
Kaspersky Anti-Virus 8.0
for Lotus Domino
Implementation Guide
APPLICATION VERSION: 8.0

2
Dear User,
Thank you for choosing our product. We hope that this documentation will help you in your work and provide answers to
most of your questions regarding this software product.
Warning! This document is the property of Kaspersky Lab ZAO (herein also referred to as Kaspersky Lab): all rights to
this document are reserved by the copyright laws of the Russian Federation, and by international treaties. Illegal
reproduction and distribution of this document or parts hereof will result in civil, administrative or criminal liability pursuant
to the laws of the Russian Federation.
Any type of reproduction or distribution of any materials, including translations, is allowed only with the written permission
of Kaspersky Lab.
This document and graphic images related to it may be used exclusively for informational, non-commercial, and personal
purposes.
This document is subject to change without prior notification. For the latest version of this document please refer to
Kaspersky Lab's website at http://www.kaspersky.com/docs.
Kaspersky Lab assumes no liability for the content, quality, relevance, or accuracy of any materials used in this document
for which the rights are held by third parties, or for any potential damages associated with the use of such documents.
This document involves the registered trademarks and service marks which are the property of their respective owners.
Last revised: 19.11.2010
© 1997-2010 Kaspersky Lab ZAO. All Rights Reserved.
http://www.kaspersky.com
http://support.kaspersky.com

3
KASPERSKY LAB END USER LICENSE AGREEMENT
IMPORTANT LEGAL NOTICE TO ALL USERS: CAREFULLY READ THE FOLLOWING LEGAL
AGREEMENT BEFORE YOU START USING THE SOFTWARE.
BY CLICKING THE ACCEPT BUTTON IN THE LICENSE AGREEMENT WINDOW OR BY ENTERING
CORRESPONDING SYMBOL(-S) YOU CONSENT TO BE BOUND BY THE TERMS AND CONDITIONS OF
THIS AGREEMENT. SUCH ACTION IS A SYMBOL OF YOUR SIGNATURE AND YOU ARE
CONSENTING TO BE BOUND BY AND ARE BECOMING A PARTY TO THIS AGREEMENT AND AGREE
THAT THIS AGREEMENT IS ENFORCEABLE LIKE ANY WRITTEN NEGOTIATED AGREEMENT
SIGNED BY YOU. IF YOU DO NOT AGREE TO ALL OF THE TERMS AND CONDITIONS OF THIS
AGREEMENT, CANCEL THE INSTALLATION OF THE SOFTWARE AND DO NOT INSTALL THE
SOFTWARE.
IF LICENSE CONTRACT OR SIMILAR DOCUMENT ACCOMPANIES SOFTWARE, TERMS OF THE
SOFTWARE USE DEFINED IN SUCH DOCUMENT PREVAIL OVER CURRENT END USER LICENSE
AGREEMENT.
AFTER CLICKING THE ACCEPT BUTTON IN THE LICENSE AGREEMENT WINDOW OR AFTER
ENTERING CORRESPONDING SYMBOL(-S) YOU HAVE THE RIGHT TO USE THE SOFTWARE IN
ACCORDANCE WITH THE TERMS AND CONDITIONS OF THIS AGREEMENT.
1. Definitions
1.1. Software means software including any Updates and related materials.
1.2. Rightholder (owner of all rights, whether exclusive or otherwise to the Software) means Kaspersky
Lab ZAO, a company incorporated according to the laws of the Russian Federation.
1.3. Computer(s) means hardware(s), including personal computers, laptops, workstations, personal
digital assistants, ‘smart phones’, hand-held devices, or other electronic devices for which the
Software was designed where the Software will be installed and/or used.
1.4. End User (You/Your) means individual(s) installing or using the Software on his or her own behalf or
who is legally using a copy of the Software; or, if the Software is being downloaded or installed on
behalf of an organization, such as an employer, "You" further means the organization for which the
Software is downloaded or installed and it is represented hereby that such organization has
authorized the person accepting this agreement to do so on its behalf. For purposes hereof the term
"organization," without limitation, includes any partnership, limited liability company, corporation,
association, joint stock company, trust, joint venture, labor organization, unincorporated organization,
or governmental authority.
1.5. Partner(s) means organizations or individual(s), who distributes the Software based on an
agreement and license with the Rightholder.
1.6. Update(s) means all upgrades, revisions, patches, enhancements, fixes, modifications, copies,
additions or maintenance packs etc.
1.7. User Manual means user manual, administrator guide, reference book and related explanatory or
other materials.
2. Grant of License
2.1. You are given a non-exclusive license to store, load, install, execute, and display (to "use") the
Software on a specified number of Computers in order to assist in protecting Your Computer on
which the Software is installed, from threats described in the User Manual, according to the all
technical requirements described in the User Manual and according to the terms and conditions of
this Agreement (the "License") and you accept this License:
Trial Version. If you have received, downloaded and/or installed a trial version of the Software and
are hereby granted an evaluation license for the Software, you may use the Software only for

