>
will produce the text:
KAVFilter1, KAVFilter2, KAVFilter3
the construct:
<FOR FILTERNAME != "KAVFilter2">%FILTERNAME%, </FOR>
will produce the text:
KAVFilter1, KAVFilter3, SimpleFilter
the construct:
<FOR FILTERNAME != "KAV*">%FILTERNAME%, </FOR>
will produce the text:
SimpleFilter
Page 65

Anti-virus protection of e-mail 65
5.7.3.3. Scope of visibility for an iterative
statement
Any iteration construct can have sub-macros, which values are defined within the
scope of visibility for the parent construct only. Iterative statements can be used
not only to output particular values of particular macros, but also to define the
scope of visibility of sub-macros.
The scope of visibility of a sub-macro is defined by the start and end tags of the
condition construct:
<FOR _macro_name_parent_ ==
"_value_1">%_macro_name_child_%</FOR>
In the above example, the scope of the macro %_macro_name_parent_% includes all sublevels (between the FOR tags) if the macro value is overridden.
5.7.3.4. Variables
Variables provide better flexibility in customizing templates using the Template
language.
A variable can be defined within the specified scope of flexibility as follows:
<DEF _var_name_ = "_const_value_"/>
This variable can be used further as a usual macro without any limitations.
The syntax for a variable definition statement is as follows:
<DEF VNAME VOP VVALUE/>
where:
<DEF – beginning of variable definition statement. The < symbol that is not
the beginning of the statement must be screened (see section 5.7.3.5
on page 66);
VNAME – variable name in the format 1*(nchar)*(nchar); the maximum
length is 64 bytes;
VOP – assignment operation in the format =, the length is 1 byte;
VVALUE – variable value in the format 1*(vchar)*(vchar); the maximum
length is 4096 bytes. The value only works in double quotes. If compared with a value that has a quote mark inside, use the screening escape symbol (see section 5.7.3.5 on page 66). Example:
<DEF _value_name_ = "\"_value_1\""/>
Page 66

66 Kaspersky Anti-Virus 5.6 for Linux Mail Server
%
marks a macro. The macro should be between two symbols "%".
Example: %VIRUSNAME%
<
opening bracket of a tag.
Example: <FOR FILTERNAME == "KAVFilter1">
>
closing bracket of a tag.
Example: <FOR FILTERNAME == "KAVFilter1">
</
opening bracket of an end tag.
Example: </FOR>
> – end of the variable definition statement. The > symbol that is not the end
of the variable definition must be screened (see section 5.7.3.5 on
page 66). Unlike the FOR statement, the DEF statement has no body.
Therefore, the tag end bracket should notify the parser that the end tag
is missing.
… – separator in the format *( )*(\t)
nchar – symbols from set a-z, A-Z, 0-9, -, _
vchar – symbols from set nchar, *, ?
If a variable is redefined in its scope, a new value will be substituted after each
redefinition. Thus, the statement:
<DEF __NAME__= "NAME_1"/>Now you will see the first
value: %__NAME__%.
<DEF __NAME__= " NAME _2"/>Now you will see the second value: %__NAME__%.
will be output as:
Now you will see the first value: NAME_1.
Now you will see the second value: NAME_2.
A variable can have a macro as its value.
<DEF _var_name_ = "%_macro_name_%"/>
In this case, the parser will first substitute the macro for a value and then it will
replace the variable with this value in the current scope.
5.7.3.5. Language syntax
Special symbols
Page 67

Anti-virus protection of e-mail 67
/>
closing bracket of the end tag for a construct without a body.
Example: <DEF __NAME __= "NAME_1"/>
\
escape symbol. Instructs the parser to treat the following special
character as a plain one. Example: \%VIRUSNAME\%
==
equal sign: a coincidence in mask or value.
Example: <FOR FILTERNAME == "KAVFilter1">
Example: <FOR FILTERNAME == "KAVFilter*">
!=
unequal sign: a non-coincidence in mask or value.
Example: <FOR FILTERNAME != "KAVFilter1">
Example: <FOR FILTERNAME != "KAVFilter*">
*
Unlimited length of all possible values. It is used only inside tags in
comparison with templates.
Example: <FOR FILTERNAME == "KAV*">
?
All possible one-character values. It is used only inside tags in com-
parison with templates.
Example: <FOR FILTERNAME == "KAVFilter?">
#
Comment; the parser ignores all characters after „#‟ till the end of
line.
FOR
Iteration construct definition.
Example: <FOR FILTERNAME = "KAVFilter1">
DEF
Variable definition (statement without an end tag). Example: <DEF
__NAME__= "NAME_1"/>
%CRLF%
Line feed macro (CR+LF)
%TAB%
Tab macro
Reserved keywords
Predefined macros
The processing is performed within a global section (no statement is needed) or
within a condition construct:
<FOR KAV_LANGUAGE == "5.0"> ... </FOR>
Page 68

68 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Note:
The template language is case sensitive. The number of spaces or tab symbols
(either their presence or absence) between the language constructs is not regulated. Reserved keywords must be separated either by white space characters or
by the special symbols.
Escape sequences
The following sequences can be used to present special characters in the template language:
To output the „\‟ symbol in the template text, enter „\\‟.
If a line is ended with „\‟, it will be interpreted as a string continued on
the following line. Additionally, an escape symbol at the end of the line
screens the following EOL which otherwise would exist in the generated
message. Such a line is concatenated with the following one during
processing before any other actions performed by the parser. This
situation is handled independently by either the escape sequence being
met inside a tag or outside a tag. See item 1 above if you want to place
a „\‟ at the end of line.
To output the „%‟ symbol into the template text, use „\%‟.
To output the „/‟ symbol into the template text, use „\/‟.
To output the „<‟ symbol into the template text, use „\<‟.
To output the „>‟ symbol into the template text, use „\>‟.
To output the „#‟ symbol into the template text, use: „\#‟.
5.7.3.6. Notification macros for the application
Macros can be used in notification templates for either entire messages or their
parts. Using macros, you can customize notifications to include additional information on the properties of an original message or object or about actions applied to them.
The administrator can use the following macro in notifications concerning entire
messages:
%VERSION% – version number of the installed Kaspersky Anti-Virus in-
stance used to scan the message.
%PRODUCT% – complete product name of Kaspersky Anti-Virus.
%CLIENT% – remote IP address of the mail client.
Page 69