I M P L E M E N T A T I O N G U I D E
4
evaluation purposes and only during the single applicable evaluation period, unless otherwise
indicated, from the date of the initial installation. Any use of the Software for other purposes or
beyond the applicable evaluation period is strictly prohibited.
Multiple Environment Software; Multiple Language Software; Dual Media Software; Multiple Copies;
Bundles. If you use different versions of the Software or different language editions of the Software, if
you receive the Software on multiple media, if you otherwise receive multiple copies of the Software,
or if you received the Software bundled with other software, the total permitted number of your
Computers on which all versions of the Software are installed shall correspond to the number of
computers specified in licenses you have obtained provided that unless the licensing terms provide
otherwise, each acquired license entitles you to install and use the Software on such a number of
Computer(s) as is specified in Clauses 2.2 and 2.3.
2.2. If the Software was acquired on a physical medium You have the right to use the Software for
protection of such a number of Computer(s) as is specified on the Software package.
2.3. If the Software was acquired via the Internet You have the right to use the Software for protection of
such a number of Computers that was specified when You acquired the License to the Software.
2.4. You have the right to make a copy of the Software solely for back-up purposes and only to replace
the legally owned copy if such copy is lost, destroyed or becomes unusable. This back-up copy
cannot be used for other purposes and must be destroyed when you lose the right to use the
Software or when Your license expires or is terminated for any other reason according to the
legislation in force in the country of your principal residence or in the country where You are using
the Software.
2.5. From the time of the Software activation or after license key file installation (with the exception of a
trial version of the Software) You have the right to receive the following services for the defined
period specified on the Software package (if the Software was acquired on a physical medium) or
specified during acquisition (if the Software was acquired via the Internet):
- Updates of the Software via the Internet when and as the Rightholder publishes them on its
website or through other online services. Any Updates that you may receive become part of the
Software and the terms and conditions of this Agreement apply to them;
- Technical Support via the Internet and Technical Support telephone hotline.
3. Activation and Term
3.1. If You modify Your Computer or make changes to other vendors’ software installed on it, You may be
required by the Rightholder to repeat activation of the Software or license key file installation. The
Rightholder reserves the right to use any means and verification procedures to verify the validity of
the License and/or legality of a copy of the Software installed and/or used on Your Computer.
3.2. If the Software was acquired on a physical medium, the Software can be used, upon your
acceptance of this Agreement, for the period that is specified on the package commencing upon
acceptance of this Agreement.
3.3. If the Software was acquired via the Internet, the Software can be used, upon your acceptance of
this Agreement, for the period that was specified during acquisition.
3.4. You have the right to use a trial version of the Software as provided in Clause 2.1 without any charge
for the single applicable evaluation period (30 days) from the time of the Software activation
according to this Agreement provided that the trial version does not entitle You Updates and
Technical support via the Internet and Technical support telephone hotline.
3.5. Your License to Use the Software is limited to the period of time as specified in Clauses 3.2 or 3.3
(as applicable) and the remaining period can be viewed via means described in User Manual.
3.6. If You have acquired the Software that is intended to be used on more than one Computer then Your
License to Use the Software is limited to the period of time starting from the date of activation of the
Software or license key file installation on the first Computer.
3.7. Without prejudice to any other remedy in law or in equity that the Rightholder may have, in the event
of any breach by You of any of the terms and conditions of this Agreement, the Rightholder shall at
any time without notice to You be entitled to terminate this License without refunding the purchase
price or any part thereof.
3.8. You agree that in using the Software and in using any report or information derived as a result of
using this Software, you will comply with all applicable international, national, state, regional and
local laws and regulations, including, without limitation, privacy, copyright, export control and
obscenity law.
K A S P E R S K Y LA B E N D U S E R L I C E N S E A G R E E M E N T
5
3.9. Except as otherwise specifically provided herein, you may not transfer or assign any of the rights
granted to you under this Agreement or any of your obligations pursuant hereto.
4. Technical Support
4.1. The Technical Support described in Clause 2.5 of this Agreement is provided to You when the latest
Update of the Software is installed (except for a trial version of the Software).
Technical support service: http://support.kaspersky.com
4.2. User’s Data, specified in Personal Cabinet/My Kaspersky Account, can be used by Technical
Support specialists only during processing User’s request.
5. Limitations
5.1. You shall not emulate, clone, rent, lend, lease, sell, modify, decompile, or reverse engineer the
Software or disassemble or create derivative works based on the Software or any portion thereof
with the sole exception of a non-waivable right granted to You by applicable legislation, and you shall
not otherwise reduce any part of the Software to human readable form or transfer the licensed
Software, or any subset of the licensed Software, nor permit any third party to do so, except to the
extent the foregoing restriction is expressly prohibited by applicable law. Neither Software’s binary
code nor source may be used or reverse engineered to re-create the program algorithm, which is
proprietary. All rights not expressly granted herein are reserved by Rightholder and/or its suppliers,
as applicable. Any such unauthorized use of the Software shall result in immediate and automatic
termination of this Agreement and the License granted hereunder and may result in criminal and/or
civil prosecution against You.
5.2. You shall not transfer the rights to use the Software to any third party.
5.3. You shall not provide the activation code and/or license key file to third parties or allow third parties
access to the activation code and/or license key which are deemed confidential data of Rightholder.
5.4. You shall not rent, lease or lend the Software to any third party.
5.5. You shall not use the Software in the creation of data or software used for detection, blocking or
treating threats described in the User Manual.
5.6. Your key file can be blocked in case You breach any of the terms and conditions of this Agreement.
5.7. If You are using the trial version of the Software You do not have the right to receive the Technical
Support specified in Clause 4 of this Agreement and You don’t have the right to transfer the license
or the rights to use the Software to any third party.
6. Limited Warranty and Disclaimer
6.1. The Rightholder guarantees that the Software will substantially perform according to the
specifications and descriptions set forth in the User Manual provided however that such limited
warranty shall not apply to the following: (w) Your Computer’s deficiencies and related infringement
for which Rightholder’s expressly disclaims any warranty responsibility; (x) malfunctions, defects, or
failures resulting from misuse; abuse; accident; neglect; improper installation, operation or
maintenance; theft; vandalism; acts of God; acts of terrorism; power failures or surges; casualty;
alteration, non-permitted modification, or repairs by any party other than Rightholder; or any other
third parties’ or Your actions or causes beyond Rightholder’s reasonable control ; (y) any defect not
made known by You to Rightholder as soon as practical after the defect first appears; and (z)
incompatibility caused by hardware and/or software components installed on Your Computer.
6.2. You acknowledge, accept and agree that no software is error free and You are advised to back-up
the Computer, with frequency and reliability suitable for You.
6.3. The Rightholder does not provide any guarantee that the Software will work correctly in case of
violations of the terms described in the User Manual or in this Agreement.
6.4. The Rightholder does not guarantee that the Software will work correctly if You do not regularly
download Updates specified in Clause 2.5 of this Agreement.
6.5. The Rightholder does not guarantee protection from the threats described in the User Manual after
the expiration of the period specified in Clauses 3.2 or 3.3 of this Agreement or after the License to
use the Software is terminated for any reason.
6.6. THE SOFTWARE IS PROVIDED "AS IS" AND THE RIGHTHOLDER MAKES NO
REPRESENTATION AND GIVES NO WARRANTY AS TO ITS USE OR PERFORMANCE. EXCEPT
FOR ANY WARRANTY, CONDITION, REPRESENTATION OR TERM THE EXTENT TO WHICH
CANNOT BE EXCLUDED OR LIMITED BY APPLICABLE LAW THE RIGHTHOLDER AND ITS
PARTNERS MAKE NO WARRANTY, CONDITION, REPRESENTATION, OR TERM (EXPRESSED
I M P L E M E N T A T I O N G U I D E
6
OR IMPLIED, WHETHER BY STATUTE, COMMON LAW, CUSTOM, USAGE OR OTHERWISE) AS
TO ANY MATTER INCLUDING, WITHOUT LIMITATION, NONINFRINGEMENT OF THIRD PARTY
RIGHTS, MERCHANTABILITY, SATISFACTORY QUALITY, INTEGRATION, OR APPLICABILITY
FOR A PARTICULAR PURPOSE. YOU ASSUME ALL FAULTS, AND THE ENTIRE RISK AS TO
PERFORMANCE AND RESPONSIBILITY FOR SELECTING THE SOFTWARE TO ACHIEVE YOUR
INTENDED RESULTS, AND FOR THE INSTALLATION OF, USE OF, AND RESULTS OBTAINED
FROM THE SOFTWARE. WITHOUT LIMITING THE FOREGOING PROVISIONS, THE
RIGHTHOLDER MAKES NO REPRESENTATION AND GIVES NO WARRANTY THAT THE
SOFTWARE WILL BE ERROR-FREE OR FREE FROM INTERRUPTIONS OR OTHER FAILURES
OR THAT THE SOFTWARE WILL MEET ANY OR ALL YOUR REQUIREMENTS WHETHER OR
NOT DISCLOSED TO THE RIGHTHOLDER .
7. Exclusion and Limitation of Liability
7.1. TO THE MAXIMUM EXTENT PERMITTED BY APPLICABLE LAW, IN NO EVENT SHALL THE
RIGHTHOLDER OR ITS PARTNERS BE LIABLE FOR ANY SPECIAL, INCIDENTAL, PUNITIVE,
INDIRECT, OR CONSEQUENTIAL DAMAGES WHATSOEVER (INCLUDING, BUT NOT LIMITED
TO, DAMAGES FOR LOSS OF PROFITS OR CONFIDENTIAL OR OTHER INFORMATION, FOR
BUSINESS INTERRUPTION, FOR LOSS OF PRIVACY, FOR CORRUPTION, DAMAGE AND LOSS
OF DATA OR PROGRAMS, FOR FAILURE TO MEET ANY DUTY INCLUDING ANY STATUTORY
DUTY, DUTY OF GOOD FAITH OR DUTY OF REASONABLE CARE, FOR NEGLIGENCE, FOR
ECONOMIC LOSS, AND FOR ANY OTHER PECUNIARY OR OTHER LOSS WHATSOEVER)
ARISING OUT OF OR IN ANY WAY RELATED TO THE USE OF OR INABILITY TO USE THE
SOFTWARE, THE PROVISION OF OR FAILURE TO PROVIDE SUPPORT OR OTHER SERVICES,
INFORMATON, SOFTWARE, AND RELATED CONTENT THROUGH THE SOFTWARE OR
OTHERWISE ARISING OUT OF THE USE OF THE SOFTWARE, OR OTHERWISE UNDER OR IN
CONNECTION WITH ANY PROVISION OF THIS AGREEMENT, OR ARISING OUT OF ANY
BREACH OF CONTRACT OR ANY TORT (INCLUDING NEGLIGENCE, MISREPRESENTATION,
ANY STRICT LIABILITY OBLIGATION OR DUTY), OR ANY BREACH OF STATUTORY DUTY, OR
ANY BREACH OF WARRANTY OF THE RIGHTHOLDER AND/OR ANY OF ITS PARTNERS, EVEN
IF THE RIGHTHOLDER AND/OR ANY PARTNER HAS BEEN ADVISED OF THE POSSIBILITY OF
SUCH DAMAGES.
YOU AGREE THAT IN THE EVENT THE RIGHTHOLDER AND/OR ITS PARTNERS ARE FOUND
LIABILE, THE LIABILITY OF THE RIGHTHOLDER AND/OR ITS PARTNERS SHALL BE LIMITED
BY THE COSTS OF THE SOFTWARE. IN NO CASE SHALL THE LIABILITY OF THE
RIGHTHOLDER AND/OR ITS PARTNERS EXCEED THE FEES PAID FOR THE SOFTWARE TO
THE RIGHTHOLDER OR THE PARTNER (AS MAY BE APPLICABLE).
NOTHING IN THIS AGREEMENT EXCLUDES OR LIMITS ANY CLAIM FOR DEATH AND
PERSONAL INJURY. FURTHER IN THE EVENT ANY DISCLAIMER, EXCLUSION OR LIMITATION
IN THIS AGREEMENT CANNOT BE EXLUDED OR LIMITED ACCORDING TO APPLICABLE LAW
THEN ONLY SUCH DISCLAIMER, EXCLUSION OR LIMITATION SHALL NOT APPLY TO YOU
AND YOU CONTINUE TO BE BOUND BY ALL THE REMAINING DISCLAIMERS, EXCLUSIONS
AND LIMITATIONS.
8. GNU and Other Third Party Licenses
8.1. The Software may include some software programs that are licensed (or sublicensed) to the user
under the GNU General Public License (GPL) or other similar free software licenses which, among
other rights, permit the user to copy, modify and redistribute certain programs, or portions thereof,
and have access to the source code ("Open Source Software"). If such licenses require that for any
software, which is distributed to someone in an executable binary format, that the source code also
be made available to those users, then the source code should be made available by sending the
request to source@kaspersky.com or the source code is supplied with the Software. If any Open
Source Software licenses require that the Rightholder provide rights to use, copy or modify an Open
Source Software program that are broader than the rights granted in this Agreement, then such
rights shall take precedence over the rights and restrictions herein.
9. Intellectual Property Ownership