Anti-virus protection of e-mail 69
%SERVER% – server‟s name of the server running the central service of the
application.
%SENDER% – sender address.
%RECIPIENTS% – recipient address.
%HEADERS% – message header.
%MSGID% – message identification number.
%SUBJECT% – subject (the Subject field) of the original message.
%DATE% – date when message was processed.
%TIME% – time when message was processed.
%BK_ACTION% – actions applied to the message that caused a backup
copy to be created (if the application is configured to back up messages).
%BK_LOCATION% – full path to the backup storage (if the storage exists).
%ACTION_LIST% – list containing information about the message and its
object and a list of actions applied to them. The information is output in
the following format:
<status> <action> <information>
for each processed part of the message.
In notifications related to objects deleted from a message, the following macros
can be used:
%INFO% – information related to the following actions performed:
list of detected viruses (malicious software) – for infected ob-
jects;
error code description – for objects that generated a scan error;
MIME type or attachment name – for filtered objects.
The macros must be specified in the text of notification templates.
Page 70

Note:
All settings of the kav4lms-kavscanner component are grouped in the [scan-
ner.*] options of the application's configuration file.
Warning!
By default, only the root and kluser users can launch an on-demand scan.
Warning!
An anti-virus scan of the entire computer is a process that requires considerable
resources. It should be noted that when you start this task, your computer's efficiency will be reduced: therefore we recommend that no other heavy application
should run at the same time. To avoid such problems, we recommend that you
scan individual selected catalogs.
CHAPTER 6. ANTI-VIRUS
PROTECTION OF FILE
SYSTEMS
The kav4lms-kavscanner component provides anti-virus protection of the computer's file systems, by scanning files and processing infected and suspicious
objects according to its settings.
You can scan the entire file system, an individual directory or a single file. All
protection settings may be divided into groups that define:
Scan scope (see 6.1 on p. 71).
How objects are to be scanned and disinfected (see 6.2 on p. 72).
Actions to be performed on objects (see 6.3 on p. 72).
The scan of your computer's file systems may be started:
As a one-time task - from the command line (see 6.4 on p. 74).
According to the schedule using the cron application (see 6.5 on p. 74).
Page 71

Anti-virus protection of file systems 71
Note:
To scan all file systems of the computer, you have to switch to the root directory,
or specify the scan scope at the command line as “/”.
Warning!
If you specified at the command line both scan paths and a text file containing a list of the scan objects, only the paths indicated in the file will
be scanned. The paths entered at the command line will be ignored.
The path to the object for scanning may not exceed 4096 bytes. Objects located
on longer paths will not be scanned.
6.1. Scan scope
The scan scope can be roughly divided into two parts:
scan path – the list of directories and objects to be searched for viruses;
scan objects – types of objects to be scanned for the presence of vi-
ruses (archives, etc.).
By default all objects of all available file systems are scanned, starting with the
current directory.
You can redefine the scan path by the following methods:
Listing at the command line (using a space as a separator) all directories
and files to be scanned, using absolute or relative (relative to the current
directory) paths.
List the scan paths in a text file, and specify this file to be used by using
the parameter -@<filename> in the command line. Each object in this file
should be entered on a new line, using its absolute path only.
Turn off the recursive scan of the catalogs ([scanner.options] section,
the Recursion setting or command line parameter -r).
Create an alternative configuration file and specify this file to be used us-
ing the command line parameter -c <filename> at component startup.
The default scan objects are specified in the kav4lms.conf configuration file
([scanner.options] section) and they can be redefined:
directly in this file;
using command line parameters at component startup;
Page 72

72 Kaspersky Anti-Virus 5.6 for Linux Mail Server
by using an alternative configuration file.
6.2. Object scan and disinfection
mode
The settings of this mode are very important, because they determine whether
the application will cure infected files when they are detected.
By default, disinfection is turned off: the default behavior is to scan objects and to
notify about detected viruses and other suspicious or corrupted files by printing
messages to the screen and in the report.
As a result of an anti-virus scan, each object will be assigned a status from those
listed below:
Clean – no viruses detected (the object is not infected).
Infected – the object is infected.
Warning – object code resembles the code of a known virus.
Suspicious – the object is suspected of being infected with an un-
known virus (not assigned if the UseCodeAnalyzer=no).
Corrupted – the object is corrupted.
Protected – the object cannot be scanned because it is encrypted
(password-protected).
Error – an error has occurred while scanning the object.
With the disinfection mode turned on (section [scanner.options], setting Cure=
yes) only objects with the Infected status will be sent for disinfection. As a result
of the disinfection, the object will be assigned a status from those listed below:
Cured – the object has been successfully disinfected.
CureFailed – the object could not be disinfected. Files with this status
will be processed according to rules specified for infected objects.
6.3. Actions to be performed on
objects
The actions to be performed on an object depend on the object's status. The
default action is only to provide notification about the detection of infected or
Page 73

Anti-virus protection of file systems 73
Warning!
Actions performed with self-extracting archives can be differentiated: if the archive itself is infected, it will be viewed as a simple object, while if objects within
the archive are infected, the archive will be viewed as a container. Therefore
actions to be performed on archives, depending on the case, will be determined
by the settings specified in different sections of the configuration file.
Note:
If no configuration file is specified in the command line at the component
startup, the operating settings will be taken from the kav4lms.conf file.
The use of this file at startup does not have to be specified.
suspicious objects. However, for objects with Infected, Suspicious, Warning,
Error, Protected and Corrupted status you can configure further responses,
including:
moving to a directory – moving objects with the given status to a direc-
tory (simple and recursive moving is supported);
deleting object from the file system;
performing a command – processing of files using standard Unix script
files, or similar.
Please note that Kaspersky Anti-Virus discriminates between simple objects
(files) and container objects (consisting of several objects, for example, an
archive). Actions performed with such objects are also discriminated; in the
configuration files these actions are located in different sections, with section
[scanner.object] for simple objects, and section [scanner.container] for
container objects.
You can select actions to be performed on an object using several methods as
follows:
You can specify them in the kav4lms.conf configuration file if you plan to
use these actions as default actions (sections [scanner.object] and
[scanner.container]).
Specify actions in the alternative configuration file and use this file at
component startup.
You can specify them for the current work session using command line
parameters when starting the kav4lms-kavscanner component.
Actions for both simple and container objects use the same syntax (sections
[scanner.object] and [scanner.container]).
Page 74

74 Kaspersky Anti-Virus 5.6 for Linux Mail Server
6.4. On-demand scan of an individual
directory
One of the commonest tasks implemented by Kaspersky Anti-Virus is the antivirus scan and disinfection of an individual directory.
Perform the anti-virus scan with the following conditions:
1. Start an anti-virus scan of the /tmp directory with automatic disinfection
of all infected objects detected. Delete all objects that cannot be disinfected.
2. Create the files infected.lst, suspicion.lst, corrupted.lst and warn-
ing.lst to record the filenames of all infected, suspicious and corrupted
objects detected during the scan.
3. The results of the component operation (starting date, information about
all files, except clean files) will be printed in the report file kavscannercurrent_date-pid.log that will be created in the current directory.
To implement this task, enter at the command line:
# /opt/kaspersky/kav4lms/bin/kav4lms-kavscanner -\
rlq -pi/tmp/infected.lst -ps/tmp/suspicion.lst -\
pc/tmp/corrupted.lst -pw/tmp/warning.lst -o /tmp/ \
kav4lms-kavscanner-`date "+%Y-%m-%d-$$"`.log -i3 \
6.5. Scheduled scan
Kaspersky Anti-Virus tasks can be scheduled to run using the cron application.
Run an anti-virus scan of the /home directory every day at 0:00, using the scan
settings specified in the configuration file /etc/kav/scanhome.conf. To perform
this task, do the following:
1. Create the configuration file /etc/kav/scanhome.conf and specify the re-
quired scan settings in this file.
2. Edit file that defines the rules for the operation of the cron (crontab -e)
process by entering the following line:
0 0 * * * /opt/kaspersky/kav4lms/bin/kav4lms-\
kavscanner -c /etc/kav/scanhome.conf /home
Page 75

Anti-virus protection of file systems 75
Warning!
The example is for Linux!
Warning!
Before launching the example, make sure that the mail utility is located at this
utility‟s standard installation path in the operating system.
6.6. Sending notifications to the
administrator
Using standard Unix tools, you can specify that notifications are sent to the administrator upon detection of infected, suspicious or corrupted objects in the
computer's file systems.
Configure administrator notification when infected files and archives are detected
during file systems scans performed using the settings specified in the
kav4lms.conf configuration file.
To perform this task, do the following:
Enter these rules for processing simple objects and container objects in
the configuration file kav4lms.conf:
[scanner.object]
OnInfected=exec echo %FULLPATH%/%FILENAME% is \
infected by %VIRUSNAME% |
mail -s kav4lms-kavscanner admin@localhost
[scanner.container]
OnInfected=exec echo archive %FULLPATH%/%FILENAME% \
is infected, viruses list is in the attached file \
%LIST% | mail -s kav4lms-kavscanner -a %LIST% \
admin@localhost
Page 76

Note:
Updates to the anti-virus database are uploaded to Kaspersky Lab's updates
servers on an hourly basis.
Note:
All settings of the kav4lms-keepup2date component are grouped in the [up-
dater.*] section of the configuration file.
CHAPTER 7. UPDATING THE
ANTI-VIRUS DATABASES
Updating the anti-virus database is performed by the kav4lms-keepup2date
component, and is an integral factor in full-fledged anti-virus protection. The default source used for updating the anti-virus database is Kaspersky Lab‟s up-
dates servers. The list of these servers includes:
http://downloads1.kaspersky-labs.com/
http://downloads2.kaspersky-labs.com/
ftp://downloads1.kaspersky-labs.com/, etc.
The list of URL‟s from which you can download the updates is contained in the
updcfg.xml file, included in the application‟s distribution kit. To view the list of
update servers, enter the following in the command line:
# /opt/kaspersky/kav4lms/bin/kav4lms-keepup2date -s
During the update process, the kav4lms-keepup2date component selects the first
address from this list and attempts to download the anti-virus database from the
server. The current computer location (as the two-lettered code of the country
according to the ISO 3166-1 standard) can be specified via the RegionSettings
parameter in the [updater.options] section of the application configuration file.
In this case the kav4lms-keepup2date component starts choosing the update
servers, marked as belonging to the specified region. If the update cannot be
performed from the address selected, the component switches to the next URL
and makes another attempt.
After a successful update, a command, specified by the PostUpdateCmd parameter of the configuration file‟s [updater.options] section, is executed. By
default, this command automatically reloads the anti-virus database. If an invalid
change is made to this setting, the application may fail to use the updated database or will function improperly.
Page 77

Updating the anti-virus databases 77
If the structure of your local area network is complex, you are advised to
download updates to the anti-virus database from the updates servers every
hour, place them in a network directory, and configure local computers throughout the network to use this directory as their update source. For details on the
creation of a network directory, see 7.3 on p. 79.
The update may be scheduled using the cron utility (see 7.1 on p. 77) or it may
be performed on-demand by the administrator who can run this task manually
from the command line (see 7.2 on p. 78).
7.1. Automatically updating the anti-
virus database
You can schedule regular automatic updates of the anti-virus database by modifying the configuration file.
Configure automatic anti-virus database updates to be performed every hour.
Only record application errors in the system log. Maintain the general log for all
tasks started, and do not print any information to the screen. To perform this
task, do the following:
1. Specify these values in the application's configuration file, for example:
[updater.options]
KeepSilent=yes
[updater.report]
Append=yes
ReportLevel=1
2. Edit the configuration file for the cron (crontab -e) process by entering the
following line:
0 0-23/1 * * * /opt/kaspersky/kav4lms/bin/kav4lms-\
keepup2date -e
Configure the kav4lms-keepup2date component to select the URL of the updates
server automatically from the list, provided with the application. To perform this
task, do the following:
Assign the value No to the UseUpdateServerUrl setting in the
[updater.options] section of the application‟s configuration file.
Page 78