K A S P E R S K Y LA B E N D U S E R L I C E N S E A G R E E M E N T
7
9.1. You agree that the Software and the authorship, systems, ideas, methods of operation,
documentation and other information contained in the Software, are proprietary intellectual property
and/or the valuable trade secrets of the Rightholder or its partners and that the Rightholder and its
partners, as applicable, are protected by civil and criminal law, and by the law of copyright, trade
secret, trademark and patent of the Russian Federation, European Union and the United States, as
well as other countries and international treaties. This Agreement does not grant to You any rights to
the intellectual property including any the Trademarks or Service Marks of the Rightholder and/or its
partners ("Trademarks"). You may use the Trademarks only insofar as to identify printed output
produced by the Software in accordance with accepted trademark practice, including identification of
the Trademark owner’s name. Such use of any Trademark does not give you any rights of
ownership in that Trademark. The Rightholder and/or its partners own and retain all right, title, and
interest in and to the Software, including without limitation any error corrections, enhancements,
Updates or other modifications to the Software, whether made by the Rightholder or any third party,
and all copyrights, patents, trade secret rights, trademarks, and other intellectual property rights
therein. Your possession, installation or use of the Software does not transfer to you any title to the
intellectual property in the Software, and you will not acquire any rights to the Software except as
expressly set forth in this Agreement. All copies of the Software made hereunder must contain the
same proprietary notices that appear on and in the Software. Except as stated herein, this
Agreement does not grant you any intellectual property rights in the Software and you acknowledge
that the License, as further defined herein, granted under this Agreement only provides you with a
right of limited use under the terms and conditions of this Agreement. Rightholder reserves all rights
not expressly granted to you in this Agreement.
9.2. You agree not to modify or alter the Software in any way. You may not remove or alter any copyright
notices or other proprietary notices on any copies of the Software.
10. Governing Law; Arbitration
10.1. This Agreement will be governed by and construed in accordance with the laws of the Russian
Federation without reference to conflicts of law rules and principles. This Agreement shall not be governed by
the United Nations Convention on Contracts for the International Sale of Goods, the application of which is
expressly excluded. Any dispute arising out of the interpretation or application of the terms of this Agreement
or any breach thereof shall, unless it is settled by direct negotiation, be settled by in the International
Commercial Arbitration Court at the Russian Federation Chamber of Commerce and Industry in Moscow, the
Russian Federation. Any award rendered by the arbitrator shall be final and binding on the parties and any
judgment on such arbitration award may be enforced in any court of competent jurisdiction. Nothing in this
Section 10 shall prevent a Party from seeking or obtaining equitable relief from a court of competent
jurisdiction, whether before, during or after arbitration proceedings.
11. Period for Bringing Actions
11.1. No action, regardless of form, arising out of the transactions under this Agreement, may be brought
by either party hereto more than one (1) year after the cause of action has occurred, or was
discovered to have occurred, except that an action for infringement of intellectual property rights may
be brought within the maximum applicable statutory period.
12. Entire Agreement; Severability; No Waiver
12.1. This Agreement is the entire agreement between you and Rightholder and supersedes any other
prior agreements, proposals, communications or advertising, oral or written, with respect to the
Software or to subject matter of this Agreement. You acknowledge that you have read this
Agreement, understand it and agree to be bound by its terms. If any provision of this Agreement is
found by a court of competent jurisdiction to be invalid, void, or unenforceable for any reason, in
whole or in part, such provision will be more narrowly construed so that it becomes legal and
enforceable, and the entire Agreement will not fail on account thereof and the balance of the
Agreement will continue in full force and effect to the maximum extent permitted by law or equity
while preserving, to the fullest extent possible, its original intent. No waiver of any provision or
condition herein shall be valid unless in writing and signed by you and an authorized representative
of Rightholder provided that no waiver of any breach of any provisions of this Agreement will
constitute a waiver of any prior, concurrent or subsequent breach. Rightholder’s failure to insist upon

I M P L E M E N T A T I O N G U I D E
8
or enforce strict performance of any provision of this Agreement or any right shall not be construed
as a waiver of any such provision or right.
13. Rightholder Contact Information
Should you have any questions concerning this Agreement, or if you desire to contact the Rightholder for any
reason, please contact our Customer Service Department at:
Kaspersky Lab ZAO, 10 build. 1, 1st Volokolamsky Proezd
Moscow, 123060
Russian Federation
Tel: +7-495-797-8700
Fax: +7-495-645-7939
E-mail: info@kaspersky.com
Web site: www.kaspersky.com
© 1997-2010 Kaspersky Lab ZAO. All Rights Reserved. The Software and any accompanying
documentation are copyrighted and protected by copyright laws and international copyright treaties, as well
as other intellectual property laws and treaties.

9
CONTENTS
KASPERSKY LAB END USER LICENSE AGREEMENT .............................................................................................. 3
ADDITIONAL SOURCES OF INFORMATION ABOUT THE APPLICATION .............................................................. 11
Sources of information to research on your own .................................................................................................... 11
Contacting the Sales Department .......................................................................................................................... 12
Contact the Technical Documentation Development Team ................................................................................... 12
Discussing Kaspersky Lab applications on the web forum .................................................................................... 12
KASPERSKY ANTI-VIRUS 8.0 FOR LOTUS DOMINO .............................................................................................. 13
HARDWARE AND SOFTWARE REQUIREMENTS .................................................................................................... 15
APPLICATION ARCHITECTURE ................................................................................................................................ 16
Anti-Virus server protection scheme ...................................................................................................................... 17
Application operation scheme .......................................................................................................................... 18
Anti-virus scanning algorithm ........................................................................................................................... 18
Attachment filtering algorithm ........................................................................................................................... 19
Processing objects and actions performed on them ......................................................................................... 20
Managing Kaspersky Anti-Virus settings................................................................................................................ 20
Configuring the Domino server security settings .................................................................................................... 22
Managing user permissions ................................................................................................................................... 22
Managing permissions at the ACL level of the Kaspersky Anti-Virus databases .............................................. 23
Managing permissions at the level of profile and server settings ..................................................................... 25
TYPICAL DEPLOYMENT SCHEMES ......................................................................................................................... 26
Distributed deployment scheme ............................................................................................................................. 26
Isolated deployment scheme ................................................................................................................................. 27
DEPLOYING THE APPLICATION ............................................................................................................................... 29
Preparing for installation ........................................................................................................................................ 29
Deleting the previous version of Kaspersky Anti-Virus and other anti-virus programs for Lotus Notes/Domino 30
Settings permissions for the user performing the installation ........................................................................... 30
Creating a group of installation servers in the Address book ........................................................................... 31
Setting server permissions ............................................................................................................................... 31
Creating a group of users for granting permissions .......................................................................................... 32
Preparing an installation database ................................................................................................................... 32
Preparing a key file .......................................................................................................................................... 33
Configuring security settings for the Lotus Notes client .................................................................................... 33
Installing the application......................................................................................................................................... 34
Step 1. Starting the installation ......................................................................................................................... 35
Step 2. Accepting the License Agreement ....................................................................................................... 36
Step 3. Configuring installation settings ........................................................................................................... 37
Step 4. Launching and performing automatic installation steps ....................................................................... 40
Step 5. Activating the license ........................................................................................................................... 43
Step 6. Finishing the installation ....................................................................................................................... 44
System modifications after installation ................................................................................................................... 44
Files and directories ......................................................................................................................................... 44
Modifying the Domino configuration file............................................................................................................ 45
Modifying the list of processes ......................................................................................................................... 45

I M P L E M E N T A T I O N G U I D E
10
Preparing for operation .......................................................................................................................................... 45
Deleting Kaspersky Anti-Virus ............................................................................................................................... 47
Deleting from the last server in a distributed deployment scheme ................................................................... 48
Deleting from a server in a distributed deployment scheme ............................................................................. 49
CONTACTING TECHNICAL SUPPORT ................................................................ ..................................................... 50
GLOSSARY ................................................................................................................................................................. 51
KASPERSKY LAB ....................................................................................................................................................... 52
INFORMATION ABOUT THIRD-PARTY SOFTWARE ................................................................................................ 53
Software ................................................................................................................................................................. 53
BOOST 1.30 ..................................................................................................................................................... 53
EXPAT 1.2 ....................................................................................................................................................... 53
GECKO SDK 1.8 .............................................................................................................................................. 53
INFO-ZIP 5.51 ................................................................................................................................ .................. 62
LIBNKFM 2.0.5 ................................................................................................................................................. 63
LZMA SDK 4.43 ............................................................................................................................................... 63
OPENSSL 0.9.8D ............................................................................................................................................. 63
PCRE 7.4 ......................................................................................................................................................... 65
RFC1321-BASED (RSA-FREE) MD5 LIBRARY .............................................................................................. 66
ZLIB 1.2............................................................................................................................................................ 66
Development tools ................................................................................................................................................. 66
AUTOCONF 2.61 ............................................................................................................................................. 66
AUTOMAKE 1.10 ............................................................................................................................................. 66
AWK 3.1.5 ........................................................................................................................................................ 66
BASH 3.2.33 .................................................................................................................................................... 67
GСС 4.1.2 ........................................................................................................................................................ 67
GСС 3.4.5 ........................................................................................................................................................ 67
GСС 3.3.6 ........................................................................................................................................................ 67
GСС 3.3.2 ........................................................................................................................................................ 67
GNU MAKE 3.81 .............................................................................................................................................. 68
GREP 2.5.1 ...................................................................................................................................................... 68
PERL 5.8.8 ....................................................................................................................................................... 68
SED 4.1.5 ......................................................................................................................................................... 70
Other information ................................................................................................................................................... 70
GNU GENERAL PUBLIC LICENSE ................................................................................................................. 70
INDEX ......................................................................................................................................................................... 91

11
ADDITIONAL SOURCES OF INFORMATION
IN THIS SECTION
Sources of information to research on your own ............................................................................................................. 11
Contacting the Sales Department .................................................................................................................................... 12
Contact the Technical Documentation Development Team ............................................................................................. 12
Discussing Kaspersky Lab applications on the web forum .............................................................................................. 12
ABOUT THE APPLICATION
If you have any questions related to purchasing, installing or using Kaspersky Anti-Virus 8.0, answers are available from
a variety of different sources. You can choose the most suitable source of information, depending on the importance and
urgency of your inquiry.
SOURCES OF INFORMATION TO RESEARCH ON YOUR OWN
You can refer to the following sources of information about the application:
Application page on the Kaspersky Lab website
Application page on the Technical Support website (in the Knowledge Base)
Help system
Documentation
Page on the Kaspersky Lab website
http://www.kaspersky.com/anti-virus_lotus_domino
This page contains general information about Kaspersky Anti-Virus, its features, and specifics of working with it. You
can purchase Kaspersky Anti-Virus or extend your license at the online store.
Application page at the Technical Support website (Knowledge Base)
http://support.kaspersky.com/lotus
On this page you can find articles created by Technical Support specialists.
These articles contain useful information, recommendations and answers to frequently asked questions (FAQ)
related to purchasing, installing and using Kaspersky Anti-Virus. They are grouped by topic, for example, "Working
with key files", "Updating databases" or "Troubleshooting". The articles may contain answers to questions related not
only to Kaspersky Anti-Virus, but to other Kaspersky Lab products as well, and may contain general Technical
Support news.