78 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Configure the keepup2date component to download updates from the URL
specified by the administrator. If the download cannot be performed from this
URL, abort the downloading process. To perform this task, do the following:
Assign the value Yes to both the UseUpdateServerUrl and
UseUpdateServerUrlOnly settings of the [updater.options] value.
Additionally, the UpdateServerUrl setting must contain the URL of the
updates server.
Configure the keepup2date component to download updates from a specified
URL. If the download cannot be performed from this URL, update the anti-virus
database from the URLs specified in the list included in the keepup2date component. To perform this task, do the following:
Assign the value Yes to the UseUpdateServerUrl setting of the
[updater.options] section, and the value No to the
UseUpdateServerUrlOnly setting. Additionally, the UpdateServerUrl
setting must contain the URL of the updates server.
7.2. On-demand updating of the anti-
virus database
You can start the update of the anti-virus database from the command line at any
time. To do that, type the following command:
# /opt/kaspersky/kav4lms/bin/kav4lms-keepup2date
Start the update of the anti-virus database and record the results in the file
/tmp/updatesreport.log. To implement this task enter at the command line:
# /opt/kaspersky/kav4lms/bin/kav4lms-keepup2date -l \
/tmp/updatesreport.log
The most convenient way to update the anti-virus database on several computers is to download the updates once from the updates servers, place the updates in a network directory and then direct the computers to treat this directory
as their update source.
Arrange updating of the anti-virus database from the network directory
ftp://10.10.10.1/home/bases and only if this directory is not accessible or empty,
update the database from Kaspersky Lab's updates servers. Print the results in
the report.txt report file.
To perform this task, do the following:
1. Specify the corresponding values for the settings in the application's configuration file:
[updater.options]
Page 79

Updating the anti-virus databases 79
UpdateServerUrl=ftp://10.10.10.1/home/bases
UseUpdateServerUrl=yes
UseUpdateServerUrlOnly=no
2. Enter at the command line:
# /opt/kaspersky/kav4lms/bin/kav4lms-keepup2date -l \
/tmp/report.txt
7.3. Creating a network directory to
store the updates
To ensure that the anti-virus database is correctly updated from the network directory, the directory must contain the same file structure as Kaspersky Lab's
updates servers. Provided below is a detailed discussion of this task.
Create a network directory from which anti-virus database updates can be copied
to local computers within the network. To perform this task, do the following:
1. Create a local directory.
2. Start the kav4lms-keepup2date component as follows:
# /opt/kaspersky/kav4lms/bin/kav4lms-keepup2date -u
<dir>
where <dir> is the full path to the local directory.
3. Grant local computers read-only network access to this catalog.
Configure the anti-virus database update to be performed via a proxy server. To
perform this task, do the following:
1. Assign the value Yes to the UseProxy setting of the [updater.options]
section.
2. Make sure that the ProxyAddress setting in the [updater.options]
section of the configuration file contains the URL of the proxy server.
The address must be specified in the format
http://username:password@ip_address:port. The values ip address
and port are mandatory, while username and password are necessary
only if the proxy server requires authorization.
or:
1. Assign value Yes to the UseProxy setting of the [updater.options]
section.
Page 80

80 Kaspersky Anti-Virus 5.6 for Linux Mail Server
2. Specify the environment variable http_proxy using format
http://username:password@ip_address:port. Note that the
environment variable will be considered only if the UseProxy setting of
the [updater.options] section is missing or is assigned value Yes.
Page 81

CHAPTER 8. KEY
MANAGEMENT
The key file gives you the right to use the application, and contains all required
information pertaining to the license that you have purchased, including the licensing scheme, the key expiration date, and details of the dealer.
In addition to the right to use the application, during the key‟s active period you
obtain:
24/7 technical support;
new updates of the anti-virus database on an hourly basis;
application updates (patches);
receiving new versions of the application (upgrades);
up-to-date information about new viruses.
Upon the expiration of the key you automatically lose the right to receive the
above services. Kaspersky Anti-Virus will continue performing anti-virus processing, but it will use the anti-virus database that was up-to-date on the key expiration date. The anti-virus database updating function will not be available. If the
anti-virus database is updated manually, its release date may be newer than the
key expiration date. In this case, the application will lose its anti-virus functionality and the corresponding note is logged.
Therefore, it is extremely important to regularly review report files that contain the
key details, and to keep track of the key expiration date.
The application supports several licensing schemes:
by traffic.
This licensing scheme offers protection for the amount of daily traffic,
specified in the key. Only the processed traffic, found clean or
notchecked, is taken into account. If the daily traffic exceeds the license limit, the administrator‟s notification is issued for the first and
subsequent messages, exceeding the license limit.
by addresses.
This licensing scheme offers protection for a certain number of mail
addresses. This applies to list of domains, specified via the
LicensedUsersDomains parameter in the [kav4lms:server.settings]
Page 82

82 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Warning!
Regular expressions are case insensitive.
section of the kav4lms.conf file, and to addresses on the server, where
the application is running.
The licensed domain names can be specified:
o as-is string
o by wildcard expression (UNIX syntax)
o by regular expression (POSIX syntax).
If number of mail addresses within a domain exceeds license limit, the
administrator will be prompted to purchase a key for the amount of extra
traffic.
8.1. Viewing key details
Apart from this, Kaspersky Anti-Virus provides a special kav4lms-
licensemanager component that allows you to view not only the full information
about the keys, but also receive some analytical data.
All information will be printed to the screen.
To view information about all keys, enter at the command line:
# /opt/kaspersky/kav4lms/bin/kav4lms-licensemanager -s
Information similar to the following will be printed to the screen:
Kaspersky license manager for Linux. Version
5.6/RELEASE #68
Copyright (C) Kaspersky Lab, 1997-2007.
Portions Copyright (C) Lan Crypto
License info:
Product name: Kaspersky Anti-Virus BO for SendMail /
Qmail / Postfix Milter API International Edition. 1014 MailAddress 1 month Beta Licence
Expiration date: 01-09-2007, expires in 28 days
Active key info:
Key file: 00BEA0DB.key
Install date: 02-08-2007
Page 83

Key management 83
Product name: Kaspersky Anti-Virus BO for SendMail
/ Qmail / Postfix Milter API International Edition.
10-14 MailAddress 1 month Beta Licence
Creation date: 02-02-2007
Expiration date: 03-03-2008
Serial: 0038-000413-00BEA0DB
Type: Beta
Count: 10
Lifespan: 30
Objs: 7:10
The Objs parameter represents the licensing object. Its value consists
of <type_of_objects>:<number_of_objects> parts. The
<type_of_objects> part can have the following values:
o 3 – represents the daily traffic;
o 7 – represents the mail addresses.
The <number_of_objects> part has the same value, as Count parameter.
To view information about a specific key, enter at the command line:
# /opt/kaspersky/kav4lms/bin/kav4lms-licensemanager\
-k <key filename>
where <key filename> is the name of the key file, for instance,
0003D3EA.key.
The following information will be printed to the screen:
Kaspersky license manager for Linux. Version
5.6/RELEASE #68
Copyright (C) Kaspersky Lab, 1997-2007.
Portions Copyright (C) Lan Crypto
Product name: Kaspersky Anti-Virus BO for SendMail
/ Qmail / Postfix Milter API International Edition.
10-14 MailAddress 1 month Beta Licence
Creation date: 02-02-2007
Expiration date: 03-03-2008
Serial: 0038-000413-00BEA0DB
Type: Beta
Count: 10
Lifespan: 30
Objs: 7:10
Page 84

84 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Note:
Kaspersky Lab Ltd. periodically announces campaigns that give you considerable discounts when you renew your license for our products. To keep informed
about our offers, visit Kaspersky Lab's corporate website and go to Products
Sales and special offers.
8.2. Renewing your key
Renewal of your key grants you the right for to restore the application‟s full functionality: that is, to update the anti-virus database, and resume the additional
services listed in 1.3 on p. 10.
The key period depends on the type of licensing that you selected when you purchased the application.
To renew your key:
Contact the dealer you purchased the application from, and renew your license for the use of Kaspersky Anti-Virus.
or:
Renew your key directly at Kaspersky Labs, by sending a request directly to
our Sales Department (sales@kaspersky.com), or filling out a form at our
website (http://www.kaspersky.com), section eStore -> Renewal. Upon receipt of your payment, we will send a new key to the e-mail address specified in your order.
You must install the key that you purchased.
To install your new key, enter at the command line:
# /opt/kaspersky/kav4lms/bin/kav4lms-licensemanager\
-a <key filename>
After this we recommend that you update your anti-virus database (see
Chapter 7 on p. 76).
To remove a key, enter at the command line:
# /opt/kaspersky/kav4lms/bin/kav4lms-licensemanager\
-da
to remove active key,
or
# /opt/kaspersky/kav4lms/bin/kav4lms-licensemanager\
-dr
to remove the additional key.
Page 85

Note:
The application supports logging for both its components: the server and the
filter. Logging options are stored correspondingly in the [kav4lms:server.log]
and [kav4lms:filter.log] sections of the kav4lms.conf file.
Warning!
Do not use the same file as the log destination for server and filter – only one
process can use the log file at once.
CHAPTER 9. REPORTING AND
STATISTICS
9.1. Application logging
Application components‟ work results are stored in either system log or a log file.
The destination is specified via the Destination parameter. The syntax for destination is:
syslog:<name>@<facility> - log as application <name>, to cate-
gory <facility>
file:<log_file_path> - messages are logged to specified file.
The type and thoroughness of logged information is specified via the Options
parameter. The Options parameter value is the list of logging options. Logging
option consists of two parts, delimited by dot:
1. Logging module. This part represents the functionality module of the
application, whose work is being logged. Possible values are:
all - includes all groups;
config - messages related to configuration;
app - events from the business logic of the product;
scan - scan status, actions;
cfilter - content filtering status, actions;
backup - backup related message;
notif - messages from notifications system;
Page 86

86 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Level symbol
Level name
Description
0, F
fatal
Information about critical errors only.
For example, the component is infected, or an error occurred during
verification, or loading of the database
or the keys. Critical errors information
is marked with „F‟ symbol in the log
file.
1, E
error
Information about other errors including those that cause the component to
close: for example, object scan error
information. Non-critical errors are
marked with „E‟ symbol in the log file.
2, W
warning
Information about errors that may
cause the application to close: for example, information about insufficient
free disk space or key expiration. Such
messages are marked with „W‟ symbol
in the log file.
3, I
info
Important informational messages: for
example, information stating whether
the component is running, the path to
the configuration file, scan scope, information about the anti-virus database, about keys, and statistical info
about the results. Informational messages are marked with „I‟ symbol in the
log file.
4, A
activity
Messages about current application
activity (for example, the name of the
object being scanned). Such messages are marked with „A‟ symbol in
the log file.
admin - events related to administrative features (for instance,
SNMP, commands);
smtp - SMTP dialog information between MTA and application.
2. Report level. This part represents the importance of the logged information. It can be specified by name, or by a letter or number. See the table
for available options and descriptions.
Page 87