I M P L E M E N T A T I O N G U I D E
12
Help system
Help contains information about how to manage server protection: how to view protection status information,
configure component protection, enable and disable protection components, start a scan of the server database, and
update anti-virus databases manually.
To open Help, click the Help tab in the Control center window of databases.
Documentation
The Kaspersky Anti-Virus documentation package contains nearly all information necessary for
working with the application. It consists of the following documents:
The Administrator's Guide contains information about how to use the application, configure it and manage the
protection of one server or a group of servers through a Lotus Notes client. The guide also tells you about the
application's web interface and the Domino server console.
The Implementation Guide allows administrators to plan for deployment of the application on a network, and
contains practical recommendations on how to install, set up, or delete the application on one server or on all
protected servers in the network.
CONTACTING THE SALES DEPARTMENT
If you have questions about selecting or purchasing the Kaspersky Anti-Virus or extending your license, please phone the
Sales Department in our Moscow Central Office, at:
+7 (495) 797-87-00, +7 (495) 645-79-39, +7 (495) 956-70-00
Our specialists speak English and Russian.
You can also send your questions to our Sales Department by email to sales@kaspersky.com.
CONTACT THE TECHNICAL DOCUMENTATION DEVELOPMENT TEAM
If you have any questions related to the documentation, or find an error, or want to leave a comment, feel free to contact
our Technical Documentation Development Team.
Send a mail message with your comments and questions to the Technical Documentation Development Team at
docfeedback@kaspersky.com. Please write Kaspersky Help Feedback: Kaspersky Anti-Virus 8.0 for Lotus Domino in the
subject field.
DISCUSSING KASPERSKY LAB APPLICATIONS ON THE
WEB FORUM
If your question does not require an urgent answer, you can discuss it with Kaspersky Lab's specialists and other users in
our forum at http://forum.kaspersky.com/index.php?showforum=5.
In this forum you can view existing topics, leave your comments, create new topics and use the search engine.
13
KASPERSKY ANTI-VIRUS 8.0 FOR LOTUS DOMINO
Kaspersky Anti-Virus 8.0 for Lotus Domino (hereinafter referred to as Kaspersky Anti-Virus) provides comprehensive antivirus protection for Domino servers. Kaspersky Anti-Virus protects email traffic and replications and scans databases
stored on the protected server.
Kaspersky Anti-Virus is installed on servers that run the Microsoft Windows or Linux operating systems. It performs the
following functions:
Scanning of all incoming, outgoing, and routed email on the Domino server. The text of messages, file
attachments and embedded OLE objects are scanned for threats. Kaspersky Anti-Virus detects all malware
objects inside attached archives and packed .exe files, except those protected by passwords.
Documents modified after replication are scanned. Documents on the protected server that are modified as a
result of replication are scanned for threats. Outgoing replications are not scanned. Fields in Rich Text format,
attached files, and embedded OLE objects in documents are scanned for threats.
Scanning of databases on the protected Domino server are performed according to a schedule or on demand.
Fields in Rich Text format, attached files, and embedded OLE objects in documents are scanned for threats.
Objects are filtered by size and name mask when email messages, replications, and databases are scanned.
Filtered objects are processed according to rules set by the administrator.
Processing of objects that are infected, potentially infected, and not scanned, which are detected when email
messages, replicated documents and database documents are scanned. Depending on the values of the
protection / scan settings, Kaspersky Anti-Virus disinfects, deletes or skips the object, notifies administrators of
detected threats and processing results, and saves statistical information.
Senders and recipients of messages, as well as administrators, are notified of infected, potentially infected, and
objects not scanned that are detected in messages. They also are notified of any remedies undertaken.
Notification of the threat of virus epidemics. Kaspersky Anti-Virus notes any attempts for mass distribution of
infected, potentially infected and damaged objects in messages and notifies administrators.
Kaspersky Anti-Virus notifies administrators of objects detected when scanning replicated documents and
database documents, and of remedies undertaken.
Kaspersky Anti-Virus stores infected and potentially infected objects in Quarantine. Saved messages and
documents identified during a replication scan and documents identified during a database scan are grouped by
type (mail / replications / scanning).
Information detected about objects that are infected, potentially infected and not scanned, and information about
actions performed, is stored in the Worklog and statistics database and is also displayed in the Domino server
console.
Anti-virus databases are updated over the Internet both automatically and manually. Kaspersky Lab's FTP and
HTTP update servers on the Internet, FTP and HTTP servers containing updates, and local and network
directories can serve as update resources.
Search for threats and disinfection of infected objects are performed on the basis of anti-virus database records. The
anti-virus databases contain descriptions of all currently known threats and of methods to disinfect objects infected
with these malicious programs. The databases also contain descriptions of potentially dangerous software.
It is extremely important to keep anti-virus databases up-to-date, because new threats appear every day.
The anti-virus databases on Kaspersky Lab's servers are updated every hour. We recommend that you update the
application's anti-virus databases just as frequently.

I M P L E M E N T A T I O N G U I D E
14
Managing Kaspersky Anti-Virus installed on several servers using profiles.
Access to Kaspersky Anti-Virus settings and control is restricted at the server and profile levels.
Managing Kaspersky Anti-Virus through the Lotus Notes client, Domino console server, and web browser.
The application can be installed or deleted through the Lotus Notes client or web browser.

15
HARDWARE AND SOFTWARE REQUIREMENTS
To function properly, Kaspersky Anti-Virus has the following minimum requirements.
Hardware requirements:
Intel Pentium 32 bit / 64 bit or higher (or equivalent)
512 MB of RAM (1GB or more recommended)
1 GB of free space on the hard drive (3 GB or more recommended)
Recommended size of swap file: twice as large as the physical memory.
Software requirements:
Supported operating systems:
32-bit platforms:
Microsoft Windows 2000 Server (Service Pack 4 or higher)
Microsoft Windows 2000 Advanced Server (Service Pack 4 or higher)
Microsoft Windows Server 2003 Standard Edition (Service Pack 2)
Microsoft Windows Server 2003 Enterprise Edition (Service Pack 2)
Novell SUSE Linux Enterprise Server 10 (Service Pack 2)
Red Hat Enterprise Linux 5 (Service Pack 3)
64-bit platforms:
Microsoft Windows Server 2003 x64 Edition (Service Pack 2)
Novell SUSE Linux Enterprise Server 10 (Service Pack 2)
Red Hat Enterprise Linux 5 (Service Pack 3)
Supported Lotus Notes/Domino servers:
Lotus Notes/Domino version 6.5
Lotus Notes/Domino version 7.0
Lotus Notes/Domino version 8.0
Lotus Notes/Domino version 8.5
Supported browsers:
Windows Internet Explorer 7
Windows Internet Explorer 8
Mozilla Firefox 3.6
Google Chrome
16
APPLICATION ARCHITECTURE
Kaspersky Anti-Virus consists of the following modules:
Control module – Provides the following functions in Kaspersky Anti-Virus:
Application management: Initiates scans of email and replications, and runs scans of databases and
scheduled updates of anti-virus databases.
Settings management: Receives and applies new settings.
Storage and analysis of statistical information: Logs statistical information and information about operational
events in the Worklog and statistics database and sends notifications to administrators.
Notifications: Sends email notifications about infected, potentially infected and damaged objects detected
during scanning.
Notifications about epidemics: Monitors the number of infected, potentially infected, and damaged objects
detected during scanning of email messages, and monitors the number of objects that contain an identical
threat. The control module also notifies administrators if an excessive number of objects are detected in a
specified time interval.
License management: License activation, analysis of license information, installation, and key file deletion.
Email and replication scan module – Performs anti-virus scans of email messages and replications.
Database scan module – Performs anti-virus scans of Domino server databases.
All modules are loaded automatically when the Domino server is started. Information about modules can be recorded in
the Worklog and statistics database, written to the log files, and displayed on the Domino server console.
All databases are stored in the staging directory for Kaspersky Anti-Virus databases (by default, the kavdatabases
directory).
The application includes the following databases:
Control center database (kavcontrolcenter.nsf) is used to manage and store Kaspersky Anti-Virus settings.
Quarantine database (kavquarantine.nsf) is used to store quarantined objects and take actions on them.
Worklog and statistics database (kaveventslog.nsf) is used to store events registered in Kaspersky Anti-Virus
operation and statistical information about scanned objects and actions taken on them.
Help database (kavhelp.nsf) contains reference information about Kaspersky Anti-Virus.
The above databases are accessed via the user interface of the Control center database.
A P P L I C A T I O N A R C H I T E C T U R E
17
IN THIS SECTION
Anti-Virus server protection scheme ................................................................................................................................ 17
Managing Kaspersky Anti-Virus settings ......................................................................................................................... 20
Configuring the Domino server security settings ............................................................................................................. 22
Managing user permissions ............................................................................................................................................. 22
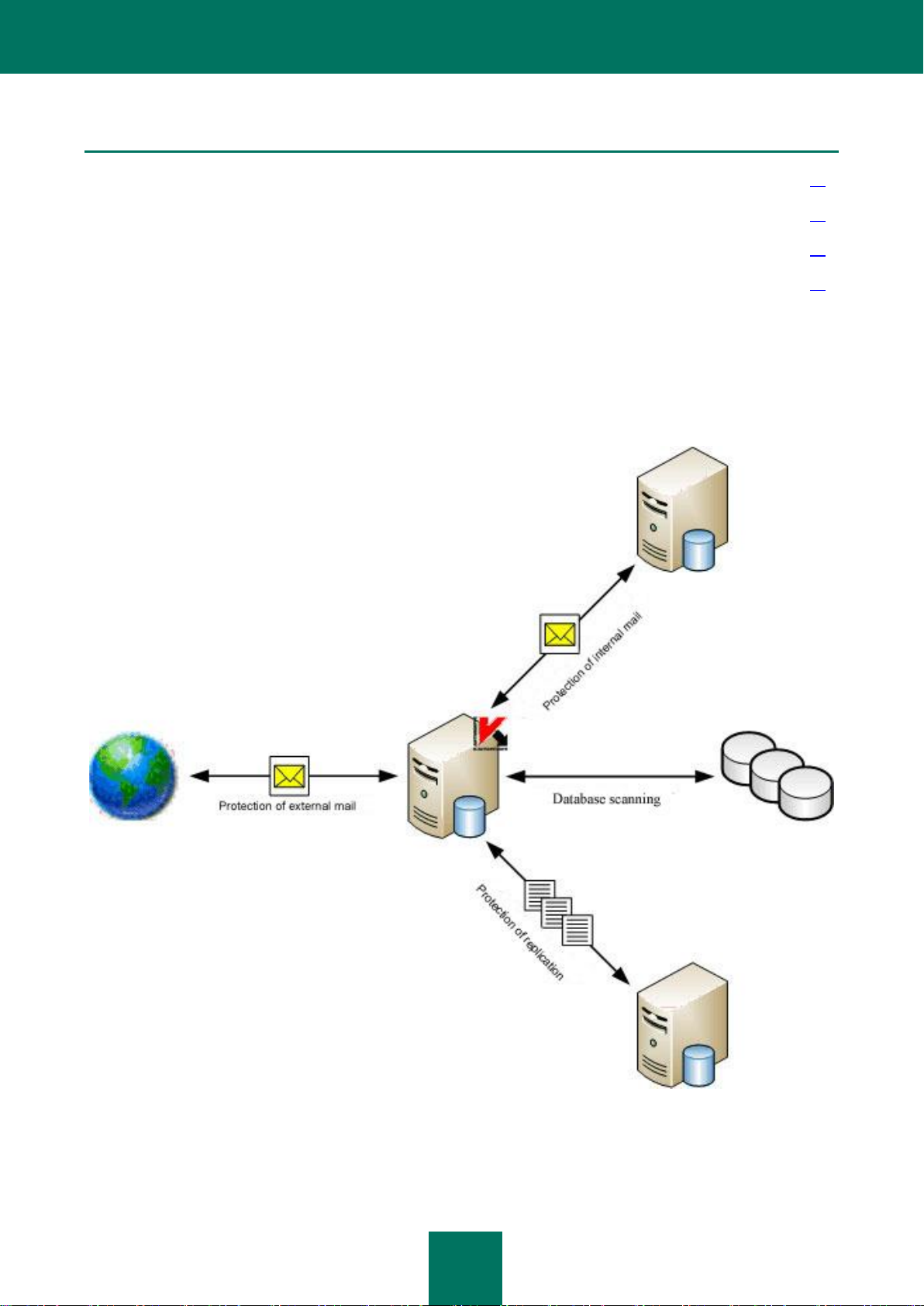
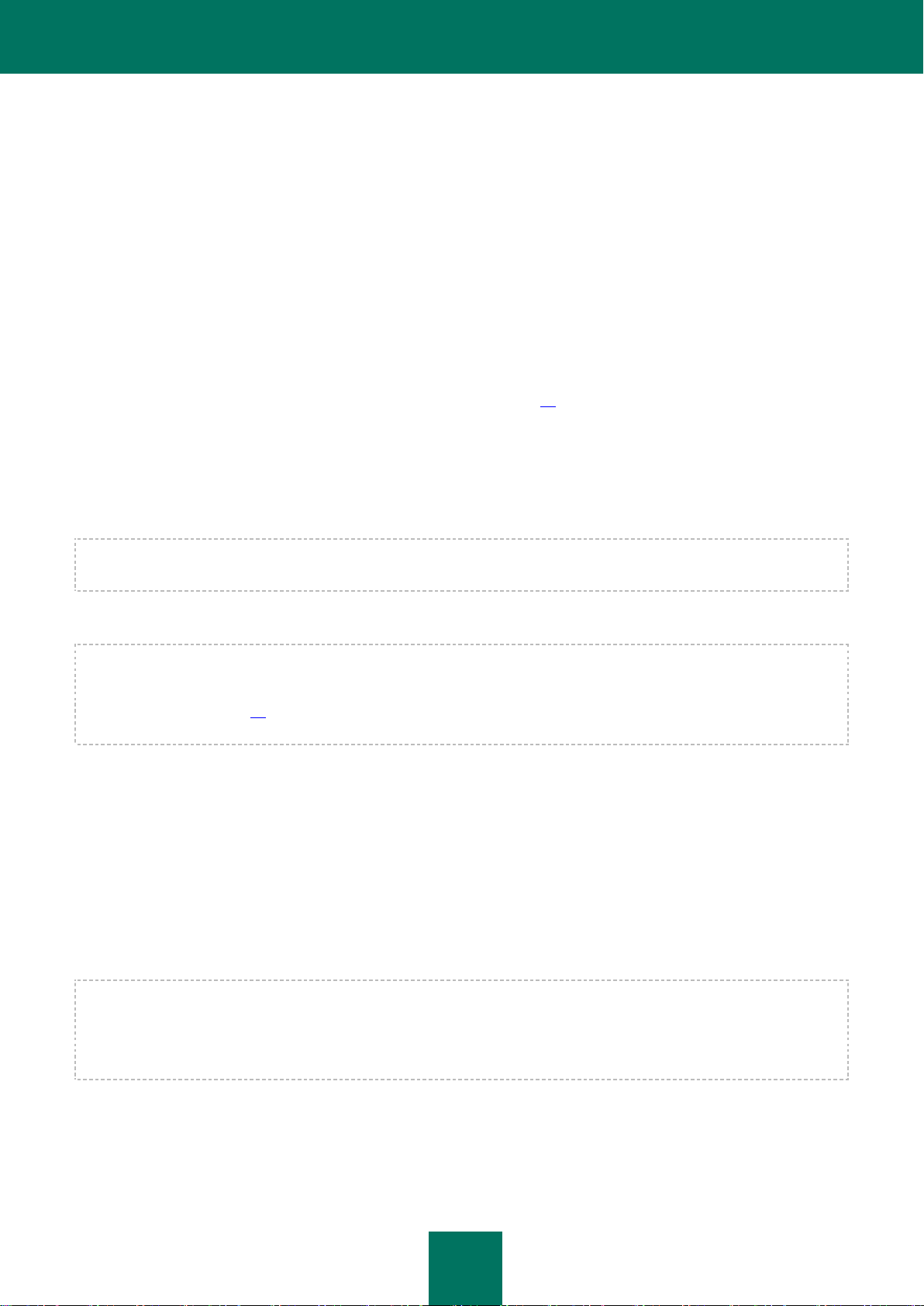
ANTI-VIRUS SERVER PROTECTION SCHEME
Kaspersky Anti-Virus protects replications and scans databases stored on the server. Server protection consists of the
following components: mail protection, replication protection, and database scanning.
Figure 1: Domino anti-virus server protection scheme
I M P L E M E N T A T I O N G U I D E
18
IN THIS SECTION
Application operation scheme ......................................................................................................................................... 18
Anti-virus scanning algorithm .......................................................................................................................................... 18
Attachment filtering algorithm .......................................................................................................................................... 19
Processing objects and actions performed on them ........................................................................................................ 20
APPLICATION OPERATION SCHEME
The application operation scheme provides for the following:
1. Control module receives information from the Domino server about an incoming message to the mail.box
service database on the protected server, or about an attempt to perform a replication on the protected server.
Control module sends an email message, or a document that was modified as a result of replication, to Email
and replication scan module.
2. Email and replication scan module scans the message or document and processes it in accordance with the
email or replication protection settings. The following actions are performed:
Scanned objects are selected. Email messages are divided into header, message body, attachments, and
OLE objects. In a document, fields in Rich Text format, attachments, and OLE objects are selected.
Attached objects are filtered (see section "Attachment filtering algorithm" on page 19) by size and (or) by
name.
Objects are scanned for threats (see section "Anti-virus scanning algorithm" on page 18).
Not infected objects are skipped, and other objects are processed according to the protection settings (see
section "Processing objects and actions performed on them" on page 20). A copy of an object can be saved
in the Quarantine database before it is processed.
Processed messages are sent to the Lotus Domino system for dispatch. Processed documents are stored
in the databases.
3. Control module sums up, in accordance with the settings for notifications about epidemics, the number of
infected, potentially infected and damaged objects detected when scanning email messages and the number of
objects containing an identical threat.
4. In accordance with the database scanning schedule or a manual command to begin scanning, the Control
module sends a command to the Database scan module to begin scanning. Database scan module
generates a list of scanned documents in accordance with the scan settings and then scans the documents
according to this list. The algorithm to scan documents is identical to the document scanning algorithm in the
Message and replication scan module.
ANTI-VIRUS SCANNING ALGORITHM
Kaspersky Anti-Virus analyzes objects sent for anti-virus scanning according to the following algorithm:
1. Objects are scanned on the basis of records in the anti-virus databases. Kaspersky Anti-Virus compares objects
with database records and determines whether they are harmful, to which category of dangerous programs they
belong, and which treatments can be applied to them.
A P P L I C A T I O N A R C H I T E C T U R E
19
The anti-virus databases contains descriptions of, and ways to neutralize, all types of potentially dangerous
programs that are known of when the anti-virus databases are created: malware, joke applications, potentially
dangerous applications, and programs that are not potentially harmful but that could be part of software to
develop harmful applications.
Incremental scanning is used to check objects – files are rescanned only when they are modified, that is, if the
date of the last revision precedes the date of the most recent scan, the file will not be scanned. Incremental
scanning can be disabled by setting the following variable: KAVNonIncrementalScan=1. By default, this variable
is not set.
Based on the scan results, the object is assigned one of the following statuses:
Not infected – The object does not contain any threats.
Object which cannot be disinfected – The object contains a threat that cannot be neutralized by using
current anti-virus databases; no remedy is available for such objects.
Disinfectable – The object contains a threat that can be neutralized by using current anti-virus
databases; after treatment the object will be assigned the "not infected" status.
Not scanned – Kaspersky Anti-Virus was unable to scan the object; the object can be a password-
protected archive or an archive compressed with an unknown algorithm, or the scan encountered an
error or timed out.
2. After being scanned by anti-virus databases, an object that is classified as not infected is then scanned by the
heuristic analyzer. Kaspersky Anti-Virus uses special mechanisms to analyze the activity of objects being
scanned in the system. If such activity is typical of harmful objects, the object will be classified as potentially
infected: This means that the object code contains either modified code from a known virus or code that
resembles a virus, but which has yet to be identified and described in Kaspersky Lab's anti-virus databases.
ATTACHMENT FILTERING ALGORITHM
Kaspersky Anti-Virus filters objects attached to email messages and documents. If an object satisfies the filter conditions,
it is assigned the status set by the filter values. No further anti-virus scans are carried out on the object. Objects are
processed according to the status assigned to them during filtering: Actions configured for objects of this status are
applied according to mail protection, replication protection and database scanning settings (see section "Processing
objects and actions performed on them" on page 20).
The application can apply the following filters to attachments:
Filter by size. Kaspersky Anti-Virus checks the size of attached objects. If the size of an object exceeds the
maximum value allowed, the object is assigned the status specified by the filter settings and is skipped by the
anti-virus scan. Objects that do not exceed the maximum size are sent to be scanned.
Filter by name. Kaspersky Anti-Virus checks the names of objects attached to a message. If the name of the
object satisfies the filter mask, the object is assigned the status specified by the filter settings and is skipped by
the scan. If the name of the object does not match any of the filter mask values, the object is sent for anti-virus
scanning.
If the protection settings are configured for both types of attachment filtering, Kaspersky Anti-Virus first scans the size of
the object. Next, if the size of the object is less than the value set in the filter settings, Kaspersky Anti-Virus scans the
name of the object. If the size of the object is more than the value set in the filter settings, Kaspersky Anti-Virus does not
scan the name of the object.
Based on the scan results, the object can be assigned one of the following statuses:
Not infected
Cannot be disinfected
Not scanned
I M P L E M E N T A T I O N G U I D E
20
Potentially infected
The attachment filter settings are configured in the mail protection, replication protection, and database scan settings for
each protection component individually.
PROCESSING OBJECTS AND ACTIONS PERFORMED ON THEM
Kaspersky Anti-Virus processes objects in accordance with the status assigned to them as a result of anti-virus scanning
(see section "Anti-virus scanning algorithm" on page 18) and filtering of attachments (see section "Attachment filtering
algorithm" on page 19). Not infected objects are returned without any modifications to the Lotus Domino server
databases (replication protection and database scanning) or to the Lotus Domino mail system (mail protection). The
following actions can be performed on the remaining objects:
Disinfect. Kaspersky Anti-Virus disinfects the object on the basis of information in the anti-virus databases
about the threat detected. The threat is neutralized and the object is classified as "not infected" and is stored in
the database by its source address or returned to the mail system. The action is only provided for disinfectable
objects.
Regardless of the application settings, OLE objects are disinfected by deleting only.
Skip. Kaspersky Anti-Virus passes the object without any modifications.
Delete. Kaspersky Anti-Virus deletes the object from a document or email message.
Actions to be performed by the application are defined separately for each status in the mail protection, replication
protection and database scanning settings.
A copy of an object can be saved in the Quarantine database before it is processed. Information about actions performed
can be stored in the Worklog and statistics database.
Kaspersky Anti-Virus can notify administrators and the senders and recipients of email messages (mail protection) about
detected objects and actions taken.
MANAGING KASPERSKY ANTI-VIRUS SETTINGS
Kaspersky Anti-Virus is managed by using the profile and server settings.
Profile is defined by the general settings for the group of servers in the profile. The profile mechanism provides
centralized control of the Kaspersky Anti-Virus settings.
A profile can include one or more servers. If Kaspersky Anti-Virus uses an isolated deployment scheme (see page 26),
the profile contains only one server.
Profiles can be used to configure all application settings, except the server license and Quarantine storage period. These
two settings are only for an individual server and are defined in the server settings. In addition, some server settings can
be redefined by the profile. This possibility allows values to be set for an individual server that correspond to the role of
the server in the anti-virus protection system and that differ from the values set in the profile. Among such server settings,
for example, are update settings, settings for saving information about events logged by Kaspersky Anti-Virus, and
statistical information.
Server documents are added to the profile automatically when Kaspersky Anti-Virus is installed on them. Server
documents are deleted from the profile automatically when the application is deleted. Only protected Kaspersky AntiVirus servers are included in the profile.
You can create and delete profiles. Servers with Kaspersky Anti-Virus installed on them can be moved from one profile to
another.
A P P L I C A T I O N A R C H I T E C T U R E
21
You can use profiles to set the Kaspersky Anti-Virus settings for a group of servers, for example, based on their
geographical location, functions or other factors. This makes it easier to manage the application if it is installed on several
servers and allows the anti-virus security status on all computers to be controlled centrally.
You can also use profiles to create a protection system with various levels of security, for example, for mail servers or
database servers. To do this, you can create several profiles with different settings. To assign a specified security level to
a server or group of servers, simply move the servers to the profile with the required settings.
You can use server settings to configure individual values corresponding to the functions of the server in the
organization's network. For example, the server settings can be used to configure a centralized scheme to update antivirus databases.
All information about the Kaspersky Anti-Virus settings is stored in the Control center database – kavcontrolcenter.nsf.
The Control center database is created in the staging directory of the Kaspersky Anti-Virus database when the
application is installed (by default, this is the kavdatabases directory). At the same time, a profile is created in the
database and the protected server is added. The profile and server settings are assigned the default values.
If Kaspersky Anti-Virus uses a distributed deployment scheme (see page 26), the kavcontrolcenter.nsf database contains
information about the operation of Kaspersky Anti-Virus on each of the servers on which the application is installed. A
database is created on one of these servers during installation and a replica of the existing Control center database is
created on each subsequent server. A database from one of the servers (selected by the administrator) on which
Kaspersky Anti-Virus is already installed is taken as a basis. The new protected server is added to the profile containing
the server from which the replica kavcontrolcenter.nsf database was created. The server settings are assigned the
default values. When Kaspersky Anti-Virus is deleted from one of the servers, information about this server is deleted
from the profile and from the Control center database.
If there is an isolated deployment scheme, the kavcontrolcenter.nsf database is placed on one server and contains
information about the configuration of this server only.
To configure and manage Kaspersky Anti-Virus, open the kavcontrolcenter.nsf database.
Rights to open the kavcontrolcenter.nsf database and configure and manage Kaspersky Anti-Virus are granted only to
authorized users from one of three functional groups: Security administrators, Control center administrators and
Administrators with limited privileges (see section "Managing permissions at the ACL level of the Kaspersky AntiVirus databases" on page 23). Before opening the database, make sure that the user account is authorized to perform
the required operations (create, delete, and configure profiles, configure servers, and so forth).
The kavcontrolcenter.nsf database can be opened on any of the protected servers using the Lotus Notes client or web
browser.
By default, changes to the profile and server settings are made to the database replica, which is located on the server to
which it is connected. During the replication process, any changes are distributed to all other protected servers. There
may be some delay before the new settings are applied. For this reason, the topology of the replications must be taken
into account when selecting the server on which to configure the settings.
If you are using Kaspersky Anti-Virus through a Lotus Notes clients, changes to the settings can be made to the Control
center database replica located on the server whose settings you are editing, regardless of which server is connected. In
this case, the new server settings will be applied much faster. When using a browser, the option of making changes to
the Control center replica is not supported and changes to the server settings are always made to the open replica.
The Control center database can be run simultaneously from several workstations or in parallel through a web browser
and Lotus Notes client. In such a case, a conflict in the replications could occur if the settings of a profile or server are
modified by two or more users simultaneously. In addition, it is not recommended to simultaneously modify the server
settings and the settings of the profile that contains the server. The server settings can be automatically redefined when
the new profile settings are applied.
I M P L E M E N T A T I O N G U I D E
22
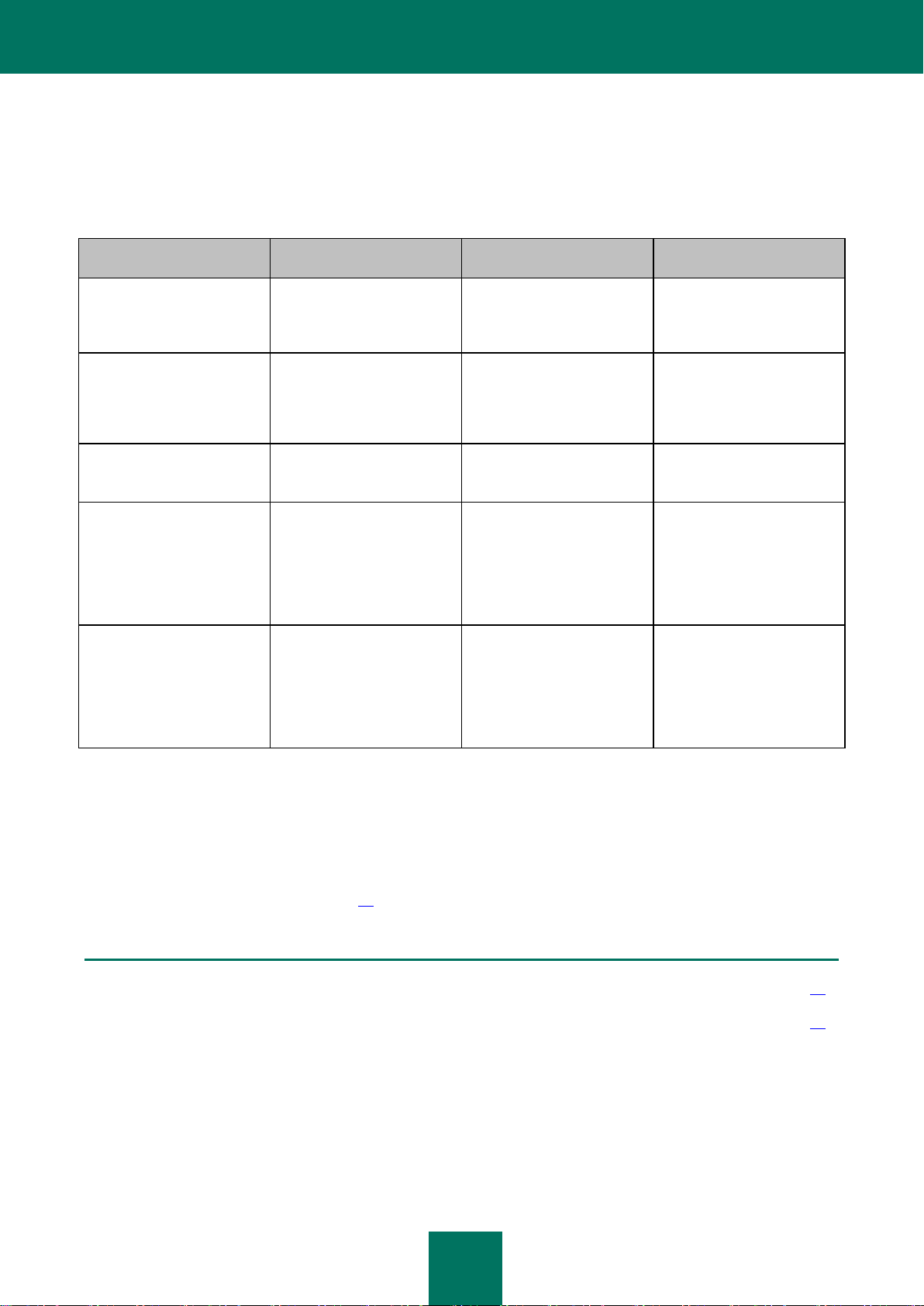
CONFIGURING THE DOMINO SERVER SECURITY SETTINGS
SECURITY SETTINGS
SETUP
WORK CYCLE
DELETION
Using a remote Domino
server
Sending console
commands to the primary
and secondary setup
server.
Sending console
commands to any server
using a common Control
center replica.
Automatically rebooting the
Domino server before
deleting service data.
Creating databases and
database templates
Creating a database of
templates with a server,
used to sign the design of
the Installing Kaspersky
Anti-Virus database.
Not required.
Not required.
Creating database replicas
Creating a database replica
with the primary and
secondary setup server.
Not required.
Not required.
Performing unrestricted
methods and operations
Background agents use run
commands with the server
file system: create
directories, view directory
contents, call external
server-side applications,
handle RichText content.
Background agents use run
commands with the server
file system: create
directories, view directory
contents, call external
server-side applications,
handle RichText content.
Background agents use run
commands with the server
file system: create
directories, view directory
contents, call external
server-side applications,
handle RichText content.
Trusted servers
Background agents of the
secondary setup server
refer to the primary setup
server database.
Server background agents
refer to database of any
other server using a
common Control center
replica.
The agent refers to the
Installing Kaspersky AntiVirus database of the
secondary setup server and
to the Control center
database of the primary
setup server.
IN THIS SECTION
Managing permissions at the ACL level of the Kaspersky Anti-Virus databases ................................ ............................. 23
Managing permissions at the level of profile and server settings .................................................................................... 25
In order to correctly run, install and delete Kaspersky Anti-Virus, you need to configure the Domino server security
settings as specified in the table.
Table 1. List of Domino server security settings
MANAGING USER PERMISSIONS
User permissions are managed at the ACL level of the Kaspersky Anti-Virus databases and at the level of individual
documents (profile settings and server settings). Permissions at the ACL level are granted through functional groups.
Permissions set at the document level are granted through functional roles (see section "Managing permissions at the
level of profile and server settings" on page 25).
A P P L I C A T I O N A R C H I T E C T U R E
23
IN THIS SECTION
Functional group permissions .......................................................................................................................................... 23
Granting functional group permissions to users .............................................................................................................. 24
FUNCTIONAL
GROUPS
CONTROL CENTER
DATABASE
WORKLOG AND
STATISTICS
DATABASE
QUARANTINE
DATABASE
HELP DATABASE
SECURITY
ADMINISTRATORS
Manager access level
with rights to create,
delete, replicate, and
copy documents.
AppAdmin role.
Manager access
level with rights to
create, delete,
replicate, and copy
documents.
Manager access
level with rights to
create, delete,
replicate, and copy
documents.
Manager access level.
CONTROL CENTER
ADMINISTRATORS
Author access level
with rights to create,
delete, replicate, and
copy documents.
AppAdmin role.
Author access level
with rights to create,
delete, replicate, and
copy documents.
Author access level
with rights to create,
delete, replicate, and
copy documents.
Reader access level.
ADMINISTRATORS
WITH LIMITED
PRIVILEGES
Author access level
with the right to
replicate or copy
documents.
Author access level
with the right to
replicate or copy
documents.
Author access level
with the right to
replicate or copy
documents.
Reader access level.
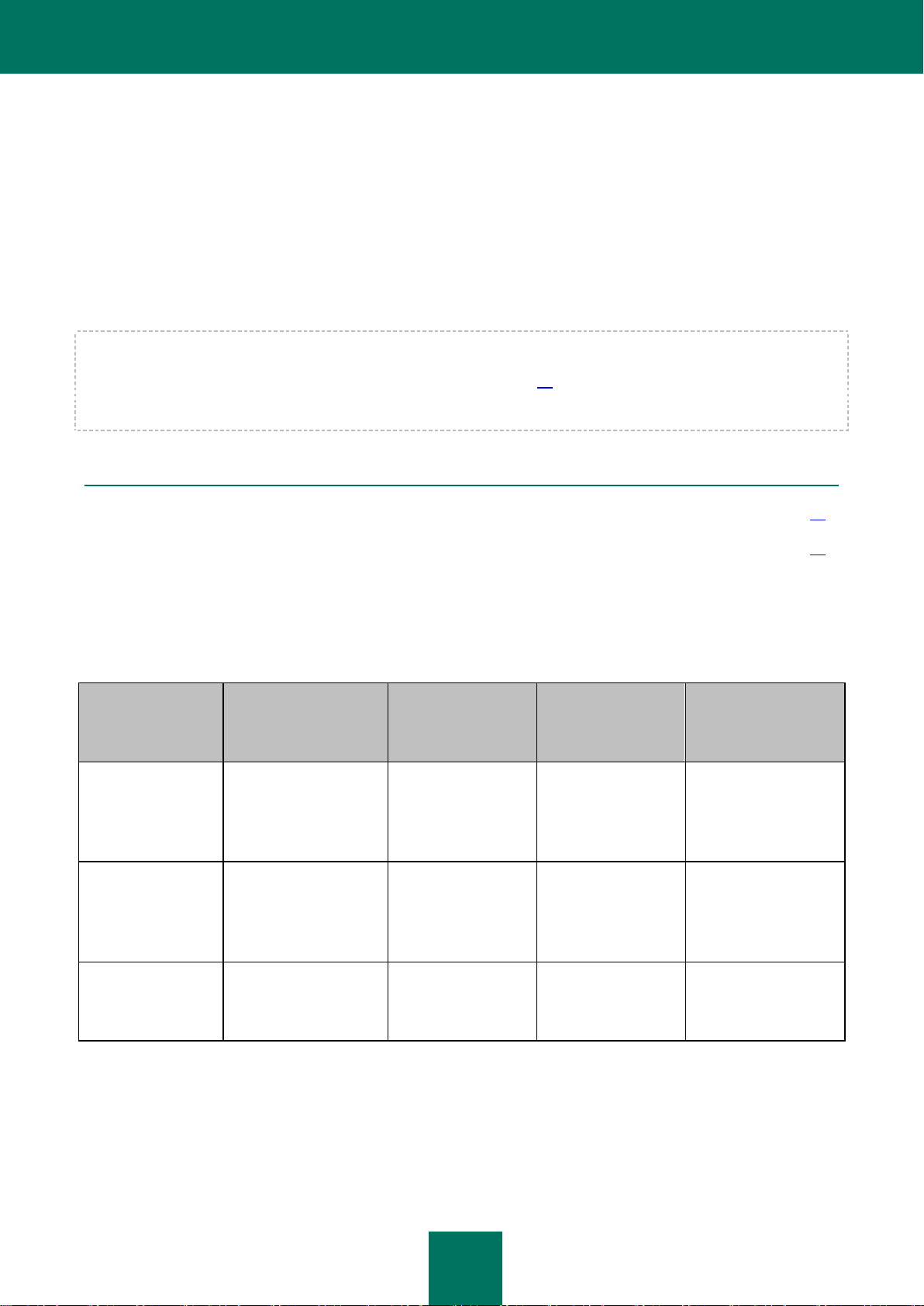
MANAGING PERMISSIONS AT THE ACL LEVEL OF THE KASPERSKY
ANTI-VIRUS DATABASES
To grant permissions at the ACL level of the Kaspersky Anti-Virus databases, the application provides three functional
groups: Security administrators, Control center administrators and Administrators with limited privileges.
The composition of each functional group is defined during installation. The administrator who installs the application
creates the functional groups by selecting users and (or) user groups from the Address Book of the Domino server.
During installation the elements of each functional group are automatically included in the ACL of the Kaspersky AntiVirus Lotus Notes databases.
The ACL of the Kaspersky Anti-Virus databases also includes the Default and Anonymous records and the servers on
which the application is installed. Servers to be included in the ACL are specified by the administrator during installation
of the application (see "Step 3. Configuring installation settings" on page 37). The servers are assigned the Manager
access level with rights to create, delete, replicate and copy documents. The No access level is set for the Default and
Anonymous records in the ACL of the Kaspersky Anti-Virus databases.
FUNCTIONAL GROUP PERMISSIONS
The permissions of the functional groups in the ACL of the Kaspersky Anti-Virus databases are listed in the table below.
After Kaspersky Anti-Virus is installed, users and user groups included in the functional groups are granted the
permissions required to use the application.
Table 2. Functional group permissions
Users included in the Security administrators group have the maximum number of permissions in Kaspersky Anti-Virus
and can perform the following actions:
Managing permissions at the ACL level of the Kaspersky Anti-Virus databases