Reporting and statistics 87
Level symbol
Level name
Description
9, D
debug
Debug messages. Such messages are
marked with „D‟ symbol in the log file.
Warning!
Report levels do not contain the previous (lower) levels. In order to select several
levels, all these levels must be listed or non-desired levels must be excluded.
Note:
The options of application statistics collection are located in the
[kav4lms:server.statistics] section of the main configuration file.
Logging options can be specified in the following manners:
a combination of group and level (for instance, scan.info);
level-group combination, prefixed with '-' will determine the exclusion of
the specified option.
Example:
[kav4lms:server.log]
Options = backup.all, config.error, scan.all, -scan.debug
Options = backup.all, config.E, scan.all, -scan.9
This will enable all backup messages, all error messages from config and all
scan messages, except debug. The second example is identical to the first one
and shows usage of level selection options.
Log files can grow very quickly, but their size can be limited by enabling the logs
rotation. This feature is enabled by setting the RotateSize and RotateRounds
parameters to non-zero values.
If logs rotation is enabled, then the log file grows until its size reaches Rotate-
Size. Then it is renamed to have „.1‟ suffix. If file with this suffix already exists,
then files with suffixes „.2‟, „.3‟, etc. are created, until their number (suffix)
reaches RotateRounds value. When this value is reached, file with „.1‟ suffix will
be used again.
9.2. Application statistics
Page 88

88 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Statistics category
Options value
Information stored
Messages
messages
Number of incoming messages,
number of scanned messages,
number of protected messages,
number of infected messages,
number of erroneous (corrupted)
messages, average of all message
sizes (in bytes), average time spent
on checking one message (in milliseconds)
System resources
resources
The time in seconds since last request for statistics was made, total
traffic size (in kilobytes), total CPU
usage by user, total CPU usage by
system
Detected threats
viruses
Latest 10 viruses detected, first 10
IP addresses that sent most viruses
Content filtering
filters
Number of MIME-filtered messages, number of messages filtered
by attachment, number of messages filtered by size, number of
messages filtered by virus name
All
all
All above mentioned
Per message statistics
raw
Comprehensive per message statistics
No statistics
none
No statistics are gathered
While the application is running, statistics of two types is collected:
General statistics gathered from time to time and reflecting overall ap-
plication activity.
Detailed statistics gathered on each processed message.
The type of statistics stored is specified via the Options parameter. The list of
available values is given in the table below.
The Options parameter‟s value is the list of the mentioned values, delimited by
commas.
Page 89

Reporting and statistics 89
Warning!
Setting the Options parameter to all does not enable raw statistics! This statistics type must be specified explicitly.
Examples:
Options = all
Will collect only the aggregate ones (messages, resources, viruses, filters)
Options = all, raw
Will also collect per message statistics.
Options = none, raw
Will collect only per-message data, no aggregates.
In order to enable statistics collecting, set the Options parameter to value, other
than none.
Sample record from the raw statistics file:
1210247100 1208 from@exmaple.com
rcpt@example.com infected EICAR-Test-File 127.0.0.1
1Ju4YW-000Du9-0U Default
where:
1210247100 – time when a message was processed (in UNIX format);
1208 – message size;
from@example.com – message sender‟s address;
rcpt@example.com – message recipient‟s address;
infected – status assigned to message after scanning;
EICAR-Test-File – name of the threat detected in message;
127.0.0.1 – IP address used to send the message;
1Ju4YW-000Du9-0U – message ID in mail system queue;
Default – name of the group associated with the settings used to proc-
ess the message.
To write statistics to a file run the following command:
# /opt/kaspersky/kav4lms/bin/kav4lms-cmd -m statistics -x \
write
This command also rewrites the existing statistics file with new information.
Page 90

90 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Note:
The statistics file must be rewritten to reflect changes after the counters have
been reset.
Warning!
In case a message contains several types of objects that have different scanning
verdicts, then the same message is accounted by each of the corresponding
counters. Therefore, counters are not cumulative - i.e. their sum may not give the
number of total scanned messages.
For example, a single message with three attachments: one infected, one password protected, and one of type application/msword might be counted (depending on configuration) for:
total_messages - because was one of the transferred messages;
scanned_messages – because it was analyzed;
protected_messages – because it had a protected part;
infected_messages –because it had an infected part;
filtered_mime – because it had a matching MIME type.
To reset internal statistics counters run the following command:
# /opt/kaspersky/kav4lms/bin/kav4lms-cmd -m statistics -x \
reset
The statistics functionality parameters are grouped in the
[kav4lms:server.statistics] section of the kav4lms.conf file.
There are two types of statistics:
aggregate - accumulated over time, reflecting overall product activity;
per message - written for each processed message, showing detailed
information about its processing; these are also called raw statistics.
The aggregate statistics are stored in the file, specified via the Destination parameter. The raw statistics are stored in the file, specified via the RawDestina-
tion parameter.
The statistics can be gathered in 2 formats:
txt-file
xml-file.
The statistics file format is specified via the Format parameter.
Page 91

Note:
The application works with agents, supporting the SNMP protocol, v1, v2, and
v3. Please note that the product sends v2 traps, so the trap sink must be configured accordingly.
CHAPTER 10. ADVANCED
SETTINGS
10.1. Monitoring of protection status
via SNMP
Beginning with version 5.6, the application offers read-only access to the following information via the SNMP protocol:
product configuration – parameters from all sections of the application„s
configuration files, including group configuration files;
operational statistics – comprehensive statistics about the application‟s
operation.
The information that can be accessed over SNMP is determined by the
SNMPServices parameter, located in the [kav4lms:server.snmp] section of the
kav4lms.conf configuration file. This parameter can take the following values:
сonfig – application configuration information;
statistics – operational statistics (see 9.2 on p. 87 for details on pub-
lished statistics);
admin – administrative information that contains:
Status.StartedOn – the date when the application was started, in
ISO 8601 format;
Status.UpTime – the time (in seconds) that has elapsed since the
application started;
update – application update information that includes:
Last.Checked – the date of the last check for an update, in ISO
8601 format;
Page 92