I M P L E M E N T A T I O N G U I D E
24
Creating and deleting profiles
Editing the settings of all profiles and servers
Deleting records from Quarantine and Worklog and statistics databases
Users included in the Control center administrators group can perform the following actions in Kaspersky Anti-Virus:
Creating and deleting profiles
Editing the settings of all profiles and servers
Deleting records from the Quarantine and Worklog and statistics databases
By default, users included in the Administrators with limited privileges group do not have the right to edit profile and
server settings or to delete records from the Quarantine and Worklog and statistics databases. Users are granted the
rights needed to use the application through functional roles (see section "Managing permissions at the level of profile
and server settings" on page 25).
Users in all three functional groups have the right to view records in the Quarantine, Worklog and statistics, and Help
databases.
GRANTING FUNCTIONAL GROUP PERMISSIONS TO USERS
When installing Kaspersky Anti-Virus, the administrator can include both individual Domino users and user groups in the
three functional groups.
To simplify the procedure for granting permissions, it is recommended that you include in the functional groups not
individual users, but groups created in the Address book of the Domino server (see section "Creating a group of users for
granting permissions" on page 32). During installation these groups are included in the ACL of the Kaspersky Anti-Virus
databases and are assigned functional group permissions (see section "Functional group permissions" on page 2323).
The Domino server administrator can subsequently grant permissions to users or restrict them by modifying the groups in
the Address Book (including or excluding users).
If during installation of the application only individual users, not user groups, are included in the functional groups, the
ACL of all the Kaspersky Anti-Virus databases will need to be edited manually to manage the permissions. To deny a
user functional group permissions, the user account must be deleted from the ACL of all the Kaspersky Anti-Virus
databases. To grant a user functional group permissions, the user account must be included in the ACL of all databases.
The ACL of the Kaspersky Anti-Virus databases can only be modified by users with permissions belonging to the
Security administrators functional group.
It is recommended that user accounts in the ACL of the Kaspersky Anti-Virus databases be included in the group.
To grant a user functional group permissions:
1. Create in the Address book of the Domino server a group with a unique name, for example,
ControlCenterAdmins.
2. To this group add the user to be granted the permissions of a particular functional group, for example, the
Control center administrators group.
3. Log on to the system under a user account with the permissions of the Security administrators functional
group.
4. Add the ControlCenterAdmins group to the ACL of the Kaspersky Anti-Virus databases (Control center, Worklog
and statistics, Quarantine, and Information) and define the permissions for the ControlCenterAdmins group to
match those of the Control center administrators functional group (see section "Functional group permissions"
on page 23).