92 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Warning!
If the local Unix socket is used, make sure that the subagent and the master
agent can access it. This may imply changing the RunAsUser and RunAs-
Group settings, as well as the access rights of a socket and data files used by
the service (and the central service, if they are both on same machine).
Last.Result – the status of the last update which can be:
o updated – successful update, new anti-virus databases were
installed;
o not-needed – update completed correctly, but no new files
were needed;
o error – update process has failed;
o rolled-back – update was successful, but anti-virus database
was corrupted so a rollback was performed;
o unknown – the last update status could not be determined.
Current.Loaded – the date of the last successful update, in ISO
8601 format;
Current.Records – the number of signatures in the anti-virus data-
base currently in use;
Current.Released – the date in ISO 8601 format when the last up-
date was released.
all – all information described above;
none – do not publish any information over SNMP.
Kaspersky Anti-Virus employs an SNMP subagent that interacts with the SNMP
master agent via AgentX protocol. The AgentX protocol parameters are as follows:
Socket – interaction socket; you can use a local file or network socket
as shown in the example:
Socket=local:/var/agentx/master
or
Socket=inet:705@127.0.0.1
Timeout – time-out (in seconds) for an AgentX request. The default
value is 5.
Retries – number of retries for an AgentX request. The default value is
10. If this parameter is not set, the application will use value 5.
Page 93

Advanced settings 93
Warning!
Actual number of retries may differ with the Retries value specified. This
occurs because of the watchdog activity and is not an issue.
Warning!
You are advised to use NET-SNMP version 5.1.2 or higher which correctly implements the AgentX protocol.
PingInterval – time interval (in seconds) between subagent attempts to
connect to master agent if it becomes disconnected.
You can use any SNMP agent that supports the AgentX protocol as a master
agent. The following section gives a configuration example for NET-SNMP agent,
in which the application subagent uses local socket to connect to NET-SNMP.
To configure the master agent, please perform these steps:
1. Add the following lines to the snmpd.conf configuration file:
master agentx
AgentXSocket /var/agentx/master
AgentXPerms 770 770 root klusers
rocommunity public localhost
trapsink localhost
or, if a network socket is used, change the second line to:
AgentXSocket tcp:127.0.0.1:705
2. Add the following lines to the snmp.conf configuration file:
For Linux:
mibdirs +/opt/kaspersky/kav4lms/share/snmp-mibs
mibs all
For FreeBSD:
mibdirs +/usr/local/share/kav4lms/snmp-mibs/
mibs all
where the path /opt/kaspersky/kav4lms/share/snmp-mibs specifies the
default directory where the MIB files for Kaspersky Anti-Virus are
stored. If the application was installed into another directory, change
this path accordingly.
3. Restart NET-SNMP.
Page 94

94 Kaspersky Anti-Virus 5.6 for Linux Mail Server
Note:
You will find more information about NET-SNMP at http://www.net-snmp.org/.
For more information about snmpd.conf and snmp.conf configuration files,
please see the corresponding manual pages.
Warning!
To get parameter values for objects in the config.Groups section, use the Walk
method instead of Get.
The product OIDs are accessible under the following branch:
.1.3.6.1.4.1.23668.1043
or, in symbolic form:
iso.org.dod.internet.private.enterprises.kaspersky.kav4lms
This node contains the following groups:
сonfig – application configuration parameters, including groups configu-
ration, divided into sections as in configuration files;
statistics – statistical information about processed messages, resources
in use and detected viruses;
update – application update information;
admin – administrative information (application start time, errors etc.).
The Administrator can also set the application to send SNMP-traps in case of
specific events. The SNMPTraps parameter, in the [kav4lms:server.snmp]
section of the kav4lms.conf configuration file, determines the events which
should trigger the sending of SNMP traps by the application. The possible values
are:
сonfig – a SNMP-trap is sent when the configuration or the databases
are reloaded (ConfigReloaded trap and BasesReloaded trap);
admin – a SNMP-trap is sent when the application starts or stops (Pro-
ductStart trap, ProductStop trap) or has a fatal error (ProductError trap).
Additionally, if the AlertThreshold parameter value is not set to zero, an
SNMP-trap will be sent if the percentage of infected messages found
during the last hour exceeds the specified value (AlertThreshold). An
AlertThreshold trap will be sent every hour since the threshold was exceeded until the percentage of infected messages falls below the defined limit.
Page 95

Advanced settings 95
Note:
There is the ConfigReloaded trap corresponding to the application
reload. However, the ProductStart, ProductStop and BasesRe-
loaded traps are also sent in this case. This occurs because the
watchdog warm-restarts the application.
Warning!
If you use NET-SNMP master agent, you should start snmptrapd daemon to receive traps.
update – a SNMP-trap is sent when the application update is performed
(UpdateStatus trap) or the anti-virus database is older than five days
(ObsoleteBases trap);
all – SNMP-trap is sent when any of the above described events oc-
curs;
none – no SNMP-traps are sent.
10.2. Using the application’s setup
script
Kaspersky Anti-Virus provides a special script, allowing managing the application
after it has been installed.
The setup script is used as follows:
# /opt/kaspersky/kav4lms/bin/kav4lms-setup.sh <option>
The available options are:
--install-services - register central and filter services with the ex-
isting system;
--remove-services - unregister all services (will not be
started/stopped with the system);
--check-services - verify if the application‟s services are registered;
--install-filter=<MTA> - register the specified filter into MTA
configuration. Note this also registers it as a service (where applicable);
--remove-filter=<MTA> - unregister the filter service from the
specified MTA;
Page 96

96 Kaspersky Anti-Virus 5.6 for Linux Mail Server
--remove-filters - remove all filters that are found active in MTA
config(s);
--check-filter=<MTA> - verify if the changes for registering with the
MTA were done;
--filter-options=<options> - sets filter specific options. This op-
tion is used only with the ––install-filter option in order to specify
the filter specific parameters. For Sendmail the following options are
available: tempfail, reject, pass;
--install-cron=<component_name> - install cron job for specified
component;
--remove-cron=<component_name> - remove cron job for specified
component;
--check-cron=<component_name> - check if the cron job for com-
ponent is registered;
--user=<user_name> - specify the user name whose credentials will
be used to run the central service and application filter. When used together with the ––install-cron and ––remove-cron parameters,
the option defines the user account, for which a schedule is created.
For example:
# /opt/kaspersky/kav4lms/bin/kav4lms-setup.sh \
--install-cron=updater --user=root
or
# /opt/kaspersky/kav4lms/bin/kav4lms-setup.sh \
--install-cron=updater --user=qmailq
--add-components-info - add product specific options to applica-
tions.setup file;
--del-components-info - remove components specific options from
application registry;
--check-components-info - verify if the product components op-
tions are present;
--install-webmin-module - add web based administration module
to Webmin;
--remove-webmin-module - remove the module from Webmin;
--check-webmin-module - verify if the Webmin module is installed;
Page 97

Advanced settings 97
Note:
All --check options are silent and return 0 for presence of the checked item or
non-0 value for its absence.
Warning!
The ka4lms-cmd tool requires running central service of the application.
--register-key=key-id - register a key by full path, or id relative to
licenses directory;
--group=<group_name> - specify the group that will be used to run
Kaspersky Anti-Virus; the option modifies the Group value in the [op-
tions] section of the application configuration file;
--switch-credentials=<user_name>[,<group_name>] - specify
the user and (if entered) group whose credentials will be used to start
the central service and filter of the application. The option modifies the
RunAsUser and (if entered) RunAsGroup values in the
[kav4lms:server.settings] and [kav4lms:filter.settings] sections of
the application configuration file. If this option is used, the central service and the filter of the application will be restarted.
The <MTA> parameter specifies the MTA to integrate with. Available values are:
exim – post-queue integration with Exim;
exim-dlfunc – pre-queue integration with Exim using dynamically
loaded library;
postfix – post-queue integration with Postfix;
qmail – integration with qmail;
sendmail-milter – integration with Sendmail.
The <component_name> parameter specifies the application‟s component
name. The available option is updater.
10.3. Managing the application from
the command line
Kaspersky Anti-Virus provides a command line management tool kav4lms-cmd,
stored in the /opt/kaspersky/kav4lms/bin directory.
Page 98

98 Kaspersky Anti-Virus 5.6 for Linux Mail Server
This tool‟s command line options are divided into two categories:
1. General application options. This includes:
-v or --version - display program version
-h or --help - display inline help message
-m or --module <argument> - selects a specific module for fur-
ther commands; available options for module are: config, filter, kavmd, statistics, update
-c or --config <argument> - specify a configuration file other
than the default one
-l or --list - list available modules
2. Module-specific options.
a) Config module. This module modifies the application‟s configura-
tion files by querying and setting the configuration keys:
o -q <key> - query the value of a configuration key. , e.g. -q
Path.TempPath;
b) Filter module. This module manages the filter component. The
available option is:
o -x <command> - invoke a filter component command; avail-
able options are: start, stop, restart, status, test-
service.
c) Central service (kavmd) module. This module manages the cen-
tral application service. The available option is:
o -x <service-command> - invoke a central service com-
mand; available options are: start, stop, restart, re-
load, status, test-service.
d) Statistics module. This module manages application‟s statistics.
The available options are:
o -x <stats-command> - invoke a statistics command; avail-
able options are: write, reset.
e) Update module. This module manages the kav4lms-keepup2date
component:
o -e <event-name> - specify the delivery of a certain event,
options are: OnUpdated, OnNotNeeded, OnError, On-
Rolledback, OnUnknown.
Page 99

Advanced settings 99
10.4. Additional informational fields
in messages
The application enables some supplementary information to be added to mail
messages as header fields using one of two separate methods:
Addition of an extension header field to mail message.
The information may indicate the application version, the date when the
anti-virus database was last updated, the time and result of message
scanning (determined by the AddXHeaders parameter in the
[kav4lms:groups.<group_name>.settings] section of the group
configuration file).
Header format:
X-Anti-Virus: <product name and version>, bases:
<date of the last update to anti-virus databases in
YYYYMMDDTHHMMSS format> #<the number of records in AV
databases>, check: <scan date in YYYYMMDD format>
<scanning status or notchecked>
where:
YYYY stands for the year in four-digit format;
MM – month;
DD – date;
HH – hour;
MM – minute;
SS - second.
For example:
X-Anti-Virus: Kaspersky Anti-Virus for Linux Mail
Server 5.6.17/RELEASE build 4,
bases: 20080415 #705877, check: 20080415 clean
Addition of disclaimer text to mail message body.
The information will be added as plain text; it may contain any
statement generated in accordance with the security policy (or other
rules) of a specific organization, and is specified by the AddDisclaimer
parameter in the [kav4lms:groups.<group_name>.settings] section.
The default message text notifies that the message has been scanned
by Kaspersky Anti-Virus. Upon the administrator‟s demand the
Page 100

100 Kaspersky Anti-Virus 5.6 for Linux Mail Server
application can modify the information format (e.g., generate disclaimer
message as a HTML text).
Deleted message part replacement.
When message is being processed, its parts can be deleted according
to the action chosen. The deleted parts can be replaced with a notice
about the reason. For this purpose set the UsePlaceholderNotice (in
[kav4lms:groups.<group_name>.settings] section of the group
configuration file) parameter to yes. If the UsePlaceholderNotice value
is no, then the respective parts will be completely removed from the
message, leaving it like that they never existed.
The notice text is taken from a template file named
part_<action_taken>, which also supports notification macros (see 5.7
on p. 57 for details).
10.5. Localization of displayed date
and time format
While operating, Kaspersky Anti-Virus compiles reports for each of its components as well as various notifications for users and administrators. Such information is always supplemented with the date and time of its output.
By default, Kaspersky Anti-Virus uses the date and time formats corresponding
to the strftime standard:
%H:%M:%S – format of time output (hh.mm.ss).
%d-%m-%y – format of date output (dd.mm.yy).
The administrator may change the date and time format. Localization of formats
is performed in the [locale] section of the kav4lms.conf configuration file. You
can define the following formats:
%I:%M:%S %P – for time output in twelve-hour format (TimeFormat
parameter).
%y/%m/%d and %m/%d/%y – for date output (DateFormat parameter)
(yy.mm.dd and mm.dd.yy respectively).
 Loading...
Loading...