A P P L I C A T I O N A R C H I T E C T U R E
25
MANAGING PERMISSIONS AT THE LEVEL OF PROFILE AND SERVER
SETTINGS
To restrict access to the application at the level of individual documents (profile and server settings), the following
functional roles are provided:
Profile administrator – Has the rights to perform the following actions:
Editing the profile settings and the settings of all servers in the profile
Deleting records from the Quarantine and Worklog and statistics databases for servers in the profile
Server administrator – Has the rights to perform the following actions:
Editing the server settings, including moving a server to another profile
Deleting records from the Quarantine and Worklog and statistics databases for the server
Profile and server administrators are assigned after the application is installed. The assignment is carried out for each
server and profile separately.
Only users with permissions from one of the three functional groups can be assigned as Profile administrator and Server
administrator.
By default, users and (or) user groups included in the Control center administrators functional group during installation
are specified as administrators in the profile and server settings.
Users from the Security administrators and Control center administrators functional groups are granted the right to
edit the settings of all servers and profiles, regardless of their functional role. To grant restricted permissions, for
example, to edit the settings of only one profile / server, users from the Administrators with limited privileges
functional group should be assigned as profile / server administrators. Users from this group are granted the right to edit
the settings of only the profiles / servers for which they have been assigned as administrators. A user from this group who
is assigned as a profile administrator is also granted the right to edit the settings of all servers in this profile.

26
TYPICAL DEPLOYMENT SCHEMES
IN THIS SECTION
Distributed deployment scheme ...................................................................................................................................... 26
Isolated deployment scheme ................................................................ ................................................................ ........... 27
This chapter contains a description of the deployment schemes in Kaspersky Anti-Virus.
The following deployment options are provided:
Isolated deployment scheme – Kaspersky Anti-Virus is installed in isolated on several servers. In this case, the
databases of Kaspersky Anti-Virus are deployed autonomously on each server.
Distributed deployment scheme – Kaspersky Anti-Virus is installed on several Domino servers and all installed
copies of Kaspersky Anti-Virus represent a single distributed system.
If the network contains several Domino servers, or a cluster of servers, it is recommended that Kaspersky Anti-Virus be
installed on each server and use a distributed deployment scheme.
Server partitioning is not supported.
Kaspersky Anti-Virus is installed for each server separately.
If Kaspersky Anti-Virus uses a distributed deployment scheme (see section "Distributed deployment scheme" on
page 26), an Primary setup is carried out first. The server on which the application is first installed is called the primary
setup server. Kaspersky Anti-Virus is then installed on the additional servers.
The Kaspersky Anti-Virus databases are created on the primary setup server. The configuration and databases are
subsequently replicated on the additional servers. During installation of each consecutive additional server, any of the
servers on which Kaspersky Anti-Virus is already installed can be selected as the primary setup server.
If the Domino network uses a star topology for replications, it is recommended that the central hub server be selected as
the primary setup server.
If an isolated deployment scheme is used, primary setup of Kaspersky Anti-Virus is carried out on each Domino server
(see section "Isolated deployment scheme" on page 27).
DISTRIBUTED DEPLOYMENT SCHEME
The distributed deployment scheme in Kaspersky Anti-Virus includes the following stages:
1. Preparing for installation. Before installing Kaspersky Anti-Virus, do the following:
Delete any previous version of Kaspersky Anti-Virus and other anti-virus programs for Lotus Notes/Domino
from each server on which the application will be installed (see section "Deleting the previous version of
Kaspersky Anti-Virus and other anti-virus programs for Lotus Notes/Domino" on page 30).
Set permissions for the user performing the installation (see section "Setting permissions for the user
performing the installation" on page 30).
In the Address book of the primary setup server, create a group of servers on which Kaspersky Anti-Virus is
to be installed (see section "Creating a group of installation servers in the Address book" on page 31).

T Y P I C A L D E P L O Y M E N T S C H E M E S
27
Set permissions for each server on which the application will be installed (see section "Setting server
permissions" on page 31).
In the Address book of the server, create a group of Domino users to be granted permissions to use the
application (see section "Creating a group of users for granting permissions" on page 32).
Move the installation database to the data directory of each Domino server on which the application will be
installed and sign it (see section "Preparing an installation database" on page 32).
Configure the security settings on the workstation, if the installation is performed through a Lotus Notes
client (see section "Configuring security settings for the Lotus Notes client" on page 33).
2. Primary setup on a server (see section "Primary setup: configuring settings" on page 38).
3. Installation on an additional server – consecutively for each additional server (see section "Primary setup:
configuring settings" on page 38).
Additional servers must be accessible to the primary setup server.
4. Preparing for operation. Before you start using the application, do the following:
Configure the security settings for each workstation on which Kaspersky Anti-Virus will run (see section
"Preparing for operation" on page 45).
Activate the license to run the application on each server where Kaspersky Anti-Virus is installed, if it was
activated during the installation process (see Administrator's Guide).
ISOLATED DEPLOYMENT SCHEME
The isolated deployment scheme in Kaspersky Anti-Virus includes the following stages:
1. Preparing for installation. Before installing Kaspersky Anti-Virus, do the following:
Delete any previous version of Kaspersky Anti-Virus and other anti-virus programs for Lotus Notes/Domino
from each server on which the application will be installed (see section "Deleting the previous version of
Kaspersky Anti-Virus and other anti-virus programs for Lotus Notes/Domino" on page 30).
Set permissions for the user performing the installation (see section "Setting permissions for the user
performing the installation" on page 30).
In the Address book, create a group of servers on which Kaspersky Anti-Virus is to be installed (see section
"Creating a group of installation servers in the Address book" on page 31).
Set permissions for each server on which the application will be installed (see section "Setting server
permissions" on page 31).
In the Address book of the installation servers, create a group of Domino users to be granted permissions to
use the application (see section "Creating a group of users for granting permissions" on page 32).
Move the installation database to the data directory of each Domino server on which the application will be
installed and sign it (see section "Preparing an installation database" on page 32).
Configure the security settings on the workstation, if the installation is performed through a Lotus Notes
client (see section "Configuring security settings for the Lotus Notes client" on page 33).
2. Primary setup on a server – consecutively for all servers on which Kaspersky Anti-Virus is to be installed (see
section "Primary setup: configuring settings" on page 38).
3. Preparing for operation. Before you start using Kaspersky Anti-Virus, do the following:

I M P L E M E N T A T I O N G U I D E
28
Configure the security settings for each workstation on which Kaspersky Anti-Virus will run (see section
"Preparing for operation" on page 45).
Activate the license to run the application on each server where Kaspersky Anti-Virus is installed, if it was
activated during the installation process (see Administrator's Guide).
 Loading...
Loading...